90964feb0ef7c19af4a935ada0ae5cdb.ppt
- Количество слайдов: 32
 Next Generation Controllers January 2013 Next Generation Security Solutions
Next Generation Controllers January 2013 Next Generation Security Solutions
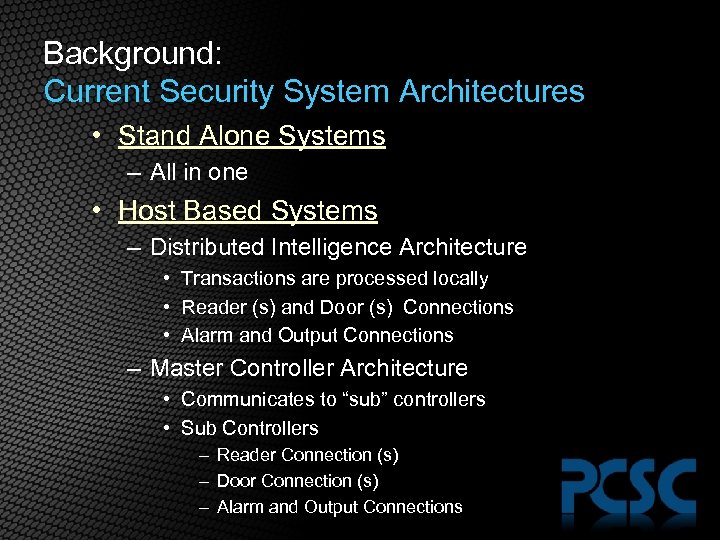 Background: Current Security System Architectures • Stand Alone Systems – All in one • Host Based Systems – Distributed Intelligence Architecture • Transactions are processed locally • Reader (s) and Door (s) Connections • Alarm and Output Connections – Master Controller Architecture • Communicates to “sub” controllers • Sub Controllers – Reader Connection (s) – Door Connection (s) – Alarm and Output Connections
Background: Current Security System Architectures • Stand Alone Systems – All in one • Host Based Systems – Distributed Intelligence Architecture • Transactions are processed locally • Reader (s) and Door (s) Connections • Alarm and Output Connections – Master Controller Architecture • Communicates to “sub” controllers • Sub Controllers – Reader Connection (s) – Door Connection (s) – Alarm and Output Connections
 Background: Distributed Intelligence System Architecture
Background: Distributed Intelligence System Architecture
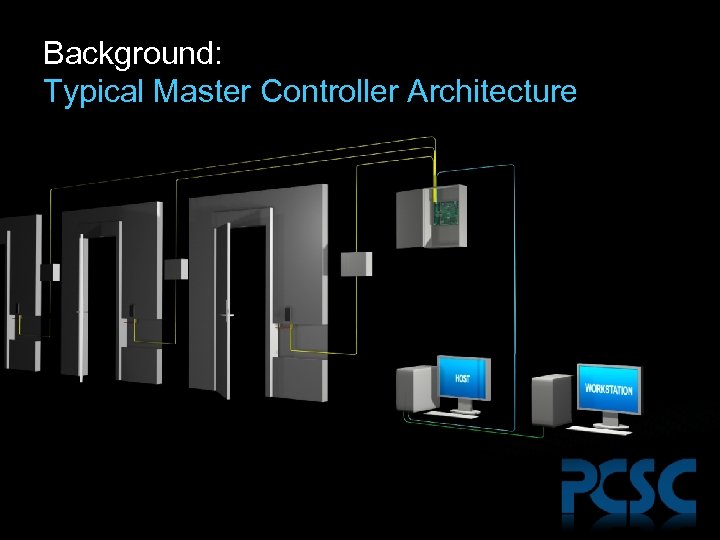 Background: Typical Master Controller Architecture
Background: Typical Master Controller Architecture
 Distributed Intelligence Architecture Typical Security Architecture Partial Failure
Distributed Intelligence Architecture Typical Security Architecture Partial Failure
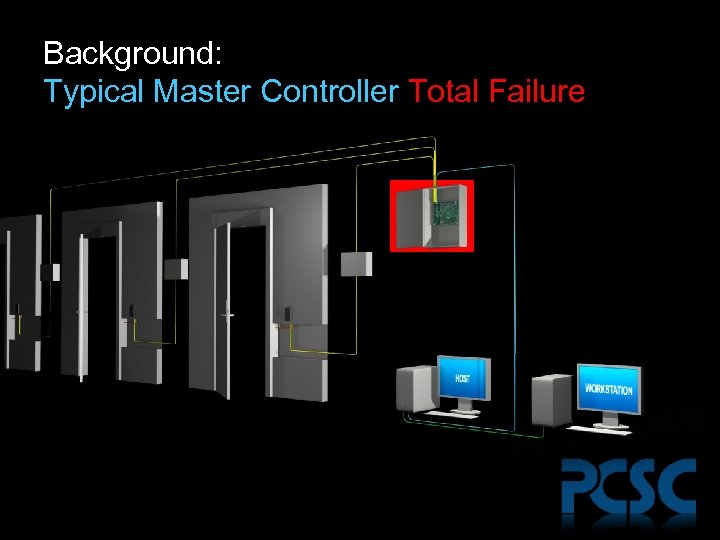 Background: Typical Master Controller Total Failure
Background: Typical Master Controller Total Failure
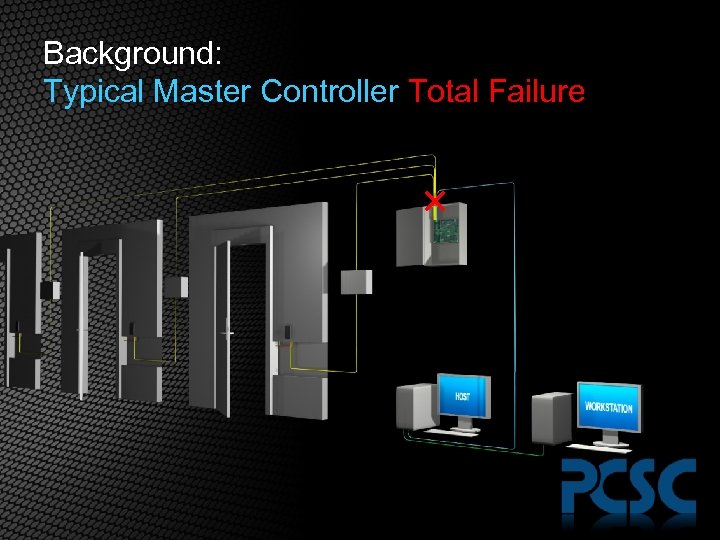 Background: Typical Master Controller Total Failure
Background: Typical Master Controller Total Failure
 Summary • Current Systems have a vulnerability – Partial or Total Depending on the Architecture • Controller Failure – Everything within the controls are affected • Distributed Intelligence has the least impact • Master Controller Architecture has Total Failure • Communication is a point of Vulnerability
Summary • Current Systems have a vulnerability – Partial or Total Depending on the Architecture • Controller Failure – Everything within the controls are affected • Distributed Intelligence has the least impact • Master Controller Architecture has Total Failure • Communication is a point of Vulnerability
 Introducing: The Next Logical Evolution of Systems…
Introducing: The Next Logical Evolution of Systems…
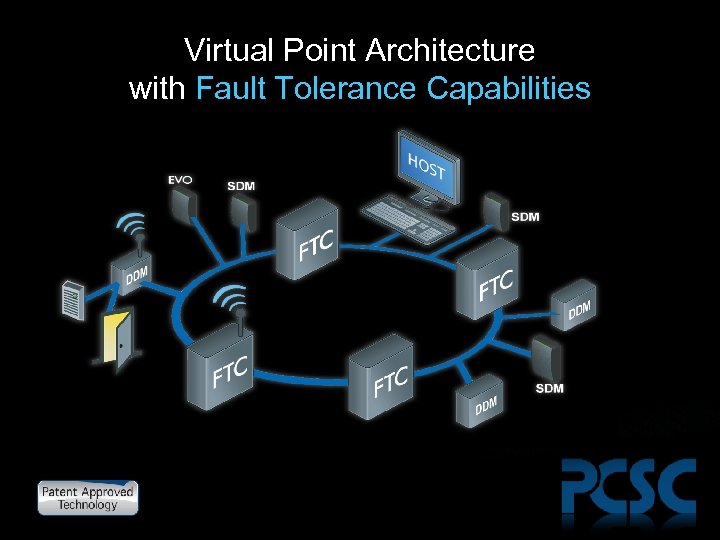 Virtual Point Architecture with Fault Tolerance Capabilities
Virtual Point Architecture with Fault Tolerance Capabilities
 Fault Tolerance Architecture Is a means of System Recovery utilizing “Automated System Reconfiguration” provided through Dynamic Network Architecture (DNA) with little or no impact on system security or operations upon a failure within any of the components of the system.
Fault Tolerance Architecture Is a means of System Recovery utilizing “Automated System Reconfiguration” provided through Dynamic Network Architecture (DNA) with little or no impact on system security or operations upon a failure within any of the components of the system.
 Fault Tolerant Architecture • Eliminates “Single Point of Failure” • Ability to Automatically “Recover” upon failure due to: – Primary or Secondary Communication Failure – Hardware Failure of a FTC (s) – Firmware Failure • Real-time Dynamic Network Architecture – Automatically “takes” over the duties of a failed FTC • Provide 100% Distributed Intelligence – Real-time decisions are made by the FTC • Hydra Protocol – FTC Network Administrator – Peer to Peer – Database Management • Eliminates System Failure!!! • Eliminates “Emergency Calls”
Fault Tolerant Architecture • Eliminates “Single Point of Failure” • Ability to Automatically “Recover” upon failure due to: – Primary or Secondary Communication Failure – Hardware Failure of a FTC (s) – Firmware Failure • Real-time Dynamic Network Architecture – Automatically “takes” over the duties of a failed FTC • Provide 100% Distributed Intelligence – Real-time decisions are made by the FTC • Hydra Protocol – FTC Network Administrator – Peer to Peer – Database Management • Eliminates System Failure!!! • Eliminates “Emergency Calls”
 FT Architecture Components • Host System (Li. NC-NXG, Plus, XS, EBI*) • Fault Tolerant Controller (FTC) – Supports 16 -32 DIM (Door Interface Modules) – 100% Distributed Intelligence – Global I/O – Global Entry-Exit • Door Interface Modules – DDM – 2 Reader Controller – SDM – 1 Reader Controller
FT Architecture Components • Host System (Li. NC-NXG, Plus, XS, EBI*) • Fault Tolerant Controller (FTC) – Supports 16 -32 DIM (Door Interface Modules) – 100% Distributed Intelligence – Global I/O – Global Entry-Exit • Door Interface Modules – DDM – 2 Reader Controller – SDM – 1 Reader Controller
 Fault Tolerant Architecture Powered by Hydra
Fault Tolerant Architecture Powered by Hydra
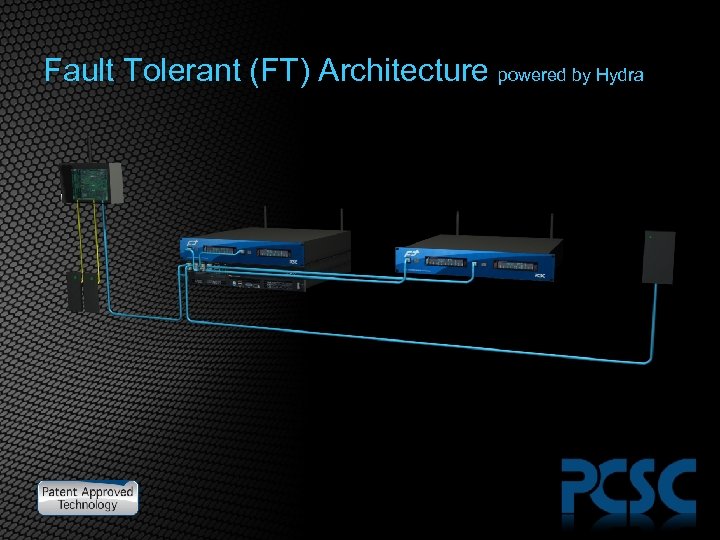 Fault Tolerant (FT) Architecture powered by Hydra
Fault Tolerant (FT) Architecture powered by Hydra
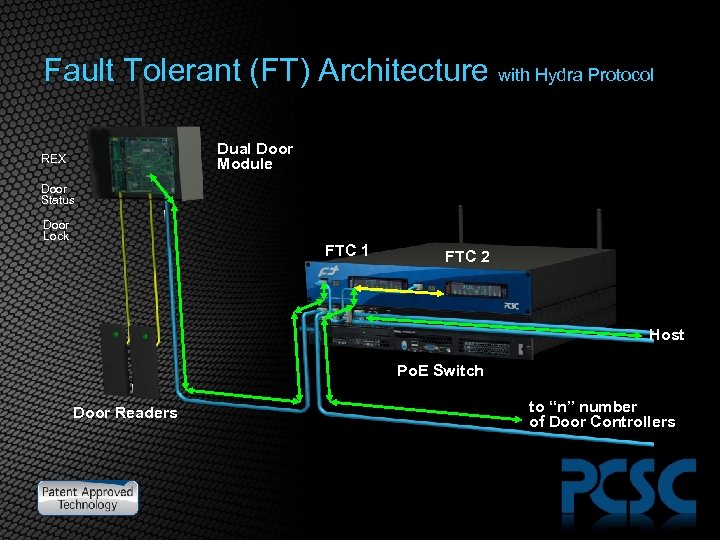 Fault Tolerant (FT) Architecture with Hydra Protocol Dual Door Module REX Door Status Door Lock FTC 1 FTC 2 Host Po. E Switch Door Readers to “n” number of Door Controllers
Fault Tolerant (FT) Architecture with Hydra Protocol Dual Door Module REX Door Status Door Lock FTC 1 FTC 2 Host Po. E Switch Door Readers to “n” number of Door Controllers
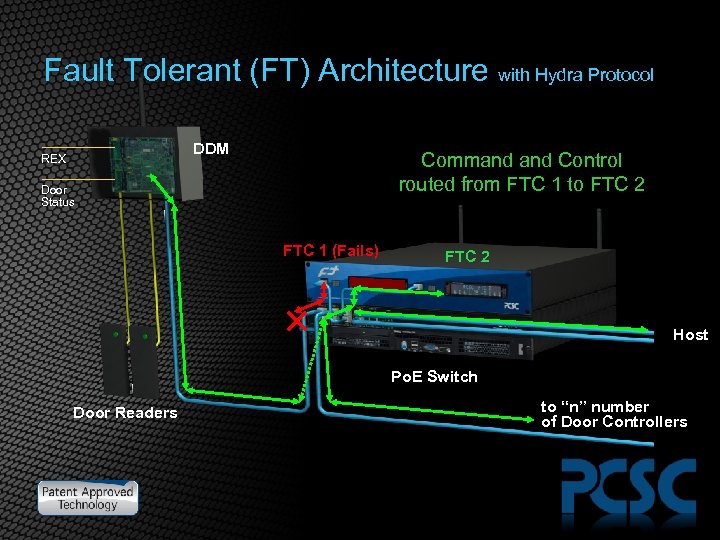 Fault Tolerant (FT) Architecture with Hydra Protocol DDM REX Command Control routed from FTC 1 to FTC 2 Door Status FTC 1 (Fails) FTC 2 Host Po. E Switch Door Readers to “n” number of Door Controllers
Fault Tolerant (FT) Architecture with Hydra Protocol DDM REX Command Control routed from FTC 1 to FTC 2 Door Status FTC 1 (Fails) FTC 2 Host Po. E Switch Door Readers to “n” number of Door Controllers
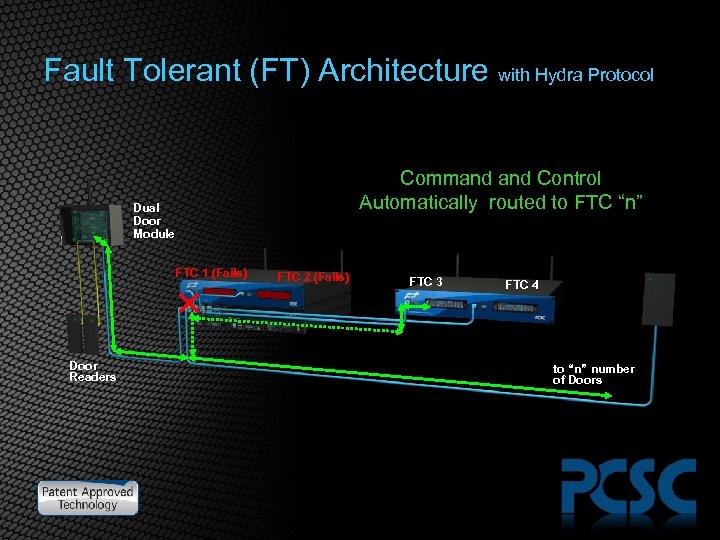 Fault Tolerant (FT) Architecture with Hydra Protocol Command Control Automatically routed to FTC “n” Dual Door Module FTC 1 (Fails) Door Readers FTC 2 (Fails) FTC 3 FTC 4 to “n” number of Doors
Fault Tolerant (FT) Architecture with Hydra Protocol Command Control Automatically routed to FTC “n” Dual Door Module FTC 1 (Fails) Door Readers FTC 2 (Fails) FTC 3 FTC 4 to “n” number of Doors
 Communication Routing Architecture Utilizing Secondary or Tertiary Paths
Communication Routing Architecture Utilizing Secondary or Tertiary Paths
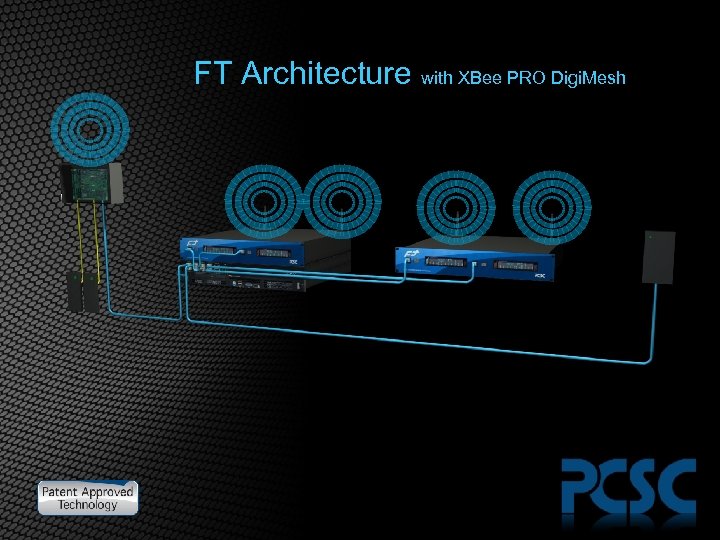 FT Architecture with XBee PRO Digi. Mesh
FT Architecture with XBee PRO Digi. Mesh
 XBee Pro Digi. Mesh • Wireless Communication • Approved for use in “All Countries” • 100 meters within buildings – Over 1 K meters line of site communication • Auto setup of Mesh Network • Uses other XBee Pro devices as relay points • More XBee Pro Devices, more Robust
XBee Pro Digi. Mesh • Wireless Communication • Approved for use in “All Countries” • 100 meters within buildings – Over 1 K meters line of site communication • Auto setup of Mesh Network • Uses other XBee Pro devices as relay points • More XBee Pro Devices, more Robust
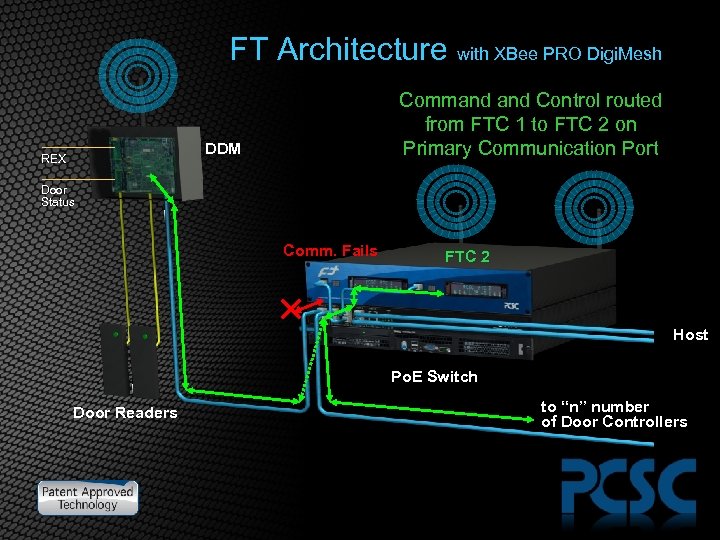 FT Architecture with XBee PRO Digi. Mesh Command Control routed from FTC 1 to FTC 2 on Primary Communication Port DDM REX Door Status Comm. Fails FTC 2 Host Po. E Switch Door Readers to “n” number of Door Controllers
FT Architecture with XBee PRO Digi. Mesh Command Control routed from FTC 1 to FTC 2 on Primary Communication Port DDM REX Door Status Comm. Fails FTC 2 Host Po. E Switch Door Readers to “n” number of Door Controllers
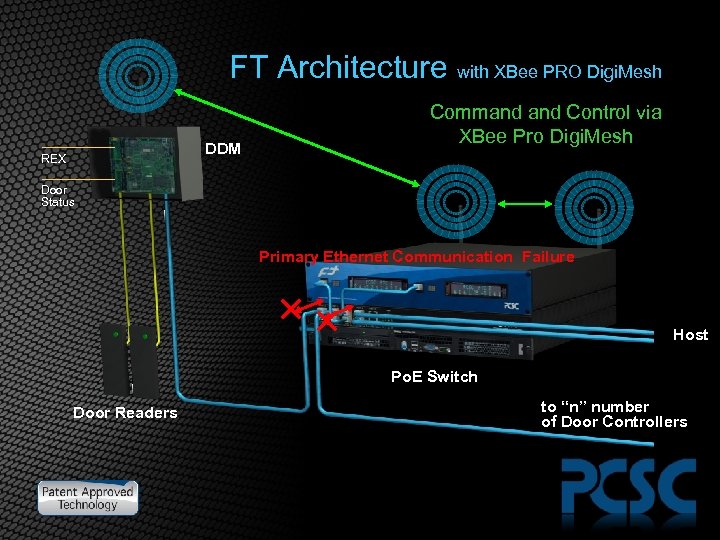 FT Architecture with XBee PRO Digi. Mesh DDM REX Command Control via XBee Pro Digi. Mesh Door Status Primary Ethernet Communication Failure Host Po. E Switch Door Readers to “n” number of Door Controllers
FT Architecture with XBee PRO Digi. Mesh DDM REX Command Control via XBee Pro Digi. Mesh Door Status Primary Ethernet Communication Failure Host Po. E Switch Door Readers to “n” number of Door Controllers
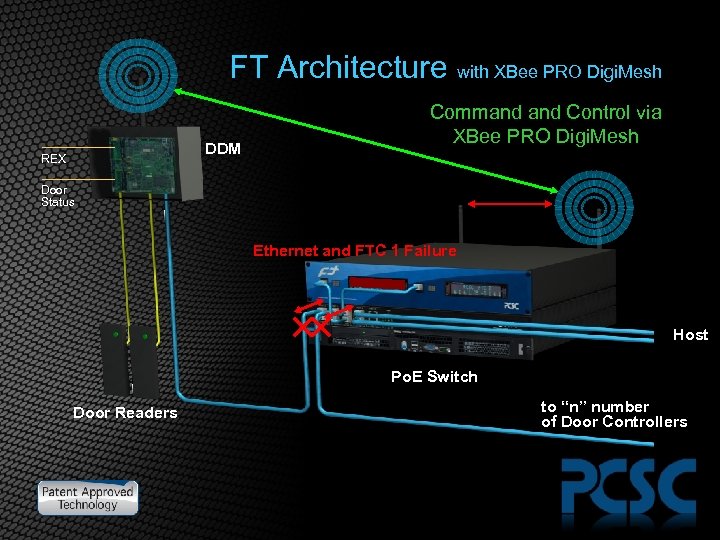 FT Architecture with XBee PRO Digi. Mesh DDM REX Command Control via XBee PRO Digi. Mesh Door Status Ethernet and FTC 1 Failure Host Po. E Switch Door Readers to “n” number of Door Controllers
FT Architecture with XBee PRO Digi. Mesh DDM REX Command Control via XBee PRO Digi. Mesh Door Status Ethernet and FTC 1 Failure Host Po. E Switch Door Readers to “n” number of Door Controllers
 Fault Tolerant Controller (FTC) • 32 Bit RISC Technology • Open Systems Operating System – Linux • Communication – Ethernet (Primary) – Ethernet or Po. E (Primary or Secondary) – Wireless - XBee PRO Digi. Mesh (Tertiary) • 7 Segment Real-Time Status Display • VFD Status Display (optional FTC only) – Clique Communication and Status Information
Fault Tolerant Controller (FTC) • 32 Bit RISC Technology • Open Systems Operating System – Linux • Communication – Ethernet (Primary) – Ethernet or Po. E (Primary or Secondary) – Wireless - XBee PRO Digi. Mesh (Tertiary) • 7 Segment Real-Time Status Display • VFD Status Display (optional FTC only) – Clique Communication and Status Information
 Fault Tolerant Controller Capabilities • FTC – 100% Distributed Intelligence • • All Real-time Decisions All Card Database Global Anti-Passback (No Host) Global Input/Output Linking (No Host) – “Hydra” Protocol • Peer to Peer – Host to FTC, FTC to DDM and SDM • • FTC Network Administrator Database Management and Synchronization Communication Path Management Firmware Administrator – Supervised Tamper protection – CEPAS Card Support – 100% TWIC, PIV and FIPS Capable (HSPD Government Regulations)
Fault Tolerant Controller Capabilities • FTC – 100% Distributed Intelligence • • All Real-time Decisions All Card Database Global Anti-Passback (No Host) Global Input/Output Linking (No Host) – “Hydra” Protocol • Peer to Peer – Host to FTC, FTC to DDM and SDM • • FTC Network Administrator Database Management and Synchronization Communication Path Management Firmware Administrator – Supervised Tamper protection – CEPAS Card Support – 100% TWIC, PIV and FIPS Capable (HSPD Government Regulations)
 FTC Capacities • Cardholders – 20, 000 – 250, 000+ – 12 or 24 Digit Card Numbers • Compatible with any card standards • CEPAS, PIV, TWIC, etc. • History Transactions – 20, 000 – 250, 000+ History Transactions • 1 Year of Holidays
FTC Capacities • Cardholders – 20, 000 – 250, 000+ – 12 or 24 Digit Card Numbers • Compatible with any card standards • CEPAS, PIV, TWIC, etc. • History Transactions – 20, 000 – 250, 000+ History Transactions • 1 Year of Holidays
 Dual Door Module (DDM) • 32 Bit RISC Technology • Open Systems Operating System – Linux • Communication – Ethernet (Primary) – Ethernet or Po. E (Secondary) – Wireless - XBee PRO Digi. Mesh (Tertiary) • 5 State Supervised Monitoring – A/D Sense Input Technology – Supervised Readers – Automatic Calibration for Cable Distance and Size • Hydra Protocol
Dual Door Module (DDM) • 32 Bit RISC Technology • Open Systems Operating System – Linux • Communication – Ethernet (Primary) – Ethernet or Po. E (Secondary) – Wireless - XBee PRO Digi. Mesh (Tertiary) • 5 State Supervised Monitoring – A/D Sense Input Technology – Supervised Readers – Automatic Calibration for Cable Distance and Size • Hydra Protocol
 Single Door Module (SDM) • SDM – All in One (Controller and Reader, shown) – Controller Only • Power over Ethernet (Po. E) – Single Communication Port SDM -ERP 40 • Supports - One Reader • REX, Door Status, Lock Output for 1 door • Hydra Protocol
Single Door Module (SDM) • SDM – All in One (Controller and Reader, shown) – Controller Only • Power over Ethernet (Po. E) – Single Communication Port SDM -ERP 40 • Supports - One Reader • REX, Door Status, Lock Output for 1 door • Hydra Protocol
 Advantages to “FT Architecture” • • World’s Most Reliable Security System Active/Active and Active/Passive Topologies No Degradation of system performance No Degradation during routine maintenance “Failures” are not an immediate Emergency Automated Firmware Authentication and Updates Authentication Protocol PCSC is the Only Provider of FT systems – Patented – Competitive Edge
Advantages to “FT Architecture” • • World’s Most Reliable Security System Active/Active and Active/Passive Topologies No Degradation of system performance No Degradation during routine maintenance “Failures” are not an immediate Emergency Automated Firmware Authentication and Updates Authentication Protocol PCSC is the Only Provider of FT systems – Patented – Competitive Edge
 Fault Tolerant Controller Features • All the Features of IQ/SIM/ULT series Controllers • Increase Authorization Groups per Cardholder to 12 (4) • Global Entry/Exit – Timed Anti-Passback • Global I/O • Card Activation and De-Activation – Date and Time • “Stale Cards” Access Denial – “Short” and “Long Term” Values • Enterprise Cards, Vacation, etc. . • Escort Definition by Cardholder and Reader • Security Threat Levels (4) – 24 (8 X 8) Authorizations Groups per Cardholder
Fault Tolerant Controller Features • All the Features of IQ/SIM/ULT series Controllers • Increase Authorization Groups per Cardholder to 12 (4) • Global Entry/Exit – Timed Anti-Passback • Global I/O • Card Activation and De-Activation – Date and Time • “Stale Cards” Access Denial – “Short” and “Long Term” Values • Enterprise Cards, Vacation, etc. . • Escort Definition by Cardholder and Reader • Security Threat Levels (4) – 24 (8 X 8) Authorizations Groups per Cardholder
 Questions?
Questions?


