1395ff22fa9cc9110eef5fb84b39ea93.ppt
- Количество слайдов: 39

New Jersey Department of Labor Unemployment Insurance Modernization Project Technical Architecture – NJ SUCCESS - Supplement 13 June 2003
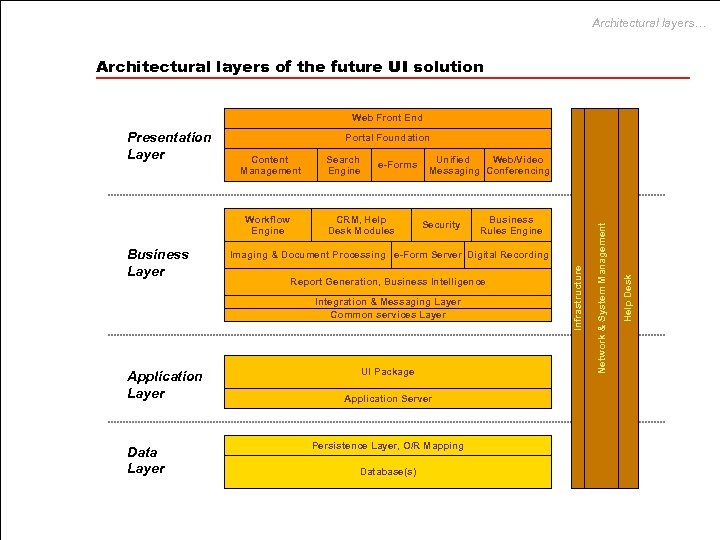
Architectural layers… Architectural layers of the future UI solution Web Front End Portal Foundation Business Layer e-Forms CRM, Help Desk Modules Unified Web/Video Messaging Conferencing Security Imaging & Document Processing e-Form Server Digital Recording Report Generation, Business Intelligence Integration & Messaging Layer Common services Layer Application Layer Data Layer Business Rules Engine UI Package Application Server Persistence Layer, O/R Mapping Database(s) Help Desk Workflow Engine Search Engine Network & System Management Content Management Infrastructure Presentation Layer
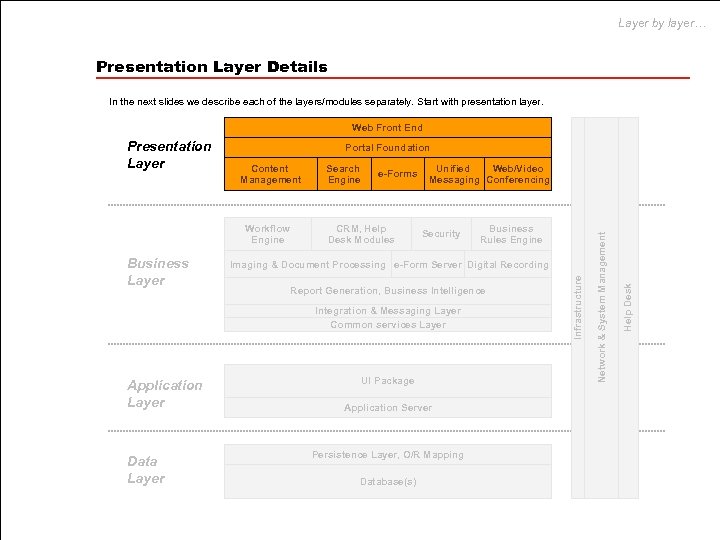
Layer by layer… Presentation Layer Details In the next slides we describe each of the layers/modules separately. Start with presentation layer. Web Front End Portal Foundation Business Layer e-Forms CRM, Help Desk Modules Unified Web/Video Messaging Conferencing Security Imaging & Document Processing e-Form Server Digital Recording Report Generation, Business Intelligence Integration & Messaging Layer Common services Layer Application Layer Data Layer Business Rules Engine UI Package Application Server Persistence Layer, O/R Mapping Database(s) Help Desk Workflow Engine Search Engine Network & System Management Content Management Infrastructure Presentation Layer

Presentation layer Elements of the web front end Beyond the typical benefits of an internet access, the following features are available to UI modernization Claimant/Agent utilities: • Calendar, Calculator(s) with UI specific features, • User profile (setting up user info, address, security, preferences, including payment options (check in the mail, direct deposit, debit card) with the ability to change profile, • Self-service utilities, “What if” and impact analysis tools Triage (Web- and IVR based): problem identification and routing person to the right part of the system; partly based on the workflow and business rules engine Behind front end: Session management: 3 tokens: security (access rights), claimant profile, case profile (area to be routed and agent skills) Conversion of emails, Web forms, IVR records and recorded voice messages into the formatted documents for case creation (appeals, etc. )

Presentation layer Portal Foundation UI Benefits: • Consolidated way of information submission and representation • Customized way of information presentation to different group of users • Delivers integrated content, applications, and services • Provides single sign-on for aggregated applications to the portal • Integrates with existing EAI, legacy, ERP, and mainframe applications through standard APIs Additional benefits: l l l Enables community creation and management while enforcing policy and access control through a single management console Includes identity management with the ability for multirole support, user provisioning, and self-registration Supports the creation and consumption of Web services-based portlets Includes a secure search engine, enabling users to search content and receive only those results that they can access Additional Portal Server products deliver real-time collaboration, knowledge management, mobile access, and secure remote access capabilities

Presentation layer Content Management Web site content management systems provide a method of organizing and controlling the information that is displayed on your web site. Without a good management system a large site can easily become a chaotic mix of pages and graphics, and be difficult to maintain. Benefits: l l l Separate design and content – Redesign entire web site by changing a couple of templates – Allows end-users to contribute content through web forms Hold status information about the submitted content as part of an approval process Categorize information (useful for personalized content delivery)
Presentation layer Search Engine Think Google or Inktomi. These engines will provide the following features to the State • Fast and easy setup • Advanced site search engine • Reports track visitors' searches • Complete customization • Scheduled re-indexing • Optional web search engine • Automatic site-map • Automatic what's new list • Content monitoring • Ease of use • No fixed page limit
Business layer E-Forms • All forms are stored in one place, accessible in a standard manner • Reduced development time • Common look and feel, data validation/correction • User interaction is separate from date representation • Snappy Interface and Reduced Bandwidth and Processing Costs • Quality of User Interaction • Sophisticated Forms Interaction • Simplified Maintenance • Automatic Generation of User Interfaces • Standards Compliance
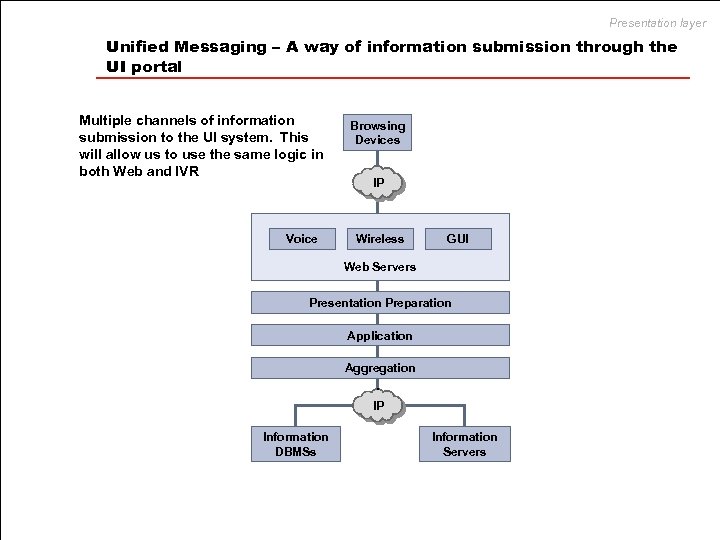
Presentation layer Unified Messaging – A way of information submission through the UI portal Multiple channels of information submission to the UI system. This will allow us to use the same logic in both Web and IVR Voice Browsing Devices IP Wireless GUI Web Servers Presentation Preparation Application Aggregation IP Information DBMSs Information Servers
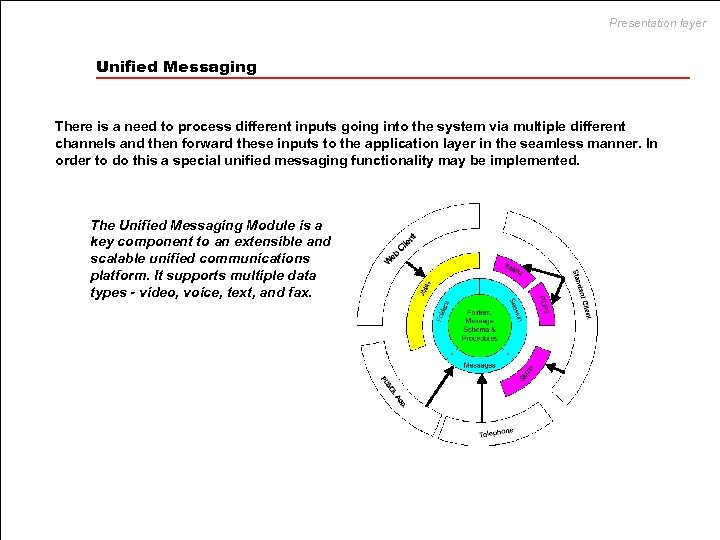
Presentation layer Unified Messaging There is a need to process different inputs going into the system via multiple different channels and then forward these inputs to the application layer in the seamless manner. In order to do this a special unified messaging functionality may be implemented. The Unified Messaging Module is a key component to an extensible and scalable unified communications platform. It supports multiple data types - video, voice, text, and fax.
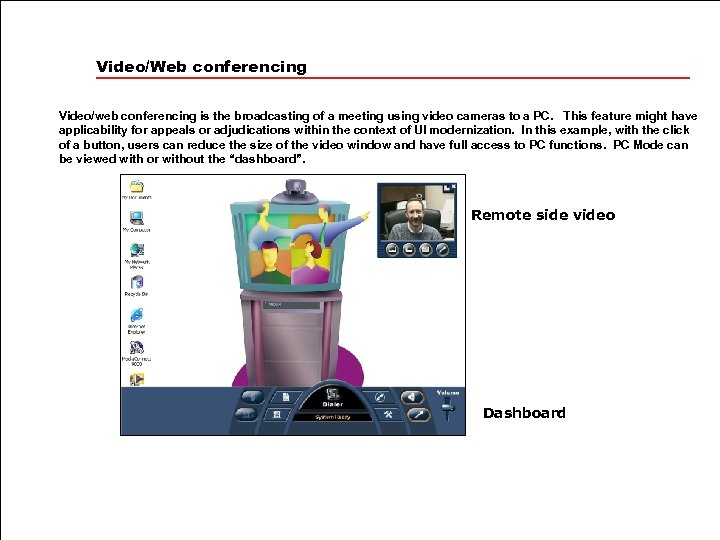
Video/Web conferencing Video/web conferencing is the broadcasting of a meeting using video cameras to a PC. This feature might have applicability for appeals or adjudications within the context of UI modernization. In this example, with the click of a button, users can reduce the size of the video window and have full access to PC functions. PC Mode can be viewed with or without the “dashboard”. Remote side video Dashboard
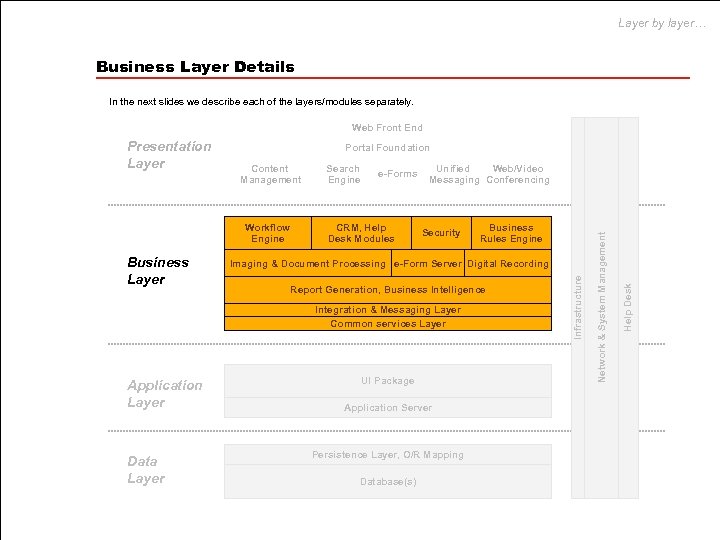
Layer by layer… Business Layer Details In the next slides we describe each of the layers/modules separately. Web Front End Portal Foundation Business Layer e-Forms CRM, Help Desk Modules Unified Web/Video Messaging Conferencing Security Imaging & Document Processing e-Form Server Digital Recording Report Generation, Business Intelligence Integration & Messaging Layer Common services Layer Application Layer Data Layer Business Rules Engine UI Package Application Server Persistence Layer, O/R Mapping Database(s) Help Desk Workflow Engine Search Engine Network & System Management Content Management Infrastructure Presentation Layer

Business layer Workflow Engine Allows to: l. Create business processes that work at e-business speed. l. Visually design and automate process flows using business skills. l. Optimize application Integration with people workflow. Standard features: l. Model-driven e-business process automation and tracking. l. Ability to find document, transaction or process, identify its status and person responsible l. Reducing work hand-off and thus cycle time, while enhancing customer service. l. Transactional and universal integration based on standard API‘s, components and XML: Nothing gets lost nor executed twice. l. Ultimate l. Eases performance that scales with growing workload needs and server capacity. process tuning based on audited experience and changing business needs. UI specific: l. Routing profiles) to the right person with the case specific skill set (based on claimant and case
Business layer CRM Companies are turning to customer-relationship management systems and strategies to gain a better understanding of their customer's wants and needs. Used in association with data warehousing, data mining, call centers and other intelligence-based applications, CRM allows companies to gather and access information about customers histories, preferences, complaints, and other data so they can better understand what customers want now and anticipate what customers will want. Benefits include: • All customer data and history in one place • Faster response to customer inquiries • Increased efficiency through automation • Deeper understanding of customers • Increased service opportunities • Identifying customers groups and trends • Receiving customer feedback that leads to new and improved products or services • Obtaining information that can be shared with business partners.
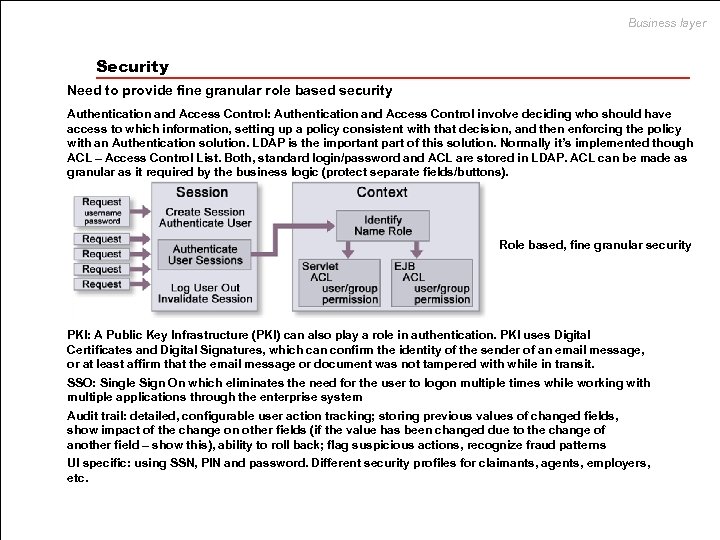
Business layer Security Need to provide fine granular role based security Authentication and Access Control: Authentication and Access Control involve deciding who should have access to which information, setting up a policy consistent with that decision, and then enforcing the policy with an Authentication solution. LDAP is the important part of this solution. Normally it’s implemented though ACL – Access Control List. Both, standard login/password and ACL are stored in LDAP. ACL can be made as granular as it required by the business logic (protect separate fields/buttons). Role based, fine granular security PKI: A Public Key Infrastructure (PKI) can also play a role in authentication. PKI uses Digital Certificates and Digital Signatures, which can confirm the identity of the sender of an email message, or at least affirm that the email message or document was not tampered with while in transit. SSO: Single Sign On which eliminates the need for the user to logon multiple times while working with multiple applications through the enterprise system Audit trail: detailed, configurable user action tracking; storing previous values of changed fields, show impact of the change on other fields (if the value has been changed due to the change of another field – show this), ability to roll back; flag suspicious actions, recognize fraud patterns UI specific: using SSN, PIN and password. Different security profiles for claimants, agents, employers, etc.
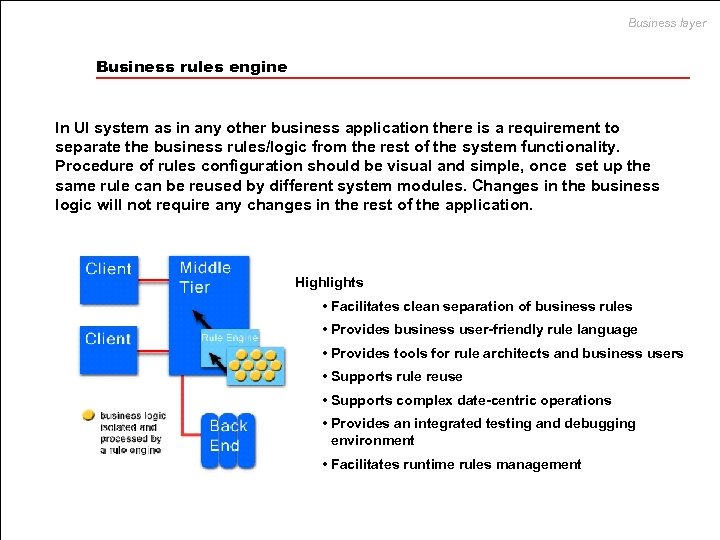
Business layer Business rules engine In UI system as in any other business application there is a requirement to separate the business rules/logic from the rest of the system functionality. Procedure of rules configuration should be visual and simple, once set up the same rule can be reused by different system modules. Changes in the business logic will not require any changes in the rest of the application. Highlights • Facilitates clean separation of business rules • Provides business user-friendly rule language • Provides tools for rule architects and business users • Supports rule reuse • Supports complex date-centric operations • Provides an integrated testing and debugging environment • Facilitates runtime rules management
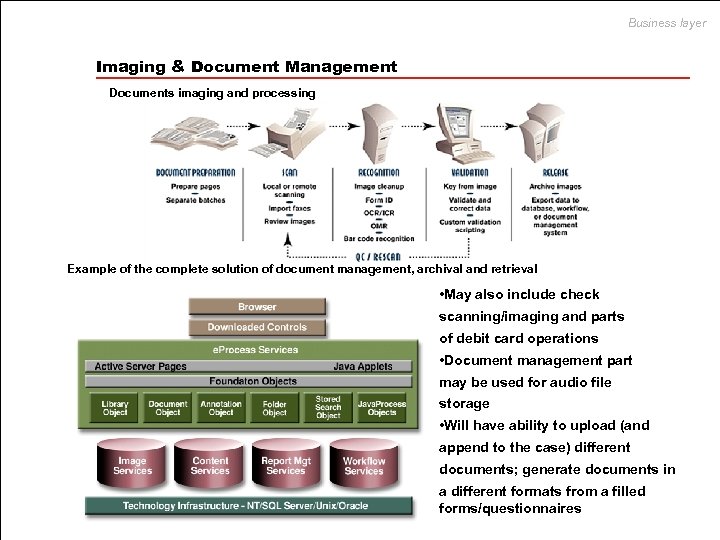
Business layer Imaging & Document Management Documents imaging and processing Example of the complete solution of document management, archival and retrieval • May also include check scanning/imaging and parts of debit card operations • Document management part may be used for audio file storage • Will have ability to upload (and append to the case) different documents; generate documents in a different formats from a filled forms/questionnaires
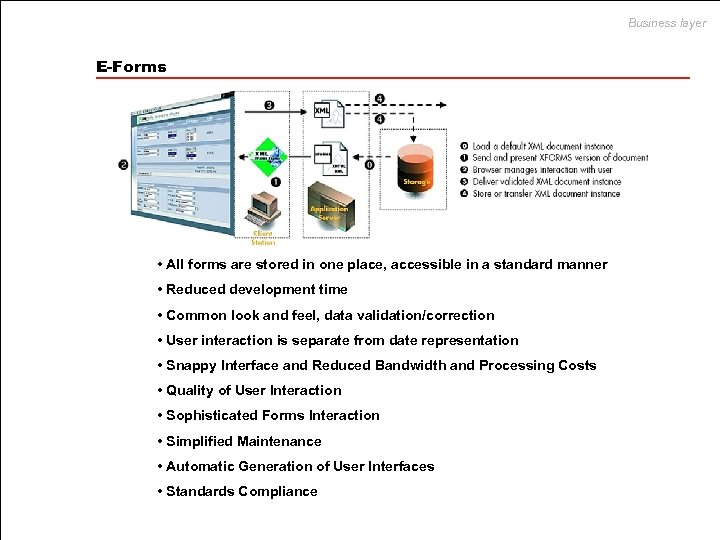
Business layer E-Forms • All forms are stored in one place, accessible in a standard manner • Reduced development time • Common look and feel, data validation/correction • User interaction is separate from date representation • Snappy Interface and Reduced Bandwidth and Processing Costs • Quality of User Interaction • Sophisticated Forms Interaction • Simplified Maintenance • Automatic Generation of User Interfaces • Standards Compliance
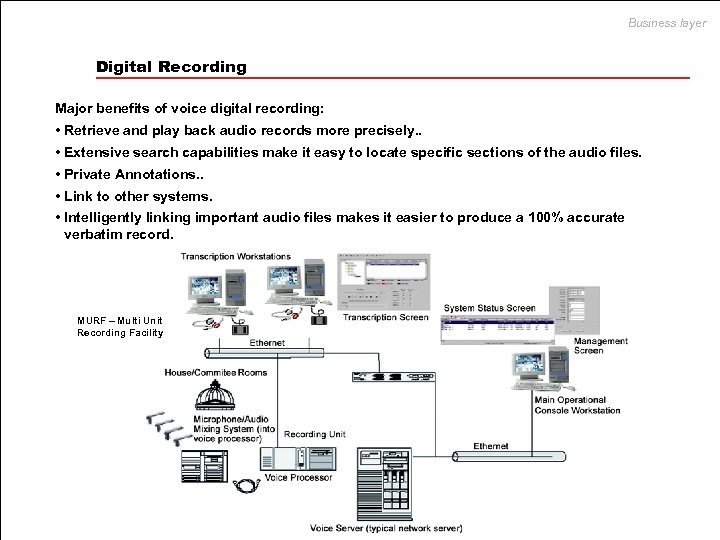
Business layer Digital Recording Major benefits of voice digital recording: • Retrieve and play back audio records more precisely. . • Extensive search capabilities make it easy to locate specific sections of the audio files. • Private Annotations. . • Link to other systems. • Intelligently linking important audio files makes it easier to produce a 100% accurate verbatim record. MURF – Multi Unit Recording Facility
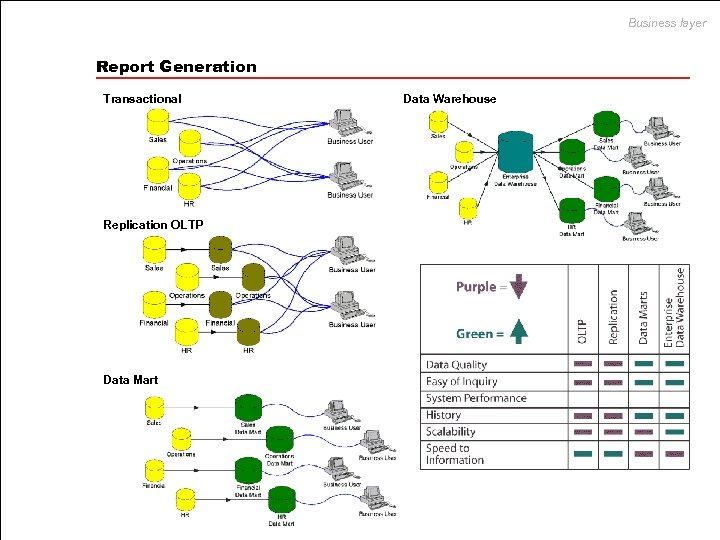
Business layer Report Generation Transactional Replication OLTP Data Mart Data Warehouse
Business layer Reporting • Access almost any data • Easy, intuitive designer • Any report type - Create virtually any report you need, including: • Cross-tab • Conditional • Drill-down • Top N • Summary • Form • OLAP • Subreports • Mailing labels • Excel and Access Add-ins • Complete formatting power • Customizable templates • Custom Functions • Powerful interactivity - Easily transform data into interactive information by automatically implementing report analysis features, including: • Charting • Mapping • Grouping • Sorting • Alerting • Field highlighting • Drill-down • Parameter prompts • Hyperlinks • Multiple export formats - Publish reports to a variety of familiar formats, including: • XML • PDF • HTML • Excel • RTF • Word • Text • CSV • ODBC • Record-style
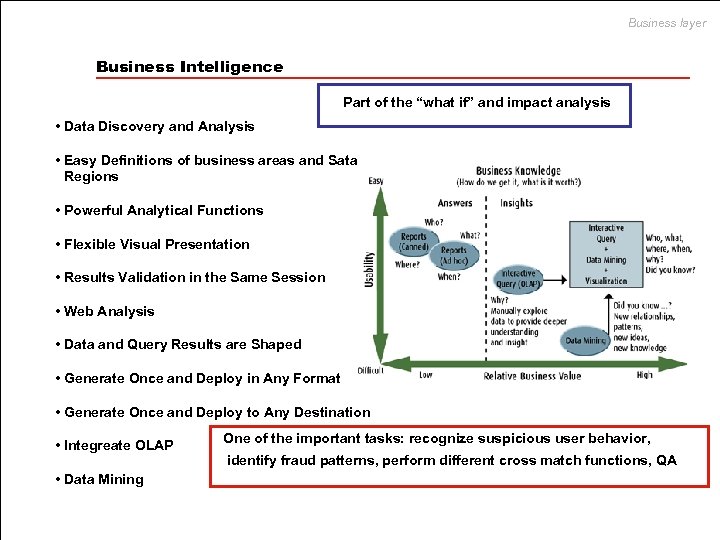
Business layer Business Intelligence Part of the “what if” and impact analysis • Data Discovery and Analysis • Easy Definitions of business areas and Sata Regions • Powerful Analytical Functions • Flexible Visual Presentation • Results Validation in the Same Session • Web Analysis • Data and Query Results are Shaped • Generate Once and Deploy in Any Format • Generate Once and Deploy to Any Destination • Integreate OLAP • Data Mining One of the important tasks: recognize suspicious user behavior, identify fraud patterns, perform different cross match functions, QA
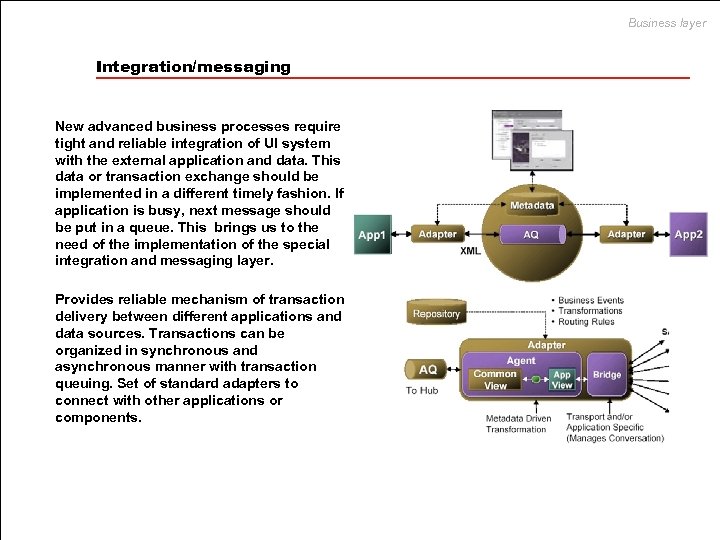
Business layer Integration/messaging New advanced business processes require tight and reliable integration of UI system with the external application and data. This data or transaction exchange should be implemented in a different timely fashion. If application is busy, next message should be put in a queue. This brings us to the need of the implementation of the special integration and messaging layer. Provides reliable mechanism of transaction delivery between different applications and data sources. Transactions can be organized in synchronous and asynchronous manner with transaction queuing. Set of standard adapters to connect with other applications or components.

Business layer Common Services Framework Once implemented, used by multiple applications Benefits: • It reduces cost, since new applications will reuse already existing functionality • It improves control of the whole system • It simplifies maintenance of the whole system • Helps to consolidate information from multiple applications into one place CSF is the set of reusable modules, components for the use by different applications through the enterprise system Examples: l Security l Audit trail/logging l Error handling/processing and diagnostics l Email l Calendar, scheduling/appointment system with the reminder l Messaging and instant messaging l ACH, EFT, other financial modules for the benefit payments l Document generation and mailing Elements of the common services framework should be easily plugged into other applications. Normally it can be done through the simple configuration process or in some cases extra coding to available API or other interface mechanism
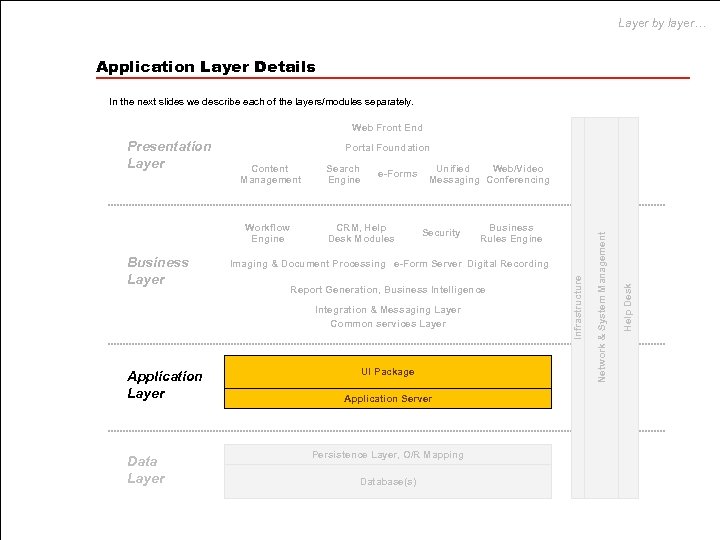
Layer by layer… Application Layer Details In the next slides we describe each of the layers/modules separately. Web Front End Portal Foundation Business Layer e-Forms CRM, Help Desk Modules Unified Web/Video Messaging Conferencing Security Imaging & Document Processing e-Form Server Digital Recording Report Generation, Business Intelligence Integration & Messaging Layer Common services Layer Application Layer Data Layer Business Rules Engine UI Package Application Server Persistence Layer, O/R Mapping Database(s) Help Desk Workflow Engine Search Engine Network & System Management Content Management Infrastructure Presentation Layer
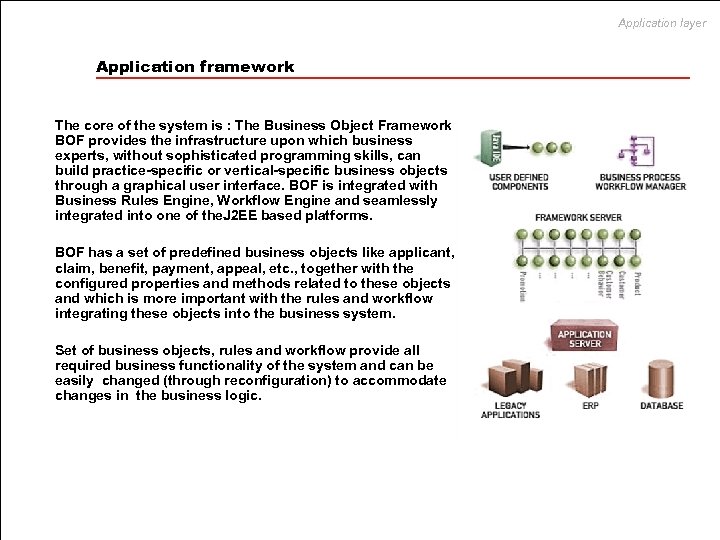
Application layer Application framework The core of the system is : The Business Object Framework BOF provides the infrastructure upon which business experts, without sophisticated programming skills, can build practice-specific or vertical-specific business objects through a graphical user interface. BOF is integrated with Business Rules Engine, Workflow Engine and seamlessly integrated into one of the. J 2 EE based platforms. BOF has a set of predefined business objects like applicant, claim, benefit, payment, appeal, etc. , together with the configured properties and methods related to these objects and which is more important with the rules and workflow integrating these objects into the business system. Set of business objects, rules and workflow provide all required business functionality of the system and can be easily changed (through reconfiguration) to accommodate changes in the business logic.
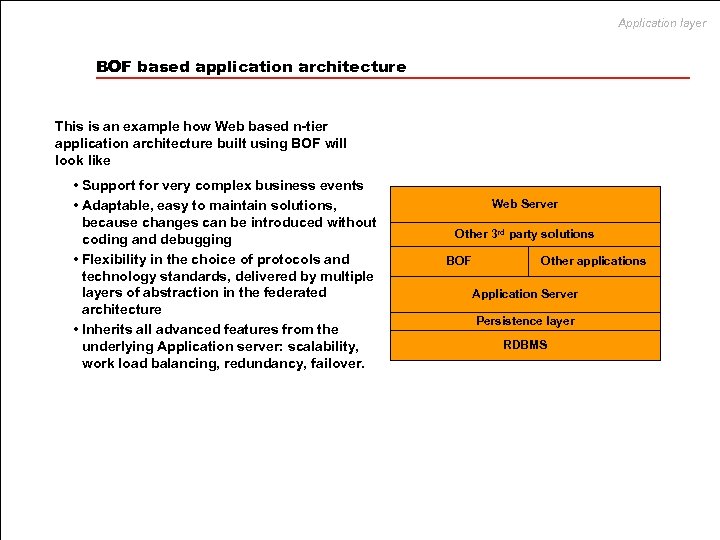
Application layer BOF based application architecture This is an example how Web based n-tier application architecture built using BOF will look like • Support for very complex business events • Adaptable, easy to maintain solutions, because changes can be introduced without coding and debugging • Flexibility in the choice of protocols and technology standards, delivered by multiple layers of abstraction in the federated architecture • Inherits all advanced features from the underlying Application server: scalability, work load balancing, redundancy, failover. Web Server Other 3 rd party solutions BOF Other applications Application Server Persistence layer RDBMS
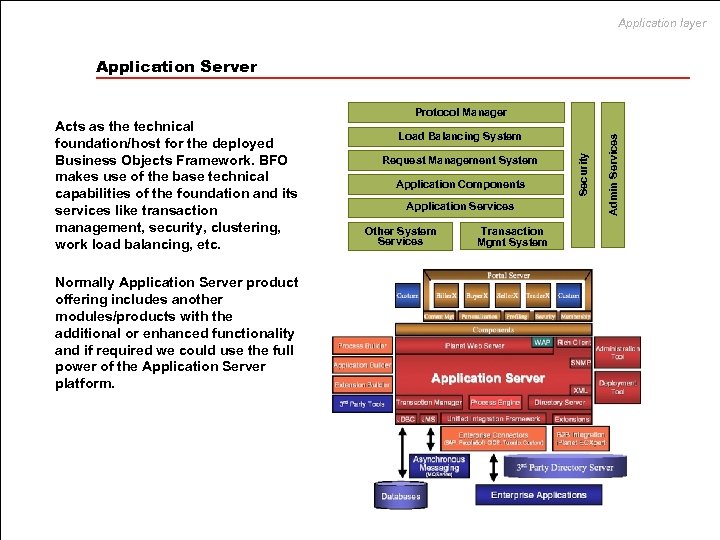
Application layer Application Server Normally Application Server product offering includes another modules/products with the additional or enhanced functionality and if required we could use the full power of the Application Server platform. Load Balancing System Request Management System Application Components Application Services Other System Services Transaction Mgmt System Admin Services Protocol Manager Security Acts as the technical foundation/host for the deployed Business Objects Framework. BFO makes use of the base technical capabilities of the foundation and its services like transaction management, security, clustering, work load balancing, etc.
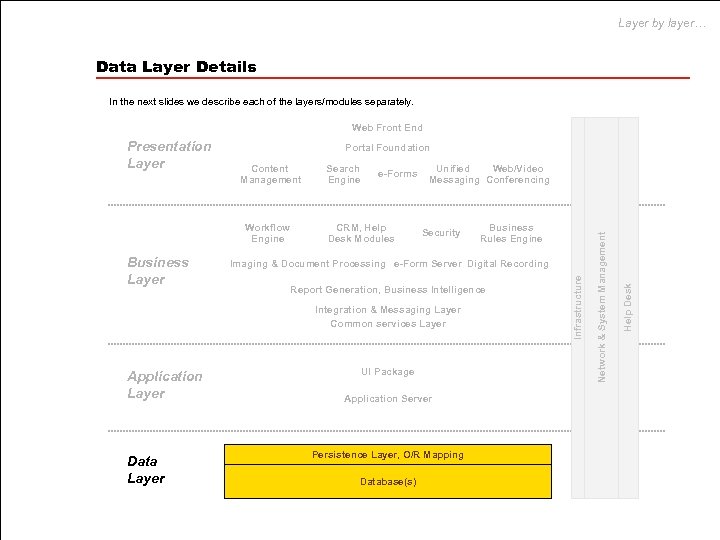
Layer by layer… Data Layer Details In the next slides we describe each of the layers/modules separately. Web Front End Portal Foundation Business Layer e-Forms CRM, Help Desk Modules Unified Web/Video Messaging Conferencing Security Imaging & Document Processing e-Form Server Digital Recording Report Generation, Business Intelligence Integration & Messaging Layer Common services Layer Application Layer Data Layer Business Rules Engine UI Package Application Server Persistence Layer, O/R Mapping Database(s) Help Desk Workflow Engine Search Engine Network & System Management Content Management Infrastructure Presentation Layer
Data layer Benefits of the persistence layer More advanced: • Caching • Querying • Locking • Sequencing • Transaction support and integration • Flexibility • Speed
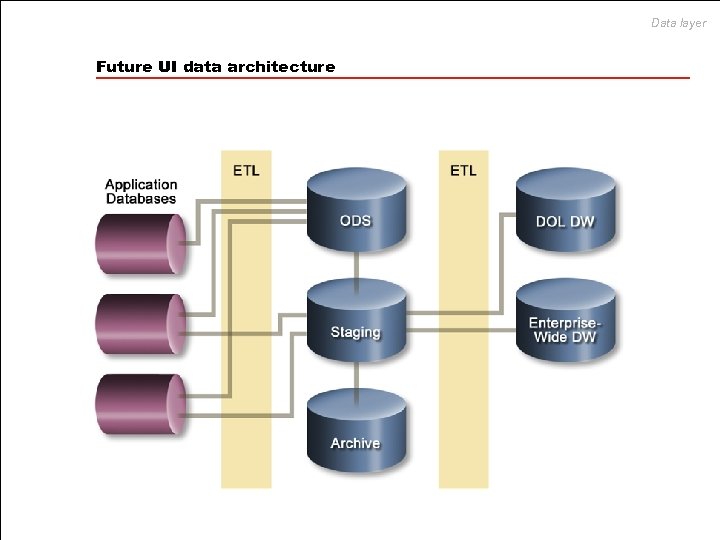
Data layer Future UI data architecture

Data layer features Putting date, time stamp into the critical records/transactions Set of stored procedures, triggers, scheduling, handling important parts of business logic Keeping track on configured time frames with the notification generation (database email or IVR request to call back or call with auto configured message) Trigger automatic basic cross checks and validations Validation/standardization of postal addresses
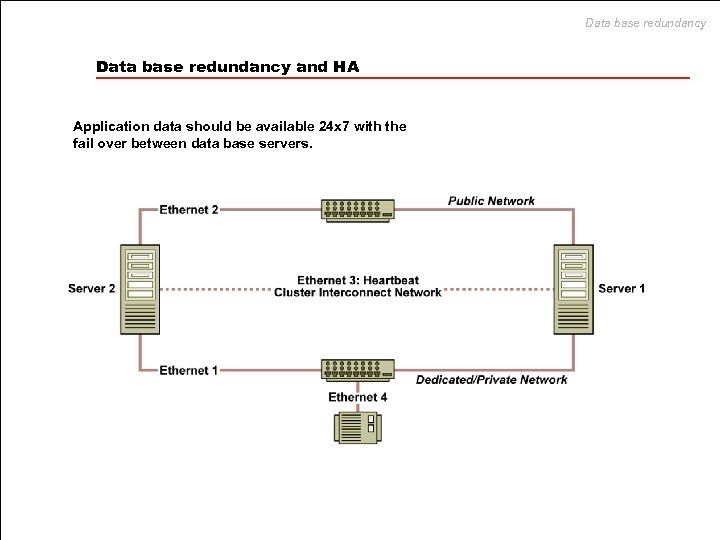
Data base redundancy and HA Application data should be available 24 x 7 with the fail over between data base servers.
Layer by layer… Infrastructure Layer Details In the next slides we describe each of the layers/modules separately. Web Front End Portal Foundation Business Layer e-Forms CRM, Help Desk Modules Unified Web/Video Messaging Conferencing Security Imaging & Document Processing e-Form Server Digital Recording Report Generation, Business Intelligence Integration & Messaging Layer Common services Layer Application Layer Data Layer Business Rules Engine UI Package Application Server Persistence Layer, O/R Mapping Database(s) Help Desk Workflow Engine Search Engine Network & System Management Content Management Infrastructure Presentation Layer

Infrastructure… Key infrastructure elements Safe Transmission: Protocols and Encryption: Special network protocols and standards such as SSL, SSH, PPTP, and S/MIME work to ensure that data that is transferred over the Internet is not easily intercepted. As an additional security measure, data transferred through these protocols is frequently encrypted. Network Intrusion Prevention and Detection: VPNs, Firewalls, and Intrusion Detection Systems (IDS) are all methods of securing a network from unauthorized access. VPNs allow users in different physical locations to share a secure network connection that spans the public internet. A Firewall regulates both inbound and outbound traffic for a private network. Firewalls can block intruders from entering the network and regulate data that is sent from the network. IDS solutions usually include monitoring or reporting tools, which can highlight who potential intruders are and how they are trying to enter the network. Such information can then be used to further strengthen network security. Protecting a network also involves maintaining software such as web servers, operating systems, and email systems. Every program has bugs or vulnerabilities that could be manipulated by someone else. Network security includes staying up-to-date on hacker attacks and security breaches, applying the latest software updates, and compensating for any known software vulnerabilities.

Infrastructure… Key infrastructure elements Content Filtering and Internet Privacy: Antivirus software remains one of the most widely implemented and recognized types of content filters. It scans an email and any attached files for known scripts and programs that can take over applications on a computer and wreak havoc. Some software will even search the text of an email message and remove specific words or images as directed. Other kinds of content filters, such as spam blockers, protect privacy by filtering email and redirecting/bouncing back email that is not sent from a recognized or authenticated sender. Many parents, corporations, and educational institutions have implemented URL Blockers, which prohibit web browsers from accessing certain web sites deemed offensive or inappropriate. Hardware Security: This form of security protects the physical aspect of information – the computer itself. Locks, cables and security systems prevent the easy removal of computer equipment by thieves. Online service providers can even track the movement of stolen computer systems with attached tracking devices.
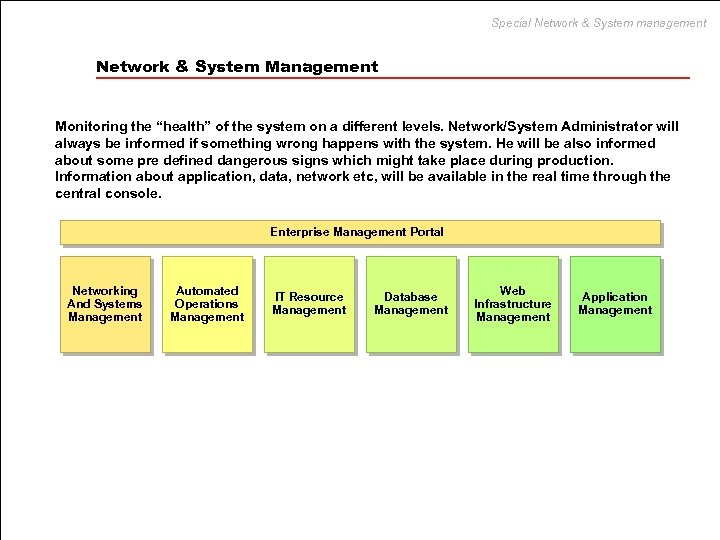
Special Network & System management Network & System Management Monitoring the “health” of the system on a different levels. Network/System Administrator will always be informed if something wrong happens with the system. He will be also informed about some pre defined dangerous signs which might take place during production. Information about application, data, network etc, will be available in the real time through the central console. Enterprise Management Portal Networking And Systems Management Automated Operations Management IT Resource Management Database Management Web Infrastructure Management Application Management
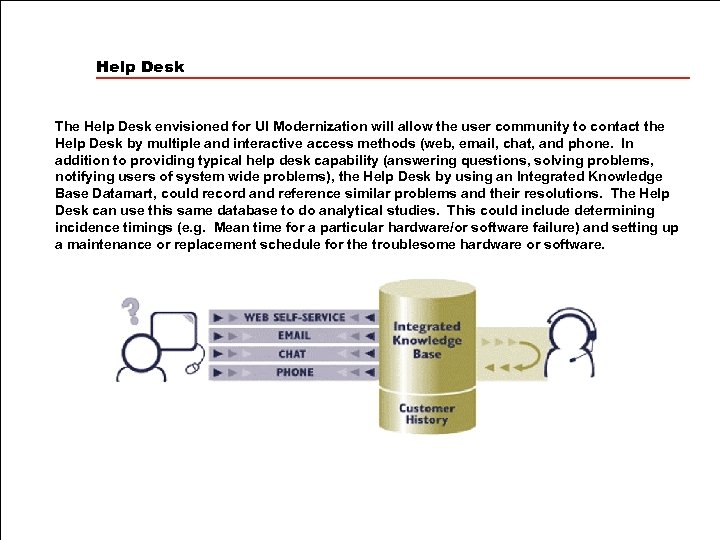
Help Desk The Help Desk envisioned for UI Modernization will allow the user community to contact the Help Desk by multiple and interactive access methods (web, email, chat, and phone. In addition to providing typical help desk capability (answering questions, solving problems, notifying users of system wide problems), the Help Desk by using an Integrated Knowledge Base Datamart, could record and reference similar problems and their resolutions. The Help Desk can use this same database to do analytical studies. This could include determining incidence timings (e. g. Mean time for a particular hardware/or software failure) and setting up a maintenance or replacement schedule for the troublesome hardware or software.

Infrastructure… Help Desk - Benefits • Help Desk Issue Tracking • Robust Administrative Tools • Complete Project Tracking • Email Notification • Web Based Flexibility • Escalation Deadlines • Completely Customizable • Powerful Search • Supports Staff Activities • Include Outside Vendors or Partners • Customer/User Activities • Robust Knowledge Base
1395ff22fa9cc9110eef5fb84b39ea93.ppt