ada2a17a7b5d921f67c41abc413d8284.ppt
- Количество слайдов: 43
 New Cryptography • Rafal Lukawiecki • • • Strategic Consultant rafal@projectbotticelli. co. uk Project Botticelli Ltd This presentation is based on work from MSDN. TEŽAVNOST: 200
New Cryptography • Rafal Lukawiecki • • • Strategic Consultant rafal@projectbotticelli. co. uk Project Botticelli Ltd This presentation is based on work from MSDN. TEŽAVNOST: 200
 2 Objectives • Explain the status and some of the problems of today’s cryptography • Discuss solutions for the problems • Introduce the new APIs for using newer forms of cryptography TEŽAVNOST: 200
2 Objectives • Explain the status and some of the problems of today’s cryptography • Discuss solutions for the problems • Introduce the new APIs for using newer forms of cryptography TEŽAVNOST: 200
 3 Agenda • Cryptography of Present • Cryptography of Tomorrow • Cryptography in Windows Vista and Longhorn TEŽAVNOST: 200
3 Agenda • Cryptography of Present • Cryptography of Tomorrow • Cryptography in Windows Vista and Longhorn TEŽAVNOST: 200
 12 Cryptography of Present TEŽAVNOST: 200
12 Cryptography of Present TEŽAVNOST: 200
 13 Today’s Recommendation • At present (June 2006), consider using the following cryptographic mechanisms available in Windows in preference to others: – AES-128 (or AES-192, or AES-256) – RSA 2048 (or longer) – “SHA-2” (i. e. SHA-256, or SHA-512) – DSA (or SHA-2/RSA signatures) TEŽAVNOST: 200
13 Today’s Recommendation • At present (June 2006), consider using the following cryptographic mechanisms available in Windows in preference to others: – AES-128 (or AES-192, or AES-256) – RSA 2048 (or longer) – “SHA-2” (i. e. SHA-256, or SHA-512) – DSA (or SHA-2/RSA signatures) TEŽAVNOST: 200
 14 DES, IDEA, RC 2, RC 5, Twofish Not Recommended • Symmetric • DES (Data Encryption Standard) is popular – DO NOT USE DES! – Keys very short: 56 bits – Brute-force attack took 3. 5 hours on a machine costing US$1 m in 1993. Today it is done real-time – Triple DES (3 DES) more secure, but better options exist • IDEA (International Data Encryption Standard) – Deceptively similar to DES, and “not” from NSA – 128 bit keys, OK but we have better ones • RC 2 & RC 5 (by R. Rivest) – RC 2 is older and RC 5 newer (1994) - similar to DES and IDEA • Blowfish, Twofish – OK, but not a standard – B. Schneier’s replacement for DES, followed by Twofish, one of the NIST competition finalists TEŽAVNOST: 200
14 DES, IDEA, RC 2, RC 5, Twofish Not Recommended • Symmetric • DES (Data Encryption Standard) is popular – DO NOT USE DES! – Keys very short: 56 bits – Brute-force attack took 3. 5 hours on a machine costing US$1 m in 1993. Today it is done real-time – Triple DES (3 DES) more secure, but better options exist • IDEA (International Data Encryption Standard) – Deceptively similar to DES, and “not” from NSA – 128 bit keys, OK but we have better ones • RC 2 & RC 5 (by R. Rivest) – RC 2 is older and RC 5 newer (1994) - similar to DES and IDEA • Blowfish, Twofish – OK, but not a standard – B. Schneier’s replacement for DES, followed by Twofish, one of the NIST competition finalists TEŽAVNOST: 200
 15 Rijndael (AES) Recommended • Current US standard – Winner of the AES (Advanced Encryption Standard) competition run by NIST (National Institute of Standards and Technology in US) in 1997 -2000 – Comes from Europe (Belgium) by Joan Daemen and Vincent Rijmen. “X-files” stories less likely (unlike DES). • Symmetric block-cipher (128, 192 or 256 bits) with variable keys (128, 192 or 256 bits, too) • Fast and a lot of good properties, such as good immunity from timing and power (electric) analysis • Construction, again, deceptively similar to DES (S TEŽAVNOST: 200 -boxes, XORs etc. ) but really different
15 Rijndael (AES) Recommended • Current US standard – Winner of the AES (Advanced Encryption Standard) competition run by NIST (National Institute of Standards and Technology in US) in 1997 -2000 – Comes from Europe (Belgium) by Joan Daemen and Vincent Rijmen. “X-files” stories less likely (unlike DES). • Symmetric block-cipher (128, 192 or 256 bits) with variable keys (128, 192 or 256 bits, too) • Fast and a lot of good properties, such as good immunity from timing and power (electric) analysis • Construction, again, deceptively similar to DES (S TEŽAVNOST: 200 -boxes, XORs etc. ) but really different
 16 CAST and GOST Not used widely anymore – avoid • CAST – – Canadians Carlisle Adams & Stafford Tavares 64 bit key and 64 bit of data Chose your S-boxes Seems resistant to differential & linear cryptanalysis and only way to break is brute force (but key is a bit short!) • GOST – Soviet Union’s “version” of DES but with a clearer design and many more repetitions of the process – 256 bit key but really 610 bits of secret, so pretty much “tank quality” – Backdoor? Who knows… TEŽAVNOST: 200
16 CAST and GOST Not used widely anymore – avoid • CAST – – Canadians Carlisle Adams & Stafford Tavares 64 bit key and 64 bit of data Chose your S-boxes Seems resistant to differential & linear cryptanalysis and only way to break is brute force (but key is a bit short!) • GOST – Soviet Union’s “version” of DES but with a clearer design and many more repetitions of the process – 256 bit key but really 610 bits of secret, so pretty much “tank quality” – Backdoor? Who knows… TEŽAVNOST: 200
 17 Rely on Cryptosystems • Indeed: never use just an algorithm, but an entire cryptosystem • For example: – If you use DES etc. in a simple “loop” to encrypt a stream of data you literally lose all security – Instead: use a technique designed for adapting an algorithm to a streams of data, such as CBC (Cipher Block Chaining) • Microsoft never implement just an algorithm – always a complete cryptosystem, e. g. RSA-OAEP etc. • Do it just by using built-in cryptographic systems, TEŽAVNOST: 200 such as various Microsoft CSPs etc.
17 Rely on Cryptosystems • Indeed: never use just an algorithm, but an entire cryptosystem • For example: – If you use DES etc. in a simple “loop” to encrypt a stream of data you literally lose all security – Instead: use a technique designed for adapting an algorithm to a streams of data, such as CBC (Cipher Block Chaining) • Microsoft never implement just an algorithm – always a complete cryptosystem, e. g. RSA-OAEP etc. • Do it just by using built-in cryptographic systems, TEŽAVNOST: 200 such as various Microsoft CSPs etc.
 18 Dangerous Implementations • Cryptographic applications from not-wellknown sources • “Just downloaded libraries” used by your in-house developers • Insist on using built-in systems where possible: – Microsoft OS: CAPI, CAPICOM, MS CSP etc. – Smartcards: certified CSPs – Elsewhere: FIPS-140 -2 compliant implementations • See csrc. nist. gov/cryptval TEŽAVNOST: 200
18 Dangerous Implementations • Cryptographic applications from not-wellknown sources • “Just downloaded libraries” used by your in-house developers • Insist on using built-in systems where possible: – Microsoft OS: CAPI, CAPICOM, MS CSP etc. – Smartcards: certified CSPs – Elsewhere: FIPS-140 -2 compliant implementations • See csrc. nist. gov/cryptval TEŽAVNOST: 200
 19 RC 4 Generally Not Recommended • Symmetric – Fast, streaming encryption • R. Rivest in 1994 – Originally secret, but “published” on sci. crypt • Related to “one-time pad”, theoretically most secure • But! • It relies on a really good random number generator – And that is the problem • Nowadays, we tend to use block ciphers in modes TEŽAVNOST: 200 of operation that work for streams
19 RC 4 Generally Not Recommended • Symmetric – Fast, streaming encryption • R. Rivest in 1994 – Originally secret, but “published” on sci. crypt • Related to “one-time pad”, theoretically most secure • But! • It relies on a really good random number generator – And that is the problem • Nowadays, we tend to use block ciphers in modes TEŽAVNOST: 200 of operation that work for streams
 20 RSA, DSA, El. Gamal • Asymmetric – Slow and computationally expensive – need a computer – Security increasingly being questioned • Rivest, Shamir, Adleman – 1978 – Popular and well researched – Strength in today’s inefficiency to factorise into prime numbers – Some worries about key generation process in some implementations • DSA (Digital Signature Algorithm) – Mainly for digital signing, not for encryption, used in US – Variant of Schnorr and El. Gamal signature algorithm • El. Gamal – Relies on complexity of discrete logarithms TEŽAVNOST: 200
20 RSA, DSA, El. Gamal • Asymmetric – Slow and computationally expensive – need a computer – Security increasingly being questioned • Rivest, Shamir, Adleman – 1978 – Popular and well researched – Strength in today’s inefficiency to factorise into prime numbers – Some worries about key generation process in some implementations • DSA (Digital Signature Algorithm) – Mainly for digital signing, not for encryption, used in US – Variant of Schnorr and El. Gamal signature algorithm • El. Gamal – Relies on complexity of discrete logarithms TEŽAVNOST: 200
 21 MD 5, SHA • Hash functions – part of the digital signature • Goals: – Not reversible: can’t obtain the message from its hash – Hash much shorter than original message – Two messages won’t have the same hash • MD 5 (R. Rivest) – 512 bits hashed into 128 – Mathematical model still unknown – Recently (July 2004) broken, do not use on its own • SHA (Secure Hash Algorithm) – US standard based on MD 5 – SHA-0 broken (July 2004), SHA-1 probably too weak (partly broken, full break alleged by Chinese recently), use SHA-256 at least TEŽAVNOST: 200
21 MD 5, SHA • Hash functions – part of the digital signature • Goals: – Not reversible: can’t obtain the message from its hash – Hash much shorter than original message – Two messages won’t have the same hash • MD 5 (R. Rivest) – 512 bits hashed into 128 – Mathematical model still unknown – Recently (July 2004) broken, do not use on its own • SHA (Secure Hash Algorithm) – US standard based on MD 5 – SHA-0 broken (July 2004), SHA-1 probably too weak (partly broken, full break alleged by Chinese recently), use SHA-256 at least TEŽAVNOST: 200
 22 Diffie-Hellman, “SSL”, Certs • Methods for key exchange and transport • DH (1976) always generates a new “keypair” for each asymmetric session • Certificates are the most common way to exchange public keys – Foundation of Public Key Infrastructure (PKI) • SSL uses a protocol to exchange keys safely, but also requires PKI TEŽAVNOST: 200
22 Diffie-Hellman, “SSL”, Certs • Methods for key exchange and transport • DH (1976) always generates a new “keypair” for each asymmetric session • Certificates are the most common way to exchange public keys – Foundation of Public Key Infrastructure (PKI) • SSL uses a protocol to exchange keys safely, but also requires PKI TEŽAVNOST: 200
 23 APIs of Today • Microsoft Crypto. API (CAPI) 2. 0 is the interface to all CSPs – Cryptographic Service Providers • Built-in or smartcard-based • . NET Framework 1. 1 and 2. 0 wraps most of the functionality of CAPI in classes: – System. Security. Cryptography and its subclasses: • . Pkcs • . X 509 Certificates • . XML • Or you can use the CAPICOM library TEŽAVNOST: 200
23 APIs of Today • Microsoft Crypto. API (CAPI) 2. 0 is the interface to all CSPs – Cryptographic Service Providers • Built-in or smartcard-based • . NET Framework 1. 1 and 2. 0 wraps most of the functionality of CAPI in classes: – System. Security. Cryptography and its subclasses: • . Pkcs • . X 509 Certificates • . XML • Or you can use the CAPICOM library TEŽAVNOST: 200
 24 Cryptography of Tomorrow TEŽAVNOST: 200
24 Cryptography of Tomorrow TEŽAVNOST: 200
 25 Quantum Cryptography? • Method for generating and passing a secret key or a random stream – Not for passing the actual data, but that’s irrelevant • Polarisation of light (photons) can be detected only in a way that destroys the “direction” (basis) – So if someone other than you observes it, you receive nothing useful and you know you were bugged • Perfectly doable over up-to-120 km dedicated fibre-optic link – Seems pretty perfect, if a bit tedious and slow – Practical implementations still use AES/DES etc. for actual encryption • Magiq QPN: http: //www. magiqtech. com/press/qpn. pdf • Don’t confuse it with quantum computing, which won’t be with us for at least another 50 years or so, or maybe longer… TEŽAVNOST: 200
25 Quantum Cryptography? • Method for generating and passing a secret key or a random stream – Not for passing the actual data, but that’s irrelevant • Polarisation of light (photons) can be detected only in a way that destroys the “direction” (basis) – So if someone other than you observes it, you receive nothing useful and you know you were bugged • Perfectly doable over up-to-120 km dedicated fibre-optic link – Seems pretty perfect, if a bit tedious and slow – Practical implementations still use AES/DES etc. for actual encryption • Magiq QPN: http: //www. magiqtech. com/press/qpn. pdf • Don’t confuse it with quantum computing, which won’t be with us for at least another 50 years or so, or maybe longer… TEŽAVNOST: 200
 26 More Practical Solution • US NSA and NIST recommendation as of Feb 2005 is to implement “Suite-B” protocols • This is very rarely done in today’s software • Good news: Microsoft supports Suite-B in Windows Vista (and Longhorn Server) – For all internal implementations Microsoft will not use weaker algorithms than Suite-B • But, of course, they will support your choice to do so if you wish TEŽAVNOST: 200
26 More Practical Solution • US NSA and NIST recommendation as of Feb 2005 is to implement “Suite-B” protocols • This is very rarely done in today’s software • Good news: Microsoft supports Suite-B in Windows Vista (and Longhorn Server) – For all internal implementations Microsoft will not use weaker algorithms than Suite-B • But, of course, they will support your choice to do so if you wish TEŽAVNOST: 200
 27 Vista Supports NSA Suite B www. nsa. gov/ia/industry/crypto_suite_b. cfm • Required cryptographic algorithms for all US non-classified and classified (SECRET and TOP-SECRET) needs – Except a small area of special-security needs (e. g. nuclear security) – guided by Suite A (definition is classified) – Announced by NSA at RSA conference in Feb 2005 TEŽAVNOST: 200
27 Vista Supports NSA Suite B www. nsa. gov/ia/industry/crypto_suite_b. cfm • Required cryptographic algorithms for all US non-classified and classified (SECRET and TOP-SECRET) needs – Except a small area of special-security needs (e. g. nuclear security) – guided by Suite A (definition is classified) – Announced by NSA at RSA conference in Feb 2005 TEŽAVNOST: 200
 28 Mathematical Designs • Many cryptographic algorithms (e. g. DSA) rely on a class of mathematical designs related to the concept of discrete logarithms • These can be implemented over the finite field of any abelian group – Normally, this means using integers modulo a prime number • Alternatively, elliptic curve groups could be used TEŽAVNOST: 200
28 Mathematical Designs • Many cryptographic algorithms (e. g. DSA) rely on a class of mathematical designs related to the concept of discrete logarithms • These can be implemented over the finite field of any abelian group – Normally, this means using integers modulo a prime number • Alternatively, elliptic curve groups could be used TEŽAVNOST: 200
 29 Elliptic Curve Cryptography ECC • More efficient design, using fewer bits of key for the same strength • Breaking these designs seems even harder than traditional ones • Leads to faster algorithms with fewer problems • Primarily used to enhance algorithms of existing design, such as DSA TEŽAVNOST: 200
29 Elliptic Curve Cryptography ECC • More efficient design, using fewer bits of key for the same strength • Breaking these designs seems even harder than traditional ones • Leads to faster algorithms with fewer problems • Primarily used to enhance algorithms of existing design, such as DSA TEŽAVNOST: 200
 30 Suite-B Algorithms • Encryption: AES • Digital Signature: EC-DSA • Key Exchange: EC-DH or EC-MQV • Hashing: SHA-2 TEŽAVNOST: 200
30 Suite-B Algorithms • Encryption: AES • Digital Signature: EC-DSA • Key Exchange: EC-DH or EC-MQV • Hashing: SHA-2 TEŽAVNOST: 200
 31 Suite-B Encryption • AES – FIPS 197 (with keys sizes of 128 and 256 bits) – This is a specific implementation of Rijndael algorithm allowing use of 128 bit data blocks only – Keys of 192 bits are not used (although FIPS specifies them) • Please note that most 256 bit implementations are much slower than 128 bits • In general, anything of 81 bits or more in this class of cryptography is considered “good enough” for typical commercial applications TEŽAVNOST: 200
31 Suite-B Encryption • AES – FIPS 197 (with keys sizes of 128 and 256 bits) – This is a specific implementation of Rijndael algorithm allowing use of 128 bit data blocks only – Keys of 192 bits are not used (although FIPS specifies them) • Please note that most 256 bit implementations are much slower than 128 bits • In general, anything of 81 bits or more in this class of cryptography is considered “good enough” for typical commercial applications TEŽAVNOST: 200
 32 Suite-B Digital Signatures • Elliptic Curve Digital Signature Algorithm (EC-DSA) – FIPS 186 -2 (using the curves with 256 and 384 -bit prime moduli) • Microsoft also supports 521 -bit keys • This is a classical DSA algorithm applied over the algebra of finite fields of elliptic curves TEŽAVNOST: 200
32 Suite-B Digital Signatures • Elliptic Curve Digital Signature Algorithm (EC-DSA) – FIPS 186 -2 (using the curves with 256 and 384 -bit prime moduli) • Microsoft also supports 521 -bit keys • This is a classical DSA algorithm applied over the algebra of finite fields of elliptic curves TEŽAVNOST: 200
 33 Suite-B Key Exchange (1 of 2) • Elliptic Curve Diffie-Hellman or Elliptic Curve MQV – Draft NIST Special Publication 800 -56 (using the curves with 256 and 384 -bit prime moduli) – Microsoft will also support 521 -bit keys • Recall: DH allows two parties to generate and communicate a secret key to each other (removing the need for key transport) • It is susceptible to man-in-the-middle attacks, so it requires authentication in most applications – Usually done (not very efficiently) with digital signatures TEŽAVNOST: 200
33 Suite-B Key Exchange (1 of 2) • Elliptic Curve Diffie-Hellman or Elliptic Curve MQV – Draft NIST Special Publication 800 -56 (using the curves with 256 and 384 -bit prime moduli) – Microsoft will also support 521 -bit keys • Recall: DH allows two parties to generate and communicate a secret key to each other (removing the need for key transport) • It is susceptible to man-in-the-middle attacks, so it requires authentication in most applications – Usually done (not very efficiently) with digital signatures TEŽAVNOST: 200
 34 Suite-B Key Exchange (2 of 2) • EC-MQV: Menezes, Qu, and Vanstone protocol • Authenticated key exchange • Design similar to DH – Uses the discrete logarithm concept – Also requires a pre-existing, verified and trusted long-term public/private keypair • Which is only used for trust establishment, not for actual encryption or signing • This gives it an important forward-secrecy property • Suite-B uses the EC implementation of MQV TEŽAVNOST: 200
34 Suite-B Key Exchange (2 of 2) • EC-MQV: Menezes, Qu, and Vanstone protocol • Authenticated key exchange • Design similar to DH – Uses the discrete logarithm concept – Also requires a pre-existing, verified and trusted long-term public/private keypair • Which is only used for trust establishment, not for actual encryption or signing • This gives it an important forward-secrecy property • Suite-B uses the EC implementation of MQV TEŽAVNOST: 200
 35 Suite-B Hashing • Secure Hash Algorithm – FIPS 180 -2 (using SHA-256 and SHA-384) • As MD 5 and SHA-0 have been broken and SHA-1 has been allegedly broken we do not have much choice – Almost no alternatives exist • SHA-2 should suffice for a few years, but ultimately it must be replaced – SHA-2 allows: 224, 256, 384, and 512 bit lengths TEŽAVNOST: 200
35 Suite-B Hashing • Secure Hash Algorithm – FIPS 180 -2 (using SHA-256 and SHA-384) • As MD 5 and SHA-0 have been broken and SHA-1 has been allegedly broken we do not have much choice – Almost no alternatives exist • SHA-2 should suffice for a few years, but ultimately it must be replaced – SHA-2 allows: 224, 256, 384, and 512 bit lengths TEŽAVNOST: 200
 36 APIs for Suite-B Today? • There are no widely used or supported libraries or APIs for Suite. B and most operating systems of today • However… TEŽAVNOST: 200
36 APIs for Suite-B Today? • There are no widely used or supported libraries or APIs for Suite. B and most operating systems of today • However… TEŽAVNOST: 200
 37 Cryptography in Widows Vista and Longhorn NB: All Information Subject to Last. Minute Changes TEŽAVNOST: 200
37 Cryptography in Widows Vista and Longhorn NB: All Information Subject to Last. Minute Changes TEŽAVNOST: 200
 38 Trusted Platform Module TPM Chip Version 1. 2 • Hardware present in the computer, e. g. a chip on the motherboard • Securely stores credentials, such as a private key of a machine certificate and is crypto-enabled – Effectively, the essence of a smartcard • TPM can be used to request digital signing of code and files and for mutual authentication of devices • See www. trustedcomputinggroup. org TEŽAVNOST: 200
38 Trusted Platform Module TPM Chip Version 1. 2 • Hardware present in the computer, e. g. a chip on the motherboard • Securely stores credentials, such as a private key of a machine certificate and is crypto-enabled – Effectively, the essence of a smartcard • TPM can be used to request digital signing of code and files and for mutual authentication of devices • See www. trustedcomputinggroup. org TEŽAVNOST: 200
 39 Bit. Locker™ Windows Vista Full Volume Encryption • Bit. Locker strongly encrypts and signs the entire hard drive using Suite-B – TPM chip (see later) provides key management – Can use additional protection factors such as a USB dongle, PIN or password • Any unauthorised off-line modification to your data or OS is discovered and no access is granted – Prevents attacks which use utilities that access the hard drive while Windows is not running and enforces Windows boot process • Protection against data loss when machine (laptop) has been stolen • Essential part of the Secure Startup – Plan data recovery strategy carefully – three scenarios supported (escrow, recovery agent, backup) TEŽAVNOST: 200
39 Bit. Locker™ Windows Vista Full Volume Encryption • Bit. Locker strongly encrypts and signs the entire hard drive using Suite-B – TPM chip (see later) provides key management – Can use additional protection factors such as a USB dongle, PIN or password • Any unauthorised off-line modification to your data or OS is discovered and no access is granted – Prevents attacks which use utilities that access the hard drive while Windows is not running and enforces Windows boot process • Protection against data loss when machine (laptop) has been stolen • Essential part of the Secure Startup – Plan data recovery strategy carefully – three scenarios supported (escrow, recovery agent, backup) TEŽAVNOST: 200
 40 New Cryptography: CNG • CAPI 1. 0 is deprecated – May be dropped altogether in future Windows releases • CNG: Cryptography Next Generation – Open cryptographic API for Windows Vista/Longhorn – Ability to plug in kernel or user mode implementations for: • Proprietary cryptographic algorithms • Replacements for standard cryptographic algorithms • Key Storage Providers (KSP) – Enables cryptography configuration at enterprise and machine levels TEŽAVNOST: 200
40 New Cryptography: CNG • CAPI 1. 0 is deprecated – May be dropped altogether in future Windows releases • CNG: Cryptography Next Generation – Open cryptographic API for Windows Vista/Longhorn – Ability to plug in kernel or user mode implementations for: • Proprietary cryptographic algorithms • Replacements for standard cryptographic algorithms • Key Storage Providers (KSP) – Enables cryptography configuration at enterprise and machine levels TEŽAVNOST: 200
 41 Regulatory Compliance • Windows Vista CNG cryptography will comply with: – Common Criteria (CC) • csrc. nist. gov/cc • Currently in version 3 – FIPS requirements for strong isolation and auditing – US NSA (National Security Agency) CSS (Central Security Service) Suite B TEŽAVNOST: 200
41 Regulatory Compliance • Windows Vista CNG cryptography will comply with: – Common Criteria (CC) • csrc. nist. gov/cc • Currently in version 3 – FIPS requirements for strong isolation and auditing – US NSA (National Security Agency) CSS (Central Security Service) Suite B TEŽAVNOST: 200
 42 Main CNG Features • Cryptography agnostic • Kernel-mode for performance and security (better performance than CAPI 1. 0) • FIPS-140 Certification – 140 -2 and Common Criteria (CC) on selected platforms – 140 -1 everywhere • CC compliance for long-term key storage and audit • Suite-B of course, but also supports all existing algorithms available through Crypto. API 1. 0 • Key Isolation and Storage using TPMs TEŽAVNOST: 200
42 Main CNG Features • Cryptography agnostic • Kernel-mode for performance and security (better performance than CAPI 1. 0) • FIPS-140 Certification – 140 -2 and Common Criteria (CC) on selected platforms – 140 -1 everywhere • CC compliance for long-term key storage and audit • Suite-B of course, but also supports all existing algorithms available through Crypto. API 1. 0 • Key Isolation and Storage using TPMs TEŽAVNOST: 200
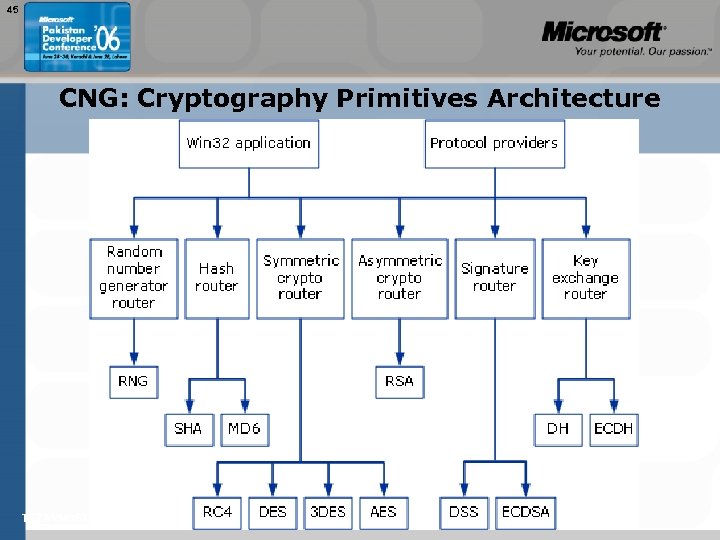
 43 CNG Design • Three APIs within CNG: – Cryptography Primitives • The “main” API: all algorithms are here – Key Storage and Retrieval • Allows interaction with the new Key Storage Providers concept – Supports existing devices (smartcards) and future types of tokens • Interface for all secure key creation, including the EC-DH and EC-MQV* methods • Interface for import and export of keys using PKCS #7 and #8 – Cryptography Configuration • For use and installation of additional cryptographic providers Read: msdn. microsoft. com/library/default. asp? url=/library/enus/seccng/security/about_cng. asp? frame=true TEŽAVNOST: 200
43 CNG Design • Three APIs within CNG: – Cryptography Primitives • The “main” API: all algorithms are here – Key Storage and Retrieval • Allows interaction with the new Key Storage Providers concept – Supports existing devices (smartcards) and future types of tokens • Interface for all secure key creation, including the EC-DH and EC-MQV* methods • Interface for import and export of keys using PKCS #7 and #8 – Cryptography Configuration • For use and installation of additional cryptographic providers Read: msdn. microsoft. com/library/default. asp? url=/library/enus/seccng/security/about_cng. asp? frame=true TEŽAVNOST: 200
 44 Other APIs • In addition to CNG: –. NET Framework 2. 0 • Microsoft will extend the. NET Fx library to cover CNG (not available at present) – TBS: TPM Base Services • For interaction with Trusted Platform Modules – Certificate Enrollment API TEŽAVNOST: 200
44 Other APIs • In addition to CNG: –. NET Framework 2. 0 • Microsoft will extend the. NET Fx library to cover CNG (not available at present) – TBS: TPM Base Services • For interaction with Trusted Platform Modules – Certificate Enrollment API TEŽAVNOST: 200
 45 CNG: Cryptography Primitives Architecture TEŽAVNOST: 200
45 CNG: Cryptography Primitives Architecture TEŽAVNOST: 200
 46 Using CNG – Two Models • Depending on your needs, you use CNG with: – Algorithms and keys provided by a Key Storage provider (such as smartcards) • All function names begin with “N”, such as NCrypt. Open. Storage. Provider – Algorithms and keys generated by the operating system’s software providers • All function names begin with “B”, such as BCrypt. Open. Algorithm. Provider • I only explain “B” in next slides, but “N” is very similar TEŽAVNOST: 200
46 Using CNG – Two Models • Depending on your needs, you use CNG with: – Algorithms and keys provided by a Key Storage provider (such as smartcards) • All function names begin with “N”, such as NCrypt. Open. Storage. Provider – Algorithms and keys generated by the operating system’s software providers • All function names begin with “B”, such as BCrypt. Open. Algorithm. Provider • I only explain “B” in next slides, but “N” is very similar TEŽAVNOST: 200
 47 Using CNG - Concepts • Designed as a Win 32 library (work in. NET) • You don’t need to be aware of any specific providers on your system (unlike in Crypto. API) • Instead, you request an algorithm, and the system offer you the default best available – Of course, you can always chose a specific provider if you prefer, by enumerating them first • BCrypt. Enum. Registered. Providers – You can check properties of a provider before you use it • BCrypt. Query. Provider. Registration – You can register a specific provider • BCrypt. Register. Provider • This solves the problem of updates, when better implementations are found in the future TEŽAVNOST: 200
47 Using CNG - Concepts • Designed as a Win 32 library (work in. NET) • You don’t need to be aware of any specific providers on your system (unlike in Crypto. API) • Instead, you request an algorithm, and the system offer you the default best available – Of course, you can always chose a specific provider if you prefer, by enumerating them first • BCrypt. Enum. Registered. Providers – You can check properties of a provider before you use it • BCrypt. Query. Provider. Registration – You can register a specific provider • BCrypt. Register. Provider • This solves the problem of updates, when better implementations are found in the future TEŽAVNOST: 200
 48 Using CNG – Encryption Steps • Generally, follow this process: – Open a CNG Algorithm Provider • BCrypt. Open. Algorithm. Provider – Generate or import keys – Calculate the size of encrypted data • Call BCrypt. Encrypt with NULL for pb. Input paramter – Encrypt data by calling BCrypt. Encrypt again • Repeat this step as needed for all data, remembering to use the correct form of operating mode (chaining) – Output or persist the result – Close the provider, unless you want to cache it for later use • BCrypt. Close. Algorithm. Provider TEŽAVNOST: 200
48 Using CNG – Encryption Steps • Generally, follow this process: – Open a CNG Algorithm Provider • BCrypt. Open. Algorithm. Provider – Generate or import keys – Calculate the size of encrypted data • Call BCrypt. Encrypt with NULL for pb. Input paramter – Encrypt data by calling BCrypt. Encrypt again • Repeat this step as needed for all data, remembering to use the correct form of operating mode (chaining) – Output or persist the result – Close the provider, unless you want to cache it for later use • BCrypt. Close. Algorithm. Provider TEŽAVNOST: 200
 49 Randomness • Use BCrypt. Gen. Random • You can use a specific algorithm, otherwise the default is used, which is FIPS-186 -2 compliant – It uses entropy gathered by the provider over the time – You can add your own entropy as a parameter TEŽAVNOST: 200
49 Randomness • Use BCrypt. Gen. Random • You can use a specific algorithm, otherwise the default is used, which is FIPS-186 -2 compliant – It uses entropy gathered by the provider over the time – You can add your own entropy as a parameter TEŽAVNOST: 200
 50 Summary • Today’s cryptography has just accelerated its evolution • Windows Vista and Longhorn Servers will be at the front of innovation in this field • You can benefit from the increased security by using Bit. Locker or the APIs such as CNG • It is an exciting time to be using cryptography! TEŽAVNOST: 200
50 Summary • Today’s cryptography has just accelerated its evolution • Windows Vista and Longhorn Servers will be at the front of innovation in this field • You can benefit from the increased security by using Bit. Locker or the APIs such as CNG • It is an exciting time to be using cryptography! TEŽAVNOST: 200
 51 References • Visit msdn. microsoft. com/security and www. microsoft. com/technet/security • Read sci. crypt (incl. archives) • For more detail, read: – Cryptography: An Introduction, N. Smart, Mc. Graw-Hill, ISBN 0 -07709987 -7 – Practical Cryptography, N. Ferguson & B. Schneier, Wiley, ISBN 0 -47122357 -3 – Contemporary Cryptography, R. Oppliger, Artech House, ISBN 1 -58053 -642 -5 (to be published May 2005, see http: //www. esecurity. ch/Books/cryptography. html) – Applied Cryptography, B. Schneier, John Wiley & Sons, ISBN 0 -47111709 -9 – Handbook of Applied Cryptography, A. J. Menezes, CRC Press, ISBN 08493 -8523 -7, www. cacr. math. uwaterloo. ca/hac (free PDF) – PKI, A. Nash et al. , RSA Press, ISBN 0 -07 -213123 -3 – Foundations of Cryptography, O. Goldereich, www. eccc. uni-trier. de/eccc-local/ECCCBooks/oded_book_readme. html – Cryptography in C and C++, M. Welschenbach, Apress, TEŽAVNOST: 200 ISBN 1 -893115 -95 -X (includes code samples CD)
51 References • Visit msdn. microsoft. com/security and www. microsoft. com/technet/security • Read sci. crypt (incl. archives) • For more detail, read: – Cryptography: An Introduction, N. Smart, Mc. Graw-Hill, ISBN 0 -07709987 -7 – Practical Cryptography, N. Ferguson & B. Schneier, Wiley, ISBN 0 -47122357 -3 – Contemporary Cryptography, R. Oppliger, Artech House, ISBN 1 -58053 -642 -5 (to be published May 2005, see http: //www. esecurity. ch/Books/cryptography. html) – Applied Cryptography, B. Schneier, John Wiley & Sons, ISBN 0 -47111709 -9 – Handbook of Applied Cryptography, A. J. Menezes, CRC Press, ISBN 08493 -8523 -7, www. cacr. math. uwaterloo. ca/hac (free PDF) – PKI, A. Nash et al. , RSA Press, ISBN 0 -07 -213123 -3 – Foundations of Cryptography, O. Goldereich, www. eccc. uni-trier. de/eccc-local/ECCCBooks/oded_book_readme. html – Cryptography in C and C++, M. Welschenbach, Apress, TEŽAVNOST: 200 ISBN 1 -893115 -95 -X (includes code samples CD)


