64a786c9a0aa92f222653648ae8611c8.ppt
- Количество слайдов: 17
 New Challenges in Securing our Communication Infrastructure Wade Trappe
New Challenges in Securing our Communication Infrastructure Wade Trappe
 Agenda l Wireless Overview – State of the Wireless Union: Where are we? – Vision for 4 G l Security Challenges for Future Wireless Networks: – – – 3 G Multicast Security Authentication in Broadcast Environments Security in Ad Hoc Networks Biologically-Inspired Self-Healing Frameworks Networks of Networks Security Issues
Agenda l Wireless Overview – State of the Wireless Union: Where are we? – Vision for 4 G l Security Challenges for Future Wireless Networks: – – – 3 G Multicast Security Authentication in Broadcast Environments Security in Ad Hoc Networks Biologically-Inspired Self-Healing Frameworks Networks of Networks Security Issues
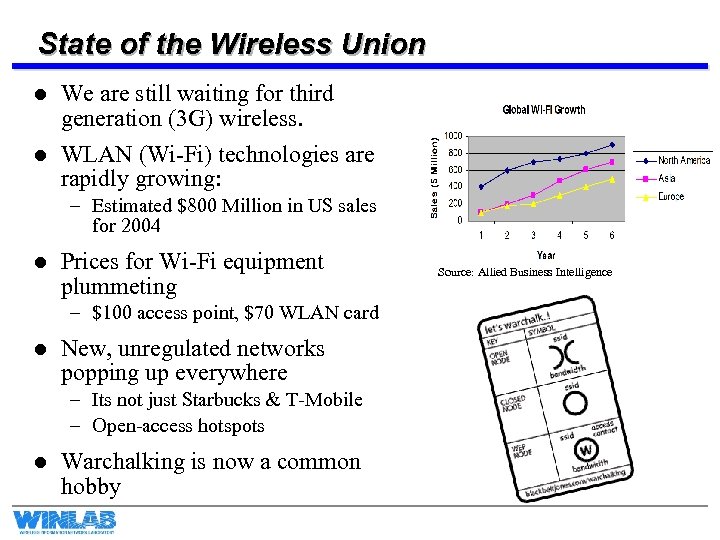 State of the Wireless Union l We are still waiting for third generation (3 G) wireless. l WLAN (Wi-Fi) technologies are rapidly growing: – Estimated $800 Million in US sales for 2004 l Prices for Wi-Fi equipment plummeting – $100 access point, $70 WLAN card l New, unregulated networks popping up everywhere – Its not just Starbucks & T-Mobile – Open-access hotspots l Warchalking is now a common hobby Source: Allied Business Intelligence
State of the Wireless Union l We are still waiting for third generation (3 G) wireless. l WLAN (Wi-Fi) technologies are rapidly growing: – Estimated $800 Million in US sales for 2004 l Prices for Wi-Fi equipment plummeting – $100 access point, $70 WLAN card l New, unregulated networks popping up everywhere – Its not just Starbucks & T-Mobile – Open-access hotspots l Warchalking is now a common hobby Source: Allied Business Intelligence
 Vision for the Fourth Generation l Wireless devices will continue to drop in price – Wireless sensors will be deployed everywhere – Ability to monitor everything, from temperature to traffic – Remote sensing and autonomic living applications l Next generation wireless systems (4 G) will seek to facilitate mass market services with new network architecture: – Self-organizing, ad-hoc wireless access networks: Ad-hoc wireless network protocols which support multihop and peer-to-peer service models, particularly for low-tier uses (in-home, sensors, etc. ) – Networks of networks: Future wireless networks will support co-existence of multiple types of networks l Security will be a critical issue: – Unregulated networks will provide an untraceable platform to launch network attacks – Mobility and power-efficiency are still concerns
Vision for the Fourth Generation l Wireless devices will continue to drop in price – Wireless sensors will be deployed everywhere – Ability to monitor everything, from temperature to traffic – Remote sensing and autonomic living applications l Next generation wireless systems (4 G) will seek to facilitate mass market services with new network architecture: – Self-organizing, ad-hoc wireless access networks: Ad-hoc wireless network protocols which support multihop and peer-to-peer service models, particularly for low-tier uses (in-home, sensors, etc. ) – Networks of networks: Future wireless networks will support co-existence of multiple types of networks l Security will be a critical issue: – Unregulated networks will provide an untraceable platform to launch network attacks – Mobility and power-efficiency are still concerns
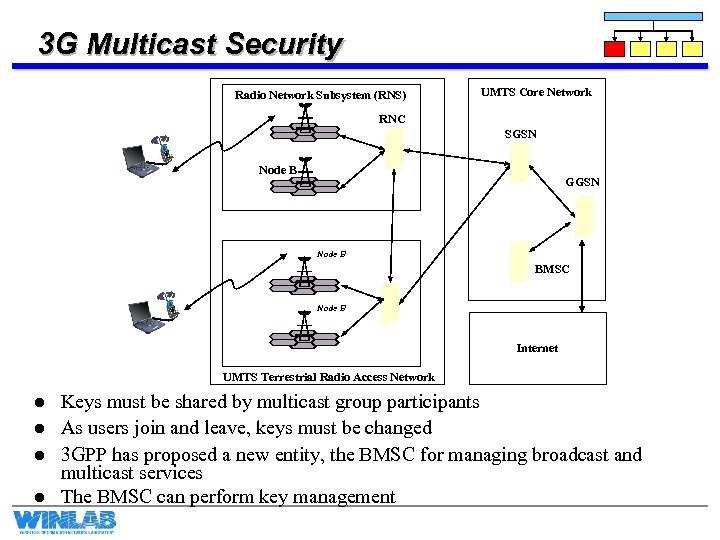 3 G Multicast Security Radio Network Subsystem (RNS) UMTS Core Network RNC SGSN Node B GGSN Node B BMSC Node B Internet UMTS Terrestrial Radio Access Network l l Keys must be shared by multicast group participants As users join and leave, keys must be changed 3 GPP has proposed a new entity, the BMSC for managing broadcast and multicast services The BMSC can perform key management
3 G Multicast Security Radio Network Subsystem (RNS) UMTS Core Network RNC SGSN Node B GGSN Node B BMSC Node B Internet UMTS Terrestrial Radio Access Network l l Keys must be shared by multicast group participants As users join and leave, keys must be changed 3 GPP has proposed a new entity, the BMSC for managing broadcast and multicast services The BMSC can perform key management
 3 G Multicast Security l 3 GPP currently is investigating several multicast frameworks l To optimize key management, one should match the key tree to underlying multicast topology l 3 GPP has not decided on a multicast topology l We are examining the performance of multicast key management at the BMSC for different 3 G multicast scenarios l Examine the issue of key management during handoff between node-B’s and RNCs Prototype Secure Chat Application has been developed • Server is implemented in J 2 SE • Clients are implemented in J 2 ME
3 G Multicast Security l 3 GPP currently is investigating several multicast frameworks l To optimize key management, one should match the key tree to underlying multicast topology l 3 GPP has not decided on a multicast topology l We are examining the performance of multicast key management at the BMSC for different 3 G multicast scenarios l Examine the issue of key management during handoff between node-B’s and RNCs Prototype Secure Chat Application has been developed • Server is implemented in J 2 SE • Clients are implemented in J 2 ME
 Broadcast/Multicast Authentication l Important challenge facing secure multicast communication is data authentication: – Ensures data is from trusted source – Ensures data was not modified en route l Unicast Data Authentication uses standard cryptographic techniques: – Digital Signatures: (RSA, DSA) u Drawbacks: Inefficient due to: l l u Large per packet computation Large communication overhead Note: Drawbacks are not critical in many applications. – Message Authentication Codes (MAC): (HMAC-MD 5) u u Class of symmetric keyed one-way hash function Advantages: l l l Computationally efficient Compressed code Computationally non-invertible
Broadcast/Multicast Authentication l Important challenge facing secure multicast communication is data authentication: – Ensures data is from trusted source – Ensures data was not modified en route l Unicast Data Authentication uses standard cryptographic techniques: – Digital Signatures: (RSA, DSA) u Drawbacks: Inefficient due to: l l u Large per packet computation Large communication overhead Note: Drawbacks are not critical in many applications. – Message Authentication Codes (MAC): (HMAC-MD 5) u u Class of symmetric keyed one-way hash function Advantages: l l l Computationally efficient Compressed code Computationally non-invertible
 Multicast Authentication l Multicast source authentication is more complex than unicast: – Symmetric Key Cryptography cannot be used u u Key is known to all receivers Packets can be forged by any receivers – Asymmetric key cryptography is required – Lost packets are not retransmitted l Digital signature schemes provide good authentication: – Each message is signed by appending digital signature – Significant drawbacks for realtime, low-power multicast applications: u u Time-to-sign and time-to-verify Bandwidth and overhead. l We want a technique that will take advantage of both l One approach: Delayed key disclosure
Multicast Authentication l Multicast source authentication is more complex than unicast: – Symmetric Key Cryptography cannot be used u u Key is known to all receivers Packets can be forged by any receivers – Asymmetric key cryptography is required – Lost packets are not retransmitted l Digital signature schemes provide good authentication: – Each message is signed by appending digital signature – Significant drawbacks for realtime, low-power multicast applications: u u Time-to-sign and time-to-verify Bandwidth and overhead. l We want a technique that will take advantage of both l One approach: Delayed key disclosure
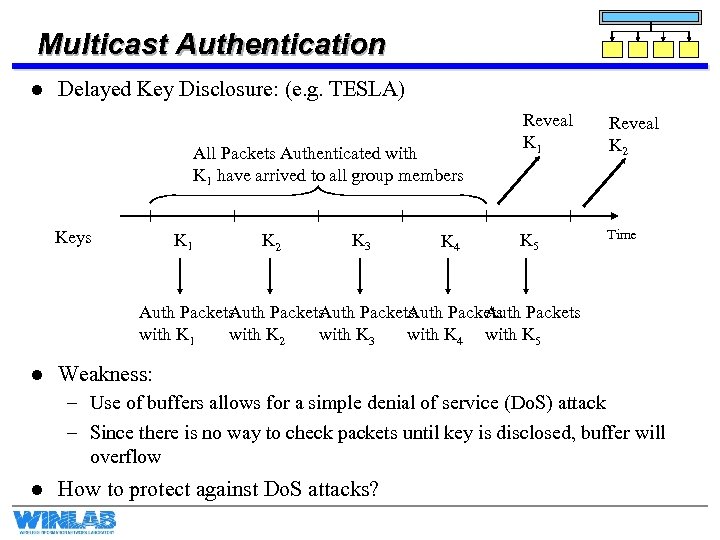 Multicast Authentication l Delayed Key Disclosure: (e. g. TESLA) All Packets Authenticated with K 1 have arrived to all group members Keys K 1 K 2 K 3 K 4 Reveal K 1 Reveal K 2 K 5 Time Auth Packets Packets Auth with K 1 with K 2 with K 3 with K 4 with K 5 l Weakness: – Use of buffers allows for a simple denial of service (Do. S) attack – Since there is no way to check packets until key is disclosed, buffer will overflow l How to protect against Do. S attacks?
Multicast Authentication l Delayed Key Disclosure: (e. g. TESLA) All Packets Authenticated with K 1 have arrived to all group members Keys K 1 K 2 K 3 K 4 Reveal K 1 Reveal K 2 K 5 Time Auth Packets Packets Auth with K 1 with K 2 with K 3 with K 4 with K 5 l Weakness: – Use of buffers allows for a simple denial of service (Do. S) attack – Since there is no way to check packets until key is disclosed, buffer will overflow l How to protect against Do. S attacks?
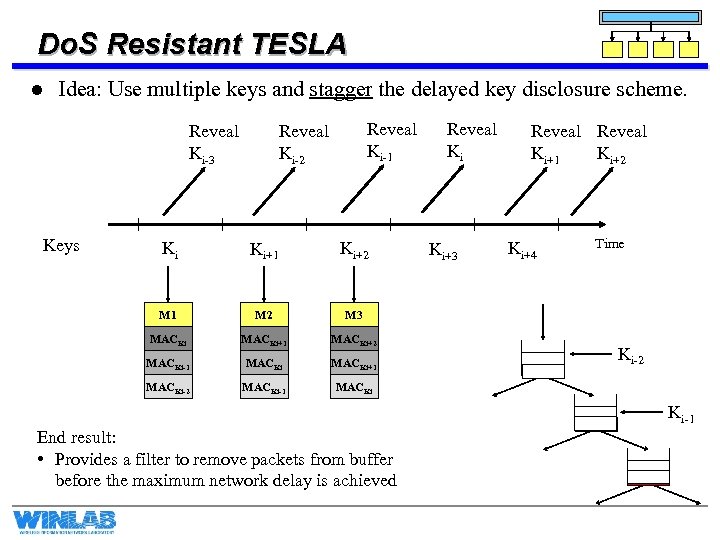 Do. S Resistant TESLA l Idea: Use multiple keys and stagger the delayed key disclosure scheme. Reveal Ki-3 Keys Reveal Ki-1 Reveal Ki-2 Ki Ki+1 Ki+2 M 1 M 2 MACKi+1 MACKi-2 MACKi-1 MACKi End result: • Provides a filter to remove packets from buffer before the maximum network delay is achieved Ki+3 Ki+4 Time MACKi+2 MACKi-1 Reveal Ki+1 Ki+2 M 3 MACKi Reveal Ki Ki-2 P 1 Ki-1 P 1
Do. S Resistant TESLA l Idea: Use multiple keys and stagger the delayed key disclosure scheme. Reveal Ki-3 Keys Reveal Ki-1 Reveal Ki-2 Ki Ki+1 Ki+2 M 1 M 2 MACKi+1 MACKi-2 MACKi-1 MACKi End result: • Provides a filter to remove packets from buffer before the maximum network delay is achieved Ki+3 Ki+4 Time MACKi+2 MACKi-1 Reveal Ki+1 Ki+2 M 3 MACKi Reveal Ki Ki-2 P 1 Ki-1 P 1
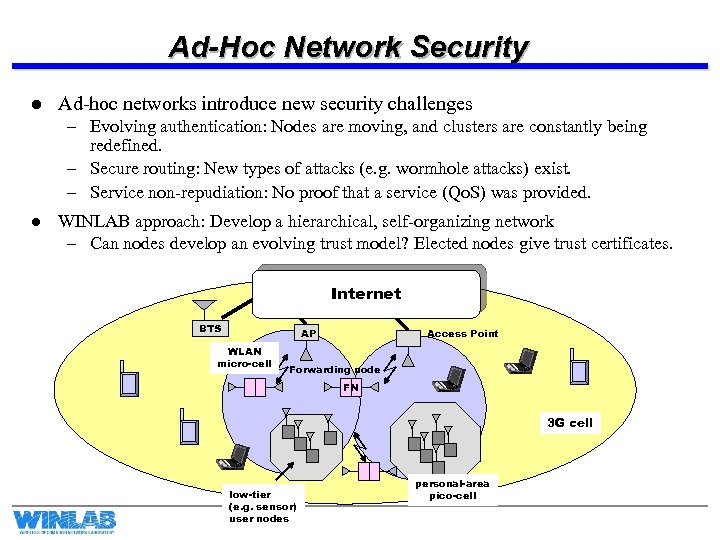 Ad-Hoc Network Security l Ad-hoc networks introduce new security challenges – Evolving authentication: Nodes are moving, and clusters are constantly being redefined. – Secure routing: New types of attacks (e. g. wormhole attacks) exist. – Service non-repudiation: No proof that a service (Qo. S) was provided. l WINLAB approach: Develop a hierarchical, self-organizing network – Can nodes develop an evolving trust model? Elected nodes give trust certificates. Internet BTS AP WLAN micro-cell Access Point Forwarding node FN 3 G cell low-tier (e. g. sensor) user nodes personal-area pico-cell
Ad-Hoc Network Security l Ad-hoc networks introduce new security challenges – Evolving authentication: Nodes are moving, and clusters are constantly being redefined. – Secure routing: New types of attacks (e. g. wormhole attacks) exist. – Service non-repudiation: No proof that a service (Qo. S) was provided. l WINLAB approach: Develop a hierarchical, self-organizing network – Can nodes develop an evolving trust model? Elected nodes give trust certificates. Internet BTS AP WLAN micro-cell Access Point Forwarding node FN 3 G cell low-tier (e. g. sensor) user nodes personal-area pico-cell
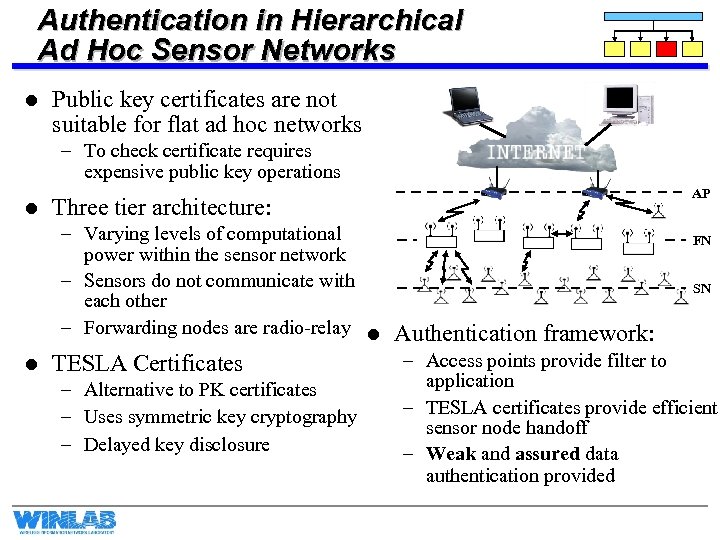 Authentication in Hierarchical Ad Hoc Sensor Networks l Public key certificates are not suitable for flat ad hoc networks – To check certificate requires expensive public key operations l AP Three tier architecture: – Varying levels of computational FN power within the sensor network – Sensors do not communicate with SN each other – Forwarding nodes are radio-relay l Authentication framework: – Access points provide filter to l TESLA Certificates application – Alternative to PK certificates – TESLA certificates provide efficient – Uses symmetric key cryptography sensor node handoff – Delayed key disclosure – Weak and assured data authentication provided
Authentication in Hierarchical Ad Hoc Sensor Networks l Public key certificates are not suitable for flat ad hoc networks – To check certificate requires expensive public key operations l AP Three tier architecture: – Varying levels of computational FN power within the sensor network – Sensors do not communicate with SN each other – Forwarding nodes are radio-relay l Authentication framework: – Access points provide filter to l TESLA Certificates application – Alternative to PK certificates – TESLA certificates provide efficient – Uses symmetric key cryptography sensor node handoff – Delayed key disclosure – Weak and assured data authentication provided
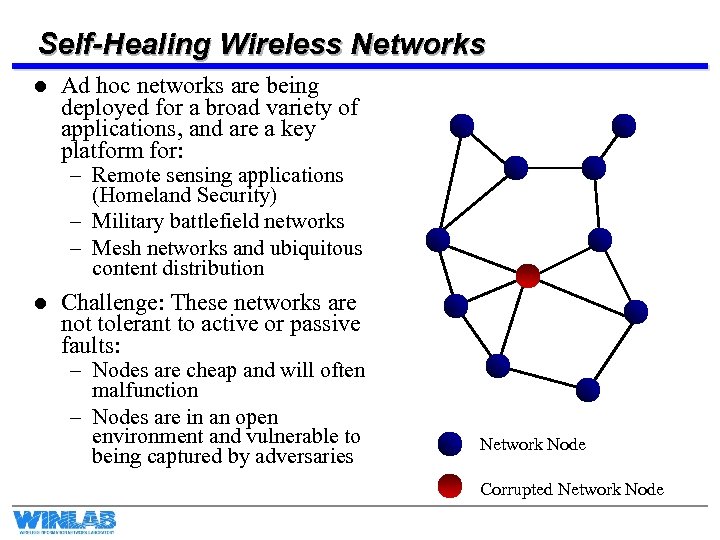 Self-Healing Wireless Networks l Ad hoc networks are being deployed for a broad variety of applications, and are a key platform for: – Remote sensing applications (Homeland Security) – Military battlefield networks – Mesh networks and ubiquitous content distribution l Challenge: These networks are not tolerant to active or passive faults: – Nodes are cheap and will often malfunction – Nodes are in an open environment and vulnerable to being captured by adversaries Network Node Corrupted Network Node
Self-Healing Wireless Networks l Ad hoc networks are being deployed for a broad variety of applications, and are a key platform for: – Remote sensing applications (Homeland Security) – Military battlefield networks – Mesh networks and ubiquitous content distribution l Challenge: These networks are not tolerant to active or passive faults: – Nodes are cheap and will often malfunction – Nodes are in an open environment and vulnerable to being captured by adversaries Network Node Corrupted Network Node
 Self-healing framework l l l In nature, we have many cases where systems get infected and must repair themselves Ad hoc networks should emulate nature and heal themselves! Model: Human immune system – Leuocytes (white blood cells): There are two types, those that develop in lymph nodes and those that develop in bone marrow – Killer T-cells: Destroy antigens either by themselves, or by recruiting other white blood cells – Lymphocytes: Produce antibodies, that seek to surround and cover an antigen, rendering it harmless until a phage can arrive to destroy the neutralized antigen – Chemotaxis: Leuocytes find their way to an antigen by following a chemical trail of “bread crumbs”
Self-healing framework l l l In nature, we have many cases where systems get infected and must repair themselves Ad hoc networks should emulate nature and heal themselves! Model: Human immune system – Leuocytes (white blood cells): There are two types, those that develop in lymph nodes and those that develop in bone marrow – Killer T-cells: Destroy antigens either by themselves, or by recruiting other white blood cells – Lymphocytes: Produce antibodies, that seek to surround and cover an antigen, rendering it harmless until a phage can arrive to destroy the neutralized antigen – Chemotaxis: Leuocytes find their way to an antigen by following a chemical trail of “bread crumbs”
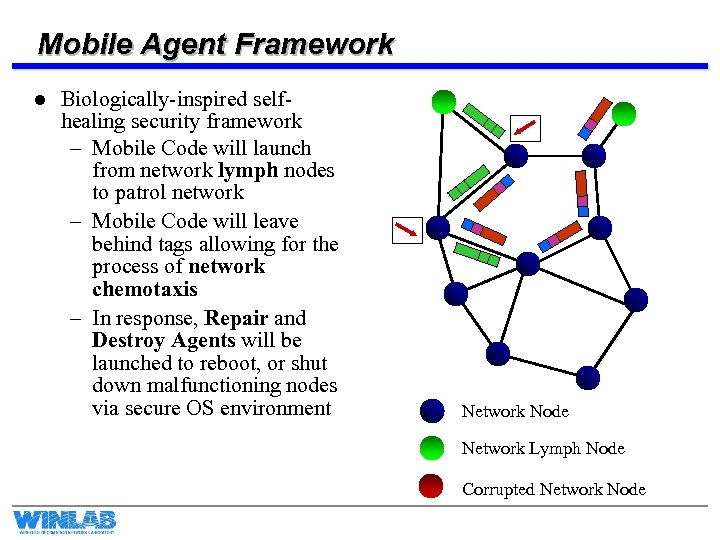 Mobile Agent Framework l Biologically-inspired selfhealing security framework – Mobile Code will launch from network lymph nodes to patrol network – Mobile Code will leave behind tags allowing for the process of network chemotaxis – In response, Repair and Destroy Agents will be launched to reboot, or shut down malfunctioning nodes via secure OS environment Network Node Network Lymph Node Corrupted Network Node
Mobile Agent Framework l Biologically-inspired selfhealing security framework – Mobile Code will launch from network lymph nodes to patrol network – Mobile Code will leave behind tags allowing for the process of network chemotaxis – In response, Repair and Destroy Agents will be launched to reboot, or shut down malfunctioning nodes via secure OS environment Network Node Network Lymph Node Corrupted Network Node
 Enabling Technologies l Enabling Technologies to be Researched: – Smart Messages (SMs): Migratory execution units that execute on ad hoc nodes, and will form the different types of mobile agents involved in a network immune system – Trajectory Routing: Self-routing mechanisms for mobile code capable of finding fast and efficient route to faulty node – Anomaly Detection: Statistical and policy-based detection mechanisms for identifying faulty network nodes – Flexible Security Policies: Describe how the network immune system responds to different types of corruptions or threats – Authorization and Secure OS: Each node must have a secure environment from which mobile agents perform their functions
Enabling Technologies l Enabling Technologies to be Researched: – Smart Messages (SMs): Migratory execution units that execute on ad hoc nodes, and will form the different types of mobile agents involved in a network immune system – Trajectory Routing: Self-routing mechanisms for mobile code capable of finding fast and efficient route to faulty node – Anomaly Detection: Statistical and policy-based detection mechanisms for identifying faulty network nodes – Flexible Security Policies: Describe how the network immune system responds to different types of corruptions or threats – Authorization and Secure OS: Each node must have a secure environment from which mobile agents perform their functions
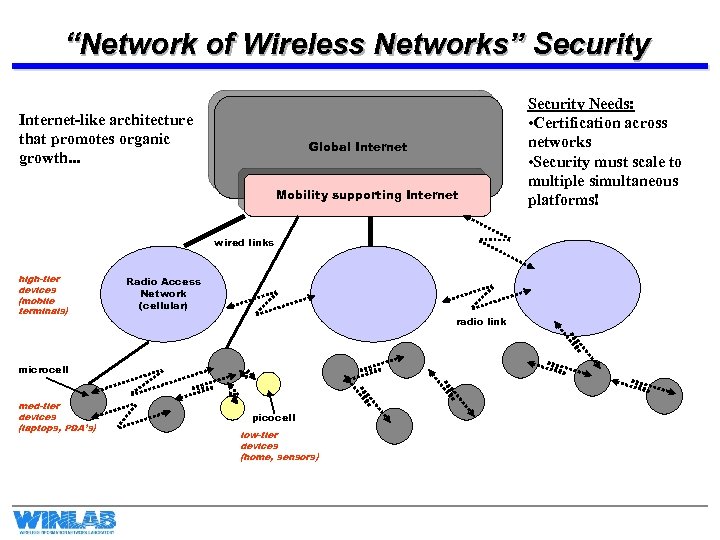 “Network of Wireless Networks” Security Internet-like architecture that promotes organic growth. . . Global Internet Mobility supporting Internet wired links high-tier devices (mobile terminals) Radio Access Network (cellular) radio link microcell med-tier devices (laptops, PDA’s) picocell low-tier devices (home, sensors) Security Needs: • Certification across networks • Security must scale to multiple simultaneous platforms!
“Network of Wireless Networks” Security Internet-like architecture that promotes organic growth. . . Global Internet Mobility supporting Internet wired links high-tier devices (mobile terminals) Radio Access Network (cellular) radio link microcell med-tier devices (laptops, PDA’s) picocell low-tier devices (home, sensors) Security Needs: • Certification across networks • Security must scale to multiple simultaneous platforms!


