60b172ba5ce145666ed95d626652c872.ppt
- Количество слайдов: 36
 NETWORKS Fall 2009 1
NETWORKS Fall 2009 1
 Review – Last Lecture • Computer Crimes • Legal Issues • Example Attack 2
Review – Last Lecture • Computer Crimes • Legal Issues • Example Attack 2
 Review - Legal Issues • If your system is broken into or is used to break into someone else’s system who is at fault? • Who can be sued and for how much? • What is your liability? • There is new legal ground being explored that may result in many multi-million dollar lawsuits in the near future. 3
Review - Legal Issues • If your system is broken into or is used to break into someone else’s system who is at fault? • Who can be sued and for how much? • What is your liability? • There is new legal ground being explored that may result in many multi-million dollar lawsuits in the near future. 3
 Review - Important Observations • Checking things only once is a problem – One of the primary classes of attacks on a host is to allow a program to validate the ownership or permissions of a file once and then to quickly introduce a different file before the program notices • Computers that are not in a paranoid mode, doing both forward and reverse DNS lookups when establishing a connection, are fairly vulnerable to being spoofed 4
Review - Important Observations • Checking things only once is a problem – One of the primary classes of attacks on a host is to allow a program to validate the ownership or permissions of a file once and then to quickly introduce a different file before the program notices • Computers that are not in a paranoid mode, doing both forward and reverse DNS lookups when establishing a connection, are fairly vulnerable to being spoofed 4
 OUTLINE • Computer Crimes • Application Attacks – Printers – DNS (part 1) 5
OUTLINE • Computer Crimes • Application Attacks – Printers – DNS (part 1) 5
 Computer Crimes 6
Computer Crimes 6
 Stolen Data (again) • The Port of Seattle says six computer disks are missing from the ID Badging Office at Seattle-Tacoma International Airport. – The disks contain sensitive personal information scanned from paper forms; the data include names, SSNs and driver's license numbers. – The breach affects 6, 936 current and former employees at the airport. 7
Stolen Data (again) • The Port of Seattle says six computer disks are missing from the ID Badging Office at Seattle-Tacoma International Airport. – The disks contain sensitive personal information scanned from paper forms; the data include names, SSNs and driver's license numbers. – The breach affects 6, 936 current and former employees at the airport. 7
 2007 Problems • According to a report from SANS, laptop security, cell phone worms and Vo. IP fraud top the list of trends to pay heed to in 2007. • As desktop computers are being replaced with more portable laptops, more data will be taken out of organizations; this is especially problematic when combined with a lack of encryption on the laptops and the possibility of the computers being lost or stolen. 8
2007 Problems • According to a report from SANS, laptop security, cell phone worms and Vo. IP fraud top the list of trends to pay heed to in 2007. • As desktop computers are being replaced with more portable laptops, more data will be taken out of organizations; this is especially problematic when combined with a lack of encryption on the laptops and the possibility of the computers being lost or stolen. 8
 Attacks from China • Cyber attackers working through servers in China have been targeting computers at the US Department of Commerce's Bureau of Industry and Security (BIS) for more than a month, – BIS oversees US exports of products that have both commercial and military uses. – The computers were attacked at night in an attempt to access BIS user accounts when they were unmanned; attackers managed to install rootkits. – BIS has decided to replace the infected workstations rather than try to clean them. – BIS has also blocked most Internet access; only stand-alone workstations that are not connected to the bureau's internal network are allowed to access the Internet 9
Attacks from China • Cyber attackers working through servers in China have been targeting computers at the US Department of Commerce's Bureau of Industry and Security (BIS) for more than a month, – BIS oversees US exports of products that have both commercial and military uses. – The computers were attacked at night in an attempt to access BIS user accounts when they were unmanned; attackers managed to install rootkits. – BIS has decided to replace the infected workstations rather than try to clean them. – BIS has also blocked most Internet access; only stand-alone workstations that are not connected to the bureau's internal network are allowed to access the Internet 9
 Application Attacks - Printers 10
Application Attacks - Printers 10
 Printers • Why users still think printers are safe – Users have had a long history with printers: Printers as old as computers – Serial/Parallel printers: local connections – Print Servers: the server is more likely to be compromised • Why printers are not safe – Network Printers • Manufacturers now adding protocols to printers • Large number of insecure protocols • Functionality over security 11
Printers • Why users still think printers are safe – Users have had a long history with printers: Printers as old as computers – Serial/Parallel printers: local connections – Print Servers: the server is more likely to be compromised • Why printers are not safe – Network Printers • Manufacturers now adding protocols to printers • Large number of insecure protocols • Functionality over security 11
 Other Hardware • Other insecure devices include: – – Webcams Photocopiers Web appliances Network File Systems • Again, Functionality over security 12
Other Hardware • Other insecure devices include: – – Webcams Photocopiers Web appliances Network File Systems • Again, Functionality over security 12
 Physical Attacks • Physical and Addressable devices – Can be easily replaced by another device – Can also have a device placed inline – Users innocently unplug devices for resources • Traffic for printer is now intercepted by another device – Replace printer with espionage-friendly devices • Firmware – Firmware is static software – Can be disassembled or source code stolen – Recompiled and updated via firmware update 13
Physical Attacks • Physical and Addressable devices – Can be easily replaced by another device – Can also have a device placed inline – Users innocently unplug devices for resources • Traffic for printer is now intercepted by another device – Replace printer with espionage-friendly devices • Firmware – Firmware is static software – Can be disassembled or source code stolen – Recompiled and updated via firmware update 13
 Remote Access • Allowing remote access to any machine is risky • Allowing remote access to a printer is very risky • Allowing unauthenticated and unencrypted remote access to the printer’s configuration mechanism is just plain stupid • There a lot of stupid printers out there 14
Remote Access • Allowing remote access to any machine is risky • Allowing remote access to a printer is very risky • Allowing unauthenticated and unencrypted remote access to the printer’s configuration mechanism is just plain stupid • There a lot of stupid printers out there 14
 Simple Network Management Protocol • SNMP by its very nature is unauthenticated remote access – Extremely simple authentication, prone to guessing or sniffing – Once authentication is broken, read or write access to configuration is possible – SNMP default on most printers – Few allow it to be turned off • Backdoors are a common (and flawed) access control mechanism – Used to access system after administrator locks it down – Usually done in the name of technical support or licensing • Forgotten passwords • Unlicensed software • Relies on security solely through obscurity for protection and rarely protected by other means 15
Simple Network Management Protocol • SNMP by its very nature is unauthenticated remote access – Extremely simple authentication, prone to guessing or sniffing – Once authentication is broken, read or write access to configuration is possible – SNMP default on most printers – Few allow it to be turned off • Backdoors are a common (and flawed) access control mechanism – Used to access system after administrator locks it down – Usually done in the name of technical support or licensing • Forgotten passwords • Unlicensed software • Relies on security solely through obscurity for protection and rarely protected by other means 15
 Typical Printer Backdoor • One of the best examples of a printer back door – Web-server on printer allows unfiltered and unauthenticated access to the printer’s configuration by simply entering a simple URL in a web-browser…(http: //printername/ncl_subjects. html) – Access to more configuration options than afforded anywhere else – Changes made are instant and unauthenticated – Allowed plain-text access to the administrator password – Number of potential denial of service and access to/distribution of information attacks given to an unauthenticated attacker 16
Typical Printer Backdoor • One of the best examples of a printer back door – Web-server on printer allows unfiltered and unauthenticated access to the printer’s configuration by simply entering a simple URL in a web-browser…(http: //printername/ncl_subjects. html) – Access to more configuration options than afforded anywhere else – Changes made are instant and unauthenticated – Allowed plain-text access to the administrator password – Number of potential denial of service and access to/distribution of information attacks given to an unauthenticated attacker 16
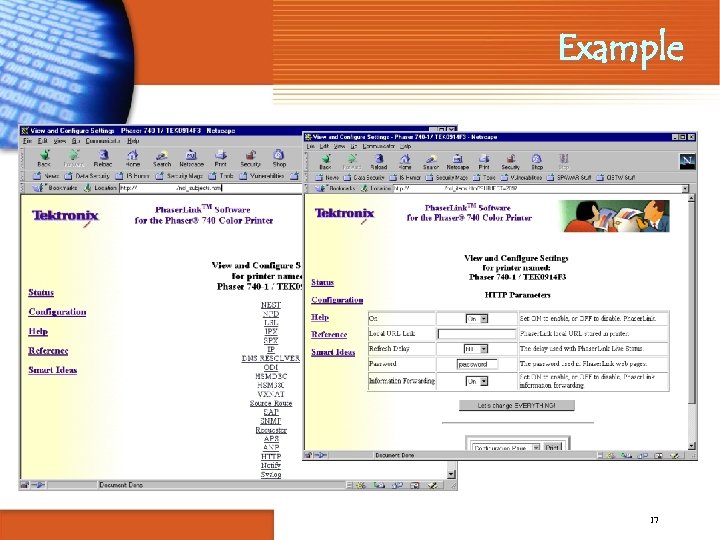 Example 17
Example 17
 Do. S Attack 1 • Using unauthenticated remote access methods to Deny Service – Changing the IP address to non-existant or duplicate address – Clicking the "Reset Printer to Factory Default" option – Changing the run-level for the printer to "Emergency Power Off" – Removing or changing services running on the machine – Changing passwords 18
Do. S Attack 1 • Using unauthenticated remote access methods to Deny Service – Changing the IP address to non-existant or duplicate address – Clicking the "Reset Printer to Factory Default" option – Changing the run-level for the printer to "Emergency Power Off" – Removing or changing services running on the machine – Changing passwords 18
 Do. S Attack 2 • The easiest Do. S to perform is to overwhelm the printer with jobs • Anonymous print capabilities to Do. S printer – Allows attacker to waste physical resources – Administrator must cancel the print jobs manually • Multiple idle connections to App. Socket – HP only allows 8 concurrent connections, with no timeout – New connections get "Connection Refused" 19
Do. S Attack 2 • The easiest Do. S to perform is to overwhelm the printer with jobs • Anonymous print capabilities to Do. S printer – Allows attacker to waste physical resources – Administrator must cancel the print jobs manually • Multiple idle connections to App. Socket – HP only allows 8 concurrent connections, with no timeout – New connections get "Connection Refused" 19
 Access to Information • A printer may be used to discover information about a system for later attacks • The ability to send status reports – Includes a lot of information useful for analysis or social engineering • Title of documents printed • Number of bytes, characters, pictures, and pages • Total number of documents sorted by length 20
Access to Information • A printer may be used to discover information about a system for later attacks • The ability to send status reports – Includes a lot of information useful for analysis or social engineering • Title of documents printed • Number of bytes, characters, pictures, and pages • Total number of documents sorted by length 20
 HP Printers • PJL (Port 9100) allows access to the printer configuration – – – Number of copies, size, etc. Locking panel Input and output trays Echo mode and Power save I/O Buffer • Security relies on PJL password – Key space of 64 K – Broken in less than 6 hours by a brute force attack 21
HP Printers • PJL (Port 9100) allows access to the printer configuration – – – Number of copies, size, etc. Locking panel Input and output trays Echo mode and Power save I/O Buffer • Security relies on PJL password – Key space of 64 K – Broken in less than 6 hours by a brute force attack 21
 RAM Disks • Printers now include the ability to create RAM Disks for storing files • Many printers include ability to add IDE/SCSI disks for storing files • Printers may use these storage devices to spool print jobs • Attacker may be able to grab files off of the spooler – HP has a write only spool directory – Others may not be as stringent 22
RAM Disks • Printers now include the ability to create RAM Disks for storing files • Many printers include ability to add IDE/SCSI disks for storing files • Printers may use these storage devices to spool print jobs • Attacker may be able to grab files off of the spooler – HP has a write only spool directory – Others may not be as stringent 22
 Bouncing Attacks • Bouncing traffic though printer to hide attacks – Victim believes the printer is attacking them – Printer owner argues that their printer couldn't be responsible – No logs of bounced traffic • Bouncing can also allow an attacker to get access to data they weren't able to get access to before – Bypassing ACLs by using printer as gateway – Why is the FTP Get command allowed on most printers? – What could a user possibly need to get from a printer? 23
Bouncing Attacks • Bouncing traffic though printer to hide attacks – Victim believes the printer is attacking them – Printer owner argues that their printer couldn't be responsible – No logs of bounced traffic • Bouncing can also allow an attacker to get access to data they weren't able to get access to before – Bypassing ACLs by using printer as gateway – Why is the FTP Get command allowed on most printers? – What could a user possibly need to get from a printer? 23
 File Storage • Files can be stored and retrieved from the printer – FTP Server which allows saving and retrieving of documents – PJL Commands download and upload • They are reversed (upload downloads a file, etc. ) • Storing exploits or spoils on printers – Will likely foil investigators • Not likely to think about a printer storing exploits or spoils – Won’t likely be found by users or administrators – Aren’t logged, making it a little more difficult to find attacker 24
File Storage • Files can be stored and retrieved from the printer – FTP Server which allows saving and retrieving of documents – PJL Commands download and upload • They are reversed (upload downloads a file, etc. ) • Storing exploits or spoils on printers – Will likely foil investigators • Not likely to think about a printer storing exploits or spoils – Won’t likely be found by users or administrators – Aren’t logged, making it a little more difficult to find attacker 24
 What can be done? • Never install a printer with defaults – Change the printer’s password – Disable unnecessary services – Secure necessary services • Use a firewall (or packet filtering) • Contact vendors about security concerns – More interest from customers brings about more security 25
What can be done? • Never install a printer with defaults – Change the printer’s password – Disable unnecessary services – Secure necessary services • Use a firewall (or packet filtering) • Contact vendors about security concerns – More interest from customers brings about more security 25
 Help with HP Printers • Assign a non default Admin password • Allow access to port 9100 on printer only from print servers • Remove this. loader from the printer • Consider putting your printers behind an IP filter device 26
Help with HP Printers • Assign a non default Admin password • Allow access to port 9100 on printer only from print servers • Remove this. loader from the printer • Consider putting your printers behind an IP filter device 26
 Application Attacks - DNS 27
Application Attacks - DNS 27
 Review – Role of DNS • DNS provides a mapping between machine names and IP addresses: – www. mydomain. org -> 192. 168. 1. 15 • Originally, the Internet just had a large /etc/hosts file that just listed machine names and IP addresses. • This was replaced by a distributed, fault-tolerant system called "Domain Name Service. " 28
Review – Role of DNS • DNS provides a mapping between machine names and IP addresses: – www. mydomain. org -> 192. 168. 1. 15 • Originally, the Internet just had a large /etc/hosts file that just listed machine names and IP addresses. • This was replaced by a distributed, fault-tolerant system called "Domain Name Service. " 28
 Why is DNS a Popular Target? • It tends to contain a whole lot of useful information. – Many network and system administrators use DNS to keep track of and share a great deal of data with their internal users. – Unfortunately, they've got to think about what other people can get from their DNS servers. – Part of the reason they don't is because general DNS practices were set back when DNS was designed, when the Internet was a much smaller, more exclusive neighbourhood. • The past few years have shown a large number of vulnerabilities in the BIND DNS server. – Couple this with the fact that it runs as root by default, and you've got some easy remote root attacks! – These attacks are often so easy that trivial worms are using them to take over machines and propagate. 29
Why is DNS a Popular Target? • It tends to contain a whole lot of useful information. – Many network and system administrators use DNS to keep track of and share a great deal of data with their internal users. – Unfortunately, they've got to think about what other people can get from their DNS servers. – Part of the reason they don't is because general DNS practices were set back when DNS was designed, when the Internet was a much smaller, more exclusive neighbourhood. • The past few years have shown a large number of vulnerabilities in the BIND DNS server. – Couple this with the fact that it runs as root by default, and you've got some easy remote root attacks! – These attacks are often so easy that trivial worms are using them to take over machines and propagate. 29
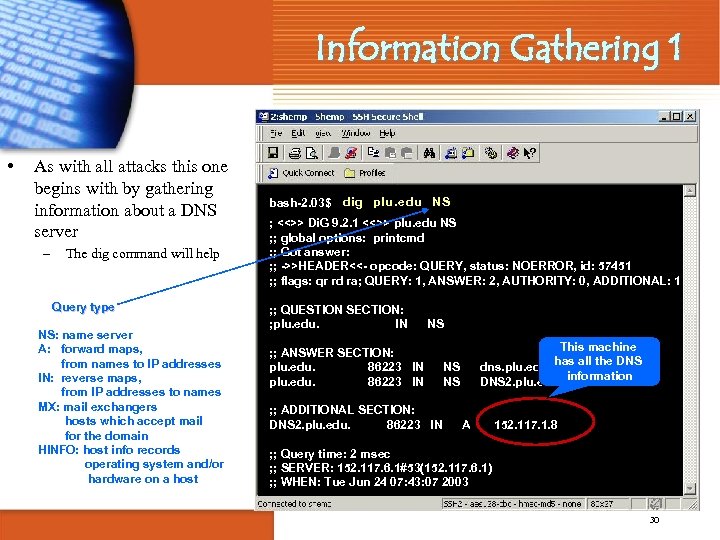 Information Gathering 1 • As with all attacks this one begins with by gathering information about a DNS server – The dig command will help Query type NS: name server A: forward maps, from names to IP addresses IN: reverse maps, from IP addresses to names MX: mail exchangers hosts which accept mail for the domain HINFO: host info records operating system and/or hardware on a host bash-2. 03$ dig plu. edu NS ; <<>> Di. G 9. 2. 1 <<>> plu. edu NS ; ; global options: printcmd ; ; Got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57451 ; ; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ; ; QUESTION SECTION: ; plu. edu. IN NS ; ; ANSWER SECTION: plu. edu. 86223 IN ; ; ADDITIONAL SECTION: DNS 2. plu. edu. 86223 IN This machine dns. plu. edu. has all the DNS 2. plu. edu. information NS NS A 152. 117. 1. 8 ; ; Query time: 2 msec ; ; SERVER: 152. 117. 6. 1#53(152. 117. 6. 1) ; ; WHEN: Tue Jun 24 07: 43: 07 2003 30
Information Gathering 1 • As with all attacks this one begins with by gathering information about a DNS server – The dig command will help Query type NS: name server A: forward maps, from names to IP addresses IN: reverse maps, from IP addresses to names MX: mail exchangers hosts which accept mail for the domain HINFO: host info records operating system and/or hardware on a host bash-2. 03$ dig plu. edu NS ; <<>> Di. G 9. 2. 1 <<>> plu. edu NS ; ; global options: printcmd ; ; Got answer: ; ; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 57451 ; ; flags: qr rd ra; QUERY: 1, ANSWER: 2, AUTHORITY: 0, ADDITIONAL: 1 ; ; QUESTION SECTION: ; plu. edu. IN NS ; ; ANSWER SECTION: plu. edu. 86223 IN ; ; ADDITIONAL SECTION: DNS 2. plu. edu. 86223 IN This machine dns. plu. edu. has all the DNS 2. plu. edu. information NS NS A 152. 117. 1. 8 ; ; Query time: 2 msec ; ; SERVER: 152. 117. 6. 1#53(152. 117. 6. 1) ; ; WHEN: Tue Jun 24 07: 43: 07 2003 30
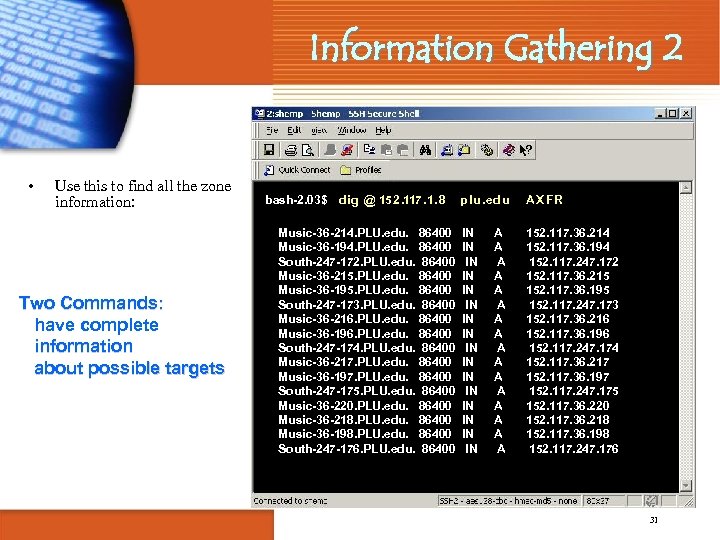 Information Gathering 2 • Use this to find all the zone information: Two Commands: have complete information about possible targets bash-2. 03$ dig @ 152. 117. 1. 8 Music-36 -214. PLU. edu. 86400 Music-36 -194. PLU. edu. 86400 South-247 -172. PLU. edu. 86400 Music-36 -215. PLU. edu. 86400 Music-36 -195. PLU. edu. 86400 South-247 -173. PLU. edu. 86400 Music-36 -216. PLU. edu. 86400 Music-36 -196. PLU. edu. 86400 South-247 -174. PLU. edu. 86400 Music-36 -217. PLU. edu. 86400 Music-36 -197. PLU. edu. 86400 South-247 -175. PLU. edu. 86400 Music-36 -220. PLU. edu. 86400 Music-36 -218. PLU. edu. 86400 Music-36 -198. PLU. edu. 86400 South-247 -176. PLU. edu. 86400 p lu. edu AX FR IN IN IN IN 152. 117. 36. 214 152. 117. 36. 194 152. 117. 247. 172 152. 117. 36. 215 152. 117. 36. 195 152. 117. 247. 173 152. 117. 36. 216 152. 117. 36. 196 152. 117. 247. 174 152. 117. 36. 217 152. 117. 36. 197 152. 117. 247. 175 152. 117. 36. 220 152. 117. 36. 218 152. 117. 36. 198 152. 117. 247. 176 A A A A 31
Information Gathering 2 • Use this to find all the zone information: Two Commands: have complete information about possible targets bash-2. 03$ dig @ 152. 117. 1. 8 Music-36 -214. PLU. edu. 86400 Music-36 -194. PLU. edu. 86400 South-247 -172. PLU. edu. 86400 Music-36 -215. PLU. edu. 86400 Music-36 -195. PLU. edu. 86400 South-247 -173. PLU. edu. 86400 Music-36 -216. PLU. edu. 86400 Music-36 -196. PLU. edu. 86400 South-247 -174. PLU. edu. 86400 Music-36 -217. PLU. edu. 86400 Music-36 -197. PLU. edu. 86400 South-247 -175. PLU. edu. 86400 Music-36 -220. PLU. edu. 86400 Music-36 -218. PLU. edu. 86400 Music-36 -198. PLU. edu. 86400 South-247 -176. PLU. edu. 86400 p lu. edu AX FR IN IN IN IN 152. 117. 36. 214 152. 117. 36. 194 152. 117. 247. 172 152. 117. 36. 215 152. 117. 36. 195 152. 117. 247. 173 152. 117. 36. 216 152. 117. 36. 196 152. 117. 247. 174 152. 117. 36. 217 152. 117. 36. 197 152. 117. 247. 175 152. 117. 36. 220 152. 117. 36. 218 152. 117. 36. 198 152. 117. 247. 176 A A A A 31
 Result Think about: 1) services offered on each machine 2) purpose of each machine 3) operating system of each machine 4) network layout Don't be afraid to guess. 32
Result Think about: 1) services offered on each machine 2) purpose of each machine 3) operating system of each machine 4) network layout Don't be afraid to guess. 32
 Cache Poisoning/DNS Spoofing Whoever takes over your internal DNS servers has an extreme ability to re-route your traffic. They can: 1) take over the entire name<->IP address mapping 2) redirect the mail (MX records) 3) have a much better attack vector for other DNS servers! 33
Cache Poisoning/DNS Spoofing Whoever takes over your internal DNS servers has an extreme ability to re-route your traffic. They can: 1) take over the entire name<->IP address mapping 2) redirect the mail (MX records) 3) have a much better attack vector for other DNS servers! 33
 BIND 8. 2 NXT Attack • Once a DNS server is identified, it can be attacked using the BIND 8. 2 NXT Attack if it has a old version of BIND running – The early versions of BIND that introduced the NXT resource record extension improperly validated these records inputs. – This bug permits a remote attacker to execute a buffer overflow to gain access to a target system at the same privilege level the named daemon is running at, for example, root. 34
BIND 8. 2 NXT Attack • Once a DNS server is identified, it can be attacked using the BIND 8. 2 NXT Attack if it has a old version of BIND running – The early versions of BIND that introduced the NXT resource record extension improperly validated these records inputs. – This bug permits a remote attacker to execute a buffer overflow to gain access to a target system at the same privilege level the named daemon is running at, for example, root. 34
 Weakness • Earlier versions of DNS were regarded as insecure because there was no ability to authenticate name servers. • In an attempt to make this protocol more secure and permit authentication, DNS Security Extensions were developed. • One of these extensions is the NXT Resource Record (RR). – The NXT RR provides the ability to securely deny the existence of a queried resource record owner name and type. – Ironically, it is this security feature that opens the door for the subject buffer overflow attack and is the reason why earlier versions of BIND were not exposed. – The details of the NXT RR and associated data fields can be found in RFC 2065 at http: //www. freesoft. org/CIE/RFC/2065/index. htm. 35
Weakness • Earlier versions of DNS were regarded as insecure because there was no ability to authenticate name servers. • In an attempt to make this protocol more secure and permit authentication, DNS Security Extensions were developed. • One of these extensions is the NXT Resource Record (RR). – The NXT RR provides the ability to securely deny the existence of a queried resource record owner name and type. – Ironically, it is this security feature that opens the door for the subject buffer overflow attack and is the reason why earlier versions of BIND were not exposed. – The details of the NXT RR and associated data fields can be found in RFC 2065 at http: //www. freesoft. org/CIE/RFC/2065/index. htm. 35
 Possible Quiz • Remember that even though each quiz is worth only 5 to 10 points, the points do add up to a significant contribution to your overall grade • If there is a quiz it might cover these issues: – Other than printers what is another hardware device that might be attacked? – What is a bouncing attack? – Why is DNS a popular target? 36
Possible Quiz • Remember that even though each quiz is worth only 5 to 10 points, the points do add up to a significant contribution to your overall grade • If there is a quiz it might cover these issues: – Other than printers what is another hardware device that might be attacked? – What is a bouncing attack? – Why is DNS a popular target? 36


