7fb5b6debcbd175984858a1836704adb.ppt
- Количество слайдов: 10

NETWORKS By : Nicolas Pottier
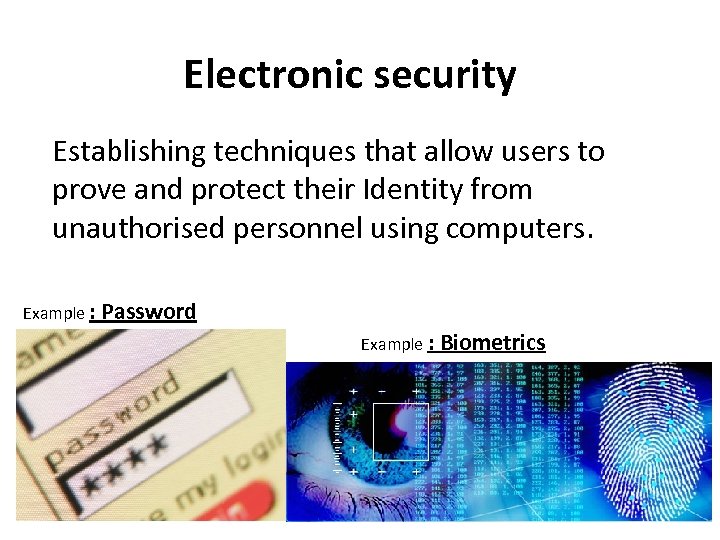
Electronic security Establishing techniques that allow users to prove and protect their Identity from unauthorised personnel using computers. Example : Password Example : Biometrics
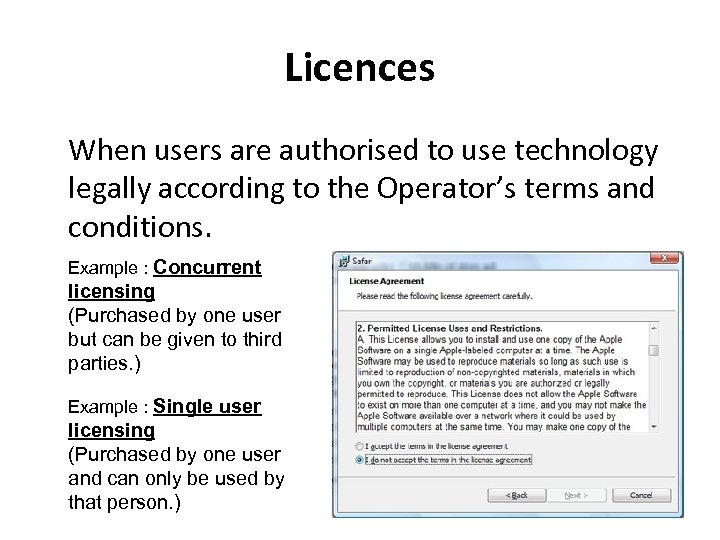
Licences When users are authorised to use technology legally according to the Operator’s terms and conditions. Example : Concurrent licensing (Purchased by one user but can be given to third parties. ) Example : Single user licensing (Purchased by one user and can only be used by that person. )

Physical security Physical barriers and controls that protect resources from any accidental or deliberate threats. Example : Locks Example : Vaults

Monitoring Keeping surveillance on and/or recording the emissions of a user in order to maintain security or for system improvements. Example : Keystroke monitoring Example : system performance
Network policies Sets of conditions, constraints, and settings that indicate to users how they can or cannot manipulate the network. Example : Disaster recovery (Recovering resources from a critical state due to human or natural disasters. ) Example : Archiving data

Codes of ethics and professional conduct Guidelines written by an organization to workers, helping them conduct their actions in accordance with its primary values and ethical standards. Example : The Association for Computing Machinery (ACM)

Data centres A facility used to house computer systems and other component systems. Example : Google server
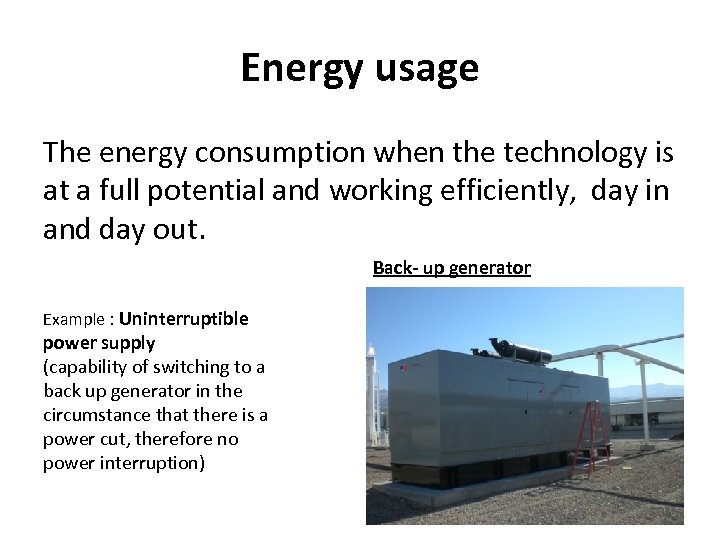
Energy usage The energy consumption when the technology is at a full potential and working efficiently, day in and day out. Back- up generator Example : Uninterruptible power supply (capability of switching to a back up generator in the circumstance that there is a power cut, therefore no power interruption)

THANK YOU!
7fb5b6debcbd175984858a1836704adb.ppt