a30347c84e71911cf5ce3ad1465960b9.ppt
- Количество слайдов: 66
 Networking Tutorial (Simple) Richa – Network Layer Nikita – Transport Sangeeta – Command Files
Networking Tutorial (Simple) Richa – Network Layer Nikita – Transport Sangeeta – Command Files
 PREREQUISITES Before this tutorial, make sure you have completed following tutorials: q. Unix tutorial
PREREQUISITES Before this tutorial, make sure you have completed following tutorials: q. Unix tutorial
 Setup Required q Access to Net. Storm/Net. Ocean q Login and password q File. Zilla, putty and Wireshark installed on the laptop
Setup Required q Access to Net. Storm/Net. Ocean q Login and password q File. Zilla, putty and Wireshark installed on the laptop
 GOALS • OSI Model • Network Layer – – – IP protocol, IP addresses, MAC Address Classful Addressing Subnetting CIDR IPV 6 Router • Transport Layer Protocols – TCP – UDP • • Basic Networking Commands Network Configuration Files Common configuration tasks TCP Dump analysis using Wireshark
GOALS • OSI Model • Network Layer – – – IP protocol, IP addresses, MAC Address Classful Addressing Subnetting CIDR IPV 6 Router • Transport Layer Protocols – TCP – UDP • • Basic Networking Commands Network Configuration Files Common configuration tasks TCP Dump analysis using Wireshark
 OSI Model
OSI Model
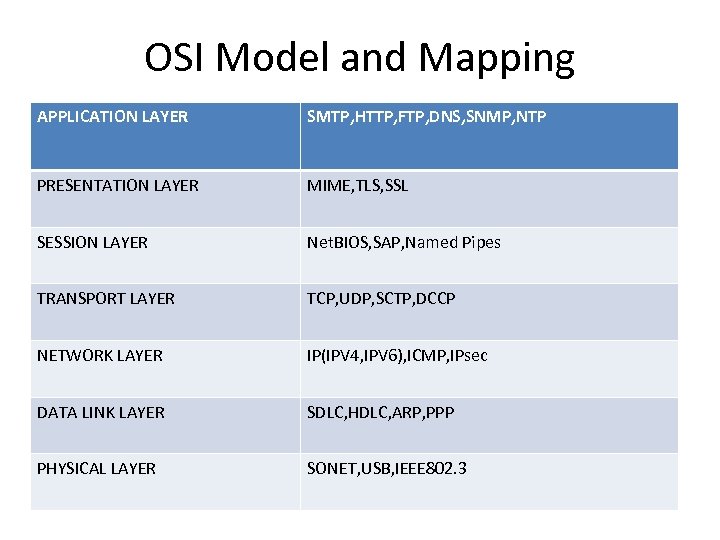 OSI Model and Mapping APPLICATION LAYER SMTP, HTTP, FTP, DNS, SNMP, NTP PRESENTATION LAYER MIME, TLS, SSL SESSION LAYER Net. BIOS, SAP, Named Pipes TRANSPORT LAYER TCP, UDP, SCTP, DCCP NETWORK LAYER IP(IPV 4, IPV 6), ICMP, IPsec DATA LINK LAYER SDLC, HDLC, ARP, PPP PHYSICAL LAYER SONET, USB, IEEE 802. 3
OSI Model and Mapping APPLICATION LAYER SMTP, HTTP, FTP, DNS, SNMP, NTP PRESENTATION LAYER MIME, TLS, SSL SESSION LAYER Net. BIOS, SAP, Named Pipes TRANSPORT LAYER TCP, UDP, SCTP, DCCP NETWORK LAYER IP(IPV 4, IPV 6), ICMP, IPsec DATA LINK LAYER SDLC, HDLC, ARP, PPP PHYSICAL LAYER SONET, USB, IEEE 802. 3
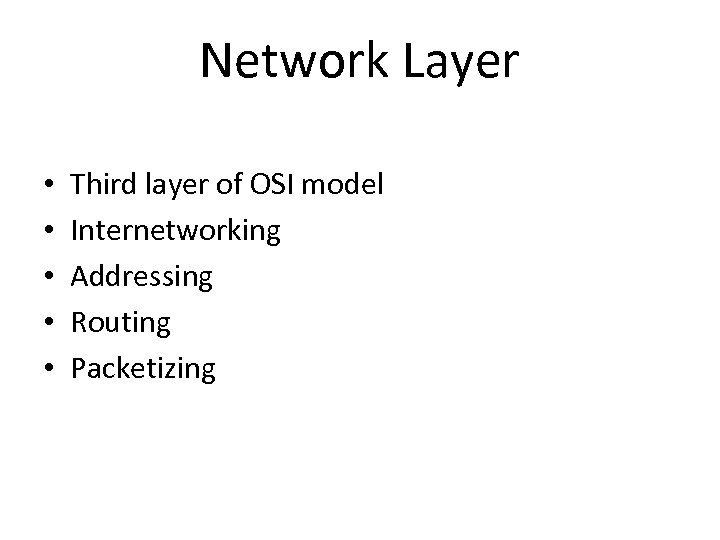 Network Layer • • • Third layer of OSI model Internetworking Addressing Routing Packetizing
Network Layer • • • Third layer of OSI model Internetworking Addressing Routing Packetizing
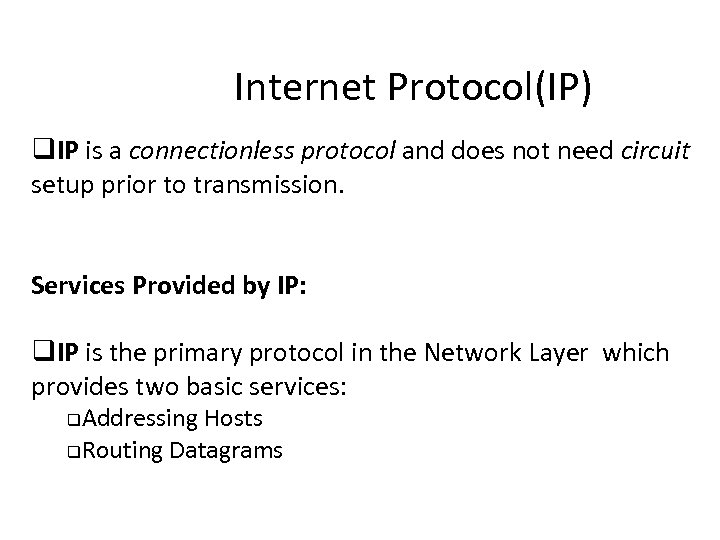 Internet Protocol(IP) q. IP is a connectionless protocol and does not need circuit setup prior to transmission. Services Provided by IP: q. IP is the primary protocol in the Network Layer which provides two basic services: Addressing Hosts q. Routing Datagrams q
Internet Protocol(IP) q. IP is a connectionless protocol and does not need circuit setup prior to transmission. Services Provided by IP: q. IP is the primary protocol in the Network Layer which provides two basic services: Addressing Hosts q. Routing Datagrams q
 IP Address • Every machine on network has an unique identifying number called IP address. • Two versions of the Internet Protocol (IP): – IP Version 4 and IP Version 6 • Each interface (eth 0) is give a IP address • Can have multiple IP address
IP Address • Every machine on network has an unique identifying number called IP address. • Two versions of the Internet Protocol (IP): – IP Version 4 and IP Version 6 • Each interface (eth 0) is give a IP address • Can have multiple IP address
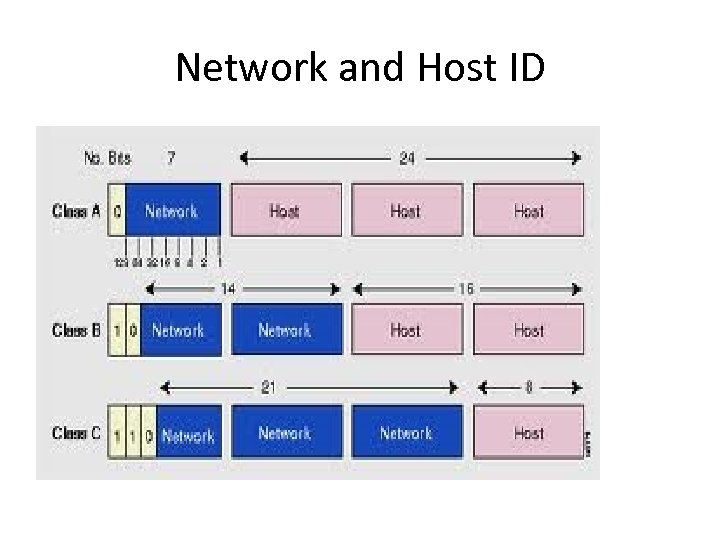 Network and Host ID
Network and Host ID
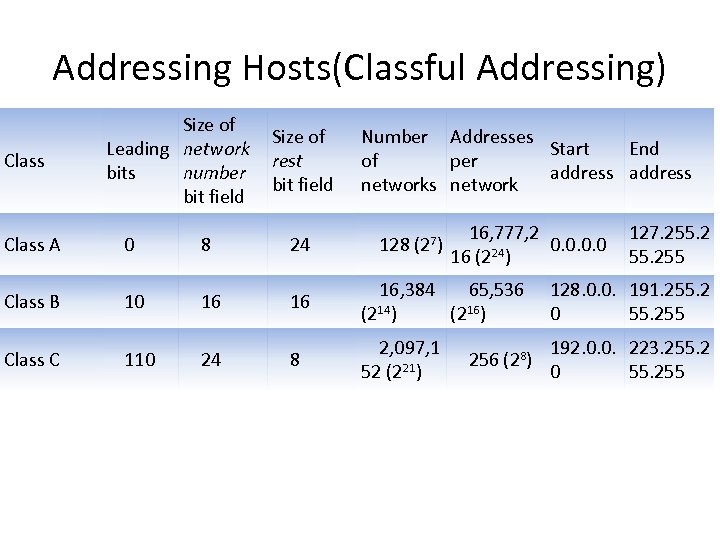 Addressing Hosts(Classful Addressing) Class Size of Leading network bits number bit field Size of rest bit field Number Addresses Start End of per address networks network Class A 0 8 24 128 (27) Class B 10 16 16 16, 384 65, 536 (214) (216) Class C 110 24 8 2, 097, 1 192. 0. 0. 223. 255. 2 256 (28) 52 (221) 0 55. 255 16, 777, 2 0. 0 16 (224) 127. 255 128. 0. 0. 191. 255. 2 0 55. 255
Addressing Hosts(Classful Addressing) Class Size of Leading network bits number bit field Size of rest bit field Number Addresses Start End of per address networks network Class A 0 8 24 128 (27) Class B 10 16 16 16, 384 65, 536 (214) (216) Class C 110 24 8 2, 097, 1 192. 0. 0. 223. 255. 2 256 (28) 52 (221) 0 55. 255 16, 777, 2 0. 0 16 (224) 127. 255 128. 0. 0. 191. 255. 2 0 55. 255
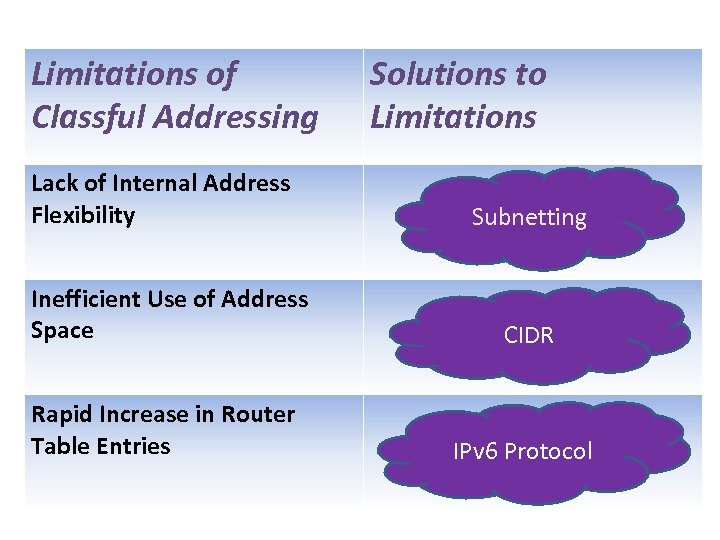 Limitations of Classful Addressing Lack of Internal Address Flexibility Solutions to Limitations Subnetting Inefficient Use of Address Space CIDR Rapid Increase in Router Table Entries IPv 6 Protocol
Limitations of Classful Addressing Lack of Internal Address Flexibility Solutions to Limitations Subnetting Inefficient Use of Address Space CIDR Rapid Increase in Router Table Entries IPv 6 Protocol
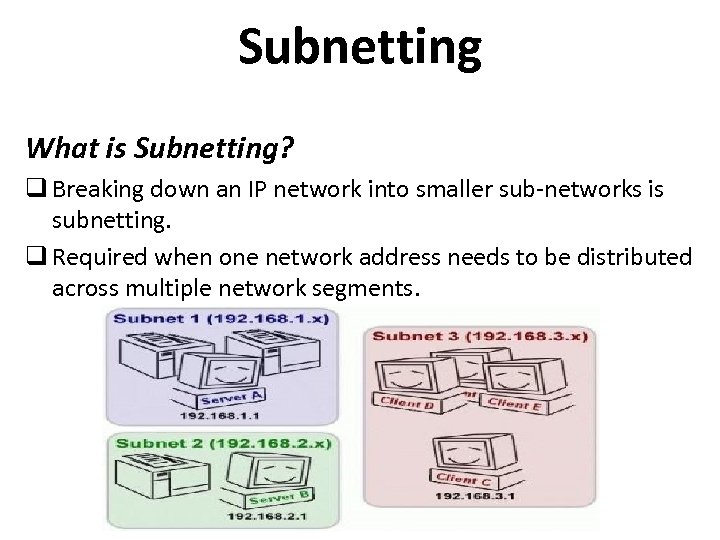 Subnetting What is Subnetting? q Breaking down an IP network into smaller sub-networks is subnetting. q Required when one network address needs to be distributed across multiple network segments.
Subnetting What is Subnetting? q Breaking down an IP network into smaller sub-networks is subnetting. q Required when one network address needs to be distributed across multiple network segments.
 How to Subnet? q Routers are used between different networks or subnets to control the flow of data or packets. q A router is nothing but a hardware network device that transmits data based on preset conditions of transmission and security.
How to Subnet? q Routers are used between different networks or subnets to control the flow of data or packets. q A router is nothing but a hardware network device that transmits data based on preset conditions of transmission and security.
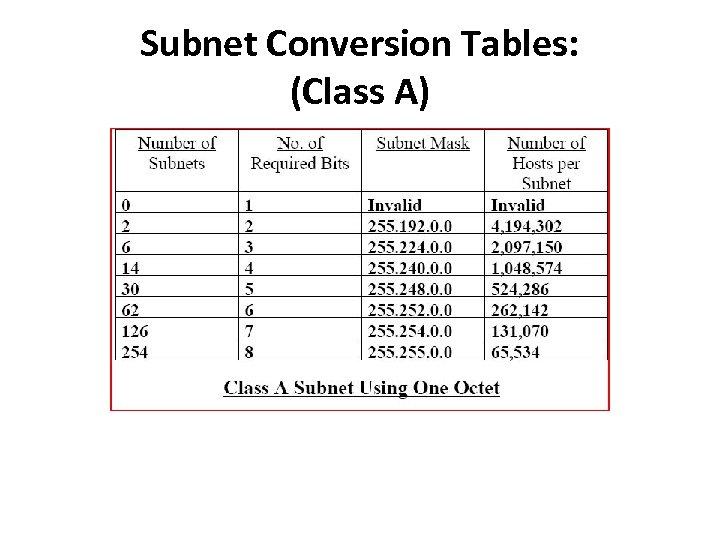 Subnet Conversion Tables: (Class A)
Subnet Conversion Tables: (Class A)
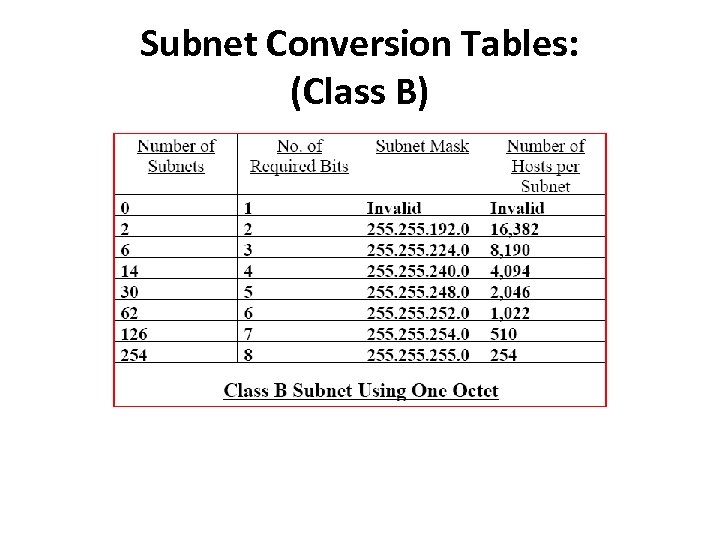 Subnet Conversion Tables: (Class B)
Subnet Conversion Tables: (Class B)
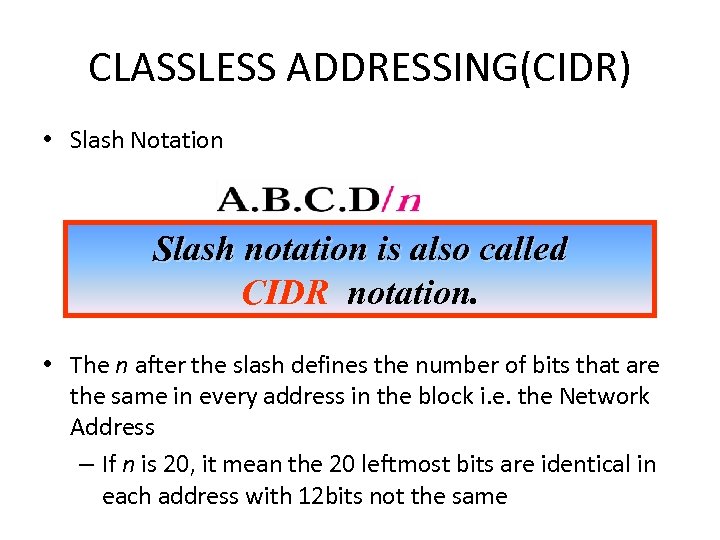 CLASSLESS ADDRESSING(CIDR) • Slash Notation Slash notation is also called CIDR notation. • The n after the slash defines the number of bits that are the same in every address in the block i. e. the Network Address – If n is 20, it mean the 20 leftmost bits are identical in each address with 12 bits not the same
CLASSLESS ADDRESSING(CIDR) • Slash Notation Slash notation is also called CIDR notation. • The n after the slash defines the number of bits that are the same in every address in the block i. e. the Network Address – If n is 20, it mean the 20 leftmost bits are identical in each address with 12 bits not the same
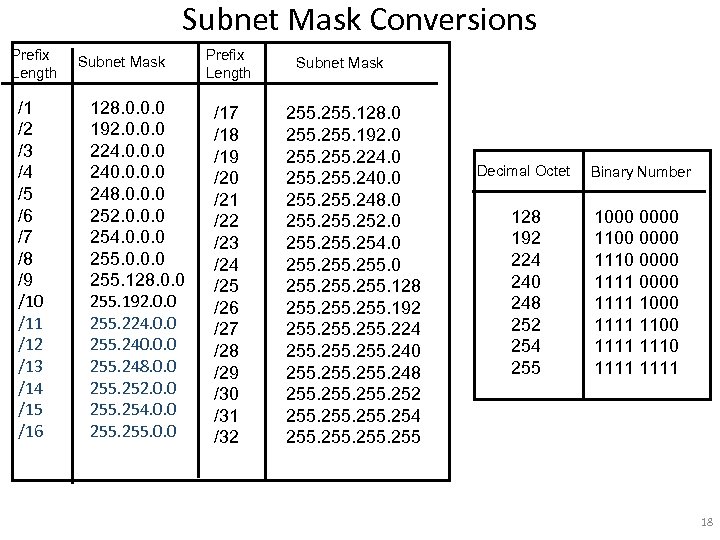 Subnet Mask Conversions Prefix Length /1 /2 /3 /4 /5 /6 /7 /8 /9 /10 /11 /12 /13 /14 /15 /16 Subnet Mask 128. 0. 0. 0 192. 0. 0. 0 224. 0. 0. 0 240. 0 248. 0. 0. 0 252. 0. 0. 0 254. 0. 0. 0 255. 128. 0. 0 255. 192. 0. 0 255. 224. 0. 0 255. 240. 0. 0 255. 248. 0. 0 255. 252. 0. 0 255. 254. 0. 0 255. 0. 0 Prefix Length /17 /18 /19 /20 /21 /22 /23 /24 /25 /26 /27 /28 /29 /30 /31 /32 Subnet Mask 255. 128. 0 255. 192. 0 255. 224. 0 255. 240. 0 255. 248. 0 255. 252. 0 255. 254. 0 255. 128 255. 192 255. 224 255. 240 255. 248 255. 252 255. 254 255 Decimal Octet Binary Number 128 192 224 240 248 252 254 255 1000 0000 1110 0000 1111 1000 1111 1110 1111 18
Subnet Mask Conversions Prefix Length /1 /2 /3 /4 /5 /6 /7 /8 /9 /10 /11 /12 /13 /14 /15 /16 Subnet Mask 128. 0. 0. 0 192. 0. 0. 0 224. 0. 0. 0 240. 0 248. 0. 0. 0 252. 0. 0. 0 254. 0. 0. 0 255. 128. 0. 0 255. 192. 0. 0 255. 224. 0. 0 255. 240. 0. 0 255. 248. 0. 0 255. 252. 0. 0 255. 254. 0. 0 255. 0. 0 Prefix Length /17 /18 /19 /20 /21 /22 /23 /24 /25 /26 /27 /28 /29 /30 /31 /32 Subnet Mask 255. 128. 0 255. 192. 0 255. 224. 0 255. 240. 0 255. 248. 0 255. 252. 0 255. 254. 0 255. 128 255. 192 255. 224 255. 240 255. 248 255. 252 255. 254 255 Decimal Octet Binary Number 128 192 224 240 248 252 254 255 1000 0000 1110 0000 1111 1000 1111 1110 1111 18
 Example 1 A small organization is given a block with the beginning address and the prefix length 205. 16. 37. 24/29 (in slash notation). What is the range of the block? Solution The beginning address is 205. 16. 37. 24. To find the last address we keep the first 29 bits and change the last 3 bits to 1 s. Beginning: 11001111 00010000 00100101 00011000 Ending : 11001111 00010000 00100101 00011111 There are only 8 addresses in this block.
Example 1 A small organization is given a block with the beginning address and the prefix length 205. 16. 37. 24/29 (in slash notation). What is the range of the block? Solution The beginning address is 205. 16. 37. 24. To find the last address we keep the first 29 bits and change the last 3 bits to 1 s. Beginning: 11001111 00010000 00100101 00011000 Ending : 11001111 00010000 00100101 00011111 There are only 8 addresses in this block.
 Example 2 What is the network address if one of the addresses is 167. 199. 170. 82/27? Solution The prefix length is 27, which means that we must keep the first 27 bits as is and change the remaining bits (5) to 0 s. The 5 bits affect only the last byte. The last byte is 01010010. Changing the last 5 bits to 0 s, we get 01000000 or 64. The network address is 167. 199. 170. 64/27.
Example 2 What is the network address if one of the addresses is 167. 199. 170. 82/27? Solution The prefix length is 27, which means that we must keep the first 27 bits as is and change the remaining bits (5) to 0 s. The 5 bits affect only the last byte. The last byte is 01010010. Changing the last 5 bits to 0 s, we get 01000000 or 64. The network address is 167. 199. 170. 64/27.
 Example 3 An organization is granted the block 130. 34. 12. 64/26. The organization needs to have four subnets. What are the subnet addresses and the range of addresses for each subnet? Solution The suffix length is 6. This means the total number of addresses in the block is 64 (26). If we create four subnets, each subnet will have 16 addresses.
Example 3 An organization is granted the block 130. 34. 12. 64/26. The organization needs to have four subnets. What are the subnet addresses and the range of addresses for each subnet? Solution The suffix length is 6. This means the total number of addresses in the block is 64 (26). If we create four subnets, each subnet will have 16 addresses.
 Solution (Continued) Let us first find the subnet prefix (subnet mask). We need four subnets, which means we need to add two more 1 s to the site prefix. The subnet prefix is then /28. Subnet 1: 130. 34. 12. 64/28 to 130. 34. 12. 79/28. Subnet 2 : 130. 34. 12. 80/28 to 130. 34. 12. 95/28. Subnet 3: 130. 34. 12. 96/28 to 130. 34. 12. 111/28. Subnet 4: 130. 34. 12. 112/28 to 130. 34. 127/28.
Solution (Continued) Let us first find the subnet prefix (subnet mask). We need four subnets, which means we need to add two more 1 s to the site prefix. The subnet prefix is then /28. Subnet 1: 130. 34. 12. 64/28 to 130. 34. 12. 79/28. Subnet 2 : 130. 34. 12. 80/28 to 130. 34. 12. 95/28. Subnet 3: 130. 34. 12. 96/28 to 130. 34. 12. 111/28. Subnet 4: 130. 34. 12. 112/28 to 130. 34. 127/28.
 IPv 6 Why IPv 6? § Enormous growth of internet. § Predicted depletion of available addresses. § Uses 128 bits for address i. e 16 octets.
IPv 6 Why IPv 6? § Enormous growth of internet. § Predicted depletion of available addresses. § Uses 128 bits for address i. e 16 octets.
 IPv 6 Addressing Notation • 128 bits address i. e. 2^128 possible addresses! • IPv 6 addresses are generally written in the following form hhhh: hhhh: hhhh Example: q E 3 D 7: 0000: 51 F 4: 9 BC 8: C 0 A 8: 6420 (Full notation) q E 3 D 7: : 51 F 4: 9 BC 8: C 0 A 8: 6420 (Shorthand Notation) q E 3 D 7: : 51 F 4: 9 BC 8: 192. 168. 100. 32 (Mixed Notation)
IPv 6 Addressing Notation • 128 bits address i. e. 2^128 possible addresses! • IPv 6 addresses are generally written in the following form hhhh: hhhh: hhhh Example: q E 3 D 7: 0000: 51 F 4: 9 BC 8: C 0 A 8: 6420 (Full notation) q E 3 D 7: : 51 F 4: 9 BC 8: C 0 A 8: 6420 (Shorthand Notation) q E 3 D 7: : 51 F 4: 9 BC 8: 192. 168. 100. 32 (Mixed Notation)
 Media Access Control(MAC) • unique identifier assigned to network interfaces for communications on the physical network segment • assigned by the manufacturer • fixed for an interface card • Usually encoded and is known as burned-in address
Media Access Control(MAC) • unique identifier assigned to network interfaces for communications on the physical network segment • assigned by the manufacturer • fixed for an interface card • Usually encoded and is known as burned-in address
 Router • Routers forward IP datagrams from one router to another on the path from source towards destination • Routing protocols – To decide on routes to be taken • Routers must have idea of topology of internet in order to pick best route to take – Decisions based on some least cost criteria – May depend on the current conditions
Router • Routers forward IP datagrams from one router to another on the path from source towards destination • Routing protocols – To decide on routes to be taken • Routers must have idea of topology of internet in order to pick best route to take – Decisions based on some least cost criteria – May depend on the current conditions
 Routing Table • One routing table is needed for each router • One entry for each destination network – Not for each destination host – Once datagram reaches router attached to destination network, that router can deliver to host router • Each entry shows next node on the route to destination – Not whole route • Routing tables may also exist in hosts – If multiple routers attached to network, host needs table saying which to use – If the attached network has single router, then not needed • All traffic must go through that router (called the gateway)
Routing Table • One routing table is needed for each router • One entry for each destination network – Not for each destination host – Once datagram reaches router attached to destination network, that router can deliver to host router • Each entry shows next node on the route to destination – Not whole route • Routing tables may also exist in hosts – If multiple routers attached to network, host needs table saying which to use – If the attached network has single router, then not needed • All traffic must go through that router (called the gateway)
 • Routing tables can be created – manually and dynamically • Network administrators manually create static routing tables • A manual table requires more administrative overhead but gives the administrator greater control over the routing process • Dynamic updates are provided through routing protocols • The routing protocols allow the routers to be updated automatically
• Routing tables can be created – manually and dynamically • Network administrators manually create static routing tables • A manual table requires more administrative overhead but gives the administrator greater control over the routing process • Dynamic updates are provided through routing protocols • The routing protocols allow the routers to be updated automatically
 Transport Layer Protocols
Transport Layer Protocols
 TCP Protocol • Over IP layer • Connection-oriented – Connection is made between two end points – Data is send over this connection • Reliable • Full-duplex • Byte-Stream
TCP Protocol • Over IP layer • Connection-oriented – Connection is made between two end points – Data is send over this connection • Reliable • Full-duplex • Byte-Stream
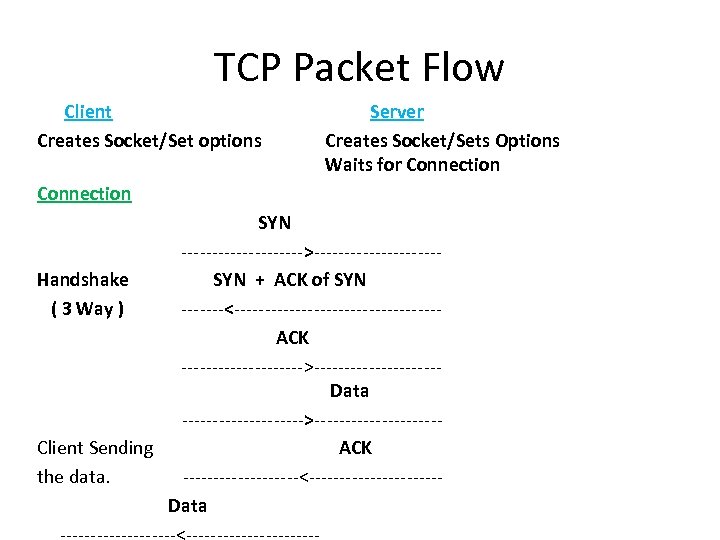 TCP Packet Flow Client Creates Socket/Set options Server Creates Socket/Sets Options Waits for Connection SYN ---------->----------Handshake SYN + ACK of SYN ( 3 Way ) -------<----------------- ACK ---------->----------Data ---------->----------Client Sending ACK the data. ----------<----------- Data
TCP Packet Flow Client Creates Socket/Set options Server Creates Socket/Sets Options Waits for Connection SYN ---------->----------Handshake SYN + ACK of SYN ( 3 Way ) -------<----------------- ACK ---------->----------Data ---------->----------Client Sending ACK the data. ----------<----------- Data
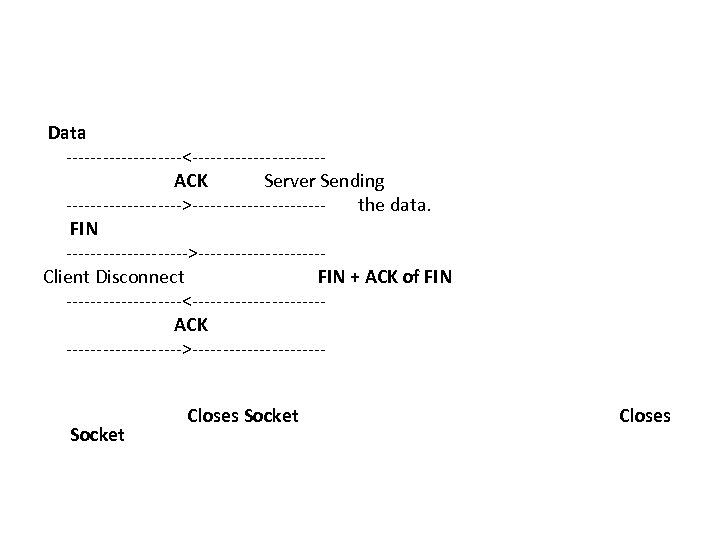 Data ----------<-----------ACK Server Sending ---------->----------- the data. FIN ---------->----------Client Disconnect FIN + ACK of FIN ----------<-----------ACK ---------->----------- Socket Closes
Data ----------<-----------ACK Server Sending ---------->----------- the data. FIN ---------->----------Client Disconnect FIN + ACK of FIN ----------<-----------ACK ---------->----------- Socket Closes
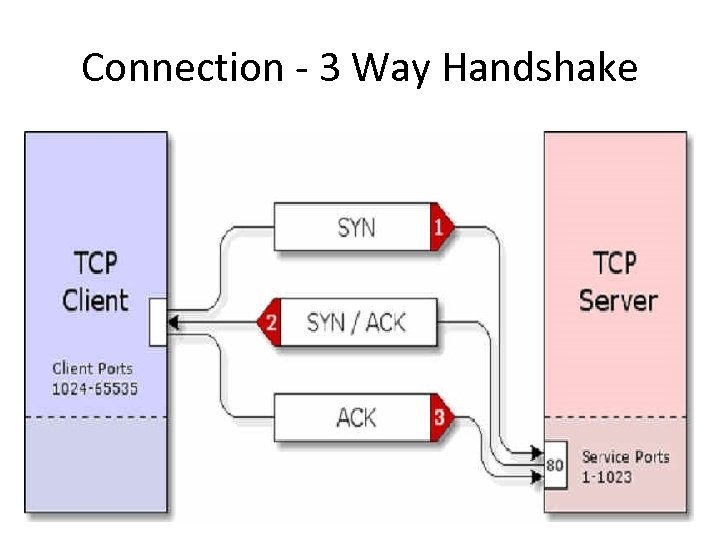 Connection - 3 Way Handshake
Connection - 3 Way Handshake
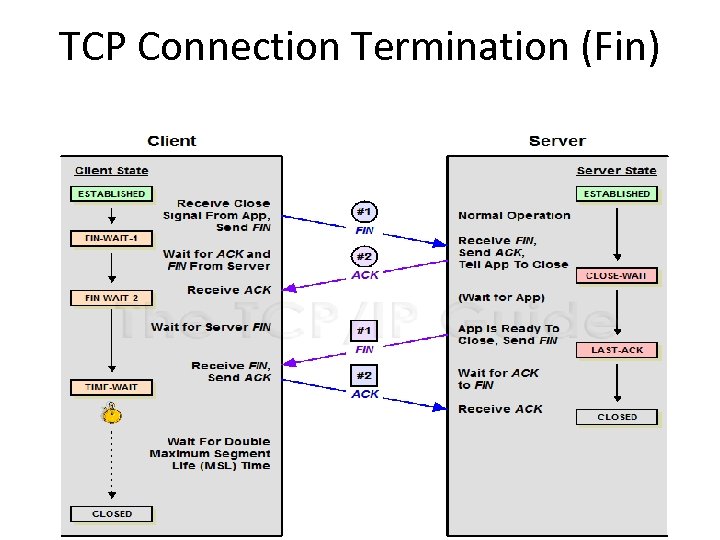 TCP Connection Termination (Fin)
TCP Connection Termination (Fin)
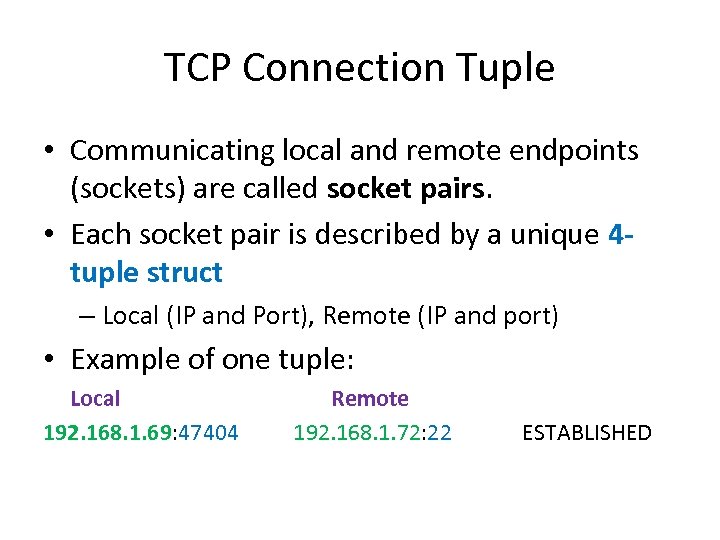 TCP Connection Tuple • Communicating local and remote endpoints (sockets) are called socket pairs. • Each socket pair is described by a unique 4 tuple struct – Local (IP and Port), Remote (IP and port) • Example of one tuple: Local Remote 192. 168. 1. 69: 47404 192. 168. 1. 72: 22 ESTABLISHED
TCP Connection Tuple • Communicating local and remote endpoints (sockets) are called socket pairs. • Each socket pair is described by a unique 4 tuple struct – Local (IP and Port), Remote (IP and port) • Example of one tuple: Local Remote 192. 168. 1. 69: 47404 192. 168. 1. 72: 22 ESTABLISHED
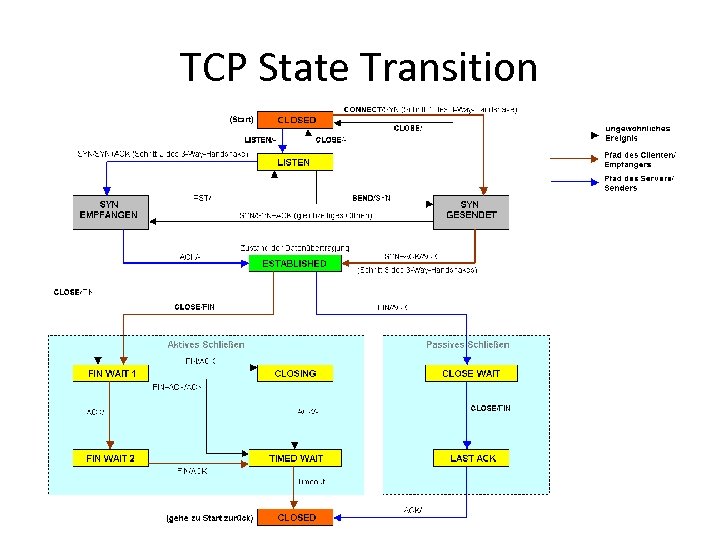 TCP State Transition
TCP State Transition
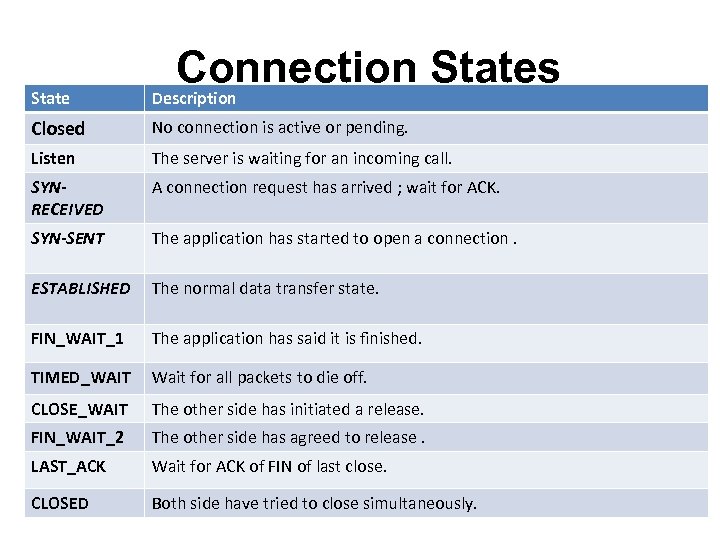 Connection States State Description Closed No connection is active or pending. Listen The server is waiting for an incoming call. SYNRECEIVED A connection request has arrived ; wait for ACK. SYN-SENT The application has started to open a connection. ESTABLISHED The normal data transfer state. FIN_WAIT_1 The application has said it is finished. TIMED_WAIT Wait for all packets to die off. CLOSE_WAIT The other side has initiated a release. FIN_WAIT_2 The other side has agreed to release. LAST_ACK Wait for ACK of FIN of last close. CLOSED Both side have tried to close simultaneously.
Connection States State Description Closed No connection is active or pending. Listen The server is waiting for an incoming call. SYNRECEIVED A connection request has arrived ; wait for ACK. SYN-SENT The application has started to open a connection. ESTABLISHED The normal data transfer state. FIN_WAIT_1 The application has said it is finished. TIMED_WAIT Wait for all packets to die off. CLOSE_WAIT The other side has initiated a release. FIN_WAIT_2 The other side has agreed to release. LAST_ACK Wait for ACK of FIN of last close. CLOSED Both side have tried to close simultaneously.
 User Datagram Protocol(UDP) • Transaction oriented – No connections are made • Not Reliable – Delivery and duplicate protection not guaranteed – Packet can be delivered in different sequence
User Datagram Protocol(UDP) • Transaction oriented – No connections are made • Not Reliable – Delivery and duplicate protection not guaranteed – Packet can be delivered in different sequence
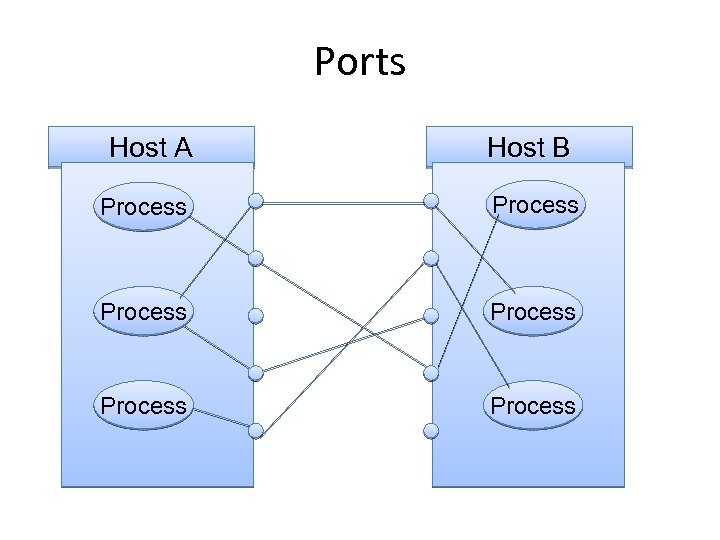 Ports Host A Host B Process Process
Ports Host A Host B Process Process
 qa port is a "logical connection place“. q specifically, using the Internet's protocol, TCP/IP, the way a client program specifies a particular server program on a computer in a network.
qa port is a "logical connection place“. q specifically, using the Internet's protocol, TCP/IP, the way a client program specifies a particular server program on a computer in a network.
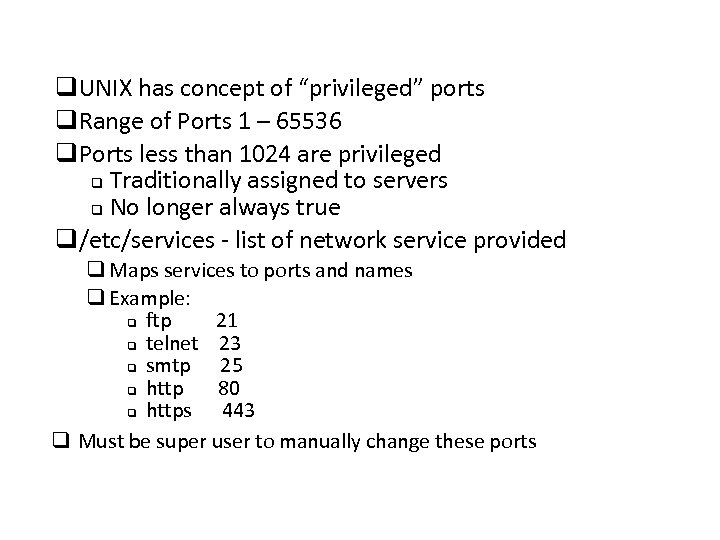 q. UNIX has concept of “privileged” ports q. Range of Ports 1 – 65536 q. Ports less than 1024 are privileged q Traditionally assigned to servers q No longer always true q/etc/services - list of network service provided q Maps services to ports and names q Example: q ftp 21 q telnet 23 q smtp 25 q http 80 q https 443 q Must be super user to manually change these ports
q. UNIX has concept of “privileged” ports q. Range of Ports 1 – 65536 q. Ports less than 1024 are privileged q Traditionally assigned to servers q No longer always true q/etc/services - list of network service provided q Maps services to ports and names q Example: q ftp 21 q telnet 23 q smtp 25 q http 80 q https 443 q Must be super user to manually change these ports
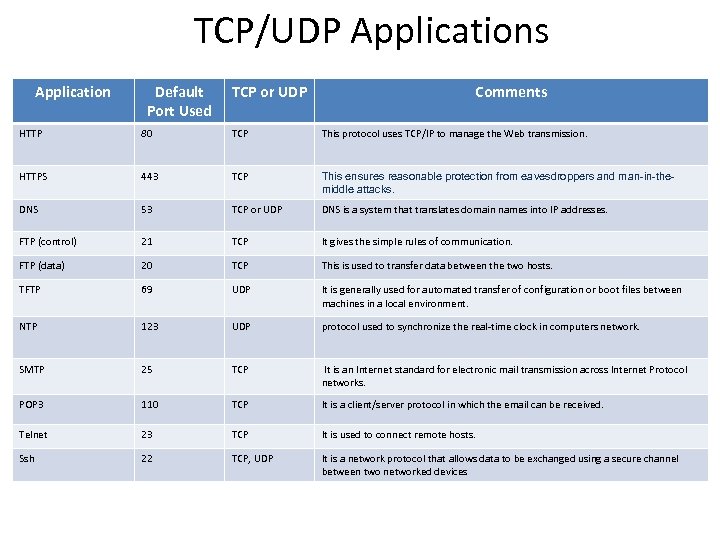 TCP/UDP Applications Application Default Port Used TCP or UDP Comments HTTP 80 TCP This protocol uses TCP/IP to manage the Web transmission. HTTPS 443 TCP This ensures reasonable protection from eavesdroppers and man-in-themiddle attacks. DNS 53 TCP or UDP DNS is a system that translates domain names into IP addresses. FTP (control) 21 TCP It gives the simple rules of communication. FTP (data) 20 TCP This is used to transfer data between the two hosts. TFTP 69 UDP It is generally used for automated transfer of configuration or boot files between machines in a local environment. NTP 123 UDP protocol used to synchronize the real-time clock in computers network. SMTP 25 TCP It is an Internet standard for electronic mail transmission across Internet Protocol networks. POP 3 110 TCP It is a client/server protocol in which the email can be received. Telnet 23 TCP It is used to connect remote hosts. Ssh 22 TCP, UDP It is a network protocol that allows data to be exchanged using a secure channel between two networked devices
TCP/UDP Applications Application Default Port Used TCP or UDP Comments HTTP 80 TCP This protocol uses TCP/IP to manage the Web transmission. HTTPS 443 TCP This ensures reasonable protection from eavesdroppers and man-in-themiddle attacks. DNS 53 TCP or UDP DNS is a system that translates domain names into IP addresses. FTP (control) 21 TCP It gives the simple rules of communication. FTP (data) 20 TCP This is used to transfer data between the two hosts. TFTP 69 UDP It is generally used for automated transfer of configuration or boot files between machines in a local environment. NTP 123 UDP protocol used to synchronize the real-time clock in computers network. SMTP 25 TCP It is an Internet standard for electronic mail transmission across Internet Protocol networks. POP 3 110 TCP It is a client/server protocol in which the email can be received. Telnet 23 TCP It is used to connect remote hosts. Ssh 22 TCP, UDP It is a network protocol that allows data to be exchanged using a secure channel between two networked devices
 Basic Networking Commands
Basic Networking Commands
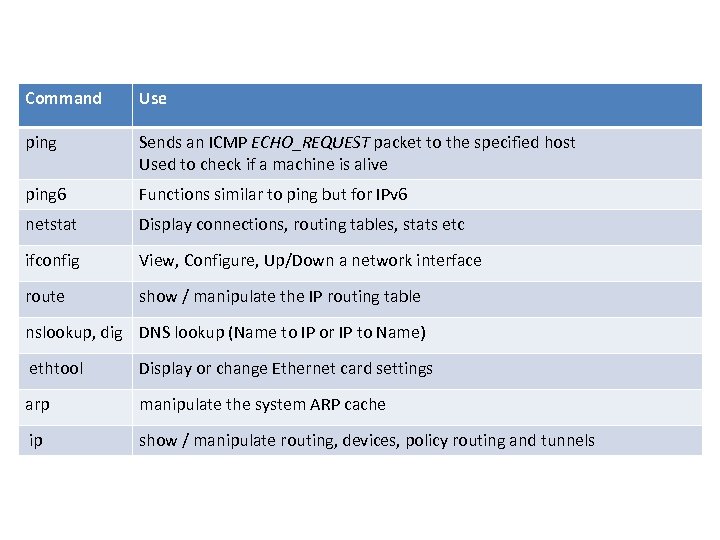 Command Use ping Sends an ICMP ECHO_REQUEST packet to the specified host Used to check if a machine is alive ping 6 Functions similar to ping but for IPv 6 netstat Display connections, routing tables, stats etc ifconfig View, Configure, Up/Down a network interface route show / manipulate the IP routing table nslookup, dig DNS lookup (Name to IP or IP to Name) ethtool Display or change Ethernet card settings arp manipulate the system ARP cache ip show / manipulate routing, devices, policy routing and tunnels
Command Use ping Sends an ICMP ECHO_REQUEST packet to the specified host Used to check if a machine is alive ping 6 Functions similar to ping but for IPv 6 netstat Display connections, routing tables, stats etc ifconfig View, Configure, Up/Down a network interface route show / manipulate the IP routing table nslookup, dig DNS lookup (Name to IP or IP to Name) ethtool Display or change Ethernet card settings arp manipulate the system ARP cache ip show / manipulate routing, devices, policy routing and tunnels
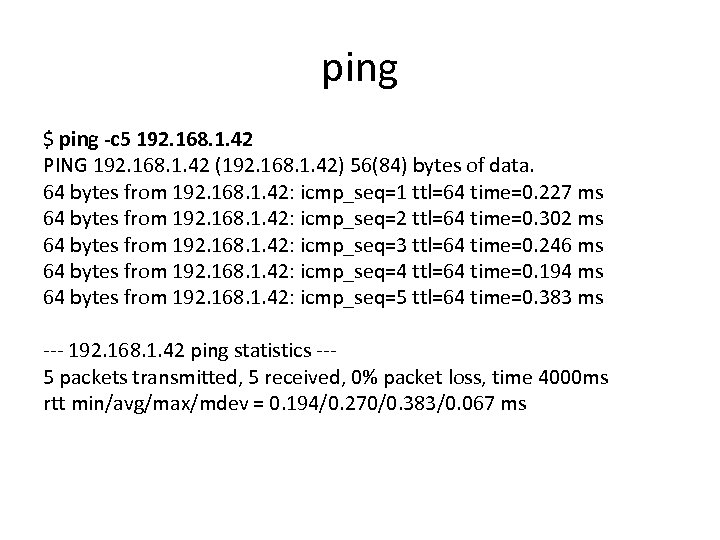 ping $ ping -c 5 192. 168. 1. 42 PING 192. 168. 1. 42 (192. 168. 1. 42) 56(84) bytes of data. 64 bytes from 192. 168. 1. 42: icmp_seq=1 ttl=64 time=0. 227 ms 64 bytes from 192. 168. 1. 42: icmp_seq=2 ttl=64 time=0. 302 ms 64 bytes from 192. 168. 1. 42: icmp_seq=3 ttl=64 time=0. 246 ms 64 bytes from 192. 168. 1. 42: icmp_seq=4 ttl=64 time=0. 194 ms 64 bytes from 192. 168. 1. 42: icmp_seq=5 ttl=64 time=0. 383 ms --- 192. 168. 1. 42 ping statistics --5 packets transmitted, 5 received, 0% packet loss, time 4000 ms rtt min/avg/max/mdev = 0. 194/0. 270/0. 383/0. 067 ms
ping $ ping -c 5 192. 168. 1. 42 PING 192. 168. 1. 42 (192. 168. 1. 42) 56(84) bytes of data. 64 bytes from 192. 168. 1. 42: icmp_seq=1 ttl=64 time=0. 227 ms 64 bytes from 192. 168. 1. 42: icmp_seq=2 ttl=64 time=0. 302 ms 64 bytes from 192. 168. 1. 42: icmp_seq=3 ttl=64 time=0. 246 ms 64 bytes from 192. 168. 1. 42: icmp_seq=4 ttl=64 time=0. 194 ms 64 bytes from 192. 168. 1. 42: icmp_seq=5 ttl=64 time=0. 383 ms --- 192. 168. 1. 42 ping statistics --5 packets transmitted, 5 received, 0% packet loss, time 4000 ms rtt min/avg/max/mdev = 0. 194/0. 270/0. 383/0. 067 ms
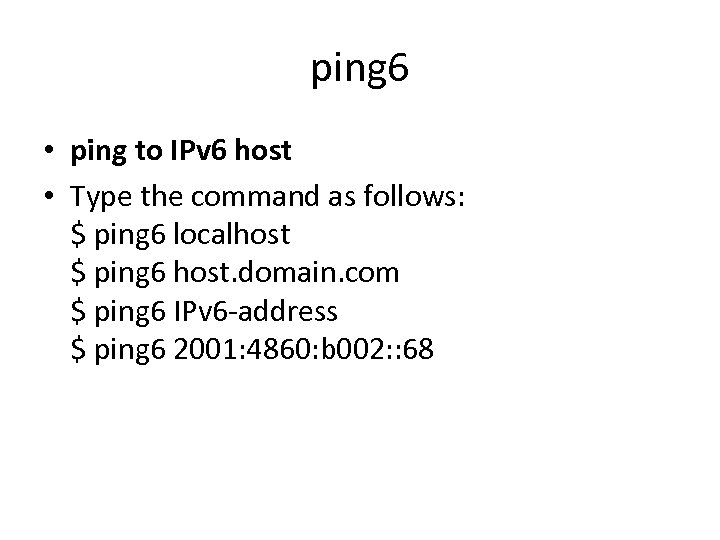 ping 6 • ping to IPv 6 host • Type the command as follows: $ ping 6 localhost $ ping 6 host. domain. com $ ping 6 IPv 6 -address $ ping 6 2001: 4860: b 002: : 68
ping 6 • ping to IPv 6 host • Type the command as follows: $ ping 6 localhost $ ping 6 host. domain. com $ ping 6 IPv 6 -address $ ping 6 2001: 4860: b 002: : 68
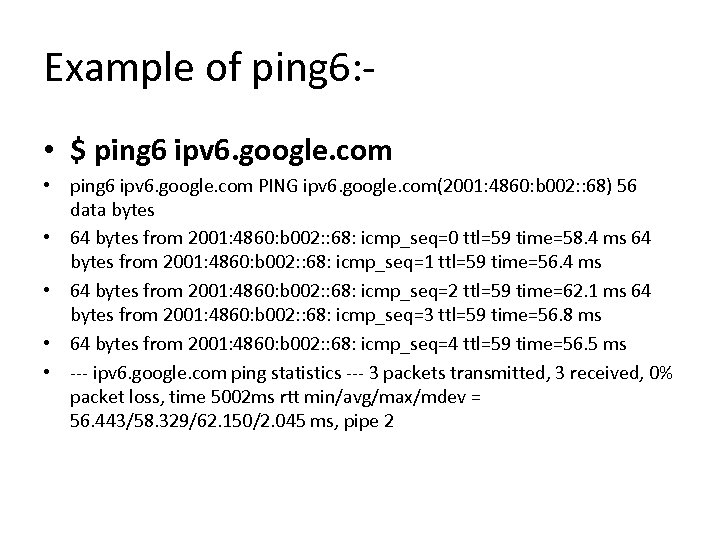 Example of ping 6: • $ ping 6 ipv 6. google. com • ping 6 ipv 6. google. com PING ipv 6. google. com(2001: 4860: b 002: : 68) 56 data bytes • 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=0 ttl=59 time=58. 4 ms 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=1 ttl=59 time=56. 4 ms • 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=2 ttl=59 time=62. 1 ms 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=3 ttl=59 time=56. 8 ms • 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=4 ttl=59 time=56. 5 ms • --- ipv 6. google. com ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 5002 ms rtt min/avg/max/mdev = 56. 443/58. 329/62. 150/2. 045 ms, pipe 2
Example of ping 6: • $ ping 6 ipv 6. google. com • ping 6 ipv 6. google. com PING ipv 6. google. com(2001: 4860: b 002: : 68) 56 data bytes • 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=0 ttl=59 time=58. 4 ms 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=1 ttl=59 time=56. 4 ms • 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=2 ttl=59 time=62. 1 ms 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=3 ttl=59 time=56. 8 ms • 64 bytes from 2001: 4860: b 002: : 68: icmp_seq=4 ttl=59 time=56. 5 ms • --- ipv 6. google. com ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 5002 ms rtt min/avg/max/mdev = 56. 443/58. 329/62. 150/2. 045 ms, pipe 2
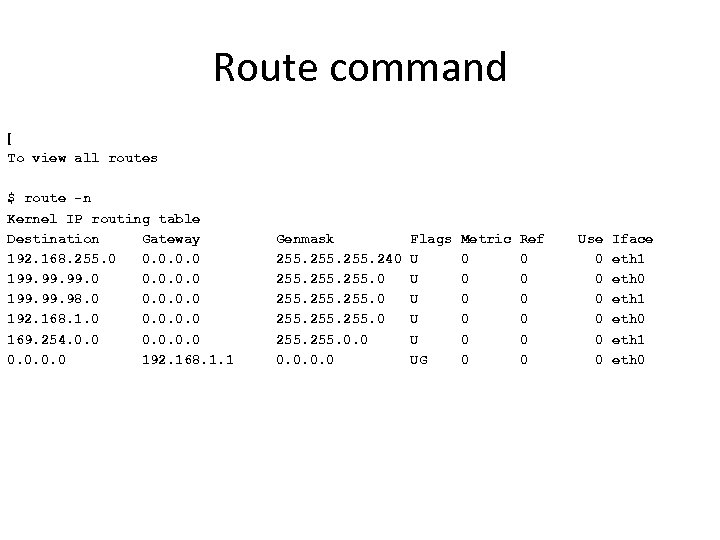 Route command [ To view all routes $ route -n Kernel IP routing table Destination Gateway 192. 168. 255. 0 0. 0 199. 99. 0 0. 0 199. 98. 0 0. 0 192. 168. 1. 0 0. 0 169. 254. 0. 0 192. 168. 1. 1 Genmask 255. 240 255. 0. 0 Flags U U UG Metric 0 0 0 Ref 0 0 0 Use 0 0 0 Iface eth 1 eth 0
Route command [ To view all routes $ route -n Kernel IP routing table Destination Gateway 192. 168. 255. 0 0. 0 199. 99. 0 0. 0 199. 98. 0 0. 0 192. 168. 1. 0 0. 0 169. 254. 0. 0 192. 168. 1. 1 Genmask 255. 240 255. 0. 0 Flags U U UG Metric 0 0 0 Ref 0 0 0 Use 0 0 0 Iface eth 1 eth 0
 Route command • To add a route • route add -net XXX. 0 netmask 255. 0 gw XXX dev eth 0 • Example • To delete a route • route delete -net XXX. 0 netmask 255. 0 gw XXX dev eth 0
Route command • To add a route • route add -net XXX. 0 netmask 255. 0 gw XXX dev eth 0 • Example • To delete a route • route delete -net XXX. 0 netmask 255. 0 gw XXX dev eth 0
![Netstat (tarffic) To see traffic [netstorm@netocean 2 src]$ netstat -i Kernel Interface table Iface Netstat (tarffic) To see traffic [netstorm@netocean 2 src]$ netstat -i Kernel Interface table Iface](https://present5.com/presentation/a30347c84e71911cf5ce3ad1465960b9/image-50.jpg) Netstat (tarffic) To see traffic [netstorm@netocean 2 src]$ netstat -i Kernel Interface table Iface MTU Met RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg • eth 0 1500 0 242335 0 0 0 264041 0 0 0 BMRU • eth 1 1500 0 350 0 716 0 0 0 BMRU • lo 16436 0 6686 0 0 0 LRU • •
Netstat (tarffic) To see traffic [netstorm@netocean 2 src]$ netstat -i Kernel Interface table Iface MTU Met RX-OK RX-ERR RX-DRP RX-OVR TX-OK TX-ERR TX-DRP TX-OVR Flg • eth 0 1500 0 242335 0 0 0 264041 0 0 0 BMRU • eth 1 1500 0 350 0 716 0 0 0 BMRU • lo 16436 0 6686 0 0 0 LRU • •
![Netstat (View routes) • [netstorm@netocean 2 src]$ netstat -rn • Kernel IP routing table Netstat (View routes) • [netstorm@netocean 2 src]$ netstat -rn • Kernel IP routing table](https://present5.com/presentation/a30347c84e71911cf5ce3ad1465960b9/image-51.jpg) Netstat (View routes) • [netstorm@netocean 2 src]$ netstat -rn • Kernel IP routing table • Destination Gateway Genmask Flags MSS Window irtt Iface • 192. 168. 255. 0 0. 0 255. 240 U 0 0 0 eth 1 • 199. 99. 0 0. 0 255. 0 U 0 0 0 eth 0 • 199. 98. 0 0. 0 255. 0 U 0 0 0 eth 1 • 192. 168. 1. 0 0. 0 255. 0 U 0 0 0 eth 0 • 169. 254. 0. 0 255. 0. 0 U 0 0 0 eth 1 • 0. 0 192. 168. 1. 1 0. 0 UG 0 0 0 eth 0
Netstat (View routes) • [netstorm@netocean 2 src]$ netstat -rn • Kernel IP routing table • Destination Gateway Genmask Flags MSS Window irtt Iface • 192. 168. 255. 0 0. 0 255. 240 U 0 0 0 eth 1 • 199. 99. 0 0. 0 255. 0 U 0 0 0 eth 0 • 199. 98. 0 0. 0 255. 0 U 0 0 0 eth 1 • 192. 168. 1. 0 0. 0 255. 0 U 0 0 0 eth 0 • 169. 254. 0. 0 255. 0. 0 U 0 0 0 eth 1 • 0. 0 192. 168. 1. 1 0. 0 UG 0 0 0 eth 0
 ethtool • • • • • • ethtool eth 0 Settings for eth 0: Supported ports: [ TP ] Supported link modes: 10 base. T/Half 10 base. T/Full 100 base. T/Half 100 base. T/Full 1000 base. T/Half 1000 base. T/Full Supports auto-negotiation: Yes Advertised link modes: 10 base. T/Half 10 base. T/Full 100 base. T/Half 100 base. T/Full 1000 base. T/Half 1000 base. T/Full Advertised auto-negotiation: Yes Speed: 100 Mb/s Duplex: Full Port: Twisted Pair PHYAD: 1 Transceiver: internal Auto-negotiation: on Supports Wake-on: g Wake-on: d Current message level: 0 x 000000 ff (255) Link detected: yes
ethtool • • • • • • ethtool eth 0 Settings for eth 0: Supported ports: [ TP ] Supported link modes: 10 base. T/Half 10 base. T/Full 100 base. T/Half 100 base. T/Full 1000 base. T/Half 1000 base. T/Full Supports auto-negotiation: Yes Advertised link modes: 10 base. T/Half 10 base. T/Full 100 base. T/Half 100 base. T/Full 1000 base. T/Half 1000 base. T/Full Advertised auto-negotiation: Yes Speed: 100 Mb/s Duplex: Full Port: Twisted Pair PHYAD: 1 Transceiver: internal Auto-negotiation: on Supports Wake-on: g Wake-on: d Current message level: 0 x 000000 ff (255) Link detected: yes
 Ip command • • View ip addresses assigned Add/view/delete Ip addresses assigned Add/View/delete routes View/delete rules
Ip command • • View ip addresses assigned Add/view/delete Ip addresses assigned Add/View/delete routes View/delete rules
![Ip command • [netstorm@netocean 2 src]$ ip addr show dev eth 0 • 2: Ip command • [netstorm@netocean 2 src]$ ip addr show dev eth 0 • 2:](https://present5.com/presentation/a30347c84e71911cf5ce3ad1465960b9/image-54.jpg) Ip command • [netstorm@netocean 2 src]$ ip addr show dev eth 0 • 2: eth 0:
Ip command • [netstorm@netocean 2 src]$ ip addr show dev eth 0 • 2: eth 0:
 Network Configuration Files
Network Configuration Files
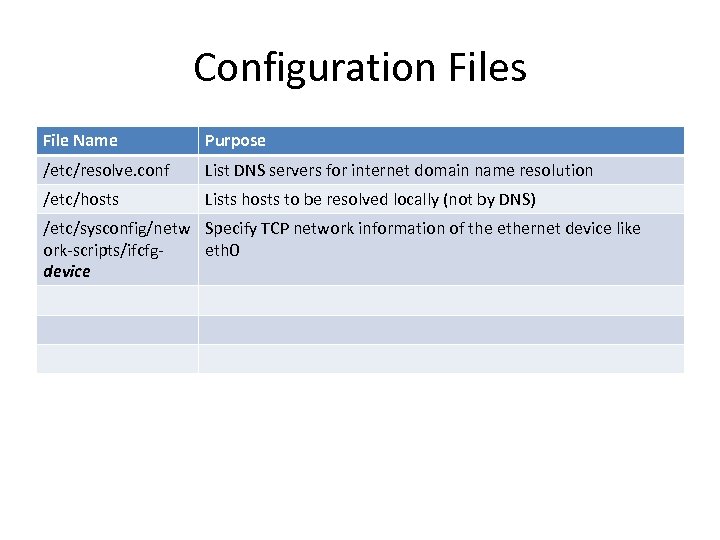 Configuration Files File Name Purpose /etc/resolve. conf List DNS servers for internet domain name resolution /etc/hosts Lists hosts to be resolved locally (not by DNS) /etc/sysconfig/netw Specify TCP network information of the ethernet device like ork-scripts/ifcfgeth 0 device
Configuration Files File Name Purpose /etc/resolve. conf List DNS servers for internet domain name resolution /etc/hosts Lists hosts to be resolved locally (not by DNS) /etc/sysconfig/netw Specify TCP network information of the ethernet device like ork-scripts/ifcfgeth 0 device
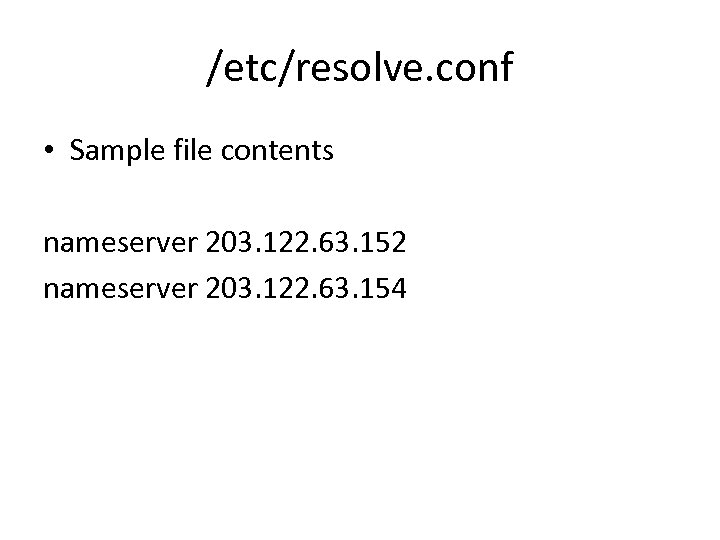 /etc/resolve. conf • Sample file contents nameserver 203. 122. 63. 152 nameserver 203. 122. 63. 154
/etc/resolve. conf • Sample file contents nameserver 203. 122. 63. 152 nameserver 203. 122. 63. 154
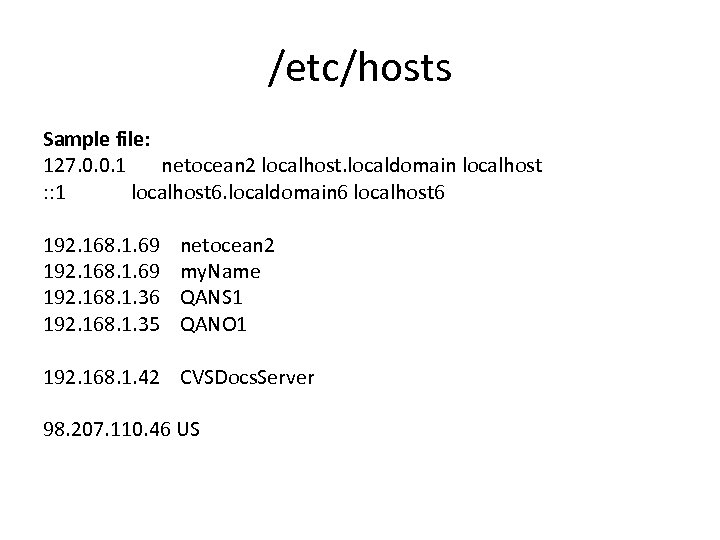 /etc/hosts Sample file: 127. 0. 0. 1 netocean 2 localhost. localdomain localhost : : 1 localhost 6. localdomain 6 localhost 6 192. 168. 1. 69 netocean 2 192. 168. 1. 69 my. Name 192. 168. 1. 36 QANS 1 192. 168. 1. 35 QANO 1 192. 168. 1. 42 CVSDocs. Server 98. 207. 110. 46 US
/etc/hosts Sample file: 127. 0. 0. 1 netocean 2 localhost. localdomain localhost : : 1 localhost 6. localdomain 6 localhost 6 192. 168. 1. 69 netocean 2 192. 168. 1. 69 my. Name 192. 168. 1. 36 QANS 1 192. 168. 1. 35 QANO 1 192. 168. 1. 42 CVSDocs. Server 98. 207. 110. 46 US
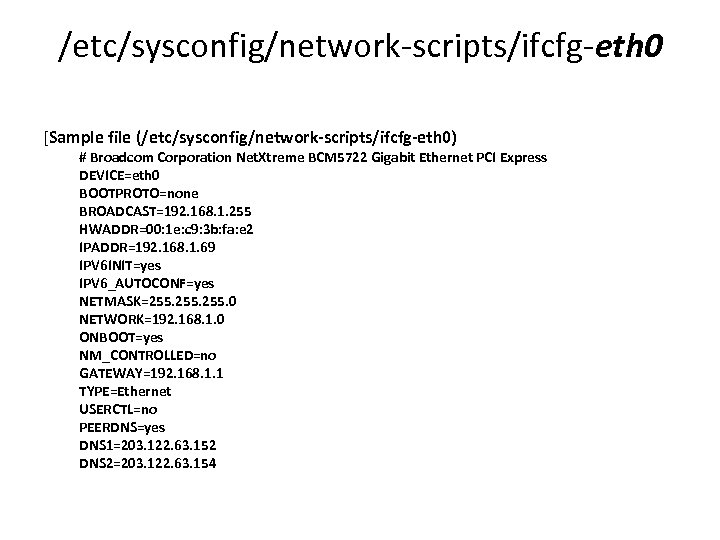 /etc/sysconfig/network-scripts/ifcfg-eth 0 [Sample file (/etc/sysconfig/network-scripts/ifcfg-eth 0) # Broadcom Corporation Net. Xtreme BCM 5722 Gigabit Ethernet PCI Express DEVICE=eth 0 BOOTPROTO=none BROADCAST=192. 168. 1. 255 HWADDR=00: 1 e: c 9: 3 b: fa: e 2 IPADDR=192. 168. 1. 69 IPV 6 INIT=yes IPV 6_AUTOCONF=yes NETMASK=255. 0 NETWORK=192. 168. 1. 0 ONBOOT=yes NM_CONTROLLED=no GATEWAY=192. 168. 1. 1 TYPE=Ethernet USERCTL=no PEERDNS=yes DNS 1=203. 122. 63. 152 DNS 2=203. 122. 63. 154
/etc/sysconfig/network-scripts/ifcfg-eth 0 [Sample file (/etc/sysconfig/network-scripts/ifcfg-eth 0) # Broadcom Corporation Net. Xtreme BCM 5722 Gigabit Ethernet PCI Express DEVICE=eth 0 BOOTPROTO=none BROADCAST=192. 168. 1. 255 HWADDR=00: 1 e: c 9: 3 b: fa: e 2 IPADDR=192. 168. 1. 69 IPV 6 INIT=yes IPV 6_AUTOCONF=yes NETMASK=255. 0 NETWORK=192. 168. 1. 0 ONBOOT=yes NM_CONTROLLED=no GATEWAY=192. 168. 1. 1 TYPE=Ethernet USERCTL=no PEERDNS=yes DNS 1=203. 122. 63. 152 DNS 2=203. 122. 63. 154
 Common Tasks
Common Tasks
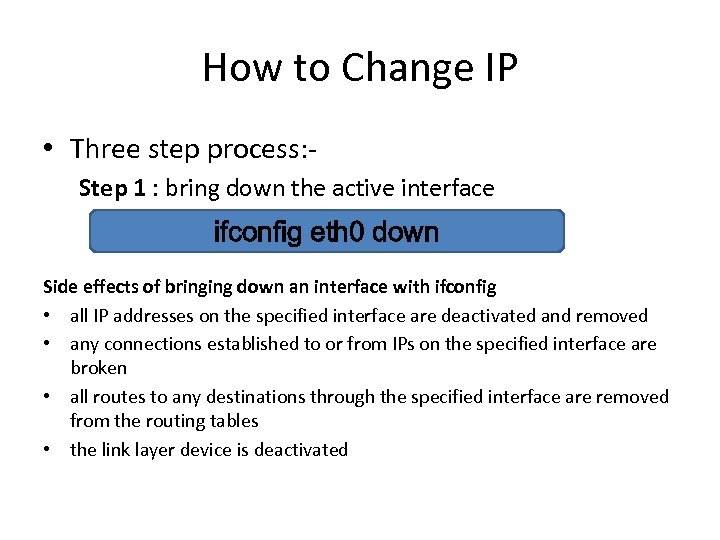 How to Change IP • Three step process: Step 1 : bring down the active interface ifconfig eth 0 down Side effects of bringing down an interface with ifconfig • all IP addresses on the specified interface are deactivated and removed • any connections established to or from IPs on the specified interface are broken • all routes to any destinations through the specified interface are removed from the routing tables • the link layer device is deactivated
How to Change IP • Three step process: Step 1 : bring down the active interface ifconfig eth 0 down Side effects of bringing down an interface with ifconfig • all IP addresses on the specified interface are deactivated and removed • any connections established to or from IPs on the specified interface are broken • all routes to any destinations through the specified interface are removed from the routing tables • the link layer device is deactivated
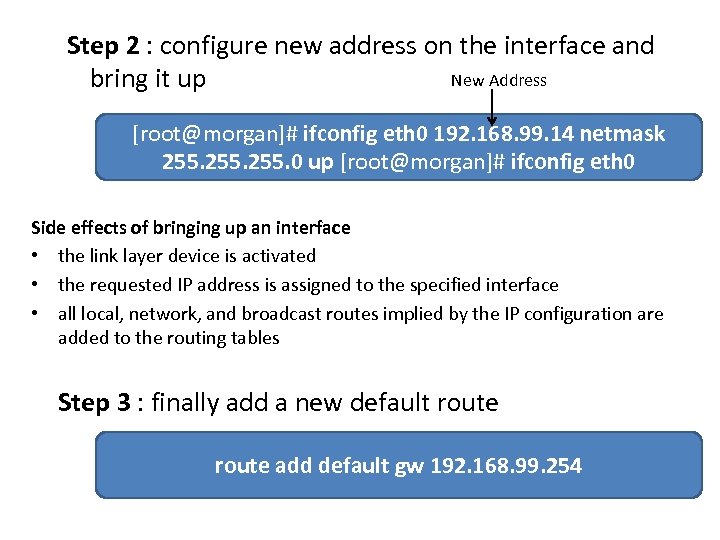 Step 2 : configure new address on the interface and New Address bring it up [root@morgan]# ifconfig eth 0 192. 168. 99. 14 netmask 255. 0 up [root@morgan]# ifconfig eth 0 Side effects of bringing up an interface • the link layer device is activated • the requested IP address is assigned to the specified interface • all local, network, and broadcast routes implied by the IP configuration are added to the routing tables Step 3 : finally add a new default route add default gw 192. 168. 99. 254
Step 2 : configure new address on the interface and New Address bring it up [root@morgan]# ifconfig eth 0 192. 168. 99. 14 netmask 255. 0 up [root@morgan]# ifconfig eth 0 Side effects of bringing up an interface • the link layer device is activated • the requested IP address is assigned to the specified interface • all local, network, and broadcast routes implied by the IP configuration are added to the routing tables Step 3 : finally add a new default route add default gw 192. 168. 99. 254
 How to change Hostname Edit file /etc/sysconfig/network using your favourite editor Example : vi /etc/sysconfig/network Look for HOSTNAME=xxxxxx Change the xxxx to the name you wish to set for your computer. (ex: HOSTNAME=netstorm. com) • Save the file and restart the xinetd service. (ex: type service xinetd restart in your shell) • • •
How to change Hostname Edit file /etc/sysconfig/network using your favourite editor Example : vi /etc/sysconfig/network Look for HOSTNAME=xxxxxx Change the xxxx to the name you wish to set for your computer. (ex: HOSTNAME=netstorm. com) • Save the file and restart the xinetd service. (ex: type service xinetd restart in your shell) • • •
 How to Enable NTP • /etc/ntp. conf file is the main configuration file for Linux NTP. • Place IP Address of Stratum 1 and Stratum 2 servers we want to use where * Stratum 1: NTP sites using an atomic clock for timing. * Stratum 2: NTP sites with slightly less accurate time sources.
How to Enable NTP • /etc/ntp. conf file is the main configuration file for Linux NTP. • Place IP Address of Stratum 1 and Stratum 2 servers we want to use where * Stratum 1: NTP sites using an atomic clock for timing. * Stratum 2: NTP sites with slightly less accurate time sources.
 • To get NTP configured to start at boot, use the line: [root@bigboy tmp]# chkconfig ntpd on • To start, stop and restart NTP after booting, follow these examples: [root@bigboy tmp]# service ntpd start [root@bigboy tmp]# service ntpd stop [root@bigboy tmp]# service ntpd restart
• To get NTP configured to start at boot, use the line: [root@bigboy tmp]# chkconfig ntpd on • To start, stop and restart NTP after booting, follow these examples: [root@bigboy tmp]# service ntpd start [root@bigboy tmp]# service ntpd stop [root@bigboy tmp]# service ntpd restart
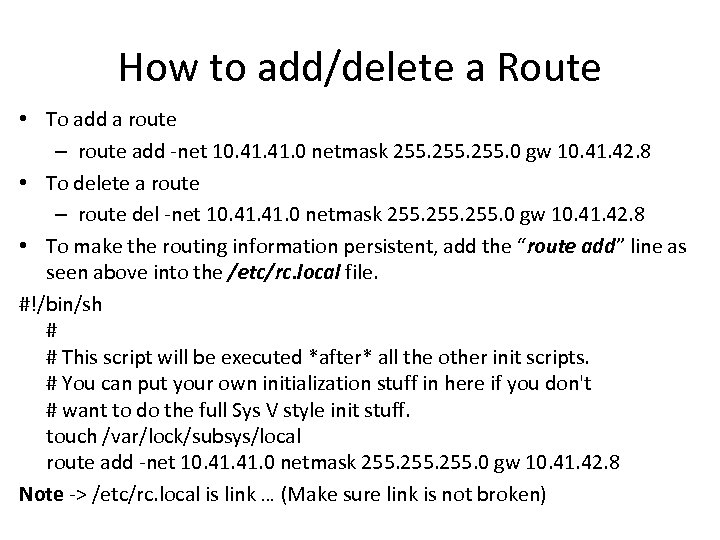 How to add/delete a Route • To add a route – route add -net 10. 41. 0 netmask 255. 0 gw 10. 41. 42. 8 • To delete a route – route del -net 10. 41. 0 netmask 255. 0 gw 10. 41. 42. 8 • To make the routing information persistent, add the “route add” line as seen above into the /etc/rc. local file. #!/bin/sh # # This script will be executed *after* all the other init scripts. # You can put your own initialization stuff in here if you don't # want to do the full Sys V style init stuff. touch /var/lock/subsys/local route add -net 10. 41. 0 netmask 255. 0 gw 10. 41. 42. 8 Note -> /etc/rc. local is link … (Make sure link is not broken)
How to add/delete a Route • To add a route – route add -net 10. 41. 0 netmask 255. 0 gw 10. 41. 42. 8 • To delete a route – route del -net 10. 41. 0 netmask 255. 0 gw 10. 41. 42. 8 • To make the routing information persistent, add the “route add” line as seen above into the /etc/rc. local file. #!/bin/sh # # This script will be executed *after* all the other init scripts. # You can put your own initialization stuff in here if you don't # want to do the full Sys V style init stuff. touch /var/lock/subsys/local route add -net 10. 41. 0 netmask 255. 0 gw 10. 41. 42. 8 Note -> /etc/rc. local is link … (Make sure link is not broken)


