lec_Network.ppt
- Количество слайдов: 55
 Networking and Telecommunications
Networking and Telecommunications
 Opening Questions • What are some advantages of networked computing relative to stand alone computing? • What is the difference between client/server and peer-to-peer networks? • What are a few common types of network topologies?
Opening Questions • What are some advantages of networked computing relative to stand alone computing? • What is the difference between client/server and peer-to-peer networks? • What are a few common types of network topologies?
 NETWORK BASICS • Telecommunication system - enable the transmission of data over public or private networks • Network - a communications, data exchange, and resource-sharing system created by linking two or more computers and establishing standards, or protocols, so that they can work together
NETWORK BASICS • Telecommunication system - enable the transmission of data over public or private networks • Network - a communications, data exchange, and resource-sharing system created by linking two or more computers and establishing standards, or protocols, so that they can work together
 Why Use Networks in Organizations? • All networks offer advantages relative to using a standalone computer… • that is, a computer that is not connected to other computers and that uses software applications and data stored on its local disks • Networks allow multiple users to share devices such as printers, and share data, for example spreadsheets which are collectively known as network resources.
Why Use Networks in Organizations? • All networks offer advantages relative to using a standalone computer… • that is, a computer that is not connected to other computers and that uses software applications and data stored on its local disks • Networks allow multiple users to share devices such as printers, and share data, for example spreadsheets which are collectively known as network resources.
 Advantages to using a Network • Sharing devices save money! • Sharing devices also saves time! • For example, rather than • For example, its faster for buying 20 printers for 20 coworkers to data over a office workers, a company network than to copy can have one printer and data to a removable have those 20 office storage device and workers share it over a physically transport the network. storage device fro one computer to another. Sneakernet: an out-dated file-sharing method in which people had to physically transport data files from one desktop to another, presumably wearing sneakers!
Advantages to using a Network • Sharing devices save money! • Sharing devices also saves time! • For example, rather than • For example, its faster for buying 20 printers for 20 coworkers to data over a office workers, a company network than to copy can have one printer and data to a removable have those 20 office storage device and workers share it over a physically transport the network. storage device fro one computer to another. Sneakernet: an out-dated file-sharing method in which people had to physically transport data files from one desktop to another, presumably wearing sneakers!
 Why else use networks? • One of the highest priority network services is email! • Reasons for networks include; Most of these listed features require a NOS, a component of a Client/Server Network 1. 2. 3. 4. 5. File & Print services Remote user access Mail services Internet services Management Services • • Traffic monitoring Load balancing Security auditing Backup and restoration services
Why else use networks? • One of the highest priority network services is email! • Reasons for networks include; Most of these listed features require a NOS, a component of a Client/Server Network 1. 2. 3. 4. 5. File & Print services Remote user access Mail services Internet services Management Services • • Traffic monitoring Load balancing Security auditing Backup and restoration services
 NETWORK BASICS • Networks are differentiated by the following: – Architecture - peer-to-peer, client/server – Topology - bus, star, ring, hybrid, wireless – Protocols - Ethernet, Transmission Control Protocol/Internet Protocol (TCP/IP) – Media - coaxial, twisted-pair, fiber-optic
NETWORK BASICS • Networks are differentiated by the following: – Architecture - peer-to-peer, client/server – Topology - bus, star, ring, hybrid, wireless – Protocols - Ethernet, Transmission Control Protocol/Internet Protocol (TCP/IP) – Media - coaxial, twisted-pair, fiber-optic
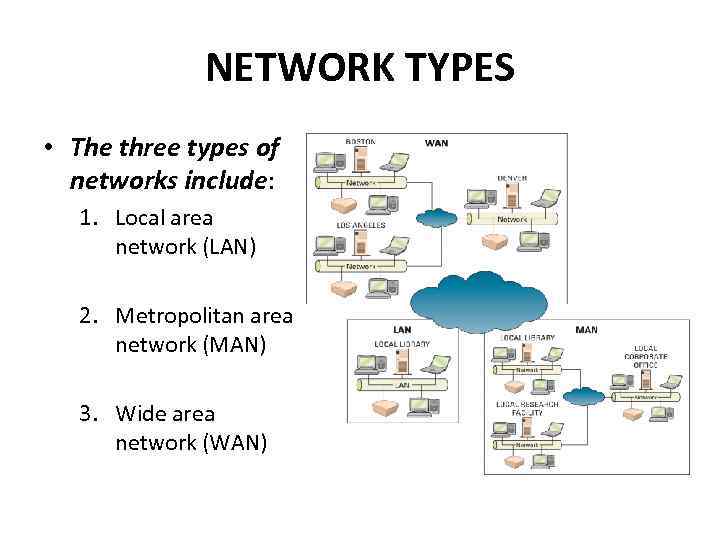 NETWORK TYPES • The three types of networks include: 1. Local area network (LAN) 2. Metropolitan area network (MAN) 3. Wide area network (WAN)
NETWORK TYPES • The three types of networks include: 1. Local area network (LAN) 2. Metropolitan area network (MAN) 3. Wide area network (WAN)
 Difference between MANS and WANS • MANS: networks that extend beyond the boundaries of a building. • It is a network that is larger than a LAN and connects clients and servers from multiple buildings • WANS: a network that connects two or more geographically distinct LANS or MANS. • Different than MANs because they typically transport data over much longer distances than MANs and as such often require different transmission methods, media, and use a greater variety of technologies
Difference between MANS and WANS • MANS: networks that extend beyond the boundaries of a building. • It is a network that is larger than a LAN and connects clients and servers from multiple buildings • WANS: a network that connects two or more geographically distinct LANS or MANS. • Different than MANs because they typically transport data over much longer distances than MANs and as such often require different transmission methods, media, and use a greater variety of technologies
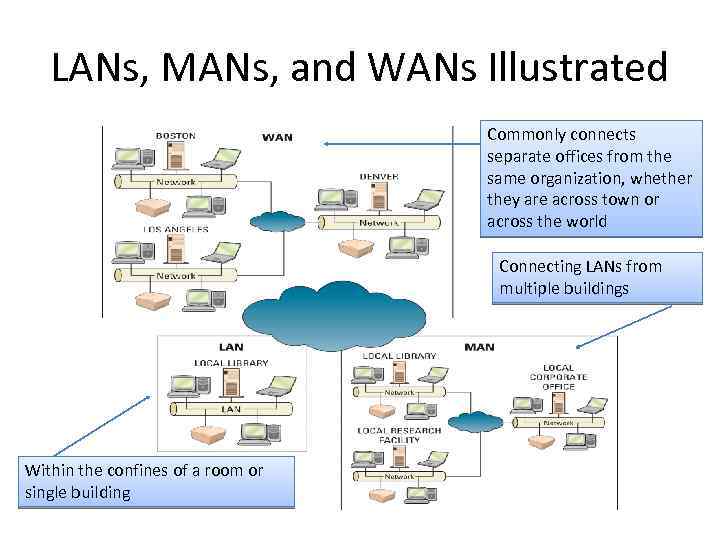 LANs, MANs, and WANs Illustrated Commonly connects separate offices from the same organization, whether they are across town or across the world Connecting LANs from multiple buildings Within the confines of a room or single building
LANs, MANs, and WANs Illustrated Commonly connects separate offices from the same organization, whether they are across town or across the world Connecting LANs from multiple buildings Within the confines of a room or single building
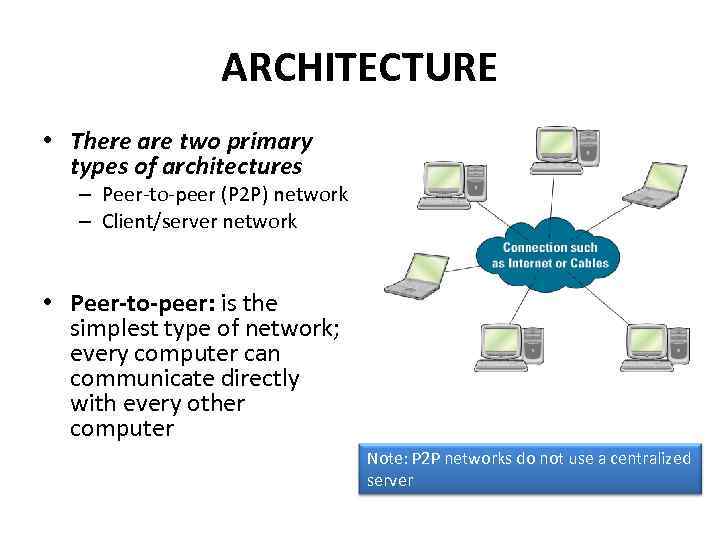 ARCHITECTURE • There are two primary types of architectures – Peer-to-peer (P 2 P) network – Client/server network • Peer-to-peer: is the simplest type of network; every computer can communicate directly with every other computer Note: P 2 P networks do not use a centralized server
ARCHITECTURE • There are two primary types of architectures – Peer-to-peer (P 2 P) network – Client/server network • Peer-to-peer: is the simplest type of network; every computer can communicate directly with every other computer Note: P 2 P networks do not use a centralized server
 Advantages & Disadvantages to P 2 P Networks Advantages Disadvantages • Simple to configure (Most home networks are P 2 P) • Not very flexible: as P 2 P networks grow, adding or changing significant elements of the network can be difficult • Not very secure: data and other resources shared by network users can be easily discovered and used by unauthorized users • Resource Sharing is not practical: each user is responsible for configuring Shared Docs and preventing access to other files: Meaning resource sharing is not controlled by a central computer or authority • Typically less expensive to setup and maintain than other types of networks.
Advantages & Disadvantages to P 2 P Networks Advantages Disadvantages • Simple to configure (Most home networks are P 2 P) • Not very flexible: as P 2 P networks grow, adding or changing significant elements of the network can be difficult • Not very secure: data and other resources shared by network users can be easily discovered and used by unauthorized users • Resource Sharing is not practical: each user is responsible for configuring Shared Docs and preventing access to other files: Meaning resource sharing is not controlled by a central computer or authority • Typically less expensive to setup and maintain than other types of networks.
 Client/Server Networks • Client/Server networks: use a central computer, known as a Server to facilitate communication and resource sharing between other computers on a network, which are known as Clients. • In terms of resource sharing you can compare the client/server network to a public library: Librarians manages the use of books and other media by patrons, a server manages the use of shared resources by clients…
Client/Server Networks • Client/Server networks: use a central computer, known as a Server to facilitate communication and resource sharing between other computers on a network, which are known as Clients. • In terms of resource sharing you can compare the client/server network to a public library: Librarians manages the use of books and other media by patrons, a server manages the use of shared resources by clients…
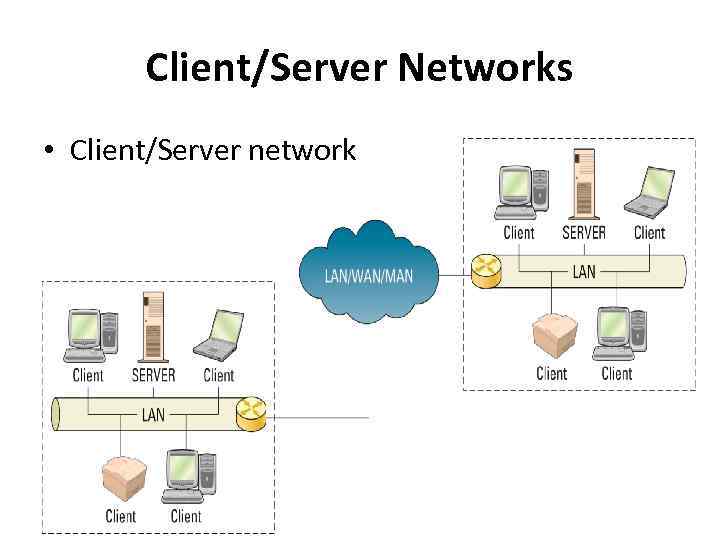 Client/Server Networks • Client/Server network
Client/Server Networks • Client/Server network
 Advantages of a Client/Server Network • Provide User logon accounts and passwords for user of the network • Access to multiple shared resources can be centrally granted to a single user or groups of users • Problems on the network can be tracked, diagnosed and often fixed from one location • Optimized for faster processing time to handle many requests from clients • Larger disk space means it is more scalable and more clients can be added as necessary
Advantages of a Client/Server Network • Provide User logon accounts and passwords for user of the network • Access to multiple shared resources can be centrally granted to a single user or groups of users • Problems on the network can be tracked, diagnosed and often fixed from one location • Optimized for faster processing time to handle many requests from clients • Larger disk space means it is more scalable and more clients can be added as necessary
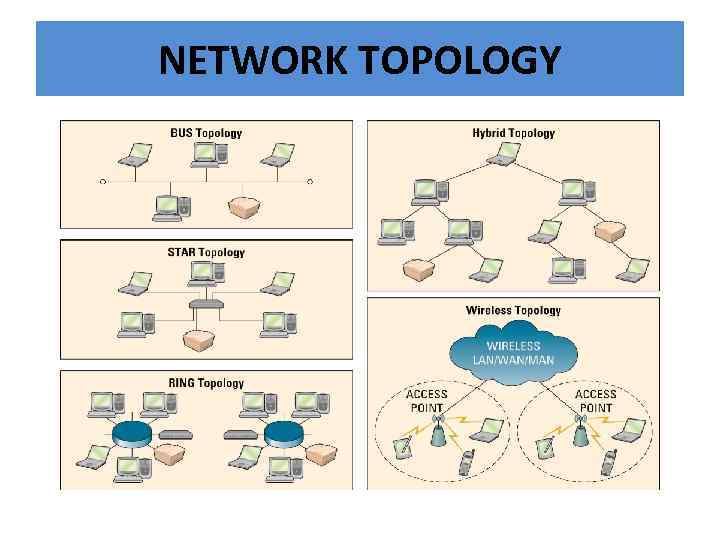
 TOPOLOGY • Network topology - refers to the geometric arrangement of the actual physical organization of the computers and other network devices) in a network – Bus – Star – Ring – Hybrid – Wireless
TOPOLOGY • Network topology - refers to the geometric arrangement of the actual physical organization of the computers and other network devices) in a network – Bus – Star – Ring – Hybrid – Wireless
 Bus/Star/Ring Topologies Bus Topology (linear bus) All devices are connected to a central cable, called the bus or backbone. These networks are relatively inexpensive and easy to install for small networks Star Topology All devices are connected to a central device, called a hub. Star networks are relatively easy to install & manage, but bottlenecks can occur because all data must pass through the hub Ring Topology The ring topology connects computers on a single circle of cable. Signals travel around the loop in one direction and pass through each computer acting like a repeater to boost the signal and send it on to the next computer.
Bus/Star/Ring Topologies Bus Topology (linear bus) All devices are connected to a central cable, called the bus or backbone. These networks are relatively inexpensive and easy to install for small networks Star Topology All devices are connected to a central device, called a hub. Star networks are relatively easy to install & manage, but bottlenecks can occur because all data must pass through the hub Ring Topology The ring topology connects computers on a single circle of cable. Signals travel around the loop in one direction and pass through each computer acting like a repeater to boost the signal and send it on to the next computer.
 Hybrid / Wireless Topologies Hybrid Topology Groups of star-configured workstations are connected to a linear bus backbone cable, combining the characteristics of bus and star topologies Wireless Devices are connected by a receiver/transmitter to a special network interface card that transmits signals between a computer and a server---all with an acceptable transmission range
Hybrid / Wireless Topologies Hybrid Topology Groups of star-configured workstations are connected to a linear bus backbone cable, combining the characteristics of bus and star topologies Wireless Devices are connected by a receiver/transmitter to a special network interface card that transmits signals between a computer and a server---all with an acceptable transmission range
 NETWORK TOPOLOGY
NETWORK TOPOLOGY
 Protocols • A protocol is a standard that specifies the format of data as well as the rules to be followed during transmission • Simply put, for one computer to talk to another computer, they must be speaking the same language. • Protocols provide the langauge
Protocols • A protocol is a standard that specifies the format of data as well as the rules to be followed during transmission • Simply put, for one computer to talk to another computer, they must be speaking the same language. • Protocols provide the langauge
 IEEE 802. 3 or Ethernet Protocol • The committee that addresses LAN standards is called the IEEE 802 Committee. – Thus, IEEE LAN protocols always start with the number 802. • Today, the world’s most popular protocol for LAN is the IEEE 802. 3 protocol. – This protocol standard, also called Ethernet, specifies hardware characteristics such as which wire carries which signals. – It also describes how messages are to be packaged and processed for transmission over the LAN.
IEEE 802. 3 or Ethernet Protocol • The committee that addresses LAN standards is called the IEEE 802 Committee. – Thus, IEEE LAN protocols always start with the number 802. • Today, the world’s most popular protocol for LAN is the IEEE 802. 3 protocol. – This protocol standard, also called Ethernet, specifies hardware characteristics such as which wire carries which signals. – It also describes how messages are to be packaged and processed for transmission over the LAN.
 IEE 802. 3 or Ethernet Protocol (Continued) • Most personal computers today are equipped with an onboard NIC that supports what is called 10/1000 Ethernet. – These products conform to the 802. 3 specification and allow for transmission at a rate of 10, 100, or 1, 000 Mbps. – Communications speeds are expressed in bits, whereas memory sizes are expressed in bytes.
IEE 802. 3 or Ethernet Protocol (Continued) • Most personal computers today are equipped with an onboard NIC that supports what is called 10/1000 Ethernet. – These products conform to the 802. 3 specification and allow for transmission at a rate of 10, 100, or 1, 000 Mbps. – Communications speeds are expressed in bits, whereas memory sizes are expressed in bytes.
 Ethernet Packets • The actual data to be sent • Media Access Control (MAC): Address of the packets source • The MAC address of the intended recipient • A Cyclic Redundancy Check or (CRC code)
Ethernet Packets • The actual data to be sent • Media Access Control (MAC): Address of the packets source • The MAC address of the intended recipient • A Cyclic Redundancy Check or (CRC code)
 Security Perspective • This system of allowing each machine to decide which packets to process does not provide any security. • Keep in mind that any device that can connect to the network cable can conceivably capture any data packet transmitted across the wire. Many network diagnostic programs, commonly referred to as packet sniffers, can tell a NIC to run in promiscuous mode.
Security Perspective • This system of allowing each machine to decide which packets to process does not provide any security. • Keep in mind that any device that can connect to the network cable can conceivably capture any data packet transmitted across the wire. Many network diagnostic programs, commonly referred to as packet sniffers, can tell a NIC to run in promiscuous mode.
 • Running in promiscuous mode, the computer will process all packets that it sees on the cable, regardless of the specified MAC addresses. • Packet sniffers can be valuable troubleshooting tools in the right hands, but Ethernet provides no protections against unscrupulous use. • If security of the data is important, consider installing some type of additional encryption software to safeguard your data
• Running in promiscuous mode, the computer will process all packets that it sees on the cable, regardless of the specified MAC addresses. • Packet sniffers can be valuable troubleshooting tools in the right hands, but Ethernet provides no protections against unscrupulous use. • If security of the data is important, consider installing some type of additional encryption software to safeguard your data
 MEDIA • Network transmission media - refers to the various types of media used to carry the signal between computers – Wire media (guided) – Wireless media (unguided)
MEDIA • Network transmission media - refers to the various types of media used to carry the signal between computers – Wire media (guided) – Wireless media (unguided)
 Wire Media • Wire media - transmission material manufactured so that signals will be confined to a narrow path and will behave predictably • Three most commonly used types include: 1. Twisted-pair wiring 2. Coaxial cable 3. Fiber optic (or optical fiber)
Wire Media • Wire media - transmission material manufactured so that signals will be confined to a narrow path and will behave predictably • Three most commonly used types include: 1. Twisted-pair wiring 2. Coaxial cable 3. Fiber optic (or optical fiber)
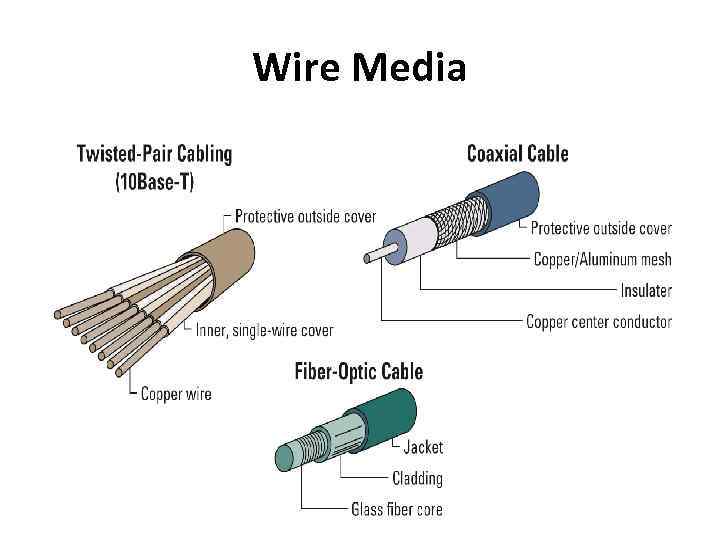 Wire Media
Wire Media
 Wireless Media • Wireless media - natural parts of the Earth’s environment that can be used as physical paths to carry electrical signals • Atmosphere and outerspace are examples of wireless media that commonly carry signals
Wireless Media • Wireless media - natural parts of the Earth’s environment that can be used as physical paths to carry electrical signals • Atmosphere and outerspace are examples of wireless media that commonly carry signals
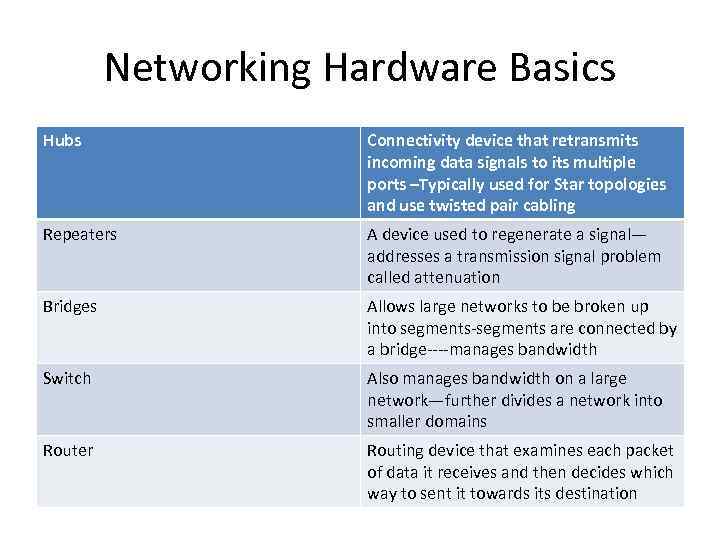 Networking Hardware Basics Hubs Connectivity device that retransmits incoming data signals to its multiple ports –Typically used for Star topologies and use twisted pair cabling Repeaters A device used to regenerate a signal— addresses a transmission signal problem called attenuation Bridges Allows large networks to be broken up into segments-segments are connected by a bridge----manages bandwidth Switch Also manages bandwidth on a large network—further divides a network into smaller domains Router Routing device that examines each packet of data it receives and then decides which way to sent it towards its destination
Networking Hardware Basics Hubs Connectivity device that retransmits incoming data signals to its multiple ports –Typically used for Star topologies and use twisted pair cabling Repeaters A device used to regenerate a signal— addresses a transmission signal problem called attenuation Bridges Allows large networks to be broken up into segments-segments are connected by a bridge----manages bandwidth Switch Also manages bandwidth on a large network—further divides a network into smaller domains Router Routing device that examines each packet of data it receives and then decides which way to sent it towards its destination
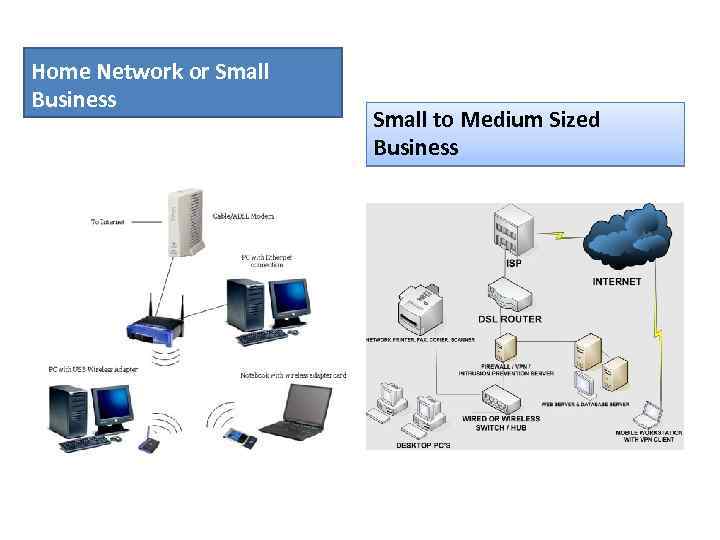 Home Network or Small Business Small to Medium Sized Business
Home Network or Small Business Small to Medium Sized Business
 E-Business Networks • Today’s industry-leading • This means; companies have • Integrating online developed internetpurchases with based products and inventory and POS services to handle many systems so that aspects of customer and customers have a supplier interactions seamless experience between purchase and return or service
E-Business Networks • Today’s industry-leading • This means; companies have • Integrating online developed internetpurchases with based products and inventory and POS services to handle many systems so that aspects of customer and customers have a supplier interactions seamless experience between purchase and return or service
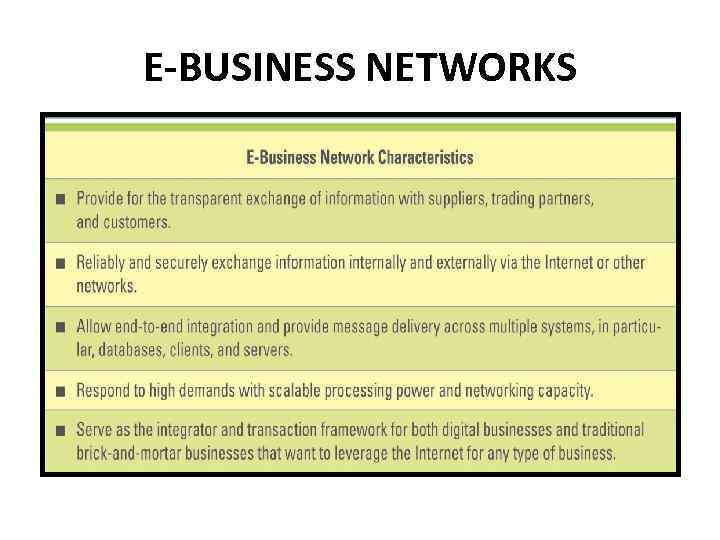 E-BUSINESS NETWORKS
E-BUSINESS NETWORKS
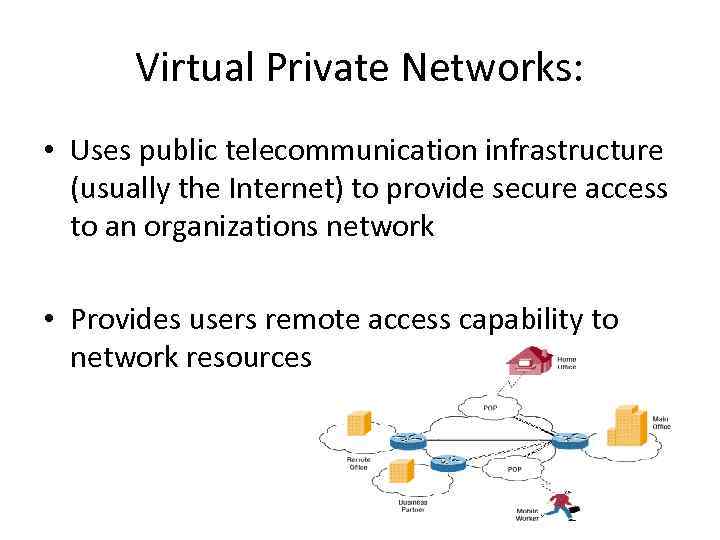 Virtual Private Networks: • Uses public telecommunication infrastructure (usually the Internet) to provide secure access to an organizations network • Provides users remote access capability to network resources
Virtual Private Networks: • Uses public telecommunication infrastructure (usually the Internet) to provide secure access to an organizations network • Provides users remote access capability to network resources
 How Hospitals are Taken Advantage of Network tech • Wireless Networking • RFID • Electronic Health Records
How Hospitals are Taken Advantage of Network tech • Wireless Networking • RFID • Electronic Health Records
 Increased Use of Technology • The medical industry is attempting to increase efficiency and functionality by adopting technology. This technology takes the form of electronic medical records, radio frequency identification for patient tracking, and wireless networking among other technologies. • These technologies increase the productivity of institutions but, also introduce new risks to patient privacy.
Increased Use of Technology • The medical industry is attempting to increase efficiency and functionality by adopting technology. This technology takes the form of electronic medical records, radio frequency identification for patient tracking, and wireless networking among other technologies. • These technologies increase the productivity of institutions but, also introduce new risks to patient privacy.
 Examples of new tech used in Healthcare • RFID: radio frequency identification combined with wireless networking technology. – RFID tags used could be used in conjunction with patient’s cell phones to provide a wide variety of dietary and health related information when buying groceries • The literature states that wireless network technology and RFID’s could provide medical providers with “location tracking, body sensors, and short range wireless communications for monitoring the health of patients.
Examples of new tech used in Healthcare • RFID: radio frequency identification combined with wireless networking technology. – RFID tags used could be used in conjunction with patient’s cell phones to provide a wide variety of dietary and health related information when buying groceries • The literature states that wireless network technology and RFID’s could provide medical providers with “location tracking, body sensors, and short range wireless communications for monitoring the health of patients.
 Concerns with RFID’s • You. Tube Video: Privacy Concerns
Concerns with RFID’s • You. Tube Video: Privacy Concerns
 Emerging Technologies: teleprensence Telepresence
Emerging Technologies: teleprensence Telepresence
 IP Addressing
IP Addressing
 What is an IP address? • An unique identifier for a computer or device (host) on a TCP/IP network • A 32 -bit binary number usually represented as 4 decimal numbers separated by a period Example: 206. 40. 185. 73 11001110. 00101000. 10111001. 01001001 41
What is an IP address? • An unique identifier for a computer or device (host) on a TCP/IP network • A 32 -bit binary number usually represented as 4 decimal numbers separated by a period Example: 206. 40. 185. 73 11001110. 00101000. 10111001. 01001001 41
 What is an IP address? • Each address is 32 bits wide • Valid addresses can range from 0. 0 to 255 WHY? Because 1111 b = 25510 42
What is an IP address? • Each address is 32 bits wide • Valid addresses can range from 0. 0 to 255 WHY? Because 1111 b = 25510 42
 What is an IP address? Theoretically, a total of » 4. 3 billion addresses are available WHY? Because 232 = 4, 294, 967, 29610 43
What is an IP address? Theoretically, a total of » 4. 3 billion addresses are available WHY? Because 232 = 4, 294, 967, 29610 43
 Two addresses in one… • Each address consists of two parts 1. The network address 2. The host address • Other systems may use more than one address (Ex: IPX) 44
Two addresses in one… • Each address consists of two parts 1. The network address 2. The host address • Other systems may use more than one address (Ex: IPX) 44
 The Five Network Classes 1. Class A – begins with 0 • 00000001 (110) to 01111111 (12610)* 2. Class B – begins with 10 • 10000000 (12810) to 10111111 (19110) 3. Class C – begins with 110 • 11000000 (19210) to 11011111 (22310) *01111111 = 12710 Addresses beginning with 127 are reserved for loopback (127. 0. 0. 1 is YOU) 45
The Five Network Classes 1. Class A – begins with 0 • 00000001 (110) to 01111111 (12610)* 2. Class B – begins with 10 • 10000000 (12810) to 10111111 (19110) 3. Class C – begins with 110 • 11000000 (19210) to 11011111 (22310) *01111111 = 12710 Addresses beginning with 127 are reserved for loopback (127. 0. 0. 1 is YOU) 45
 The Five Network Classes 4. Class D – begins with 1110 • 22410 to 23910 • Reserved for multicasting 5. Class E – begins with 1111 • 24010 to 25410 • Reserved for future use These should not be used for host addressing 46
The Five Network Classes 4. Class D – begins with 1110 • 22410 to 23910 • Reserved for multicasting 5. Class E – begins with 1111 • 24010 to 25410 • Reserved for future use These should not be used for host addressing 46
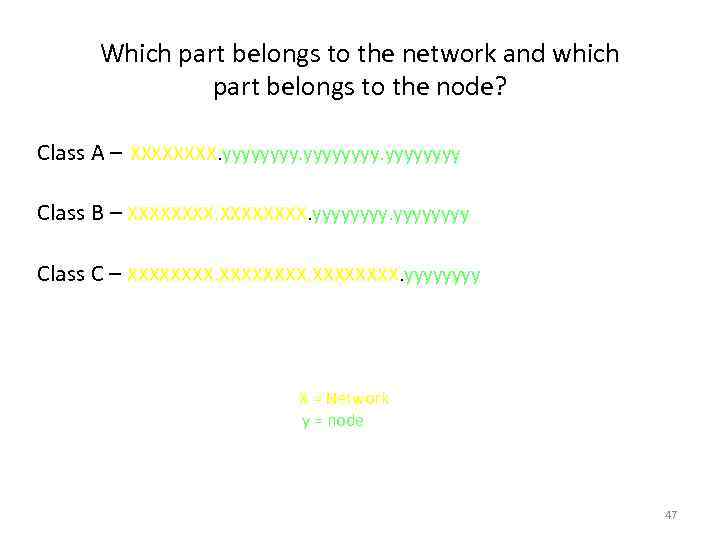 Which part belongs to the network and which part belongs to the node? Class A – XXXX. yyyyyyyy Class B – XXXXXXXX. yyyy Class C – XXXXXXXX. yyyy Where X = Network and y = node 47
Which part belongs to the network and which part belongs to the node? Class A – XXXX. yyyyyyyy Class B – XXXXXXXX. yyyy Class C – XXXXXXXX. yyyy Where X = Network and y = node 47
 There are three IP network addresses reserved for private networks 1. 10. 0/8 2. 172. 16. 0. 0/12 3. 192. 168. 0. 0/16 These can be used by anyone setting up an internal network. Routers will never forward packets coming from these addresses. 48
There are three IP network addresses reserved for private networks 1. 10. 0/8 2. 172. 16. 0. 0/12 3. 192. 168. 0. 0/16 These can be used by anyone setting up an internal network. Routers will never forward packets coming from these addresses. 48
 Subnetting • …can be done for a variety of reasons – Organization – Use of different physical media – Preservation of address space – Security • The most common reason is to control network traffic 49
Subnetting • …can be done for a variety of reasons – Organization – Use of different physical media – Preservation of address space – Security • The most common reason is to control network traffic 49
 Subnetting • In an Ethernet network, all nodes on a segment see all packets transmitted by other nodes on that segment • Performance can be adversely affected under heavy traffic loads • A router is used to connect IP networks to minimize the amount of traffic each segment must receive 50
Subnetting • In an Ethernet network, all nodes on a segment see all packets transmitted by other nodes on that segment • Performance can be adversely affected under heavy traffic loads • A router is used to connect IP networks to minimize the amount of traffic each segment must receive 50
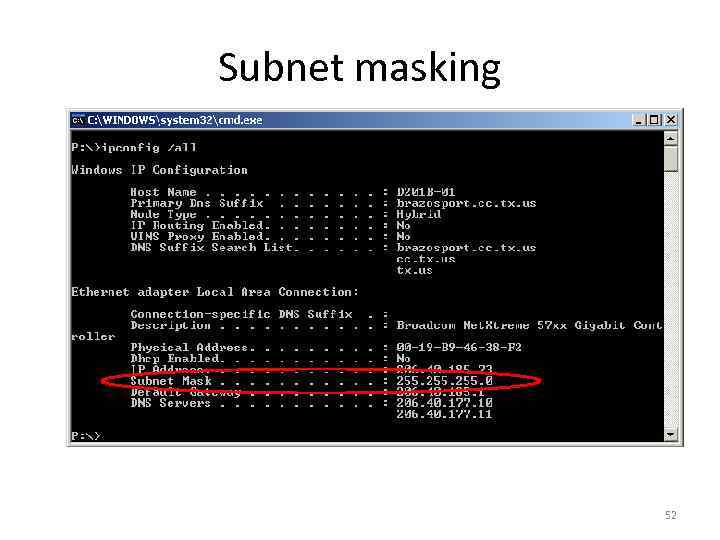
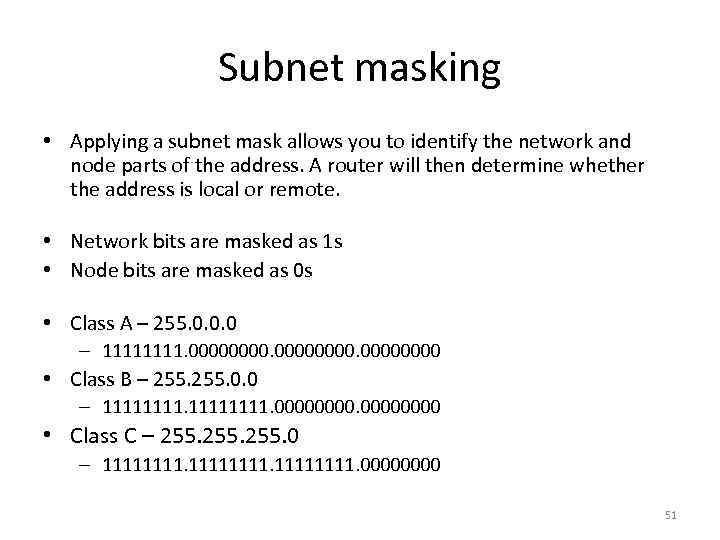 Subnet masking • Applying a subnet mask allows you to identify the network and node parts of the address. A router will then determine whether the address is local or remote. • Network bits are masked as 1 s • Node bits are masked as 0 s • Class A – 255. 0. 0. 0 – 1111. 00000000 • Class B – 255. 0. 0 – 11111111. 0000 • Class C – 255. 0 – 11111111. 0000 51
Subnet masking • Applying a subnet mask allows you to identify the network and node parts of the address. A router will then determine whether the address is local or remote. • Network bits are masked as 1 s • Node bits are masked as 0 s • Class A – 255. 0. 0. 0 – 1111. 00000000 • Class B – 255. 0. 0 – 11111111. 0000 • Class C – 255. 0 – 11111111. 0000 51
 Subnet masking 52
Subnet masking 52
 Subnet masking • Performing a bitwise logical AND between the IP address and the subnet mask results in the network address • Ex: Class - B 140. 179. 240. 200 10001100. 10110011. 11110000. 11001000 11111111. 0000 10001100. 10110011. 00000000 Network Address = 140. 179. 000 53
Subnet masking • Performing a bitwise logical AND between the IP address and the subnet mask results in the network address • Ex: Class - B 140. 179. 240. 200 10001100. 10110011. 11110000. 11001000 11111111. 0000 10001100. 10110011. 00000000 Network Address = 140. 179. 000 53
 A Few Rules… 1. Each device on a node has a unique MAC address 2. Each device on a node needs a unique IP address 3. All devices on the same physical segment share a common network ID (subnet mask) 4. Each physical segment has a unique Network ID (subnet mask) 54
A Few Rules… 1. Each device on a node has a unique MAC address 2. Each device on a node needs a unique IP address 3. All devices on the same physical segment share a common network ID (subnet mask) 4. Each physical segment has a unique Network ID (subnet mask) 54
 Address Resolution Protocol (ARP) • Before an IP packet can be forwarded to another host, the MAC address (usually 6 bytes written in hex (Ex: 02 -FE-87 -4 A 8 C-A 9) of the receiving machine must be known • ARP determines the MAC addresses that correspond to an IP address • A router will choose direct paths for the network packets based on the addressing of the IP frame it is handling (different routes to different networks) 55
Address Resolution Protocol (ARP) • Before an IP packet can be forwarded to another host, the MAC address (usually 6 bytes written in hex (Ex: 02 -FE-87 -4 A 8 C-A 9) of the receiving machine must be known • ARP determines the MAC addresses that correspond to an IP address • A router will choose direct paths for the network packets based on the addressing of the IP frame it is handling (different routes to different networks) 55


