b65535ce725a1c0c5afb32f40bad637e.ppt
- Количество слайдов: 58
 Network Security
Network Security
 Why Network Security? q Malicious people share your network q Problem made more severe the more the Internet became commercialized 2
Why Network Security? q Malicious people share your network q Problem made more severe the more the Internet became commercialized 2
 What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 3
What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 3
 Security Tools q Cryptography/Encryption: v v Encode a message in a way that only the communicating parties can interpret it Used for secrecy and authentication 4
Security Tools q Cryptography/Encryption: v v Encode a message in a way that only the communicating parties can interpret it Used for secrecy and authentication 4
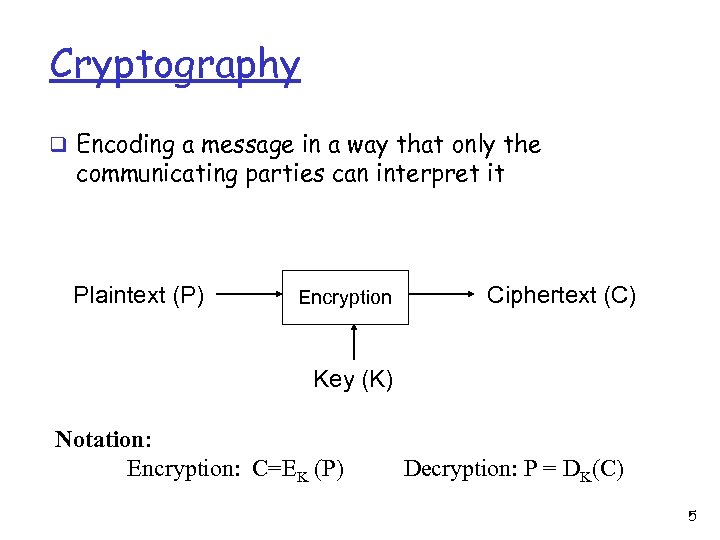 Cryptography q Encoding a message in a way that only the communicating parties can interpret it Plaintext (P) Encryption Ciphertext (C) Key (K) Notation: Encryption: C=EK (P) Decryption: P = DK(C) 5
Cryptography q Encoding a message in a way that only the communicating parties can interpret it Plaintext (P) Encryption Ciphertext (C) Key (K) Notation: Encryption: C=EK (P) Decryption: P = DK(C) 5
 Rules for Encryption q Encryption requires: v Algorithm: • Public, known to all – Inspires trust that the algorithm works v Keys: • Long enough to prevent easy breaking of the encryption • Short enough to keep algorithm efficient • Typical key lengths: 56 -bit, 128 -bit, 256 -bit, 512 -bit 6
Rules for Encryption q Encryption requires: v Algorithm: • Public, known to all – Inspires trust that the algorithm works v Keys: • Long enough to prevent easy breaking of the encryption • Short enough to keep algorithm efficient • Typical key lengths: 56 -bit, 128 -bit, 256 -bit, 512 -bit 6
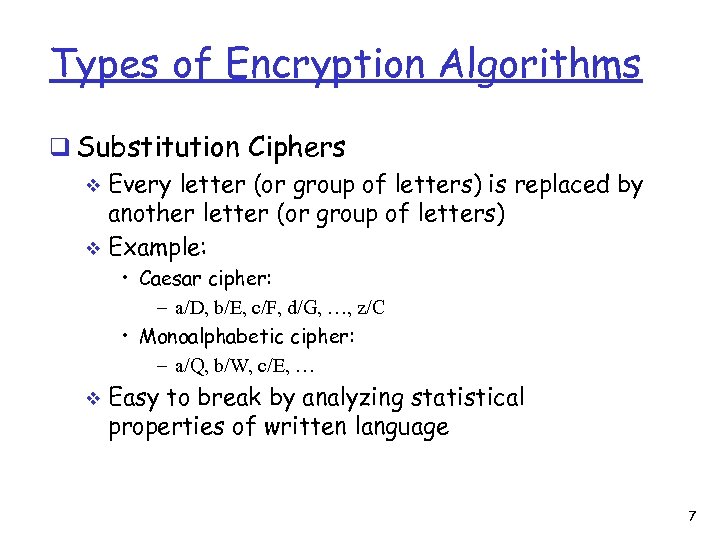 Types of Encryption Algorithms q Substitution Ciphers v Every letter (or group of letters) is replaced by another letter (or group of letters) v Example: • Caesar cipher: – a/D, b/E, c/F, d/G, …, z/C • Monoalphabetic cipher: – a/Q, b/W, c/E, … v Easy to break by analyzing statistical properties of written language 7
Types of Encryption Algorithms q Substitution Ciphers v Every letter (or group of letters) is replaced by another letter (or group of letters) v Example: • Caesar cipher: – a/D, b/E, c/F, d/G, …, z/C • Monoalphabetic cipher: – a/Q, b/W, c/E, … v Easy to break by analyzing statistical properties of written language 7
 Types of Encryption (cont’d) q Transposition Ciphers v Instead of substituting letters in the plaintext, we change their order A 1 t a g l t y N 4 h m e d o p D 2 i e i l e t R 5 s s w i n n E 3 i s o k c o W 6 s a u e r w Key = ANDREW Plaintext = thisisamessageiwould liketoencryptnow Ciphertext = tagltyieiletisokco hmedopsswinnsauerw 8
Types of Encryption (cont’d) q Transposition Ciphers v Instead of substituting letters in the plaintext, we change their order A 1 t a g l t y N 4 h m e d o p D 2 i e i l e t R 5 s s w i n n E 3 i s o k c o W 6 s a u e r w Key = ANDREW Plaintext = thisisamessageiwould liketoencryptnow Ciphertext = tagltyieiletisokco hmedopsswinnsauerw 8
 Transposition Cipher Decryption q The following message has been encrypted using transposition. The transposition key is “SKYBLUE”. q SRMTISHEAGIIETHNASGSIOLE q Give the plaintext message? 9
Transposition Cipher Decryption q The following message has been encrypted using transposition. The transposition key is “SKYBLUE”. q SRMTISHEAGIIETHNASGSIOLE q Give the plaintext message? 9
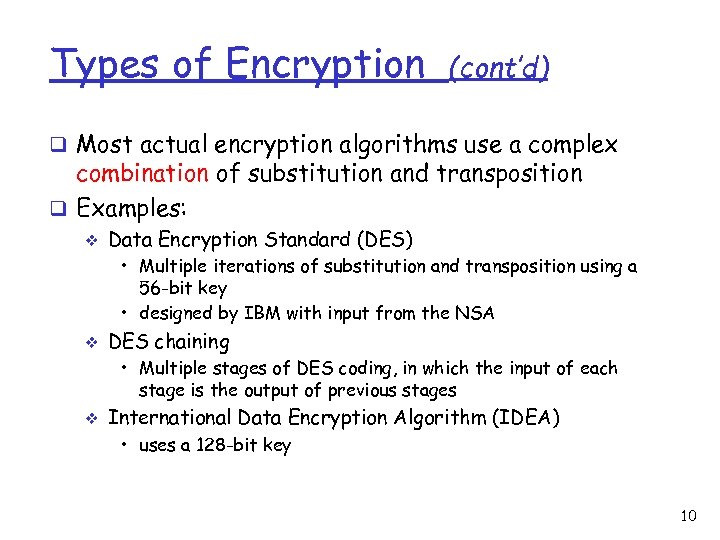 Types of Encryption (cont’d) q Most actual encryption algorithms use a complex combination of substitution and transposition q Examples: v Data Encryption Standard (DES) • Multiple iterations of substitution and transposition using a 56 -bit key • designed by IBM with input from the NSA v DES chaining • Multiple stages of DES coding, in which the input of each stage is the output of previous stages v International Data Encryption Algorithm (IDEA) • uses a 128 -bit key 10
Types of Encryption (cont’d) q Most actual encryption algorithms use a complex combination of substitution and transposition q Examples: v Data Encryption Standard (DES) • Multiple iterations of substitution and transposition using a 56 -bit key • designed by IBM with input from the NSA v DES chaining • Multiple stages of DES coding, in which the input of each stage is the output of previous stages v International Data Encryption Algorithm (IDEA) • uses a 128 -bit key 10
 Symmetric Encryption q Problem with all the cryptography algorithms used so far? How to communicate the shared key safely 11
Symmetric Encryption q Problem with all the cryptography algorithms used so far? How to communicate the shared key safely 11
 Public Key Cryptography symmetric key crypto q requires sender, receiver know shared secret key public key cryptography q sender, receiver do not share secret key q public encryption key known to all q private decryption key known only to receiver 12
Public Key Cryptography symmetric key crypto q requires sender, receiver know shared secret key public key cryptography q sender, receiver do not share secret key q public encryption key known to all q private decryption key known only to receiver 12
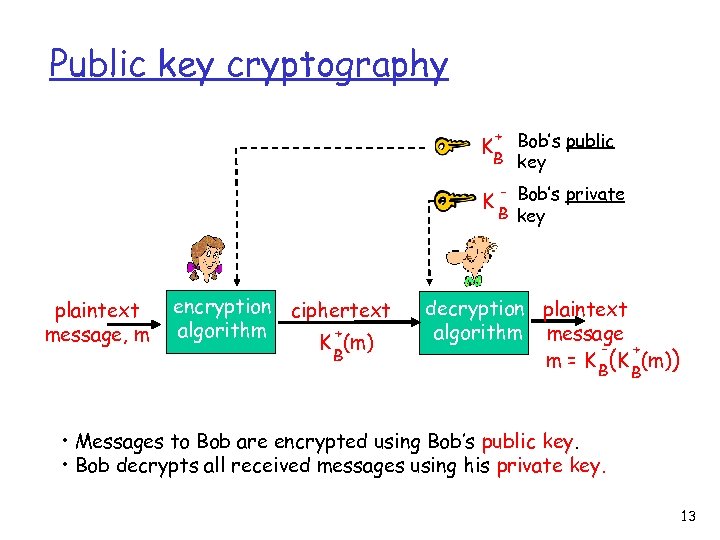 Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B • Messages to Bob are encrypted using Bob’s public key. • Bob decrypts all received messages using his private key. 13
Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B • Messages to Bob are encrypted using Bob’s public key. • Bob decrypts all received messages using his private key. 13
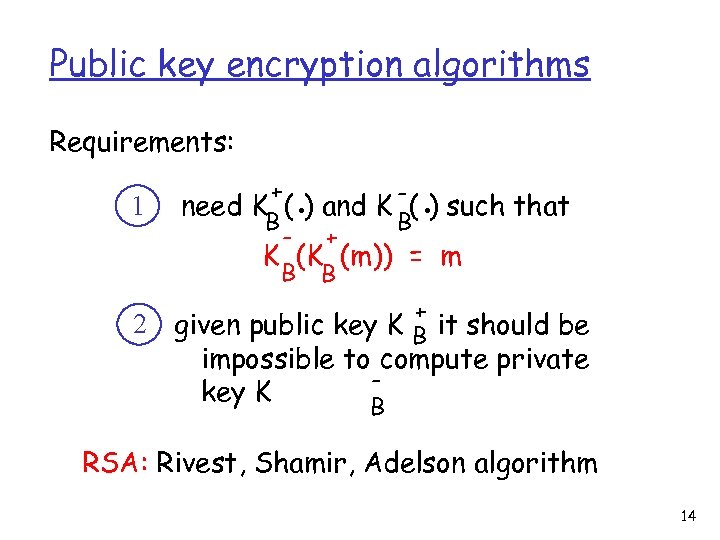 Public key encryption algorithms Requirements: 1 + B - . B . need K ( ) and K ( ) such that + K (K (m)) = m B B + 2 given public key K B it should be impossible to compute private key K B RSA: Rivest, Shamir, Adelson algorithm 14
Public key encryption algorithms Requirements: 1 + B - . B . need K ( ) and K ( ) such that + K (K (m)) = m B B + 2 given public key K B it should be impossible to compute private key K B RSA: Rivest, Shamir, Adelson algorithm 14
 RSA: Choosing keys 1. Choose two large prime numbers p, q. (e. g. , 1024 bits each) 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e
RSA: Choosing keys 1. Choose two large prime numbers p, q. (e. g. , 1024 bits each) 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e
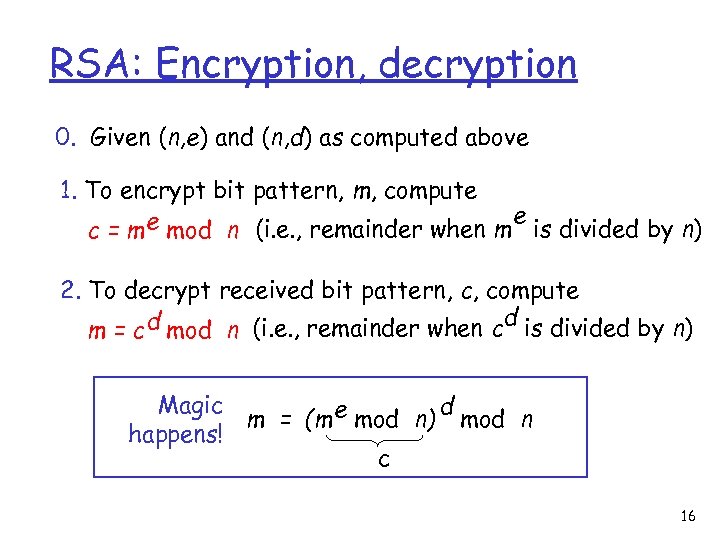 RSA: Encryption, decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt bit pattern, m, compute e mod n (i. e. , remainder when m e is divided by n) c=m 2. To decrypt received bit pattern, c, compute d m = c d mod n (i. e. , remainder when c is divided by n) Magic d m = (m e mod n) mod n happens! c 16
RSA: Encryption, decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt bit pattern, m, compute e mod n (i. e. , remainder when m e is divided by n) c=m 2. To decrypt received bit pattern, c, compute d m = c d mod n (i. e. , remainder when c is divided by n) Magic d m = (m e mod n) mod n happens! c 16
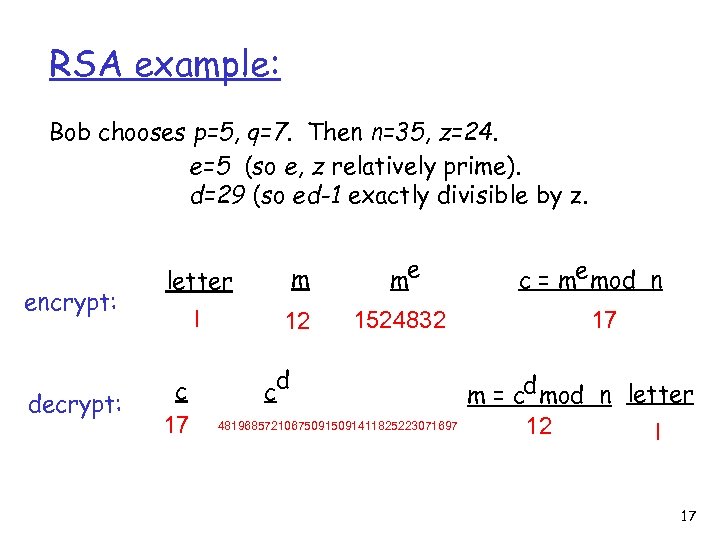 RSA example: Bob chooses p=5, q=7. Then n=35, z=24. e=5 (so e, z relatively prime). d=29 (so ed-1 exactly divisible by z. encrypt: decrypt: letter m me l 12 1524832 c 17 d c 48196857210675091411825223071697 c = me mod n 17 m = cd mod n letter 12 l 17
RSA example: Bob chooses p=5, q=7. Then n=35, z=24. e=5 (so e, z relatively prime). d=29 (so ed-1 exactly divisible by z. encrypt: decrypt: letter m me l 12 1524832 c 17 d c 48196857210675091411825223071697 c = me mod n 17 m = cd mod n letter 12 l 17
 RSA: m = (m e mod n) Why is that d mod n Useful number theory result: If p, q prime and n = pq, then: y y mod (p-1)(q-1) x mod n = x mod n e (m mod n) d mod n = med mod n = m ed mod (p-1)(q-1) mod n (using number theory result above) 1 = m mod n (since we chose ed to be divisible by (p-1)(q-1) with remainder 1 ) = m 18
RSA: m = (m e mod n) Why is that d mod n Useful number theory result: If p, q prime and n = pq, then: y y mod (p-1)(q-1) x mod n = x mod n e (m mod n) d mod n = med mod n = m ed mod (p-1)(q-1) mod n (using number theory result above) 1 = m mod n (since we chose ed to be divisible by (p-1)(q-1) with remainder 1 ) = m 18
 RSA: another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! 19
RSA: another important property The following property will be very useful later: - + B B K (K (m)) + = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key Result is the same! 19
 Cryptography question q Suppose N people want to communicate with each of N-1 other people. All communication between any two people, i and j is visible to all other people in the group and security is guaranteed by the encryption scheme. v v With symmetric key encryption, how many keys are required in the system as a whole? Express you answer in terms of N. How many keys are required (total) using public/private key cryptography. Express your answer in terms of N. 20
Cryptography question q Suppose N people want to communicate with each of N-1 other people. All communication between any two people, i and j is visible to all other people in the group and security is guaranteed by the encryption scheme. v v With symmetric key encryption, how many keys are required in the system as a whole? Express you answer in terms of N. How many keys are required (total) using public/private key cryptography. Express your answer in terms of N. 20
 What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 21
What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 21
 Authentication Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” Failure scenario? ? 22
Authentication Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” Failure scenario? ? 22
 Authentication Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” in a network, Bob can not “see” Alice, so Trudy simply declares herself to be Alice 23
Authentication Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” in a network, Bob can not “see” Alice, so Trudy simply declares herself to be Alice 23
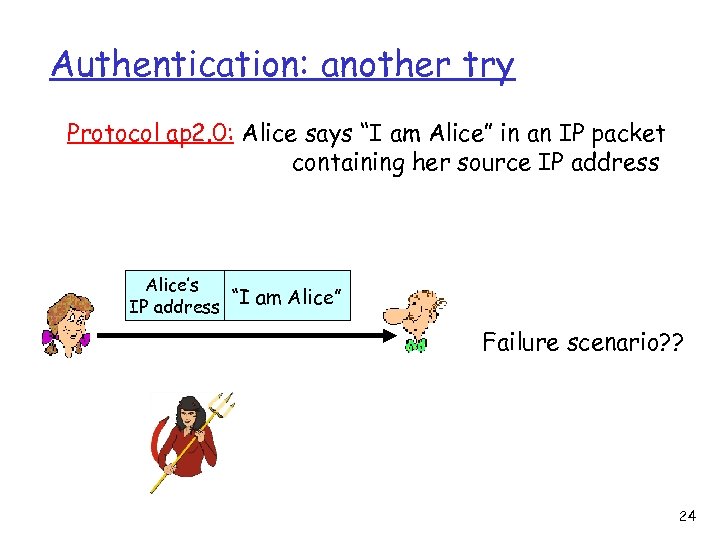 Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address Failure scenario? ? 24
Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address Failure scenario? ? 24
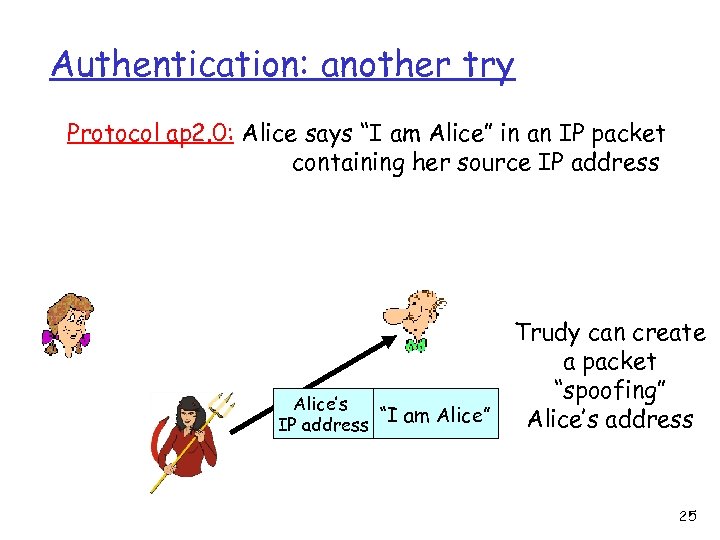 Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s IP address Trudy can create a packet “spoofing” “I am Alice” Alice’s address 25
Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s IP address Trudy can create a packet “spoofing” “I am Alice” Alice’s address 25
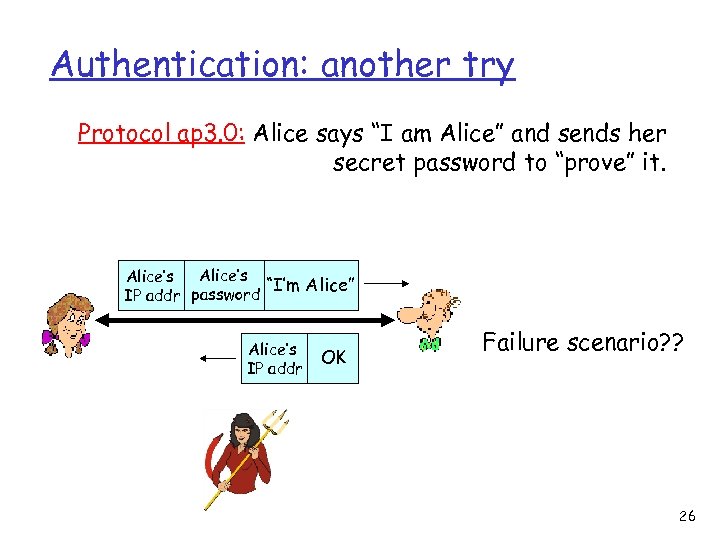 Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr OK Failure scenario? ? 26
Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr OK Failure scenario? ? 26
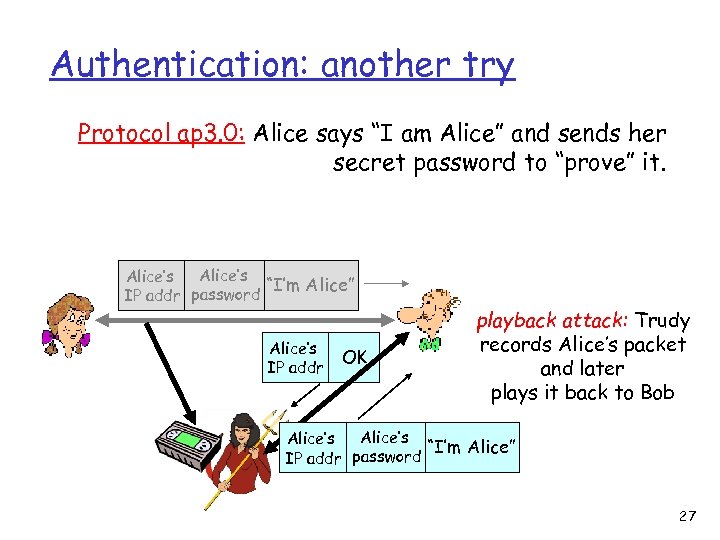 Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr OK playback attack: Trudy records Alice’s packet and later plays it back to Bob Alice’s “I’m Alice” IP addr password 27
Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr OK playback attack: Trudy records Alice’s packet and later plays it back to Bob Alice’s “I’m Alice” IP addr password 27
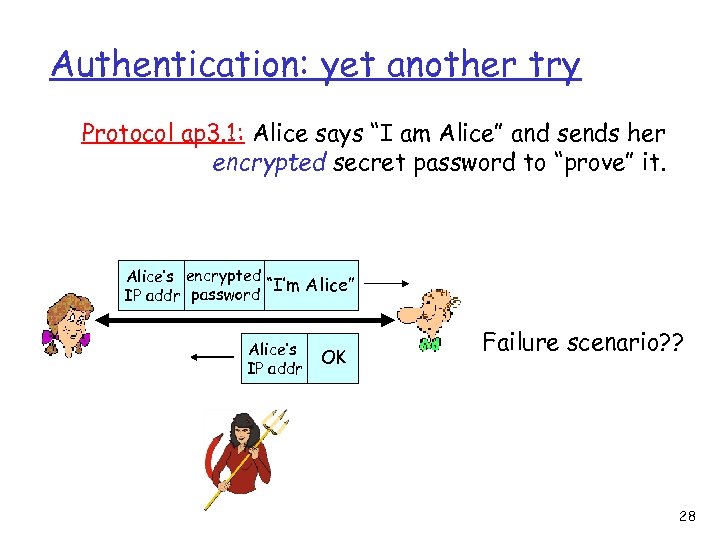 Authentication: yet another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr OK Failure scenario? ? 28
Authentication: yet another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr OK Failure scenario? ? 28
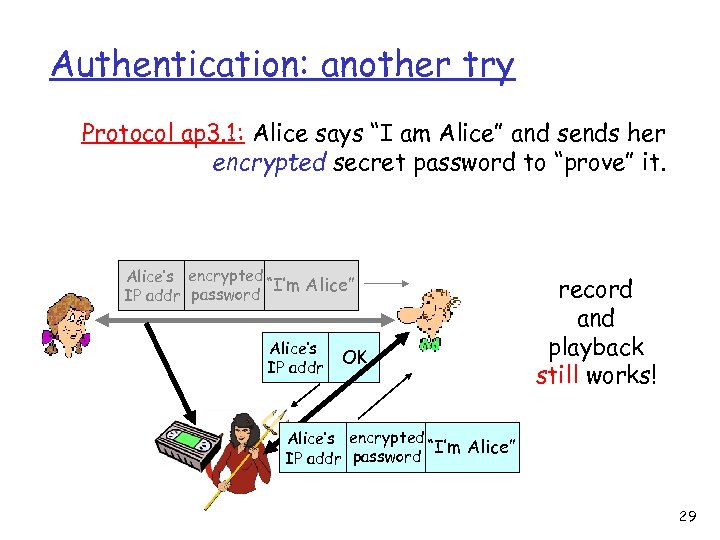 Authentication: another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr OK record and playback still works! Alice’s encrypted “I’m Alice” IP addr password 29
Authentication: another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr OK record and playback still works! Alice’s encrypted “I’m Alice” IP addr password 29
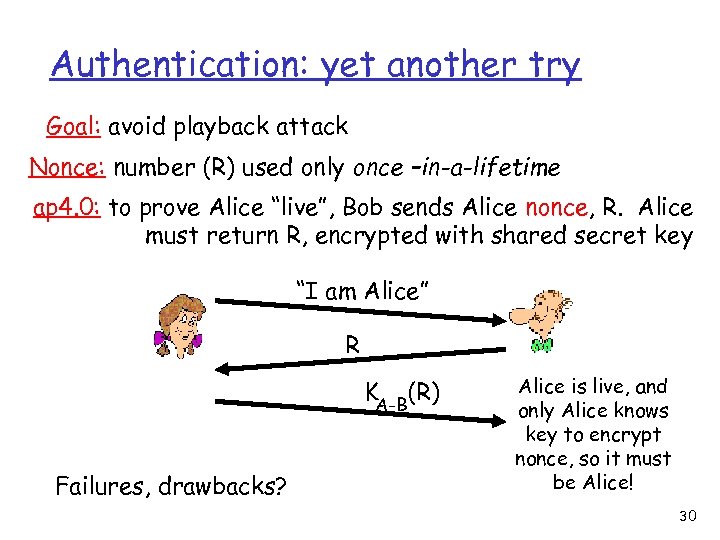 Authentication: yet another try Goal: avoid playback attack Nonce: number (R) used only once –in-a-lifetime ap 4. 0: to prove Alice “live”, Bob sends Alice nonce, R. Alice must return R, encrypted with shared secret key “I am Alice” R KA-B(R) Failures, drawbacks? Alice is live, and only Alice knows key to encrypt nonce, so it must be Alice! 30
Authentication: yet another try Goal: avoid playback attack Nonce: number (R) used only once –in-a-lifetime ap 4. 0: to prove Alice “live”, Bob sends Alice nonce, R. Alice must return R, encrypted with shared secret key “I am Alice” R KA-B(R) Failures, drawbacks? Alice is live, and only Alice knows key to encrypt nonce, so it must be Alice! 30
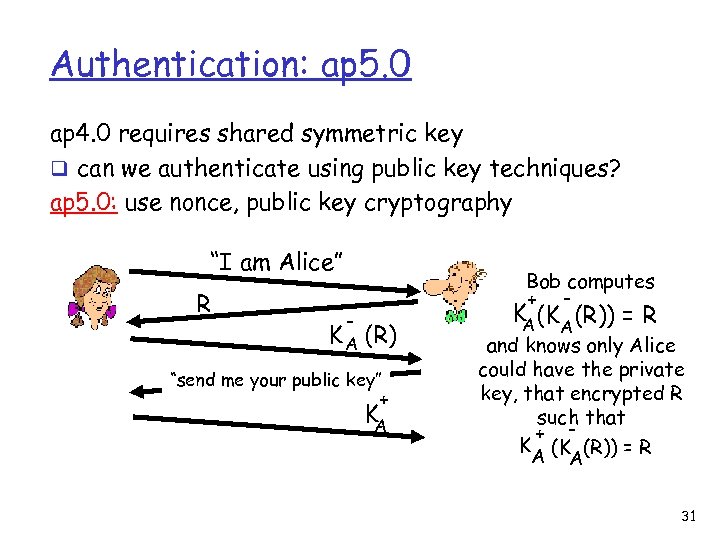 Authentication: ap 5. 0 ap 4. 0 requires shared symmetric key q can we authenticate using public key techniques? ap 5. 0: use nonce, public key cryptography “I am Alice” R Bob computes + - - K A (R) “send me your public key” + KA KA(KA (R)) = R and knows only Alice could have the private key, that encrypted R such that + K (K (R)) = R A A 31
Authentication: ap 5. 0 ap 4. 0 requires shared symmetric key q can we authenticate using public key techniques? ap 5. 0: use nonce, public key cryptography “I am Alice” R Bob computes + - - K A (R) “send me your public key” + KA KA(KA (R)) = R and knows only Alice could have the private key, that encrypted R such that + K (K (R)) = R A A 31
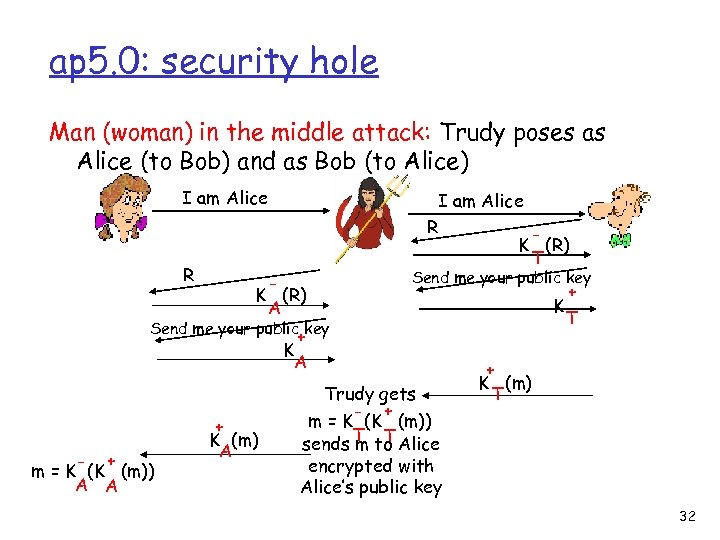 ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) I am Alice R K (R) T K (R) A Send me your public key + K T Send me your public key + K A - + m = K (K (m)) A A + K (m) A Trudy gets - + m = K (K (m)) sends T to Alice m T + K (m) T encrypted with Alice’s public key 32
ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) I am Alice R K (R) T K (R) A Send me your public key + K T Send me your public key + K A - + m = K (K (m)) A A + K (m) A Trudy gets - + m = K (K (m)) sends T to Alice m T + K (m) T encrypted with Alice’s public key 32
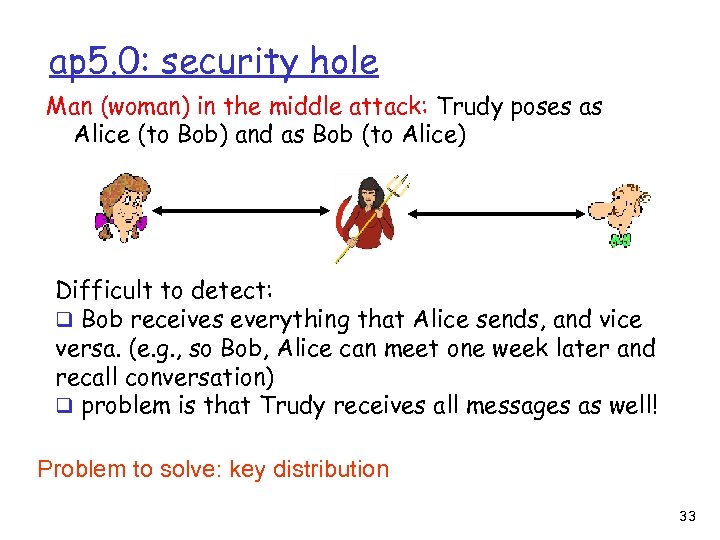 ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) Difficult to detect: q Bob receives everything that Alice sends, and vice versa. (e. g. , so Bob, Alice can meet one week later and recall conversation) q problem is that Trudy receives all messages as well! Problem to solve: key distribution 33
ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) Difficult to detect: q Bob receives everything that Alice sends, and vice versa. (e. g. , so Bob, Alice can meet one week later and recall conversation) q problem is that Trudy receives all messages as well! Problem to solve: key distribution 33
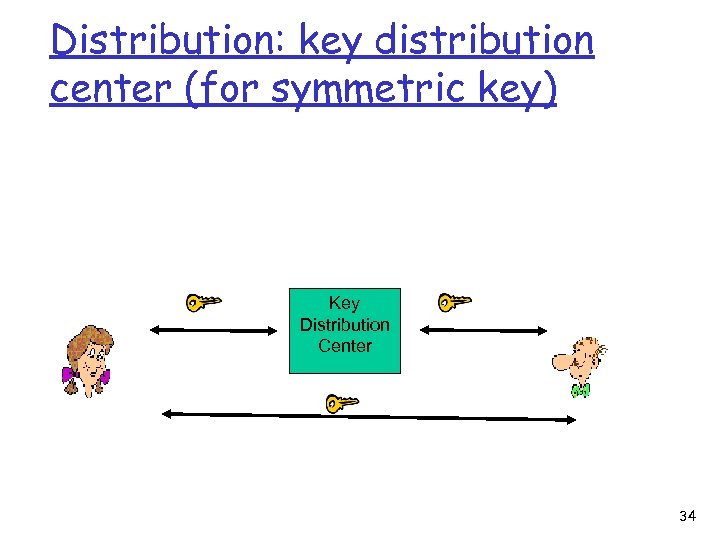 Distribution: key distribution center (for symmetric key) Key Distribution Center 34
Distribution: key distribution center (for symmetric key) Key Distribution Center 34
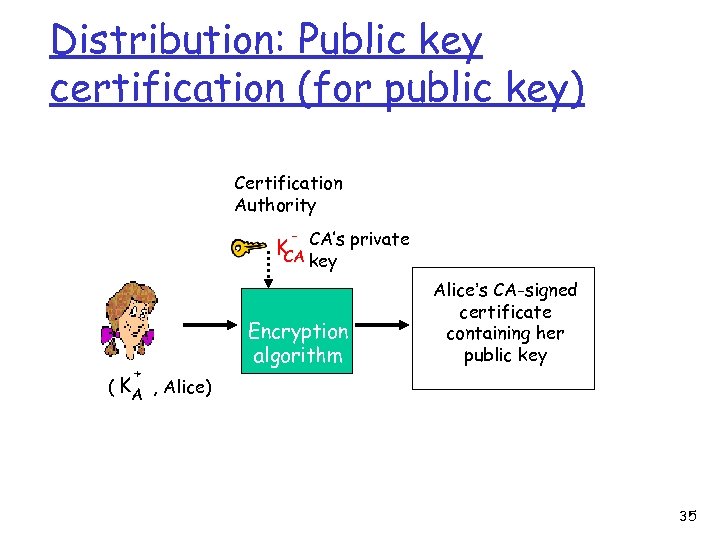 Distribution: Public key certification (for public key) Certification Authority - K CA’s private CA key + Encryption algorithm Alice’s CA-signed certificate containing her public key ( KA , Alice) 35
Distribution: Public key certification (for public key) Certification Authority - K CA’s private CA key + Encryption algorithm Alice’s CA-signed certificate containing her public key ( KA , Alice) 35
 What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 36
What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 36
 Digital Signatures Cryptographic technique analogous to handwritten signatures. q sender (Bob) digitally signs document, establishing he is document owner/creator. q verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document 37
Digital Signatures Cryptographic technique analogous to handwritten signatures. q sender (Bob) digitally signs document, establishing he is document owner/creator. q verifiable, nonforgeable: recipient (Alice) can prove to someone that Bob, and no one else (including Alice), must have signed document 37
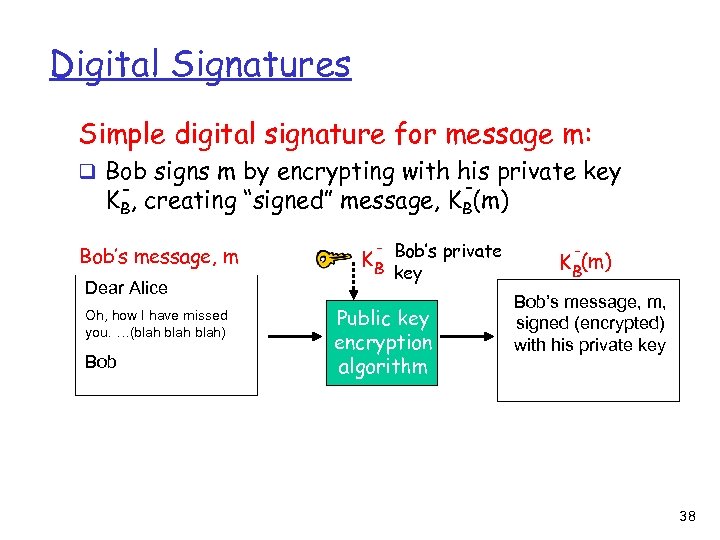 Digital Signatures Simple digital signature for message m: q Bob signs m by encrypting with his private key - KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. …(blah) Bob K B Bob’s private key Public key encryption algorithm K B(m) Bob’s message, m, signed (encrypted) with his private key 38
Digital Signatures Simple digital signature for message m: q Bob signs m by encrypting with his private key - KB, creating “signed” message, KB(m) Bob’s message, m Dear Alice Oh, how I have missed you. …(blah) Bob K B Bob’s private key Public key encryption algorithm K B(m) Bob’s message, m, signed (encrypted) with his private key 38
 Digital Signatures (more) + - q If KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. 39
Digital Signatures (more) + - q If KB(KB(m) ) = m, whoever signed m must have used Bob’s private key. Non-repudiation: ü Alice can take m, and signature KB(m) to court and prove that Bob signed m. 39
 Message Digests Computationally expensive to public-key-encrypt long messages Goal: fixed-length, easy- to-compute digital “fingerprint” v apply hash function H to m, get fixed size message digest, H(m). 40
Message Digests Computationally expensive to public-key-encrypt long messages Goal: fixed-length, easy- to-compute digital “fingerprint” v apply hash function H to m, get fixed size message digest, H(m). 40
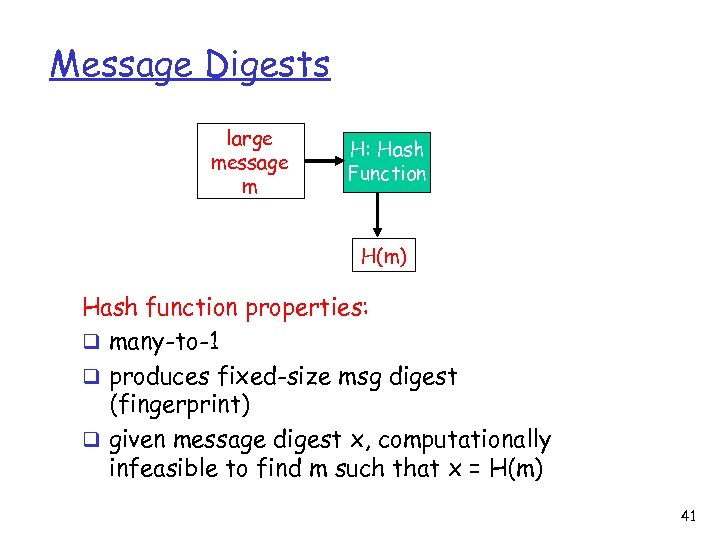 Message Digests large message m H: Hash Function H(m) Hash function properties: q many-to-1 q produces fixed-size msg digest (fingerprint) q given message digest x, computationally infeasible to find m such that x = H(m) 41
Message Digests large message m H: Hash Function H(m) Hash function properties: q many-to-1 q produces fixed-size msg digest (fingerprint) q given message digest x, computationally infeasible to find m such that x = H(m) 41
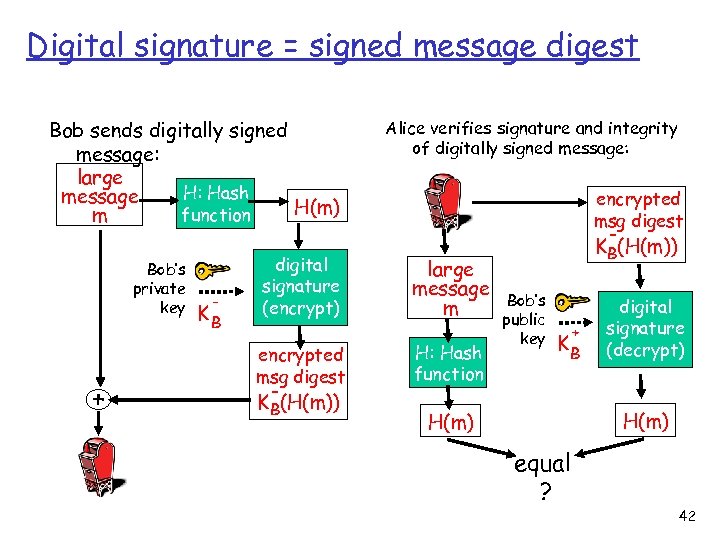 Digital signature = signed message digest Bob sends digitally signed message: large H: Hash message H(m) function m Bob’s private key + - KB digital signature (encrypt) encrypted msg digest KB(H(m)) Alice verifies signature and integrity of digitally signed message: encrypted msg digest large message m H: Hash function KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ? 42
Digital signature = signed message digest Bob sends digitally signed message: large H: Hash message H(m) function m Bob’s private key + - KB digital signature (encrypt) encrypted msg digest KB(H(m)) Alice verifies signature and integrity of digitally signed message: encrypted msg digest large message m H: Hash function KB(H(m)) Bob’s public key + KB digital signature (decrypt) H(m) equal ? 42
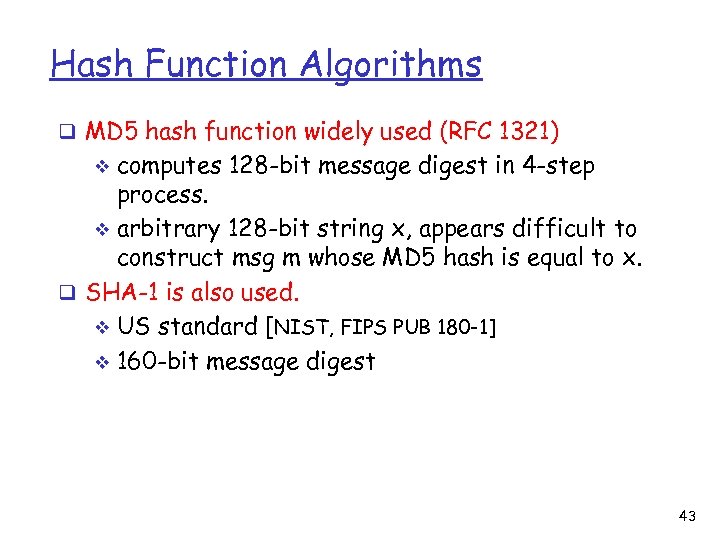 Hash Function Algorithms q MD 5 hash function widely used (RFC 1321) computes 128 -bit message digest in 4 -step process. v arbitrary 128 -bit string x, appears difficult to construct msg m whose MD 5 hash is equal to x. q SHA-1 is also used. v US standard [NIST, FIPS PUB 180 -1] v 160 -bit message digest v 43
Hash Function Algorithms q MD 5 hash function widely used (RFC 1321) computes 128 -bit message digest in 4 -step process. v arbitrary 128 -bit string x, appears difficult to construct msg m whose MD 5 hash is equal to x. q SHA-1 is also used. v US standard [NIST, FIPS PUB 180 -1] v 160 -bit message digest v 43
 What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 44
What are the Security metrics? q Confidentiality: can a 3 rd party see it? q Authentication: Am I talking to the person I intend to? q Non-repudiation: can you claim you didn’t send it even if you really did? q Integrity: was it altered before I got it? q Authorization: Are you allowed to perform the action (method)? 44
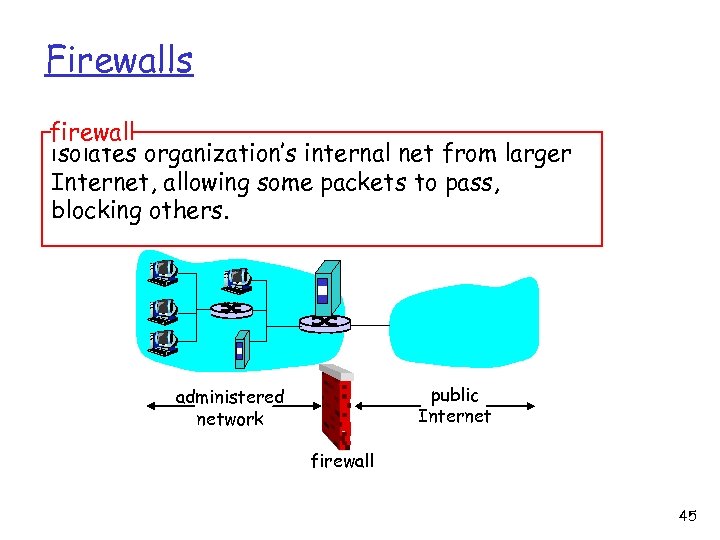 Firewalls firewall isolates organization’s internal net from larger Internet, allowing some packets to pass, blocking others. public Internet administered network firewall 45
Firewalls firewall isolates organization’s internal net from larger Internet, allowing some packets to pass, blocking others. public Internet administered network firewall 45
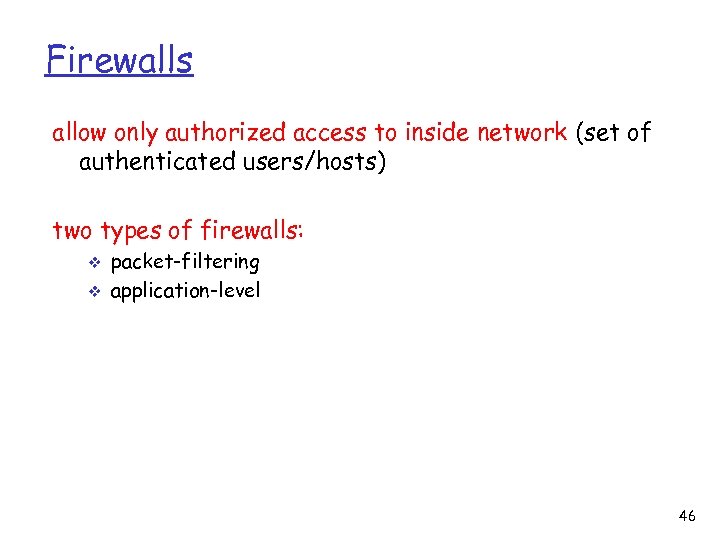 Firewalls allow only authorized access to inside network (set of authenticated users/hosts) two types of firewalls: v v packet-filtering application-level 46
Firewalls allow only authorized access to inside network (set of authenticated users/hosts) two types of firewalls: v v packet-filtering application-level 46
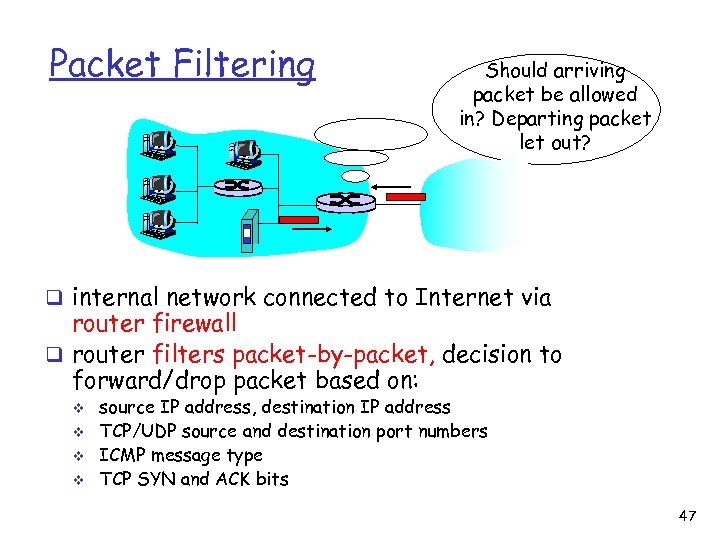 Packet Filtering Should arriving packet be allowed in? Departing packet let out? q internal network connected to Internet via router firewall q router filters packet-by-packet, decision to forward/drop packet based on: v v source IP address, destination IP address TCP/UDP source and destination port numbers ICMP message type TCP SYN and ACK bits 47
Packet Filtering Should arriving packet be allowed in? Departing packet let out? q internal network connected to Internet via router firewall q router filters packet-by-packet, decision to forward/drop packet based on: v v source IP address, destination IP address TCP/UDP source and destination port numbers ICMP message type TCP SYN and ACK bits 47
 Packet Filtering q Example 1: block incoming and outgoing datagrams with IP protocol field = 17 and with either source or dest port = 23. v All incoming and outgoing UDP flows and telnet connections are blocked. q Example 2: Block inbound TCP segments with ACK=0. v Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. 48
Packet Filtering q Example 1: block incoming and outgoing datagrams with IP protocol field = 17 and with either source or dest port = 23. v All incoming and outgoing UDP flows and telnet connections are blocked. q Example 2: Block inbound TCP segments with ACK=0. v Prevents external clients from making TCP connections with internal clients, but allows internal clients to connect to outside. 48
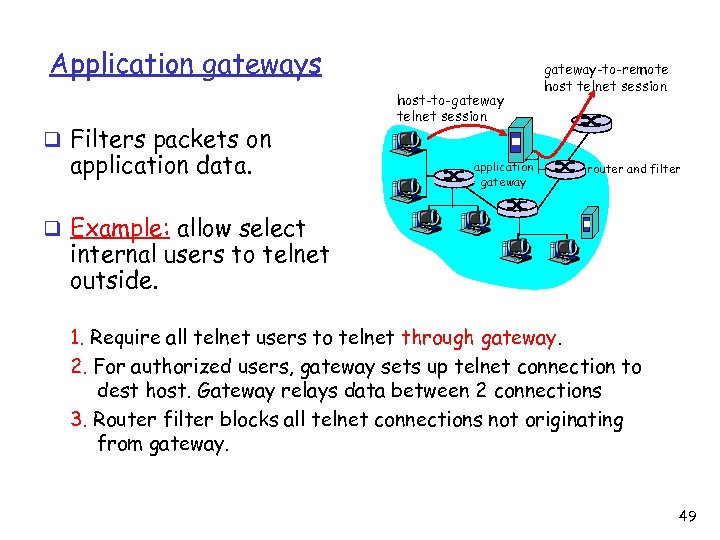 Application gateways q Filters packets on application data. host-to-gateway telnet session application gateway-to-remote host telnet session router and filter q Example: allow select internal users to telnet outside. 1. Require all telnet users to telnet through gateway. 2. For authorized users, gateway sets up telnet connection to dest host. Gateway relays data between 2 connections 3. Router filter blocks all telnet connections not originating from gateway. 49
Application gateways q Filters packets on application data. host-to-gateway telnet session application gateway-to-remote host telnet session router and filter q Example: allow select internal users to telnet outside. 1. Require all telnet users to telnet through gateway. 2. For authorized users, gateway sets up telnet connection to dest host. Gateway relays data between 2 connections 3. Router filter blocks all telnet connections not originating from gateway. 49
 Limitations of firewalls and gateways q IP spoofing: router can’t know if data “really” comes from claimed source q if multiple app’s. need special treatment, each has own app. gateway. q client software must know how to contact gateway. v q filters often use all or nothing policy for UDP. q tradeoff: degree of communication with outside world, level of security q many highly protected sites still suffer from attacks. e. g. , must set IP address of proxy in Web browser 50
Limitations of firewalls and gateways q IP spoofing: router can’t know if data “really” comes from claimed source q if multiple app’s. need special treatment, each has own app. gateway. q client software must know how to contact gateway. v q filters often use all or nothing policy for UDP. q tradeoff: degree of communication with outside world, level of security q many highly protected sites still suffer from attacks. e. g. , must set IP address of proxy in Web browser 50
 A little more on Internet Security Threat Examples
A little more on Internet Security Threat Examples
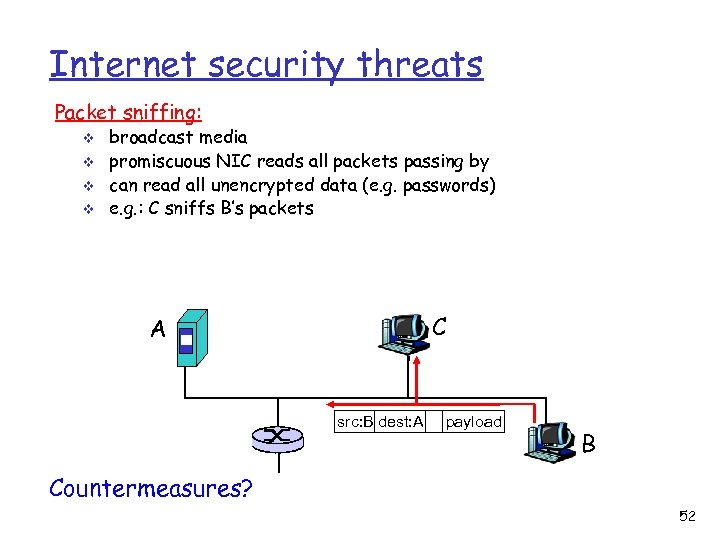 Internet security threats Packet sniffing: v v broadcast media promiscuous NIC reads all packets passing by can read all unencrypted data (e. g. passwords) e. g. : C sniffs B’s packets C A src: B dest: A payload B Countermeasures? 52
Internet security threats Packet sniffing: v v broadcast media promiscuous NIC reads all packets passing by can read all unencrypted data (e. g. passwords) e. g. : C sniffs B’s packets C A src: B dest: A payload B Countermeasures? 52
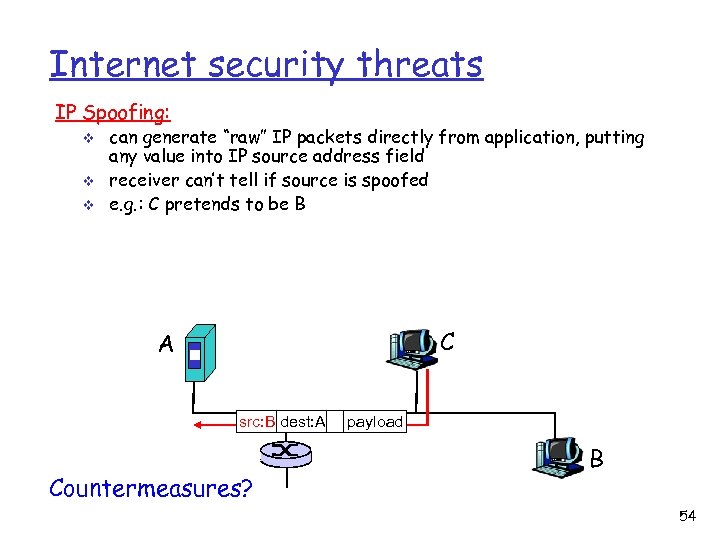 Internet security threats IP Spoofing: v v v can generate “raw” IP packets directly from application, putting any value into IP source address field receiver can’t tell if source is spoofed e. g. : C pretends to be B C A src: B dest: A Countermeasures? payload B 54
Internet security threats IP Spoofing: v v v can generate “raw” IP packets directly from application, putting any value into IP source address field receiver can’t tell if source is spoofed e. g. : C pretends to be B C A src: B dest: A Countermeasures? payload B 54
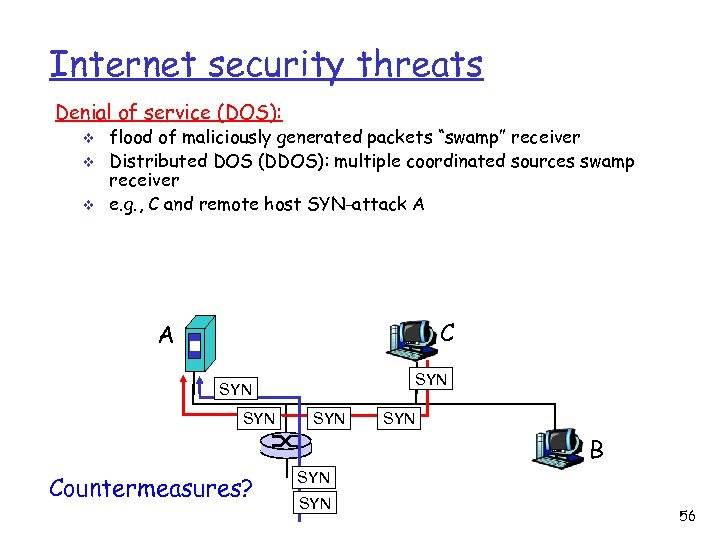 Internet security threats Denial of service (DOS): v v v flood of maliciously generated packets “swamp” receiver Distributed DOS (DDOS): multiple coordinated sources swamp receiver e. g. , C and remote host SYN-attack A C A SYN SYN SYN B Countermeasures? SYN 56
Internet security threats Denial of service (DOS): v v v flood of maliciously generated packets “swamp” receiver Distributed DOS (DDOS): multiple coordinated sources swamp receiver e. g. , C and remote host SYN-attack A C A SYN SYN SYN B Countermeasures? SYN 56
 SSL and TLS • Secure Sockets Layer (SSL) is a different approach - a new layer is added that provides a secure channel over a TCP only link. • TLS is Transport Layer Security (IETF standard based on SSL). 58
SSL and TLS • Secure Sockets Layer (SSL) is a different approach - a new layer is added that provides a secure channel over a TCP only link. • TLS is Transport Layer Security (IETF standard based on SSL). 58
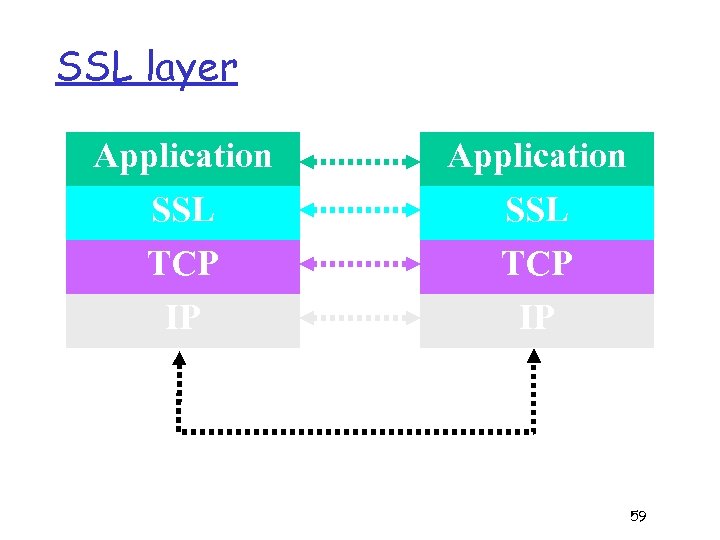 SSL layer Application SSL TCP IP 59
SSL layer Application SSL TCP IP 59
 Advantages of SSL/TLS • Independent of application layer • Includes support for negotiated encryption techniques. v • easy to add new techniques. Possible to switch encryption algorithms in the middle of a session. 60
Advantages of SSL/TLS • Independent of application layer • Includes support for negotiated encryption techniques. v • easy to add new techniques. Possible to switch encryption algorithms in the middle of a session. 60
 HTTPS Usage • HTTPS is HTTP running over SSL. used for most secure web transactions. v HTTPS server usually runs on port 443. v Include notion of verification of server via a certificate. v Central trusted source of certificates. v 61
HTTPS Usage • HTTPS is HTTP running over SSL. used for most secure web transactions. v HTTPS server usually runs on port 443. v Include notion of verification of server via a certificate. v Central trusted source of certificates. v 61


