3ee17b89cf94518f85d9dcf8da57d6bc.ppt
- Количество слайдов: 21

Network Security Slides taken from: Computer Networking by Kurose and Ross

Cryptography ¡ ¡ ¡ Greek word meaning “secret writing” Historically the study has been utilized by: (1) the military, (2) diplomatic corps, (3) diarists, and (4) lovers Ciphers: character-for-character transformation Code: replaces one word with another Vocabulary: l l l plaintext key ciphertext
Network Security Friends and enemies: Alice, Bob, Trudy
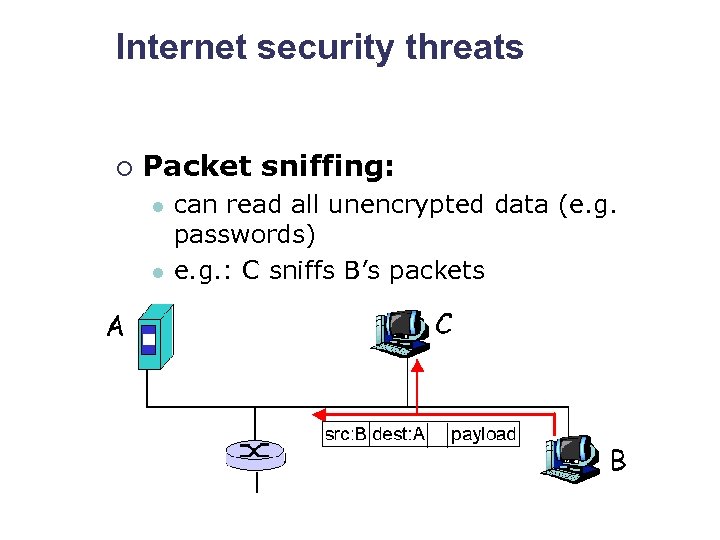
Internet security threats ¡ Packet sniffing: l l can read all unencrypted data (e. g. passwords) e. g. : C sniffs B’s packets
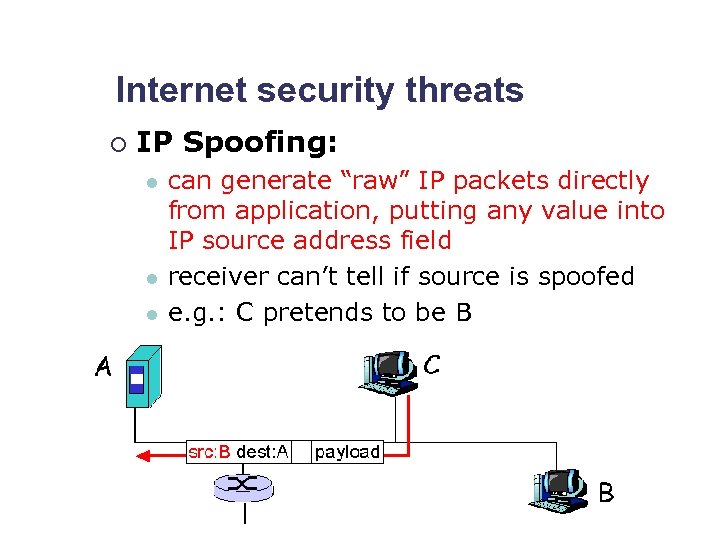
Internet security threats ¡ IP Spoofing: l l l can generate “raw” IP packets directly from application, putting any value into IP source address field receiver can’t tell if source is spoofed e. g. : C pretends to be B
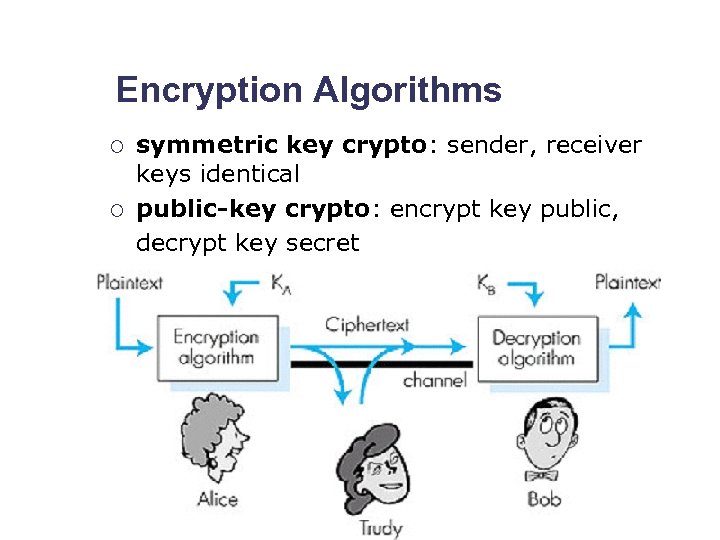
Encryption Algorithms ¡ ¡ symmetric key crypto: sender, receiver keys identical public-key crypto: encrypt key public, decrypt key secret

Symmetric key cryptography
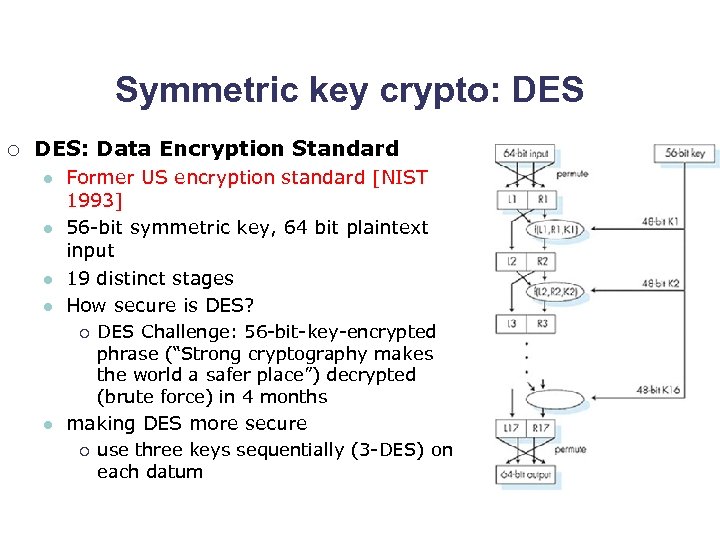
Symmetric key crypto: DES ¡ DES: Data Encryption Standard l l Former US encryption standard [NIST 1993] 56 -bit symmetric key, 64 bit plaintext input 19 distinct stages How secure is DES? ¡ l DES Challenge: 56 -bit-key-encrypted phrase (“Strong cryptography makes the world a safer place”) decrypted (brute force) in 4 months making DES more secure ¡ use three keys sequentially (3 -DES) on each datum
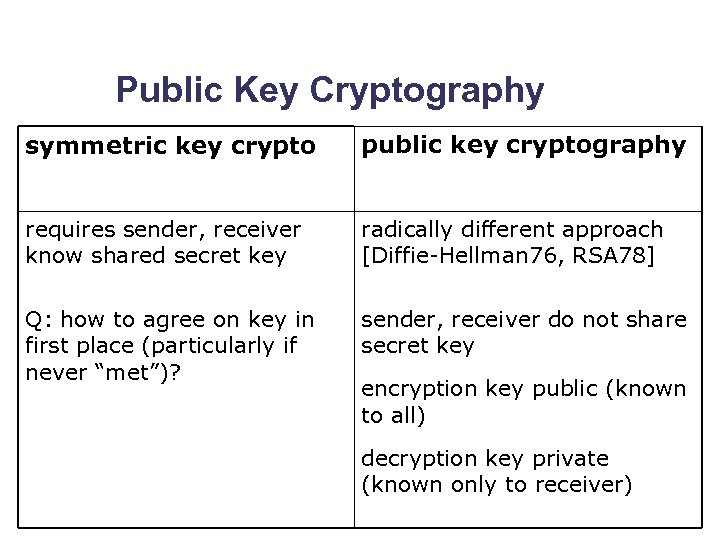
Public Key Cryptography symmetric key crypto public key cryptography requires sender, receiver know shared secret key radically different approach [Diffie-Hellman 76, RSA 78] Q: how to agree on key in first place (particularly if never “met”)? sender, receiver do not share secret key encryption key public (known to all) decryption key private (known only to receiver)
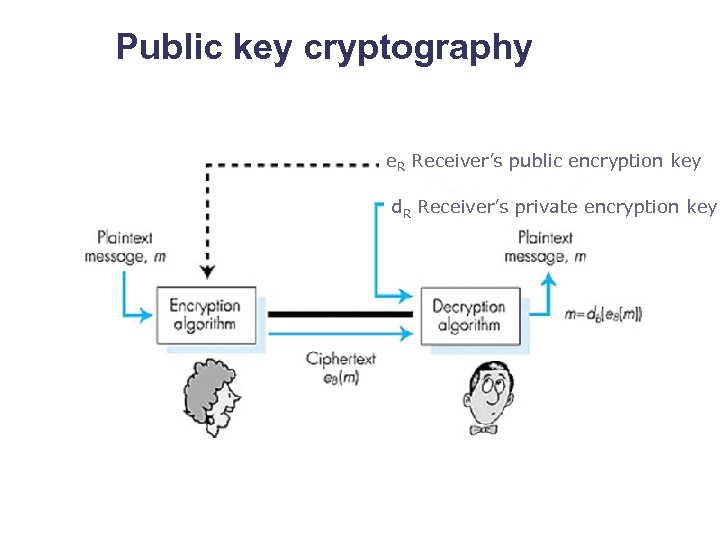
Public key cryptography e. R Receiver’s public encryption key d. R Receiver’s private encryption key
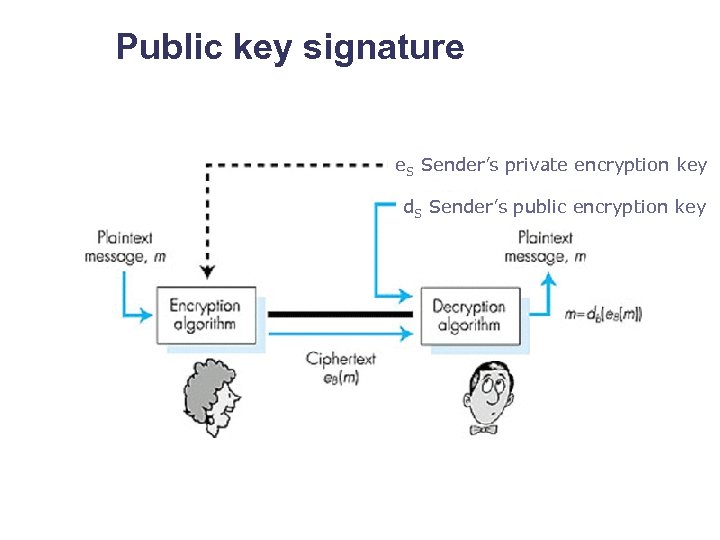
Public key signature e. S Sender’s private encryption key d. S Sender’s public encryption key
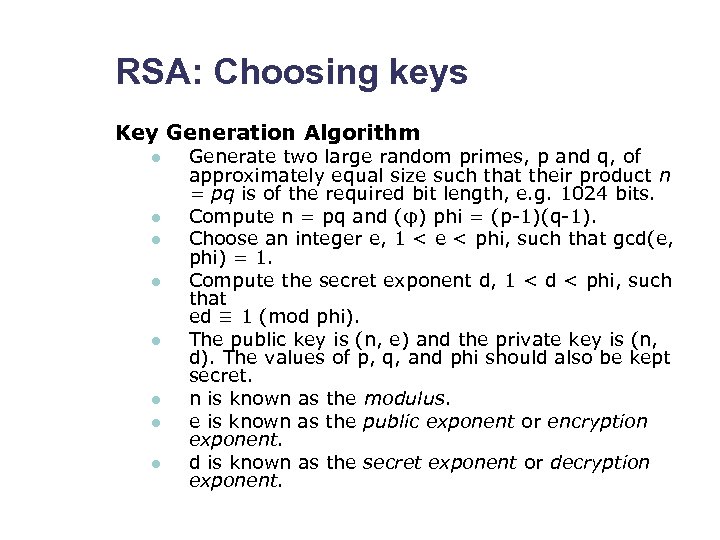
RSA: Choosing keys Key Generation Algorithm l l l l Generate two large random primes, p and q, of approximately equal size such that their product n = pq is of the required bit length, e. g. 1024 bits. Compute n = pq and (φ) phi = (p-1)(q-1). Choose an integer e, 1 < e < phi, such that gcd(e, phi) = 1. Compute the secret exponent d, 1 < d < phi, such that ed ≡ 1 (mod phi). The public key is (n, e) and the private key is (n, d). The values of p, q, and phi should also be kept secret. n is known as the modulus. e is known as the public exponent or encryption exponent. d is known as the secret exponent or decryption exponent.
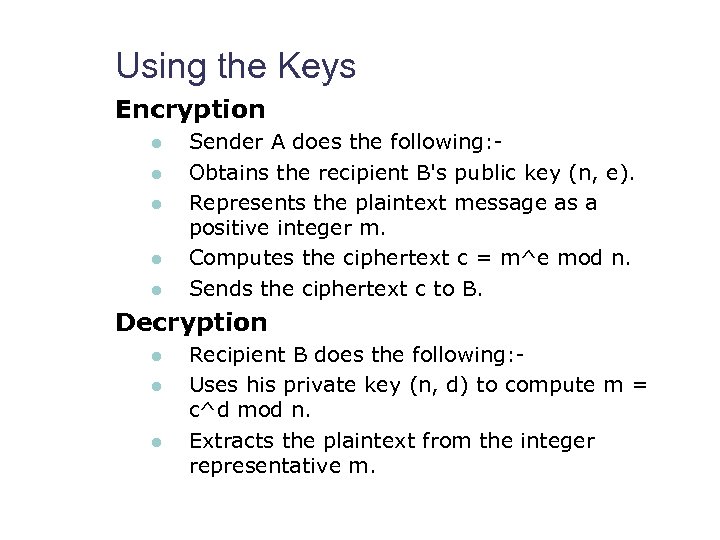
Using the Keys Encryption l l l Sender A does the following: Obtains the recipient B's public key (n, e). Represents the plaintext message as a positive integer m. Computes the ciphertext c = m^e mod n. Sends the ciphertext c to B. Decryption l l l Recipient B does the following: Uses his private key (n, d) to compute m = c^d mod n. Extracts the plaintext from the integer representative m.

Trusted Public Keys: Digital Certificates ¡ ¡ ¡ In a public key environment, it is vital that you are assured that the public key to which you are encrypting data is the public key of the intended recipient. Digital certificates are used to thwart attempts to substitute one person's key for another. A digital certificate consists of three things: l l l A public key. Certificate information. ("Identity" information about the user, such as name, user ID, and so on. ) One or more digital signatures.

Putting It all Together ¡ ¡ ¡ Systems can combine the best features of both symmetric and public key cryptography: hybrid cryptosystems. These systems create a session key, which is a one-time-only secret key. This key is a random number generated from the random movements of your mouse and the keystrokes you type. This session key works with a very secure, fast conventional encryption algorithm to encrypt the plaintext; the result is ciphertext. Once the data is encrypted, the session key is then encrypted to the recipient's public key. This public key-encrypted session key is transmitted along with the ciphertext to the recipient.

Applications ¡ Secure Shell (SSH) part of the Linux distribution l ¡ Pu. TTY for Windows machines l ¡ Seems to include secure FTP Includes secure FTP PGP for secure email l Internet e-mail encryption scheme, a de-facto standard. Uses symmetric key cryptography, and public key cryptography Inventor, Phil Zimmerman, was target of 3 -year federal investigation.
In-class assignment Use telnet to connect to your CSCI account using SSH. Start SSH: Start -> All Programs-> SSH Secure Shell -> Secure Shell Client
In-class assignment ¡ ¡ Login to your csci account by selecting the Quick Connect option on the tool bar Enter the machine name: busbee. cs. unca. edu Enter your user name: the first 6 letters of your last name followed by your first initial and middle initial Answer YES in the next window and then enter your password: csci followed by last 4 digits of student id
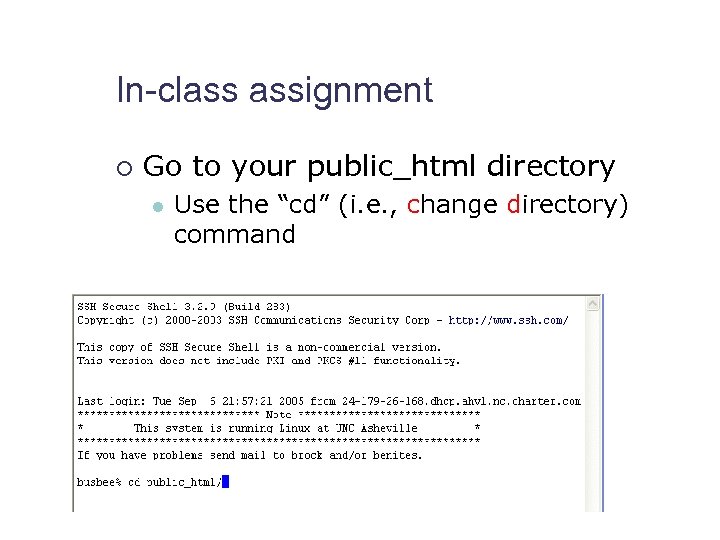
In-class assignment ¡ Go to your public_html directory l Use the “cd” (i. e. , change directory) command
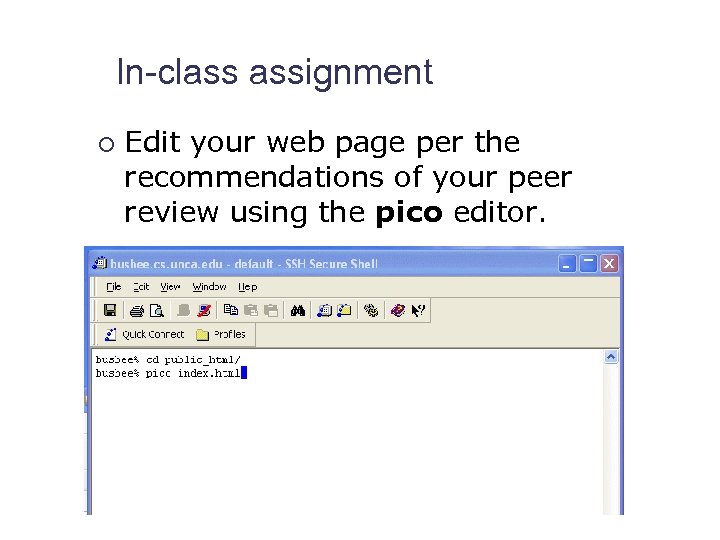
In-class assignment ¡ Edit your web page per the recommendations of your peer review using the pico editor.
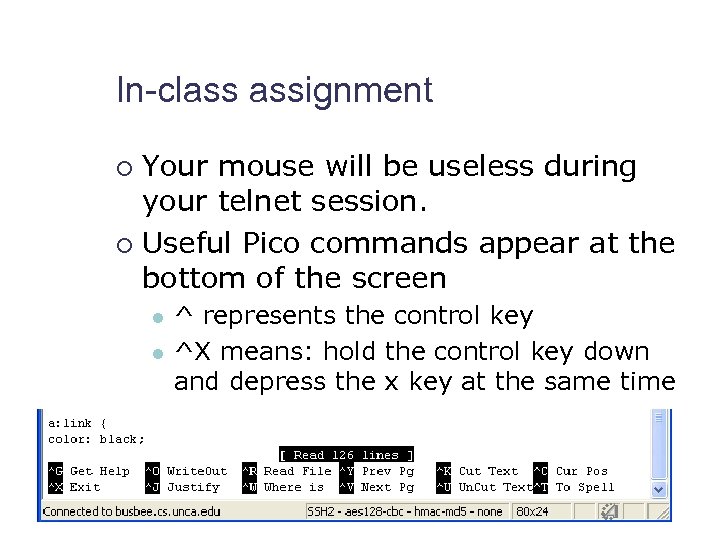
In-class assignment Your mouse will be useless during your telnet session. ¡ Useful Pico commands appear at the bottom of the screen ¡ l l ^ represents the control key ^X means: hold the control key down and depress the x key at the same time
3ee17b89cf94518f85d9dcf8da57d6bc.ppt