Network Security.pptx
- Количество слайдов: 47

NETWORK SECURITY DONE BY: RAUAN RAKHMET CHECKED BY: ANEESH PRADEEP Almaty, 2014

OUTLINE WHAT IS NETWORK SECURITY? TYPES OF ATTACK: PASSIVE ACTIVE ENCRYPTION TECHNIQUES AND ITS FRIENDS SUMMARY
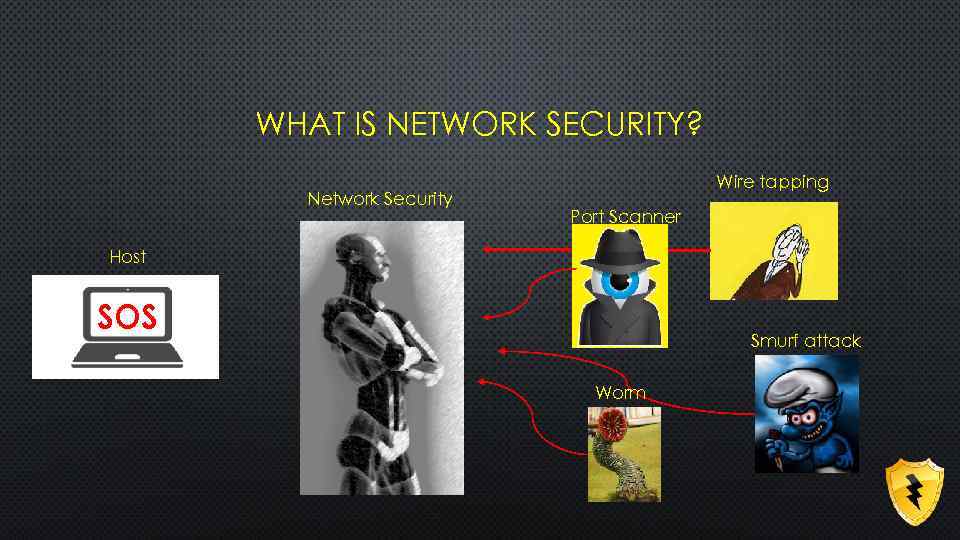
WHAT IS NETWORK SECURITY? Network Security Wire tapping Port Scanner Host SOS Smurf attack Worm
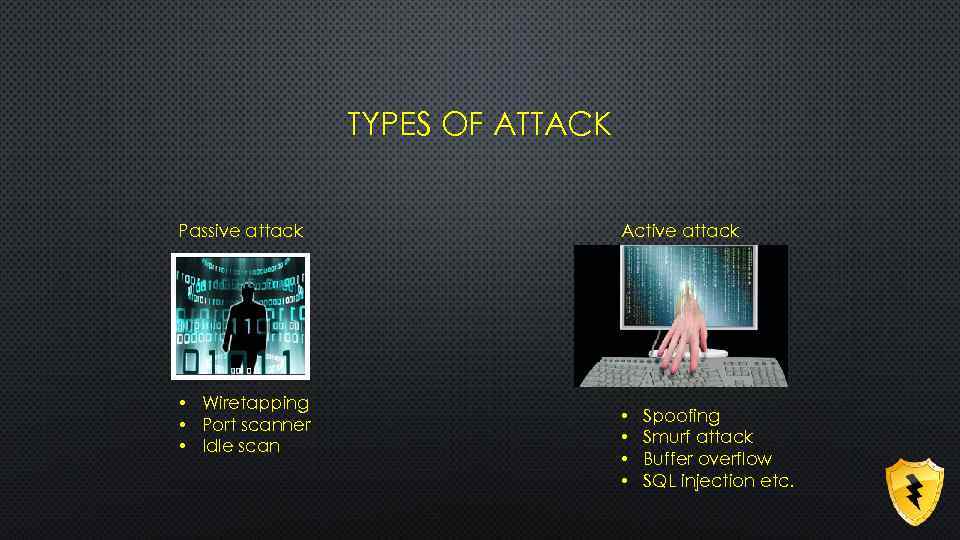
TYPES OF ATTACK Passive attack • Wiretapping • Port scanner • Idle scan Active attack • • Spoofing Smurf attack Buffer overflow SQL injection etc.

PASSIVE ATTACKS WIRETAPPING PORT SCANNER IDLE SCAN
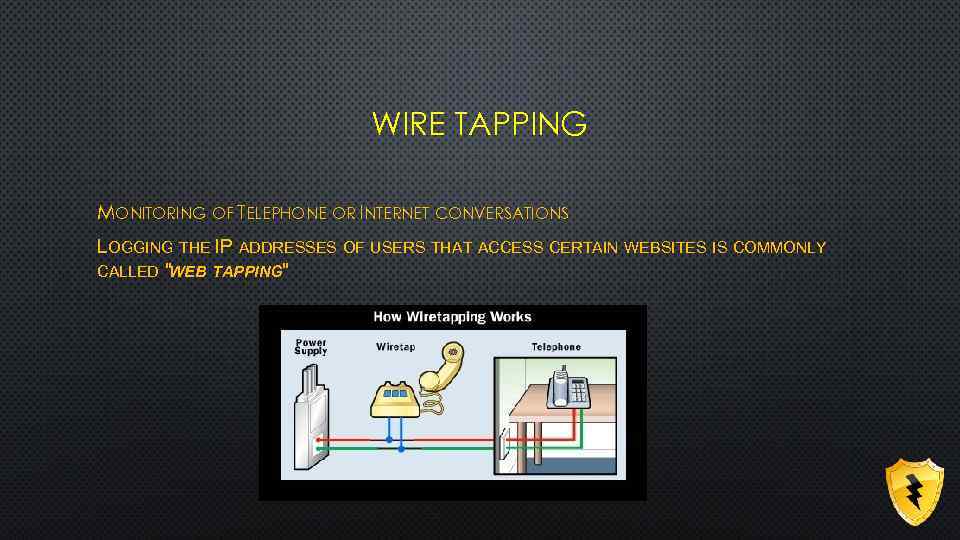
WIRE TAPPING MONITORING OF TELEPHONE OR INTERNET CONVERSATIONS LOGGING THE IP ADDRESSES OF USERS THAT ACCESS CERTAIN WEBSITES IS COMMONLY CALLED "WEB TAPPING"
WIRE TAPPING HOW BECOME PROTECTED? Using VPN(Virtual Private Network) HOW IT WORKS?
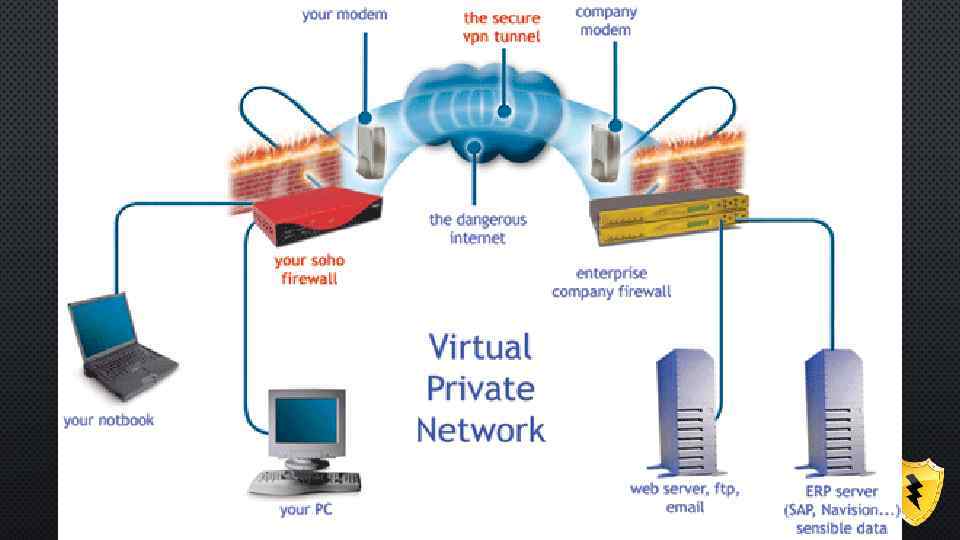

HOW VPN WORKS ? • USE OF VIRTUAL POINT-TO-POINT CONNECTION • USE OF ENCRYPTION TECHNIQUES • USE OF TUNNELING PROTOCOLS

VPN SECURITY MODEL • CONFIDENTIALITY • AUTHENTICATION • INTEGRITY Internet Protocol Security (IPsec) Transport Layer Security (SSL/TLS)
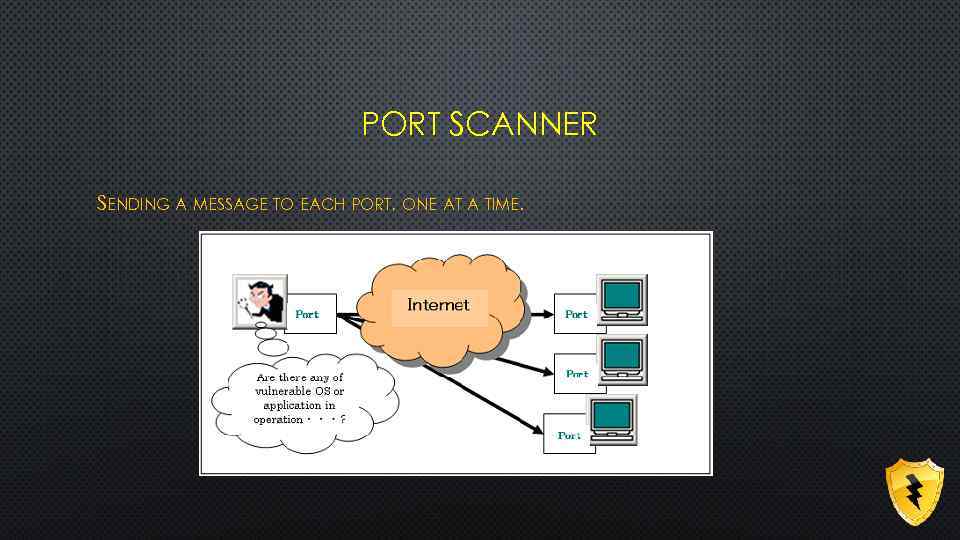
PORT SCANNER SENDING A MESSAGE TO EACH PORT, ONE AT A TIME.

• MISCONFIGURE SOCKS • BOUNCE SCANS • UDP SCANNING • FIREWALL AND EDUCATION
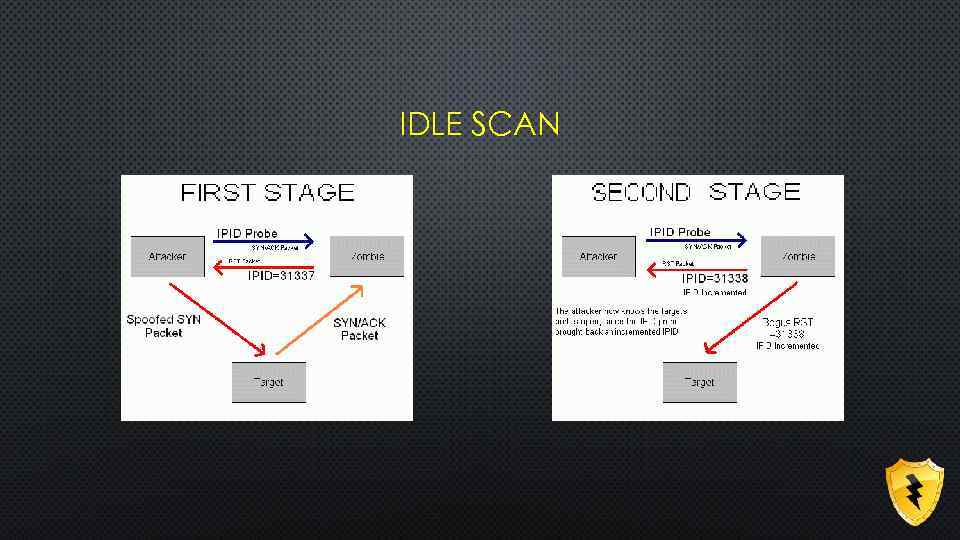
IDLE SCAN

SOLUTION

ACTIVE ATTACKS DENIAL-OF-SERVICE ATTACK SMURF ATTACK SPOOFING MAN IN THE MIDDLE SQL INJECTION

DOS ATTACKS • Aimed to deny normal service provided by target computer • Communication-stopping attacks • Resource-exhausting attacks
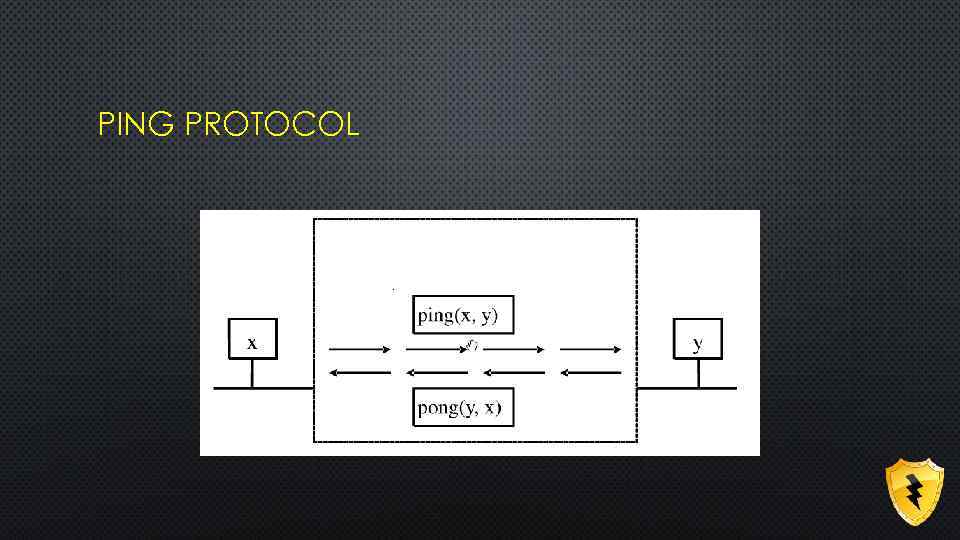
PING PROTOCOL
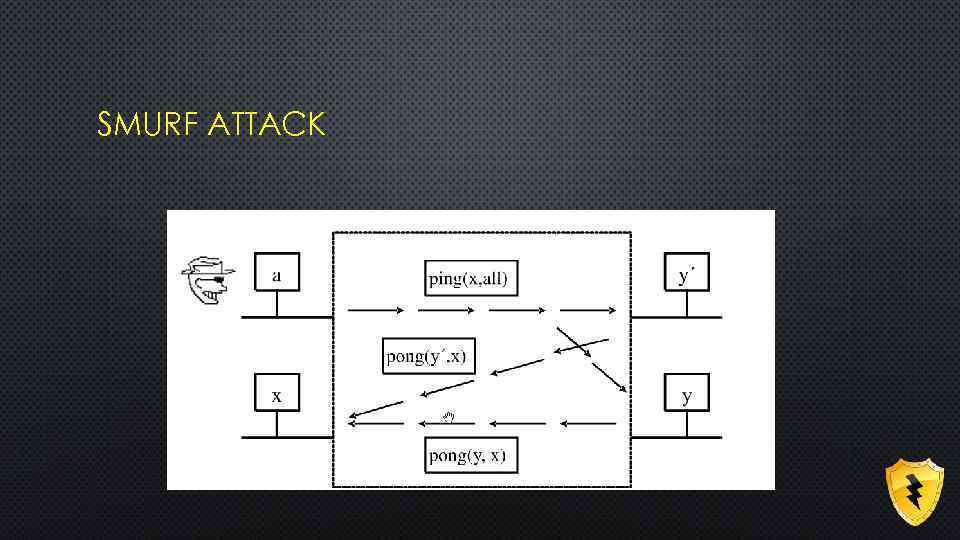
SMURF ATTACK
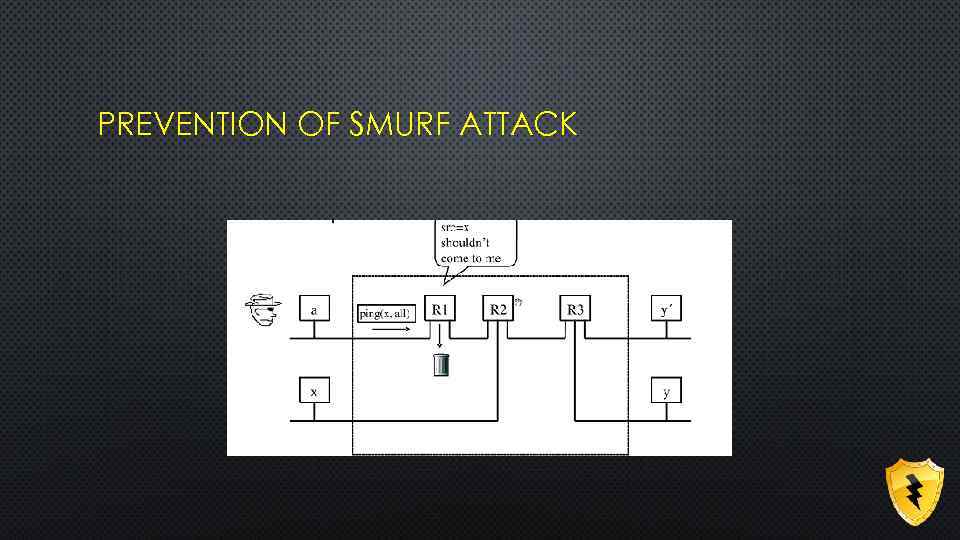
PREVENTION OF SMURF ATTACK
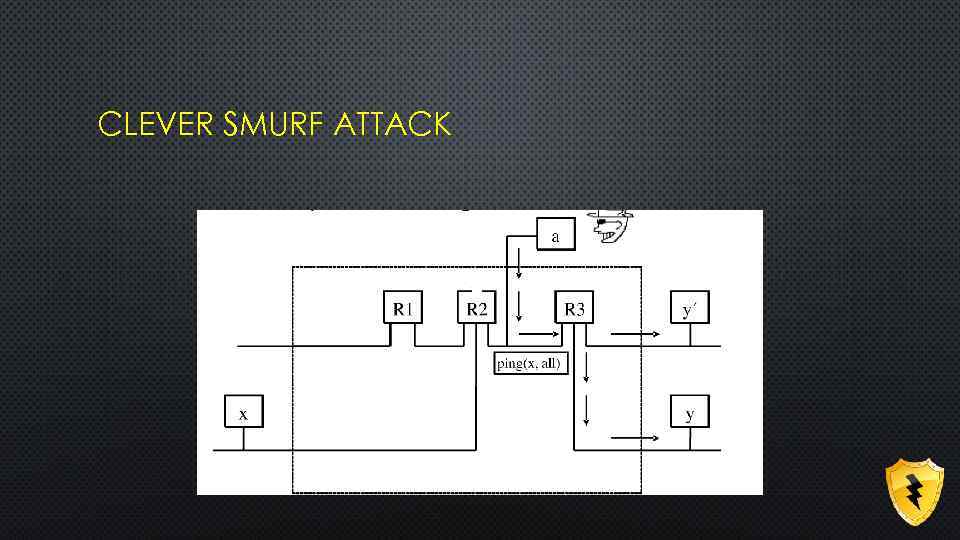
CLEVER SMURF ATTACK

PREVENTION TO CLEVER SMURF ATTACK USAGE OF HOP INTEGRITY PROTOCOL: • DETECTION OF MESSAGE MODIFICATION • DETECTION OF MESSAGE REPLAY
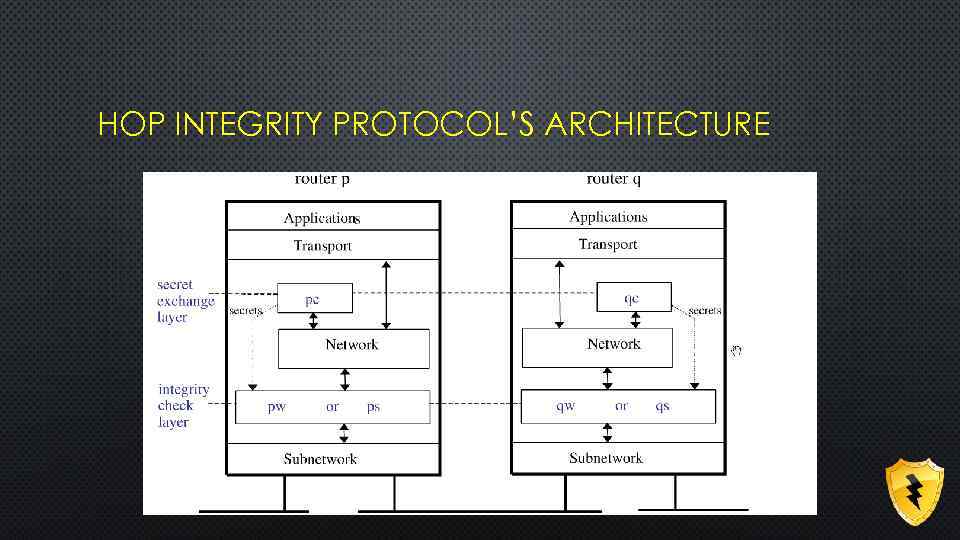
HOP INTEGRITY PROTOCOL’S ARCHITECTURE

COMPONENT OF HOP INTEGRITY PROTOCOLS • SECRET EXCHANGE PROTOCOL • WEAK INTEGRITY PROTOCOL • STRONG INTEGRITY PROTOCOL
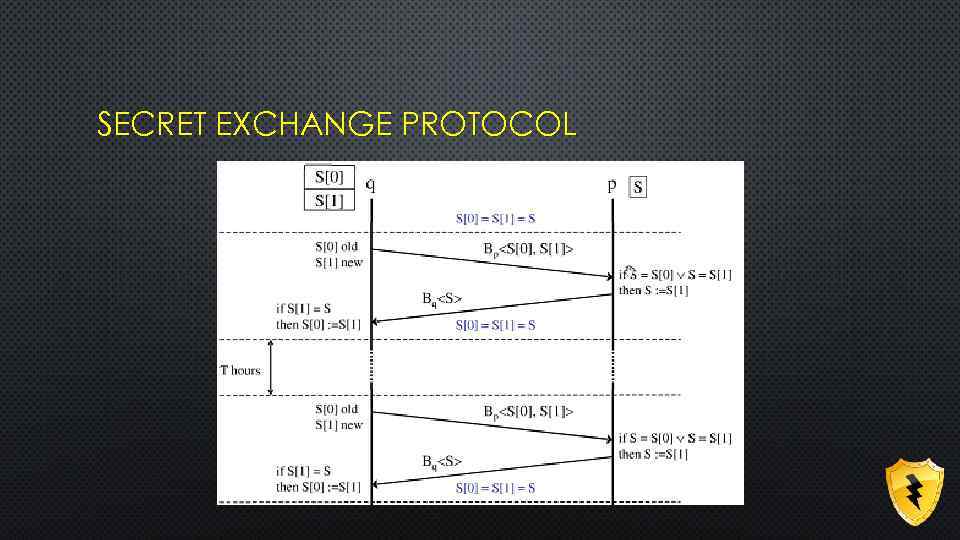
SECRET EXCHANGE PROTOCOL

SPOOFING ATTACK A SPOOFING ATTACK - PROGRAM SUCCESSFULLY MASQUERADES AS ANOTHER BY FALSIFYING DATA AND THEREBY GAINING AN ILLEGITIMATE ADVANTAGE.

TYPES OF SPOOFING ATTACK • WEB SPOOFING • DNS SPOOFING • TCP SPOOFING • IP SPOOFING
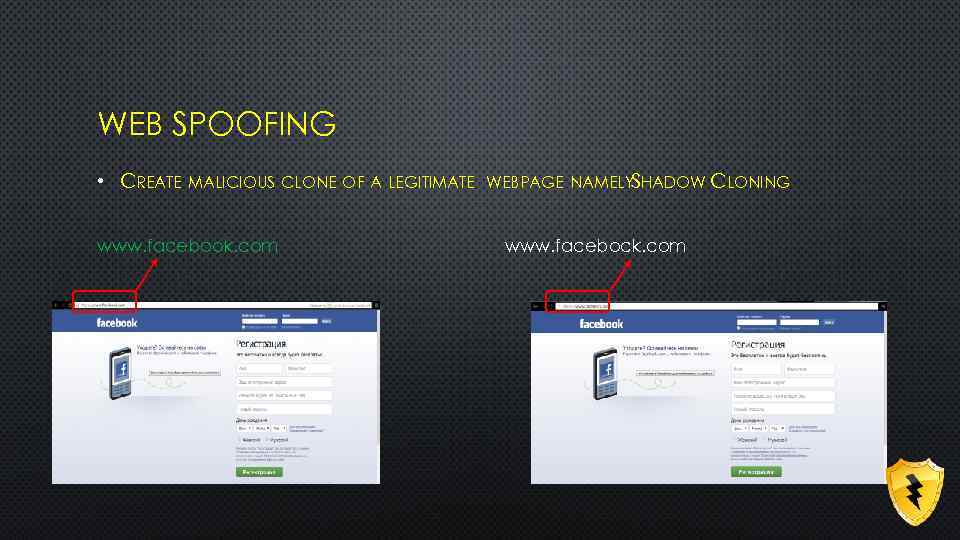
WEB SPOOFING • CREATE MALICIOUS CLONE OF A LEGITIMATE www. facebook. com WEBPAGE NAMELY HADOW CLONING S www. facebock. com

THE HOOK • SPOOFED EMAILS LURE VISITORS THROUGH FALSE CLAIMS • URL PARODY COUNTER MEASURES • USE ANTI-POPUP SOFTWARE • CHECK DIGITAL CERTIFICATES( SSL CONNECTION)

DNS SPOOFING • DNS PROTOCOL USES UDP FOR REQUEST AND REPLIES. • UDP DOES NOT HAVE ANY PROTECTION TO GUARD AGAINST IP SPOOFING.

TCP SPOOFING

HOW TO PREVENT • AVOID USING THE SOURCE ADDRESS • USE ENCRYPTED AUTHENTICATION TO SECURE THE NETWORK
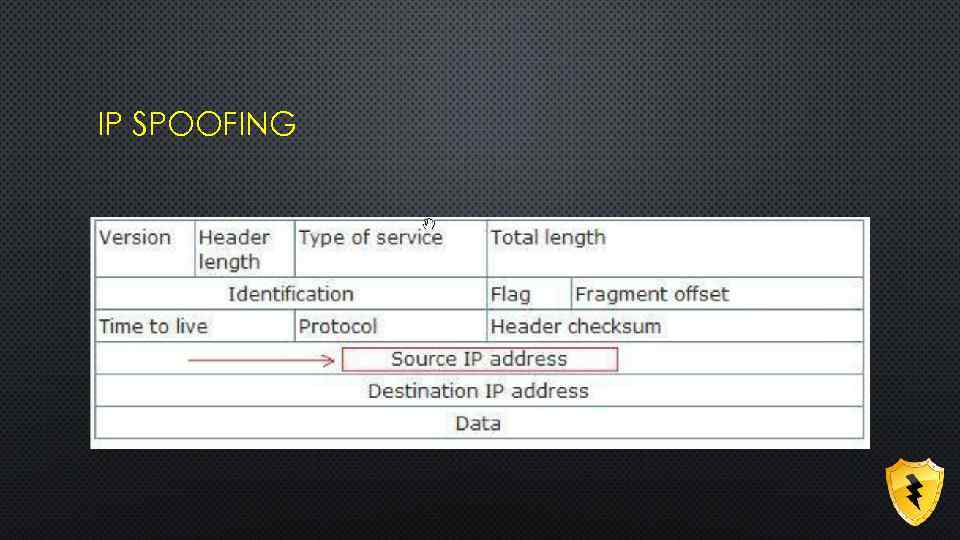
IP SPOOFING

HOW TO PREVENT • PACKET FILTERING: • INGRESS FILTERING • EGRESS FILTERING • ISP FILTERING
MAN IN THE MIDDLE
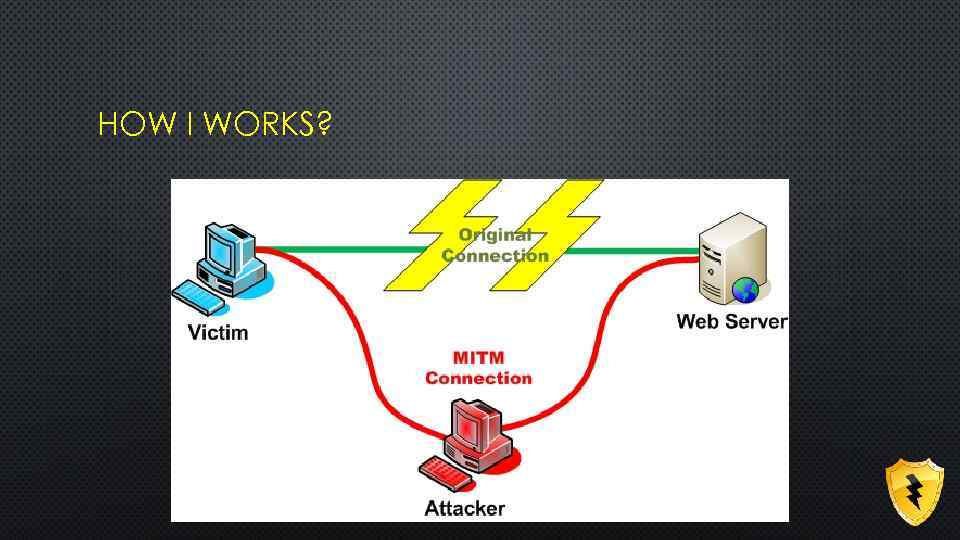
HOW I WORKS?

SOLUTION?

• STRONG ENCRYPTION • PUBLIC KEY INFRASTRUCTURES • STRONGER MUTUAL AUTHENTICATION • PRIVATE SECRET TUNNELS
SQL INJECTION
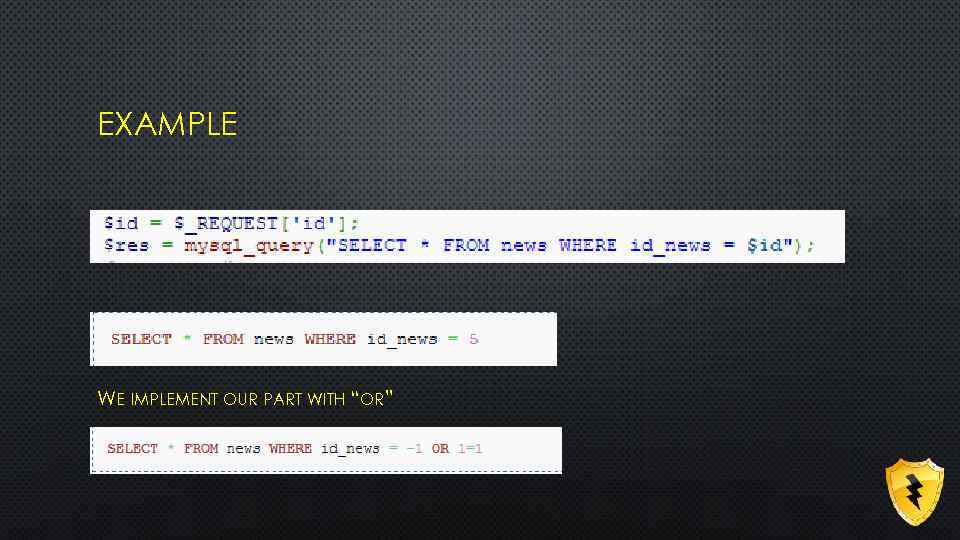
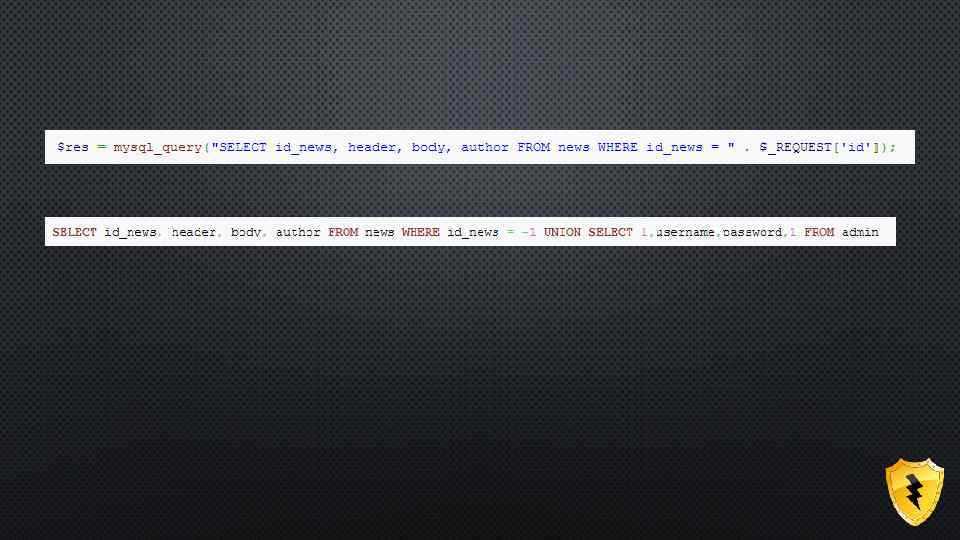
EXAMPLE WE IMPLEMENT OUR PART WITH “OR”
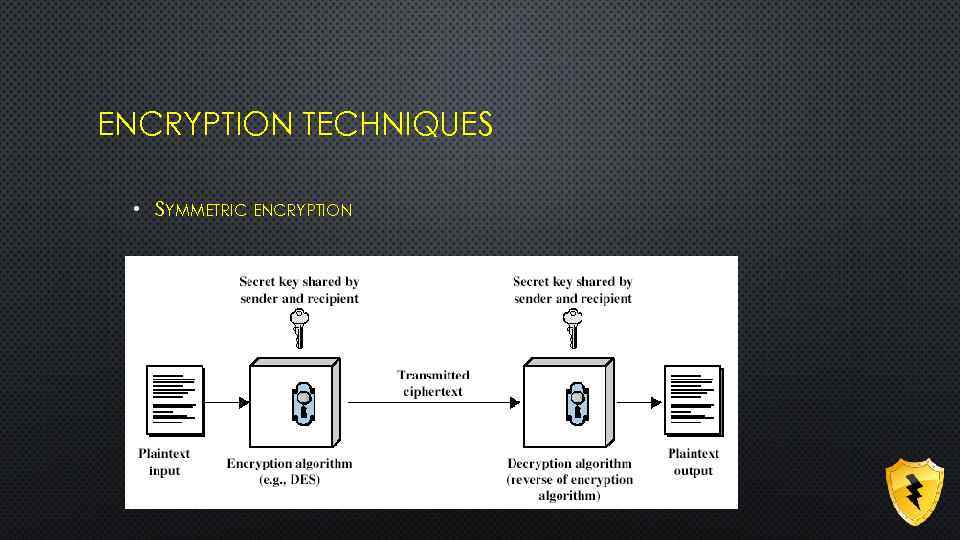
ENCRYPTION TECHNIQUES • SYMMETRIC ENCRYPTION
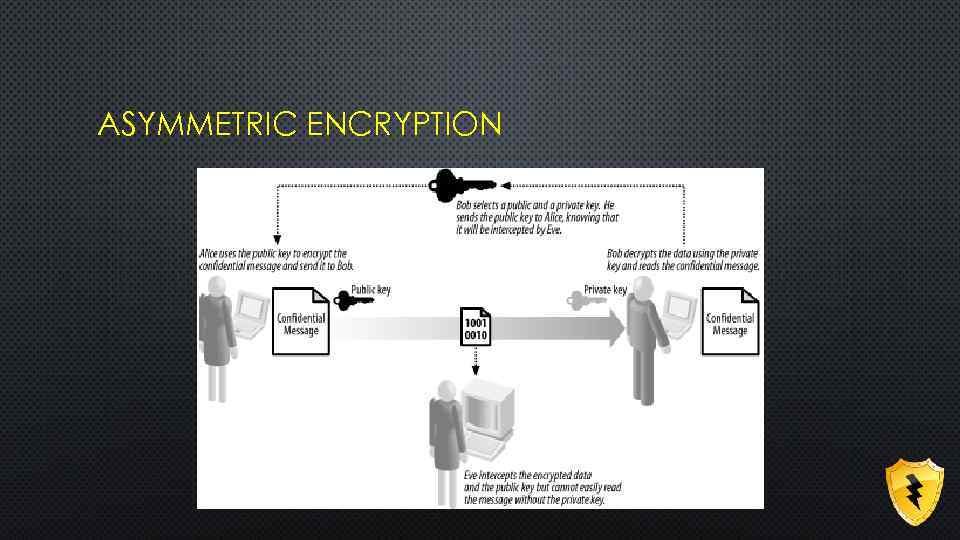
ASYMMETRIC ENCRYPTION

AES CIPHER • COMPLICATED VERSION OF CEASER CIPHER • DESIGNED BY RIJMEN-DAEMEN IN BELGIUM HAS 128/192/256 BIT KEYS, 128 BIT DATA • RESISTANT AGAINST KNOWN ATTACKS SPEED AND CODE COMPACTNESS ON MANY CPUS DESIGN SIMPLICITY
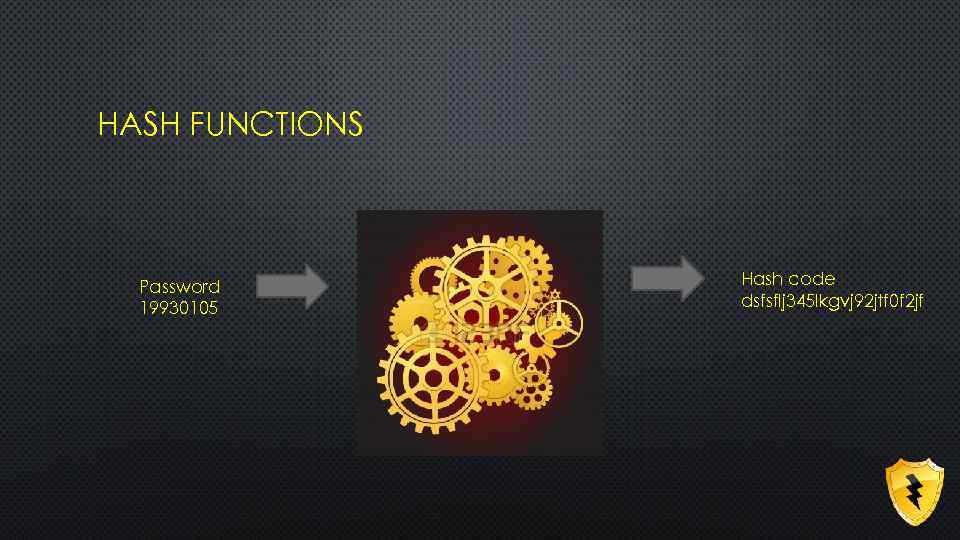
HASH FUNCTIONS Password 19930105 Hash code dsfsflj 345 lkgvj 92 jtf 0 f 2 jf
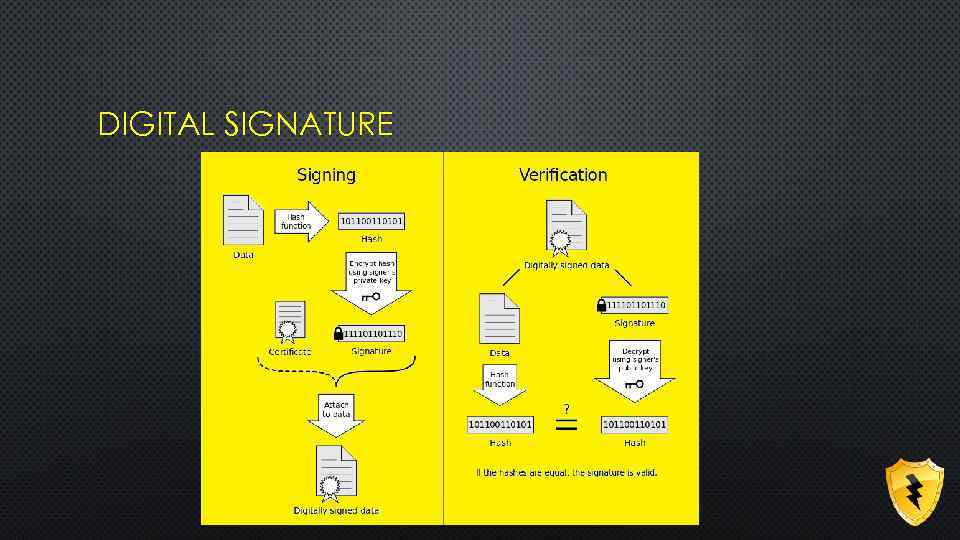
DIGITAL SIGNATURE
SUMMARY • WHAT WE KNOW ABOUT ATTACKS? • WHAT WE KNOW ABOUT DEFENSE?
THANK YOU FOR ATTENTION
Network Security.pptx