f25eb3e4f4218f3c4668d5075bbc48df.ppt
- Количество слайдов: 43
 Network Security Design Fundamentals ET-IDA-082 Lecture-17 Network Security Primitives SSL 31. 05. 2011, v 07 31. 05. 2011, Prof. W. Adi Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 1
Network Security Design Fundamentals ET-IDA-082 Lecture-17 Network Security Primitives SSL 31. 05. 2011, v 07 31. 05. 2011, Prof. W. Adi Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 1
 Outlines • Introduction network security primitives and terminology • • • SSL (Secure Socket Layer) IPSEC Kerberos Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 2
Outlines • Introduction network security primitives and terminology • • • SSL (Secure Socket Layer) IPSEC Kerberos Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 2
 Recommended Textbooks: 1. Computer Networking: A Top Down Approach Featuring the Internet, 4 th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007. 2. Network Security Essentials: Applications and Standards, 3 rd Edition William Stallings, Prentice Hall, © 2007, ISBN: 0 -13 -238033 -1 Copyright notice: Part of the slides (those without foot note) are adapted from the slides of the following text book adopted for this course: Computer Networking: A Top Down Approach Featuring the Internet, 4 th edition. Jim Kurose, Keith Ross, Addison-Wesley, July 2007. Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 3
Recommended Textbooks: 1. Computer Networking: A Top Down Approach Featuring the Internet, 4 th edition. Jim Kurose, Keith Ross Addison-Wesley, July 2007. 2. Network Security Essentials: Applications and Standards, 3 rd Edition William Stallings, Prentice Hall, © 2007, ISBN: 0 -13 -238033 -1 Copyright notice: Part of the slides (those without foot note) are adapted from the slides of the following text book adopted for this course: Computer Networking: A Top Down Approach Featuring the Internet, 4 th edition. Jim Kurose, Keith Ross, Addison-Wesley, July 2007. Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 3
![Chapter 8: Network Security [1] Chapter goals: • understand principles of network security: – Chapter 8: Network Security [1] Chapter goals: • understand principles of network security: –](https://present5.com/presentation/f25eb3e4f4218f3c4668d5075bbc48df/image-4.jpg) Chapter 8: Network Security [1] Chapter goals: • understand principles of network security: – cryptography and its many uses beyond “confidentiality” – authentication – key distribution – message integrity Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 4
Chapter 8: Network Security [1] Chapter goals: • understand principles of network security: – cryptography and its many uses beyond “confidentiality” – authentication – key distribution – message integrity Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 4
 What is network security? Confidentiality: only sender, intended receiver should “understand” message contents – sender encrypts message – receiver decrypts message Authentication: sender, receiver want to confirm identity of each other Message Integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection Access and Availability: services must be accessible and available to users Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 5
What is network security? Confidentiality: only sender, intended receiver should “understand” message contents – sender encrypts message – receiver decrypts message Authentication: sender, receiver want to confirm identity of each other Message Integrity: sender, receiver want to ensure message not altered (in transit, or afterwards) without detection Access and Availability: services must be accessible and available to users Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 5
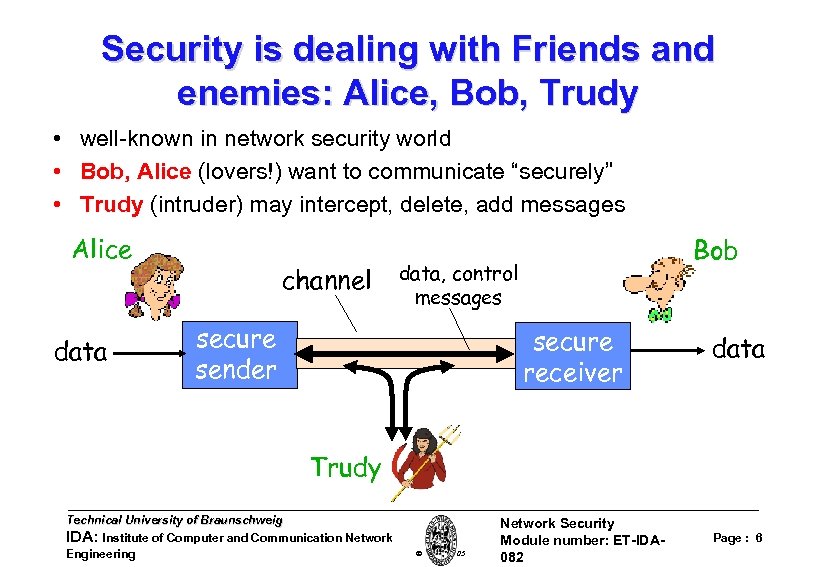 Security is dealing with Friends and enemies: Alice, Bob, Trudy • well-known in network security world • Bob, Alice (lovers!) want to communicate “securely” • Trudy (intruder) may intercept, delete, add messages Alice data channel Bob data, control messages secure sender secure receiver data Trudy Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 6
Security is dealing with Friends and enemies: Alice, Bob, Trudy • well-known in network security world • Bob, Alice (lovers!) want to communicate “securely” • Trudy (intruder) may intercept, delete, add messages Alice data channel Bob data, control messages secure sender secure receiver data Trudy Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 6
 Who might Bob, Alice be? … well, real-life Bobs and Alices! • Web browser/server for electronic transactions (e. g. , on-line purchases) • on-line banking client/server • DNS servers • routers exchanging routing table updates • other examples? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 7
Who might Bob, Alice be? … well, real-life Bobs and Alices! • Web browser/server for electronic transactions (e. g. , on-line purchases) • on-line banking client/server • DNS servers • routers exchanging routing table updates • other examples? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 7
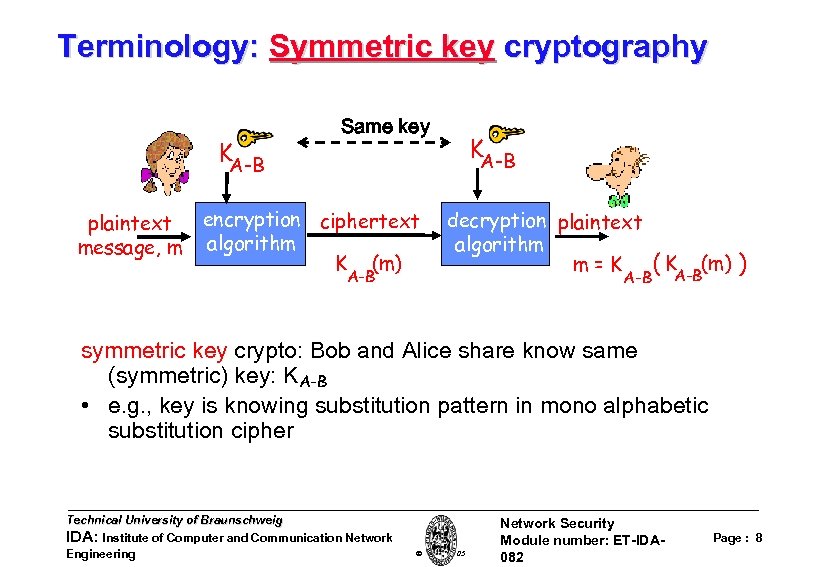 Terminology: Symmetric key cryptography KA-B plaintext message, m Same key encryption ciphertext algorithm K (m) A-B KA-B decryption plaintext algorithm m=K A-B ( KA-B(m) ) symmetric key crypto: Bob and Alice share know same (symmetric) key: KA-B • e. g. , key is knowing substitution pattern in mono alphabetic substitution cipher Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 8
Terminology: Symmetric key cryptography KA-B plaintext message, m Same key encryption ciphertext algorithm K (m) A-B KA-B decryption plaintext algorithm m=K A-B ( KA-B(m) ) symmetric key crypto: Bob and Alice share know same (symmetric) key: KA-B • e. g. , key is knowing substitution pattern in mono alphabetic substitution cipher Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 8
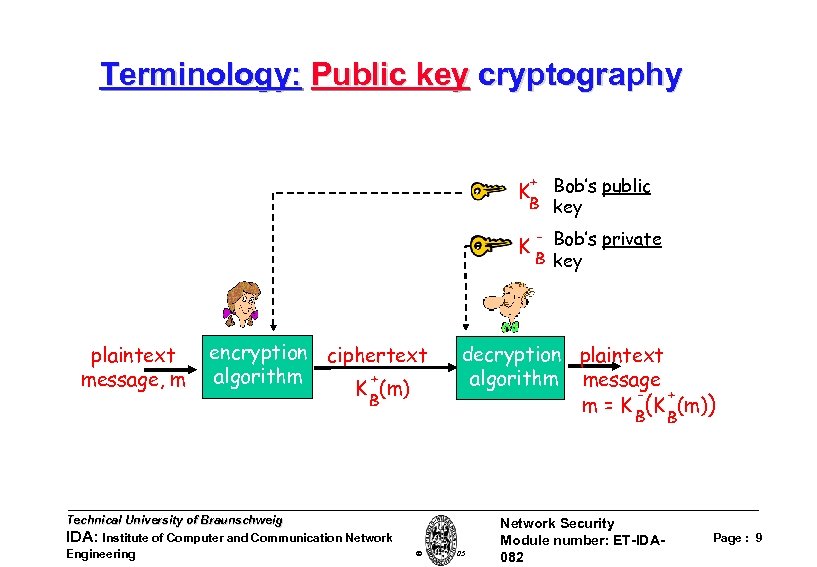 Terminology: Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 9
Terminology: Public key cryptography + Bob’s public B key K K plaintext message, m encryption ciphertext algorithm + K (m) B Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering - Bob’s private B key decryption plaintext algorithm message + m = K B(K (m)) B W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 9
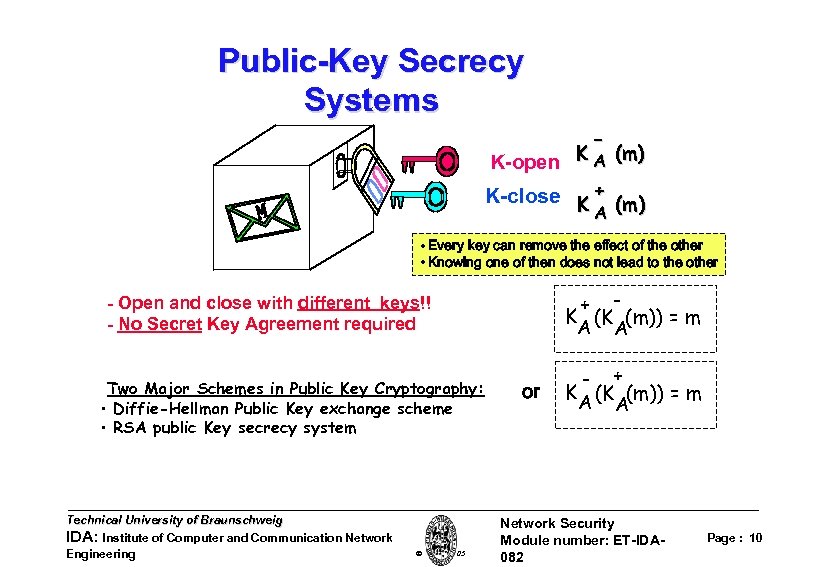 Public-Key Secrecy Systems - K-open K A (m) K-close K + (m) A • Every key can remove the effect of the other • Knowing one of then does not lead to the other + K (K (m)) = m A A - Open and close with different keys!! - No Secret Key Agreement required Two Major Schemes in Public Key Cryptography: • Diffie-Hellman Public Key exchange scheme • RSA public Key secrecy system Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 or - + K (K (m)) = m A A Network Security Module number: ET-IDA 082 Page : 10
Public-Key Secrecy Systems - K-open K A (m) K-close K + (m) A • Every key can remove the effect of the other • Knowing one of then does not lead to the other + K (K (m)) = m A A - Open and close with different keys!! - No Secret Key Agreement required Two Major Schemes in Public Key Cryptography: • Diffie-Hellman Public Key exchange scheme • RSA public Key secrecy system Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 or - + K (K (m)) = m A A Network Security Module number: ET-IDA 082 Page : 10
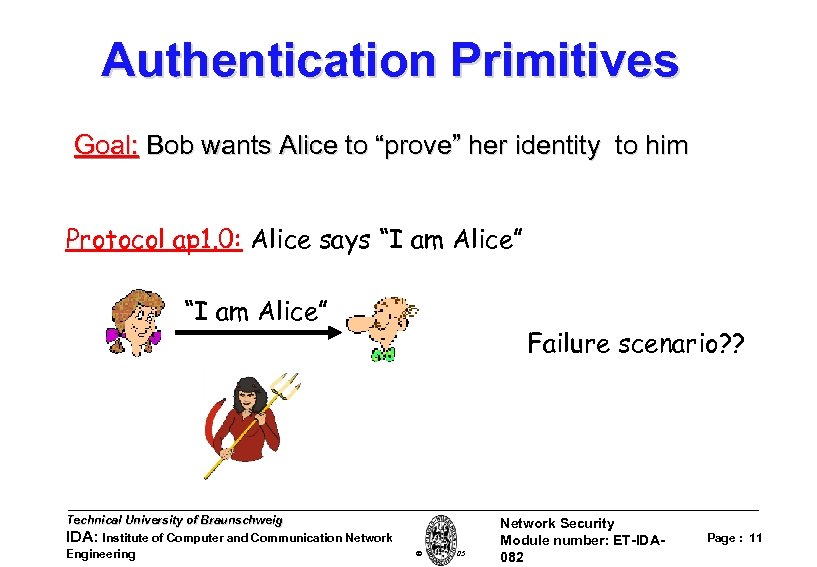 Authentication Primitives Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering Failure scenario? ? W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 11
Authentication Primitives Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering Failure scenario? ? W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 11
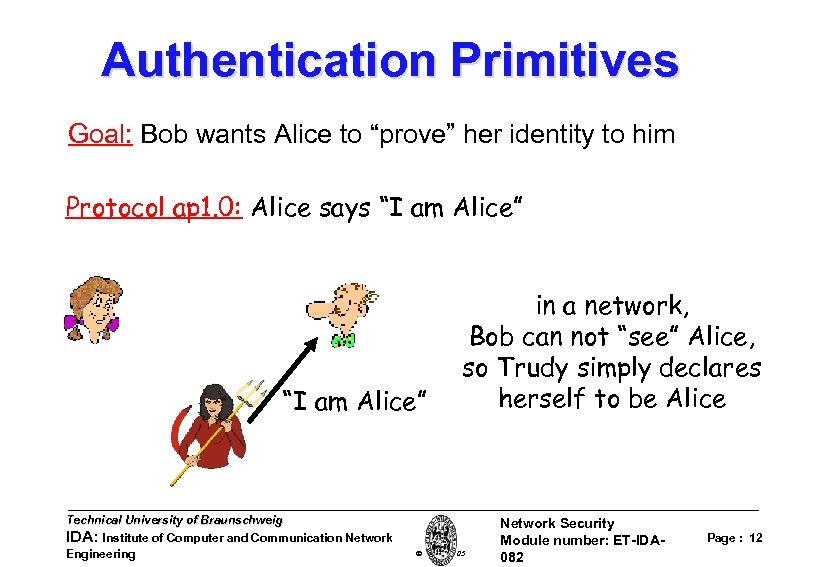 Authentication Primitives Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering in a network, Bob can not “see” Alice, so Trudy simply declares herself to be Alice W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 12
Authentication Primitives Goal: Bob wants Alice to “prove” her identity to him Protocol ap 1. 0: Alice says “I am Alice” Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering in a network, Bob can not “see” Alice, so Trudy simply declares herself to be Alice W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 12
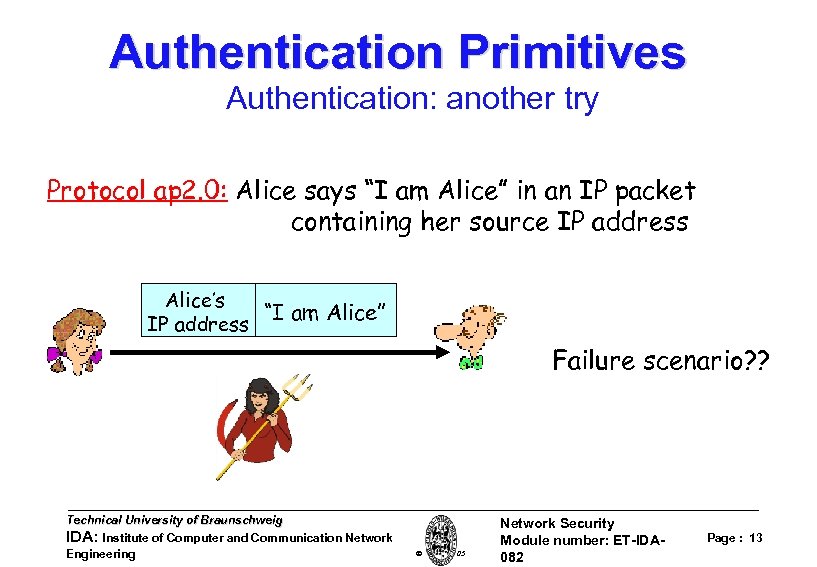 Authentication Primitives Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address Failure scenario? ? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 13
Authentication Primitives Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address Failure scenario? ? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 13
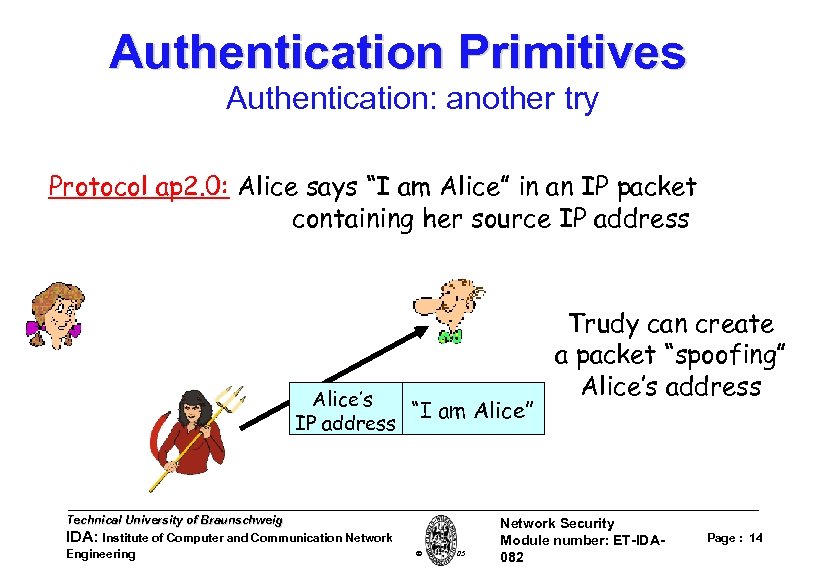 Authentication Primitives Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Trudy can create a packet “spoofing” Alice’s address Network Security Module number: ET-IDA 082 Page : 14
Authentication Primitives Authentication: another try Protocol ap 2. 0: Alice says “I am Alice” in an IP packet containing her source IP address Alice’s “I am Alice” IP address Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Trudy can create a packet “spoofing” Alice’s address Network Security Module number: ET-IDA 082 Page : 14
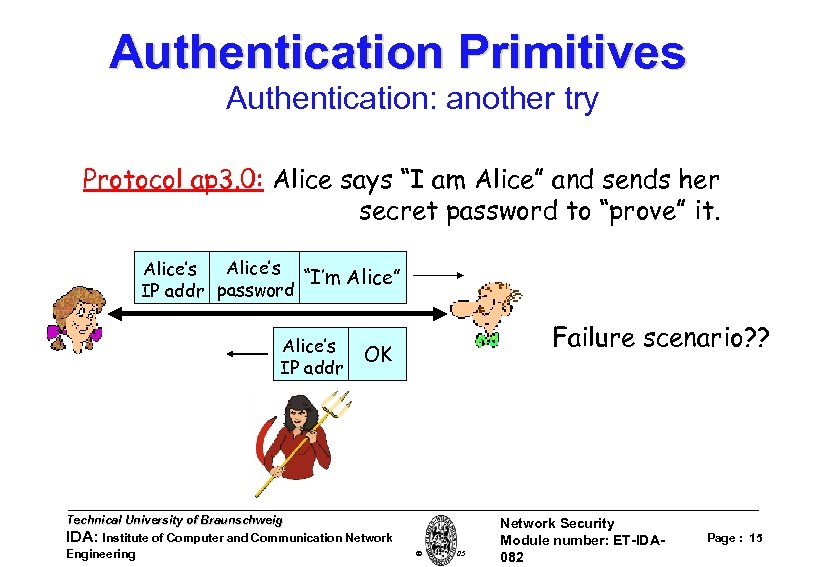 Authentication Primitives Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr Failure scenario? ? OK Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 15
Authentication Primitives Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr Failure scenario? ? OK Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 15
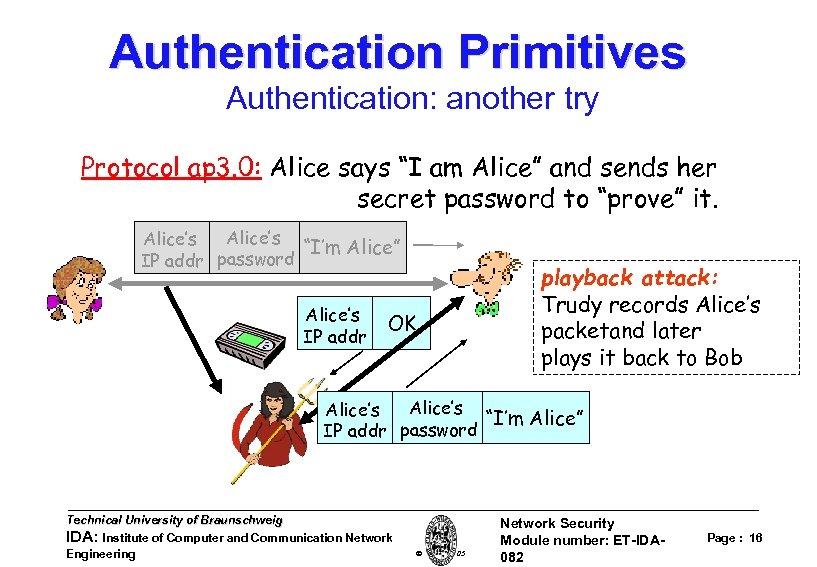 Authentication Primitives Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr playback attack: Trudy records Alice’s packetand later plays it back to Bob OK Alice’s “I’m Alice” IP addr password Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 16
Authentication Primitives Authentication: another try Protocol ap 3. 0: Alice says “I am Alice” and sends her secret password to “prove” it. Alice’s “I’m Alice” IP addr password Alice’s IP addr playback attack: Trudy records Alice’s packetand later plays it back to Bob OK Alice’s “I’m Alice” IP addr password Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 16
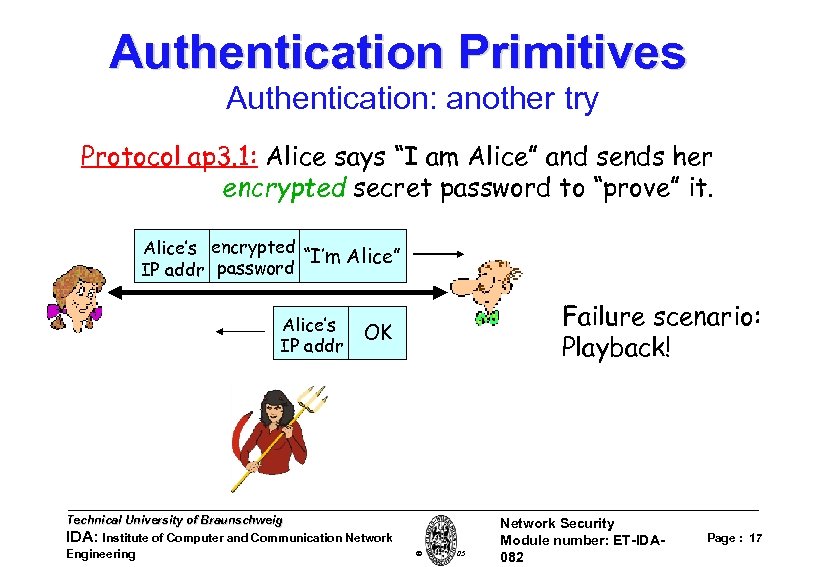 Authentication Primitives Authentication: another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr Failure scenario: Playback! OK Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 17
Authentication Primitives Authentication: another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr Failure scenario: Playback! OK Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 17
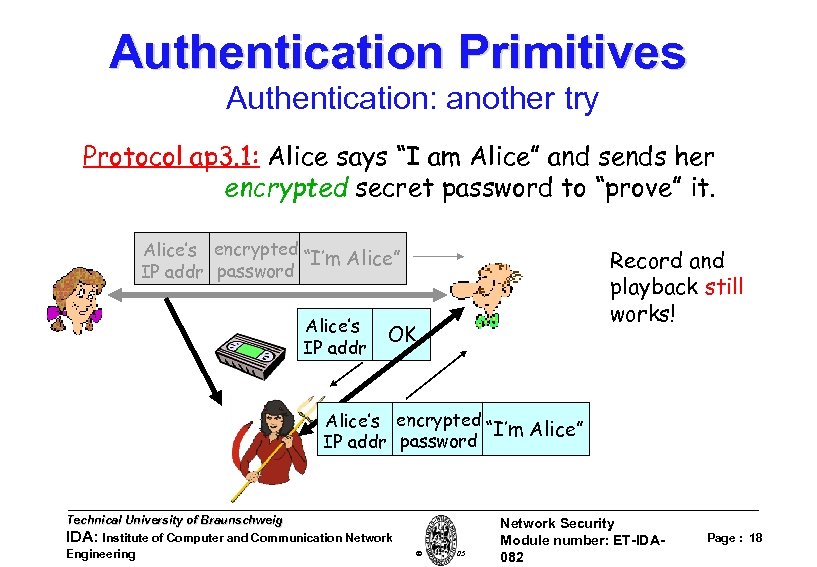 Authentication Primitives Authentication: another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr Record and playback still works! OK Alice’s encrypted “I’m Alice” IP addr password Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 18
Authentication Primitives Authentication: another try Protocol ap 3. 1: Alice says “I am Alice” and sends her encrypted secret password to “prove” it. Alice’s encrypted “I’m Alice” IP addr password Alice’s IP addr Record and playback still works! OK Alice’s encrypted “I’m Alice” IP addr password Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 18
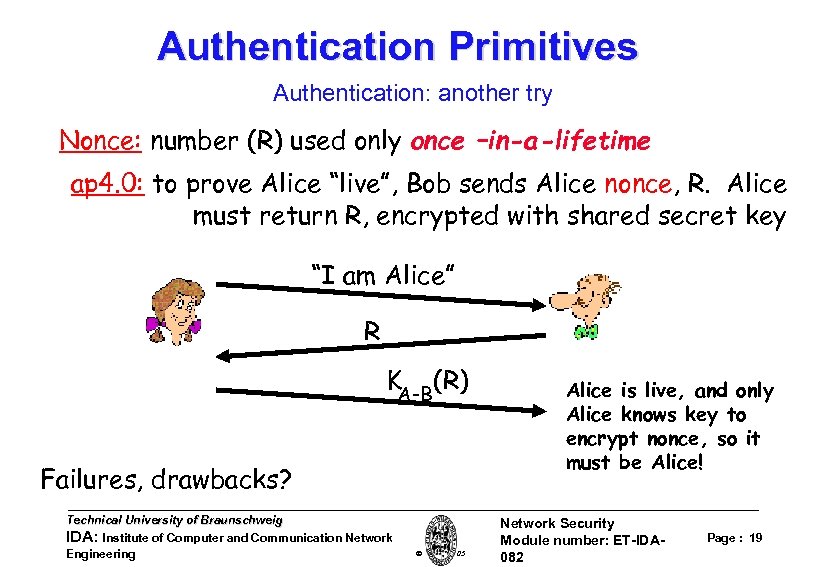 Authentication Primitives Authentication: another try Goal: avoid playback attack Nonce: number (R) used only once –in-a-lifetime ap 4. 0: to prove Alice “live”, Bob sends Alice nonce, R. Alice must return R, encrypted with shared secret key “I am Alice” R KA-B(R) Failures, drawbacks? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Alice is live, and only Alice knows key to encrypt nonce, so it must be Alice! Network Security Module number: ET-IDA 082 Page : 19
Authentication Primitives Authentication: another try Goal: avoid playback attack Nonce: number (R) used only once –in-a-lifetime ap 4. 0: to prove Alice “live”, Bob sends Alice nonce, R. Alice must return R, encrypted with shared secret key “I am Alice” R KA-B(R) Failures, drawbacks? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Alice is live, and only Alice knows key to encrypt nonce, so it must be Alice! Network Security Module number: ET-IDA 082 Page : 19
 Authentication Primitives Authentication: another try ap 4. 0 requires shared symmetric key • can we authenticate using public key techniques? …. yes ap 5. 0: use nonce, public key cryptography “I am Alice” R Bob computes + - - K A (R) “send me your public key” + KA Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 KA (R)) = R and knows only Alice could have the private key, that encrypted R such that + K (K (R)) = R A A Network Security Module number: ET-IDA 082 Page : 20
Authentication Primitives Authentication: another try ap 4. 0 requires shared symmetric key • can we authenticate using public key techniques? …. yes ap 5. 0: use nonce, public key cryptography “I am Alice” R Bob computes + - - K A (R) “send me your public key” + KA Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 KA (R)) = R and knows only Alice could have the private key, that encrypted R such that + K (K (R)) = R A A Network Security Module number: ET-IDA 082 Page : 20
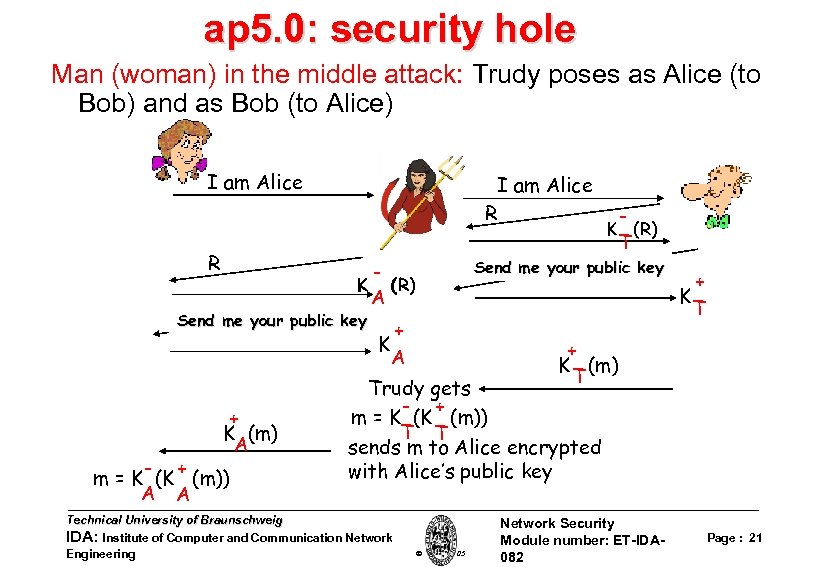 ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) I am Alice R R + K (m) A - + m = K (K (m)) A A K T K (R) Send me your public key K (R) A Send me your public key I am Alice K + A + T + K (m) T Trudy gets - + m = K (K (m)) T T sends m to Alice encrypted with Alice’s public key Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 21
ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) I am Alice R R + K (m) A - + m = K (K (m)) A A K T K (R) Send me your public key K (R) A Send me your public key I am Alice K + A + T + K (m) T Trudy gets - + m = K (K (m)) T T sends m to Alice encrypted with Alice’s public key Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 21
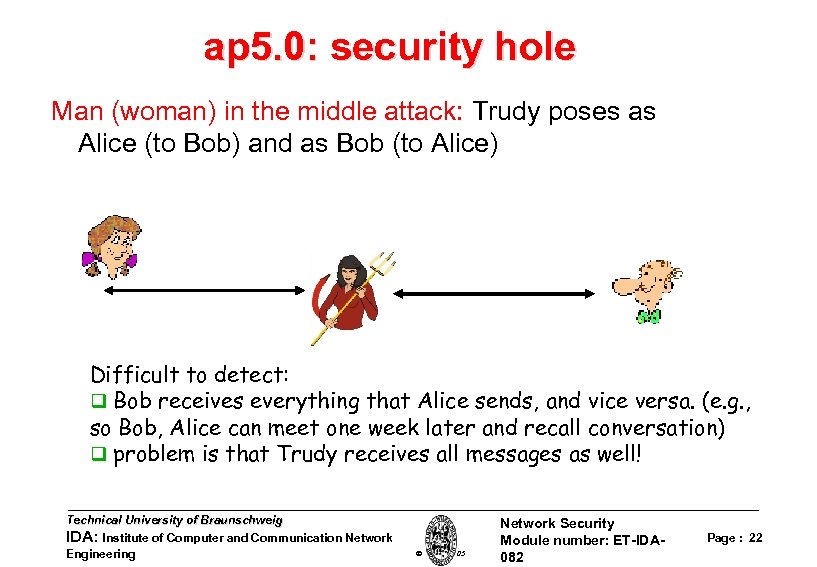 ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) Difficult to detect: q Bob receives everything that Alice sends, and vice versa. (e. g. , so Bob, Alice can meet one week later and recall conversation) q problem is that Trudy receives all messages as well! Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 22
ap 5. 0: security hole Man (woman) in the middle attack: Trudy poses as Alice (to Bob) and as Bob (to Alice) Difficult to detect: q Bob receives everything that Alice sends, and vice versa. (e. g. , so Bob, Alice can meet one week later and recall conversation) q problem is that Trudy receives all messages as well! Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 22
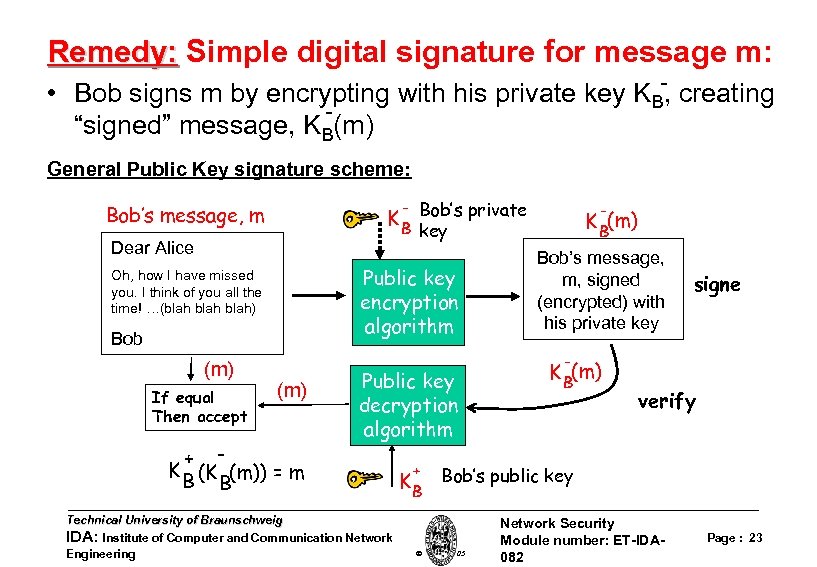 Remedy: Simple digital signature for message m: • Bob signs m by encrypting with his private key KB-, creating “signed” message, KB(m) General Public Key signature scheme: K B Bob’s private Bob’s message, m key Dear Alice Public key encryption algorithm Oh, how I have missed you. I think of you all the time! …(blah) Bob (m) If equal Then accept - K B(m) + K (K (m)) = m B B Public key decryption algorithm Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering Bob’s message, m, signed (encrypted) with his private key signe - K B(m) verify + K B Bob’s public key W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 23
Remedy: Simple digital signature for message m: • Bob signs m by encrypting with his private key KB-, creating “signed” message, KB(m) General Public Key signature scheme: K B Bob’s private Bob’s message, m key Dear Alice Public key encryption algorithm Oh, how I have missed you. I think of you all the time! …(blah) Bob (m) If equal Then accept - K B(m) + K (K (m)) = m B B Public key decryption algorithm Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering Bob’s message, m, signed (encrypted) with his private key signe - K B(m) verify + K B Bob’s public key W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 23
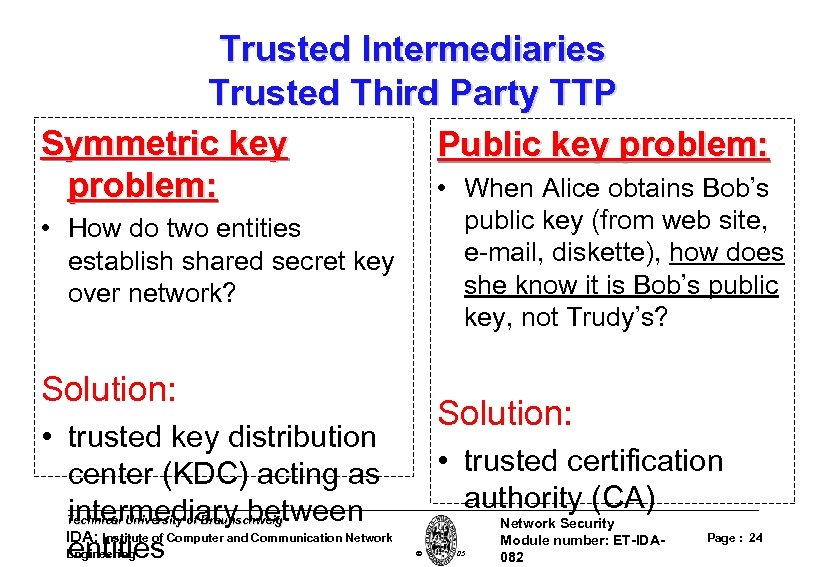 Trusted Intermediaries Trusted Third Party TTP Symmetric key Public key problem: • When Alice obtains Bob’s problem: • How do two entities establish shared secret key over network? Solution: • trusted key distribution center (KDC) acting as intermediary between IDA: entities Technical University of Braunschweig Institute of Computer and Communication Network Engineering public key (from web site, e-mail, diskette), how does she know it is Bob’s public key, not Trudy’s? Solution: • trusted certification authority (CA) W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 24
Trusted Intermediaries Trusted Third Party TTP Symmetric key Public key problem: • When Alice obtains Bob’s problem: • How do two entities establish shared secret key over network? Solution: • trusted key distribution center (KDC) acting as intermediary between IDA: entities Technical University of Braunschweig Institute of Computer and Communication Network Engineering public key (from web site, e-mail, diskette), how does she know it is Bob’s public key, not Trudy’s? Solution: • trusted certification authority (CA) W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 24
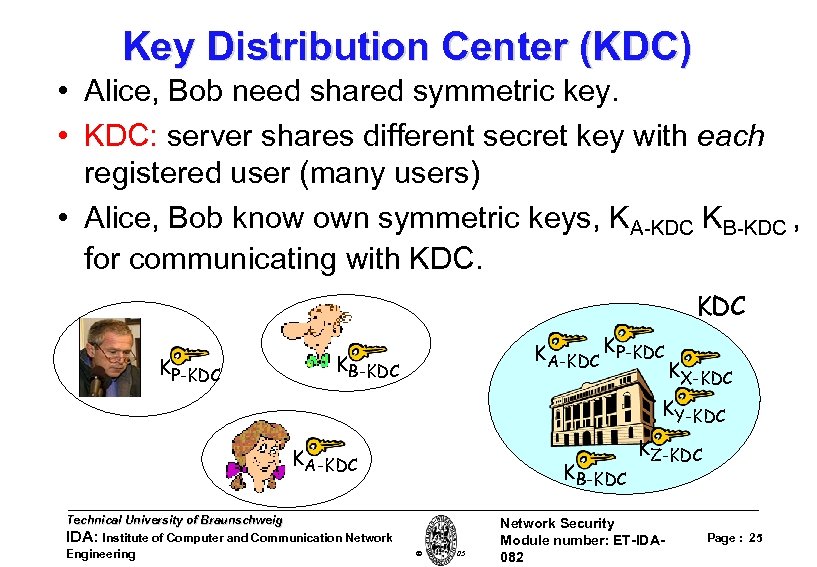 Key Distribution Center (KDC) • Alice, Bob need shared symmetric key. • KDC: server shares different secret key with each registered user (many users) • Alice, Bob know own symmetric keys, KA-KDC KB-KDC , for communicating with KDC KP-KDC KA-KDC KP-KDC KB-KDC KX-KDC KY-KDC KA-KDC Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering KB-KDC W. Adi 2005 KZ-KDC Network Security Module number: ET-IDA 082 Page : 25
Key Distribution Center (KDC) • Alice, Bob need shared symmetric key. • KDC: server shares different secret key with each registered user (many users) • Alice, Bob know own symmetric keys, KA-KDC KB-KDC , for communicating with KDC KP-KDC KA-KDC KP-KDC KB-KDC KX-KDC KY-KDC KA-KDC Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering KB-KDC W. Adi 2005 KZ-KDC Network Security Module number: ET-IDA 082 Page : 25
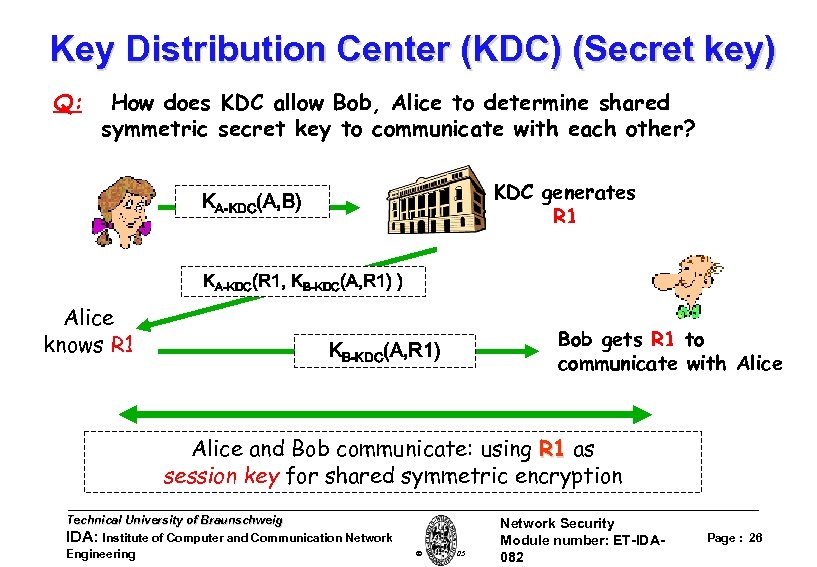 Key Distribution Center (KDC) (Secret key) Q: How does KDC allow Bob, Alice to determine shared symmetric secret key to communicate with each other? KDC generates R 1 KA-KDC(A, B) KA-KDC(R 1, KB-KDC(A, R 1) ) Alice knows R 1 KB-KDC(A, R 1) Bob gets R 1 to communicate with Alice and Bob communicate: using R 1 as session key for shared symmetric encryption Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 26
Key Distribution Center (KDC) (Secret key) Q: How does KDC allow Bob, Alice to determine shared symmetric secret key to communicate with each other? KDC generates R 1 KA-KDC(A, B) KA-KDC(R 1, KB-KDC(A, R 1) ) Alice knows R 1 KB-KDC(A, R 1) Bob gets R 1 to communicate with Alice and Bob communicate: using R 1 as session key for shared symmetric encryption Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 26
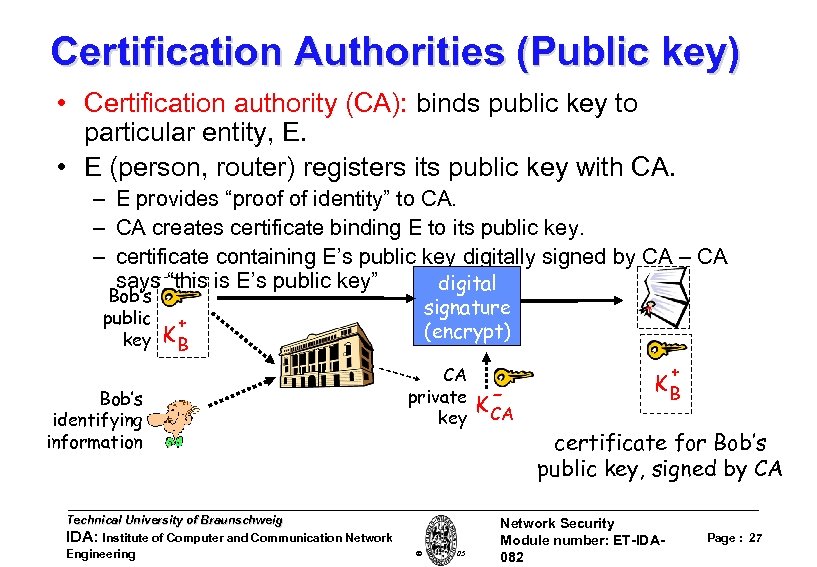 Certification Authorities (Public key) • Certification authority (CA): binds public key to particular entity, E. • E (person, router) registers its public key with CA. – E provides “proof of identity” to CA. – CA creates certificate binding E to its public key. – certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” digital Bob’s public key + KB Bob’s identifying information Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering signature (encrypt) CA private key W. Adi 2005 K CA + KB certificate for Bob’s public key, signed by CA Network Security Module number: ET-IDA 082 Page : 27
Certification Authorities (Public key) • Certification authority (CA): binds public key to particular entity, E. • E (person, router) registers its public key with CA. – E provides “proof of identity” to CA. – CA creates certificate binding E to its public key. – certificate containing E’s public key digitally signed by CA – CA says “this is E’s public key” digital Bob’s public key + KB Bob’s identifying information Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering signature (encrypt) CA private key W. Adi 2005 K CA + KB certificate for Bob’s public key, signed by CA Network Security Module number: ET-IDA 082 Page : 27
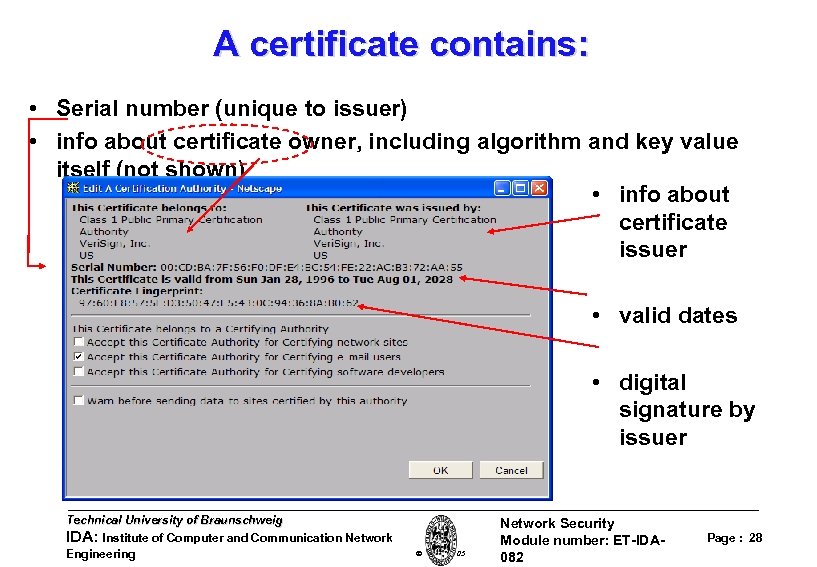 A certificate contains: • Serial number (unique to issuer) • info about certificate owner, including algorithm and key value itself (not shown) • info about certificate issuer • valid dates • digital signature by issuer Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 28
A certificate contains: • Serial number (unique to issuer) • info about certificate owner, including algorithm and key value itself (not shown) • info about certificate issuer • valid dates • digital signature by issuer Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 28
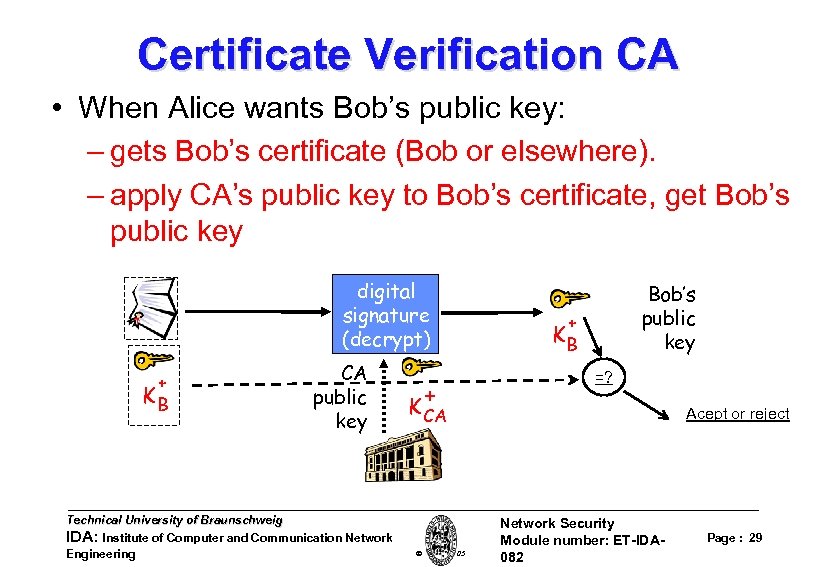 Certificate Verification CA • When Alice wants Bob’s public key: – gets Bob’s certificate (Bob or elsewhere). – apply CA’s public key to Bob’s certificate, get Bob’s public key digital signature (decrypt) + KB CA public key Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering + K CA W. Adi 2005 Bob’s public key + KB =? Acept or reject Network Security Module number: ET-IDA 082 Page : 29
Certificate Verification CA • When Alice wants Bob’s public key: – gets Bob’s certificate (Bob or elsewhere). – apply CA’s public key to Bob’s certificate, get Bob’s public key digital signature (decrypt) + KB CA public key Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering + K CA W. Adi 2005 Bob’s public key + KB =? Acept or reject Network Security Module number: ET-IDA 082 Page : 29
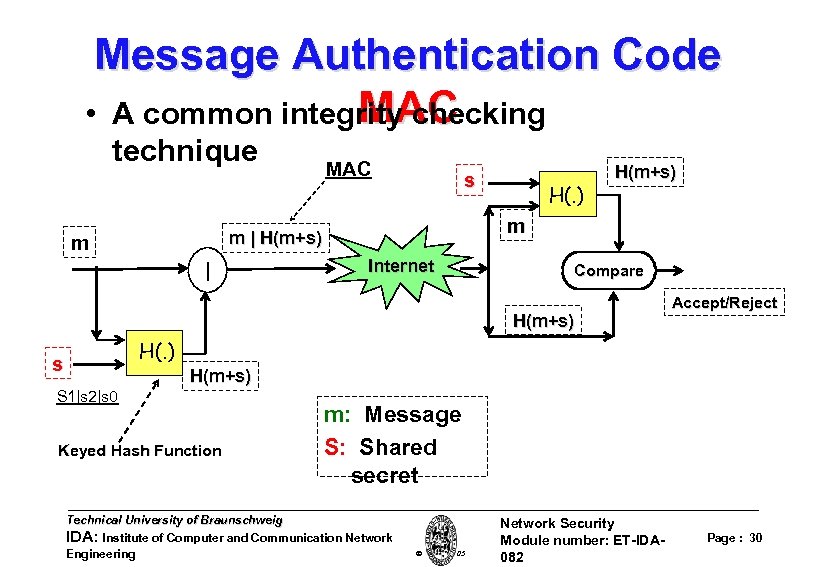 Message Authentication Code MAC • A common integrity checking technique MAC s m m | H(m+s) m | H(. ) H(m+s) Internet Compare H(m+s) Accept/Reject H(. ) s H(m+s) S 1|s 2|s 0 Keyed Hash Function m: Message S: Shared secret Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 30
Message Authentication Code MAC • A common integrity checking technique MAC s m m | H(m+s) m | H(. ) H(m+s) Internet Compare H(m+s) Accept/Reject H(. ) s H(m+s) S 1|s 2|s 0 Keyed Hash Function m: Message S: Shared secret Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 30
 SSL Secure Socket Layer Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 31
SSL Secure Socket Layer Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 31
 Security on the Internet • TCP/IP provides no security • Must retrofit Internet for security – Application layer • PGP, S/MIME, SSH, … – “Socket layer” • SSL/TLS (really part of application layer) – Network layer • IPSec Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 32
Security on the Internet • TCP/IP provides no security • Must retrofit Internet for security – Application layer • PGP, S/MIME, SSH, … – “Socket layer” • SSL/TLS (really part of application layer) – Network layer • IPSec Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 32
 Application Layer Security • Pretty Good Privacy (PGP) – Developed by Phil Zimmerman – No backdoor? • “We don’t hire that kind of person” • Secure/Multipurpose Internet Mail Extensions (S/MIME) – Secure email • Secure Shell (SSH) – Secure “tunnel” for remote access Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 33
Application Layer Security • Pretty Good Privacy (PGP) – Developed by Phil Zimmerman – No backdoor? • “We don’t hire that kind of person” • Secure/Multipurpose Internet Mail Extensions (S/MIME) – Secure email • Secure Shell (SSH) – Secure “tunnel” for remote access Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 33
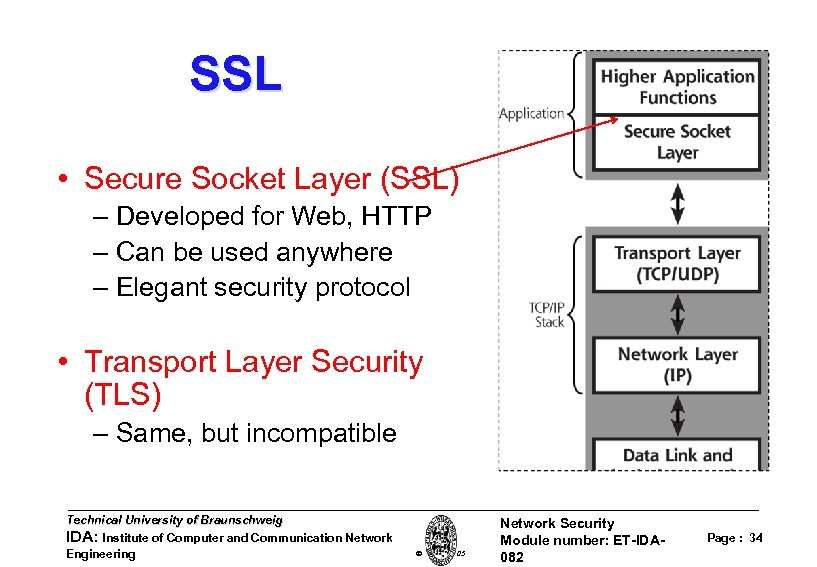 SSL • Secure Socket Layer (SSL) – Developed for Web, HTTP – Can be used anywhere – Elegant security protocol • Transport Layer Security (TLS) – Same, but incompatible Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 34
SSL • Secure Socket Layer (SSL) – Developed for Web, HTTP – Can be used anywhere – Elegant security protocol • Transport Layer Security (TLS) – Same, but incompatible Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 34
 SSL • Provides: Authentication, confidentiality, integrity • You use SSL all the time – Whenever “lock” (or “key”) appears in browser – HTTPS == HTTP with SSL • Secure transactions on Internet Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 35
SSL • Provides: Authentication, confidentiality, integrity • You use SSL all the time – Whenever “lock” (or “key”) appears in browser – HTTPS == HTTP with SSL • Secure transactions on Internet Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 35
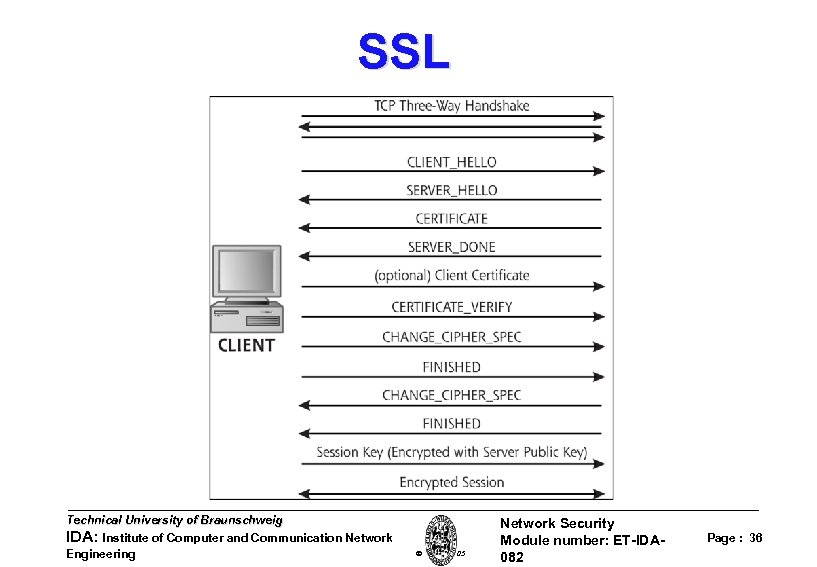 SSL Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 36
SSL Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 36
 SSL Secure Socket Layer Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 37
SSL Secure Socket Layer Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 37
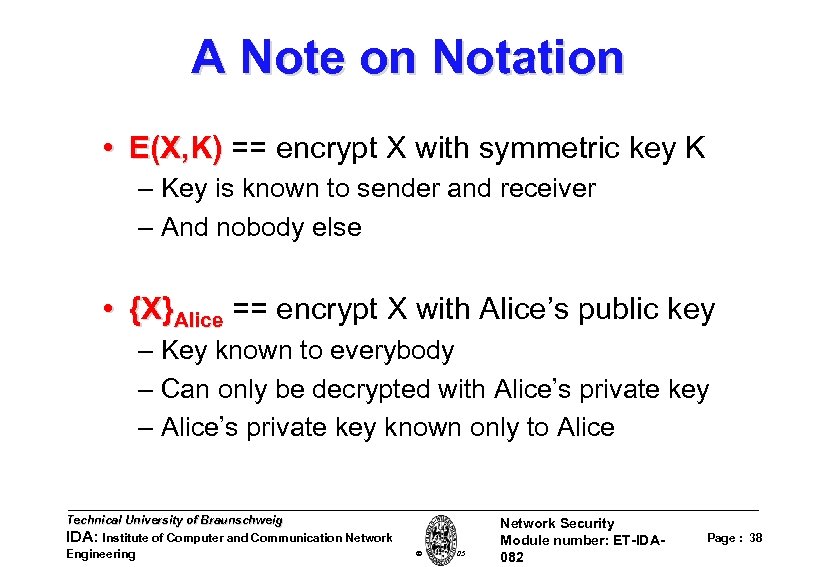 A Note on Notation • E(X, K) == encrypt X with symmetric key K – Key is known to sender and receiver – And nobody else • {X}Alice == encrypt X with Alice’s public key – Key known to everybody – Can only be decrypted with Alice’s private key – Alice’s private key known only to Alice Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 38
A Note on Notation • E(X, K) == encrypt X with symmetric key K – Key is known to sender and receiver – And nobody else • {X}Alice == encrypt X with Alice’s public key – Key known to everybody – Can only be decrypted with Alice’s private key – Alice’s private key known only to Alice Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 38
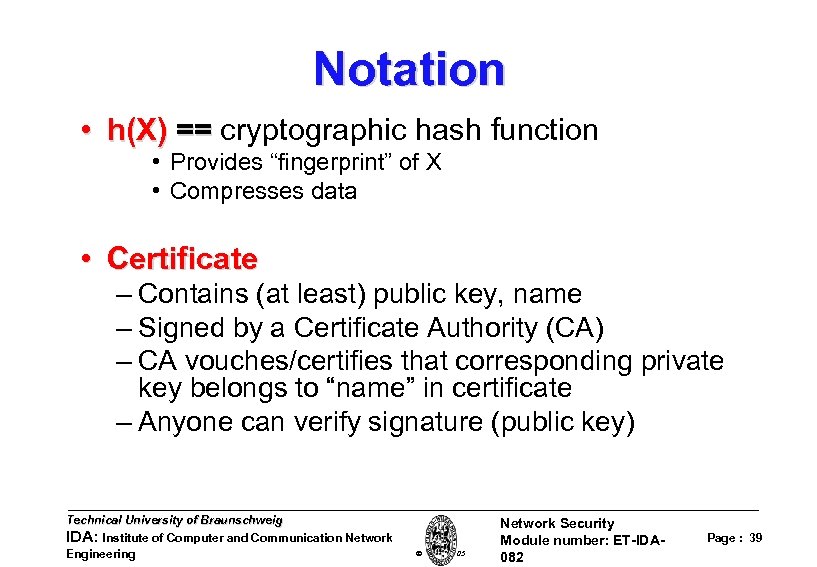 Notation • h(X) == cryptographic hash function • Provides “fingerprint” of X • Compresses data • Certificate – Contains (at least) public key, name – Signed by a Certificate Authority (CA) – CA vouches/certifies that corresponding private key belongs to “name” in certificate – Anyone can verify signature (public key) Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 39
Notation • h(X) == cryptographic hash function • Provides “fingerprint” of X • Compresses data • Certificate – Contains (at least) public key, name – Signed by a Certificate Authority (CA) – CA vouches/certifies that corresponding private key belongs to “name” in certificate – Anyone can verify signature (public key) Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 39
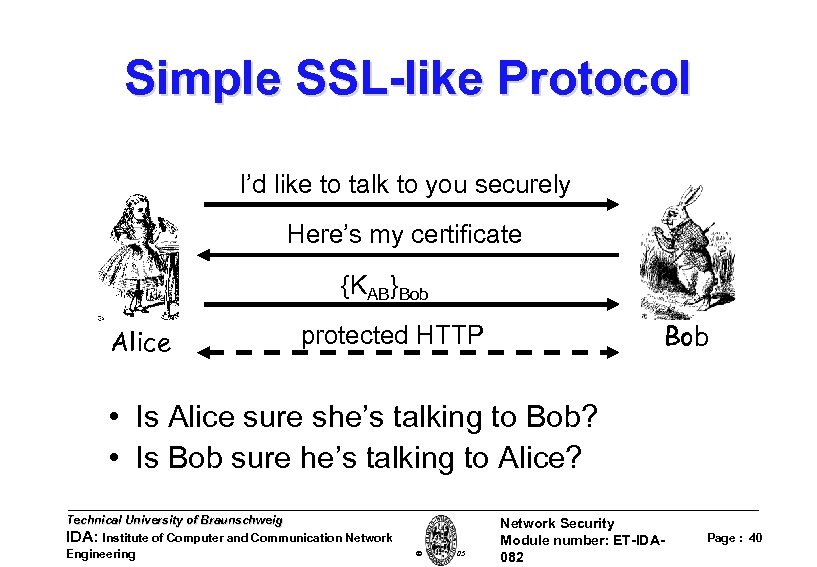 Simple SSL-like Protocol I’d like to talk to you securely Here’s my certificate {KAB}Bob Alice Bob protected HTTP • Is Alice sure she’s talking to Bob? • Is Bob sure he’s talking to Alice? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 40
Simple SSL-like Protocol I’d like to talk to you securely Here’s my certificate {KAB}Bob Alice Bob protected HTTP • Is Alice sure she’s talking to Bob? • Is Bob sure he’s talking to Alice? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 40
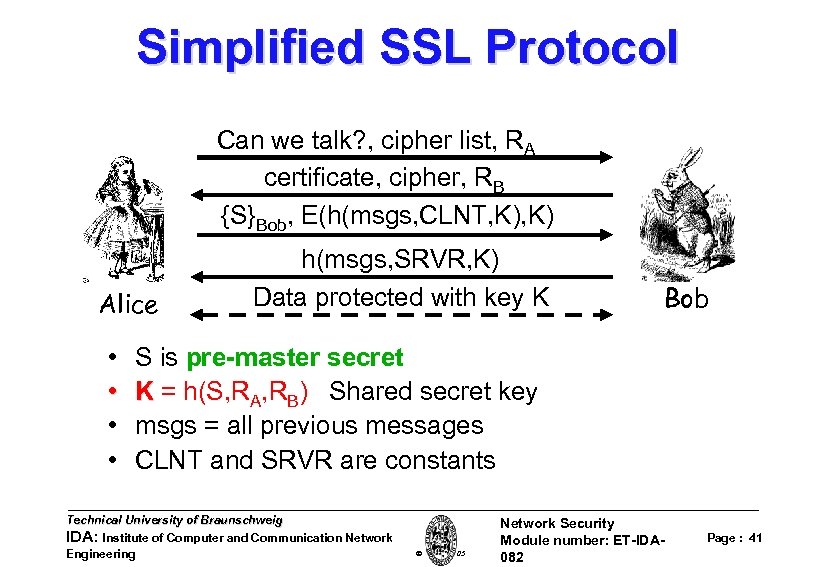 Simplified SSL Protocol Can we talk? , cipher list, RA certificate, cipher, RB {S}Bob, E(h(msgs, CLNT, K) Alice • • h(msgs, SRVR, K) Data protected with key K Bob S is pre-master secret K = h(S, RA, RB) Shared secret key msgs = all previous messages CLNT and SRVR are constants Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 41
Simplified SSL Protocol Can we talk? , cipher list, RA certificate, cipher, RB {S}Bob, E(h(msgs, CLNT, K) Alice • • h(msgs, SRVR, K) Data protected with key K Bob S is pre-master secret K = h(S, RA, RB) Shared secret key msgs = all previous messages CLNT and SRVR are constants Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 41
 SSL Authentication • Alice authenticates Bob, not vice-versa – How does client authenticate server? – Why does server not authenticate client? • Mutual authentication is possible: Bob sends certificate request in message 2 – This requires client to have certificate – If server wants to authenticate client, server could instead require (encrypted) password Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 42
SSL Authentication • Alice authenticates Bob, not vice-versa – How does client authenticate server? – Why does server not authenticate client? • Mutual authentication is possible: Bob sends certificate request in message 2 – This requires client to have certificate – If server wants to authenticate client, server could instead require (encrypted) password Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 42
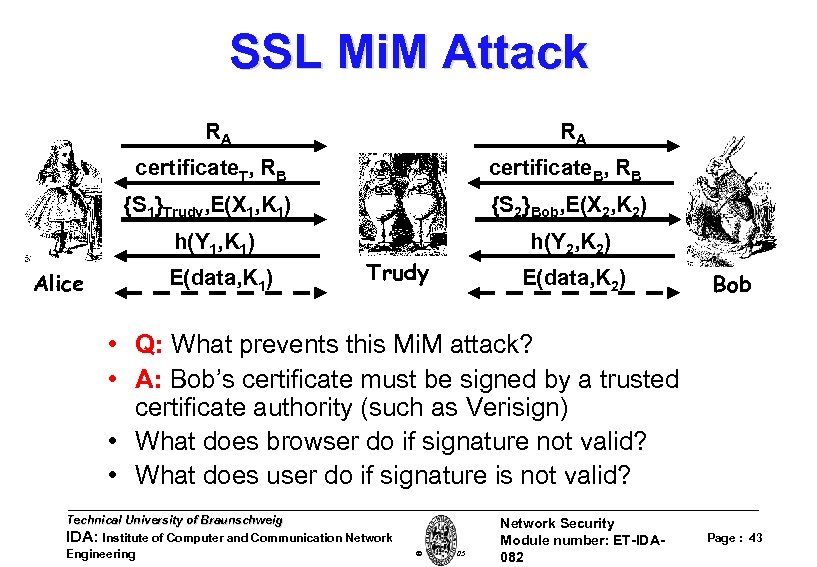 SSL Mi. M Attack RA RA certificate. T, RB certificate. B, RB {S 1}Trudy, E(X 1, K 1) {S 2}Bob, E(X 2, K 2) h(Y 1, K 1) Alice E(data, K 1) Trudy h(Y 2, K 2) E(data, K 2) Bob • Q: What prevents this Mi. M attack? • A: Bob’s certificate must be signed by a trusted certificate authority (such as Verisign) • What does browser do if signature not valid? • What does user do if signature is not valid? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 43
SSL Mi. M Attack RA RA certificate. T, RB certificate. B, RB {S 1}Trudy, E(X 1, K 1) {S 2}Bob, E(X 2, K 2) h(Y 1, K 1) Alice E(data, K 1) Trudy h(Y 2, K 2) E(data, K 2) Bob • Q: What prevents this Mi. M attack? • A: Bob’s certificate must be signed by a trusted certificate authority (such as Verisign) • What does browser do if signature not valid? • What does user do if signature is not valid? Technical University of Braunschweig IDA: Institute of Computer and Communication Network Engineering W. Adi 2005 Network Security Module number: ET-IDA 082 Page : 43


