43f4422439d49807f9887d19a4abca40.ppt
- Количество слайдов: 93

Network Security Basics 1

Outline of Network Security Basics § § What is Network Security? Threats and Attacks Defenses Cryptography 2

What is Security? § “The quality or state of being secure—to be free from danger” § A successful organization should have multiple layers of security in place: § § § Physical security Personal security Operations security Network security Information security 3

What is Network Security? § Network security refers to any activities designed to protect your network, which protect the usability, reliability, integrity, and safety of your network and data. Effective network security targets a variety of threats and stops them from entering or spreading on your network 4

Balancing Security and Access § Impossible to obtain perfect security—it is a process, not an absolute § Security should be considered balance between protection and availability § To achieve balance, level of security must allow reasonable access, yet protect against threats 5
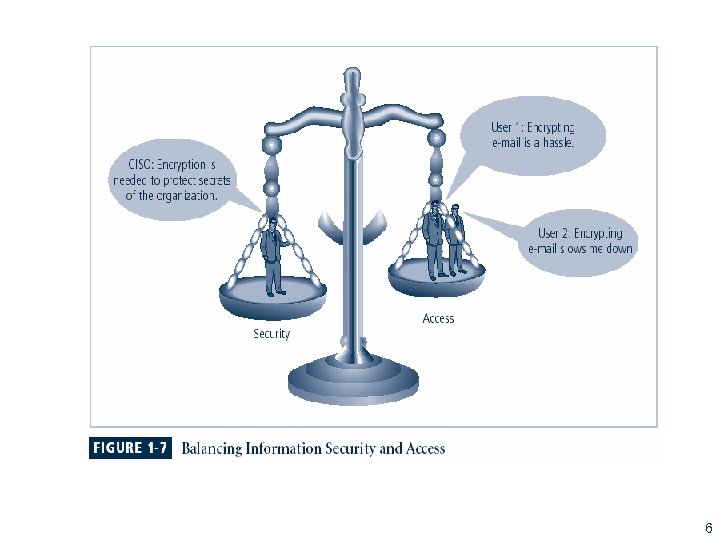
Figure 1 -6 – Balancing Security and Access 6

Outline of Network Security Basics § § What is Network Security? Threats and Attacks Defenses Cryptography 7

Threats § Threat: an object, person, or other entity that represents a constant danger to an asset § Management must be informed of the different threats facing the organization § By examining each threat category, management effectively protects information through policy, education, training, and technology controls 8
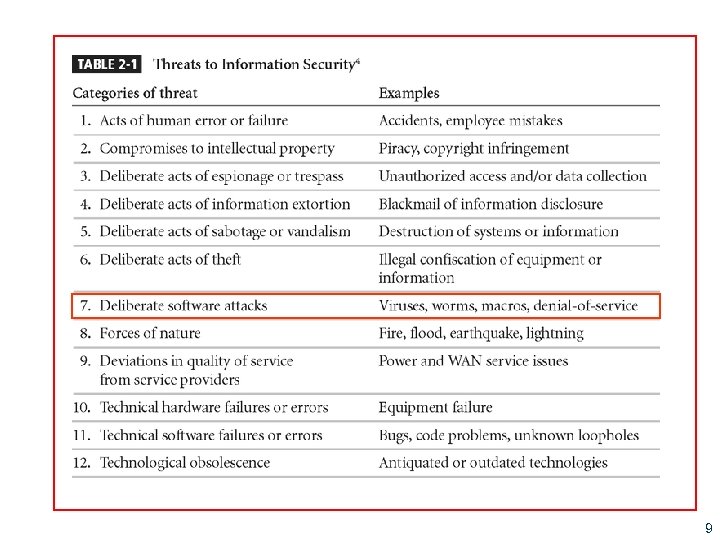
Threats to Information Security 9

Acts of Human Error or Failure § Includes acts performed without malicious intent § Causes include: § Inexperience § Improper training § Incorrect assumptions § Employees are among the greatest threats to an organization’s data 10

Acts of Human Error or Failure (continued) § Employee mistakes can easily lead to: § Revelation of classified data § Entry of erroneous data § Accidental data deletion or modification § Data storage in unprotected areas § Failure to protect information § Many of these threats can be prevented with controls 11

Forces of Nature § Forces of nature among the most dangerous threats § Disrupt not only individual lives, but also storage, transmission, and use of information § Organizations must implement controls to limit damage and prepare contingency plans for continued operations 12

Deviations in Quality of Service § Includes situations where products or services not delivered as expected § Information system depends on many interdependent support systems § Internet service, communications, and power irregularities dramatically affect availability of information and systems 13

Internet Service Issues § Internet service provider (ISP) failures can considerably undermine availability of information § Outsourced Web hosting provider assumes responsibility for all Internet services as well as hardware and Web site operating system software 14

Attacks § Act or action that exploits vulnerability (i. e. , an identified weakness) in controlled system § Accomplished by threat agent which damages or steals organization’s information 15
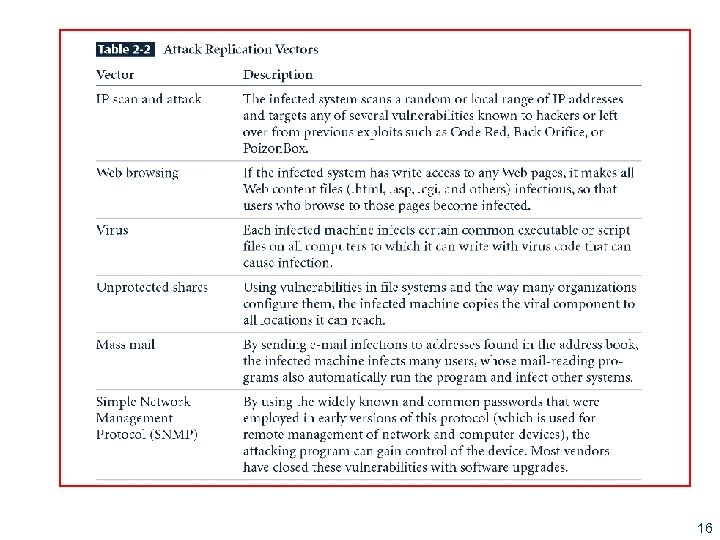
Table 2 -2 - Attack Replication Vectors New Table 16

Attacks (continued) § Malicious code: includes execution of viruses, worms, Trojan horses, and active Web scripts with intent to destroy or steal information § Back door: gaining access to system or network using known or previously unknown/newly discovered access mechanism 17

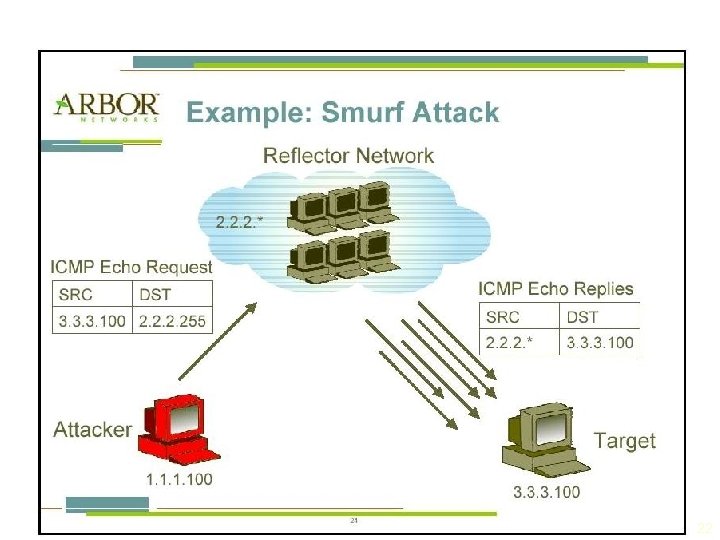
Attacks (continued) § Spoofing: technique used to gain unauthorized access; intruder assumes a trusted IP address § Man-in-the-middle: attacker monitors network packets, modifies them, and inserts them back into network § Spam: unsolicited commercial e-mail; more a nuisance than an attack, though is emerging as a vector for some attacks 18
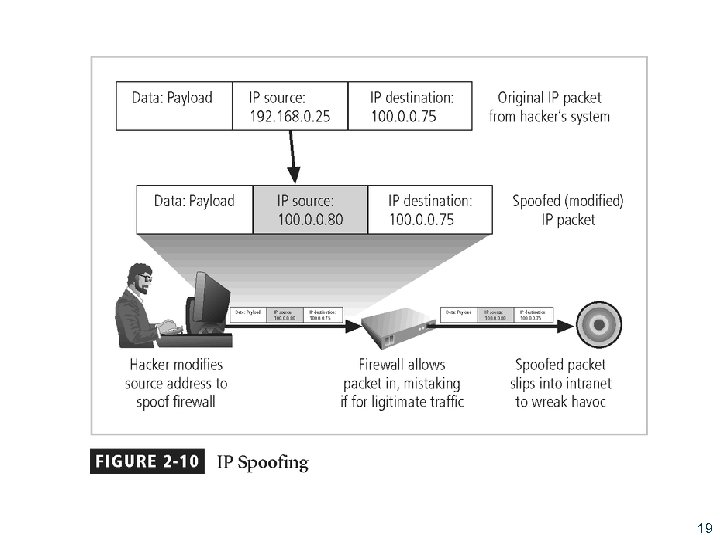
19
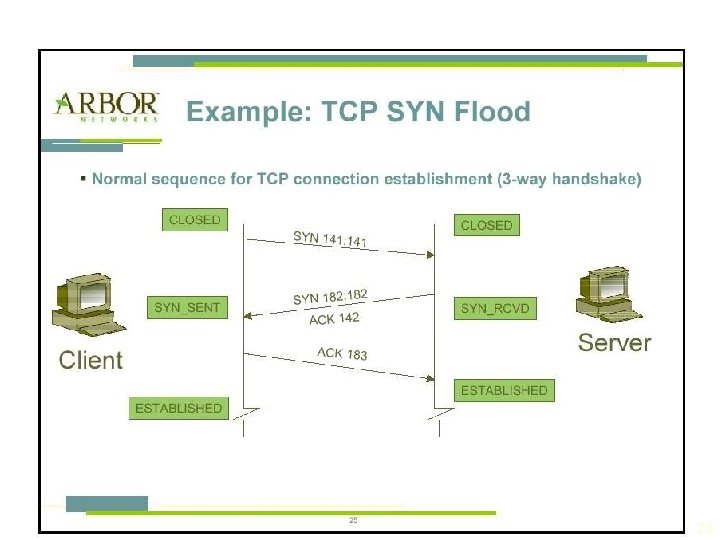
Attacks (continued) § Denial-of-service (Do. S): attacker sends large number of connection or information requests to a target § Target system cannot handle successfully along with other, legitimate service requests § May result in system crash or inability to perform ordinary functions § Distributed denial-of-service (DDo. S): coordinated stream of requests is launched against target from many locations simultaneously 20
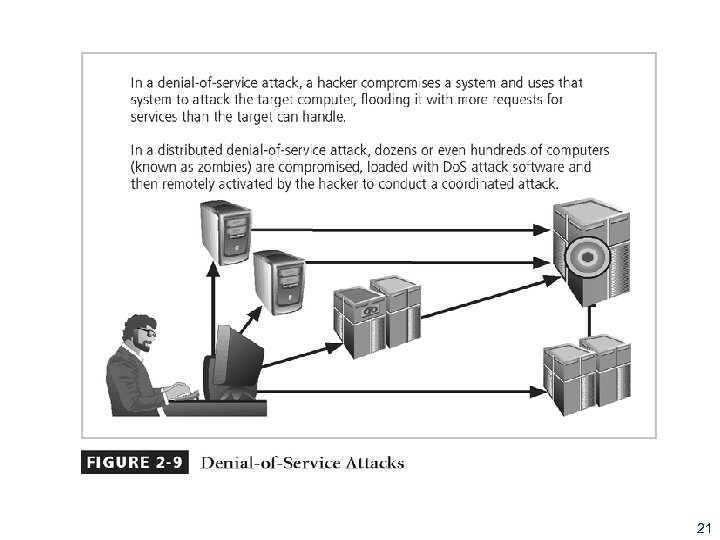
Figure 2 -9 - Denial-of-Service Attacks 21
22
23
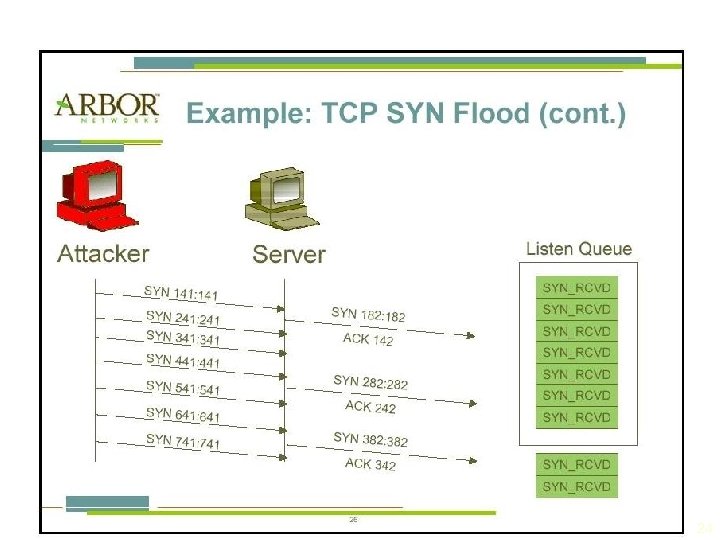
24

What Makes DDo. S Attacks Possible? § Internet was designed with functionality & not security in mind § Internet security is highly interdependent § Internet resources are limited § Power of many is greater than power of a few 25

Summary on Threats and Attacks § Threat: object, person, or other entity representing a constant danger to an asset § Attack: a deliberate act that exploits vulnerability 26

Outline of Network Security Basics § § What is Network Security? Threats and Attacks Defenses Cryptography 27
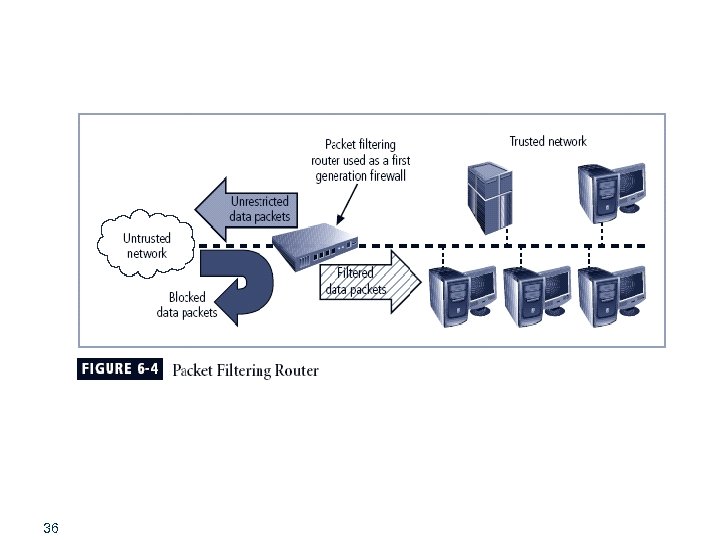
Firewalls § Prevent specific types of information from moving between the outside world (untrusted network) and the inside world (trusted network) § May be separate computer system; a software service running on existing router or server; or a separate network containing supporting devices 28
Firewall Categorization § § 29 Processing mode Development era Intended deployment structure Architectural implementation

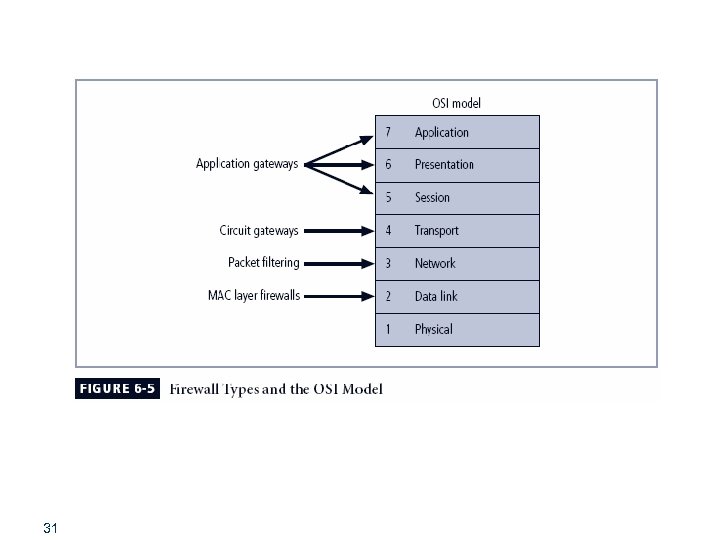
Firewalls Categorized by Processing Modes § § § 30 Packet filtering Application gateways Circuit gateways MAC layer firewalls Hybrids
31
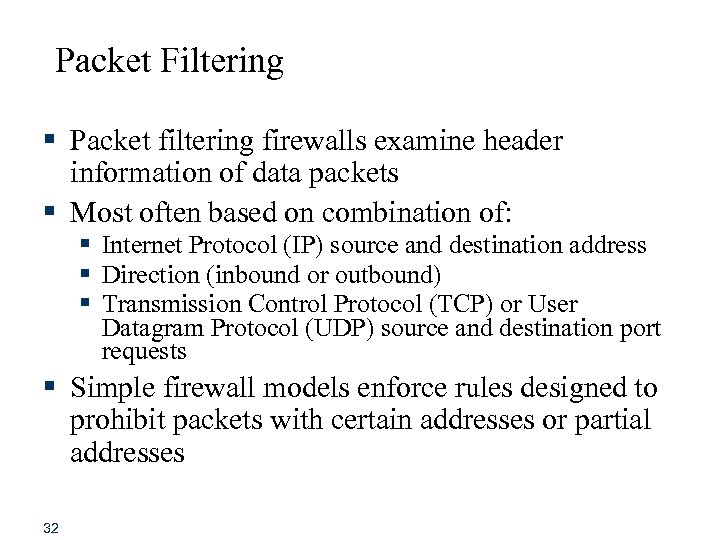
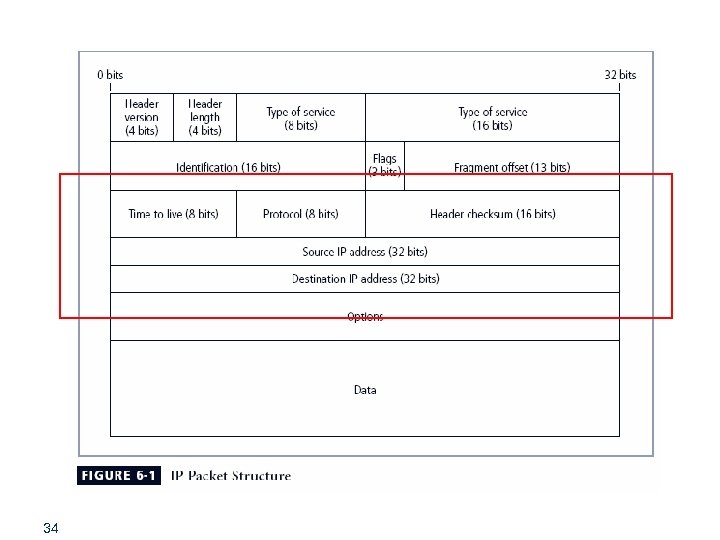
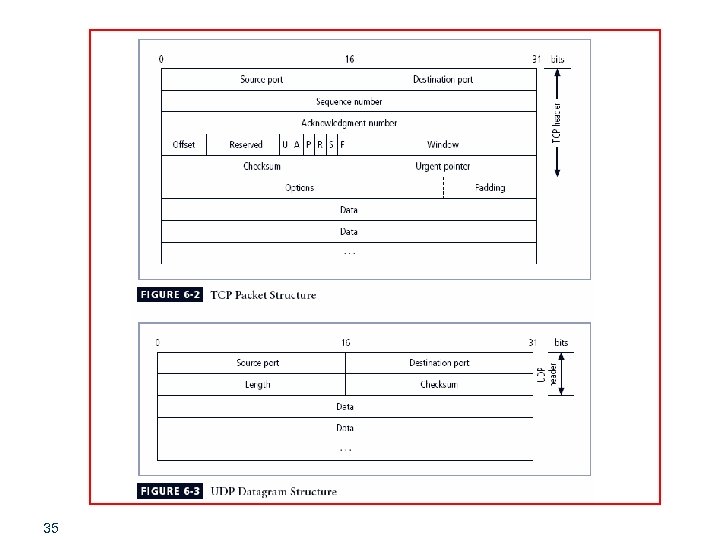
Packet Filtering § Packet filtering firewalls examine header information of data packets § Most often based on combination of: § Internet Protocol (IP) source and destination address § Direction (inbound or outbound) § Transmission Control Protocol (TCP) or User Datagram Protocol (UDP) source and destination port requests § Simple firewall models enforce rules designed to prohibit packets with certain addresses or partial addresses 32

Packet Filtering (continued) § Three subsets of packet filtering firewalls: § Static filtering: requires that filtering rules governing how the firewall decides which packets are allowed and which are denied are developed and installed § Dynamic filtering: allows firewall to react to emergent event and update or create rules to deal with event § Stateful inspection: firewalls that keep track of each network connection between internal and external systems using a state table 33
34
35
36
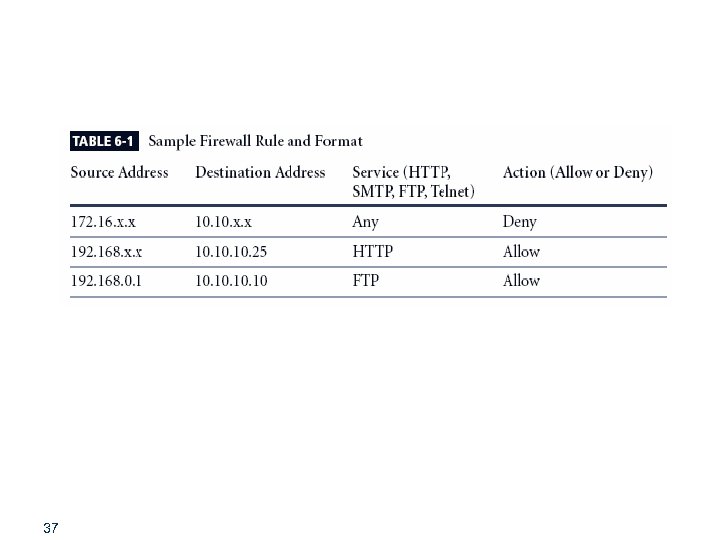
37
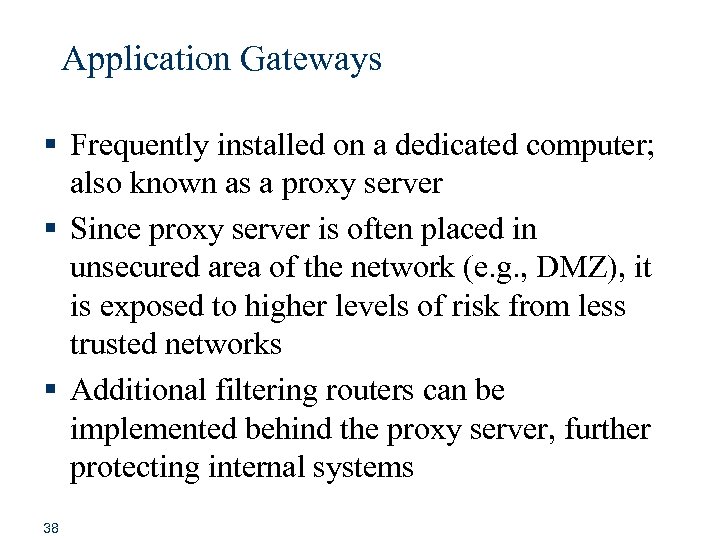
Application Gateways § Frequently installed on a dedicated computer; also known as a proxy server § Since proxy server is often placed in unsecured area of the network (e. g. , DMZ), it is exposed to higher levels of risk from less trusted networks § Additional filtering routers can be implemented behind the proxy server, further protecting internal systems 38
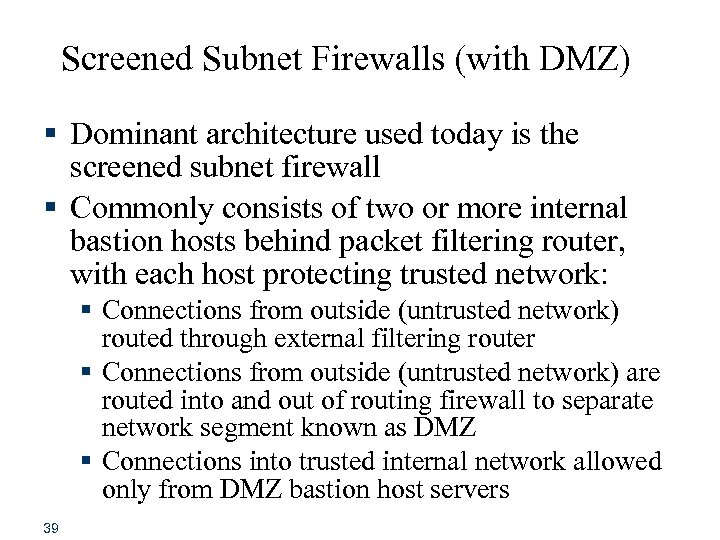
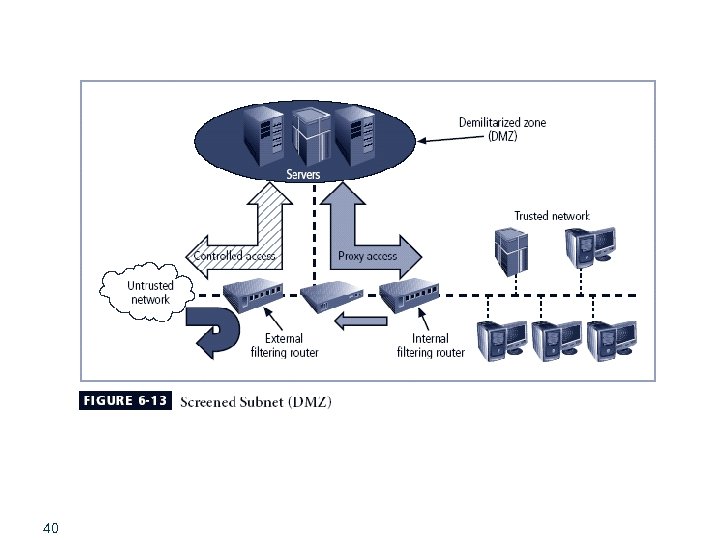
Screened Subnet Firewalls (with DMZ) § Dominant architecture used today is the screened subnet firewall § Commonly consists of two or more internal bastion hosts behind packet filtering router, with each host protecting trusted network: § Connections from outside (untrusted network) routed through external filtering router § Connections from outside (untrusted network) are routed into and out of routing firewall to separate network segment known as DMZ § Connections into trusted internal network allowed only from DMZ bastion host servers 39
40

Virtual Private Networks (VPNs) § Private and secure network connection between systems; uses data communication capability of unsecured and public network § Securely extends organization’s internal network connections to remote locations beyond trusted network 41
Virtual Private Networks (VPNs) (continued) § VPN must accomplish: § Encapsulation of incoming and outgoing data § Encryption of incoming and outgoing data § Authentication of remote computer and (perhaps) remote user as well 42
Transport Mode § § § Data within IP packet is encrypted, but header information is not Allows user to establish secure link directly with remote host, encrypting only data contents of packet Two popular uses: § § 43 End-to-end transport of encrypted data Remote access worker connects to office network over Internet by connecting to a VPN server on the perimeter
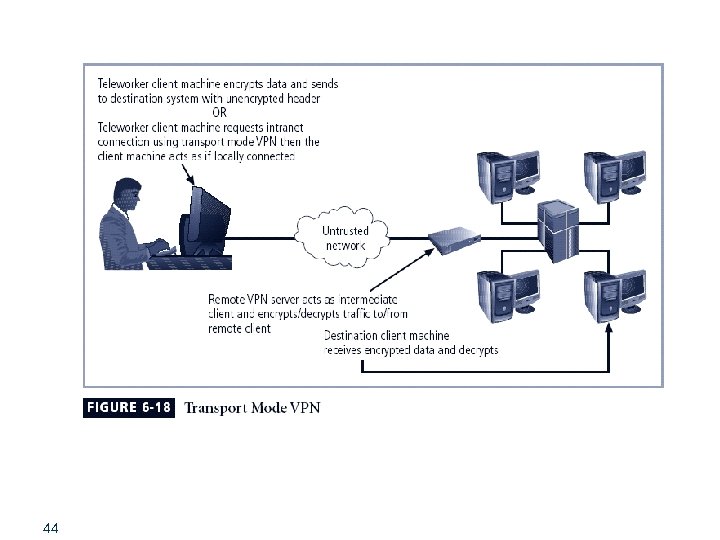
44
Tunnel Mode § Organization establishes two perimeter tunnel servers § These servers act as encryption points, encrypting all traffic that will traverse unsecured network § Primary benefit to this model is that an intercepted packet reveals nothing about true destination system § Example of tunnel mode VPN: Microsoft’s Internet Security and Acceleration (ISA) Server 45
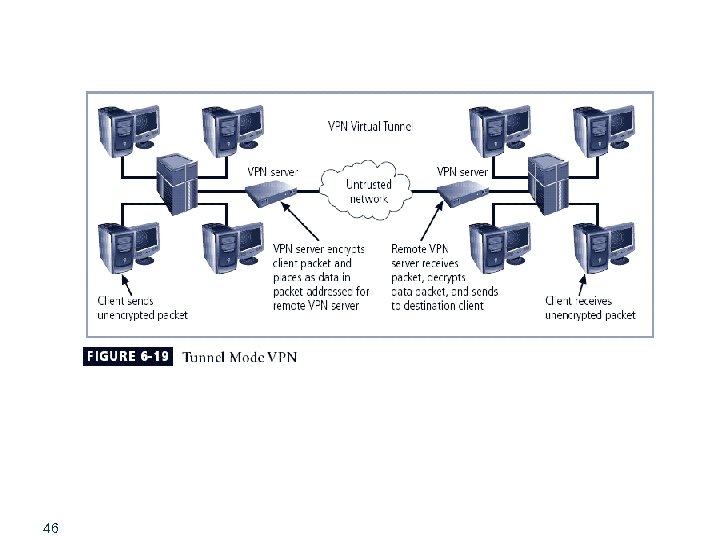
46
Summary of Firewalls and VPNs § Firewall technology § Four methods for categorization § Firewall configuration and management § Virtual Private Networks § Two modes 47
Defenses against Intrusion § Intrusion: type of attack on information assets in which instigator attempts to gain entry into or disrupt system with harmful intent § Intrusion detection: consists of procedures and systems created and operated to detect system intrusions § Intrusion reaction: encompasses actions an organization undertakes when intrusion event is detected § Intrusion correction activities: finalize restoration of operations to a normal state § Intrusion prevention: consists of activities that seek to deter an intrusion from occurring 48
Intrusion Detection Systems (IDSs) § Detects a violation of its configuration and activates alarm § Many IDSs enable administrators to configure systems to notify them directly of trouble via email or pagers § Systems can also be configured to notify an external security service organization of a “break-in” 49

IDS Terminology § Alert or alarm § False negative § The failure of an IDS system to react to an actual attack event. § False positive § An alarm or alert that indicates that an attack is in progress or that an attack has successfully occurred when in fact there was no such attack. § Confidence value § Alarm filtering 50
IDSs Classification § All IDSs use one of two detection methods: § Signature-based § Statistical anomaly-based § IDSs operate as: § network-based § host-based § application-based systems 51
Signature-Based IDS § Examine data traffic in search of patterns that match known signatures § Widely used because many attacks have clear and distinct signatures § Problem with this approach is that as new attack strategies are identified, the IDS’s database of signatures must be continually updated 52
Statistical Anomaly-Based IDS § The statistical anomaly-based IDS (stat IDS) or behavior-based IDS sample network activity to compare to traffic that is known to be normal § When measured activity is outside baseline parameters or clipping level, IDS will trigger an alert § IDS can detect new types of attacks § Requires much more overhead and processing capacity than signature-based § May generate many false positives 53
54
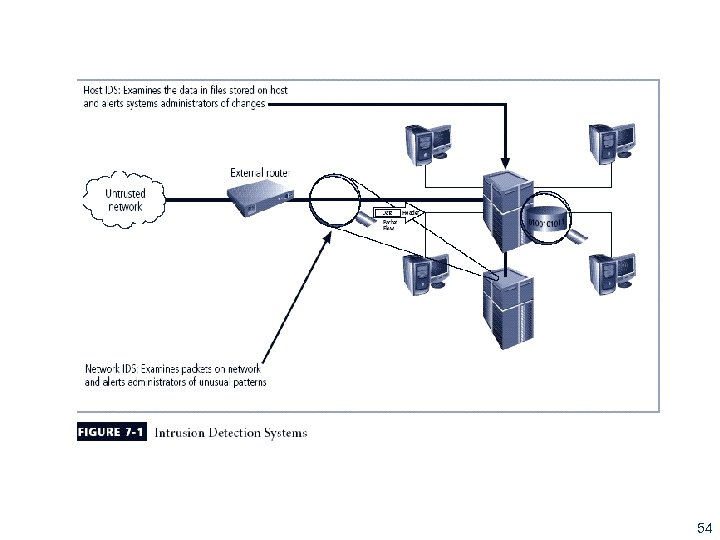
Network-Based IDS (NIDS) § Resides on computer or appliance connected to segment of an organization’s network; looks for signs of attacks § When examining packets, a NIDS looks for attack patterns § Installed at specific place in the network where it can watch traffic going into and out of particular network segment 55

Advantages and Disadvantages of NIDSs § Good network design and placement of NIDS can enable organization to use a few devices to monitor large network § NIDSs are usually passive and can be deployed into existing networks with little disruption to normal network operations § NIDSs not usually susceptible to direct attack and may not be detectable by attackers 56

Advantages and Disadvantages of NIDSs (continued) § Can become overwhelmed by network volume and fail to recognize attacks § Require access to all traffic to be monitored § Cannot analyze encrypted packets § Cannot reliably ascertain if attack was successful or not § Some forms of attack are not easily discerned by NIDSs, specifically those involving fragmented packets 57
Host-Based IDS § Host-based IDS (HIDS) resides on a particular computer or server and monitors activity only on that system § Benchmark and monitor the status of key system files and detect when intruder creates, modifies, or deletes files § Most HIDSs work on the principle of configuration or change management § Advantage over NIDS: can usually be installed so that it can access information encrypted when traveling over network 58
Advantages and Disadvantages of HIDSs § Can detect local events on host systems and detect attacks that may elude a network-based IDS § Functions on host system, where encrypted traffic will have been decrypted and is available for processing § Not affected by use of switched network protocols § Can detect inconsistencies in how applications and systems programs were used by examining records stored in audit logs 59
Advantages and Disadvantages of HIDSs (continued) § Pose more management issues § Vulnerable both to direct attacks and attacks against host operating system § Does not detect multi-host scanning, nor scanning of non-host network devices § Susceptible to some denial-of-service attacks § Can use large amounts of disk space § Can inflict a performance overhead on its host systems 60

Honey Pots, Honey Nets, and Padded Cell Systems § Honey pots: decoy systems designed to lure potential attackers away from critical systems and encourage attacks against themselves § Honey nets: collection of honey pots connecting several honey pot systems on a subnet § Honey pots designed to: § Divert attacker from accessing critical systems § Collect information about attacker’s activity § Encourage attacker to stay on system long enough for administrators to document event and, perhaps, respond 61

Outline of Network Security Basics § § What is Network Security? Threats and Attacks Defenses Cryptography 62

Cipher Methods § Plaintext can be encrypted through bit stream or block cipher method § Bit stream: each plaintext bit transformed into cipher bit one bit at a time § Block cipher: message divided into blocks (e. g. , sets of 8 - or 16 -bit blocks) and each is transformed into encrypted block of cipher bits using algorithm and key 63
Cipher Methods (continued) § Substitution cipher: substitute one value for another § Monoalphabetic substitution: uses only one alphabet § Polyalphabetic substitution: more advanced; uses two or more alphabets § Transposition cipher: rearranges values within a block to create ciphertext § Exclusive OR (XOR): function of Boolean algebra; two bits are compared § If two bits are identical, result is binary 0 § If two bits not identical, result is binary 1 64
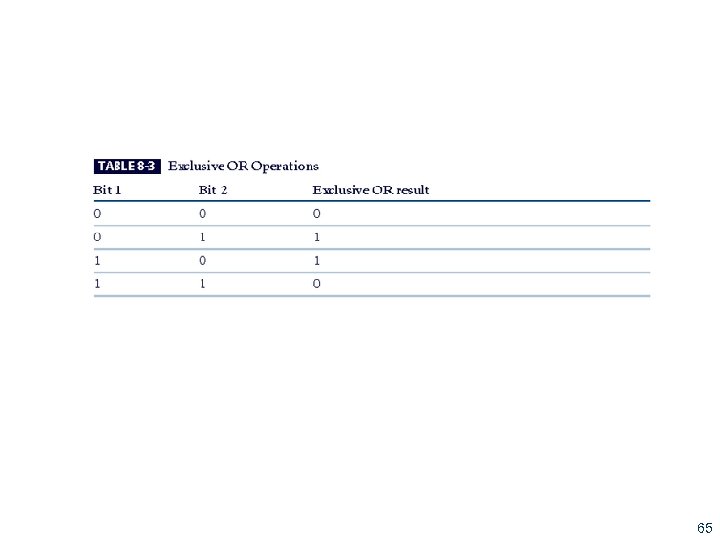
Table 8 -1 Exclusive OR Operations 65
Cryptographic Algorithms § Often grouped into two broad categories, symmetric and asymmetric; today’s popular cryptosystems use hybrid combination of symmetric and asymmetric algorithms § Symmetric and asymmetric algorithms distinguished by types of keys used for encryption and decryption operations 66

Cryptographic Algorithms (continued) § Symmetric encryption: uses same “secret key” to encipher and decipher message § Encryption methods can be extremely efficient, requiring minimal processing § Both sender and receiver must possess encryption key § If either copy of key is compromised, an intermediate can decrypt and read messages 67
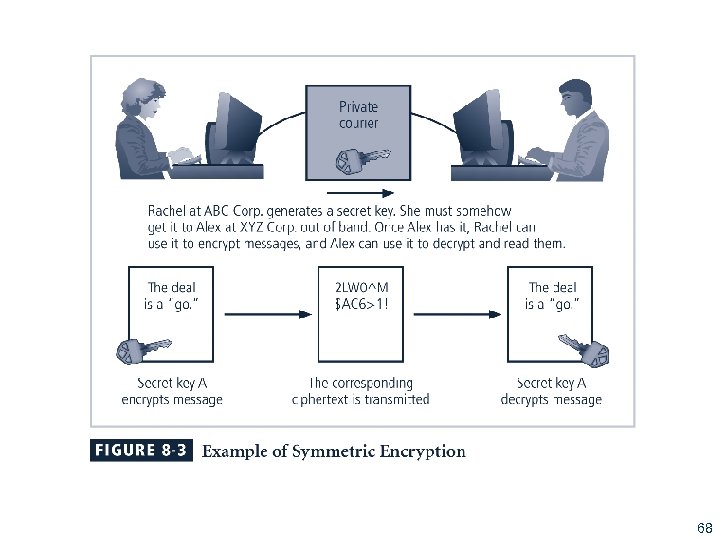
Figure 8 -3 Symmetric Encryption Example 68
Cryptographic Algorithms (continued) § Data Encryption Standard (DES): one of most popular symmetric encryption cryptosystems § 64 -bit block size; 56 -bit key § Adopted by NIST in 1976 as federal standard for encrypting non-classified information § Triple DES (3 DES): created to provide security far beyond DES § Advanced Encryption Standard (AES): developed to replace both DES and 3 DES 69
Cryptographic Algorithms (continued) § Asymmetric Encryption (public key encryption) § Uses two different but related keys; either key can encrypt or decrypt message § If Key A encrypts message, only Key B can decrypt § Highest value when one key serves as private key and the other serves as public key 70
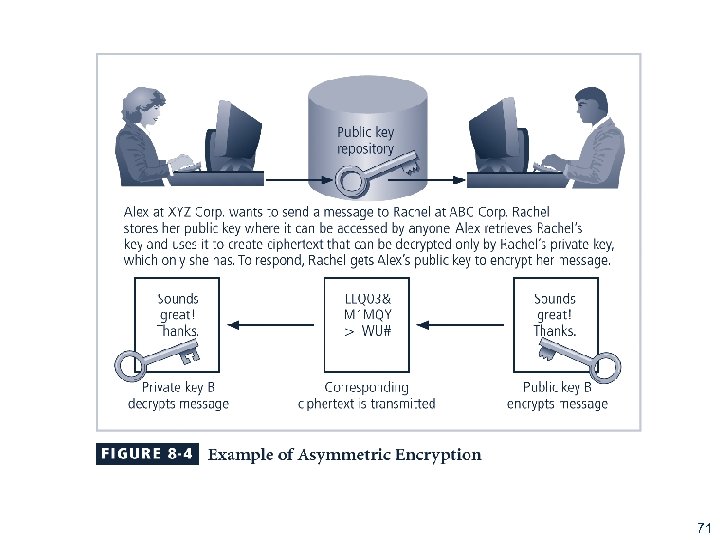
Figure 8 -4 Using Public Keys 71
![Symmetric Key Crypto: DES: Data Encryption Standard § § US encryption standard [NIST 1993] Symmetric Key Crypto: DES: Data Encryption Standard § § US encryption standard [NIST 1993]](https://present5.com/presentation/43f4422439d49807f9887d19a4abca40/image-72.jpg)
Symmetric Key Crypto: DES: Data Encryption Standard § § US encryption standard [NIST 1993] 56 -bit symmetric key, 64 -bit plaintext input Block cipher with cipher block chaining How secure is DES? § DES Challenge: 56 -bit-key-encrypted phrase decrypted (brute force) in less than a day § No known good analytic attack § To make DES more secure: § 3 DES: encrypt 3 times with 3 different keys 72
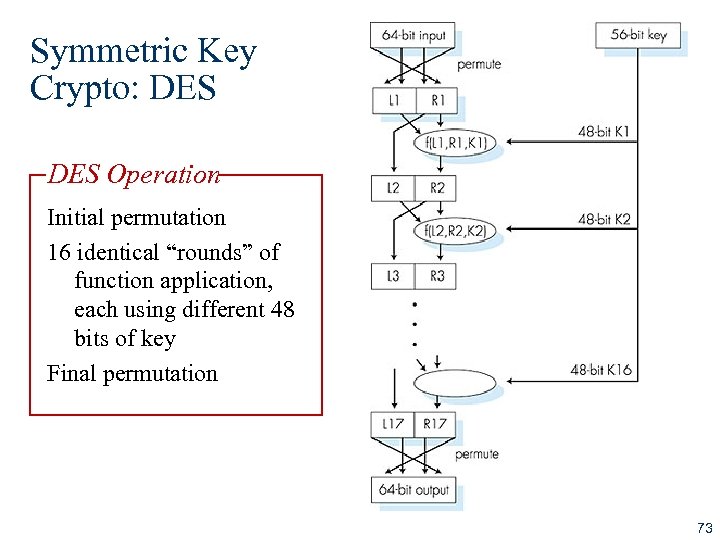
Symmetric Key Crypto: DES Operation Initial permutation 16 identical “rounds” of function application, each using different 48 bits of key Final permutation 73

AES: Advanced Encryption Standard § Symmetric-key NIST standard, replaced DES (Nov 2001) § Processes data in 128 bit blocks § 128, 192, or 256 bit keys § Brute force decryption (try each key) taking 1 sec on DES, takes 149 trillion years for AES 74
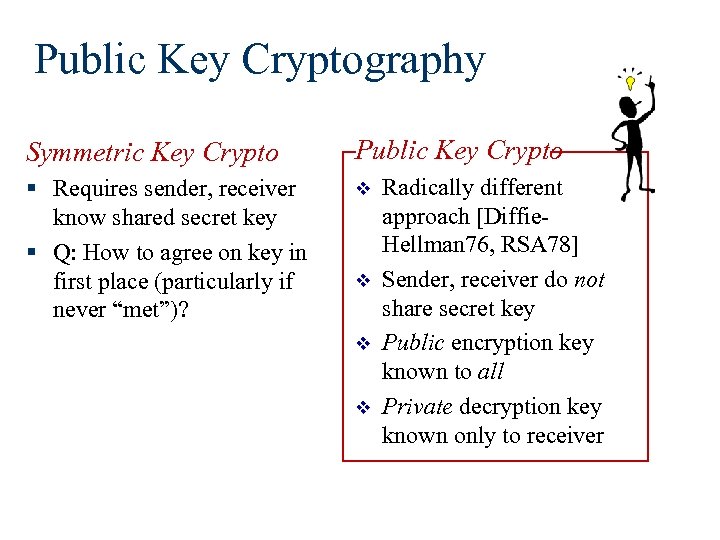
Public Key Cryptography Symmetric Key Crypto Public Key Crypto § Requires sender, receiver know shared secret key § Q: How to agree on key in first place (particularly if never “met”)? v v Radically different approach [Diffie. Hellman 76, RSA 78] Sender, receiver do not share secret key Public encryption key known to all Private decryption key known only to receiver
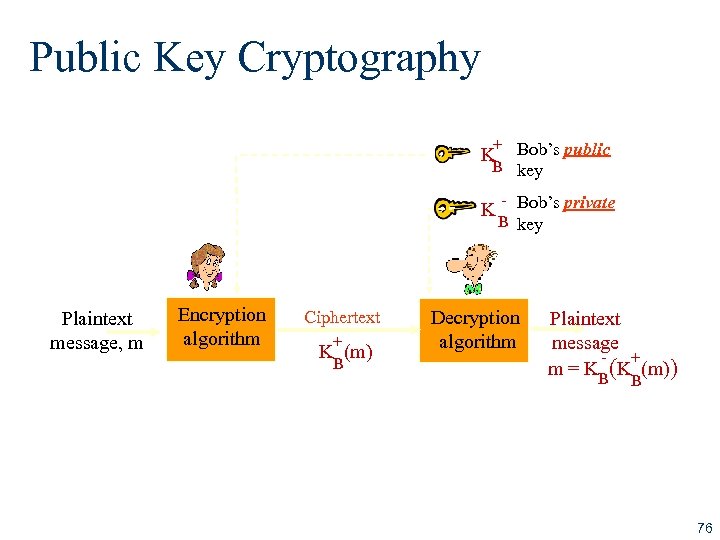
Public Key Cryptography + K Bob’s public B key K Bob’s private B key Plaintext message, m Encryption algorithm Ciphertext + B K (m) Decryption algorithm Plaintext message + m = K (K (m)) B B 76
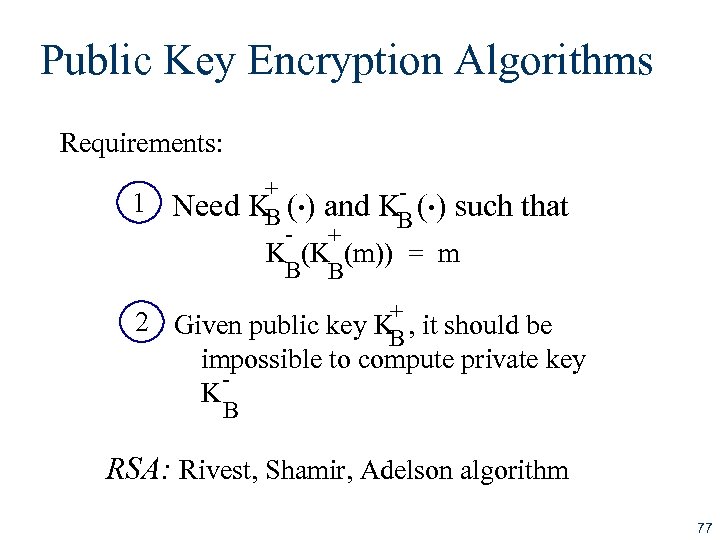
Public Key Encryption Algorithms Requirements: 1 . . + Need K ( ) and K ( ) such that B B - + K (K (m)) = m B B + 2 Given public key K , it should be B impossible to compute private key K B RSA: Rivest, Shamir, Adelson algorithm 77
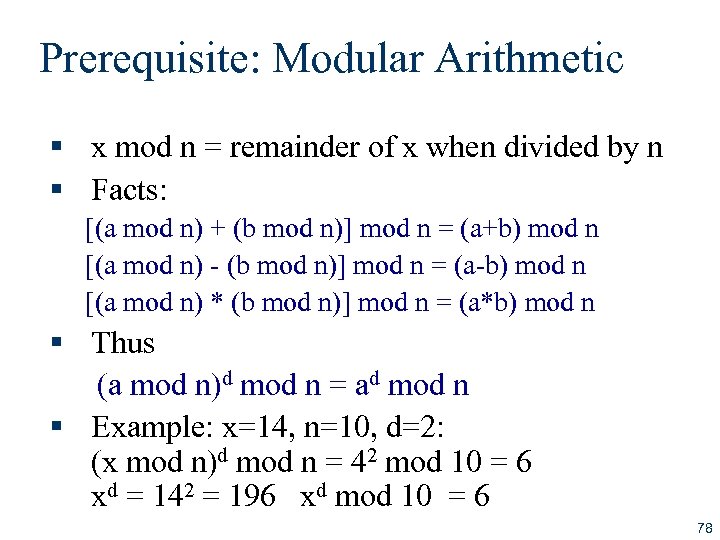
Prerequisite: Modular Arithmetic § x mod n = remainder of x when divided by n § Facts: [(a mod n) + (b mod n)] mod n = (a+b) mod n [(a mod n) - (b mod n)] mod n = (a-b) mod n [(a mod n) * (b mod n)] mod n = (a*b) mod n § Thus (a mod n)d mod n = ad mod n § Example: x=14, n=10, d=2: (x mod n)d mod n = 42 mod 10 = 6 xd = 142 = 196 xd mod 10 = 6 78

RSA: Getting Ready § Message: just a bit pattern § Bit pattern can be uniquely represented by an integer number § Thus, encrypting a message is equivalent to encrypting a number. Example: § m=10010001. This message is uniquely represented by the decimal number 145. § To encrypt m, we encrypt the corresponding number, which gives a new number (the ciphertext). 79
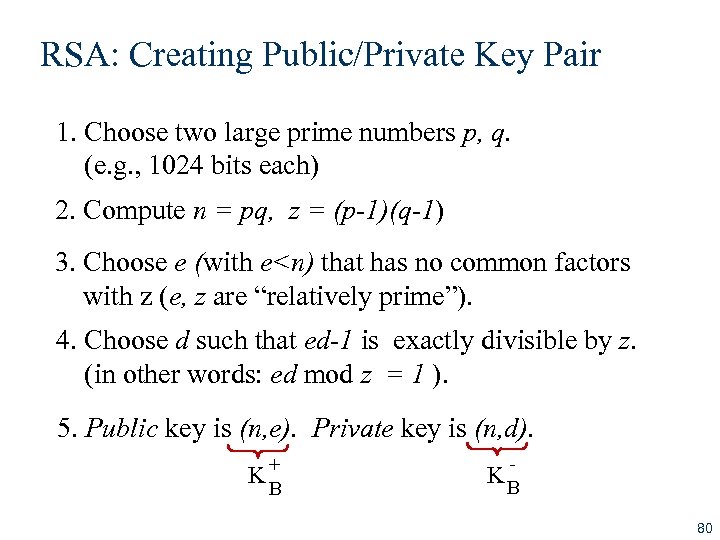
RSA: Creating Public/Private Key Pair 1. Choose two large prime numbers p, q. (e. g. , 1024 bits each) 2. Compute n = pq, z = (p-1)(q-1) 3. Choose e (with e<n) that has no common factors with z (e, z are “relatively prime”). 4. Choose d such that ed-1 is exactly divisible by z. (in other words: ed mod z = 1 ). 5. Public key is (n, e). Private key is (n, d). + K B - K B 80
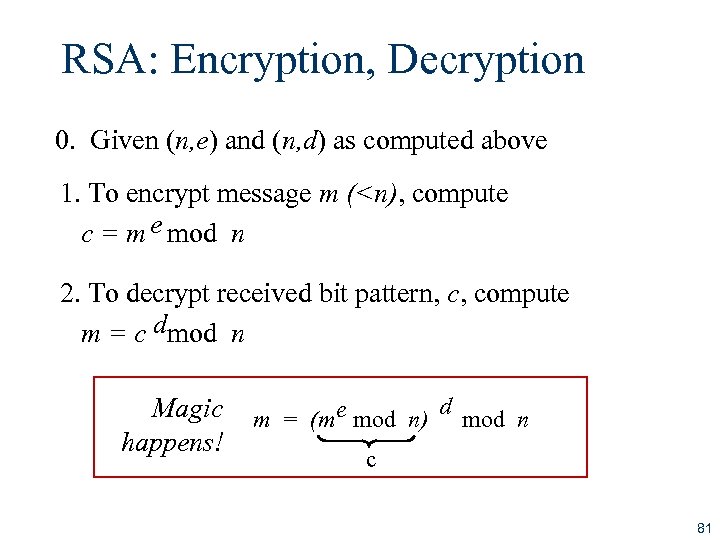
RSA: Encryption, Decryption 0. Given (n, e) and (n, d) as computed above 1. To encrypt message m (<n), compute c = m e mod n 2. To decrypt received bit pattern, c, compute m = c dmod n Magic happens! m = (me mod n) d mod n c 81
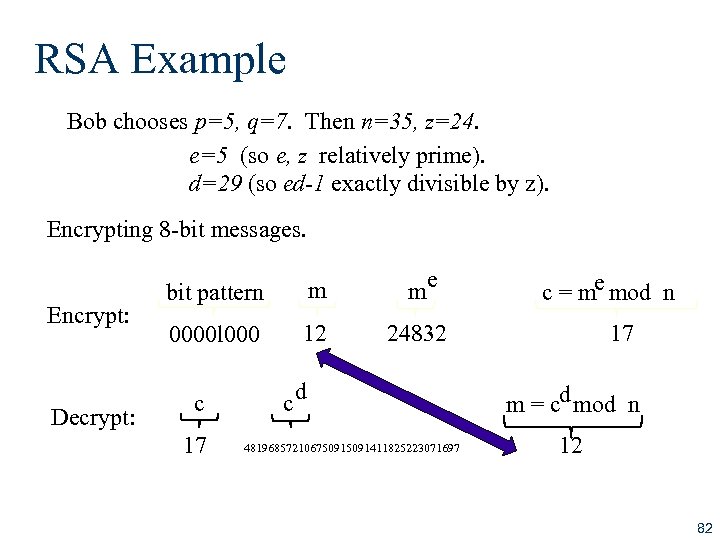
RSA Example Bob chooses p=5, q=7. Then n=35, z=24. e=5 (so e, z relatively prime). d=29 (so ed-1 exactly divisible by z). Encrypting 8 -bit messages. Encrypt: Decrypt: bit pattern m me 0000 l 000 12 24832 c 17 c d 48196857210675091411825223071697 e c = m mod n 17 d m = c mod n 12 82

Why Does RSA Work? § Must show that cd mod n = m where c = me mod n § Fact: for any x and y: xy mod n = x(y mod z) mod n § where n= pq and z = (p-1)(q-1) § Thus, cd mod n = (me mod n)d mod n = med mod n = m(ed mod z) mod n = m 1 mod n = m 83
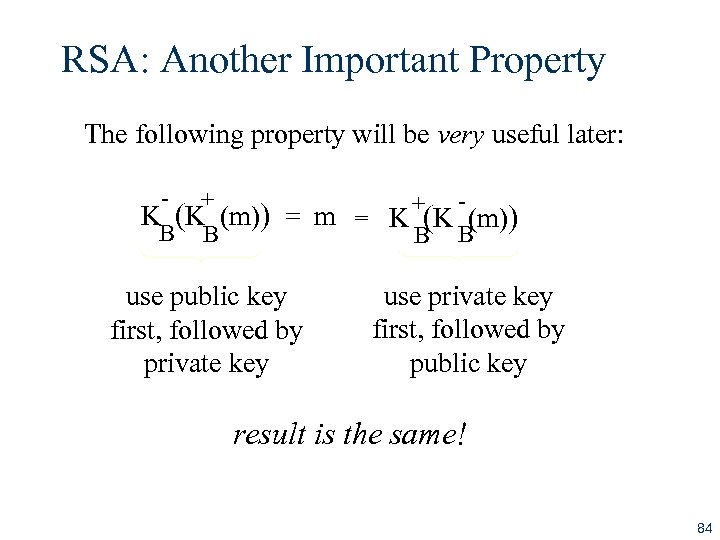
RSA: Another Important Property The following property will be very useful later: - + + K (K (m)) = m = K (K (m)) B B use public key first, followed by private key use private key first, followed by public key result is the same! 84
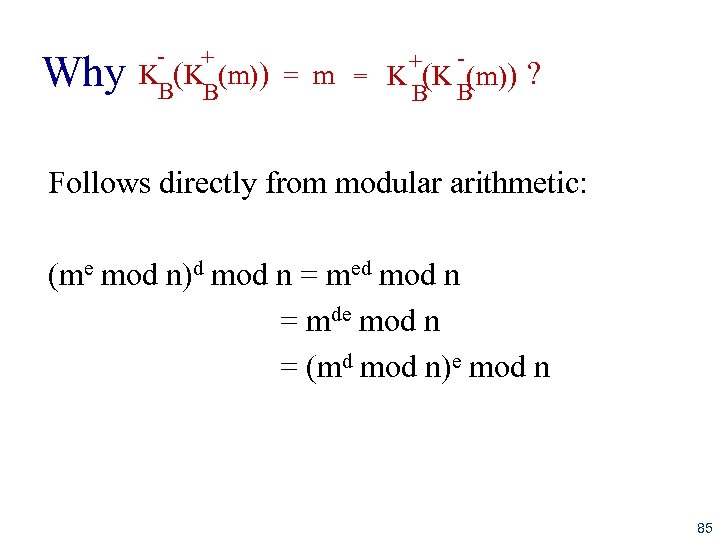
Why - + + K (K (m)) = m = K (K (m)) ? B B Follows directly from modular arithmetic: (me mod n)d mod n = med mod n = mde mod n = (md mod n)e mod n 85

Why Is RSA Secure? § Suppose you know Bob’s public key (n, e). How hard is it to determine d? § Essentially need to find factors of n without knowing the two factors p and q § Fact: Factoring a big number is hard 86

RSA In Practice: Session Keys § Exponentiation in RSA is computationally intensive § DES is at least 100 times faster than RSA § Use public key crypto to establish secure connection, then establish second key – symmetric session key – for encrypting data Session key, KS § Bob and Alice use RSA to exchange a symmetric key KS § Once both have KS, they use symmetric key cryptography 87

Cryptography Tools § Public Key Infrastructure (PKI): integrated system of software, encryption methodologies, protocols, legal agreements, and third-party services enabling users to communicate securely § PKI systems based on public key cryptosystems; include digital certificates and certificate authorities (CAs) 88

Digital Signatures § Encrypted messages that can be mathematically proven to be authentic § Created in response to rising need to verify information transferred using electronic systems § Asymmetric encryption processes used to create digital signatures 89

Digital Certificates § Electronic document containing key value and identifying information about entity that controls key § Digital signature attached to certificate’s container file to certify file is from entity it claims to be from 90
Figure 8 -5 Digital Signatures 91

Summary of Cryptography § Cryptography and encryption provide sophisticated approach to security § Many security-related tools use embedded encryption technologies § Encryption converts a message into a form that is unreadable by the unauthorized § Many tools are available and can be classified as symmetric or asymmetric, each having advantages and special capabilities 92

Acknowledgement These slides are partially from our course reference texts: James Kurose and Keith Ross, Computer Networking: A Top-Down Approach Featuring the Internet, Addison Wesley, 2010, ISBN 13: 978 -0 -13 -607967 -5 (5 th edition or later) Michael E. Whitman and Herbert J. Mattord, Principles of Information Security, Thomson/Course Technology, ISBN 0 -619 -21625 -5, Fourth Edition, 2012 93
43f4422439d49807f9887d19a4abca40.ppt