f9034b19c8822124811892482f379ed1.ppt
- Количество слайдов: 30
 Network security and Hot topics in networking EECS 489 Computer Networks http: //www. eecs. umich. edu/courses/eecs 489/w 07 Z. Morley Mao Wednesday, April 11, 2007
Network security and Hot topics in networking EECS 489 Computer Networks http: //www. eecs. umich. edu/courses/eecs 489/w 07 Z. Morley Mao Wednesday, April 11, 2007
 Announcements r Agenda today: m Icecream to celebrate almost finishing EECS 489 m Finish up network security m Where to go from here? Hot topics in networks. m Course evaluation (need volunteer) r Practice final is posted (announcement page) m Solution available next Monday r Mandatory PA 3 Demo: m Starting Thursday (4/12), last day is Friday (4/20), signup available. r Next Monday 4/16 m Course summary and review for final r Final exam: 4/19
Announcements r Agenda today: m Icecream to celebrate almost finishing EECS 489 m Finish up network security m Where to go from here? Hot topics in networks. m Course evaluation (need volunteer) r Practice final is posted (announcement page) m Solution available next Monday r Mandatory PA 3 Demo: m Starting Thursday (4/12), last day is Friday (4/20), signup available. r Next Monday 4/16 m Course summary and review for final r Final exam: 4/19
 Chapter 8 roadmap 8. 1 What is network security? 8. 2 Principles of cryptography 8. 3 Authentication 8. 4 Integrity 8. 5 Key Distribution and certification 8. 6 Access control: firewalls 8. 7 Attacks and counter measures 8. 8 Security in many layers 8. 8. 1. Secure email 8. 8. 2. Secure sockets 8. 8. 3. IPsec 8. 8. 4. Security in 802. 11
Chapter 8 roadmap 8. 1 What is network security? 8. 2 Principles of cryptography 8. 3 Authentication 8. 4 Integrity 8. 5 Key Distribution and certification 8. 6 Access control: firewalls 8. 7 Attacks and counter measures 8. 8 Security in many layers 8. 8. 1. Secure email 8. 8. 2. Secure sockets 8. 8. 3. IPsec 8. 8. 4. Security in 802. 11
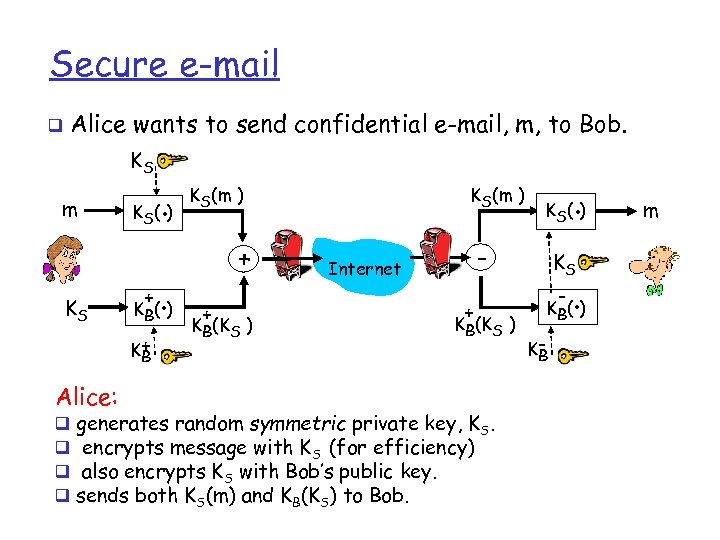 Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Alice: q q . K B( ) KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and KB(KS) to Bob. KS - . K B( ) KB m
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Alice: q q . K B( ) KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) generates random symmetric private key, KS. encrypts message with KS (for efficiency) also encrypts KS with Bob’s public key. sends both KS(m) and KB(KS) to Bob. KS - . K B( ) KB m
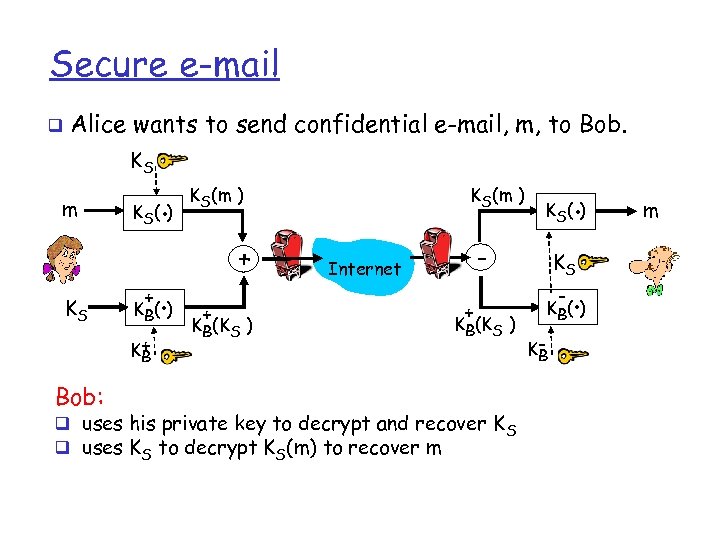 Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Bob: . K B( ) KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m KS - . K B( ) KB m
Secure e-mail q Alice wants to send confidential e-mail, m, to Bob. KS m KS K (. ) S + K+ B Bob: . K B( ) KS(m ) + + KB(KS ) . K S( ) - Internet + KB(KS ) q uses his private key to decrypt and recover K S q uses KS to decrypt KS(m) to recover m KS - . K B( ) KB m
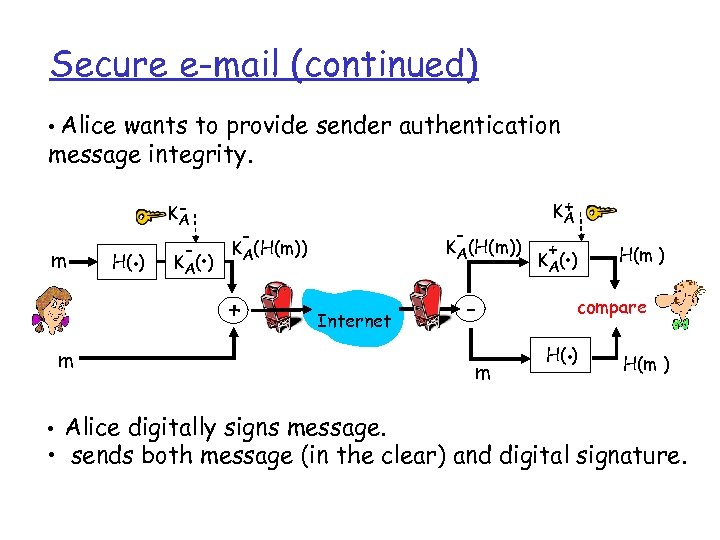 Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m • Alice digitally signs message. m + . K A( ) H(m ) compare . H( ) H(m ) • sends both message (in the clear) and digital signature.
Secure e-mail (continued) • Alice wants to provide sender authentication message integrity. m H(. ) KA - . K A( ) - - KA(H(m)) + + KA Internet m • Alice digitally signs message. m + . K A( ) H(m ) compare . H( ) H(m ) • sends both message (in the clear) and digital signature.
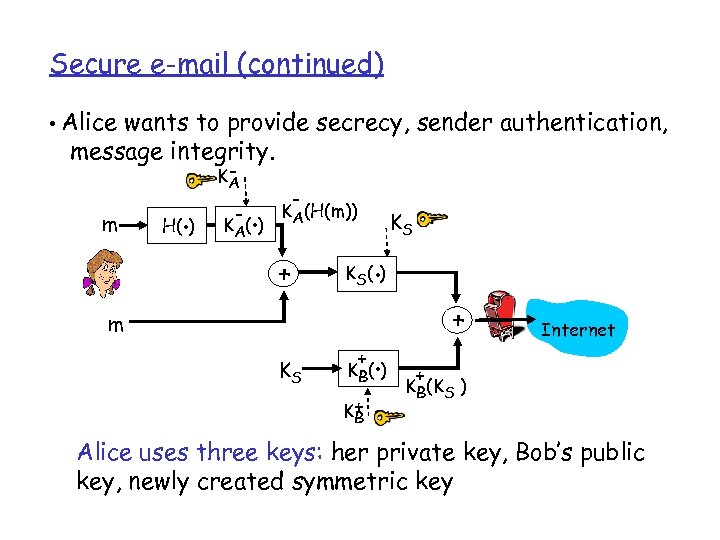 Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key
Secure e-mail (continued) • Alice wants to provide secrecy, sender authentication, message integrity. m . H( ) KA - . K A( ) - KA(H(m)) + . K S( ) m KS KS + . K B( ) K+ B + Internet + KB(KS ) Alice uses three keys: her private key, Bob’s public key, newly created symmetric key
 Pretty good privacy (PGP) r Internet e-mail encryption scheme, defacto standard. r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r provides secrecy, sender authentication, integrity. r inventor, Phil Zimmerman, was target of 3 -year federal investigation due to US export regulations. A PGP signed message: ---BEGIN PGP SIGNED MESSAGE-Hash: SHA 1 Alice: I developed a new worm that can exploit the zeroday flaw on Windows Vista. Bob ---BEGIN PGP SIGNATURE--Version: PGP 5. 0 Charset: noconv yh. HJRHh. GJGhgg/12 Ep. J+lo 8 g. E 4 v. B 3 mq. Jh. FEv. ZP 9 t 6 n 7 G 6 m 5 Gw 2 ---END PGP SIGNATURE---
Pretty good privacy (PGP) r Internet e-mail encryption scheme, defacto standard. r uses symmetric key cryptography, public key cryptography, hash function, and digital signature as described. r provides secrecy, sender authentication, integrity. r inventor, Phil Zimmerman, was target of 3 -year federal investigation due to US export regulations. A PGP signed message: ---BEGIN PGP SIGNED MESSAGE-Hash: SHA 1 Alice: I developed a new worm that can exploit the zeroday flaw on Windows Vista. Bob ---BEGIN PGP SIGNATURE--Version: PGP 5. 0 Charset: noconv yh. HJRHh. GJGhgg/12 Ep. J+lo 8 g. E 4 v. B 3 mq. Jh. FEv. ZP 9 t 6 n 7 G 6 m 5 Gw 2 ---END PGP SIGNATURE---
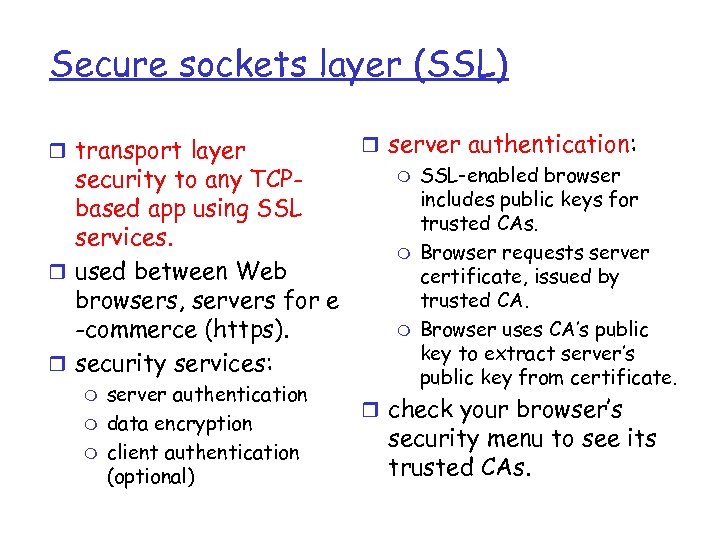 Secure sockets layer (SSL) r transport layer security to any TCPbased app using SSL services. r used between Web browsers, servers for e -commerce (https). r security services: m m m server authentication data encryption client authentication (optional) r server authentication: m SSL-enabled browser includes public keys for trusted CAs. m Browser requests server certificate, issued by trusted CA. m Browser uses CA’s public key to extract server’s public key from certificate. r check your browser’s security menu to see its trusted CAs.
Secure sockets layer (SSL) r transport layer security to any TCPbased app using SSL services. r used between Web browsers, servers for e -commerce (https). r security services: m m m server authentication data encryption client authentication (optional) r server authentication: m SSL-enabled browser includes public keys for trusted CAs. m Browser requests server certificate, issued by trusted CA. m Browser uses CA’s public key to extract server’s public key from certificate. r check your browser’s security menu to see its trusted CAs.
 SSL (continued) Encrypted SSL session: r Browser generates symmetric session key, encrypts it with server’s public key, sends encrypted key to server. r Using private key, server decrypts session key. r Browser, server know session key m All data sent into TCP socket (by client or server) encrypted with session key. r SSL: basis of IETF Transport Layer Security (TLS). r SSL can be used for non-Web applications, e. g. , IMAP. r Client authentication can be done with client certificates.
SSL (continued) Encrypted SSL session: r Browser generates symmetric session key, encrypts it with server’s public key, sends encrypted key to server. r Using private key, server decrypts session key. r Browser, server know session key m All data sent into TCP socket (by client or server) encrypted with session key. r SSL: basis of IETF Transport Layer Security (TLS). r SSL can be used for non-Web applications, e. g. , IMAP. r Client authentication can be done with client certificates.
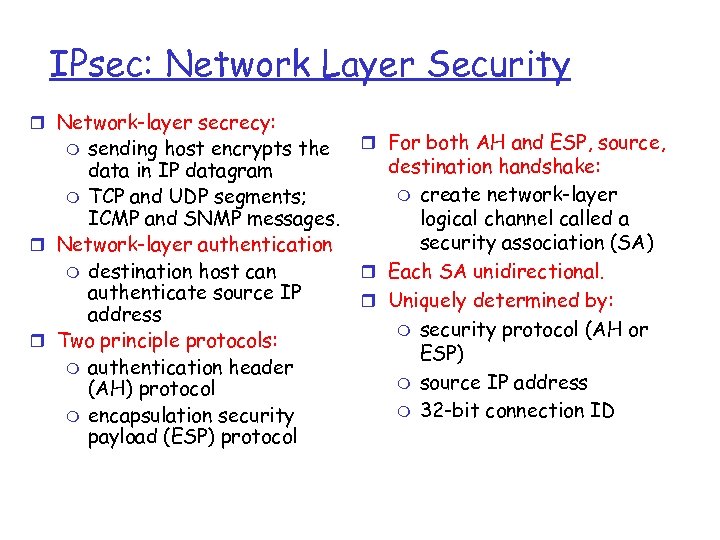 IPsec: Network Layer Security r Network-layer secrecy: sending host encrypts the data in IP datagram m TCP and UDP segments; ICMP and SNMP messages. r Network-layer authentication m destination host can authenticate source IP address r Two principle protocols: m authentication header (AH) protocol m encapsulation security payload (ESP) protocol m r For both AH and ESP, source, destination handshake: m create network-layer logical channel called a security association (SA) r Each SA unidirectional. r Uniquely determined by: m security protocol (AH or ESP) m source IP address m 32 -bit connection ID
IPsec: Network Layer Security r Network-layer secrecy: sending host encrypts the data in IP datagram m TCP and UDP segments; ICMP and SNMP messages. r Network-layer authentication m destination host can authenticate source IP address r Two principle protocols: m authentication header (AH) protocol m encapsulation security payload (ESP) protocol m r For both AH and ESP, source, destination handshake: m create network-layer logical channel called a security association (SA) r Each SA unidirectional. r Uniquely determined by: m security protocol (AH or ESP) m source IP address m 32 -bit connection ID
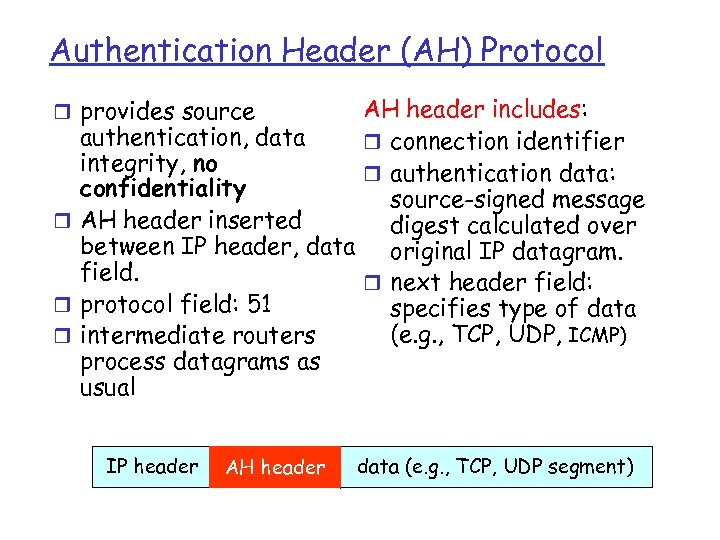 Authentication Header (AH) Protocol AH header includes: authentication, data r connection identifier integrity, no r authentication data: confidentiality source-signed message r AH header inserted digest calculated over between IP header, data original IP datagram. field. r next header field: r protocol field: 51 specifies type of data (e. g. , TCP, UDP, ICMP) r intermediate routers process datagrams as usual r provides source IP header AH header data (e. g. , TCP, UDP segment)
Authentication Header (AH) Protocol AH header includes: authentication, data r connection identifier integrity, no r authentication data: confidentiality source-signed message r AH header inserted digest calculated over between IP header, data original IP datagram. field. r next header field: r protocol field: 51 specifies type of data (e. g. , TCP, UDP, ICMP) r intermediate routers process datagrams as usual r provides source IP header AH header data (e. g. , TCP, UDP segment)
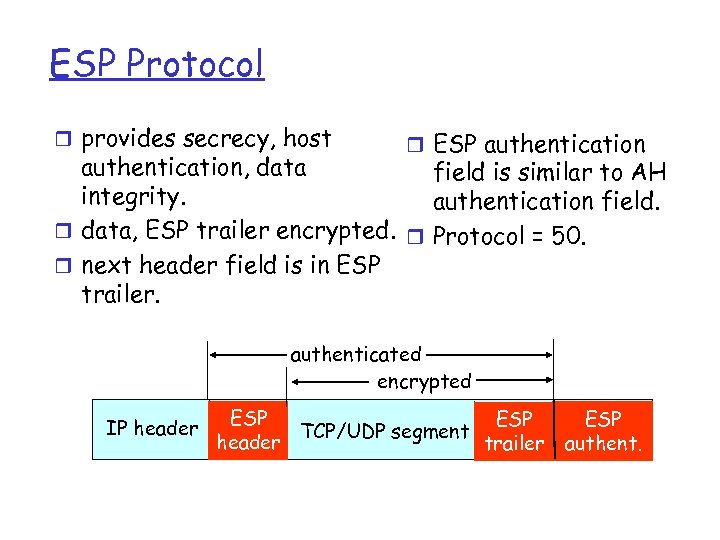 ESP Protocol r provides secrecy, host r ESP authentication, data field is similar to AH integrity. authentication field. r data, ESP trailer encrypted. r Protocol = 50. r next header field is in ESP trailer. authenticated encrypted IP header ESP TCP/UDP segment header trailer ESP authent.
ESP Protocol r provides secrecy, host r ESP authentication, data field is similar to AH integrity. authentication field. r data, ESP trailer encrypted. r Protocol = 50. r next header field is in ESP trailer. authenticated encrypted IP header ESP TCP/UDP segment header trailer ESP authent.
 IEEE 802. 11 security r War-driving: drive around Bay Area, see what 802. 11 networks available? m More than 9000 accessible from public roadways m 85% use no encryption/authentication m packet-sniffing and various attacks easy! r Securing 802. 11 m encryption, authentication m first attempt at 802. 11 security: Wired Equivalent Privacy (WEP): a failure m current attempt: 802. 11 i
IEEE 802. 11 security r War-driving: drive around Bay Area, see what 802. 11 networks available? m More than 9000 accessible from public roadways m 85% use no encryption/authentication m packet-sniffing and various attacks easy! r Securing 802. 11 m encryption, authentication m first attempt at 802. 11 security: Wired Equivalent Privacy (WEP): a failure m current attempt: 802. 11 i
 Wired Equivalent Privacy (WEP): r authentication as in protocol ap 4. 0 m host requests authentication from access point sends 128 bit nonce m host encrypts nonce using shared symmetric key m access point decrypts nonce, authenticates host r no key distribution mechanism r authentication: knowing the shared key is enough
Wired Equivalent Privacy (WEP): r authentication as in protocol ap 4. 0 m host requests authentication from access point sends 128 bit nonce m host encrypts nonce using shared symmetric key m access point decrypts nonce, authenticates host r no key distribution mechanism r authentication: knowing the shared key is enough
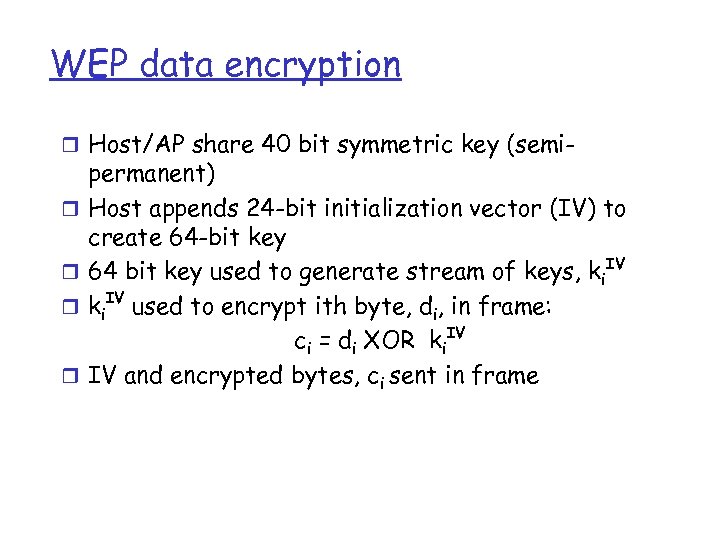 WEP data encryption r Host/AP share 40 bit symmetric key (semir r permanent) Host appends 24 -bit initialization vector (IV) to create 64 -bit key 64 bit key used to generate stream of keys, ki. IV used to encrypt ith byte, di, in frame: ci = di XOR ki. IV IV and encrypted bytes, ci sent in frame
WEP data encryption r Host/AP share 40 bit symmetric key (semir r permanent) Host appends 24 -bit initialization vector (IV) to create 64 -bit key 64 bit key used to generate stream of keys, ki. IV used to encrypt ith byte, di, in frame: ci = di XOR ki. IV IV and encrypted bytes, ci sent in frame
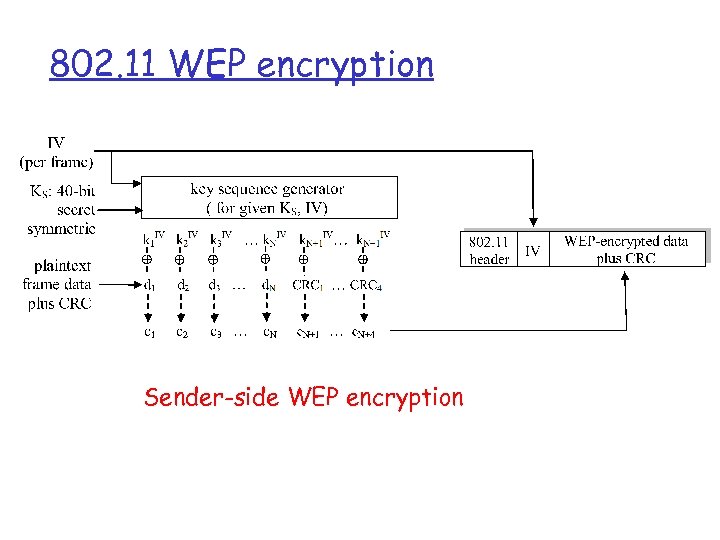 802. 11 WEP encryption Sender-side WEP encryption
802. 11 WEP encryption Sender-side WEP encryption
 Breaking 802. 11 WEP encryption Security hole: r 24 -bit IV, one IV per frame, -> IV’s eventually reused r IV transmitted in plaintext -> IV reuse detected r Attack: m Trudy causes Alice to encrypt known plaintext d 1 d 2 d 3 d 4 … IV m Trudy sees: ci = di XOR ki knows ci di, so can compute ki. IV IV m Trudy knows encrypting key sequence k 1 k 2 k 3 … m Next time IV is used, Trudy can decrypt! m Trudy
Breaking 802. 11 WEP encryption Security hole: r 24 -bit IV, one IV per frame, -> IV’s eventually reused r IV transmitted in plaintext -> IV reuse detected r Attack: m Trudy causes Alice to encrypt known plaintext d 1 d 2 d 3 d 4 … IV m Trudy sees: ci = di XOR ki knows ci di, so can compute ki. IV IV m Trudy knows encrypting key sequence k 1 k 2 k 3 … m Next time IV is used, Trudy can decrypt! m Trudy
 802. 11 i: improved security r numerous (stronger) forms of encryption possible r provides key distribution r uses authentication server separate from access point r Wi-Fi Protected Access (WPA) m implements the majority of this standard
802. 11 i: improved security r numerous (stronger) forms of encryption possible r provides key distribution r uses authentication server separate from access point r Wi-Fi Protected Access (WPA) m implements the majority of this standard
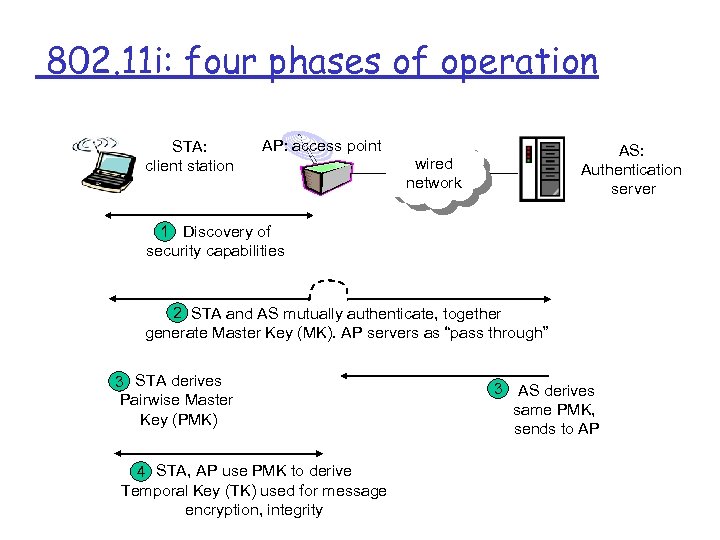 802. 11 i: four phases of operation STA: client station AP: access point AS: Authentication server wired network 1 Discovery of security capabilities 2 STA and AS mutually authenticate, together generate Master Key (MK). AP servers as “pass through” 3 STA derives Pairwise Master Key (PMK) 4 STA, AP use PMK to derive Temporal Key (TK) used for message encryption, integrity 3 AS derives same PMK, sends to AP
802. 11 i: four phases of operation STA: client station AP: access point AS: Authentication server wired network 1 Discovery of security capabilities 2 STA and AS mutually authenticate, together generate Master Key (MK). AP servers as “pass through” 3 STA derives Pairwise Master Key (PMK) 4 STA, AP use PMK to derive Temporal Key (TK) used for message encryption, integrity 3 AS derives same PMK, sends to AP
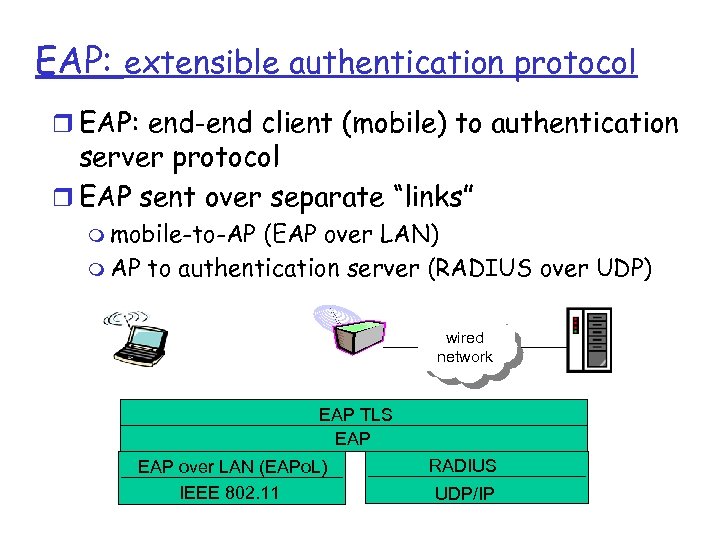 EAP: extensible authentication protocol r EAP: end-end client (mobile) to authentication server protocol r EAP sent over separate “links” m mobile-to-AP (EAP over LAN) m AP to authentication server (RADIUS over UDP) wired network EAP TLS EAP over LAN (EAPo. L) IEEE 802. 11 RADIUS UDP/IP
EAP: extensible authentication protocol r EAP: end-end client (mobile) to authentication server protocol r EAP sent over separate “links” m mobile-to-AP (EAP over LAN) m AP to authentication server (RADIUS over UDP) wired network EAP TLS EAP over LAN (EAPo. L) IEEE 802. 11 RADIUS UDP/IP
 SSH (rfc 4251) r Establishes a secure channel between a local and remote computer r Uses public-key crypto to authenticate remote host and user r Provides confidentiality, integrity r Authentication m Password-based m Public-key based • Public and private key pair generation using ssh-keygen
SSH (rfc 4251) r Establishes a secure channel between a local and remote computer r Uses public-key crypto to authenticate remote host and user r Provides confidentiality, integrity r Authentication m Password-based m Public-key based • Public and private key pair generation using ssh-keygen
 Host keys r ssh liberty. eecs. umich. edu r @@@@@@@@@@@@@@@@@@@ r r r r @@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is 00: 61: 14: 7 c: 76: 02: 5 a: 94: 42: a 1: 8 e: ce: e 1: ef: d 7: 9 a. Please contact your system administrator. Add correct host key in /n/edinburgh/x/zmao/. ssh/known_hosts to get rid of this message. Offending key in /n/edinburgh/x/zmao/. ssh/known_hosts: 276 Password authentication is disabled to avoid man-in-the-middle attacks. Keyboard-interactive authentication is disabled to avoid man-in-the-middle attacks. Enter passphrase for key '/n/edinburgh/x/zmao/. ssh/id_rsa':
Host keys r ssh liberty. eecs. umich. edu r @@@@@@@@@@@@@@@@@@@ r r r r @@@@@@@@@@@ @ WARNING: REMOTE HOST IDENTIFICATION HAS CHANGED! @ @@@@@@@@@@@@@@@@@@@ IT IS POSSIBLE THAT SOMEONE IS DOING SOMETHING NASTY! Someone could be eavesdropping on you right now (man-in-the-middle attack)! It is also possible that the RSA host key has just been changed. The fingerprint for the RSA key sent by the remote host is 00: 61: 14: 7 c: 76: 02: 5 a: 94: 42: a 1: 8 e: ce: e 1: ef: d 7: 9 a. Please contact your system administrator. Add correct host key in /n/edinburgh/x/zmao/. ssh/known_hosts to get rid of this message. Offending key in /n/edinburgh/x/zmao/. ssh/known_hosts: 276 Password authentication is disabled to avoid man-in-the-middle attacks. Keyboard-interactive authentication is disabled to avoid man-in-the-middle attacks. Enter passphrase for key '/n/edinburgh/x/zmao/. ssh/id_rsa':
 One time password RSA Secur. ID tokens (has a built-in accurate clock) r Opposite of static passwords m constantly altering passwords r Password generation algorithms m math algorithm: generates next password based on the previous one, e. g. , hash chain. m time sychronization btw. client and authentication server m math algorithm: next password based on a challenge and counter (e. g. , used by smart cards).
One time password RSA Secur. ID tokens (has a built-in accurate clock) r Opposite of static passwords m constantly altering passwords r Password generation algorithms m math algorithm: generates next password based on the previous one, e. g. , hash chain. m time sychronization btw. client and authentication server m math algorithm: next password based on a challenge and counter (e. g. , used by smart cards).
 Network Security (summary) Basic techniques…. . . m cryptography (symmetric and public) m authentication m message integrity m key distribution …. used in many different security scenarios m secure email m secure transport (SSL) m IP sec m 802. 11
Network Security (summary) Basic techniques…. . . m cryptography (symmetric and public) m authentication m message integrity m key distribution …. used in many different security scenarios m secure email m secure transport (SSL) m IP sec m 802. 11
 What are hot topics in networking? r Information sharing m Fighting Coordinated Attackers with Cross. Organizational Information Sharing r Social networks m SPACE: Secure Protocol for Address Book based Connection Establishment m Exploiting Social Networks for Internet Search m Detect Sybil Attacks r Revisiting Internet design m Decongestion control m IP multicast r Evolutionary PKI, security through publicity
What are hot topics in networking? r Information sharing m Fighting Coordinated Attackers with Cross. Organizational Information Sharing r Social networks m SPACE: Secure Protocol for Address Book based Connection Establishment m Exploiting Social Networks for Internet Search m Detect Sybil Attacks r Revisiting Internet design m Decongestion control m IP multicast r Evolutionary PKI, security through publicity
 What are hot topics in networking? r next-generation Internet m new addressing, routing schemes r Churn in distributed systems r Troubleshooting, diagnosis, mitigation r Detecting Evasion Attacks at High Speeds without Reassembly r New network applications
What are hot topics in networking? r next-generation Internet m new addressing, routing schemes r Churn in distributed systems r Troubleshooting, diagnosis, mitigation r Detecting Evasion Attacks at High Speeds without Reassembly r New network applications
 Internet is not the only network r “New” networks m vehicular networks m sensor networks m wireless networks m cellular networks m delay-tolerant networks m networks in rural areas m integration with Internet r Biggest problem with today’s Internet: m Lack of security m Lack of manageability and Qo. S assurance m Other desirable properties: mobility, faultresilience.
Internet is not the only network r “New” networks m vehicular networks m sensor networks m wireless networks m cellular networks m delay-tolerant networks m networks in rural areas m integration with Internet r Biggest problem with today’s Internet: m Lack of security m Lack of manageability and Qo. S assurance m Other desirable properties: mobility, faultresilience.
 Network security is an ongoing arms race r Measuring Internet-scale Adversaries m Endemic worms, malicious scanning m Huge dataset headache m Huge privacy/legal/policy/commercial hurdles m Attacks on passive monitoring • state, analysis flooding • bugs in analyzers: adversary crafts such a packet, overruns buffer, causes analyzer to execute arbitrary code • evasion, confuse monitoring analysis algorithms r Defense m Automated response
Network security is an ongoing arms race r Measuring Internet-scale Adversaries m Endemic worms, malicious scanning m Huge dataset headache m Huge privacy/legal/policy/commercial hurdles m Attacks on passive monitoring • state, analysis flooding • bugs in analyzers: adversary crafts such a packet, overruns buffer, causes analyzer to execute arbitrary code • evasion, confuse monitoring analysis algorithms r Defense m Automated response
 Unwanted traffic r spam r reconnaissance, probe traffic r attack traffic r misconfigurations
Unwanted traffic r spam r reconnaissance, probe traffic r attack traffic r misconfigurations


