dfb076ddf699655724b2853bee0b14f4.ppt
- Количество слайдов: 48
 Network Security ( An Overview) Data Communication and Networks
Network Security ( An Overview) Data Communication and Networks
 Security Threats ¡ Passive attacks l l ¡ Eavesdropping on, or monitoring, transmissions Electronic mail, file transfers, and client/server exchanges are examples of transmissions that can be monitored Active attacks l l Modification of transmitted data Attempts to gain unauthorized access to computer systems Data Communication and Networks 2
Security Threats ¡ Passive attacks l l ¡ Eavesdropping on, or monitoring, transmissions Electronic mail, file transfers, and client/server exchanges are examples of transmissions that can be monitored Active attacks l l Modification of transmitted data Attempts to gain unauthorized access to computer systems Data Communication and Networks 2
 Encryption Methods The essential technology underlying virtually all automated network and computer security applications is cryptography ¡ Two fundamental approaches are in use: ¡ l l conventional encryption, also known as symmetric encryption public-key encryption, also known as asymmetric encryption Data Communication and Networks 3
Encryption Methods The essential technology underlying virtually all automated network and computer security applications is cryptography ¡ Two fundamental approaches are in use: ¡ l l conventional encryption, also known as symmetric encryption public-key encryption, also known as asymmetric encryption Data Communication and Networks 3
 Conventional Encryption ¡ ¡ The only form of encryption prior to late 1970 s Five components to the algorithm l l l Plaintext: The original message or data Encryption algorithm: Performs various substitutions and transformations on the plaintext. Secret key: Input to the encryption algorithm. Substitutions and transformations performed depend on this key Ciphertext: Scrambled message produced as output. depends on the plaintext and the secret key Decryption algorithm: Encryption algorithm run in 4 reverse. Uses Data Communication and Networks ciphertext and the secret key to
Conventional Encryption ¡ ¡ The only form of encryption prior to late 1970 s Five components to the algorithm l l l Plaintext: The original message or data Encryption algorithm: Performs various substitutions and transformations on the plaintext. Secret key: Input to the encryption algorithm. Substitutions and transformations performed depend on this key Ciphertext: Scrambled message produced as output. depends on the plaintext and the secret key Decryption algorithm: Encryption algorithm run in 4 reverse. Uses Data Communication and Networks ciphertext and the secret key to
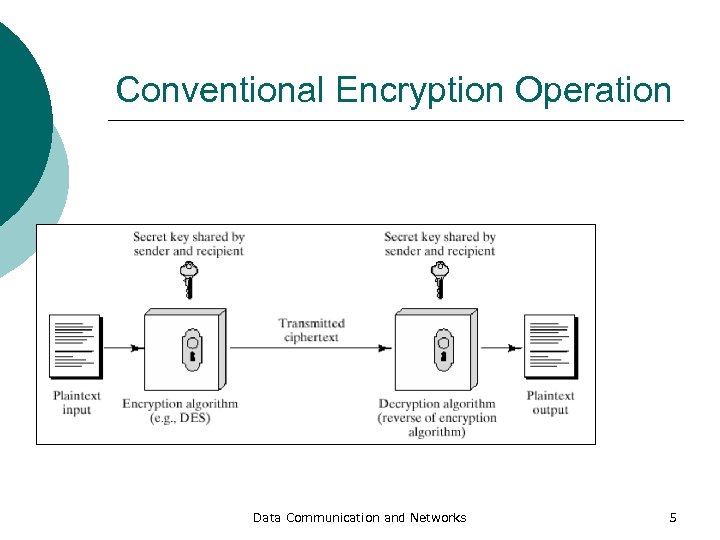 Conventional Encryption Operation Data Communication and Networks 5
Conventional Encryption Operation Data Communication and Networks 5
 Conventional Encryption Requirements & Weaknesses ¡ Requirements l l ¡ A strong encryption algorithm Secure process for sender & receiver to obtain secret keys Methods of Attack l l Cryptanalysis Brute force Data Communication and Networks 6
Conventional Encryption Requirements & Weaknesses ¡ Requirements l l ¡ A strong encryption algorithm Secure process for sender & receiver to obtain secret keys Methods of Attack l l Cryptanalysis Brute force Data Communication and Networks 6
 Data Encryption Standard (DES) Adopted in 1977, reaffirmed for 5 years in 1994, by NBS/NIST ¡ Plaintext is 64 bits (or blocks of 64 bits), key is 56 bits ¡ Plaintext goes through 16 iterations, each producing an intermediate value that is used in the next iteration. ¡ DES is now too easy to crack to be a useful encryption method Data Communication and Networks 7 ¡
Data Encryption Standard (DES) Adopted in 1977, reaffirmed for 5 years in 1994, by NBS/NIST ¡ Plaintext is 64 bits (or blocks of 64 bits), key is 56 bits ¡ Plaintext goes through 16 iterations, each producing an intermediate value that is used in the next iteration. ¡ DES is now too easy to crack to be a useful encryption method Data Communication and Networks 7 ¡
 Triple DEA Alternative to DES, uses multiple encryption with DES and multiple keys ¡ With three distinct keys, TDEA has an effective key length of 168 bits, so is essentially immune to brute force attacks ¡ Principal drawback of TDEA is that the algorithm is relatively sluggish in software ¡ Data Communication and Networks 8
Triple DEA Alternative to DES, uses multiple encryption with DES and multiple keys ¡ With three distinct keys, TDEA has an effective key length of 168 bits, so is essentially immune to brute force attacks ¡ Principal drawback of TDEA is that the algorithm is relatively sluggish in software ¡ Data Communication and Networks 8
 Public-Key Encryption Based on mathematical functions rather than on simple operations on bit patterns ¡ Asymmetric, involving the use of two separate keys ¡ Misconceptions about public key encryption ¡ l l it is more secure from cryptanalysis it is a general-purpose technique that has made conventional encryption Data obsolete Communication and Networks 9
Public-Key Encryption Based on mathematical functions rather than on simple operations on bit patterns ¡ Asymmetric, involving the use of two separate keys ¡ Misconceptions about public key encryption ¡ l l it is more secure from cryptanalysis it is a general-purpose technique that has made conventional encryption Data obsolete Communication and Networks 9
 Public-Key Encryption Components Plaintext ¡ Encryption algorithm ¡ Public key ¡ Private key ¡ Ciphertext ¡ Decryption algorithm ¡ Data Communication and Networks 10
Public-Key Encryption Components Plaintext ¡ Encryption algorithm ¡ Public key ¡ Private key ¡ Ciphertext ¡ Decryption algorithm ¡ Data Communication and Networks 10
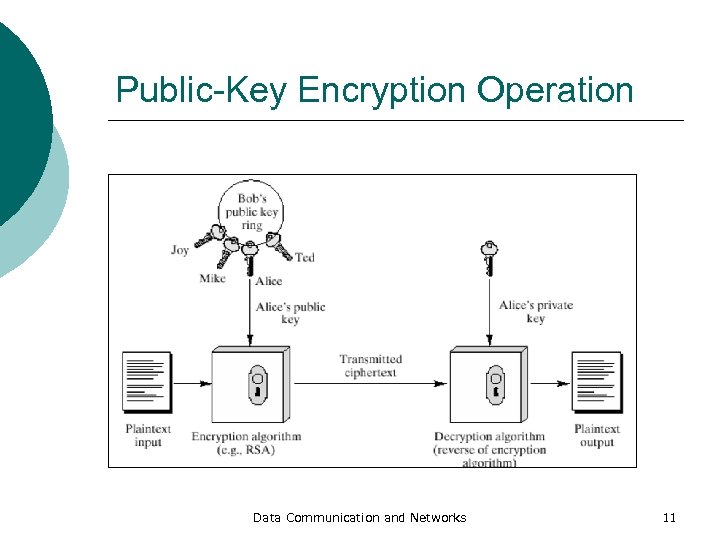 Public-Key Encryption Operation Data Communication and Networks 11
Public-Key Encryption Operation Data Communication and Networks 11
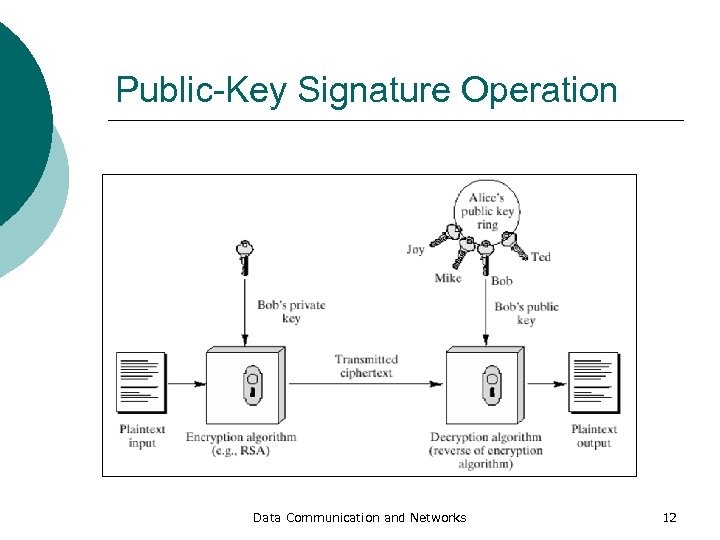 Public-Key Signature Operation Data Communication and Networks 12
Public-Key Signature Operation Data Communication and Networks 12
 Characteristics of Public-Key Infeasible to determine the decryption key given knowledge of the cryptographic algorithm and the encryption key. ¡ Either of the two related keys can be used for encryption, with the other used for decryption. ¡ Slow, but provides tremendous flexibility to perform a number of security-related functions ¡ Data Communication and Networks 13
Characteristics of Public-Key Infeasible to determine the decryption key given knowledge of the cryptographic algorithm and the encryption key. ¡ Either of the two related keys can be used for encryption, with the other used for decryption. ¡ Slow, but provides tremendous flexibility to perform a number of security-related functions ¡ Data Communication and Networks 13
 Location of Encryption Devices ¡ Link encryption l l l ¡ Each vulnerable communications link is equipped on both ends with an encryption device. All traffic over all communications links is secured. Vulnerable at each switch End-to-end encryption l l the encryption process is carried out at the two end systems. Encrypted data are transmitted unaltered across the network to the destination, which shares a key with the source to decrypt the 14 Data Communication and Networks data
Location of Encryption Devices ¡ Link encryption l l l ¡ Each vulnerable communications link is equipped on both ends with an encryption device. All traffic over all communications links is secured. Vulnerable at each switch End-to-end encryption l l the encryption process is carried out at the two end systems. Encrypted data are transmitted unaltered across the network to the destination, which shares a key with the source to decrypt the 14 Data Communication and Networks data
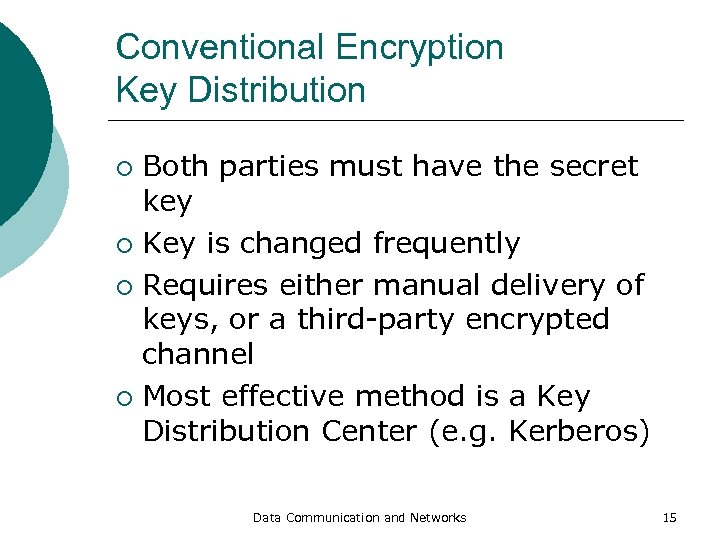 Conventional Encryption Key Distribution Both parties must have the secret key ¡ Key is changed frequently ¡ Requires either manual delivery of keys, or a third-party encrypted channel ¡ Most effective method is a Key Distribution Center (e. g. Kerberos) ¡ Data Communication and Networks 15
Conventional Encryption Key Distribution Both parties must have the secret key ¡ Key is changed frequently ¡ Requires either manual delivery of keys, or a third-party encrypted channel ¡ Most effective method is a Key Distribution Center (e. g. Kerberos) ¡ Data Communication and Networks 15
 Public-Key Encryption Key Distribution ¡ ¡ Parties create a pair of keys; public key is broadly distributed, private key is not To reduce computational overhead, the following process is then used: 1. Prepare a message. 2. Encrypt that message using conventional encryption with a one-time conventional session key. 3. Encrypt the session key using public-key encryption with recipient’s public key. 4. Attach the encrypted session key to the message and send it. Data Communication and Networks 16
Public-Key Encryption Key Distribution ¡ ¡ Parties create a pair of keys; public key is broadly distributed, private key is not To reduce computational overhead, the following process is then used: 1. Prepare a message. 2. Encrypt that message using conventional encryption with a one-time conventional session key. 3. Encrypt the session key using public-key encryption with recipient’s public key. 4. Attach the encrypted session key to the message and send it. Data Communication and Networks 16
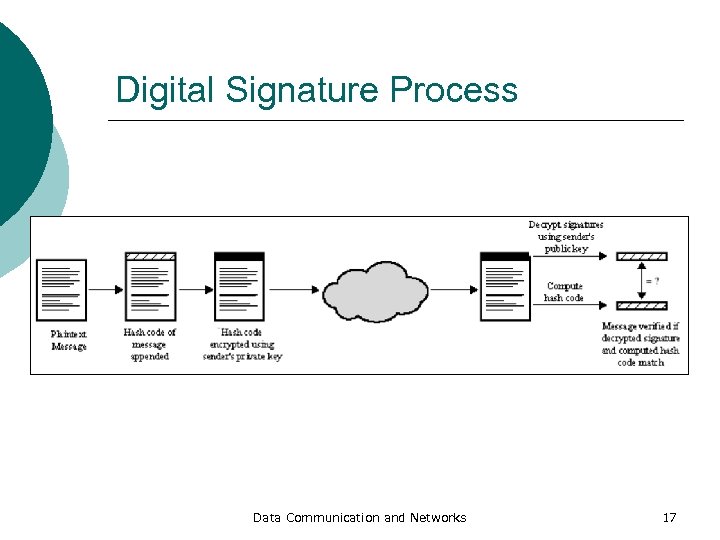 Digital Signature Process Data Communication and Networks 17
Digital Signature Process Data Communication and Networks 17
 Public Key Certificates 1. A public key is generated by the user and submitted to Agency X for certification. 2. X determines by some procedure, such as a face-to-face meeting, that this is authentically the user’s public key. 3. X appends a timestamp to the public key, generates the hash code of the result, and encrypts that result with X’s private key forming the signature. 4. The signature is attached to the public key. Data Communication and Networks 18
Public Key Certificates 1. A public key is generated by the user and submitted to Agency X for certification. 2. X determines by some procedure, such as a face-to-face meeting, that this is authentically the user’s public key. 3. X appends a timestamp to the public key, generates the hash code of the result, and encrypts that result with X’s private key forming the signature. 4. The signature is attached to the public key. Data Communication and Networks 18
 Web Vulnerabilities Unauthorized alteration of data at the Web site ¡ Unauthorized access to the underlying operating system at the Web server ¡ Eavesdropping on messages passed between a Web server and a Web browser ¡ Impersonation ¡ Data Communication and Networks 19
Web Vulnerabilities Unauthorized alteration of data at the Web site ¡ Unauthorized access to the underlying operating system at the Web server ¡ Eavesdropping on messages passed between a Web server and a Web browser ¡ Impersonation ¡ Data Communication and Networks 19
 Methods for Improving Web Security ¡ Securing the Web site itself l l l ¡ install operating system security patches install the Web server software with minimal system privileges use a more secure platform Securing the Web application Data Communication and Networks 20
Methods for Improving Web Security ¡ Securing the Web site itself l l l ¡ install operating system security patches install the Web server software with minimal system privileges use a more secure platform Securing the Web application Data Communication and Networks 20
 Web Application Security Secure Hyper. Text Transfer Protocol (SHTTP) ¡ Secure Sockets Layer (SSL) ¡ Web server packages should incorporate both of these protocols ¡ Data Communication and Networks 21
Web Application Security Secure Hyper. Text Transfer Protocol (SHTTP) ¡ Secure Sockets Layer (SSL) ¡ Web server packages should incorporate both of these protocols ¡ Data Communication and Networks 21
 Virtual Private Networks (VPNs) ¡ ¡ ¡ The use of encryption and authentication in the lower protocol layers to provide a secure connection through an otherwise insecure network, typically the Internet. Generally cheaper than real private networks using private lines but rely on having the same encryption and authentication system at both ends. The encryption may be performed by firewall software or possibly by routers. Data Communication and Networks 22
Virtual Private Networks (VPNs) ¡ ¡ ¡ The use of encryption and authentication in the lower protocol layers to provide a secure connection through an otherwise insecure network, typically the Internet. Generally cheaper than real private networks using private lines but rely on having the same encryption and authentication system at both ends. The encryption may be performed by firewall software or possibly by routers. Data Communication and Networks 22
 IPSec Can secure communications across a LAN, WANs, and/or the Internet ¡ Examples of use: ¡ l l Secure branch office connectivity over the Internet Secure remote access over the Internet Establishing extranet and intranet connectivity with partners Enhancing electronic commerce security Data Communication and Networks 23
IPSec Can secure communications across a LAN, WANs, and/or the Internet ¡ Examples of use: ¡ l l Secure branch office connectivity over the Internet Secure remote access over the Internet Establishing extranet and intranet connectivity with partners Enhancing electronic commerce security Data Communication and Networks 23
 Benefits of IPSec When implemented in a firewall or router, provides strong security for all traffic crossing the perimeter ¡ IPSec in a firewall is resistant to bypass ¡ Runs below the transport layer (TCP, UDP) and so is transparent to applications ¡ Can be transparent to end users ¡ Can provide security for individual 24 Data Communication and Networks ¡
Benefits of IPSec When implemented in a firewall or router, provides strong security for all traffic crossing the perimeter ¡ IPSec in a firewall is resistant to bypass ¡ Runs below the transport layer (TCP, UDP) and so is transparent to applications ¡ Can be transparent to end users ¡ Can provide security for individual 24 Data Communication and Networks ¡
 IPSec Functions ¡ IPSec provides three main facilities l l l ¡ authentication-only function referred to as Authentication Header (AH) combined authentication/encryption function called Encapsulating Security Payload (ESP) a key exchange function For VPNs, both authentication and encryption are generally desired Data Communication and Networks 25
IPSec Functions ¡ IPSec provides three main facilities l l l ¡ authentication-only function referred to as Authentication Header (AH) combined authentication/encryption function called Encapsulating Security Payload (ESP) a key exchange function For VPNs, both authentication and encryption are generally desired Data Communication and Networks 25
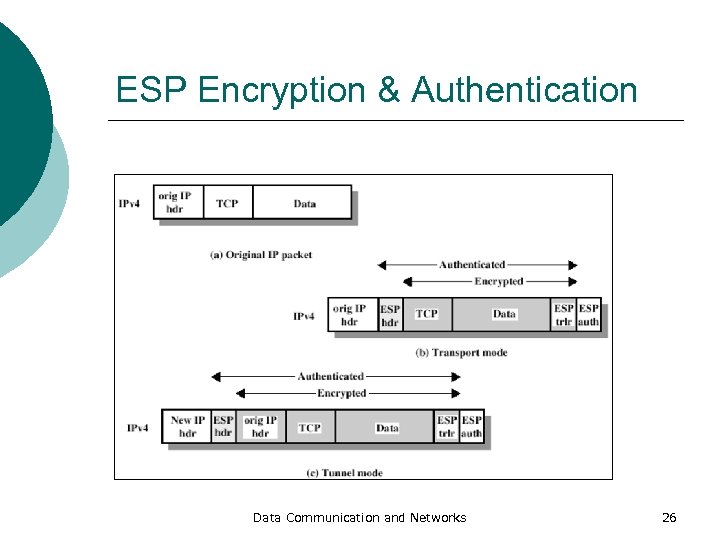 ESP Encryption & Authentication Data Communication and Networks 26
ESP Encryption & Authentication Data Communication and Networks 26
 IPSec Key Management ¡ Manual l l ¡ System administrator manually configures each system with its own keys and with the keys of other communicating systems Practical for small, relatively static environments Automated l l Enables the on-demand creation of keys for SAs and facilitates the use of keys in a large distributed system Most flexible but requires more effort to configure and requires more software Data Communication and Networks 27
IPSec Key Management ¡ Manual l l ¡ System administrator manually configures each system with its own keys and with the keys of other communicating systems Practical for small, relatively static environments Automated l l Enables the on-demand creation of keys for SAs and facilitates the use of keys in a large distributed system Most flexible but requires more effort to configure and requires more software Data Communication and Networks 27
 Cryptography Data Communication and Networks 28
Cryptography Data Communication and Networks 28
 INTRODUCTION Let us introduce the issues involved in cryptography. First, we need to define some terms; then we give some taxonomies. Topics discussed in this section: Definitions Two Categories Data Communication and Networks 29
INTRODUCTION Let us introduce the issues involved in cryptography. First, we need to define some terms; then we give some taxonomies. Topics discussed in this section: Definitions Two Categories Data Communication and Networks 29
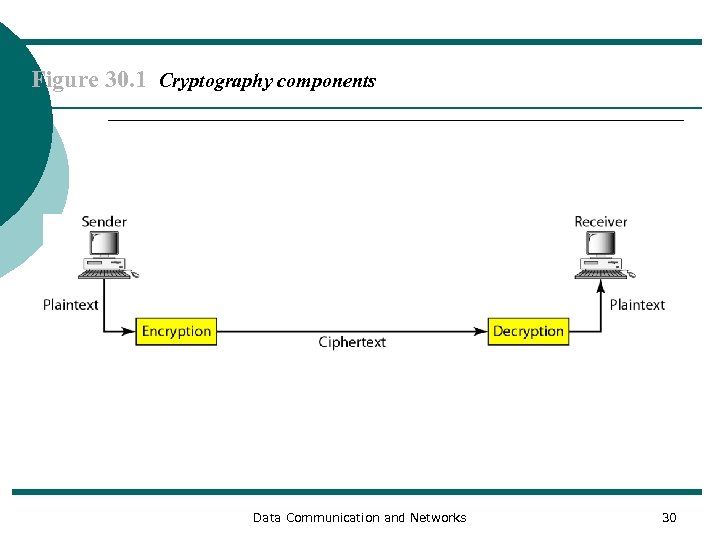 Figure 30. 1 Cryptography components Data Communication and Networks 30
Figure 30. 1 Cryptography components Data Communication and Networks 30
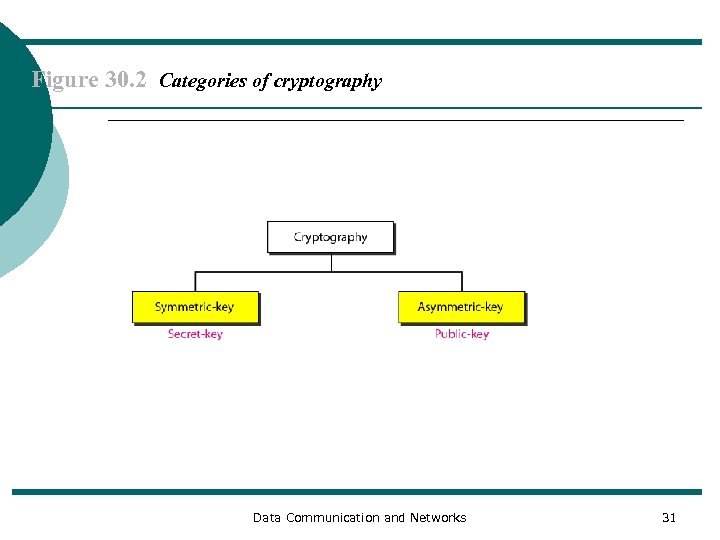 Figure 30. 2 Categories of cryptography Data Communication and Networks 31
Figure 30. 2 Categories of cryptography Data Communication and Networks 31
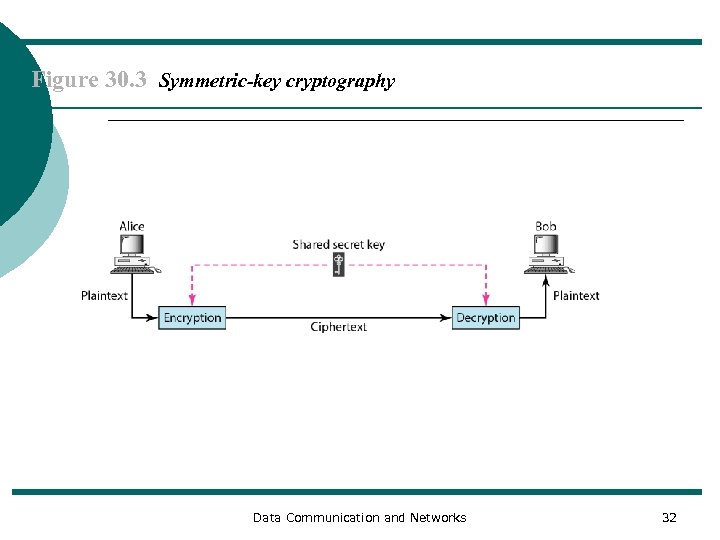 Figure 30. 3 Symmetric-key cryptography Data Communication and Networks 32
Figure 30. 3 Symmetric-key cryptography Data Communication and Networks 32
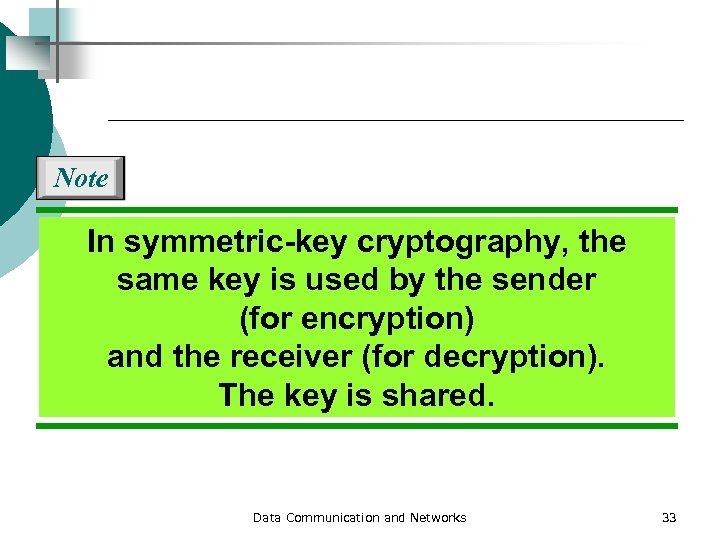 Note In symmetric-key cryptography, the same key is used by the sender (for encryption) and the receiver (for decryption). The key is shared. Data Communication and Networks 33
Note In symmetric-key cryptography, the same key is used by the sender (for encryption) and the receiver (for decryption). The key is shared. Data Communication and Networks 33
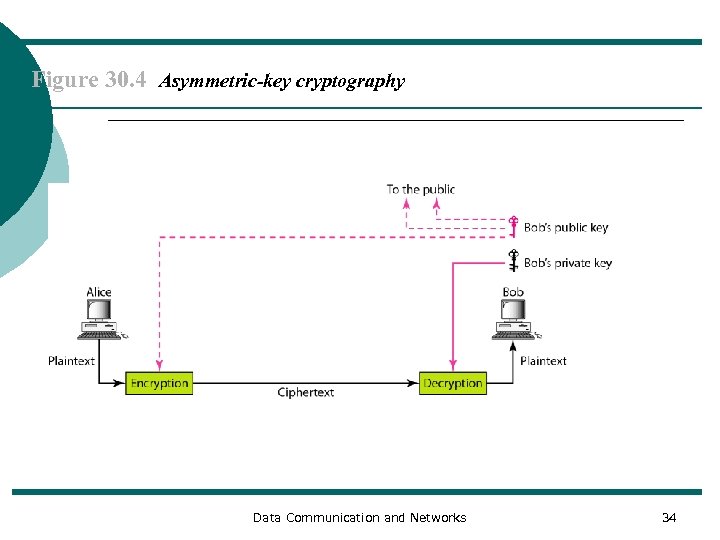 Figure 30. 4 Asymmetric-key cryptography Data Communication and Networks 34
Figure 30. 4 Asymmetric-key cryptography Data Communication and Networks 34
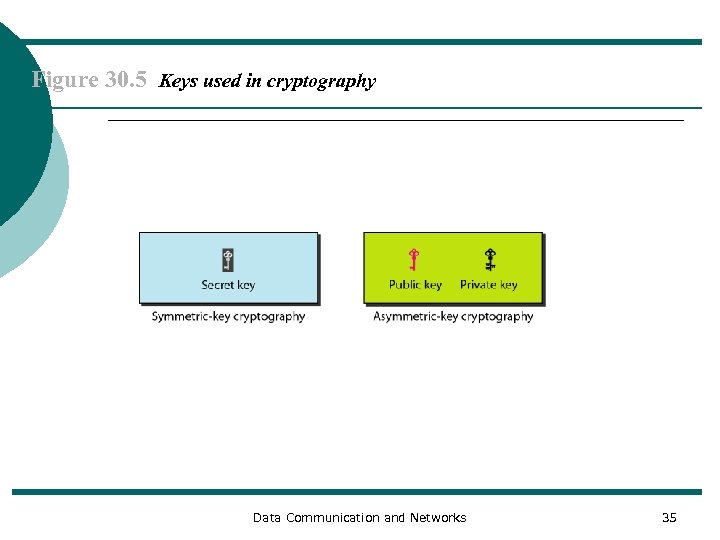 Figure 30. 5 Keys used in cryptography Data Communication and Networks 35
Figure 30. 5 Keys used in cryptography Data Communication and Networks 35
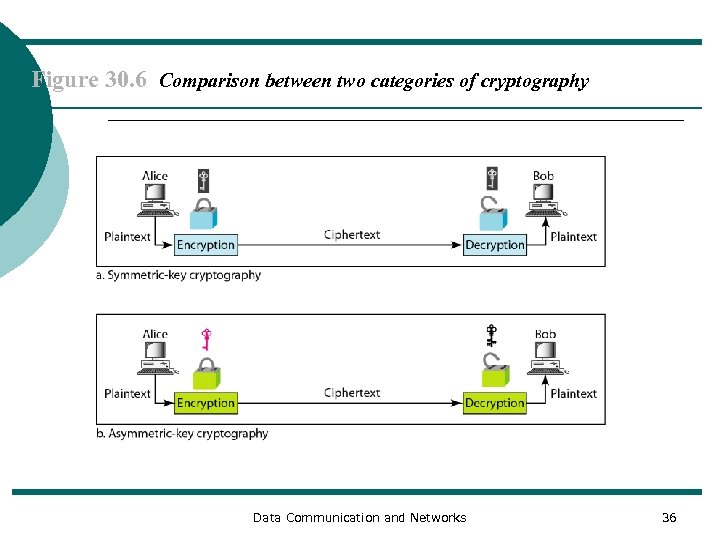 Figure 30. 6 Comparison between two categories of cryptography Data Communication and Networks 36
Figure 30. 6 Comparison between two categories of cryptography Data Communication and Networks 36
 30 -2 SYMMETRIC-KEY CRYPTOGRAPHY Symmetric-key cryptography started thousands of years ago when people needed to exchange secrets (for example, in a war). We still mainly use symmetric-key cryptography in our network security. Topics discussed in this section: Traditional Ciphers Simple Modern Ciphers Modern Round Ciphers Mode of Operation Data Communication and Networks 37
30 -2 SYMMETRIC-KEY CRYPTOGRAPHY Symmetric-key cryptography started thousands of years ago when people needed to exchange secrets (for example, in a war). We still mainly use symmetric-key cryptography in our network security. Topics discussed in this section: Traditional Ciphers Simple Modern Ciphers Modern Round Ciphers Mode of Operation Data Communication and Networks 37
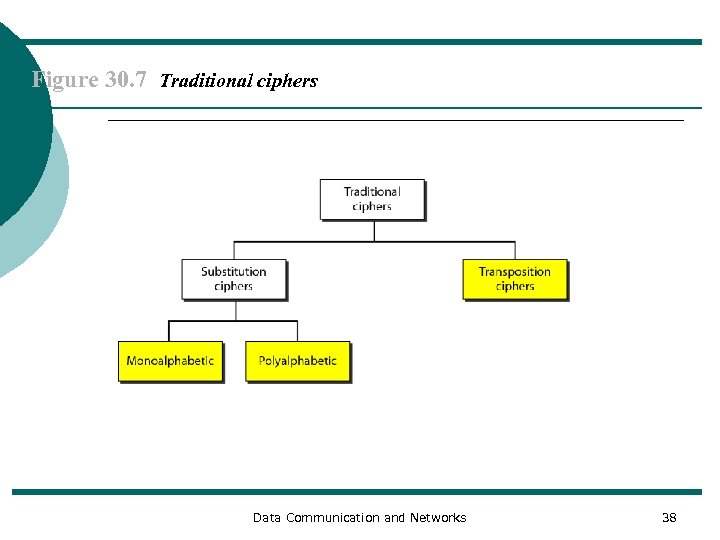 Figure 30. 7 Traditional ciphers Data Communication and Networks 38
Figure 30. 7 Traditional ciphers Data Communication and Networks 38
 Note A substitution cipher replaces one symbol with another. Data Communication and Networks 39
Note A substitution cipher replaces one symbol with another. Data Communication and Networks 39
 Example 30. 1 The following shows a plaintext and its corresponding ciphertext. Is the cipher monoalphabetic? Solution The cipher is probably monoalphabetic because both occurrences of L’s are encrypted as O’s. Data Communication and Networks 40
Example 30. 1 The following shows a plaintext and its corresponding ciphertext. Is the cipher monoalphabetic? Solution The cipher is probably monoalphabetic because both occurrences of L’s are encrypted as O’s. Data Communication and Networks 40
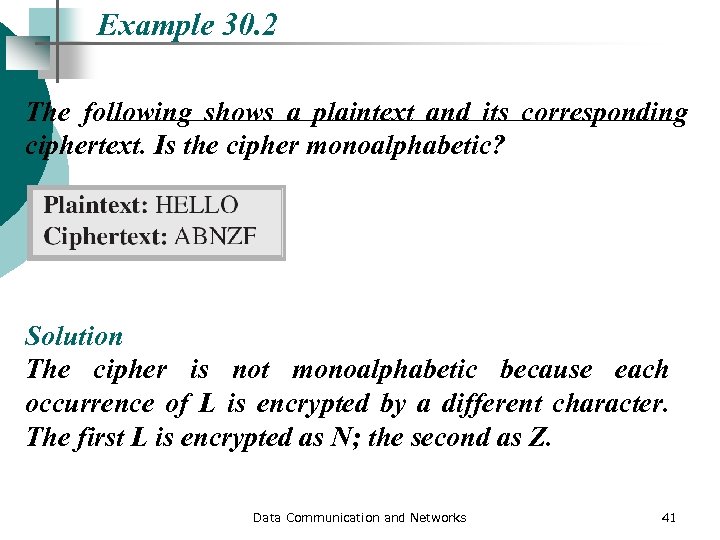 Example 30. 2 The following shows a plaintext and its corresponding ciphertext. Is the cipher monoalphabetic? Solution The cipher is not monoalphabetic because each occurrence of L is encrypted by a different character. The first L is encrypted as N; the second as Z. Data Communication and Networks 41
Example 30. 2 The following shows a plaintext and its corresponding ciphertext. Is the cipher monoalphabetic? Solution The cipher is not monoalphabetic because each occurrence of L is encrypted by a different character. The first L is encrypted as N; the second as Z. Data Communication and Networks 41
 Note The shift cipher is sometimes referred to as the Caesar cipher. Data Communication and Networks 42
Note The shift cipher is sometimes referred to as the Caesar cipher. Data Communication and Networks 42
 Example 30. 3 Use the shift cipher with key = 15 to encrypt the message “HELLO. ” Solution We encrypt one character at a time. Each character is shifted 15 characters down. Letter H is encrypted to W. Letter E is encrypted to T. The first L is encrypted to A. The second L is also encrypted to A. And O is encrypted to D. The cipher text is WTAAD. Data Communication and Networks 43
Example 30. 3 Use the shift cipher with key = 15 to encrypt the message “HELLO. ” Solution We encrypt one character at a time. Each character is shifted 15 characters down. Letter H is encrypted to W. Letter E is encrypted to T. The first L is encrypted to A. The second L is also encrypted to A. And O is encrypted to D. The cipher text is WTAAD. Data Communication and Networks 43
 Example 30. 4 Use the shift cipher with key = 15 to decrypt the message “WTAAD. ” Solution We decrypt one character at a time. Each character is shifted 15 characters up. Letter W is decrypted to H. Letter T is decrypted to E. The first A is decrypted to L. The second A is decrypted to L. And, finally, D is decrypted to O. The plaintext is HELLO. Data Communication and Networks 44
Example 30. 4 Use the shift cipher with key = 15 to decrypt the message “WTAAD. ” Solution We decrypt one character at a time. Each character is shifted 15 characters up. Letter W is decrypted to H. Letter T is decrypted to E. The first A is decrypted to L. The second A is decrypted to L. And, finally, D is decrypted to O. The plaintext is HELLO. Data Communication and Networks 44
 Note A transposition cipher reorders (permutes) symbols in a block of symbols. Data Communication and Networks 45
Note A transposition cipher reorders (permutes) symbols in a block of symbols. Data Communication and Networks 45
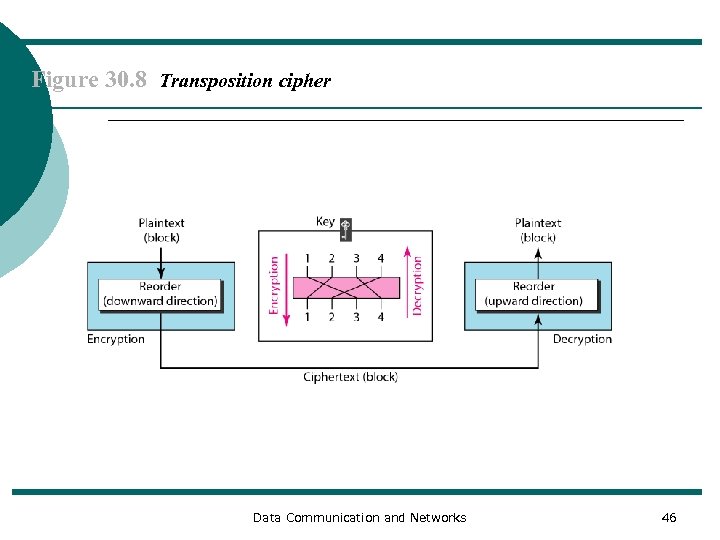 Figure 30. 8 Transposition cipher Data Communication and Networks 46
Figure 30. 8 Transposition cipher Data Communication and Networks 46
 Example 30. 5 Encrypt the message “HELLO MY DEAR, ” using the key shown in Figure 30. 8. Solution We first remove the spaces in the message. We then divide the text into blocks of four characters. We add a bogus character Z at the end of the third block. The result is HELL OMYD EARZ. We create a three-block ciphertext ELHLMDOYAZER. Data Communication and Networks 47
Example 30. 5 Encrypt the message “HELLO MY DEAR, ” using the key shown in Figure 30. 8. Solution We first remove the spaces in the message. We then divide the text into blocks of four characters. We add a bogus character Z at the end of the third block. The result is HELL OMYD EARZ. We create a three-block ciphertext ELHLMDOYAZER. Data Communication and Networks 47
 Example 30. 6 Using Example 30. 5, “ELHLMDOYAZER”. decrypt the message Solution The result is HELL OMYD EARZ. After removing the bogus character and combining the characters, we get the original message “HELLO MY DEAR. ” Data Communication and Networks 48
Example 30. 6 Using Example 30. 5, “ELHLMDOYAZER”. decrypt the message Solution The result is HELL OMYD EARZ. After removing the bogus character and combining the characters, we get the original message “HELLO MY DEAR. ” Data Communication and Networks 48


