474e0e7191e8e1abb0275601c7b950b2.ppt
- Количество слайдов: 47
 Network Security Accessing the WAN – Chapter 4 Red Book – Chapter 4 Sandra Coleman, CCNA, CCAI
Network Security Accessing the WAN – Chapter 4 Red Book – Chapter 4 Sandra Coleman, CCNA, CCAI
 Objectives Identify security threats to enterprise networks Describe methods to mitigate security threats to enterprise networks Configure basic router security Disable unused router services and interfaces Use the Cisco SDM one-step lockdown feature Manage files and software images with the Cisco IOS Integrated File System (IFS)
Objectives Identify security threats to enterprise networks Describe methods to mitigate security threats to enterprise networks Configure basic router security Disable unused router services and interfaces Use the Cisco SDM one-step lockdown feature Manage files and software images with the Cisco IOS Integrated File System (IFS)
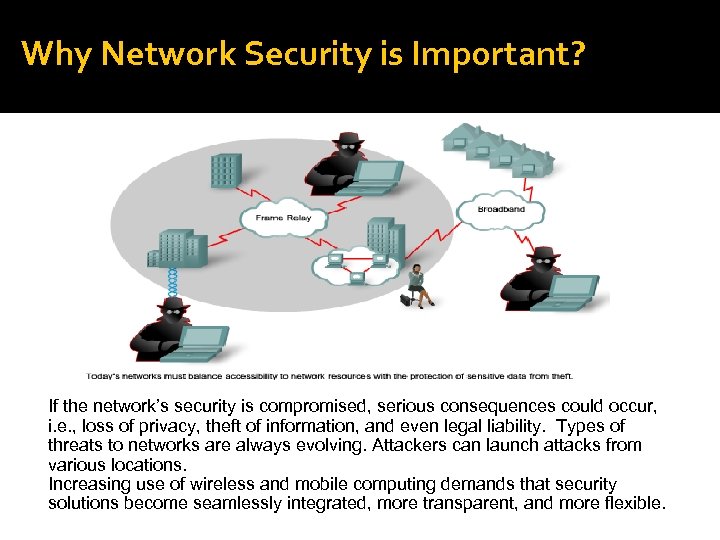 Why Network Security is Important? If the network’s security is compromised, serious consequences could occur, i. e. , loss of privacy, theft of information, and even legal liability. Types of threats to networks are always evolving. Attackers can launch attacks from various locations. Increasing use of wireless and mobile computing demands that security solutions become seamlessly integrated, more transparent, and more flexible.
Why Network Security is Important? If the network’s security is compromised, serious consequences could occur, i. e. , loss of privacy, theft of information, and even legal liability. Types of threats to networks are always evolving. Attackers can launch attacks from various locations. Increasing use of wireless and mobile computing demands that security solutions become seamlessly integrated, more transparent, and more flexible.
 Increasing threat of Attackers Go to section 4. 1. 1. 2 Check out the graphic here… WOW… Does this surprise you? Most commonly reported acts of computer crimes: *Insider abuse of network access Viruses Mobile device theft Phishing IM misuse *Denial of Service *Password sniffing *System penetration Unauthorized access to information…. the list goes on… (pg. 193 -194) *can be alleviated by effective network management!
Increasing threat of Attackers Go to section 4. 1. 1. 2 Check out the graphic here… WOW… Does this surprise you? Most commonly reported acts of computer crimes: *Insider abuse of network access Viruses Mobile device theft Phishing IM misuse *Denial of Service *Password sniffing *System penetration Unauthorized access to information…. the list goes on… (pg. 193 -194) *can be alleviated by effective network management!
 Network Security As time goes on, attacker’s methods and tools improved and they no longer are required to have an intimate knowledge of computing. People who would not have previously participated in computer crime, now can.
Network Security As time goes on, attacker’s methods and tools improved and they no longer are required to have an intimate knowledge of computing. People who would not have previously participated in computer crime, now can.
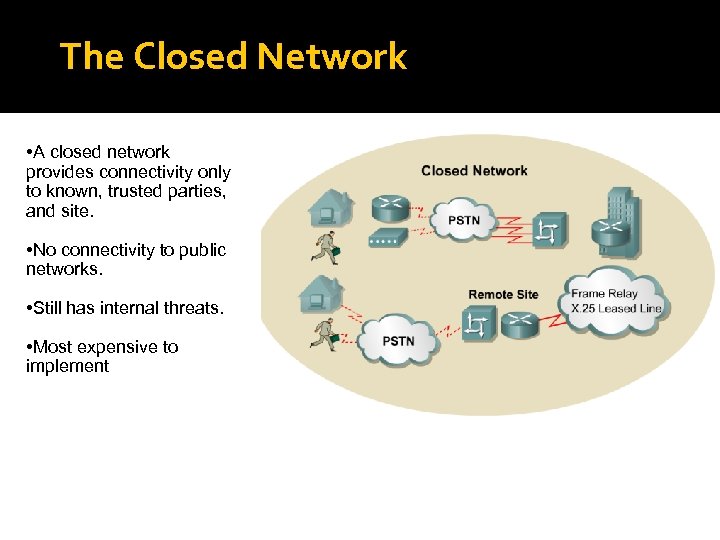 The Closed Network • A closed network provides connectivity only to known, trusted parties, and site. • No connectivity to public networks. • Still has internal threats. • Most expensive to implement
The Closed Network • A closed network provides connectivity only to known, trusted parties, and site. • No connectivity to public networks. • Still has internal threats. • Most expensive to implement
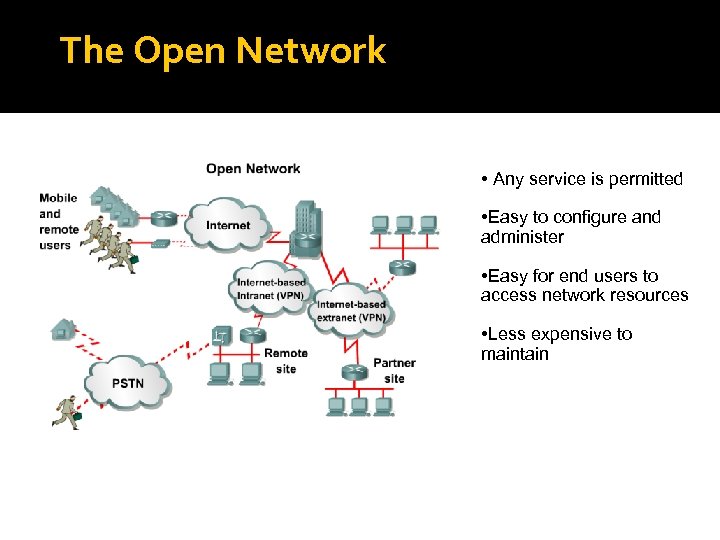 The Open Network • Any service is permitted • Easy to configure and administer • Easy for end users to access network resources • Less expensive to maintain
The Open Network • Any service is permitted • Easy to configure and administer • Easy for end users to access network resources • Less expensive to maintain
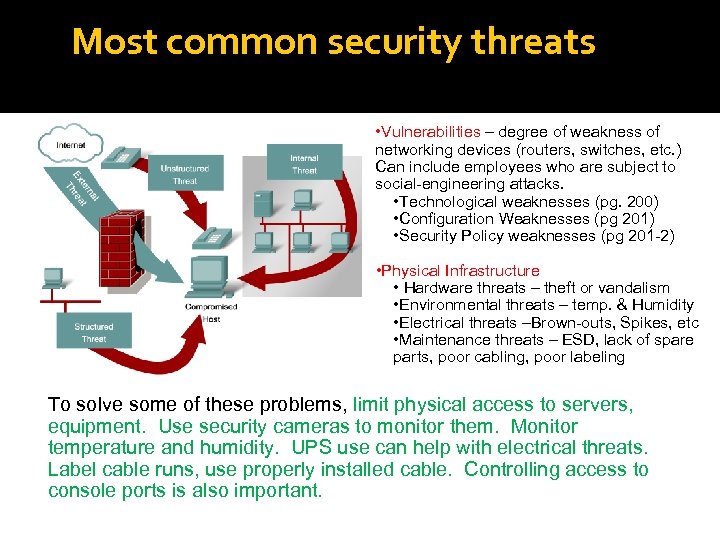 Most common security threats • Vulnerabilities – degree of weakness of networking devices (routers, switches, etc. ) Can include employees who are subject to social-engineering attacks. • Technological weaknesses (pg. 200) • Configuration Weaknesses (pg 201) • Security Policy weaknesses (pg 201 -2) • Physical Infrastructure • Hardware threats – theft or vandalism • Environmental threats – temp. & Humidity • Electrical threats –Brown-outs, Spikes, etc • Maintenance threats – ESD, lack of spare parts, poor cabling, poor labeling To solve some of these problems, limit physical access to servers, equipment. Use security cameras to monitor them. Monitor temperature and humidity. UPS use can help with electrical threats. Label cable runs, use properly installed cable. Controlling access to console ports is also important.
Most common security threats • Vulnerabilities – degree of weakness of networking devices (routers, switches, etc. ) Can include employees who are subject to social-engineering attacks. • Technological weaknesses (pg. 200) • Configuration Weaknesses (pg 201) • Security Policy weaknesses (pg 201 -2) • Physical Infrastructure • Hardware threats – theft or vandalism • Environmental threats – temp. & Humidity • Electrical threats –Brown-outs, Spikes, etc • Maintenance threats – ESD, lack of spare parts, poor cabling, poor labeling To solve some of these problems, limit physical access to servers, equipment. Use security cameras to monitor them. Monitor temperature and humidity. UPS use can help with electrical threats. Label cable runs, use properly installed cable. Controlling access to console ports is also important.
 Threats to Networks Unstructured – inexperienced individuals using hacking tools. Hacking a website…etc. Structured – Technically competent people who are highly motivated. They know the vulnerabilities and how to exploit them. They commit fraud, alter records, and create havoc. External – OUTSIDE of the company. DO NOT have authorized access to equipment. Internal – WITHIN the company. A disgruntled employee or one with a criminal intent on destruction. Social Engineering – easiest attack. Trick someone into giving out valuable information. Preys on personal vulnerabilities. May include fake documents. Phishing – using e-mail to trick you into providing sensitive info. The phisher appears to be a trusted party and seeks access to credit card info, passwords, etc. See pg. 205 Training users is the best defense.
Threats to Networks Unstructured – inexperienced individuals using hacking tools. Hacking a website…etc. Structured – Technically competent people who are highly motivated. They know the vulnerabilities and how to exploit them. They commit fraud, alter records, and create havoc. External – OUTSIDE of the company. DO NOT have authorized access to equipment. Internal – WITHIN the company. A disgruntled employee or one with a criminal intent on destruction. Social Engineering – easiest attack. Trick someone into giving out valuable information. Preys on personal vulnerabilities. May include fake documents. Phishing – using e-mail to trick you into providing sensitive info. The phisher appears to be a trusted party and seeks access to credit card info, passwords, etc. See pg. 205 Training users is the best defense.
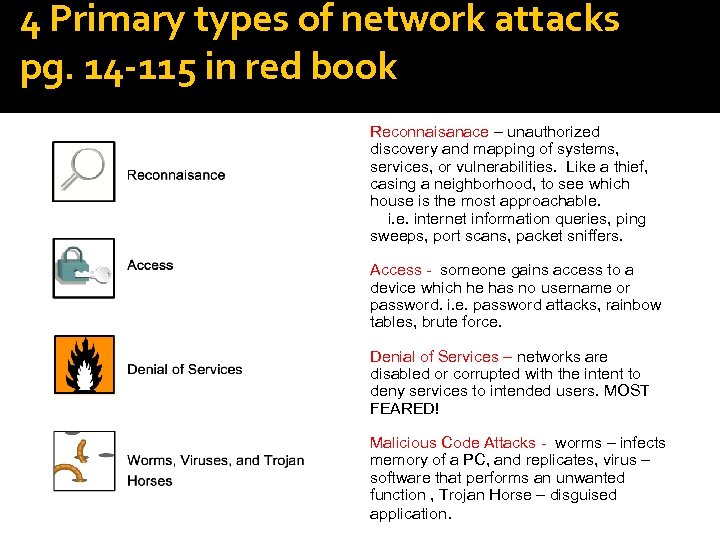 4 Primary types of network attacks pg. 14 -115 in red book Reconnaisanace – unauthorized discovery and mapping of systems, services, or vulnerabilities. Like a thief, casing a neighborhood, to see which house is the most approachable. internet information queries, ping sweeps, port scans, packet sniffers. Access - someone gains access to a device which he has no username or password. i. e. password attacks, rainbow tables, brute force. Denial of Services – networks are disabled or corrupted with the intent to deny services to intended users. MOST FEARED! Malicious Code Attacks - worms – infects memory of a PC, and replicates, virus – software that performs an unwanted function , Trojan Horse – disguised application.
4 Primary types of network attacks pg. 14 -115 in red book Reconnaisanace – unauthorized discovery and mapping of systems, services, or vulnerabilities. Like a thief, casing a neighborhood, to see which house is the most approachable. internet information queries, ping sweeps, port scans, packet sniffers. Access - someone gains access to a device which he has no username or password. i. e. password attacks, rainbow tables, brute force. Denial of Services – networks are disabled or corrupted with the intent to deny services to intended users. MOST FEARED! Malicious Code Attacks - worms – infects memory of a PC, and replicates, virus – software that performs an unwanted function , Trojan Horse – disguised application.
 Reconnaissance Attacks – pg 117 red book Examples include – nslookup, whois utilities. These are designed to gain a public IP address for a corp. then to use a ping sweep tool to see which IP’s are vulnerable. Fping or gping – pings all IP addresses in a given range. Once IP addresses are discovered, a port scanner can be used to discern which network ports can be exploited. Nmap, Superscan. Eavesdropping – accumulate as much info as possible for information or for theft purposes (credit card #’s)
Reconnaissance Attacks – pg 117 red book Examples include – nslookup, whois utilities. These are designed to gain a public IP address for a corp. then to use a ping sweep tool to see which IP’s are vulnerable. Fping or gping – pings all IP addresses in a given range. Once IP addresses are discovered, a port scanner can be used to discern which network ports can be exploited. Nmap, Superscan. Eavesdropping – accumulate as much info as possible for information or for theft purposes (credit card #’s)
 Access Attacks – pg 115 -116 red book Password attacks – packet sniffers can capture pwds sent in clear text. Brute-force attacks searches for a pwd using a combination of characters to compute every possible password. Trust exploitation – compromise a trusted host and use it to stage attacks on other hosts. (pg. 210) Port Redirection – use a compromised host to pass traffic through a firewall that would otherwise be blocked. (pg. 211) Devices in the DMZ should NOT be fully trusted by internal devices and their access should be authenticated! Man-in-the-middle – intruders position themselves between 2 legitimate hosts. Periodically manipulates traffic. Can occur in the WAN using VPNs.
Access Attacks – pg 115 -116 red book Password attacks – packet sniffers can capture pwds sent in clear text. Brute-force attacks searches for a pwd using a combination of characters to compute every possible password. Trust exploitation – compromise a trusted host and use it to stage attacks on other hosts. (pg. 210) Port Redirection – use a compromised host to pass traffic through a firewall that would otherwise be blocked. (pg. 211) Devices in the DMZ should NOT be fully trusted by internal devices and their access should be authenticated! Man-in-the-middle – intruders position themselves between 2 legitimate hosts. Periodically manipulates traffic. Can occur in the WAN using VPNs.
 Do. S Attacks – pg 119 -121 red book Do. S – rendering a system unavailable by corrupting the services with intent to deny trusted users access. Can be physically disconnecting, crashing the system, or slowing it down so slow that it is unusable. Most Feared attack! Ping of Death – modifying size of ping packet from 64 to 65, 535 bytes. Can bring legacy systems DOWN. SYN flood attacks – Exploits TCP 3 -way handshake. Sending lots of SYN requests (1000’s) and never responding with an ACK until it eventually runs out of resources. E-mail bombs – sending bulk emails which monopolizes email services Malicious applets – Java, Java. Script, Active. X programs that tie up computer resources.
Do. S Attacks – pg 119 -121 red book Do. S – rendering a system unavailable by corrupting the services with intent to deny trusted users access. Can be physically disconnecting, crashing the system, or slowing it down so slow that it is unusable. Most Feared attack! Ping of Death – modifying size of ping packet from 64 to 65, 535 bytes. Can bring legacy systems DOWN. SYN flood attacks – Exploits TCP 3 -way handshake. Sending lots of SYN requests (1000’s) and never responding with an ACK until it eventually runs out of resources. E-mail bombs – sending bulk emails which monopolizes email services Malicious applets – Java, Java. Script, Active. X programs that tie up computer resources.
 DDos Attacks – pg 119 -120 red book Smurf attack Tribe Flood Network (TFN) Stacheldraht My. Doom How to stop Dos/Ddos Attacks? Implement antispoof and anti-Dos ACL’s. ISP’s can implement traffic rate policies.
DDos Attacks – pg 119 -120 red book Smurf attack Tribe Flood Network (TFN) Stacheldraht My. Doom How to stop Dos/Ddos Attacks? Implement antispoof and anti-Dos ACL’s. ISP’s can implement traffic rate policies.
 Malicious Code Attacks A worm executes code and installs copies of itself in the memory of the infected computer, which can, in turn, infect other hosts. A virus is malicious software that is attached to another program for the purpose of executing a particular unwanted function on a workstation.
Malicious Code Attacks A worm executes code and installs copies of itself in the memory of the infected computer, which can, in turn, infect other hosts. A virus is malicious software that is attached to another program for the purpose of executing a particular unwanted function on a workstation.
 Common mitigation techniques
Common mitigation techniques
 Common mitigation techniques (contd) Host- and Server based Security – Device Hardening – involved changing default settings on OS. The default level of security is inadequate. Here are some of the things to do: Change default usernames/passwords IMMEDIATELY Restrict access to system resources to authorized personnel only Turn off or uninstall unnecessary services and applications Configure system logging and tracking
Common mitigation techniques (contd) Host- and Server based Security – Device Hardening – involved changing default settings on OS. The default level of security is inadequate. Here are some of the things to do: Change default usernames/passwords IMMEDIATELY Restrict access to system resources to authorized personnel only Turn off or uninstall unnecessary services and applications Configure system logging and tracking
 Other Host- and Server-based security Antivirus Software Personal firewalls OS Patches – download frequently Intrusion Detection Systems (IDS) – detects attacks and logs it to a management console.
Other Host- and Server-based security Antivirus Software Personal firewalls OS Patches – download frequently Intrusion Detection Systems (IDS) – detects attacks and logs it to a management console.
 Common Security Appliances and Applications Adaptive Security Appliance Intrusion Prevention System Network Admission Control
Common Security Appliances and Applications Adaptive Security Appliance Intrusion Prevention System Network Admission Control
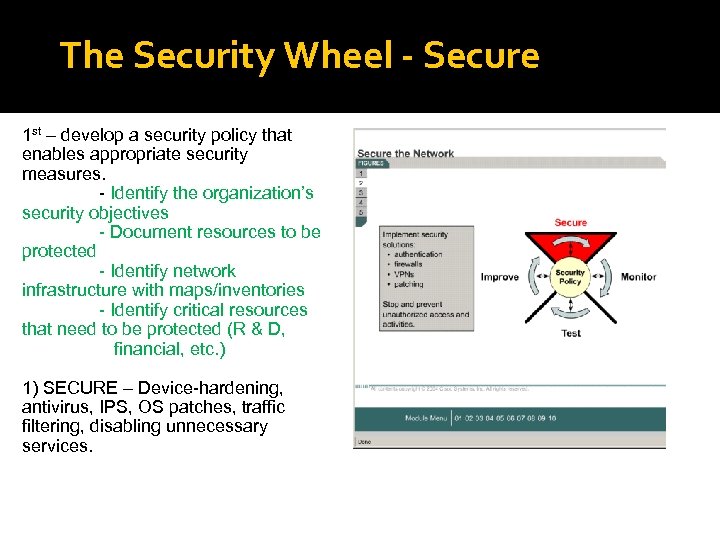 The Security Wheel - Secure 1 st – develop a security policy that enables appropriate security measures. - Identify the organization’s security objectives - Document resources to be protected - Identify network infrastructure with maps/inventories - Identify critical resources that need to be protected (R & D, financial, etc. ) 1) SECURE – Device-hardening, antivirus, IPS, OS patches, traffic filtering, disabling unnecessary services.
The Security Wheel - Secure 1 st – develop a security policy that enables appropriate security measures. - Identify the organization’s security objectives - Document resources to be protected - Identify network infrastructure with maps/inventories - Identify critical resources that need to be protected (R & D, financial, etc. ) 1) SECURE – Device-hardening, antivirus, IPS, OS patches, traffic filtering, disabling unnecessary services.
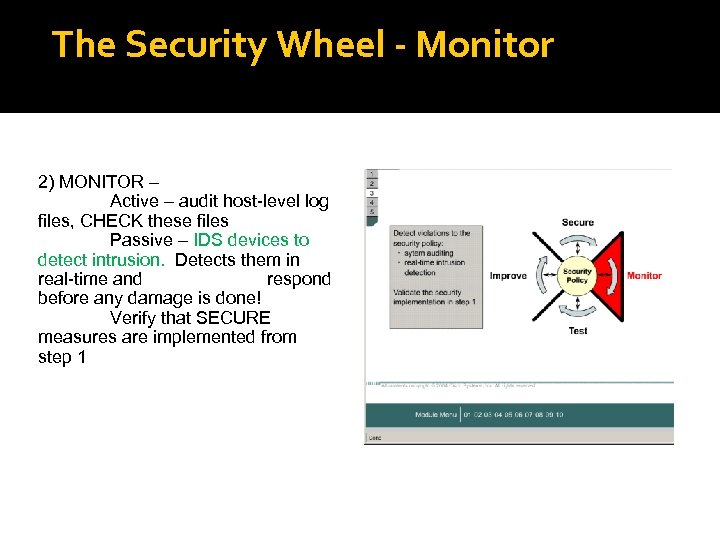 The Security Wheel - Monitor 2) MONITOR – Active – audit host-level log files, CHECK these files Passive – IDS devices to detect intrusion. Detects them in real-time and respond before any damage is done! Verify that SECURE measures are implemented from step 1
The Security Wheel - Monitor 2) MONITOR – Active – audit host-level log files, CHECK these files Passive – IDS devices to detect intrusion. Detects them in real-time and respond before any damage is done! Verify that SECURE measures are implemented from step 1
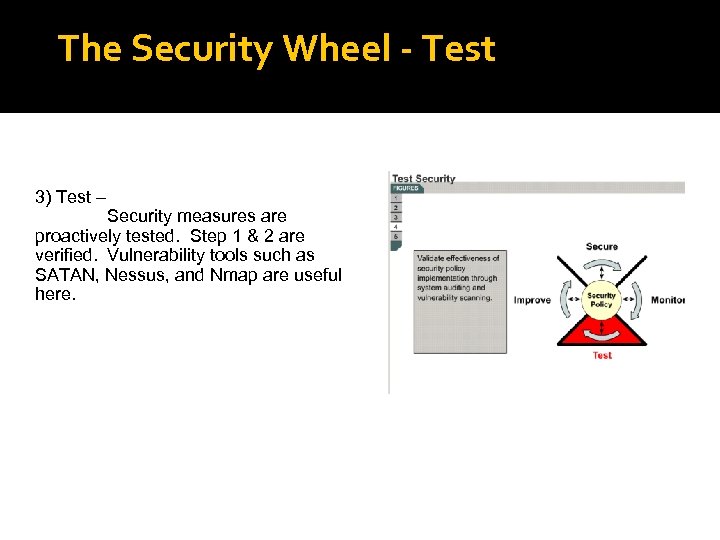 The Security Wheel - Test 3) Test – Security measures are proactively tested. Step 1 & 2 are verified. Vulnerability tools such as SATAN, Nessus, and Nmap are useful here.
The Security Wheel - Test 3) Test – Security measures are proactively tested. Step 1 & 2 are verified. Vulnerability tools such as SATAN, Nessus, and Nmap are useful here.
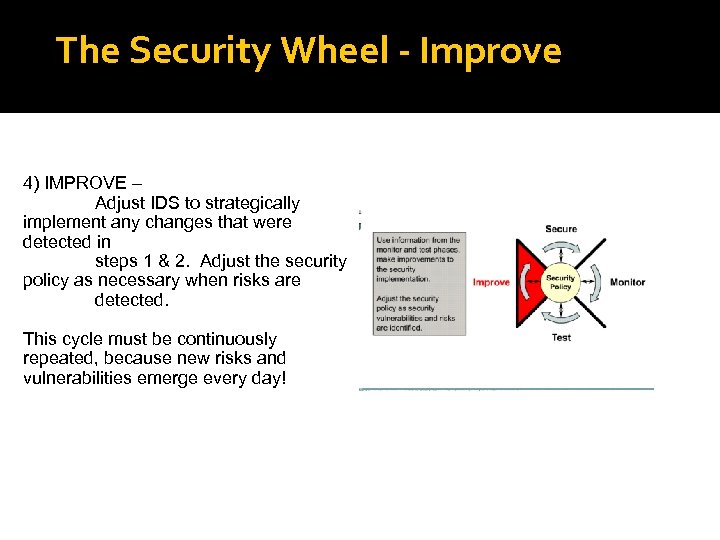 The Security Wheel - Improve 4) IMPROVE – Adjust IDS to strategically implement any changes that were detected in steps 1 & 2. Adjust the security policy as necessary when risks are detected. This cycle must be continuously repeated, because new risks and vulnerabilities emerge every day!
The Security Wheel - Improve 4) IMPROVE – Adjust IDS to strategically implement any changes that were detected in steps 1 & 2. Adjust the security policy as necessary when risks are detected. This cycle must be continuously repeated, because new risks and vulnerabilities emerge every day!
 Goals of a comprehensive security policy in an organization v. What is a security policy? v. Formal statement of the rules by which people who are given access to an organization’s technology and information assets must abide. v. Characteristics of a security Policy - Defines acceptable and unacceptable use of resources - Communicates consensus and defines roles - Defines how to handle security incidents
Goals of a comprehensive security policy in an organization v. What is a security policy? v. Formal statement of the rules by which people who are given access to an organization’s technology and information assets must abide. v. Characteristics of a security Policy - Defines acceptable and unacceptable use of resources - Communicates consensus and defines roles - Defines how to handle security incidents
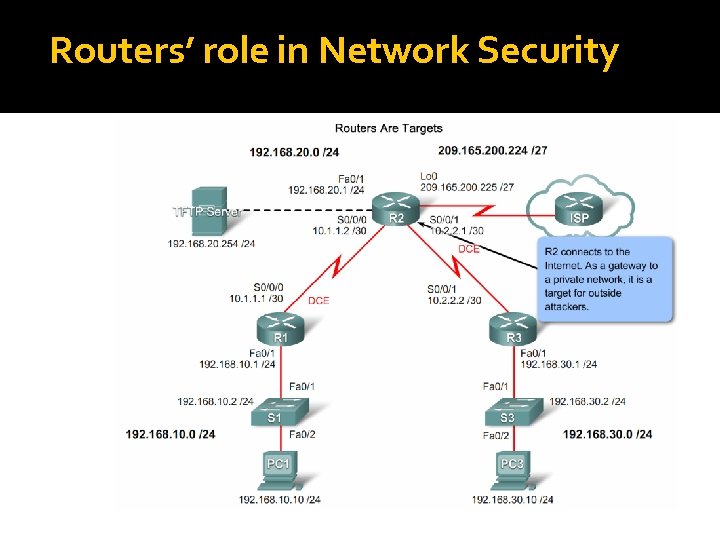 Routers’ role in Network Security
Routers’ role in Network Security
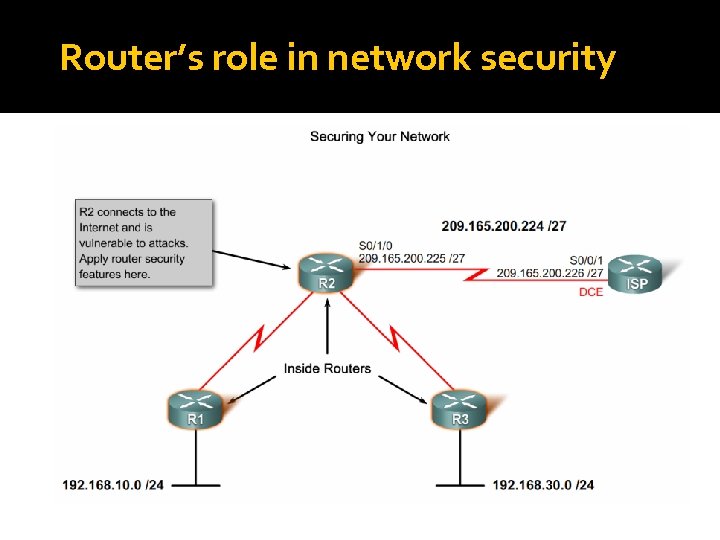 Router’s role in network security
Router’s role in network security
 Basic Router Security
Basic Router Security
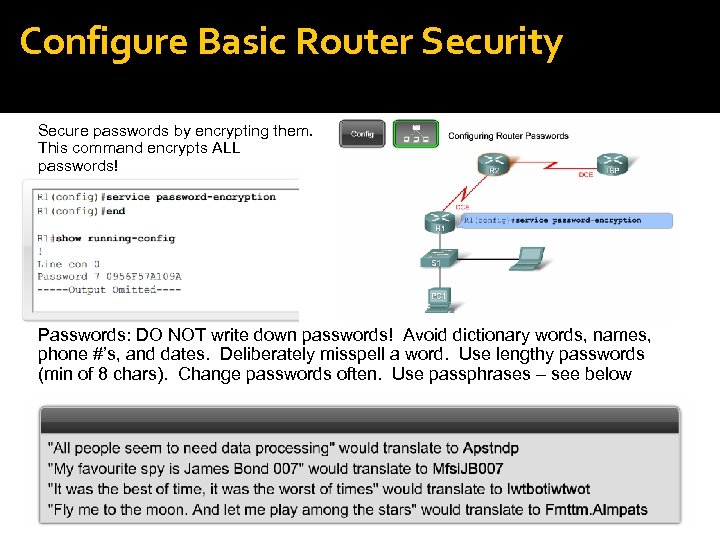 Configure Basic Router Security Secure passwords by encrypting them. This command encrypts ALL passwords! Passwords: DO NOT write down passwords! Avoid dictionary words, names, phone #’s, and dates. Deliberately misspell a word. Use lengthy passwords (min of 8 chars). Change passwords often. Use passphrases – see below
Configure Basic Router Security Secure passwords by encrypting them. This command encrypts ALL passwords! Passwords: DO NOT write down passwords! Avoid dictionary words, names, phone #’s, and dates. Deliberately misspell a word. Use lengthy passwords (min of 8 chars). Change passwords often. Use passphrases – see below
 Encryption methods Simple encryption – type 7 – uses a simple encryption algorithm Can be used on enable, user, and line passwords. Not as secure as type 5, but better than nothing. Complex encryption – type 5 – uses MD 5 hash Used when using the secret command for passwords. i. e. enable secret class – when displayed using show run shows up as encrypted. Min password length – security passwords min-length command Some routing protocols use passwords – i. e. Ip ospf message-disges-key 1 md 5 cisco - sets a key that is used to authenticate routing updates.
Encryption methods Simple encryption – type 7 – uses a simple encryption algorithm Can be used on enable, user, and line passwords. Not as secure as type 5, but better than nothing. Complex encryption – type 5 – uses MD 5 hash Used when using the secret command for passwords. i. e. enable secret class – when displayed using show run shows up as encrypted. Min password length – security passwords min-length command Some routing protocols use passwords – i. e. Ip ospf message-disges-key 1 md 5 cisco - sets a key that is used to authenticate routing updates.
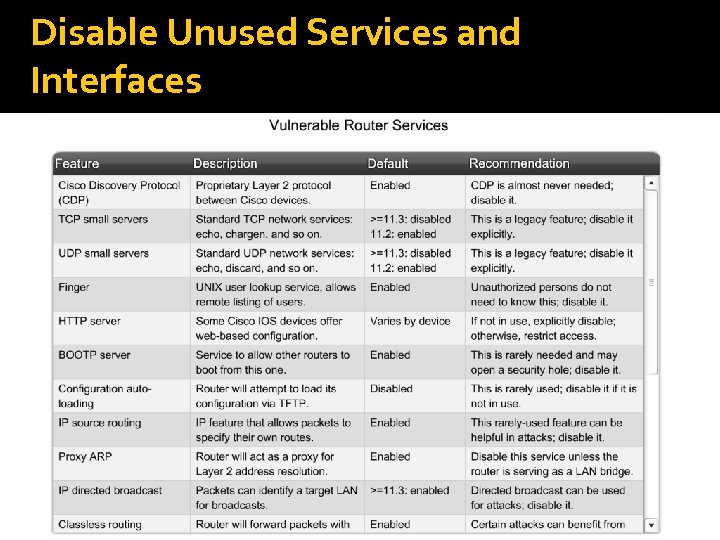 Disable Unused Services and Interfaces
Disable Unused Services and Interfaces
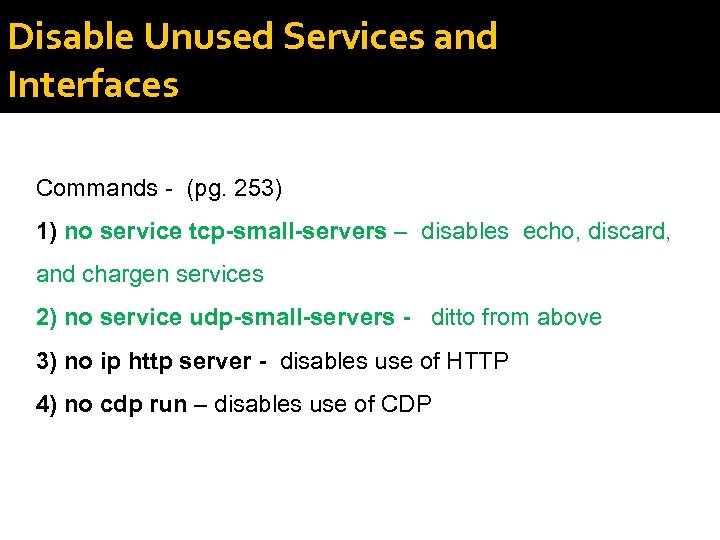 Disable Unused Services and Interfaces Commands - (pg. 253) 1) no service tcp-small-servers – disables echo, discard, and chargen services 2) no service udp-small-servers - ditto from above 3) no ip http server - disables use of HTTP 4) no cdp run – disables use of CDP
Disable Unused Services and Interfaces Commands - (pg. 253) 1) no service tcp-small-servers – disables echo, discard, and chargen services 2) no service udp-small-servers - ditto from above 3) no ip http server - disables use of HTTP 4) no cdp run – disables use of CDP
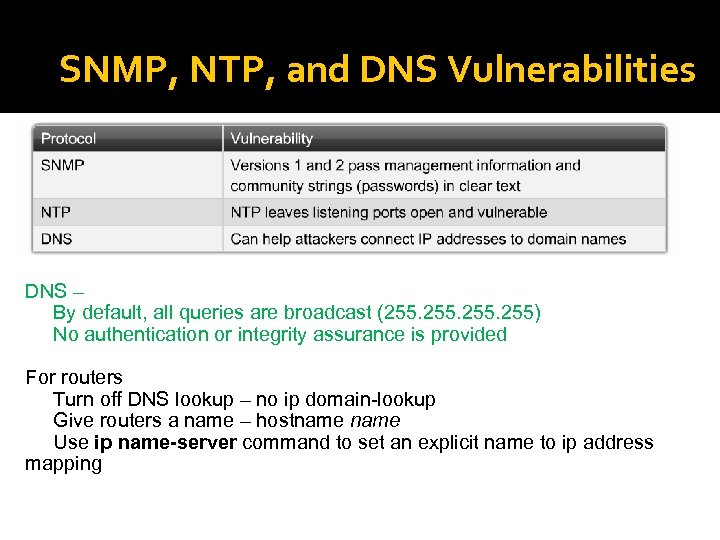 SNMP, NTP, and DNS Vulnerabilities DNS – By default, all queries are broadcast (255. 255) No authentication or integrity assurance is provided For routers Turn off DNS lookup – no ip domain-lookup Give routers a name – hostname Use ip name-server command to set an explicit name to ip address mapping
SNMP, NTP, and DNS Vulnerabilities DNS – By default, all queries are broadcast (255. 255) No authentication or integrity assurance is provided For routers Turn off DNS lookup – no ip domain-lookup Give routers a name – hostname Use ip name-server command to set an explicit name to ip address mapping
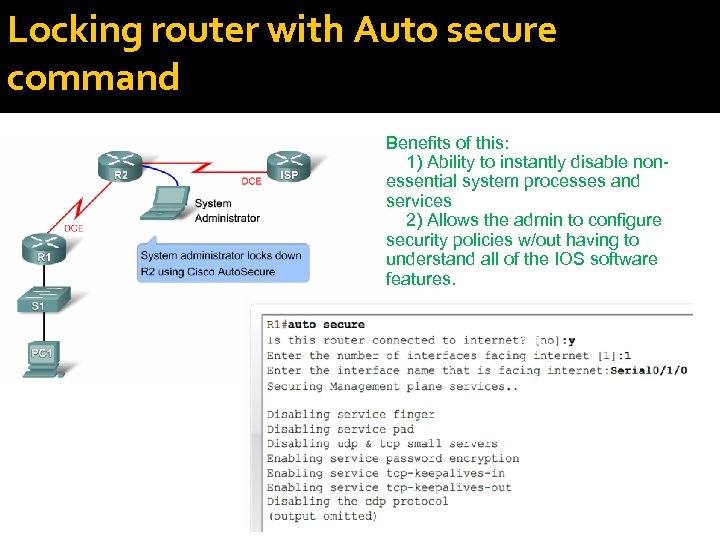 Locking router with Auto secure command Benefits of this: 1) Ability to instantly disable nonessential system processes and services 2) Allows the admin to configure security policies w/out having to understand all of the IOS software features.
Locking router with Auto secure command Benefits of this: 1) Ability to instantly disable nonessential system processes and services 2) Allows the admin to configure security policies w/out having to understand all of the IOS software features.
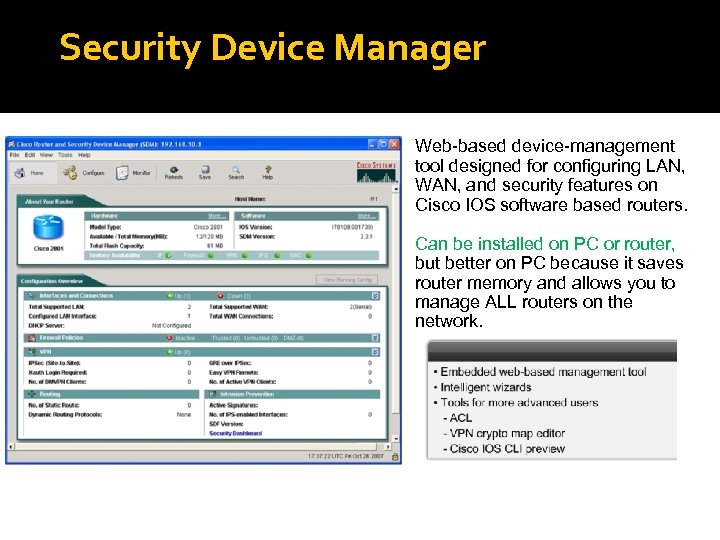 Security Device Manager Web-based device-management tool designed for configuring LAN, WAN, and security features on Cisco IOS software based routers. Can be installed on PC or router, but better on PC because it saves router memory and allows you to manage ALL routers on the network.
Security Device Manager Web-based device-management tool designed for configuring LAN, WAN, and security features on Cisco IOS software based routers. Can be installed on PC or router, but better on PC because it saves router memory and allows you to manage ALL routers on the network.
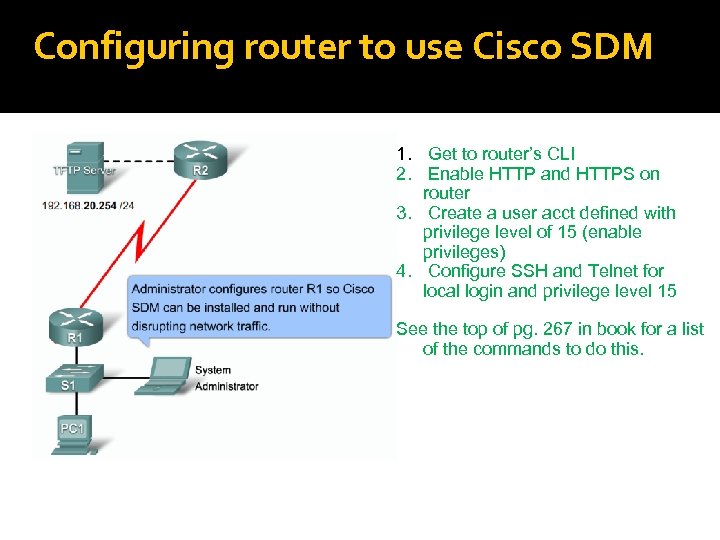 Configuring router to use Cisco SDM 1. Get to router’s CLI 2. Enable HTTP and HTTPS on router 3. Create a user acct defined with privilege level of 15 (enable privileges) 4. Configure SSH and Telnet for local login and privilege level 15 See the top of pg. 267 in book for a list of the commands to do this.
Configuring router to use Cisco SDM 1. Get to router’s CLI 2. Enable HTTP and HTTPS on router 3. Create a user acct defined with privilege level of 15 (enable privileges) 4. Configure SSH and Telnet for local login and privilege level 15 See the top of pg. 267 in book for a list of the commands to do this.
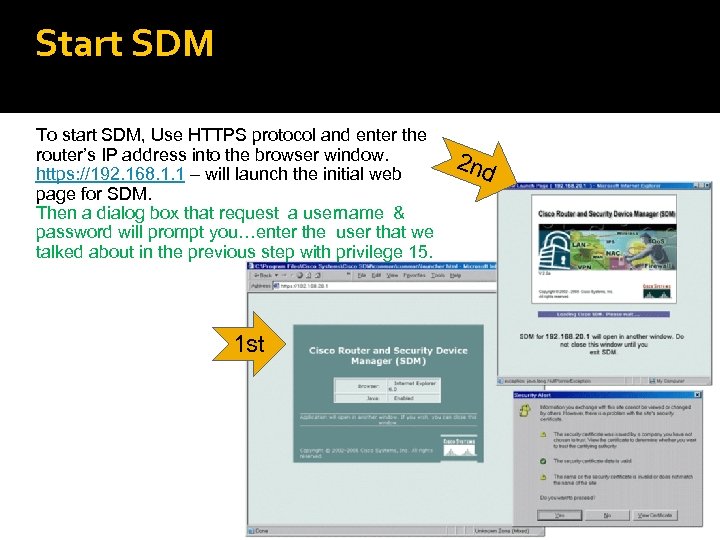 Start SDM To start SDM, Use HTTPS protocol and enter the router’s IP address into the browser window. https: //192. 168. 1. 1 – will launch the initial web page for SDM. Then a dialog box that request a username & password will prompt you…enter the user that we talked about in the previous step with privilege 15. 1 st 2 nd
Start SDM To start SDM, Use HTTPS protocol and enter the router’s IP address into the browser window. https: //192. 168. 1. 1 – will launch the initial web page for SDM. Then a dialog box that request a username & password will prompt you…enter the user that we talked about in the previous step with privilege 15. 1 st 2 nd
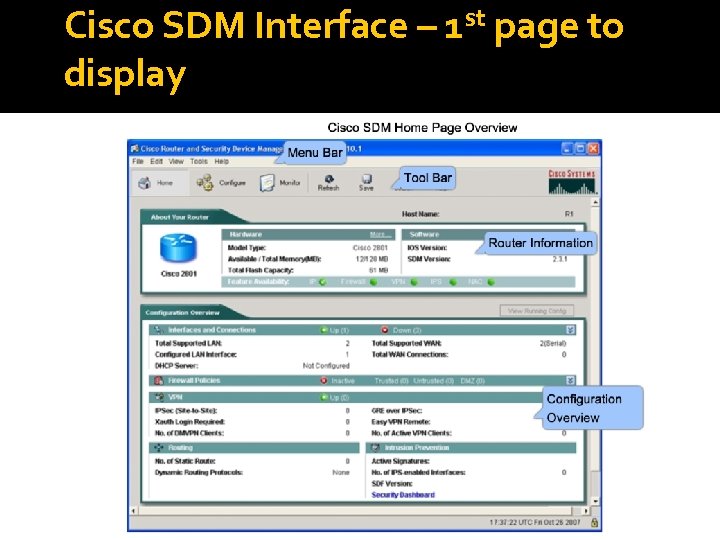 Cisco SDM Interface – 1 st page to display
Cisco SDM Interface – 1 st page to display
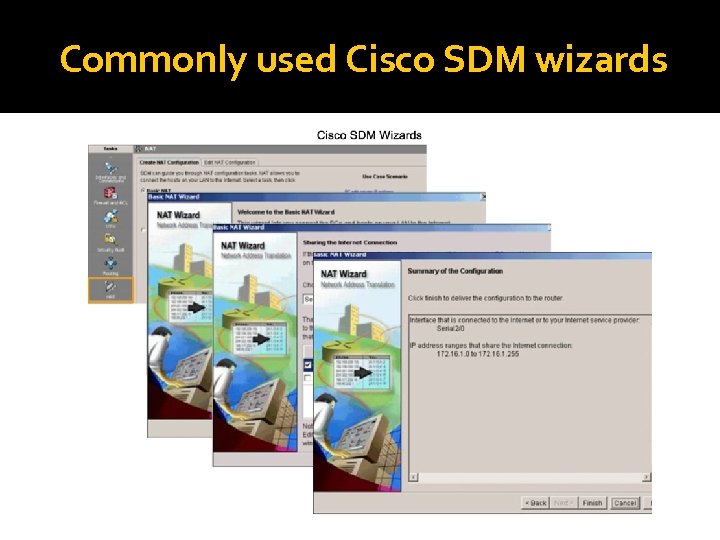 Commonly used Cisco SDM wizards
Commonly used Cisco SDM wizards
 Locking down your router with SDM 1. Use the Security Audit Wizard to find and fix configuration changes that may leave your network vulnerable.
Locking down your router with SDM 1. Use the Security Audit Wizard to find and fix configuration changes that may leave your network vulnerable.
 IOS Maintenance Periodically, the router requires updates to be loaded to either the operating system or the configuration file. These updates are necessary to fix known security vulnerabilities, support new features that allow more advanced security policies, or improve performance Naming convention for IOS – (pg. 282) C 1841 -ipbase-mz. 123 -14. t 7. bin C 1841 – platform (cisco 1841 router) ipbase – feature set (basic IP networking image…there are others) mz – where the image runs and if it is compressed. (RAM, compressed) 123 -14. T 7 – version # bin – file extension (binary executable)
IOS Maintenance Periodically, the router requires updates to be loaded to either the operating system or the configuration file. These updates are necessary to fix known security vulnerabilities, support new features that allow more advanced security policies, or improve performance Naming convention for IOS – (pg. 282) C 1841 -ipbase-mz. 123 -14. t 7. bin C 1841 – platform (cisco 1841 router) ipbase – feature set (basic IP networking image…there are others) mz – where the image runs and if it is compressed. (RAM, compressed) 123 -14. T 7 – version # bin – file extension (binary executable)
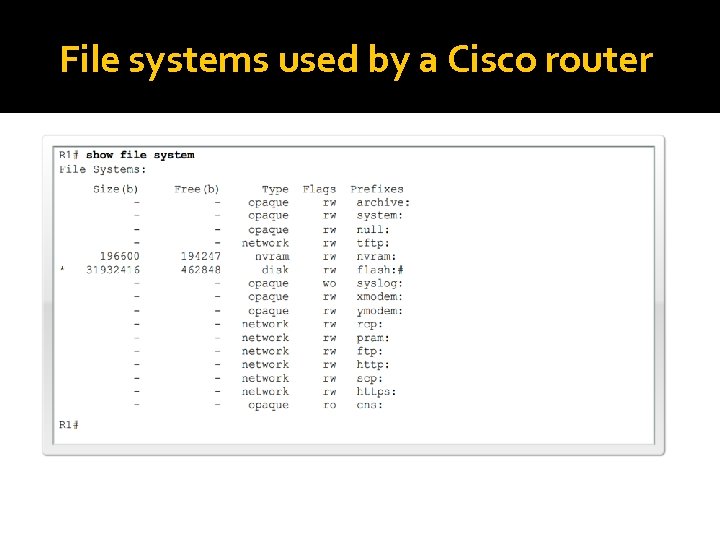 File systems used by a Cisco router
File systems used by a Cisco router
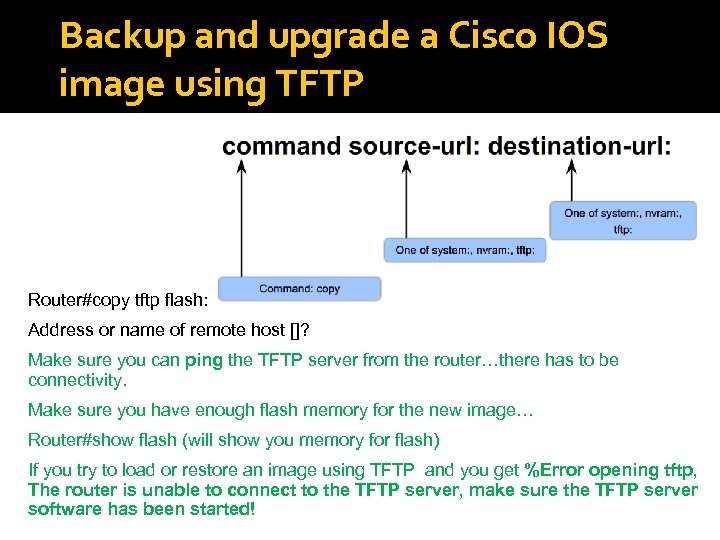 Backup and upgrade a Cisco IOS image using TFTP Router#copy tftp flash: Address or name of remote host []? Make sure you can ping the TFTP server from the router…there has to be connectivity. Make sure you have enough flash memory for the new image… Router#show flash (will show you memory for flash) If you try to load or restore an image using TFTP and you get %Error opening tftp, The router is unable to connect to the TFTP server, make sure the TFTP server software has been started!
Backup and upgrade a Cisco IOS image using TFTP Router#copy tftp flash: Address or name of remote host []? Make sure you can ping the TFTP server from the router…there has to be connectivity. Make sure you have enough flash memory for the new image… Router#show flash (will show you memory for flash) If you try to load or restore an image using TFTP and you get %Error opening tftp, The router is unable to connect to the TFTP server, make sure the TFTP server software has been started!
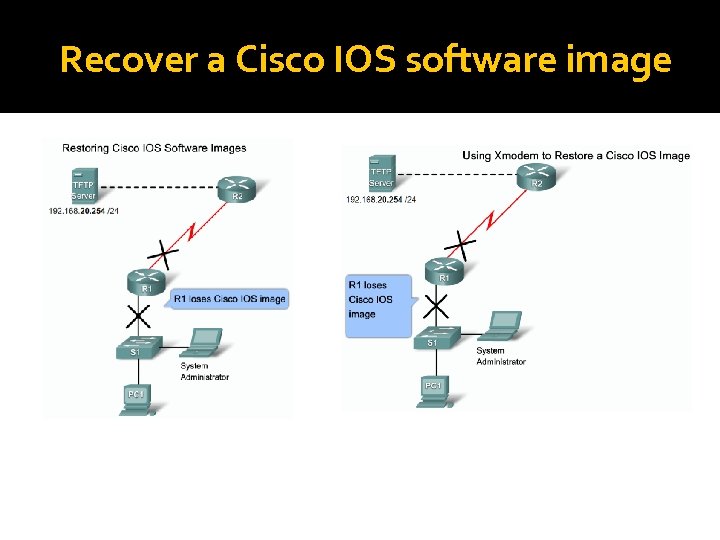 Recover a Cisco IOS software image
Recover a Cisco IOS software image
 Cisco IOS Troubleshooting We have used various show and debug commands during these last 3 or 4 semesters… Here a few pointers 1) Debug – use it carefully…it gets CPU priority. With debug, it is helpful to know what you are looking for before you start. 2) Show – displays static information. Used to confirm configuration changes.
Cisco IOS Troubleshooting We have used various show and debug commands during these last 3 or 4 semesters… Here a few pointers 1) Debug – use it carefully…it gets CPU priority. With debug, it is helpful to know what you are looking for before you start. 2) Show – displays static information. Used to confirm configuration changes.
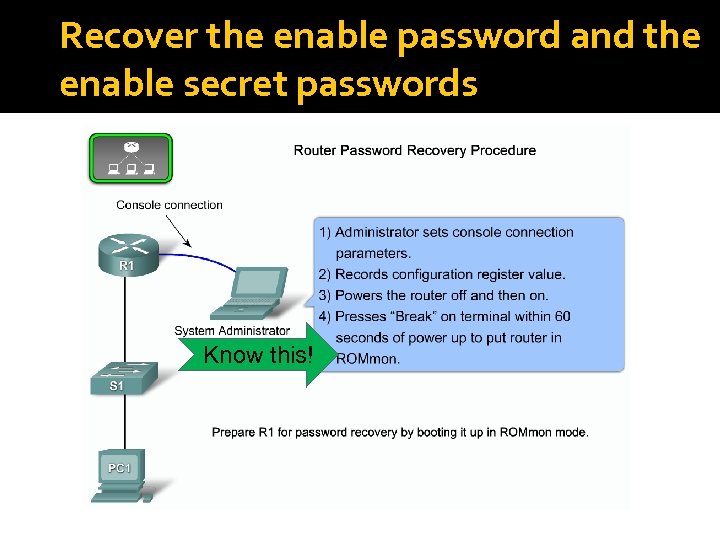 Recover the enable password and the enable secret passwords Know this!
Recover the enable password and the enable secret passwords Know this!
 Steps in password recovery Connect via the console port Show version – show current config register Turn off router – turn router back on and press Break on the keyboard within 60 seconds. 4. You will be at rommon> prompt 5. Change the config register to 0 x 2142 which will bypass NVRAM when you re-boot. 6. Type reset at the prompt 7. Get into privilege mode 8. Config t – get into global config mode 9. Change password – enable secret password 10. Enter config-register 0 x 2102 to reset the config register 11. Copy run start – your password and config register is reset! 1. 2. 3.
Steps in password recovery Connect via the console port Show version – show current config register Turn off router – turn router back on and press Break on the keyboard within 60 seconds. 4. You will be at rommon> prompt 5. Change the config register to 0 x 2142 which will bypass NVRAM when you re-boot. 6. Type reset at the prompt 7. Get into privilege mode 8. Config t – get into global config mode 9. Change password – enable secret password 10. Enter config-register 0 x 2102 to reset the config register 11. Copy run start – your password and config register is reset! 1. 2. 3.
 Whew…this chapter is over Study guide Pg. 126 - Matching Pg. 128 -129 – Configuring Router Passwords Pg. 131 – Preparing a router for SDM Labs 4 -1, pg. 135 Online Test – On until Wed, Feb. 27, midnite! Test – You will be asked to write a 1 -2 page article on a topic dealing with network security. I will check for grammar, spelling, and content. This will be done in class at the next class meeting.
Whew…this chapter is over Study guide Pg. 126 - Matching Pg. 128 -129 – Configuring Router Passwords Pg. 131 – Preparing a router for SDM Labs 4 -1, pg. 135 Online Test – On until Wed, Feb. 27, midnite! Test – You will be asked to write a 1 -2 page article on a topic dealing with network security. I will check for grammar, spelling, and content. This will be done in class at the next class meeting.


