731edda9fadb281d5d88d830f03c344a.ppt
- Количество слайдов: 42
 Network Security 2 Module 5 – Configure Site-to-Site VPNs Using Digital Certificates © 2006 Cisco Systems, Inc. All rights reserved.
Network Security 2 Module 5 – Configure Site-to-Site VPNs Using Digital Certificates © 2006 Cisco Systems, Inc. All rights reserved.
 Module 5 – Configure Site-to-Site VPNs Using Digital Certificates Lesson 5. 1 Configure CA Support on a Cisco Router © 2006 Cisco Systems, Inc. All rights reserved.
Module 5 – Configure Site-to-Site VPNs Using Digital Certificates Lesson 5. 1 Configure CA Support on a Cisco Router © 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
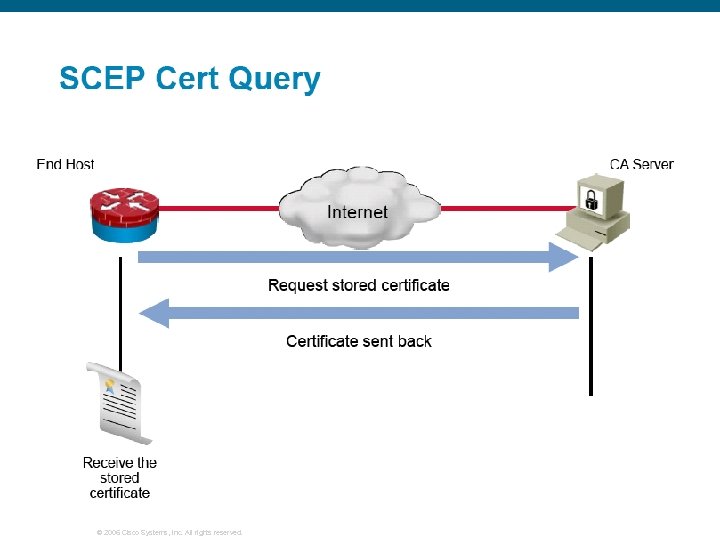
 (Optional) Manage NVRAM Memory Usage Types of certificates stored on a router: The identity certificate of the router The root certificate of the CA Root certificates obtained from CA servers Two RA certificates, these are CA vendor-specific The number of CRLs stored on a router: One, if the CA does not support an RA Multiple, if the CA supports an RA Turn on query mode by using crypto ca certificate query © 2006 Cisco Systems, Inc. All rights reserved.
(Optional) Manage NVRAM Memory Usage Types of certificates stored on a router: The identity certificate of the router The root certificate of the CA Root certificates obtained from CA servers Two RA certificates, these are CA vendor-specific The number of CRLs stored on a router: One, if the CA does not support an RA Multiple, if the CA supports an RA Turn on query mode by using crypto ca certificate query © 2006 Cisco Systems, Inc. All rights reserved.
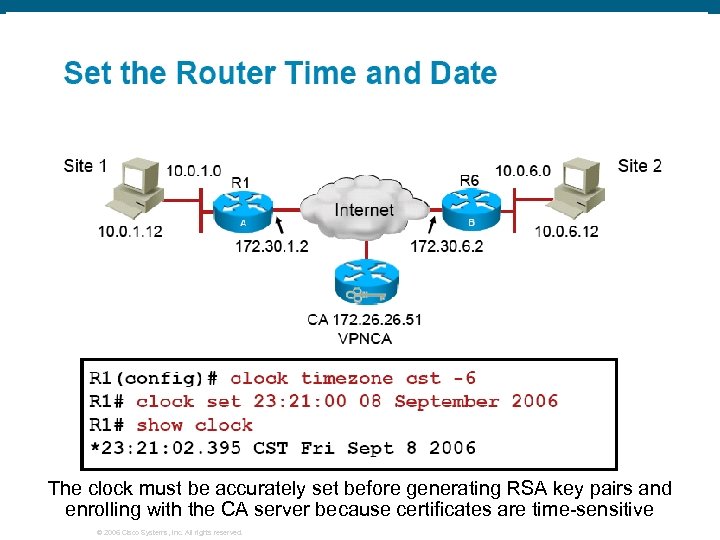 The clock must be accurately set before generating RSA key pairs and enrolling with the CA server because certificates are time-sensitive © 2006 Cisco Systems, Inc. All rights reserved.
The clock must be accurately set before generating RSA key pairs and enrolling with the CA server because certificates are time-sensitive © 2006 Cisco Systems, Inc. All rights reserved.
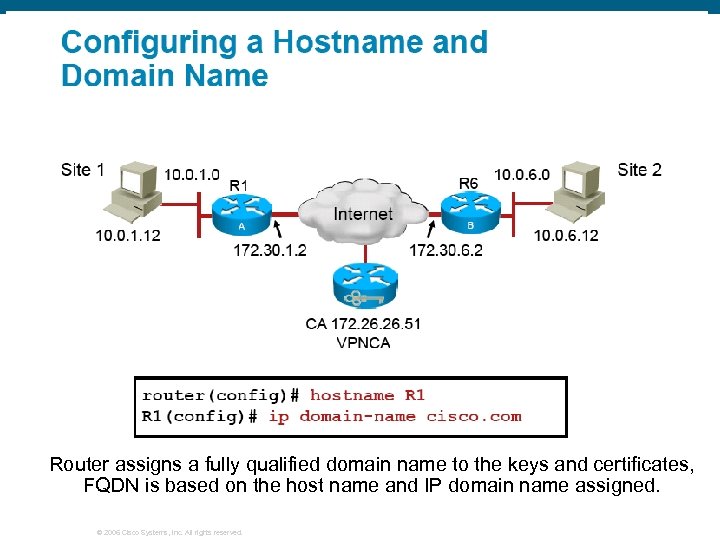 Router assigns a fully qualified domain name to the keys and certificates, FQDN is based on the host name and IP domain name assigned. © 2006 Cisco Systems, Inc. All rights reserved.
Router assigns a fully qualified domain name to the keys and certificates, FQDN is based on the host name and IP domain name assigned. © 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 RSA key pairs are used to sign and encrypt IKE key management messages and are required before obtaining a certificate for the router. © 2006 Cisco Systems, Inc. All rights reserved.
RSA key pairs are used to sign and encrypt IKE key management messages and are required before obtaining a certificate for the router. © 2006 Cisco Systems, Inc. All rights reserved.
 Generating RSA Keys § Two mutually exclusive types of RSA key pairs § Special-usage Keys Two pairs of RSA keys are created. One for RSA signatures, and the other for RSA encrypted nonces as the authentication method. § Each key is not unnecessarily exposed § General-purpose Keys One pair of RSA keys is created. Used with IKE policies specifying either RSA signatures or RSA encrypted nonces. § A longer modulus could offer stronger security, but takes longer to generate and also takes longer to use. § Cisco recommends using a minimum modulus of 1024. © 2006 Cisco Systems, Inc. All rights reserved.
Generating RSA Keys § Two mutually exclusive types of RSA key pairs § Special-usage Keys Two pairs of RSA keys are created. One for RSA signatures, and the other for RSA encrypted nonces as the authentication method. § Each key is not unnecessarily exposed § General-purpose Keys One pair of RSA keys is created. Used with IKE policies specifying either RSA signatures or RSA encrypted nonces. § A longer modulus could offer stronger security, but takes longer to generate and also takes longer to use. § Cisco recommends using a minimum modulus of 1024. © 2006 Cisco Systems, Inc. All rights reserved.
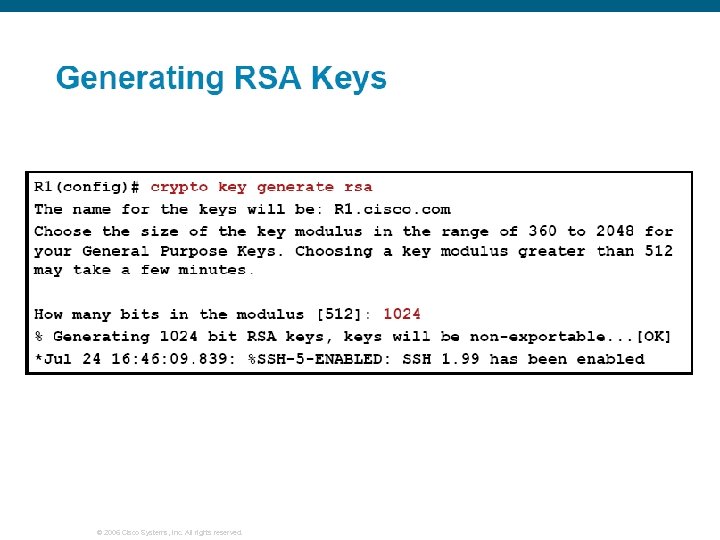 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
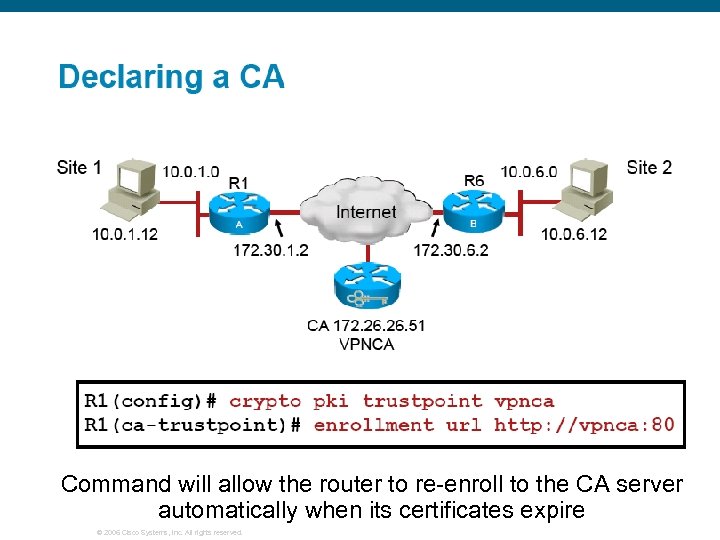 Command will allow the router to re-enroll to the CA server automatically when its certificates expire © 2006 Cisco Systems, Inc. All rights reserved.
Command will allow the router to re-enroll to the CA server automatically when its certificates expire © 2006 Cisco Systems, Inc. All rights reserved.
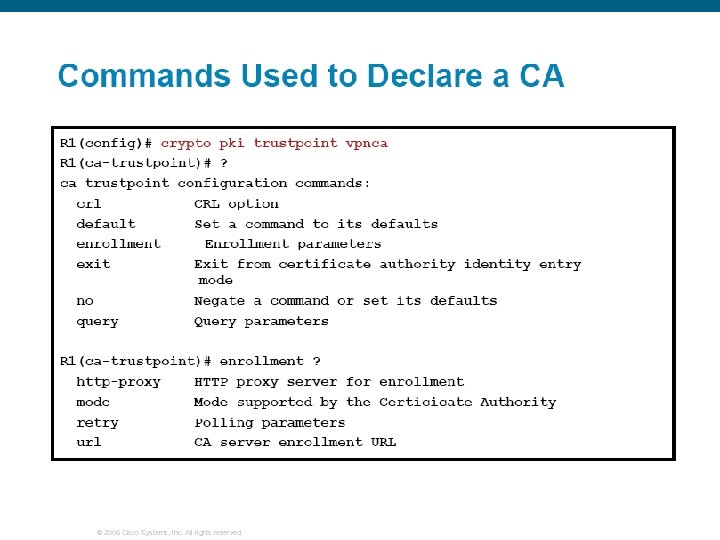 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
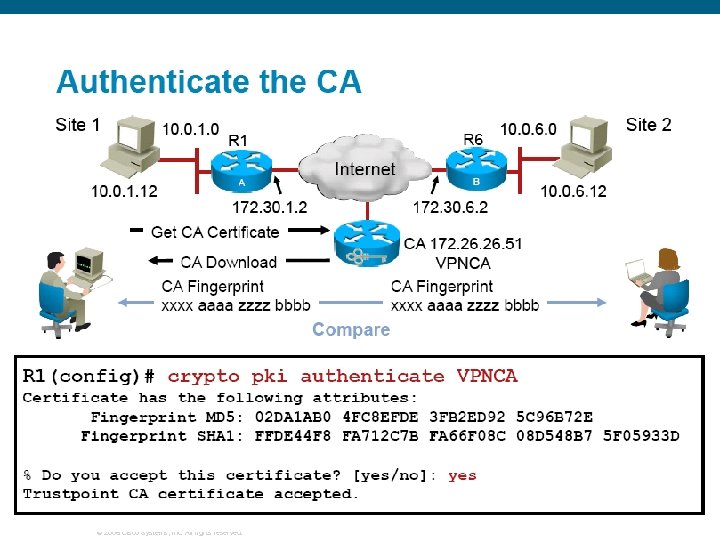 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 Authenticate CA § The router needs to authenticate the CA to verify that it is valid. § Done by obtaining the self-signed certificate of the CA Contains the public key of the CA. § Because the CA certificate is self-signed the public key of the CA should be manually authenticated. Done by contacting the CA administrator to verify the fingerprint of the CA certificate. § To get the public key of the CA, use the crypto pki authenticatename command § Use the same name that was used when declaring the CA with the crypto pki trustpoint command. © 2006 Cisco Systems, Inc. All rights reserved.
Authenticate CA § The router needs to authenticate the CA to verify that it is valid. § Done by obtaining the self-signed certificate of the CA Contains the public key of the CA. § Because the CA certificate is self-signed the public key of the CA should be manually authenticated. Done by contacting the CA administrator to verify the fingerprint of the CA certificate. § To get the public key of the CA, use the crypto pki authenticatename command § Use the same name that was used when declaring the CA with the crypto pki trustpoint command. © 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
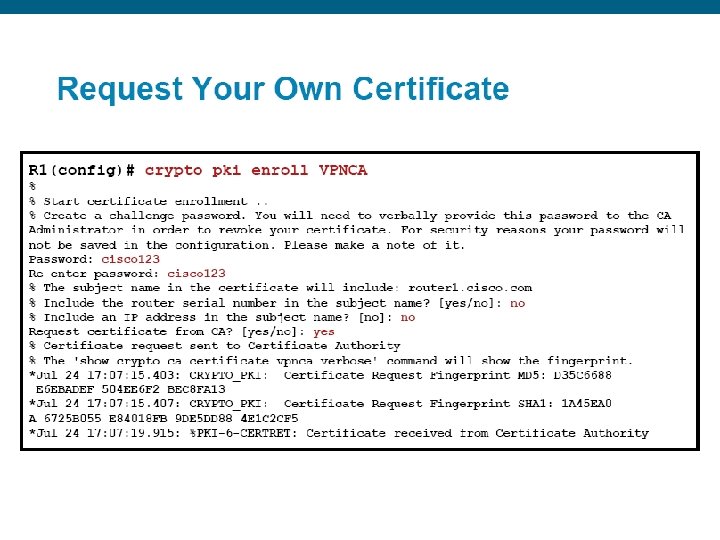
 Request a certificate for the router § A signed certificate must be obtained from the CA for each RSA key pair on the router. crypto pki enroll name § During the enrollment process, a challenge password is created. Can be used by the CA administrator to validate the identity of the individual that is requesting the certificate. § If a certificate for the keys already exists, the administrator is prompted to remove the existing certificate first. no certificate command. © 2006 Cisco Systems, Inc. All rights reserved.
Request a certificate for the router § A signed certificate must be obtained from the CA for each RSA key pair on the router. crypto pki enroll name § During the enrollment process, a challenge password is created. Can be used by the CA administrator to validate the identity of the individual that is requesting the certificate. § If a certificate for the keys already exists, the administrator is prompted to remove the existing certificate first. no certificate command. © 2006 Cisco Systems, Inc. All rights reserved.
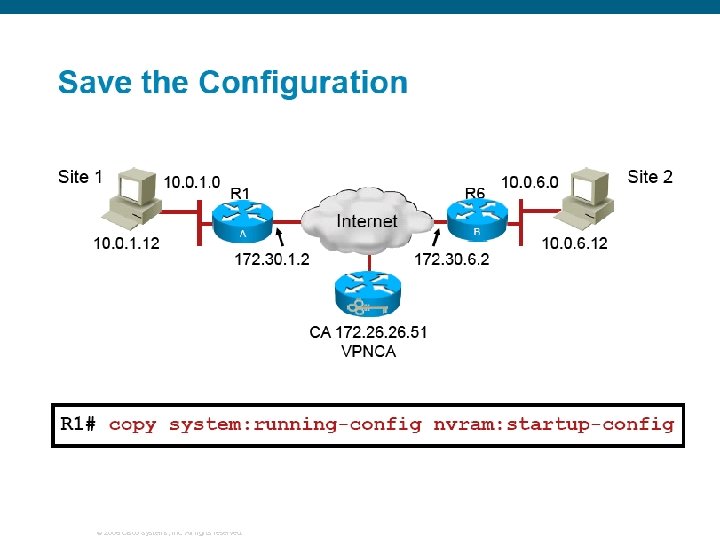 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 Monitor and Maintain CA Interoperability (Optional) § The following steps are optional, depending on the particular requirements: Request a CRL Query a CRL Delete RSA Keys from the router Delete peer public keys Delete certificates from the configuration View keys and certificates © 2006 Cisco Systems, Inc. All rights reserved.
Monitor and Maintain CA Interoperability (Optional) § The following steps are optional, depending on the particular requirements: Request a CRL Query a CRL Delete RSA Keys from the router Delete peer public keys Delete certificates from the configuration View keys and certificates © 2006 Cisco Systems, Inc. All rights reserved.
 Request a Certificate Revocation List § When the router receives a certificate from a peer, the router will download a CRL from the CA. § Router then checks the CRL to make sure the certificate that the peer sent has not been revoked. § If the certificate appears on the CRL, the router will not accept the certificate and will not authenticate the peer. § A CRL can be reused with subsequent certificates until the CRL expires if query mode is off. § To request immediate download of the latest CRL, use the crypto pki crl request name © 2006 Cisco Systems, Inc. All rights reserved.
Request a Certificate Revocation List § When the router receives a certificate from a peer, the router will download a CRL from the CA. § Router then checks the CRL to make sure the certificate that the peer sent has not been revoked. § If the certificate appears on the CRL, the router will not accept the certificate and will not authenticate the peer. § A CRL can be reused with subsequent certificates until the CRL expires if query mode is off. § To request immediate download of the latest CRL, use the crypto pki crl request name © 2006 Cisco Systems, Inc. All rights reserved.
 Delete RSA Keys from the Router § If the RSA keys are believed to be compromised § crypto key zeroize rsa § After the RSA keys are deleted, the CA administrator should be asked to revoke certificates for the router at the CA. § It will be necessary to supply the challenge password created when the certificated were obtained with the crypto pki enroll command. § The certificates should also be manually removed from the router configuration. © 2006 Cisco Systems, Inc. All rights reserved.
Delete RSA Keys from the Router § If the RSA keys are believed to be compromised § crypto key zeroize rsa § After the RSA keys are deleted, the CA administrator should be asked to revoke certificates for the router at the CA. § It will be necessary to supply the challenge password created when the certificated were obtained with the crypto pki enroll command. § The certificates should also be manually removed from the router configuration. © 2006 Cisco Systems, Inc. All rights reserved.
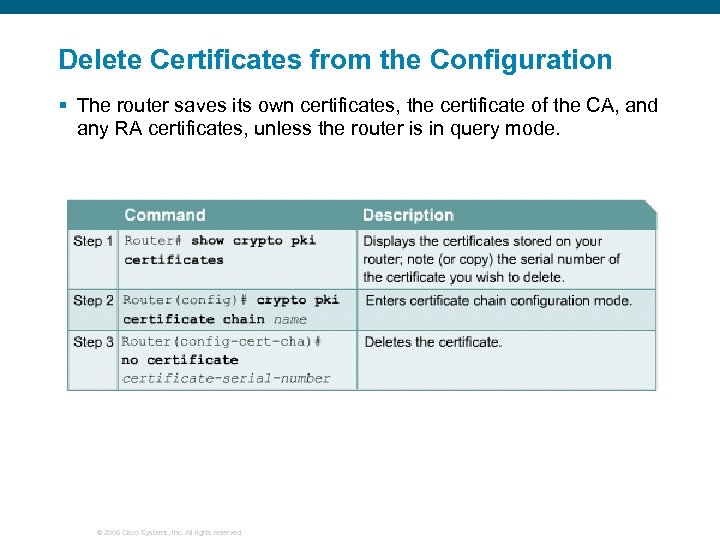 Delete Certificates from the Configuration § The router saves its own certificates, the certificate of the CA, and any RA certificates, unless the router is in query mode. © 2006 Cisco Systems, Inc. All rights reserved.
Delete Certificates from the Configuration § The router saves its own certificates, the certificate of the CA, and any RA certificates, unless the router is in query mode. © 2006 Cisco Systems, Inc. All rights reserved.
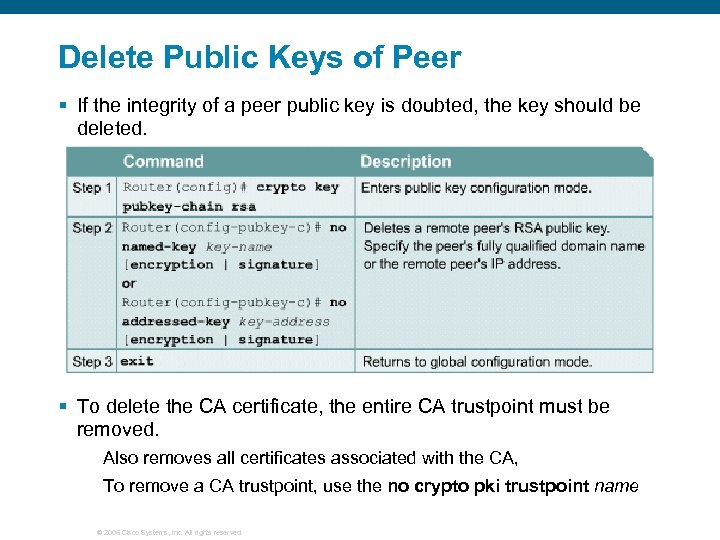 Delete Public Keys of Peer § If the integrity of a peer public key is doubted, the key should be deleted. § To delete the CA certificate, the entire CA trustpoint must be removed. Also removes all certificates associated with the CA, To remove a CA trustpoint, use the no crypto pki trustpoint name © 2006 Cisco Systems, Inc. All rights reserved.
Delete Public Keys of Peer § If the integrity of a peer public key is doubted, the key should be deleted. § To delete the CA certificate, the entire CA trustpoint must be removed. Also removes all certificates associated with the CA, To remove a CA trustpoint, use the no crypto pki trustpoint name © 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
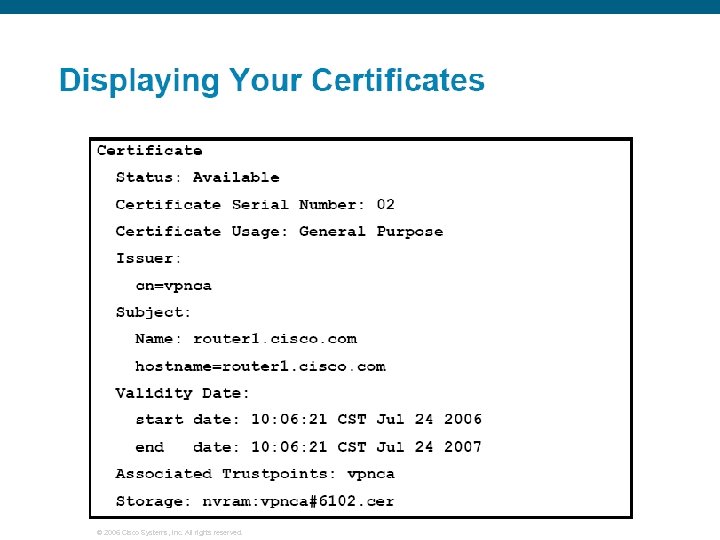 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
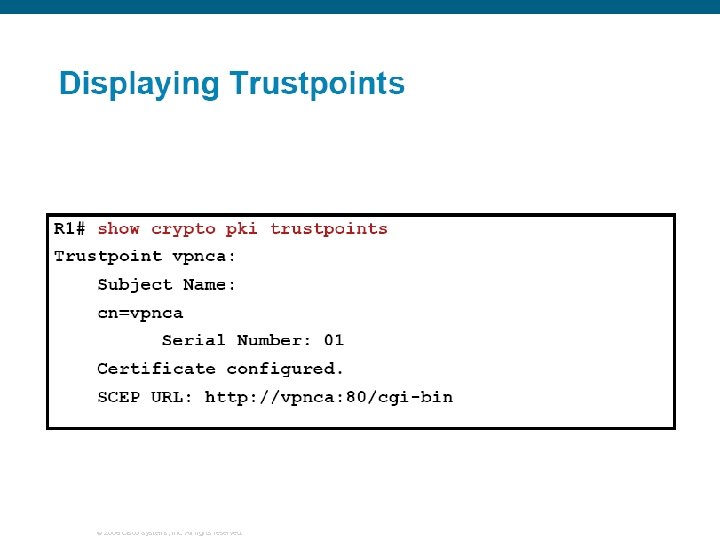 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
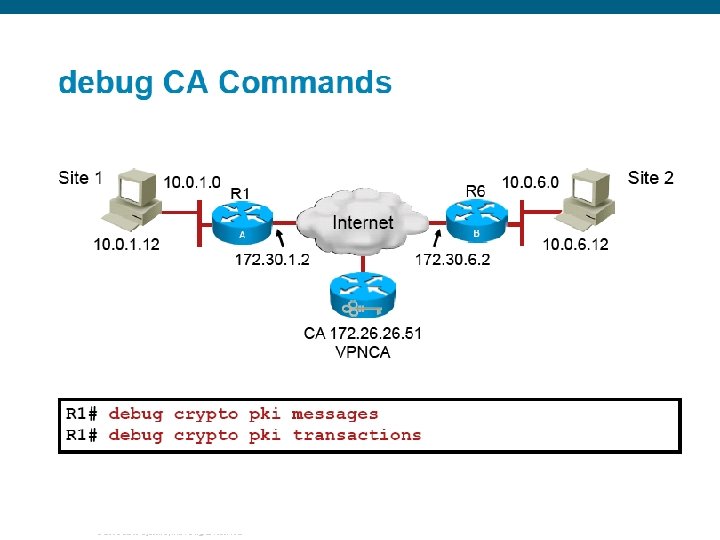 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.
 Q and A © 2006 Cisco Systems, Inc. All rights reserved.
Q and A © 2006 Cisco Systems, Inc. All rights reserved.
 © 2006 Cisco Systems, Inc. All rights reserved.
© 2006 Cisco Systems, Inc. All rights reserved.


