98e2dfbcb9ef5c0859de4ed083202132.ppt
- Количество слайдов: 27
 Network Layer Security: IPSec
Network Layer Security: IPSec
 Overview § IPSec is an Internet standard for network layer security § components: – an authentication protocol (Authentication Header – AH) – a combined encryption and authentication protocol (Encapsulated Security Payload – ESP) – key management protocols (the default is ISAKMP/Oakley) § important RFCs – – – RFC 2401: an overview of the IPSec security architecture RFC 2402: specification of AH RFC 2406: specification of ESP RFC 2408: specification of ISAKMP RFC 2412: specification of Oakley § IPSec is mandatory for IPv 6 and optional for IPv 4 2
Overview § IPSec is an Internet standard for network layer security § components: – an authentication protocol (Authentication Header – AH) – a combined encryption and authentication protocol (Encapsulated Security Payload – ESP) – key management protocols (the default is ISAKMP/Oakley) § important RFCs – – – RFC 2401: an overview of the IPSec security architecture RFC 2402: specification of AH RFC 2406: specification of ESP RFC 2408: specification of ISAKMP RFC 2412: specification of Oakley § IPSec is mandatory for IPv 6 and optional for IPv 4 2
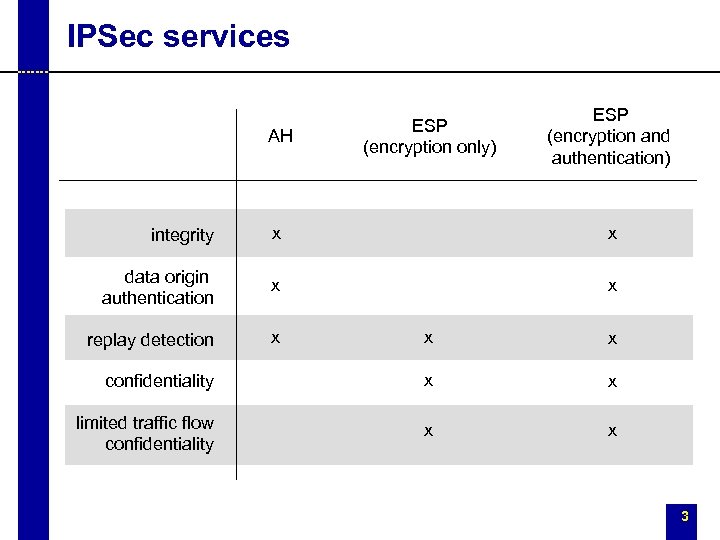 IPSec services AH ESP (encryption only) ESP (encryption and authentication) integrity x x data origin authentication x x replay detection x x x confidentiality x x limited traffic flow confidentiality x x 3
IPSec services AH ESP (encryption only) ESP (encryption and authentication) integrity x x data origin authentication x x replay detection x x x confidentiality x x limited traffic flow confidentiality x x 3
 Security associations (SA) § an SA is a one-way relationship between a sender and a receiver system § an SA is used either for AH or for ESP but never for both § an SA is uniquely identified by three parameters – Security Parameters Index (SPI) Security Associations • a bit string assigned to the SA • carried in AH and ESP headers to allow the receiving party to select the SA which must be used to process the packet – IP destination address • address of an end-system or a network element (e. g. , router) – security protocol identifier • indicates whether the SA is an AH or an ESP SA 4
Security associations (SA) § an SA is a one-way relationship between a sender and a receiver system § an SA is used either for AH or for ESP but never for both § an SA is uniquely identified by three parameters – Security Parameters Index (SPI) Security Associations • a bit string assigned to the SA • carried in AH and ESP headers to allow the receiving party to select the SA which must be used to process the packet – IP destination address • address of an end-system or a network element (e. g. , router) – security protocol identifier • indicates whether the SA is an AH or an ESP SA 4
 SA parameters § sequence number counter – counts the packets sent using this SA § sequence counter overflow flag – indicates whether overflow of the sequence number counter should prevent further transmission using this SA § anti-replay window – used to determine whether an inbound AH or ESP packet is a replay § AH / ESP information Security Associations – algorithm, key, and related parameters § lifetime – a time interval or byte count after which this SA must be terminated § protocol mode – tunnel or transport mode § path MTU – any observed maximum transmission unit 5
SA parameters § sequence number counter – counts the packets sent using this SA § sequence counter overflow flag – indicates whether overflow of the sequence number counter should prevent further transmission using this SA § anti-replay window – used to determine whether an inbound AH or ESP packet is a replay § AH / ESP information Security Associations – algorithm, key, and related parameters § lifetime – a time interval or byte count after which this SA must be terminated § protocol mode – tunnel or transport mode § path MTU – any observed maximum transmission unit 5
 SA selectors § Security Policy Database (SPD) – each entry defines a subset of IP traffic and points to the SAs to be applied to that traffic – subset of IP traffic is defined in terms of selectors Security Associations • destination IP address (single, enumerated list, range, or mask) • source IP address (single, enumerated list, range, or mask) • transport layer protocol (single, enumerated list, or range) • destination port (single, enumerated list, range, or wildcard) • … § outbound processing – compare the selector fields of the packet to the values in the SPD – determine which SAs should be used for the packet and their SPIs – do the requiered IPSec processing 6
SA selectors § Security Policy Database (SPD) – each entry defines a subset of IP traffic and points to the SAs to be applied to that traffic – subset of IP traffic is defined in terms of selectors Security Associations • destination IP address (single, enumerated list, range, or mask) • source IP address (single, enumerated list, range, or mask) • transport layer protocol (single, enumerated list, or range) • destination port (single, enumerated list, range, or wildcard) • … § outbound processing – compare the selector fields of the packet to the values in the SPD – determine which SAs should be used for the packet and their SPIs – do the requiered IPSec processing 6
 Modes of operation § transport mode – provides protection primarily for upper layer protocols – protection is applied to the payload of the IP packet • ESP in transport mode encrypts and optionally authenticates the IP payload but not the IP header • AH in transport mode authenticates the IP payload and selected fields of the IP header – usually used between end-systems § tunnel mode – provides protection to the entire IP packet – the entire IP packet is considered as payload and encapsulated in another IP packet (with potentially different source and destination addresses) • ESP in tunnel mode encrypts and optionally authenticates the entire inner IP packet • AH in transport mode authenticates the entire inner IP packet and selected fields of the outer IP header – usually used between security gateways (routers, firewalls) 7
Modes of operation § transport mode – provides protection primarily for upper layer protocols – protection is applied to the payload of the IP packet • ESP in transport mode encrypts and optionally authenticates the IP payload but not the IP header • AH in transport mode authenticates the IP payload and selected fields of the IP header – usually used between end-systems § tunnel mode – provides protection to the entire IP packet – the entire IP packet is considered as payload and encapsulated in another IP packet (with potentially different source and destination addresses) • ESP in tunnel mode encrypts and optionally authenticates the entire inner IP packet • AH in transport mode authenticates the entire inner IP packet and selected fields of the outer IP header – usually used between security gateways (routers, firewalls) 7
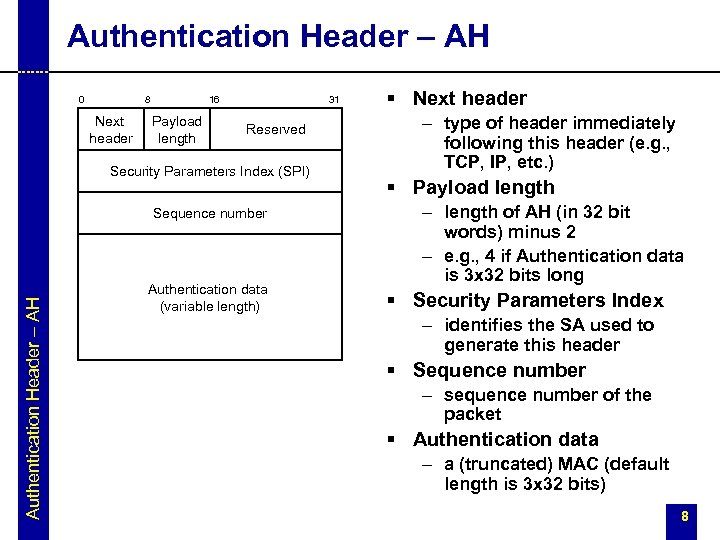 Authentication Header – AH 0 8 Next header 16 Payload length 31 Reserved Security Parameters Index (SPI) Authentication Header – AH Sequence number Authentication data (variable length) § Next header – type of header immediately following this header (e. g. , TCP, IP, etc. ) § Payload length – length of AH (in 32 bit words) minus 2 – e. g. , 4 if Authentication data is 3 x 32 bits long § Security Parameters Index – identifies the SA used to generate this header § Sequence number – sequence number of the packet § Authentication data – a (truncated) MAC (default length is 3 x 32 bits) 8
Authentication Header – AH 0 8 Next header 16 Payload length 31 Reserved Security Parameters Index (SPI) Authentication Header – AH Sequence number Authentication data (variable length) § Next header – type of header immediately following this header (e. g. , TCP, IP, etc. ) § Payload length – length of AH (in 32 bit words) minus 2 – e. g. , 4 if Authentication data is 3 x 32 bits long § Security Parameters Index – identifies the SA used to generate this header § Sequence number – sequence number of the packet § Authentication data – a (truncated) MAC (default length is 3 x 32 bits) 8
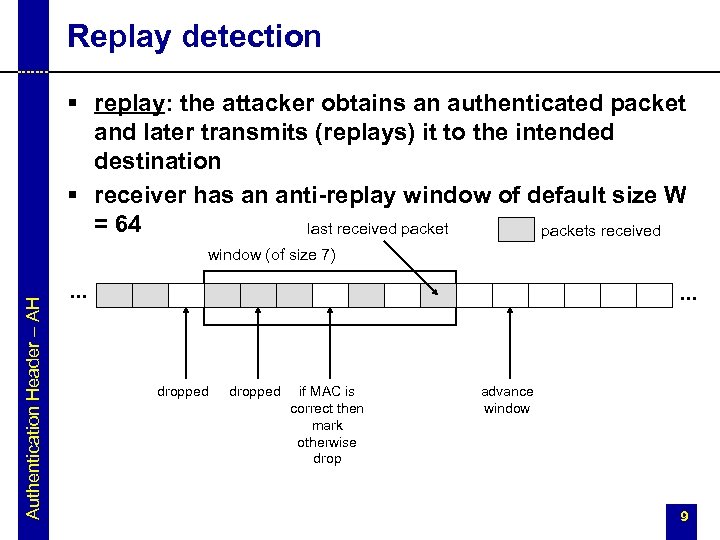 Replay detection § replay: the attacker obtains an authenticated packet and later transmits (replays) it to the intended destination § receiver has an anti-replay window of default size W = 64 last received packets received Authentication Header – AH window (of size 7) . . . dropped if MAC is correct then mark otherwise drop advance window 9
Replay detection § replay: the attacker obtains an authenticated packet and later transmits (replays) it to the intended destination § receiver has an anti-replay window of default size W = 64 last received packets received Authentication Header – AH window (of size 7) . . . dropped if MAC is correct then mark otherwise drop advance window 9
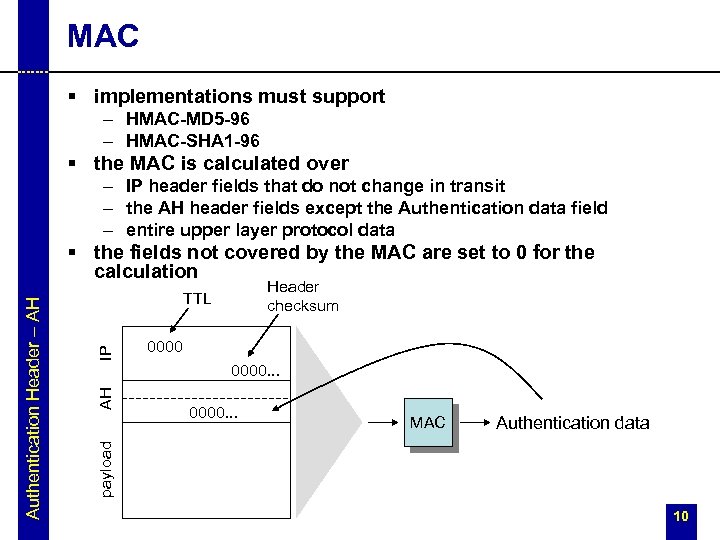 MAC § implementations must support – HMAC-MD 5 -96 – HMAC-SHA 1 -96 § the MAC is calculated over – IP header fields that do not change in transit – the AH header fields except the Authentication data field – entire upper layer protocol data Header checksum IP TTL 0000 AH 0000. . . MAC Authentication data payload Authentication Header – AH § the fields not covered by the MAC are set to 0 for the calculation 10
MAC § implementations must support – HMAC-MD 5 -96 – HMAC-SHA 1 -96 § the MAC is calculated over – IP header fields that do not change in transit – the AH header fields except the Authentication data field – entire upper layer protocol data Header checksum IP TTL 0000 AH 0000. . . MAC Authentication data payload Authentication Header – AH § the fields not covered by the MAC are set to 0 for the calculation 10
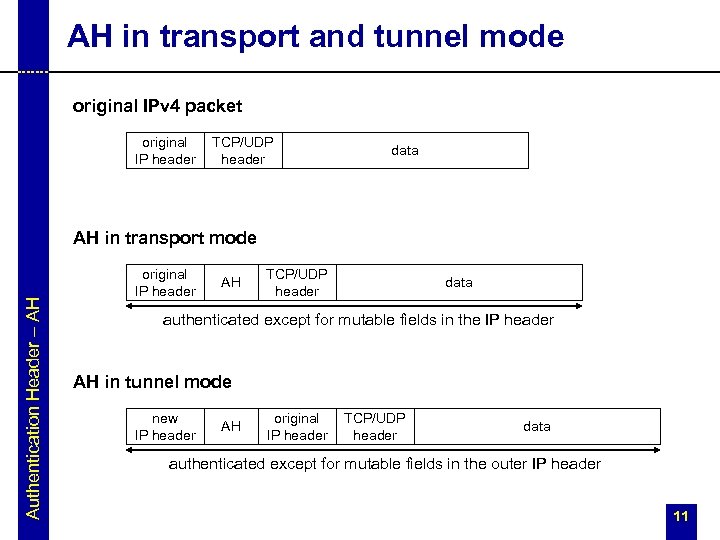 AH in transport and tunnel mode original IPv 4 packet original IP header TCP/UDP header data Authentication Header – AH AH in transport mode original IP header AH TCP/UDP header data authenticated except for mutable fields in the IP header AH in tunnel mode new IP header AH original IP header TCP/UDP header data authenticated except for mutable fields in the outer IP header 11
AH in transport and tunnel mode original IPv 4 packet original IP header TCP/UDP header data Authentication Header – AH AH in transport mode original IP header AH TCP/UDP header data authenticated except for mutable fields in the IP header AH in tunnel mode new IP header AH original IP header TCP/UDP header data authenticated except for mutable fields in the outer IP header 11
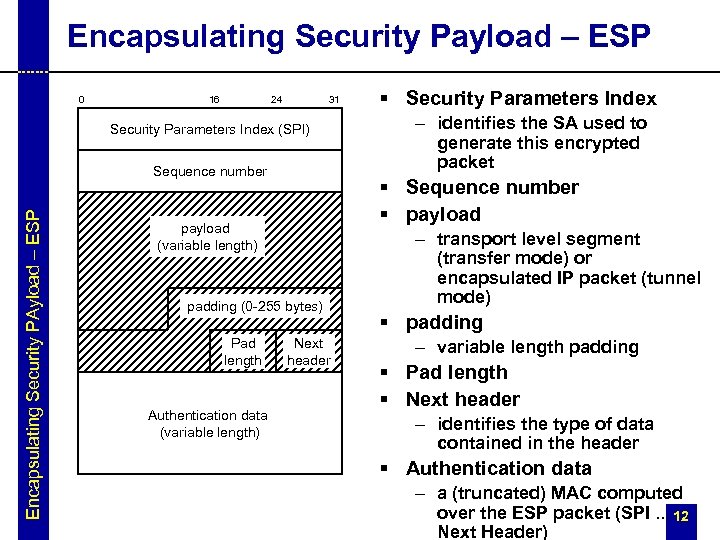 Encapsulating Security Payload – ESP 0 16 24 31 Security Parameters Index (SPI) Encapsulating Security PAyload – ESP Sequence number padding (0 -255 bytes) Authentication data (variable length) – identifies the SA used to generate this encrypted packet § Sequence number § payload (variable length) Pad length § Security Parameters Index Next header – transport level segment (transfer mode) or encapsulated IP packet (tunnel mode) § padding – variable length padding § Pad length § Next header – identifies the type of data contained in the header § Authentication data – a (truncated) MAC computed over the ESP packet (SPI. . . 12 Next Header)
Encapsulating Security Payload – ESP 0 16 24 31 Security Parameters Index (SPI) Encapsulating Security PAyload – ESP Sequence number padding (0 -255 bytes) Authentication data (variable length) – identifies the SA used to generate this encrypted packet § Sequence number § payload (variable length) Pad length § Security Parameters Index Next header – transport level segment (transfer mode) or encapsulated IP packet (tunnel mode) § padding – variable length padding § Pad length § Next header – identifies the type of data contained in the header § Authentication data – a (truncated) MAC computed over the ESP packet (SPI. . . 12 Next Header)
 Encryption and MAC algorithms Encapsulating Security PAyload – ESP § encryption – applied to the payload, padding, pad length, and next header fields – if an IV is needed, then it is explicitly carried at the beginning of the payload data (the IV is not encrypted) – implementations must support DES-CBC – other suggested algorithms: 3 DES, RC 5, IDEA, 3 IDEA, CAST, Blowfish § MAC – default length is 3 x 32 bits – implementations must support HMAC-MD 5 -96 and HMACSHA 1 -96 – MAC is computed over the SPI, sequence number, and encrypted payload, padding, pad length, and next header fields – unlike in AH, here the MAC does not cover the preceding IP 13
Encryption and MAC algorithms Encapsulating Security PAyload – ESP § encryption – applied to the payload, padding, pad length, and next header fields – if an IV is needed, then it is explicitly carried at the beginning of the payload data (the IV is not encrypted) – implementations must support DES-CBC – other suggested algorithms: 3 DES, RC 5, IDEA, 3 IDEA, CAST, Blowfish § MAC – default length is 3 x 32 bits – implementations must support HMAC-MD 5 -96 and HMACSHA 1 -96 – MAC is computed over the SPI, sequence number, and encrypted payload, padding, pad length, and next header fields – unlike in AH, here the MAC does not cover the preceding IP 13
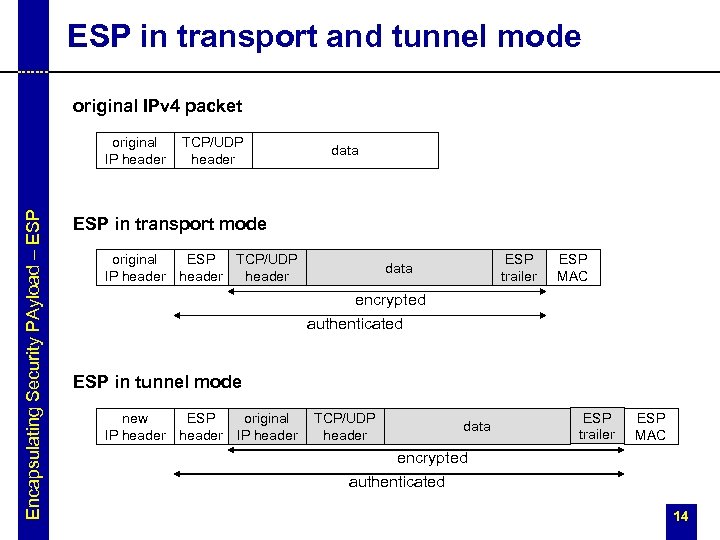 ESP in transport and tunnel mode original IPv 4 packet Encapsulating Security PAyload – ESP original IP header TCP/UDP header data ESP in transport mode original ESP TCP/UDP IP header ESP trailer data ESP MAC encrypted authenticated ESP in tunnel mode new ESP original IP header TCP/UDP header data ESP trailer ESP MAC encrypted authenticated 14
ESP in transport and tunnel mode original IPv 4 packet Encapsulating Security PAyload – ESP original IP header TCP/UDP header data ESP in transport mode original ESP TCP/UDP IP header ESP trailer data ESP MAC encrypted authenticated ESP in tunnel mode new ESP original IP header TCP/UDP header data ESP trailer ESP MAC encrypted authenticated 14
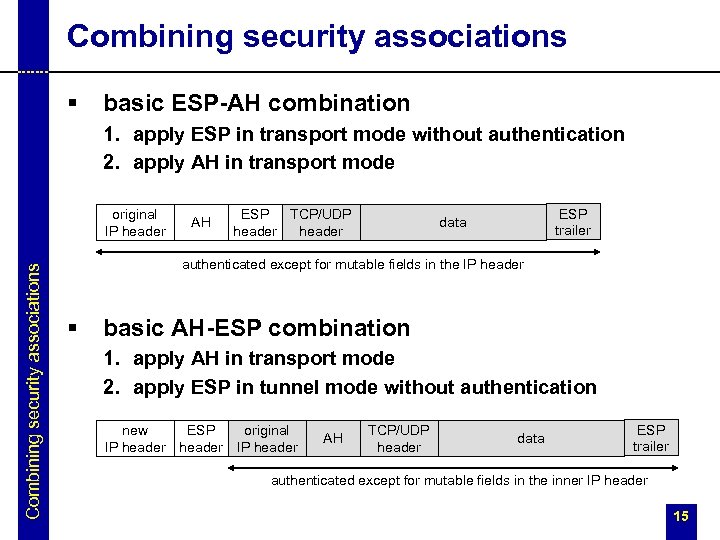 Combining security associations § basic ESP-AH combination 1. apply ESP in transport mode without authentication 2. apply AH in transport mode Combining security associations original IP header AH ESP TCP/UDP header ESP trailer data authenticated except for mutable fields in the IP header § basic AH-ESP combination 1. apply AH in transport mode 2. apply ESP in tunnel mode without authentication new ESP original IP header AH TCP/UDP header data ESP trailer authenticated except for mutable fields in the inner IP header 15
Combining security associations § basic ESP-AH combination 1. apply ESP in transport mode without authentication 2. apply AH in transport mode Combining security associations original IP header AH ESP TCP/UDP header ESP trailer data authenticated except for mutable fields in the IP header § basic AH-ESP combination 1. apply AH in transport mode 2. apply ESP in tunnel mode without authentication new ESP original IP header AH TCP/UDP header data ESP trailer authenticated except for mutable fields in the inner IP header 15
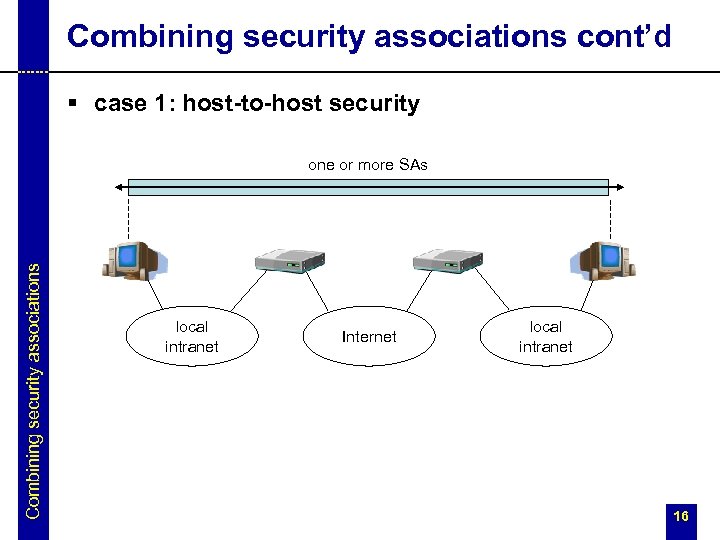 Combining security associations cont’d § case 1: host-to-host security Combining security associations one or more SAs local intranet Internet local intranet 16
Combining security associations cont’d § case 1: host-to-host security Combining security associations one or more SAs local intranet Internet local intranet 16
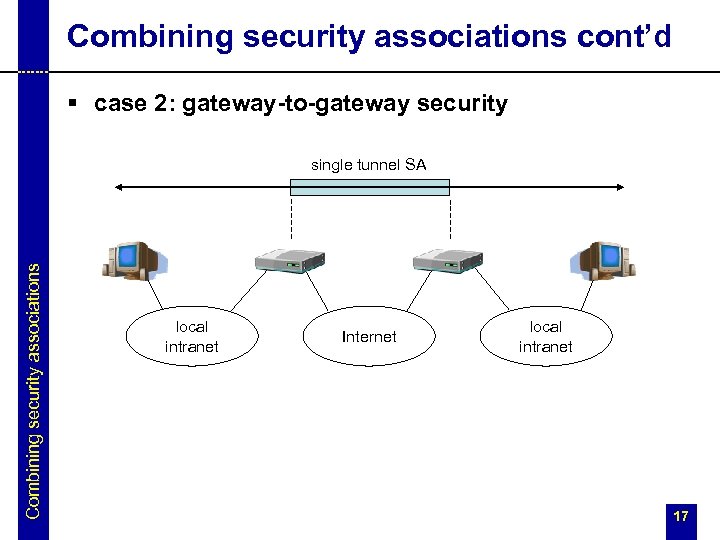 Combining security associations cont’d § case 2: gateway-to-gateway security Combining security associations single tunnel SA local intranet Internet local intranet 17
Combining security associations cont’d § case 2: gateway-to-gateway security Combining security associations single tunnel SA local intranet Internet local intranet 17
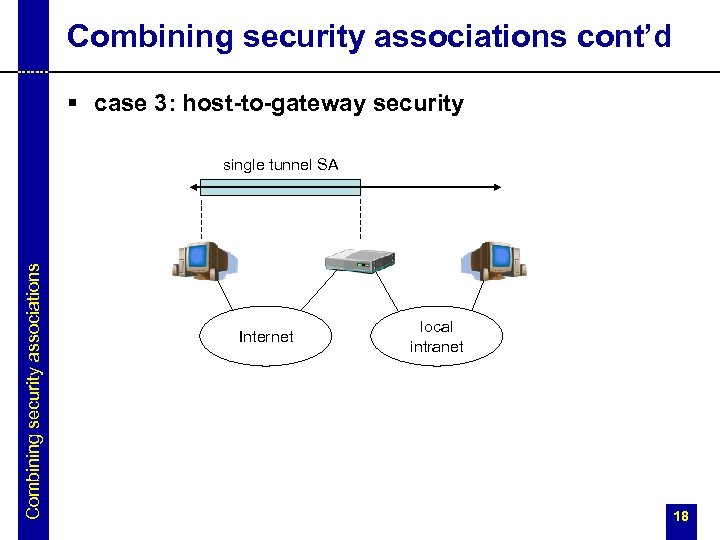 Combining security associations cont’d § case 3: host-to-gateway security Combining security associations single tunnel SA Internet local intranet 18
Combining security associations cont’d § case 3: host-to-gateway security Combining security associations single tunnel SA Internet local intranet 18
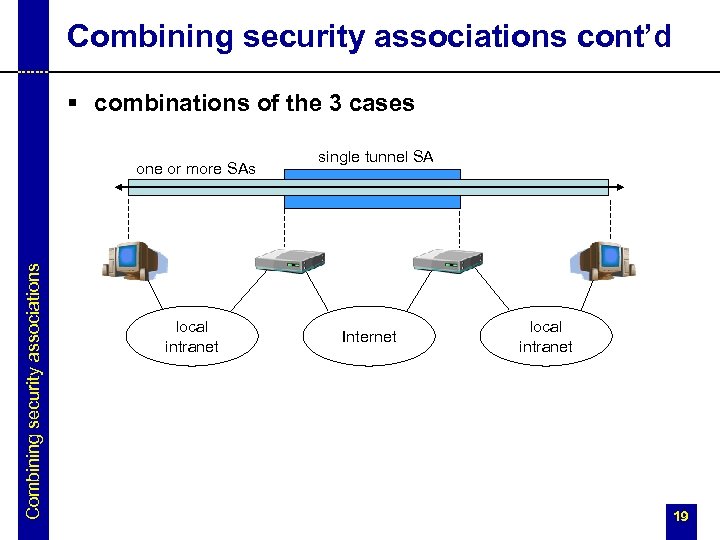 Combining security associations cont’d § combinations of the 3 cases Combining security associations one or more SAs local intranet single tunnel SA Internet local intranet 19
Combining security associations cont’d § combinations of the 3 cases Combining security associations one or more SAs local intranet single tunnel SA Internet local intranet 19
 Key management § two types must be supported by implementations – manual • system administrator configures each system with the necessary keys – automated • on-demand creation of keys for SAs § default automated method is ISAKMP/Oakley – Oakley key determination protocol Key management • a key exchange protocol based on Diffie-Hellman • provides added security (e. g. , authentication) – ISAKMP – Internet Security Association and Key Management Protocol • provides a framework for key exchange • defines message formats that can carry the messages of various key exchange protocols 20
Key management § two types must be supported by implementations – manual • system administrator configures each system with the necessary keys – automated • on-demand creation of keys for SAs § default automated method is ISAKMP/Oakley – Oakley key determination protocol Key management • a key exchange protocol based on Diffie-Hellman • provides added security (e. g. , authentication) – ISAKMP – Internet Security Association and Key Management Protocol • provides a framework for key exchange • defines message formats that can carry the messages of various key exchange protocols 20
 Oakley key determination protocol § problems with basic DH: – it is subject to a man-in-the-middle type attack – it is vulnerable to a clogging attack • attacker sends fake DH messages to a victim from a forged IP address • victim starts performing modular exponentiations to compute a secret key • victim can be blocked with useless work Key management / Oakley § added security features of Oakley – cookie exchange to thwart clogging attacks • hash(src IP addr, dst IP addr, src UDP port, dst UDP port, local secret) • local secret is periodically changed – uses nonces to detect replay attacks – authenticates the DH exchange to thwart man-in-the-middle attacks • based on digital signatures, public key encryption, or symmetric key encryption – enables the parties to negotiate the global parameters of the DH 21 exchange (e. g. , the prime p that defines the group and the
Oakley key determination protocol § problems with basic DH: – it is subject to a man-in-the-middle type attack – it is vulnerable to a clogging attack • attacker sends fake DH messages to a victim from a forged IP address • victim starts performing modular exponentiations to compute a secret key • victim can be blocked with useless work Key management / Oakley § added security features of Oakley – cookie exchange to thwart clogging attacks • hash(src IP addr, dst IP addr, src UDP port, dst UDP port, local secret) • local secret is periodically changed – uses nonces to detect replay attacks – authenticates the DH exchange to thwart man-in-the-middle attacks • based on digital signatures, public key encryption, or symmetric key encryption – enables the parties to negotiate the global parameters of the DH 21 exchange (e. g. , the prime p that defines the group and the
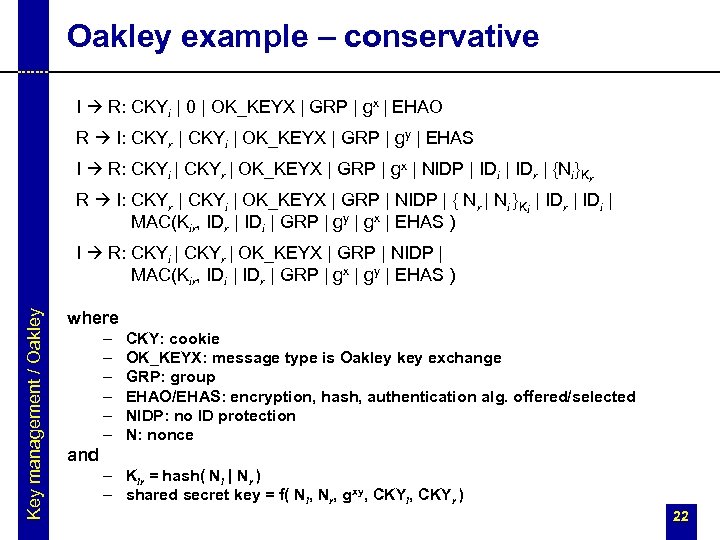 Oakley example – conservative I R: CKYi | 0 | OK_KEYX | GRP | gx | EHAO R I: CKYr | CKYi | OK_KEYX | GRP | gy | EHAS I R: CKYi | CKYr | OK_KEYX | GRP | gx | NIDP | IDi | IDr | {Ni}Kr R I: CKYr | CKYi | OK_KEYX | GRP | NIDP | { Nr | Ni }Ki | IDr | IDi | MAC(Kir, IDr | IDi | GRP | gy | gx | EHAS ) Key management / Oakley I R: CKYi | CKYr | OK_KEYX | GRP | NIDP | MAC(Kir, IDi | IDr | GRP | gx | gy | EHAS ) where – – – CKY: cookie OK_KEYX: message type is Oakley key exchange GRP: group EHAO/EHAS: encryption, hash, authentication alg. offered/selected NIDP: no ID protection N: nonce and – Kir = hash( Ni | Nr ) – shared secret key = f( Ni, Nr, gxy, CKYi, CKYr ) 22
Oakley example – conservative I R: CKYi | 0 | OK_KEYX | GRP | gx | EHAO R I: CKYr | CKYi | OK_KEYX | GRP | gy | EHAS I R: CKYi | CKYr | OK_KEYX | GRP | gx | NIDP | IDi | IDr | {Ni}Kr R I: CKYr | CKYi | OK_KEYX | GRP | NIDP | { Nr | Ni }Ki | IDr | IDi | MAC(Kir, IDr | IDi | GRP | gy | gx | EHAS ) Key management / Oakley I R: CKYi | CKYr | OK_KEYX | GRP | NIDP | MAC(Kir, IDi | IDr | GRP | gx | gy | EHAS ) where – – – CKY: cookie OK_KEYX: message type is Oakley key exchange GRP: group EHAO/EHAS: encryption, hash, authentication alg. offered/selected NIDP: no ID protection N: nonce and – Kir = hash( Ni | Nr ) – shared secret key = f( Ni, Nr, gxy, CKYi, CKYr ) 22
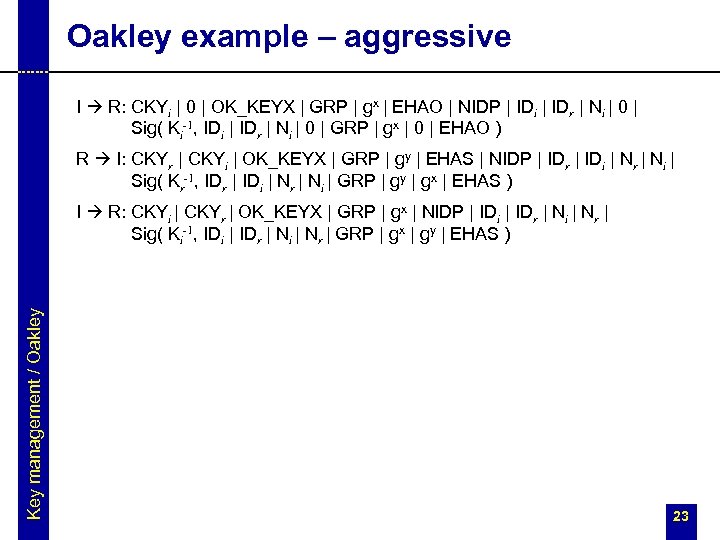 Oakley example – aggressive I R: CKYi | 0 | OK_KEYX | GRP | gx | EHAO | NIDP | IDi | IDr | Ni | 0 | Sig( Ki-1, IDi | IDr | Ni | 0 | GRP | gx | 0 | EHAO ) R I: CKYr | CKYi | OK_KEYX | GRP | gy | EHAS | NIDP | IDr | IDi | Nr | Ni | Sig( Kr-1, IDr | IDi | Nr | Ni | GRP | gy | gx | EHAS ) Key management / Oakley I R: CKYi | CKYr | OK_KEYX | GRP | gx | NIDP | IDi | IDr | Ni | Nr | Sig( Ki-1, IDi | IDr | Ni | Nr | GRP | gx | gy | EHAS ) 23
Oakley example – aggressive I R: CKYi | 0 | OK_KEYX | GRP | gx | EHAO | NIDP | IDi | IDr | Ni | 0 | Sig( Ki-1, IDi | IDr | Ni | 0 | GRP | gx | 0 | EHAO ) R I: CKYr | CKYi | OK_KEYX | GRP | gy | EHAS | NIDP | IDr | IDi | Nr | Ni | Sig( Kr-1, IDr | IDi | Nr | Ni | GRP | gy | gx | EHAS ) Key management / Oakley I R: CKYi | CKYr | OK_KEYX | GRP | gx | NIDP | IDi | IDr | Ni | Nr | Sig( Ki-1, IDi | IDr | Ni | Nr | GRP | gx | gy | EHAS ) 23
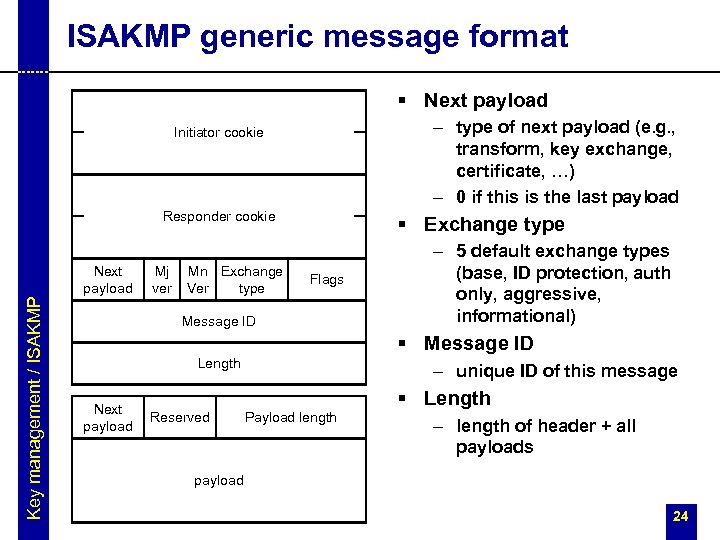 ISAKMP generic message format § Next payload – type of next payload (e. g. , transform, key exchange, certificate, …) – 0 if this is the last payload Initiator cookie Responder cookie Key management / ISAKMP Next payload Mj ver Mn Exchange Ver type § Exchange type Flags Message ID – 5 default exchange types (base, ID protection, auth only, aggressive, informational) § Message ID Length Next payload – unique ID of this message § Length Reserved Payload length – length of header + all payloads payload 24
ISAKMP generic message format § Next payload – type of next payload (e. g. , transform, key exchange, certificate, …) – 0 if this is the last payload Initiator cookie Responder cookie Key management / ISAKMP Next payload Mj ver Mn Exchange Ver type § Exchange type Flags Message ID – 5 default exchange types (base, ID protection, auth only, aggressive, informational) § Message ID Length Next payload – unique ID of this message § Length Reserved Payload length – length of header + all payloads payload 24
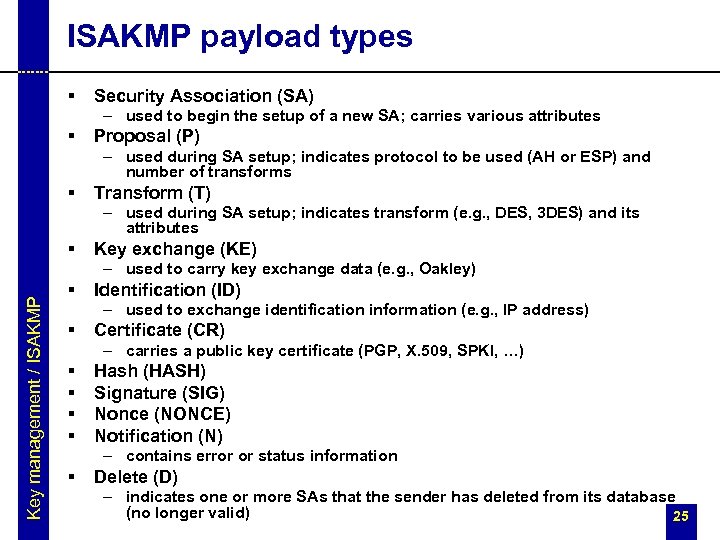 ISAKMP payload types § Security Association (SA) – used to begin the setup of a new SA; carries various attributes § Proposal (P) – used during SA setup; indicates protocol to be used (AH or ESP) and number of transforms § Transform (T) – used during SA setup; indicates transform (e. g. , DES, 3 DES) and its attributes § Key exchange (KE) Key management / ISAKMP – used to carry key exchange data (e. g. , Oakley) § Identification (ID) – used to exchange identification information (e. g. , IP address) § Certificate (CR) – carries a public key certificate (PGP, X. 509, SPKI, …) § § Hash (HASH) Signature (SIG) Nonce (NONCE) Notification (N) – contains error or status information § Delete (D) – indicates one or more SAs that the sender has deleted from its database (no longer valid) 25
ISAKMP payload types § Security Association (SA) – used to begin the setup of a new SA; carries various attributes § Proposal (P) – used during SA setup; indicates protocol to be used (AH or ESP) and number of transforms § Transform (T) – used during SA setup; indicates transform (e. g. , DES, 3 DES) and its attributes § Key exchange (KE) Key management / ISAKMP – used to carry key exchange data (e. g. , Oakley) § Identification (ID) – used to exchange identification information (e. g. , IP address) § Certificate (CR) – carries a public key certificate (PGP, X. 509, SPKI, …) § § Hash (HASH) Signature (SIG) Nonce (NONCE) Notification (N) – contains error or status information § Delete (D) – indicates one or more SAs that the sender has deleted from its database (no longer valid) 25
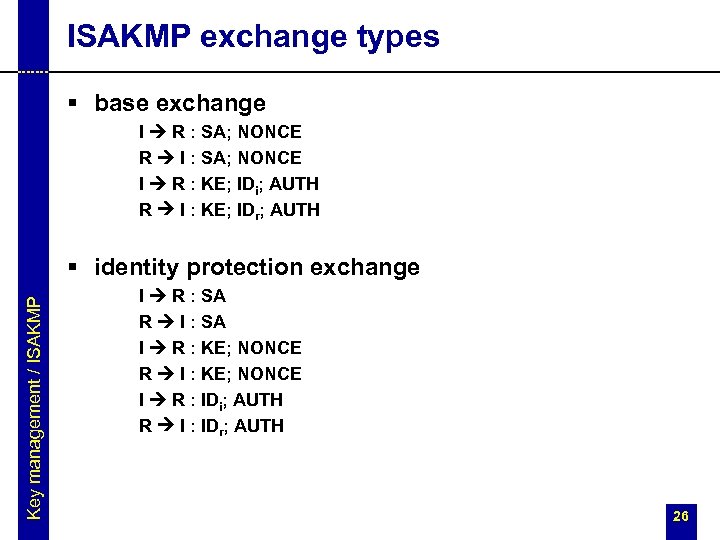 ISAKMP exchange types § base exchange I R : SA; NONCE R I : SA; NONCE I R : KE; IDi; AUTH R I : KE; IDr; AUTH Key management / ISAKMP § identity protection exchange I R : SA R I : SA I R : KE; NONCE R I : KE; NONCE I R : IDi; AUTH R I : IDr; AUTH 26
ISAKMP exchange types § base exchange I R : SA; NONCE R I : SA; NONCE I R : KE; IDi; AUTH R I : KE; IDr; AUTH Key management / ISAKMP § identity protection exchange I R : SA R I : SA I R : KE; NONCE R I : KE; NONCE I R : IDi; AUTH R I : IDr; AUTH 26
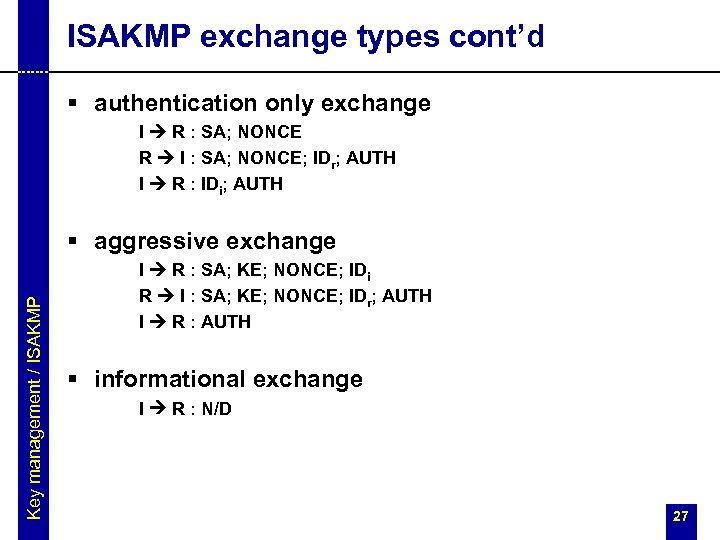 ISAKMP exchange types cont’d § authentication only exchange I R : SA; NONCE R I : SA; NONCE; IDr; AUTH I R : IDi; AUTH Key management / ISAKMP § aggressive exchange I R : SA; KE; NONCE; IDi R I : SA; KE; NONCE; IDr; AUTH I R : AUTH § informational exchange I R : N/D 27
ISAKMP exchange types cont’d § authentication only exchange I R : SA; NONCE R I : SA; NONCE; IDr; AUTH I R : IDi; AUTH Key management / ISAKMP § aggressive exchange I R : SA; KE; NONCE; IDi R I : SA; KE; NONCE; IDr; AUTH I R : AUTH § informational exchange I R : N/D 27


