dc94a1978adcbeedafe4d3922c40b0e2.ppt
- Количество слайдов: 66
 Network Infrastructure Insecurity The authentication, management and routing protocols that run your network Jeremy Rauch
Network Infrastructure Insecurity The authentication, management and routing protocols that run your network Jeremy Rauch
 Topics u Overview u Basic protocol flaws u Network allocation flaws u Routing protocol flaws u Authentication flaws u Network Management and other fun flaws u Application of attacks
Topics u Overview u Basic protocol flaws u Network allocation flaws u Routing protocol flaws u Authentication flaws u Network Management and other fun flaws u Application of attacks
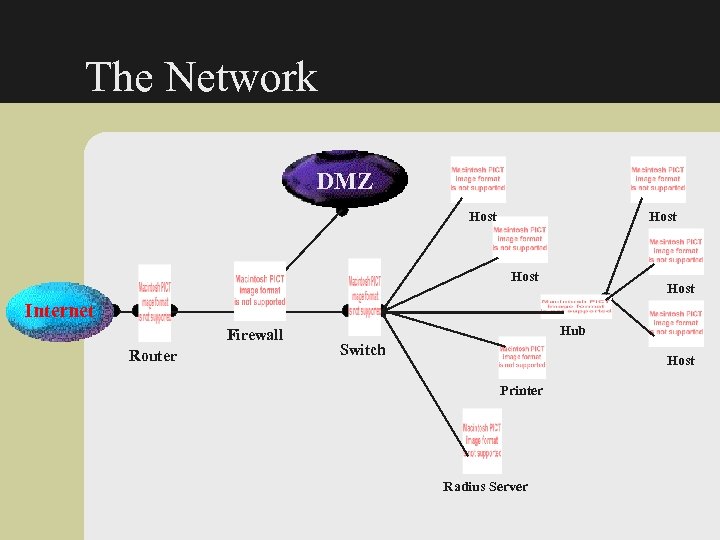 The Network DMZ Host Internet Firewall Router Hub Switch Host Printer Radius Server
The Network DMZ Host Internet Firewall Router Hub Switch Host Printer Radius Server
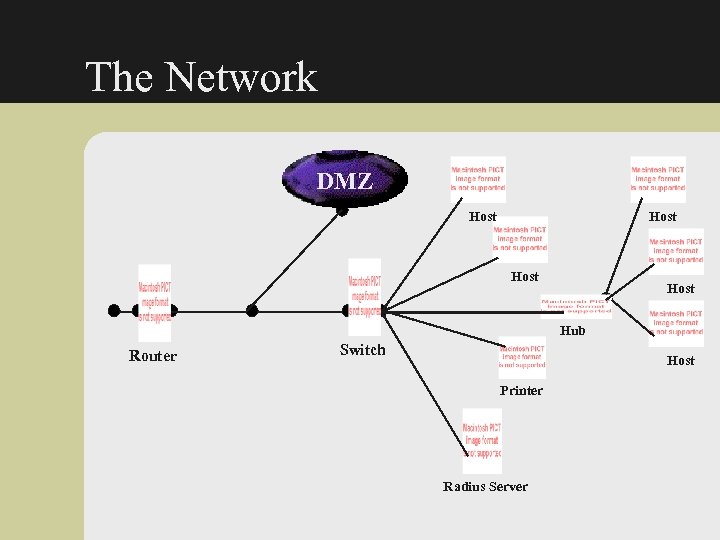 The Network DMZ Host Hub Router Switch Host Printer Radius Server
The Network DMZ Host Hub Router Switch Host Printer Radius Server
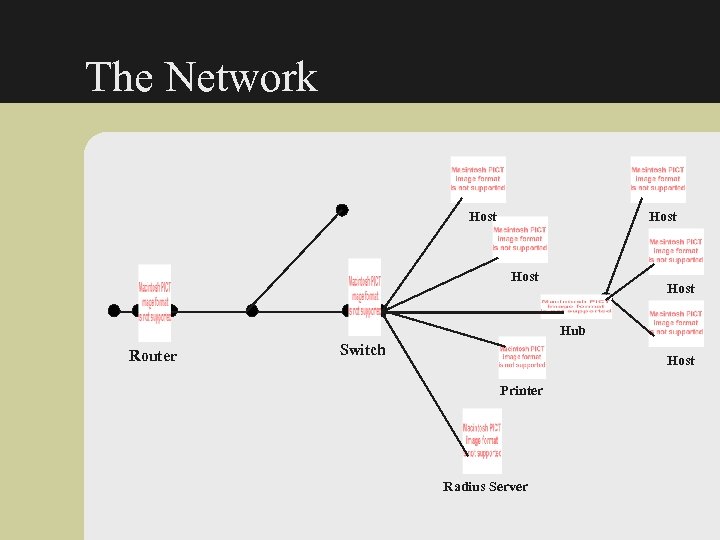 The Network Host Hub Router Switch Host Printer Radius Server
The Network Host Hub Router Switch Host Printer Radius Server
 The Network Hub Router Switch Printer Radius Server
The Network Hub Router Switch Printer Radius Server
 Overview u Network Infrastructure – The building blocks of a network » basic network protocols » network management » authentication » routing » other random things switches, hubs u printers u routers u
Overview u Network Infrastructure – The building blocks of a network » basic network protocols » network management » authentication » routing » other random things switches, hubs u printers u routers u
 Overview u Does this stuff matter? – Absolutely - the network depends on these » Basic protocols - obvious » network management & allocation u simplify network design and machine deployment » Authentication u access control » Routing u Getting from A to B » Other stuff u The network RUNS on these
Overview u Does this stuff matter? – Absolutely - the network depends on these » Basic protocols - obvious » network management & allocation u simplify network design and machine deployment » Authentication u access control » Routing u Getting from A to B » Other stuff u The network RUNS on these
 Overview u Impacts – Attacking protocols can allow for hijacking, spoofing and impersonation – control network devices – elevate access – change network flow – hide connections – sniffing – …and more
Overview u Impacts – Attacking protocols can allow for hijacking, spoofing and impersonation – control network devices – elevate access – change network flow – hide connections – sniffing – …and more
 Basic Protocols u Security at the IP layer discussed over and over u Security at the link layer ignored
Basic Protocols u Security at the IP layer discussed over and over u Security at the link layer ignored
 ARP u Address Resolution Protocol – Used for mapping network IP addresses to physical (in the case of ethernet, MAC) interface addresses. – Broadcast at the link layer.
ARP u Address Resolution Protocol – Used for mapping network IP addresses to physical (in the case of ethernet, MAC) interface addresses. – Broadcast at the link layer.
 ARP Security Flaws u Lack of Authentication u Limited Table Entries – ARP caches can be overpopulated and flushed
ARP Security Flaws u Lack of Authentication u Limited Table Entries – ARP caches can be overpopulated and flushed
 ARP Authentication Flaws u Lack of Authentication – Arp replies are typically accepted and cached without concern for origin when received. – No method to distinguish between legitimate and illegitimate messages
ARP Authentication Flaws u Lack of Authentication – Arp replies are typically accepted and cached without concern for origin when received. – No method to distinguish between legitimate and illegitimate messages
 ARP Lack of Authentication u Invalid ARP replies – When an ARP who-is is broadcast on the wire, anyone can reply and be mapped to the associated network address. u Gratuitous ARP replies – ARP replies without requests can be sent out and cached, diverting traffic from the compromised network address to the attacker.
ARP Lack of Authentication u Invalid ARP replies – When an ARP who-is is broadcast on the wire, anyone can reply and be mapped to the associated network address. u Gratuitous ARP replies – ARP replies without requests can be sent out and cached, diverting traffic from the compromised network address to the attacker.
 ARP Attacks u Replace entries in arp caches for existing addresses – Denial of Service – Reply to requests with compromised host adress as router or nameserver. – Non-blind traffic hijacking – Exploitation of host-based trusts.
ARP Attacks u Replace entries in arp caches for existing addresses – Denial of Service – Reply to requests with compromised host adress as router or nameserver. – Non-blind traffic hijacking – Exploitation of host-based trusts.
 ARP Attacks u ARP Cache Overpopulation – Sending too many gratuitous ARP replies flushing the target ARP cache in some implementations. » Reach cache maximum, can cause devices like switches to re-enter “learning mode”
ARP Attacks u ARP Cache Overpopulation – Sending too many gratuitous ARP replies flushing the target ARP cache in some implementations. » Reach cache maximum, can cause devices like switches to re-enter “learning mode”
 DHCP u Dynamic Host Configuration Protocol – Popular amongst pc users for ease of installation and configuration – UDP transport – To broadcast, from 0. 0
DHCP u Dynamic Host Configuration Protocol – Popular amongst pc users for ease of installation and configuration – UDP transport – To broadcast, from 0. 0
 DHCP Security Problems u Unauthenticated – Anyone can request an address u Undirected – Anyone can respond u Limited ACL capabilities – Limit addresses per mac
DHCP Security Problems u Unauthenticated – Anyone can request an address u Undirected – Anyone can respond u Limited ACL capabilities – Limit addresses per mac
 DHCP Attacks u Get all addresses – Denial Of Service – Reply to requests with compromised host set as router or nameserver u Deregister hosts – hijack ip’s, connections
DHCP Attacks u Get all addresses – Denial Of Service – Reply to requests with compromised host set as router or nameserver u Deregister hosts – hijack ip’s, connections
 DHCP Fixes u Authentication – ISC is adding authentication in their 3. 1 implementation – Others have implemented proprietary authentication mechanisms u Don’t allow dynamic assignment of DNS servers or routers – Statically define these
DHCP Fixes u Authentication – ISC is adding authentication in their 3. 1 implementation – Others have implemented proprietary authentication mechanisms u Don’t allow dynamic assignment of DNS servers or routers – Statically define these
 Gateway Protocols u IGP – RIPv 1 – RIPv 2 – OSPF
Gateway Protocols u IGP – RIPv 1 – RIPv 2 – OSPF
 RIP u Routing Information Protocol – Widely used distance-vector IGP (Interior Gateway Protocol) within autonomous systems. – Exists in two forms, Version 1 and the backwards compatible Version 2. u RIPv 1 attack. is extremely vulnerable to serious
RIP u Routing Information Protocol – Widely used distance-vector IGP (Interior Gateway Protocol) within autonomous systems. – Exists in two forms, Version 1 and the backwards compatible Version 2. u RIPv 1 attack. is extremely vulnerable to serious
 RIP Security Flaws u Transport Method u Authentication
RIP Security Flaws u Transport Method u Authentication
 RIP Transport Method Flaws u Based on UDP, utilizing port 520 for sending and receiving messages. – UDP is unreliable, no sequencing of packets. Easy to send arbitrary data to target. – Since sequencing is not a concern, forging source address can be very effective. – May be able to receive data from anywhere on the internet.
RIP Transport Method Flaws u Based on UDP, utilizing port 520 for sending and receiving messages. – UDP is unreliable, no sequencing of packets. Easy to send arbitrary data to target. – Since sequencing is not a concern, forging source address can be very effective. – May be able to receive data from anywhere on the internet.
 RIP Authentication Flaws u Lack of any authentication in RIPv 1 u Cleartext Authentication recommended in RFC 2453 RIPv 2 Specifications u MD 5 Key/Key. ID Digest Based Authentication described in RFC 2082.
RIP Authentication Flaws u Lack of any authentication in RIPv 1 u Cleartext Authentication recommended in RFC 2453 RIPv 2 Specifications u MD 5 Key/Key. ID Digest Based Authentication described in RFC 2082.
 RIP Attacks u Forging RIP messages – Spoofing source address and sending invalid routes, altering traffic flow. » Traffic Hijacking » Traffic Monitoring » Redirecting traffic from trusted to untrusted. – Obtaining Cleartext RIPv 2 "password" when sent across network. » Using retrieved password to send authenticated updates to RIPv 2 routers, altering traffic flow with consequences listed above.
RIP Attacks u Forging RIP messages – Spoofing source address and sending invalid routes, altering traffic flow. » Traffic Hijacking » Traffic Monitoring » Redirecting traffic from trusted to untrusted. – Obtaining Cleartext RIPv 2 "password" when sent across network. » Using retrieved password to send authenticated updates to RIPv 2 routers, altering traffic flow with consequences listed above.
 RIP Solutions u Disabling RIPv 1 and using RIPv 2 with MD 5 authentication. u Enabling MD 5 based authentication for RIPv 2 u Disabling RIP completely and using OSPF with MD 5 authentication as interior gateway protocol. OSPF is the suggested IGP.
RIP Solutions u Disabling RIPv 1 and using RIPv 2 with MD 5 authentication. u Enabling MD 5 based authentication for RIPv 2 u Disabling RIP completely and using OSPF with MD 5 authentication as interior gateway protocol. OSPF is the suggested IGP.
 OSPF u OSPF - Open Shortest Path First – Link-State Interior Gateway Protocol. In wide use within autonomous systems. – OSPF is the recommended IGP, intended as a replacement for RIP.
OSPF u OSPF - Open Shortest Path First – Link-State Interior Gateway Protocol. In wide use within autonomous systems. – OSPF is the recommended IGP, intended as a replacement for RIP.
 OSPF Security Flaws u Authentication
OSPF Security Flaws u Authentication
 OSPF Authentication Flaws u Default Lack of Authentication – By default in some implementations, OSPF authentication may be off. u Cleartext "simple password" Authentication – Commonly a default setting, clear-text password included in OSPF message used to authenticate peers. u Type of authentication determined by "CODE" field in the OSPF message header.
OSPF Authentication Flaws u Default Lack of Authentication – By default in some implementations, OSPF authentication may be off. u Cleartext "simple password" Authentication – Commonly a default setting, clear-text password included in OSPF message used to authenticate peers. u Type of authentication determined by "CODE" field in the OSPF message header.
 OSPF Attacks u Forging OSPF messages – Can be somewhat difficult but theoretically possible if no authentication required or cleartext password obtained.
OSPF Attacks u Forging OSPF messages – Can be somewhat difficult but theoretically possible if no authentication required or cleartext password obtained.
 OSPF Solution u Enable MD 5 Authentication in OSPF implementation.
OSPF Solution u Enable MD 5 Authentication in OSPF implementation.
 Authentication Flaw Overview u Authentication is a means for verification and granting of access u Problems range from denial of service to active and passive attacks leading to total compromise – gain access – elevate access
Authentication Flaw Overview u Authentication is a means for verification and granting of access u Problems range from denial of service to active and passive attacks leading to total compromise – gain access – elevate access
 Authentication Mechanisms u Radius u TACACS, u NIS/NIS+ u LDAP XTACACS, TACACS+
Authentication Mechanisms u Radius u TACACS, u NIS/NIS+ u LDAP XTACACS, TACACS+
 RADIUS u Remote Authentication Dial In User Service u RFC 2138 & 2139 u Used to authenticate users u Off-machine/device authentication – Central authentication server called a NAS – Popular implementations from Livingston and Merit
RADIUS u Remote Authentication Dial In User Service u RFC 2138 & 2139 u Used to authenticate users u Off-machine/device authentication – Central authentication server called a NAS – Popular implementations from Livingston and Merit
 Radius Security Model u UDP Based transport u Each packet contains an authenticator – Access-Requests » md 5(secret + authenticator) ^ user password – Access-Reject & Access-Accept » md 5(Code + ID + Length + Request-Auth + Attributes + Secret)
Radius Security Model u UDP Based transport u Each packet contains an authenticator – Access-Requests » md 5(secret + authenticator) ^ user password – Access-Reject & Access-Accept » md 5(Code + ID + Length + Request-Auth + Attributes + Secret)
 Radius Flaws u Gaining the shared secret – Send Access-Request with all known values » Authenticator = 0 » User Name/Password = known » Code = Access-Request (1) » ID = 0, length = known » Reply will come back with the following u md 5(1 + 0 + length + 0 + user name attr + user pass attr + Secret) » Dictionary attack for Secret u radbrute. tar. gz
Radius Flaws u Gaining the shared secret – Send Access-Request with all known values » Authenticator = 0 » User Name/Password = known » Code = Access-Request (1) » ID = 0, length = known » Reply will come back with the following u md 5(1 + 0 + length + 0 + user name attr + user pass attr + Secret) » Dictionary attack for Secret u radbrute. tar. gz
 Radius Flaws. . . u Passive attack – Knowledge of a user password will allow attack if sniffing is possible – Request-Access user password + authenticator + shared secret » md 5(authenticator + shared secret) ^ user pass » obtain md 5 by ^ userpass » brute force dictionary attack with known authenticator
Radius Flaws. . . u Passive attack – Knowledge of a user password will allow attack if sniffing is possible – Request-Access user password + authenticator + shared secret » md 5(authenticator + shared secret) ^ user pass » obtain md 5 by ^ userpass » brute force dictionary attack with known authenticator
 Radius Flaws. . . u Replay – Radius servers must not reuse authenticator » if authenticator isn’t cryptographically random, repeat authentications until an authenticator is reused, and replay server Request-Accept u Failure limits and logging limit the effectivity » Predictable authenticator u If authenticator can be predicted, replay attacks become easier and more effective
Radius Flaws. . . u Replay – Radius servers must not reuse authenticator » if authenticator isn’t cryptographically random, repeat authentications until an authenticator is reused, and replay server Request-Accept u Failure limits and logging limit the effectivity » Predictable authenticator u If authenticator can be predicted, replay attacks become easier and more effective
 TACACS, XTACACS and TACACS+ u Terminal Access Controller Access Control System? ? – Old protocol developed by BBN for Milnet u Similar in concept to RADIUS – Central authentication server moves authentication off device or host u RFC 1492, Internet Draft “The TACACS+ Protocol”
TACACS, XTACACS and TACACS+ u Terminal Access Controller Access Control System? ? – Old protocol developed by BBN for Milnet u Similar in concept to RADIUS – Central authentication server moves authentication off device or host u RFC 1492, Internet Draft “The TACACS+ Protocol”
 TACACS, etc Flaws u TACACS & XTACACS – UDP Transport » spoof RESPONSE messages from server trivially – Cleartext authentication normal » User names and password sent exposed u MD 5 in newer implementations – Good way to crack passwords online » Easy, fast way to grind for accounts with bad passwords
TACACS, etc Flaws u TACACS & XTACACS – UDP Transport » spoof RESPONSE messages from server trivially – Cleartext authentication normal » User names and password sent exposed u MD 5 in newer implementations – Good way to crack passwords online » Easy, fast way to grind for accounts with bad passwords
 TACACS+ u TCP Transport – Doesn’t suffer from easy spoofing; may be hijackable u Authentication and Encryption – May be possible to conduct attacks similar to RADIUS u Defaults and failure modes may pose problems – tacacs-server last-resort succeed
TACACS+ u TCP Transport – Doesn’t suffer from easy spoofing; may be hijackable u Authentication and Encryption – May be possible to conduct attacks similar to RADIUS u Defaults and failure modes may pose problems – tacacs-server last-resort succeed
 TACACS+. . . u Authentication – No integrity checking – Vulnerable to replay u Encryption – Heavy dependence on session id’s » may be easy to force collision » too small – Lack of padding in critical places
TACACS+. . . u Authentication – No integrity checking – Vulnerable to replay u Encryption – Heavy dependence on session id’s » may be easy to force collision » too small – Lack of padding in critical places
 NIS and NIS+ u Network Information Service u Originally from Sun u Popular scheme for distributing password, name service, etc u RPC based transport
NIS and NIS+ u Network Information Service u Originally from Sun u Popular scheme for distributing password, name service, etc u RPC based transport
 NIS and NIS+ Flaws u NIS transports in plaintext u NIS is only protected by a domainname – easily guessed u Many vulnerabilities in implementations – quick search for NIS and NIS+ vulnerabilities resulted in over a dozen individual problems u NIS+ is sufficiently complex to install that no one uses it
NIS and NIS+ Flaws u NIS transports in plaintext u NIS is only protected by a domainname – easily guessed u Many vulnerabilities in implementations – quick search for NIS and NIS+ vulnerabilities resulted in over a dozen individual problems u NIS+ is sufficiently complex to install that no one uses it
 NIS and NIS+ Solutions u Run NIS+ if at all possible u Investigate alternatives like LDAP
NIS and NIS+ Solutions u Run NIS+ if at all possible u Investigate alternatives like LDAP
 LDAP u Lightweight Directory Access Protocol u Operates on distinguished name (DN) and attribute pairs or collections
LDAP u Lightweight Directory Access Protocol u Operates on distinguished name (DN) and attribute pairs or collections
 LDAP Flaws u New and relatively untested u Unfamiliar u Default ACL’s are typically poor u Authentication mechanisms still not fully implemented – CA based authentication still only part there u Do. S attacks – Flood with requests
LDAP Flaws u New and relatively untested u Unfamiliar u Default ACL’s are typically poor u Authentication mechanisms still not fully implemented – CA based authentication still only part there u Do. S attacks – Flood with requests
 Network Management and Other Fun Flaws u SNMP u printers
Network Management and Other Fun Flaws u SNMP u printers
 SNMP u Simple Network Management Protocol – The most popular network management protocol – Hosts, firewalls, routers, switches…UPS, power strips, ATM cards -- ubiquitous u “One of the single biggest security nightmares on networks today”
SNMP u Simple Network Management Protocol – The most popular network management protocol – Hosts, firewalls, routers, switches…UPS, power strips, ATM cards -- ubiquitous u “One of the single biggest security nightmares on networks today”
 SNMPv 1 Security Flaws u Transport Mechanism – Data manipulation – Denial of Service – Replay u Authentication – Host Based – Community Based u Information Disclosure
SNMPv 1 Security Flaws u Transport Mechanism – Data manipulation – Denial of Service – Replay u Authentication – Host Based – Community Based u Information Disclosure
 SNMP Transport Mechanism Flaws u UDP Based – Unreliable - packets may or may not be received – Easily forged - trivial to forge source of packets
SNMP Transport Mechanism Flaws u UDP Based – Unreliable - packets may or may not be received – Easily forged - trivial to forge source of packets
 SNMP Authentication Flaws u Host Based – Fails due to UDP transport – DNS cache poisoning u Community Based – Cleartext community – Community name prediction/brute forcing – Default communities
SNMP Authentication Flaws u Host Based – Fails due to UDP transport – DNS cache poisoning u Community Based – Cleartext community – Community name prediction/brute forcing – Default communities
 SNMP Popular Defaults u Popular – – – – – defaults public private write “all private” monitor manager security admin lan – – – – – default password tivoli openview community snmpd system and on. . .
SNMP Popular Defaults u Popular – – – – – defaults public private write “all private” monitor manager security admin lan – – – – – default password tivoli openview community snmpd system and on. . .
 SNMPv 1 Information Disclosure u Routing tables u Network topology u Network traffic patterns u Filter rules
SNMPv 1 Information Disclosure u Routing tables u Network topology u Network traffic patterns u Filter rules
 RMON and RMON 2 Security u SNMPv 1’s flaws u additional hazards by introducing “action invocation” objects u collects extensive info on subnet u packet captures
RMON and RMON 2 Security u SNMPv 1’s flaws u additional hazards by introducing “action invocation” objects u collects extensive info on subnet u packet captures
 SNMP Fixes u Disable u ACL it It u Read-Only
SNMP Fixes u Disable u ACL it It u Read-Only
 Printers Flaws u Actually a very large potential problem u Laundering of hacking spoils u bounce attacks u Denial of service
Printers Flaws u Actually a very large potential problem u Laundering of hacking spoils u bounce attacks u Denial of service
 Printer flaws. . . u Many printers have FTP servers – Allow anonymous access » store as much data as memory or disk space in the printer - great place to store hacking tools, sniffer logs, and other stolen things – Most are poor implementations » easily used in more complex attacks ftp bounce u Berkeley lpd flaws u
Printer flaws. . . u Many printers have FTP servers – Allow anonymous access » store as much data as memory or disk space in the printer - great place to store hacking tools, sniffer logs, and other stolen things – Most are poor implementations » easily used in more complex attacks ftp bounce u Berkeley lpd flaws u
 Printer flaws. . . u Denial of Service – Used as a tool to conduct Do. S » most love to respond to broadcast pings u smurf – Service denied » poor tcp/ip implementations u crash easily » poor service implementation SNMP u ftp u
Printer flaws. . . u Denial of Service – Used as a tool to conduct Do. S » most love to respond to broadcast pings u smurf – Service denied » poor tcp/ip implementations u crash easily » poor service implementation SNMP u ftp u
 Printer fixes? u Disable everything you can
Printer fixes? u Disable everything you can
 Example applications u Defeat sniffing – Race hosts on ARP replies – reply to ARP’s with broadcast address – overpopulate caches » some switches will flush their caches – alter routing on the host you want to sniff
Example applications u Defeat sniffing – Race hosts on ARP replies – reply to ARP’s with broadcast address – overpopulate caches » some switches will flush their caches – alter routing on the host you want to sniff
 Examples u Defeating things like SSH – Alter routing – Create SSH proxy » Client will note key mismatch, but who ever pays attention? u Gaining router access – Obtain auth protocol key via brute force – Extract passwords on the wire – Just plain old sniff
Examples u Defeating things like SSH – Alter routing – Create SSH proxy » Client will note key mismatch, but who ever pays attention? u Gaining router access – Obtain auth protocol key via brute force – Extract passwords on the wire – Just plain old sniff
 What to do? u Maintain good perimeter defenses – At least you only have to trust your employees… u Use cryptographically secure transports – Crypto is good » But crypto fails without good policy u Disable unneeded services – Not using SNMP?
What to do? u Maintain good perimeter defenses – At least you only have to trust your employees… u Use cryptographically secure transports – Crypto is good » But crypto fails without good policy u Disable unneeded services – Not using SNMP?
 What to do. . . u Disable things like routed on hosts – 99% of the time, static routes work fine on end machines u Use the strongest authentication methods possible – Long keys, strong crypto
What to do. . . u Disable things like routed on hosts – 99% of the time, static routes work fine on end machines u Use the strongest authentication methods possible – Long keys, strong crypto
 Questions? Jeremy Rauch
Questions? Jeremy Rauch


