949d7d1b1c839d5f7ff76018a876d8fd.ppt
- Количество слайдов: 132
 Network Implementation and Management Strategies
Network Implementation and Management Strategies
 Outline n n n n Explain why a network implementation strategy is needed Examine the principles of network design Explain why a network management strategy is needed Describe network management categories and related activities Classify current network management tools according to functionality Examine different network management strategies Select a management strategy for this book
Outline n n n n Explain why a network implementation strategy is needed Examine the principles of network design Explain why a network management strategy is needed Describe network management categories and related activities Classify current network management tools according to functionality Examine different network management strategies Select a management strategy for this book
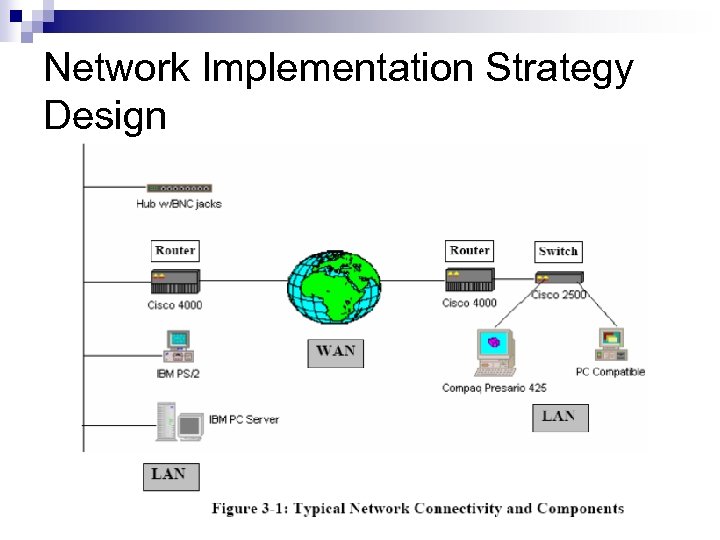 Network Implementation Strategy Design
Network Implementation Strategy Design
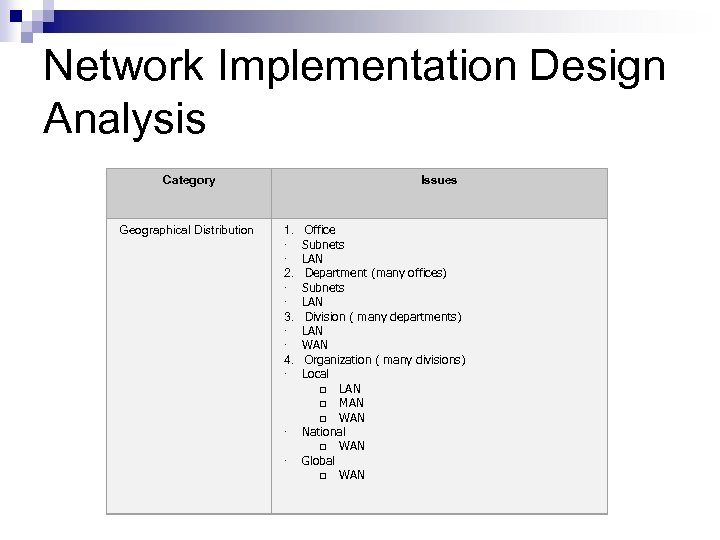 Network Implementation Design Analysis Category Geographical Distribution Issues 1. Office · Subnets · LAN 2. Department (many offices) · Subnets · LAN 3. Division ( many departments) · LAN · WAN 4. Organization ( many divisions) · Local q LAN q MAN q WAN · National q WAN · Global q WAN
Network Implementation Design Analysis Category Geographical Distribution Issues 1. Office · Subnets · LAN 2. Department (many offices) · Subnets · LAN 3. Division ( many departments) · LAN · WAN 4. Organization ( many divisions) · Local q LAN q MAN q WAN · National q WAN · Global q WAN
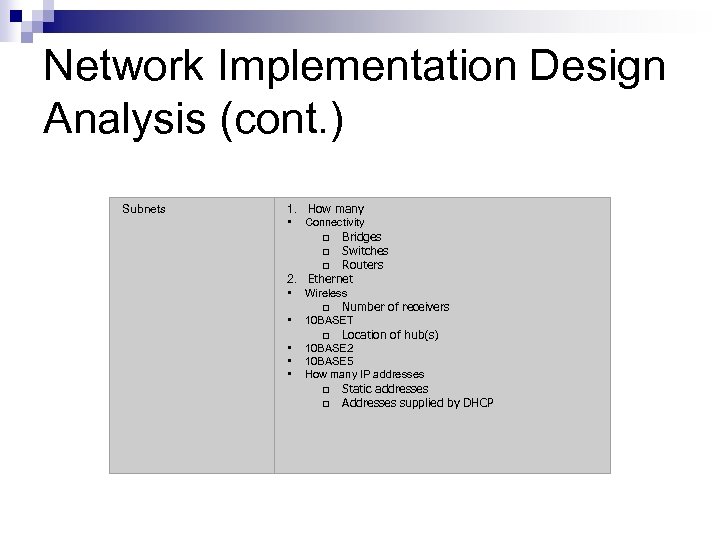 Network Implementation Design Analysis (cont. ) Subnets 1. How many • Connectivity q Bridges q Switches q Routers 2. Ethernet • Wireless q Number of receivers • 10 BASET q Location of hub(s) • 10 BASE 2 • 10 BASE 5 • How many IP addresses q Static addresses q Addresses supplied by DHCP
Network Implementation Design Analysis (cont. ) Subnets 1. How many • Connectivity q Bridges q Switches q Routers 2. Ethernet • Wireless q Number of receivers • 10 BASET q Location of hub(s) • 10 BASE 2 • 10 BASE 5 • How many IP addresses q Static addresses q Addresses supplied by DHCP
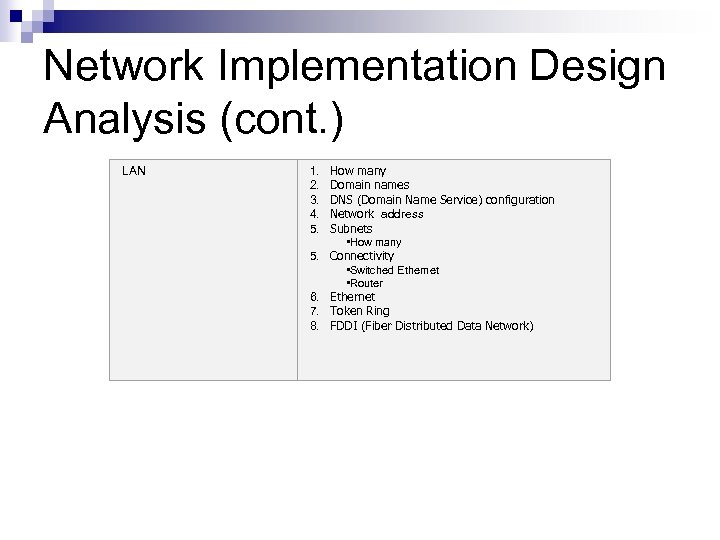 Network Implementation Design Analysis (cont. ) LAN 1. How many 2. Domain names 3. DNS (Domain Name Service) configuration 4. Network address 5. Subnets • How many 5. Connectivity • Switched Ethernet • Router 6. Ethernet 7. Token Ring 8. FDDI (Fiber Distributed Data Network)
Network Implementation Design Analysis (cont. ) LAN 1. How many 2. Domain names 3. DNS (Domain Name Service) configuration 4. Network address 5. Subnets • How many 5. Connectivity • Switched Ethernet • Router 6. Ethernet 7. Token Ring 8. FDDI (Fiber Distributed Data Network)
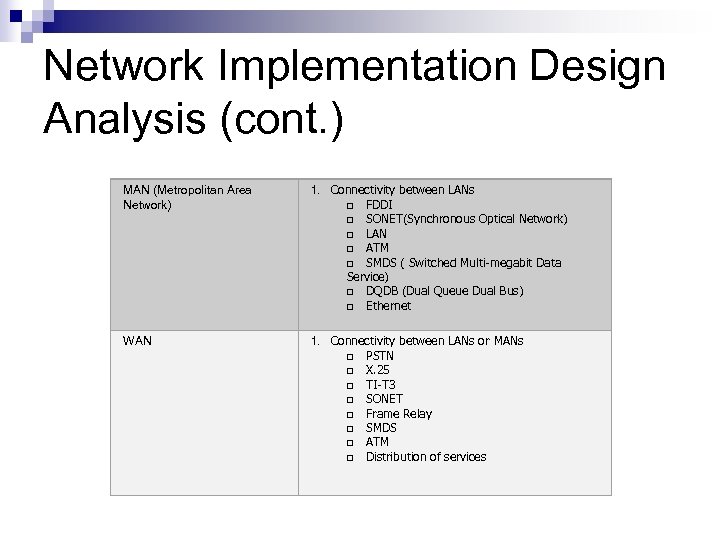 Network Implementation Design Analysis (cont. ) MAN (Metropolitan Area Network) 1. Connectivity between LANs q FDDI q SONET(Synchronous Optical Network) q LAN q ATM q SMDS ( Switched Multi-megabit Data Service) q DQDB (Dual Queue Dual Bus) q Ethernet WAN 1. Connectivity between LANs or MANs q PSTN q X. 25 q TI-T 3 q SONET q Frame Relay q SMDS q ATM q Distribution of services
Network Implementation Design Analysis (cont. ) MAN (Metropolitan Area Network) 1. Connectivity between LANs q FDDI q SONET(Synchronous Optical Network) q LAN q ATM q SMDS ( Switched Multi-megabit Data Service) q DQDB (Dual Queue Dual Bus) q Ethernet WAN 1. Connectivity between LANs or MANs q PSTN q X. 25 q TI-T 3 q SONET q Frame Relay q SMDS q ATM q Distribution of services
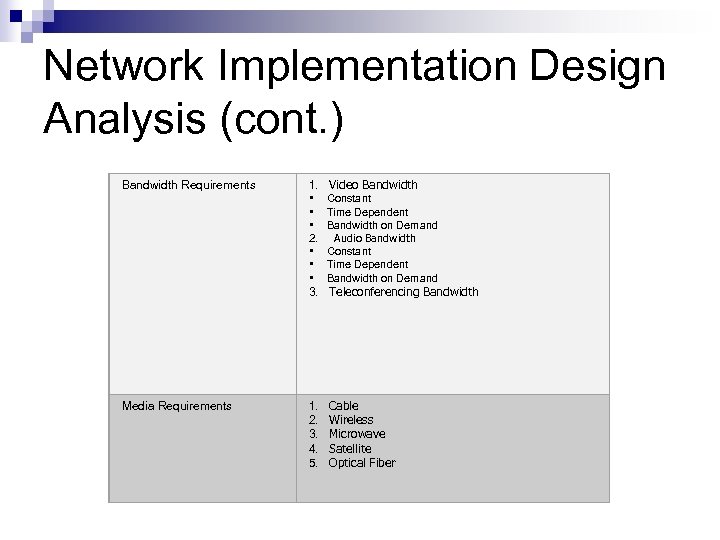 Network Implementation Design Analysis (cont. ) Bandwidth Requirements 1. Video Bandwidth • Constant • Time Dependent • Bandwidth on Demand 2. Audio Bandwidth • Constant • Time Dependent • Bandwidth on Demand 3. Teleconferencing Bandwidth Media Requirements 1. Cable 2. Wireless 3. Microwave 4. Satellite 5. Optical Fiber
Network Implementation Design Analysis (cont. ) Bandwidth Requirements 1. Video Bandwidth • Constant • Time Dependent • Bandwidth on Demand 2. Audio Bandwidth • Constant • Time Dependent • Bandwidth on Demand 3. Teleconferencing Bandwidth Media Requirements 1. Cable 2. Wireless 3. Microwave 4. Satellite 5. Optical Fiber
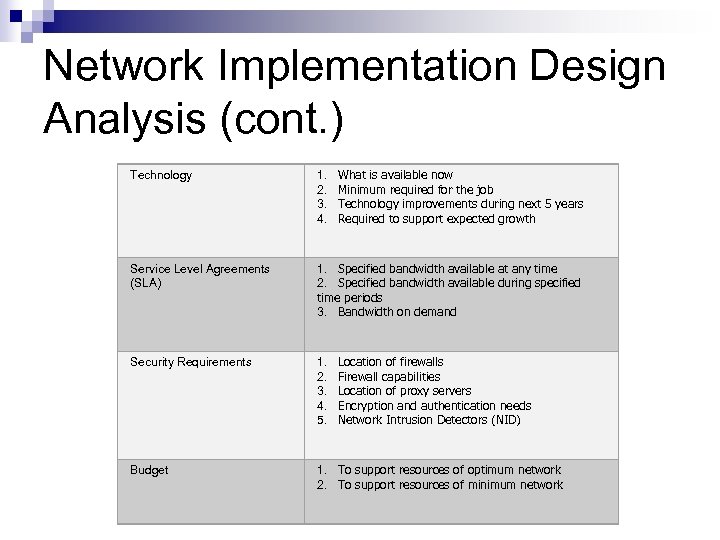 Network Implementation Design Analysis (cont. ) Technology 1. What is available now 2. Minimum required for the job 3. Technology improvements during next 5 years 4. Required to support expected growth Service Level Agreements (SLA) 1. Specified bandwidth available at any time 2. Specified bandwidth available during specified time periods 3. Bandwidth on demand Security Requirements 1. Location of firewalls 2. Firewall capabilities 3. Location of proxy servers 4. Encryption and authentication needs 5. Network Intrusion Detectors (NID) Budget 1. To support resources of optimum network 2. To support resources of minimum network
Network Implementation Design Analysis (cont. ) Technology 1. What is available now 2. Minimum required for the job 3. Technology improvements during next 5 years 4. Required to support expected growth Service Level Agreements (SLA) 1. Specified bandwidth available at any time 2. Specified bandwidth available during specified time periods 3. Bandwidth on demand Security Requirements 1. Location of firewalls 2. Firewall capabilities 3. Location of proxy servers 4. Encryption and authentication needs 5. Network Intrusion Detectors (NID) Budget 1. To support resources of optimum network 2. To support resources of minimum network
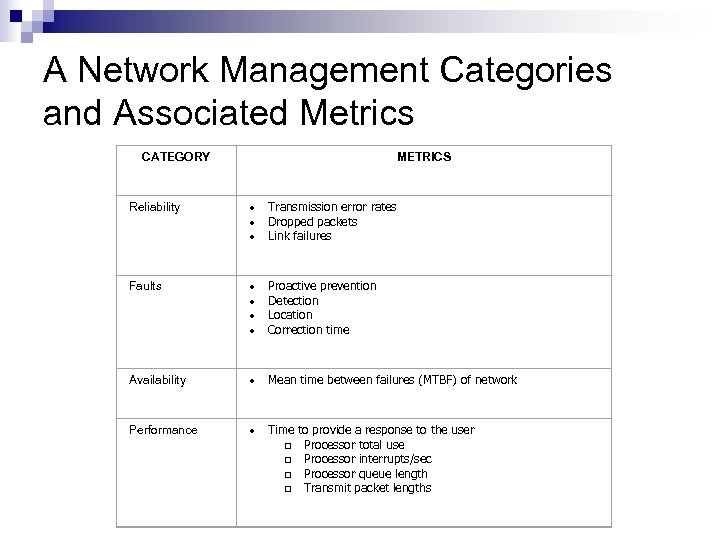 A Network Management Categories and Associated Metrics CATEGORY METRICS Reliability · Transmission error rates · Dropped packets · Link failures Faults · Proactive prevention · Detection · Location · Correction time Availability · Mean time between failures (MTBF) of network Performance · Time to provide a response to the user q Processor total use q Processor interrupts/sec q Processor queue length q Transmit packet lengths
A Network Management Categories and Associated Metrics CATEGORY METRICS Reliability · Transmission error rates · Dropped packets · Link failures Faults · Proactive prevention · Detection · Location · Correction time Availability · Mean time between failures (MTBF) of network Performance · Time to provide a response to the user q Processor total use q Processor interrupts/sec q Processor queue length q Transmit packet lengths
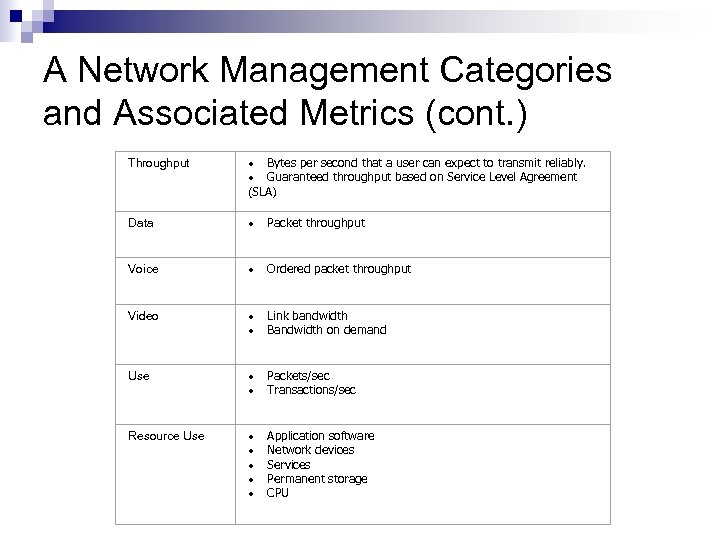 A Network Management Categories and Associated Metrics (cont. ) Throughput · Bytes per second that a user can expect to transmit reliably. · Guaranteed throughput based on Service Level Agreement (SLA) Data · Packet throughput Voice · Ordered packet throughput Video · Link bandwidth · Bandwidth on demand Use · Packets/sec · Transactions/sec Resource Use · Application software · Network devices · Services · Permanent storage · CPU
A Network Management Categories and Associated Metrics (cont. ) Throughput · Bytes per second that a user can expect to transmit reliably. · Guaranteed throughput based on Service Level Agreement (SLA) Data · Packet throughput Voice · Ordered packet throughput Video · Link bandwidth · Bandwidth on demand Use · Packets/sec · Transactions/sec Resource Use · Application software · Network devices · Services · Permanent storage · CPU
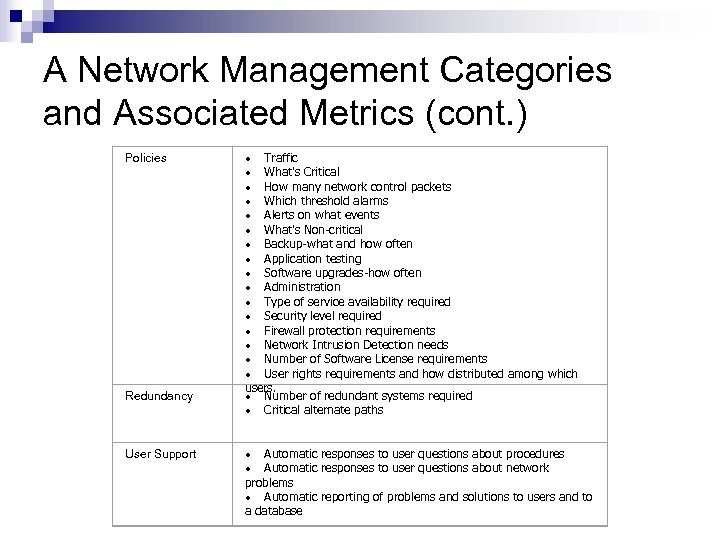 A Network Management Categories and Associated Metrics (cont. ) Policies Redundancy User Support · Traffic · What's Critical · How many network control packets · Which threshold alarms · Alerts on what events · What's Non-critical · Backup-what and how often · Application testing · Software upgrades-how often · Administration · Type of service availability required · Security level required · Firewall protection requirements · Network Intrusion Detection needs · Number of Software License requirements · User rights requirements and how distributed among which users. · Number of redundant systems required · Critical alternate paths · Automatic responses to user questions about procedures · Automatic responses to user questions about network problems · Automatic reporting of problems and solutions to users and to a database
A Network Management Categories and Associated Metrics (cont. ) Policies Redundancy User Support · Traffic · What's Critical · How many network control packets · Which threshold alarms · Alerts on what events · What's Non-critical · Backup-what and how often · Application testing · Software upgrades-how often · Administration · Type of service availability required · Security level required · Firewall protection requirements · Network Intrusion Detection needs · Number of Software License requirements · User rights requirements and how distributed among which users. · Number of redundant systems required · Critical alternate paths · Automatic responses to user questions about procedures · Automatic responses to user questions about network problems · Automatic reporting of problems and solutions to users and to a database
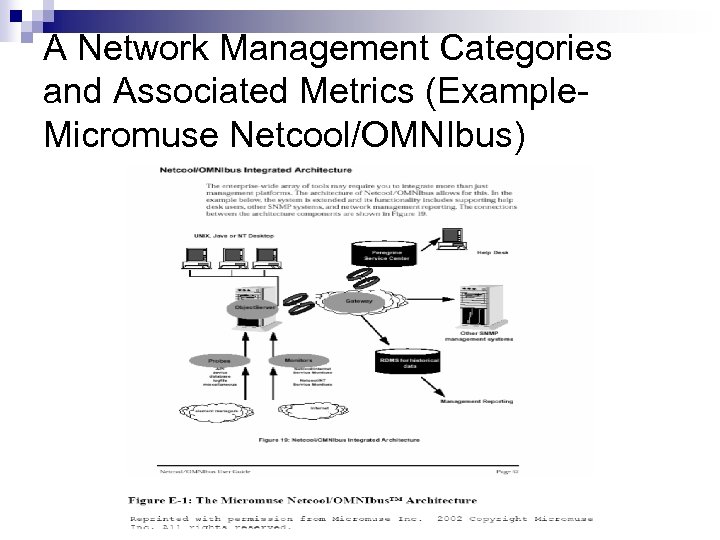 A Network Management Categories and Associated Metrics (Example. Micromuse Netcool/OMNIbus)
A Network Management Categories and Associated Metrics (Example. Micromuse Netcool/OMNIbus)
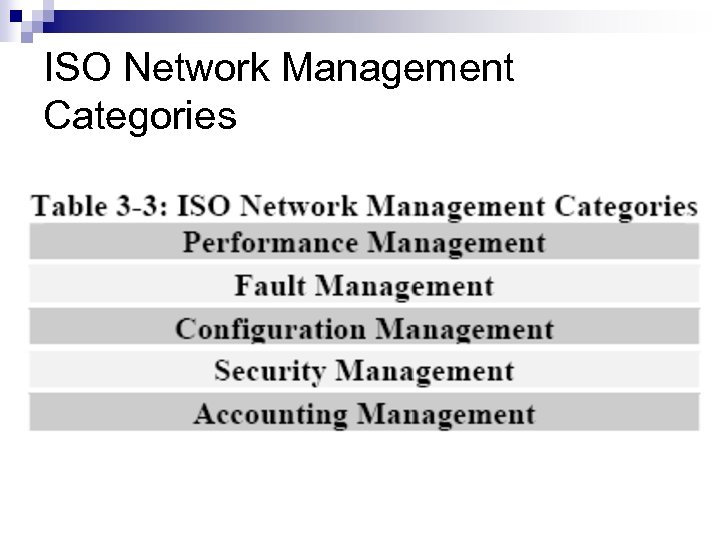 ISO Network Management Categories
ISO Network Management Categories
 ISO Network Management Categories (Cont. ) n 效能管理 (Performance Management) ¨ Tells you how the network is doing n 障礙管理 (Fault Management) ¨ Tells you what your network is doing n 組態管理 (Configuration Management) ¨ Tells you where everything is in the network n 安全管理 (Security Management) ¨ Tells you who is using your network n 計量管理 (Accounting Management) ¨ Tells you when your network is used
ISO Network Management Categories (Cont. ) n 效能管理 (Performance Management) ¨ Tells you how the network is doing n 障礙管理 (Fault Management) ¨ Tells you what your network is doing n 組態管理 (Configuration Management) ¨ Tells you where everything is in the network n 安全管理 (Security Management) ¨ Tells you who is using your network n 計量管理 (Accounting Management) ¨ Tells you when your network is used
 Performance Management (效 能管理 ) n Performance Management ¨ Measuring the performance of network hardware, software, and media n Measuring Metrics: ¨ Overall throughput ¨ Percentage utilization ¨ Error rate ¨ Response time
Performance Management (效 能管理 ) n Performance Management ¨ Measuring the performance of network hardware, software, and media n Measuring Metrics: ¨ Overall throughput ¨ Percentage utilization ¨ Error rate ¨ Response time
 Performance Management Sub. Categories and Related Activities Collecting Baseline Utilization Data · Measuring link utilization using a probe · Counting packets received/transmitted by a specific device · Measuring device processor usage · Monitoring device queue lengths · Monitoring device memory utilization · Measuring total response times Collecting a History of Utilization Data · Measuring utilization and response times at different times of the day · Measuring utilization and response times on different days over an extended period Capacity Planning · Manually graphing or using a network management tool to graph utilization as a function of time to detect trends · Preparing trend reports to document projected need for and the cost of network expansion.
Performance Management Sub. Categories and Related Activities Collecting Baseline Utilization Data · Measuring link utilization using a probe · Counting packets received/transmitted by a specific device · Measuring device processor usage · Monitoring device queue lengths · Monitoring device memory utilization · Measuring total response times Collecting a History of Utilization Data · Measuring utilization and response times at different times of the day · Measuring utilization and response times on different days over an extended period Capacity Planning · Manually graphing or using a network management tool to graph utilization as a function of time to detect trends · Preparing trend reports to document projected need for and the cost of network expansion.
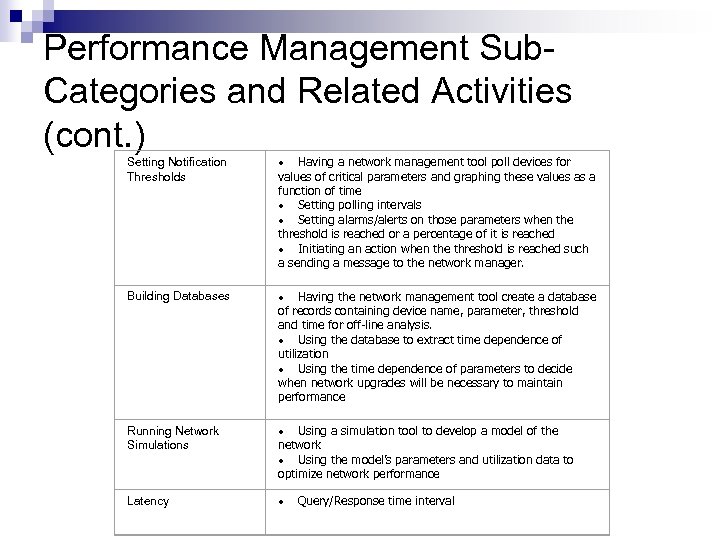 Performance Management Sub. Categories and Related Activities (cont. ) Setting Notification Thresholds · Having a network management tool poll devices for values of critical parameters and graphing these values as a function of time · Setting polling intervals · Setting alarms/alerts on those parameters when the threshold is reached or a percentage of it is reached · Initiating an action when the threshold is reached such a sending a message to the network manager. Building Databases · Having the network management tool create a database of records containing device name, parameter, threshold and time for off-line analysis. · Using the database to extract time dependence of utilization · Using the time dependence of parameters to decide when network upgrades will be necessary to maintain performance Running Network Simulations · Using a simulation tool to develop a model of the network · Using the model’s parameters and utilization data to optimize network performance Latency · Query/Response time interval
Performance Management Sub. Categories and Related Activities (cont. ) Setting Notification Thresholds · Having a network management tool poll devices for values of critical parameters and graphing these values as a function of time · Setting polling intervals · Setting alarms/alerts on those parameters when the threshold is reached or a percentage of it is reached · Initiating an action when the threshold is reached such a sending a message to the network manager. Building Databases · Having the network management tool create a database of records containing device name, parameter, threshold and time for off-line analysis. · Using the database to extract time dependence of utilization · Using the time dependence of parameters to decide when network upgrades will be necessary to maintain performance Running Network Simulations · Using a simulation tool to develop a model of the network · Using the model’s parameters and utilization data to optimize network performance Latency · Query/Response time interval
 Implementing Steps of Performance Management 1. 搜集目前網路設備與鏈結之使用效能相關 資訊。 2. 分析所搜集之效能相關資訊。 3. 設定使用率或相關效能參數之臨界值 (Threshold) 。 4. 進行網路模擬。
Implementing Steps of Performance Management 1. 搜集目前網路設備與鏈結之使用效能相關 資訊。 2. 分析所搜集之效能相關資訊。 3. 設定使用率或相關效能參數之臨界值 (Threshold) 。 4. 進行網路模擬。
 搜集效能相關資訊 n 網路伺服器: ¨ processor load, disk access rate, network interface card utilization n 橋接器/路由器: ¨ packet forwarding rate, processor load, percentage of dropped frames on each interface, number of packets being held in a queue.
搜集效能相關資訊 n 網路伺服器: ¨ processor load, disk access rate, network interface card utilization n 橋接器/路由器: ¨ packet forwarding rate, processor load, percentage of dropped frames on each interface, number of packets being held in a queue.
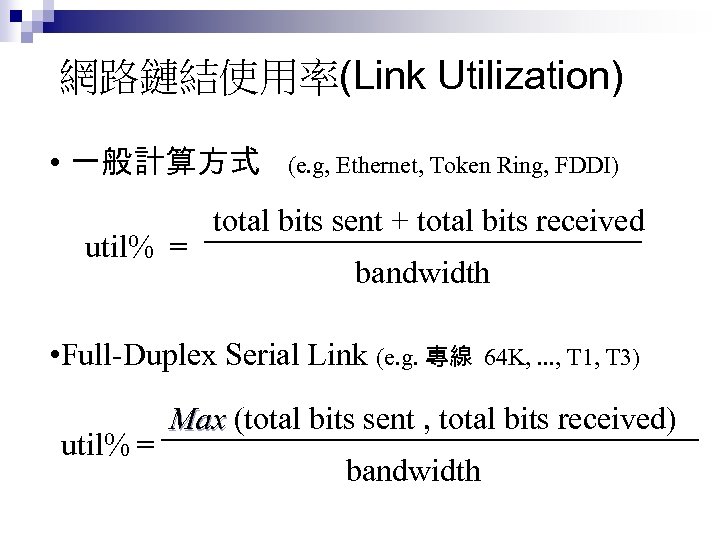 網路鏈結使用率(Link Utilization) • 一般計算方式 (e. g, Ethernet, Token Ring, FDDI) total bits sent + total bits received util% = bandwidth • Full-Duplex Serial Link (e. g. 專線 64 K, . . . , T 1, T 3) util% = Max (total bits sent , total bits received) bandwidth
網路鏈結使用率(Link Utilization) • 一般計算方式 (e. g, Ethernet, Token Ring, FDDI) total bits sent + total bits received util% = bandwidth • Full-Duplex Serial Link (e. g. 專線 64 K, . . . , T 1, T 3) util% = Max (total bits sent , total bits received) bandwidth
 利用SNMP讀取流量資訊 n n 一般網路設備會隨時記錄其網路介面卡從開機至 目前為止已流入及已流出之位元組個數,即 SNMP MIB II 中之 if. In. Octets 及 if. Out. Octets。 使用SNMP,每隔一段時間週期性地讀取對應某 一網路介面卡之if. In. Octets及if. Out. Octets值。 此次所讀得之值減去上次所讀得之值,即為此段 時間內之流量。 使用率 = 一週期內之流量 / (頻寬 週期)
利用SNMP讀取流量資訊 n n 一般網路設備會隨時記錄其網路介面卡從開機至 目前為止已流入及已流出之位元組個數,即 SNMP MIB II 中之 if. In. Octets 及 if. Out. Octets。 使用SNMP,每隔一段時間週期性地讀取對應某 一網路介面卡之if. In. Octets及if. Out. Octets值。 此次所讀得之值減去上次所讀得之值,即為此段 時間內之流量。 使用率 = 一週期內之流量 / (頻寬 週期)
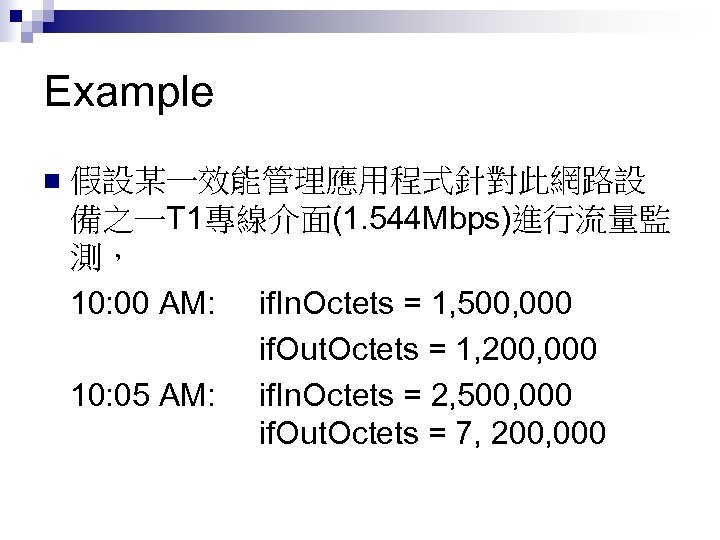 Example 假設某一效能管理應用程式針對此網路設 備之一T 1專線介面(1. 544 Mbps)進行流量監 測, 10: 00 AM: if. In. Octets = 1, 500, 000 if. Out. Octets = 1, 200, 000 10: 05 AM: if. In. Octets = 2, 500, 000 if. Out. Octets = 7, 200, 000 n
Example 假設某一效能管理應用程式針對此網路設 備之一T 1專線介面(1. 544 Mbps)進行流量監 測, 10: 00 AM: if. In. Octets = 1, 500, 000 if. Out. Octets = 1, 200, 000 10: 05 AM: if. In. Octets = 2, 500, 000 if. Out. Octets = 7, 200, 000 n
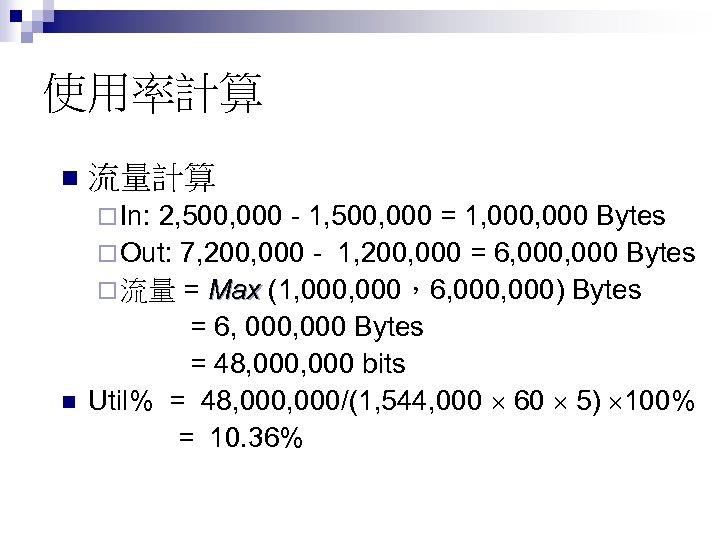 使用率計算 n 流量計算 ¨ In: 2, 500, 000 - 1, 500, 000 = 1, 000 Bytes ¨ Out: 7, 200, 000 - 1, 200, 000 = 6, 000 Bytes ¨ 流量 = Max (1, 000,6, 000) Bytes Max = 6, 000 Bytes = 48, 000 bits n Util% = 48, 000/(1, 544, 000 60 5) 100% = 10. 36%
使用率計算 n 流量計算 ¨ In: 2, 500, 000 - 1, 500, 000 = 1, 000 Bytes ¨ Out: 7, 200, 000 - 1, 200, 000 = 6, 000 Bytes ¨ 流量 = Max (1, 000,6, 000) Bytes Max = 6, 000 Bytes = 48, 000 bits n Util% = 48, 000/(1, 544, 000 60 5) 100% = 10. 36%
 Service Level Measurement n Total Response Time n Rejection Rate n Availability
Service Level Measurement n Total Response Time n Rejection Rate n Availability
 Service Level Measurement (Cont. ) n Total Response Time ¨ the amount of time it takes a datum to enter the network and be processed and for a response to leave the network. ¨ From the viewpoint of applications ¨ Round Trip Time (R. T. T) is measured from the viewpoint of transport protocol.
Service Level Measurement (Cont. ) n Total Response Time ¨ the amount of time it takes a datum to enter the network and be processed and for a response to leave the network. ¨ From the viewpoint of applications ¨ Round Trip Time (R. T. T) is measured from the viewpoint of transport protocol.
 Service Level Measurement (Cont. ) n Rejection Rate ¨ the percentage of time the network cannot transfer information because of the lack of resources and performance. n Availability ¨ the percentage of time the network is accessible for use and operational. ¨ Usually measured as MTBF (Mean Time Between Failure)
Service Level Measurement (Cont. ) n Rejection Rate ¨ the percentage of time the network cannot transfer information because of the lack of resources and performance. n Availability ¨ the percentage of time the network is accessible for use and operational. ¨ Usually measured as MTBF (Mean Time Between Failure)
 Analysis of Performance Information n Graphic performance informantion ¨Historical plots: weekly, monthly, quarterly, yearly ¨Real-time graphical analysis ¨Trend Prediction
Analysis of Performance Information n Graphic performance informantion ¨Historical plots: weekly, monthly, quarterly, yearly ¨Real-time graphical analysis ¨Trend Prediction
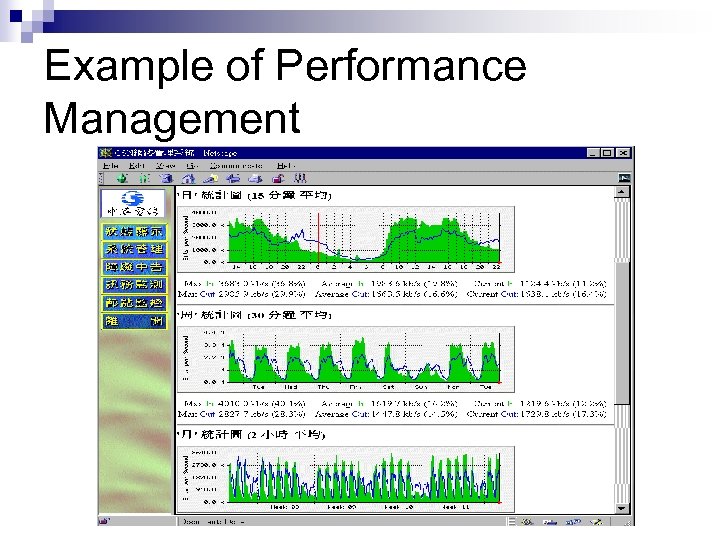 Example of Performance Management
Example of Performance Management
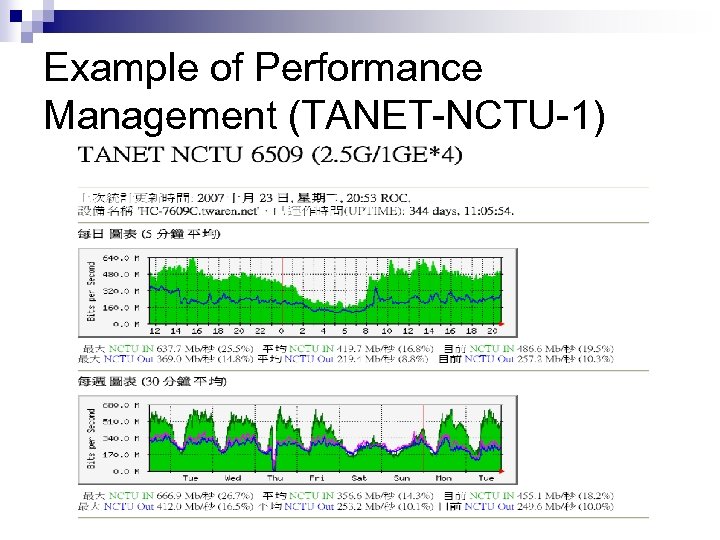 Example of Performance Management (TANET-NCTU-1)
Example of Performance Management (TANET-NCTU-1)
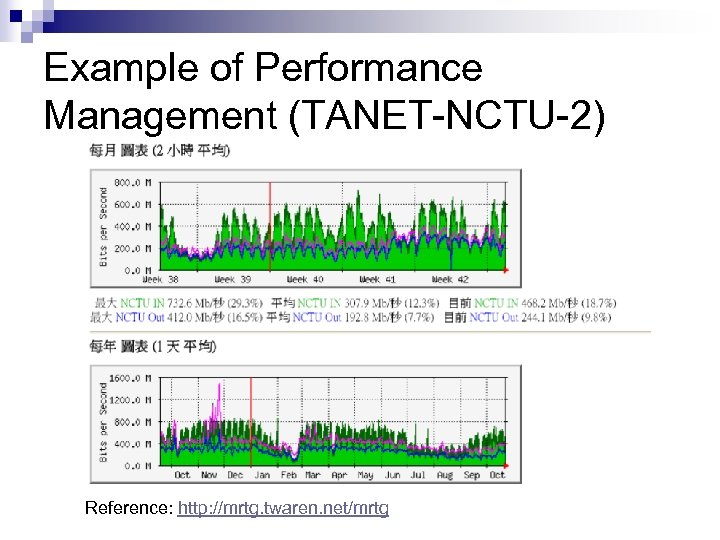 Example of Performance Management (TANET-NCTU-2) Reference: http: //mrtg. twaren. net/mrtg
Example of Performance Management (TANET-NCTU-2) Reference: http: //mrtg. twaren. net/mrtg
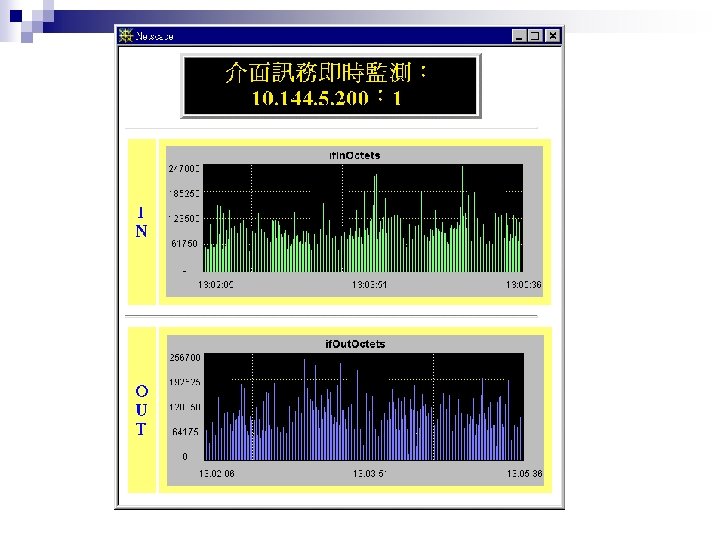
 What to be Analyzed/Graphed? n Device Information ¨ memory usage, processor utilization, disk access rate, number of sessions. n Link Information ¨ utilization, error rate, error percentage
What to be Analyzed/Graphed? n Device Information ¨ memory usage, processor utilization, disk access rate, number of sessions. n Link Information ¨ utilization, error rate, error percentage
 Threshold Setup Set thresholds on a variety of items affecting network performance n When the thresholds are crossed, events are reported. n In general, the values of thresholds are determined according to past experience. n
Threshold Setup Set thresholds on a variety of items affecting network performance n When the thresholds are crossed, events are reported. n In general, the values of thresholds are determined according to past experience. n
 Thresholds n Threshold Priority ¨ In general, priority: low, medium, high ¨ Multiple threshold values for the same item ¨ Thresholds for multiple items n Use rearm mechanism to avoid frequent rearm threshold events
Thresholds n Threshold Priority ¨ In general, priority: low, medium, high ¨ Multiple threshold values for the same item ¨ Thresholds for multiple items n Use rearm mechanism to avoid frequent rearm threshold events
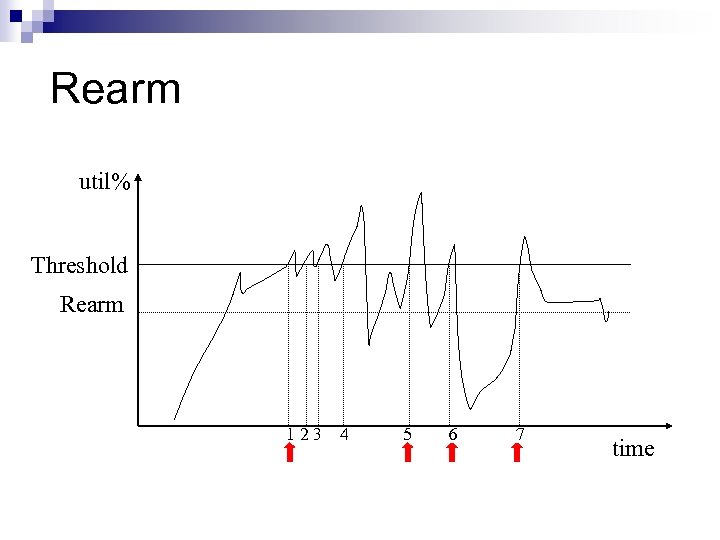 Rearm util% Threshold Rearm 1 2 3 4 5 6 7 time
Rearm util% Threshold Rearm 1 2 3 4 5 6 7 time
 Performance Prediction n Use Regression to predict future trend. n Apply Statistics Theory n Should consider possible factors that affect the prediction. n Network Simulation
Performance Prediction n Use Regression to predict future trend. n Apply Statistics Theory n Should consider possible factors that affect the prediction. n Network Simulation
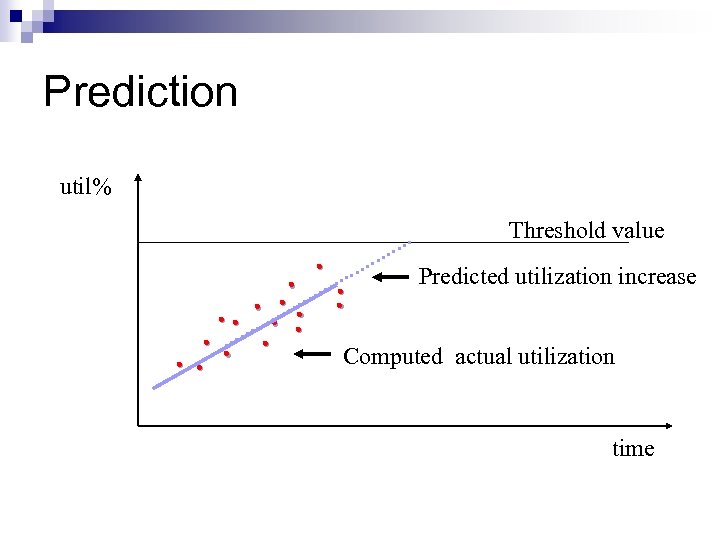 Prediction util% . Threshold value Predicted utilization increase. . . Computed actual utilization. . time
Prediction util% . Threshold value Predicted utilization increase. . . Computed actual utilization. . time
 Fault Management (障礙管理 ) n Fault Management ¨ Detection of a problem, fault isolation and correction to normal operation ¨ A goal is to use trend analysis to predict faults and change network conditions so that the network is always available to users n Fault Management involves the following steps ¨ Discover the problem ¨ Isolate the problem ¨ Fix the problem (if possible)
Fault Management (障礙管理 ) n Fault Management ¨ Detection of a problem, fault isolation and correction to normal operation ¨ A goal is to use trend analysis to predict faults and change network conditions so that the network is always available to users n Fault Management involves the following steps ¨ Discover the problem ¨ Isolate the problem ¨ Fix the problem (if possible)
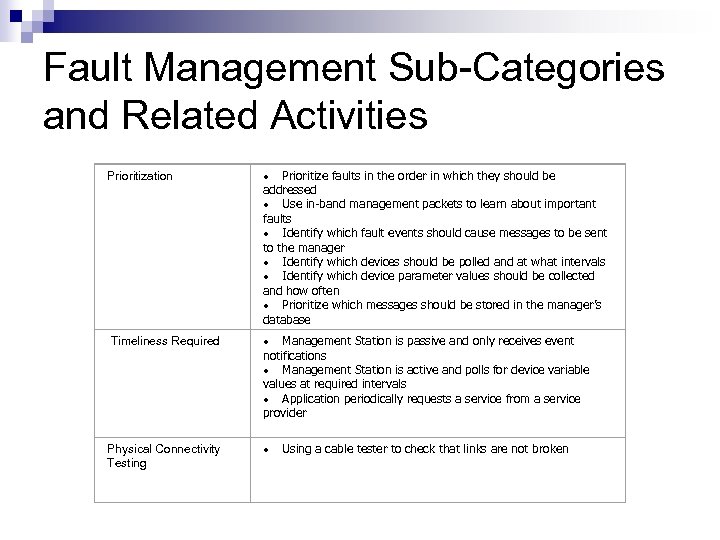 Fault Management Sub-Categories and Related Activities Prioritization · Prioritize faults in the order in which they should be addressed · Use in-band management packets to learn about important faults · Identify which fault events should cause messages to be sent to the manager · Identify which devices should be polled and at what intervals · Identify which device parameter values should be collected and how often · Prioritize which messages should be stored in the manager’s database Timeliness Required · Management Station is passive and only receives event notifications · Management Station is active and polls for device variable values at required intervals · Application periodically requests a service from a service provider Physical Connectivity Testing · Using a cable tester to check that links are not broken
Fault Management Sub-Categories and Related Activities Prioritization · Prioritize faults in the order in which they should be addressed · Use in-band management packets to learn about important faults · Identify which fault events should cause messages to be sent to the manager · Identify which devices should be polled and at what intervals · Identify which device parameter values should be collected and how often · Prioritize which messages should be stored in the manager’s database Timeliness Required · Management Station is passive and only receives event notifications · Management Station is active and polls for device variable values at required intervals · Application periodically requests a service from a service provider Physical Connectivity Testing · Using a cable tester to check that links are not broken
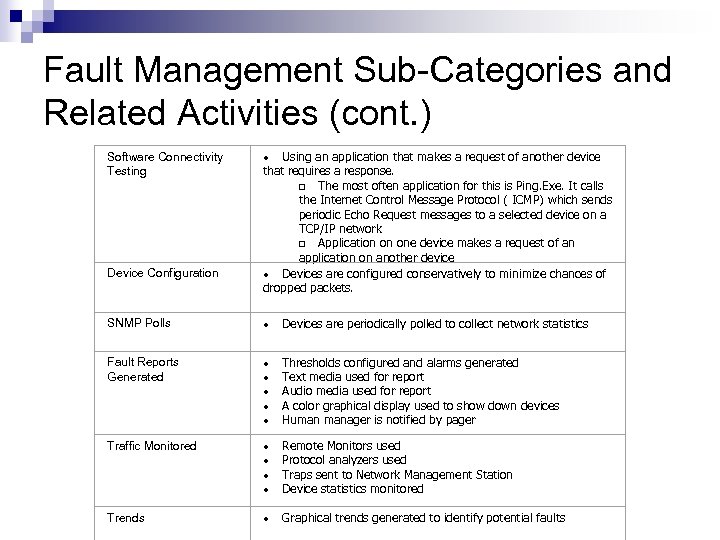 Fault Management Sub-Categories and Related Activities (cont. ) Software Connectivity Testing Device Configuration · Using an application that makes a request of another device that requires a response. q The most often application for this is Ping. Exe. It calls the Internet Control Message Protocol ( ICMP) which sends periodic Echo Request messages to a selected device on a TCP/IP network q Application on one device makes a request of an application on another device · Devices are configured conservatively to minimize chances of dropped packets. SNMP Polls · Devices are periodically polled to collect network statistics Fault Reports Generated · Thresholds configured and alarms generated · Text media used for report · Audio media used for report · A color graphical display used to show down devices · Human manager is notified by pager Traffic Monitored · Remote Monitors used · Protocol analyzers used · Traps sent to Network Management Station · Device statistics monitored Trends · Graphical trends generated to identify potential faults
Fault Management Sub-Categories and Related Activities (cont. ) Software Connectivity Testing Device Configuration · Using an application that makes a request of another device that requires a response. q The most often application for this is Ping. Exe. It calls the Internet Control Message Protocol ( ICMP) which sends periodic Echo Request messages to a selected device on a TCP/IP network q Application on one device makes a request of an application on another device · Devices are configured conservatively to minimize chances of dropped packets. SNMP Polls · Devices are periodically polled to collect network statistics Fault Reports Generated · Thresholds configured and alarms generated · Text media used for report · Audio media used for report · A color graphical display used to show down devices · Human manager is notified by pager Traffic Monitored · Remote Monitors used · Protocol analyzers used · Traps sent to Network Management Station · Device statistics monitored Trends · Graphical trends generated to identify potential faults
 Executing Steps for Fault Management Discover the problem ¨Identifying the occurrence of a fault on the network. n Isolate the problem ¨Isolating the cause of the fault. n Fix the problem (if possible) ¨Correcting the fault. n
Executing Steps for Fault Management Discover the problem ¨Identifying the occurrence of a fault on the network. n Isolate the problem ¨Isolating the cause of the fault. n Fix the problem (if possible) ¨Correcting the fault. n
 Discover the Problem n Event report ¨ 網路設備自行發現問題時,主動向網管系統發 出事件報告(Event Report)。 ¨ 注意:當網路設備完全故障時,無法發出任何 事件報告。 n Periodic Polling ¨ 網管系統每隔一段時間主動發出偵測訊息至被 管設備,或向被管設備要求障礙相關網管資訊 。
Discover the Problem n Event report ¨ 網路設備自行發現問題時,主動向網管系統發 出事件報告(Event Report)。 ¨ 注意:當網路設備完全故障時,無法發出任何 事件報告。 n Periodic Polling ¨ 網管系統每隔一段時間主動發出偵測訊息至被 管設備,或向被管設備要求障礙相關網管資訊 。
 Periodic Polling 障礙監測之探詢週期一般設為 5~15分鐘 n 探詢週期決定因素: n ¨ 及時性需求 ¨ 被管設備之數目 ¨ 網路頻寬 ¨ 處理時間 ¨ 網管通信協定之限制 例如: SNMP: Counter (32 -bit) 資料歸零問題
Periodic Polling 障礙監測之探詢週期一般設為 5~15分鐘 n 探詢週期決定因素: n ¨ 及時性需求 ¨ 被管設備之數目 ¨ 網路頻寬 ¨ 處理時間 ¨ 網管通信協定之限制 例如: SNMP: Counter (32 -bit) 資料歸零問題
 PING: Packet Internet Groper n PING為一利用ICMP ECHO / ECHO Reply 所設計之TCP/IP網路探測 具。 n 功能: n ¨ 測試可否通達某一主機 ¨ 計算封包來回時間 (Round Trip Time) ¨ 估算封包漏失率 (Packet Loss Rate)
PING: Packet Internet Groper n PING為一利用ICMP ECHO / ECHO Reply 所設計之TCP/IP網路探測 具。 n 功能: n ¨ 測試可否通達某一主機 ¨ 計算封包來回時間 (Round Trip Time) ¨ 估算封包漏失率 (Packet Loss Rate)
 An Example of PING
An Example of PING
 網管系統障礙管理功能 n 問題偵測 ¨ n 問題存錄(Log) ¨ n 將發生問題之設備名稱、問題發現時間、可能原因等資訊記錄 於存錄(Log)檔案中。 狀態顏色改變 ¨ n 利用類似Ping方式,對每一被管設備進行偵測。 改變在網管系統圖形化介面中代表發生問題之設備的圖示之顏 色。 偵測介面狀態 ¨ 每一網路設備可能含有多個介面卡(Interface),一般網管系統會監 測每一介面卡之運作狀態(Operational Status)。
網管系統障礙管理功能 n 問題偵測 ¨ n 問題存錄(Log) ¨ n 將發生問題之設備名稱、問題發現時間、可能原因等資訊記錄 於存錄(Log)檔案中。 狀態顏色改變 ¨ n 利用類似Ping方式,對每一被管設備進行偵測。 改變在網管系統圖形化介面中代表發生問題之設備的圖示之顏 色。 偵測介面狀態 ¨ 每一網路設備可能含有多個介面卡(Interface),一般網管系統會監 測每一介面卡之運作狀態(Operational Status)。
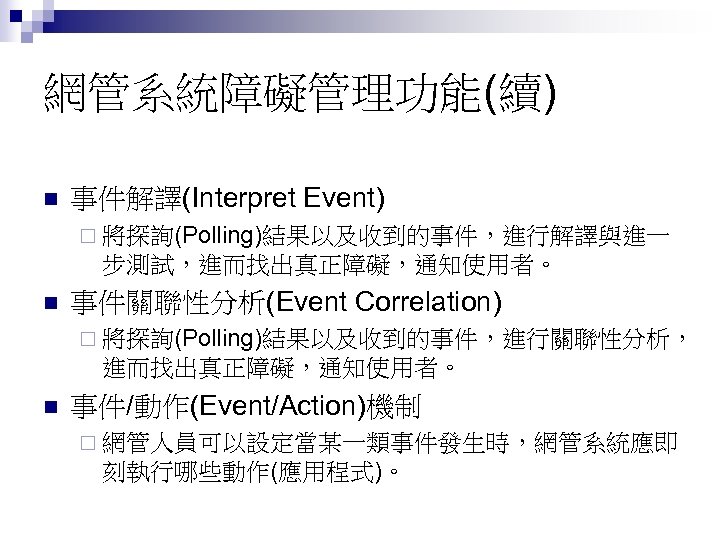 網管系統障礙管理功能(續) n 事件解譯(Interpret Event) ¨ 將探詢(Polling)結果以及收到的事件,進行解譯與進一 步測試,進而找出真正障礙,通知使用者。 n 事件關聯性分析(Event Correlation) ¨ 將探詢(Polling)結果以及收到的事件,進行關聯性分析, 進而找出真正障礙,通知使用者。 n 事件/動作(Event/Action)機制 ¨ 網管人員可以設定當某一類事件發生時,網管系統應即 刻執行哪些動作(應用程式)。
網管系統障礙管理功能(續) n 事件解譯(Interpret Event) ¨ 將探詢(Polling)結果以及收到的事件,進行解譯與進一 步測試,進而找出真正障礙,通知使用者。 n 事件關聯性分析(Event Correlation) ¨ 將探詢(Polling)結果以及收到的事件,進行關聯性分析, 進而找出真正障礙,通知使用者。 n 事件/動作(Event/Action)機制 ¨ 網管人員可以設定當某一類事件發生時,網管系統應即 刻執行哪些動作(應用程式)。
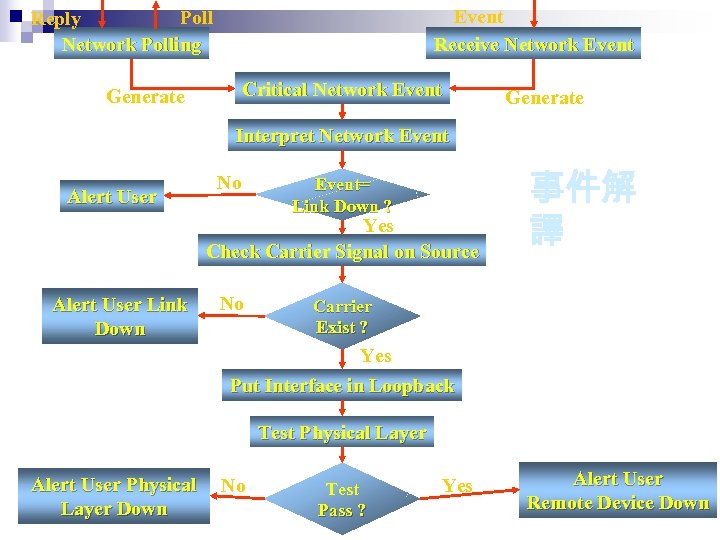 Event Receive Network Event Poll Reply Network Polling Critical Network Event Generate Interpret Network Event Alert User No Event= Link Down ? Yes Check Carrier Signal on Source Alert User Link Down No 事件解 譯 Carrier Exist ? Yes Put Interface in Loopback Test Physical Layer Alert User Physical Layer Down No Test Pass ? Yes Alert User Remote Device Down
Event Receive Network Event Poll Reply Network Polling Critical Network Event Generate Interpret Network Event Alert User No Event= Link Down ? Yes Check Carrier Signal on Source Alert User Link Down No 事件解 譯 Carrier Exist ? Yes Put Interface in Loopback Test Physical Layer Alert User Physical Layer Down No Test Pass ? Yes Alert User Remote Device Down
 障礙(事件)報告方式 n 文字 (Text) ¨ 以純文字訊息方式,顯示於螢幕上或圖形化使用者介面 上之事件瀏覽器。 n 圖示 (Picture) ¨ 改變圖示顏色,或加以閃爍方式提醒網管人員。 n 聲音 (Audio) ¨ 以聲響方式引起網管人員注意。 n Pager ¨ 以B. B. Call或行動電話短訊服務方式,即時告知網管人 員。 n E-mail ¨ 以E-mail方式,通知網管人員或客戶。
障礙(事件)報告方式 n 文字 (Text) ¨ 以純文字訊息方式,顯示於螢幕上或圖形化使用者介面 上之事件瀏覽器。 n 圖示 (Picture) ¨ 改變圖示顏色,或加以閃爍方式提醒網管人員。 n 聲音 (Audio) ¨ 以聲響方式引起網管人員注意。 n Pager ¨ 以B. B. Call或行動電話短訊服務方式,即時告知網管人 員。 n E-mail ¨ 以E-mail方式,通知網管人員或客戶。
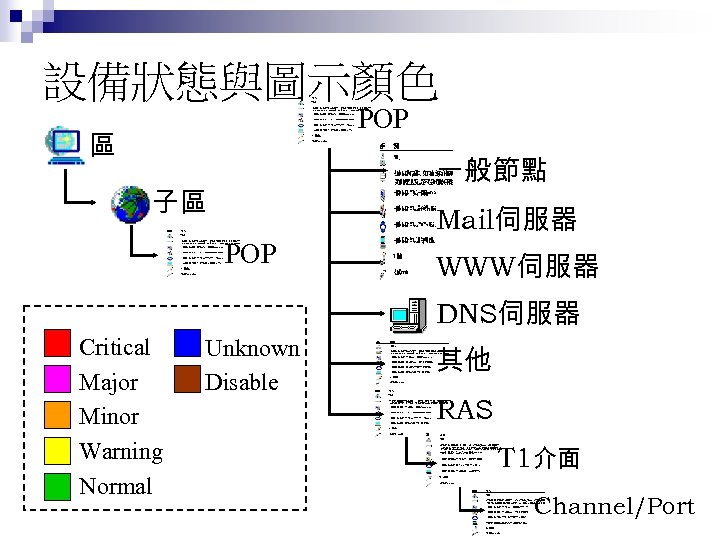 設備狀態與圖示顏色 POP 區 一般節點 子區 Mail伺服器 POP WWW伺服器 DNS伺服器 Critical Major Minor Warning Normal Unknown Disable 其他 RAS T 1介面 Channel/Port
設備狀態與圖示顏色 POP 區 一般節點 子區 Mail伺服器 POP WWW伺服器 DNS伺服器 Critical Major Minor Warning Normal Unknown Disable 其他 RAS T 1介面 Channel/Port
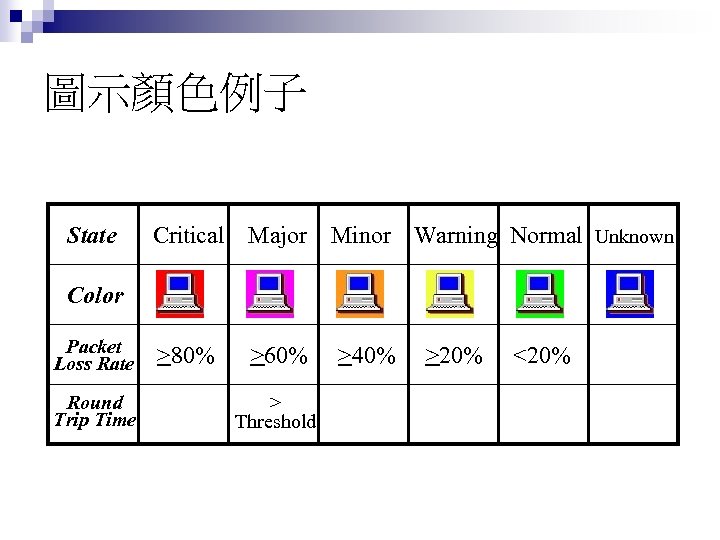 圖示顏色例子 State Critical Major Minor Warning Normal Unknown Color Packet >80% >60% >40% >20% <20% Loss Rate Round Trip Time > Threshold
圖示顏色例子 State Critical Major Minor Warning Normal Unknown Color Packet >80% >60% >40% >20% <20% Loss Rate Round Trip Time > Threshold
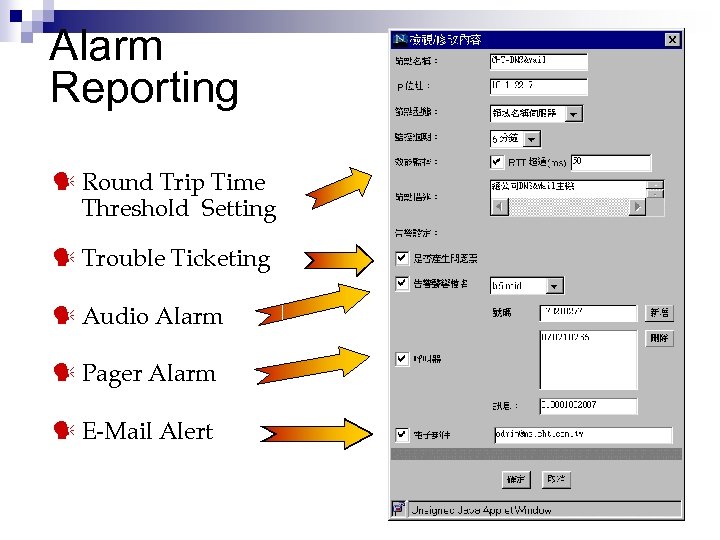 Alarm Reporting Round Trip Time Threshold Setting Trouble Ticketing Audio Alarm Pager Alarm E-Mail Alert
Alarm Reporting Round Trip Time Threshold Setting Trouble Ticketing Audio Alarm Pager Alarm E-Mail Alert
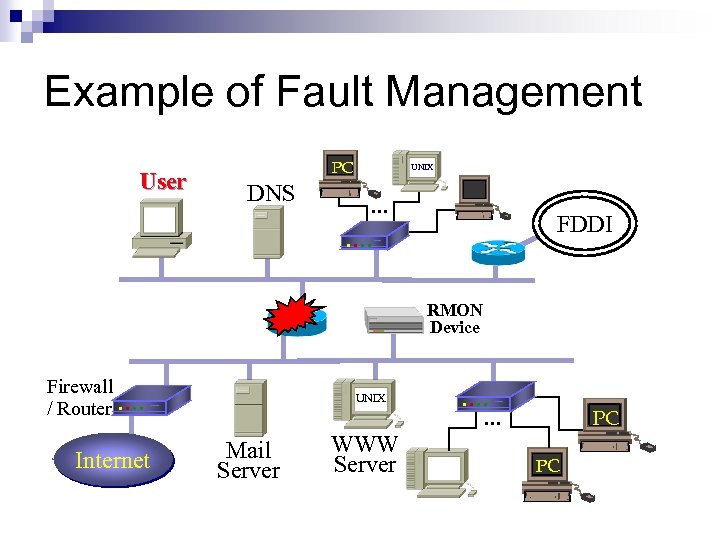 Example of Fault Management DNS UNIX . . . User PC FDDI . . RMON Device Firewall / Router. . Internet . . UNIX Mail Server WWW Server . . . UNIX PC PC
Example of Fault Management DNS UNIX . . . User PC FDDI . . RMON Device Firewall / Router. . Internet . . UNIX Mail Server WWW Server . . . UNIX PC PC
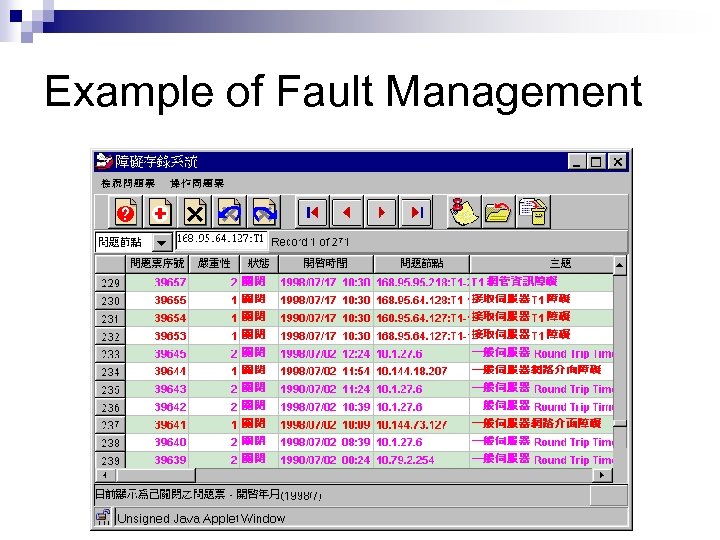 Example of Fault Management
Example of Fault Management
 Configuration Management (組 態管理 ) n Configuration Management ¨ The process of finding and setting up (configuring) network devices ¨ Automated configuration is becoming a more important part of network management as the sizes of networks grow
Configuration Management (組 態管理 ) n Configuration Management ¨ The process of finding and setting up (configuring) network devices ¨ Automated configuration is becoming a more important part of network management as the sizes of networks grow
 Configuration Management Sub. Categories and Related Activities Configuration (Local) · Choice of medium access protocol · Choice of correct cabling and connectors · Choice of cabling layout · Determining the number of physical interfaces on devices · Setting device interface parameter values q Interrupts q I/O Addresses q DMA numbers q Network layer addresses (e. g. IP, Net. Ware, etc) · Configuration of multiport devices (e. g. hubs, switches and routers) · Use of the Windows Registry · Comparing current versus stored configurations · Checking software environments · SNMP service Configuration (Remote) · From the network management station q Disabling device ports q Redirecting port forwarding q Disabling devices q Comparing current versus stored configurations q Configuring routing tables q Configuring security parameters such as community strings and user names q Configuring addresses of management stations to which traps should be sent · Verifying integrity of changes
Configuration Management Sub. Categories and Related Activities Configuration (Local) · Choice of medium access protocol · Choice of correct cabling and connectors · Choice of cabling layout · Determining the number of physical interfaces on devices · Setting device interface parameter values q Interrupts q I/O Addresses q DMA numbers q Network layer addresses (e. g. IP, Net. Ware, etc) · Configuration of multiport devices (e. g. hubs, switches and routers) · Use of the Windows Registry · Comparing current versus stored configurations · Checking software environments · SNMP service Configuration (Remote) · From the network management station q Disabling device ports q Redirecting port forwarding q Disabling devices q Comparing current versus stored configurations q Configuring routing tables q Configuring security parameters such as community strings and user names q Configuring addresses of management stations to which traps should be sent · Verifying integrity of changes
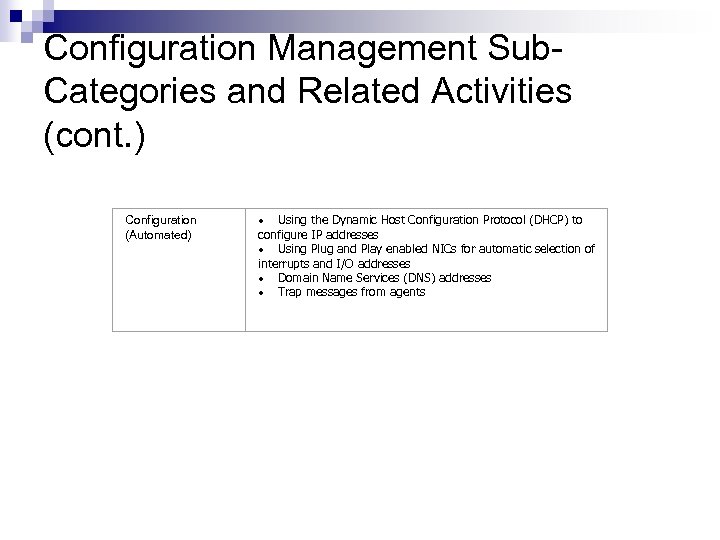 Configuration Management Sub. Categories and Related Activities (cont. ) Configuration (Automated) · Using the Dynamic Host Configuration Protocol (DHCP) to configure IP addresses · Using Plug and Play enabled NICs for automatic selection of interrupts and I/O addresses · Domain Name Services (DNS) addresses · Trap messages from agents
Configuration Management Sub. Categories and Related Activities (cont. ) Configuration (Automated) · Using the Dynamic Host Configuration Protocol (DHCP) to configure IP addresses · Using Plug and Play enabled NICs for automatic selection of interrupts and I/O addresses · Domain Name Services (DNS) addresses · Trap messages from agents
 Configuration Management Sub. Categories and Related Activities (cont. ) Inventory (Manual) · Maintaining records of cable runs and the types of cables used · Maintaining device configuration records · Creating network database containing for each device: q Device types q Software environment for each device q operating systems q utilities q drivers q applications q versions q configuration files (. ncf, . ini, . sys) q vendor contact information q IP address q Subnet address Inventory (Automated) · Auto-discovery of devices on the network using an NMS · Auto-determination of device configurations using an NMS · Creation of a network database · Auto-mapping of current devices to produce a network topological map · Accessing device statistics using an NMS and the Desktop Management Protocol
Configuration Management Sub. Categories and Related Activities (cont. ) Inventory (Manual) · Maintaining records of cable runs and the types of cables used · Maintaining device configuration records · Creating network database containing for each device: q Device types q Software environment for each device q operating systems q utilities q drivers q applications q versions q configuration files (. ncf, . ini, . sys) q vendor contact information q IP address q Subnet address Inventory (Automated) · Auto-discovery of devices on the network using an NMS · Auto-determination of device configurations using an NMS · Creation of a network database · Auto-mapping of current devices to produce a network topological map · Accessing device statistics using an NMS and the Desktop Management Protocol
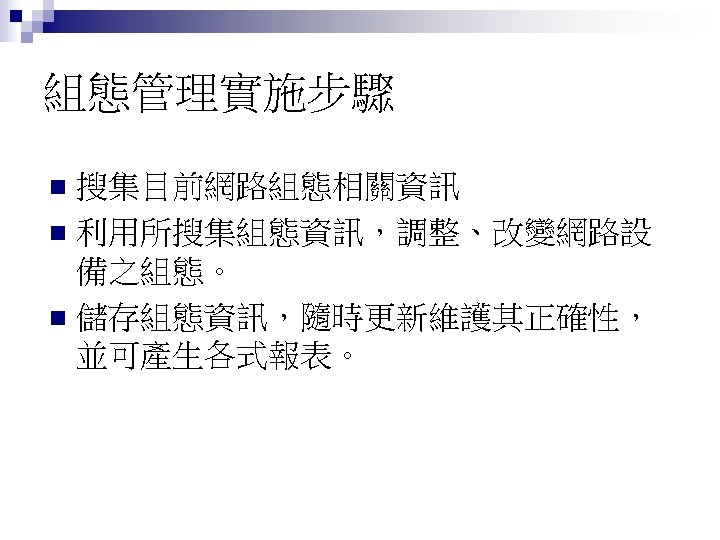 組態管理實施步驟 搜集目前網路組態相關資訊 n 利用所搜集組態資訊,調整、改變網路設 備之組態。 n 儲存組態資訊,隨時更新維護其正確性, 並可產生各式報表。 n
組態管理實施步驟 搜集目前網路組態相關資訊 n 利用所搜集組態資訊,調整、改變網路設 備之組態。 n 儲存組態資訊,隨時更新維護其正確性, 並可產生各式報表。 n
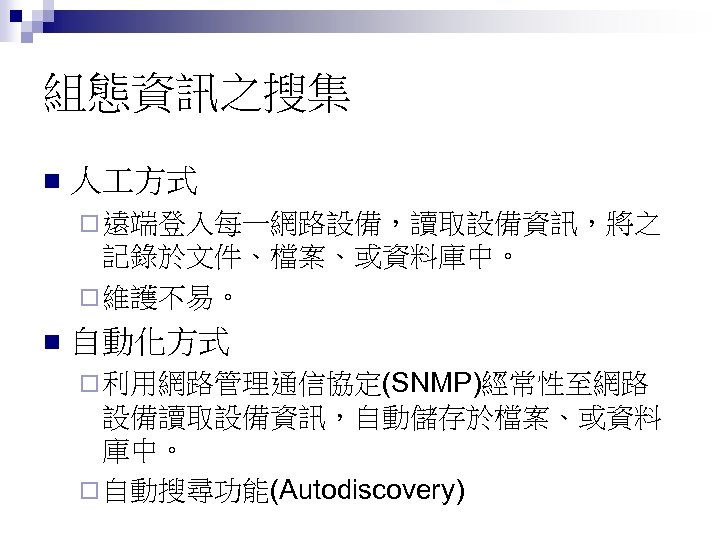 組態資訊之搜集 n 人 方式 ¨ 遠端登入每一網路設備,讀取設備資訊,將之 記錄於文件、檔案、或資料庫中。 ¨ 維護不易。 n 自動化方式 ¨ 利用網路管理通信協定(SNMP)經常性至網路 設備讀取設備資訊,自動儲存於檔案、或資料 庫中。 ¨ 自動搜尋功能(Autodiscovery)
組態資訊之搜集 n 人 方式 ¨ 遠端登入每一網路設備,讀取設備資訊,將之 記錄於文件、檔案、或資料庫中。 ¨ 維護不易。 n 自動化方式 ¨ 利用網路管理通信協定(SNMP)經常性至網路 設備讀取設備資訊,自動儲存於檔案、或資料 庫中。 ¨ 自動搜尋功能(Autodiscovery)
 Auto-discovery A method used by a network management system to dynamically find the devices attached to a data network. n 兩種常見方式 n ¨ 1. 利用Ping及網管通信協定 ¨ 2. 利用網管通信協定
Auto-discovery A method used by a network management system to dynamically find the devices attached to a data network. n 兩種常見方式 n ¨ 1. 利用Ping及網管通信協定 ¨ 2. 利用網管通信協定
 1. 利用Ping及網管通信協定 (1). Send out a query, such as ICMP Echo (ping) to every possible address on the network. (2). When a device answers the query, ask for detailed information using network management protocol (e. g. SNMP).
1. 利用Ping及網管通信協定 (1). Send out a query, such as ICMP Echo (ping) to every possible address on the network. (2). When a device answers the query, ask for detailed information using network management protocol (e. g. SNMP).
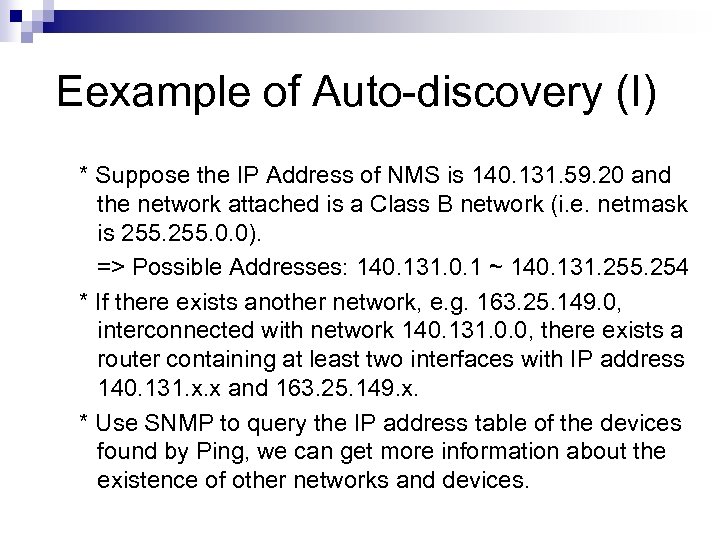 Eexample of Auto-discovery (I) * Suppose the IP Address of NMS is 140. 131. 59. 20 and the network attached is a Class B network (i. e. netmask is 255. 0. 0). => Possible Addresses: 140. 131. 0. 1 ~ 140. 131. 255. 254 * If there exists another network, e. g. 163. 25. 149. 0, interconnected with network 140. 131. 0. 0, there exists a router containing at least two interfaces with IP address 140. 131. x. x and 163. 25. 149. x. * Use SNMP to query the IP address table of the devices found by Ping, we can get more information about the existence of other networks and devices.
Eexample of Auto-discovery (I) * Suppose the IP Address of NMS is 140. 131. 59. 20 and the network attached is a Class B network (i. e. netmask is 255. 0. 0). => Possible Addresses: 140. 131. 0. 1 ~ 140. 131. 255. 254 * If there exists another network, e. g. 163. 25. 149. 0, interconnected with network 140. 131. 0. 0, there exists a router containing at least two interfaces with IP address 140. 131. x. x and 163. 25. 149. x. * Use SNMP to query the IP address table of the devices found by Ping, we can get more information about the existence of other networks and devices.
 2. 利用網管通信協定 (1). Find one device on the network and query it by NM protocol to discover all of the devices it has communicated with recently. (2). Repeatedly use NM protocol to query the devices found previously.
2. 利用網管通信協定 (1). Find one device on the network and query it by NM protocol to discover all of the devices it has communicated with recently. (2). Repeatedly use NM protocol to query the devices found previously.
 Eexample of Auto-discovery (II) * Suppose the IP Address of NMS is 140. 131. 59. 20 and its default gateway is 140. 131. 59. 254. => * Use SNMP to query 140. 131. 59. 20 itself or 140. 131. 59. 254. n ARP Cache, TCP/UDP Connection Table, IP Address Table, Routing Table. * Use SNMP to query the devices found in the previous query.
Eexample of Auto-discovery (II) * Suppose the IP Address of NMS is 140. 131. 59. 20 and its default gateway is 140. 131. 59. 254. => * Use SNMP to query 140. 131. 59. 20 itself or 140. 131. 59. 254. n ARP Cache, TCP/UDP Connection Table, IP Address Table, Routing Table. * Use SNMP to query the devices found in the previous query.
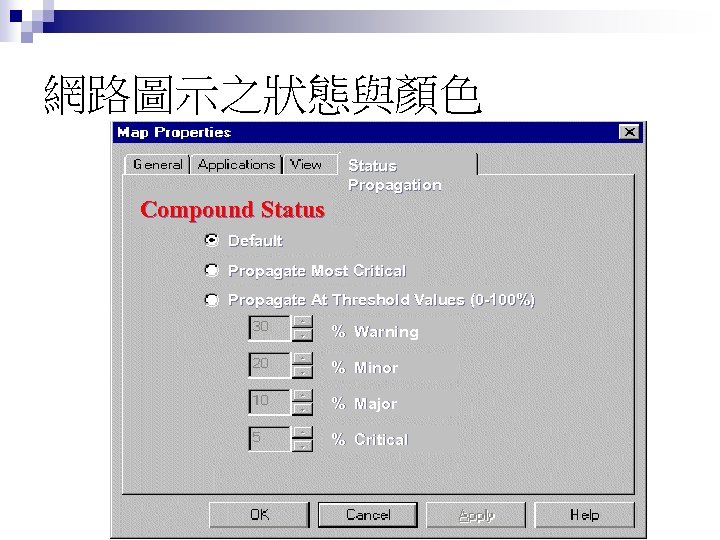 網路圖示之狀態與顏色 Status Propagation Compound Status Default Propagate Most Critical Propagate At Threshold Values (0 -100%) % Warning % Minor % Major % Critical
網路圖示之狀態與顏色 Status Propagation Compound Status Default Propagate Most Critical Propagate At Threshold Values (0 -100%) % Warning % Minor % Major % Critical
 組態資訊之調整、改變 Manual modification is not efficient. n Automatic modification should be recorded n NMS can verify the configuration change. n
組態資訊之調整、改變 Manual modification is not efficient. n Automatic modification should be recorded n NMS can verify the configuration change. n
 組態資訊之儲存 Stored in a central location n Consistency and Availability of configuration data is important. n CM data can be stored in ASCII Text Files or DBMSs. n
組態資訊之儲存 Stored in a central location n Consistency and Availability of configuration data is important. n CM data can be stored in ASCII Text Files or DBMSs. n
 網管系統組態管理功能 Provide for central storage of all network information. n Autodiscovery mechanism n Automapping facility n Automatic data acquisition n Allow user to manually additional configuration information n Search function n
網管系統組態管理功能 Provide for central storage of all network information. n Autodiscovery mechanism n Automapping facility n Automatic data acquisition n Allow user to manually additional configuration information n Search function n
 網管系統組態管理功能 (續) Automatically compare current and stored configuration data. n View running configuration graphically. n Make configuration change. n Centralized storage and easy retrieval of data. n Configuration Event/Alarm. n Graphical logical/physical view of devices n
網管系統組態管理功能 (續) Automatically compare current and stored configuration data. n View running configuration graphically. n Make configuration change. n Centralized storage and easy retrieval of data. n Configuration Event/Alarm. n Graphical logical/physical view of devices n
 Configuration Alarms
Configuration Alarms
 網管系統組態管理功能 (續) The use of DBMS n Evaluate device configurations n Allow complex query of data in DBMS. n Produce inventory reports. n Provide simple query interface for critical data. n
網管系統組態管理功能 (續) The use of DBMS n Evaluate device configurations n Allow complex query of data in DBMS. n Produce inventory reports. n Provide simple query interface for critical data. n
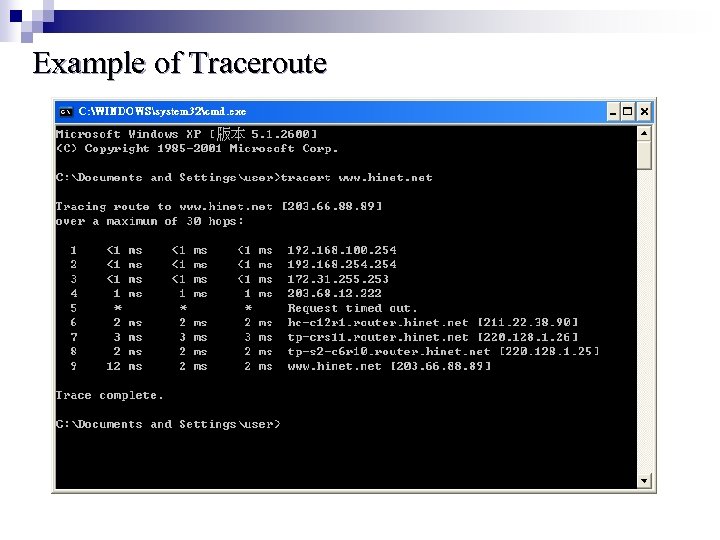 Example of Traceroute
Example of Traceroute
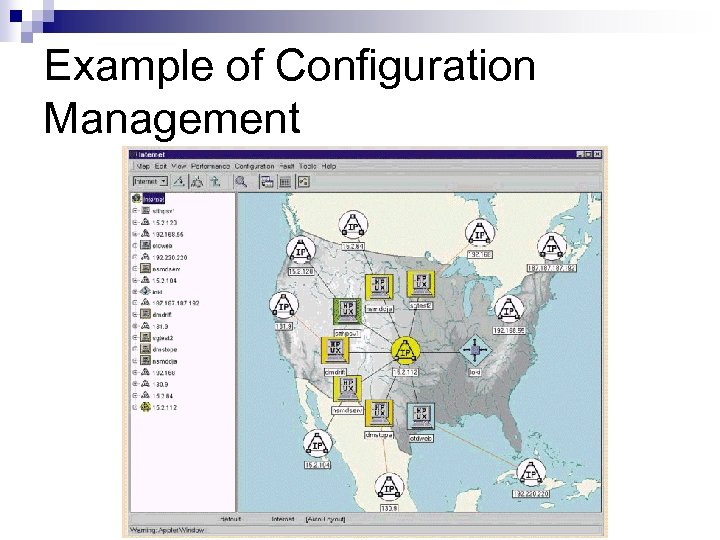 Example of Configuration Management
Example of Configuration Management
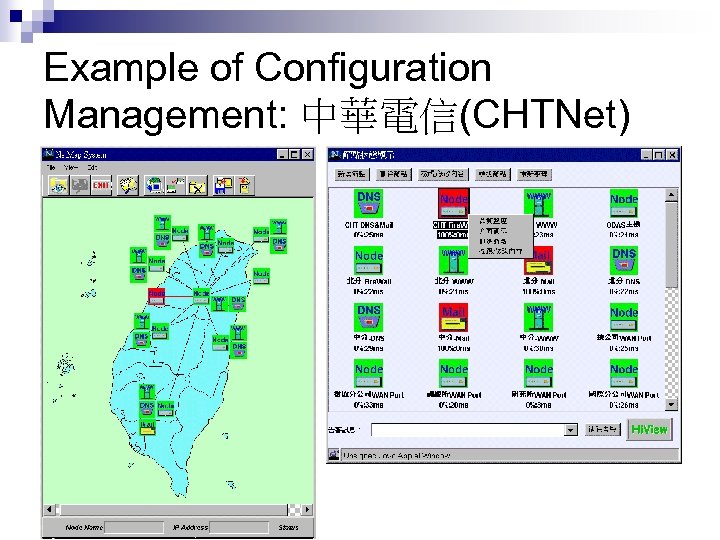 Example of Configuration Management: 中華電信(CHTNet)
Example of Configuration Management: 中華電信(CHTNet)
 Security Management (安全管理 ) n Security Management ¨ The process of controlling access to information on the networked system
Security Management (安全管理 ) n Security Management ¨ The process of controlling access to information on the networked system
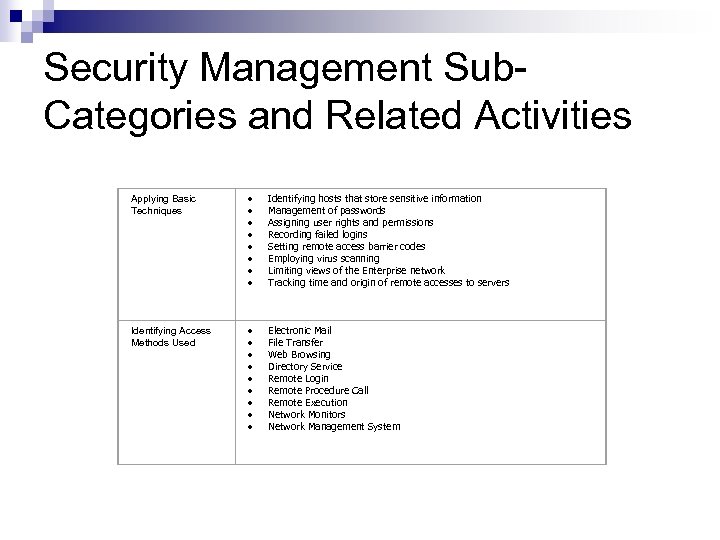 Security Management Sub. Categories and Related Activities Applying Basic Techniques · Identifying hosts that store sensitive information · Management of passwords · Assigning user rights and permissions · Recording failed logins · Setting remote access barrier codes · Employing virus scanning · Limiting views of the Enterprise network · Tracking time and origin of remote accesses to servers Identifying Access Methods Used · Electronic Mail · File Transfer · Web Browsing · Directory Service · Remote Login · Remote Procedure Call · Remote Execution · Network Monitors · Network Management System
Security Management Sub. Categories and Related Activities Applying Basic Techniques · Identifying hosts that store sensitive information · Management of passwords · Assigning user rights and permissions · Recording failed logins · Setting remote access barrier codes · Employing virus scanning · Limiting views of the Enterprise network · Tracking time and origin of remote accesses to servers Identifying Access Methods Used · Electronic Mail · File Transfer · Web Browsing · Directory Service · Remote Login · Remote Procedure Call · Remote Execution · Network Monitors · Network Management System
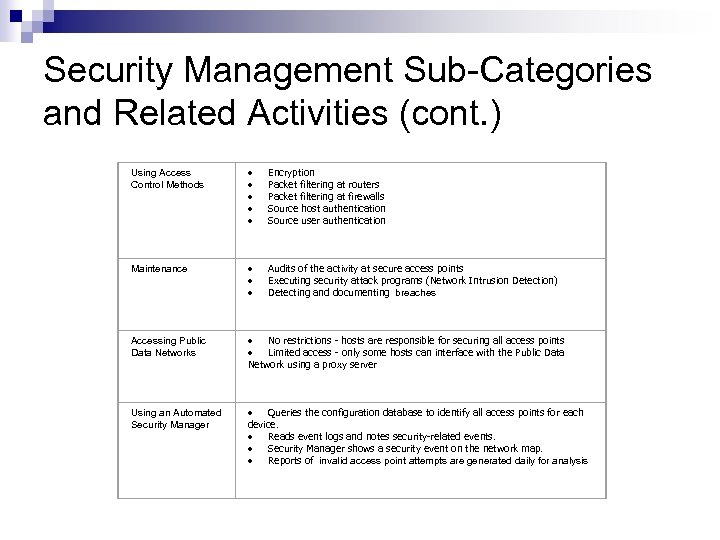 Security Management Sub-Categories and Related Activities (cont. ) Using Access Control Methods · Encryption · Packet filtering at routers · Packet filtering at firewalls · Source host authentication · Source user authentication Maintenance · Audits of the activity at secure access points · Executing security attack programs (Network Intrusion Detection) · Detecting and documenting breaches Accessing Public Data Networks · No restrictions - hosts are responsible for securing all access points · Limited access - only some hosts can interface with the Public Data Network using a proxy server Using an Automated Security Manager · Queries the configuration database to identify all access points for each device. · Reads event logs and notes security-related events. · Security Manager shows a security event on the network map. · Reports of invalid access point attempts are generated daily for analysis
Security Management Sub-Categories and Related Activities (cont. ) Using Access Control Methods · Encryption · Packet filtering at routers · Packet filtering at firewalls · Source host authentication · Source user authentication Maintenance · Audits of the activity at secure access points · Executing security attack programs (Network Intrusion Detection) · Detecting and documenting breaches Accessing Public Data Networks · No restrictions - hosts are responsible for securing all access points · Limited access - only some hosts can interface with the Public Data Network using a proxy server Using an Automated Security Manager · Queries the configuration database to identify all access points for each device. · Reads event logs and notes security-related events. · Security Manager shows a security event on the network map. · Reports of invalid access point attempts are generated daily for analysis
 Functions of Security Management The creation, deletion, and control of security services and mechanisms. n The distribution of security-relevant information. n The reporting of security-relevant events. n
Functions of Security Management The creation, deletion, and control of security services and mechanisms. n The distribution of security-relevant information. n The reporting of security-relevant events. n
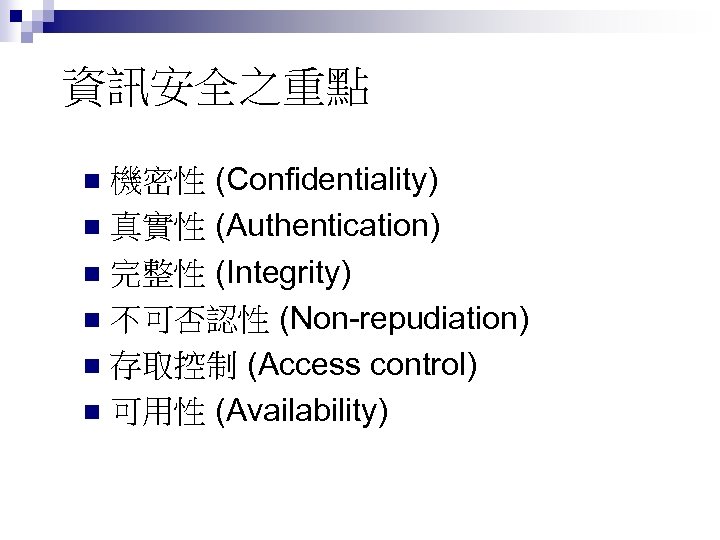 資訊安全之重點 機密性 (Confidentiality) n 真實性 (Authentication) n 完整性 (Integrity) n 不可否認性 (Non-repudiation) n 存取控制 (Access control) n 可用性 (Availability) n
資訊安全之重點 機密性 (Confidentiality) n 真實性 (Authentication) n 完整性 (Integrity) n 不可否認性 (Non-repudiation) n 存取控制 (Access control) n 可用性 (Availability) n
 安全管理實施步驟 1. Identifying the sensitive information to be protected 2. Finding the access points 3. Securing the access points 4. Maintaining the access points
安全管理實施步驟 1. Identifying the sensitive information to be protected 2. Finding the access points 3. Securing the access points 4. Maintaining the access points
 Access Point n A piece of network hardware or software that allows access to the data network. ¨ Software services ¨ Hardware components ¨ Network media
Access Point n A piece of network hardware or software that allows access to the data network. ¨ Software services ¨ Hardware components ¨ Network media
 Finding the Access Points Physical Wiring/Media n Network Services n ¨ Remote Login ¨ File Transfer ¨ E-mail ¨ Remote Execution ¨ Directory Service ¨… n NMS
Finding the Access Points Physical Wiring/Media n Network Services n ¨ Remote Login ¨ File Transfer ¨ E-mail ¨ Remote Execution ¨ Directory Service ¨… n NMS
 Securing the Access Points (1). Packet Filtering (2). Host Authentication (3). User Authentication (4). Key Authentication (5). Encryption
Securing the Access Points (1). Packet Filtering (2). Host Authentication (3). User Authentication (4). Key Authentication (5). Encryption
 (1). Packet Filtering n n n Packet filtering usually can be performed in bridges, switches, and routers. Packet filtering stops packets to or from unsecured hosts before they reach an access point. Issues ¨ Each network device to perform packet filtering must be configured. ¨ Packet filtering doesn't work if the unsecured host changes its address.
(1). Packet Filtering n n n Packet filtering usually can be performed in bridges, switches, and routers. Packet filtering stops packets to or from unsecured hosts before they reach an access point. Issues ¨ Each network device to perform packet filtering must be configured. ¨ Packet filtering doesn't work if the unsecured host changes its address.
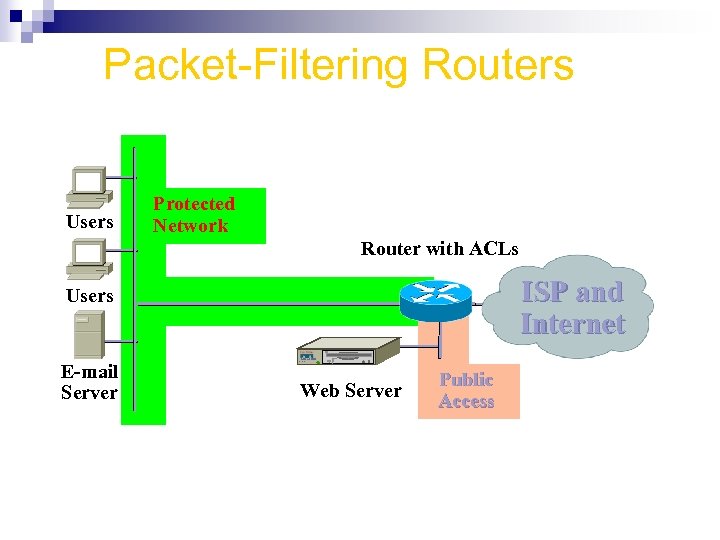 Packet-Filtering Routers Users Protected Network Router with ACLs ISP and Internet Micro Webserver E-mail Server Micro Webserver zip 100 Users Web Server Public Access
Packet-Filtering Routers Users Protected Network Router with ACLs ISP and Internet Micro Webserver E-mail Server Micro Webserver zip 100 Users Web Server Public Access
 (2). Host Authentication n Allow access to a service based on a source host identifier, e. g. network address. Service Remote Login File Transfer Directory … n Allow Host-B, Host-C, 140. 131. 59. 20 Host-A, Host-B, PC-bmw, Host-C, 140. 131. 62. 211, PC-benz … Issues ¨ ¨ A host can change its network address. Different users in the same host have the same authority.
(2). Host Authentication n Allow access to a service based on a source host identifier, e. g. network address. Service Remote Login File Transfer Directory … n Allow Host-B, Host-C, 140. 131. 59. 20 Host-A, Host-B, PC-bmw, Host-C, 140. 131. 62. 211, PC-benz … Issues ¨ ¨ A host can change its network address. Different users in the same host have the same authority.
 (3). User Authentication Enable service to identify each user before allowing that user access. n Password Mechanism n Generally, passwords are transferred on the network without any encryption. ¨ Use encrypted passwords. ¨ Users tend to make passwords easy to remember. ¨ If the passwords are not common words, users will write them down. ¨ n Host Authentication + User Authentication
(3). User Authentication Enable service to identify each user before allowing that user access. n Password Mechanism n Generally, passwords are transferred on the network without any encryption. ¨ Use encrypted passwords. ¨ Users tend to make passwords easy to remember. ¨ If the passwords are not common words, users will write them down. ¨ n Host Authentication + User Authentication
 (4). Key Authentication n Key ¨ A unique piece of information that authenticates the data in a transaction. n Key Authentication ¨ The destination host requires the source host of a transaction to present a key for the transaction. n Key Server ¨ A server that validates requests for transactions between hosts by giving out keys.
(4). Key Authentication n Key ¨ A unique piece of information that authenticates the data in a transaction. n Key Authentication ¨ The destination host requires the source host of a transaction to present a key for the transaction. n Key Server ¨ A server that validates requests for transactions between hosts by giving out keys.
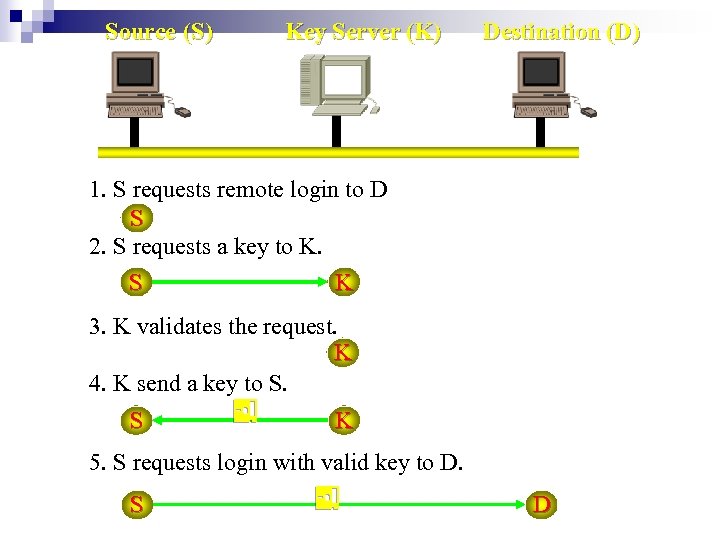 Source (S) Key Server (K) Destination (D) 1. S requests remote login to D S 2. S requests a key to K. S K S 3. K validates the request. K 4. K send a key to S. K 5. S requests login with valid key to D. S D
Source (S) Key Server (K) Destination (D) 1. S requests remote login to D S 2. S requests a key to K. S K S 3. K validates the request. K 4. K send a key to S. K 5. S requests login with valid key to D. S D
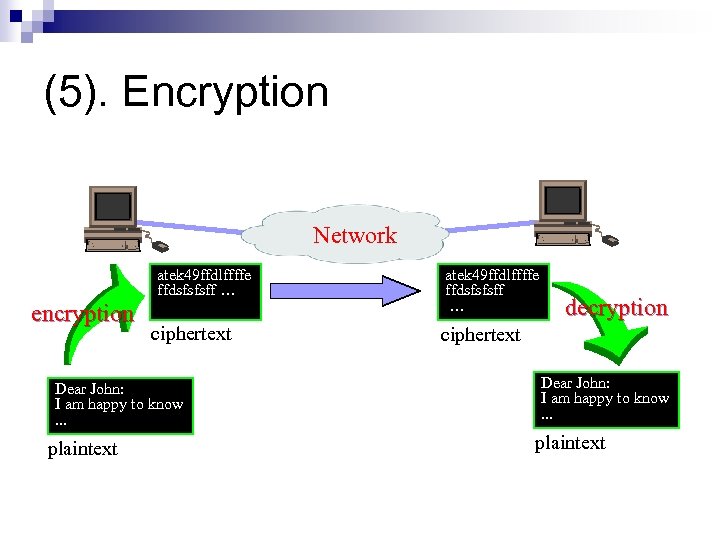 (5). Encryption Network atek 49 ffdlffffe ffdsfsfsff … encryption ciphertext Dear John: I am happy to know. . . plaintext atek 49 ffdlffffe ffdsfsfsff … decryption ciphertext Dear John: I am happy to know. . . plaintext
(5). Encryption Network atek 49 ffdlffffe ffdsfsfsff … encryption ciphertext Dear John: I am happy to know. . . plaintext atek 49 ffdlffffe ffdsfsfsff … decryption ciphertext Dear John: I am happy to know. . . plaintext
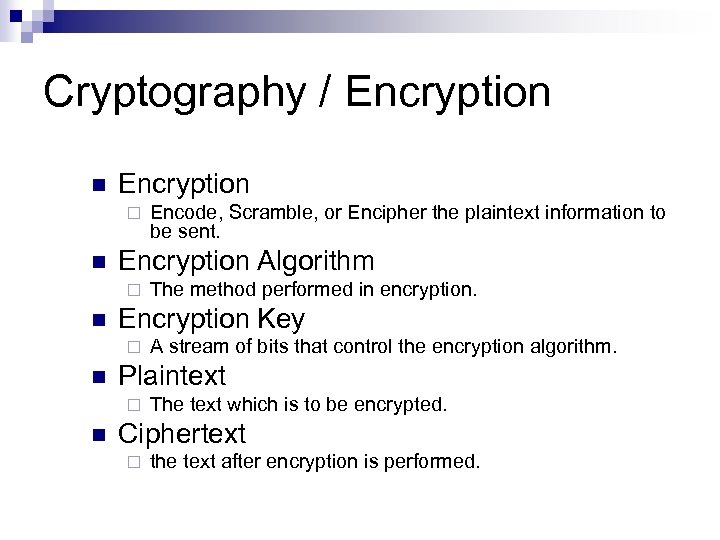 Cryptography / Encryption n Encryption ¨ n Encryption Algorithm ¨ n A stream of bits that control the encryption algorithm. Plaintext ¨ n The method performed in encryption. Encryption Key ¨ n Encode, Scramble, or Encipher the plaintext information to be sent. The text which is to be encrypted. Ciphertext ¨ the text after encryption is performed.
Cryptography / Encryption n Encryption ¨ n Encryption Algorithm ¨ n A stream of bits that control the encryption algorithm. Plaintext ¨ n The method performed in encryption. Encryption Key ¨ n Encode, Scramble, or Encipher the plaintext information to be sent. The text which is to be encrypted. Ciphertext ¨ the text after encryption is performed.
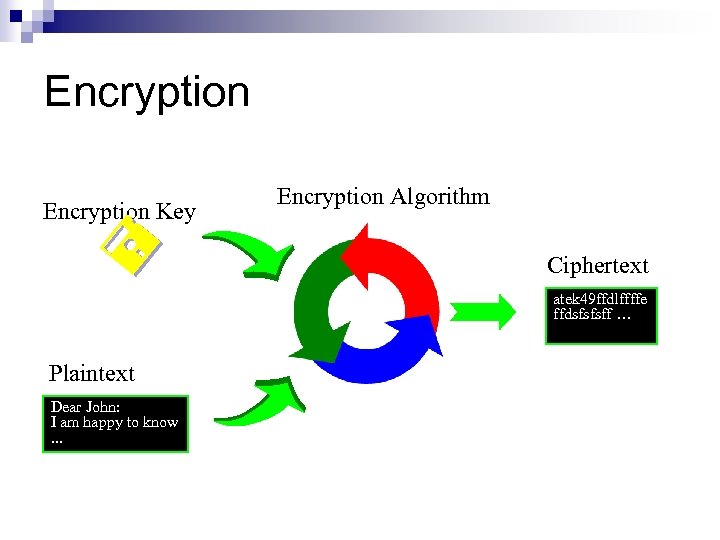 Encryption Key Encryption Algorithm Ciphertext atek 49 ffdlffffe ffdsfsfsff … Plaintext Dear John: I am happy to know. . .
Encryption Key Encryption Algorithm Ciphertext atek 49 ffdlffffe ffdsfsfsff … Plaintext Dear John: I am happy to know. . .
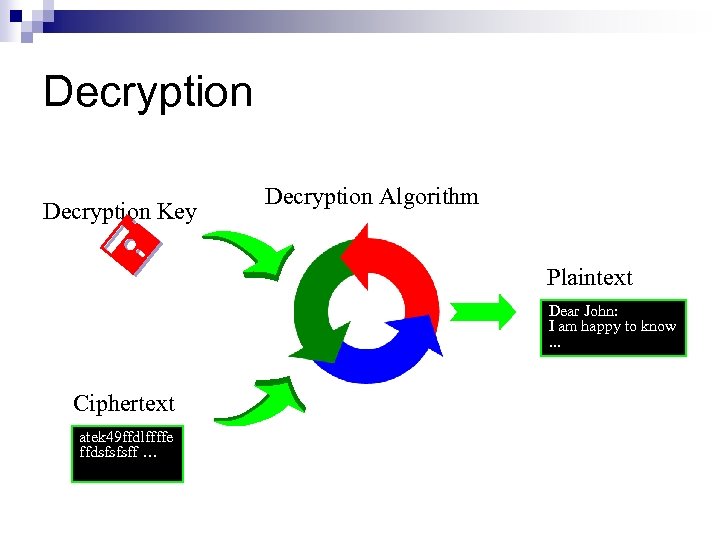 Decryption Key Decryption Algorithm Plaintext Dear John: I am happy to know. . . Ciphertext atek 49 ffdlffffe ffdsfsfsff …
Decryption Key Decryption Algorithm Plaintext Dear John: I am happy to know. . . Ciphertext atek 49 ffdlffffe ffdsfsfsff …
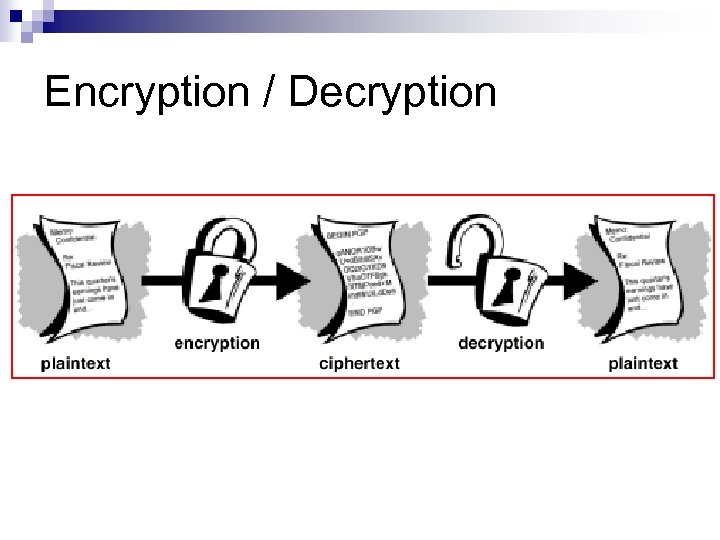 Encryption / Decryption
Encryption / Decryption
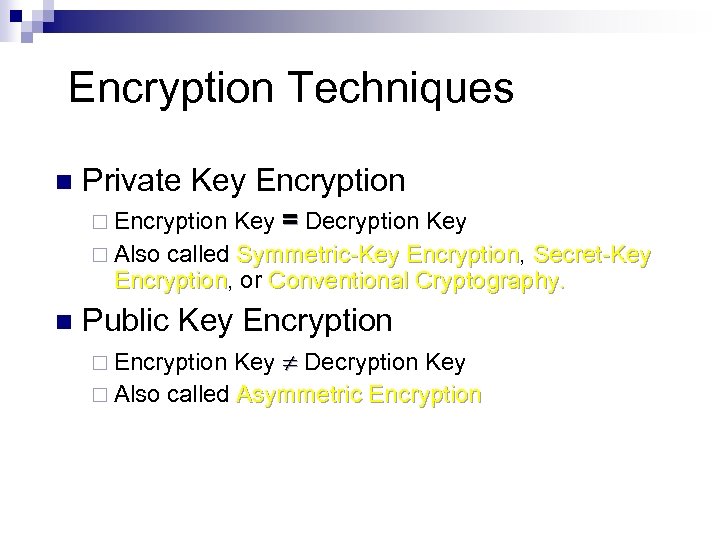 Encryption Techniques n Private Key Encryption ¨ Encryption Key = Decryption Key ¨ Also called Symmetric-Key Encryption, Secret-Key Symmetric-Key Encryption, or Conventional Cryptography. Encryption Conventional Cryptography. n Public Key Encryption ¨ Encryption Key Decryption Key ¨ Also called Asymmetric Encryption
Encryption Techniques n Private Key Encryption ¨ Encryption Key = Decryption Key ¨ Also called Symmetric-Key Encryption, Secret-Key Symmetric-Key Encryption, or Conventional Cryptography. Encryption Conventional Cryptography. n Public Key Encryption ¨ Encryption Key Decryption Key ¨ Also called Asymmetric Encryption
 Private Key Encryption: - DES (Data Encryption Standard) n n n Adopted by U. S. Federal Government. Both the sender and receiver must know the same secret key code to encrypt and decrypt messages with DES Operates on 64 -bit blocks with a 56 -bit key DES is a fast encryption scheme and works well for bulk encryption. Issues: ¨ How to deliver the key to the sender safely?
Private Key Encryption: - DES (Data Encryption Standard) n n n Adopted by U. S. Federal Government. Both the sender and receiver must know the same secret key code to encrypt and decrypt messages with DES Operates on 64 -bit blocks with a 56 -bit key DES is a fast encryption scheme and works well for bulk encryption. Issues: ¨ How to deliver the key to the sender safely?
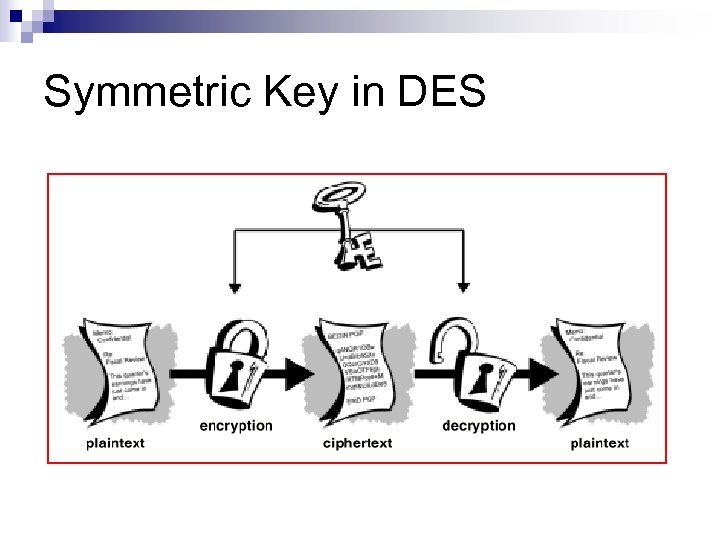 Symmetric Key in DES
Symmetric Key in DES
 Other Symmetric Key Encryption Techniques n 3 DES ¨ Triple DES RC 2, RC 4 n IDEA n ¨ International Data Encryption Algorithm
Other Symmetric Key Encryption Techniques n 3 DES ¨ Triple DES RC 2, RC 4 n IDEA n ¨ International Data Encryption Algorithm
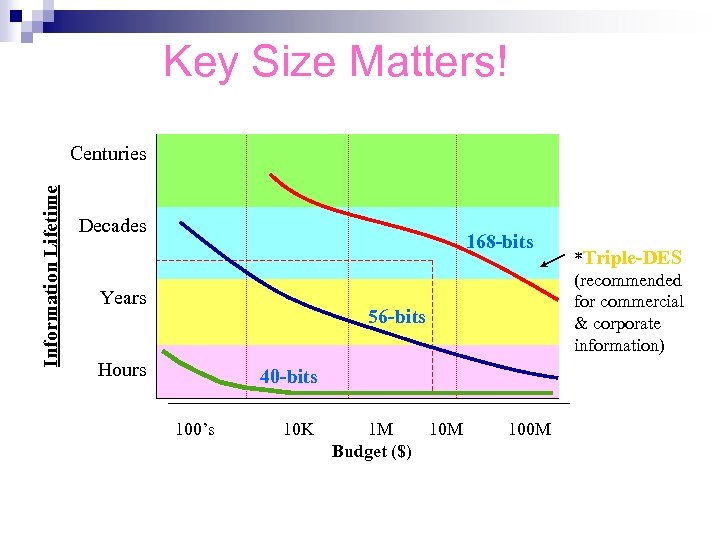 Key Size Matters! Information Lifetime Centuries Decades 168 -bits Years Hours 56 -bits 40 -bits 100’s 10 K 1 M 10 M 100 M Budget ($) *Triple-DES (recommended for commercial & corporate information)
Key Size Matters! Information Lifetime Centuries Decades 168 -bits Years Hours 56 -bits 40 -bits 100’s 10 K 1 M 10 M 100 M Budget ($) *Triple-DES (recommended for commercial & corporate information)
 Public Key Encryption: - RSA n n The public key is disseminated as widely as possible. The secrete key is only known by the receiver. Named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman RSA is well established as a de facto standard RSA is fine for encrypting small messages
Public Key Encryption: - RSA n n The public key is disseminated as widely as possible. The secrete key is only known by the receiver. Named after its inventors Ron Rivest, Adi Shamir, and Leonard Adleman RSA is well established as a de facto standard RSA is fine for encrypting small messages
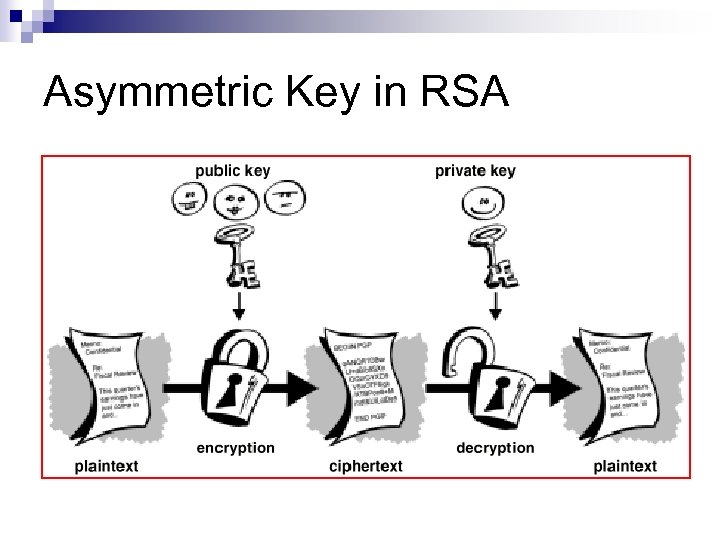 Asymmetric Key in RSA
Asymmetric Key in RSA
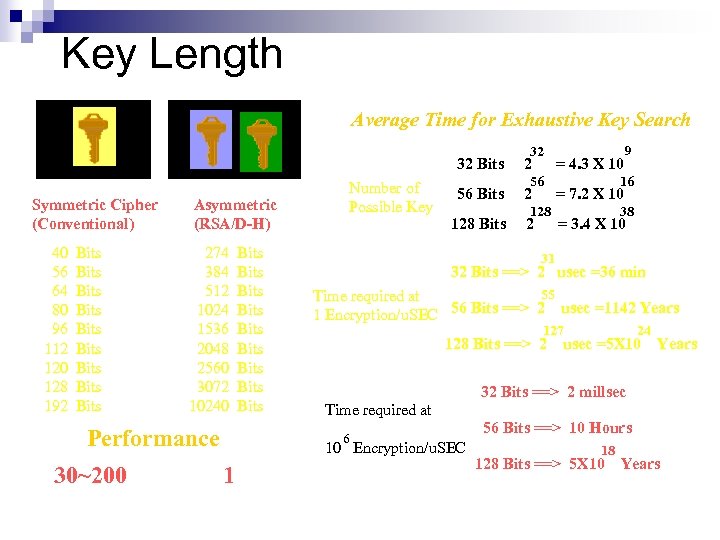 Key Length Average Time for Exhaustive Key Search 32 32 Bits Symmetric Cipher (Conventional) Asymmetric (RSA/D-H) 40 Bits 274 Bits 56 Bits 384 Bits 64 Bits 512 Bits 80 Bits 1024 Bits 96 Bits 1536 Bits 112 Bits 2048 Bits 120 Bits 2560 Bits 128 Bits 3072 Bits 192 Bits 10240 Bits Performance 30~200 Number of Possible Key 2 56 Bits 2 128 16 = 7. 2 X 10 38 = 3. 4 X 10 31 32 Bits ==> 2 usec =36 min 55 Time required at 1 Encryption/u. SEC 56 Bits ==> 2 usec =1142 Years 127 128 Bits ==> 2 24 usec =5 X 10 Years 32 Bits ==> 2 millsec Time required at 6 10 Encryption/u. SEC 1 56 = 4. 3 X 10 9 56 Bits ==> 10 Hours 18 128 Bits ==> 5 X 10 Years
Key Length Average Time for Exhaustive Key Search 32 32 Bits Symmetric Cipher (Conventional) Asymmetric (RSA/D-H) 40 Bits 274 Bits 56 Bits 384 Bits 64 Bits 512 Bits 80 Bits 1024 Bits 96 Bits 1536 Bits 112 Bits 2048 Bits 120 Bits 2560 Bits 128 Bits 3072 Bits 192 Bits 10240 Bits Performance 30~200 Number of Possible Key 2 56 Bits 2 128 16 = 7. 2 X 10 38 = 3. 4 X 10 31 32 Bits ==> 2 usec =36 min 55 Time required at 1 Encryption/u. SEC 56 Bits ==> 2 usec =1142 Years 127 128 Bits ==> 2 24 usec =5 X 10 Years 32 Bits ==> 2 millsec Time required at 6 10 Encryption/u. SEC 1 56 = 4. 3 X 10 9 56 Bits ==> 10 Hours 18 128 Bits ==> 5 X 10 Years
 Hybrid Encryption Technology: PGP (Pretty Good Privacy) n Hybrid Encryption Technique ¨ ¨ ¨ First compresses the plaintext. Then creates a session key, which is a one-time-only secret key. Using the session key, apply a fast conventional encryption algorithm to encrypt the plaintext. The session key is then encrypted to the recipient’s public key. This public key-encrypted session key is transmitted along with the ciphertext to the recipient.
Hybrid Encryption Technology: PGP (Pretty Good Privacy) n Hybrid Encryption Technique ¨ ¨ ¨ First compresses the plaintext. Then creates a session key, which is a one-time-only secret key. Using the session key, apply a fast conventional encryption algorithm to encrypt the plaintext. The session key is then encrypted to the recipient’s public key. This public key-encrypted session key is transmitted along with the ciphertext to the recipient.
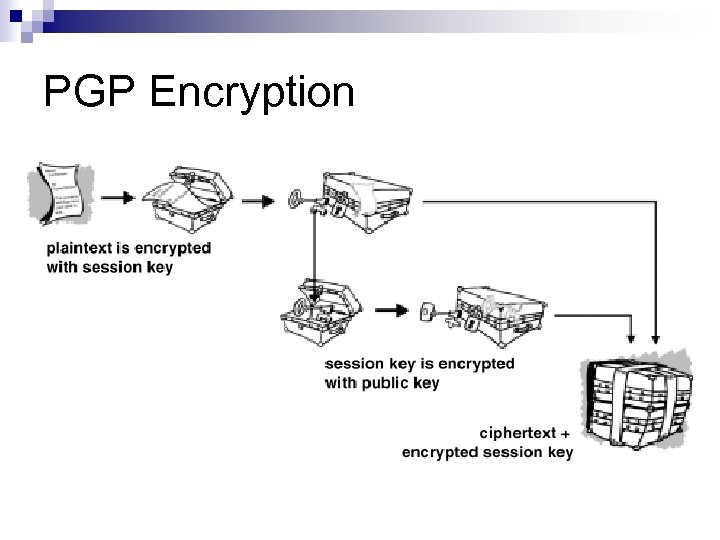 PGP Encryption
PGP Encryption
 PGP Decryption The recipient uses its private key to recover the temporary session key n Use the session key to decrypt the conventionally-encrypted ciphertext. n
PGP Decryption The recipient uses its private key to recover the temporary session key n Use the session key to decrypt the conventionally-encrypted ciphertext. n
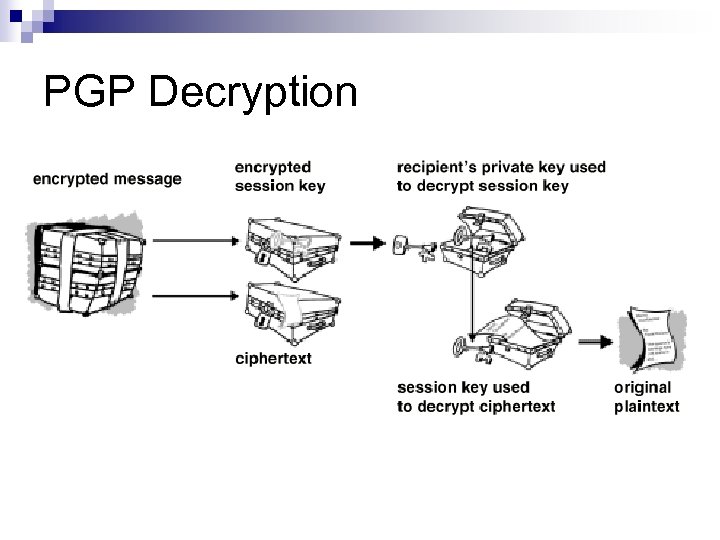 PGP Decryption
PGP Decryption
 Digital Signatures n n Digital signatures enable the recipient of information to verify the authenticity of the information’s origin, and also verify that the information is intact. Public key digital signatures provide authentication ¨ data integrity ¨ non-repudiation ¨ n Technique: public key cryptography
Digital Signatures n n Digital signatures enable the recipient of information to verify the authenticity of the information’s origin, and also verify that the information is intact. Public key digital signatures provide authentication ¨ data integrity ¨ non-repudiation ¨ n Technique: public key cryptography
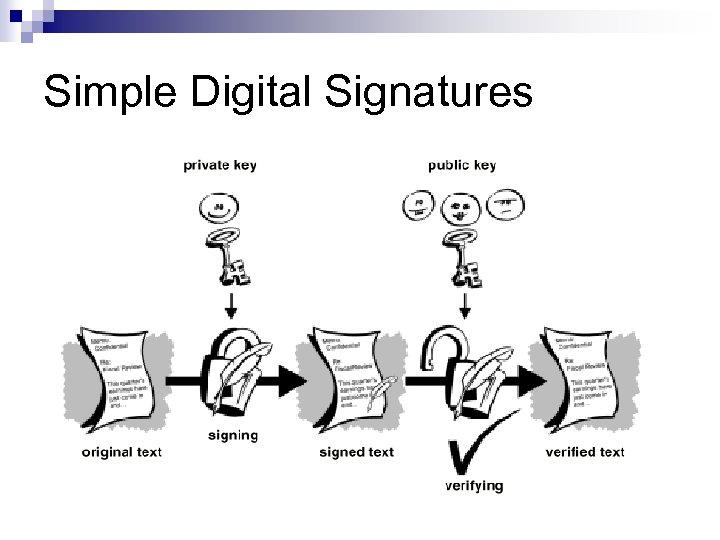 Simple Digital Signatures
Simple Digital Signatures
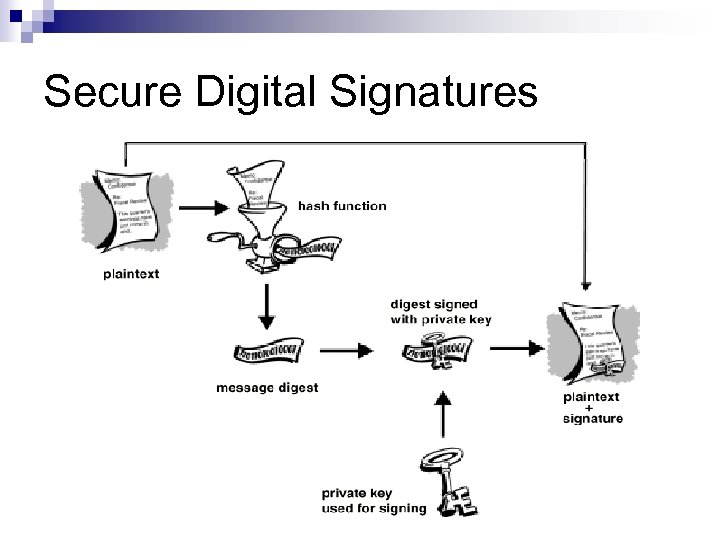 Secure Digital Signatures
Secure Digital Signatures
 Maintaining the Secure Access Points Locate potential and actual security breaches. n Audit Trail n Security Test Programs n
Maintaining the Secure Access Points Locate potential and actual security breaches. n Audit Trail n Security Test Programs n
 Attaching to a Public Network No Access n Full Access n ¨ All individual computers should have security management. n Limited Access ¨ Use a firewall to enforce security between firewall private and public networks.
Attaching to a Public Network No Access n Full Access n ¨ All individual computers should have security management. n Limited Access ¨ Use a firewall to enforce security between firewall private and public networks.
 防火牆 (Firewall) Firewall為一組軟硬體系統,用來控制內部 與外部網路間之通訊。 n Firewall建置方式 n ¨ Packet Filtering Firewall ¨ Dual-Homed Host Firewall ¨ Screened Subnet Firewall http: //www. movies. acmecity. com/silent/6/doc/fwppt. zip
防火牆 (Firewall) Firewall為一組軟硬體系統,用來控制內部 與外部網路間之通訊。 n Firewall建置方式 n ¨ Packet Filtering Firewall ¨ Dual-Homed Host Firewall ¨ Screened Subnet Firewall http: //www. movies. acmecity. com/silent/6/doc/fwppt. zip
 VPN (Virtual Private Network) n VPN: 虛擬私人網路 ¨ 藉由虛擬的方式,在公眾數據網路上建立一 個能夠秘密通訊的私人網路。 n VPN所使用之公眾數據網路 n n X. 25 Frame Relay ATM Internet
VPN (Virtual Private Network) n VPN: 虛擬私人網路 ¨ 藉由虛擬的方式,在公眾數據網路上建立一 個能夠秘密通訊的私人網路。 n VPN所使用之公眾數據網路 n n X. 25 Frame Relay ATM Internet
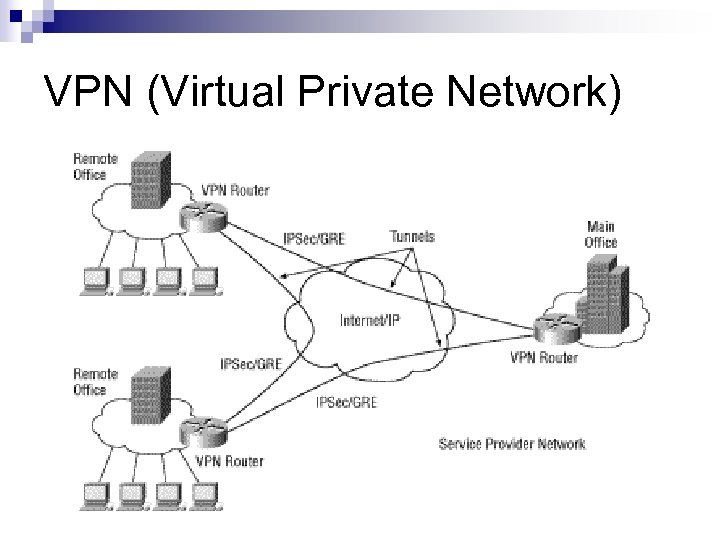 VPN (Virtual Private Network)
VPN (Virtual Private Network)
 VPN技術 n 穿隧技術 (Tunneling) ¨ ¨ ¨ n 加解密技術 (Encryption/Decryption) ¨ n Private/Public/Hybrid Key Encryption 密鑰管理 (Key Management) ¨ ¨ n IPSec (IP Security) PPTP (Point-to-Point Tunneling Protocol) L 2 TP (Layer 2 Tunneling Protocol) SKIP (Simple Key Management for IP) IKE (ISAKMP/Oakley) 使用者與設備身份認證技術 (Authentication) ¨ ¨ Username/Password + Token Number X. 509 Certificate by Certificate Authority (CA)
VPN技術 n 穿隧技術 (Tunneling) ¨ ¨ ¨ n 加解密技術 (Encryption/Decryption) ¨ n Private/Public/Hybrid Key Encryption 密鑰管理 (Key Management) ¨ ¨ n IPSec (IP Security) PPTP (Point-to-Point Tunneling Protocol) L 2 TP (Layer 2 Tunneling Protocol) SKIP (Simple Key Management for IP) IKE (ISAKMP/Oakley) 使用者與設備身份認證技術 (Authentication) ¨ ¨ Username/Password + Token Number X. 509 Certificate by Certificate Authority (CA)
 Accounting Management (計量 管理 ) n Accounting Management ¨ Tracking each individual and group user's utilization of network resources to better ensure that users have sufficient resources ¨ Enable charges to be established for the use of network resources, and the costs to be identified for the use of those network resources
Accounting Management (計量 管理 ) n Accounting Management ¨ Tracking each individual and group user's utilization of network resources to better ensure that users have sufficient resources ¨ Enable charges to be established for the use of network resources, and the costs to be identified for the use of those network resources
 Accounting Management Sub. Categories and Related Activities Gather Network Device Utilization Data · Measure usage of resources by cost center · Set quotas to enable fair use of resources · Site metering to track adherence to software licensing Bill Users of Network Resources · Set charges based on usage. · Measure one of the following q Number of transactions q Number of packets q Number of bytes · Set charges on direction of information flow Use and Accounting Management Tools · Query usage database to measure statistics versus quotas · Define network billing domains · Implement automatic billing based on usage by users in the domain · Enable billing predictions · Enable user selection of billing domains on the network map Reporting · Create historical billings trends · Automatic distribution of billing to Cost Centers · Project future billings by cost center
Accounting Management Sub. Categories and Related Activities Gather Network Device Utilization Data · Measure usage of resources by cost center · Set quotas to enable fair use of resources · Site metering to track adherence to software licensing Bill Users of Network Resources · Set charges based on usage. · Measure one of the following q Number of transactions q Number of packets q Number of bytes · Set charges on direction of information flow Use and Accounting Management Tools · Query usage database to measure statistics versus quotas · Define network billing domains · Implement automatic billing based on usage by users in the domain · Enable billing predictions · Enable user selection of billing domains on the network map Reporting · Create historical billings trends · Automatic distribution of billing to Cost Centers · Project future billings by cost center
 AM名詞說明 n Metrics ¨ Measurement of network resources used. n Quotas ¨ The amount of a network's resources allowed for a user or group. n Billing ¨ The process of charging users for the use of the data network and its associated services.
AM名詞說明 n Metrics ¨ Measurement of network resources used. n Quotas ¨ The amount of a network's resources allowed for a user or group. n Billing ¨ The process of charging users for the use of the data network and its associated services.
 計費方式 n n One-Time Installation Fee and Monthly Fees Fee Based on Amount of Network Resource Consumed ¨ Total numbers of transactions ¨ Total packets ¨ Total bytes sent ¨ Total bytes received n } 哪一種方式 較合理? Fee Based on Amount of Time (For Dial-Up Serial Links)
計費方式 n n One-Time Installation Fee and Monthly Fees Fee Based on Amount of Network Resource Consumed ¨ Total numbers of transactions ¨ Total packets ¨ Total bytes sent ¨ Total bytes received n } 哪一種方式 較合理? Fee Based on Amount of Time (For Dial-Up Serial Links)
 網管系統計量管理功能 n Monitor for any metrics that exceeds a quota. n Store metric data into the database of NMS. n Report the metric data that exceeds a quota. n Use database's "trigger" ability to automatically generate reports
網管系統計量管理功能 n Monitor for any metrics that exceeds a quota. n Store metric data into the database of NMS. n Report the metric data that exceeds a quota. n Use database's "trigger" ability to automatically generate reports
 網管系統計量管理功能 (續) Perform network billing. n Determine where to poll for billing information. n Forecast the need of network resources n To establish reasonable metrics and quotas To predict network billing cost for users n Generate accounting reports
網管系統計量管理功能 (續) Perform network billing. n Determine where to poll for billing information. n Forecast the need of network resources n To establish reasonable metrics and quotas To predict network billing cost for users n Generate accounting reports
 Billing Process Example 1. Get network topology from DBMS 2. Get region user selected on network map 3. Determine devices in region 4. Find devices to query (with the aids of user's input). 5. Get billing information 6. Get pricing information 7. Get polling rate 8. Start performing queries and calculations
Billing Process Example 1. Get network topology from DBMS 2. Get region user selected on network map 3. Determine devices in region 4. Find devices to query (with the aids of user's input). 5. Get billing information 6. Get pricing information 7. Get polling rate 8. Start performing queries and calculations
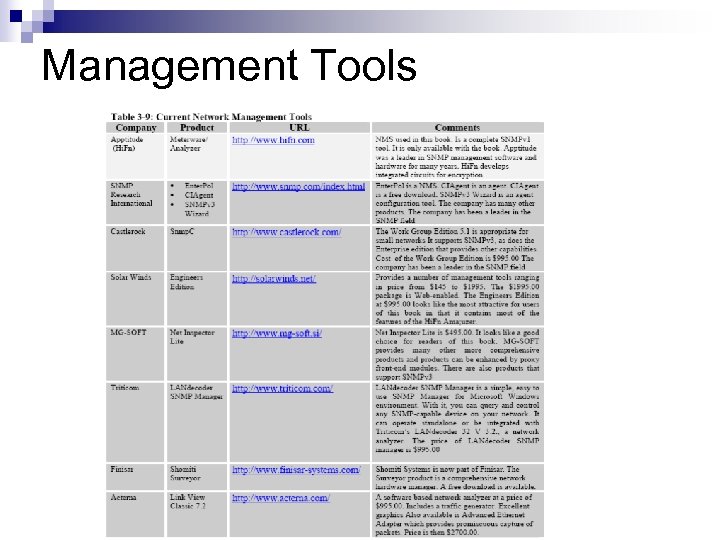 Management Tools
Management Tools
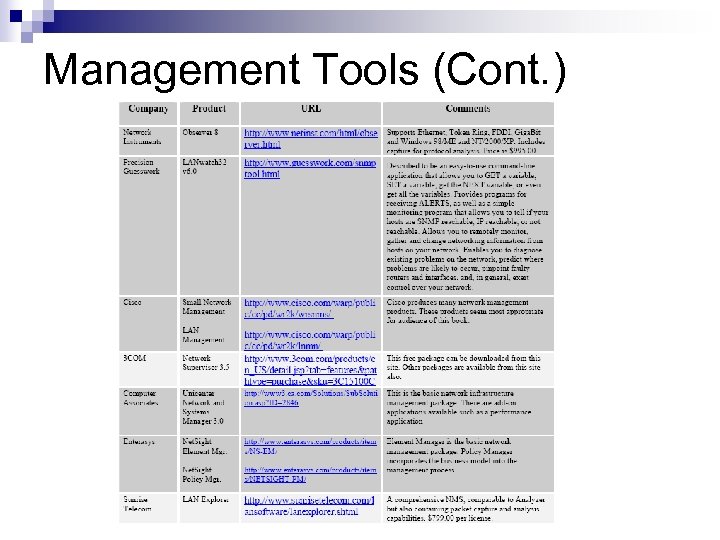 Management Tools (Cont. )
Management Tools (Cont. )
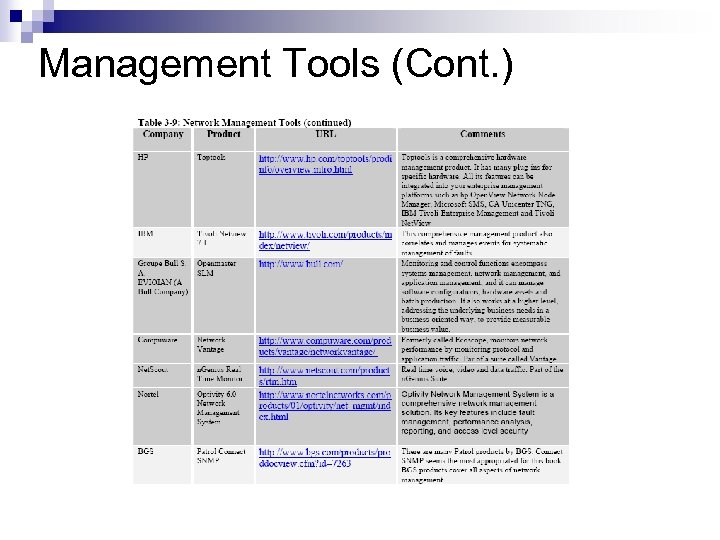 Management Tools (Cont. )
Management Tools (Cont. )
 Network Management Configurations n Centralized configuration ¨ Management is centralized to the network management station on the backbone network n Distributed configuration ¨ The LANs are managed by a local NMS while an NMS host connects to the backbone network
Network Management Configurations n Centralized configuration ¨ Management is centralized to the network management station on the backbone network n Distributed configuration ¨ The LANs are managed by a local NMS while an NMS host connects to the backbone network
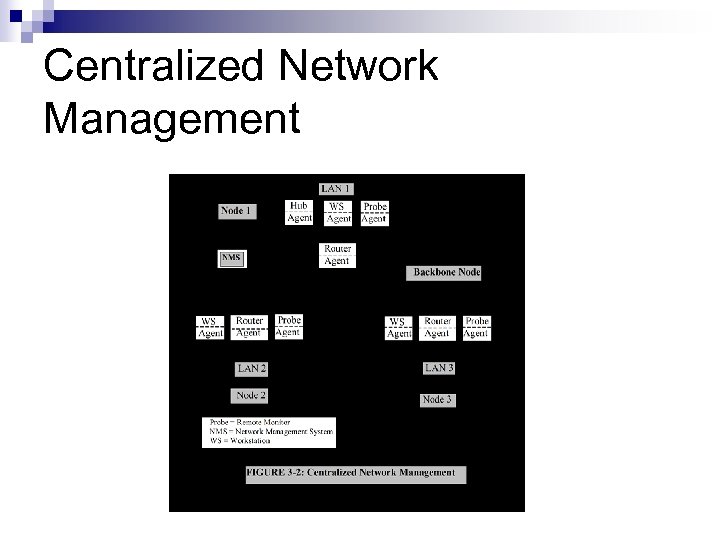 Centralized Network Management
Centralized Network Management
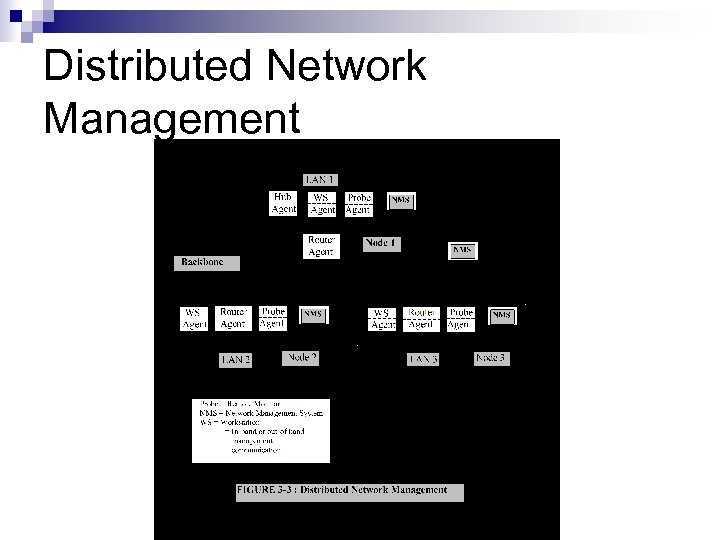 Distributed Network Management
Distributed Network Management
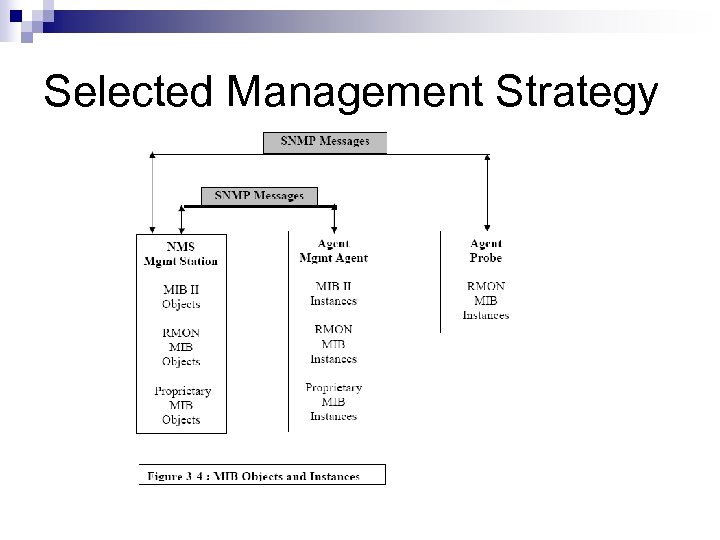 Selected Management Strategy
Selected Management Strategy


