9d1f0a06acdb5b7191dd738fdd0d0419.ppt
- Количество слайдов: 34

Network Access Control for Mobile Ad Hoc Network Pan Wang North Carolina State University

Outline • • Background Problem statement Related work Proposed scheme – Key Synchronization – Packet Retransmission • Analysis, simulation and field test • Summary 2
Background • Mobile Ad Hoc Network (MANET) – A MANET consists of mobile platforms (e. g. , a router with multiple hosts and wireless communications devices), which are free to move about arbitrarily. -- IETF RFC 2501 – Characteristics of MANET • • No pre-determined infrastructure Ease of deployment Dynamic topologies (e. g. , mobility, network partition ) Constrained resources (e. g. , bandwidth, energy ) 3

Background (Cont) • Network access control – Not media access control – Who has the right to access the network • Physical* • Technical * • Administrative * – Firewalls • Conventional network • Using network topology and service information * H. F. Tipton, Handbook of information security management 4
Problem Statement • An attacker may inject “bogus” packets to consume the network resources, or insert itself into critical routes • No mature access control scheme for MANET – more complicated due to open media and dynamic topology 5
Related Work • DHCP Access Control Gateway • Kerberos • Distributed firewall • Pebblenets • Distributed access control scheme for consumer operated MANET • LHAP 6
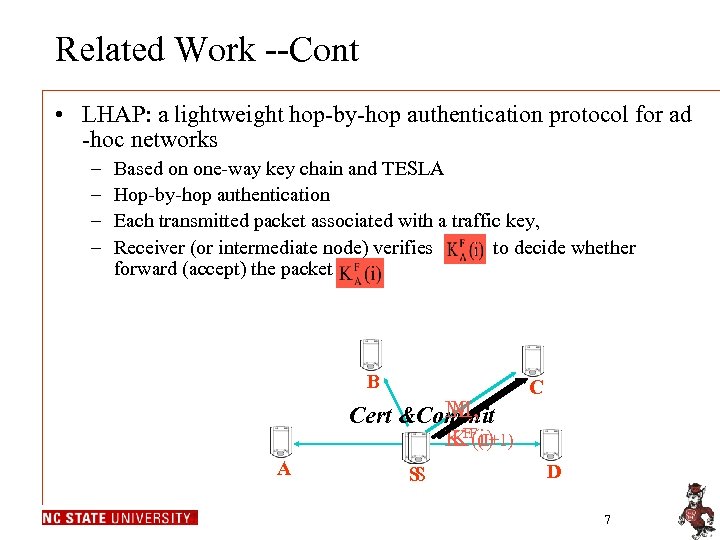
Related Work --Cont • LHAP: a lightweight hop-by-hop authentication protocol for ad -hoc networks – – Based on one-way key chain and TESLA Hop-by-hop authentication Each transmitted packet associated with a traffic key, Receiver (or intermediate node) verifies to decide whether forward (accept) the packet B M, M, Cert &Commit KFF(I+1) K (i) A S S C D 7
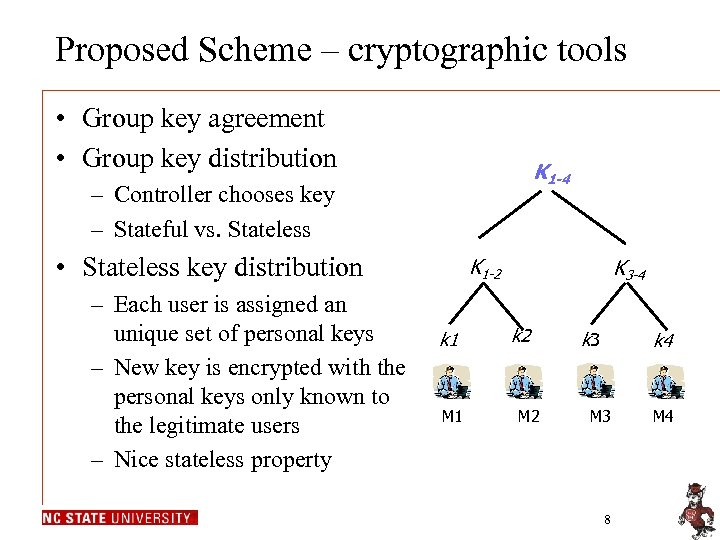
Proposed Scheme – cryptographic tools • Group key agreement • Group key distribution K 1 -4 – Controller chooses key – Stateful vs. Stateless • Stateless key distribution – Each user is assigned an unique set of personal keys – New key is encrypted with the personal keys only known to the legitimate users – Nice stateless property K 1 -2 k 1 M 1 K 3 -4 k 2 M 2 k 3 k 4 M 3 8 M 4
Proposed Scheme – underlying models • Network model – All nodes come from one domain – A node’s access to the network is controlled by a domain manager (i. e. , key manager) – Each node has a unique ID and a set of personal secret keys • Attack model – Attackers inject packets to deplete the resources of node relaying the packets 9

• pan wang: Proposed Scheme - outline • Basic idea – Cryptography-oriented (using group key) – Authenticate all the packets with a networkwide access control (group session) key. – Any “bogus” packet that has incorrect authentication information will be filtered out immediately. – As a result, illegitimate nodes will be excluded from communication (routes). 10
Research challenges • Two critical challenges – Synchronization of network access control key – Interaction between data transmission and key distribution If these two challenges can be solved, the proposed group key based network access control scheme will be done. 11
Key Synchronization • Problem statement – A key update message may fail to propagate across MANET. Thus, two legitimate user may simultaneously hold different session key (lack of key synchronization) 12
Key Synchronization (Cont-1) • An example of lack of key synchronization 13
Key Synchronization (Cont-2) • Solution – Exploit the stateless feature of the proposed stateless group key distribution scheme – Each user buffers the key update message most recently received – Transmit the buffered message to the other users that are using old session keys 14
Key Synchronization (Cont-3) • Scheme details – Proactive part • Broadcast the buffered key update message every t time unites – Reactive part • Send a key synchronization request, if a received packet has higher session ID • Send the buffered key update message, if a received packet has a lower session ID 15
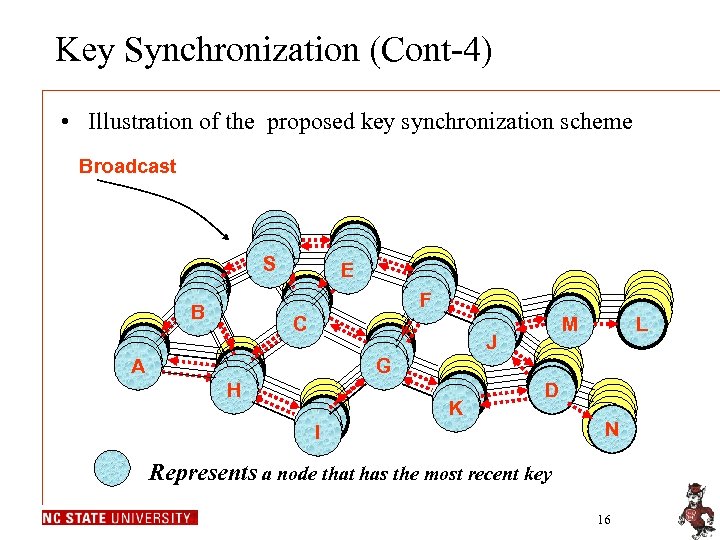
Key Synchronization (Cont-4) • Illustration of the proposed key synchronization scheme Broadcast S S S B B B A A A E E E C C C H H H F F F G G G I I I J J J K K K M M M D D D L L L N N N Represents a node that has the most recent key 16
Key Synchronization (Cont-5) • Security analysis (possible attacks) – Resource consumption via forged key update message • Solution: lightweight authentication methods (Oneway key chain & Merkle hash tree) – Resource consumption via forged data packet • Constrained to one-hop • – Logically partition MANET via refusing forwarding key update message • Multiple paths, watchdog 17
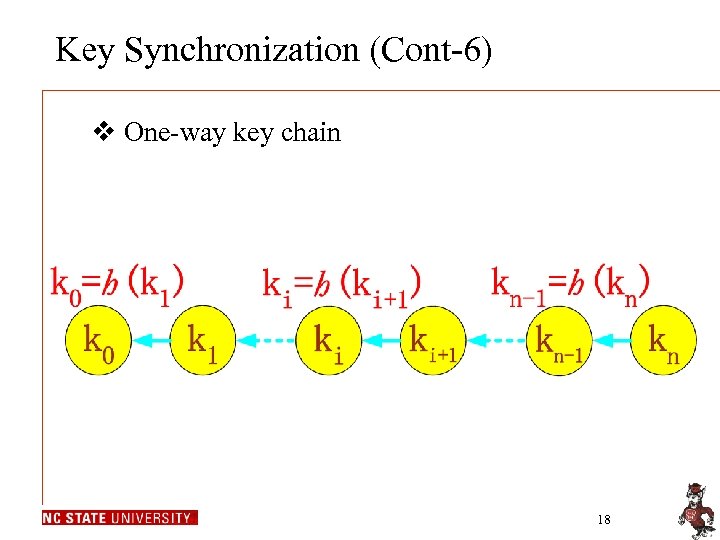
Key Synchronization (Cont-6) v One-way key chain 18
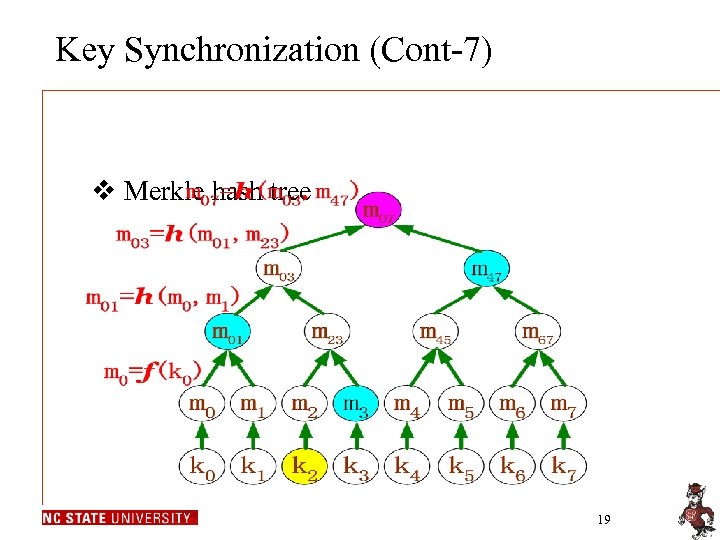
Key Synchronization (Cont-7) v Merkle hash tree 19
Key Synchronization (Cont-8) • Performance analysis – Rely on the adopted stateless group key distribution scheme – Storage • One message – Computation – Communication • Depends on t and number of users using an old key 20
Packet Retransmission • Problem statement – The interaction between data transmission and key distribution. That is, in the case of a lack of key synchronization, a user may receives some (unverified) packets authenticated with a different session key. 21
Packet Retransmission (Cont-1) • Possible options – Simply drop – Buffer and then verify – Synchronize the keys before sending every data packet • All of them have serious drawbacks 22
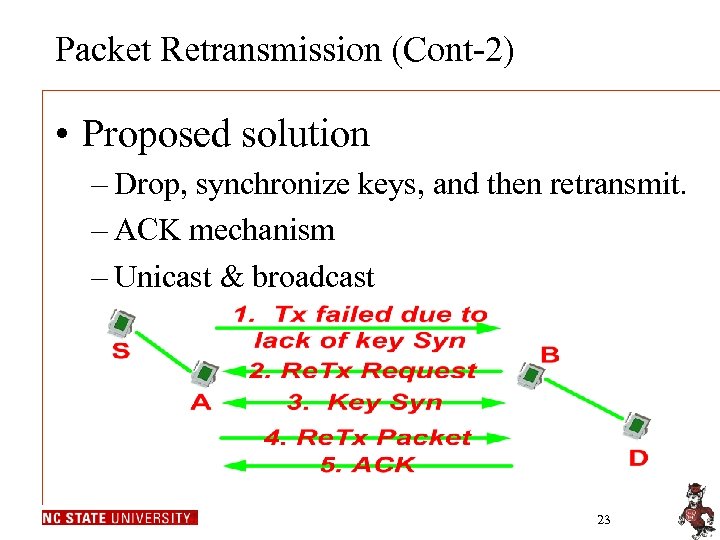
Packet Retransmission (Cont-2) • Proposed solution – Drop, synchronize keys, and then retransmit. – ACK mechanism – Unicast & broadcast 23
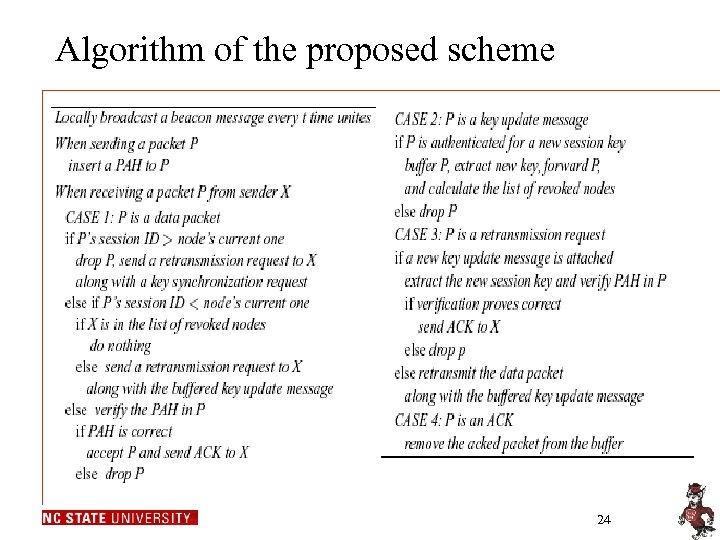
Algorithm of the proposed scheme 24
Packet Retransmission (Cont-3) • Security analysis (possible attacks) – Resource consumption attack – Forged ACK message – Packet modification 25
Packet Retransmission (Cont-4) • Performance analysis – Computation • Authentication & verification • Pentium 4 2. 1 GHz processor * MD 5 216. 674 MB/s SHA-1 67. 977 MB/s – Communication • Retransmission rate 26
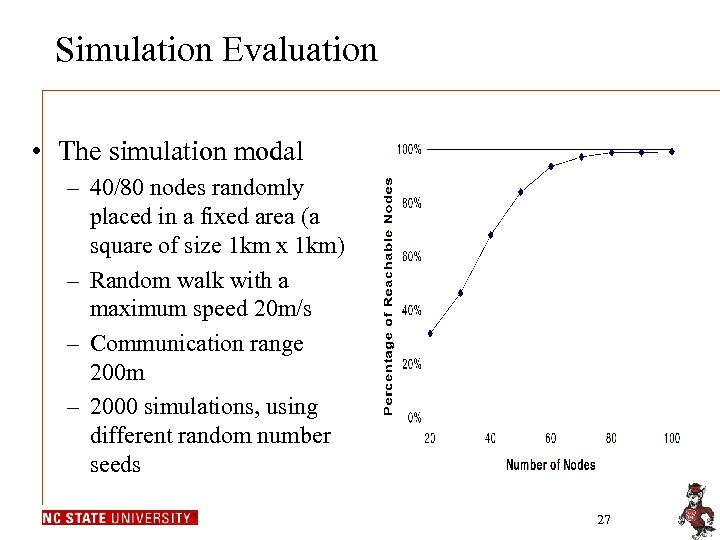
Simulation Evaluation • The simulation modal – 40/80 nodes randomly placed in a fixed area (a square of size 1 km x 1 km) – Random walk with a maximum speed 20 m/s – Communication range 200 m – 2000 simulations, using different random number seeds 27
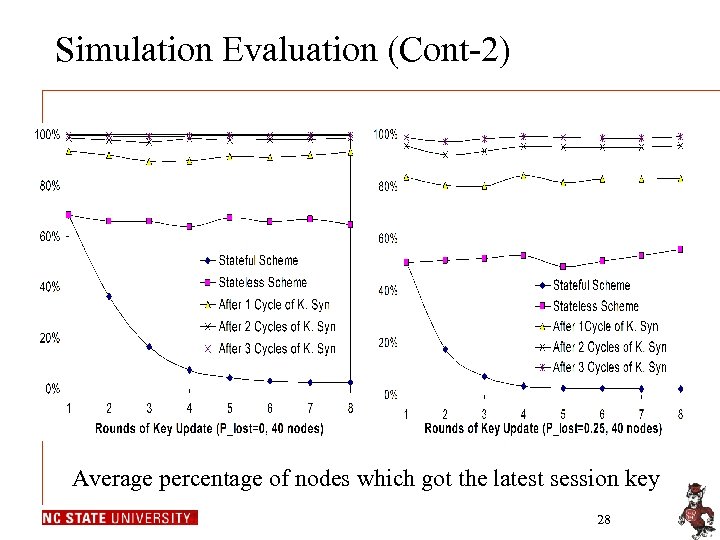
Simulation Evaluation (Cont-2) Average percentage of nodes which got the latest session key 28
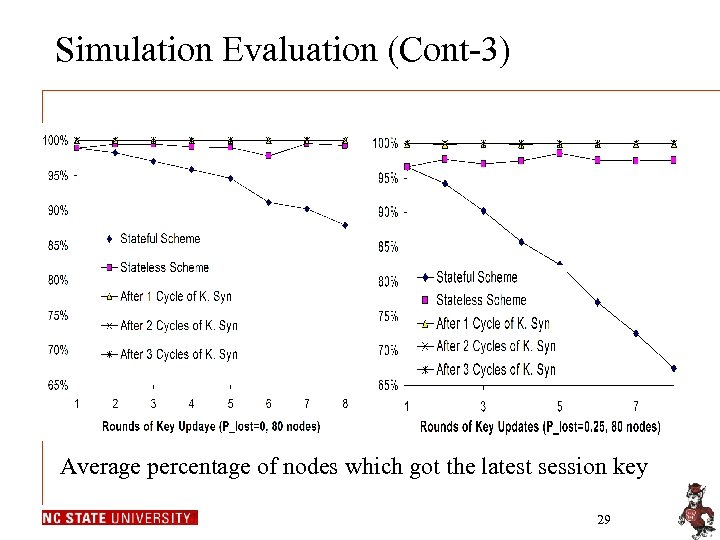
Simulation Evaluation (Cont-3) Average percentage of nodes which got the latest session key 29
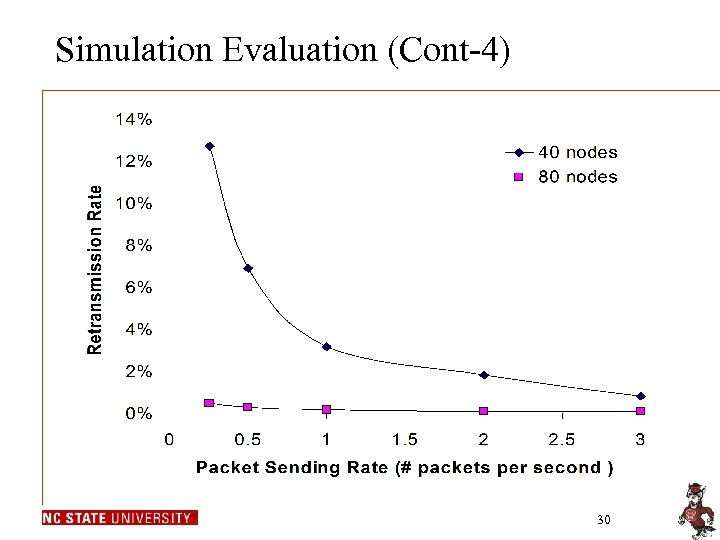
Simulation Evaluation (Cont-4) 30
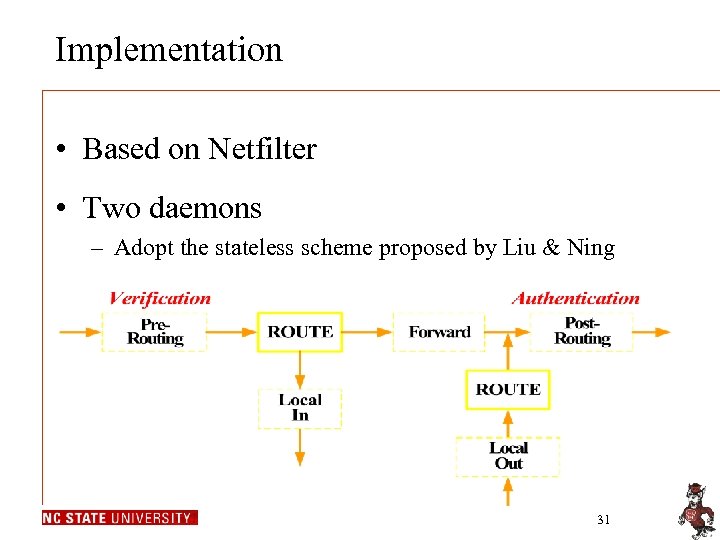
Implementation • Based on Netfilter • Two daemons – Adopt the stateless scheme proposed by Liu & Ning 31
Field Test • Test bed – One Dell P 4 laptop with Linux 9. 0 (kernel 2. 4. 20) – Two Compaq i. PAQ 3970 PDAs with Familiar v 0. 7. 2 (kernel 2. 4. 19 -rmk-pxal-hh 30) – Lucent Orinoco wireless cards • Tests – – Key distribution User revocation Packet authentication and verification Key synchronization 32

Summary • Network access control is an important issue for MANET • Cryptography-oriented solution exploiting the stateless feature of stateless group key distribution scheme • Simulation as well as functioning prototype indicates it practical and effective 33

Question 34
9d1f0a06acdb5b7191dd738fdd0d0419.ppt