6f59e2f1787062bd86f7e0d990239b89.ppt
- Количество слайдов: 33
 NETW 703 Network Protocols PROTOCOL CORECTNESS Dr. Eng Amr T. Abdel-Hamid Winter 2007 Based on Lectures notes from: * Dr. Igor Potapov, The University of Liverpool * Dr. Junzhao Sun, University of Oulu * Dr. Rachida Dssouli, Dr. Sofiene Tahar, and Dr. Ferhat Kendek Concordia University
NETW 703 Network Protocols PROTOCOL CORECTNESS Dr. Eng Amr T. Abdel-Hamid Winter 2007 Based on Lectures notes from: * Dr. Igor Potapov, The University of Liverpool * Dr. Junzhao Sun, University of Oulu * Dr. Rachida Dssouli, Dr. Sofiene Tahar, and Dr. Ferhat Kendek Concordia University
 Amr Talaat What is a Concurrent Program? A sequential program has a single thread of control. A concurrent program has multiple threads of control allowing it perform multiple computations in parallel and to control multiple external activities which occur at the same time. 2/43
Amr Talaat What is a Concurrent Program? A sequential program has a single thread of control. A concurrent program has multiple threads of control allowing it perform multiple computations in parallel and to control multiple external activities which occur at the same time. 2/43
 Amr Talaat Is Concurrent Programming Great? Concurrency is widespread but ERROR PORNE. n n Therac - 25 computerized radiation therapy machine n Concurrent programming errors contributed to accidents causing deaths and serious injuries. Mars Rover n Problems with interaction between concurrent tasks caused periodic software resets reducing availability for exploration. 3/43
Amr Talaat Is Concurrent Programming Great? Concurrency is widespread but ERROR PORNE. n n Therac - 25 computerized radiation therapy machine n Concurrent programming errors contributed to accidents causing deaths and serious injuries. Mars Rover n Problems with interaction between concurrent tasks caused periodic software resets reducing availability for exploration. 3/43
 Amr Talaat Safety and Liveness properties n n n Safety (invariant) and Liveness properties Safety property (nothing bad will ever happen). ¨ simultaneous access will never be granted to both A and B. If false, can be detected by finite sequences. ¨ simultaneous Green light will never exist. Liveness property (something good will eventually happen). ¨ Green light will be turned on sometime in the future. 4/43
Amr Talaat Safety and Liveness properties n n n Safety (invariant) and Liveness properties Safety property (nothing bad will ever happen). ¨ simultaneous access will never be granted to both A and B. If false, can be detected by finite sequences. ¨ simultaneous Green light will never exist. Liveness property (something good will eventually happen). ¨ Green light will be turned on sometime in the future. 4/43
 Amr Talaat Correctness Properties of the Protocols n n n Liveness: ¨ Freedom from deadlocks ¨ Freedom of Starvation ¨ Boundedness Freedom from unspecified receptions Freedom from Non-executable States and Transitions Completeness Self-synchronization 5/43
Amr Talaat Correctness Properties of the Protocols n n n Liveness: ¨ Freedom from deadlocks ¨ Freedom of Starvation ¨ Boundedness Freedom from unspecified receptions Freedom from Non-executable States and Transitions Completeness Self-synchronization 5/43
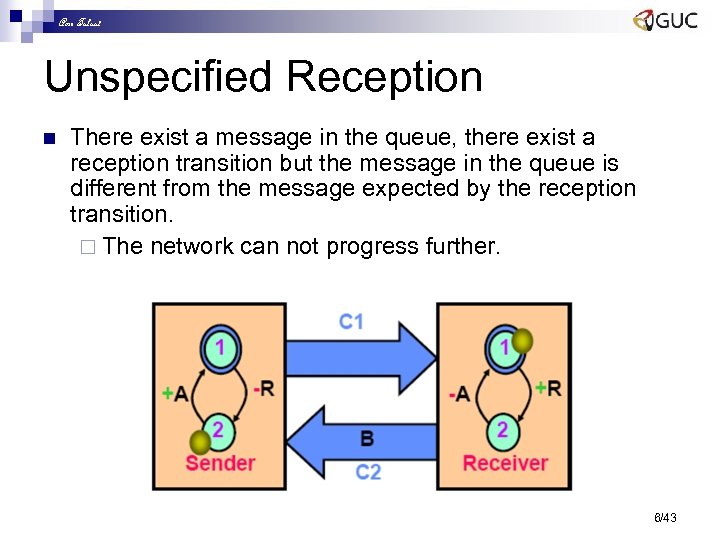 Amr Talaat Unspecified Reception n There exist a message in the queue, there exist a reception transition but the message in the queue is different from the message expected by the reception transition. ¨ The network can not progress further. 6/43
Amr Talaat Unspecified Reception n There exist a message in the queue, there exist a reception transition but the message in the queue is different from the message expected by the reception transition. ¨ The network can not progress further. 6/43
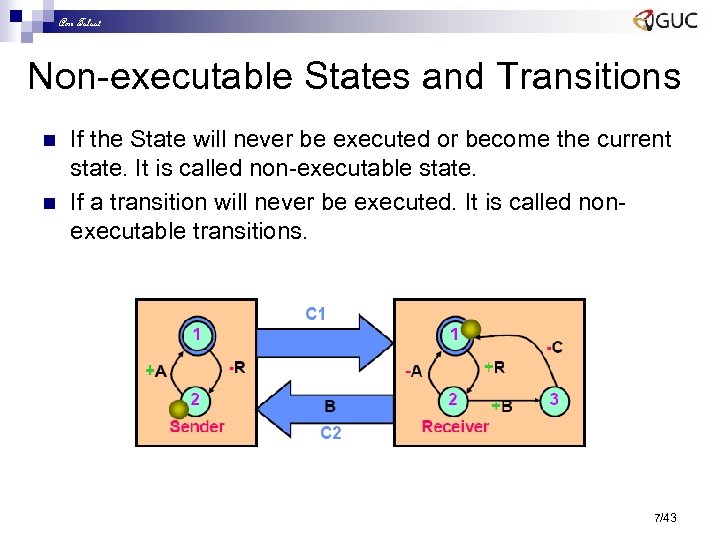 Amr Talaat Non-executable States and Transitions n n If the State will never be executed or become the current state. It is called non-executable state. If a transition will never be executed. It is called nonexecutable transitions. 7/43
Amr Talaat Non-executable States and Transitions n n If the State will never be executed or become the current state. It is called non-executable state. If a transition will never be executed. It is called nonexecutable transitions. 7/43
 Amr Talaat Other Protocol Design Errors n n n Instability or state ambiguity: If an initial state of one protocol entity may coexist with different states of other cooperating entities. The result of such an error is the potential loss of synchronization between the cooperating entities. Unboundedness or overflow: If a protocol state can be reached such that the channel linking any pair of communicating protocol entities contains a number of messages exceeding the predefined capacity for that channel Self-synchronization or self-stabilizing: If a transient error arbitrarily changes the protocol state, a self-stabilizing protocol always returns to a desirable state within a finite number of transitions, and resumes normal operation. 8/43
Amr Talaat Other Protocol Design Errors n n n Instability or state ambiguity: If an initial state of one protocol entity may coexist with different states of other cooperating entities. The result of such an error is the potential loss of synchronization between the cooperating entities. Unboundedness or overflow: If a protocol state can be reached such that the channel linking any pair of communicating protocol entities contains a number of messages exceeding the predefined capacity for that channel Self-synchronization or self-stabilizing: If a transient error arbitrarily changes the protocol state, a self-stabilizing protocol always returns to a desirable state within a finite number of transitions, and resumes normal operation. 8/43
 Amr Talaat Protocol Design Errors – Deadlock n Deadlock ¨ Both machines are at receiving states and channels are empty. ¨ The network can not progress further ¨ Receiving state is a state where all its outgoing transition are all receiving transition. It can not move without msg in its incoming channel n Livelock (hard to extract) ¨ A system is in the livelock (dynamic deadlock) if the processes are exchanging messages that are not useful for providing the service and so not making "effective progress". 9/43
Amr Talaat Protocol Design Errors – Deadlock n Deadlock ¨ Both machines are at receiving states and channels are empty. ¨ The network can not progress further ¨ Receiving state is a state where all its outgoing transition are all receiving transition. It can not move without msg in its incoming channel n Livelock (hard to extract) ¨ A system is in the livelock (dynamic deadlock) if the processes are exchanging messages that are not useful for providing the service and so not making "effective progress". 9/43
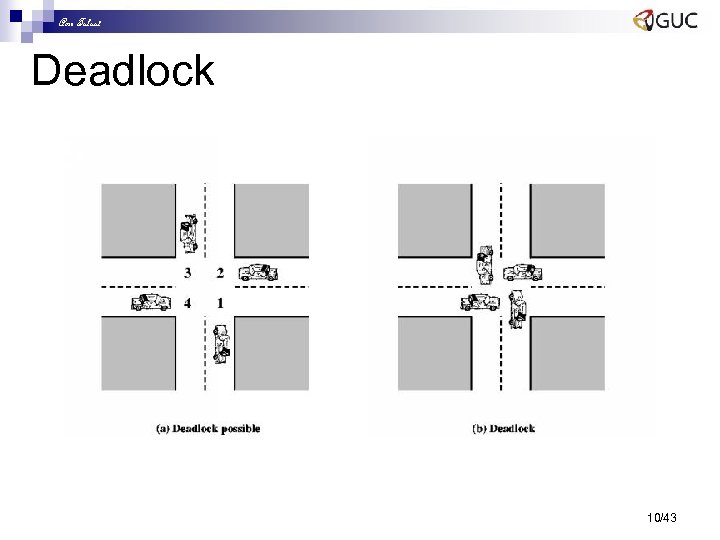 Amr Talaat Deadlock 10/43
Amr Talaat Deadlock 10/43
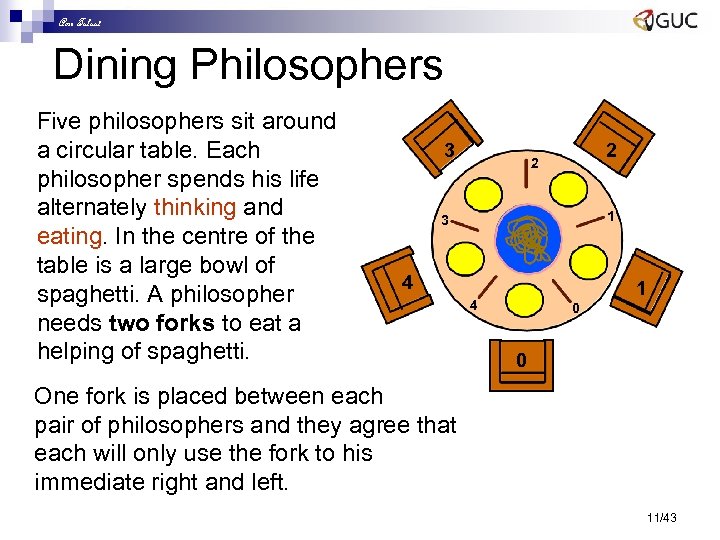 Amr Talaat Dining Philosophers Five philosophers sit around a circular table. Each philosopher spends his life alternately thinking and eating. In the centre of the table is a large bowl of spaghetti. A philosopher needs two forks to eat a helping of spaghetti. 3 2 2 1 3 4 1 4 0 0 One fork is placed between each pair of philosophers and they agree that each will only use the fork to his immediate right and left. 11/43
Amr Talaat Dining Philosophers Five philosophers sit around a circular table. Each philosopher spends his life alternately thinking and eating. In the centre of the table is a large bowl of spaghetti. A philosopher needs two forks to eat a helping of spaghetti. 3 2 2 1 3 4 1 4 0 0 One fork is placed between each pair of philosophers and they agree that each will only use the fork to his immediate right and left. 11/43
 Amr Talaat Dining Philosophers 12/43
Amr Talaat Dining Philosophers 12/43
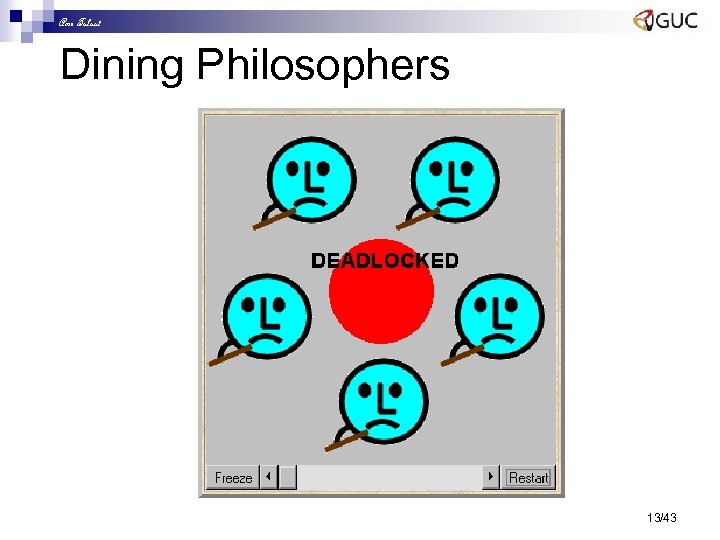 Amr Talaat Dining Philosophers 13/43
Amr Talaat Dining Philosophers 13/43
 Amr Talaat Philosopher’s lifecycle n n n A thinking philosopher has no forks. Who needs a fork to think? A thinking philosopher may become hungry (after time t). A hungry philosopher tries to grab the fork to the left and thus becomes hungry philosopher with a left fork. But one fork is not enough: a philosopher starts eating only upon obtaining both forks. The fork to right can be obtained only if it is not being used. After Eating: back to thinking after putting down both forks. 14/43
Amr Talaat Philosopher’s lifecycle n n n A thinking philosopher has no forks. Who needs a fork to think? A thinking philosopher may become hungry (after time t). A hungry philosopher tries to grab the fork to the left and thus becomes hungry philosopher with a left fork. But one fork is not enough: a philosopher starts eating only upon obtaining both forks. The fork to right can be obtained only if it is not being used. After Eating: back to thinking after putting down both forks. 14/43
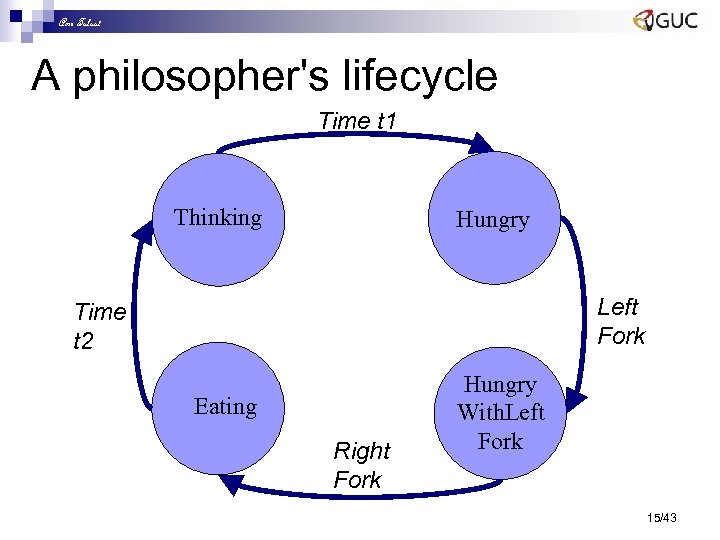 Amr Talaat A philosopher's lifecycle Time t 1 Thinking Hungry Left Fork Time t 2 Eating Right Fork Hungry With. Left Fork 15/43
Amr Talaat A philosopher's lifecycle Time t 1 Thinking Hungry Left Fork Time t 2 Eating Right Fork Hungry With. Left Fork 15/43
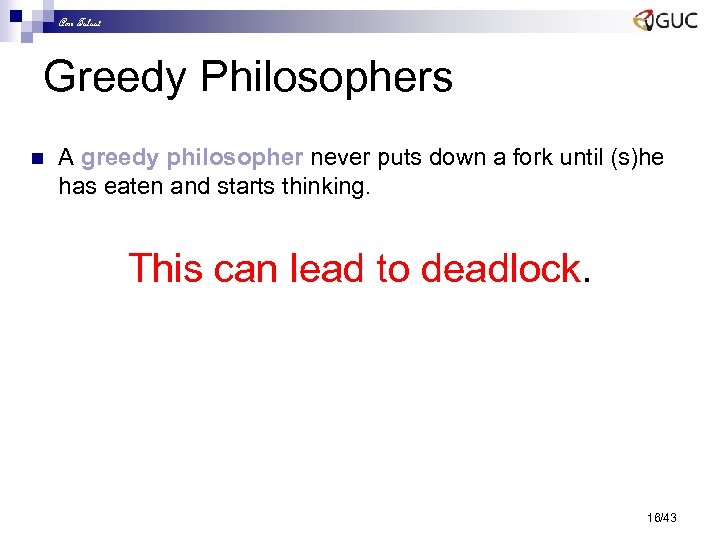 Amr Talaat Greedy Philosophers n A greedy philosopher never puts down a fork until (s)he has eaten and starts thinking. This can lead to deadlock. 16/43
Amr Talaat Greedy Philosophers n A greedy philosopher never puts down a fork until (s)he has eaten and starts thinking. This can lead to deadlock. 16/43
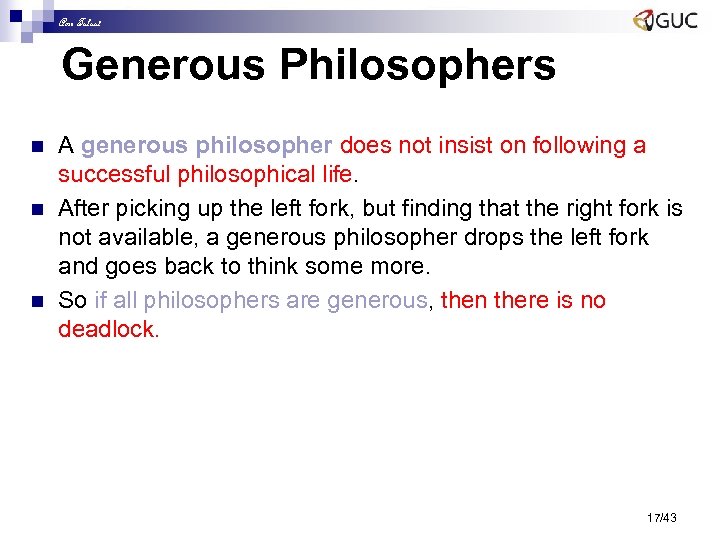 Amr Talaat Generous Philosophers n n n A generous philosopher does not insist on following a successful philosophical life. After picking up the left fork, but finding that the right fork is not available, a generous philosopher drops the left fork and goes back to think some more. So if all philosophers are generous, then there is no deadlock. 17/43
Amr Talaat Generous Philosophers n n n A generous philosopher does not insist on following a successful philosophical life. After picking up the left fork, but finding that the right fork is not available, a generous philosopher drops the left fork and goes back to think some more. So if all philosophers are generous, then there is no deadlock. 17/43
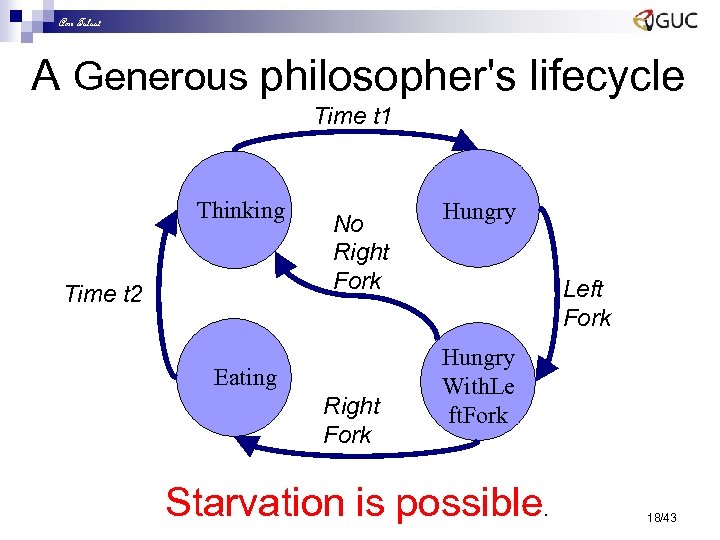 Amr Talaat A Generous philosopher's lifecycle Time t 1 Thinking Time t 2 No Right Fork Eating Right Fork Hungry Left Fork Hungry With. Le ft. Fork Starvation is possible. 18/43
Amr Talaat A Generous philosopher's lifecycle Time t 1 Thinking Time t 2 No Right Fork Eating Right Fork Hungry Left Fork Hungry With. Le ft. Fork Starvation is possible. 18/43
 Amr Talaat Dijkstra's Solution n One solution is to order the forks and require the philosophers to pick up the forks in increasing order. ¨ label the philosophers P 1, P 2, P 3, P 4, and P 5 ¨ label the forks F 1, F 2, F 3, F 4, and F 5. ¨ Each philosopher must pick up forks in a prescribed order and cannot pick up a fork another philosopher already has. ¨ Upon acquiring two forks, a philosopher may eat. ¨ Philosophers P 1 through P 4 follow the rule that Px must pick up fork Fx first and then may pick up fork Fx+1. ¨ Philosopher P 5 follows a slightly different rule, picking up fork F 1 before picking up fork F 5. If P 5 followed the same rule as the others, F 5 would come before F 1. This change in behavior for P 5 creates an asymmetry that prevents deadlock. 19/43
Amr Talaat Dijkstra's Solution n One solution is to order the forks and require the philosophers to pick up the forks in increasing order. ¨ label the philosophers P 1, P 2, P 3, P 4, and P 5 ¨ label the forks F 1, F 2, F 3, F 4, and F 5. ¨ Each philosopher must pick up forks in a prescribed order and cannot pick up a fork another philosopher already has. ¨ Upon acquiring two forks, a philosopher may eat. ¨ Philosophers P 1 through P 4 follow the rule that Px must pick up fork Fx first and then may pick up fork Fx+1. ¨ Philosopher P 5 follows a slightly different rule, picking up fork F 1 before picking up fork F 5. If P 5 followed the same rule as the others, F 5 would come before F 1. This change in behavior for P 5 creates an asymmetry that prevents deadlock. 19/43
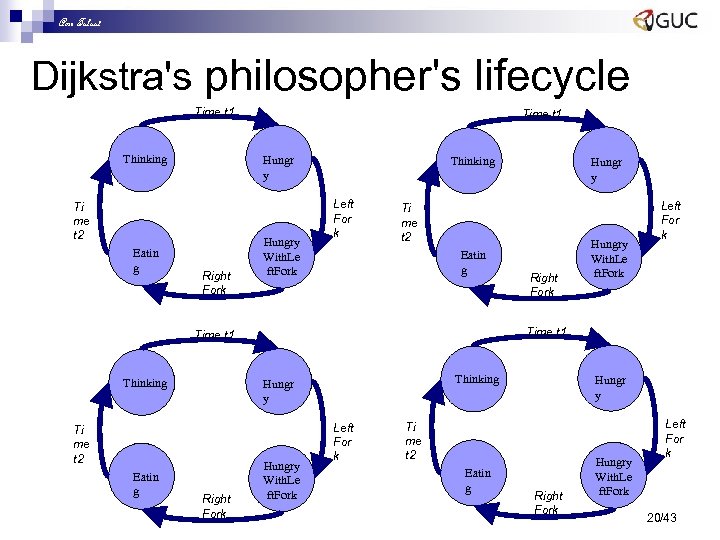 Amr Talaat Dijkstra's philosopher's lifecycle Time t 1 Thinking Hungr y Ti me t 2 Eatin g Time t 1 Right Fork Hungry With. Le ft. Fork Thinking Left For k Ti me t 2 Eatin g Thinking Hungr y Ti me t 2 Right Fork Hungry With. Le ft. Fork Left For k Time t 1 Thinking Hungr y Hungry With. Le ft. Fork Left For k Hungr y Ti me t 2 Eatin g Right Fork Hungry With. Le ft. Fork Left For k 20/43
Amr Talaat Dijkstra's philosopher's lifecycle Time t 1 Thinking Hungr y Ti me t 2 Eatin g Time t 1 Right Fork Hungry With. Le ft. Fork Thinking Left For k Ti me t 2 Eatin g Thinking Hungr y Ti me t 2 Right Fork Hungry With. Le ft. Fork Left For k Time t 1 Thinking Hungr y Hungry With. Le ft. Fork Left For k Hungr y Ti me t 2 Eatin g Right Fork Hungry With. Le ft. Fork Left For k 20/43
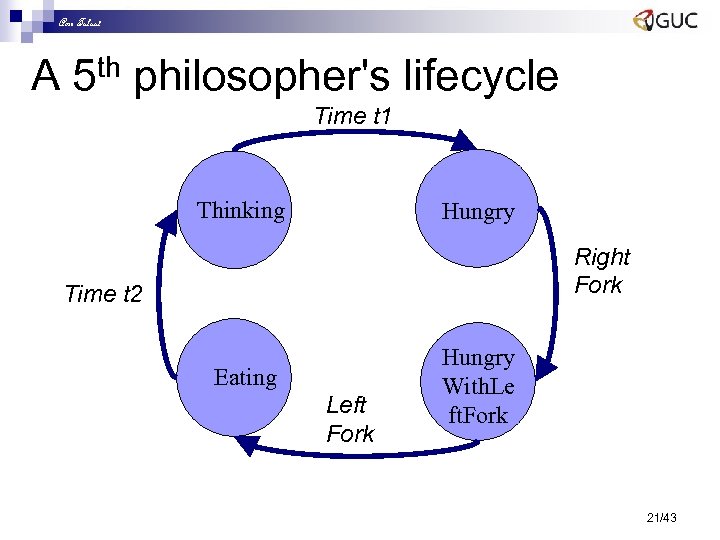 Amr Talaat A 5 th philosopher's lifecycle Time t 1 Thinking Hungry Right Fork Time t 2 Eating Left Fork Hungry With. Le ft. Fork 21/43
Amr Talaat A 5 th philosopher's lifecycle Time t 1 Thinking Hungry Right Fork Time t 2 Eating Left Fork Hungry With. Le ft. Fork 21/43
 Amr Talaat Reachability Analysis n n Reachability Analysis is a global state exploration process that Starts from the initial global state, and recursively explores all possible transitions that lead to new global states ¨ The result is a reachability graph, which captures all possible states A global state
Amr Talaat Reachability Analysis n n Reachability Analysis is a global state exploration process that Starts from the initial global state, and recursively explores all possible transitions that lead to new global states ¨ The result is a reachability graph, which captures all possible states A global state , denoted =>* to
 Amr Talaat Global State In CFSMs n A global state of a system, is a pair of
Amr Talaat Global State In CFSMs n A global state of a system, is a pair of
 Amr Talaat Reachability Graph (Tree) n n n Nodes represents regular global states Directed arc, connecting two nodes or states
Amr Talaat Reachability Graph (Tree) n n n Nodes represents regular global states Directed arc, connecting two nodes or states and , corresponds to a transition in one of the communicating processes Root of the Tree corresponds to the initial state A path in the Tree corresponds to an execution sequence of the interleaved receptions and transmissions, and it represents the reachability of the last state in the path from the initial state of the path The expansion of the tree from a particular node stops if one of the following conditions is satisfied: ¨ the node already exist in the tree ¨ the node correspond to a deadlock state ¨ an unspecified reception error is detected at the node ¨ the node corresponds to a final state 24/43
 Amr Talaat Global State In CFSMs n The next global state is obtained as:
Amr Talaat Global State In CFSMs n The next global state is obtained as:
 Amr Talaat Reachability Analysis Process n n n Starting from initial global state, where channels are empty and machines at their initial states Explore all possible reachable state by firing all the possible transitions (and generating global states) from any given reachable state. All deadlock and unspecified reception errors will be captured and marked as individual global state By examining the number of messages in the channels we can design the buffer size for the protocol Can detect non-executable states and transitions by marking those states that are touched and transitions that are fired during the reachability analysis 26/43
Amr Talaat Reachability Analysis Process n n n Starting from initial global state, where channels are empty and machines at their initial states Explore all possible reachable state by firing all the possible transitions (and generating global states) from any given reachable state. All deadlock and unspecified reception errors will be captured and marked as individual global state By examining the number of messages in the channels we can design the buffer size for the protocol Can detect non-executable states and transitions by marking those states that are touched and transitions that are fired during the reachability analysis 26/43
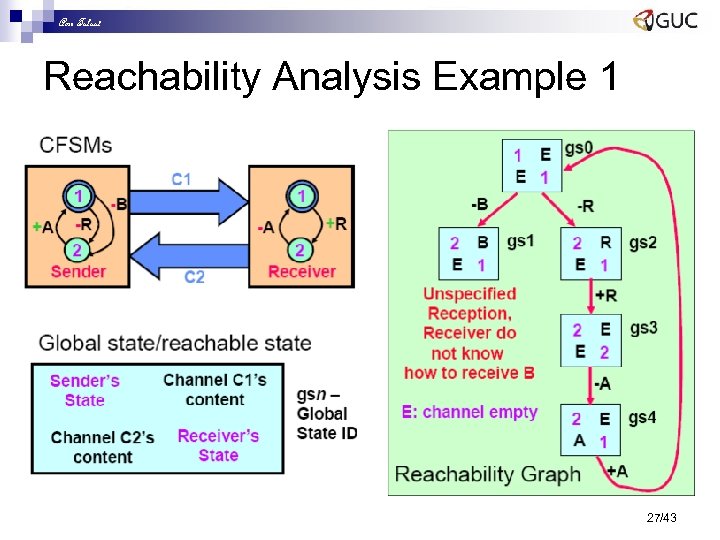 Amr Talaat Reachability Analysis Example 1 27/43
Amr Talaat Reachability Analysis Example 1 27/43
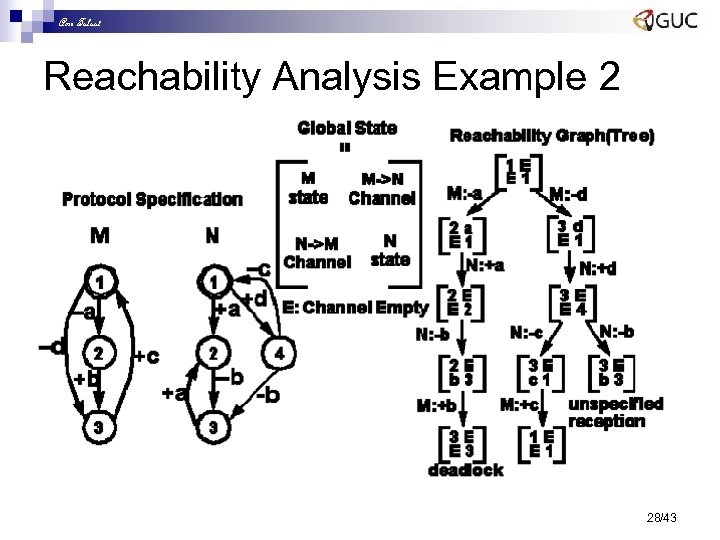 Amr Talaat Reachability Analysis Example 2 28/43
Amr Talaat Reachability Analysis Example 2 28/43
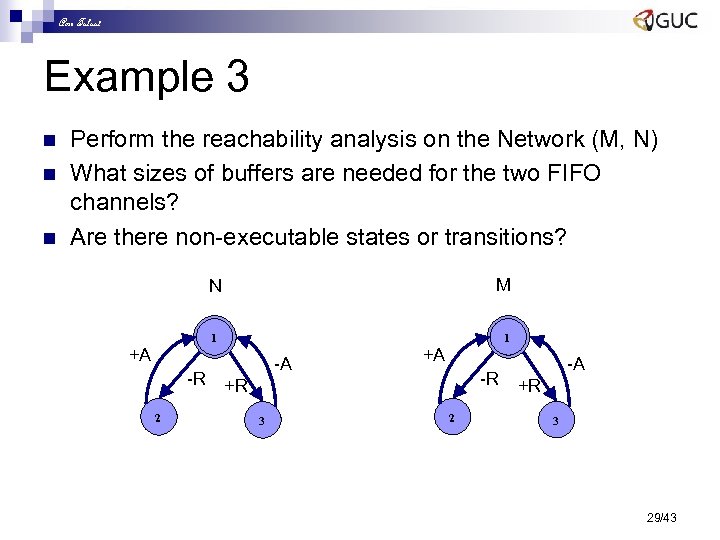 Amr Talaat Example 3 n n n Perform the reachability analysis on the Network (M, N) What sizes of buffers are needed for the two FIFO channels? Are there non-executable states or transitions? M N 1 1 +A -R 2 -A +A -R +R 3 2 -A +R 3 29/43
Amr Talaat Example 3 n n n Perform the reachability analysis on the Network (M, N) What sizes of buffers are needed for the two FIFO channels? Are there non-executable states or transitions? M N 1 1 +A -R 2 -A +A -R +R 3 2 -A +R 3 29/43
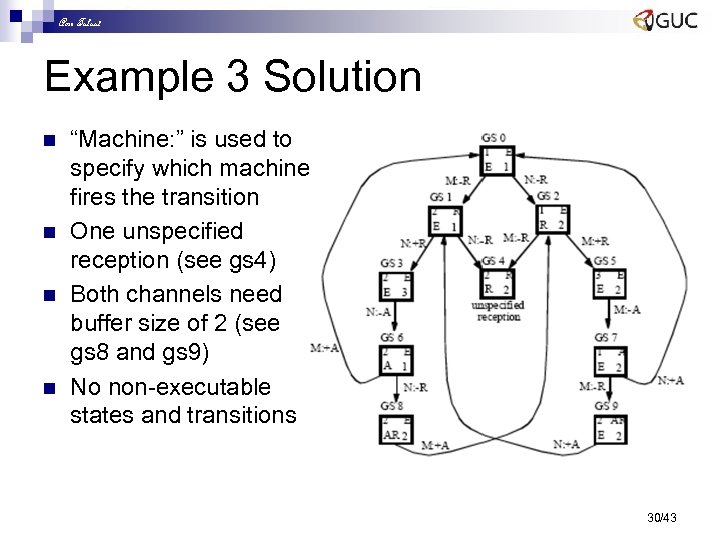 Amr Talaat Example 3 Solution n n “Machine: ” is used to specify which machine fires the transition One unspecified reception (see gs 4) Both channels need buffer size of 2 (see gs 8 and gs 9) No non-executable states and transitions 30/43
Amr Talaat Example 3 Solution n n “Machine: ” is used to specify which machine fires the transition One unspecified reception (see gs 4) Both channels need buffer size of 2 (see gs 8 and gs 9) No non-executable states and transitions 30/43
 Amr Talaat Reachability Analysis n n Advantages: ¨ Easily automated ¨ Many logical errors can be detected by only examining individual global states in the reachability graph Disadvantages: ¨ State space explosion problem ¨ Does not work on unbounded protocols ¨ Many relationships among the protocol state variables, expressing the desirable logical correctness properties of the protocol are not apparent from simply traversing the reachability graph 31/43
Amr Talaat Reachability Analysis n n Advantages: ¨ Easily automated ¨ Many logical errors can be detected by only examining individual global states in the reachability graph Disadvantages: ¨ State space explosion problem ¨ Does not work on unbounded protocols ¨ Many relationships among the protocol state variables, expressing the desirable logical correctness properties of the protocol are not apparent from simply traversing the reachability graph 31/43
 Amr Talaat Other Techniques n n n Full search is simplest but for small class of protocols Controlled partial search tries to optimize the quality of analysis ¨ Depth-bounds, place a bound on the length of the execution sequences ¨ Scatter searches, executions are selected that lead closer to potential deadlock states ¨ Guided searches, a dynamically evaluated cost function as state selection criterion ¨ Probabilistic searches, successor states are explored in decreasing order of their probability of occurrence ¨ Partial orders, based on the definition of a heuristic for fair or maximum progress state exploration Random simulation is for systems of even complexity ¨ Explore the state space with a random simulation or “random walk” 32/43
Amr Talaat Other Techniques n n n Full search is simplest but for small class of protocols Controlled partial search tries to optimize the quality of analysis ¨ Depth-bounds, place a bound on the length of the execution sequences ¨ Scatter searches, executions are selected that lead closer to potential deadlock states ¨ Guided searches, a dynamically evaluated cost function as state selection criterion ¨ Probabilistic searches, successor states are explored in decreasing order of their probability of occurrence ¨ Partial orders, based on the definition of a heuristic for fair or maximum progress state exploration Random simulation is for systems of even complexity ¨ Explore the state space with a random simulation or “random walk” 32/43
 Amr Talaat Petri Nets Testing • • • Reachability • “Can we reach one particular state from another? ” Boundedness • “Will a storage place overflow? ” Liveness • “Will the system die in a particular state? ” 33/43
Amr Talaat Petri Nets Testing • • • Reachability • “Can we reach one particular state from another? ” Boundedness • “Will a storage place overflow? ” Liveness • “Will the system die in a particular state? ” 33/43


