5ef9c7b364eb2e32f7f4e073b23a6e8a.ppt
- Количество слайдов: 132

NETGEAR Product Training Firewall VPN Products Presented by Hien Ly Level 3, Sr. Tech Support Engineer November, 2007

Agenda » Introduction to NETGEAR Firewall VPN Products • Firewall Overview » Types of Firewall » DMZ • NETGEAR DMZ » How to Choose a Firewall? • VPN Overview » What is VPN? » Encryption » IPsec Basics • IPsec Protocols • Security Associations (SA) • IKE Phases » SSL 312 VPN Introduction » NETGEAR Firewall VPN Router Features • Unique Features highlight • NETGEAR VPN Configuration Screenshots • Pro. Safe VPN Client Software » Troubleshooting Tips and Lab • VPN Troubleshooting Flow • Hands-on lab © 1996 -2006 NETGEAR ®. All rights reserved. 2

Course Objectives » Agents should be able to do the following after this course: • Recognize the Firewall VPN products that NETGEAR has to offer • Be able to understand the basic Firewall concepts • Be able to understand the basic VPN concepts • Be able to understand the differences between IPSec and SSL VPN • Be able to understand the different types of firewall settings on the NETGEAR routers • Be able to configure and establish VPN sessions using various NETGEAR products: » Box-to-box VPN » Client-to-box VPN » Hub & Spoke VPN © 1996 -2006 NETGEAR ®. All rights reserved. 3
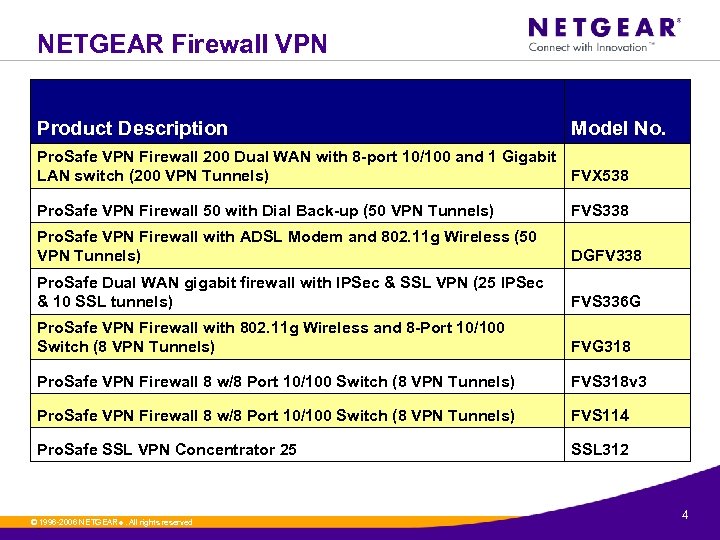
NETGEAR Firewall VPN Product Description Model No. Pro. Safe VPN Firewall 200 Dual WAN with 8 -port 10/100 and 1 Gigabit LAN switch (200 VPN Tunnels) FVX 538 Pro. Safe VPN Firewall 50 with Dial Back-up (50 VPN Tunnels) FVS 338 Pro. Safe VPN Firewall with ADSL Modem and 802. 11 g Wireless (50 VPN Tunnels) DGFV 338 Pro. Safe Dual WAN gigabit firewall with IPSec & SSL VPN (25 IPSec & 10 SSL tunnels) FVS 336 G Pro. Safe VPN Firewall with 802. 11 g Wireless and 8 -Port 10/100 Switch (8 VPN Tunnels) FVG 318 Pro. Safe VPN Firewall 8 w/8 Port 10/100 Switch (8 VPN Tunnels) FVS 318 v 3 Pro. Safe VPN Firewall 8 w/8 Port 10/100 Switch (8 VPN Tunnels) FVS 114 Pro. Safe SSL VPN Concentrator 25 SSL 312 © 1996 -2006 NETGEAR ®. All rights reserved. 4
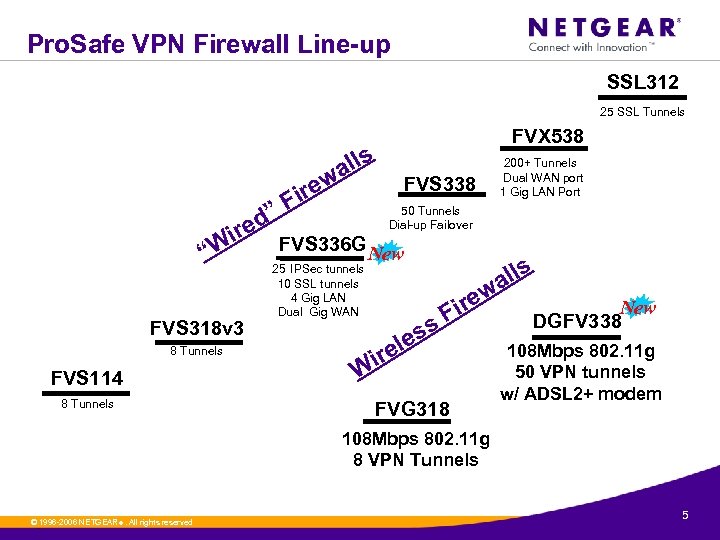
Pro. Safe VPN Firewall Line-up SSL 312 25 SSL Tunnels FVX 538 s all w ” ed r Wi “ FVS 318 v 3 8 Tunnels FVS 114 8 Tunnels ire F 200+ Tunnels Dual WAN port 1 Gig LAN Port FVS 338 50 Tunnels Dial-up Failover FVS 336 G New 25 IPSec tunnels 10 SSL tunnels 4 Gig LAN Dual Gig WAN ss le s all w ire F ire W FVG 318 New DGFV 338 108 Mbps 802. 11 g 50 VPN tunnels w/ ADSL 2+ modem 108 Mbps 802. 11 g 8 VPN Tunnels © 1996 -2006 NETGEAR ®. All rights reserved. 5

Firewall 101
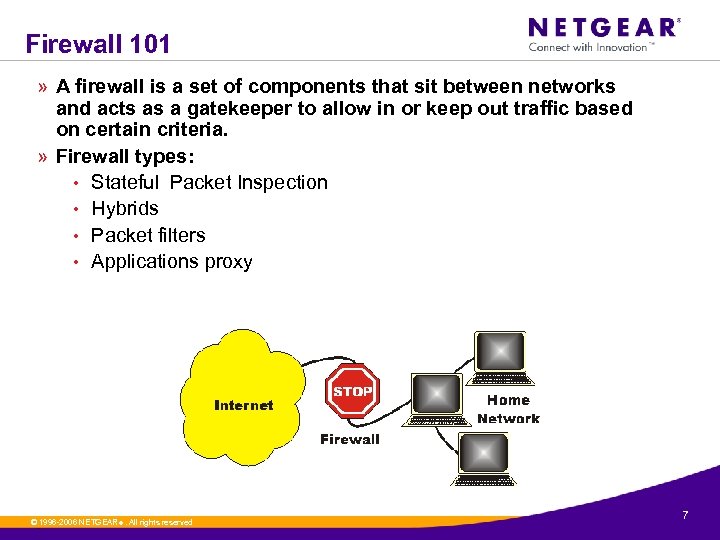
Firewall 101 » A firewall is a set of components that sit between networks and acts as a gatekeeper to allow in or keep out traffic based on certain criteria. » Firewall types: • Stateful Packet Inspection • Hybrids • Packet filters • Applications proxy © 1996 -2006 NETGEAR ®. All rights reserved. 7
Stateful Packet Inspection (SPI) » Examine each packet passed through. » Allows or drops packets depends of rules. » Maintains tables of information about current connections. • Information traveling from inside the firewall to the outside is monitored for specific defining characteristics, then incoming information is compared to these characteristics. If the comparison yields a reasonable match, the information is allowed through. Otherwise it is discarded. » Use current state of connections in tables to determine if it will allow or drops incoming packets. » When a connection terminates, it removes the reference from the internal table. Most of the Firewalls available today are Hybrids. © 1996 -2006 NETGEAR ®. All rights reserved. 8
Hybrid Firewall » Offers the best of all world: • Application-Level Packet Filtering • Proxy-ARP Transparency isolates internal systems from attack • Policy-based routing for efficient use of dual network connections • Multiple redundant / balanced Internet links for fail-safe operation • Traffic shaping and QOS control for priority services • Address translation and port/address forwarding hides the internal network © 1996 -2006 NETGEAR ®. All rights reserved. 9
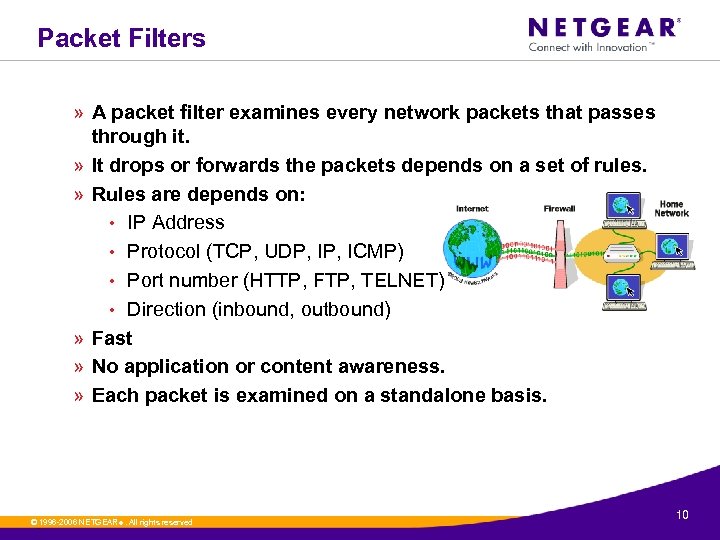
Packet Filters » A packet filter examines every network packets that passes through it. » It drops or forwards the packets depends on a set of rules. » Rules are depends on: • IP Address • Protocol (TCP, UDP, ICMP) • Port number (HTTP, FTP, TELNET) • Direction (inbound, outbound) » Fast » No application or content awareness. » Each packet is examined on a standalone basis. © 1996 -2006 NETGEAR ®. All rights reserved. 10
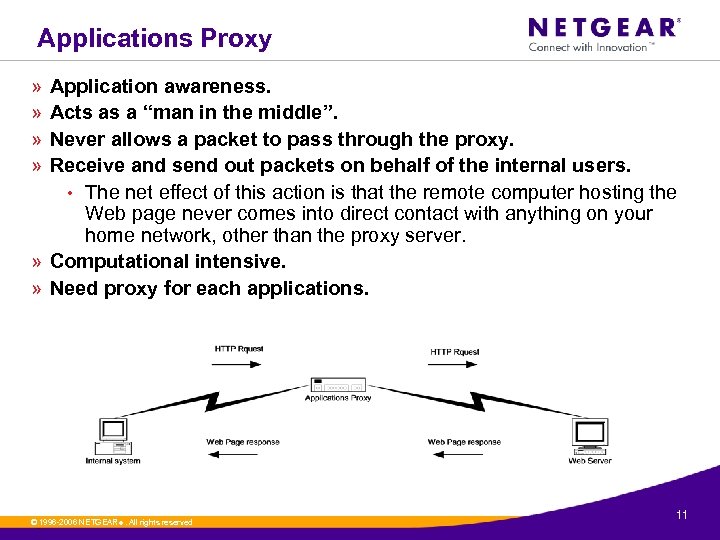
Applications Proxy » » Application awareness. Acts as a “man in the middle”. Never allows a packet to pass through the proxy. Receive and send out packets on behalf of the internal users. • The net effect of this action is that the remote computer hosting the Web page never comes into direct contact with anything on your home network, other than the proxy server. » Computational intensive. » Need proxy for each applications. © 1996 -2006 NETGEAR ®. All rights reserved. 11
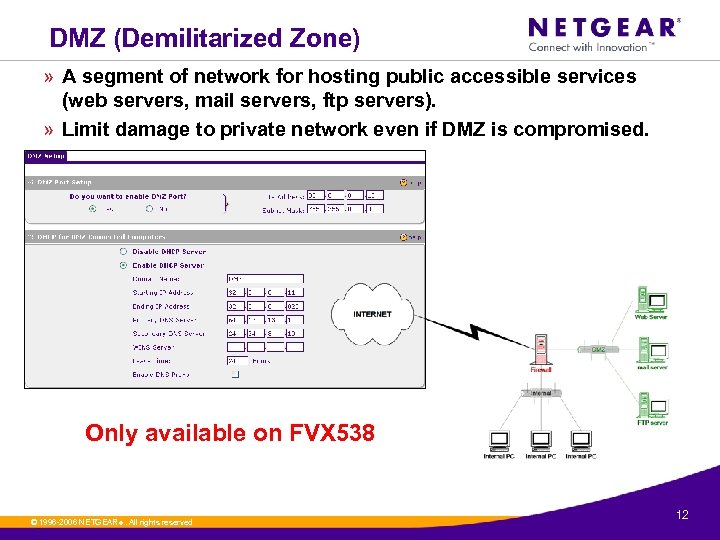
DMZ (Demilitarized Zone) » A segment of network for hosting public accessible services (web servers, mail servers, ftp servers). » Limit damage to private network even if DMZ is compromised. Only available on FVX 538 © 1996 -2006 NETGEAR ®. All rights reserved. 12
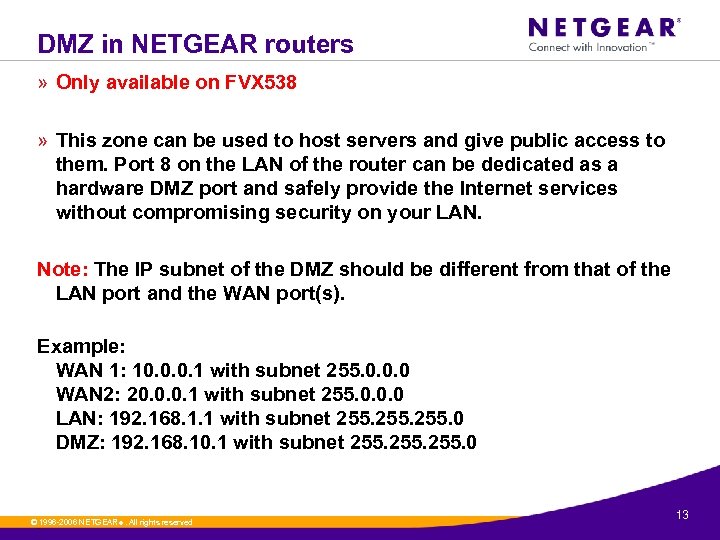
DMZ in NETGEAR routers » Only available on FVX 538 » This zone can be used to host servers and give public access to them. Port 8 on the LAN of the router can be dedicated as a hardware DMZ port and safely provide the Internet services without compromising security on your LAN. Note: The IP subnet of the DMZ should be different from that of the LAN port and the WAN port(s). Example: WAN 1: 10. 0. 0. 1 with subnet 255. 0. 0. 0 WAN 2: 20. 0. 0. 1 with subnet 255. 0. 0. 0 LAN: 192. 168. 1. 1 with subnet 255. 0 DMZ: 192. 168. 10. 1 with subnet 255. 0 © 1996 -2006 NETGEAR ®. All rights reserved. 13

How to choose a firewall? » Security. » Features: • Flexibility in defining rules – by time/date. • User authentications. • URL Filtering. • Content filtering. • Port forwarding (NAT). » Performance » Support – updates, enhancement. » Audit Trail – logs, alarms. » Manageability – a firewall is as security as it is configured. © 1996 -2006 NETGEAR ®. All rights reserved. 14

VPN Overview
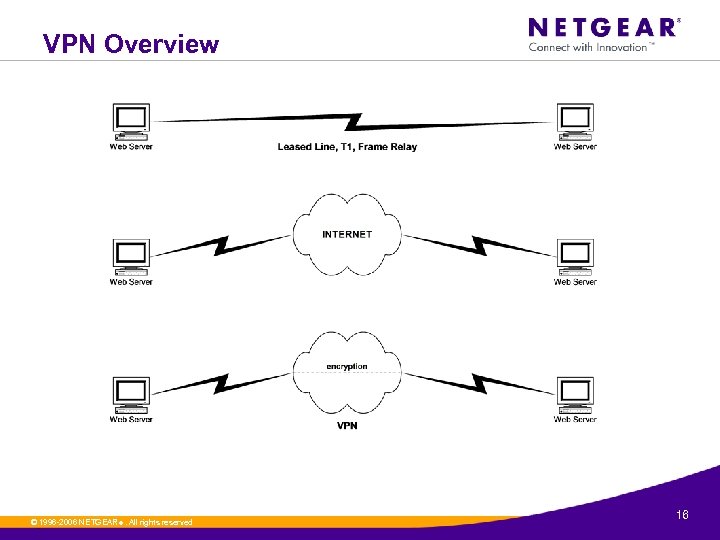
VPN Overview © 1996 -2006 NETGEAR ®. All rights reserved. 16
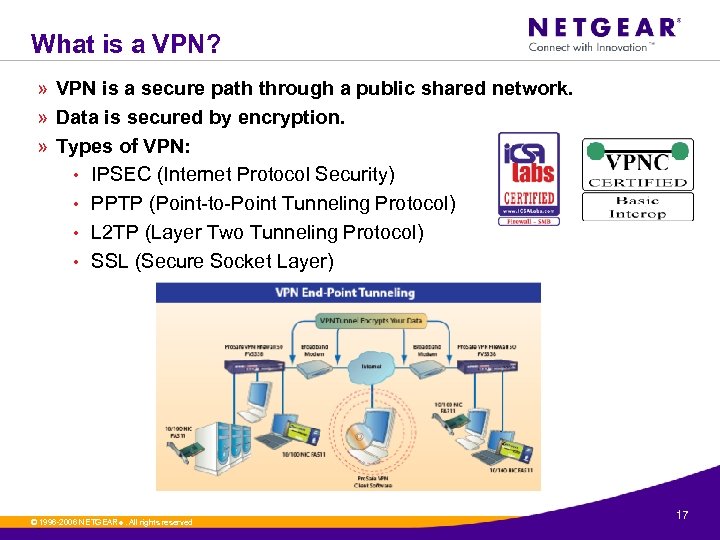
What is a VPN? » VPN is a secure path through a public shared network. » Data is secured by encryption. » Types of VPN: • IPSEC (Internet Protocol Security) • PPTP (Point-to-Point Tunneling Protocol) • L 2 TP (Layer Two Tunneling Protocol) • SSL (Secure Socket Layer) © 1996 -2006 NETGEAR ®. All rights reserved. 17

Encryption » A mathematical function to convert data into secret. » Encryption convert cleartext to ciphertext. - Encrypt(cleartext, key) = ciphertext - Decrypt(ciphertext, key) = cleartext » Symmetric encryption (DES, 3 DES) » Asymmetric encryption (public key) » Hash algorithm - Hash(A, key) = B Low probability that another data will be hashed into B. Fast. © 1996 -2006 NETGEAR ®. All rights reserved. 18
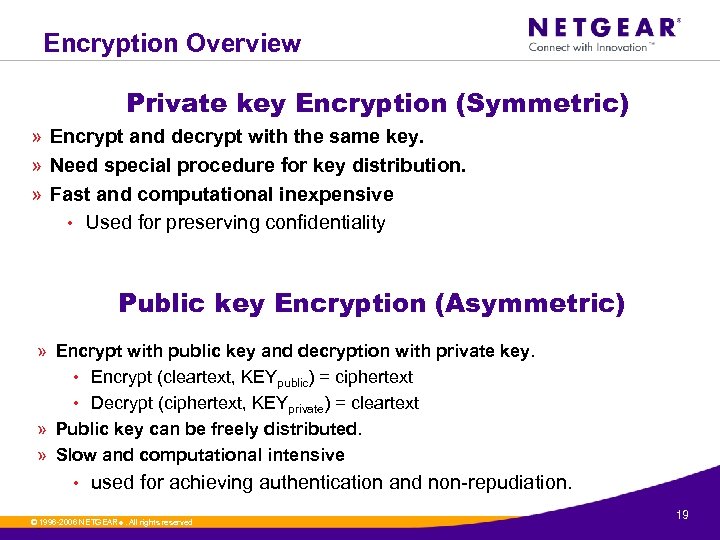
Encryption Overview Private key Encryption (Symmetric) » Encrypt and decrypt with the same key. » Need special procedure for key distribution. » Fast and computational inexpensive • Used for preserving confidentiality Public key Encryption (Asymmetric) » Encrypt with public key and decryption with private key. • Encrypt (cleartext, KEYpublic) = ciphertext • Decrypt (ciphertext, KEYprivate) = cleartext » Public key can be freely distributed. » Slow and computational intensive • used for achieving authentication and non-repudiation. © 1996 -2006 NETGEAR ®. All rights reserved. 19
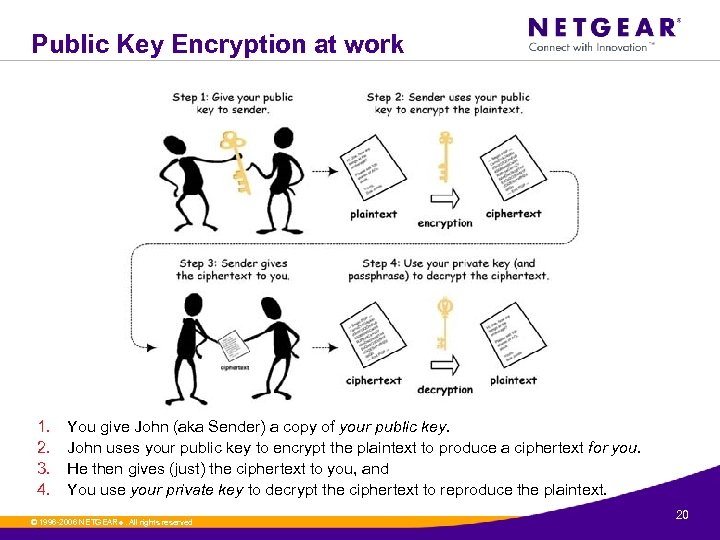
Public Key Encryption at work 1. 2. 3. 4. You give John (aka Sender) a copy of your public key. John uses your public key to encrypt the plaintext to produce a ciphertext for you. He then gives (just) the ciphertext to you, and You use your private key to decrypt the ciphertext to reproduce the plaintext. © 1996 -2006 NETGEAR ®. All rights reserved. 20
IPsec Basics » » » Applications transparency. Automated key management. Interoperability with PKI (Public Key Infrastructure). Fast deployment. Implemented in existing routers/CPE. © 1996 -2006 NETGEAR ®. All rights reserved. 21
IPsec Protocols » Three main Protocols of IPsec • IKE (Internet Key Exchange) » Defines a method for the secure exchange of the initial encryption keys between the two endpoints of a VPN (establishing SA). » UDP protocol 500 • AH (Authentication Header) » Used to ensure integrity of the header information and payload as the packet makes its way through the Internet. Authentication only, no encryption » 128 -bit MD 5 or 160 -bit SHA-1 keys used to compute the integrity checksum value (ICV) » TCP protocol 51 • ESP (Encapsulating Security Payload) » Performs the actual encryption of the data to provide data confidentiality, and data integrity. » Encrypt with DES/3 DES. » TCP protocol 50 © 1996 -2006 NETGEAR ®. All rights reserved. 22

Security Associations (SA) » What is Security Associations (SA)? • Basic concepts of IPsec • Represents a policy contract between two VPN endpoints describing how they will use IPsec to secure network traffic • Contains all the security parameters to establish VPN connection • Unidirectional – one SA for each direction. • Each established SA is identified by a 32 -bit number (SPI) • SPI are written into IPsec packet headers to locate the appropriate SA. © 1996 -2006 NETGEAR ®. All rights reserved. 23
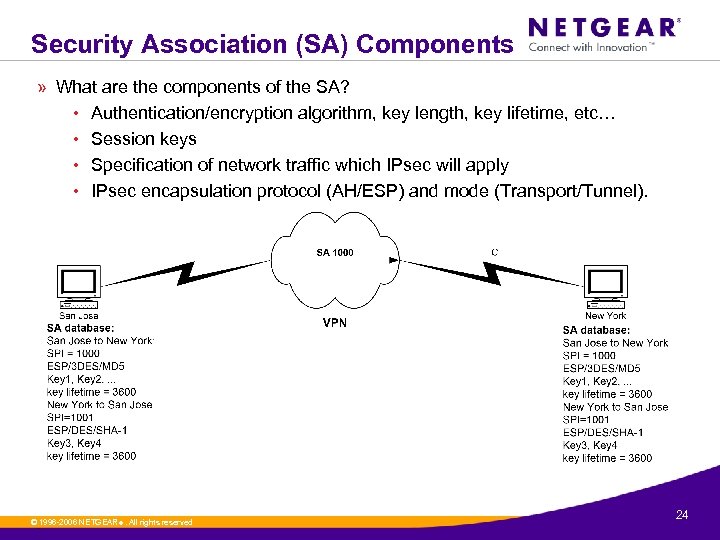
Security Association (SA) Components » What are the components of the SA? • Authentication/encryption algorithm, key length, key lifetime, etc… • Session keys • Specification of network traffic which IPsec will apply • IPsec encapsulation protocol (AH/ESP) and mode (Transport/Tunnel). © 1996 -2006 NETGEAR ®. All rights reserved. 24
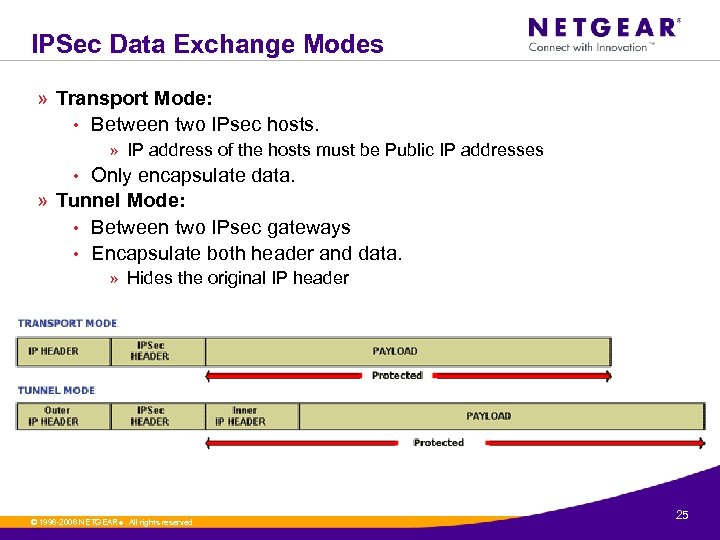
IPSec Data Exchange Modes » Transport Mode: • Between two IPsec hosts. » IP address of the hosts must be Public IP addresses • Only encapsulate data. » Tunnel Mode: • Between two IPsec gateways • Encapsulate both header and data. » Hides the original IP header © 1996 -2006 NETGEAR ®. All rights reserved. 25
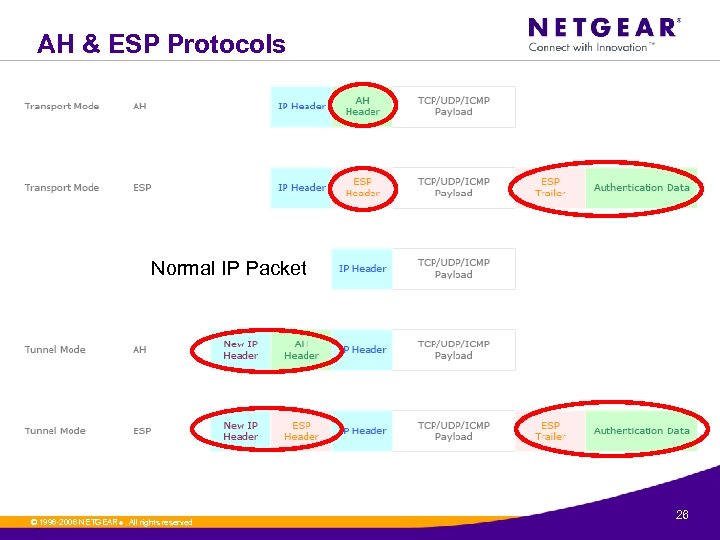
AH & ESP Protocols Normal IP Packet © 1996 -2006 NETGEAR ®. All rights reserved. 26
IKE – Internet Key Exchange Protocol » ISAKMP (Internet Security Association and Key Management Protocol) • Protocol to negotiate and establish SA. » Oakley • Define mechanism for key exchange over the IKE session • By default, use Diffie-Hellman algorithm for key exchange » Each IKE peer has an IKE identitiy which based on: • IP address • FQDN (Fully qualified domain name) • X. 500 (certificate) name • Email address » IKE session are protected by cryptographic algorithms. » IKE peers must agree exactly on a set of algorithms and protocols to protect the IKE session © 1996 -2006 NETGEAR ®. All rights reserved. 27
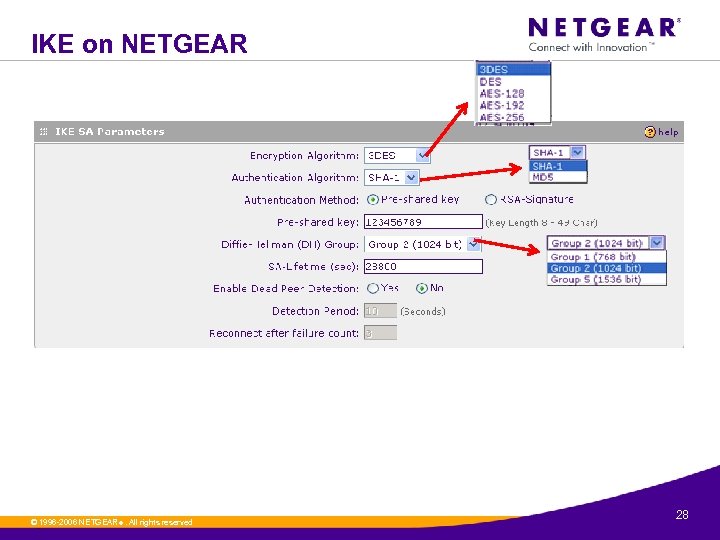
IKE on NETGEAR © 1996 -2006 NETGEAR ®. All rights reserved. 28

IKE Operations » Phase 1 (Authentication Phase) • Main mode or Aggressive mode • Used to establish a secure channel, authenticate the negotiating parties, and generate shared keys to protect IKE protocol messages • Negotiates IKE SA » Phase 2 (Key Exchange Phase) • AKA: Quick mode • Used to establish the IPSec SA and to generate new keying material • Negotiates IPsec SA © 1996 -2006 NETGEAR ®. All rights reserved. 29
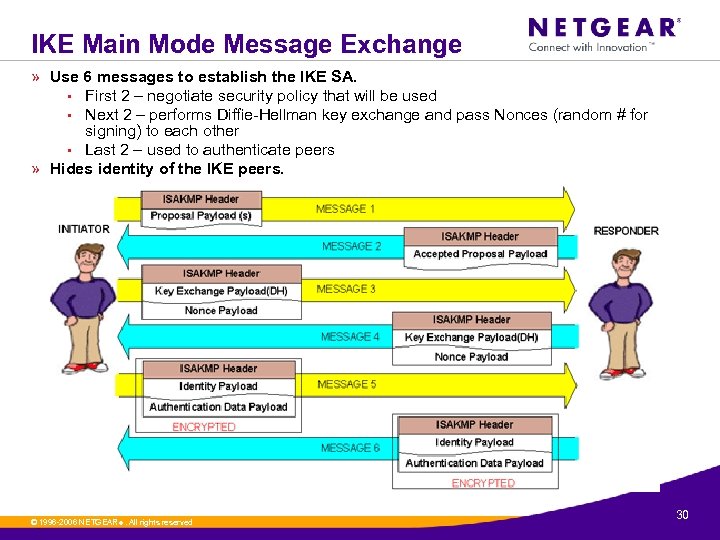
IKE Main Mode Message Exchange » Use 6 messages to establish the IKE SA. • First 2 – negotiate security policy that will be used • Next 2 – performs Diffie-Hellman key exchange and pass Nonces (random # for signing) to each other • Last 2 – used to authenticate peers » Hides identity of the IKE peers. © 1996 -2006 NETGEAR ®. All rights reserved. 30
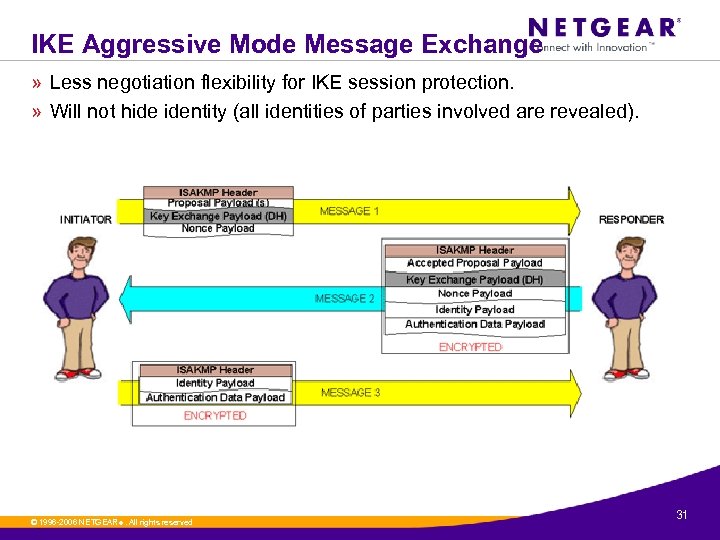
IKE Aggressive Mode Message Exchange » Less negotiation flexibility for IKE session protection. » Will not hide identity (all identities of parties involved are revealed). © 1996 -2006 NETGEAR ®. All rights reserved. 31
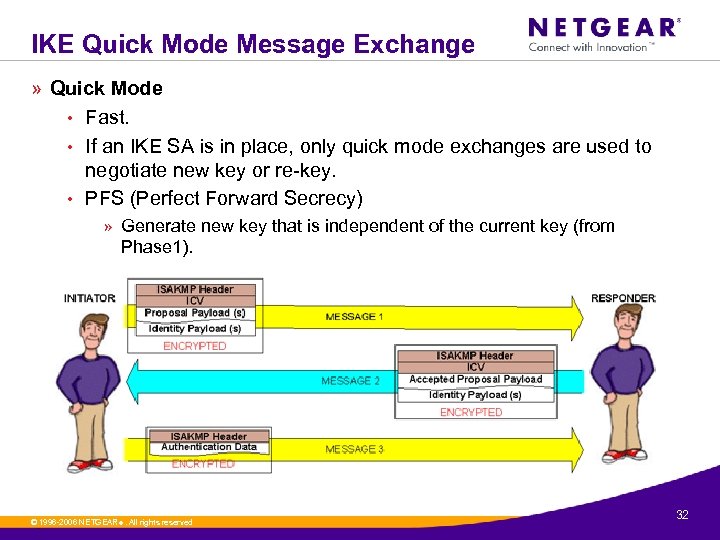
IKE Quick Mode Message Exchange » Quick Mode • Fast. • If an IKE SA is in place, only quick mode exchanges are used to negotiate new key or re-key. • PFS (Perfect Forward Secrecy) » Generate new key that is independent of the current key (from Phase 1). © 1996 -2006 NETGEAR ®. All rights reserved. 32
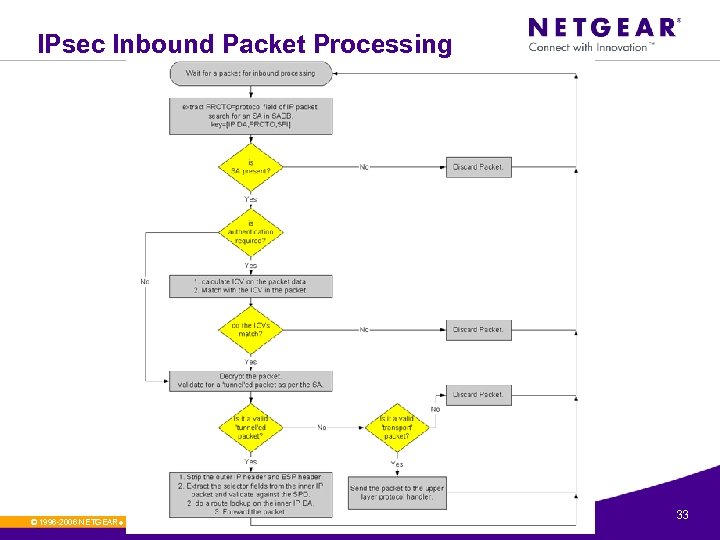
IPsec Inbound Packet Processing © 1996 -2006 NETGEAR ®. All rights reserved. 33
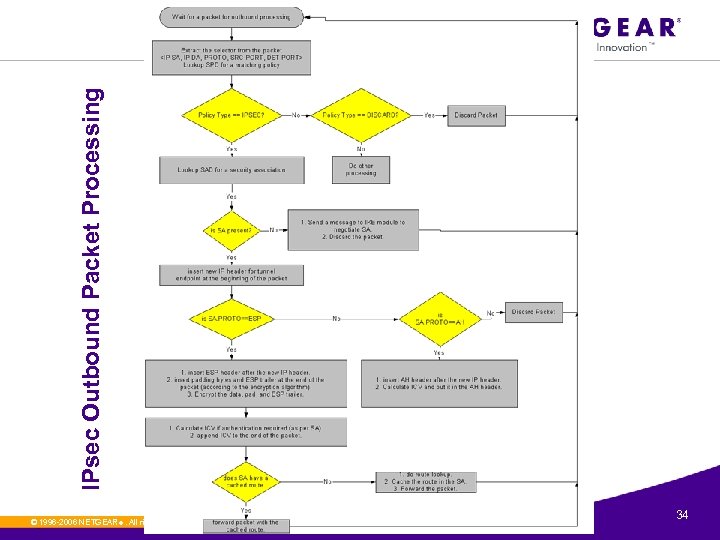
IPsec Outbound Packet Processing © 1996 -2006 NETGEAR ®. All rights reserved. 34
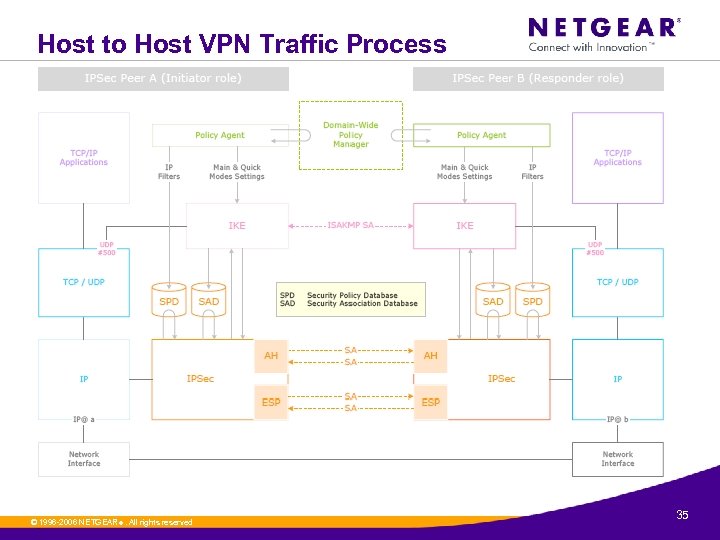
Host to Host VPN Traffic Process © 1996 -2006 NETGEAR ®. All rights reserved. 35
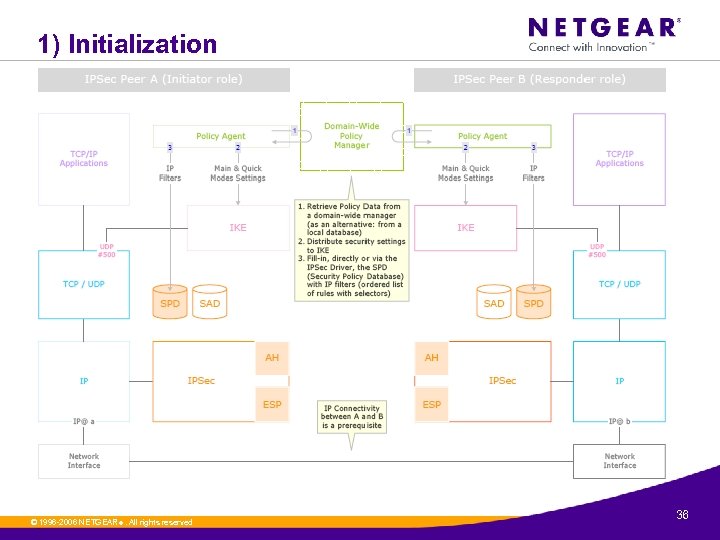
1) Initialization © 1996 -2006 NETGEAR ®. All rights reserved. 36
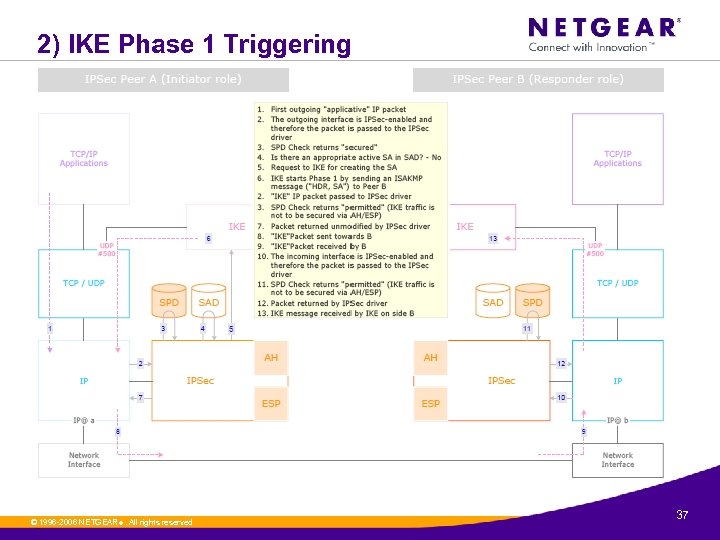
2) IKE Phase 1 Triggering © 1996 -2006 NETGEAR ®. All rights reserved. 37
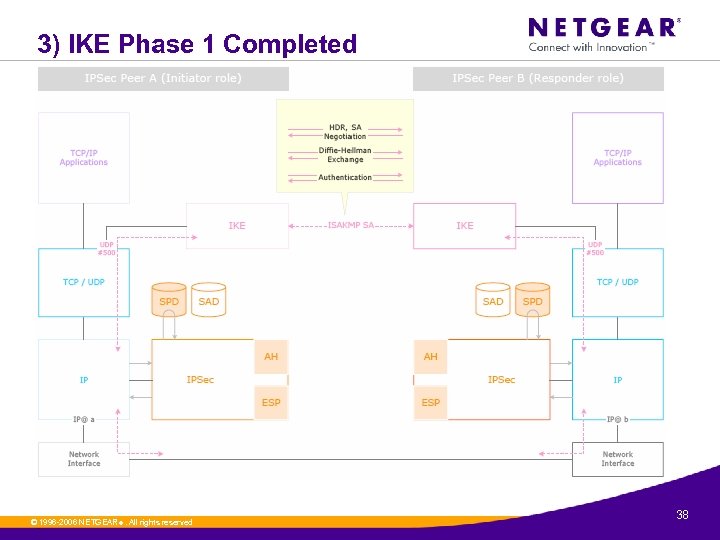
3) IKE Phase 1 Completed © 1996 -2006 NETGEAR ®. All rights reserved. 38
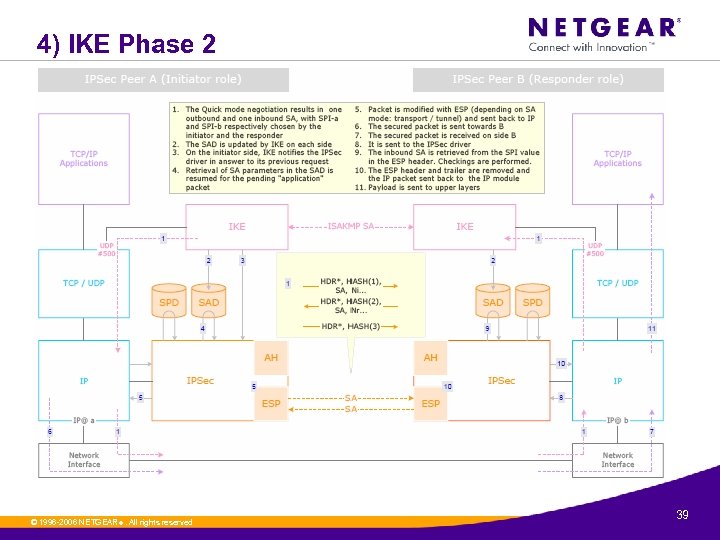
4) IKE Phase 2 © 1996 -2006 NETGEAR ®. All rights reserved. 39
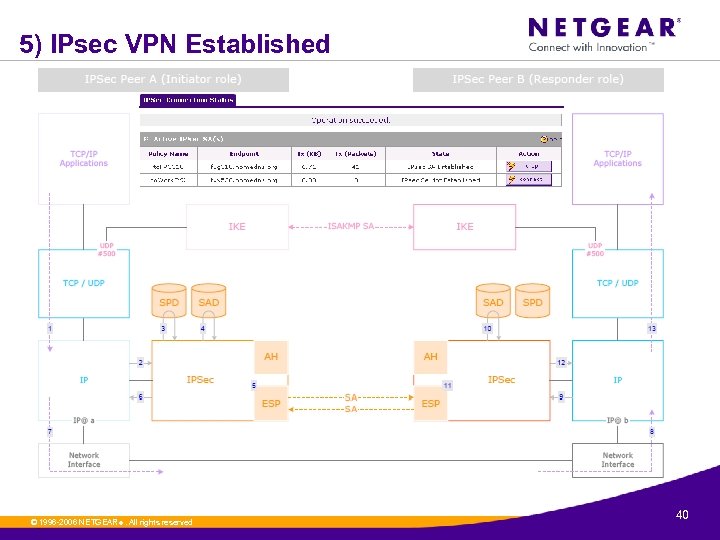
5) IPsec VPN Established © 1996 -2006 NETGEAR ®. All rights reserved. 40

VPN Policy requirements? » Who are the VPN parties? • IKE Identifiers (WAN IP, FQDN, FQUN, DN). » Where are the VPN parties? • VPN gateway addresses (WAN IP, FQDN). » What traffics are included in the VPN? • Local VPN subnet, remote VPN subnet. » How the VPN secure the communication? • Main mode / Aggressive mode. • Pre-shared key. • Key lifetime. • ESP / AH (authentication algorithm, encryption algorithm). • PFS? © 1996 -2006 NETGEAR ®. All rights reserved. 41
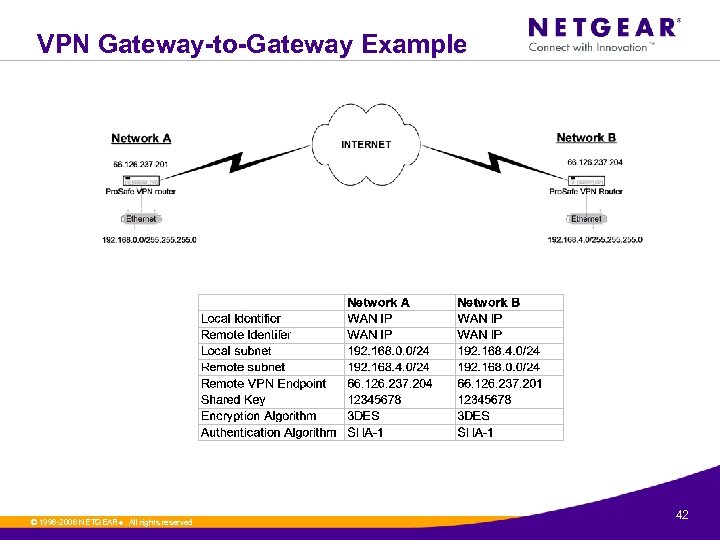
VPN Gateway-to-Gateway Example © 1996 -2006 NETGEAR ®. All rights reserved. 42
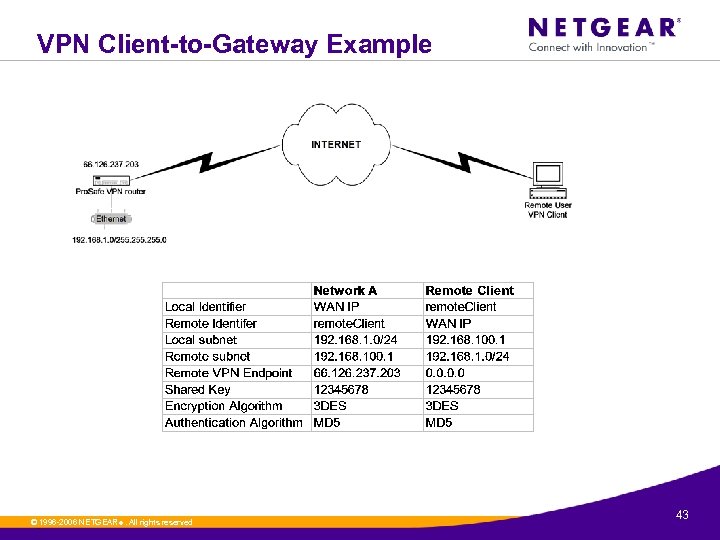
VPN Client-to-Gateway Example © 1996 -2006 NETGEAR ®. All rights reserved. 43
What is SSL VPN? » SSL VPNs create secure tunnels by performing two functions: • Requiring authentication from users before allowing access so that only authorized parties can establish tunnels • Encrypting all data transmitted to and from the user by implementing the actual tunnel using SSL » The process of establishing an SSL tunnel requires exchange of different configuration information between the computers on either end of the connection. © 1996 -2006 NETGEAR ®. All rights reserved. 44
SSL VPN on OSI Network Model » IPSec VPN operates at the Network Layer – Layer 3 » SSL VPN establish connectivity using SSL, which functions at Layers 4 & 5 » Information gets encapsulate at Layer 6 & 7 of the OSI model » So why don't SSL VPNs simply use SSL to tunnel network-level communications as IPSec does and not worry about the higher levels? • Technical limitations of many devices prevent the establishment of Network-Layer communications over SSL, but allow applicationlayer access from a web browser. • Security considerations and policies normally prohibit attaching Internet kiosks and borrowed computers as nodes on your corporate network. » Cannot install VPN client software on public Kiosks © 1996 -2006 NETGEAR ®. All rights reserved. 45
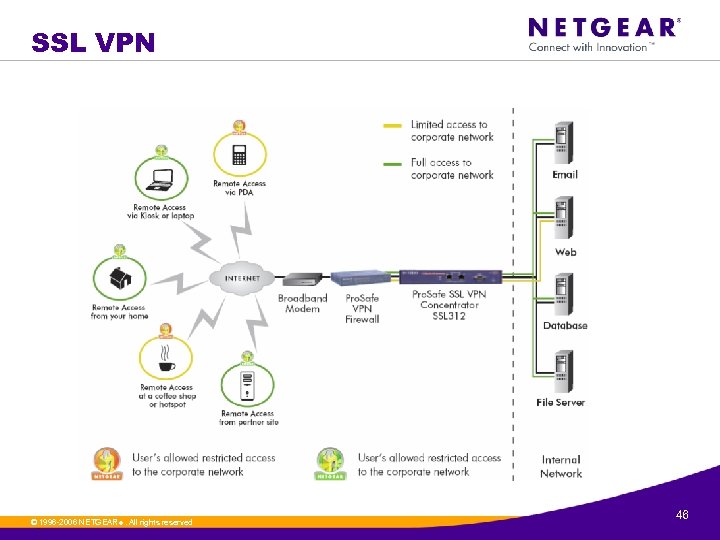
SSL VPN © 1996 -2006 NETGEAR ®. All rights reserved. 46
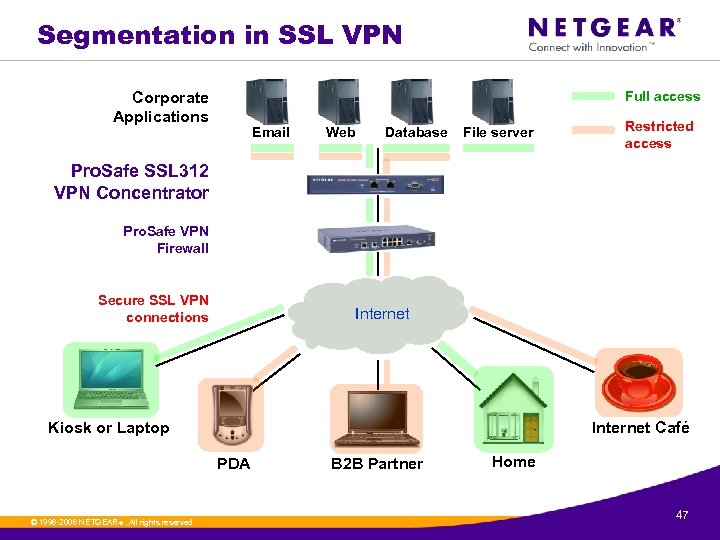
Segmentation in SSL VPN Full access Corporate Applications Email Web Database File server Restricted access Pro. Safe SSL 312 VPN Concentrator Pro. Safe VPN Firewall Secure SSL VPN connections Internet Kiosk or Laptop Internet Café PDA © 1996 -2006 NETGEAR ®. All rights reserved. B 2 B Partner Home 47
Unique Router Features
Serial Modem – FR 328 S, FVS 328, FWG 114 P L O E © 1996 -2006 NETGEAR ®. All rights reserved. 49
Serial Port – Auto Failover FVS 328, FR 328 S, FWG 114 P L O E © 1996 -2006 NETGEAR ®. All rights reserved. 50
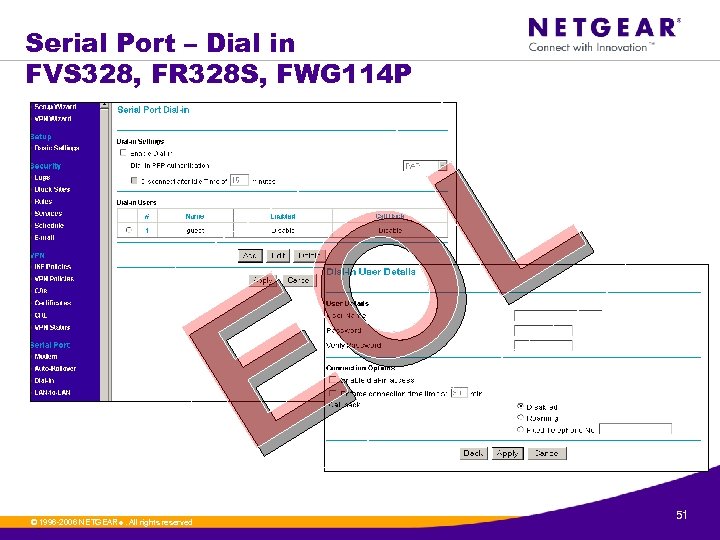
Serial Port – Dial in FVS 328, FR 328 S, FWG 114 P L O E © 1996 -2006 NETGEAR ®. All rights reserved. 51
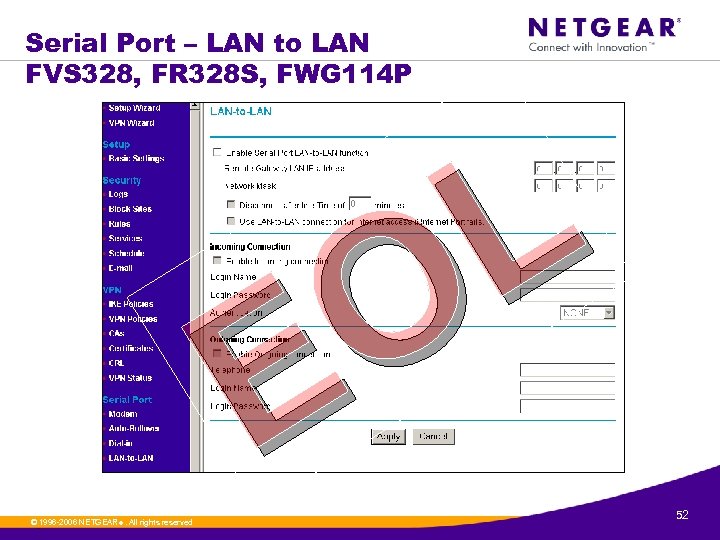
Serial Port – LAN to LAN FVS 328, FR 328 S, FWG 114 P L O E © 1996 -2006 NETGEAR ®. All rights reserved. 52
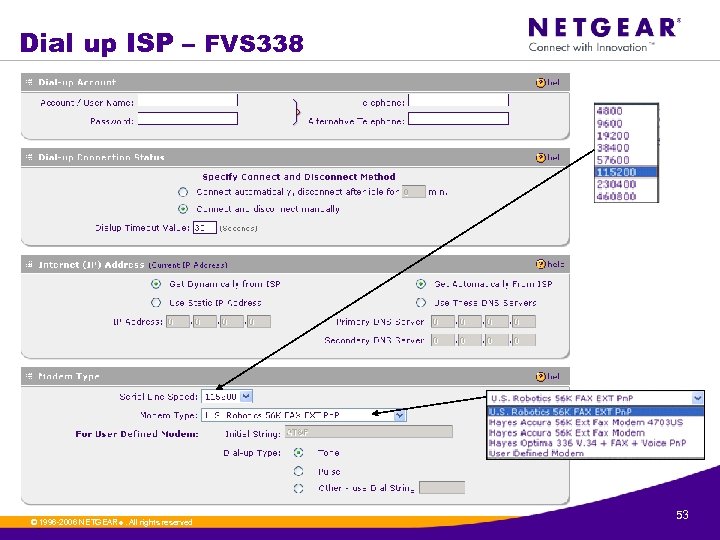
Dial up ISP – FVS 338 © 1996 -2006 NETGEAR ®. All rights reserved. 53
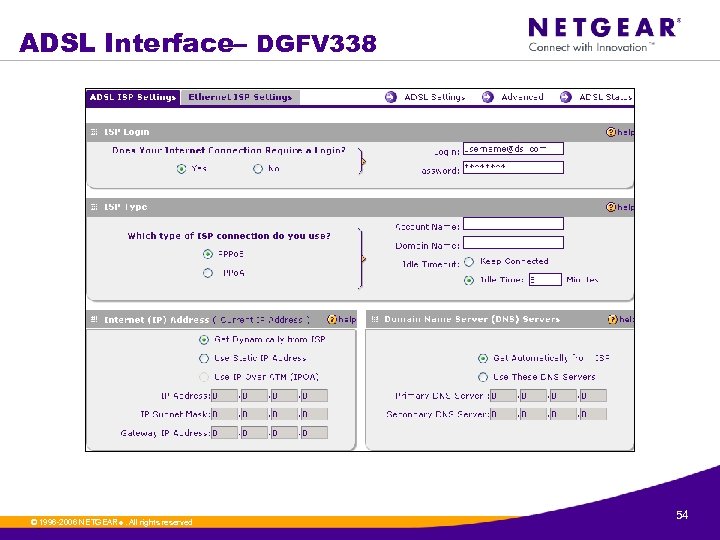
ADSL Interface– DGFV 338 © 1996 -2006 NETGEAR ®. All rights reserved. 54
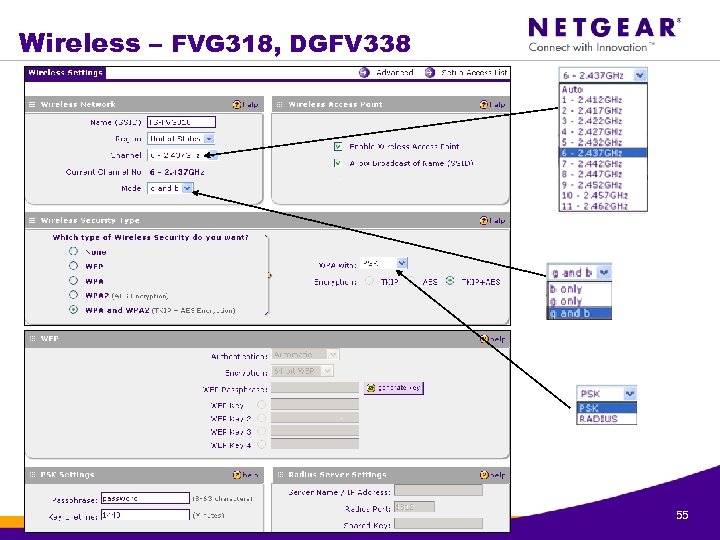
Wireless – FVG 318, DGFV 338 © 1996 -2006 NETGEAR ®. All rights reserved. 55
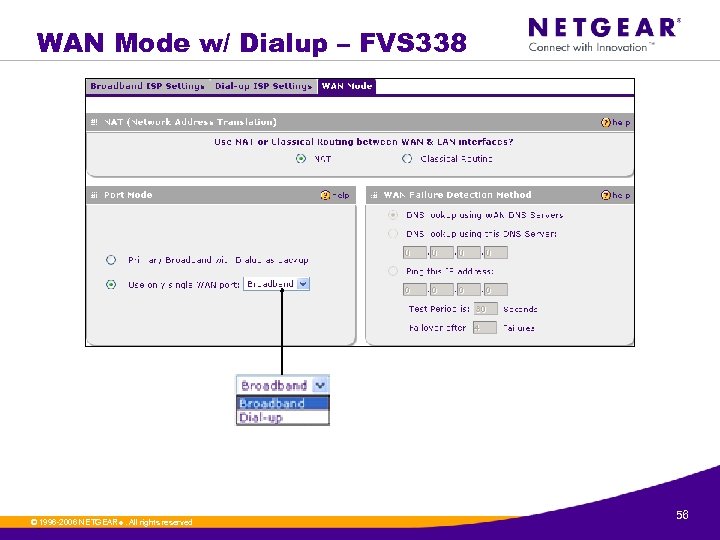
WAN Mode w/ Dialup – FVS 338 © 1996 -2006 NETGEAR ®. All rights reserved. 56
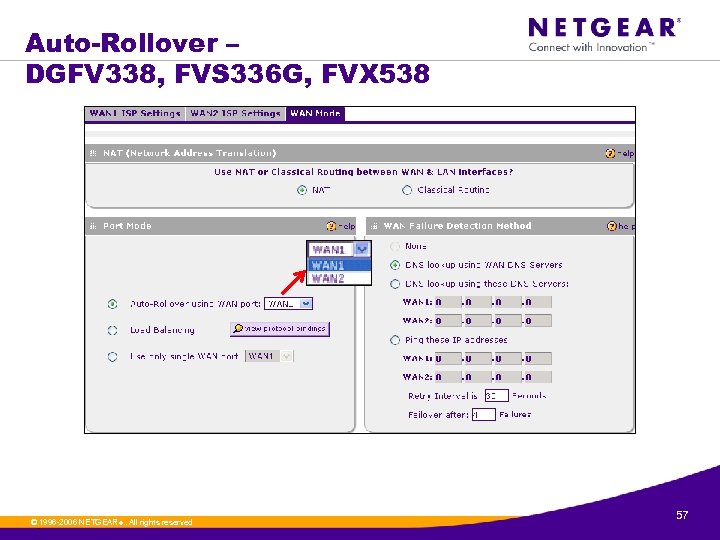
Auto-Rollover – DGFV 338, FVS 336 G, FVX 538 © 1996 -2006 NETGEAR ®. All rights reserved. 57

Auto-Rollover – DGFV 338, FVS 336 G, FVX 538 » If you want to use a redundant ISP link for backup purposes, select the WAN port that will act as the primary link for this mode. Ensure that the backup WAN port has also been configured and that you configure the WAN Failure Detection Method to support Auto-Rollover. » Link failure is detected in one of the following ways: • By sending DNS queries to a DNS server, or • By sending a Ping request to an IP address, or • None (no failure detection is performed). » From each WAN interface, DNS queries or Ping requests are sent to the specified IP address. If replies are not received, after a specified number of retries, the corresponding WAN interface is considered down. » As long as the primary link is up, all traffic is sent over the primary link. Once the primary WAN interface goes down, the rollover link is brought up to send the traffic. Traffic will automatically roll back to the original primary link once the original primary link is back up and running again. © 1996 -2006 NETGEAR ®. All rights reserved. 58
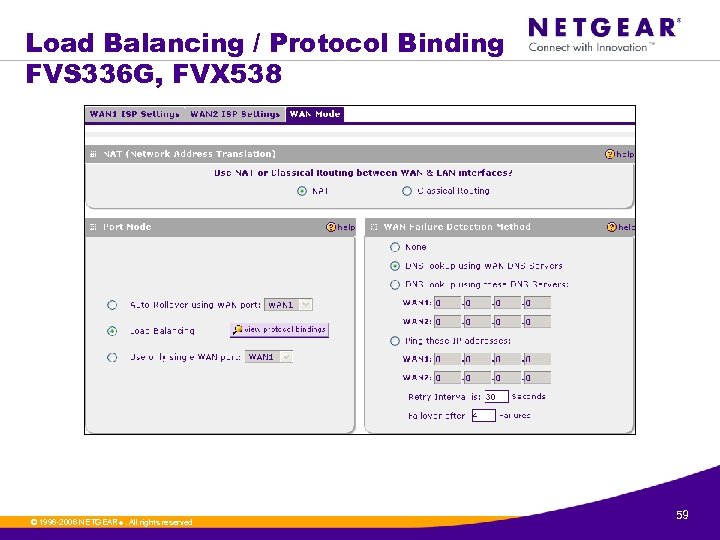
Load Balancing / Protocol Binding FVS 336 G, FVX 538 © 1996 -2006 NETGEAR ®. All rights reserved. 59
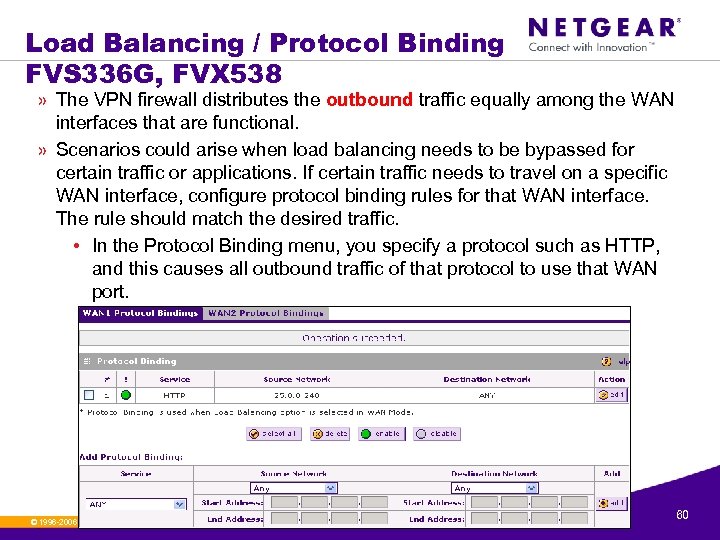
Load Balancing / Protocol Binding FVS 336 G, FVX 538 » The VPN firewall distributes the outbound traffic equally among the WAN interfaces that are functional. » Scenarios could arise when load balancing needs to be bypassed for certain traffic or applications. If certain traffic needs to travel on a specific WAN interface, configure protocol binding rules for that WAN interface. The rule should match the desired traffic. • In the Protocol Binding menu, you specify a protocol such as HTTP, and this causes all outbound traffic of that protocol to use that WAN port. © 1996 -2006 NETGEAR ®. All rights reserved. 60
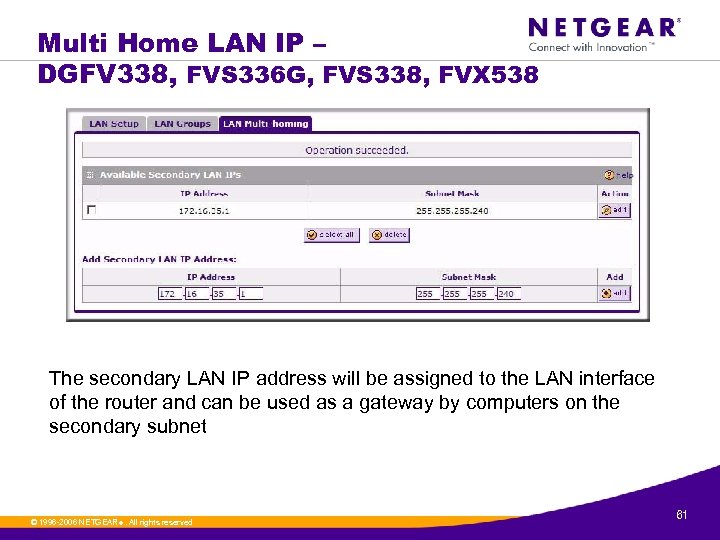
Multi Home LAN IP – DGFV 338, FVS 336 G, FVS 338, FVX 538 The secondary LAN IP address will be assigned to the LAN interface of the router and can be used as a gateway by computers on the secondary subnet © 1996 -2006 NETGEAR ®. All rights reserved. 61
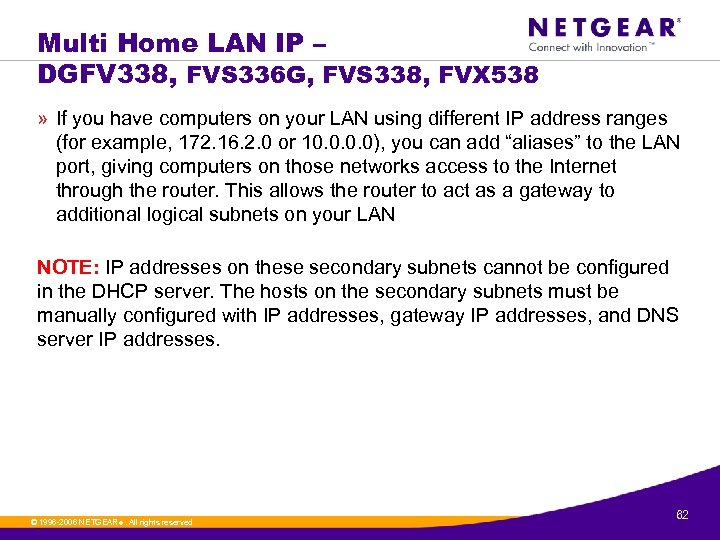
Multi Home LAN IP – DGFV 338, FVS 336 G, FVS 338, FVX 538 » If you have computers on your LAN using different IP address ranges (for example, 172. 16. 2. 0 or 10. 0), you can add “aliases” to the LAN port, giving computers on those networks access to the Internet through the router. This allows the router to act as a gateway to additional logical subnets on your LAN NOTE: IP addresses on these secondary subnets cannot be configured in the DHCP server. The hosts on the secondary subnets must be manually configured with IP addresses, gateway IP addresses, and DNS server IP addresses. © 1996 -2006 NETGEAR ®. All rights reserved. 62
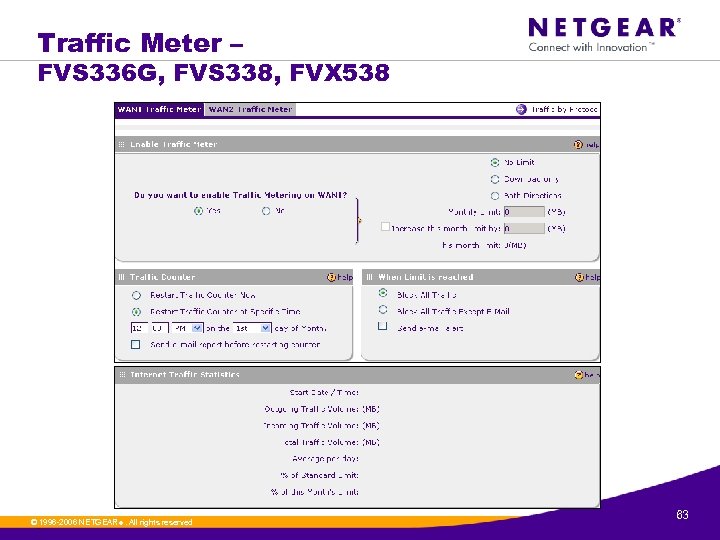
Traffic Meter – FVS 336 G, FVS 338, FVX 538 © 1996 -2006 NETGEAR ®. All rights reserved. 63
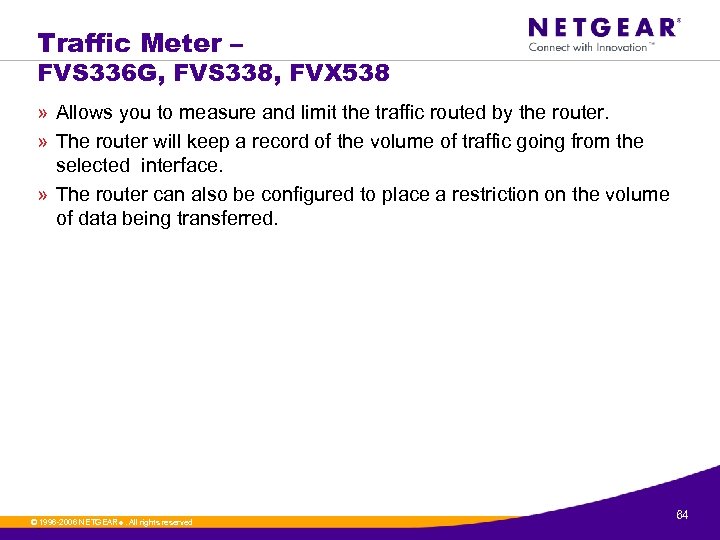
Traffic Meter – FVS 336 G, FVS 338, FVX 538 » Allows you to measure and limit the traffic routed by the router. » The router will keep a record of the volume of traffic going from the selected interface. » The router can also be configured to place a restriction on the volume of data being transferred. © 1996 -2006 NETGEAR ®. All rights reserved. 64
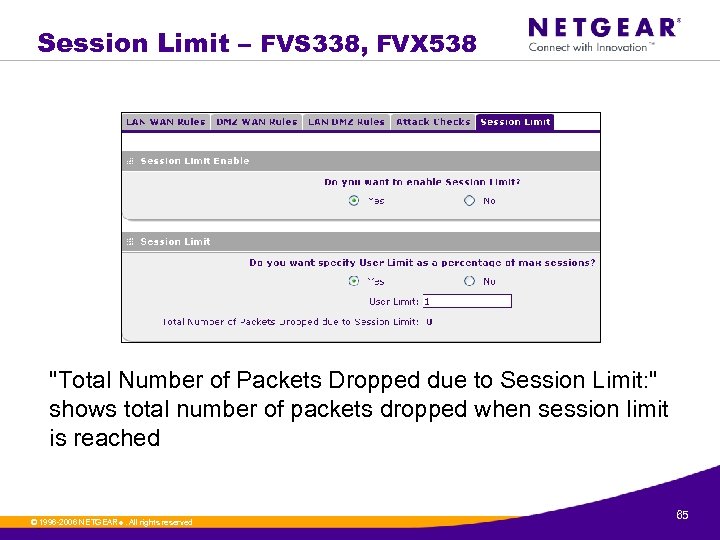
Session Limit – FVS 338, FVX 538 "Total Number of Packets Dropped due to Session Limit: " shows total number of packets dropped when session limit is reached © 1996 -2006 NETGEAR ®. All rights reserved. 65
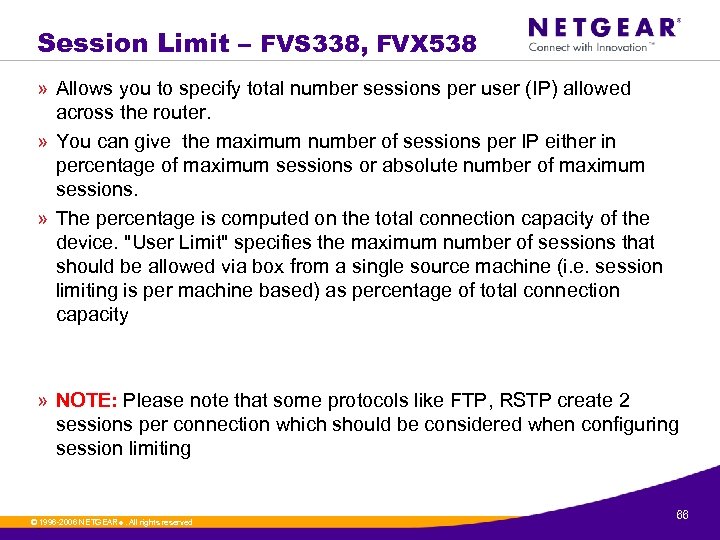
Session Limit – FVS 338, FVX 538 » Allows you to specify total number sessions per user (IP) allowed across the router. » You can give the maximum number of sessions per IP either in percentage of maximum sessions or absolute number of maximum sessions. » The percentage is computed on the total connection capacity of the device. "User Limit" specifies the maximum number of sessions that should be allowed via box from a single source machine (i. e. session limiting is per machine based) as percentage of total connection capacity » NOTE: Please note that some protocols like FTP, RSTP create 2 sessions per connection which should be considered when configuring session limiting © 1996 -2006 NETGEAR ®. All rights reserved. 66
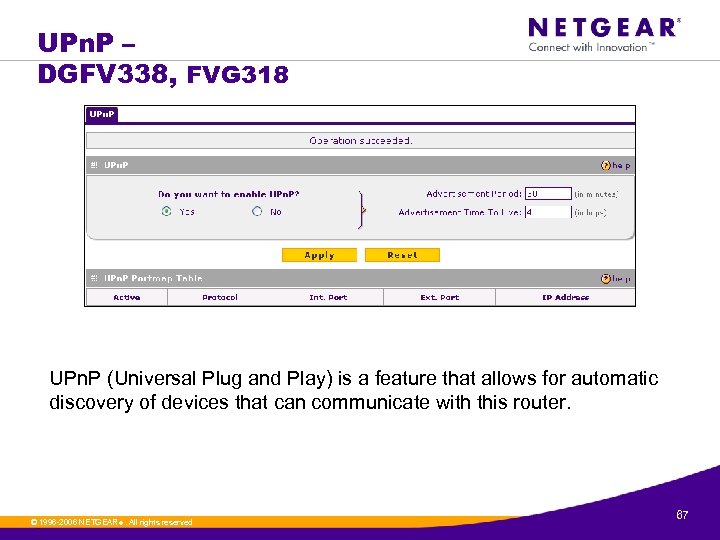
UPn. P – DGFV 338, FVG 318 UPn. P (Universal Plug and Play) is a feature that allows for automatic discovery of devices that can communicate with this router. © 1996 -2006 NETGEAR ®. All rights reserved. 67

Firewall Features
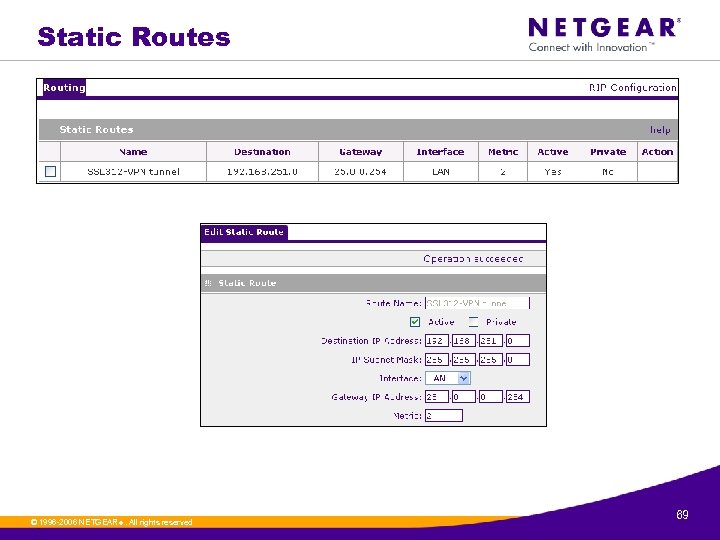
Static Routes © 1996 -2006 NETGEAR ®. All rights reserved. 69
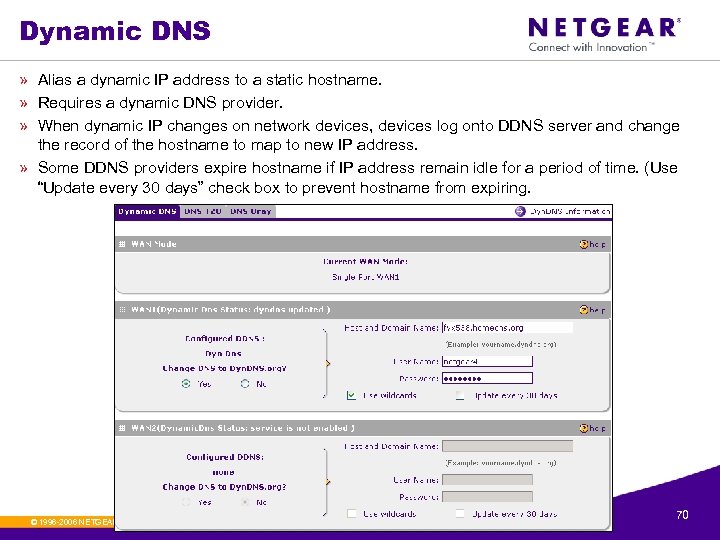
Dynamic DNS » Alias a dynamic IP address to a static hostname. » Requires a dynamic DNS provider. » When dynamic IP changes on network devices, devices log onto DDNS server and change the record of the hostname to map to new IP address. » Some DDNS providers expire hostname if IP address remain idle for a period of time. (Use “Update every 30 days” check box to prevent hostname from expiring. © 1996 -2006 NETGEAR ®. All rights reserved. 70
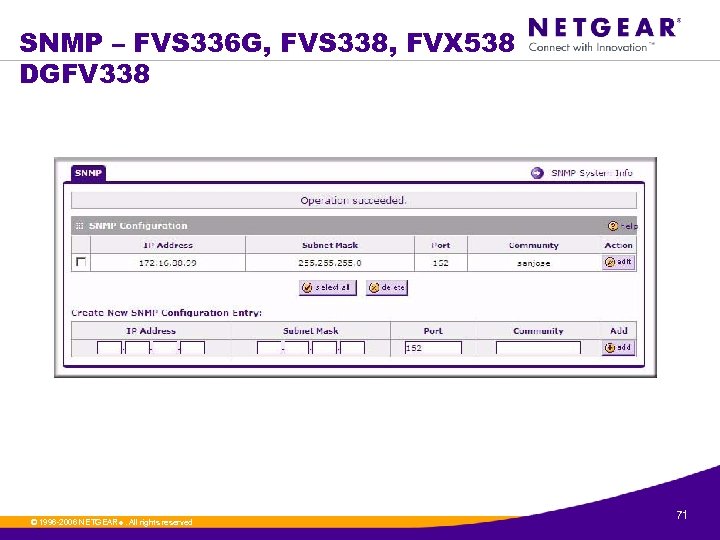
SNMP – FVS 336 G, FVS 338, FVX 538 DGFV 338 © 1996 -2006 NETGEAR ®. All rights reserved. 71
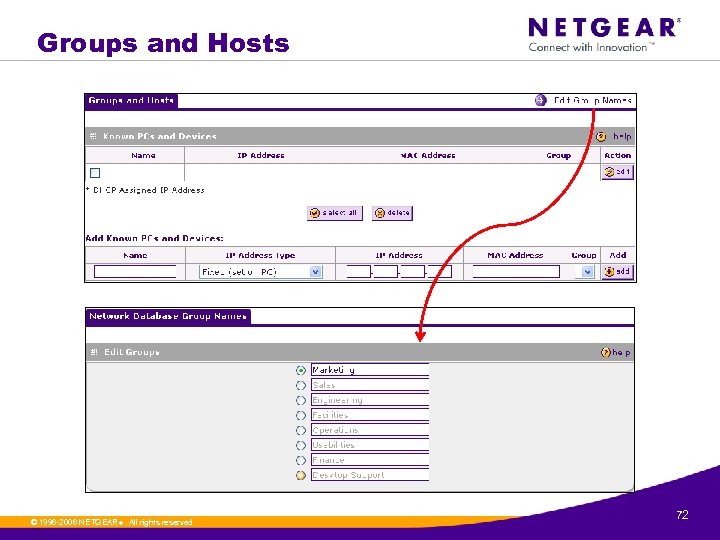
Groups and Hosts © 1996 -2006 NETGEAR ®. All rights reserved. 72
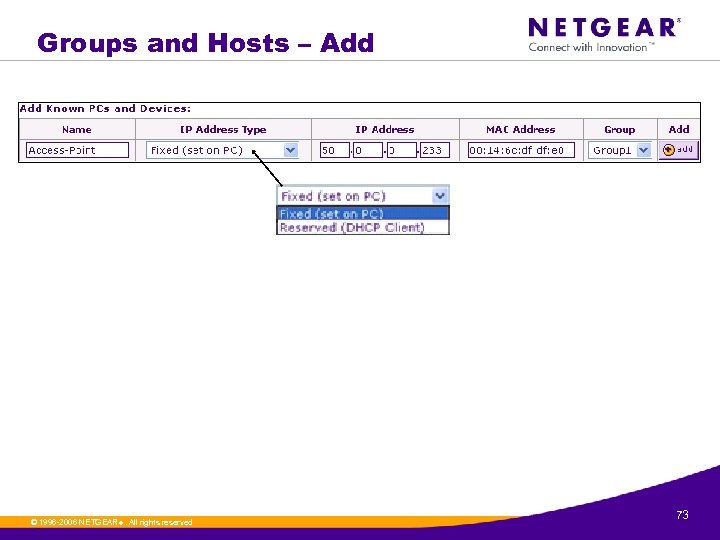
Groups and Hosts – Add © 1996 -2006 NETGEAR ®. All rights reserved. 73
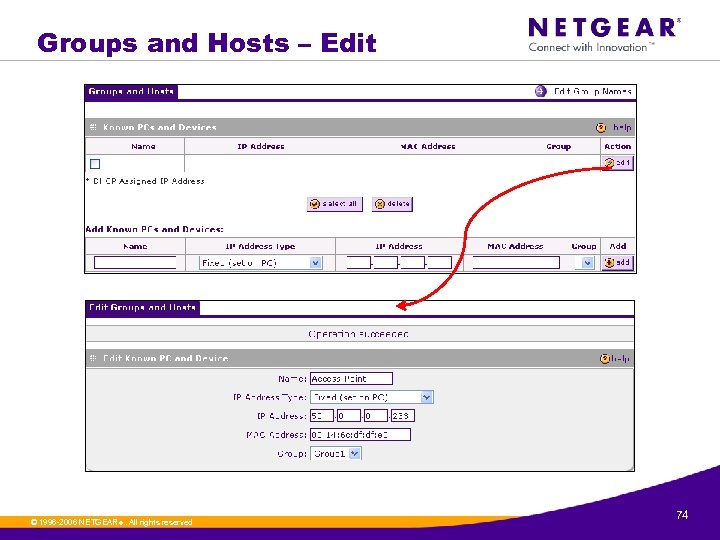
Groups and Hosts – Edit © 1996 -2006 NETGEAR ®. All rights reserved. 74
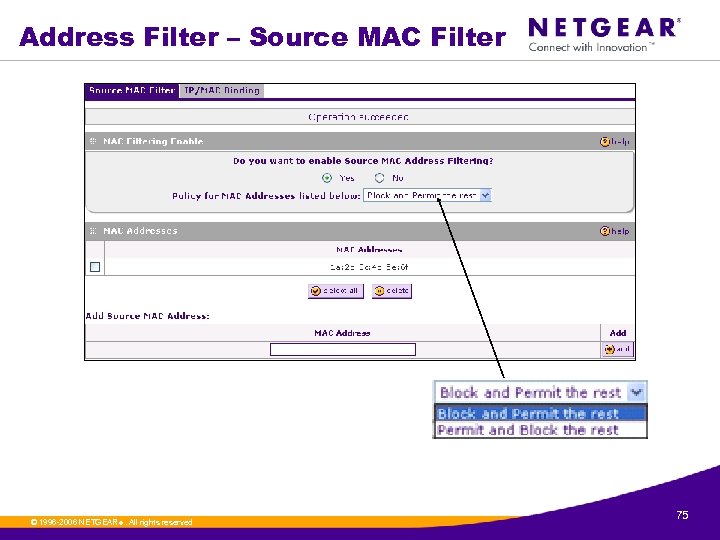
Address Filter – Source MAC Filter © 1996 -2006 NETGEAR ®. All rights reserved. 75
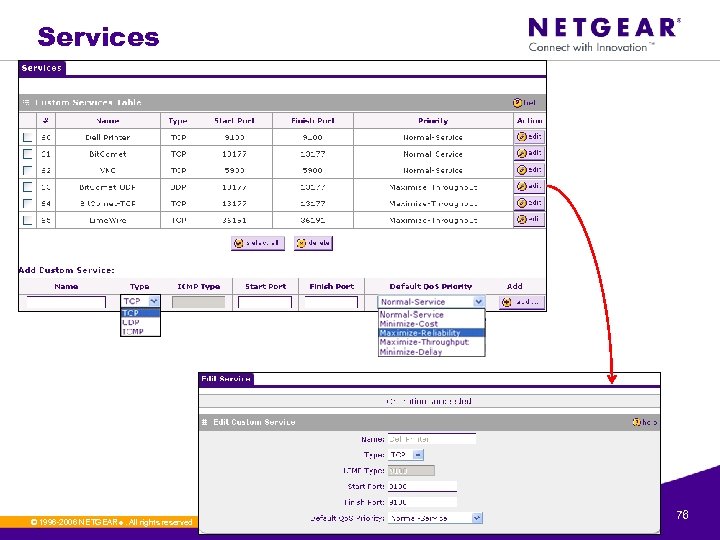
Services © 1996 -2006 NETGEAR ®. All rights reserved. 76
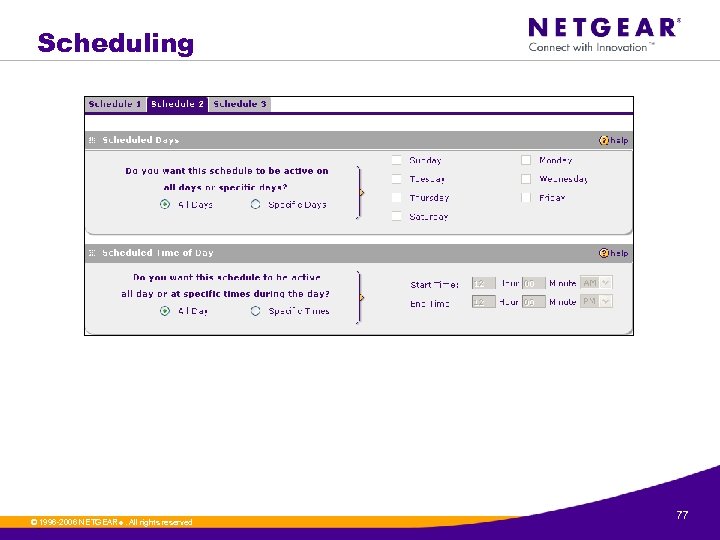
Scheduling © 1996 -2006 NETGEAR ®. All rights reserved. 77
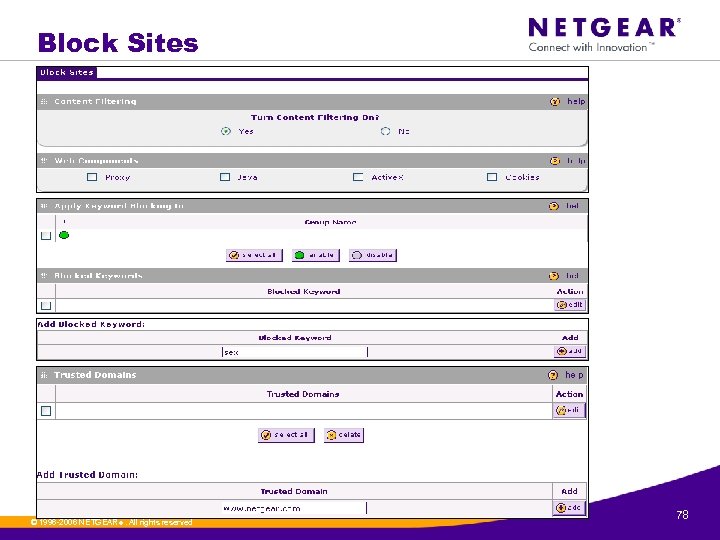
Block Sites © 1996 -2006 NETGEAR ®. All rights reserved. 78
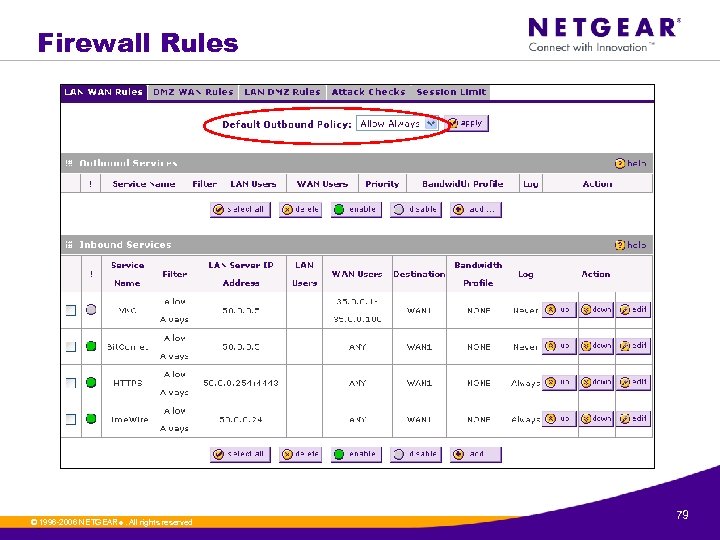
Firewall Rules © 1996 -2006 NETGEAR ®. All rights reserved. 79
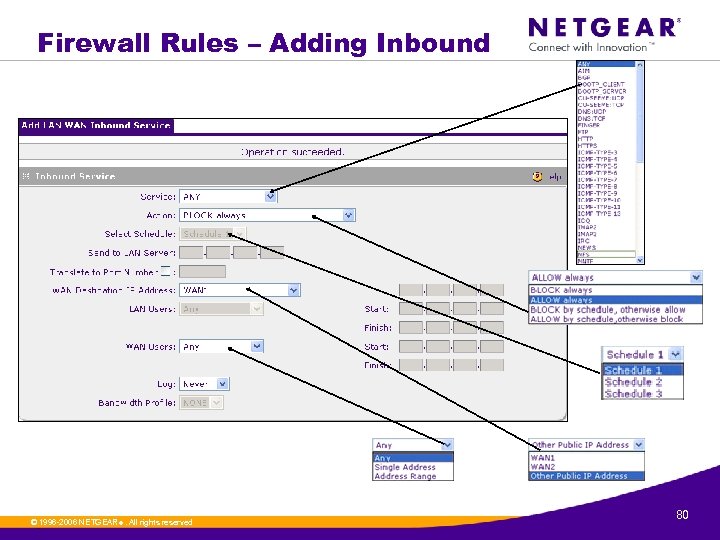
Firewall Rules – Adding Inbound © 1996 -2006 NETGEAR ®. All rights reserved. 80
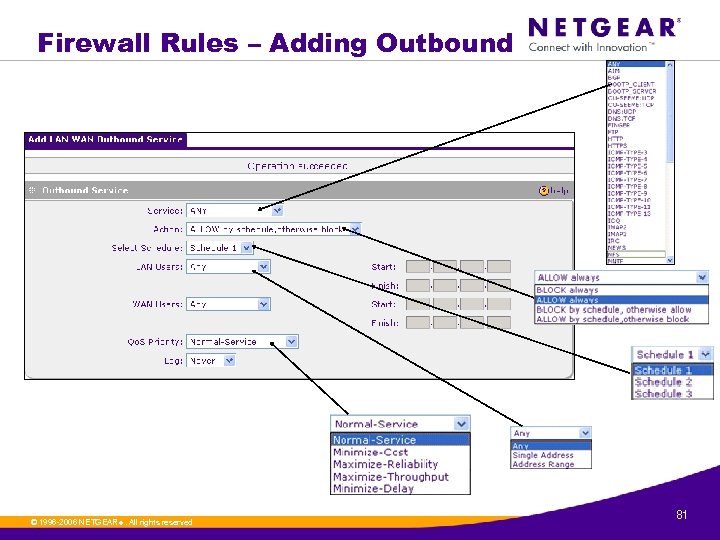
Firewall Rules – Adding Outbound © 1996 -2006 NETGEAR ®. All rights reserved. 81
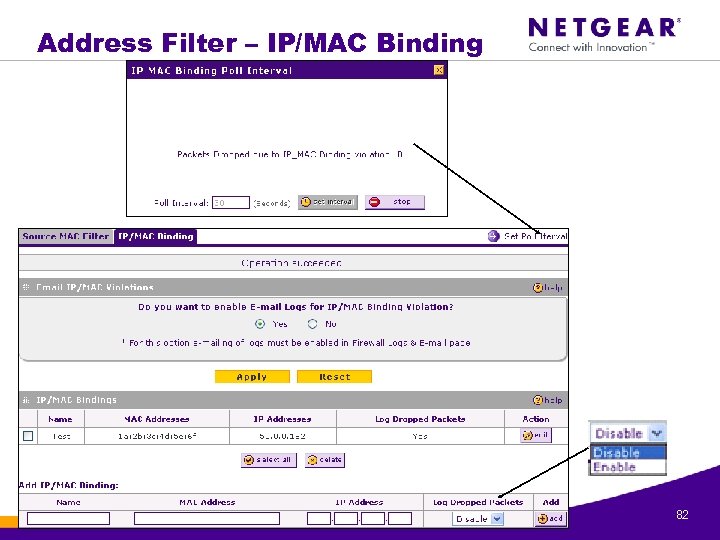
Address Filter – IP/MAC Binding © 1996 -2006 NETGEAR ®. All rights reserved. 82
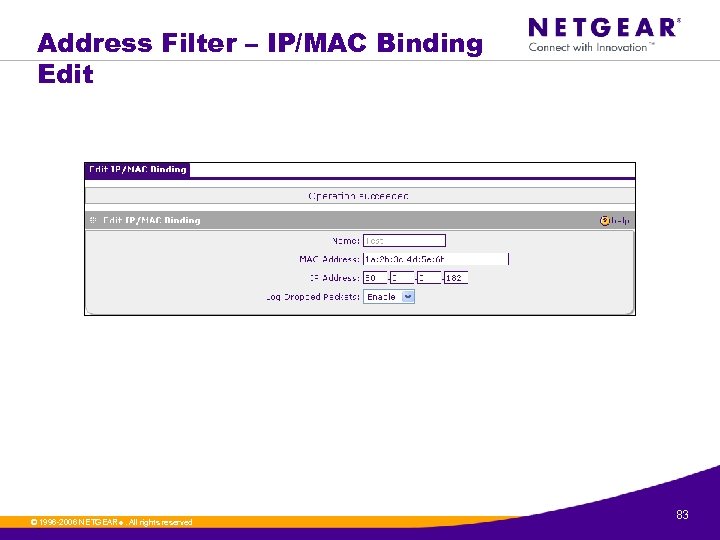
Address Filter – IP/MAC Binding Edit © 1996 -2006 NETGEAR ®. All rights reserved. 83
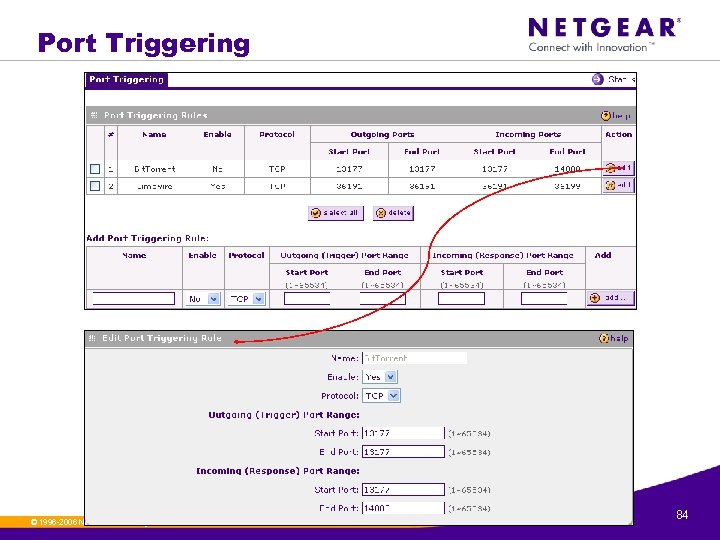
Port Triggering © 1996 -2006 NETGEAR ®. All rights reserved. 84
Port Triggering Once configured, operation is as follows: 1. A PC makes an outgoing connection using a port number defined in the Port Triggering table. 2. This Router records this connection, opens the INCOMING port or ports associated with this entry in the Port Triggering table, and associates them with the PC. 3. The remote system receives the PCs request, and responds using a different port number. 4. This Router matches the response to the previous request, and forwards the response to the PC. (Without Port Triggering, this response would be treated as a new connection request rather than a response. As such, it would be handled in accordance with the Port Forwarding rules. ) © 1996 -2006 NETGEAR ®. All rights reserved. 85
Port Triggering Note: » Only 1 PC can use a "Port Triggering" application at any time. » After a PC has finished using a "Port Triggering" application, there is a "Time-out" period before the application can be used by another PC. This is required because this Router cannot be sure when the application has terminated. » Normally for games and chat. © 1996 -2006 NETGEAR ®. All rights reserved. 86
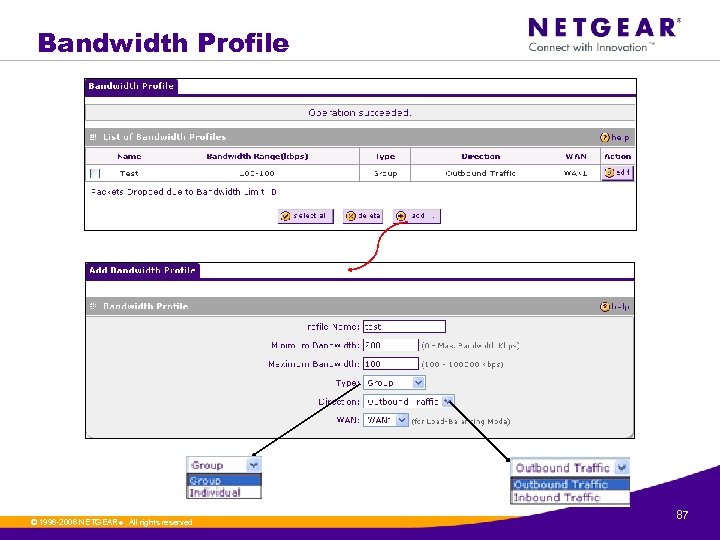
Bandwidth Profile © 1996 -2006 NETGEAR ®. All rights reserved. 87
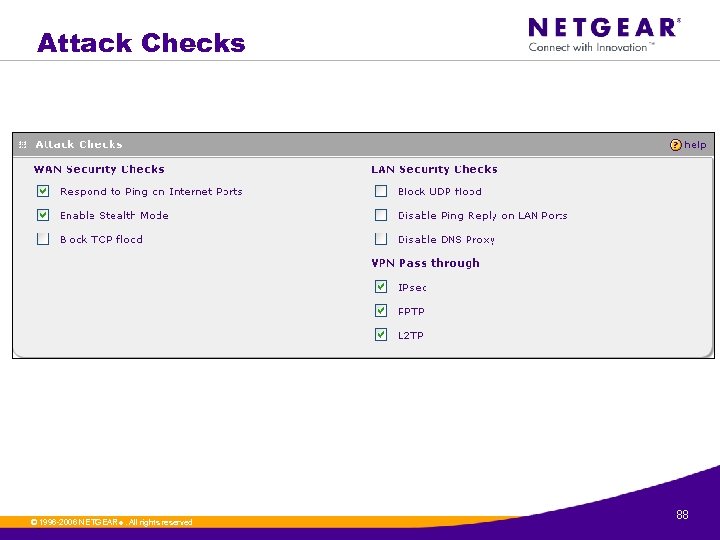
Attack Checks © 1996 -2006 NETGEAR ®. All rights reserved. 88
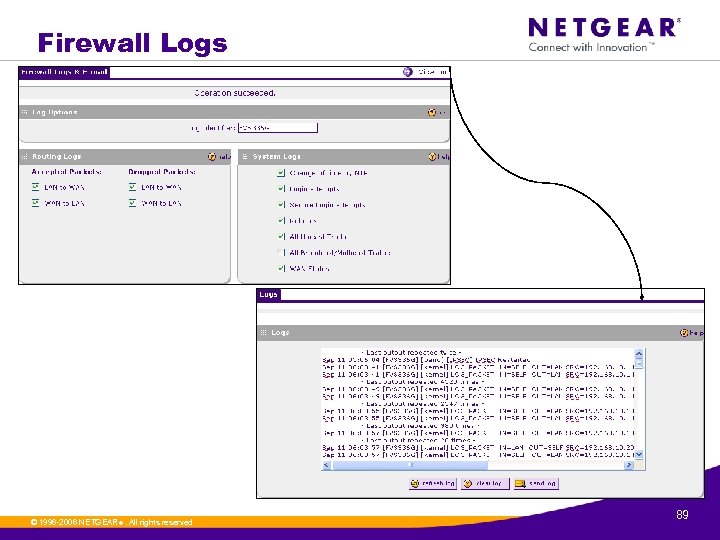
Firewall Logs © 1996 -2006 NETGEAR ®. All rights reserved. 89
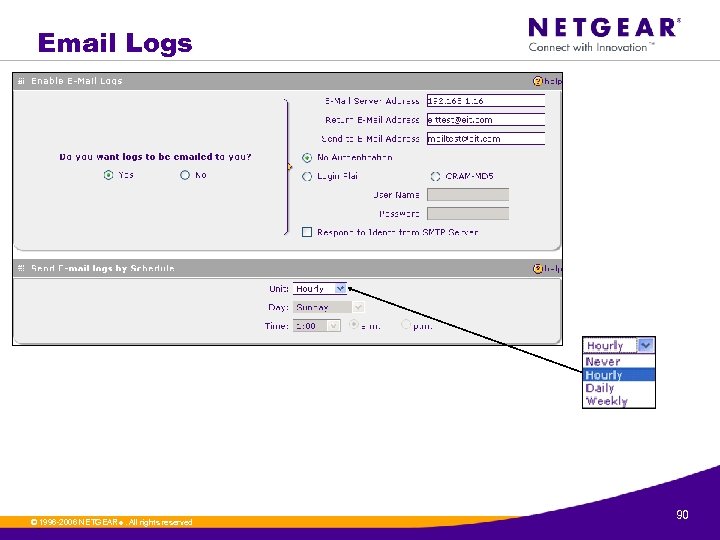
Email Logs © 1996 -2006 NETGEAR ®. All rights reserved. 90
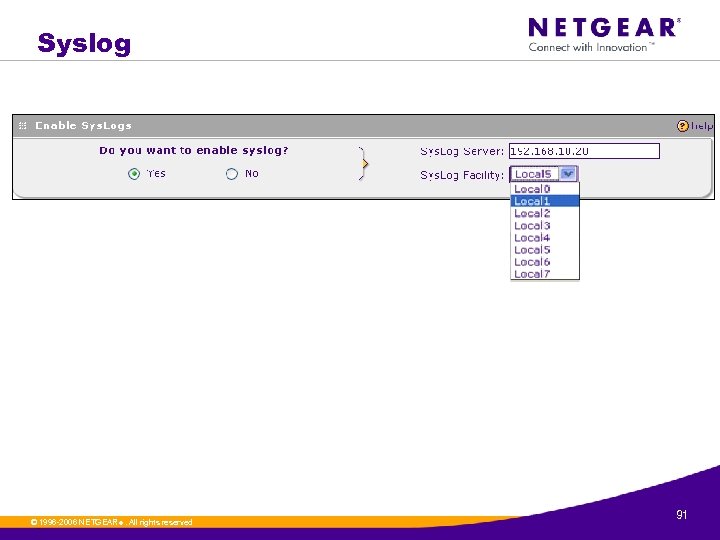
Syslog © 1996 -2006 NETGEAR ®. All rights reserved. 91

VPN Logs © 1996 -2006 NETGEAR ®. All rights reserved. 92

Troubleshooting Features
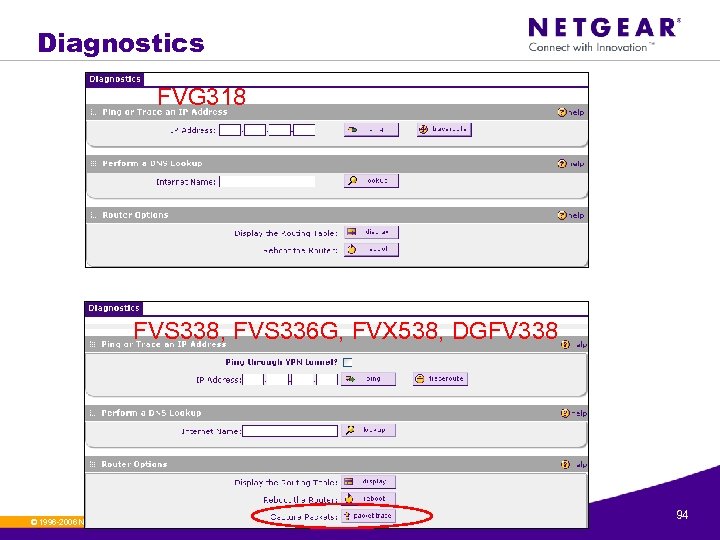
Diagnostics FVG 318 FVS 338, FVS 336 G, FVX 538, DGFV 338 © 1996 -2006 NETGEAR ®. All rights reserved. 94

Diagnostics – Packets Capture © 1996 -2006 NETGEAR ®. All rights reserved. 95

VPN Features
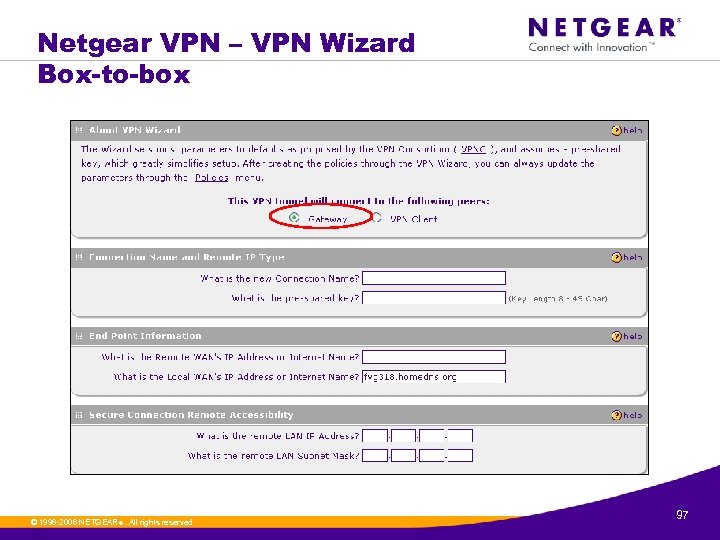
Netgear VPN – VPN Wizard Box-to-box © 1996 -2006 NETGEAR ®. All rights reserved. 97
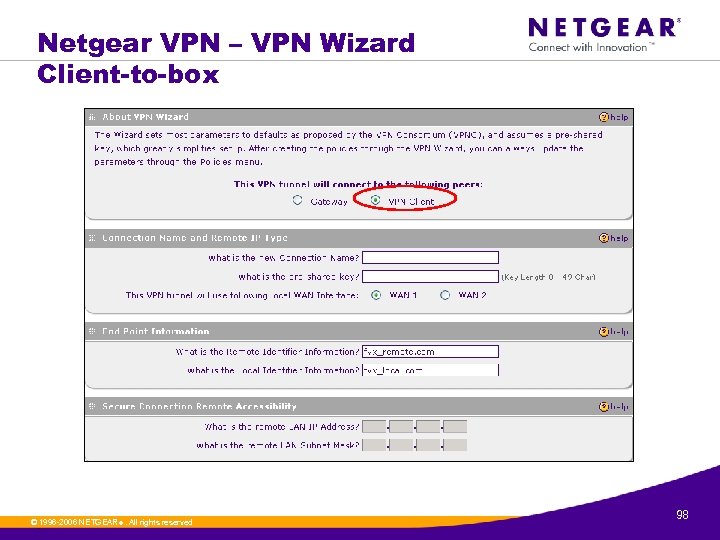
Netgear VPN – VPN Wizard Client-to-box © 1996 -2006 NETGEAR ®. All rights reserved. 98
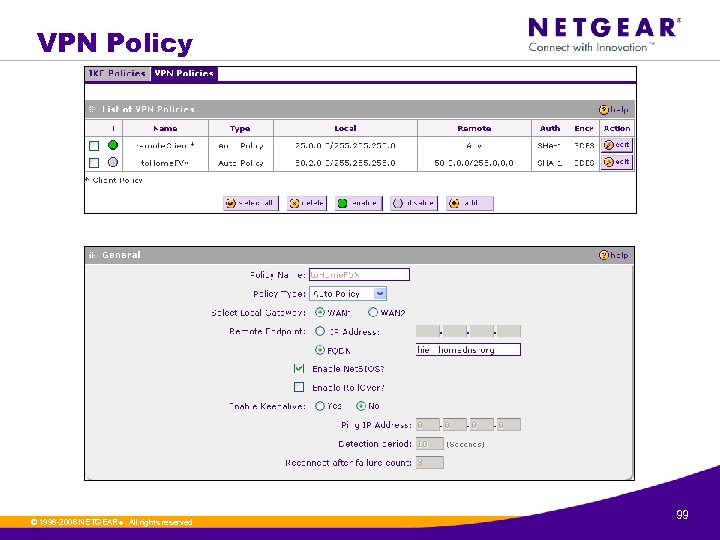
VPN Policy © 1996 -2006 NETGEAR ®. All rights reserved. 99
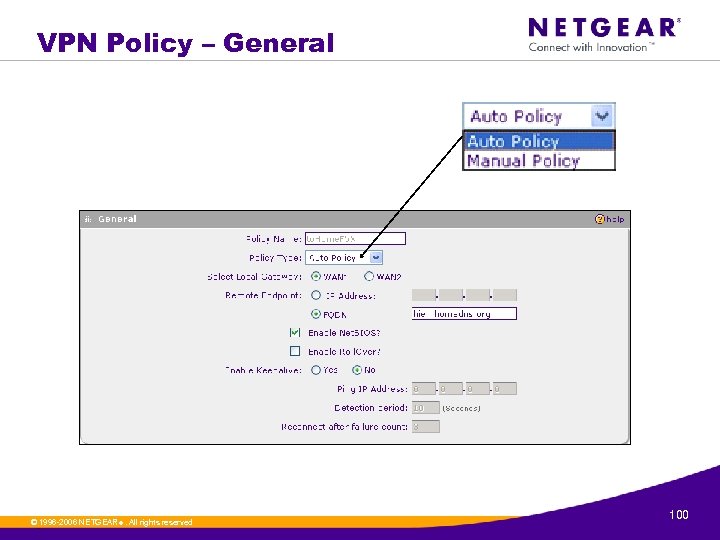
VPN Policy – General © 1996 -2006 NETGEAR ®. All rights reserved. 100
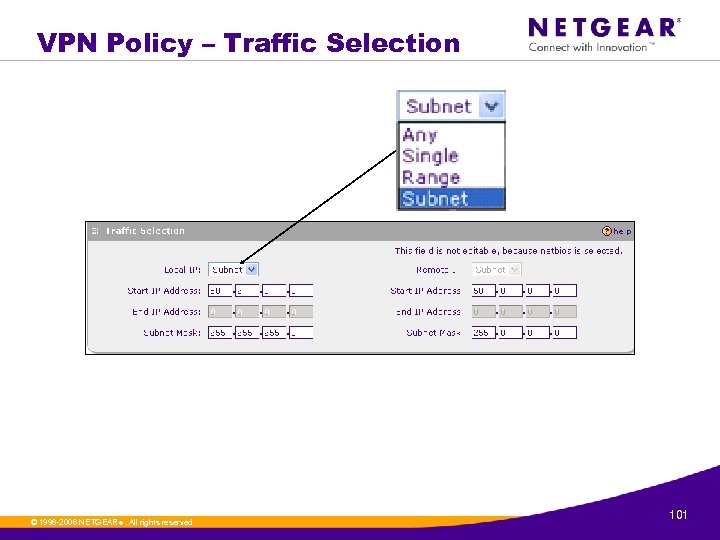
VPN Policy – Traffic Selection © 1996 -2006 NETGEAR ®. All rights reserved. 101
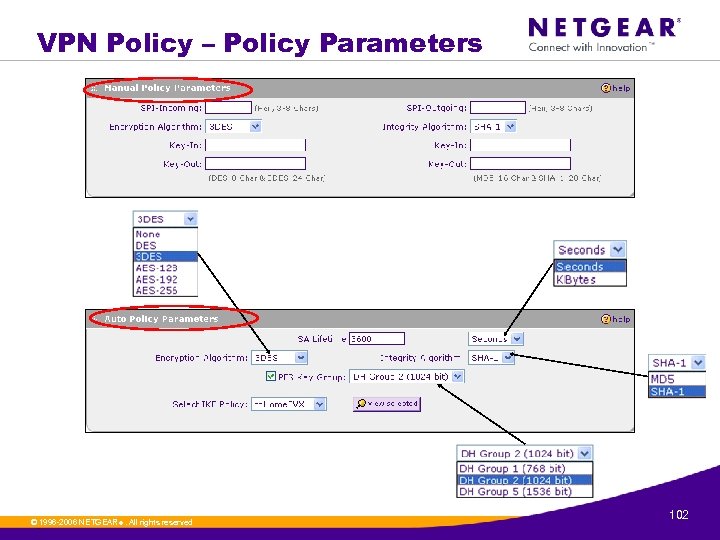
VPN Policy – Policy Parameters © 1996 -2006 NETGEAR ®. All rights reserved. 102
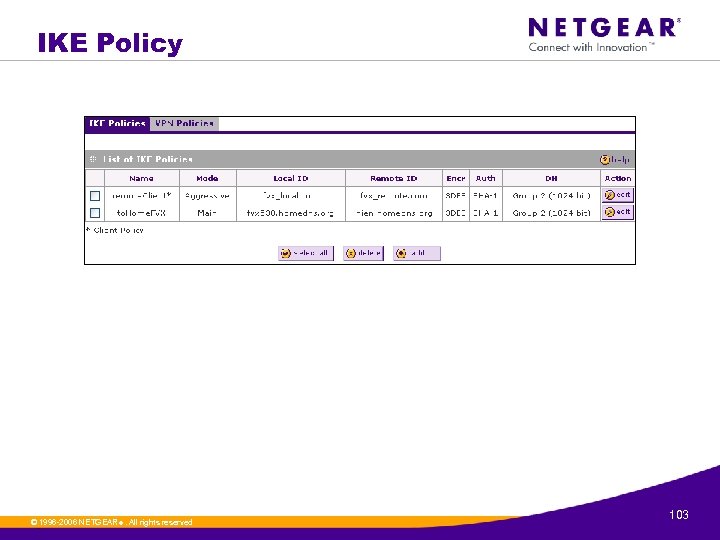
IKE Policy © 1996 -2006 NETGEAR ®. All rights reserved. 103
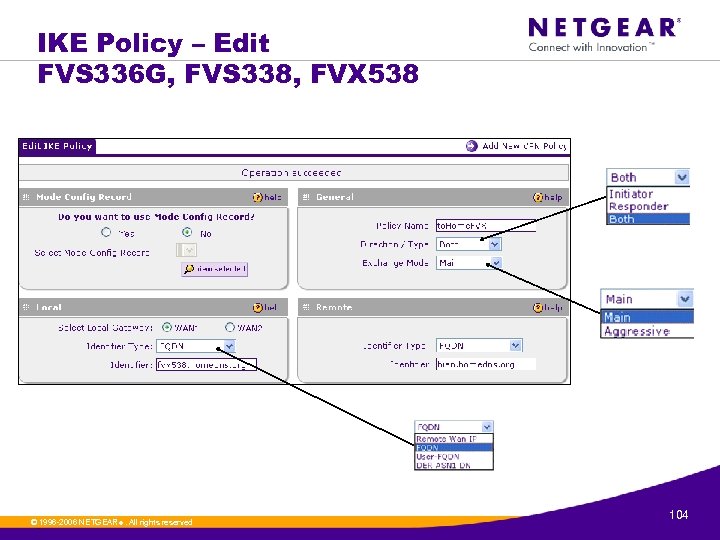
IKE Policy – Edit FVS 336 G, FVS 338, FVX 538 © 1996 -2006 NETGEAR ®. All rights reserved. 104
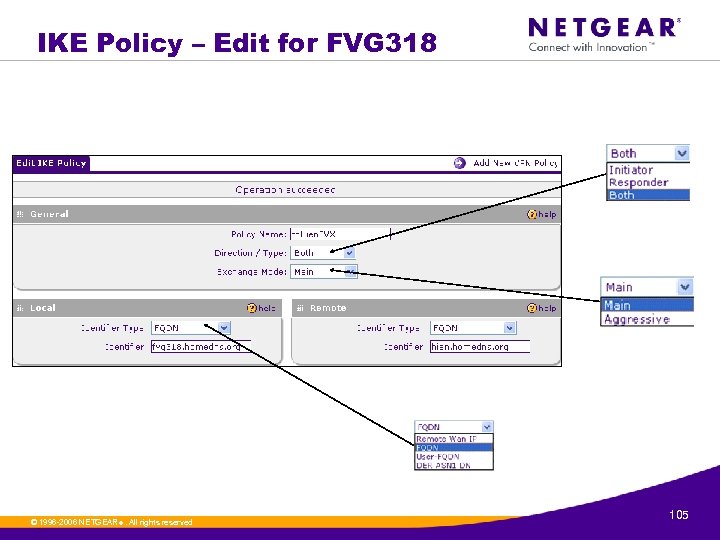
IKE Policy – Edit for FVG 318 © 1996 -2006 NETGEAR ®. All rights reserved. 105
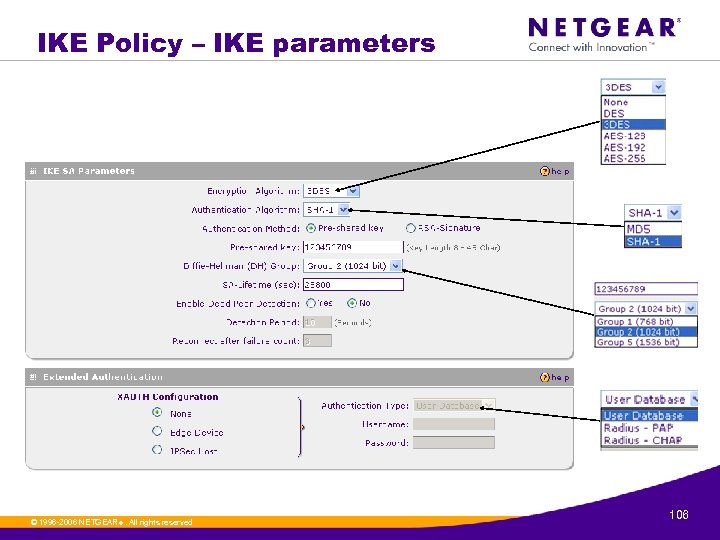
IKE Policy – IKE parameters © 1996 -2006 NETGEAR ®. All rights reserved. 106
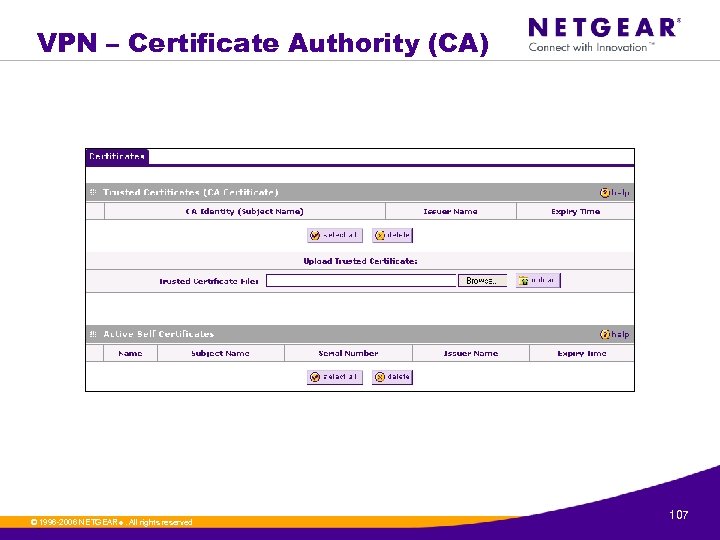
VPN – Certificate Authority (CA) © 1996 -2006 NETGEAR ®. All rights reserved. 107
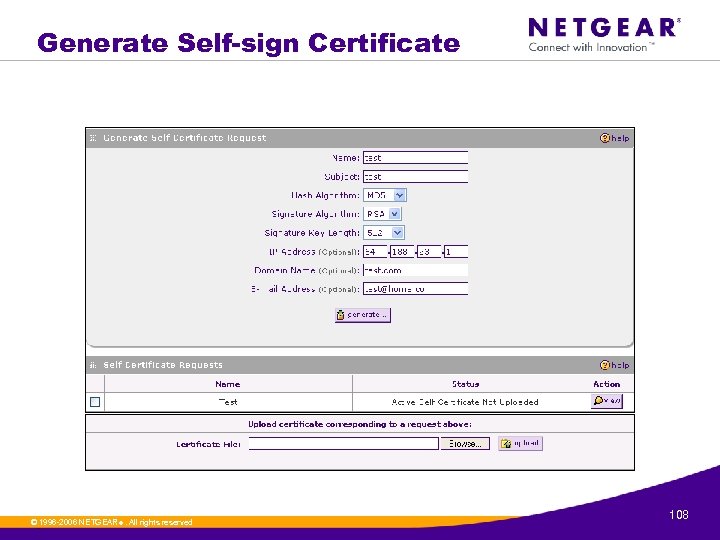
Generate Self-sign Certificate © 1996 -2006 NETGEAR ®. All rights reserved. 108
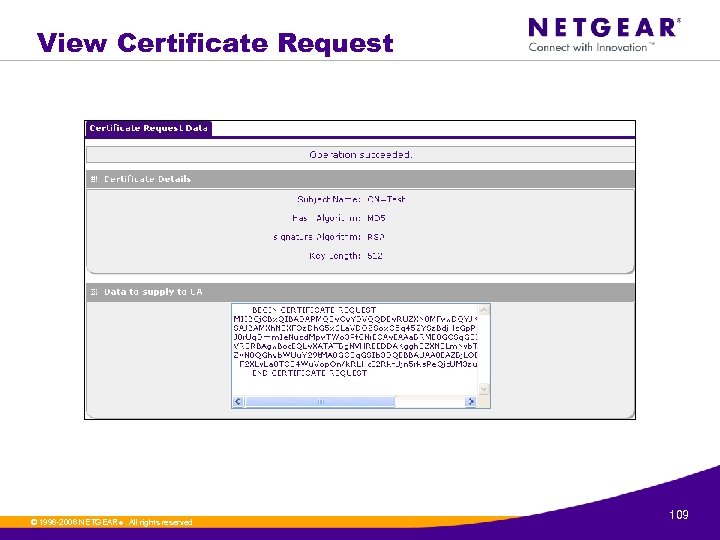
View Certificate Request © 1996 -2006 NETGEAR ®. All rights reserved. 109
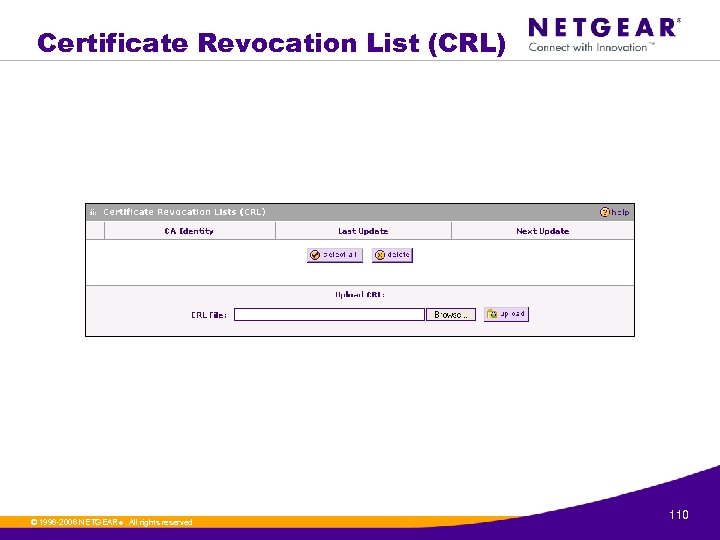
Certificate Revocation List (CRL) © 1996 -2006 NETGEAR ®. All rights reserved. 110
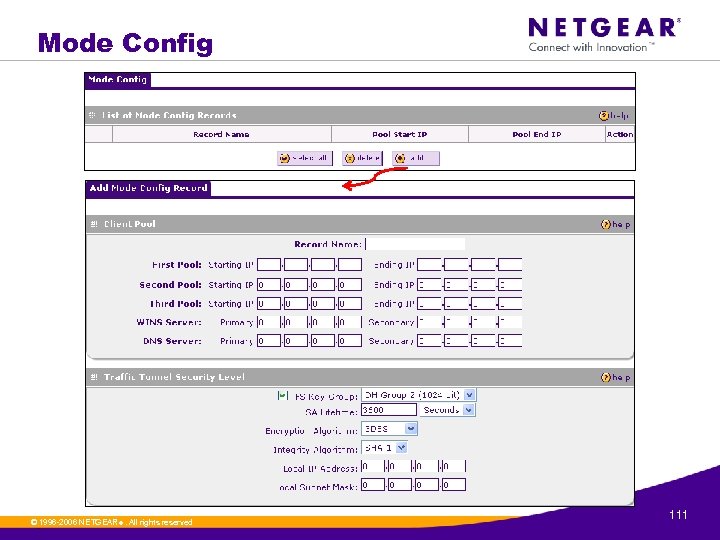
Mode Config © 1996 -2006 NETGEAR ®. All rights reserved. 111
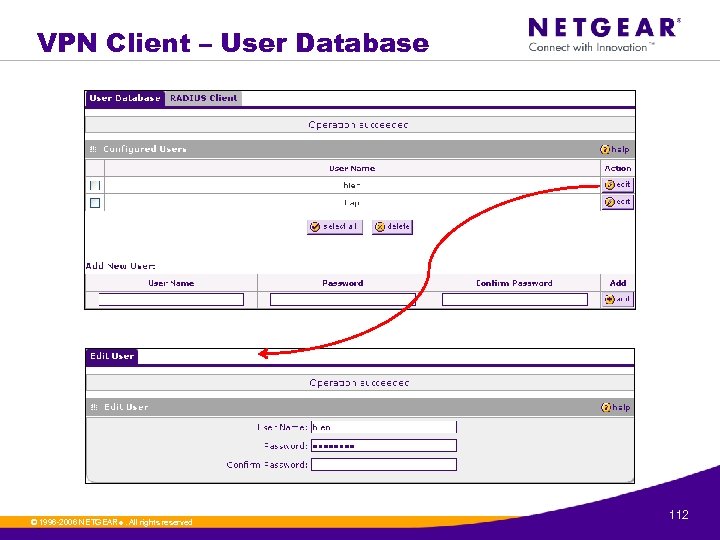
VPN Client – User Database © 1996 -2006 NETGEAR ®. All rights reserved. 112
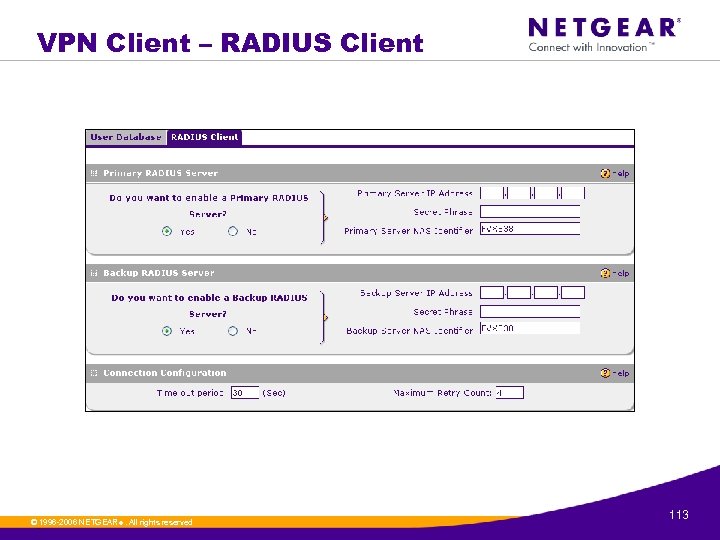
VPN Client – RADIUS Client © 1996 -2006 NETGEAR ®. All rights reserved. 113

VPN 01 L_VPN 05 L Pro. Safe VPN Client Software
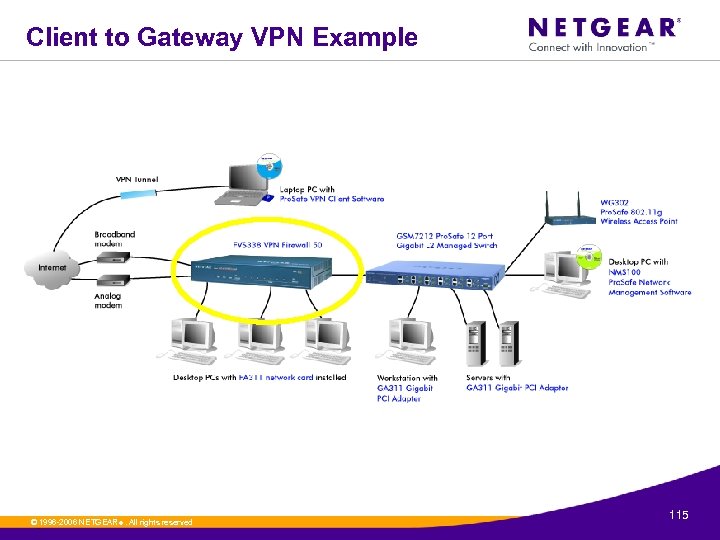
Client to Gateway VPN Example © 1996 -2006 NETGEAR ®. All rights reserved. 115
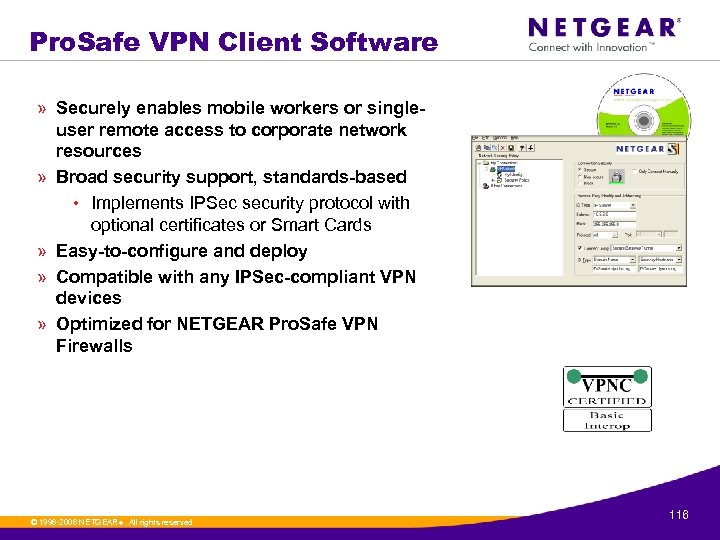
Pro. Safe VPN Client Software » Securely enables mobile workers or singleuser remote access to corporate network resources » Broad security support, standards-based • Implements IPSec security protocol with optional certificates or Smart Cards » Easy-to-configure and deploy » Compatible with any IPSec-compliant VPN devices » Optimized for NETGEAR Pro. Safe VPN Firewalls © 1996 -2006 NETGEAR ®. All rights reserved. 116
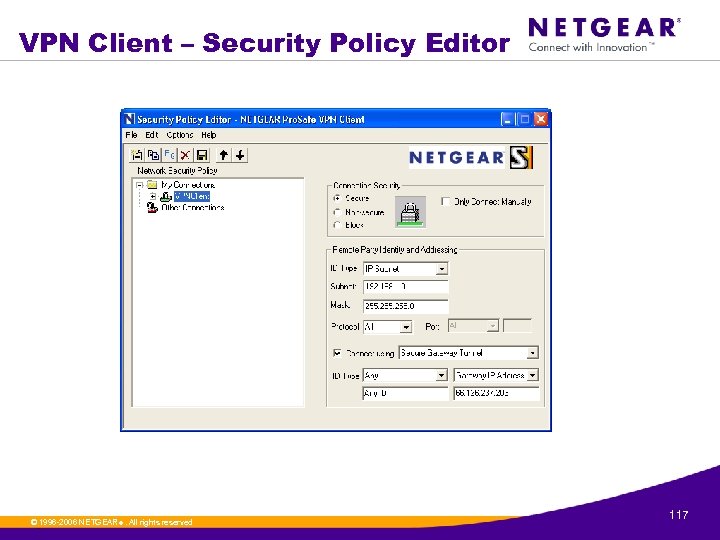
VPN Client – Security Policy Editor © 1996 -2006 NETGEAR ®. All rights reserved. 117
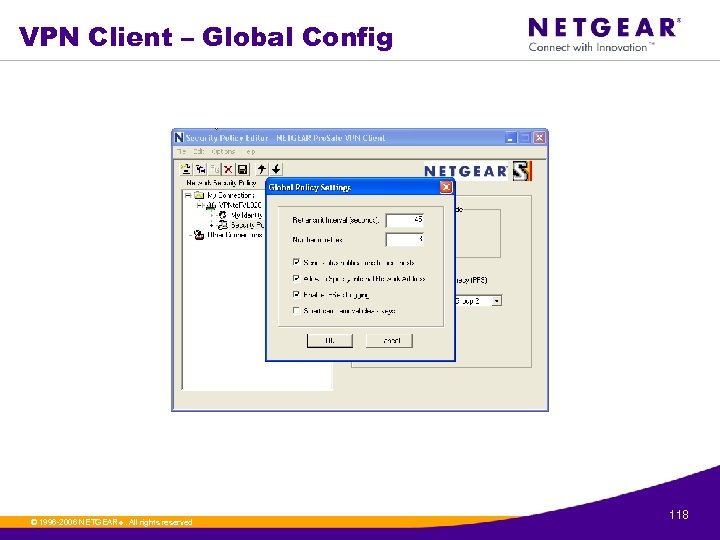
VPN Client – Global Config © 1996 -2006 NETGEAR ®. All rights reserved. 118
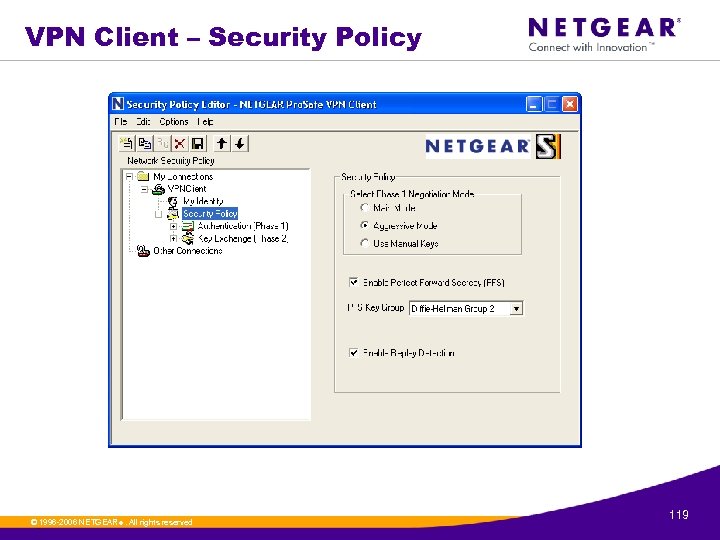
VPN Client – Security Policy © 1996 -2006 NETGEAR ®. All rights reserved. 119
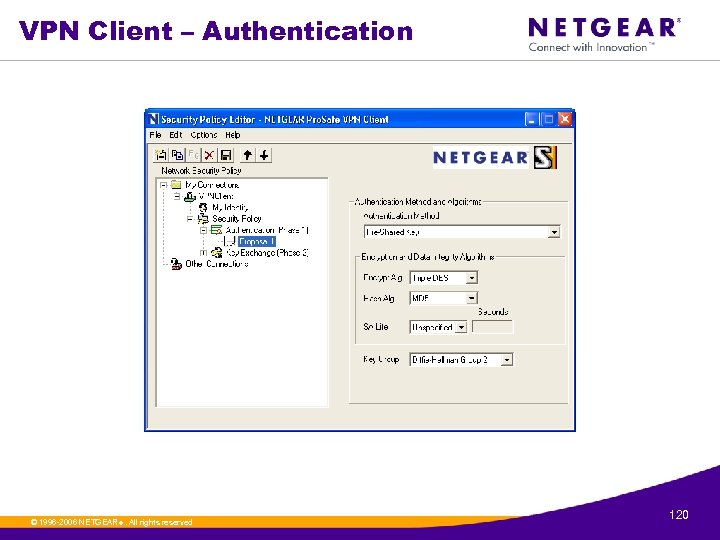
VPN Client – Authentication © 1996 -2006 NETGEAR ®. All rights reserved. 120
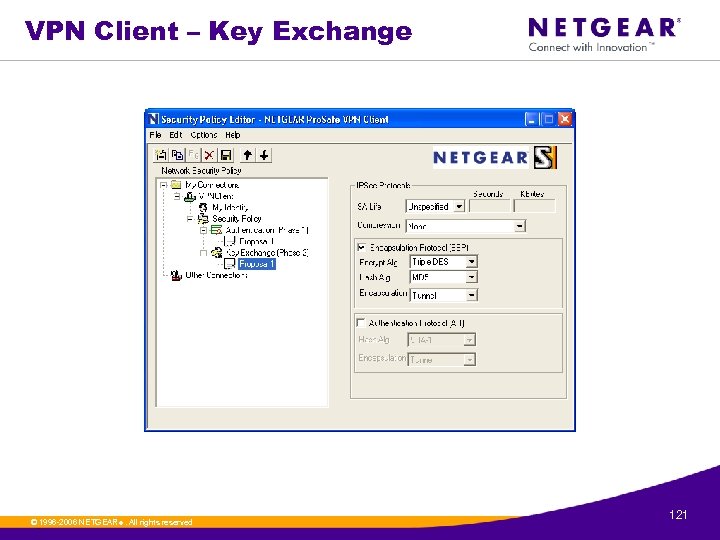
VPN Client – Key Exchange © 1996 -2006 NETGEAR ®. All rights reserved. 121
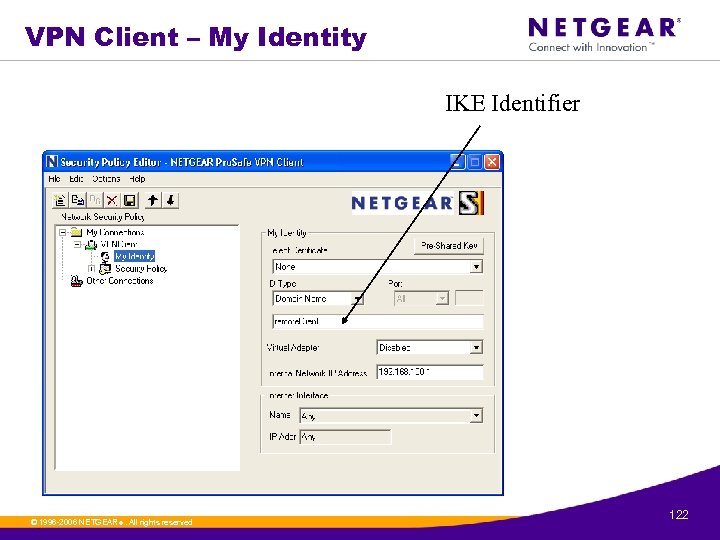
VPN Client – My Identity IKE Identifier © 1996 -2006 NETGEAR ®. All rights reserved. 122
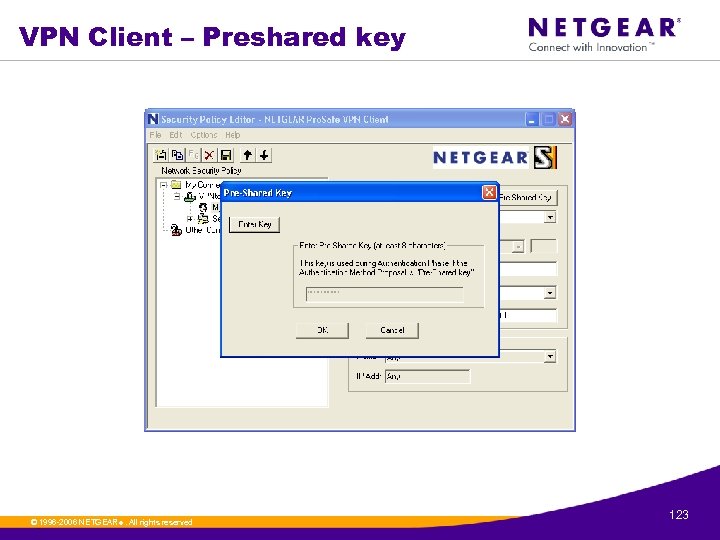
VPN Client – Preshared key © 1996 -2006 NETGEAR ®. All rights reserved. 123
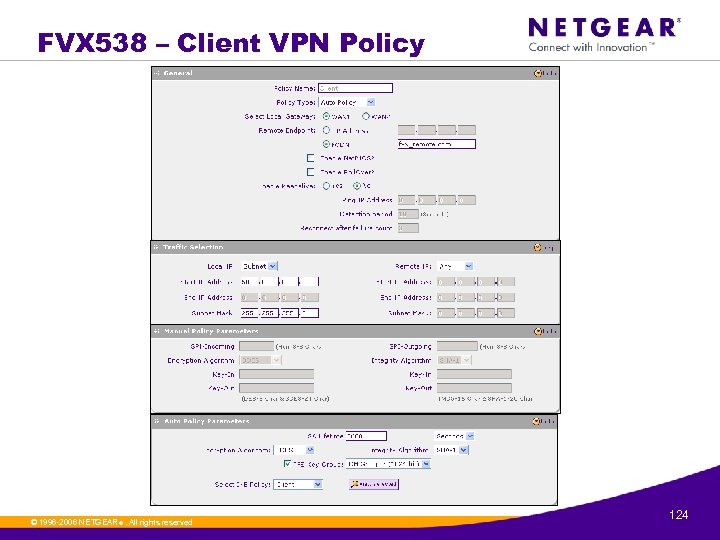
FVX 538 – Client VPN Policy © 1996 -2006 NETGEAR ®. All rights reserved. 124
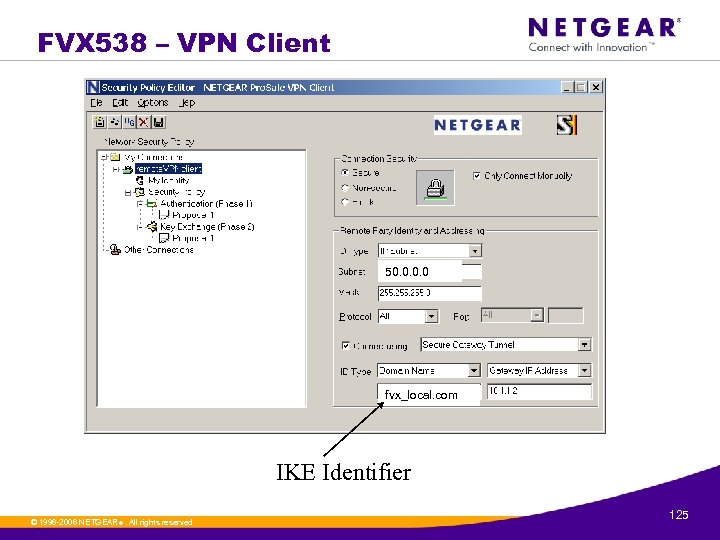
FVX 538 – VPN Client 50. 0 fvx_local. com IKE Identifier © 1996 -2006 NETGEAR ®. All rights reserved. 125
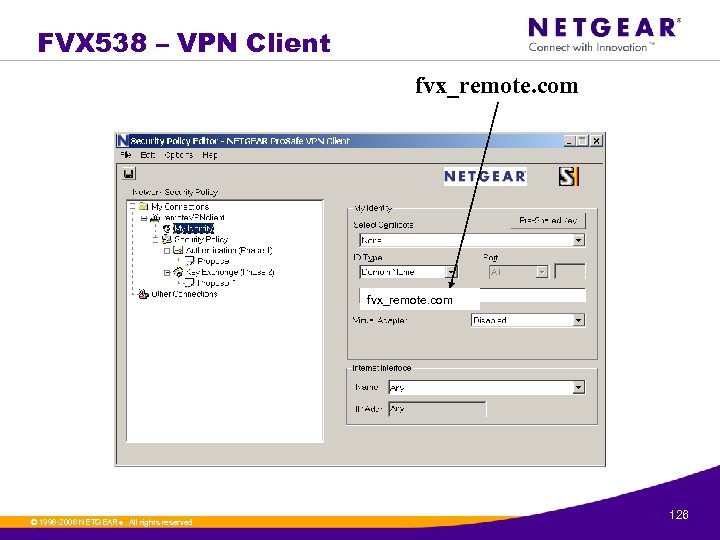
FVX 538 – VPN Client fvx_remote. com © 1996 -2006 NETGEAR ®. All rights reserved. 126
Exercise Set up the following two scenario
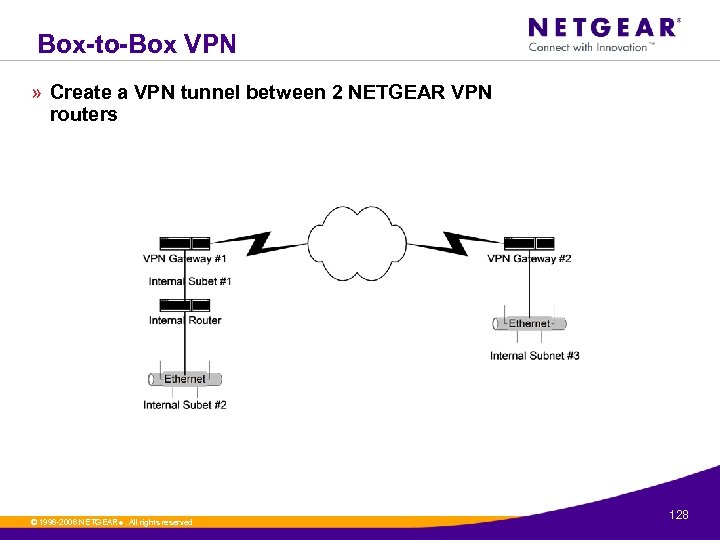
Box-to-Box VPN » Create a VPN tunnel between 2 NETGEAR VPN routers © 1996 -2006 NETGEAR ®. All rights reserved. 128
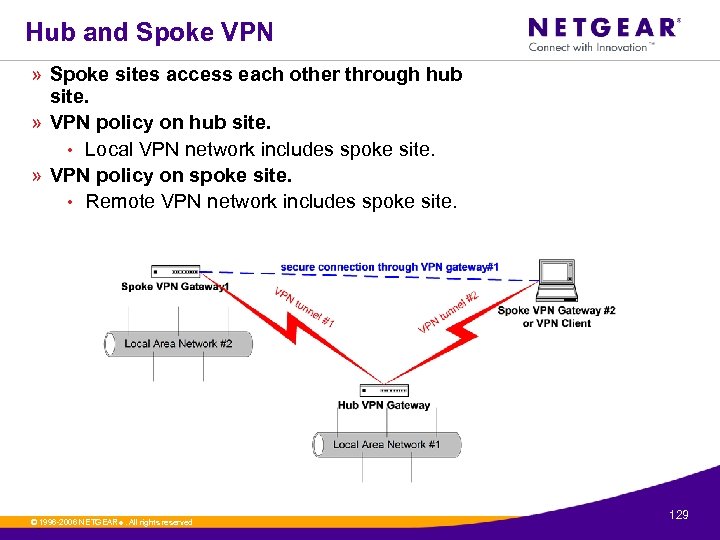
Hub and Spoke VPN » Spoke sites access each other through hub site. » VPN policy on hub site. • Local VPN network includes spoke site. » VPN policy on spoke site. • Remote VPN network includes spoke site. © 1996 -2006 NETGEAR ®. All rights reserved. 129

VPN Troubleshooting » Can the other VPN end point reach you? • What is the remote VPN endpoint? » FQDN: resolve to remote WAN IP? » IP Address: Is IP address reachable? » 0. 0: VPN uses aggressive mode? » Do the VPN parameters matches on both endpoints? • What are the remote/local IKE identities? » Do they match the remote endpoint’s local/remote IKE identities? • What are the local/remote VPN networks? » Do they match remote endpoint’s remote/local VPN networks? • What is the pre-shared key? » Does it match the remote endpoint’s pre-shared key? • What are the encryption/authentication algorithms? » Do they match the remote endpoint’s algorithms? • What is the IKE mode (main/aggressive)? » Does it match the remote endpoint’s IKE mode? © 1996 -2006 NETGEAR ®. All rights reserved. 130
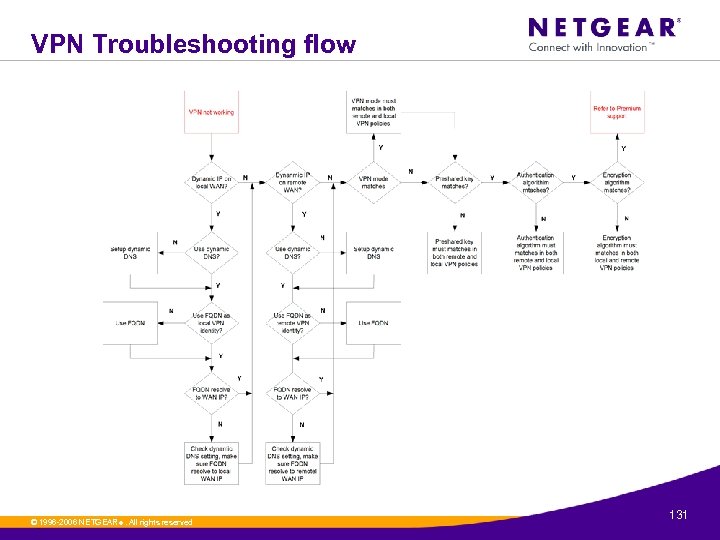
VPN Troubleshooting flow © 1996 -2006 NETGEAR ®. All rights reserved. 131

Questions & Answers © 1996 -2006 NETGEAR ®. All rights reserved. 132
5ef9c7b364eb2e32f7f4e073b23a6e8a.ppt