9e9784e04e50c9ef561c41acbfaf3c1e.ppt
- Количество слайдов: 140
 Net Security: . A Tutorial Ravi Mukkamala Department of Computer Science Old Dominion University Norfolk, Virginia, USA mukka@cs. odu. edu 3/17/201 8 1
Net Security: . A Tutorial Ravi Mukkamala Department of Computer Science Old Dominion University Norfolk, Virginia, USA mukka@cs. odu. edu 3/17/201 8 1
 Organization Introduction ◦ Security ◦. NET Framework Security Features Identities , Principals & Impersonation ASP. NET Security with IIS Authentication Authorization Summary Resources 3/17/201 8 2
Organization Introduction ◦ Security ◦. NET Framework Security Features Identities , Principals & Impersonation ASP. NET Security with IIS Authentication Authorization Summary Resources 3/17/201 8 2
 Security Considerations Consider the following when designing an application: Impersonation Security goals Security risks Authentication Authorization Securing Data Transmission 3/17/201 8 Delegation Operating system security Securing physical access Code access security 3
Security Considerations Consider the following when designing an application: Impersonation Security goals Security risks Authentication Authorization Securing Data Transmission 3/17/201 8 Delegation Operating system security Securing physical access Code access security 3
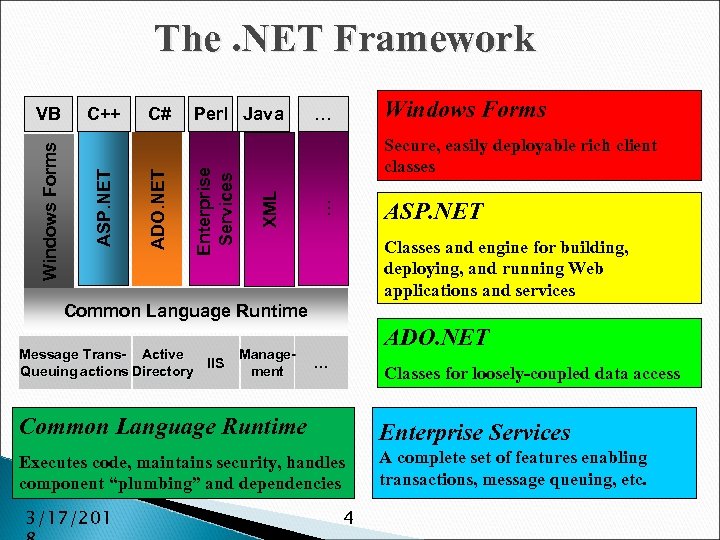 The. NET Framework Perl Java Windows Forms … Secure, easily deployable rich client classes ASP. NET … XML Enterprise Services C# ADO. NET C++ ASP. NET Windows Forms VB Classes and engine for building, deploying, and running Web applications and services Common Language Runtime Message Trans- Active IIS Queuing actions Directory Management ADO. NET … Classes for loosely-coupled data access Common Language Runtime Enterprise Services Executes code, maintains security, handles component “plumbing” and dependencies A complete set of features enabling transactions, message queuing, etc. 3/17/201 4
The. NET Framework Perl Java Windows Forms … Secure, easily deployable rich client classes ASP. NET … XML Enterprise Services C# ADO. NET C++ ASP. NET Windows Forms VB Classes and engine for building, deploying, and running Web applications and services Common Language Runtime Message Trans- Active IIS Queuing actions Directory Management ADO. NET … Classes for loosely-coupled data access Common Language Runtime Enterprise Services Executes code, maintains security, handles component “plumbing” and dependencies A complete set of features enabling transactions, message queuing, etc. 3/17/201 4
 CLR Security Design Goals Provide a robust security system for partially-trusted, mobile code Make it easy to: ◦ Express fine- grained authorizations ◦ Extend & customize the system ◦ Perform security checks in user code No end-user UI! ◦ Never ask a user to make a security decision “on the fly” 3/17/201 8 5
CLR Security Design Goals Provide a robust security system for partially-trusted, mobile code Make it easy to: ◦ Express fine- grained authorizations ◦ Extend & customize the system ◦ Perform security checks in user code No end-user UI! ◦ Never ask a user to make a security decision “on the fly” 3/17/201 8 5
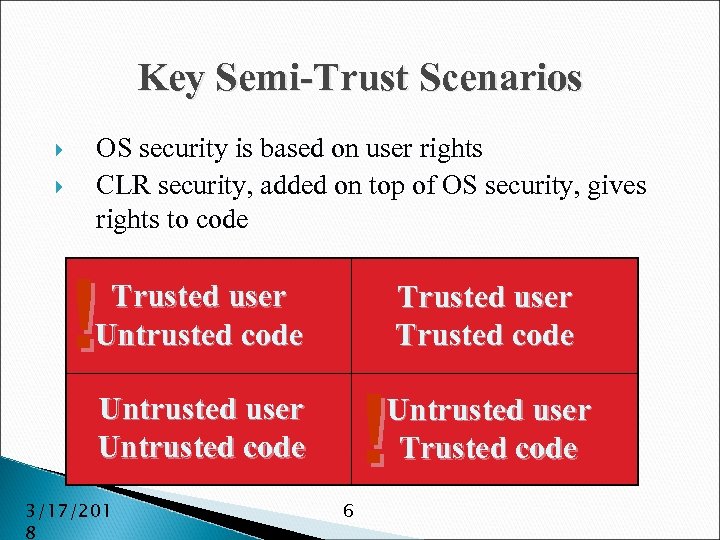 Key Semi-Trust Scenarios OS security is based on user rights CLR security, added on top of OS security, gives rights to code ! Trusted user Untrusted code Trusted user Trusted code ! Untrusted user Untrusted code 3/17/201 8 Untrusted user Trusted code 6
Key Semi-Trust Scenarios OS security is based on user rights CLR security, added on top of OS security, gives rights to code ! Trusted user Untrusted code Trusted user Trusted code ! Untrusted user Untrusted code 3/17/201 8 Untrusted user Trusted code 6
 . NET Managed Execution Security The. NET Framework security features ◦ Assist you in developing secure applications ◦ Include many components, including: Type Checker Exception Manager Security Engine ◦ Complement Windows Security 3/17/201 8 7
. NET Managed Execution Security The. NET Framework security features ◦ Assist you in developing secure applications ◦ Include many components, including: Type Checker Exception Manager Security Engine ◦ Complement Windows Security 3/17/201 8 7
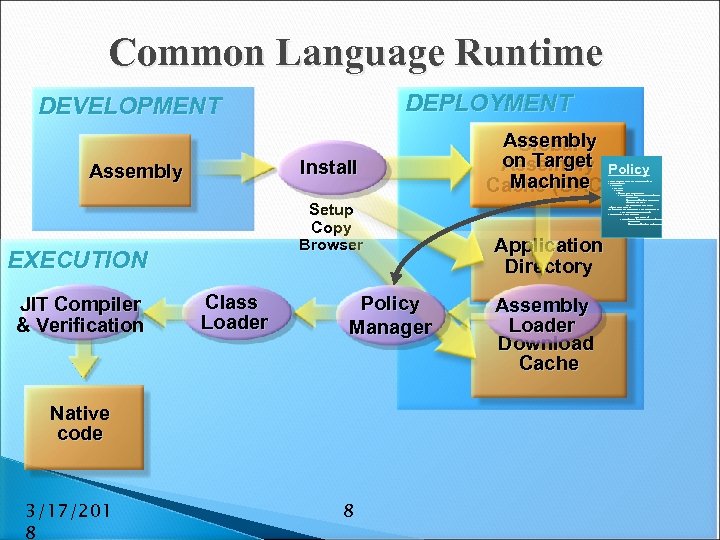 Common Language Runtime DEPLOYMENT DEVELOPMENT Install Assembly Setup Copy Browser EXECUTION JIT Compiler & Verification Class Loader Policy Manager Native code 3/17/201 8 8 Assembly Global on Target Assembly Policy Machine Cache (GAC)
Common Language Runtime DEPLOYMENT DEVELOPMENT Install Assembly Setup Copy Browser EXECUTION JIT Compiler & Verification Class Loader Policy Manager Native code 3/17/201 8 8 Assembly Global on Target Assembly Policy Machine Cache (GAC)
 A Type-Safe System Type-safe code: ◦ Prevents buffer overruns ◦ Restricts access to authorized memory locations ◦ Allows multiple assemblies to run in the same process App Domains provide: ◦ Increased performance ◦ Increased code security 3/17/201 8 9
A Type-Safe System Type-safe code: ◦ Prevents buffer overruns ◦ Restricts access to authorized memory locations ◦ Allows multiple assemblies to run in the same process App Domains provide: ◦ Increased performance ◦ Increased code security 3/17/201 8 9
 Strong-Named Assemblies Strong names are ◦ Unique identifiers (containing a public key) ◦ Used to digitally sign assemblies sn –k My. Full. Key. snk Strong-named assemblies ◦ Prevent tampering ◦ Confirm the identity of the assembly’s publisher ◦ Allow side-by-side components 3/17/201 8 10
Strong-Named Assemblies Strong names are ◦ Unique identifiers (containing a public key) ◦ Used to digitally sign assemblies sn –k My. Full. Key. snk Strong-named assemblies ◦ Prevent tampering ◦ Confirm the identity of the assembly’s publisher ◦ Allow side-by-side components 3/17/201 8 10
 Isolated Storage Provides a virtual file system Allows quotas Implements file system isolation based on: ◦ Application identity ◦ User identity Isolated. Storage. File iso. Store = Isolated. Storage. File. Get. User. Store. For. Assembly(); 3/17/201 8 11
Isolated Storage Provides a virtual file system Allows quotas Implements file system isolation based on: ◦ Application identity ◦ User identity Isolated. Storage. File iso. Store = Isolated. Storage. File. Get. User. Store. For. Assembly(); 3/17/201 8 11
 Security § . NET Framework Security features § Role-based § Code-based § Evidence-based § Cryptography 3/17/201 8 12
Security § . NET Framework Security features § Role-based § Code-based § Evidence-based § Cryptography 3/17/201 8 12
 Role-based Security § Applications use role-based security to enforce business rule constraints § Individuals are grouped into roles with varying levels of access §. NET role-based security works by making user and role information available to the current thread § Unified model for Authentication & Authorization 3/17/201 8 13
Role-based Security § Applications use role-based security to enforce business rule constraints § Individuals are grouped into roles with varying levels of access §. NET role-based security works by making user and role information available to the current thread § Unified model for Authentication & Authorization 3/17/201 8 13
 Role-based Security § Role-based Security (Contd. . ) § Authentication : § Examining user credentials § Authorization : § Analyzing user roles – what rights and operations allowed to perform §. NET Framework provides support for common authentication protocols § KERBEROS § SSL/TLS etc. 3/17/201 8 14
Role-based Security § Role-based Security (Contd. . ) § Authentication : § Examining user credentials § Authorization : § Analyzing user roles – what rights and operations allowed to perform §. NET Framework provides support for common authentication protocols § KERBEROS § SSL/TLS etc. 3/17/201 8 14
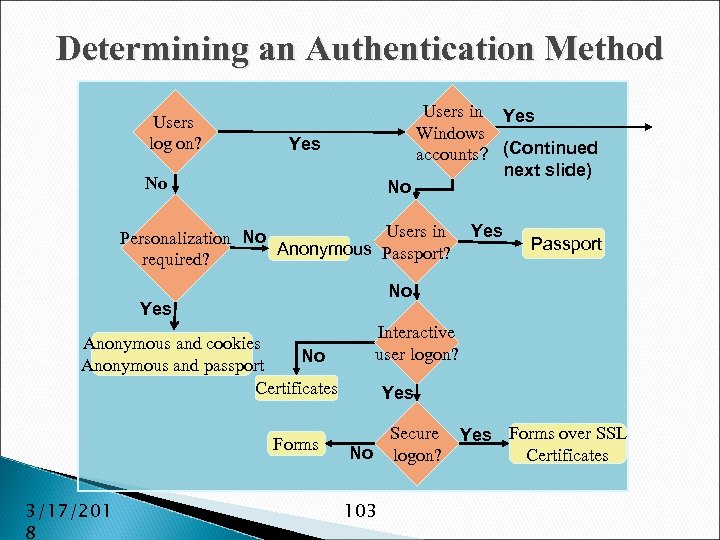
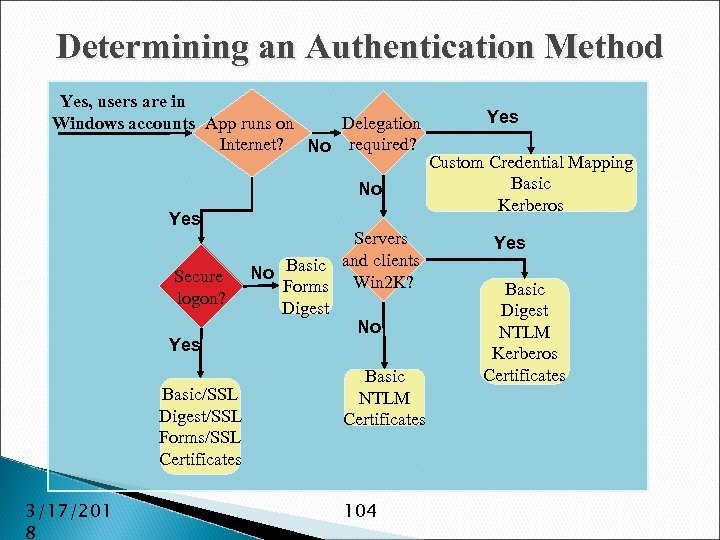
 Role-Based Security: Authentication Unified programming model for all forms of authentication: ◦ ◦ ◦ ◦ Basic Digest NTLM Kerberos Microsoft Passport Forms/Custom Client Certificates 3/17/201 8 15
Role-Based Security: Authentication Unified programming model for all forms of authentication: ◦ ◦ ◦ ◦ Basic Digest NTLM Kerberos Microsoft Passport Forms/Custom Client Certificates 3/17/201 8 15
 Role-Based Security: Authorization Maximum flexibility again ◦ Access Control Lists ◦ Active Directory ◦ URL Authorization via Configuration Files ◦ Custom 3/17/201 8 16
Role-Based Security: Authorization Maximum flexibility again ◦ Access Control Lists ◦ Active Directory ◦ URL Authorization via Configuration Files ◦ Custom 3/17/201 8 16
 Code Access Security Allows partially trusted code to run with reduced rights Evidence-based security model No more “all-or-none” or “sandbox” Granular permissions Flexible, extensible 3/17/201 8 17
Code Access Security Allows partially trusted code to run with reduced rights Evidence-based security model No more “all-or-none” or “sandbox” Granular permissions Flexible, extensible 3/17/201 8 17
 History Prior to. NET, we lived almost exclusively in a world of tokens and access control lists Security model implied a world based exclusively on trust ◦ “Please buy my component. Don’t worry; I won’t trash your machine. ” Component reuse took some “convincing” from vendors 3/17/201 8 18
History Prior to. NET, we lived almost exclusively in a world of tokens and access control lists Security model implied a world based exclusively on trust ◦ “Please buy my component. Don’t worry; I won’t trash your machine. ” Component reuse took some “convincing” from vendors 3/17/201 8 18
 It’s Time to Stop the Madness “We need leverage the existing model…” “We need make components more trustworthy…” “We need give sysadmins more control over what code and cannot do…” Question: Can we can have our cake and eat it too? 3/17/201 8 19
It’s Time to Stop the Madness “We need leverage the existing model…” “We need make components more trustworthy…” “We need give sysadmins more control over what code and cannot do…” Question: Can we can have our cake and eat it too? 3/17/201 8 19
 Solution A Tale of Two Securities: ◦ Code Access Security ◦ Evidence Based Security These two models allow us (as component vendors and sysadmins) to live safely and sanely in this new. NET world Component reuse is now a reality Control over code is now a reality The security infrastructure of the CLR provides evidence, policy, permissions, and enforcement services 3/17/201 8 20
Solution A Tale of Two Securities: ◦ Code Access Security ◦ Evidence Based Security These two models allow us (as component vendors and sysadmins) to live safely and sanely in this new. NET world Component reuse is now a reality Control over code is now a reality The security infrastructure of the CLR provides evidence, policy, permissions, and enforcement services 3/17/201 8 20
 Code Access Security CAS is a mechanism that controls the access that code has to protected resources and operations CAS allows code to be trusted to varying degrees, depending on where the code originates and on other aspects of the code's identity CAS also enforces the varying levels of trust on code, which minimizes the amount of code that must be fully trusted in order to run 3/17/201 8 21
Code Access Security CAS is a mechanism that controls the access that code has to protected resources and operations CAS allows code to be trusted to varying degrees, depending on where the code originates and on other aspects of the code's identity CAS also enforces the varying levels of trust on code, which minimizes the amount of code that must be fully trusted in order to run 3/17/201 8 21
 Why Code Access Security? Using CAS can reduce the likelihood that your code can be misused by malicious or error-filled code It can reduce your liability because you can specify the set of operations your code should be allowed to perform as well as the operations your code should never be allowed to perform Code access security can also help minimize the damage that can result from security vulnerabilities in your code 3/17/201 8 22
Why Code Access Security? Using CAS can reduce the likelihood that your code can be misused by malicious or error-filled code It can reduce your liability because you can specify the set of operations your code should be allowed to perform as well as the operations your code should never be allowed to perform Code access security can also help minimize the damage that can result from security vulnerabilities in your code 3/17/201 8 22
 Code Access Security: The Result We take security very, very seriously by hoisting a secure infrastructure directly into the common language runtime (CLR) CLR is the Mother of All Control This is a good thing; we need much more security than what Windows alone is able to provide 3/17/201 8 23
Code Access Security: The Result We take security very, very seriously by hoisting a secure infrastructure directly into the common language runtime (CLR) CLR is the Mother of All Control This is a good thing; we need much more security than what Windows alone is able to provide 3/17/201 8 23
 Code Access Permissions Represent access to a protected resource or the ability to perform a protected operation They are a fundamental part of the common language runtime's mechanism for enforcing security restrictions on managed code 3/17/201 8 24
Code Access Permissions Represent access to a protected resource or the ability to perform a protected operation They are a fundamental part of the common language runtime's mechanism for enforcing security restrictions on managed code 3/17/201 8 24
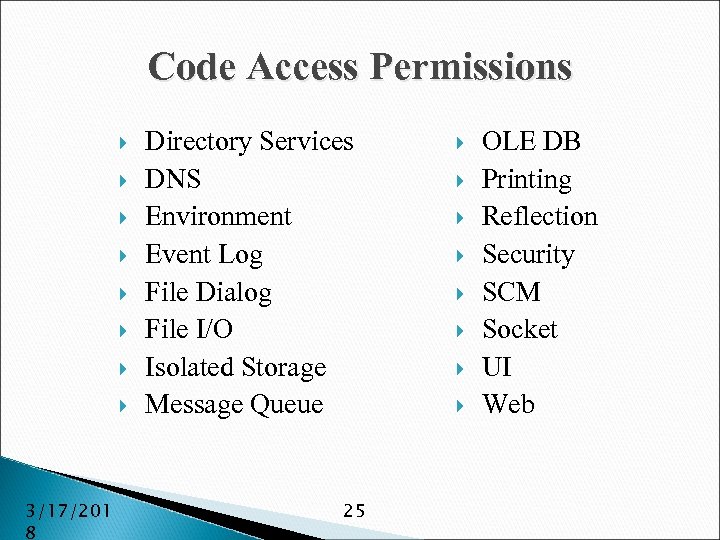 Code Access Permissions 3/17/201 8 Directory Services DNS Environment Event Log File Dialog File I/O Isolated Storage Message Queue 25 OLE DB Printing Reflection Security SCM Socket UI Web
Code Access Permissions 3/17/201 8 Directory Services DNS Environment Event Log File Dialog File I/O Isolated Storage Message Queue 25 OLE DB Printing Reflection Security SCM Socket UI Web
 Code Access Permissions Are Cool Note: These permissions are extensible! Every permission inherits from Code. Access. Permission Secure your resources/types with your own permissions – very cool 3/17/201 8 26
Code Access Permissions Are Cool Note: These permissions are extensible! Every permission inherits from Code. Access. Permission Secure your resources/types with your own permissions – very cool 3/17/201 8 26
 Code Access Permissions Code access permissions may be applied either explicitly or declaratively Code access permissions support a number of operations that control what code can or cannot do 3/17/201 8 27
Code Access Permissions Code access permissions may be applied either explicitly or declaratively Code access permissions support a number of operations that control what code can or cannot do 3/17/201 8 27
 Code Access Permissions All code access permissions derive from Code. Access. Permission defines the underlying structure of all code access permissions Code access permissions use a stack walk to ensure that all callers of the code have been granted a permission 3/17/201 8 28
Code Access Permissions All code access permissions derive from Code. Access. Permission defines the underlying structure of all code access permissions Code access permissions use a stack walk to ensure that all callers of the code have been granted a permission 3/17/201 8 28
 Security. Exception Security. Exception forms the basis of all security violations committed by code running in the CLR If the system denies a request, it does so by throwing an exception of type Security. Exceptions represent a virtual slap-on-thewrist; “Don’t do that…” 3/17/201 8 29
Security. Exception Security. Exception forms the basis of all security violations committed by code running in the CLR If the system denies a request, it does so by throwing an exception of type Security. Exceptions represent a virtual slap-on-thewrist; “Don’t do that…” 3/17/201 8 29
 Code Access Permissions Code access permissions support the following methods: ◦ Assert ◦ Demand ◦ Deny ◦ Permit. Only ◦ Revert. All ◦ Revert. Assert ◦ Revert. Deny ◦ Revert. Permit. Only 3/17/201 8 30
Code Access Permissions Code access permissions support the following methods: ◦ Assert ◦ Demand ◦ Deny ◦ Permit. Only ◦ Revert. All ◦ Revert. Assert ◦ Revert. Deny ◦ Revert. Permit. Only 3/17/201 8 30
 Assert Calling Assert prevents a stack walk originating lower in the call stack from proceeding up the call stack beyond the code that calls this method Disables the stack walk for the frame ALWAYS VERIFY YOUR ASSERTS! 3/17/201 8 31
Assert Calling Assert prevents a stack walk originating lower in the call stack from proceeding up the call stack beyond the code that calls this method Disables the stack walk for the frame ALWAYS VERIFY YOUR ASSERTS! 3/17/201 8 31
 Demand Forces a Security. Exception at run time if all callers higher in the call stack have not been granted the permission specified by the current instance A good way to test for available permissions 3/17/201 8 32
Demand Forces a Security. Exception at run time if all callers higher in the call stack have not been granted the permission specified by the current instance A good way to test for available permissions 3/17/201 8 32
 Deny Prevents callers higher in the call stack from accessing a resource specified by the current instance ◦ Pseudo-sandboxing 3/17/201 8 33
Deny Prevents callers higher in the call stack from accessing a resource specified by the current instance ◦ Pseudo-sandboxing 3/17/201 8 33
 Permit. Only Prevents callers higher in the call stack from using the code that calls this method to access all resources except for the resource specified by the current instance Similar to Deny in that both cause stack walks to fail when they would otherwise succeed ◦ However, Permit. Only specifies permissions that do not cause the stack walk to fail 3/17/201 8 34
Permit. Only Prevents callers higher in the call stack from using the code that calls this method to access all resources except for the resource specified by the current instance Similar to Deny in that both cause stack walks to fail when they would otherwise succeed ◦ However, Permit. Only specifies permissions that do not cause the stack walk to fail 3/17/201 8 34
 Revert. All Causes all previous overrides for the current frame to be removed and no longer in effect Rolls back all overrides made for the current frame 3/17/201 8 35
Revert. All Causes all previous overrides for the current frame to be removed and no longer in effect Rolls back all overrides made for the current frame 3/17/201 8 35
 Revert. Assert, Revert. Deny, and Revert. Permit. Only… Oh My! Each of these methods causes any previous Assert/Deny/Permit. Only for the current frame to be removed and no longer in effect 3/17/201 8 36
Revert. Assert, Revert. Deny, and Revert. Permit. Only… Oh My! Each of these methods causes any previous Assert/Deny/Permit. Only for the current frame to be removed and no longer in effect 3/17/201 8 36
 When to Assert? Clearly, the ability to assert permissions can be abused Unfortunately, the issue regards assertions is a bit cloudy ◦ Unmanaged code requires assertions ◦ “Gatekeeper” classes Rule: Demand before Assert Rule: Always code review your assertions! 3/17/201 8 37
When to Assert? Clearly, the ability to assert permissions can be abused Unfortunately, the issue regards assertions is a bit cloudy ◦ Unmanaged code requires assertions ◦ “Gatekeeper” classes Rule: Demand before Assert Rule: Always code review your assertions! 3/17/201 8 37
 Evidence-based Security Evidence ◦ Is assessed when an assembly is loaded ◦ Is used to determine the permissions for the assembly ◦ Can include the assembly’s: Strong name information URL Zone Authenticode signature 3/17/201 8 38
Evidence-based Security Evidence ◦ Is assessed when an assembly is loaded ◦ Is used to determine the permissions for the assembly ◦ Can include the assembly’s: Strong name information URL Zone Authenticode signature 3/17/201 8 38
 . NET Security Currency Evidence ◦ Inputs to policy about code ◦ Strong name, site, zone, Authenticode signature Permissions ◦ Specific authorizations ◦ Define a level of access to a resource Policy ◦ Determines what code can do ◦ Grants permissions to an assembly 3/17/201 8 39
. NET Security Currency Evidence ◦ Inputs to policy about code ◦ Strong name, site, zone, Authenticode signature Permissions ◦ Specific authorizations ◦ Define a level of access to a resource Policy ◦ Determines what code can do ◦ Grants permissions to an assembly 3/17/201 8 39
 Evidence The CLR examines evidence about code to determine which permissions to grant Evidence is presented by an assembly at load time: ◦ From what site was this assembly obtained? ◦ From what URL was this assembly obtained? ◦ From what Zone was this assembly obtained? ◦ What’s the strong name of this assembly? ◦ Who signed this assembly? 3/17/201 8 40
Evidence The CLR examines evidence about code to determine which permissions to grant Evidence is presented by an assembly at load time: ◦ From what site was this assembly obtained? ◦ From what URL was this assembly obtained? ◦ From what Zone was this assembly obtained? ◦ What’s the strong name of this assembly? ◦ Who signed this assembly? 3/17/201 8 40
 Evidence = input to policy Example: Info about a code assembly ◦ Strong names cryptographically ◦ Publisher identity computed/validated ◦ Hash ◦ Location of origin (URL, IE zone, site) Evidence is completely extensible ◦ Any object can be a piece of evidence Time of day, 3 rd party certification, etc. ◦ Only impacts grants if there is a code group membership condition that tests for it ◦ Assemblies may contain untrusted evidence 3/17/201 8 } 41
Evidence = input to policy Example: Info about a code assembly ◦ Strong names cryptographically ◦ Publisher identity computed/validated ◦ Hash ◦ Location of origin (URL, IE zone, site) Evidence is completely extensible ◦ Any object can be a piece of evidence Time of day, 3 rd party certification, etc. ◦ Only impacts grants if there is a code group membership condition that tests for it ◦ Assemblies may contain untrusted evidence 3/17/201 8 } 41
 Policy Evaluation in the CLR Policy is the process of determining the set of permissions to grant to code based on evidence known about that code This is a classic trust management problem ◦ Requiring end users to write programs to express policies was simply out of the question. . . ◦ This is why Microsoft has given us a declarative, administrative model! 3/17/201 8 42
Policy Evaluation in the CLR Policy is the process of determining the set of permissions to grant to code based on evidence known about that code This is a classic trust management problem ◦ Requiring end users to write programs to express policies was simply out of the question. . . ◦ This is why Microsoft has given us a declarative, administrative model! 3/17/201 8 42
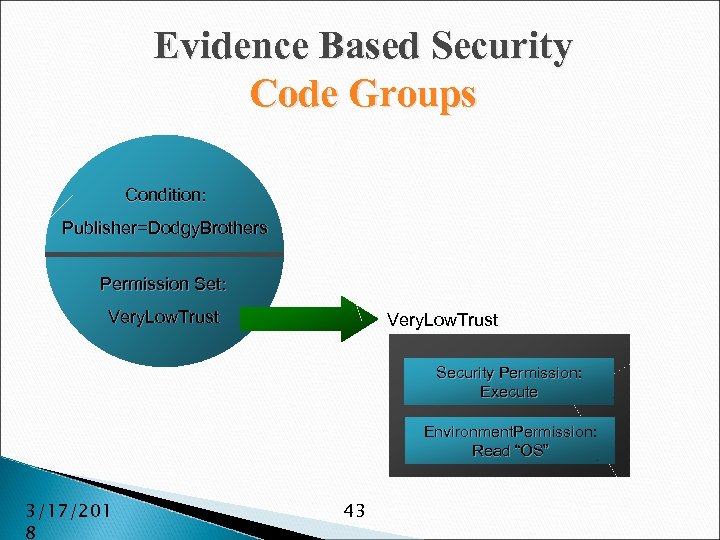 Evidence Based Security Code Groups Condition: Publisher=Dodgy. Brothers Permission Set: Very. Low. Trust Security Permission: Execute Environment. Permission: Read “OS” 3/17/201 8 43
Evidence Based Security Code Groups Condition: Publisher=Dodgy. Brothers Permission Set: Very. Low. Trust Security Permission: Execute Environment. Permission: Read “OS” 3/17/201 8 43
 Evidence Based Security Membership Conditions A code group may have only one membership condition It is comprised of an attribute that matches evidence presented by an assembly ◦ Zone of originating assembly ◦ URL of originating assembly ◦ Digital signature of assembly publisher ◦ Web site of the originating assembly 3/17/201 8 44
Evidence Based Security Membership Conditions A code group may have only one membership condition It is comprised of an attribute that matches evidence presented by an assembly ◦ Zone of originating assembly ◦ URL of originating assembly ◦ Digital signature of assembly publisher ◦ Web site of the originating assembly 3/17/201 8 44
 Evidence Based Security Default Security Policy Comprised of many code groups that map to different assembly types ◦ Local, intranet, internet assemblies Installed as part of the. NET Framework Can be modified by an administrator 3/17/201 8 45
Evidence Based Security Default Security Policy Comprised of many code groups that map to different assembly types ◦ Local, intranet, internet assemblies Installed as part of the. NET Framework Can be modified by an administrator 3/17/201 8 45
 Evidence Based Security Policy Four levels of policy in. NET ◦ Enterprise ◦ Machine ◦ User ◦ Application Domain Each level contains code groups that map assemblies to permissions Policy evaluation is from Enterprise down to Application Domain 3/17/201 8 46
Evidence Based Security Policy Four levels of policy in. NET ◦ Enterprise ◦ Machine ◦ User ◦ Application Domain Each level contains code groups that map assemblies to permissions Policy evaluation is from Enterprise down to Application Domain 3/17/201 8 46
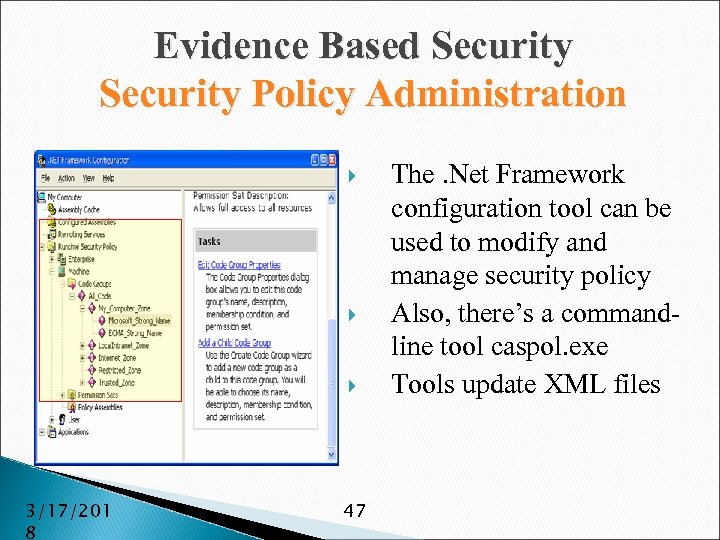 Evidence Based Security Policy Administration 3/17/201 8 47 The. Net Framework configuration tool can be used to modify and manage security policy Also, there’s a commandline tool caspol. exe Tools update XML files
Evidence Based Security Policy Administration 3/17/201 8 47 The. Net Framework configuration tool can be used to modify and manage security policy Also, there’s a commandline tool caspol. exe Tools update XML files
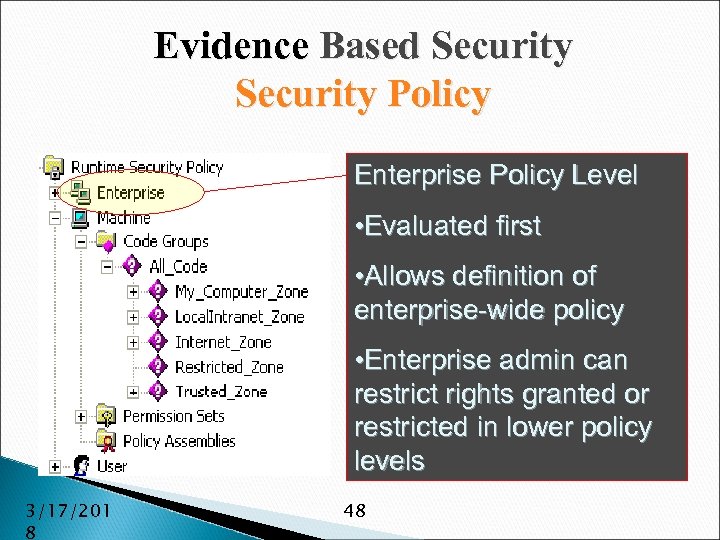 Evidence Based Security Policy Enterprise Policy Level • Evaluated first • Allows definition of enterprise-wide policy • Enterprise admin can restrict rights granted or restricted in lower policy levels 3/17/201 8 48
Evidence Based Security Policy Enterprise Policy Level • Evaluated first • Allows definition of enterprise-wide policy • Enterprise admin can restrict rights granted or restricted in lower policy levels 3/17/201 8 48
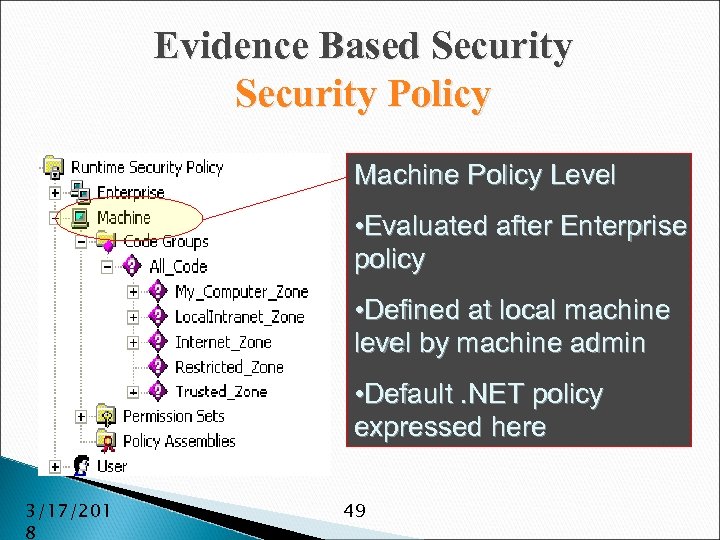 Evidence Based Security Policy Machine Policy Level • Evaluated after Enterprise policy • Defined at local machine level by machine admin • Default. NET policy expressed here 3/17/201 8 49
Evidence Based Security Policy Machine Policy Level • Evaluated after Enterprise policy • Defined at local machine level by machine admin • Default. NET policy expressed here 3/17/201 8 49
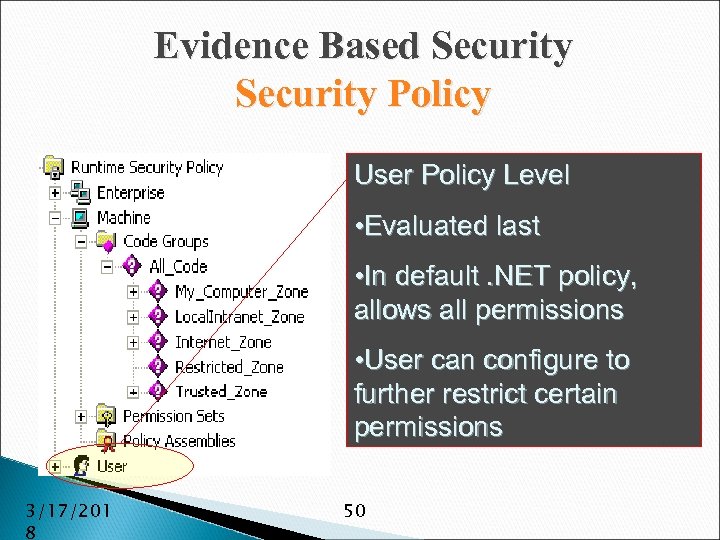 Evidence Based Security Policy User Policy Level • Evaluated last • In default. NET policy, allows all permissions • User can configure to further restrict certain permissions 3/17/201 8 50
Evidence Based Security Policy User Policy Level • Evaluated last • In default. NET policy, allows all permissions • User can configure to further restrict certain permissions 3/17/201 8 50
 Evidence Based Security Code Groups Each policy level has a set of code groups ◦ Code groups are related hierarchically ◦ There must be at least one code group for each policy level ◦ Once the CLR determines that a code group does not map to an assembly, no dependent code groups are examined 3/17/201 8 51
Evidence Based Security Code Groups Each policy level has a set of code groups ◦ Code groups are related hierarchically ◦ There must be at least one code group for each policy level ◦ Once the CLR determines that a code group does not map to an assembly, no dependent code groups are examined 3/17/201 8 51
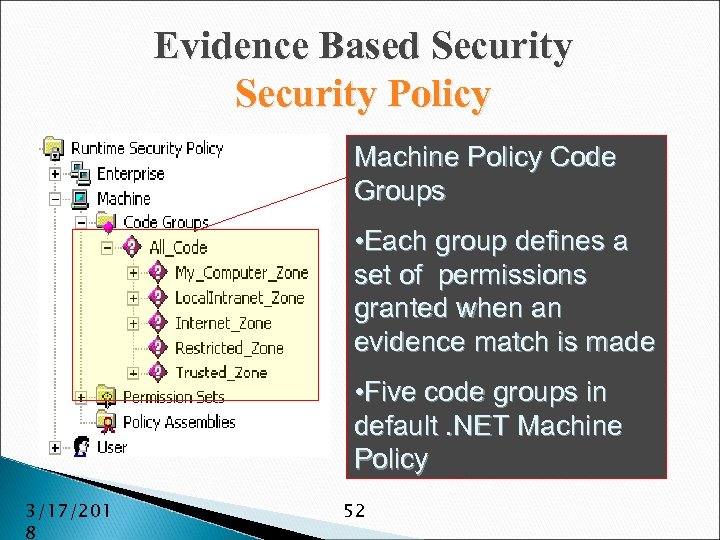 Evidence Based Security Policy Machine Policy Code Groups • Each group defines a set of permissions granted when an evidence match is made • Five code groups in default. NET Machine Policy 3/17/201 8 52
Evidence Based Security Policy Machine Policy Code Groups • Each group defines a set of permissions granted when an evidence match is made • Five code groups in default. NET Machine Policy 3/17/201 8 52
 Evidence Based Security Permissions A code group may have only one permission set ◦ A permission set may be comprised of a variety of different permissions Full trust to all protected system resources Read/Write access to a local file Read access to a specified environment variable 3/17/201 8 53
Evidence Based Security Permissions A code group may have only one permission set ◦ A permission set may be comprised of a variety of different permissions Full trust to all protected system resources Read/Write access to a local file Read access to a specified environment variable 3/17/201 8 53
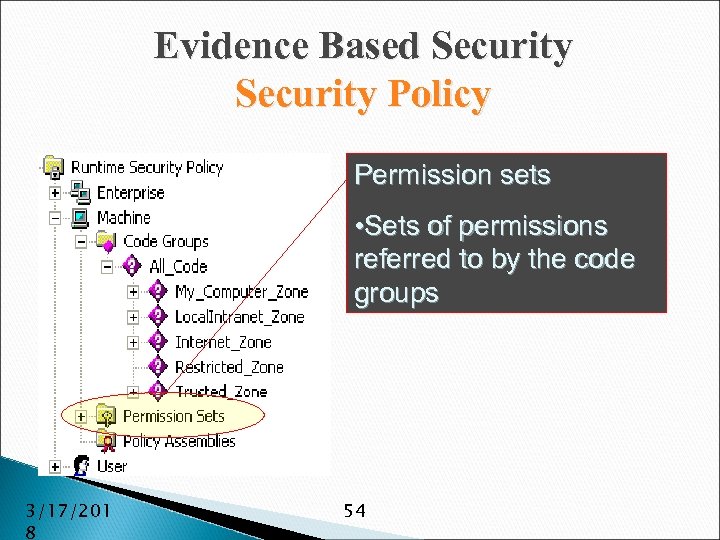 Evidence Based Security Policy Permission sets • Sets of permissions referred to by the code groups 3/17/201 8 54
Evidence Based Security Policy Permission sets • Sets of permissions referred to by the code groups 3/17/201 8 54
 Evidence Based Security Code Group Evaluation More than one code group within a policy level may map to the evidence of an assembly A policy level has the combination (union) of all code group permissions that map to an assembly 3/17/201 8 55
Evidence Based Security Code Group Evaluation More than one code group within a policy level may map to the evidence of an assembly A policy level has the combination (union) of all code group permissions that map to an assembly 3/17/201 8 55
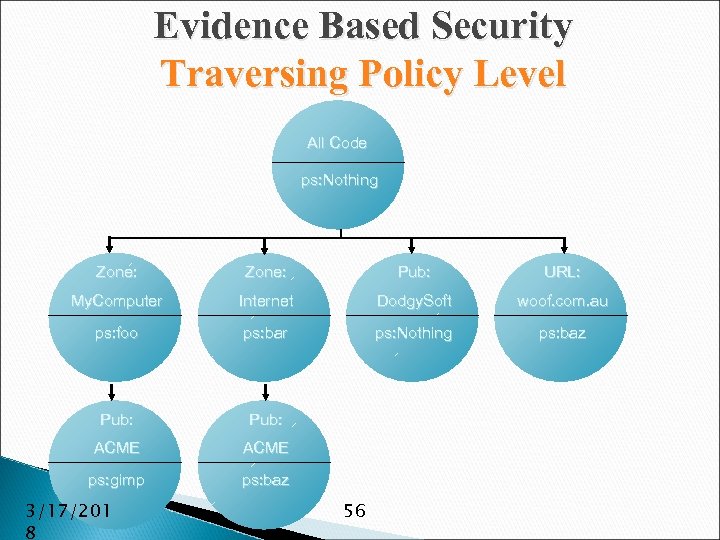 Evidence Based Security Traversing Policy Level All Code ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: baz Pub: ACME ps: gimp ps: baz 3/17/201 8 56
Evidence Based Security Traversing Policy Level All Code ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: baz Pub: ACME ps: gimp ps: baz 3/17/201 8 56
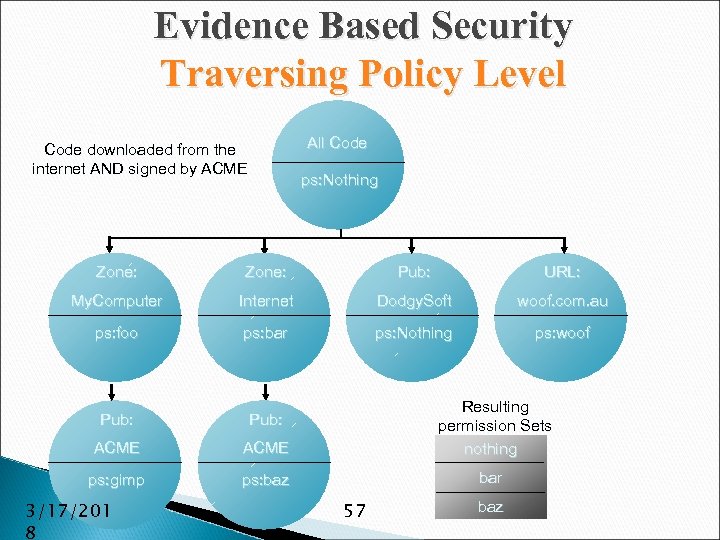 Evidence Based Security Traversing Policy Level All Code downloaded from the internet AND signed by ACME ps: nothing ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: woof Pub: ACME Resulting permission Sets nothing ps: gimp ps: baz bar 3/17/201 8 57 baz
Evidence Based Security Traversing Policy Level All Code downloaded from the internet AND signed by ACME ps: nothing ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: woof Pub: ACME Resulting permission Sets nothing ps: gimp ps: baz bar 3/17/201 8 57 baz
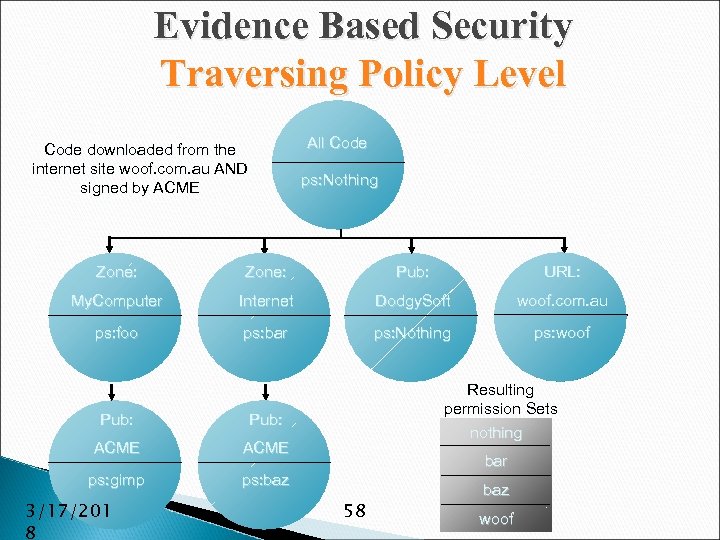 Evidence Based Security Traversing Policy Level All Code downloaded from the internet site woof. com. au AND signed by ACME ps: nothing ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: woof Pub: ACME ps: gimp Resulting permission Sets nothing ps: baz 3/17/201 8 bar 58 baz woof
Evidence Based Security Traversing Policy Level All Code downloaded from the internet site woof. com. au AND signed by ACME ps: nothing ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: woof Pub: ACME ps: gimp Resulting permission Sets nothing ps: baz 3/17/201 8 bar 58 baz woof
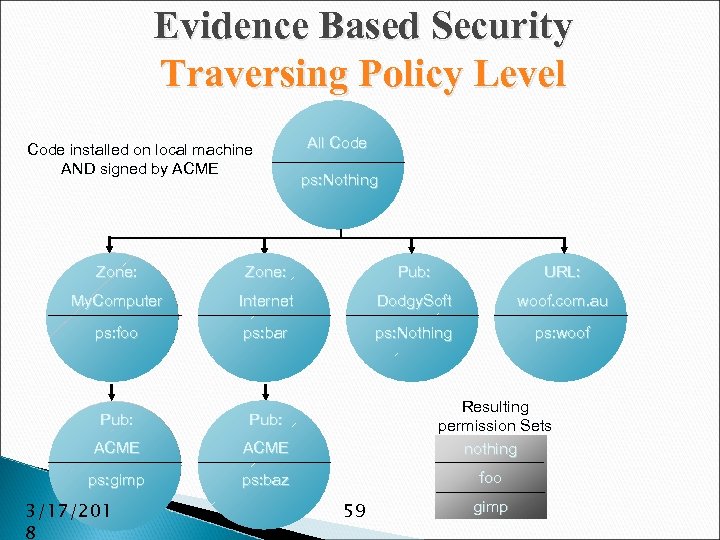 Evidence Based Security Traversing Policy Level Code installed on local machine AND signed by ACME All Code ps: nothing ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: woof Pub: ACME Resulting permission Sets nothing ps: gimp ps: baz foo 3/17/201 8 59 gimp
Evidence Based Security Traversing Policy Level Code installed on local machine AND signed by ACME All Code ps: nothing ps: Nothing Zone: Pub: URL: My. Computer Internet Dodgy. Soft woof. com. au ps: foo ps: bar ps: Nothing ps: woof Pub: ACME Resulting permission Sets nothing ps: gimp ps: baz foo 3/17/201 8 59 gimp
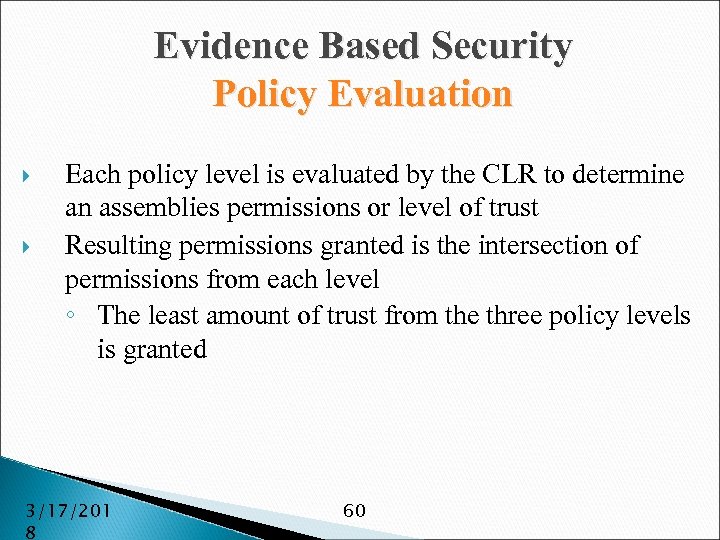 Evidence Based Security Policy Evaluation Each policy level is evaluated by the CLR to determine an assemblies permissions or level of trust Resulting permissions granted is the intersection of permissions from each level ◦ The least amount of trust from the three policy levels is granted 3/17/201 8 60
Evidence Based Security Policy Evaluation Each policy level is evaluated by the CLR to determine an assemblies permissions or level of trust Resulting permissions granted is the intersection of permissions from each level ◦ The least amount of trust from the three policy levels is granted 3/17/201 8 60
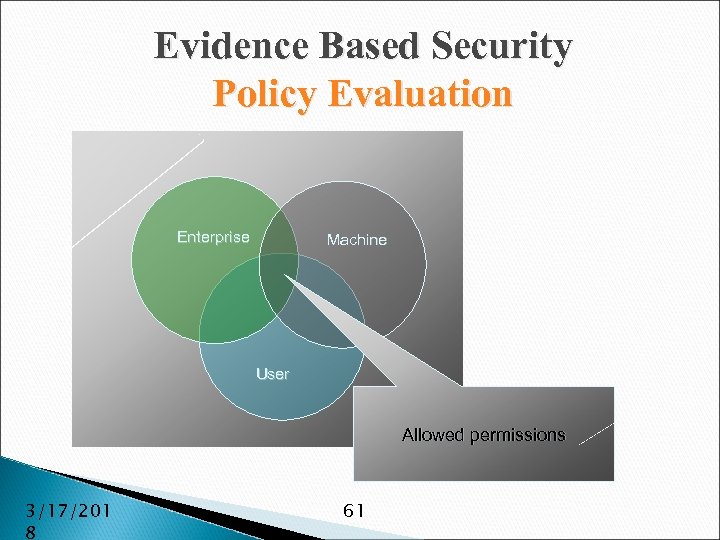 Evidence Based Security Policy Evaluation Enterprise Machine User Allowed permissions 3/17/201 8 61
Evidence Based Security Policy Evaluation Enterprise Machine User Allowed permissions 3/17/201 8 61
 3 Key Elements Evidence ◦ Inputs to policy about code ◦ Strong name, site, zone, Authenticode signature, hash value, app directory, etc. Permissions ◦ Specific authorizations for code (not users) ◦ Define a level of access to a resource or operation Policy ◦ Matches permissions to evidence via “code groups” ◦ Grants permissions to an assembly 3/17/201 8 62
3 Key Elements Evidence ◦ Inputs to policy about code ◦ Strong name, site, zone, Authenticode signature, hash value, app directory, etc. Permissions ◦ Specific authorizations for code (not users) ◦ Define a level of access to a resource or operation Policy ◦ Matches permissions to evidence via “code groups” ◦ Grants permissions to an assembly 3/17/201 8 62
 Local Machine Permissions Full. Trust Permission. Set Full access to all machine capabilities But: App must be installed on machine by machine’s admin 3/17/201 8 63
Local Machine Permissions Full. Trust Permission. Set Full access to all machine capabilities But: App must be installed on machine by machine’s admin 3/17/201 8 63
 Intranet Permissions l l l l 3/17/201 8 Unlimited UI Same protocol access to site & DNS File read access to origin Open/Save File Dialog Default printer Unlimited Isolated Storage Write to Event Log Env for USERNAME, TEMP, TMP 64
Intranet Permissions l l l l 3/17/201 8 Unlimited UI Same protocol access to site & DNS File read access to origin Open/Save File Dialog Default printer Unlimited Isolated Storage Write to Event Log Env for USERNAME, TEMP, TMP 64
 Programmatic access APIs to access code access security system ◦ Refuse unnecessary permissions ◦ Refuse to run if not granted necessary permissions ◦ Check to see if granted a permission and tweak app behavior based on response 3/17/201 8 65
Programmatic access APIs to access code access security system ◦ Refuse unnecessary permissions ◦ Refuse to run if not granted necessary permissions ◦ Check to see if granted a permission and tweak app behavior based on response 3/17/201 8 65
 Permission Requests Used by developers to state required permissions Implemented by attributes Prevents an assembly from loading when minimum permissions are not available //I will only run if I can call unmanaged code [assembly: Security. Permission (Security. Action. Request. Minimum, Unmanaged. Code=true)] 3/17/201 8 66
Permission Requests Used by developers to state required permissions Implemented by attributes Prevents an assembly from loading when minimum permissions are not available //I will only run if I can call unmanaged code [assembly: Security. Permission (Security. Action. Request. Minimum, Unmanaged. Code=true)] 3/17/201 8 66
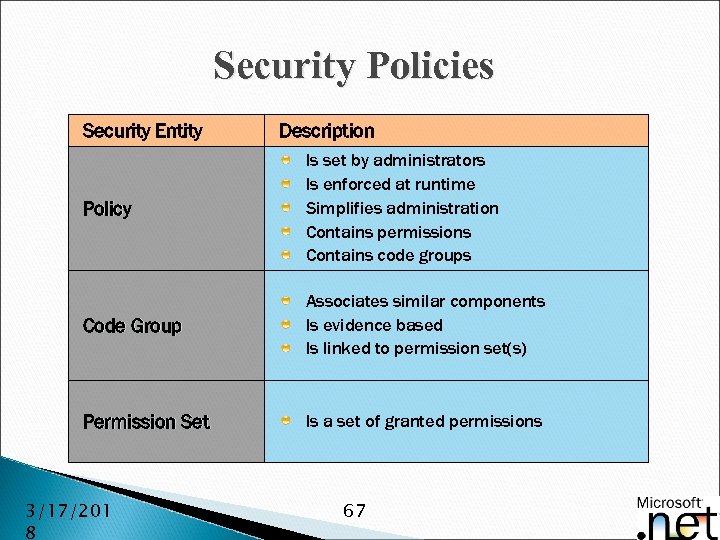 Security Policies Security Entity Description Policy Is set by administrators Is enforced at runtime Simplifies administration Contains permissions Contains code groups Code Group Associates similar components Is evidence based Is linked to permission set(s) Permission Set Is a set of granted permissions 3/17/201 8 67
Security Policies Security Entity Description Policy Is set by administrators Is enforced at runtime Simplifies administration Contains permissions Contains code groups Code Group Associates similar components Is evidence based Is linked to permission set(s) Permission Set Is a set of granted permissions 3/17/201 8 67
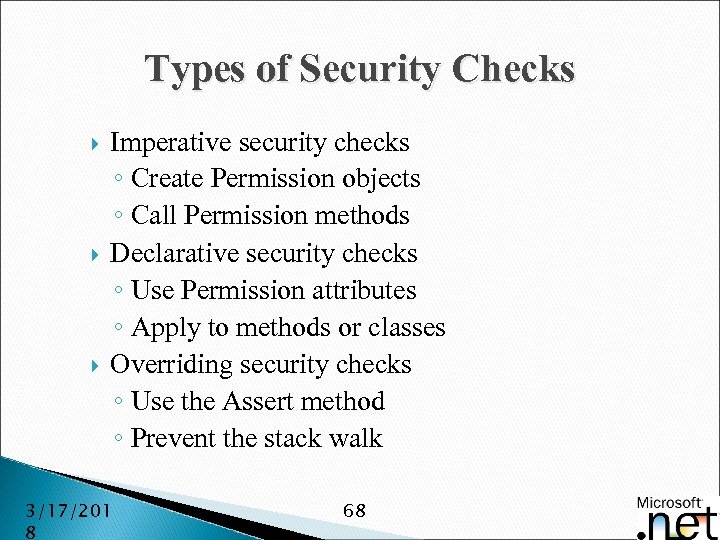 Types of Security Checks Imperative security checks ◦ Create Permission objects ◦ Call Permission methods Declarative security checks ◦ Use Permission attributes ◦ Apply to methods or classes Overriding security checks ◦ Use the Assert method ◦ Prevent the stack walk 3/17/201 8 68
Types of Security Checks Imperative security checks ◦ Create Permission objects ◦ Call Permission methods Declarative security checks ◦ Use Permission attributes ◦ Apply to methods or classes Overriding security checks ◦ Use the Assert method ◦ Prevent the stack walk 3/17/201 8 68
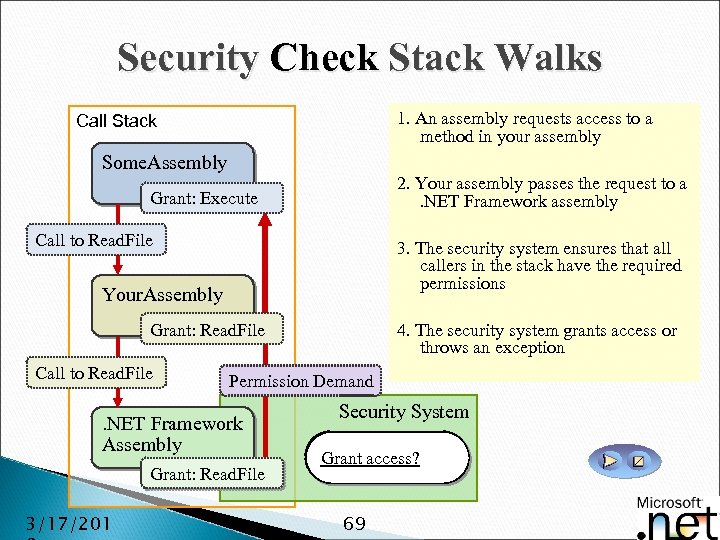 Security Check Stack Walks 1. An assembly requests access to a method in your assembly Call Stack Some. Assembly 2. Your assembly passes the request to a. NET Framework assembly Grant: Execute Call to Read. File 3. The security system ensures that all callers in the stack have the required permissions Your. Assembly Grant: Read. File Call to Read. File Permission Demand . NET Framework Assembly Grant: Read. File 3/17/201 4. The security system grants access or throws an exception Security System Security exception Grant access? Access denied 69
Security Check Stack Walks 1. An assembly requests access to a method in your assembly Call Stack Some. Assembly 2. Your assembly passes the request to a. NET Framework assembly Grant: Execute Call to Read. File 3. The security system ensures that all callers in the stack have the required permissions Your. Assembly Grant: Read. File Call to Read. File Permission Demand . NET Framework Assembly Grant: Read. File 3/17/201 4. The security system grants access or throws an exception Security System Security exception Grant access? Access denied 69
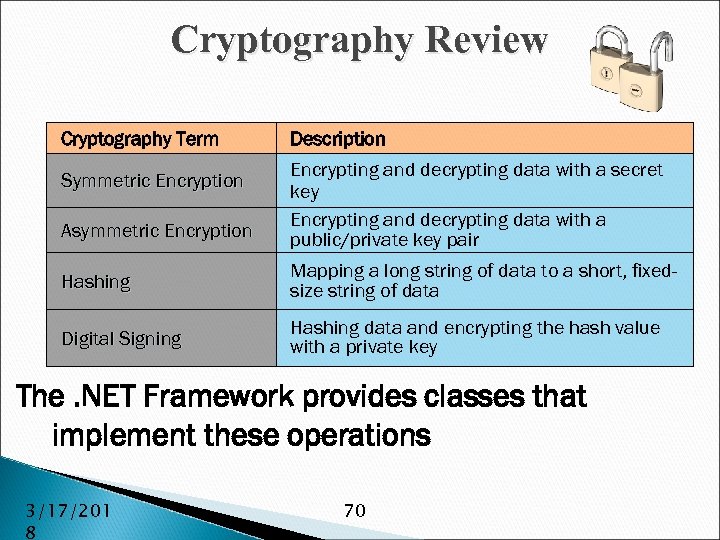 Cryptography Review Cryptography Term Description Asymmetric Encryption Encrypting and decrypting data with a secret key Encrypting and decrypting data with a public/private key pair Hashing Mapping a long string of data to a short, fixedsize string of data Digital Signing Hashing data and encrypting the hash value with a private key Symmetric Encryption The. NET Framework provides classes that implement these operations 3/17/201 8 70
Cryptography Review Cryptography Term Description Asymmetric Encryption Encrypting and decrypting data with a secret key Encrypting and decrypting data with a public/private key pair Hashing Mapping a long string of data to a short, fixedsize string of data Digital Signing Hashing data and encrypting the hash value with a private key Symmetric Encryption The. NET Framework provides classes that implement these operations 3/17/201 8 70
 Using Symmetric Algorithms Choose an algorithm ◦ Triple. DESCrypto. Service. Provider ◦ Rijndael. Managed Generate a secret key Use the same secret key to encrypt and decrypt data: ◦ File. Stream ◦ Memory. Stream ◦ Network. Stream 3/17/201 8 71
Using Symmetric Algorithms Choose an algorithm ◦ Triple. DESCrypto. Service. Provider ◦ Rijndael. Managed Generate a secret key Use the same secret key to encrypt and decrypt data: ◦ File. Stream ◦ Memory. Stream ◦ Network. Stream 3/17/201 8 71
 Using Asymmetric Algorithms Choose an algorithm ◦ RSACrypto. Service. Provider ◦ DSACrypto. Service. Provider Generate a private and public key pair Encrypt or decrypt data 3/17/201 8 72
Using Asymmetric Algorithms Choose an algorithm ◦ RSACrypto. Service. Provider ◦ DSACrypto. Service. Provider Generate a private and public key pair Encrypt or decrypt data 3/17/201 8 72
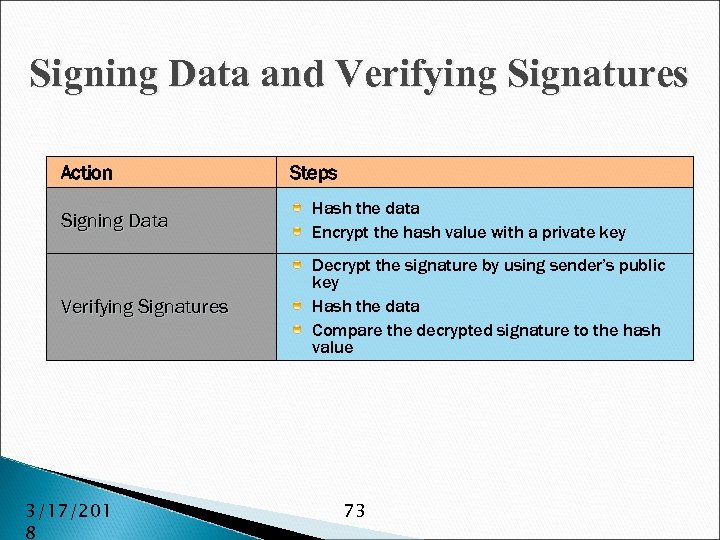 Signing Data and Verifying Signatures Action Steps Signing Data Hash the data Encrypt the hash value with a private key Verifying Signatures Decrypt the signature by using sender’s public key Hash the data Compare the decrypted signature to the hash value 3/17/201 8 73
Signing Data and Verifying Signatures Action Steps Signing Data Hash the data Encrypt the hash value with a private key Verifying Signatures Decrypt the signature by using sender’s public key Hash the data Compare the decrypted signature to the hash value 3/17/201 8 73
 Identities and Principals An identity contains information about a user, such as the user’s logon name A principal contains role information about a user or computer The. NET Framework provides: Windows. Identity and Windows. Principal objects Generic. Identity and Generic. Principal objects 3/17/201 8 74
Identities and Principals An identity contains information about a user, such as the user’s logon name A principal contains role information about a user or computer The. NET Framework provides: Windows. Identity and Windows. Principal objects Generic. Identity and Generic. Principal objects 3/17/201 8 74
 Identities An identity represents a certain user Identity is established through authentication by an authority Processes run code under an identity Access to some resources is granted based on a proven identity ◦ NTFS file system ◦ SQL Server and other server products working with Windows Integrated security ◦ Registry 3/17/201 8 75
Identities An identity represents a certain user Identity is established through authentication by an authority Processes run code under an identity Access to some resources is granted based on a proven identity ◦ NTFS file system ◦ SQL Server and other server products working with Windows Integrated security ◦ Registry 3/17/201 8 75
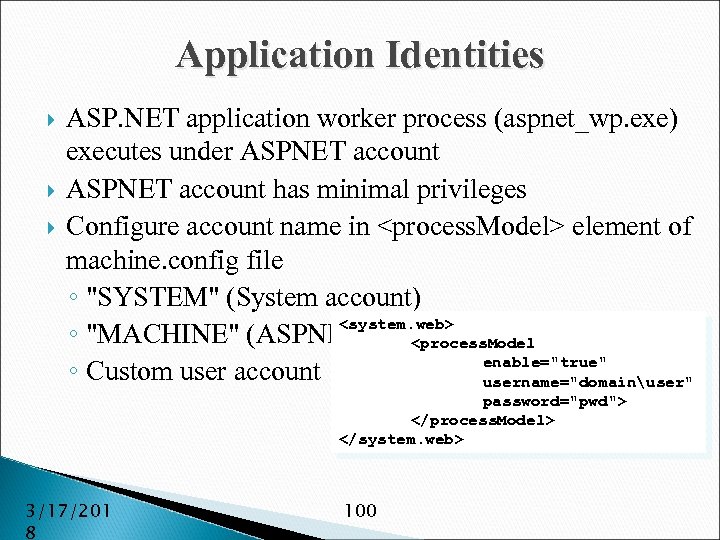
 Identities (cont'd) Usually identities are of type: ◦ Windows user ◦ ASP. NET Forms authenticated user ◦ Passport account ◦ Custom application account 3/17/201 8 76
Identities (cont'd) Usually identities are of type: ◦ Windows user ◦ ASP. NET Forms authenticated user ◦ Passport account ◦ Custom application account 3/17/201 8 76
 Principals A principal represents an identity AND its roles Allows you to make security decisions ◦ Role Based Security (RBS): Role membership is tested on a principal Role is group of users with similar rights ◦ Identity 3/17/201 8 77
Principals A principal represents an identity AND its roles Allows you to make security decisions ◦ Role Based Security (RBS): Role membership is tested on a principal Role is group of users with similar rights ◦ Identity 3/17/201 8 77
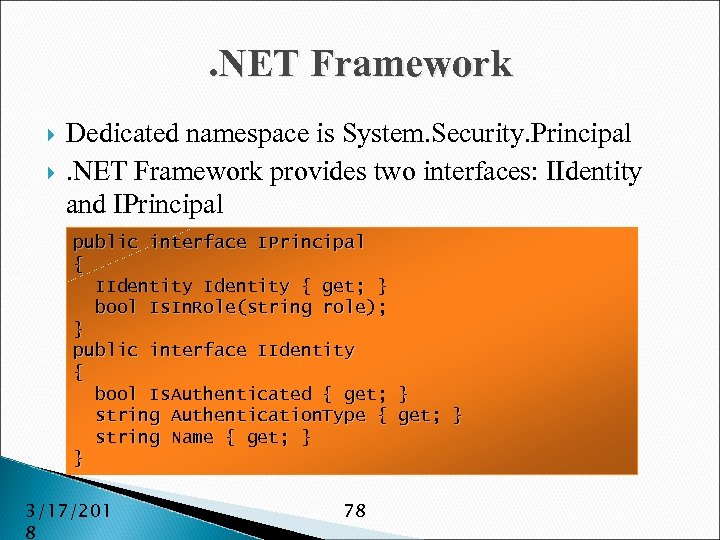 . NET Framework Dedicated namespace is System. Security. Principal. NET Framework provides two interfaces: IIdentity and IPrincipal public interface IPrincipal { IIdentity { get; } bool Is. In. Role(string role); } public interface IIdentity { bool Is. Authenticated { get; } string Authentication. Type { get; } string Name { get; } } 3/17/201 8 78
. NET Framework Dedicated namespace is System. Security. Principal. NET Framework provides two interfaces: IIdentity and IPrincipal public interface IPrincipal { IIdentity { get; } bool Is. In. Role(string role); } public interface IIdentity { bool Is. Authenticated { get; } string Authentication. Type { get; } string Name { get; } } 3/17/201 8 78
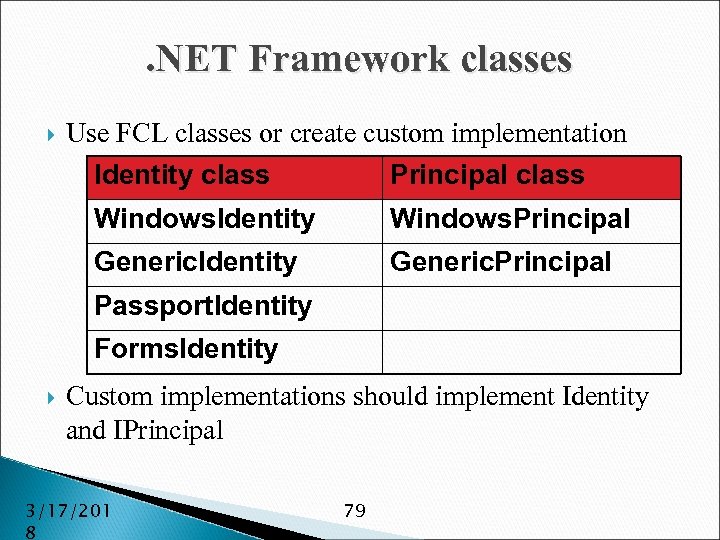 . NET Framework classes Use FCL classes or create custom implementation Identity class Principal class Windows. Identity Windows. Principal Generic. Identity Generic. Principal Passport. Identity Forms. Identity Custom implementations should implement Identity and IPrincipal 3/17/201 8 79
. NET Framework classes Use FCL classes or create custom implementation Identity class Principal class Windows. Identity Windows. Principal Generic. Identity Generic. Principal Passport. Identity Forms. Identity Custom implementations should implement Identity and IPrincipal 3/17/201 8 79
 Acquiring a principal Principal objects can be acquired in two ways ◦ Windows. Identity. Get. Current() method, then create Windows. Principal ◦ Thread. Current. Principal property ◦ ASP. NET only: Http. Context. Current. User Once acquired evaluate identities properties and/or check for role membership 3/17/201 8 80
Acquiring a principal Principal objects can be acquired in two ways ◦ Windows. Identity. Get. Current() method, then create Windows. Principal ◦ Thread. Current. Principal property ◦ ASP. NET only: Http. Context. Current. User Once acquired evaluate identities properties and/or check for role membership 3/17/201 8 80
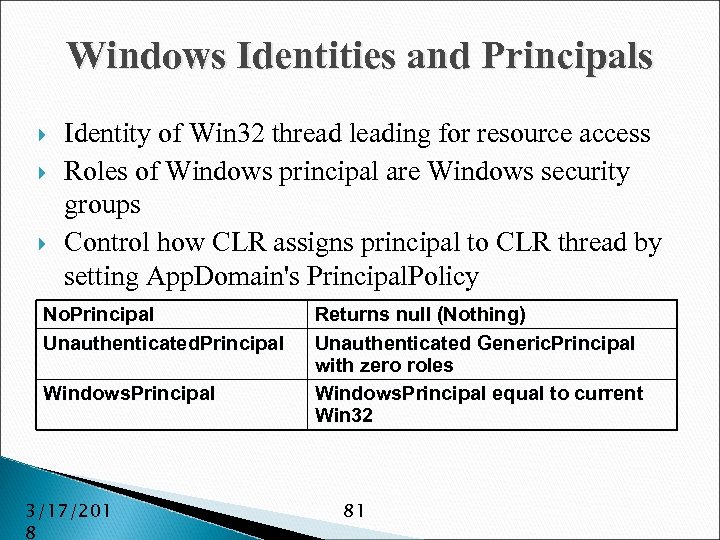 Windows Identities and Principals Identity of Win 32 thread leading for resource access Roles of Windows principal are Windows security groups Control how CLR assigns principal to CLR thread by setting App. Domain's Principal. Policy No. Principal Unauthenticated. Principal Windows. Principal 3/17/201 8 Returns null (Nothing) Unauthenticated Generic. Principal with zero roles Windows. Principal equal to current Win 32 81
Windows Identities and Principals Identity of Win 32 thread leading for resource access Roles of Windows principal are Windows security groups Control how CLR assigns principal to CLR thread by setting App. Domain's Principal. Policy No. Principal Unauthenticated. Principal Windows. Principal 3/17/201 8 Returns null (Nothing) Unauthenticated Generic. Principal with zero roles Windows. Principal equal to current Win 32 81
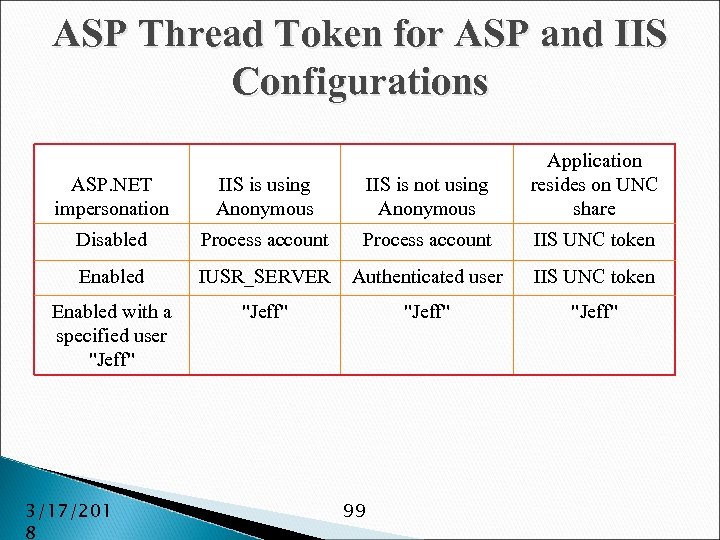
 Taking control of Windows. Identity of Win 32 thread determined by user token of process Different ways of setting ◦ Win 32 executables: Console Windows Forms Windows (NT) Services ◦ ASP. NET ◦ COM+ application (Enterprise Services) 3/17/201 8 82
Taking control of Windows. Identity of Win 32 thread determined by user token of process Different ways of setting ◦ Win 32 executables: Console Windows Forms Windows (NT) Services ◦ ASP. NET ◦ COM+ application (Enterprise Services) 3/17/201 8 82
 Impersonation Setting a new identity onto executing Win 32 thread, e. g. when: ◦ Identity of calling user has to be assumed ◦ Resource must be accessed through privileged account Windows. Identity class has Impersonate method ◦ Takes a token of user to impersonate ◦ Returns a Windows. Impersonation. Context ◦ Identity assumed until Undo is called 3/17/201 8 83
Impersonation Setting a new identity onto executing Win 32 thread, e. g. when: ◦ Identity of calling user has to be assumed ◦ Resource must be accessed through privileged account Windows. Identity class has Impersonate method ◦ Takes a token of user to impersonate ◦ Returns a Windows. Impersonation. Context ◦ Identity assumed until Undo is called 3/17/201 8 83
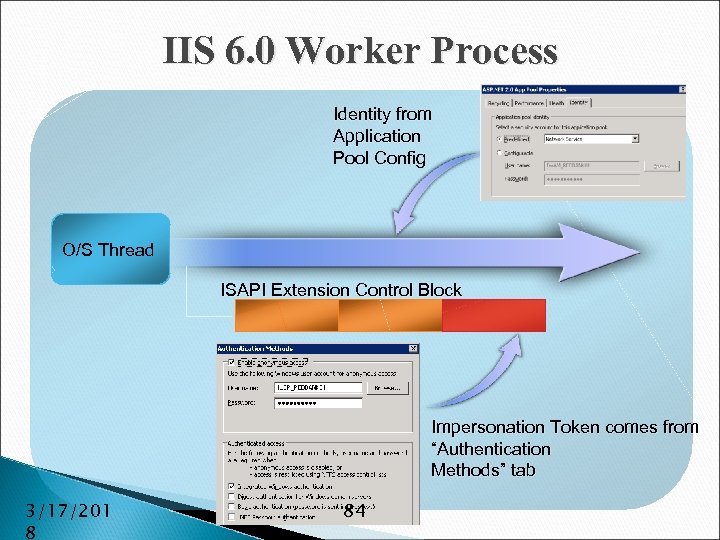 IIS 6. 0 Worker Process Identity from Application Pool Config O/S Thread ISAPI Extension Control Block Impersonation Token comes from “Authentication Methods” tab 3/17/201 8 84
IIS 6. 0 Worker Process Identity from Application Pool Config O/S Thread ISAPI Extension Control Block Impersonation Token comes from “Authentication Methods” tab 3/17/201 8 84
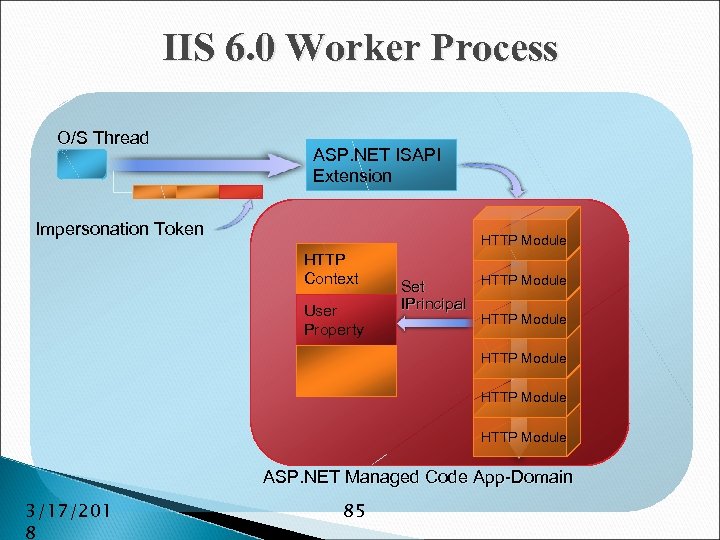 IIS 6. 0 Worker Process O/S Thread ASP. NET ISAPI Extension Impersonation Token HTTP Module HTTP Context User Property HTTP Module Set IPrincipal HTTP Module ASP. NET Managed Code App-Domain 3/17/201 8 85
IIS 6. 0 Worker Process O/S Thread ASP. NET ISAPI Extension Impersonation Token HTTP Module HTTP Context User Property HTTP Module Set IPrincipal HTTP Module ASP. NET Managed Code App-Domain 3/17/201 8 85
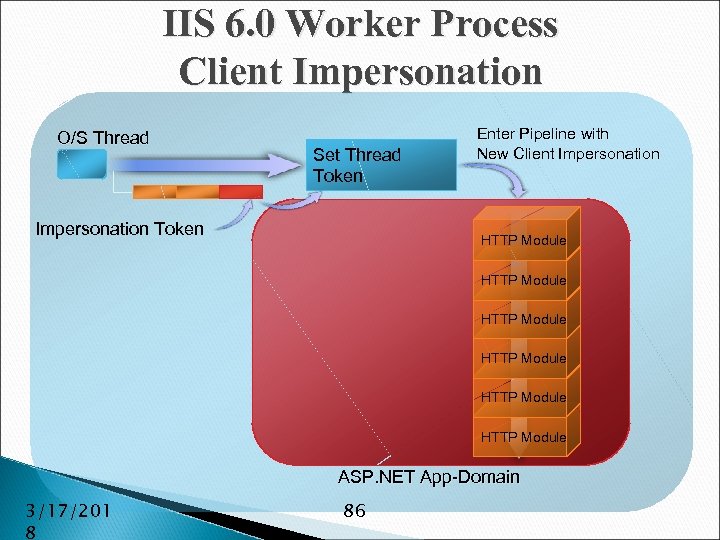 IIS 6. 0 Worker Process Client Impersonation O/S Thread Set Thread Token Impersonation Token Enter Pipeline with New Client Impersonation HTTP Module HTTP Module ASP. NET App-Domain 3/17/201 8 86
IIS 6. 0 Worker Process Client Impersonation O/S Thread Set Thread Token Impersonation Token Enter Pipeline with New Client Impersonation HTTP Module HTTP Module ASP. NET App-Domain 3/17/201 8 86
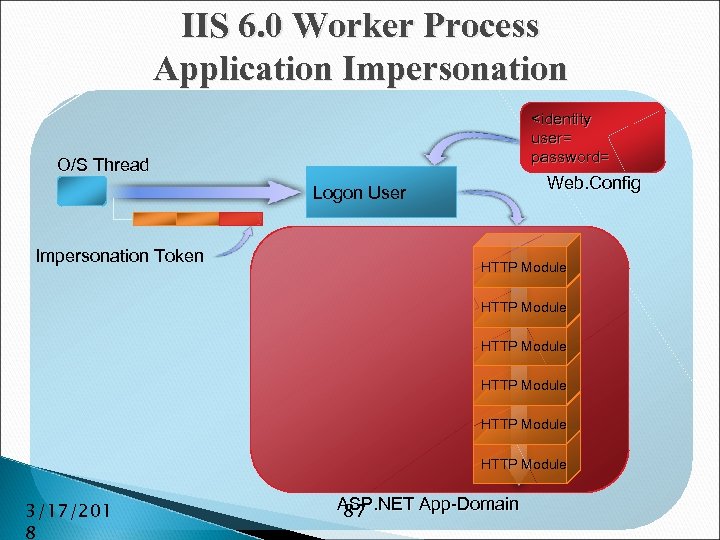 IIS 6. 0 Worker Process Application Impersonation
IIS 6. 0 Worker Process Application Impersonation
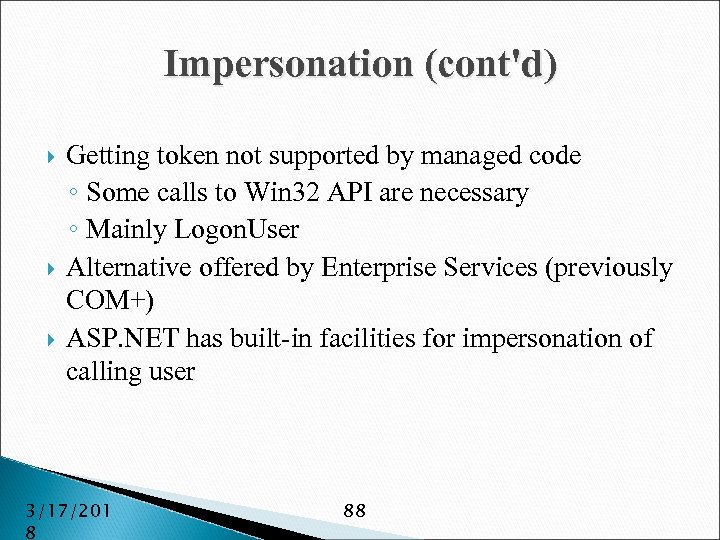 Impersonation (cont'd) Getting token not supported by managed code ◦ Some calls to Win 32 API are necessary ◦ Mainly Logon. User Alternative offered by Enterprise Services (previously COM+) ASP. NET has built-in facilities for impersonation of calling user 3/17/201 8 88
Impersonation (cont'd) Getting token not supported by managed code ◦ Some calls to Win 32 API are necessary ◦ Mainly Logon. User Alternative offered by Enterprise Services (previously COM+) ASP. NET has built-in facilities for impersonation of calling user 3/17/201 8 88
 Working with principals Create your own principals ◦ Windows. Principals are only created explicitly to evaluate Windows groups ◦ Generic principals for ASP. NET and custom authentication Set or replace principal of current thread ◦ By default new threads take principal from spawning thread ◦ Set principal for new threads using current App. Domain's Set. Thread. Principal method ◦ Code needs to have Control. Principal rights 3/17/201 8 89
Working with principals Create your own principals ◦ Windows. Principals are only created explicitly to evaluate Windows groups ◦ Generic principals for ASP. NET and custom authentication Set or replace principal of current thread ◦ By default new threads take principal from spawning thread ◦ Set principal for new threads using current App. Domain's Set. Thread. Principal method ◦ Code needs to have Control. Principal rights 3/17/201 8 89
 Generic classes Generic. Identity and Generic. Principal ◦ For custom authentication ◦ Used by ASP. NET Forms Authentication Complete freedom on choice of identity names and corresponding roles ◦ Probably based upon application specific scenario or requirements 3/17/201 8 90
Generic classes Generic. Identity and Generic. Principal ◦ For custom authentication ◦ Used by ASP. NET Forms Authentication Complete freedom on choice of identity names and corresponding roles ◦ Probably based upon application specific scenario or requirements 3/17/201 8 90
 Working with generic objects Common scenario ◦ Retrieve names and roles from database ◦ If credentials are stored in database, securely store password Create Generic. Identity first ◦ Constructor accepts string for username Principal is created by supplying: ◦ Previously created (Generic)Identity ◦ String array containing names of roles 3/17/201 8 91
Working with generic objects Common scenario ◦ Retrieve names and roles from database ◦ If credentials are stored in database, securely store password Create Generic. Identity first ◦ Constructor accepts string for username Principal is created by supplying: ◦ Previously created (Generic)Identity ◦ String array containing names of roles 3/17/201 8 91
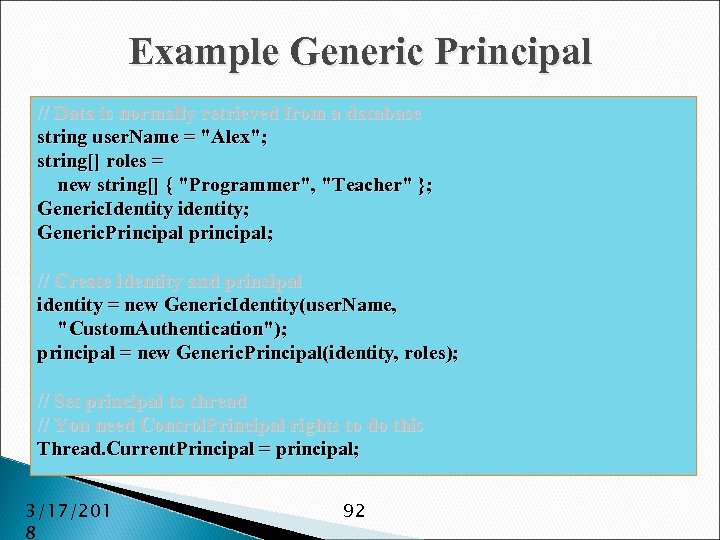 Example Generic Principal // Data is normally retrieved from a database string user. Name = "Alex"; string[] roles = new string[] { "Programmer", "Teacher" }; Generic. Identity identity; Generic. Principal principal; // Create identity and principal identity = new Generic. Identity(user. Name, "Custom. Authentication"); principal = new Generic. Principal(identity, roles); // Set principal to thread // You need Control. Principal rights to do this Thread. Current. Principal = principal; 3/17/201 8 92
Example Generic Principal // Data is normally retrieved from a database string user. Name = "Alex"; string[] roles = new string[] { "Programmer", "Teacher" }; Generic. Identity identity; Generic. Principal principal; // Create identity and principal identity = new Generic. Identity(user. Name, "Custom. Authentication"); principal = new Generic. Principal(identity, roles); // Set principal to thread // You need Control. Principal rights to do this Thread. Current. Principal = principal; 3/17/201 8 92
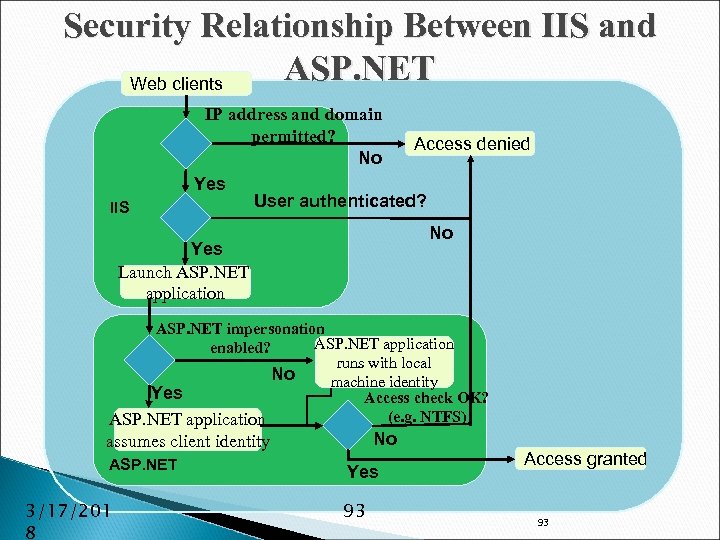 Security Relationship Between IIS and ASP. NET Web clients IIS IP address and domain permitted? Access denied No Yes User authenticated? No Yes Launch ASP. NET application ASP. NET impersonation ASP. NET application enabled? runs with local No machine identity Yes Access check OK? (e. g. NTFS) ASP. NET application No assumes client identity ASP. NET 3/17/201 8 Yes 93 Access granted 93
Security Relationship Between IIS and ASP. NET Web clients IIS IP address and domain permitted? Access denied No Yes User authenticated? No Yes Launch ASP. NET application ASP. NET impersonation ASP. NET application enabled? runs with local No machine identity Yes Access check OK? (e. g. NTFS) ASP. NET application No assumes client identity ASP. NET 3/17/201 8 Yes 93 Access granted 93
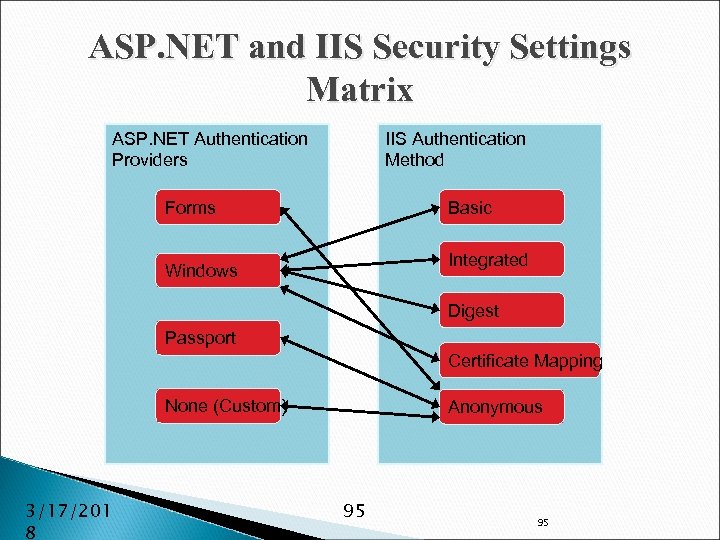
 ASP. NET Authentication Providers and IIS Security ASP. NET supports three authentication providers: ◦ Forms Authentication – Relies on a logon form and cookies ◦ Passport Authentication – Centralized authentication service provided by Microsoft ◦ Windows Authentication – IIS handles authentication Provider web. config file --> Web. config file
ASP. NET Authentication Providers and IIS Security ASP. NET supports three authentication providers: ◦ Forms Authentication – Relies on a logon form and cookies ◦ Passport Authentication – Centralized authentication service provided by Microsoft ◦ Windows Authentication – IIS handles authentication Provider web. config file --> Web. config file
 Overview of Basic Authentication IIS instructs the browser to send the user's credentials over HTTP ◦ Browser prompts the user with a dialog box ◦ User names and passwords are sent using Base 64 encoding, which is NOT secure Most browsers support Basic authentication 3/17/201 8 109
Overview of Basic Authentication IIS instructs the browser to send the user's credentials over HTTP ◦ Browser prompts the user with a dialog box ◦ User names and passwords are sent using Base 64 encoding, which is NOT secure Most browsers support Basic authentication 3/17/201 8 109
 Basic Authentication Typical usage scenarios Consider Basic authentication when you require: ◦ Users to have Windows NT Domain or Active Directory accounts ◦ Support for multiple browsers ◦ Support for authentication over the Internet ◦ Access to the clear text password in your application code ◦ Delegation Do not use Basic authentication when you require: ◦ Secure logon while not using a secure channel, such as Secure Sockets Layer (SSL) ◦ Storage of information in a custom database ◦ A customized form presented to the user as a logon page 3/17/201 8 110
Basic Authentication Typical usage scenarios Consider Basic authentication when you require: ◦ Users to have Windows NT Domain or Active Directory accounts ◦ Support for multiple browsers ◦ Support for authentication over the Internet ◦ Access to the clear text password in your application code ◦ Delegation Do not use Basic authentication when you require: ◦ Secure logon while not using a secure channel, such as Secure Sockets Layer (SSL) ◦ Storage of information in a custom database ◦ A customized form presented to the user as a logon page 3/17/201 8 110
 Basic Authentication Other considerations Delegation is possible using Basic authentication Combine Basic authentication with SSL to prevent passwords from being deciphered 3/17/201 8 111
Basic Authentication Other considerations Delegation is possible using Basic authentication Combine Basic authentication with SSL to prevent passwords from being deciphered 3/17/201 8 111
 Basic Authentication Implementation Configure IIS for Basic authentication Configure user accounts to have "log on locally" enabled on Web server Configure the ASP. NET Web. config file
Basic Authentication Implementation Configure IIS for Basic authentication Configure user accounts to have "log on locally" enabled on Web server Configure the ASP. NET Web. config file
 Overview of Digest Authentication New to Windows 2000 and IIS 5. 0 Encrypts the user's password using MD 5 Dependent on browser and server capabilities Cannot perform delegation 3/17/201 8 113
Overview of Digest Authentication New to Windows 2000 and IIS 5. 0 Encrypts the user's password using MD 5 Dependent on browser and server capabilities Cannot perform delegation 3/17/201 8 113
 Digest Authentication Typical usage scenarios Consider Digest authentication when: ◦ The Web server is running Windows 2000 and users have Windows accounts stored in Active Directory ◦ All clients use either the. NET platform or Internet Explorer 5. 0 or later ◦ Password encryption above that of Basic authentication is required ◦ Support of authentication over the Internet is required Do not use Digest authentication when: ◦ Some clients use platforms other than. NET or Internet Explorer 5. 0 or later ◦ Users do not have Windows accounts stored in Active Directory ◦ Delegation is required 3/17/201 8 114
Digest Authentication Typical usage scenarios Consider Digest authentication when: ◦ The Web server is running Windows 2000 and users have Windows accounts stored in Active Directory ◦ All clients use either the. NET platform or Internet Explorer 5. 0 or later ◦ Password encryption above that of Basic authentication is required ◦ Support of authentication over the Internet is required Do not use Digest authentication when: ◦ Some clients use platforms other than. NET or Internet Explorer 5. 0 or later ◦ Users do not have Windows accounts stored in Active Directory ◦ Delegation is required 3/17/201 8 114
 Digest Authentication Other considerations Security ◦ Digest authentication is more secure than Basic authentication alone ◦ Less secure than Basic authentication with SSL ◦ Can also be combined with SSL Platform requirements for Digest authentication ◦ Clients –. NET or Internet Explorer 5. 0 (or later) ◦ Server – running Active Directory with user accounts configured for Digest authentication 3/17/201 8 115
Digest Authentication Other considerations Security ◦ Digest authentication is more secure than Basic authentication alone ◦ Less secure than Basic authentication with SSL ◦ Can also be combined with SSL Platform requirements for Digest authentication ◦ Clients –. NET or Internet Explorer 5. 0 (or later) ◦ Server – running Active Directory with user accounts configured for Digest authentication 3/17/201 8 115
 Digest Authentication Implementation Configure IIS for Digest authentication Configure the ASP. NET Web. config file
Digest Authentication Implementation Configure IIS for Digest authentication Configure the ASP. NET Web. config file
 Overview of Integrated Windows Authentication Uses either NTLM challenge/response or Kerberos to authenticate users with a Windows NT Domain or Active Directory account No password is sent across the network Best suited to an intranet environment Works with Internet Explorer 3. 01 or later 3/17/201 8 117
Overview of Integrated Windows Authentication Uses either NTLM challenge/response or Kerberos to authenticate users with a Windows NT Domain or Active Directory account No password is sent across the network Best suited to an intranet environment Works with Internet Explorer 3. 01 or later 3/17/201 8 117
 Integrated Windows Authentication Typical usage scenarios Consider Integrated Windows authentication when: ◦ ◦ ◦ Users have Windows NT Domain or Active Directory accounts Your application runs on an intranet (behind a firewall) All clients are running Internet Explorer 3. 01 or later Delegation is required (requires Kerberos) Seamless logon procedure for domain users is required (e. g. without pop-up logon dialog boxes) Do not use Integrated Windows authentication when: ◦ ◦ User accounts are stored in an external database Authentication over the Internet is required Clients are using non-Microsoft browsers You need the client's clear text password 3/17/201 8 118
Integrated Windows Authentication Typical usage scenarios Consider Integrated Windows authentication when: ◦ ◦ ◦ Users have Windows NT Domain or Active Directory accounts Your application runs on an intranet (behind a firewall) All clients are running Internet Explorer 3. 01 or later Delegation is required (requires Kerberos) Seamless logon procedure for domain users is required (e. g. without pop-up logon dialog boxes) Do not use Integrated Windows authentication when: ◦ ◦ User accounts are stored in an external database Authentication over the Internet is required Clients are using non-Microsoft browsers You need the client's clear text password 3/17/201 8 118
 Integrated Windows Authentication Other considerations NTLM and Kerberos are considered highly secure NTLM does not support delegation; Kerberos does Neither NTLM or Kerberos are commonly used over the Internet Kerberos is faster than NTLM, but neither is as fast as Basic authentication 3/17/201 8 119
Integrated Windows Authentication Other considerations NTLM and Kerberos are considered highly secure NTLM does not support delegation; Kerberos does Neither NTLM or Kerberos are commonly used over the Internet Kerberos is faster than NTLM, but neither is as fast as Basic authentication 3/17/201 8 119
 Integrated Windows Authentication Implementation Clients and servers must be running Windows 2000 in a Windows 2000 domain ◦ User and service accounts must be enabled for delegation Configure IIS for Integrated Windows authentication Configure the ASP. NET Web. config file
Integrated Windows Authentication Implementation Clients and servers must be running Windows 2000 in a Windows 2000 domain ◦ User and service accounts must be enabled for delegation Configure IIS for Integrated Windows authentication Configure the ASP. NET Web. config file
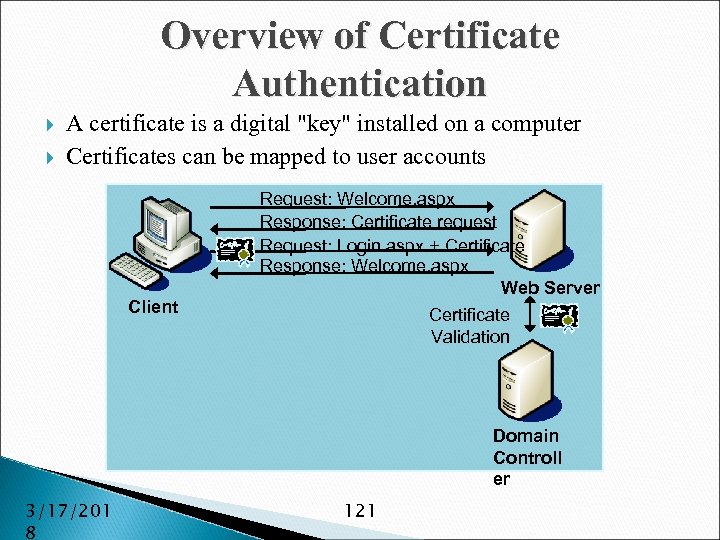 Overview of Certificate Authentication A certificate is a digital "key" installed on a computer Certificates can be mapped to user accounts Client Request: Welcome. aspx Response: Certificate request Request: Login. aspx + Certificate Response: Welcome. aspx Web Server Certificate Validation Domain Controll er 3/17/201 8 121
Overview of Certificate Authentication A certificate is a digital "key" installed on a computer Certificates can be mapped to user accounts Client Request: Welcome. aspx Response: Certificate request Request: Login. aspx + Certificate Response: Welcome. aspx Web Server Certificate Validation Domain Controll er 3/17/201 8 121
 Certificate Authentication Typical usage scenarios Consider Certificate authentication when: ◦ Data is considered very sensitive and you require a very secure solution ◦ Mutual authentication is required ◦ Third parties will manage the relationship between the server and the certificate holder ◦ Client interaction must be seamless; for example, automated B 2 B exchanges Do not use Certificate authentication when: ◦ The cost of issuing and managing client certificates outweighs the value of the added security 3/17/201 8 122
Certificate Authentication Typical usage scenarios Consider Certificate authentication when: ◦ Data is considered very sensitive and you require a very secure solution ◦ Mutual authentication is required ◦ Third parties will manage the relationship between the server and the certificate holder ◦ Client interaction must be seamless; for example, automated B 2 B exchanges Do not use Certificate authentication when: ◦ The cost of issuing and managing client certificates outweighs the value of the added security 3/17/201 8 122
 Certificate Authentication Other considerations Client certificates must be deployed to the client workstations Map certificates to: ◦ Individual user accounts (one-to-one mapping) ◦ Any user from a single company (many-to-one mapping) 3/17/201 8 123
Certificate Authentication Other considerations Client certificates must be deployed to the client workstations Map certificates to: ◦ Individual user accounts (one-to-one mapping) ◦ Any user from a single company (many-to-one mapping) 3/17/201 8 123
 Certificate Authentication Implementation Configure IIS for Certificate authentication Configure the ASP. NET Web. config file
Certificate Authentication Implementation Configure IIS for Certificate authentication Configure the ASP. NET Web. config file
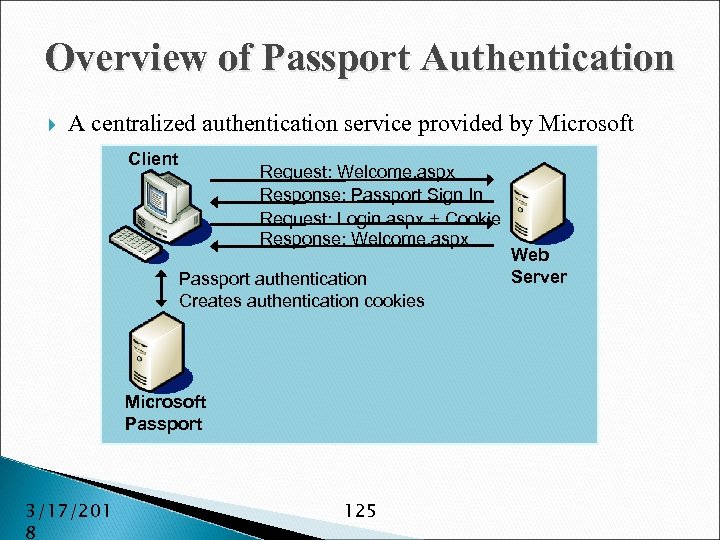 Overview of Passport Authentication A centralized authentication service provided by Microsoft Client Request: Welcome. aspx Response: Passport Sign In Request: Login. aspx + Cookie Response: Welcome. aspx Passport authentication Creates authentication cookies Microsoft Passport 3/17/201 8 125 Web Server
Overview of Passport Authentication A centralized authentication service provided by Microsoft Client Request: Welcome. aspx Response: Passport Sign In Request: Login. aspx + Cookie Response: Welcome. aspx Passport authentication Creates authentication cookies Microsoft Passport 3/17/201 8 125 Web Server
 Passport Authentication Typical usage scenarios Consider Passport authentication when: ◦ Your site will interact with other Passport-enabled sites ◦ Single sign-on capability is required ◦ External maintenance of user names and passwords is useful Do not use Passport authentication when: ◦ You want to user names and passwords already stored in your own database or Active Directory ◦ Clients are other applications that access the site programmatically 3/17/201 8 126
Passport Authentication Typical usage scenarios Consider Passport authentication when: ◦ Your site will interact with other Passport-enabled sites ◦ Single sign-on capability is required ◦ External maintenance of user names and passwords is useful Do not use Passport authentication when: ◦ You want to user names and passwords already stored in your own database or Active Directory ◦ Clients are other applications that access the site programmatically 3/17/201 8 126
 Passport Authentication Other considerations Requires registration with the Passport service and installation of the Passport SDK on the server Delegation is not possible on Windows 2000 Passport User ID (PUID) is an identity only ◦ Implement code to map PUID to users in Active Directory or custom database Passport uses encrypted cookies making system secure ◦ Combine Passport with SSL to prevent replay attacks for highest level of security 3/17/201 8 127
Passport Authentication Other considerations Requires registration with the Passport service and installation of the Passport SDK on the server Delegation is not possible on Windows 2000 Passport User ID (PUID) is an identity only ◦ Implement code to map PUID to users in Active Directory or custom database Passport uses encrypted cookies making system secure ◦ Combine Passport with SSL to prevent replay attacks for highest level of security 3/17/201 8 127
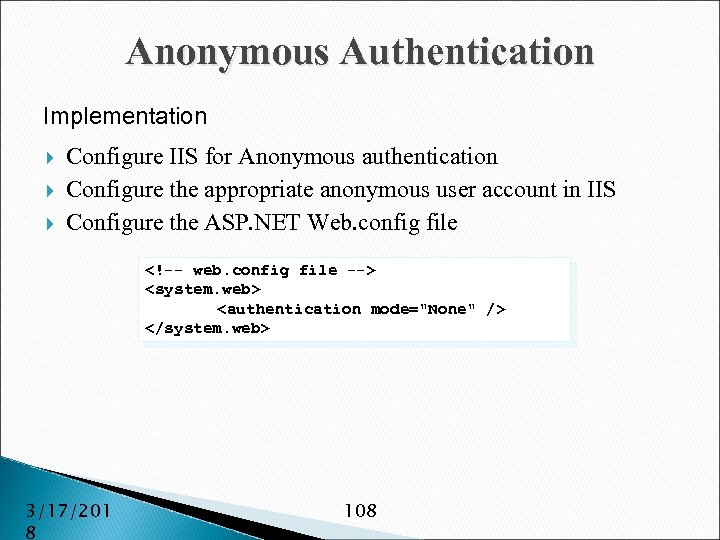
 Passport Authentication Implementation Install Passport SDK on server Register with Passport service Configure IIS for Anonymous authentication Configure the ASP. NET Web. config file
Passport Authentication Implementation Install Passport SDK on server Register with Passport service Configure IIS for Anonymous authentication Configure the ASP. NET Web. config file
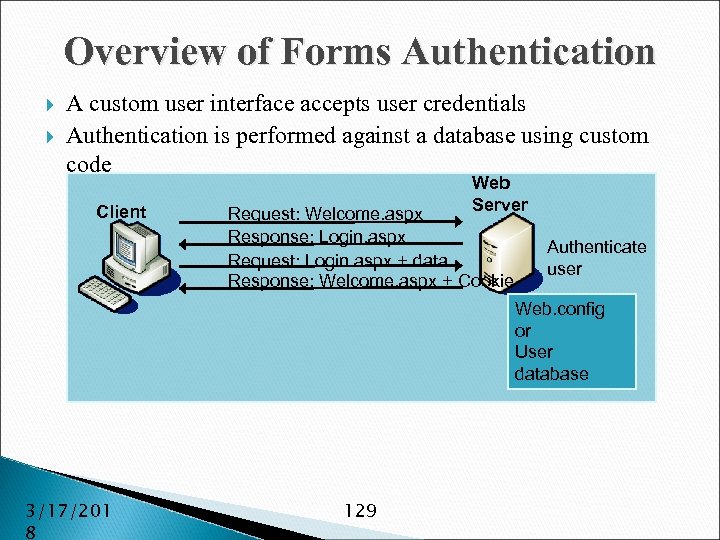 Overview of Forms Authentication A custom user interface accepts user credentials Authentication is performed against a database using custom code Client Web Server Request: Welcome. aspx Response: Login. aspx Request: Login. aspx + data Response: Welcome. aspx + Cookie Authenticate user Web. config or User database 3/17/201 8 129
Overview of Forms Authentication A custom user interface accepts user credentials Authentication is performed against a database using custom code Client Web Server Request: Welcome. aspx Response: Login. aspx Request: Login. aspx + data Response: Welcome. aspx + Cookie Authenticate user Web. config or User database 3/17/201 8 129
 Forms Authentication Flow 3/17/201 8 130
Forms Authentication Flow 3/17/201 8 130
 Forms Authentication Typical usage scenarios Consider Forms authentication when: ◦ User names and passwords are stored somewhere other than Windows accounts ◦ Your application runs over the Internet ◦ Support for all browsers and client operating systems is required ◦ A custom logon page is needed Do not use Forms authentication when: ◦ Applications are deployed on a corporate intranet and can take advantage of Integrated Windows authentication ◦ You cannot programmatically verify the user name and password 3/17/201 8 131
Forms Authentication Typical usage scenarios Consider Forms authentication when: ◦ User names and passwords are stored somewhere other than Windows accounts ◦ Your application runs over the Internet ◦ Support for all browsers and client operating systems is required ◦ A custom logon page is needed Do not use Forms authentication when: ◦ Applications are deployed on a corporate intranet and can take advantage of Integrated Windows authentication ◦ You cannot programmatically verify the user name and password 3/17/201 8 131
 Forms Authentication Other considerations Use SSL to secure passwords submitted via the logon page Set cookie expiration to avoid cookie theft and misuse SSL degrades performance, so consider separating logon and content servers Checking for the cookie is automatic in ASP. NET applications Use Forms authentication with Windows accounts as an alternative to Basic or Digest authentication 3/17/201 8 132
Forms Authentication Other considerations Use SSL to secure passwords submitted via the logon page Set cookie expiration to avoid cookie theft and misuse SSL degrades performance, so consider separating logon and content servers Checking for the cookie is automatic in ASP. NET applications Use Forms authentication with Windows accounts as an alternative to Basic or Digest authentication 3/17/201 8 132
 Forms Authentication Implementation Create a logon page Create your custom account information lookup code Configure IIS for Anonymous authentication Configure the ASP. NET Web. config file, including the redirect URL for unauthenticated clients
Forms Authentication Implementation Create a logon page Create your custom account information lookup code Configure IIS for Anonymous authentication Configure the ASP. NET Web. config file, including the redirect URL for unauthenticated clients
 Authorization Process of determining whether a user is allowed to perform a requested action File-based authorization ◦ Performed by File. Authorization. Module ◦ Performs checks against Windows ACLs Custom – handle Authorize. Request event ◦ Application level (global. asax) ◦ HTTP module (implement IHttp. Module) URL-based authorization ◦ Performed by Url. Authorization. Module 3/17/201 8 134
Authorization Process of determining whether a user is allowed to perform a requested action File-based authorization ◦ Performed by File. Authorization. Module ◦ Performs checks against Windows ACLs Custom – handle Authorize. Request event ◦ Application level (global. asax) ◦ HTTP module (implement IHttp. Module) URL-based authorization ◦ Performed by Url. Authorization. Module 3/17/201 8 134
 Windows Users(Check Roles) If User. Is. In. Role("BUILTINAdministrators") then Response. Write("You are an Admin") Else If User. Is. In. Role("BUILTINUsers") then Response. Write("You are a User") Else Response. Write("Invalid user") End if 3/17/201 8 135
Windows Users(Check Roles) If User. Is. In. Role("BUILTINAdministrators") then Response. Write("You are an Admin") Else If User. Is. In. Role("BUILTINUsers") then Response. Write("You are a User") Else Response. Write("Invalid user") End if 3/17/201 8 135
 Non-Windows Users(Attach Roles) Handle Authenticate. Request event ◦ Create Generic. Principle ◦ Attach roles to Identity ◦ Assign new Principle to User Sub Application_Authenticate. Request(s As Object, e As Event. Args) If Not (User Is Nothing) Then If User. Identity. Authentication. Type = "Forms" Then Dim Roles(1) As String Roles(0) = "Admin" User = new Generic. Principle(User. Identity, Roles) End If End Sub 3/17/201 8 136
Non-Windows Users(Attach Roles) Handle Authenticate. Request event ◦ Create Generic. Principle ◦ Attach roles to Identity ◦ Assign new Principle to User Sub Application_Authenticate. Request(s As Object, e As Event. Args) If Not (User Is Nothing) Then If User. Identity. Authentication. Type = "Forms" Then Dim Roles(1) As String Roles(0) = "Admin" User = new Generic. Principle(User. Identity, Roles) End If End Sub 3/17/201 8 136
 Non-Windows Users (Check Roles) if User. Is. In. Role("Admin") then Response. Write ("You are an Administrator") Else Response. Write ("You do not have any role assigned") End if 3/17/201 8 137
Non-Windows Users (Check Roles) if User. Is. In. Role("Admin") then Response. Write ("You are an Administrator") Else Response. Write ("You do not have any role assigned") End if 3/17/201 8 137
 Summary Security is a war! Don’t fight fair. Defense in Layers Make Security part of every aspect of your projects o should be about 12% of effort per project. NET provides means for the info to travel seamlessly and securely between applications , web sites and devices. . NET provides all round security in to the new world of distributed computing and WS. Rich set of cryptography services 3/17/201 8 138
Summary Security is a war! Don’t fight fair. Defense in Layers Make Security part of every aspect of your projects o should be about 12% of effort per project. NET provides means for the info to travel seamlessly and securely between applications , web sites and devices. . NET provides all round security in to the new world of distributed computing and WS. Rich set of cryptography services 3/17/201 8 138
 More Information How ASP Security Works ◦ An overview of ASP Security http: //msdn 2. microsoft. com/en-us/security/aa 336653. aspx How to Security ◦ Learn about security as it applies to. NET. http: //msdn 2. microsoft. com/en-us/security/aa 570406. aspx Tech. Net Security Site (IT professionals) http: //www. microsoft. com/technet/security/default. mspx Other Resources ◦ http: //www. gotdotnet. com/ 3/17/201 8 139
More Information How ASP Security Works ◦ An overview of ASP Security http: //msdn 2. microsoft. com/en-us/security/aa 336653. aspx How to Security ◦ Learn about security as it applies to. NET. http: //msdn 2. microsoft. com/en-us/security/aa 570406. aspx Tech. Net Security Site (IT professionals) http: //www. microsoft. com/technet/security/default. mspx Other Resources ◦ http: //www. gotdotnet. com/ 3/17/201 8 139
 Questions 3/17/201 8 140
Questions 3/17/201 8 140