a08515800e0094c619ec82c3c7d6737b.ppt
- Количество слайдов: 39
 NCMS Capital Region Chapter 11 August 2010 Presented by: Tanya Elliott CACI
NCMS Capital Region Chapter 11 August 2010 Presented by: Tanya Elliott CACI
 Procedures Governing Use of JPAS by Cleared Contractors Defense Security Service – April 2007 § DSS will suspend the access of contractors that do not comply with these procedures or violate the terms of user agreements § National Industrial Security Program Operating Manual (NISPOM) paragraph 2 -200 b states that “When the CSA [Cognizant Security Agency] has designated a database as the system of record for contractor eligibility and access, the contractor shall be responsible for annotating and maintaining the accuracy of their employees’ access records. Specific procedures will be provided by the CSA. ” The Department of Defense, acting as a CSA, has designated the Joint Personnel Adjudication System (JPAS) as the Do. D system of record for contractor eligibility and access. § JPAS is a U. S. Government information system that contains official government records. The information in JPAS must be protected from unauthorized disclosure and used only for authorized purposes. Contractors may only use their JPAS accounts to manage the access records of their employees and consultants, and to verify the access levels and affiliations (e. g. , employee of ABC Company) of incoming visitors who require access to classified information. § The following procedures are issued under the authority provided by NISPOM paragraph 2 -200 b. Contractors shall follow these procedures when using JPAS and shall ensure that authorized users of JPAS have been properly informed about these procedures and any other specific policies governing access to and use of JPAS. 1. Contractors shall accurately maintain the JPAS records pertaining to their employees and consultants. Contractors must expeditiously update these records when changes occur (e. g. , termination of employment). 2. Contractors are prohibited from placing false information in JPAS, and DSS will seek appropriate sanctions against contractors and contractor employees who knowingly place false information in JPAS.
Procedures Governing Use of JPAS by Cleared Contractors Defense Security Service – April 2007 § DSS will suspend the access of contractors that do not comply with these procedures or violate the terms of user agreements § National Industrial Security Program Operating Manual (NISPOM) paragraph 2 -200 b states that “When the CSA [Cognizant Security Agency] has designated a database as the system of record for contractor eligibility and access, the contractor shall be responsible for annotating and maintaining the accuracy of their employees’ access records. Specific procedures will be provided by the CSA. ” The Department of Defense, acting as a CSA, has designated the Joint Personnel Adjudication System (JPAS) as the Do. D system of record for contractor eligibility and access. § JPAS is a U. S. Government information system that contains official government records. The information in JPAS must be protected from unauthorized disclosure and used only for authorized purposes. Contractors may only use their JPAS accounts to manage the access records of their employees and consultants, and to verify the access levels and affiliations (e. g. , employee of ABC Company) of incoming visitors who require access to classified information. § The following procedures are issued under the authority provided by NISPOM paragraph 2 -200 b. Contractors shall follow these procedures when using JPAS and shall ensure that authorized users of JPAS have been properly informed about these procedures and any other specific policies governing access to and use of JPAS. 1. Contractors shall accurately maintain the JPAS records pertaining to their employees and consultants. Contractors must expeditiously update these records when changes occur (e. g. , termination of employment). 2. Contractors are prohibited from placing false information in JPAS, and DSS will seek appropriate sanctions against contractors and contractor employees who knowingly place false information in JPAS.
 Procedures Governing Use of JPAS by Cleared Contractors Defense Security Service – April 2007 3. Do. D issues JPAS accounts exclusively for use by a specific contractor or corporate family of contractors. Persons given access to JPAS as account holders may only use JPAS on behalf of the cleared contractor or corporate family of contractors through which the account was issued. For example, an employee of ABC Company holding a JPAS account issued through ABC Company and who works at a government site is not authorized to use the contractor-granted account in support of the government customer. If the government customer requires the contractor employee to review or update JPAS records on behalf of the government customer, the government customer must provide the JPAS account for the contractor employee to use. 4. The JPAS account manager must be a company employee. The JPAS account manager cannot be a subcontractor or consultant. 5. Contractors may subcontract or obtain consultant support for administering security services. The using contractor will provide a JPAS account to the subcontractor or consultant under the using contractor’s Security Management Office (SMO) for the sole purpose of permitting the subcontractor or consultant to provide security services for the using company. Subcontractors or consultants providing such security services must be under the direct supervision of the using contractor’s FSO or FSO’s designee. 6. Each individual accessing JPAS must have a separate and unique account created by the individual’s JPAS account manager. The account manager must maintain a current record of every JPAS account established. 7. JPAS users may never share their user names, passwords, or other authentication information with any other individual, including anyone who is a designee or an alternate to the account holder. 8. Contractors must not allow any practices that include sharing user names, passwords, or other authentication information, and must have policies in place that guard against such practices. Contractors can establish JPAS accounts for additional users when a reasonable need exists.
Procedures Governing Use of JPAS by Cleared Contractors Defense Security Service – April 2007 3. Do. D issues JPAS accounts exclusively for use by a specific contractor or corporate family of contractors. Persons given access to JPAS as account holders may only use JPAS on behalf of the cleared contractor or corporate family of contractors through which the account was issued. For example, an employee of ABC Company holding a JPAS account issued through ABC Company and who works at a government site is not authorized to use the contractor-granted account in support of the government customer. If the government customer requires the contractor employee to review or update JPAS records on behalf of the government customer, the government customer must provide the JPAS account for the contractor employee to use. 4. The JPAS account manager must be a company employee. The JPAS account manager cannot be a subcontractor or consultant. 5. Contractors may subcontract or obtain consultant support for administering security services. The using contractor will provide a JPAS account to the subcontractor or consultant under the using contractor’s Security Management Office (SMO) for the sole purpose of permitting the subcontractor or consultant to provide security services for the using company. Subcontractors or consultants providing such security services must be under the direct supervision of the using contractor’s FSO or FSO’s designee. 6. Each individual accessing JPAS must have a separate and unique account created by the individual’s JPAS account manager. The account manager must maintain a current record of every JPAS account established. 7. JPAS users may never share their user names, passwords, or other authentication information with any other individual, including anyone who is a designee or an alternate to the account holder. 8. Contractors must not allow any practices that include sharing user names, passwords, or other authentication information, and must have policies in place that guard against such practices. Contractors can establish JPAS accounts for additional users when a reasonable need exists.
 Procedures Governing Use of JPAS by Cleared Contractors Defense Security Service – April 2007 9. Access to JPAS is only authorized by means of company or government-owned equipment with appropriate security controls in place. JPAS users may not access their accounts from personal or home computers. 10. Contractors are not permitted to change an existing date notation in JPAS for the Classified Information Nondisclosure Agreement (SF 312). Contractors must, however, input the date that the SF 312 was signed when JPAS does not reflect a date. 11. Contractors are authorized to verify prospective employees’ eligibility for access to classified information in JPAS prior to an offer of employment being extended. However, contractors may not use JPAS for recruiting purposes. 12. While access to JPAS is only granted to contractors who have a legitimate need for such access in support of classified work being performed for the Government, JPAS is not a classified system. DSS will not grant a facility security clearance (FCL) for the sole purpose of allowing a company or its employees to gain access to JPAS. 13. Any contractor with JPAS access that becomes aware of a violation of these procedures shall immediately report the nature of the violation, the names of the responsible parties, and a description of remedial action taken, to the servicing DSS Industrial Security Representative. NOTE: Violations of the procedures may lead DSS to suspend or withdraw JPAS access, terminate the JPAS account, or exclude culpable companies or persons from access to JPAS for a specified or indefinite period. DSS will also refer information concerning violations of these procedures to other federal agencies for consideration of administrative, civil or criminal sanctions when circumstances warrant.
Procedures Governing Use of JPAS by Cleared Contractors Defense Security Service – April 2007 9. Access to JPAS is only authorized by means of company or government-owned equipment with appropriate security controls in place. JPAS users may not access their accounts from personal or home computers. 10. Contractors are not permitted to change an existing date notation in JPAS for the Classified Information Nondisclosure Agreement (SF 312). Contractors must, however, input the date that the SF 312 was signed when JPAS does not reflect a date. 11. Contractors are authorized to verify prospective employees’ eligibility for access to classified information in JPAS prior to an offer of employment being extended. However, contractors may not use JPAS for recruiting purposes. 12. While access to JPAS is only granted to contractors who have a legitimate need for such access in support of classified work being performed for the Government, JPAS is not a classified system. DSS will not grant a facility security clearance (FCL) for the sole purpose of allowing a company or its employees to gain access to JPAS. 13. Any contractor with JPAS access that becomes aware of a violation of these procedures shall immediately report the nature of the violation, the names of the responsible parties, and a description of remedial action taken, to the servicing DSS Industrial Security Representative. NOTE: Violations of the procedures may lead DSS to suspend or withdraw JPAS access, terminate the JPAS account, or exclude culpable companies or persons from access to JPAS for a specified or indefinite period. DSS will also refer information concerning violations of these procedures to other federal agencies for consideration of administrative, civil or criminal sanctions when circumstances warrant.
 JPAS Training - JPAS/JCAVS Virtual Training for Security Professionals § Course Title: JPAS/JCAVS VIRTUAL TRAINING FOR SECURITY PROFESSIONALS § Course Description: JPAS/JCAVS Virtual Training for Security Professionals provides an overview of the Joint Personnel Adjudication System (JPAS) and a detailed explanation of its subsystem, the Joint Clearance and Access Verification System (JCAVS) used extensively by Do. D Personnel Security Managers (PSMs) and contractor Facility Security Officers (FSOs) for eligibility and investigation verification. The course is formatted to include demonstration followed by knowledge checks and practical exercises. Participants will complete task in a virtual JPAS environment and navigate various windows and practice specific actions to perform desired functions. § Link to ENROL: The following link will take you to the Defense Security Service (DSS) ENROL system: https: //enrol. dss. mil/enrol/lang-default/SYS_login. asp. where you can register for the course or create a new account.
JPAS Training - JPAS/JCAVS Virtual Training for Security Professionals § Course Title: JPAS/JCAVS VIRTUAL TRAINING FOR SECURITY PROFESSIONALS § Course Description: JPAS/JCAVS Virtual Training for Security Professionals provides an overview of the Joint Personnel Adjudication System (JPAS) and a detailed explanation of its subsystem, the Joint Clearance and Access Verification System (JCAVS) used extensively by Do. D Personnel Security Managers (PSMs) and contractor Facility Security Officers (FSOs) for eligibility and investigation verification. The course is formatted to include demonstration followed by knowledge checks and practical exercises. Participants will complete task in a virtual JPAS environment and navigate various windows and practice specific actions to perform desired functions. § Link to ENROL: The following link will take you to the Defense Security Service (DSS) ENROL system: https: //enrol. dss. mil/enrol/lang-default/SYS_login. asp. where you can register for the course or create a new account.
 Personally Identifiable Information (PII) – DSS Requirement Training Requirement as of August 2008: § All personnel, Do. D employees and on/off-site contractors, accessing DSS Systems containing PII (JPAS, ISFD, DCII, ENROL, and SWFT) are required to complete the "Personally Identifiable Information (PII)" e. Learning course. Defense Information Systems Agency (DISA) produced this training to ensure that all personnel accessing PII are adequately trained for handling PII and reporting any theft, loss, or compromise of this information. The course also provides a basic level of understanding of current Do. D PII-related information security principles and requirements. § The following link will take you to the Defense Security Service (DSS) ENROL system: https: //enrol. dss. mil/enrol/lang-default/SYS_login. asp. where you can register for the course or create a new account. § The following file: "access_pii_course. pdf" contains instructions on how to register and start the PII course. § For additional information regarding an ENROL account, contact the Do. D Security Service Center, 1 -888 -282 -7682, occ. cust. serv@dss. mil; for information about the course content contact IA/CND at DSSIACND@dss. mil
Personally Identifiable Information (PII) – DSS Requirement Training Requirement as of August 2008: § All personnel, Do. D employees and on/off-site contractors, accessing DSS Systems containing PII (JPAS, ISFD, DCII, ENROL, and SWFT) are required to complete the "Personally Identifiable Information (PII)" e. Learning course. Defense Information Systems Agency (DISA) produced this training to ensure that all personnel accessing PII are adequately trained for handling PII and reporting any theft, loss, or compromise of this information. The course also provides a basic level of understanding of current Do. D PII-related information security principles and requirements. § The following link will take you to the Defense Security Service (DSS) ENROL system: https: //enrol. dss. mil/enrol/lang-default/SYS_login. asp. where you can register for the course or create a new account. § The following file: "access_pii_course. pdf" contains instructions on how to register and start the PII course. § For additional information regarding an ENROL account, contact the Do. D Security Service Center, 1 -888 -282 -7682, occ. cust. serv@dss. mil; for information about the course content contact IA/CND at DSSIACND@dss. mil
 Release of JPAS Records ISL 2010 -01 #5 § (NISPOM 6 -104 a) Release of JPAS records JPAS, as a U. S. Government information system, contains official government records. The information in JPAS must be protected from unauthorized disclosure and used only for authorized purposes. Contractor personnel may only use their JPAS accounts to manage the access records of their company’s employees and consultants, and to verify the access levels and employment affiliations of incoming visitors who require access to classified information. Contractor personnel are not authorized to, and may not, release printed or electronic copies of JPAS records to any person or entity. The appropriate U. S. Government release authority (commonly in an agency Privacy Act Office) is responsible for making release decisions regarding all JPAS records in accordance with the Privacy Act of 1974. § Update - further clarification and guidance: At a recent DSS Stakeholders meeting the issue of the ISL 2010 -01 #5 regarding the restrictions for the release of JPAS records was addressed. DSS leadership and Policy personnel have acknowledged that additional research and coordination within the US Government is needed on this item. Therefore, in coordination with DSS, and as a temporary measure, industry may continue to use JPAS records when requested or required by any US Government customer for personnel security related processing.
Release of JPAS Records ISL 2010 -01 #5 § (NISPOM 6 -104 a) Release of JPAS records JPAS, as a U. S. Government information system, contains official government records. The information in JPAS must be protected from unauthorized disclosure and used only for authorized purposes. Contractor personnel may only use their JPAS accounts to manage the access records of their company’s employees and consultants, and to verify the access levels and employment affiliations of incoming visitors who require access to classified information. Contractor personnel are not authorized to, and may not, release printed or electronic copies of JPAS records to any person or entity. The appropriate U. S. Government release authority (commonly in an agency Privacy Act Office) is responsible for making release decisions regarding all JPAS records in accordance with the Privacy Act of 1974. § Update - further clarification and guidance: At a recent DSS Stakeholders meeting the issue of the ISL 2010 -01 #5 regarding the restrictions for the release of JPAS records was addressed. DSS leadership and Policy personnel have acknowledged that additional research and coordination within the US Government is needed on this item. Therefore, in coordination with DSS, and as a temporary measure, industry may continue to use JPAS records when requested or required by any US Government customer for personnel security related processing.
 Foreign Passport Disposition § DISCO will not grant or continue a personnel clearance if the individual possesses a current foreign passport § If the FSO accepts a surrendered passport and returns it while it is still current, you must submit an incident report with details concerning the return of the passport § Reasons for the return of the passport should be provided in the incident report § An incident report must be submitted if the passport is returned at the time of the individual's employment termination See DSS News dated: 11/20/09 “Foreign Passport Disposition Influences Personnel Clearance Eligibility” or click the following link: http: //www. dss. mil/diss/jpas. html
Foreign Passport Disposition § DISCO will not grant or continue a personnel clearance if the individual possesses a current foreign passport § If the FSO accepts a surrendered passport and returns it while it is still current, you must submit an incident report with details concerning the return of the passport § Reasons for the return of the passport should be provided in the incident report § An incident report must be submitted if the passport is returned at the time of the individual's employment termination See DSS News dated: 11/20/09 “Foreign Passport Disposition Influences Personnel Clearance Eligibility” or click the following link: http: //www. dss. mil/diss/jpas. html
 PRs for Cleared NISP Contractors (eftv 6/9/10) § DISCO will identify and notify NISP cleared contractor facilities of cleared personnel who are eligible or overdue for a periodic reinvestigation (PR). § Eligibility for a PR is contingent upon the access level and the closed date of the investigation. § Once a cleared contractor facility is notified a PR is due, the contractor facility will have 60 days to submit the SF-86 to DISCO via JPAS. § If the information is not received in 60 days, DISCO will assume the clearance is no longer required, remove the clearance eligibility and send notification to the FSO that the eligibility was withdrawn due to failure to submit the requested forms. § If the cleared contractor facility identifies that the individual still requires a clearance after the eligibility has been withdrawn, the clearance eligibility will be reinstated upon submission of the required information. Access to classified information is not valid during the period that the eligibility is withdrawn until DISCO reinstates the clearance eligibility.
PRs for Cleared NISP Contractors (eftv 6/9/10) § DISCO will identify and notify NISP cleared contractor facilities of cleared personnel who are eligible or overdue for a periodic reinvestigation (PR). § Eligibility for a PR is contingent upon the access level and the closed date of the investigation. § Once a cleared contractor facility is notified a PR is due, the contractor facility will have 60 days to submit the SF-86 to DISCO via JPAS. § If the information is not received in 60 days, DISCO will assume the clearance is no longer required, remove the clearance eligibility and send notification to the FSO that the eligibility was withdrawn due to failure to submit the requested forms. § If the cleared contractor facility identifies that the individual still requires a clearance after the eligibility has been withdrawn, the clearance eligibility will be reinstated upon submission of the required information. Access to classified information is not valid during the period that the eligibility is withdrawn until DISCO reinstates the clearance eligibility.
 PSM Net Validation § From the Main Menu select “PSM Net” § Will take you to JCAVS Maintain PSM Net Screen § Select “Person Categories by Organization” § Click “Add” - Will take you to PSM Net Add Organization Category § Hit “Select Organization” - Will take you to organization search § Select Do. D Contractor Companies § Enter your cage code (plus *) in last box § Click “Search” – selected cage will show up § Click blue link indicating cage code; company name will move to top line § Click “OK” – Will take you back to “PSM Net Add Org…” § Click “Search” § Search result will indicate all persons associated with your cage that are not in your PSM Net § Determine if each person listed should be in your PSM Net § If Yes – In-process and indoctrinate § If No – In-process and out-process using the same date; then go to Maintain Person screen and enter separation date and separation code. At midnight the person will drop out of your PSM Net and will no longer be associated with your Cage
PSM Net Validation § From the Main Menu select “PSM Net” § Will take you to JCAVS Maintain PSM Net Screen § Select “Person Categories by Organization” § Click “Add” - Will take you to PSM Net Add Organization Category § Hit “Select Organization” - Will take you to organization search § Select Do. D Contractor Companies § Enter your cage code (plus *) in last box § Click “Search” – selected cage will show up § Click blue link indicating cage code; company name will move to top line § Click “OK” – Will take you back to “PSM Net Add Org…” § Click “Search” § Search result will indicate all persons associated with your cage that are not in your PSM Net § Determine if each person listed should be in your PSM Net § If Yes – In-process and indoctrinate § If No – In-process and out-process using the same date; then go to Maintain Person screen and enter separation date and separation code. At midnight the person will drop out of your PSM Net and will no longer be associated with your Cage
 Report Types § Act PC-Access/No PSM Net - Lists organizations that have a Person Category for a subject without a PSM Net relationship owned or serviced § Inv Rqst by Duty Pos - This report indicates all Investigation Requests currently in your PSM Net by Duty Position. § Non-SCI Totals - List of all Non-SCI Access’s, for owned and or serviced Person Categories in your PSM Net or subordinate organization. § Periodic Reinvest - List of Personnel within your PSM Net or subordinate organization whose investigation may be out-of-scope and may require a Periodic Reinvestigation § Personnel - Detailed list of Personnel in your PSM Net and or subordinate organization, including access, eligibility and investigation information. § PSM Net Personnel - Abbreviated list of all personnel in your PSM Net or subordinate organization. § SMO-No PSM Net - Retrieve information regarding SMOs in your hierarchy that have not established a PSM Net. § SMO-No Users - Retrieve information regarding SMOs in your hierarchy that have established their SMO but have no Personnel with an Owning or Servicing relationship in their PSM Net. § SMO-PC-No Access - Retrieve information regarding SMOs in your hierarchy that have established their PSM Net but don’t have an access indoctrinated for a Person Category. § Suspense - Retrieves information regarding Suspense information the JCAVS user created from a subject’s Person Summery screen / Suspense Data link. § Suspensions - Information regarding Suspensions (eligibility and/or Access) for personnel in your PSM Net and or subordinate organization.
Report Types § Act PC-Access/No PSM Net - Lists organizations that have a Person Category for a subject without a PSM Net relationship owned or serviced § Inv Rqst by Duty Pos - This report indicates all Investigation Requests currently in your PSM Net by Duty Position. § Non-SCI Totals - List of all Non-SCI Access’s, for owned and or serviced Person Categories in your PSM Net or subordinate organization. § Periodic Reinvest - List of Personnel within your PSM Net or subordinate organization whose investigation may be out-of-scope and may require a Periodic Reinvestigation § Personnel - Detailed list of Personnel in your PSM Net and or subordinate organization, including access, eligibility and investigation information. § PSM Net Personnel - Abbreviated list of all personnel in your PSM Net or subordinate organization. § SMO-No PSM Net - Retrieve information regarding SMOs in your hierarchy that have not established a PSM Net. § SMO-No Users - Retrieve information regarding SMOs in your hierarchy that have established their SMO but have no Personnel with an Owning or Servicing relationship in their PSM Net. § SMO-PC-No Access - Retrieve information regarding SMOs in your hierarchy that have established their PSM Net but don’t have an access indoctrinated for a Person Category. § Suspense - Retrieves information regarding Suspense information the JCAVS user created from a subject’s Person Summery screen / Suspense Data link. § Suspensions - Information regarding Suspensions (eligibility and/or Access) for personnel in your PSM Net and or subordinate organization.
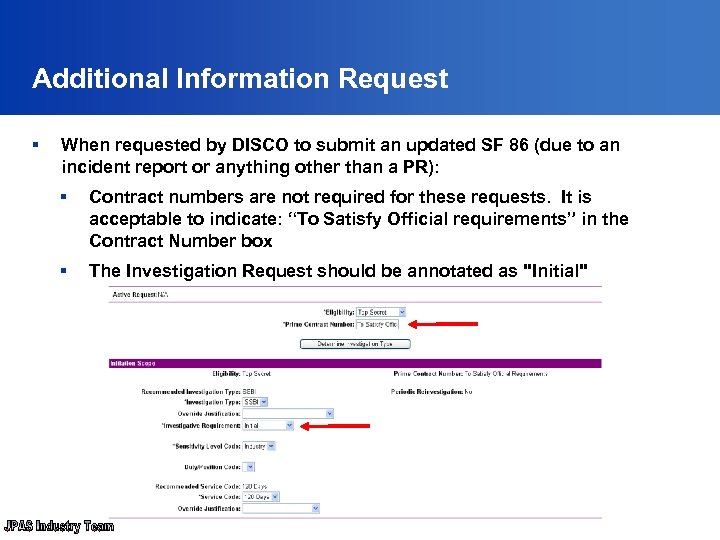 Additional Information Request § When requested by DISCO to submit an updated SF 86 (due to an incident report or anything other than a PR): § Contract numbers are not required for these requests. It is acceptable to indicate: “To Satisfy Official requirements” in the Contract Number box § The Investigation Request should be annotated as "Initial"
Additional Information Request § When requested by DISCO to submit an updated SF 86 (due to an incident report or anything other than a PR): § Contract numbers are not required for these requests. It is acceptable to indicate: “To Satisfy Official requirements” in the Contract Number box § The Investigation Request should be annotated as "Initial"
 Changes to Investigation Request 346 W
Changes to Investigation Request 346 W
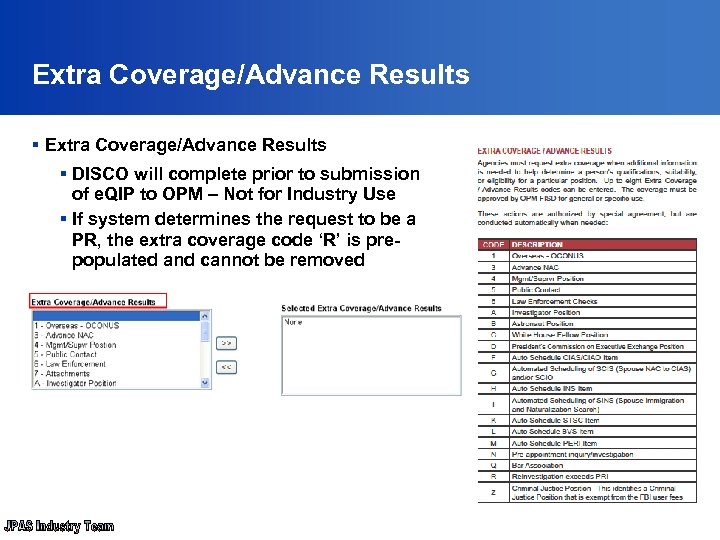 Extra Coverage/Advance Results § DISCO will complete prior to submission of e. QIP to OPM – Not for Industry Use § If system determines the request to be a PR, the extra coverage code ‘R’ is prepopulated and cannot be removed
Extra Coverage/Advance Results § DISCO will complete prior to submission of e. QIP to OPM – Not for Industry Use § If system determines the request to be a PR, the extra coverage code ‘R’ is prepopulated and cannot be removed
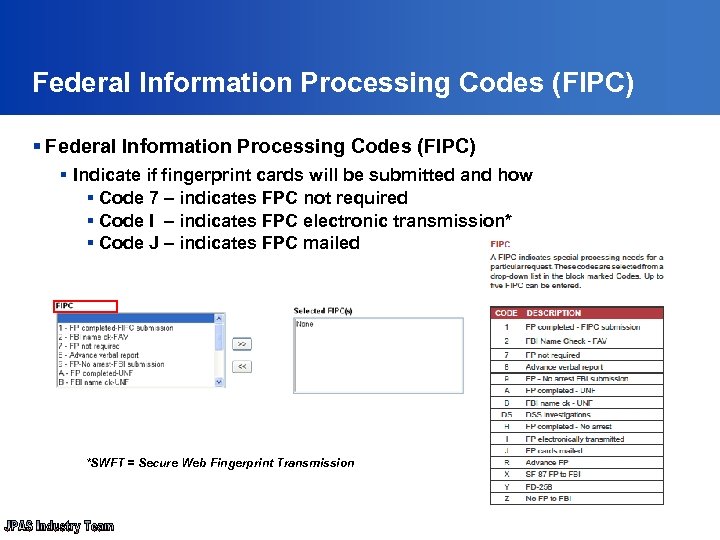 Federal Information Processing Codes (FIPC) § Indicate if fingerprint cards will be submitted and how § Code 7 – indicates FPC not required § Code I – indicates FPC electronic transmission* § Code J – indicates FPC mailed *SWFT = Secure Web Fingerprint Transmission
Federal Information Processing Codes (FIPC) § Indicate if fingerprint cards will be submitted and how § Code 7 – indicates FPC not required § Code I – indicates FPC electronic transmission* § Code J – indicates FPC mailed *SWFT = Secure Web Fingerprint Transmission
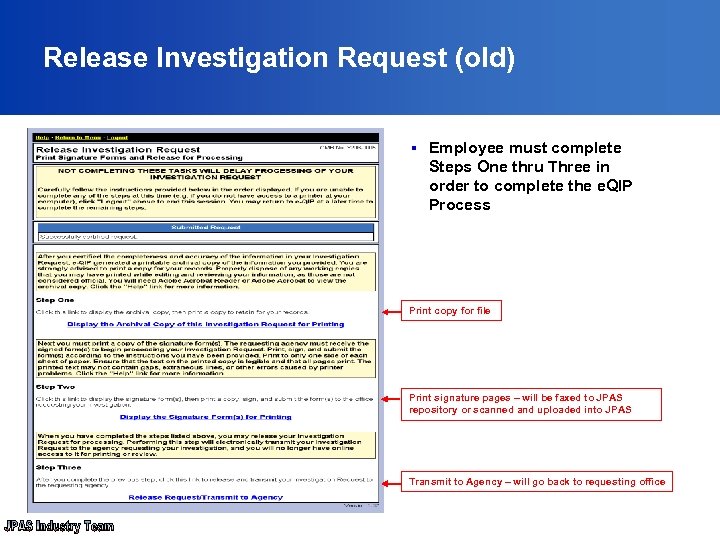 Release Investigation Request (old) § Employee must complete Steps One thru Three in order to complete the e. QIP Process Print copy for file Print signature pages – will be faxed to JPAS repository or scanned and uploaded into JPAS Transmit to Agency – will go back to requesting office
Release Investigation Request (old) § Employee must complete Steps One thru Three in order to complete the e. QIP Process Print copy for file Print signature pages – will be faxed to JPAS repository or scanned and uploaded into JPAS Transmit to Agency – will go back to requesting office
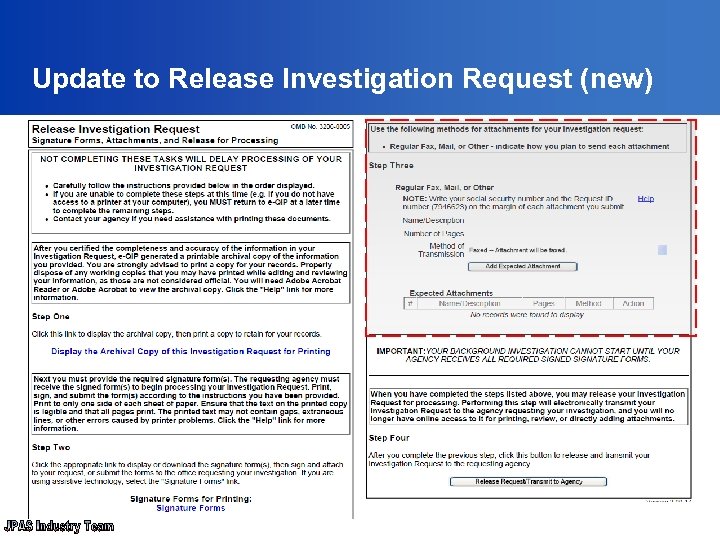 Update to Release Investigation Request (new)
Update to Release Investigation Request (new)
 e. QIP Direct for Industry § § § § New SF 86 effective 1 January 2011 e. QIP investigation requests will no longer be initiated via JPAS All requests initiated in JPAS must be completed prior to 1 Jan ’ 11 No old forms will be accepted Additional drop downs for yes/no questions (can yield up to 447 qs) New form should address all concerned (even some 3 letter agencies) Everyone within federal govt will have to transfer to e. QIP Direct, not just Do. D No Interims will be granted until NAC portion of FPC has been conducted Everyone with CAC card will be required to use it; must have CAC reader DMDC will require everyone to have some type of secure communication: Personal Identity Verification (PIV), Public Key Infrastructure (PKI) encryption or authentication Account Management functions will be limited, permissions need to be defined/established DISCO will approve e. QIP for Industry and forward to OPM e. QIP actions will be time stamped and can be seen from start to finish The Do. D Call Center not able to fully assist e-QIP users initiated via e-QIP Direct; e-QIP Direct does not interface with JPAS Call Center can not view e. QIP, can not reset golden questions § Users should contact appropriate military agency or unit security manager or officer for assistance.
e. QIP Direct for Industry § § § § New SF 86 effective 1 January 2011 e. QIP investigation requests will no longer be initiated via JPAS All requests initiated in JPAS must be completed prior to 1 Jan ’ 11 No old forms will be accepted Additional drop downs for yes/no questions (can yield up to 447 qs) New form should address all concerned (even some 3 letter agencies) Everyone within federal govt will have to transfer to e. QIP Direct, not just Do. D No Interims will be granted until NAC portion of FPC has been conducted Everyone with CAC card will be required to use it; must have CAC reader DMDC will require everyone to have some type of secure communication: Personal Identity Verification (PIV), Public Key Infrastructure (PKI) encryption or authentication Account Management functions will be limited, permissions need to be defined/established DISCO will approve e. QIP for Industry and forward to OPM e. QIP actions will be time stamped and can be seen from start to finish The Do. D Call Center not able to fully assist e-QIP users initiated via e-QIP Direct; e-QIP Direct does not interface with JPAS Call Center can not view e. QIP, can not reset golden questions § Users should contact appropriate military agency or unit security manager or officer for assistance.
 E-QIP Training - Virtual Training for Security Professionals (3/4/10) § Online e-QIP Training: § Provides high-level overview of the purpose, history, and benefits of the e-QIP system. § Includes instruction for accessing and navigating in e-QIP. § Introduces various e-QIP end-user roles and responsibilities, and identifies the tasks involved in initiating, reviewing, and approving investigation requests. § Delivers solutions to common applicant issues and includes walkthroughs with knowledge checks and practical exercises and tasks completed in a virtual e-QIP environment. § To register for this training, visit the ENROL Web site at https: //enrol. dss. mil/enrol/lang-default/SYS_login. asp.
E-QIP Training - Virtual Training for Security Professionals (3/4/10) § Online e-QIP Training: § Provides high-level overview of the purpose, history, and benefits of the e-QIP system. § Includes instruction for accessing and navigating in e-QIP. § Introduces various e-QIP end-user roles and responsibilities, and identifies the tasks involved in initiating, reviewing, and approving investigation requests. § Delivers solutions to common applicant issues and includes walkthroughs with knowledge checks and practical exercises and tasks completed in a virtual e-QIP environment. § To register for this training, visit the ENROL Web site at https: //enrol. dss. mil/enrol/lang-default/SYS_login. asp.
 Secure Web Fingerprint Transmission (SWFT) § SWFT is a secure web-based system that allows cleared contractors to submit electronic fingerprints (e. FPCs) and demographic information to DSS. § Cleared contractors can transmit e. FPCs to DSS for release to OPM based on the approval of a JPAS/e-QIP submission by DISCO. § Cleared contractors can upload fingerprint files to the SWFT website. § The website will conduct a virus scan of the uploaded files prior to sending them to the SWFT Store and Forward server. § Fingerprint files will be matched against approved e-QIP submissions and automatically forwarded to OPM and then on to FBI. § DSS accepting additional cleared contractors as of 3 August 2009. § SWFT NOT mandatory, but highly recommended. For additional info, see SWFT website: http: //www. dss. mil/diss/swft. html
Secure Web Fingerprint Transmission (SWFT) § SWFT is a secure web-based system that allows cleared contractors to submit electronic fingerprints (e. FPCs) and demographic information to DSS. § Cleared contractors can transmit e. FPCs to DSS for release to OPM based on the approval of a JPAS/e-QIP submission by DISCO. § Cleared contractors can upload fingerprint files to the SWFT website. § The website will conduct a virus scan of the uploaded files prior to sending them to the SWFT Store and Forward server. § Fingerprint files will be matched against approved e-QIP submissions and automatically forwarded to OPM and then on to FBI. § DSS accepting additional cleared contractors as of 3 August 2009. § SWFT NOT mandatory, but highly recommended. For additional info, see SWFT website: http: //www. dss. mil/diss/swft. html
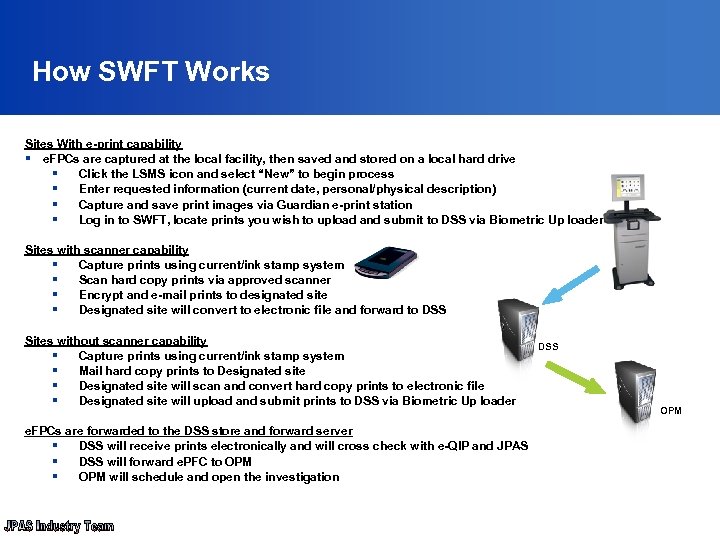 How SWFT Works Sites With e-print capability § e. FPCs are captured at the local facility, then saved and stored on a local hard drive § Click the LSMS icon and select “New” to begin process § Enter requested information (current date, personal/physical description) § Capture and save print images via Guardian e-print station § Log in to SWFT, locate prints you wish to upload and submit to DSS via Biometric Up loader Sites with scanner capability § Capture prints using current/ink stamp system § Scan hard copy prints via approved scanner § Encrypt and e-mail prints to designated site § Designated site will convert to electronic file and forward to DSS Sites without scanner capability § Capture prints using current/ink stamp system § Mail hard copy prints to Designated site § Designated site will scan and convert hard copy prints to electronic file § Designated site will upload and submit prints to DSS via Biometric Up loader e. FPCs are forwarded to the DSS store and forward server § DSS will receive prints electronically and will cross check with e-QIP and JPAS § DSS will forward e. PFC to OPM § OPM will schedule and open the investigation DSS OPM
How SWFT Works Sites With e-print capability § e. FPCs are captured at the local facility, then saved and stored on a local hard drive § Click the LSMS icon and select “New” to begin process § Enter requested information (current date, personal/physical description) § Capture and save print images via Guardian e-print station § Log in to SWFT, locate prints you wish to upload and submit to DSS via Biometric Up loader Sites with scanner capability § Capture prints using current/ink stamp system § Scan hard copy prints via approved scanner § Encrypt and e-mail prints to designated site § Designated site will convert to electronic file and forward to DSS Sites without scanner capability § Capture prints using current/ink stamp system § Mail hard copy prints to Designated site § Designated site will scan and convert hard copy prints to electronic file § Designated site will upload and submit prints to DSS via Biometric Up loader e. FPCs are forwarded to the DSS store and forward server § DSS will receive prints electronically and will cross check with e-QIP and JPAS § DSS will forward e. PFC to OPM § OPM will schedule and open the investigation DSS OPM

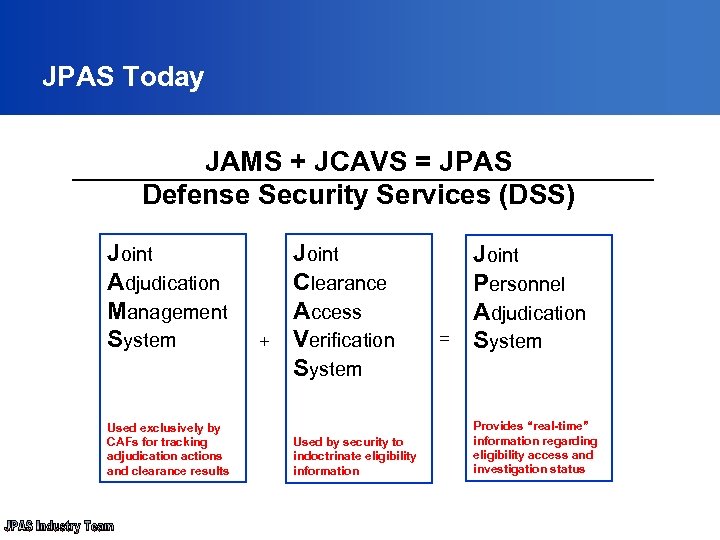 JPAS Today JAMS + JCAVS = JPAS Defense Security Services (DSS) Joint Adjudication Management System Used exclusively by CAFs for tracking adjudication actions and clearance results + Joint Clearance Access Verification System Used by security to indoctrinate eligibility information = Joint Personnel Adjudication System Provides “real-time” information regarding eligibility access and investigation status
JPAS Today JAMS + JCAVS = JPAS Defense Security Services (DSS) Joint Adjudication Management System Used exclusively by CAFs for tracking adjudication actions and clearance results + Joint Clearance Access Verification System Used by security to indoctrinate eligibility information = Joint Personnel Adjudication System Provides “real-time” information regarding eligibility access and investigation status
 Transition from DSS to Defense Manpower Data Center (DMDC) eftv 21 June 2010 § DMDC serves under the Office of the Secretary of Defense to collate personnel, manpower, training, financial, and other data for the Department of Defense. § IT Systems to transfer to DMDC: JPAS, DCII, SWFT, IRR § New URL for JPAS: https: //jpasapp. dmdc. osd. mil/JPASDisclosure § New DMDC Web Page will display October 2010 and will allow the following log-in options: § Military/Civilian: § Dual Login Option – Password or CAC Card § Industry: § Password (If current password does not meet regulations, change requirement will be enforced) § Additional information will be posted on DSS (www. dss. mil) and DMDC (www. dmdc. osd. mil) as it becomes available.
Transition from DSS to Defense Manpower Data Center (DMDC) eftv 21 June 2010 § DMDC serves under the Office of the Secretary of Defense to collate personnel, manpower, training, financial, and other data for the Department of Defense. § IT Systems to transfer to DMDC: JPAS, DCII, SWFT, IRR § New URL for JPAS: https: //jpasapp. dmdc. osd. mil/JPASDisclosure § New DMDC Web Page will display October 2010 and will allow the following log-in options: § Military/Civilian: § Dual Login Option – Password or CAC Card § Industry: § Password (If current password does not meet regulations, change requirement will be enforced) § Additional information will be posted on DSS (www. dss. mil) and DMDC (www. dmdc. osd. mil) as it becomes available.
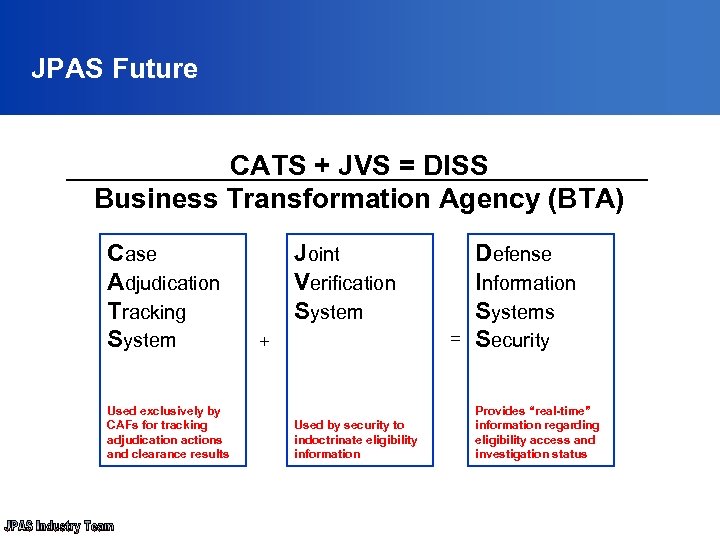 JPAS Future CATS + JVS = DISS Business Transformation Agency (BTA) Case Adjudication Tracking System Used exclusively by CAFs for tracking adjudication actions and clearance results Joint Verification System = + Used by security to indoctrinate eligibility information Defense Information Systems Security Provides “real-time” information regarding eligibility access and investigation status
JPAS Future CATS + JVS = DISS Business Transformation Agency (BTA) Case Adjudication Tracking System Used exclusively by CAFs for tracking adjudication actions and clearance results Joint Verification System = + Used by security to indoctrinate eligibility information Defense Information Systems Security Provides “real-time” information regarding eligibility access and investigation status
 Why the New System? § JPAS was built in early 2000 and the software is not compatible with systems currently used by BTA (CATS, e. QIP by Design) § JPAS was initially built for the Govt. and was not Industry specific § JPAS was initially built to host ~45, 000 users, but is currently hosting over 100, 000 users, which far exceeds the initial capacity § JPAS is very difficult and expensive to update § New system being built from scratch
Why the New System? § JPAS was built in early 2000 and the software is not compatible with systems currently used by BTA (CATS, e. QIP by Design) § JPAS was initially built for the Govt. and was not Industry specific § JPAS was initially built to host ~45, 000 users, but is currently hosting over 100, 000 users, which far exceeds the initial capacity § JPAS is very difficult and expensive to update § New system being built from scratch
 Business Transformation Agency (BTA) § Established October 2005 § Specifically responsible as a corporate-level service organization for the Do. D, accountable for successful definition and execution of Do. D-wide business improvement initiatives and system investments § The BTA Mission is: to guide transformation of business operations throughout the Department of Defense and to deliver Enterprise-level capabilities that align to Warfighter needs
Business Transformation Agency (BTA) § Established October 2005 § Specifically responsible as a corporate-level service organization for the Do. D, accountable for successful definition and execution of Do. D-wide business improvement initiatives and system investments § The BTA Mission is: to guide transformation of business operations throughout the Department of Defense and to deliver Enterprise-level capabilities that align to Warfighter needs
 Case Adjudication Tracking System (CATS) § CATS is the case management system that allows electronic transmission of investigative reports from the Office of Personnel Management to DISCO § DISCO will use CATS to adjudicate electronic investigations, and CATS will update JPAS § CATS has been deployed to Army, DISCO, Navy § CATS is in process of deploying to WHS and AF
Case Adjudication Tracking System (CATS) § CATS is the case management system that allows electronic transmission of investigative reports from the Office of Personnel Management to DISCO § DISCO will use CATS to adjudicate electronic investigations, and CATS will update JPAS § CATS has been deployed to Army, DISCO, Navy § CATS is in process of deploying to WHS and AF
 JVS § JVS will provide the following benefits: § Continuous Evaluation/Incident Event Trigger Report working with ACES § Will provide SMOs a more robust work management tool § Will be able to leverage capabilities of other DISS systems to create a specialty management tool combining, tracking, and evaluating the information provided by CATS and ACES § Enterprise Services will be deployed with JVS § Portal § Workflow § Document Management
JVS § JVS will provide the following benefits: § Continuous Evaluation/Incident Event Trigger Report working with ACES § Will provide SMOs a more robust work management tool § Will be able to leverage capabilities of other DISS systems to create a specialty management tool combining, tracking, and evaluating the information provided by CATS and ACES § Enterprise Services will be deployed with JVS § Portal § Workflow § Document Management
 JVS Requirements § Overarching requirements completed in Dec ’ 09 § Industry PMOs met with BTA and provided detailed guidance on JCAVS Use Cases (industry processes and procedures) § Working group sessions with JPAS user community to elicit system requirements § Review, update and define security management process models § Validate individual JVS Use Cases § Follow-up ‘playback sessions’ that allow JVS stakeholder community to provide input
JVS Requirements § Overarching requirements completed in Dec ’ 09 § Industry PMOs met with BTA and provided detailed guidance on JCAVS Use Cases (industry processes and procedures) § Working group sessions with JPAS user community to elicit system requirements § Review, update and define security management process models § Validate individual JVS Use Cases § Follow-up ‘playback sessions’ that allow JVS stakeholder community to provide input
 JVS Initial Capabilities Identified § JVS will provide current JCAVS functionality § Additional requirements identified: § Mass personnel updates § Electronic document transmission § Notifications, messaging, and correspondence § Robust reporting and business intelligence § Federated search § Clearance tracker § Digital signature § Excel based queries
JVS Initial Capabilities Identified § JVS will provide current JCAVS functionality § Additional requirements identified: § Mass personnel updates § Electronic document transmission § Notifications, messaging, and correspondence § Robust reporting and business intelligence § Federated search § Clearance tracker § Digital signature § Excel based queries
 JVS Use Cases Discussed § Access Subject Record § Allows Security Officer to request a Subject's record via certain selection criteria and returns screens and data as appropriate to the Security Officer's relationship to the Subject. § Grant Non-SCI/SCI Access § System shall prevent a Subject from being Indoctrinated into an access higher than the Organization Clearance level based § System shall notify the servicing Security Officer when a Subject's access is granted or removed for a particular Person Category § System shall allow a Security Officer to send a request that another Security Officer grant access for a Subject's Person Category if the Subject is transferring to a new Security Office. § Create Subject Record § System shall automatically populate a Subject's record when a Personnel Security Questionnaire (PSQ) is sent based on Electronic Questionnaires for Investigation Processing (e-QIP) as designed. § Remove Subject Relationship § System shall ensure that Subjects have completed access removal/debriefing prior to out-processing. § Establish Subject Relationship § There can only be one Owning Security Officer per Person Category for a Subject. § In the instance where a Subject already has an existing Owning Relationship in a Person Category, the existing Owner must manually remove the Subject Relationship before another Owning relationship can be taken.
JVS Use Cases Discussed § Access Subject Record § Allows Security Officer to request a Subject's record via certain selection criteria and returns screens and data as appropriate to the Security Officer's relationship to the Subject. § Grant Non-SCI/SCI Access § System shall prevent a Subject from being Indoctrinated into an access higher than the Organization Clearance level based § System shall notify the servicing Security Officer when a Subject's access is granted or removed for a particular Person Category § System shall allow a Security Officer to send a request that another Security Officer grant access for a Subject's Person Category if the Subject is transferring to a new Security Office. § Create Subject Record § System shall automatically populate a Subject's record when a Personnel Security Questionnaire (PSQ) is sent based on Electronic Questionnaires for Investigation Processing (e-QIP) as designed. § Remove Subject Relationship § System shall ensure that Subjects have completed access removal/debriefing prior to out-processing. § Establish Subject Relationship § There can only be one Owning Security Officer per Person Category for a Subject. § In the instance where a Subject already has an existing Owning Relationship in a Person Category, the existing Owner must manually remove the Subject Relationship before another Owning relationship can be taken.
 JVS Use Cases to be Discussed § Deactivating Person Categories § Adding/Creating/Deactivating SMOs § Reactivating a SMO § Granting/Removing access to DISS § Security Officer Permissions § Mass Personnel Changes § Incident Reporting § Managing PRs § Visits § Initiating Investigation Requests § Notifications § Reports – Predefined and Ad-Hoc
JVS Use Cases to be Discussed § Deactivating Person Categories § Adding/Creating/Deactivating SMOs § Reactivating a SMO § Granting/Removing access to DISS § Security Officer Permissions § Mass Personnel Changes § Incident Reporting § Managing PRs § Visits § Initiating Investigation Requests § Notifications § Reports – Predefined and Ad-Hoc
 Defense Information System for Security (DISS) § DISS will replace JPAS and incorporate Enterprise Services § CATS will replace JAMS § JVS will replace JCAVS § DISS will be used to implement Joint Reform Team (JRT) principles within Do. D § Validate Need for hiring and clearance requests § Automated Records Check (utilizing both govt and commercial data) § Enhanced Subject Interview (in-depth interviews based on application information and results of ARC) § Continuous Evaluation (utilize ARC annually for TS/SCI, once every 5 years for S) § Automatic Continuous Evaluation Check (ACES) is in pilot status; will provide Automatic Records Check (ARC) services § DISS will be a single point of entry for the Do. D security process
Defense Information System for Security (DISS) § DISS will replace JPAS and incorporate Enterprise Services § CATS will replace JAMS § JVS will replace JCAVS § DISS will be used to implement Joint Reform Team (JRT) principles within Do. D § Validate Need for hiring and clearance requests § Automated Records Check (utilizing both govt and commercial data) § Enhanced Subject Interview (in-depth interviews based on application information and results of ARC) § Continuous Evaluation (utilize ARC annually for TS/SCI, once every 5 years for S) § Automatic Continuous Evaluation Check (ACES) is in pilot status; will provide Automatic Records Check (ARC) services § DISS will be a single point of entry for the Do. D security process
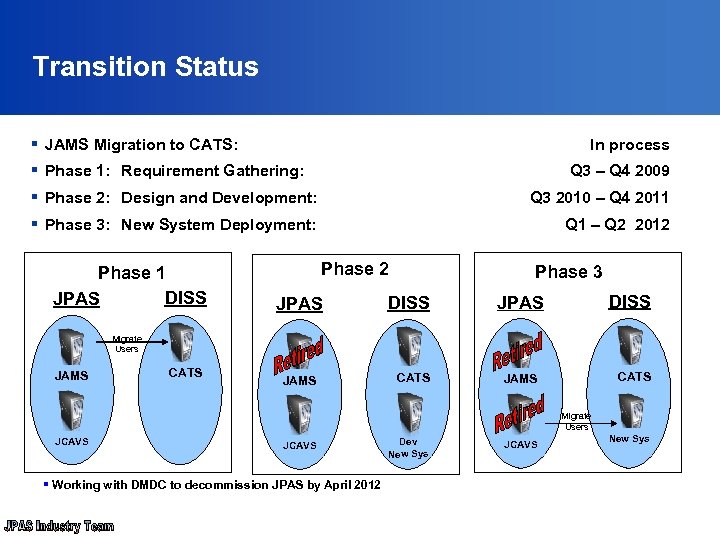 Transition Status § JAMS Migration to CATS: In process § Phase 1: Requirement Gathering: Q 3 – Q 4 2009 § Phase 2: Design and Development: Q 3 2010 – Q 4 2011 § Phase 3: New System Deployment: Q 1 – Q 2 2012 Phase 1 DISS JPAS Phase 2 JPAS Phase 3 DISS JPAS Migrate Users JAMS CATS JAMS Migrate Users JCAVS § Working with DMDC to decommission JPAS by April 2012 Dev New Sys JCAVS New Sys
Transition Status § JAMS Migration to CATS: In process § Phase 1: Requirement Gathering: Q 3 – Q 4 2009 § Phase 2: Design and Development: Q 3 2010 – Q 4 2011 § Phase 3: New System Deployment: Q 1 – Q 2 2012 Phase 1 DISS JPAS Phase 2 JPAS Phase 3 DISS JPAS Migrate Users JAMS CATS JAMS Migrate Users JCAVS § Working with DMDC to decommission JPAS by April 2012 Dev New Sys JCAVS New Sys
 Successful Implementation of DISS § Ensure only those positions that require a clearance are submitted § Provide near real-time security clearance investigative and adjudicative information § Support efficient and effective resourcing and management of security clearance requirements § Support compliance with Do. D security clearance policies § Provide timely and consistent information that will allow decisionmakers to make sound security clearance decisions
Successful Implementation of DISS § Ensure only those positions that require a clearance are submitted § Provide near real-time security clearance investigative and adjudicative information § Support efficient and effective resourcing and management of security clearance requirements § Support compliance with Do. D security clearance policies § Provide timely and consistent information that will allow decisionmakers to make sound security clearance decisions
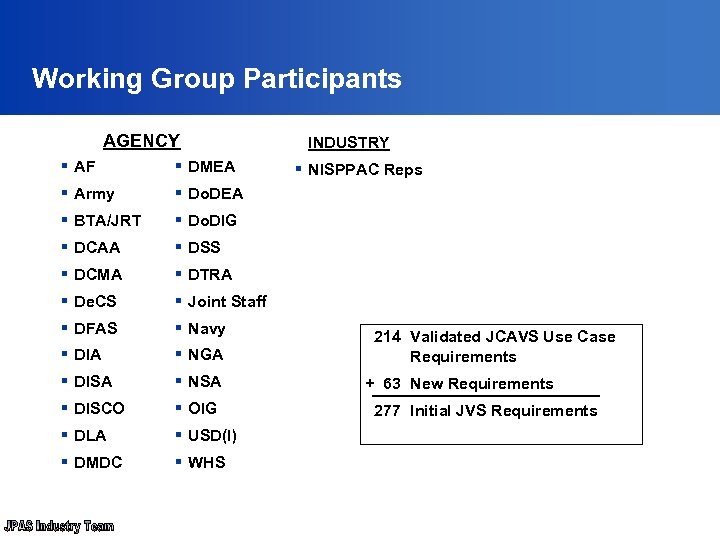 Working Group Participants AGENCY § AF § DMEA § Army § Do. DEA § BTA/JRT § Do. DIG § DCAA § DSS § DCMA § DTRA § De. CS § Joint Staff § DFAS § Navy § DIA § NGA § DISA § NSA § DISCO § OIG § DLA § USD(I) § DMDC § WHS INDUSTRY § NISPPAC Reps 214 Validated JCAVS Use Case Requirements + 63 New Requirements 277 Initial JVS Requirements
Working Group Participants AGENCY § AF § DMEA § Army § Do. DEA § BTA/JRT § Do. DIG § DCAA § DSS § DCMA § DTRA § De. CS § Joint Staff § DFAS § Navy § DIA § NGA § DISA § NSA § DISCO § OIG § DLA § USD(I) § DMDC § WHS INDUSTRY § NISPPAC Reps 214 Validated JCAVS Use Case Requirements + 63 New Requirements 277 Initial JVS Requirements
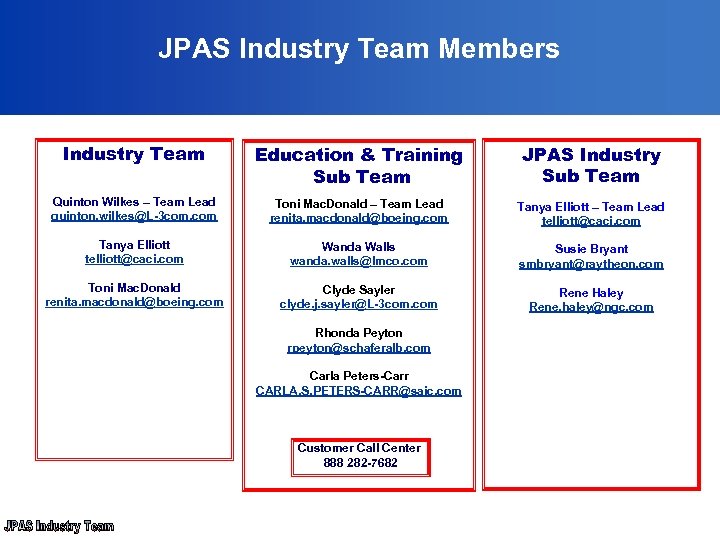 JPAS Industry Team Members Industry Team Education & Training Sub Team JPAS Industry Sub Team Quinton Wilkes – Team Lead quinton. wilkes@L-3 com. com Toni Mac. Donald – Team Lead renita. macdonald@boeing. com Tanya Elliott – Team Lead telliott@caci. com Tanya Elliott telliott@caci. com Wanda Walls wanda. walls@lmco. com Susie Bryant smbryant@raytheon. com Toni Mac. Donald renita. macdonald@boeing. com Clyde Sayler clyde. j. sayler@L-3 com. com Rene Haley Rene. haley@ngc. com Rhonda Peyton rpeyton@schaferalb. com Carla Peters-Carr CARLA. S. PETERS-CARR@saic. com Customer Call Center 888 282 -7682
JPAS Industry Team Members Industry Team Education & Training Sub Team JPAS Industry Sub Team Quinton Wilkes – Team Lead quinton. wilkes@L-3 com. com Toni Mac. Donald – Team Lead renita. macdonald@boeing. com Tanya Elliott – Team Lead telliott@caci. com Tanya Elliott telliott@caci. com Wanda Walls wanda. walls@lmco. com Susie Bryant smbryant@raytheon. com Toni Mac. Donald renita. macdonald@boeing. com Clyde Sayler clyde. j. sayler@L-3 com. com Rene Haley Rene. haley@ngc. com Rhonda Peyton rpeyton@schaferalb. com Carla Peters-Carr CARLA. S. PETERS-CARR@saic. com Customer Call Center 888 282 -7682



