7be85eca8af78c2cc9660119936e1f37.ppt
- Количество слайдов: 34
 National Information Assurance Training and Education Center Idaho State University Int egr i tial den nfi ity Co ty Availability
National Information Assurance Training and Education Center Idaho State University Int egr i tial den nfi ity Co ty Availability
 Information Assurance Copyright 2003 Corey Schou April 2003 Schou@NIATEC. ISU. EDU
Information Assurance Copyright 2003 Corey Schou April 2003 Schou@NIATEC. ISU. EDU
 Agenda t t What is information assurance (IA) What is the relationship of IA to the emerging role of college and university security professionals? What are the opportunities for partnerships between campus security officers and academics involved in establishing centers of academic excellence in information assurance? What are the best paths for training, professional development, and certification of higher education IT security professionals?
Agenda t t What is information assurance (IA) What is the relationship of IA to the emerging role of college and university security professionals? What are the opportunities for partnerships between campus security officers and academics involved in establishing centers of academic excellence in information assurance? What are the best paths for training, professional development, and certification of higher education IT security professionals?
 The Threat t “The greatest threat you face is not the viruses or the hackers or the whatever, but rather complacency. ” t. Michael Tucker, editor, SC magazine, sep 99
The Threat t “The greatest threat you face is not the viruses or the hackers or the whatever, but rather complacency. ” t. Michael Tucker, editor, SC magazine, sep 99
 There Is Nothing To Worry About t This is one approach to the problem
There Is Nothing To Worry About t This is one approach to the problem
 Systems Are Vulnerable t Threats by people – Unintentional actions => 50 -60% – Intentional actions => 15 -20% – Outside actions => 1 -3% t Physical and environmental threats – Fire damage => 10 -15% – Water damage => 1 -5% – Natural disaster => 1% t Other => 5 -10%
Systems Are Vulnerable t Threats by people – Unintentional actions => 50 -60% – Intentional actions => 15 -20% – Outside actions => 1 -3% t Physical and environmental threats – Fire damage => 10 -15% – Water damage => 1 -5% – Natural disaster => 1% t Other => 5 -10%
 What Is Information Assurance t t You and I used to call it computer security or perhaps privacy It is much more than that… – Integrity – Trust – Confidentiality
What Is Information Assurance t t You and I used to call it computer security or perhaps privacy It is much more than that… – Integrity – Trust – Confidentiality
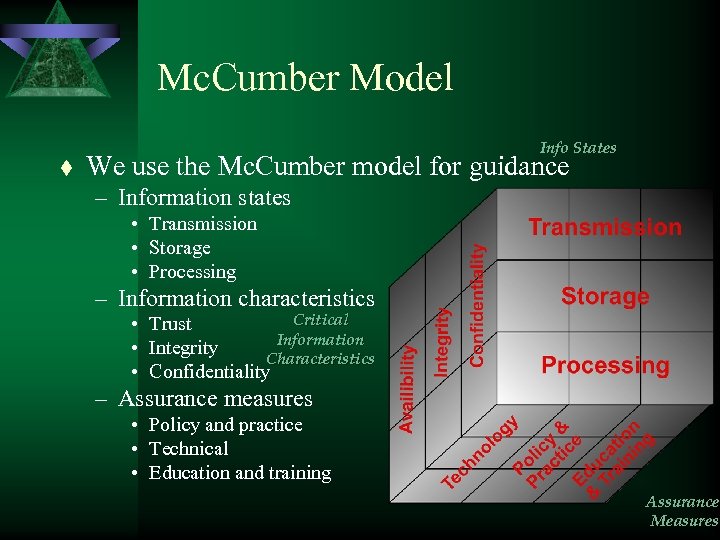 Mc. Cumber Model t Info States We use the Mc. Cumber model for guidance – Information states • Transmission • Storage • Processing – Information characteristics Critical • Trust Information • Integrity Characteristics • Confidentiality – Assurance measures • Policy and practice • Technical • Education and training Assurance Measures
Mc. Cumber Model t Info States We use the Mc. Cumber model for guidance – Information states • Transmission • Storage • Processing – Information characteristics Critical • Trust Information • Integrity Characteristics • Confidentiality – Assurance measures • Policy and practice • Technical • Education and training Assurance Measures
 Defense-in-depth TECHNOLOGY OPERATIONS PEOPLE Fundamentally, only THREE countermeasures available to protect critical information infrastructures.
Defense-in-depth TECHNOLOGY OPERATIONS PEOPLE Fundamentally, only THREE countermeasures available to protect critical information infrastructures.
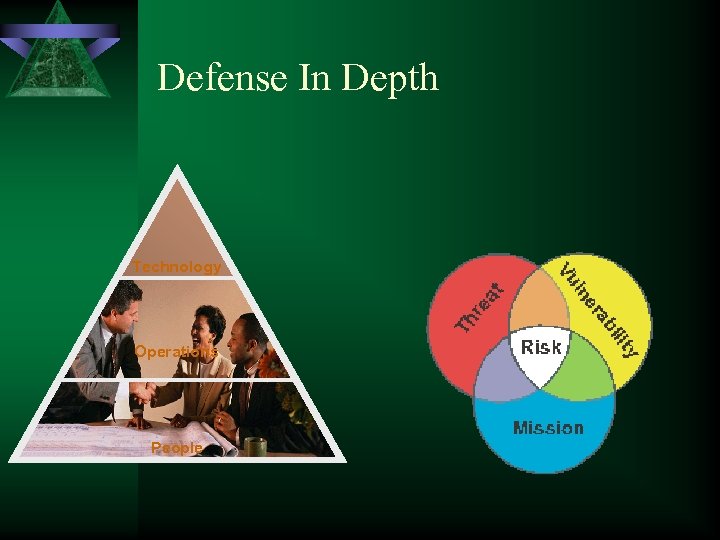 Defense In Depth Technology Operations People
Defense In Depth Technology Operations People
 Information Assurance Is Everyone’s Responsibility
Information Assurance Is Everyone’s Responsibility
 Information Assurance Partnerships With Academic Unit Copyright 2003
Information Assurance Partnerships With Academic Unit Copyright 2003
 The Not So Good News* t Today there are only four declared, dedicated computer security research centers in degree granting departments at universities in the United States – Six years later there are only ten. Dr. Eugene Spafford Testimony to House Science Comm. Feb. 11, 1997
The Not So Good News* t Today there are only four declared, dedicated computer security research centers in degree granting departments at universities in the United States – Six years later there are only ten. Dr. Eugene Spafford Testimony to House Science Comm. Feb. 11, 1997
 The Not So Good News* t t Over the past five years, approximately 5, 500 Ph. Ds in computer science and engineering were awarded by universities in the US Only 16 of those were awarded for securityrelated research at these major centers (only 8 of the 16 were U. S. Nationals)
The Not So Good News* t t Over the past five years, approximately 5, 500 Ph. Ds in computer science and engineering were awarded by universities in the US Only 16 of those were awarded for securityrelated research at these major centers (only 8 of the 16 were U. S. Nationals)
 IA Training Centers
IA Training Centers
 NSA-Designated Centers Of Academic Excellence In Information Assurance Education
NSA-Designated Centers Of Academic Excellence In Information Assurance Education
 Existing Standards NSTISSI TRAINING STANDARDS NSTISSI 4011 National Training Standard for INFOSEC Professionals NSTISSI 4012 National Training Standard for Designated Approving Authorities NSTISSI 4013 National Training Standard for System Administrators in INFOSEC NSTISSI 4014 National Training Standard for Information System Security Officers
Existing Standards NSTISSI TRAINING STANDARDS NSTISSI 4011 National Training Standard for INFOSEC Professionals NSTISSI 4012 National Training Standard for Designated Approving Authorities NSTISSI 4013 National Training Standard for System Administrators in INFOSEC NSTISSI 4014 National Training Standard for Information System Security Officers
 What’s In It For You t t Grants Scholarship for Service Do. D Scholarship for Service Faculty Development
What’s In It For You t t Grants Scholarship for Service Do. D Scholarship for Service Faculty Development
 Information Assurance Role On The Campus Copyright 2003
Information Assurance Role On The Campus Copyright 2003
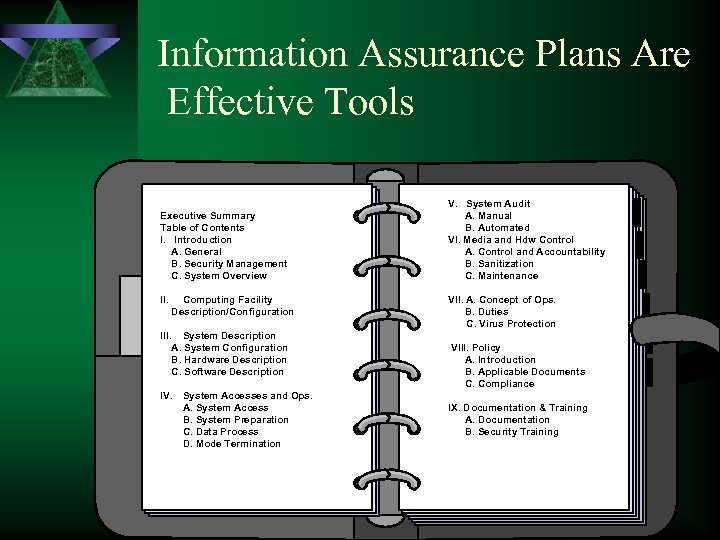 Information Assurance Plans Are Effective Tools Executive Summary Table of Contents I. Introduction A. General B. Security Management C. System Overview II. Computing Facility Description/Configuration System Description A. System Configuration B. Hardware Description C. Software Description V. System Audit A. Manual B. Automated VI. Media and Hdw Control A. Control and Accountability B. Sanitization C. Maintenance VII. A. Concept of Ops. B. Duties C. Virus Protection III. IV. System Accesses and Ops. A. System Access B. System Preparation C. Data Process D. Mode Termination VIII. Policy A. Introduction B. Applicable Documents C. Compliance IX. Documentation & Training A. Documentation B. Security Training
Information Assurance Plans Are Effective Tools Executive Summary Table of Contents I. Introduction A. General B. Security Management C. System Overview II. Computing Facility Description/Configuration System Description A. System Configuration B. Hardware Description C. Software Description V. System Audit A. Manual B. Automated VI. Media and Hdw Control A. Control and Accountability B. Sanitization C. Maintenance VII. A. Concept of Ops. B. Duties C. Virus Protection III. IV. System Accesses and Ops. A. System Access B. System Preparation C. Data Process D. Mode Termination VIII. Policy A. Introduction B. Applicable Documents C. Compliance IX. Documentation & Training A. Documentation B. Security Training
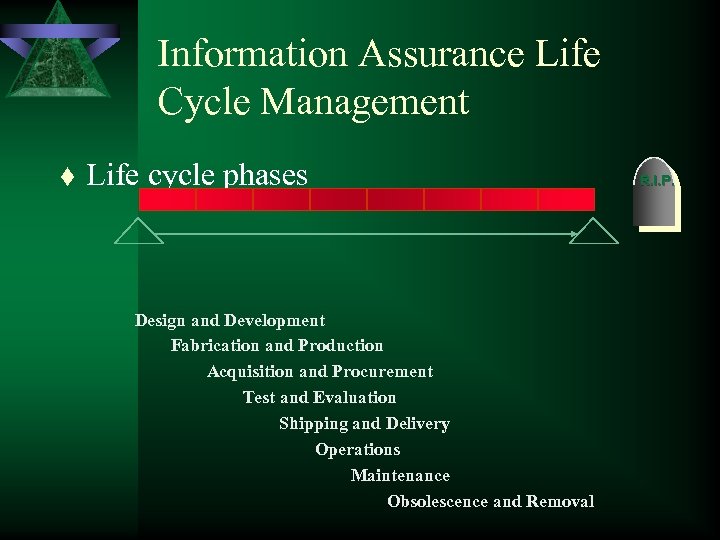 Information Assurance Life Cycle Management t Life cycle phases Design and Development Fabrication and Production Acquisition and Procurement Test and Evaluation Shipping and Delivery Operations Maintenance Obsolescence and Removal R. I. P.
Information Assurance Life Cycle Management t Life cycle phases Design and Development Fabrication and Production Acquisition and Procurement Test and Evaluation Shipping and Delivery Operations Maintenance Obsolescence and Removal R. I. P.
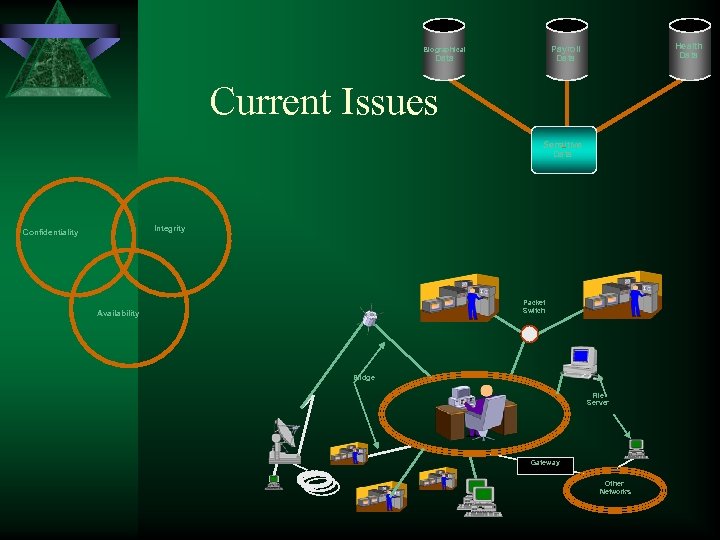 Health Data Payroll Data Biographical Data Current Issues Sensitive Data Integrity Confidentiality Packet Switch Availability Bridge File Server Gateway Other Networks
Health Data Payroll Data Biographical Data Current Issues Sensitive Data Integrity Confidentiality Packet Switch Availability Bridge File Server Gateway Other Networks
 Current Issues Confidentiality Integrity Availability
Current Issues Confidentiality Integrity Availability
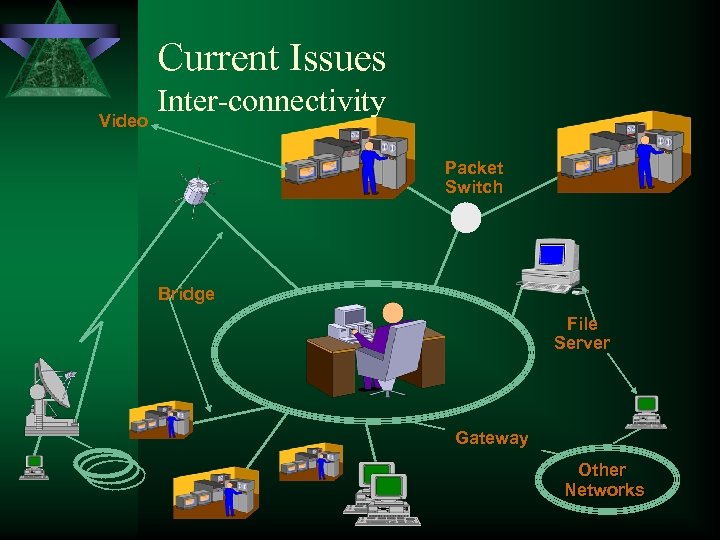 Current Issues Video Inter-connectivity Packet Switch Bridge File Server Gateway Other Networks
Current Issues Video Inter-connectivity Packet Switch Bridge File Server Gateway Other Networks
 Information Assurance Training And Professional Development Copyright 2003
Information Assurance Training And Professional Development Copyright 2003
 NAITEC Industry, Government and Industry Participants t t Faculty and administration short courses in aspects of information assurance Courses for institutions serving minorities to establish curriculum for their students Faculty curriculum development grants Special programs to encourage two-year, professional and certificate programs at participating academic institutions to fulfill requirements for professionalization t t t Curriculum and faculty sharing among participating organizations Faculty training and outreach programs for K-12 institutions Online course and curriculum materials in information assurance Quarterly CD-ROMS with teaching materials and best practices International outreach to establish best practice in information assurance world wide http: //security. isu. edu
NAITEC Industry, Government and Industry Participants t t Faculty and administration short courses in aspects of information assurance Courses for institutions serving minorities to establish curriculum for their students Faculty curriculum development grants Special programs to encourage two-year, professional and certificate programs at participating academic institutions to fulfill requirements for professionalization t t t Curriculum and faculty sharing among participating organizations Faculty training and outreach programs for K-12 institutions Online course and curriculum materials in information assurance Quarterly CD-ROMS with teaching materials and best practices International outreach to establish best practice in information assurance world wide http: //security. isu. edu
 (ISC)2 t Certified information systems security professional (CISSP) – Requires direct full-time security professional work experience in one or more of the ten test domains of the information systems security common body of knowledge (CBK) • Four years experience • Or three years experience with a college degree or equivalent life experience t Systems security certified professional (SSCP) – One year of cumulative work experience in one or more of the seven test domains in information systems [IS] security http: //www. isc 2. org
(ISC)2 t Certified information systems security professional (CISSP) – Requires direct full-time security professional work experience in one or more of the ten test domains of the information systems security common body of knowledge (CBK) • Four years experience • Or three years experience with a college degree or equivalent life experience t Systems security certified professional (SSCP) – One year of cumulative work experience in one or more of the seven test domains in information systems [IS] security http: //www. isc 2. org
 CISSP t The CISSP recognizes mastery of an international standard for information security and understanding of a common body of knowledge (CBK).
CISSP t The CISSP recognizes mastery of an international standard for information security and understanding of a common body of knowledge (CBK).
 CISSP t t t t t Access control systems & methodology Applications & systems development Business continuity planning Cryptography Law, investigation & ethics Operations security Physical security Security architecture & models Security management practices Telecommunications, network & internet security
CISSP t t t t t Access control systems & methodology Applications & systems development Business continuity planning Cryptography Law, investigation & ethics Operations security Physical security Security architecture & models Security management practices Telecommunications, network & internet security
 SSCP t The SSCP focuses on practices, roles and responsibilities as defined by experts from major IS industries – – – – Access controls Administration Audit and monitoring Risk, response and recovery Cryptography Data communications Malicious Code/Malware
SSCP t The SSCP focuses on practices, roles and responsibilities as defined by experts from major IS industries – – – – Access controls Administration Audit and monitoring Risk, response and recovery Cryptography Data communications Malicious Code/Malware
 SANS t GIAC – Global Information Assurance Certification program. – GIAC tests knowledge and ability to put it into practice – GIAC has practical focus for individuals who have technical security responsibilities • • • security essentials intrusion detection incident handling firewalls and perimeter protection operating system security
SANS t GIAC – Global Information Assurance Certification program. – GIAC tests knowledge and ability to put it into practice – GIAC has practical focus for individuals who have technical security responsibilities • • • security essentials intrusion detection incident handling firewalls and perimeter protection operating system security
 comp. TIA t A+ Certification http: //www. comptia. org/
comp. TIA t A+ Certification http: //www. comptia. org/
 CISSE t Colloquium for Information Systems Security Education – Hosted by white house t Monday faculty workshops – Tuesday keynote secretary ridge – Wednesday keynote Australia AG – Thursday keynote VP Research Oracle http: //www. ncisse. org
CISSE t Colloquium for Information Systems Security Education – Hosted by white house t Monday faculty workshops – Tuesday keynote secretary ridge – Wednesday keynote Australia AG – Thursday keynote VP Research Oracle http: //www. ncisse. org
 CISSE Cyber Security Strategy: Meeting the Multi National Challenge Washington, DC June 1 -5 2003 http: //security. isu. edu http: //apec. isu. edu http: //seclab. cs. ucdavis. edu/projects/history Copyright 2003 Colloquium For Information Systems Security Education
CISSE Cyber Security Strategy: Meeting the Multi National Challenge Washington, DC June 1 -5 2003 http: //security. isu. edu http: //apec. isu. edu http: //seclab. cs. ucdavis. edu/projects/history Copyright 2003 Colloquium For Information Systems Security Education


