d0fa46aeb2dd74d84e9d9792b83e4dd2.ppt
- Количество слайдов: 16
 National Australia Group (UK) With Hindsight!
National Australia Group (UK) With Hindsight!
 Rules of Engagement If you have a question… raise your hand. If you are shy… speak to me later or drop me an email at: Stephen. Swann@eu. nabgroup. com
Rules of Engagement If you have a question… raise your hand. If you are shy… speak to me later or drop me an email at: Stephen. Swann@eu. nabgroup. com
 About the National The Group is an international financial services organisation that provides a comprehensive and integrated range of financial products and services. Our Purpose Growth through excellent relationships. Our Vision We will be a leading international financial services company which is trusted by you and renowned for getting it right. STRATEGIC OVERVIEW Deliver solutions that help meet customer’s complete financial needs Build and sustain a high level performance culture Build trusted relationships with all stakeholders Build and manage our portfolio of businesses for strong and sustainable total shareholder return Create and leverage strategic assets and capabilities for competitive advantage
About the National The Group is an international financial services organisation that provides a comprehensive and integrated range of financial products and services. Our Purpose Growth through excellent relationships. Our Vision We will be a leading international financial services company which is trusted by you and renowned for getting it right. STRATEGIC OVERVIEW Deliver solutions that help meet customer’s complete financial needs Build and sustain a high level performance culture Build trusted relationships with all stakeholders Build and manage our portfolio of businesses for strong and sustainable total shareholder return Create and leverage strategic assets and capabilities for competitive advantage
 So You’re Australian, right? • National Australia Group’s UK interests include: • Clydesdale Bank • Yorkshire Bank. • National Australia Bank (London) • The UK division has its own Technology team based in development centres in • Glasgow (Scotland) • Leeds (England) • Belfast (Northern Ireland) • More information can be found at www. nabgroup. com
So You’re Australian, right? • National Australia Group’s UK interests include: • Clydesdale Bank • Yorkshire Bank. • National Australia Bank (London) • The UK division has its own Technology team based in development centres in • Glasgow (Scotland) • Leeds (England) • Belfast (Northern Ireland) • More information can be found at www. nabgroup. com
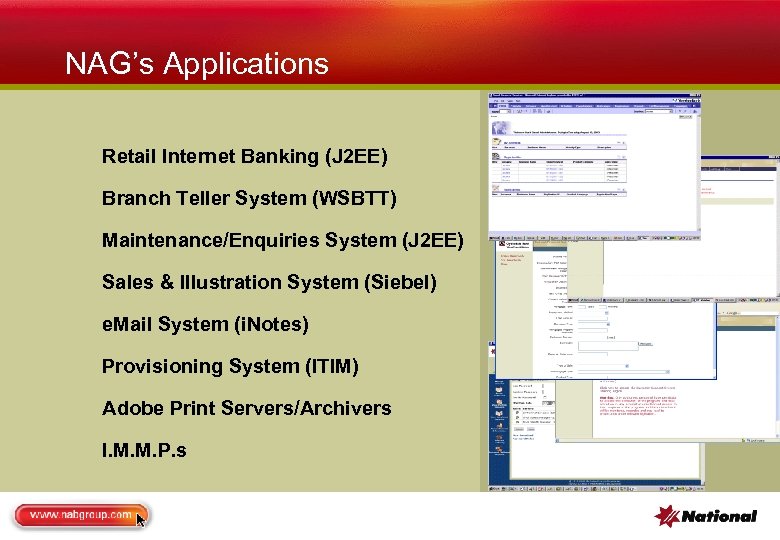 NAG’s Applications Retail Internet Banking (J 2 EE) Branch Teller System (WSBTT) Maintenance/Enquiries System (J 2 EE) Sales & Illustration System (Siebel) e. Mail System (i. Notes) Provisioning System (ITIM) Adobe Print Servers/Archivers I. M. M. P. s
NAG’s Applications Retail Internet Banking (J 2 EE) Branch Teller System (WSBTT) Maintenance/Enquiries System (J 2 EE) Sales & Illustration System (Siebel) e. Mail System (i. Notes) Provisioning System (ITIM) Adobe Print Servers/Archivers I. M. M. P. s
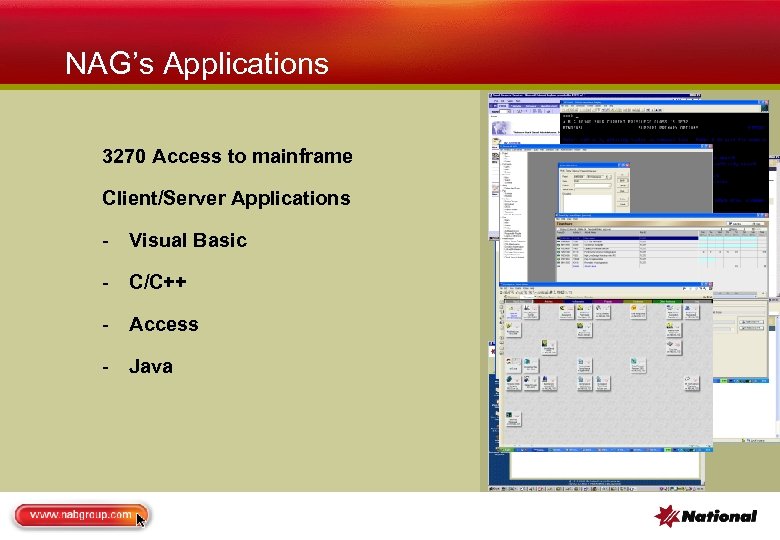 NAG’s Applications 3270 Access to mainframe Client/Server Applications - Visual Basic - C/C++ - Access - Java
NAG’s Applications 3270 Access to mainframe Client/Server Applications - Visual Basic - C/C++ - Access - Java
 NAG Project Methodology & Success Criteria Phase Business Process IM Technology Success Criteria Phase 1 (2003) Front End Replacement Common authentication & authorisation service for J 2 EE application, Siebel and i. Notes Tivoli Access Manager/e. Trust Directory New applications protected by security architecture Tivoli Access Manager/e. Trust Directory Phase 2 (2004) New Application Rollout Reduction in User. IDs & Passwords Reuse of User. IDs & Passwords Phase 3 (2005) Internet Banking Programme We are here Reuse of security architecture for customer interfaces Phase 4 (2006) Teller Replacement Account Management Tivoli Access Manager/e. Trust Directory Creation of internet facing infrastructure Tivoli Identity Manager Self-Password Reset & Provisioning Phase 5 (2006) 3 rd Party Integration Single Sign-On from company intranet to internet applications hosted by trusted 3 rd Parties Tivoli Federated Identity Manager Reuse of User. IDs & Passwords
NAG Project Methodology & Success Criteria Phase Business Process IM Technology Success Criteria Phase 1 (2003) Front End Replacement Common authentication & authorisation service for J 2 EE application, Siebel and i. Notes Tivoli Access Manager/e. Trust Directory New applications protected by security architecture Tivoli Access Manager/e. Trust Directory Phase 2 (2004) New Application Rollout Reduction in User. IDs & Passwords Reuse of User. IDs & Passwords Phase 3 (2005) Internet Banking Programme We are here Reuse of security architecture for customer interfaces Phase 4 (2006) Teller Replacement Account Management Tivoli Access Manager/e. Trust Directory Creation of internet facing infrastructure Tivoli Identity Manager Self-Password Reset & Provisioning Phase 5 (2006) 3 rd Party Integration Single Sign-On from company intranet to internet applications hosted by trusted 3 rd Parties Tivoli Federated Identity Manager Reuse of User. IDs & Passwords
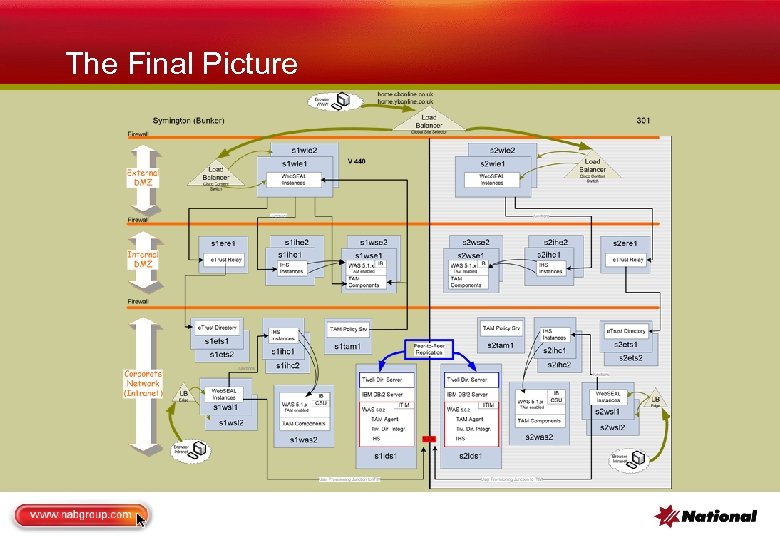 The Final Picture
The Final Picture
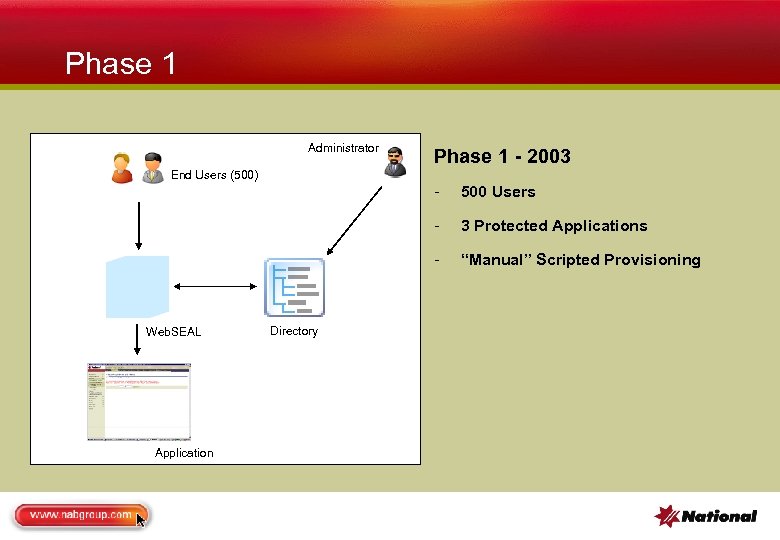 Phase 1 Administrator Phase 1 - 2003 End Users (500) - Application Directory 3 Protected Applications - Web. SEAL 500 Users “Manual” Scripted Provisioning
Phase 1 Administrator Phase 1 - 2003 End Users (500) - Application Directory 3 Protected Applications - Web. SEAL 500 Users “Manual” Scripted Provisioning
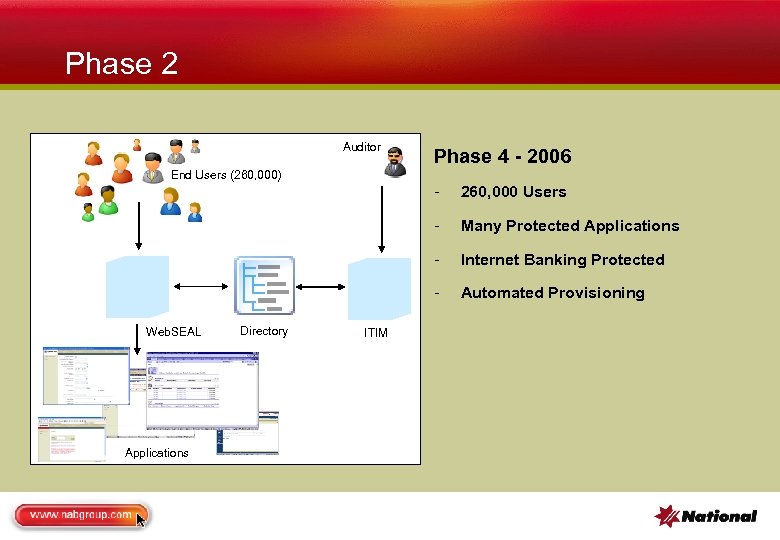 Phase 2 Auditor Phase 4 - 2006 End Users (260, 000) - Applications ITIM Internet Banking Protected Directory Many Protected Applications - Web. SEAL 260, 000 Users Automated Provisioning
Phase 2 Auditor Phase 4 - 2006 End Users (260, 000) - Applications ITIM Internet Banking Protected Directory Many Protected Applications - Web. SEAL 260, 000 Users Automated Provisioning
 NAG’s User Base & Tivoli Products • Web based access control for staff based applications • 10, 000 staff across hundreds of retail outlets and Head Office locations. • Web based access control for customer based applications • 250, 000 Internet Banking customers ( -> 700, 000 by Dec. 06) • Applications Protected • 14 Web based applications (including Internet Banking) • The Tivoli Products in use are: Tivoli Access Manager v 5. 1 Tivoli Identity Manager v 4. 5. 1 Tivoli Directory Server v 5. 2 Tivoli Directory Integrator v 6. 0
NAG’s User Base & Tivoli Products • Web based access control for staff based applications • 10, 000 staff across hundreds of retail outlets and Head Office locations. • Web based access control for customer based applications • 250, 000 Internet Banking customers ( -> 700, 000 by Dec. 06) • Applications Protected • 14 Web based applications (including Internet Banking) • The Tivoli Products in use are: Tivoli Access Manager v 5. 1 Tivoli Identity Manager v 4. 5. 1 Tivoli Directory Server v 5. 2 Tivoli Directory Integrator v 6. 0
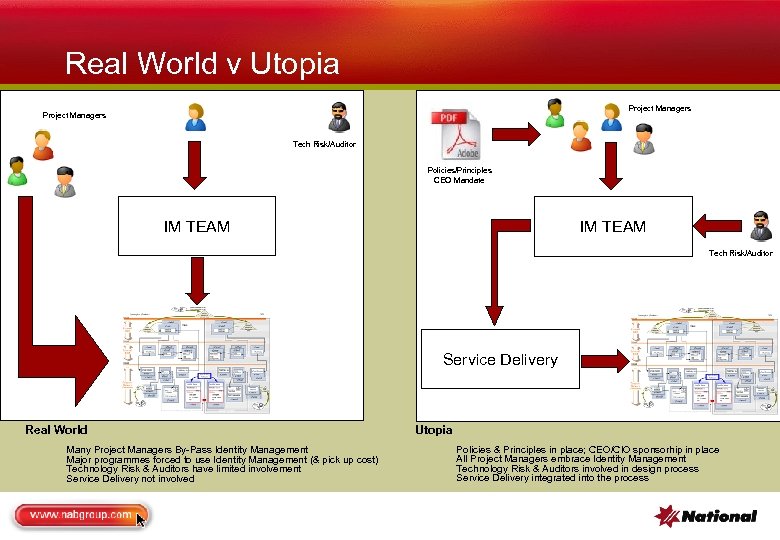 Real World v Utopia Project Managers Tech Risk/Auditor Policies/Principles CEO Mandate IM TEAM Tech Risk/Auditor Service Delivery Real World Many Project Managers By-Pass Identity Management Major programmes forced to use Identity Management (& pick up cost) Technology Risk & Auditors have limited involvement Service Delivery not involved Utopia Policies & Principles in place; CEO/CIO sponsorhip in place All Project Managers embrace Identity Management Technology Risk & Auditors involved in design process Service Delivery integrated into the process
Real World v Utopia Project Managers Tech Risk/Auditor Policies/Principles CEO Mandate IM TEAM Tech Risk/Auditor Service Delivery Real World Many Project Managers By-Pass Identity Management Major programmes forced to use Identity Management (& pick up cost) Technology Risk & Auditors have limited involvement Service Delivery not involved Utopia Policies & Principles in place; CEO/CIO sponsorhip in place All Project Managers embrace Identity Management Technology Risk & Auditors involved in design process Service Delivery integrated into the process
 If We Had It All To Do Again… • Identity Management Programme • Create an Identity Management programme rather than relying on projects to fund the infrastructure • • • Create strategy for future utilisation of infrastructure (rather than deployment by stealth Create the architectural policies, principles and guidelines up-front Deploy a provisioning solution up-front • Enterprise Support • Get Leadership Team sponsorship – both Business Sponsorship (CEO? ) and Technology (CIO? ) • Engage Audit and Technology Risk teams earlier in the design phase • Management Tools • Spend additional time working on Configuration Management; Log File Management; Auditing Capabilities and infrastructure monitoring(!)
If We Had It All To Do Again… • Identity Management Programme • Create an Identity Management programme rather than relying on projects to fund the infrastructure • • • Create strategy for future utilisation of infrastructure (rather than deployment by stealth Create the architectural policies, principles and guidelines up-front Deploy a provisioning solution up-front • Enterprise Support • Get Leadership Team sponsorship – both Business Sponsorship (CEO? ) and Technology (CIO? ) • Engage Audit and Technology Risk teams earlier in the design phase • Management Tools • Spend additional time working on Configuration Management; Log File Management; Auditing Capabilities and infrastructure monitoring(!)
 If We Had It All To Do Again… • Pay our full-time employees a lot more money!
If We Had It All To Do Again… • Pay our full-time employees a lot more money!
 Will We Achieve Our Aims? • Tivoli Access Manager for e. Business • YES • TAMeb is well integrated into our infrastructure • Performance is good & Reliability is good – “despite what they say” • Enhances productivity – Java developers no longer need worry about security • Tivoli Identity Manager • YES • Work is required to fully understand the organisational structure • Provisioning new target platforms required to fully embed the product in the infrastructure • Would greatly enhance productivity; reduce costs and free up resources – benefits, however, still to be realised • Other Tivoli Security Products • Tivoli Federated Identity Manager is a good fit for us but we are waiting on other 3 rd parties to catch up with the technology!
Will We Achieve Our Aims? • Tivoli Access Manager for e. Business • YES • TAMeb is well integrated into our infrastructure • Performance is good & Reliability is good – “despite what they say” • Enhances productivity – Java developers no longer need worry about security • Tivoli Identity Manager • YES • Work is required to fully understand the organisational structure • Provisioning new target platforms required to fully embed the product in the infrastructure • Would greatly enhance productivity; reduce costs and free up resources – benefits, however, still to be realised • Other Tivoli Security Products • Tivoli Federated Identity Manager is a good fit for us but we are waiting on other 3 rd parties to catch up with the technology!
 THANK YOU National Australia Group’s Hindsight
THANK YOU National Australia Group’s Hindsight


