3da8b21714f2056c943eec0bfa5d45d2.ppt
- Количество слайдов: 33
 My. Proxy: A Multi-Purpose Grid Authentication Service Jim Basney Senior Research Scientist NCSA jbasney@ncsa. uiuc. edu
My. Proxy: A Multi-Purpose Grid Authentication Service Jim Basney Senior Research Scientist NCSA jbasney@ncsa. uiuc. edu
 What is My. Proxy? l A service for managing X. 509 PKI credentials u l An Online Credential Repository u u l Issues short-lived X. 509 End Entity Certificates Supporting multiple authentication methods u l Issues short-lived X. 509 Proxy Certificates Long-lived private keys never leave the server An Online Certificate Authority u l A credential repository and certificate authority Passphrase, Certificate, PAM, SASL, Kerberos Open Source Software u u u WCGA 2006 Included in Globus Toolkit, VDT, and Co. G Kits C, Java, Python, and Perl clients available Contributions from EDG, UVA, LBNL, and others http: //myproxy. ncsa. uiuc. edu/ 2
What is My. Proxy? l A service for managing X. 509 PKI credentials u l An Online Credential Repository u u l Issues short-lived X. 509 End Entity Certificates Supporting multiple authentication methods u l Issues short-lived X. 509 Proxy Certificates Long-lived private keys never leave the server An Online Certificate Authority u l A credential repository and certificate authority Passphrase, Certificate, PAM, SASL, Kerberos Open Source Software u u u WCGA 2006 Included in Globus Toolkit, VDT, and Co. G Kits C, Java, Python, and Perl clients available Contributions from EDG, UVA, LBNL, and others http: //myproxy. ncsa. uiuc. edu/ 2
 My. Proxy Logon l Authenticate to retrieve PKI credentials u u Trusted CA Certificates u l End Entity or Proxy Certificate Revocation Lists (CRLs) My. Proxy maintains the user’s PKI context u u u WCGA 2006 Users don’t need to manage long-lived credentials Enables server-side monitoring and policy enforcement (ex. passphrase quality checks) CA certificates & CRLs updated automatically at login http: //myproxy. ncsa. uiuc. edu/ 3
My. Proxy Logon l Authenticate to retrieve PKI credentials u u Trusted CA Certificates u l End Entity or Proxy Certificate Revocation Lists (CRLs) My. Proxy maintains the user’s PKI context u u u WCGA 2006 Users don’t need to manage long-lived credentials Enables server-side monitoring and policy enforcement (ex. passphrase quality checks) CA certificates & CRLs updated automatically at login http: //myproxy. ncsa. uiuc. edu/ 3
 My. Proxy Authentication l Key Passphrase l X. 509 Certificate u l Used for credential renewal Pluggable Authentication Modules (PAM) u u One Time Password (OTP) u l Kerberos password Lightweight Directory Access Protocol (LDAP) password Simple Authentication and Security Layer (SASL) u WCGA 2006 Kerberos ticket (SASL GSSAPI) http: //myproxy. ncsa. uiuc. edu/ 4
My. Proxy Authentication l Key Passphrase l X. 509 Certificate u l Used for credential renewal Pluggable Authentication Modules (PAM) u u One Time Password (OTP) u l Kerberos password Lightweight Directory Access Protocol (LDAP) password Simple Authentication and Security Layer (SASL) u WCGA 2006 Kerberos ticket (SASL GSSAPI) http: //myproxy. ncsa. uiuc. edu/ 4
 My. Proxy Online Certificate Authority l Issues short-lived X. 509 End Entity Certificates u u l Ties in to site authentication and accounting u u l l Leverages My. Proxy authentication mechanisms Compatible with existing My. Proxy clients Using PAM and/or Kerberos authentication Map username to certificate subject via “gridmap” file or LDAP query Avoid need for long-lived user keys Server can function as both CA and repository u WCGA 2006 Issues certificate if no credentials for user are stored http: //myproxy. ncsa. uiuc. edu/ 5
My. Proxy Online Certificate Authority l Issues short-lived X. 509 End Entity Certificates u u l Ties in to site authentication and accounting u u l l Leverages My. Proxy authentication mechanisms Compatible with existing My. Proxy clients Using PAM and/or Kerberos authentication Map username to certificate subject via “gridmap” file or LDAP query Avoid need for long-lived user keys Server can function as both CA and repository u WCGA 2006 Issues certificate if no credentials for user are stored http: //myproxy. ncsa. uiuc. edu/ 5
 My. Proxy Online Credential Repository l Stores X. 509 End Entity and Proxy credentials u u Credentials may be stored directly or via proxy delegation u l Private keys encrypted with user-chosen passphrases Users can store multiple credentials from different CAs Access to credentials controlled by user and administrator policies u u u l Set authentication requirements Control whether credentials can be retrieved directly or if only proxy delegation is allowed Restrict lifetime of retrieved proxy credentials Can be deployed for a single user, a site, a virtual organization, a resource provider, a CA, etc. WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 6
My. Proxy Online Credential Repository l Stores X. 509 End Entity and Proxy credentials u u Credentials may be stored directly or via proxy delegation u l Private keys encrypted with user-chosen passphrases Users can store multiple credentials from different CAs Access to credentials controlled by user and administrator policies u u u l Set authentication requirements Control whether credentials can be retrieved directly or if only proxy delegation is allowed Restrict lifetime of retrieved proxy credentials Can be deployed for a single user, a site, a virtual organization, a resource provider, a CA, etc. WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 6
 Talk Outline l l My. Proxy Introduction PKI Introduction and My. Proxy CA Proxy Certificates and My. Proxy Repository My. Proxy Scenarios u u u l l Administratively Loaded Credentials Registration Portals Web Portal Authentication and Delegation Password-based Delegation Credential Renewal Web Single Sign-On (SSO) Demos Conclusion WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 7
Talk Outline l l My. Proxy Introduction PKI Introduction and My. Proxy CA Proxy Certificates and My. Proxy Repository My. Proxy Scenarios u u u l l Administratively Loaded Credentials Registration Portals Web Portal Authentication and Delegation Password-based Delegation Credential Renewal Web Single Sign-On (SSO) Demos Conclusion WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 7
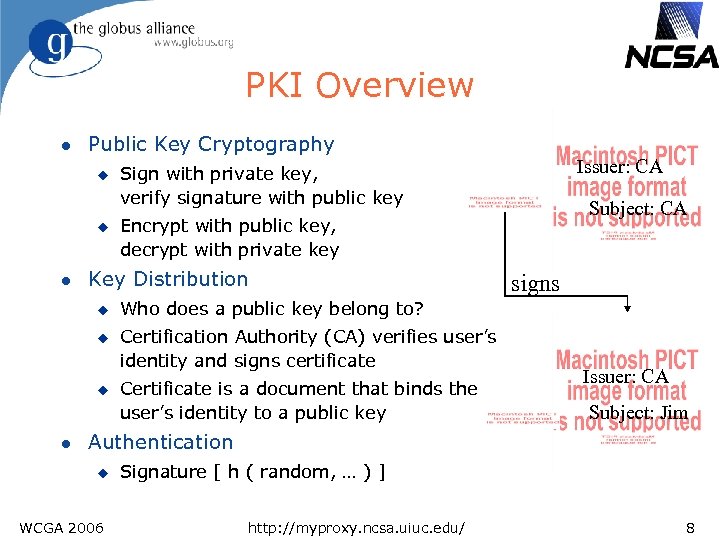 PKI Overview l Public Key Cryptography u u l Subject: CA Encrypt with public key, decrypt with private key Key Distribution u Issuer: CA Sign with private key, verify signature with public key signs Who does a public key belong to? Certification Authority (CA) verifies user’s identity and signs certificate Certificate is a document that binds the user’s identity to a public key Issuer: CA Subject: Jim Authentication u WCGA 2006 Signature [ h ( random, … ) ] http: //myproxy. ncsa. uiuc. edu/ 8
PKI Overview l Public Key Cryptography u u l Subject: CA Encrypt with public key, decrypt with private key Key Distribution u Issuer: CA Sign with private key, verify signature with public key signs Who does a public key belong to? Certification Authority (CA) verifies user’s identity and signs certificate Certificate is a document that binds the user’s identity to a public key Issuer: CA Subject: Jim Authentication u WCGA 2006 Signature [ h ( random, … ) ] http: //myproxy. ncsa. uiuc. edu/ 8
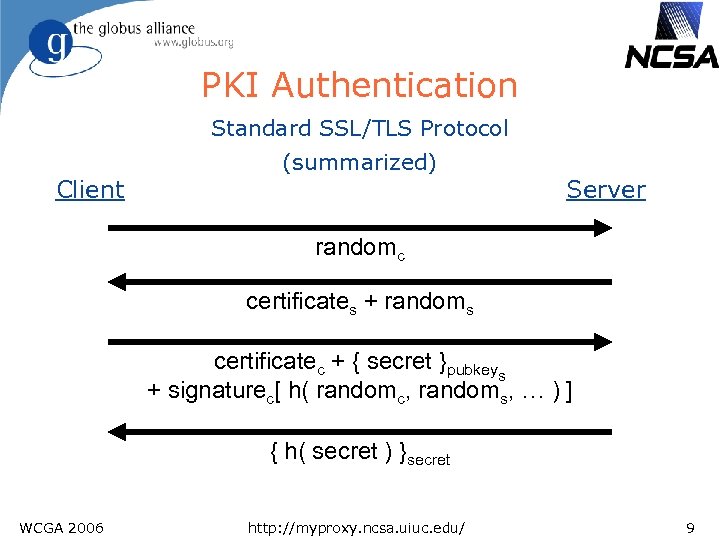 PKI Authentication Standard SSL/TLS Protocol Client (summarized) Server randomc certificates + randoms certificatec + { secret }pubkeys + signaturec[ h( randomc, randoms, … ) ] { h( secret ) }secret WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 9
PKI Authentication Standard SSL/TLS Protocol Client (summarized) Server randomc certificates + randoms certificatec + { secret }pubkeys + signaturec[ h( randomc, randoms, … ) ] { h( secret ) }secret WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 9
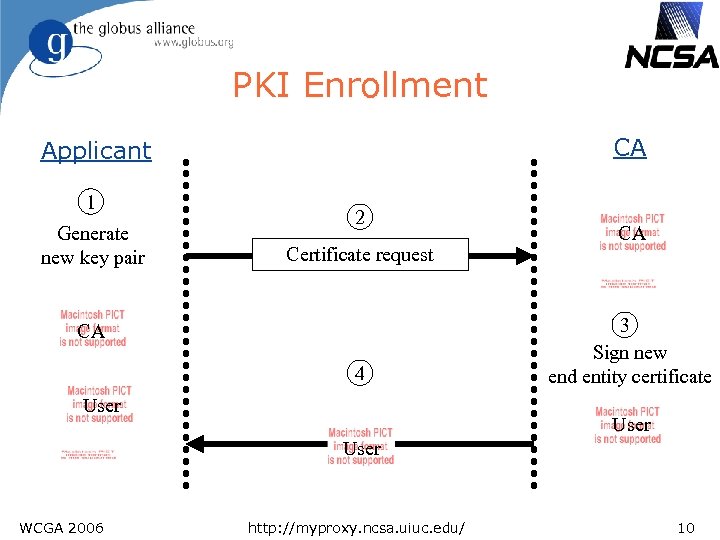 PKI Enrollment CA Applicant 1 Generate new key pair 2 Certificate request CA 4 User CA 3 Sign new end entity certificate User WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 10
PKI Enrollment CA Applicant 1 Generate new key pair 2 Certificate request CA 4 User CA 3 Sign new end entity certificate User WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 10
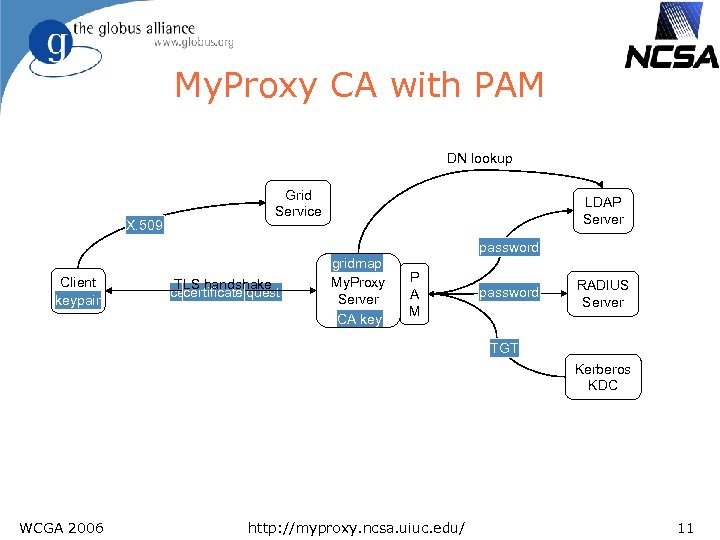 My. Proxy CA with PAM DN lookup X. 509 Grid Service LDAP Server password Client keypair TLS handshake certificate request certificate password gridmap My. Proxy Server CA key P A M password RADIUS Server TGT Kerberos KDC WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 11
My. Proxy CA with PAM DN lookup X. 509 Grid Service LDAP Server password Client keypair TLS handshake certificate request certificate password gridmap My. Proxy Server CA key P A M password RADIUS Server TGT Kerberos KDC WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 11
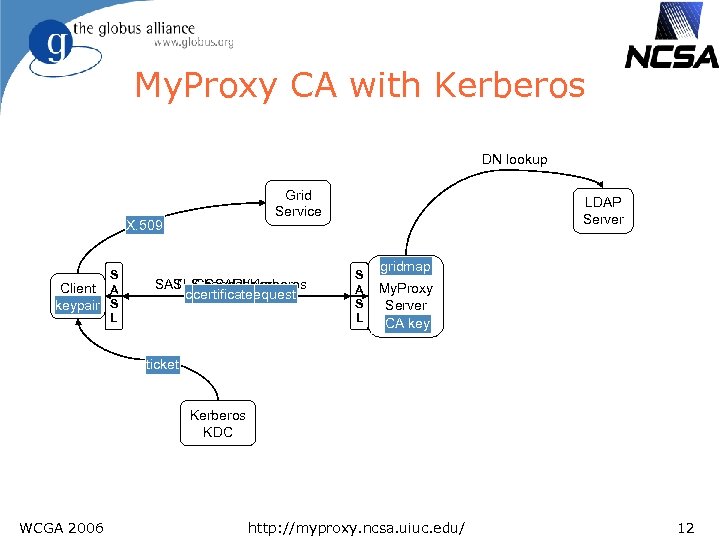 My. Proxy CA with Kerberos DN lookup Grid Service X. 509 S Client A keypair S L TLS handshake SASL/GSSAPI/Kerberos certificate request certificate LDAP Server S A S L gridmap My. Proxy Server CA key ticket Kerberos KDC WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 12
My. Proxy CA with Kerberos DN lookup Grid Service X. 509 S Client A keypair S L TLS handshake SASL/GSSAPI/Kerberos certificate request certificate LDAP Server S A S L gridmap My. Proxy Server CA key ticket Kerberos KDC WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 12
 PAM/SASL Issues l PAM Conversation u u PAM modules can require multiple rounds of user interaction No standard protocol l SASL/PLAIN doesn’t support multiple rounds Need something like SSH keyboard-interactive protocol SASL client-side setup u u WCGA 2006 Requires SASL library and configuration of SASL mechanisms Alternative: native Kerberos protocol support http: //myproxy. ncsa. uiuc. edu/ 13
PAM/SASL Issues l PAM Conversation u u PAM modules can require multiple rounds of user interaction No standard protocol l SASL/PLAIN doesn’t support multiple rounds Need something like SSH keyboard-interactive protocol SASL client-side setup u u WCGA 2006 Requires SASL library and configuration of SASL mechanisms Alternative: native Kerberos protocol support http: //myproxy. ncsa. uiuc. edu/ 13
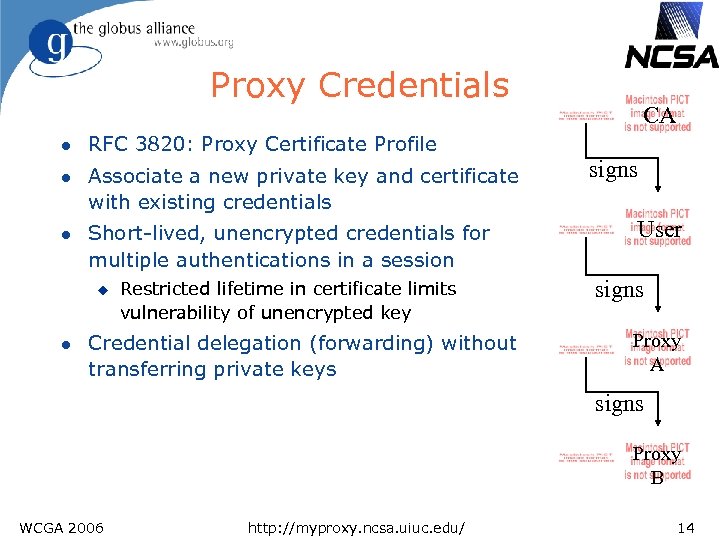 Proxy Credentials l RFC 3820: Proxy Certificate Profile l Associate a new private key and certificate with existing credentials l Short-lived, unencrypted credentials for multiple authentications in a session u l Restricted lifetime in certificate limits vulnerability of unencrypted key Credential delegation (forwarding) without transferring private keys CA signs User signs Proxy A signs Proxy B WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 14
Proxy Credentials l RFC 3820: Proxy Certificate Profile l Associate a new private key and certificate with existing credentials l Short-lived, unencrypted credentials for multiple authentications in a session u l Restricted lifetime in certificate limits vulnerability of unencrypted key Credential delegation (forwarding) without transferring private keys CA signs User signs Proxy A signs Proxy B WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 14
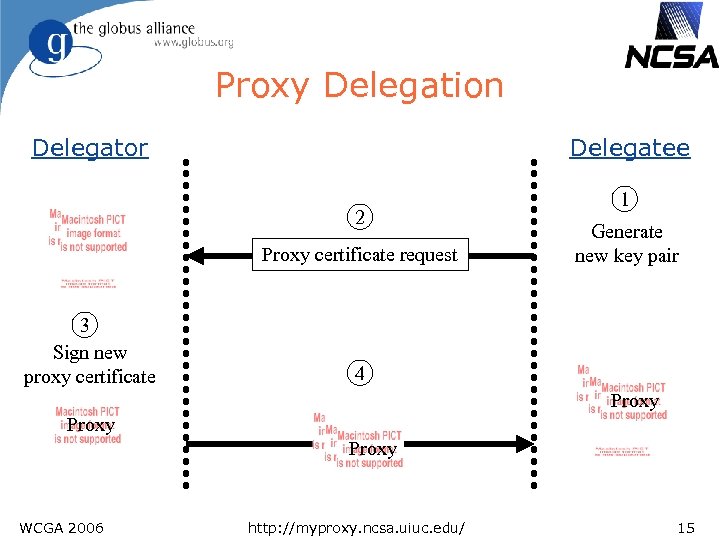 Proxy Delegation Delegator Delegatee 2 Proxy certificate request 3 Sign new proxy certificate 1 Generate new key pair 4 Proxy WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 15
Proxy Delegation Delegator Delegatee 2 Proxy certificate request 3 Sign new proxy certificate 1 Generate new key pair 4 Proxy WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 15
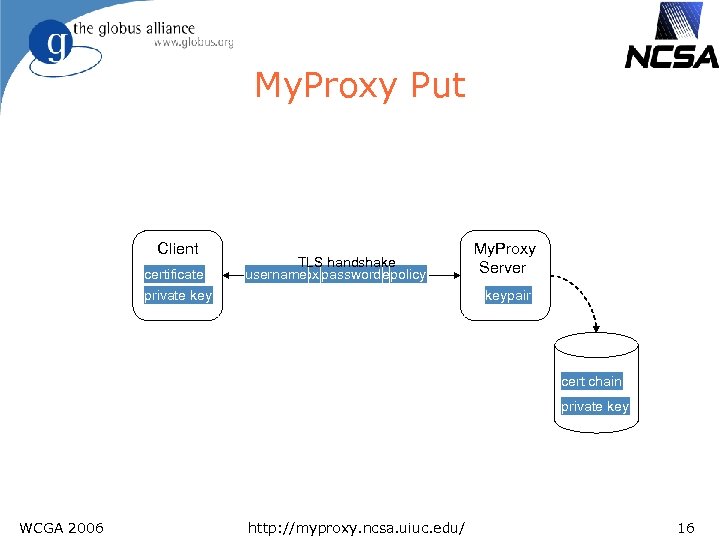 My. Proxy Put Client certificate private key TLS handshake username certificate request proxy certificate policy password chain My. Proxy Server keypair cert chain private key WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 16
My. Proxy Put Client certificate private key TLS handshake username certificate request proxy certificate policy password chain My. Proxy Server keypair cert chain private key WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 16
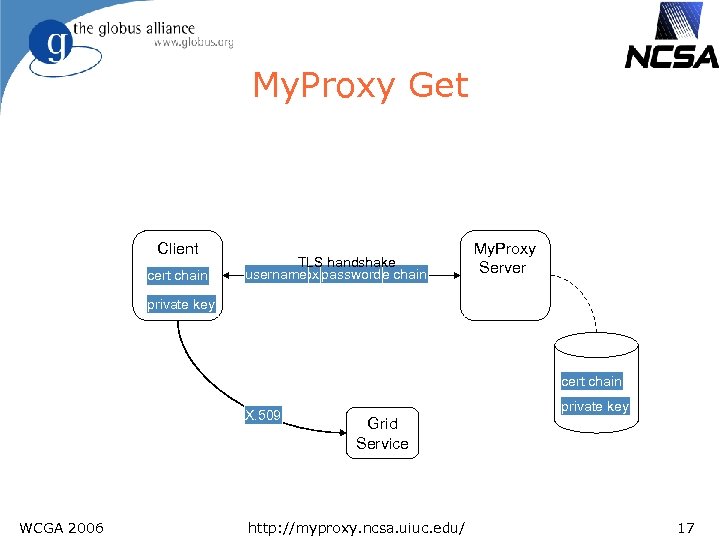 My. Proxy Get Client cert chain TLS handshake username certificate request proxy certificate chain password My. Proxy Server private key cert chain X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 17
My. Proxy Get Client cert chain TLS handshake username certificate request proxy certificate chain password My. Proxy Server private key cert chain X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 17
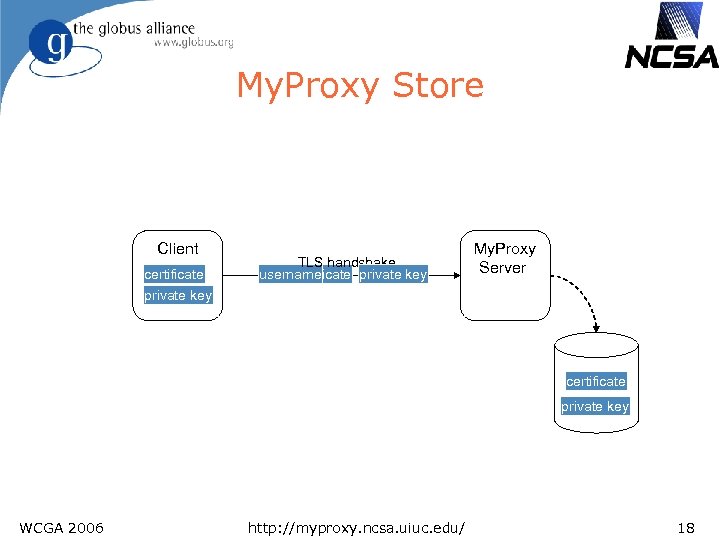 My. Proxy Store Client certificate private key TLS handshake username certificate private key policy My. Proxy Server certificate private key WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 18
My. Proxy Store Client certificate private key TLS handshake username certificate private key policy My. Proxy Server certificate private key WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 18
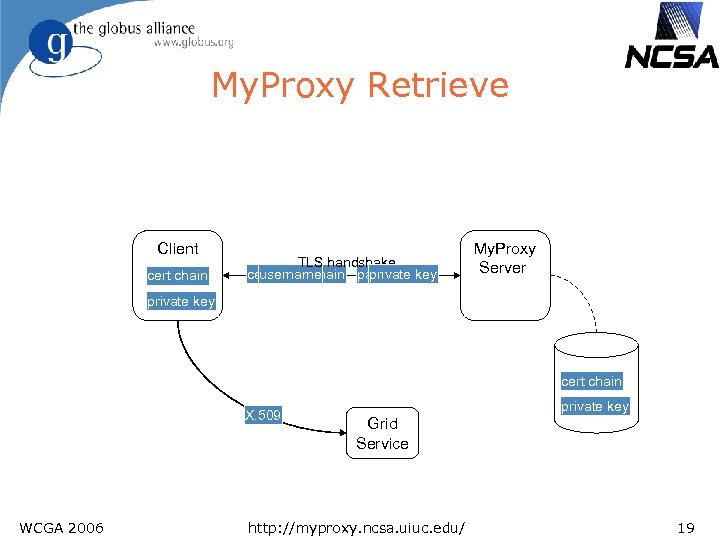 My. Proxy Retrieve Client cert chain TLS handshake certificate chain passwordkey username private My. Proxy Server private key cert chain X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 19
My. Proxy Retrieve Client cert chain TLS handshake certificate chain passwordkey username private My. Proxy Server private key cert chain X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 19
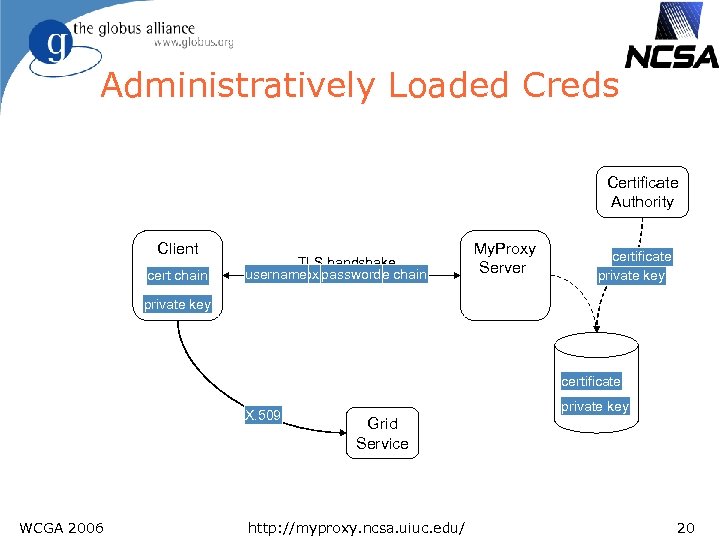 Administratively Loaded Creds Certificate Authority Client cert chain TLS handshake username certificate request proxy certificate chain password My. Proxy Server certificate private key certificate X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 20
Administratively Loaded Creds Certificate Authority Client cert chain TLS handshake username certificate request proxy certificate chain password My. Proxy Server certificate private key certificate X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 20
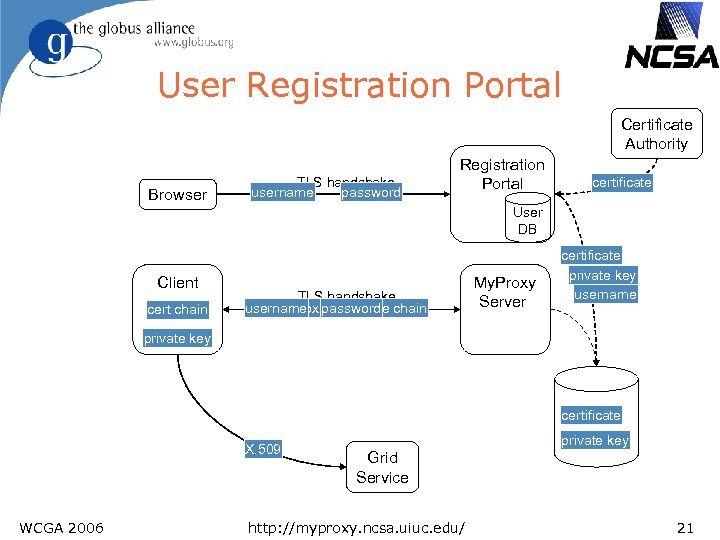 User Registration Portal Certificate Authority Browser TLS handshake username password Registration Portal certificate User DB Client cert chain TLS handshake username certificate request proxy certificate chain password My. Proxy Server certificate private key username private key certificate X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 21
User Registration Portal Certificate Authority Browser TLS handshake username password Registration Portal certificate User DB Client cert chain TLS handshake username certificate request proxy certificate chain password My. Proxy Server certificate private key username private key certificate X. 509 WCGA 2006 private key Grid Service http: //myproxy. ncsa. uiuc. edu/ 21
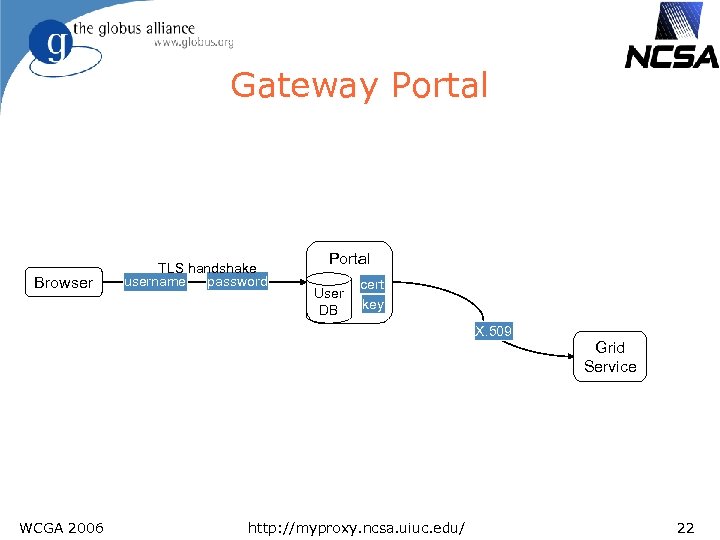 Gateway Portal Browser TLS handshake password username Portal User DB cert key X. 509 WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ Grid Service 22
Gateway Portal Browser TLS handshake password username Portal User DB cert key X. 509 WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ Grid Service 22
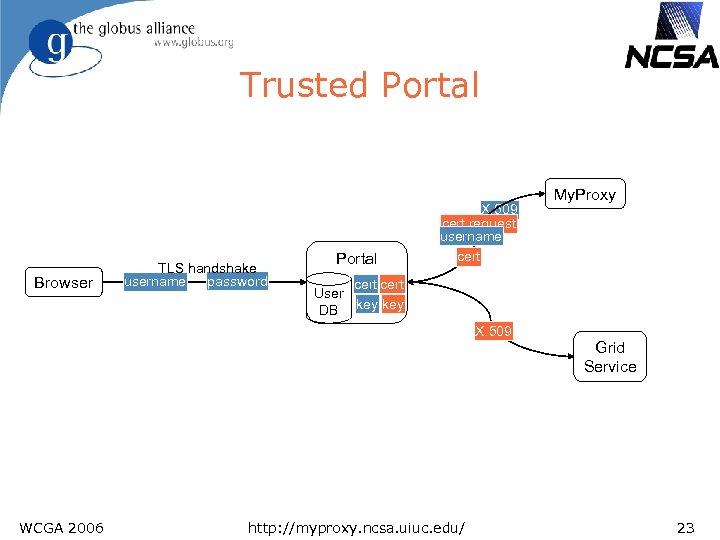 Trusted Portal Browser TLS handshake password username Portal X. 509 cert request username cert User DB key X. 509 WCGA 2006 My. Proxy http: //myproxy. ncsa. uiuc. edu/ Grid Service 23
Trusted Portal Browser TLS handshake password username Portal X. 509 cert request username cert User DB key X. 509 WCGA 2006 My. Proxy http: //myproxy. ncsa. uiuc. edu/ Grid Service 23
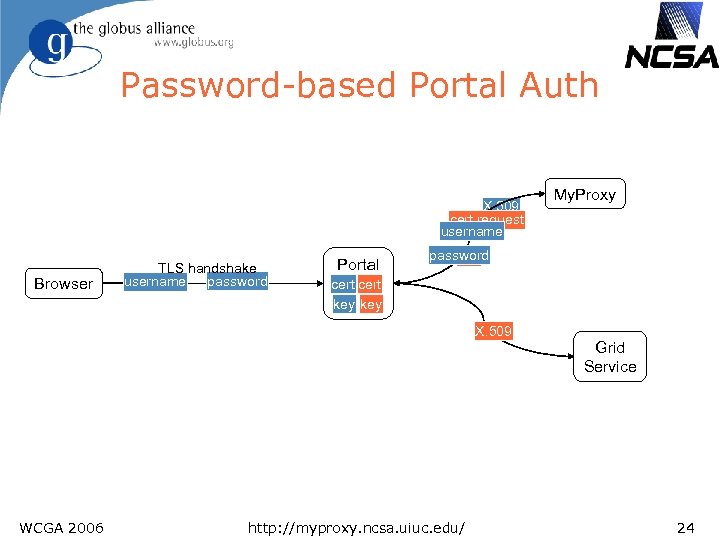 Password-based Portal Auth X. 509 cert request username Browser TLS handshake password username Portal password cert key X. 509 WCGA 2006 My. Proxy http: //myproxy. ncsa. uiuc. edu/ Grid Service 24
Password-based Portal Auth X. 509 cert request username Browser TLS handshake password username Portal password cert key X. 509 WCGA 2006 My. Proxy http: //myproxy. ncsa. uiuc. edu/ Grid Service 24
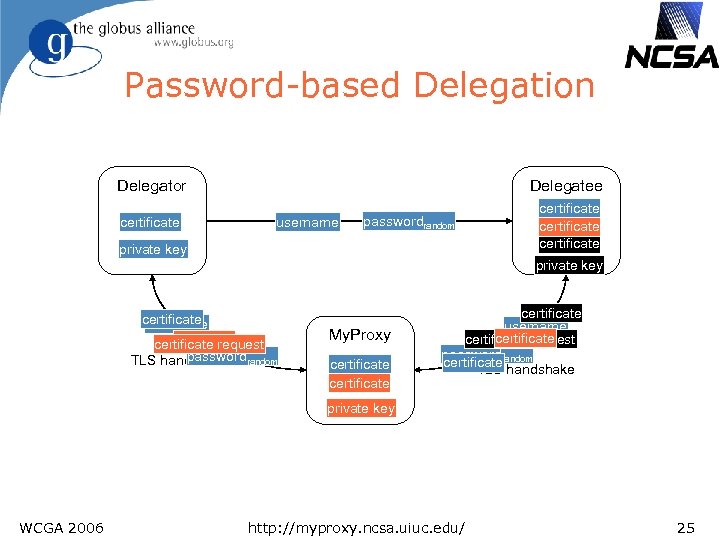 Password-based Delegation Delegator certificate Delegatee username passwordrandom private key certificate private key certificate username certificate request password TLS handshake random My. Proxy certificate username certificate request passwordrandom certificate handshake TLS private key WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 25
Password-based Delegation Delegator certificate Delegatee username passwordrandom private key certificate private key certificate username certificate request password TLS handshake random My. Proxy certificate username certificate request passwordrandom certificate handshake TLS private key WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 25
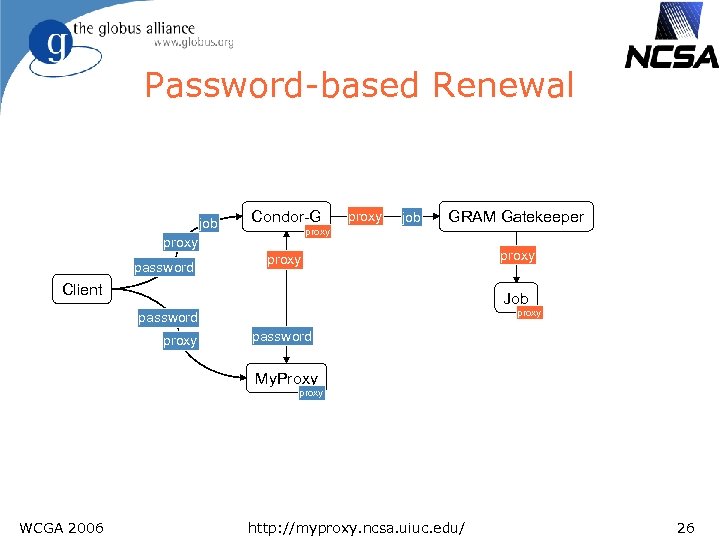 Password-based Renewal job Condor-G proxy password proxy job GRAM Gatekeeper proxy Client proxy Job proxy password My. Proxy proxy WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 26
Password-based Renewal job Condor-G proxy password proxy job GRAM Gatekeeper proxy Client proxy Job proxy password My. Proxy proxy WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 26
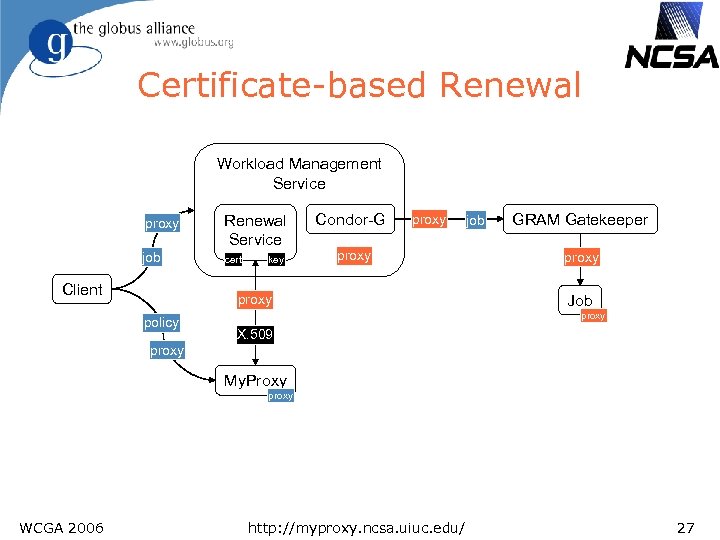 Certificate-based Renewal Workload Management Service proxy Renewal Service job cert Client key Condor-G proxy policy job GRAM Gatekeeper proxy Job proxy X. 509 proxy My. Proxy proxy WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 27
Certificate-based Renewal Workload Management Service proxy Renewal Service job cert Client key Condor-G proxy policy job GRAM Gatekeeper proxy Job proxy X. 509 proxy My. Proxy proxy WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 27
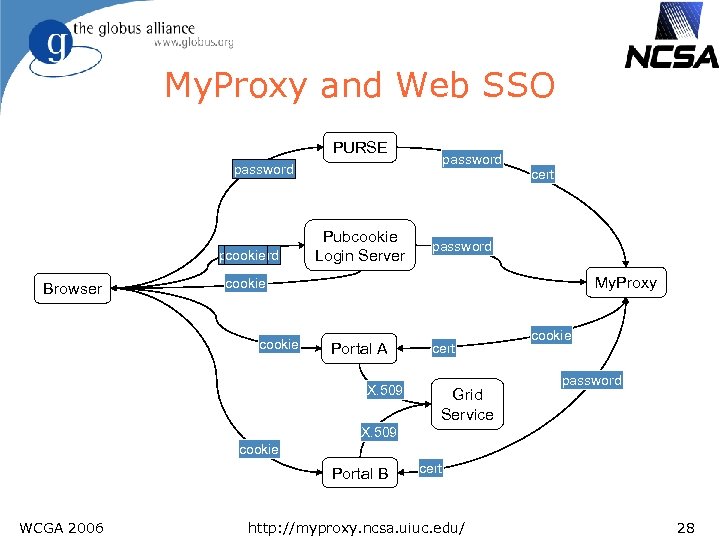 My. Proxy and Web SSO PURSE password cookie Browser Pubcookie Login Server cert password My. Proxy cookie Portal A X. 509 cert Grid Service cookie password X. 509 cookie Portal B WCGA 2006 cert http: //myproxy. ncsa. uiuc. edu/ 28
My. Proxy and Web SSO PURSE password cookie Browser Pubcookie Login Server cert password My. Proxy cookie Portal A X. 509 cert Grid Service cookie password X. 509 cookie Portal B WCGA 2006 cert http: //myproxy. ncsa. uiuc. edu/ 28
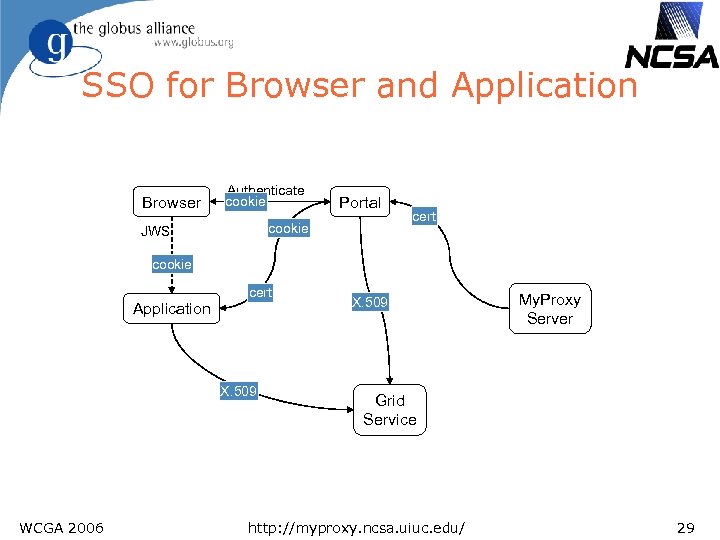 SSO for Browser and Application Browser Authenticate cookie Portal cookie JWS cert cookie Application cert X. 509 WCGA 2006 X. 509 My. Proxy Server Grid Service http: //myproxy. ncsa. uiuc. edu/ 29
SSO for Browser and Application Browser Authenticate cookie Portal cookie JWS cert cookie Application cert X. 509 WCGA 2006 X. 509 My. Proxy Server Grid Service http: //myproxy. ncsa. uiuc. edu/ 29
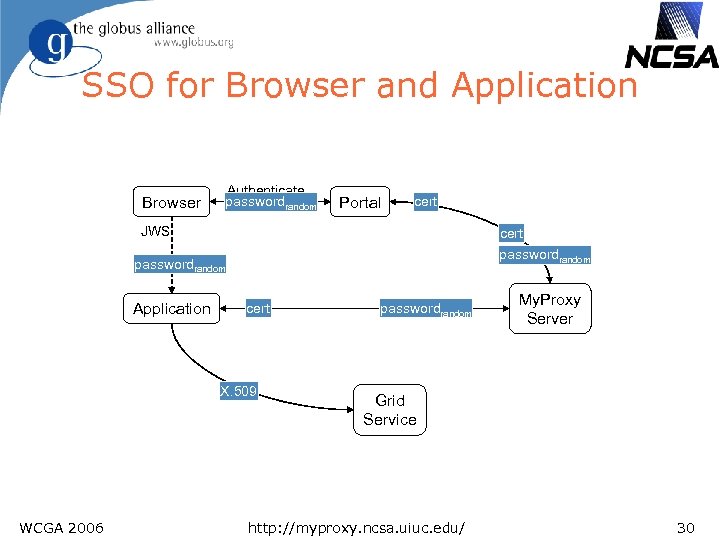 SSO for Browser and Application Browser Authenticate passwordrandom Portal cert JWS cert passwordrandom Application cert X. 509 WCGA 2006 passwordrandom My. Proxy Server Grid Service http: //myproxy. ncsa. uiuc. edu/ 30
SSO for Browser and Application Browser Authenticate passwordrandom Portal cert JWS cert passwordrandom Application cert X. 509 WCGA 2006 passwordrandom My. Proxy Server Grid Service http: //myproxy. ncsa. uiuc. edu/ 30
 Demonstrations WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 31
Demonstrations WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 31
 Conclusion l My. Proxy: A Multi-Purpose Grid Authentication Service u l Used in many delegation and single sign-on scenarios My. Proxy provides practical authentication solutions u u Minimize changes to existing software and protocols Leverage community standards l l PAM, SASL, Kerberos, LDAP, Pubcookie, Shibboleth Active My. Proxy open source community u u WCGA 2006 Deploy new developments via My. Proxy Benefit from the work of others http: //myproxy. ncsa. uiuc. edu/ 32
Conclusion l My. Proxy: A Multi-Purpose Grid Authentication Service u l Used in many delegation and single sign-on scenarios My. Proxy provides practical authentication solutions u u Minimize changes to existing software and protocols Leverage community standards l l PAM, SASL, Kerberos, LDAP, Pubcookie, Shibboleth Active My. Proxy open source community u u WCGA 2006 Deploy new developments via My. Proxy Benefit from the work of others http: //myproxy. ncsa. uiuc. edu/ 32
 Thank you! Obrigado! WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 33
Thank you! Obrigado! WCGA 2006 http: //myproxy. ncsa. uiuc. edu/ 33


