1197e427ad18ccd35ed057f76ff91ed9.ppt
- Количество слайдов: 19

MSRC: (M)icropayment (S)cheme with Ability to (R)eturn (C)hanges Source: Journal of Information Science and Engineering in review Presenter: Tsuei-Hung Sun (孫翠鴻) Date: 2010/11/26

Outline éIntroduction éMotivation éScheme éSecurity analysis éComparison éAdvantage vs. weakness éComment 2
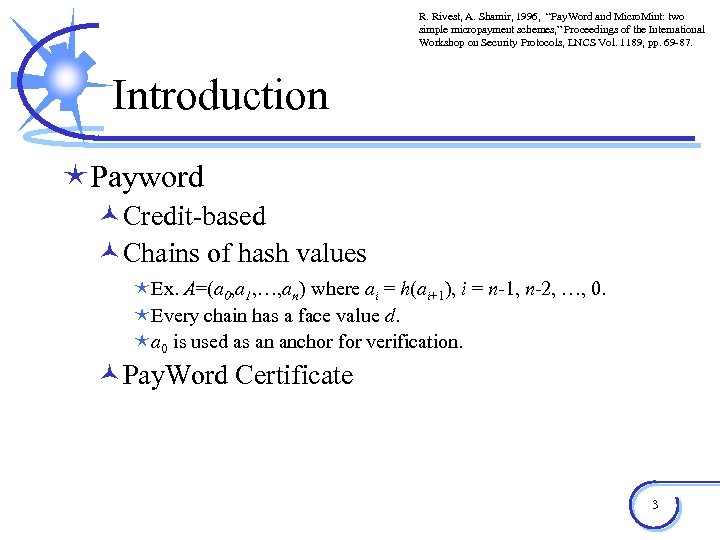
R. Rivest, A. Shamir, 1996, “Pay. Word and Micro. Mint: two simple micropayment schemes, ” Proceedings of the International Workshop on Security Protocols, LNCS Vol. 1189, pp. 69 -87. Introduction éPayword ©Credit-based ©Chains of hash values éEx. A=(a 0, a 1, …, an) where ai = h(ai+1), i = n-1, n-2, …, 0. éEvery chain has a face value d. éa 0 is used as an anchor for verification. ©Pay. Word Certificate 3
Introduction é Micropayment Scheme Using Single-Pay. Word Chain (MSSC) ©Only one denomination. é Micropayment Scheme Using Multi-Pay. Word Chains (MSMC) ©Multiple denomination. ©Combining several single-payword chains with different denomination values. ©Using to reduce the length of hash chain and the hash operations of verification. 4
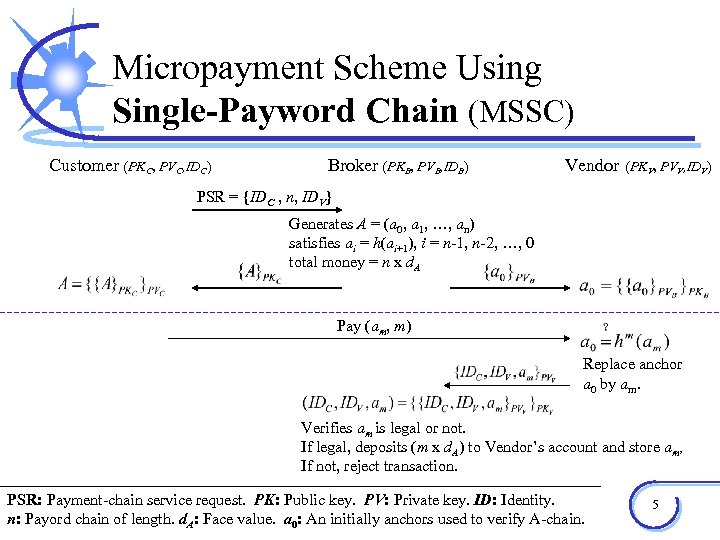
Micropayment Scheme Using Single-Payword Chain (MSSC) Customer (PKC, PVC, IDC) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) PSR = {IDC , n, IDV} Generates A = (a 0, a 1, …, an) satisfies ai = h(ai+1), i = n-1, n-2, …, 0 total money = n x d. A Pay (am, m) Replace anchor a 0 by am. Verifies am is legal or not. If legal, deposits (m x d. A) to Vendor’s account and store am, If not, reject transaction. PSR: Payment-chain service request. PK: Public key. PV: Private key. ID: Identity. n: Payord chain of length. d. A: Face value. a 0: An initially anchors used to verify A-chain. 5
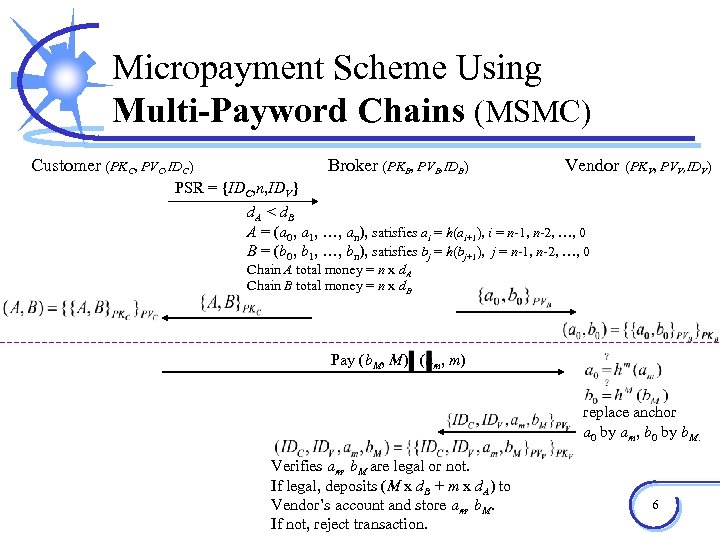
Micropayment Scheme Using Multi-Payword Chains (MSMC) Customer (PKC, PVC, IDC) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) PSR = {IDC, n, IDV} d. A < d. B A = (a 0, a 1, …, an), satisfies ai = h(ai+1), i = n-1, n-2, …, 0 B = (b 0, b 1, …, bn), satisfies bj = h(bj+1), j = n-1, n-2, …, 0 Chain A total money = n x d. A Chain B total money = n x d. B Pay (b. M, M) (am, m) replace anchor a 0 by am, b 0 by b. M. Verifies am, b. M are legal or not. If legal, deposits (M x d. B + m x d. A) to Vendor’s account and store am, b. M. If not, reject transaction. 6

Motivation éProblems of MSMC ©Find the minimum hash chain in a payment. ©Equally spend every single chain. éThis paper propose three approaches to handle above two problems and supporting the ability of returning changes. 7
Scheme éThree approaches methods ©MSRC-I: counter-mode encryption. ©MSRC-II: hashing function. ©MSRC-III: keyed hashing function. 8
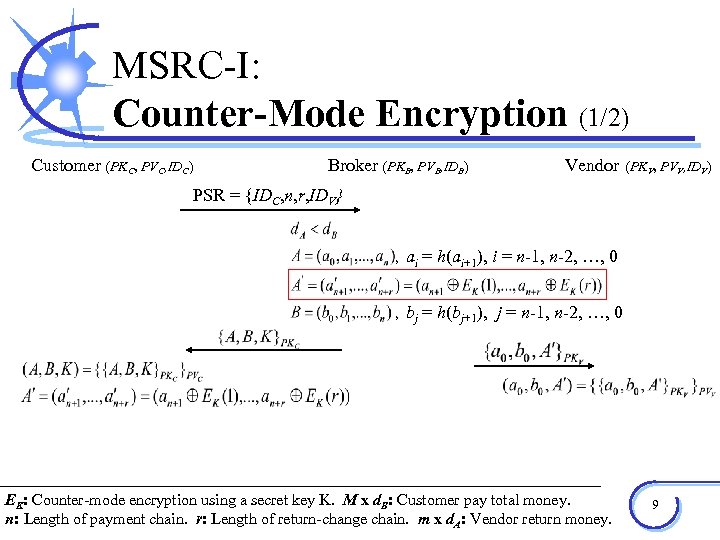
MSRC-I: Counter-Mode Encryption (1/2) Customer (PKC, PVC, IDC) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) PSR = {IDC, n, r, IDV} , ai = h(ai+1), i = n-1, n-2, …, 0 , bj = h(bj+1), j = n-1, n-2, …, 0 EK: Counter-mode encryption using a secret key K. M x d. B: Customer pay total money. n: Length of payment chain. r: Length of return-change chain. m x d. A: Vendor return money. 9
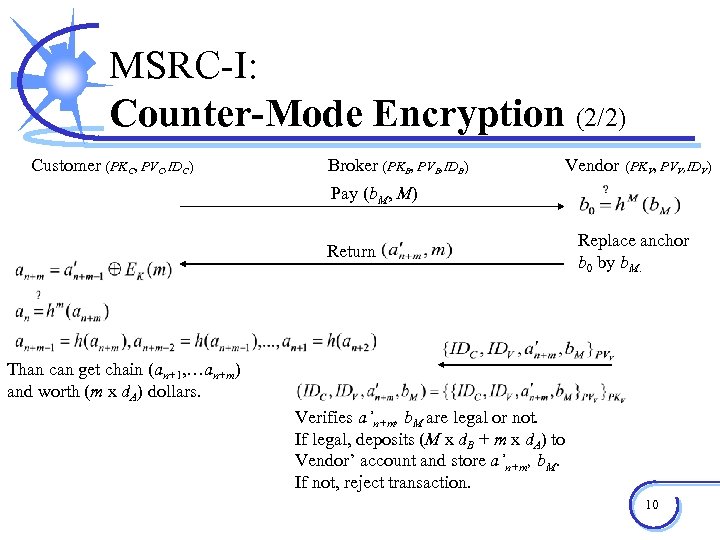
MSRC-I: Counter-Mode Encryption (2/2) Customer (PKC, PVC, IDC) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) Pay (b. M, M) Return Replace anchor b 0 by b. M. Than can get chain (an+1, …an+m) and worth (m x d. A) dollars. Verifies a’n+m, b. M are legal or not. If legal, deposits (M x d. B + m x d. A) to Vendor’ account and store a’n+m, b. M. If not, reject transaction. 10
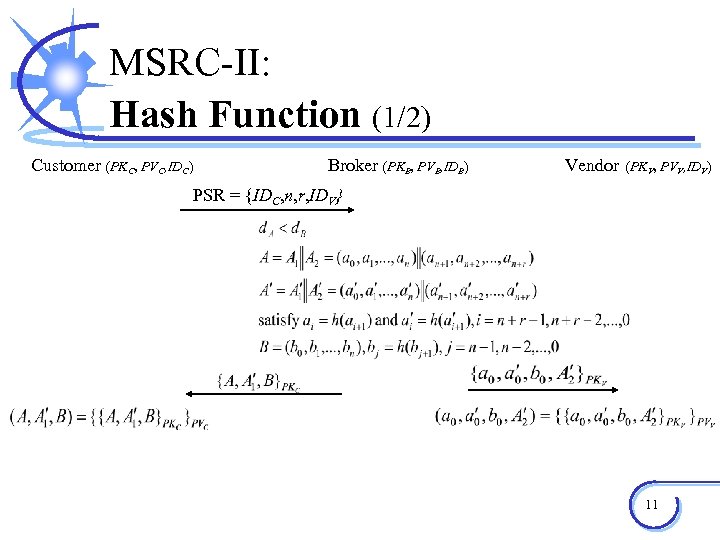
MSRC-II: Hash Function (1/2) Customer (PKC, PVC, IDC) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) PSR = {IDC, n, r, IDV} 11
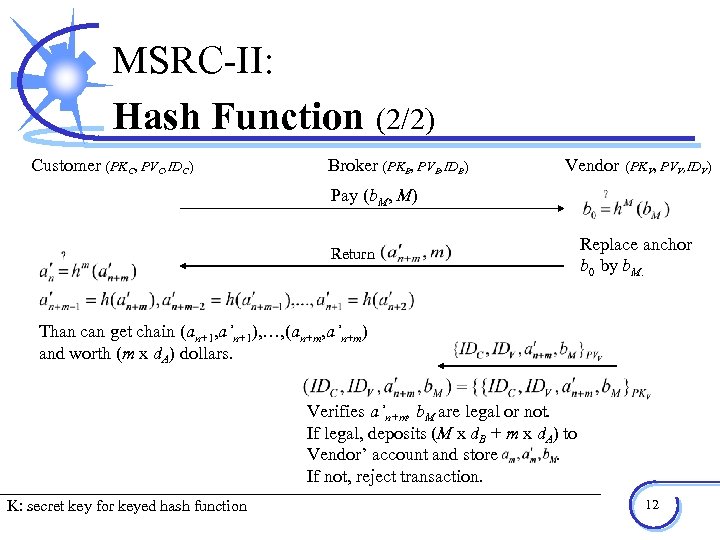
MSRC-II: Hash Function Customer (PKC, PVC, IDC) (2/2) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) Pay (b. M, M) Return Replace anchor b 0 by b. M. Than can get chain (an+1, a’n+1), …, (an+m, a’n+m) and worth (m x d. A) dollars. Verifies a’n+m, b. M are legal or not. If legal, deposits (M x d. B + m x d. A) to Vendor’ account and store. If not, reject transaction. K: secret key for keyed hash function 12
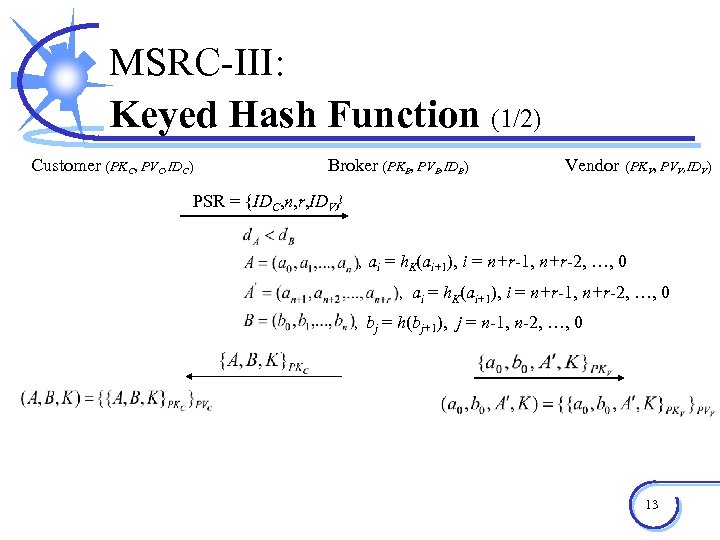
MSRC-III: Keyed Hash Function (1/2) Customer (PKC, PVC, IDC) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) PSR = {IDC, n, r, IDV} , ai = h. K(ai+1), i = n+r-1, n+r-2, …, 0 , bj = h(bj+1), j = n-1, n-2, …, 0 13
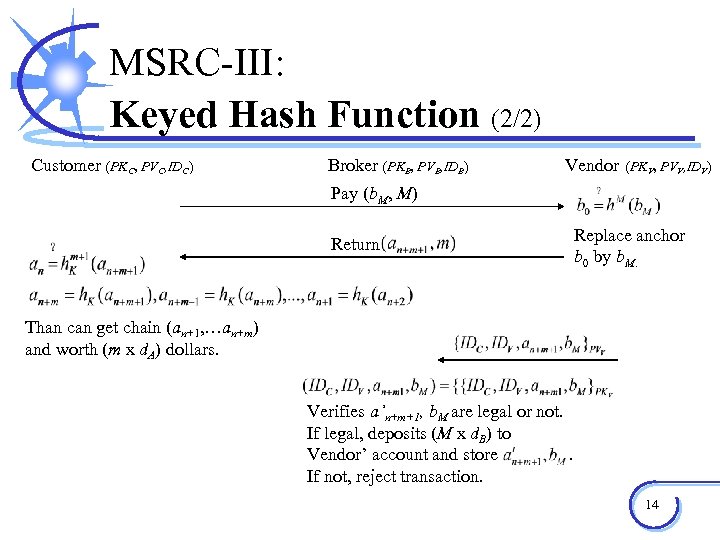
MSRC-III: Keyed Hash Function (2/2) Customer (PKC, PVC, IDC) Broker (PKB, PVB, IDB) Vendor (PKV, PVV, IDV) Pay (b. M, M) Return Replace anchor b 0 by b. M. Than can get chain (an+1, …an+m) and worth (m x d. A) dollars. Verifies a’n+m+1, b. M are legal or not. If legal, deposits (M x d. B) to Vendor’ account and store. If not, reject transaction. 14
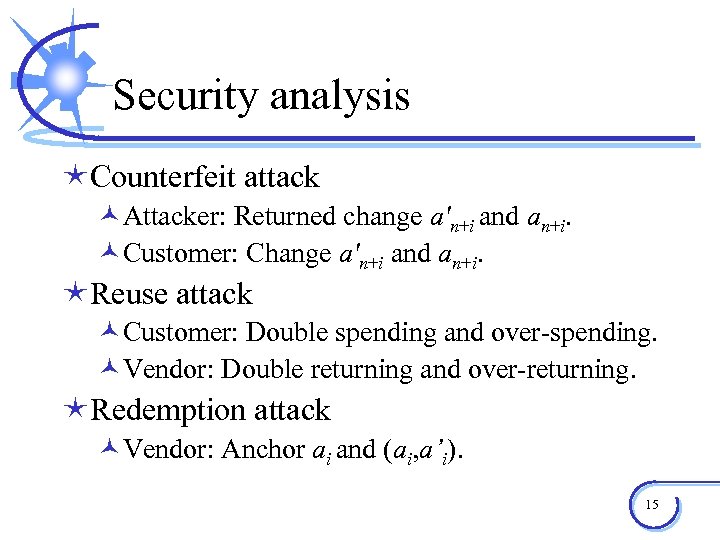
Security analysis éCounterfeit attack ©Attacker: Returned change a'n+i and an+i. ©Customer: Change a'n+i and an+i. éReuse attack ©Customer: Double spending and over-spending. ©Vendor: Double returning and over-returning. éRedemption attack ©Vendor: Anchor ai and (ai, a’i). 15
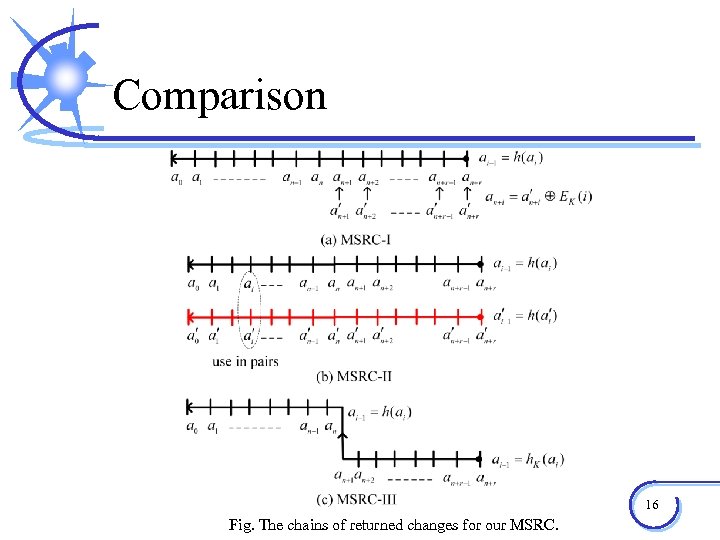
Comparison 16 Fig. The chains of returned changes for our MSRC.
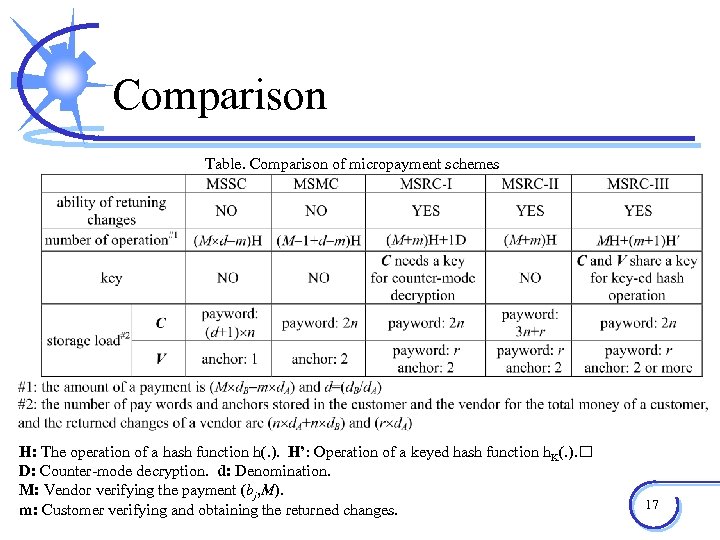
Comparison Table. Comparison of micropayment schemes H: The operation of a hash function h(. ). H’: Operation of a keyed hash function h. K(. ). D: Counter-mode decryption. d: Denomination. M: Vendor verifying the payment (bj, M). m: Customer verifying and obtaining the returned changes. 17
Advantage vs. weakness éAdvantage ©It can be implemented on mobile devices feasibly. ©The return change is useful for avoid some special pay word chain be exhausted. ©All three mode are well protect, and the overhead of these mode are not very heavy, so Customer can choose one is better for him or her. éWeakness ©Customer may need to maintain many kind of pay word chains. 18

Comment éIf the kind of face value of e-coin are many, that will be come a burden of Customer, Broker, and Vendor. éThis is very inconvenient to trade only once, because Customer and Vendor need to redeem them cash after transaction. éCustomer still using return changes after it expired that may incur collusion attack. éThe largest denomination may incur some attack, because it didn’t have any protect. 19
1197e427ad18ccd35ed057f76ff91ed9.ppt