16909877b5d966bd329178966a6f36b9.ppt
- Количество слайдов: 68
 MPLS What’s in it for Research & Education Networks? John Jamison University of Illinois at Chicago November 17, 2000 1
MPLS What’s in it for Research & Education Networks? John Jamison University of Illinois at Chicago November 17, 2000 1
 Juniper Networks Product Family Sept 2000 M 10 Sept 2000 M 5 Sept 1998 M 40 Nov 1999 M 20 Mar 2000 M 160 2
Juniper Networks Product Family Sept 2000 M 10 Sept 2000 M 5 Sept 1998 M 40 Nov 1999 M 20 Mar 2000 M 160 2
 Juniper Networks Research and Education Customers u MCI Worldcom – v. BNS/v. BNS+ Department of Energy – ESnet u DANTE - TEN-155 (Pan-European Research & Education Backbone) u University of Illinois – NCSA (National Center for Supercomputing Applications) u University of California, San Diego SDSC (San Diego Supercomputer Center) u NYSERNet – New York State Education & Research Network u University of Southern California, Information Sciences Institute u Georgia Tech – SOX Giga. Po. P u Indiana University u University of Washington – Pacific/Northwest Giga. Po. P u Stanford University u STAR TAP (International Research & u University of California, Davis Education Network Meet Point) u California Institute of Technology u APAN (Asia Pacific Advanced Network) u North Carolina State University Consortium u University of Alaska u NOAA (National Oceanographic and Atmospheric Administration) u University of Hiroshima, Japan u NASA – Goddard Space Flight Center u Korea Telcom Research Lab u ETRI (Electronic and Transmission u NIH (National Institutes of Health) Research Institute), Korea u Do. D (Department of Defense) u u US Army Engineer Research and Development Center 3
Juniper Networks Research and Education Customers u MCI Worldcom – v. BNS/v. BNS+ Department of Energy – ESnet u DANTE - TEN-155 (Pan-European Research & Education Backbone) u University of Illinois – NCSA (National Center for Supercomputing Applications) u University of California, San Diego SDSC (San Diego Supercomputer Center) u NYSERNet – New York State Education & Research Network u University of Southern California, Information Sciences Institute u Georgia Tech – SOX Giga. Po. P u Indiana University u University of Washington – Pacific/Northwest Giga. Po. P u Stanford University u STAR TAP (International Research & u University of California, Davis Education Network Meet Point) u California Institute of Technology u APAN (Asia Pacific Advanced Network) u North Carolina State University Consortium u University of Alaska u NOAA (National Oceanographic and Atmospheric Administration) u University of Hiroshima, Japan u NASA – Goddard Space Flight Center u Korea Telcom Research Lab u ETRI (Electronic and Transmission u NIH (National Institutes of Health) Research Institute), Korea u Do. D (Department of Defense) u u US Army Engineer Research and Development Center 3
 Original Agenda u MPLS Fundamentals u Traffic Engineering u Constraint-Based Routing u Refreshment Break u Virtual Private Networks u Optical Applications for MPLS Signaling (GMPLS/MPλS) u Juniper Networks Solutions u Questions and Comments 4
Original Agenda u MPLS Fundamentals u Traffic Engineering u Constraint-Based Routing u Refreshment Break u Virtual Private Networks u Optical Applications for MPLS Signaling (GMPLS/MPλS) u Juniper Networks Solutions u Questions and Comments 4
 Our Agenda u MPLS Overview u Traffic Engineering u VPNs 5
Our Agenda u MPLS Overview u Traffic Engineering u VPNs 5
 What are we missing out on? u A bunch of pure marketing slides u A bunch of filler slides u Slides with content that is of interest mainly to ISPs v Here is how you can use MPLS to bring in more revenue, offer different services, etc. u Some Details of MPLS Signaling Protocols and RFC 2547 VPNs v You can (and should) only cover so much in one talk u Some MP(Lambda)S Details v Seems too much like slide ware right now 6
What are we missing out on? u A bunch of pure marketing slides u A bunch of filler slides u Slides with content that is of interest mainly to ISPs v Here is how you can use MPLS to bring in more revenue, offer different services, etc. u Some Details of MPLS Signaling Protocols and RFC 2547 VPNs v You can (and should) only cover so much in one talk u Some MP(Lambda)S Details v Seems too much like slide ware right now 6
 What are we gaining? u Besides being spared marketing and ISP centric stuff: v We will see some examples from networks and applications we are familiar with v We will save some time and cover almost as much information 7
What are we gaining? u Besides being spared marketing and ISP centric stuff: v We will see some examples from networks and applications we are familiar with v We will save some time and cover almost as much information 7
 Why Is MPLS an Important Technology? u Fully integrates IP routing & L 2 switching u Leverages existing IP infrastructures u Optimizes IP networks by facilitating traffic engineering u Enables multi-service networking u Seamlessly integrates private and public networks u The natural choice for exploring new and richer IP service offerings u Dynamic optical bandwidth provisioning 8
Why Is MPLS an Important Technology? u Fully integrates IP routing & L 2 switching u Leverages existing IP infrastructures u Optimizes IP networks by facilitating traffic engineering u Enables multi-service networking u Seamlessly integrates private and public networks u The natural choice for exploring new and richer IP service offerings u Dynamic optical bandwidth provisioning 8
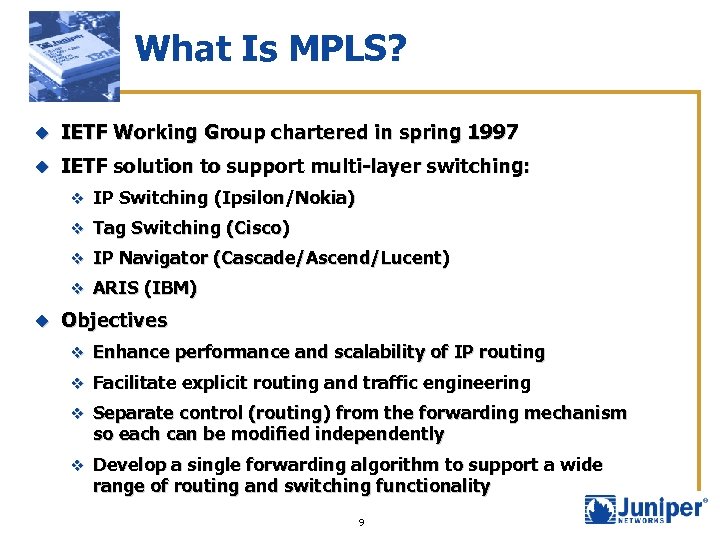 What Is MPLS? u IETF Working Group chartered in spring 1997 u IETF solution to support multi-layer switching: v IP Switching (Ipsilon/Nokia) v Tag Switching (Cisco) v IP Navigator (Cascade/Ascend/Lucent) v ARIS (IBM) u Objectives v Enhance performance and scalability of IP routing v Facilitate explicit routing and traffic engineering v Separate control (routing) from the forwarding mechanism so each can be modified independently v Develop a single forwarding algorithm to support a wide range of routing and switching functionality 9
What Is MPLS? u IETF Working Group chartered in spring 1997 u IETF solution to support multi-layer switching: v IP Switching (Ipsilon/Nokia) v Tag Switching (Cisco) v IP Navigator (Cascade/Ascend/Lucent) v ARIS (IBM) u Objectives v Enhance performance and scalability of IP routing v Facilitate explicit routing and traffic engineering v Separate control (routing) from the forwarding mechanism so each can be modified independently v Develop a single forwarding algorithm to support a wide range of routing and switching functionality 9
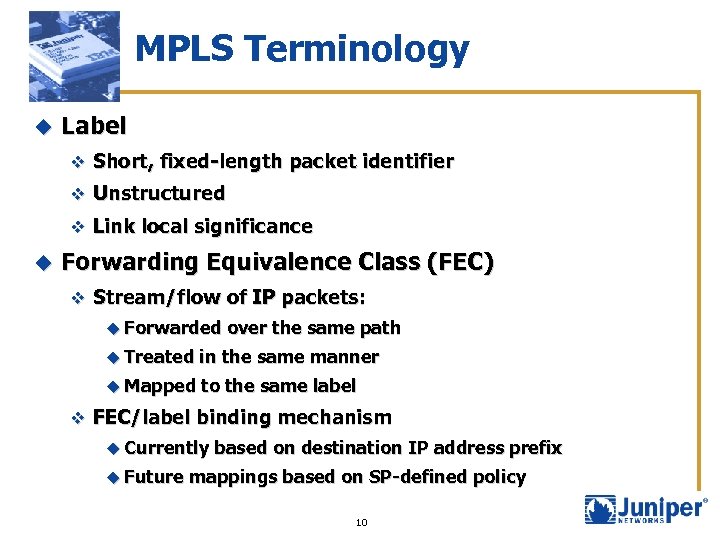 MPLS Terminology u Label v Short, fixed-length packet identifier v Unstructured v Link local significance u Forwarding Equivalence Class (FEC) v Stream/flow of IP packets: u Forwarded over the same path u Treated in the same manner u Mapped to the same label v FEC/label binding mechanism u Currently u Future based on destination IP address prefix mappings based on SP-defined policy 10
MPLS Terminology u Label v Short, fixed-length packet identifier v Unstructured v Link local significance u Forwarding Equivalence Class (FEC) v Stream/flow of IP packets: u Forwarded over the same path u Treated in the same manner u Mapped to the same label v FEC/label binding mechanism u Currently u Future based on destination IP address prefix mappings based on SP-defined policy 10
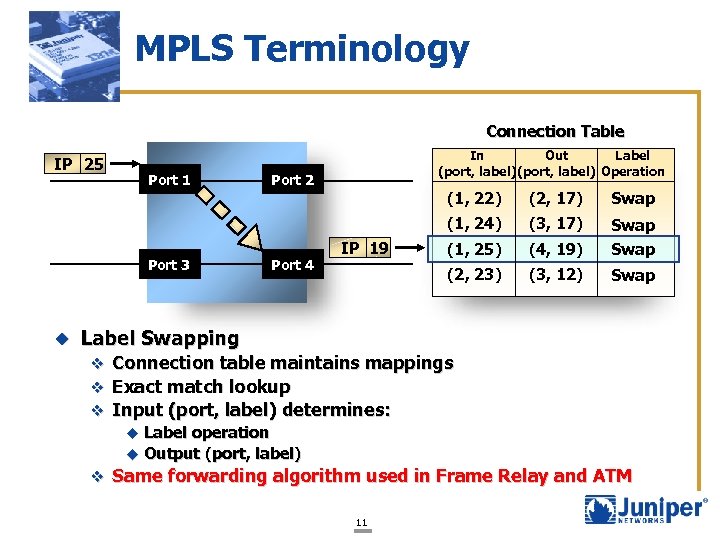 MPLS Terminology Connection Table IP 25 Port 1 In Out Label (port, label) Operation Port 2 u Port 4 Swap (3, 17) (1, 25) (4, 19) Swap (2, 23) IP 19 (2, 17) (1, 24) Port 3 (1, 22) (3, 12) Swap Label Swapping v Connection table maintains mappings v Exact match lookup v Input (port, label) determines: u Label operation u Output (port, label) v Same forwarding algorithm used in Frame Relay and ATM 11
MPLS Terminology Connection Table IP 25 Port 1 In Out Label (port, label) Operation Port 2 u Port 4 Swap (3, 17) (1, 25) (4, 19) Swap (2, 23) IP 19 (2, 17) (1, 24) Port 3 (1, 22) (3, 12) Swap Label Swapping v Connection table maintains mappings v Exact match lookup v Input (port, label) determines: u Label operation u Output (port, label) v Same forwarding algorithm used in Frame Relay and ATM 11
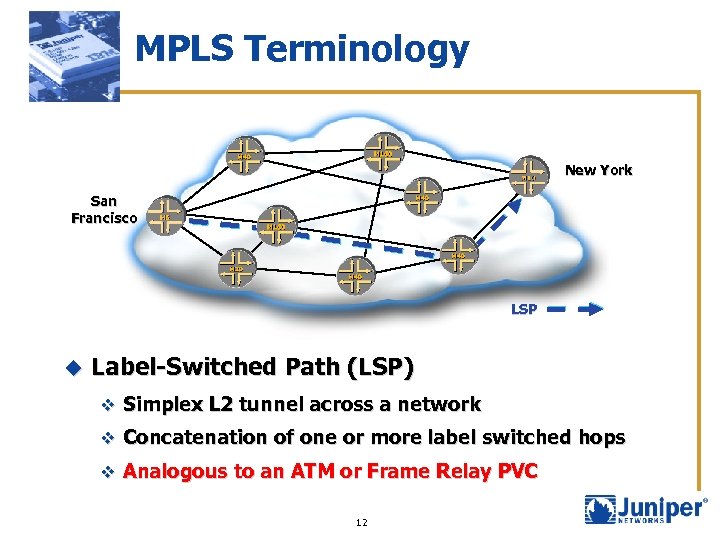 MPLS Terminology New York San Francisco LSP u Label-Switched Path (LSP) v Simplex L 2 tunnel across a network v Concatenation of one or more label switched hops v Analogous to an ATM or Frame Relay PVC 12
MPLS Terminology New York San Francisco LSP u Label-Switched Path (LSP) v Simplex L 2 tunnel across a network v Concatenation of one or more label switched hops v Analogous to an ATM or Frame Relay PVC 12
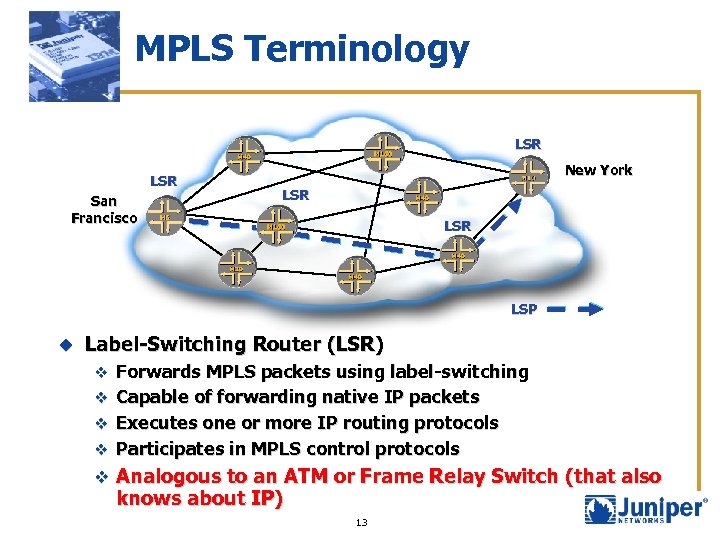 MPLS Terminology LSR San Francisco New York LSR LSP u Label-Switching Router (LSR) v Forwards MPLS packets using label-switching v Capable of forwarding native IP packets v Executes one or more IP routing protocols v Participates in MPLS control protocols v Analogous to an ATM or Frame Relay Switch (that also knows about IP) 13
MPLS Terminology LSR San Francisco New York LSR LSP u Label-Switching Router (LSR) v Forwards MPLS packets using label-switching v Capable of forwarding native IP packets v Executes one or more IP routing protocols v Participates in MPLS control protocols v Analogous to an ATM or Frame Relay Switch (that also knows about IP) 13
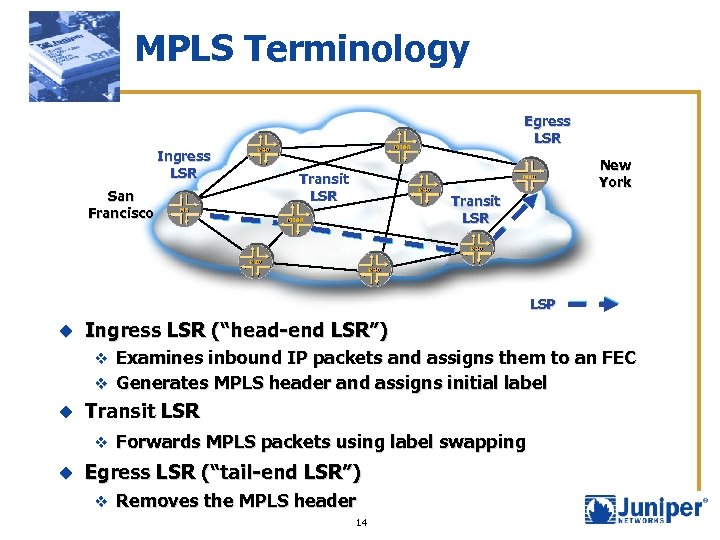 MPLS Terminology Egress LSR Ingress LSR San Francisco New York Transit LSR LSP u Ingress LSR (“head-end LSR”) v Examines inbound IP packets and assigns them to an FEC v Generates MPLS header and assigns initial label u Transit LSR v Forwards MPLS packets using label swapping u Egress LSR (“tail-end LSR”) v Removes the MPLS header 14
MPLS Terminology Egress LSR Ingress LSR San Francisco New York Transit LSR LSP u Ingress LSR (“head-end LSR”) v Examines inbound IP packets and assigns them to an FEC v Generates MPLS header and assigns initial label u Transit LSR v Forwards MPLS packets using label swapping u Egress LSR (“tail-end LSR”) v Removes the MPLS header 14
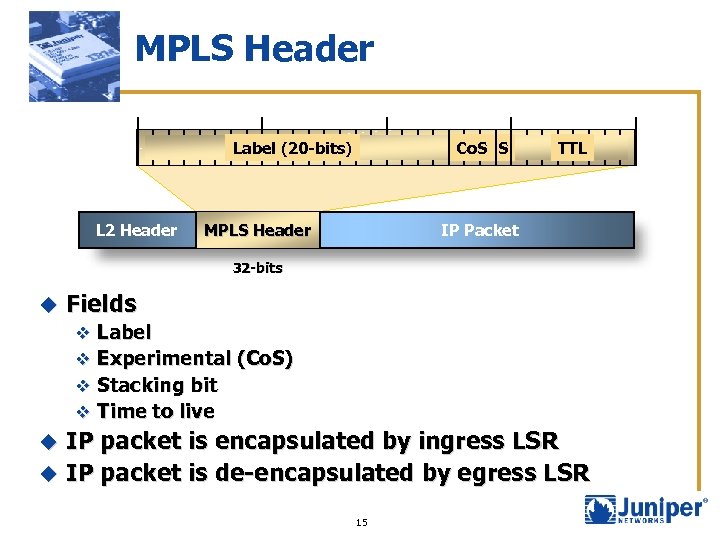 MPLS Header Label (20 -bits) L 2 Header Co. S S TTL IP Packet MPLS Header 32 -bits u Fields v Label v Experimental (Co. S) v Stacking bit v Time to live IP packet is encapsulated by ingress LSR u IP packet is de-encapsulated by egress LSR u 15
MPLS Header Label (20 -bits) L 2 Header Co. S S TTL IP Packet MPLS Header 32 -bits u Fields v Label v Experimental (Co. S) v Stacking bit v Time to live IP packet is encapsulated by ingress LSR u IP packet is de-encapsulated by egress LSR u 15
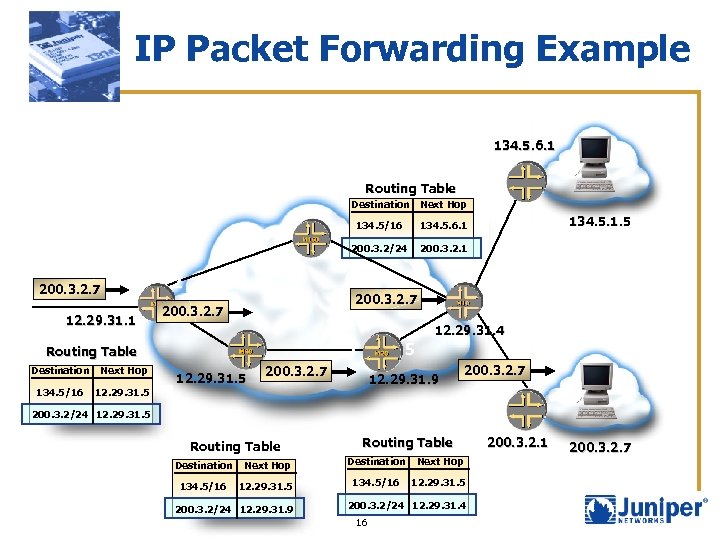 IP Packet Forwarding Example 134. 5. 6. 1 Routing Table Destination 134. 5/16 12. 29. 31. 1 2 Next Hop 134. 5/16 12. 29. 31. 5 200. 3. 2. 1 134. 5. 1. 5 200. 3. 2. 7 12. 29. 31. 4 3 Routing Table Destination 134. 5. 6. 1 200. 3. 2/24 200. 3. 2. 7 Next Hop 12. 29. 31. 5 5 200. 3. 2. 7 12. 29. 31. 9 200. 3. 2. 7 200. 3. 2/24 12. 29. 31. 5 Routing Table Destination Next Hop Destination 134. 5/16 12. 29. 31. 5 134. 5/16 200. 3. 2/24 12. 29. 31. 9 Next Hop 12. 29. 31. 5 200. 3. 2/24 12. 29. 31. 4 16 200. 3. 2. 1 200. 3. 2. 7
IP Packet Forwarding Example 134. 5. 6. 1 Routing Table Destination 134. 5/16 12. 29. 31. 1 2 Next Hop 134. 5/16 12. 29. 31. 5 200. 3. 2. 1 134. 5. 1. 5 200. 3. 2. 7 12. 29. 31. 4 3 Routing Table Destination 134. 5. 6. 1 200. 3. 2/24 200. 3. 2. 7 Next Hop 12. 29. 31. 5 5 200. 3. 2. 7 12. 29. 31. 9 200. 3. 2. 7 200. 3. 2/24 12. 29. 31. 5 Routing Table Destination Next Hop Destination 134. 5/16 12. 29. 31. 5 134. 5/16 200. 3. 2/24 12. 29. 31. 9 Next Hop 12. 29. 31. 5 200. 3. 2/24 12. 29. 31. 4 16 200. 3. 2. 1 200. 3. 2. 7
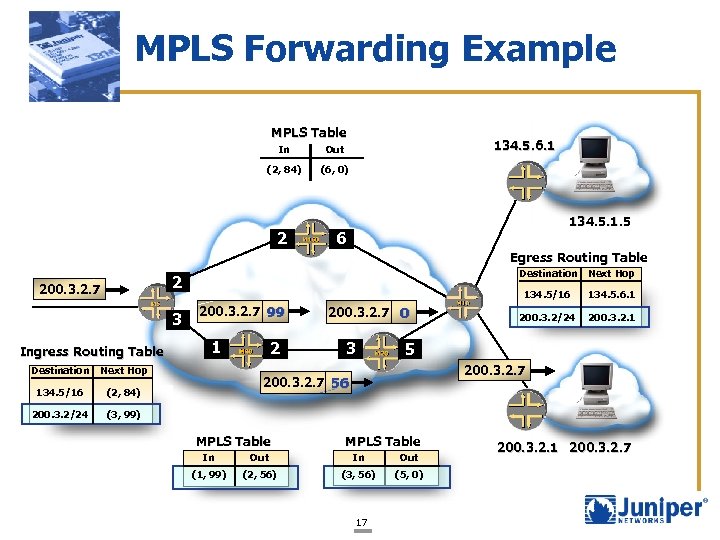 MPLS Forwarding Example MPLS Table In (2, 84) 134. 5. 6. 1 Out (6, 0) 2 134. 5. 1. 5 6 Egress Routing Table Destination 200. 3. 2. 7 3 Ingress Routing Table Destination (2, 84) 200. 3. 2/24 1 Next Hop 134. 5/16 200. 3. 2. 7 99 2 200. 3. 2. 7 0 3 Next Hop 134. 5/16 2 134. 5. 6. 1 200. 3. 2/24 200. 3. 2. 1 5 200. 3. 2. 7 (3, 99) 200. 3. 2. 7 56 MPLS Table In Out (1, 99) (2, 56) (3, 56) (5, 0) 17 200. 3. 2. 1 200. 3. 2. 7
MPLS Forwarding Example MPLS Table In (2, 84) 134. 5. 6. 1 Out (6, 0) 2 134. 5. 1. 5 6 Egress Routing Table Destination 200. 3. 2. 7 3 Ingress Routing Table Destination (2, 84) 200. 3. 2/24 1 Next Hop 134. 5/16 200. 3. 2. 7 99 2 200. 3. 2. 7 0 3 Next Hop 134. 5/16 2 134. 5. 6. 1 200. 3. 2/24 200. 3. 2. 1 5 200. 3. 2. 7 (3, 99) 200. 3. 2. 7 56 MPLS Table In Out (1, 99) (2, 56) (3, 56) (5, 0) 17 200. 3. 2. 1 200. 3. 2. 7
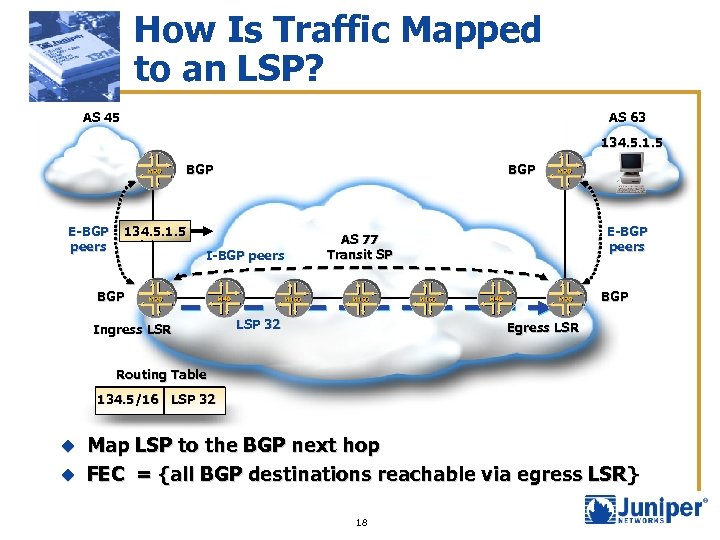 How Is Traffic Mapped to an LSP? AS 45 AS 63 134. 5. 1. 5 BGP E-BGP peers BGP 134. 5. 1. 5 I-BGP peers E-BGP peers AS 77 Transit SP BGP Ingress LSR BGP LSP 32 Egress LSR Routing Table 134. 5/16 LSP 32 Map LSP to the BGP next hop u FEC = {all BGP destinations reachable via egress LSR} u 18
How Is Traffic Mapped to an LSP? AS 45 AS 63 134. 5. 1. 5 BGP E-BGP peers BGP 134. 5. 1. 5 I-BGP peers E-BGP peers AS 77 Transit SP BGP Ingress LSR BGP LSP 32 Egress LSR Routing Table 134. 5/16 LSP 32 Map LSP to the BGP next hop u FEC = {all BGP destinations reachable via egress LSR} u 18
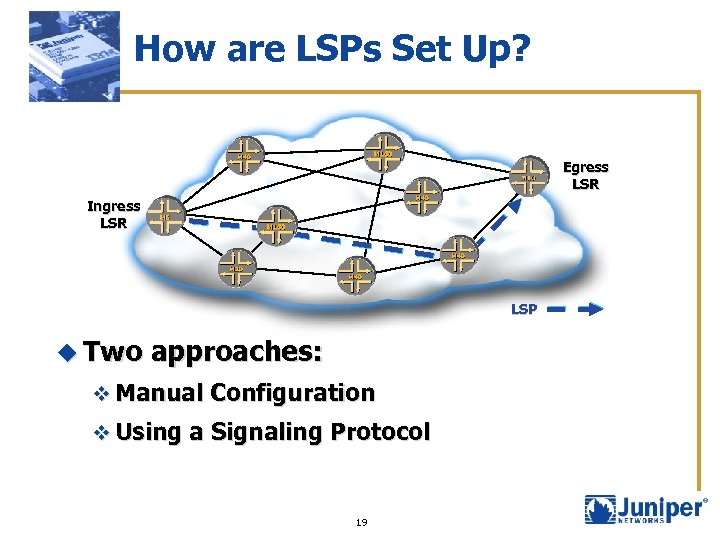 How are LSPs Set Up? Egress LSR Ingress LSR LSP u Two approaches: v Manual Configuration v Using a Signaling Protocol 19
How are LSPs Set Up? Egress LSR Ingress LSR LSP u Two approaches: v Manual Configuration v Using a Signaling Protocol 19
 MPLS Signaling Protocols u The IETF MPLS architecture does not assume a single label distribution protocol u LDP v Executes hop-by-hop v Selects same physical path as IGP v Does not support traffic engineering u RSVP v Easily extensible for explicit routes and label distribution v Deployed by providers in production networks u CR-LDP v Extends LDP to support explicit routes v Functionally identical to RSVP v Not deployed 20
MPLS Signaling Protocols u The IETF MPLS architecture does not assume a single label distribution protocol u LDP v Executes hop-by-hop v Selects same physical path as IGP v Does not support traffic engineering u RSVP v Easily extensible for explicit routes and label distribution v Deployed by providers in production networks u CR-LDP v Extends LDP to support explicit routes v Functionally identical to RSVP v Not deployed 20
 How Is the LSP Physical Path Determined? Egress LSR Ingress LSR LSP u Two approaches: v Offline path calculation (in house or 3 rd party tools) v Online path calculation (constraint-based routing) u A hybrid approach may be used 21
How Is the LSP Physical Path Determined? Egress LSR Ingress LSR LSP u Two approaches: v Offline path calculation (in house or 3 rd party tools) v Online path calculation (constraint-based routing) u A hybrid approach may be used 21
 Offline Path Calculation u Simultaneously considers v All link resource constraints v All ingress to egress traffic trunks u Benefits v Similar to mechanisms used v v u in overlay networks Global resource optimization Predictable LSP placement Stability Decision support system In-house and third-party tools 22
Offline Path Calculation u Simultaneously considers v All link resource constraints v All ingress to egress traffic trunks u Benefits v Similar to mechanisms used v v u in overlay networks Global resource optimization Predictable LSP placement Stability Decision support system In-house and third-party tools 22
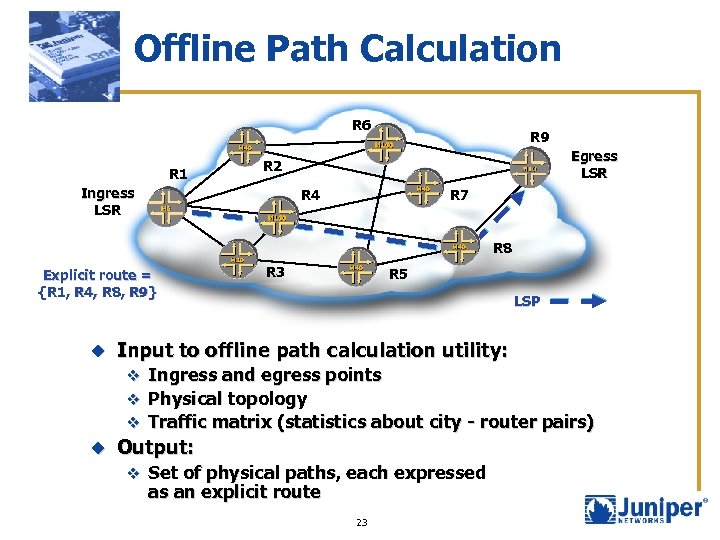 Offline Path Calculation R 6 R 1 R 9 Egress LSR R 2 Ingress LSR R 7 R 4 R 8 Explicit route = {R 1, R 4, R 8, R 9} u R 3 R 5 LSP Input to offline path calculation utility: v Ingress and egress points v Physical topology v Traffic matrix (statistics about city - router pairs) u Output: v Set of physical paths, each expressed as an explicit route 23
Offline Path Calculation R 6 R 1 R 9 Egress LSR R 2 Ingress LSR R 7 R 4 R 8 Explicit route = {R 1, R 4, R 8, R 9} u R 3 R 5 LSP Input to offline path calculation utility: v Ingress and egress points v Physical topology v Traffic matrix (statistics about city - router pairs) u Output: v Set of physical paths, each expressed as an explicit route 23
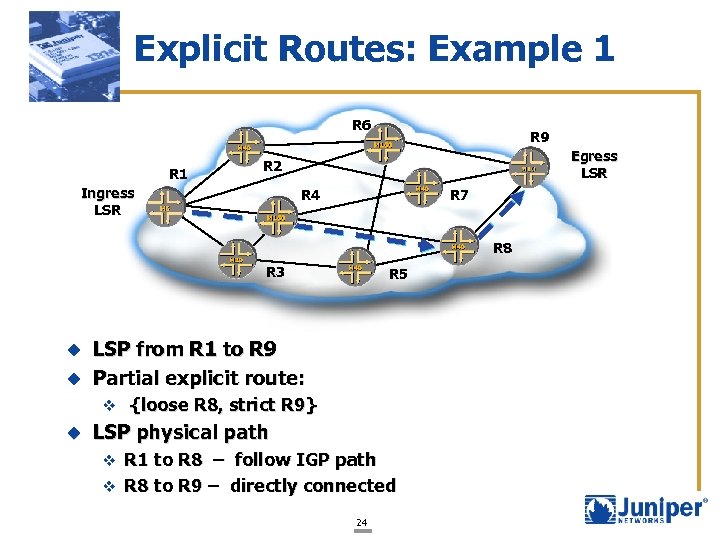 Explicit Routes: Example 1 R 6 R 1 R 9 Egress LSR R 2 Ingress LSR R 7 R 4 R 8 R 3 R 5 LSP from R 1 to R 9 u Partial explicit route: u v {loose R 8, strict R 9} u LSP physical path v R 1 to R 8 – follow IGP path v R 8 to R 9 – directly connected 24
Explicit Routes: Example 1 R 6 R 1 R 9 Egress LSR R 2 Ingress LSR R 7 R 4 R 8 R 3 R 5 LSP from R 1 to R 9 u Partial explicit route: u v {loose R 8, strict R 9} u LSP physical path v R 1 to R 8 – follow IGP path v R 8 to R 9 – directly connected 24
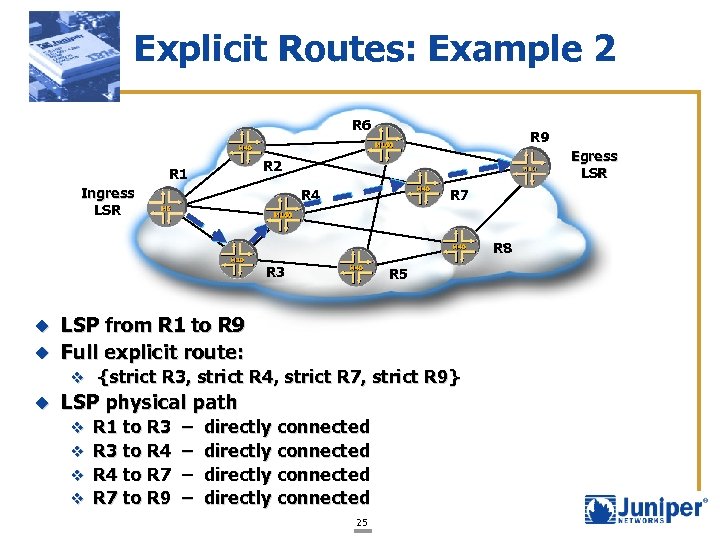 Explicit Routes: Example 2 R 6 R 1 R 9 Egress LSR R 2 Ingress LSR R 7 R 4 R 8 R 3 R 5 LSP from R 1 to R 9 u Full explicit route: u v {strict R 3, strict R 4, strict R 7, strict R 9} u LSP physical path v R 1 to R 3 – directly connected v R 3 to R 4 – directly connected v R 4 to R 7 – directly connected v R 7 to R 9 – directly connected 25
Explicit Routes: Example 2 R 6 R 1 R 9 Egress LSR R 2 Ingress LSR R 7 R 4 R 8 R 3 R 5 LSP from R 1 to R 9 u Full explicit route: u v {strict R 3, strict R 4, strict R 7, strict R 9} u LSP physical path v R 1 to R 3 – directly connected v R 3 to R 4 – directly connected v R 4 to R 7 – directly connected v R 7 to R 9 – directly connected 25
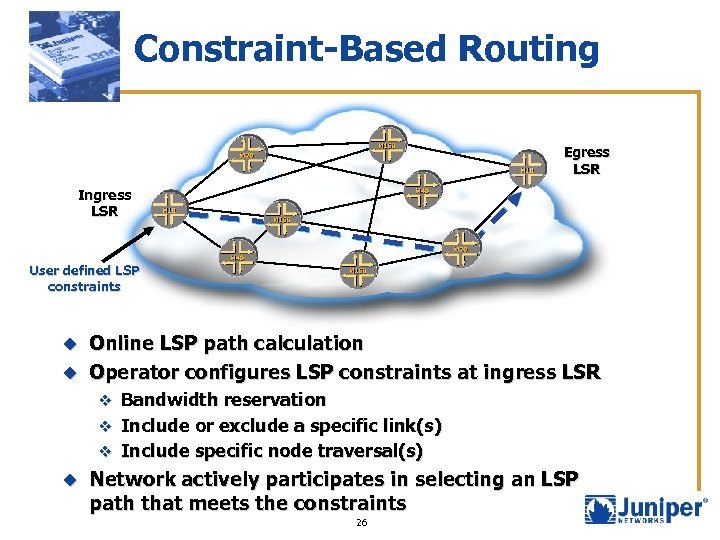 Constraint-Based Routing Egress LSR Ingress LSR User defined LSP constraints Online LSP path calculation u Operator configures LSP constraints at ingress LSR u v Bandwidth reservation v Include or exclude a specific link(s) v Include specific node traversal(s) u Network actively participates in selecting an LSP path that meets the constraints 26
Constraint-Based Routing Egress LSR Ingress LSR User defined LSP constraints Online LSP path calculation u Operator configures LSP constraints at ingress LSR u v Bandwidth reservation v Include or exclude a specific link(s) v Include specific node traversal(s) u Network actively participates in selecting an LSP path that meets the constraints 26
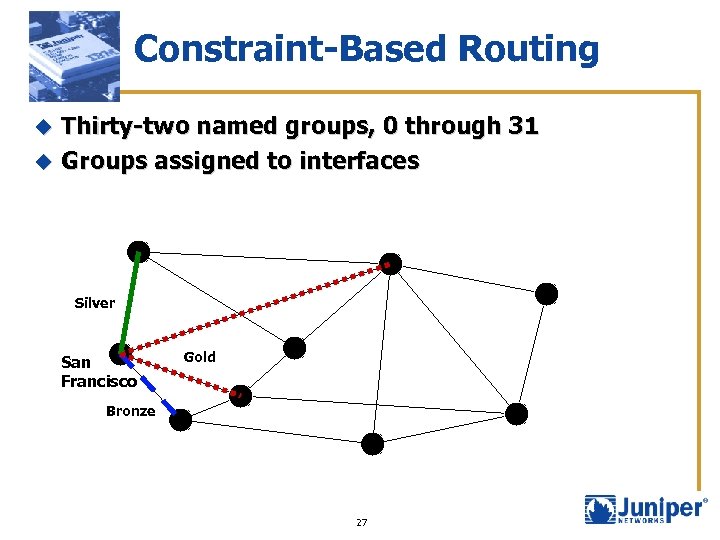 Constraint-Based Routing Thirty-two named groups, 0 through 31 u Groups assigned to interfaces u Silver San Francisco Gold Bronze 27
Constraint-Based Routing Thirty-two named groups, 0 through 31 u Groups assigned to interfaces u Silver San Francisco Gold Bronze 27
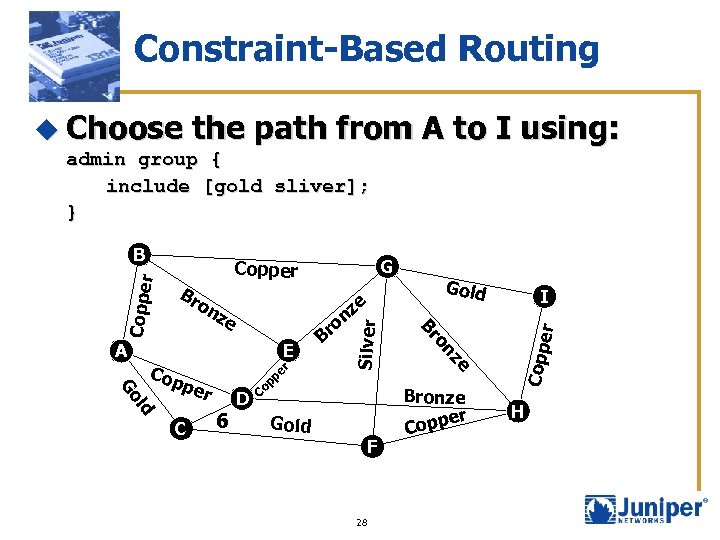 Constraint-Based Routing u Choose the path from A to I using: admin group { include [gold sliver]; } ze pp e r C Co per ld Go Cop 6 D Gold F 28 ze E ro B I er e nz Gold Bronze er Copp on Silver Br on A G Copper Br Coppe r B H
Constraint-Based Routing u Choose the path from A to I using: admin group { include [gold sliver]; } ze pp e r C Co per ld Go Cop 6 D Gold F 28 ze E ro B I er e nz Gold Bronze er Copp on Silver Br on A G Copper Br Coppe r B H
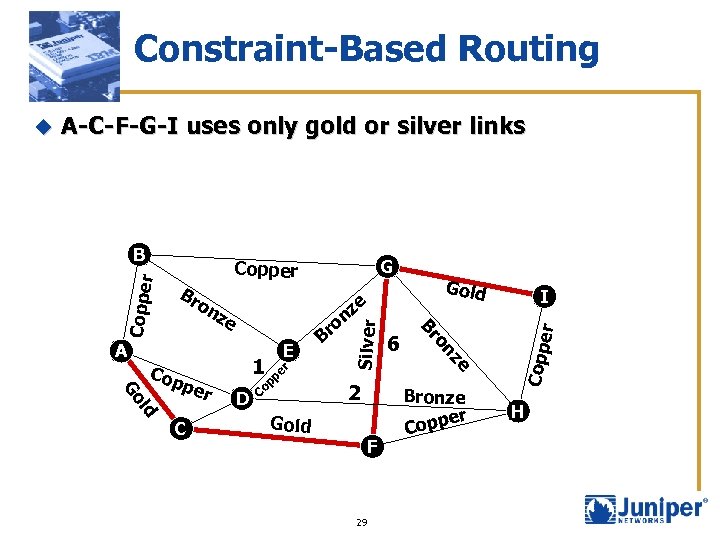 Constraint-Based Routing A-C-F-G-I uses only gold or silver links C r pp e 1 D 2 Gold F 29 6 I er E ro B ze per ze on ld Go Cop e nz Gold Bronze er Copp on Silver Br Br A G Copper Co r B Coppe u H
Constraint-Based Routing A-C-F-G-I uses only gold or silver links C r pp e 1 D 2 Gold F 29 6 I er E ro B ze per ze on ld Go Cop e nz Gold Bronze er Copp on Silver Br Br A G Copper Co r B Coppe u H
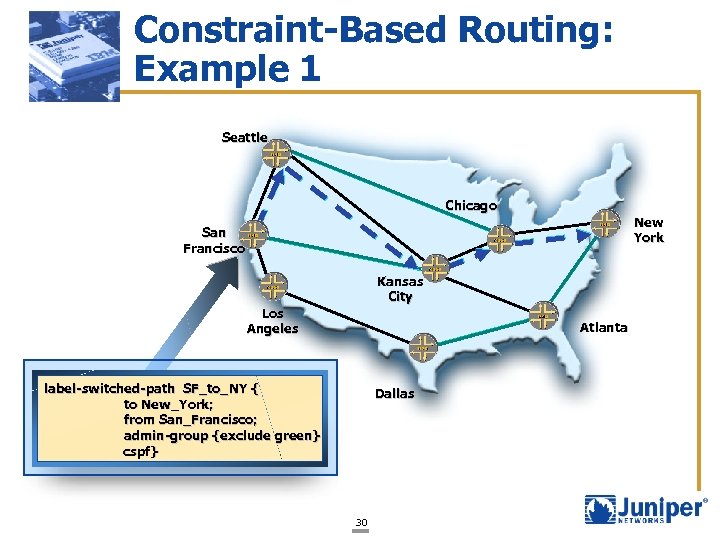 Constraint-Based Routing: Example 1 Seattle Chicago New York San Francisco Kansas City Los Angeles Atlanta label-switched-path SF_to_NY { to New_York; from San_Francisco; admin-group {exclude green} cspf} Dallas 30
Constraint-Based Routing: Example 1 Seattle Chicago New York San Francisco Kansas City Los Angeles Atlanta label-switched-path SF_to_NY { to New_York; from San_Francisco; admin-group {exclude green} cspf} Dallas 30
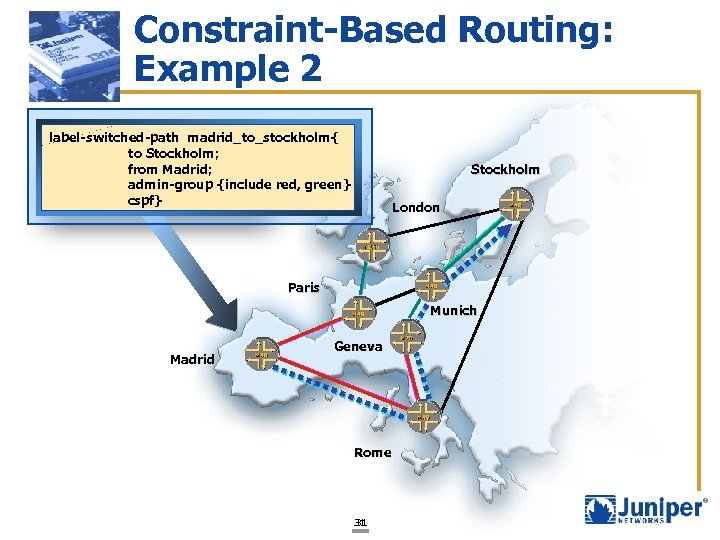 Constraint-Based Routing: Example 2 label-switched-path madrid_to_stockholm{ to Stockholm; from Madrid; admin-group {include red, green} cspf} Stockholm London Paris Munich Madrid Geneva Rome 31 31
Constraint-Based Routing: Example 2 label-switched-path madrid_to_stockholm{ to Stockholm; from Madrid; admin-group {include red, green} cspf} Stockholm London Paris Munich Madrid Geneva Rome 31 31
 Other Neat MPLS Stuff u Secondary u Fast LSPs Reroute u Label Stacking u GMPLS 32
Other Neat MPLS Stuff u Secondary u Fast LSPs Reroute u Label Stacking u GMPLS 32
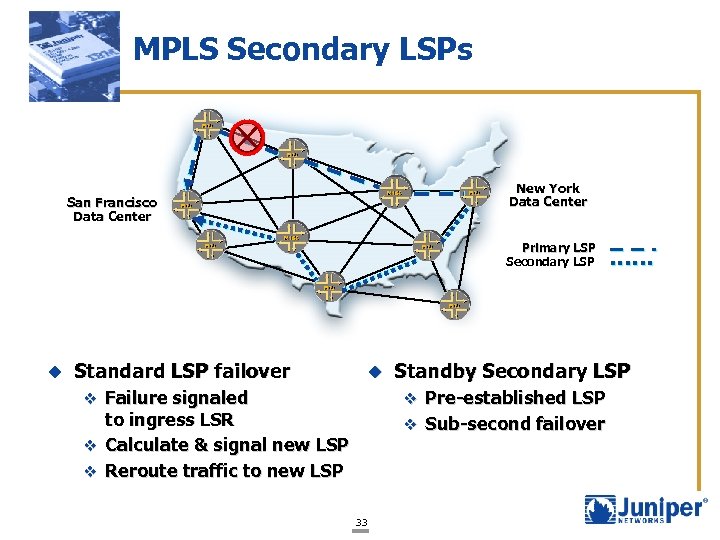 MPLS Secondary LSPs New York Data Center San Francisco Data Center Primary LSP Secondary LSP u Standard LSP failover u v Failure signaled Standby Secondary LSP v Pre-established LSP to ingress LSR v Calculate & signal new LSP v Reroute traffic to new LSP v Sub-second failover 33
MPLS Secondary LSPs New York Data Center San Francisco Data Center Primary LSP Secondary LSP u Standard LSP failover u v Failure signaled Standby Secondary LSP v Pre-established LSP to ingress LSR v Calculate & signal new LSP v Reroute traffic to new LSP v Sub-second failover 33
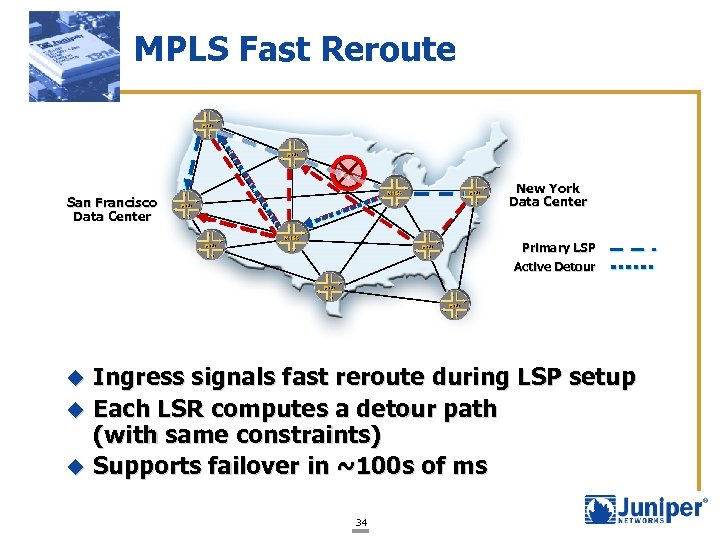 MPLS Fast Reroute New York Data Center San Francisco Data Center Primary LSP Active Detour Ingress signals fast reroute during LSP setup u Each LSR computes a detour path (with same constraints) u Supports failover in ~100 s of ms u 34
MPLS Fast Reroute New York Data Center San Francisco Data Center Primary LSP Active Detour Ingress signals fast reroute during LSP setup u Each LSR computes a detour path (with same constraints) u Supports failover in ~100 s of ms u 34
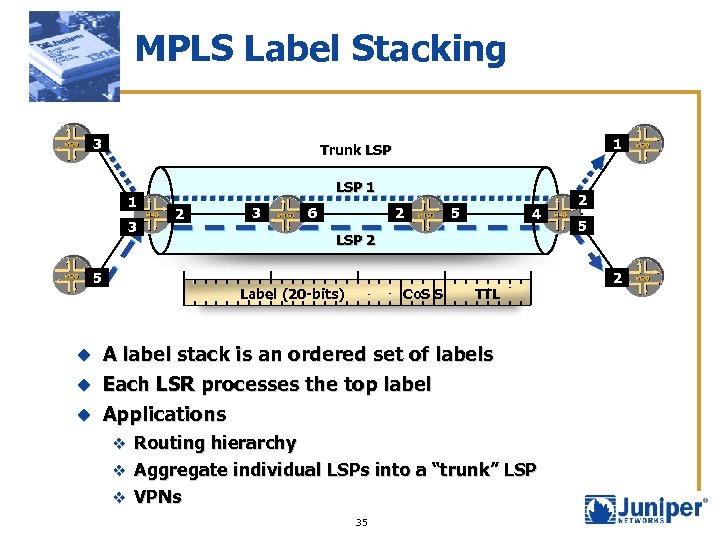 MPLS Label Stacking 3 1 Trunk LSP 1 3 LSP 1 2 5 3 6 2 5 4 LSP 2 Label (20 -bits) Co. S S TTL A label stack is an ordered set of labels u Each LSR processes the top label u u Applications v Routing hierarchy v Aggregate individual LSPs into a “trunk” LSP v VPNs 35 2
MPLS Label Stacking 3 1 Trunk LSP 1 3 LSP 1 2 5 3 6 2 5 4 LSP 2 Label (20 -bits) Co. S S TTL A label stack is an ordered set of labels u Each LSR processes the top label u u Applications v Routing hierarchy v Aggregate individual LSPs into a “trunk” LSP v VPNs 35 2
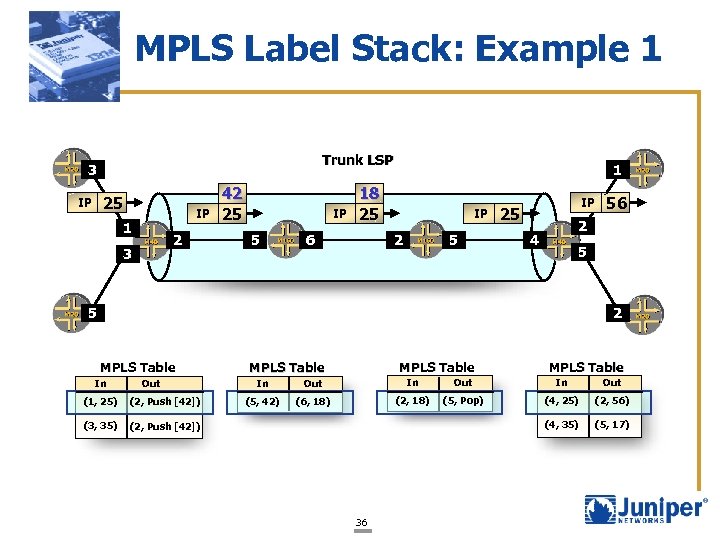 MPLS Label Stack: Example 1 Trunk LSP 3 25 IP IP 1 2 3 42 25 IP 5 1 18 25 6 IP 2 5 IP 25 56 2 4 5 2 5 MPLS Table In Out (1, 25) (2, Push [42]) (3, 35) MPLS Table In Out (5, 42) (6, 18) (2, 18) (5, Pop) (4, 25) (2, 56) (4, 35) (5, 17) (2, Push [42]) 36
MPLS Label Stack: Example 1 Trunk LSP 3 25 IP IP 1 2 3 42 25 IP 5 1 18 25 6 IP 2 5 IP 25 56 2 4 5 2 5 MPLS Table In Out (1, 25) (2, Push [42]) (3, 35) MPLS Table In Out (5, 42) (6, 18) (2, 18) (5, Pop) (4, 25) (2, 56) (4, 35) (5, 17) (2, Push [42]) 36
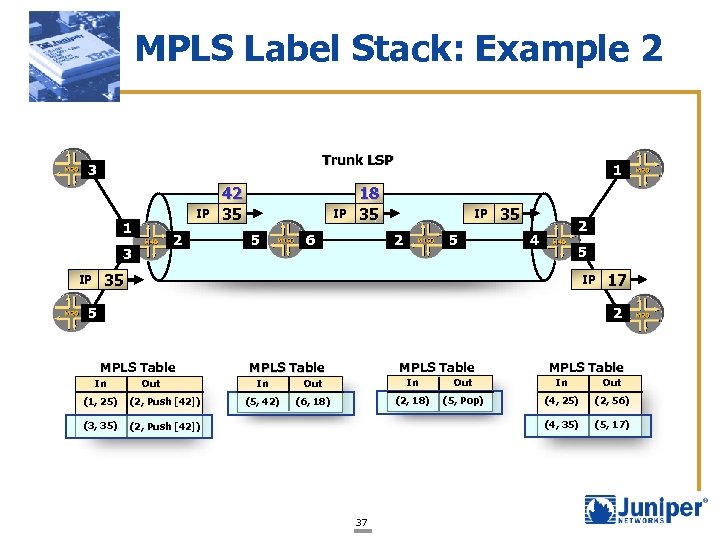 MPLS Label Stack: Example 2 Trunk LSP 3 IP 1 2 3 42 35 IP 5 1 18 35 6 IP 2 5 35 2 4 5 35 IP IP 17 2 5 MPLS Table In Out (1, 25) (2, Push [42]) (3, 35) MPLS Table In Out (5, 42) (6, 18) (2, 18) (5, Pop) (4, 25) (2, 56) (4, 35) (5, 17) (2, Push [42]) 37
MPLS Label Stack: Example 2 Trunk LSP 3 IP 1 2 3 42 35 IP 5 1 18 35 6 IP 2 5 35 2 4 5 35 IP IP 17 2 5 MPLS Table In Out (1, 25) (2, Push [42]) (3, 35) MPLS Table In Out (5, 42) (6, 18) (2, 18) (5, Pop) (4, 25) (2, 56) (4, 35) (5, 17) (2, Push [42]) 37
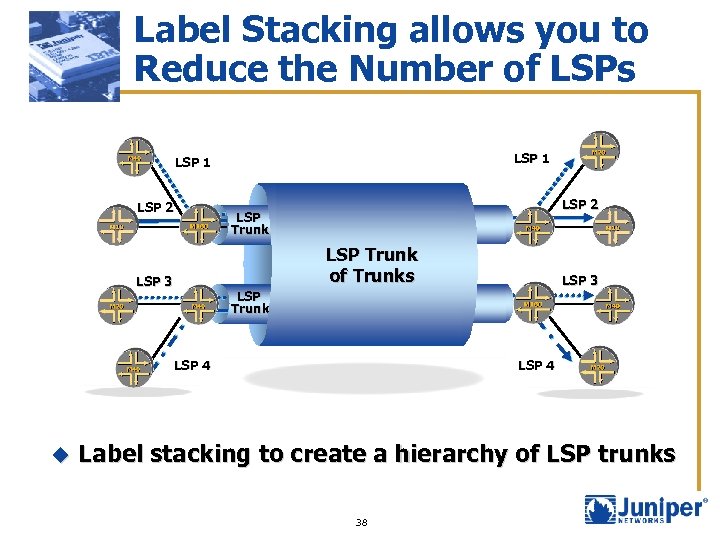 Label Stacking allows you to Reduce the Number of LSPs LSP 1 LSP 2 LSP Trunk of Trunks LSP 3 LSP Trunk LSP 4 u LSP 3 Label stacking to create a hierarchy of LSP trunks 38
Label Stacking allows you to Reduce the Number of LSPs LSP 1 LSP 2 LSP Trunk of Trunks LSP 3 LSP Trunk LSP 4 u LSP 3 Label stacking to create a hierarchy of LSP trunks 38
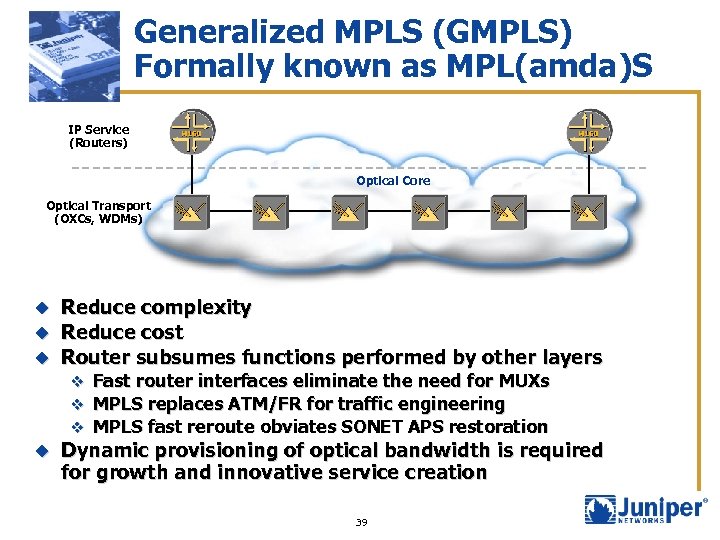 Generalized MPLS (GMPLS) Formally known as MPL(amda)S IP Service (Routers) Optical Core Optical Transport (OXCs, WDMs) Reduce complexity Reduce cost u Router subsumes functions performed by other layers u u v Fast router interfaces eliminate the need for MUXs v MPLS replaces ATM/FR for traffic engineering v MPLS fast reroute obviates SONET APS restoration u Dynamic provisioning of optical bandwidth is required for growth and innovative service creation 39
Generalized MPLS (GMPLS) Formally known as MPL(amda)S IP Service (Routers) Optical Core Optical Transport (OXCs, WDMs) Reduce complexity Reduce cost u Router subsumes functions performed by other layers u u v Fast router interfaces eliminate the need for MUXs v MPLS replaces ATM/FR for traffic engineering v MPLS fast reroute obviates SONET APS restoration u Dynamic provisioning of optical bandwidth is required for growth and innovative service creation 39
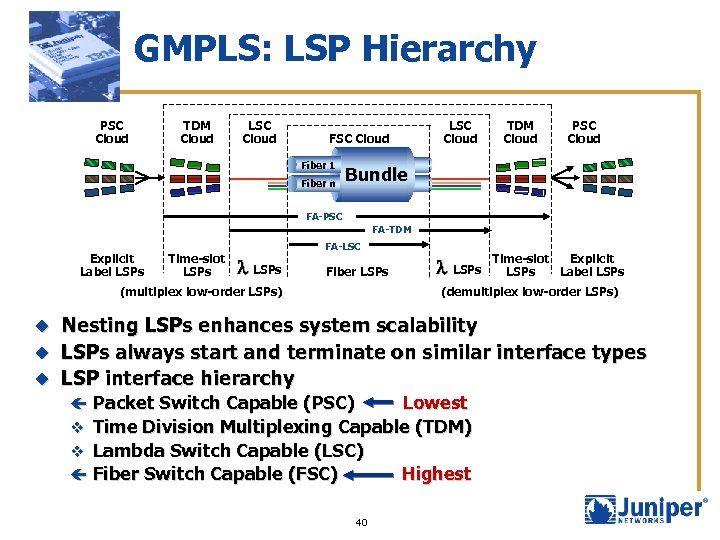 GMPLS: LSP Hierarchy PSC Cloud TDM Cloud LSC Cloud FSC Cloud Fiber 1 Fiber n TDM Cloud PSC Cloud Bundle FA-PSC FA-TDM Explicit Label LSPs Time-slot LSPs FA-LSC l LSPs Fiber LSPs (multiplex low-order LSPs) l LSPs Time-slot Explicit LSPs Label LSPs (demultiplex low-order LSPs) Nesting LSPs enhances system scalability u LSPs always start and terminate on similar interface types u LSP interface hierarchy u ç Packet Switch Capable (PSC) Lowest v Time Division Multiplexing Capable (TDM) v Lambda Switch Capable (LSC) ç Fiber Switch Capable (FSC) 40 Highest
GMPLS: LSP Hierarchy PSC Cloud TDM Cloud LSC Cloud FSC Cloud Fiber 1 Fiber n TDM Cloud PSC Cloud Bundle FA-PSC FA-TDM Explicit Label LSPs Time-slot LSPs FA-LSC l LSPs Fiber LSPs (multiplex low-order LSPs) l LSPs Time-slot Explicit LSPs Label LSPs (demultiplex low-order LSPs) Nesting LSPs enhances system scalability u LSPs always start and terminate on similar interface types u LSP interface hierarchy u ç Packet Switch Capable (PSC) Lowest v Time Division Multiplexing Capable (TDM) v Lambda Switch Capable (LSC) ç Fiber Switch Capable (FSC) 40 Highest
 AGENDA u MPLS Overview u Traffic Engineering u VPNs 41
AGENDA u MPLS Overview u Traffic Engineering u VPNs 41
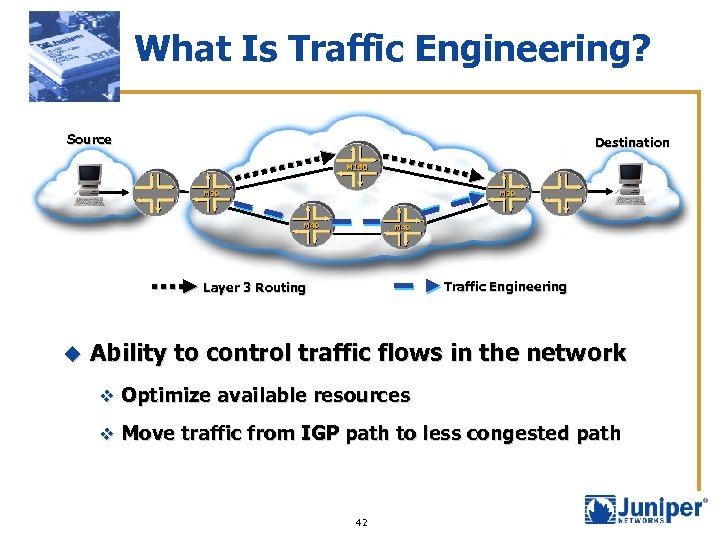 What Is Traffic Engineering? Source Destination Traffic Engineering Layer 3 Routing u Ability to control traffic flows in the network v Optimize available resources v Move traffic from IGP path to less congested path 42
What Is Traffic Engineering? Source Destination Traffic Engineering Layer 3 Routing u Ability to control traffic flows in the network v Optimize available resources v Move traffic from IGP path to less congested path 42
 Brief History u Early 1990’s v Internet core was connected with T 1 and T 3 links between routers v Only a handful of routers and links to manage and configure v Humans could do the work manually v Metric-based traffic control was sufficient 43
Brief History u Early 1990’s v Internet core was connected with T 1 and T 3 links between routers v Only a handful of routers and links to manage and configure v Humans could do the work manually v Metric-based traffic control was sufficient 43
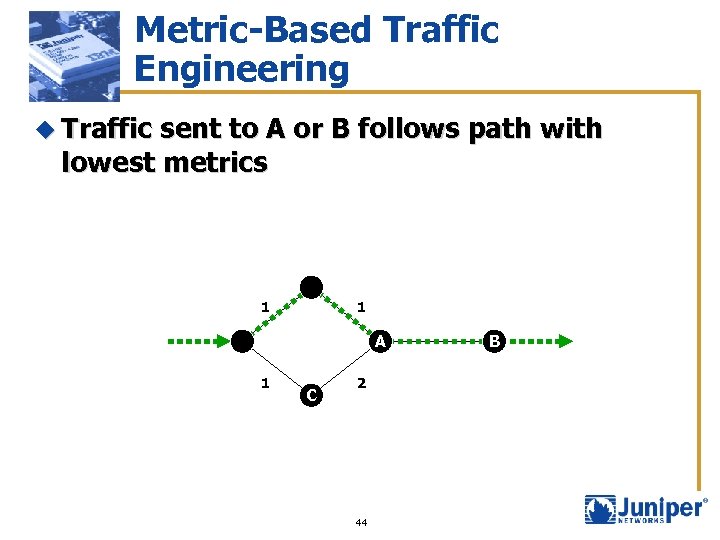 Metric-Based Traffic Engineering u Traffic sent to A or B follows path with lowest metrics 1 1 A 1 C 2 44 B
Metric-Based Traffic Engineering u Traffic sent to A or B follows path with lowest metrics 1 1 A 1 C 2 44 B
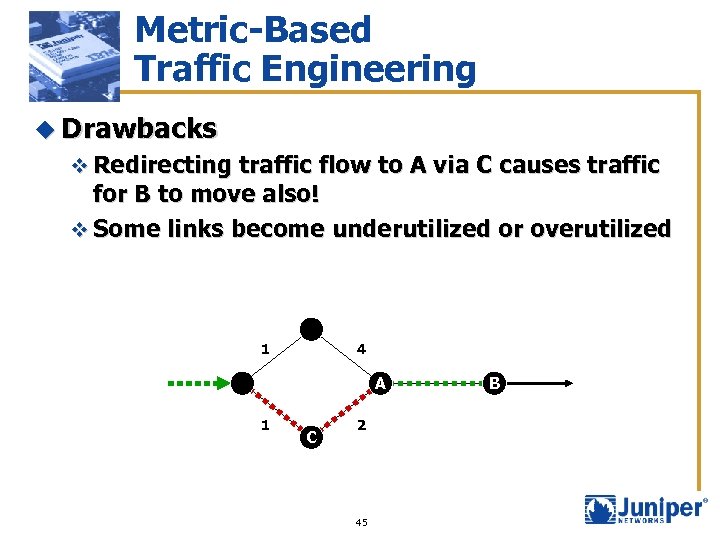 Metric-Based Traffic Engineering u Drawbacks v Redirecting traffic flow to A via C causes traffic for B to move also! v Some links become underutilized or overutilized 1 4 A 1 C 2 45 B
Metric-Based Traffic Engineering u Drawbacks v Redirecting traffic flow to A via C causes traffic for B to move also! v Some links become underutilized or overutilized 1 4 A 1 C 2 45 B
 Metric-Based Traffic Engineering u Drawbacks v Complexity made metric control tricky v Adjusting one metric might destabilize network 46
Metric-Based Traffic Engineering u Drawbacks v Complexity made metric control tricky v Adjusting one metric might destabilize network 46
 Discomfort Grows u Mid 1990’s v ISPs became uncomfortable with size of Internet core v Large growth spurt imminent v Routers too slow v Metric “engineering” too complex v IGP routing calculation was topology driven, not traffic driven v Router based cores lacked predictability 47
Discomfort Grows u Mid 1990’s v ISPs became uncomfortable with size of Internet core v Large growth spurt imminent v Routers too slow v Metric “engineering” too complex v IGP routing calculation was topology driven, not traffic driven v Router based cores lacked predictability 47
 Overlay Networks are Born ATM switches offered performance and predictable behavior u ISPs created “overlay” networks that presented a virtual topology to the edge routers in their network u Using ATM virtual circuits, the virtual network could be reengineered without changing the physical network u Benefits u v Full traffic control v Per-circuit statistics v More balanced flow of traffic across links 48
Overlay Networks are Born ATM switches offered performance and predictable behavior u ISPs created “overlay” networks that presented a virtual topology to the edge routers in their network u Using ATM virtual circuits, the virtual network could be reengineered without changing the physical network u Benefits u v Full traffic control v Per-circuit statistics v More balanced flow of traffic across links 48
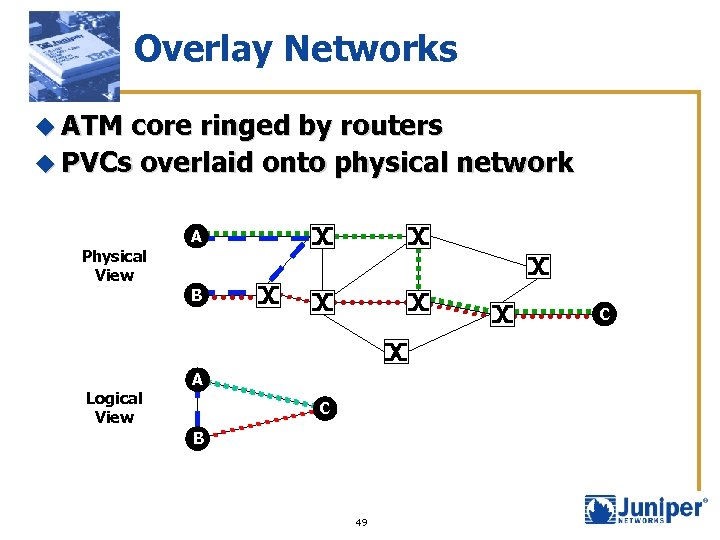 Overlay Networks u ATM core ringed by routers u PVCs overlaid onto physical network A Physical View B Logical View C A C B 49
Overlay Networks u ATM core ringed by routers u PVCs overlaid onto physical network A Physical View B Logical View C A C B 49
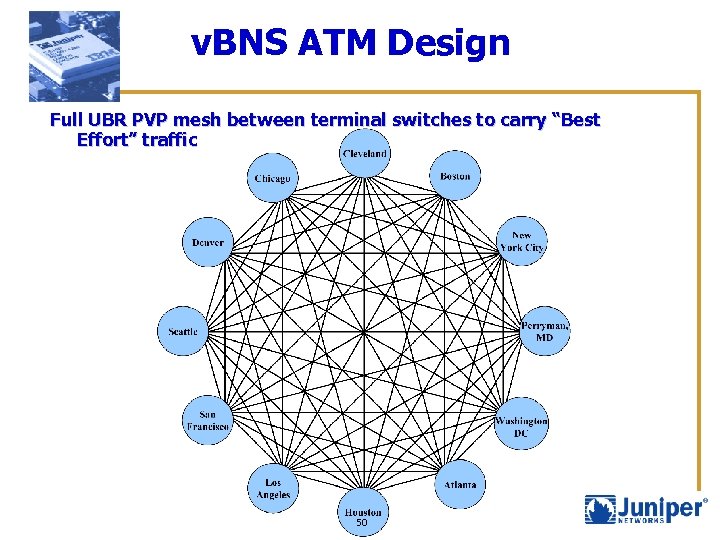 v. BNS ATM Design Full UBR PVP mesh between terminal switches to carry “Best Effort” traffic 50
v. BNS ATM Design Full UBR PVP mesh between terminal switches to carry “Best Effort” traffic 50
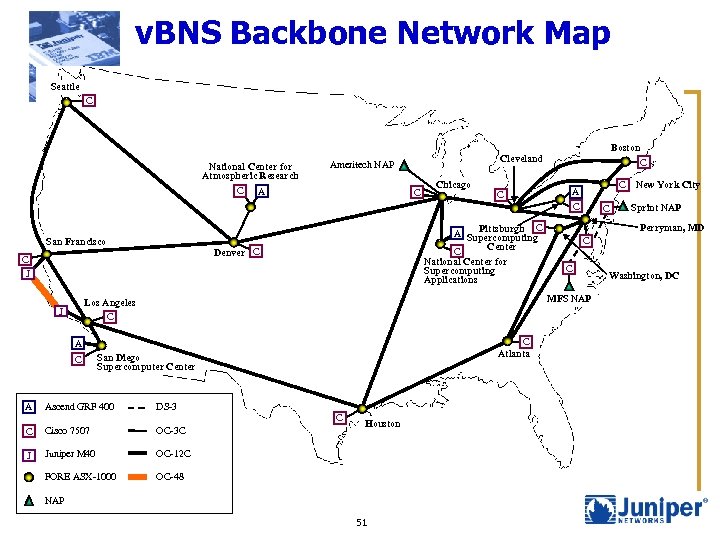 v. BNS Backbone Network Map Seattle C National Center for Atmospheric Research C San Francisco Ameritech NAP A C C J Chicago C Pittsburgh C A Supercomputing Center C National Center for Supercomputing Applications Denver C C Atlanta A C C C New York City A C C San Diego Supercomputer Center A Ascend GRF 400 DS-3 C Cisco 7507 OC-3 C J Juniper M 40 OC-12 C FORE ASX-1000 OC-48 C Houston NAP 51 Sprint NAP Perryman, MD C C MFS NAP Los Angeles C J Boston Cleveland Washington, DC
v. BNS Backbone Network Map Seattle C National Center for Atmospheric Research C San Francisco Ameritech NAP A C C J Chicago C Pittsburgh C A Supercomputing Center C National Center for Supercomputing Applications Denver C C Atlanta A C C C New York City A C C San Diego Supercomputer Center A Ascend GRF 400 DS-3 C Cisco 7507 OC-3 C J Juniper M 40 OC-12 C FORE ASX-1000 OC-48 C Houston NAP 51 Sprint NAP Perryman, MD C C MFS NAP Los Angeles C J Boston Cleveland Washington, DC
 Overlay Nets Had Drawbacks Growth in full mesh of ATM PVCs stresses everything u Router IGP runs out of steam u Practical limitation of updating configurations in each switch and router u ATM 20% Cell Tax u ATM SAR speed limitations v OC-48 SAR very difficult/expensive to build v OC-192 SAR? u 52
Overlay Nets Had Drawbacks Growth in full mesh of ATM PVCs stresses everything u Router IGP runs out of steam u Practical limitation of updating configurations in each switch and router u ATM 20% Cell Tax u ATM SAR speed limitations v OC-48 SAR very difficult/expensive to build v OC-192 SAR? u 52
 In the mean time: u Routers caught up v Current generation of routers have u High speed, wire-rate interfaces u Deterministic performance u Software advances u MPLS came along v Fuses best aspects of ATM PVCs with highperformance routing engines v Uses low-overhead circuit mechanism v Automates path selection and configuration v Implements quick failure recovery 53
In the mean time: u Routers caught up v Current generation of routers have u High speed, wire-rate interfaces u Deterministic performance u Software advances u MPLS came along v Fuses best aspects of ATM PVCs with highperformance routing engines v Uses low-overhead circuit mechanism v Automates path selection and configuration v Implements quick failure recovery 53
 MPLS for Traffic Engineering Low-overhead virtual circuits for IP u Originally designed to make routers faster u v Fixed label lookup faster than longest match used by IP routing v Not true anymore Value of MPLS is now in traffic engineering u Other MPLS Benefits: u v No second network v A fully integrated IP solution – no second technology v Traffic engineering v Lower cost v A Co. S enabler v Failover/link protection v Multi-service and VPN support 54
MPLS for Traffic Engineering Low-overhead virtual circuits for IP u Originally designed to make routers faster u v Fixed label lookup faster than longest match used by IP routing v Not true anymore Value of MPLS is now in traffic engineering u Other MPLS Benefits: u v No second network v A fully integrated IP solution – no second technology v Traffic engineering v Lower cost v A Co. S enabler v Failover/link protection v Multi-service and VPN support 54
 AGENDA u MPLS Overview u Traffic Engineering u VPNs 55
AGENDA u MPLS Overview u Traffic Engineering u VPNs 55
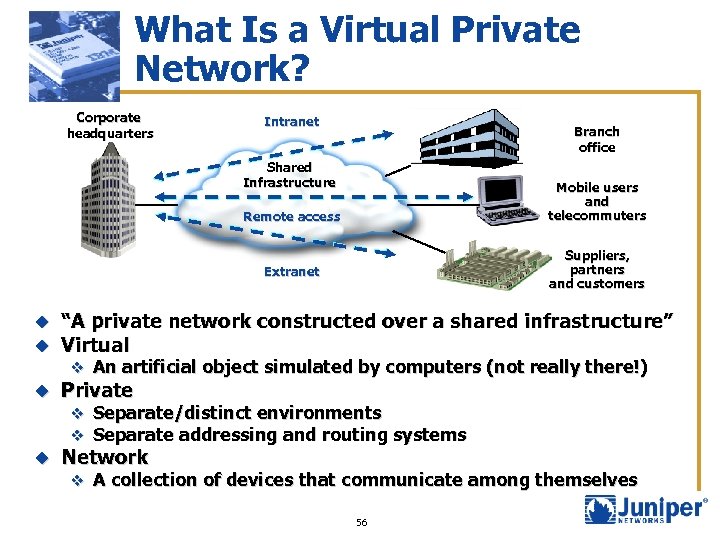 What Is a Virtual Private Network? Corporate headquarters Intranet Branch office Shared Infrastructure Mobile users and telecommuters Remote access Suppliers, partners and customers Extranet u u “A private network constructed over a shared infrastructure” Virtual u Private u Network v An artificial object simulated by computers (not really there!) v Separate/distinct environments v Separate addressing and routing systems v A collection of devices that communicate among themselves 56
What Is a Virtual Private Network? Corporate headquarters Intranet Branch office Shared Infrastructure Mobile users and telecommuters Remote access Suppliers, partners and customers Extranet u u “A private network constructed over a shared infrastructure” Virtual u Private u Network v An artificial object simulated by computers (not really there!) v Separate/distinct environments v Separate addressing and routing systems v A collection of devices that communicate among themselves 56
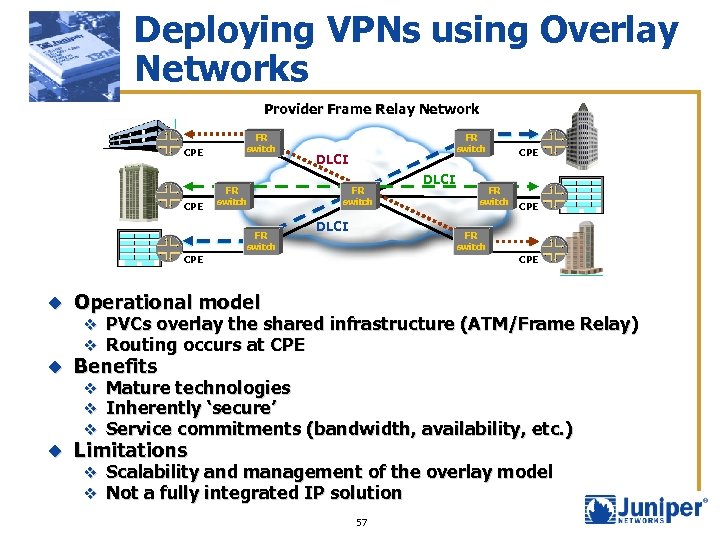 Deploying VPNs using Overlay Networks Provider Frame Relay Network CPE FR switch DLCI FR switch DLCI CPE Benefits u CPE Operational model u FR switch CPE u DLCI CPE Limitations v PVCs overlay the shared infrastructure (ATM/Frame Relay) v Routing occurs at CPE v Mature technologies v Inherently ‘secure’ v Service commitments (bandwidth, availability, etc. ) v Scalability and management of the overlay model v Not a fully integrated IP solution 57
Deploying VPNs using Overlay Networks Provider Frame Relay Network CPE FR switch DLCI FR switch DLCI CPE Benefits u CPE Operational model u FR switch CPE u DLCI CPE Limitations v PVCs overlay the shared infrastructure (ATM/Frame Relay) v Routing occurs at CPE v Mature technologies v Inherently ‘secure’ v Service commitments (bandwidth, availability, etc. ) v Scalability and management of the overlay model v Not a fully integrated IP solution 57
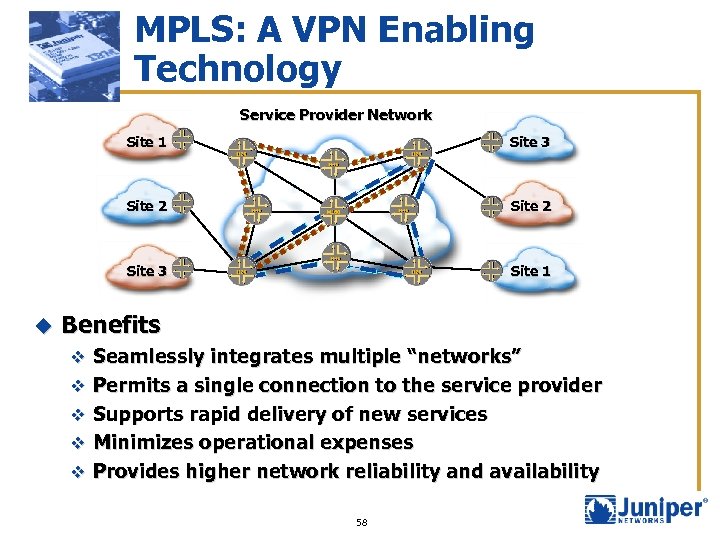 MPLS: A VPN Enabling Technology Service Provider Network Site 1 Site 2 Site 3 u Site 3 Site 1 Benefits v Seamlessly integrates multiple “networks” v Permits a single connection to the service provider v Supports rapid delivery of new services v Minimizes operational expenses v Provides higher network reliability and availability 58
MPLS: A VPN Enabling Technology Service Provider Network Site 1 Site 2 Site 3 u Site 3 Site 1 Benefits v Seamlessly integrates multiple “networks” v Permits a single connection to the service provider v Supports rapid delivery of new services v Minimizes operational expenses v Provides higher network reliability and availability 58
 There are Three Types of VPNs u End to End (CPE Based) VPNs v L 2 PT & PPTP v IPSEC u Layer 2 VPNs v CCC & MPLS Hybrid u Layer 3 VPNs v RFC 2547 bis 59
There are Three Types of VPNs u End to End (CPE Based) VPNs v L 2 PT & PPTP v IPSEC u Layer 2 VPNs v CCC & MPLS Hybrid u Layer 3 VPNs v RFC 2547 bis 59
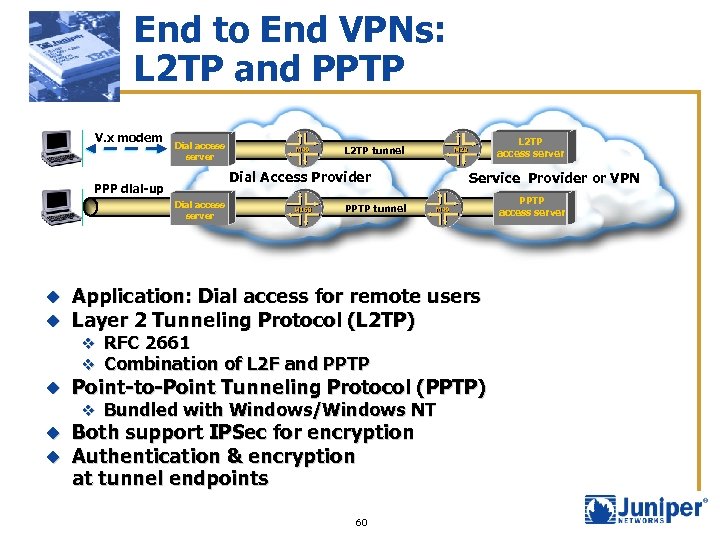 End to End VPNs: L 2 TP and PPTP V. x modem Dial access server Dial Access Provider PPP dial-up Dial access server L 2 TP tunnel Service Provider or VPN PPTP tunnel u u Application: Dial access for remote users Layer 2 Tunneling Protocol (L 2 TP) u Point-to-Point Tunneling Protocol (PPTP) u u Both support IPSec for encryption Authentication & encryption at tunnel endpoints v RFC 2661 v Combination of L 2 F and PPTP v Bundled with Windows/Windows NT 60 PPTP access server
End to End VPNs: L 2 TP and PPTP V. x modem Dial access server Dial Access Provider PPP dial-up Dial access server L 2 TP tunnel Service Provider or VPN PPTP tunnel u u Application: Dial access for remote users Layer 2 Tunneling Protocol (L 2 TP) u Point-to-Point Tunneling Protocol (PPTP) u u Both support IPSec for encryption Authentication & encryption at tunnel endpoints v RFC 2661 v Combination of L 2 F and PPTP v Bundled with Windows/Windows NT 60 PPTP access server
 End to End VPNs: The IP Security Protocol (IPSec) u Defines the IETF’s layer 3 security architecture u Applications: v Strong security requirements v Extend a VPN across multiple service providers u Security services include: v Access control v Data origin authentication v Replay protection v Data integrity v Data privacy (encryption) v Key management 61
End to End VPNs: The IP Security Protocol (IPSec) u Defines the IETF’s layer 3 security architecture u Applications: v Strong security requirements v Extend a VPN across multiple service providers u Security services include: v Access control v Data origin authentication v Replay protection v Data integrity v Data privacy (encryption) v Key management 61
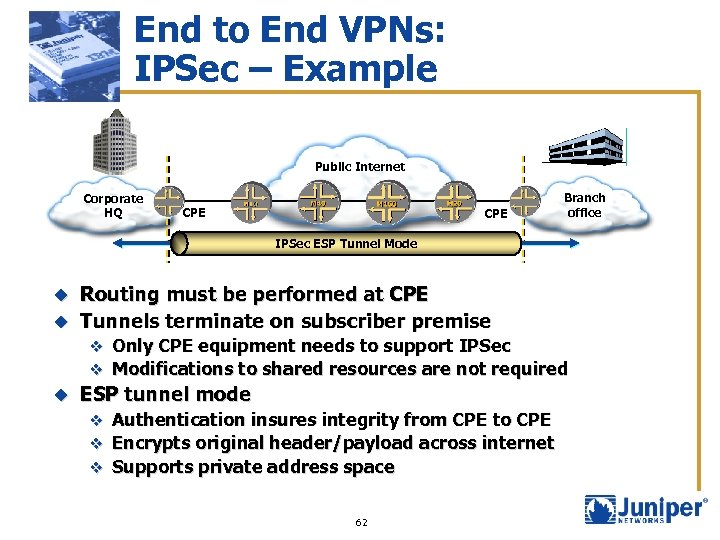 End to End VPNs: IPSec – Example Public Internet Corporate HQ CPE Branch office IPSec ESP Tunnel Mode Routing must be performed at CPE u Tunnels terminate on subscriber premise u v v u Only CPE equipment needs to support IPSec Modifications to shared resources are not required ESP tunnel mode v Authentication insures integrity from CPE to CPE v Encrypts original header/payload across internet v Supports private address space 62
End to End VPNs: IPSec – Example Public Internet Corporate HQ CPE Branch office IPSec ESP Tunnel Mode Routing must be performed at CPE u Tunnels terminate on subscriber premise u v v u Only CPE equipment needs to support IPSec Modifications to shared resources are not required ESP tunnel mode v Authentication insures integrity from CPE to CPE v Encrypts original header/payload across internet v Supports private address space 62
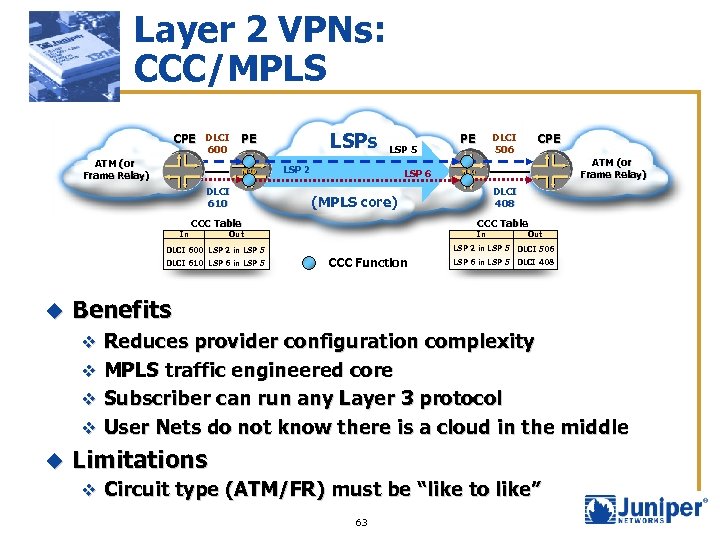 Layer 2 VPNs: CCC/MPLS LSPs CPE DLCI PE 600 ATM (or Frame Relay) LSP 5 LSP 2 DLCI 610 In ATM (or Frame Relay) DLCI 408 (MPLS core) CCC Table In Out LSP 2 in LSP 5 DLCI 506 DLCI 600 LSP 2 in LSP 5 u PE CPE LSP 6 CCC Table DLCI 610 LSP 6 in LSP 5 DLCI 506 PE CCC Function LSP 6 in LSP 5 DLCI 408 Benefits v Reduces provider configuration complexity v MPLS traffic engineered core v Subscriber can run any Layer 3 protocol v User Nets do not know there is a cloud in the middle u Limitations v Circuit type (ATM/FR) must be “like to like” 63
Layer 2 VPNs: CCC/MPLS LSPs CPE DLCI PE 600 ATM (or Frame Relay) LSP 5 LSP 2 DLCI 610 In ATM (or Frame Relay) DLCI 408 (MPLS core) CCC Table In Out LSP 2 in LSP 5 DLCI 506 DLCI 600 LSP 2 in LSP 5 u PE CPE LSP 6 CCC Table DLCI 610 LSP 6 in LSP 5 DLCI 506 PE CCC Function LSP 6 in LSP 5 DLCI 408 Benefits v Reduces provider configuration complexity v MPLS traffic engineered core v Subscriber can run any Layer 3 protocol v User Nets do not know there is a cloud in the middle u Limitations v Circuit type (ATM/FR) must be “like to like” 63
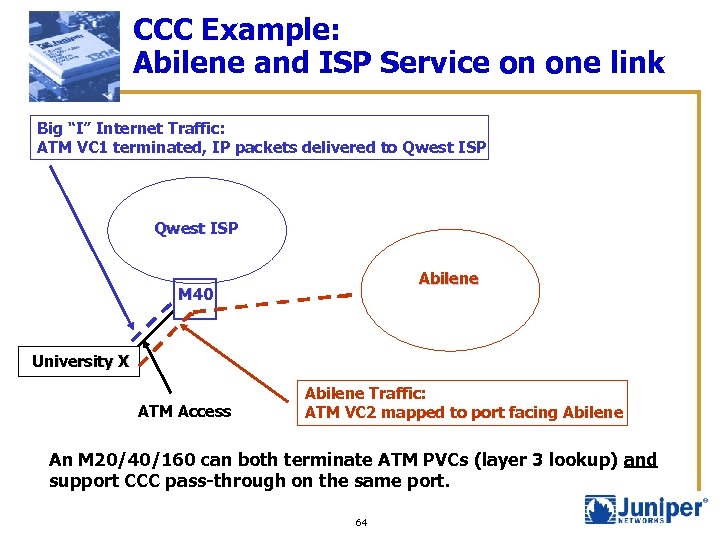 CCC Example: Abilene and ISP Service on one link Big “I” Internet Traffic: ATM VC 1 terminated, IP packets delivered to Qwest ISP Abilene M 40 University X ATM Access Abilene Traffic: ATM VC 2 mapped to port facing Abilene An M 20/40/160 can both terminate ATM PVCs (layer 3 lookup) and support CCC pass-through on the same port. 64
CCC Example: Abilene and ISP Service on one link Big “I” Internet Traffic: ATM VC 1 terminated, IP packets delivered to Qwest ISP Abilene M 40 University X ATM Access Abilene Traffic: ATM VC 2 mapped to port facing Abilene An M 20/40/160 can both terminate ATM PVCs (layer 3 lookup) and support CCC pass-through on the same port. 64
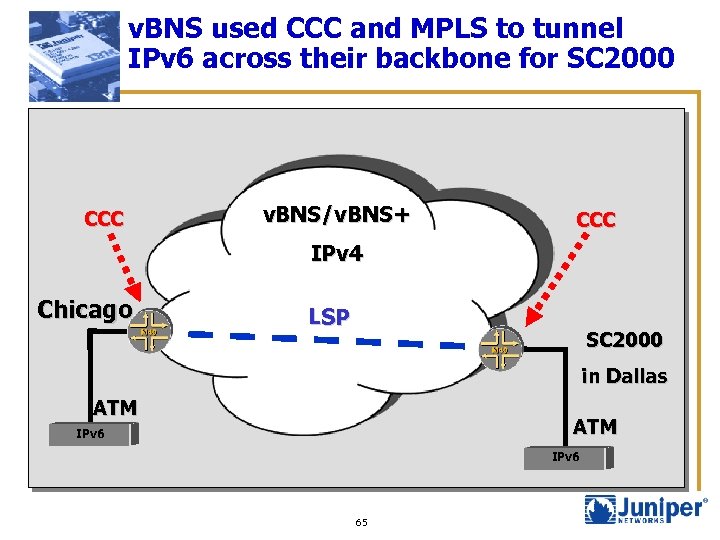 v. BNS used CCC and MPLS to tunnel IPv 6 across their backbone for SC 2000 CCC v. BNS/v. BNS+ CCC IPv 4 Chicago LSP SC 2000 in Dallas ATM IPv 6 65
v. BNS used CCC and MPLS to tunnel IPv 6 across their backbone for SC 2000 CCC v. BNS/v. BNS+ CCC IPv 4 Chicago LSP SC 2000 in Dallas ATM IPv 6 65
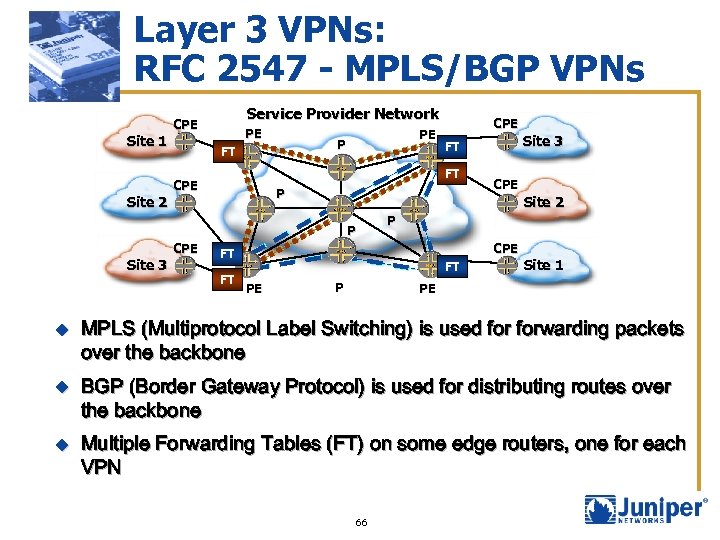 Layer 3 VPNs: RFC 2547 - MPLS/BGP VPNs Site 1 Site 2 Service Provider Network CPE PE PE P FT P P CPE FT FT CPE Site 2 P Site 3 FT FT CPE CPE FT PE P Site 1 PE u MPLS (Multiprotocol Label Switching) is used forwarding packets over the backbone u BGP (Border Gateway Protocol) is used for distributing routes over the backbone u Multiple Forwarding Tables (FT) on some edge routers, one for each VPN 66
Layer 3 VPNs: RFC 2547 - MPLS/BGP VPNs Site 1 Site 2 Service Provider Network CPE PE PE P FT P P CPE FT FT CPE Site 2 P Site 3 FT FT CPE CPE FT PE P Site 1 PE u MPLS (Multiprotocol Label Switching) is used forwarding packets over the backbone u BGP (Border Gateway Protocol) is used for distributing routes over the backbone u Multiple Forwarding Tables (FT) on some edge routers, one for each VPN 66
 Questions? 67
Questions? 67
 Thank You jjamison@juniper. net http: //www. juniper. net 68
Thank You jjamison@juniper. net http: //www. juniper. net 68


