9e9c467eedeb0a9b255e9a095d73ddf4.ppt
- Количество слайдов: 26
 Module 5 Securing SCOoffice Server 1
Module 5 Securing SCOoffice Server 1
 Securing SCOoffice Server 2
Securing SCOoffice Server 2
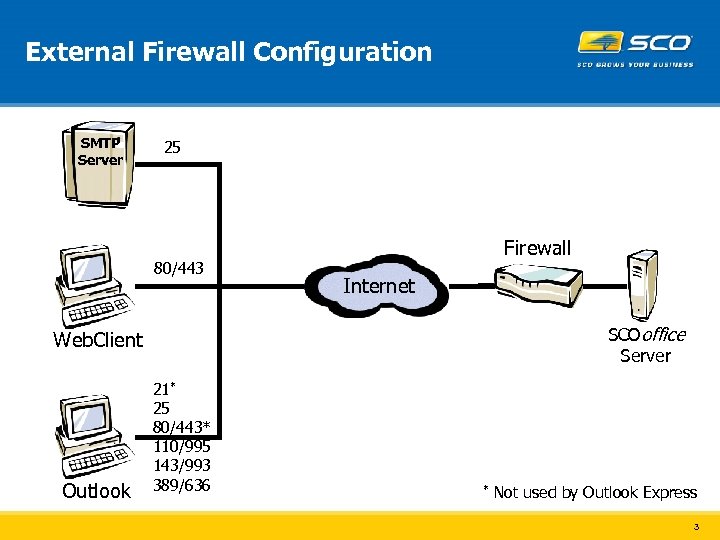 External Firewall Configuration SMTP Server 25 80/443 Firewall Internet SCOoffice Server Web. Client Outlook 21* 25 80/443* 110/995 143/993 389/636 * Not used by Outlook Express 3
External Firewall Configuration SMTP Server 25 80/443 Firewall Internet SCOoffice Server Web. Client Outlook 21* 25 80/443* 110/995 143/993 389/636 * Not used by Outlook Express 3
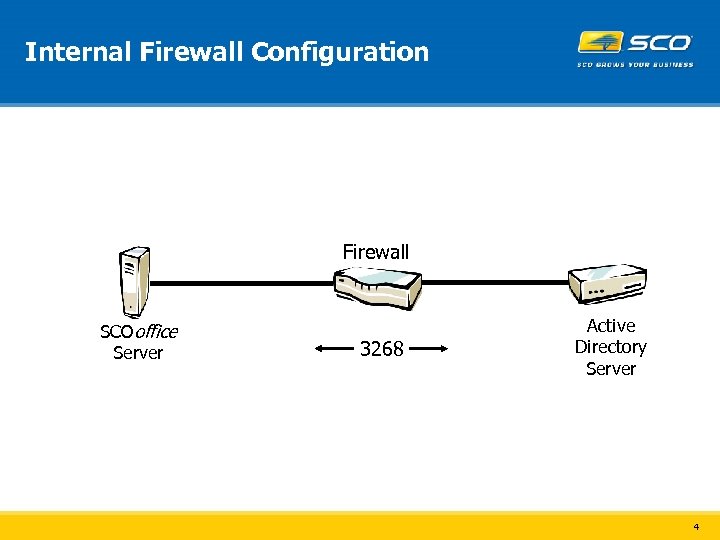 Internal Firewall Configuration Firewall SCOoffice Server 3268 Active Directory Server 4
Internal Firewall Configuration Firewall SCOoffice Server 3268 Active Directory Server 4
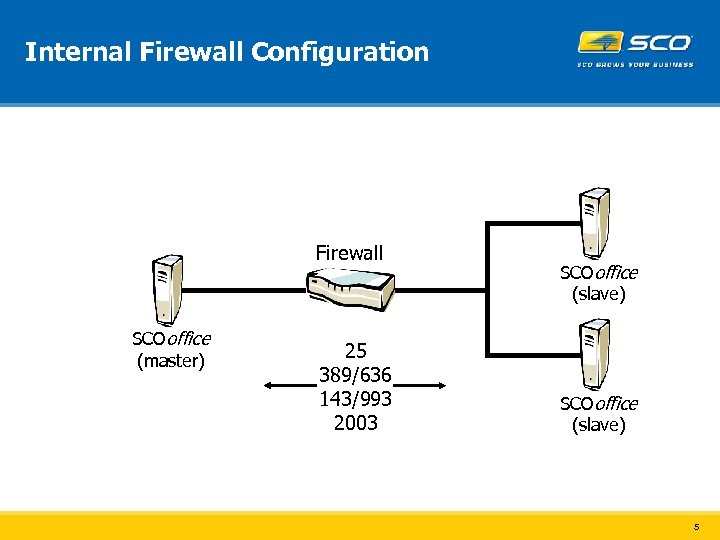 Internal Firewall Configuration Firewall SCOoffice (master) 25 389/636 143/993 2003 SCOoffice (slave) 5
Internal Firewall Configuration Firewall SCOoffice (master) 25 389/636 143/993 2003 SCOoffice (slave) 5
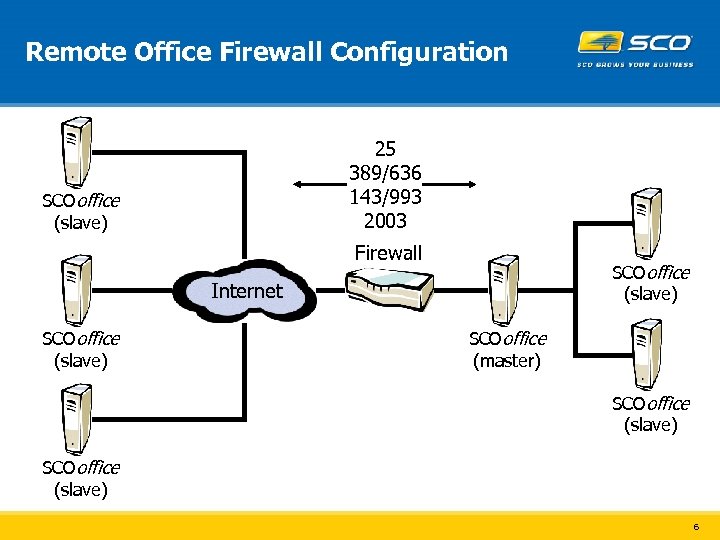 Remote Office Firewall Configuration 25 389/636 143/993 2003 SCOoffice (slave) Firewall SCOoffice (slave) Internet SCOoffice (slave) SCOoffice (master) SCOoffice (slave) 6
Remote Office Firewall Configuration 25 389/636 143/993 2003 SCOoffice (slave) Firewall SCOoffice (slave) Internet SCOoffice (slave) SCOoffice (master) SCOoffice (slave) 6
 SCO Open. Server’s HTTP Servers § SCO Open. Server runs HTTP servers on ports: § § 80 – SCOoffice Server’s HTTP server 443 – SCOoffice Server’s HTTPS server 615 – Internet Configuration Manager 8457 – Doc. View: Access to SCO Open. Server documentation 7
SCO Open. Server’s HTTP Servers § SCO Open. Server runs HTTP servers on ports: § § 80 – SCOoffice Server’s HTTP server 443 – SCOoffice Server’s HTTPS server 615 – Internet Configuration Manager 8457 – Doc. View: Access to SCO Open. Server documentation 7
 Other SCOoffice Server Related Ports § SCOoffice Server runs daemons on ports: § § § § 21 – Pro. FTP 25 – SMTP 110 – POP 3 143 – IMAP 389 – Open. LDAP 993 – IMAP 4 over TLS/SSL 995 – POP 3 over TLS/SSL 2000 –Cyrusmaster (sieve) 2003 –Cyrusmaster (LMTP) 2583 – MON 4840 – SASLAUTHD 4844 – SASLAUTHD 10024 – AMa. Vi. S 8
Other SCOoffice Server Related Ports § SCOoffice Server runs daemons on ports: § § § § 21 – Pro. FTP 25 – SMTP 110 – POP 3 143 – IMAP 389 – Open. LDAP 993 – IMAP 4 over TLS/SSL 995 – POP 3 over TLS/SSL 2000 –Cyrusmaster (sieve) 2003 –Cyrusmaster (LMTP) 2583 – MON 4840 – SASLAUTHD 4844 – SASLAUTHD 10024 – AMa. Vi. S 8
 Disallowing Open Relay § Don’t let server be used as an open relay § Numerous ways to prevent open relay § We will configure SASLAUTHD + TLS # telnet rose. example. net smtp 220 rose. example. net ESMTP Postfix (2. 0. 20) HELO nuisance. spammer. net 250 rose. example. net MAIL FROM: nice_guy@example. net 250 Ok RCPT TO: victim@example. com 250 Ok. . . 9
Disallowing Open Relay § Don’t let server be used as an open relay § Numerous ways to prevent open relay § We will configure SASLAUTHD + TLS # telnet rose. example. net smtp 220 rose. example. net ESMTP Postfix (2. 0. 20) HELO nuisance. spammer. net 250 rose. example. net MAIL FROM: nice_guy@example. net 250 Ok RCPT TO: victim@example. com 250 Ok. . . 9
 Disallowing Open Relay § Useful for blocking unwanted SMTP sessions: § smtpd_client_restrictions § smtpd_sender_restrictions § smtpd_recipient_restrictions Stored in LDAP 10
Disallowing Open Relay § Useful for blocking unwanted SMTP sessions: § smtpd_client_restrictions § smtpd_sender_restrictions § smtpd_recipient_restrictions Stored in LDAP 10
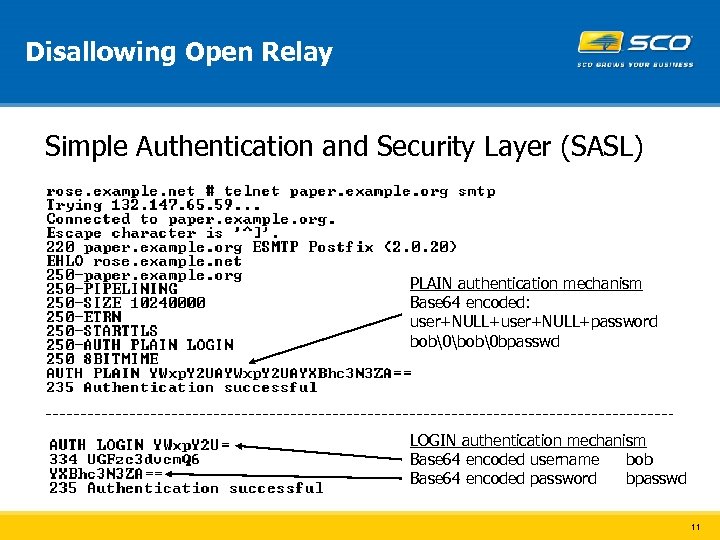 Disallowing Open Relay Simple Authentication and Security Layer (SASL) PLAIN authentication mechanism Base 64 encoded: user+NULL+password bob�bob� bpasswd LOGIN authentication mechanism Base 64 encoded username bob Base 64 encoded password bpasswd 11
Disallowing Open Relay Simple Authentication and Security Layer (SASL) PLAIN authentication mechanism Base 64 encoded: user+NULL+password bob�bob� bpasswd LOGIN authentication mechanism Base 64 encoded username bob Base 64 encoded password bpasswd 11
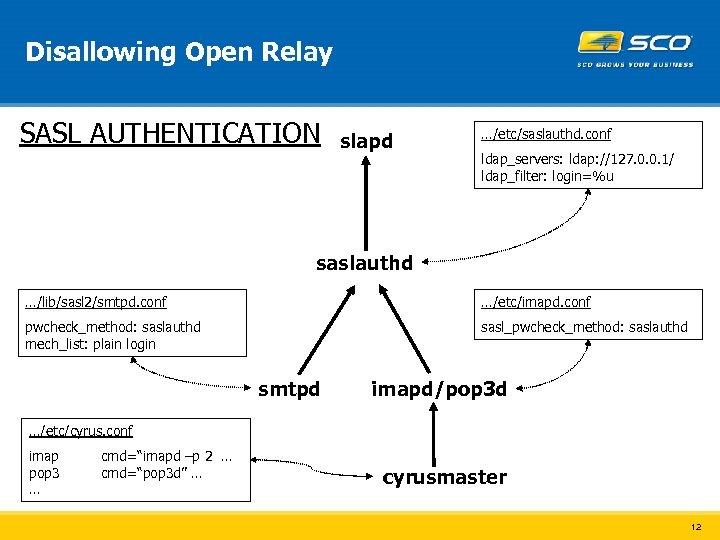 Disallowing Open Relay SASL AUTHENTICATION slapd …/etc/saslauthd. conf ldap_servers: ldap: //127. 0. 0. 1/ ldap_filter: login=%u saslauthd …/lib/sasl 2/smtpd. conf …/etc/imapd. conf pwcheck_method: saslauthd mech_list: plain login sasl_pwcheck_method: saslauthd smtpd imapd/pop 3 d …/etc/cyrus. conf imap pop 3 … cmd=“imapd –p 2 … cmd=“pop 3 d” … cyrusmaster 12
Disallowing Open Relay SASL AUTHENTICATION slapd …/etc/saslauthd. conf ldap_servers: ldap: //127. 0. 0. 1/ ldap_filter: login=%u saslauthd …/lib/sasl 2/smtpd. conf …/etc/imapd. conf pwcheck_method: saslauthd mech_list: plain login sasl_pwcheck_method: saslauthd smtpd imapd/pop 3 d …/etc/cyrus. conf imap pop 3 … cmd=“imapd –p 2 … cmd=“pop 3 d” … cyrusmaster 12
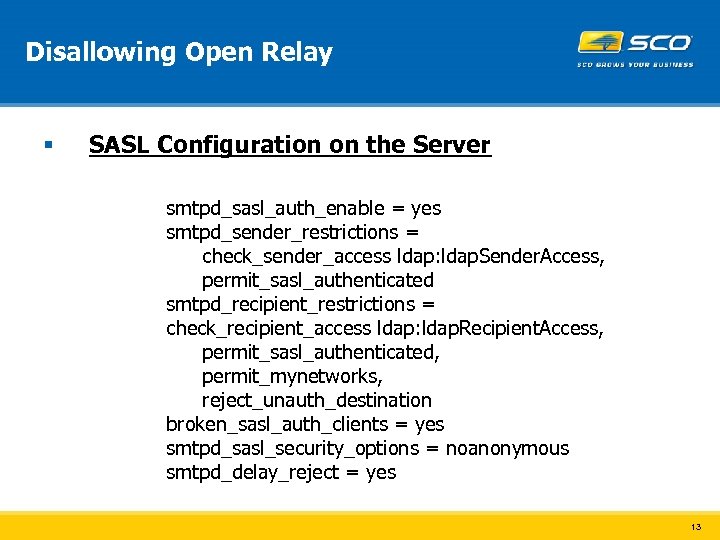 Disallowing Open Relay § SASL Configuration on the Server smtpd_sasl_auth_enable = yes smtpd_sender_restrictions = check_sender_access ldap: ldap. Sender. Access, permit_sasl_authenticated smtpd_recipient_restrictions = check_recipient_access ldap: ldap. Recipient. Access, permit_sasl_authenticated, permit_mynetworks, reject_unauth_destination broken_sasl_auth_clients = yes smtpd_sasl_security_options = noanonymous smtpd_delay_reject = yes 13
Disallowing Open Relay § SASL Configuration on the Server smtpd_sasl_auth_enable = yes smtpd_sender_restrictions = check_sender_access ldap: ldap. Sender. Access, permit_sasl_authenticated smtpd_recipient_restrictions = check_recipient_access ldap: ldap. Recipient. Access, permit_sasl_authenticated, permit_mynetworks, reject_unauth_destination broken_sasl_auth_clients = yes smtpd_sasl_security_options = noanonymous smtpd_delay_reject = yes 13
 Disallowing Open Relay § SASL Configuration on the Client smtp_sasl_auth_enable = yes smtp_sasl_password_maps = hash: /opt/insight/etc/postfix/sasl_passwd smtp_sasl_security_options = noanonymous 14
Disallowing Open Relay § SASL Configuration on the Client smtp_sasl_auth_enable = yes smtp_sasl_password_maps = hash: /opt/insight/etc/postfix/sasl_passwd smtp_sasl_security_options = noanonymous 14
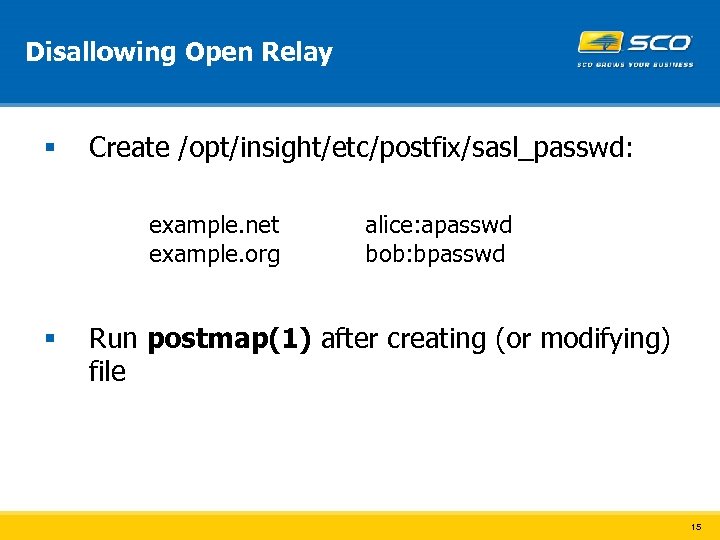 Disallowing Open Relay § Create /opt/insight/etc/postfix/sasl_passwd: example. net example. org § alice: apasswd bob: bpasswd Run postmap(1) after creating (or modifying) file 15
Disallowing Open Relay § Create /opt/insight/etc/postfix/sasl_passwd: example. net example. org § alice: apasswd bob: bpasswd Run postmap(1) after creating (or modifying) file 15
 Disallowing Open Relay § § § TLS v 1 is based on SSL v 3 Encrypt SMTP traffic using TLS X. 509 certificates 16
Disallowing Open Relay § § § TLS v 1 is based on SSL v 3 Encrypt SMTP traffic using TLS X. 509 certificates 16
 Disallowing Open Relay § TLS Configuration on the Server smtpd_tls_cert_file = /opt/insight/etc/ssl/server. pem smtpd_tls_key_file = /opt/insight/etc/ssl/server. pem smtpd_tls_CAfile = /opt/insight/etc/ssl/server. pem smtpd_use_tls = yes 17
Disallowing Open Relay § TLS Configuration on the Server smtpd_tls_cert_file = /opt/insight/etc/ssl/server. pem smtpd_tls_key_file = /opt/insight/etc/ssl/server. pem smtpd_tls_CAfile = /opt/insight/etc/ssl/server. pem smtpd_use_tls = yes 17
 Disallowing Open Relay § TLS Configuration on the Client smtp_tls_cert_file = /opt/insight/etc/ssl/server. pem smtp_tls_key_file = /opt/insight/etc/ssl/server. pem smtp_tls_CAfile = /opt/insight/etc/ssl/server. pem smtp_use_tls = yes 18
Disallowing Open Relay § TLS Configuration on the Client smtp_tls_cert_file = /opt/insight/etc/ssl/server. pem smtp_tls_key_file = /opt/insight/etc/ssl/server. pem smtp_tls_CAfile = /opt/insight/etc/ssl/server. pem smtp_use_tls = yes 18
 Disallowing Open Relay § Using a Certificate Authority’s Certificate smtp_tls_CApath = /opt/insight/etc/ssl/ca_cert. pem smtpd_tls_CApath = /opt/insight/etc/ssl/ca_cert. pem 19
Disallowing Open Relay § Using a Certificate Authority’s Certificate smtp_tls_CApath = /opt/insight/etc/ssl/ca_cert. pem smtpd_tls_CApath = /opt/insight/etc/ssl/ca_cert. pem 19
 Disallowing Open Relay § To test to see if a mail server is an open relay: § § Log into the mail server telnet rt. njabl. org 2500 20
Disallowing Open Relay § To test to see if a mail server is an open relay: § § Log into the mail server telnet rt. njabl. org 2500 20
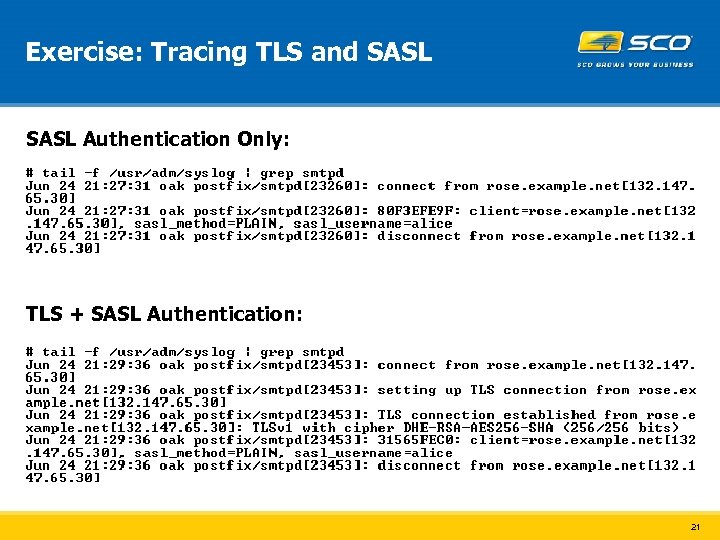 Exercise: Tracing TLS and SASL Authentication Only: TLS + SASL Authentication: 21
Exercise: Tracing TLS and SASL Authentication Only: TLS + SASL Authentication: 21
 Other Restrictions § § § Other useful restrictions: smtpd_client_restrictions smtpd_helo_restrictions smtpd_sender_restrictions See www. postfix. org/uce. html 22
Other Restrictions § § § Other useful restrictions: smtpd_client_restrictions smtpd_helo_restrictions smtpd_sender_restrictions See www. postfix. org/uce. html 22
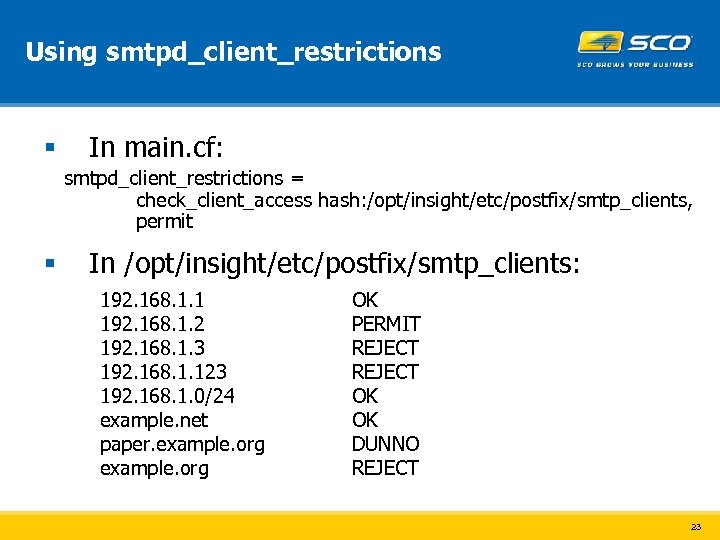 Using smtpd_client_restrictions § In main. cf: smtpd_client_restrictions = check_client_access hash: /opt/insight/etc/postfix/smtp_clients, permit § In /opt/insight/etc/postfix/smtp_clients: 192. 168. 1. 1 192. 168. 1. 2 192. 168. 1. 3 192. 168. 1. 123 192. 168. 1. 0/24 example. net paper. example. org OK PERMIT REJECT OK OK DUNNO REJECT 23
Using smtpd_client_restrictions § In main. cf: smtpd_client_restrictions = check_client_access hash: /opt/insight/etc/postfix/smtp_clients, permit § In /opt/insight/etc/postfix/smtp_clients: 192. 168. 1. 1 192. 168. 1. 2 192. 168. 1. 3 192. 168. 1. 123 192. 168. 1. 0/24 example. net paper. example. org OK PERMIT REJECT OK OK DUNNO REJECT 23
 Using smtpd_helo_restrictions § § check_helo_access reject_invalid_hostname reject_non_fqdn_hostname reject_unknown hostname § In main. cf: smtpd_helo_restrictions = reject_invalid_hostname, check_helo_access hash: /opt/insight/etc/postfix/helo § In /opt/insight/etc/postfix/helo: example. org example. net OK REJECT 24
Using smtpd_helo_restrictions § § check_helo_access reject_invalid_hostname reject_non_fqdn_hostname reject_unknown hostname § In main. cf: smtpd_helo_restrictions = reject_invalid_hostname, check_helo_access hash: /opt/insight/etc/postfix/helo § In /opt/insight/etc/postfix/helo: example. org example. net OK REJECT 24
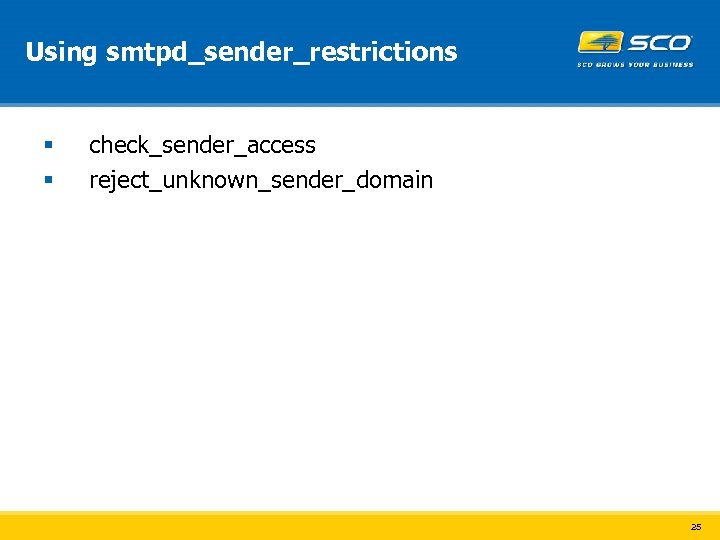 Using smtpd_sender_restrictions § § check_sender_access reject_unknown_sender_domain 25
Using smtpd_sender_restrictions § § check_sender_access reject_unknown_sender_domain 25
 Creating a Chroot Jail § § A chroot jail adds a layer of protection Limits daemon(s) to /opt/insight/var/spool/postfix § Set the fifth field in master. cf to ‘y’ 26
Creating a Chroot Jail § § A chroot jail adds a layer of protection Limits daemon(s) to /opt/insight/var/spool/postfix § Set the fifth field in master. cf to ‘y’ 26


