522721d62d867182f3d0a40aa3e79dbe.ppt
- Количество слайдов: 128
 Module 2: TCP/IP As a Solution for Networking
Module 2: TCP/IP As a Solution for Networking
 Overview n Introducing TCP/IP n Designing a Functional TCP/IP Solution n Securing a TCP/IP Solution n Enhancing a TCP/IP Design for Availability n Optimizing a TCP/IP Design for Performance
Overview n Introducing TCP/IP n Designing a Functional TCP/IP Solution n Securing a TCP/IP Solution n Enhancing a TCP/IP Design for Availability n Optimizing a TCP/IP Design for Performance
 n Organizations are facing a growing need for Internet connectivity, and connectivity between dissimilar operating systems and hardware platforms spread over large geographic distances. Because Transmission Control Protocol/Internet Protocol (TCP/IP) operates on a wide variety of physical networks and can be scaled to suit small to large networks, it is the only protocol that can meet the requirements of these organizations.
n Organizations are facing a growing need for Internet connectivity, and connectivity between dissimilar operating systems and hardware platforms spread over large geographic distances. Because Transmission Control Protocol/Internet Protocol (TCP/IP) operates on a wide variety of physical networks and can be scaled to suit small to large networks, it is the only protocol that can meet the requirements of these organizations.
 At the end of this module, you will be able to: n Identify the features of TCP/IP in Microsoft® Windows® 2000 and the functionality provided by those features. n Recognize the IP address structure appropriate for private or public network TCP/IP functionality. n Describe methods available to secure TCP/IP data traffic. n Describe strategies to improve the availability of TCP/IP routing structures. n Describe strategies for efficient use of IP traffic data transmission.
At the end of this module, you will be able to: n Identify the features of TCP/IP in Microsoft® Windows® 2000 and the functionality provided by those features. n Recognize the IP address structure appropriate for private or public network TCP/IP functionality. n Describe methods available to secure TCP/IP data traffic. n Describe strategies to improve the availability of TCP/IP routing structures. n Describe strategies for efficient use of IP traffic data transmission.
 u. Introducing TCP/IP n TCP/IP Protocol Suite n Design Decisions for a TCP/IP Solution n TCP/IP Features
u. Introducing TCP/IP n TCP/IP Protocol Suite n Design Decisions for a TCP/IP Solution n TCP/IP Features
 TCP/IP operates on a wide variety of physical networks and can be scaled to suit small to large networks. IP is the protocol used for communications on public networks such as the Internet. To design a TCP/IP network infrastructure, you need to: n Describe the components of the TCP/IP protocol suite. n Determine the design decisions influencing a TCP/IP solution. n Describe the features and functionality provided by TCP/IP in Windows 2000.
TCP/IP operates on a wide variety of physical networks and can be scaled to suit small to large networks. IP is the protocol used for communications on public networks such as the Internet. To design a TCP/IP network infrastructure, you need to: n Describe the components of the TCP/IP protocol suite. n Determine the design decisions influencing a TCP/IP solution. n Describe the features and functionality provided by TCP/IP in Windows 2000.
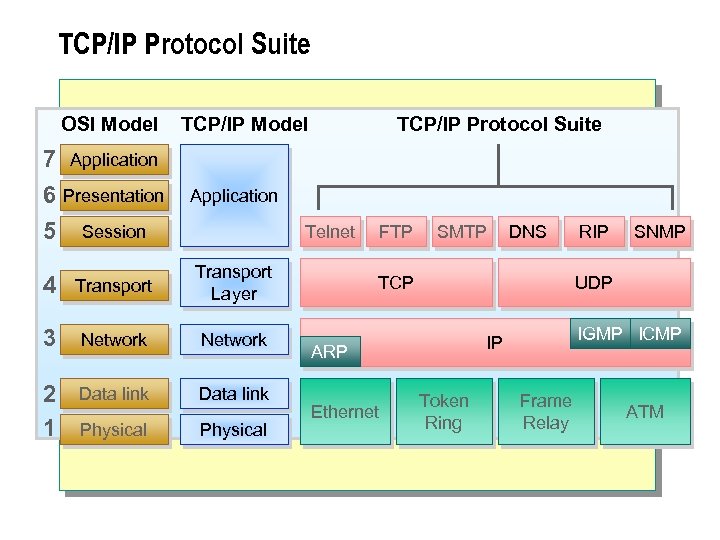 TCP/IP Protocol Suite OSI Model 7 Application 6 Presentation 5 Session TCP/IP Model TCP/IP Protocol Suite Application Telnet 4 Transport Layer 3 Network 2 1 Data link Physical FTP SMTP DNS TCP SNMP UDP IGMP ICMP IP ARP Ethernet RIP Token Ring Frame Relay ATM
TCP/IP Protocol Suite OSI Model 7 Application 6 Presentation 5 Session TCP/IP Model TCP/IP Protocol Suite Application Telnet 4 Transport Layer 3 Network 2 1 Data link Physical FTP SMTP DNS TCP SNMP UDP IGMP ICMP IP ARP Ethernet RIP Token Ring Frame Relay ATM
 n The TCP/IP suite of protocols allows the design of a logical peer network by using an underlying physical network infrastructure. These vendor-independent protocols can be used to implement IP networks ranging from small local area networks (LANs) to large enterprise networks. The Internet Engineering Task Force (IETF) continues to revise and improve the TCP/IP suite of protocols. Microsoft continuously updates the TCP/IP implementation to comply with the latest IETF standards. The preceding illustration shows the mapping of the Open Systems Interconnection (OSI) seven-layer model to the TCP/IP four-layer model, and the major components of the TCP/IP suite. The OSI layer one and two infrastructure is considered to be in place for any design considerations in this module.
n The TCP/IP suite of protocols allows the design of a logical peer network by using an underlying physical network infrastructure. These vendor-independent protocols can be used to implement IP networks ranging from small local area networks (LANs) to large enterprise networks. The Internet Engineering Task Force (IETF) continues to revise and improve the TCP/IP suite of protocols. Microsoft continuously updates the TCP/IP implementation to comply with the latest IETF standards. The preceding illustration shows the mapping of the Open Systems Interconnection (OSI) seven-layer model to the TCP/IP four-layer model, and the major components of the TCP/IP suite. The OSI layer one and two infrastructure is considered to be in place for any design considerations in this module.
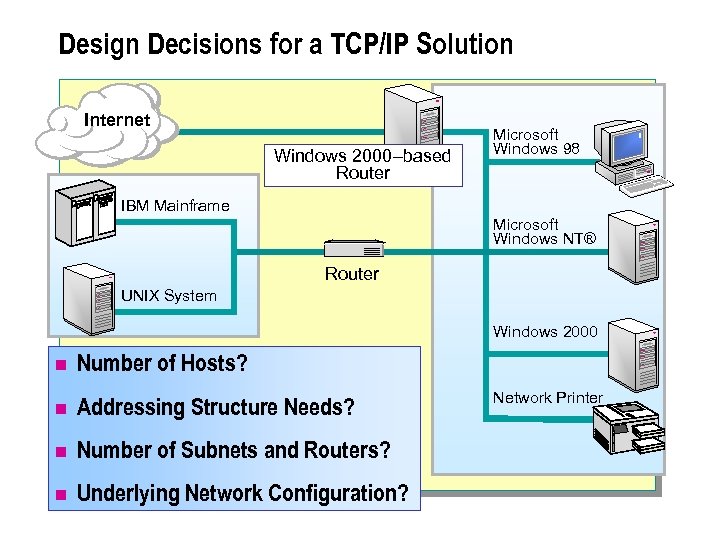 Design Decisions for a TCP/IP Solution Internet Windows 2000–based Router Microsoft Windows 98 IBM Mainframe Microsoft Windows NT® Router UNIX System Windows 2000 n Number of Hosts? n Addressing Structure Needs? n Number of Subnets and Routers? n Underlying Network Configuration? Network Printer
Design Decisions for a TCP/IP Solution Internet Windows 2000–based Router Microsoft Windows 98 IBM Mainframe Microsoft Windows NT® Router UNIX System Windows 2000 n Number of Hosts? n Addressing Structure Needs? n Number of Subnets and Routers? n Underlying Network Configuration? Network Printer
 n Windows 2000 uses TCP/IP for authentication processes, file and print services, information replication, and other common network functions such as communication in heterogeneous, multiple-vendor networks. Before you design a TCP/IP solution, you must identify the design decisions that influence the design.
n Windows 2000 uses TCP/IP for authentication processes, file and print services, information replication, and other common network functions such as communication in heterogeneous, multiple-vendor networks. Before you design a TCP/IP solution, you must identify the design decisions that influence the design.
 To design a TCP/IP solution, you need to analyze: n The number of hosts requiring IP connectivity. n The requirement for public and/or private IP addressing. n The number of physical subnets and routers. n The OSI layer 1 and 2 network configuration.
To design a TCP/IP solution, you need to analyze: n The number of hosts requiring IP connectivity. n The requirement for public and/or private IP addressing. n The number of physical subnets and routers. n The OSI layer 1 and 2 network configuration.
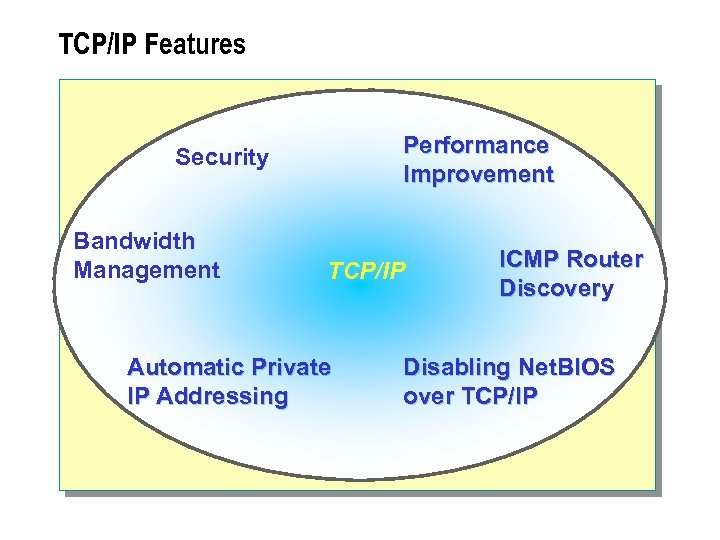 TCP/IP Features Performance Improvement Security Bandwidth Management TCP/IP Automatic Private IP Addressing ICMP Router Discovery Disabling Net. BIOS over TCP/IP
TCP/IP Features Performance Improvement Security Bandwidth Management TCP/IP Automatic Private IP Addressing ICMP Router Discovery Disabling Net. BIOS over TCP/IP
 n To design an effective TCP/IP solution, you must understand the features of TCP/IP and how these features solve the connectivity requirements of your organization. TCP/IP Features
n To design an effective TCP/IP solution, you must understand the features of TCP/IP and how these features solve the connectivity requirements of your organization. TCP/IP Features
 Security n TCP/IP allows enhanced data and connection security by supporting a number of IETF-proposed standards for data encryption, authentication, and filtering. The Windows 2000 implementation of TCP/IP supports Internet Protocol Security (IPSec) and TCP/IP filtering for packet-level authentication and data encryption, and for filtering data.
Security n TCP/IP allows enhanced data and connection security by supporting a number of IETF-proposed standards for data encryption, authentication, and filtering. The Windows 2000 implementation of TCP/IP supports Internet Protocol Security (IPSec) and TCP/IP filtering for packet-level authentication and data encryption, and for filtering data.
 Bandwidth Management n Time-sensitive IP traffic streams such as streaming multimedia require connection protocols that provide bandwidth reservation within a network. TCP/IP supports bandwidth reservation by using Quality of Service (Qo. S) mechanisms, which allow IP traffic to be prioritized.
Bandwidth Management n Time-sensitive IP traffic streams such as streaming multimedia require connection protocols that provide bandwidth reservation within a network. TCP/IP supports bandwidth reservation by using Quality of Service (Qo. S) mechanisms, which allow IP traffic to be prioritized.
 Automatic Private IP Addressing n Automatic Private IP Addressing (APIPA) automates TCP/IP address configuration for hosts on a single-subnet network that has no DHCP server. APIPA eliminates IP address configuration for simple networks not connected to the Internet. The IP addresses for APIPA are allocated from 169. 254. 0. 0/16, which is reserved by the Internet Assigned Numbers Authority (IANA).
Automatic Private IP Addressing n Automatic Private IP Addressing (APIPA) automates TCP/IP address configuration for hosts on a single-subnet network that has no DHCP server. APIPA eliminates IP address configuration for simple networks not connected to the Internet. The IP addresses for APIPA are allocated from 169. 254. 0. 0/16, which is reserved by the Internet Assigned Numbers Authority (IANA).
 Performance Improvement The following features of TCP/IP have been enhanced to improve the performance of TCP/IP solutions. n Large TCP Windows. TCP window size reflects the maximum number of packets that can be sent without waiting for positive acknowledgment. TCP window scaling (RFC 1323) improves TCP/IP performance when a large amount of data is in transit between the sender and receiver, such as in wide area network (WAN) environments. n TCP Selective Acknowledgment A selective. acknowledgment (SACK) is a TCP option (RFC 2018) that allows the receiver to selectively notify and request that the sender resend only data that is actually missing. This results in smaller amounts of data requiring retransmission and in better use of network bandwidth.
Performance Improvement The following features of TCP/IP have been enhanced to improve the performance of TCP/IP solutions. n Large TCP Windows. TCP window size reflects the maximum number of packets that can be sent without waiting for positive acknowledgment. TCP window scaling (RFC 1323) improves TCP/IP performance when a large amount of data is in transit between the sender and receiver, such as in wide area network (WAN) environments. n TCP Selective Acknowledgment A selective. acknowledgment (SACK) is a TCP option (RFC 2018) that allows the receiver to selectively notify and request that the sender resend only data that is actually missing. This results in smaller amounts of data requiring retransmission and in better use of network bandwidth.
 ICMP Router Discovery n Windows 2000 -based computers running Routing and Remote Access support Internet Control Message Protocol (ICMP) router discovery (RFC 1256). This allows a host to discover the router automatically, although a default gateway is not configured for the host. ICMP router discovery is disabled by default on TCP/IP for Windows 2000 hosts, and is managed by using DHCP.
ICMP Router Discovery n Windows 2000 -based computers running Routing and Remote Access support Internet Control Message Protocol (ICMP) router discovery (RFC 1256). This allows a host to discover the router automatically, although a default gateway is not configured for the host. ICMP router discovery is disabled by default on TCP/IP for Windows 2000 hosts, and is managed by using DHCP.
 Disabling Net. BIOS over TCP/IP n Windows 2000 allows you to disable network basic input/output system (Net. BIOS) over TCP/IP (Net. BT) for computers that use only DNS name registration and resolution. These computers can browse resources only on those computers that: l Have Net. BT disabled. l Use Client for Microsoft Networks, and File and Print Sharing for Microsoft Networks components
Disabling Net. BIOS over TCP/IP n Windows 2000 allows you to disable network basic input/output system (Net. BIOS) over TCP/IP (Net. BT) for computers that use only DNS name registration and resolution. These computers can browse resources only on those computers that: l Have Net. BT disabled. l Use Client for Microsoft Networks, and File and Print Sharing for Microsoft Networks components
 Disabling Net. BIOS over TCP/IP (continued)
Disabling Net. BIOS over TCP/IP (continued)
 Disabling Net. BIOS over TCP/IP (continued) n Tip: When creating custom templates, select functionbased names for the templates. Function-based names allow users to easily select the proper certificates based on the tasks that the user is performing at that time.
Disabling Net. BIOS over TCP/IP (continued) n Tip: When creating custom templates, select functionbased names for the templates. Function-based names allow users to easily select the proper certificates based on the tasks that the user is performing at that time.
 u. Designing a Functional TCP/IP Solution n Reviewing IP Addressing n IP Addressing for a Private Network n IP Address Subnet Requirements n IP Configuration Methodology n Discussion: Evaluating TCP/IP Functional Requirements
u. Designing a Functional TCP/IP Solution n Reviewing IP Addressing n IP Addressing for a Private Network n IP Address Subnet Requirements n IP Configuration Methodology n Discussion: Evaluating TCP/IP Functional Requirements
 n To determine the appropriate TCP/IP infrastructure, you must evaluate your Internet accessibility needs, the use of routers, and public address availability. To allow peer-topeer communication, all hosts in a TCP/IP network require unique IP addresses. IP supports a 32 -bit address structure, publicly administered by a standards body (IETF), which can be used to implement both public and private address structures.
n To determine the appropriate TCP/IP infrastructure, you must evaluate your Internet accessibility needs, the use of routers, and public address availability. To allow peer-topeer communication, all hosts in a TCP/IP network require unique IP addresses. IP supports a 32 -bit address structure, publicly administered by a standards body (IETF), which can be used to implement both public and private address structures.
 In designing a functional IP network, you need to consider: n The IP address and mask configuration. n The addressing structures for private network operation. n The addressing structures to allow subnet routing. n A methodology for a consistent design of IP networks.
In designing a functional IP network, you need to consider: n The IP address and mask configuration. n The addressing structures for private network operation. n The addressing structures to allow subnet routing. n A methodology for a consistent design of IP networks.
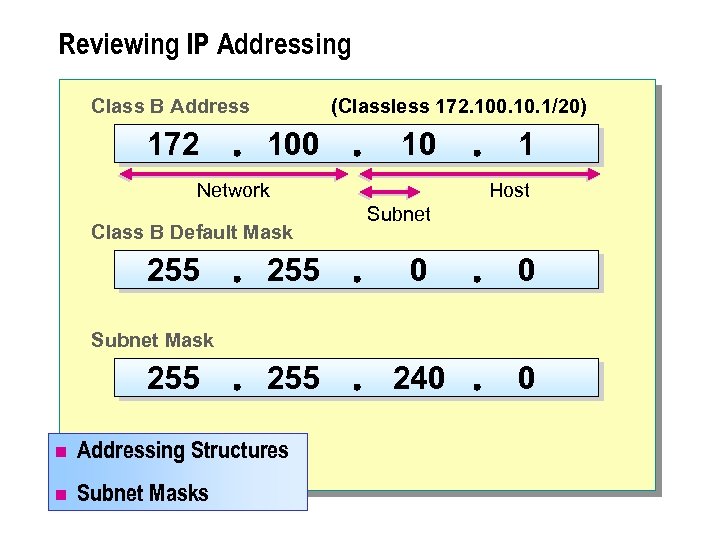 Reviewing IP Addressing Class B Address 172 (Classless 172. 100. 1/20) 100 10 Network Class B Default Mask 255 1 Host Subnet 255 0 0 255 240 0 Subnet Mask 255 n Addressing Structures n Subnet Masks
Reviewing IP Addressing Class B Address 172 (Classless 172. 100. 1/20) 100 10 Network Class B Default Mask 255 1 Host Subnet 255 0 0 255 240 0 Subnet Mask 255 n Addressing Structures n Subnet Masks
 n Each TCP/IP host is identified by a logical IP address. This address is unique for each host that communicates by using TCP/IP. Because IP addresses identify devices on a network, you must assign a unique IP address to each device on the network. The standard for IP addressing is referred to as IP version 4 (v 4). The standard uses a 32 -bit address field and 32 -bit mask field.
n Each TCP/IP host is identified by a logical IP address. This address is unique for each host that communicates by using TCP/IP. Because IP addresses identify devices on a network, you must assign a unique IP address to each device on the network. The standard for IP addressing is referred to as IP version 4 (v 4). The standard uses a 32 -bit address field and 32 -bit mask field.
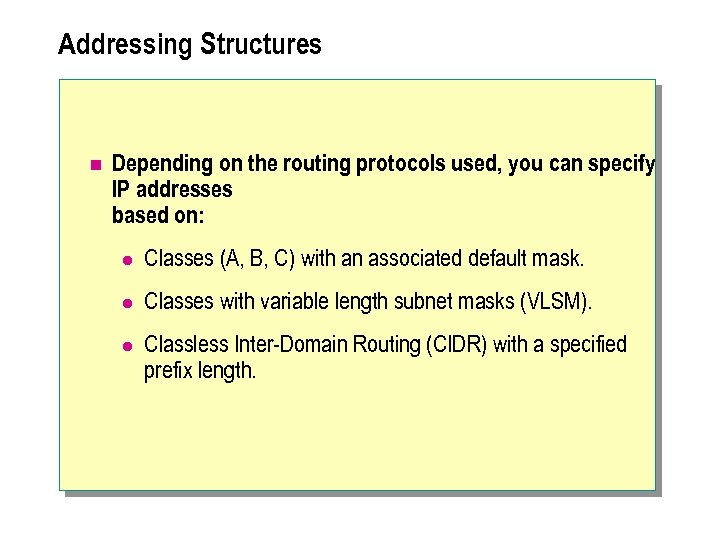 Addressing Structures n Depending on the routing protocols used, you can specify IP addresses based on: l Classes (A, B, C) with an associated default mask. l Classes with variable length subnet masks (VLSM). l Classless Inter-Domain Routing (CIDR) with a specified prefix length.
Addressing Structures n Depending on the routing protocols used, you can specify IP addresses based on: l Classes (A, B, C) with an associated default mask. l Classes with variable length subnet masks (VLSM). l Classless Inter-Domain Routing (CIDR) with a specified prefix length.
 n Class-based networks support a single subnet mask, and are suitable for networks routed by using Routing Information Protocol (RIP) version 1. VLSM and CIDR support multiple masks or prefixes per network. Both VLSM and CIDR require routers that support more advanced interior routing protocols such as RIP version 2 and Open Shortest Path First (OSPF).
n Class-based networks support a single subnet mask, and are suitable for networks routed by using Routing Information Protocol (RIP) version 1. VLSM and CIDR support multiple masks or prefixes per network. Both VLSM and CIDR require routers that support more advanced interior routing protocols such as RIP version 2 and Open Shortest Path First (OSPF).
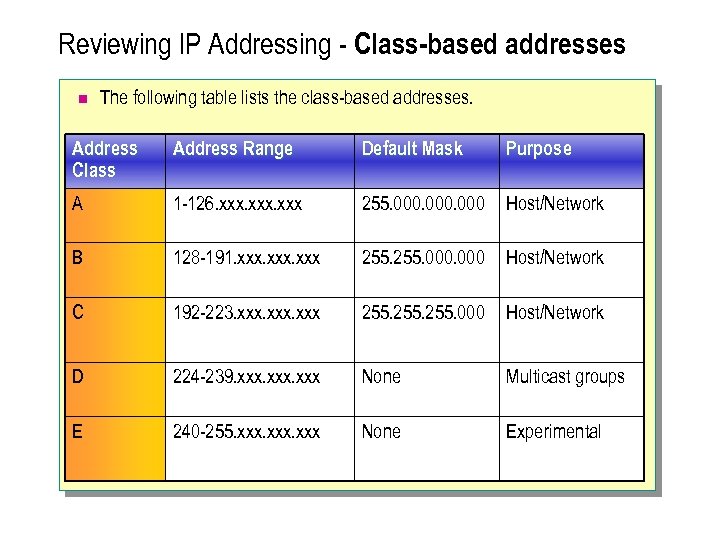 Reviewing IP Addressing - Class-based addresses n The following table lists the class-based addresses. Address Class Address Range Default Mask Purpose A 1 -126. xxx 255. 000 Host/Network B 128 -191. xxx 255. 000 Host/Network C 192 -223. xxx 255. 000 Host/Network D 224 -239. xxx None Multicast groups E 240 -255. xxx None Experimental
Reviewing IP Addressing - Class-based addresses n The following table lists the class-based addresses. Address Class Address Range Default Mask Purpose A 1 -126. xxx 255. 000 Host/Network B 128 -191. xxx 255. 000 Host/Network C 192 -223. xxx 255. 000 Host/Network D 224 -239. xxx None Multicast groups E 240 -255. xxx None Experimental
 Subnet Masks n Class-based IP addresses are split into two portions-the network and host address fields. The subnet mask allows the derivation of network and host fields of the IP address. The network field is required to make routing decisions. n Note: When using class-based addresses and VLSM, you cannot decrease the number of bits that determine the network address below the number that is assigned to the default subnet mask.
Subnet Masks n Class-based IP addresses are split into two portions-the network and host address fields. The subnet mask allows the derivation of network and host fields of the IP address. The network field is required to make routing decisions. n Note: When using class-based addresses and VLSM, you cannot decrease the number of bits that determine the network address below the number that is assigned to the default subnet mask.
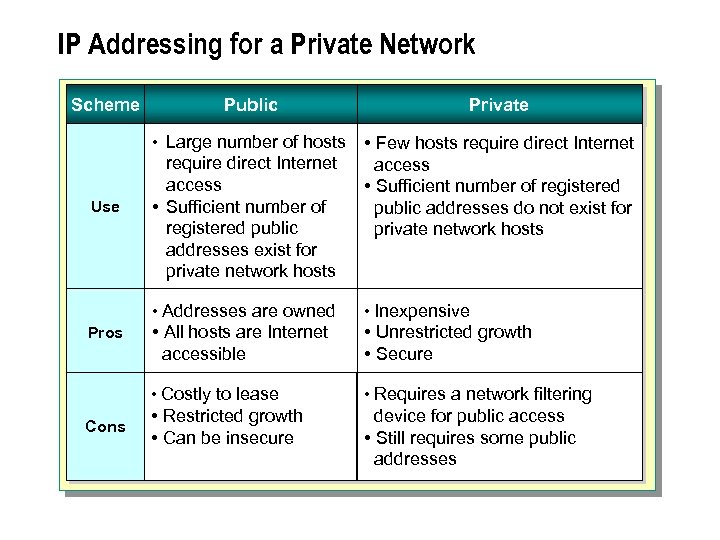 IP Addressing for a Private Network Scheme Private • Large number of hosts Use Public • Few hosts require direct Internet access • Sufficient number of registered public addresses do not exist for private network hosts require direct Internet access • Sufficient number of registered public addresses exist for private network hosts • Addresses are owned Cons • All hosts are Internet accessible • Unrestricted growth • Secure • Costly to lease Pros • Inexpensive • Requires a network filtering • Restricted growth • Can be insecure device for public access • Still requires some public addresses
IP Addressing for a Private Network Scheme Private • Large number of hosts Use Public • Few hosts require direct Internet access • Sufficient number of registered public addresses do not exist for private network hosts require direct Internet access • Sufficient number of registered public addresses exist for private network hosts • Addresses are owned Cons • All hosts are Internet accessible • Unrestricted growth • Secure • Costly to lease Pros • Inexpensive • Requires a network filtering • Restricted growth • Can be insecure device for public access • Still requires some public addresses
 n When designing an IP network, you must determine whether a public or a private address strategy is best for the majority of network hosts. Hosts that are not directly connected to the Internet can be assigned either a public or private address, but if connection to the Internet is required, at least one public IP address is essential.
n When designing an IP network, you must determine whether a public or a private address strategy is best for the majority of network hosts. Hosts that are not directly connected to the Internet can be assigned either a public or private address, but if connection to the Internet is required, at least one public IP address is essential.
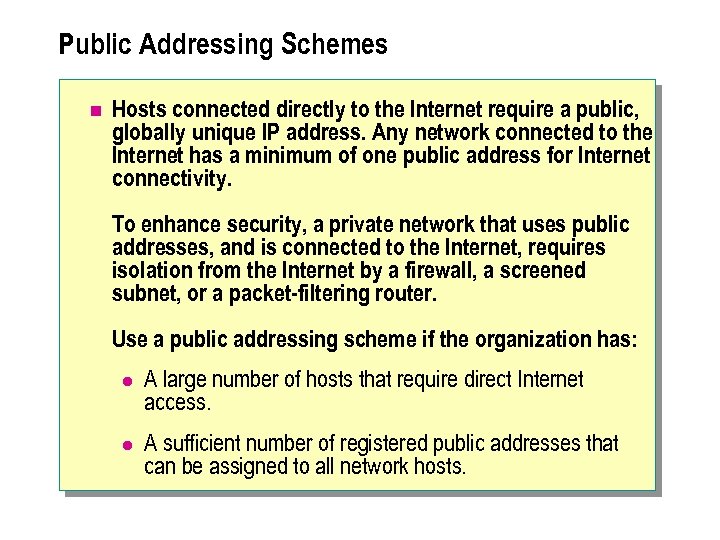 Public Addressing Schemes n Hosts connected directly to the Internet require a public, globally unique IP address. Any network connected to the Internet has a minimum of one public address for Internet connectivity. To enhance security, a private network that uses public addresses, and is connected to the Internet, requires isolation from the Internet by a firewall, a screened subnet, or a packet-filtering router. Use a public addressing scheme if the organization has: l A large number of hosts that require direct Internet access. l A sufficient number of registered public addresses that can be assigned to all network hosts.
Public Addressing Schemes n Hosts connected directly to the Internet require a public, globally unique IP address. Any network connected to the Internet has a minimum of one public address for Internet connectivity. To enhance security, a private network that uses public addresses, and is connected to the Internet, requires isolation from the Internet by a firewall, a screened subnet, or a packet-filtering router. Use a public addressing scheme if the organization has: l A large number of hosts that require direct Internet access. l A sufficient number of registered public addresses that can be assigned to all network hosts.
 n If the network design requires that a large number of IP addresses be accessible from the Internet, you must obtain a suitable range of public IP addresses. You can apply for public IP addresses from an Internet service provider (ISP) or Internet registry. Acquiring a large number of public addresses is expensive to maintain and in most cases unnecessary. n Organizations that use a public addressing scheme must also anticipate their network growth. The total number of addresses available can restrict network growth. After you assign all of the public addresses, you cannot additional devices to the network unless more public addresses are acquired.
n If the network design requires that a large number of IP addresses be accessible from the Internet, you must obtain a suitable range of public IP addresses. You can apply for public IP addresses from an Internet service provider (ISP) or Internet registry. Acquiring a large number of public addresses is expensive to maintain and in most cases unnecessary. n Organizations that use a public addressing scheme must also anticipate their network growth. The total number of addresses available can restrict network growth. After you assign all of the public addresses, you cannot additional devices to the network unless more public addresses are acquired.
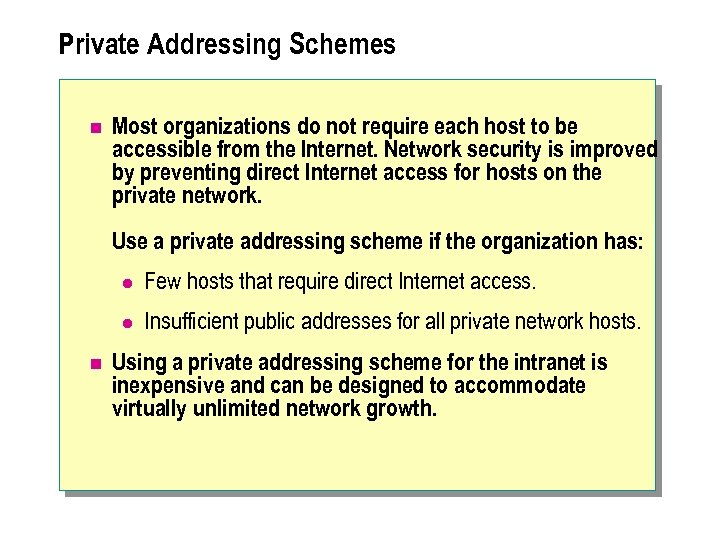 Private Addressing Schemes n Most organizations do not require each host to be accessible from the Internet. Network security is improved by preventing direct Internet access for hosts on the private network. Use a private addressing scheme if the organization has: l l n Few hosts that require direct Internet access. Insufficient public addresses for all private network hosts. Using a private addressing scheme for the intranet is inexpensive and can be designed to accommodate virtually unlimited network growth.
Private Addressing Schemes n Most organizations do not require each host to be accessible from the Internet. Network security is improved by preventing direct Internet access for hosts on the private network. Use a private addressing scheme if the organization has: l l n Few hosts that require direct Internet access. Insufficient public addresses for all private network hosts. Using a private addressing scheme for the intranet is inexpensive and can be designed to accommodate virtually unlimited network growth.
 n In your network design, include a firewall and a network address translation (NAT) device to act as an intermediary between the organization's private network and the Internet. The only IP address directly addressable from the Internet is the external IP address of the NAT device. RFC 1918 lists the IP address ranges that are reserved by the IETF and available for use in private addressing schemes.
n In your network design, include a firewall and a network address translation (NAT) device to act as an intermediary between the organization's private network and the Internet. The only IP address directly addressable from the Internet is the external IP address of the NAT device. RFC 1918 lists the IP address ranges that are reserved by the IETF and available for use in private addressing schemes.
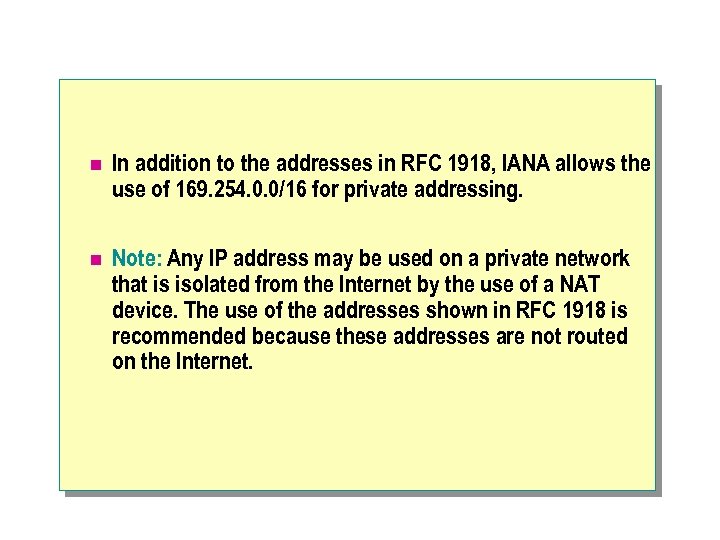 n In addition to the addresses in RFC 1918, IANA allows the use of 169. 254. 0. 0/16 for private addressing. n Note: Any IP address may be used on a private network that is isolated from the Internet by the use of a NAT device. The use of the addresses shown in RFC 1918 is recommended because these addresses are not routed on the Internet.
n In addition to the addresses in RFC 1918, IANA allows the use of 169. 254. 0. 0/16 for private addressing. n Note: Any IP address may be used on a private network that is isolated from the Internet by the use of a NAT device. The use of the addresses shown in RFC 1918 is recommended because these addresses are not routed on the Internet.
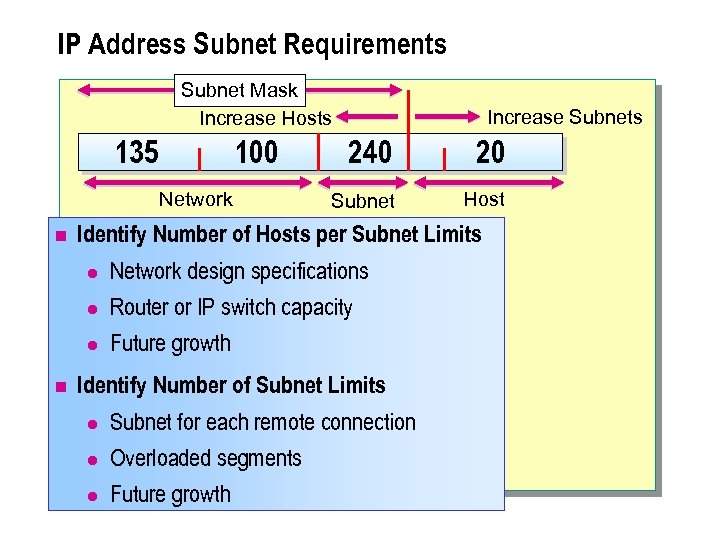 IP Address Subnet Requirements Subnet Mask Increase Hosts 135 100 Network n Increase Subnets 240 20 Subnet Host Identify Number of Hosts per Subnet Limits l Network design specifications Router or IP switch capacity l Future growth l n Identify Number of Subnet Limits l Subnet for each remote connection Overloaded segments l Future growth l
IP Address Subnet Requirements Subnet Mask Increase Hosts 135 100 Network n Increase Subnets 240 20 Subnet Host Identify Number of Hosts per Subnet Limits l Network design specifications Router or IP switch capacity l Future growth l n Identify Number of Subnet Limits l Subnet for each remote connection Overloaded segments l Future growth l
 n An IP-routed network design requires that you examine the interrelationship between the number of hosts per subnet and the number of subnets. An IP-switched network design evaluates only the number of WAN connections. Your network design must optimize the number of subnets and the number of hosts per subnet. In designing an IP network and selecting the masks required to permit routing, you may be limited by: l l The number of logical subnets that you can create. l n The number of physical subnets that exist. The host population on both physical and logical subnets. A good subnet mask design does not restrict expected growth in either the number of subnets or the number of hosts per subnet. You need to adjust the subnet mask to provide for expected host population and network growth.
n An IP-routed network design requires that you examine the interrelationship between the number of hosts per subnet and the number of subnets. An IP-switched network design evaluates only the number of WAN connections. Your network design must optimize the number of subnets and the number of hosts per subnet. In designing an IP network and selecting the masks required to permit routing, you may be limited by: l l The number of logical subnets that you can create. l n The number of physical subnets that exist. The host population on both physical and logical subnets. A good subnet mask design does not restrict expected growth in either the number of subnets or the number of hosts per subnet. You need to adjust the subnet mask to provide for expected host population and network growth.
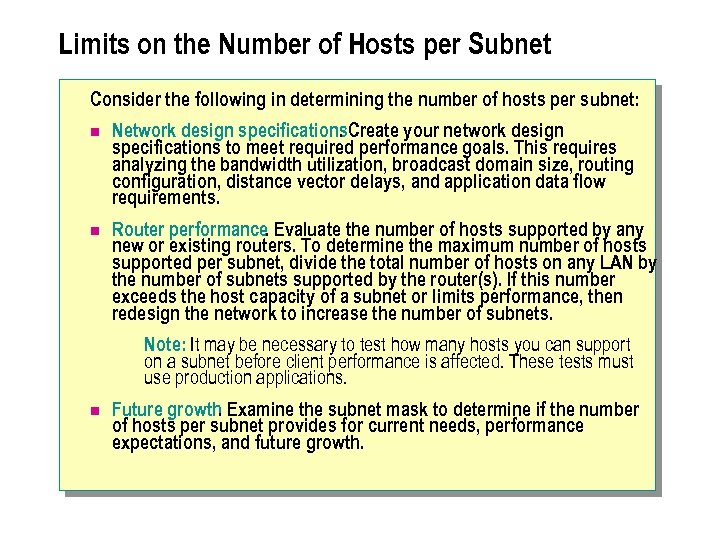 Limits on the Number of Hosts per Subnet Consider the following in determining the number of hosts per subnet: n Network design specifications. Create your network design. specifications to meet required performance goals. This requires analyzing the bandwidth utilization, broadcast domain size, routing configuration, distance vector delays, and application data flow requirements. n Router performance. Evaluate the number of hosts supported by any new or existing routers. To determine the maximum number of hosts supported per subnet, divide the total number of hosts on any LAN by the number of subnets supported by the router(s). If this number exceeds the host capacity of a subnet or limits performance, then redesign the network to increase the number of subnets. Note: It may be necessary to test how many hosts you can support on a subnet before client performance is affected. These tests must use production applications. n Future growth Examine the subnet mask to determine if the number. of hosts per subnet provides for current needs, performance expectations, and future growth.
Limits on the Number of Hosts per Subnet Consider the following in determining the number of hosts per subnet: n Network design specifications. Create your network design. specifications to meet required performance goals. This requires analyzing the bandwidth utilization, broadcast domain size, routing configuration, distance vector delays, and application data flow requirements. n Router performance. Evaluate the number of hosts supported by any new or existing routers. To determine the maximum number of hosts supported per subnet, divide the total number of hosts on any LAN by the number of subnets supported by the router(s). If this number exceeds the host capacity of a subnet or limits performance, then redesign the network to increase the number of subnets. Note: It may be necessary to test how many hosts you can support on a subnet before client performance is affected. These tests must use production applications. n Future growth Examine the subnet mask to determine if the number. of hosts per subnet provides for current needs, performance expectations, and future growth.
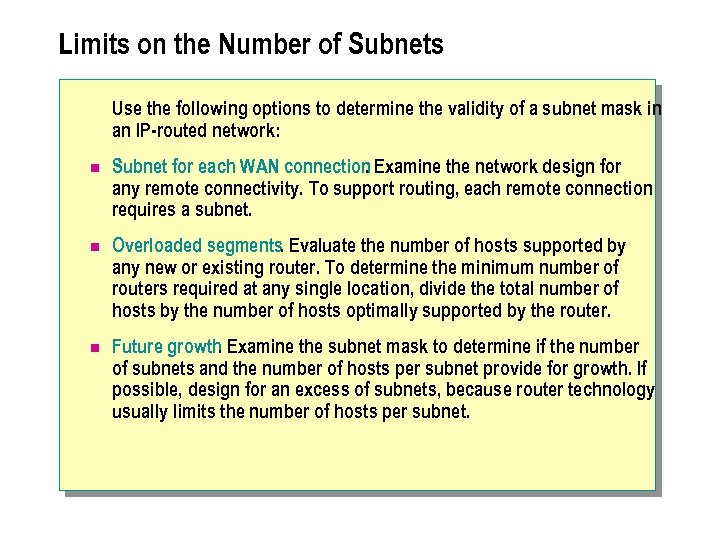 Limits on the Number of Subnets Use the following options to determine the validity of a subnet mask in an IP-routed network: n Subnet for each WAN connection Examine the network design for. any remote connectivity. To support routing, each remote connection requires a subnet. n Overloaded segments. Evaluate the number of hosts supported by any new or existing router. To determine the minimum number of routers required at any single location, divide the total number of hosts by the number of hosts optimally supported by the router. n Future growth Examine the subnet mask to determine if the number. of subnets and the number of hosts per subnet provide for growth. If possible, design for an excess of subnets, because router technology usually limits the number of hosts per subnet.
Limits on the Number of Subnets Use the following options to determine the validity of a subnet mask in an IP-routed network: n Subnet for each WAN connection Examine the network design for. any remote connectivity. To support routing, each remote connection requires a subnet. n Overloaded segments. Evaluate the number of hosts supported by any new or existing router. To determine the minimum number of routers required at any single location, divide the total number of hosts by the number of hosts optimally supported by the router. n Future growth Examine the subnet mask to determine if the number. of subnets and the number of hosts per subnet provide for growth. If possible, design for an excess of subnets, because router technology usually limits the number of hosts per subnet.
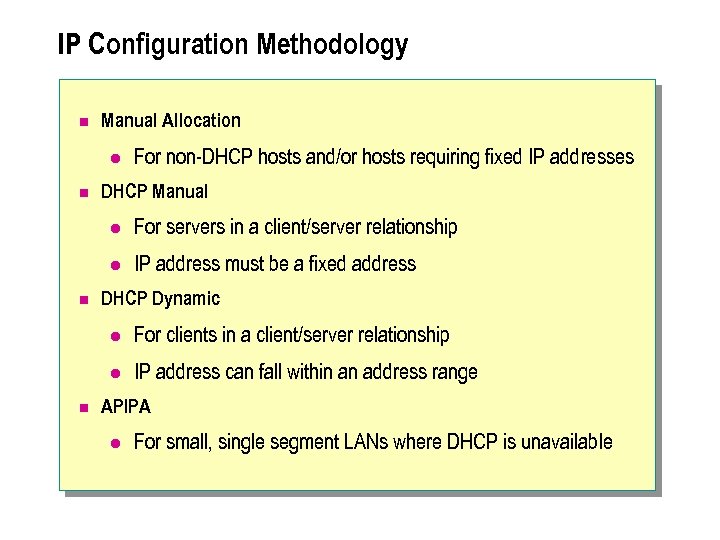 IP Configuration Methodology n Manual Allocation l n For non-DHCP hosts and/or hosts requiring fixed IP addresses DHCP Manual l l n For servers in a client/server relationship IP address must be a fixed address DHCP Dynamic l l n For clients in a client/server relationship IP address can fall within an address range APIPA l For small, single segment LANs where DHCP is unavailable
IP Configuration Methodology n Manual Allocation l n For non-DHCP hosts and/or hosts requiring fixed IP addresses DHCP Manual l l n For servers in a client/server relationship IP address must be a fixed address DHCP Dynamic l l n For clients in a client/server relationship IP address can fall within an address range APIPA l For small, single segment LANs where DHCP is unavailable
 n Windows 2000 automates the process for providing a host IP address by using DHCP manual assignment, DHCP dynamic assignment, or APIPA automatic assignment. Depending upon the type of network device or client in your network, you can use any of these IP configuration methods.
n Windows 2000 automates the process for providing a host IP address by using DHCP manual assignment, DHCP dynamic assignment, or APIPA automatic assignment. Depending upon the type of network device or client in your network, you can use any of these IP configuration methods.
 Manual Allocation n Some hosts on a network, such as special function servers, routers, and NAT devices, require manual configuration of the address, mask, and neighbor or gateway addresses. Server applications that assign IP addresses and resolve symbolic names to IP addresses require a fixed IP address, subnet mask, and default gateway. n Addresses are usually configured manually for DHCP servers, DNS servers, WINS servers, routers, and non. Microsoft hosts that do not support DHCP.
Manual Allocation n Some hosts on a network, such as special function servers, routers, and NAT devices, require manual configuration of the address, mask, and neighbor or gateway addresses. Server applications that assign IP addresses and resolve symbolic names to IP addresses require a fixed IP address, subnet mask, and default gateway. n Addresses are usually configured manually for DHCP servers, DNS servers, WINS servers, routers, and non. Microsoft hosts that do not support DHCP.
 DHCP Manual Method n A system administrator configures the address for a host in the DHCP database. The address is then issued to the host by using the Dynamic Host Configuration Protocol (DHCP). Use the manual configuration method for devices that function primarily as servers in a client/server relationship and require fixed IP addresses.
DHCP Manual Method n A system administrator configures the address for a host in the DHCP database. The address is then issued to the host by using the Dynamic Host Configuration Protocol (DHCP). Use the manual configuration method for devices that function primarily as servers in a client/server relationship and require fixed IP addresses.
 DHCP Dynamic Method n DHCP leases addresses from a scope defined for each subnet. Use dynamic address allocation if the majority of clients on a network support this method and do not require fixed IP addresses. n Note: By setting the lease time to infinite, you can also use DHCP to configure clients with a permanent IP address. Setting the lease time to infinite provides flexibility in allocating permanent addresses where the host is DHCP-enabled.
DHCP Dynamic Method n DHCP leases addresses from a scope defined for each subnet. Use dynamic address allocation if the majority of clients on a network support this method and do not require fixed IP addresses. n Note: By setting the lease time to infinite, you can also use DHCP to configure clients with a permanent IP address. Setting the lease time to infinite provides flexibility in allocating permanent addresses where the host is DHCP-enabled.
 Automatic Private IP Addressing n Automatic Private IP Addressing (APIPA) allows a computer running Windows 2000 in a small, singlesegment network to select an IP address automatically when DHCP is not available. n Note: The APIPA address is selected from the IANAreserved address block 169. 254. 0. 0/16. APIPA does not provide a default gateway IP address to the client and as a result, the client cannot operate in a routed network.
Automatic Private IP Addressing n Automatic Private IP Addressing (APIPA) allows a computer running Windows 2000 in a small, singlesegment network to select an IP address automatically when DHCP is not available. n Note: The APIPA address is selected from the IANAreserved address block 169. 254. 0. 0/16. APIPA does not provide a default gateway IP address to the client and as a result, the client cannot operate in a routed network.
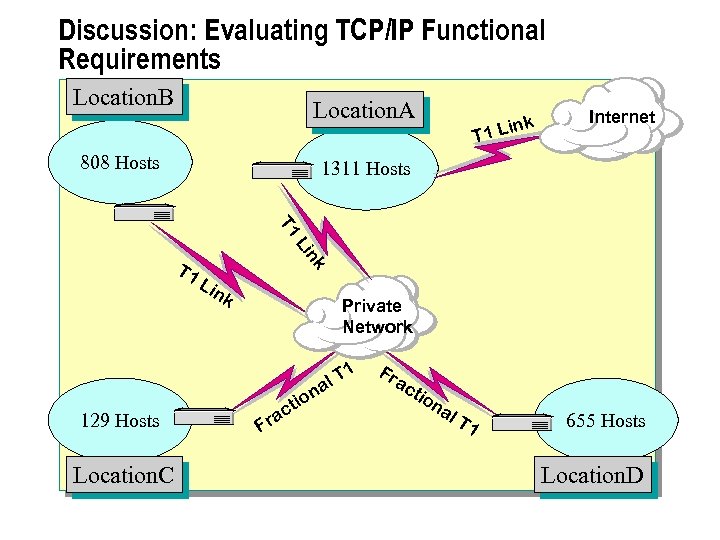 Discussion: Evaluating TCP/IP Functional Requirements Location. B Location. A 808 Hosts ink T 1 L Internet 1311 Hosts T 1 nk Li T 1 L ink Private Network 1 129 Hosts Location. C F ra ct ion T al Fr ac tio na l. T 1 655 Hosts Location. D
Discussion: Evaluating TCP/IP Functional Requirements Location. B Location. A 808 Hosts ink T 1 L Internet 1311 Hosts T 1 nk Li T 1 L ink Private Network 1 129 Hosts Location. C F ra ct ion T al Fr ac tio na l. T 1 655 Hosts Location. D
 n To design a functional TCP/IP solution for connecting networks, you must decide on the number of subnets required for each location, and the number of public and private IP addresses required for the design. The following scenario describes an organization's current network configuration.
n To design a functional TCP/IP solution for connecting networks, you must decide on the number of subnets required for each location, and the number of public and private IP addresses required for the design. The following scenario describes an organization's current network configuration.
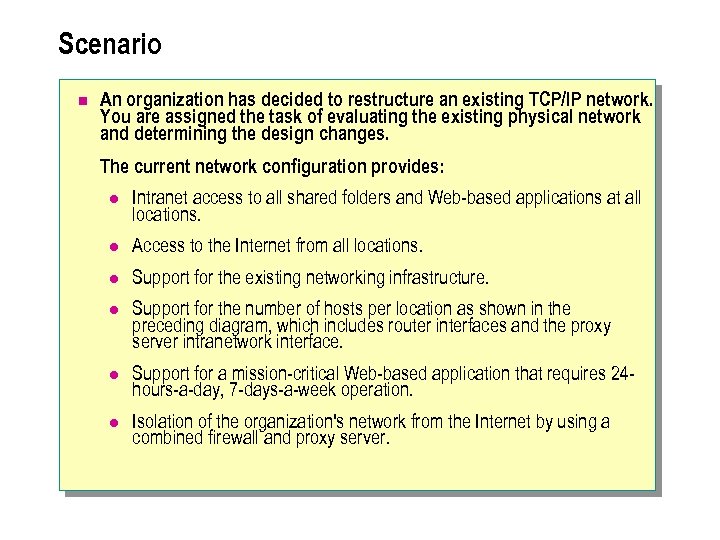 Scenario n An organization has decided to restructure an existing TCP/IP network. You are assigned the task of evaluating the existing physical network and determining the design changes. The current network configuration provides: l Intranet access to all shared folders and Web-based applications at all locations. l Access to the Internet from all locations. l Support for the existing networking infrastructure. l Support for the number of hosts per location as shown in the preceding diagram, which includes router interfaces and the proxy server intranetwork interface. l Support for a mission-critical Web-based application that requires 24 hours-a-day, 7 -days-a-week operation. l Isolation of the organization's network from the Internet by using a combined firewall and proxy server.
Scenario n An organization has decided to restructure an existing TCP/IP network. You are assigned the task of evaluating the existing physical network and determining the design changes. The current network configuration provides: l Intranet access to all shared folders and Web-based applications at all locations. l Access to the Internet from all locations. l Support for the existing networking infrastructure. l Support for the number of hosts per location as shown in the preceding diagram, which includes router interfaces and the proxy server intranetwork interface. l Support for a mission-critical Web-based application that requires 24 hours-a-day, 7 -days-a-week operation. l Isolation of the organization's network from the Internet by using a combined firewall and proxy server.
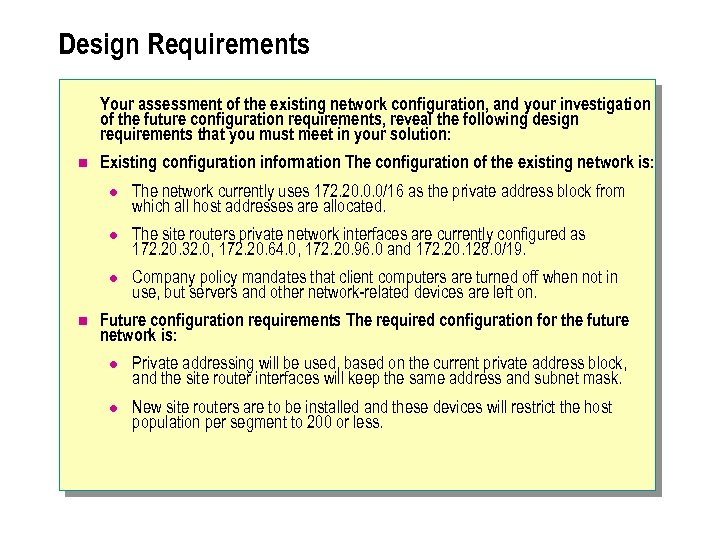 Design Requirements Your assessment of the existing network configuration, and your investigation of the future configuration requirements, reveal the following design requirements that you must meet in your solution: n Existing configuration information The configuration of the existing network is: l l The site routers private network interfaces are currently configured as 172. 20. 32. 0, 172. 20. 64. 0, 172. 20. 96. 0 and 172. 20. 128. 0/19. l n The network currently uses 172. 20. 0. 0/16 as the private address block from which all host addresses are allocated. Company policy mandates that client computers are turned off when not in use, but servers and other network-related devices are left on. Future configuration requirements The required configuration for the future network is: l Private addressing will be used, based on the current private address block, and the site router interfaces will keep the same address and subnet mask. l New site routers are to be installed and these devices will restrict the host population per segment to 200 or less.
Design Requirements Your assessment of the existing network configuration, and your investigation of the future configuration requirements, reveal the following design requirements that you must meet in your solution: n Existing configuration information The configuration of the existing network is: l l The site routers private network interfaces are currently configured as 172. 20. 32. 0, 172. 20. 64. 0, 172. 20. 96. 0 and 172. 20. 128. 0/19. l n The network currently uses 172. 20. 0. 0/16 as the private address block from which all host addresses are allocated. Company policy mandates that client computers are turned off when not in use, but servers and other network-related devices are left on. Future configuration requirements The required configuration for the future network is: l Private addressing will be used, based on the current private address block, and the site router interfaces will keep the same address and subnet mask. l New site routers are to be installed and these devices will restrict the host population per segment to 200 or less.
 u. Securing a TCP/IP Solution n Protecting IP Traffic with Filters n Protecting Data with. IPSec n IPSec Protection Levels n IPSec Internet Key Exchange
u. Securing a TCP/IP Solution n Protecting IP Traffic with Filters n Protecting Data with. IPSec n IPSec Protection Levels n IPSec Internet Key Exchange
 n The security of a network design is measured by the ability of the design to prevent unauthorized access to data transmission and intranet-based resources. TCP/IP incorporates security features that provide protection of the TCP/IP data as it is sent on the network, along with configuration of the types of local host traffic that are processed.
n The security of a network design is measured by the ability of the design to prevent unauthorized access to data transmission and intranet-based resources. TCP/IP incorporates security features that provide protection of the TCP/IP data as it is sent on the network, along with configuration of the types of local host traffic that are processed.
 You can secure data traffic by: n Filtering IP packets within the TCP/IP protocol. n Encrypting data with IPSec. n Authenticating and encrypting data with the IPSec protection levels. n Using the security keys negotiated by the IPSec Internet Key Exchange (IKE).
You can secure data traffic by: n Filtering IP packets within the TCP/IP protocol. n Encrypting data with IPSec. n Authenticating and encrypting data with the IPSec protection levels. n Using the security keys negotiated by the IPSec Internet Key Exchange (IKE).
 Protecting IP Traffic with Filters n Control Traffic to Dedicated Servers n Block All Inbound Traffic Unless Specified n Provide Filtering at the Application Layer
Protecting IP Traffic with Filters n Control Traffic to Dedicated Servers n Block All Inbound Traffic Unless Specified n Provide Filtering at the Application Layer
 n Minimizing the protocols and ports exposed on a host can reduce the risk of unauthorized access. By using a firewall, you can filter IP traffic to minimize the risks. This type of filtering may be difficult to manage, particularly if many hosts have different filtering requirements. The Windows 2000 implementation of TCP/IP supports application layer filtering of IP traffic by allowing you to set filters on a host-by-host basis. TCP/IP filtering blocks the delivery of any IP packets that do not conform to the preset criteria. You can use TCP/IP filtering for dedicated servers that provide services on well -known protocols, TCP ports, and User Datagram Protocol (UDP) ports. TCP/IP filtering does not apply to routed traffic that is forwarded between interfaces.
n Minimizing the protocols and ports exposed on a host can reduce the risk of unauthorized access. By using a firewall, you can filter IP traffic to minimize the risks. This type of filtering may be difficult to manage, particularly if many hosts have different filtering requirements. The Windows 2000 implementation of TCP/IP supports application layer filtering of IP traffic by allowing you to set filters on a host-by-host basis. TCP/IP filtering blocks the delivery of any IP packets that do not conform to the preset criteria. You can use TCP/IP filtering for dedicated servers that provide services on well -known protocols, TCP ports, and User Datagram Protocol (UDP) ports. TCP/IP filtering does not apply to routed traffic that is forwarded between interfaces.
 Include TCP/IP filtering in your network design to: n Control traffic to dedicated servers. n Block all inbound trafficexcept that which you specifically list. n Provide filtering at the application layer. Caution: For most situations, you permit the acceptance of all IP traffic. Evaluate the effect of any enabled TCP/IP filters to ensure proper computer operation. It is not recommended to enable filtering because it may restrict the operation of essential services.
Include TCP/IP filtering in your network design to: n Control traffic to dedicated servers. n Block all inbound trafficexcept that which you specifically list. n Provide filtering at the application layer. Caution: For most situations, you permit the acceptance of all IP traffic. Evaluate the effect of any enabled TCP/IP filters to ensure proper computer operation. It is not recommended to enable filtering because it may restrict the operation of essential services.
 You can filter IP packets based on the following criteria: n TCP port number. n UDP port number. n IP protocol type (except for TCP, UDP, ICMP, IGMP or IPSec).
You can filter IP packets based on the following criteria: n TCP port number. n UDP port number. n IP protocol type (except for TCP, UDP, ICMP, IGMP or IPSec).
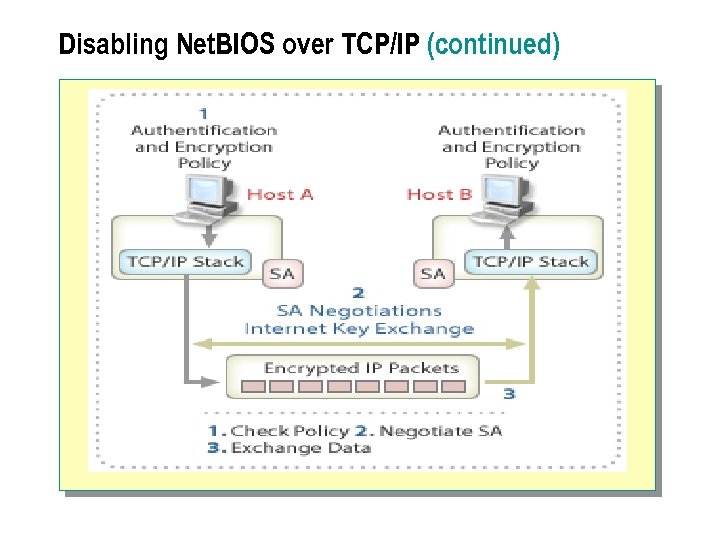
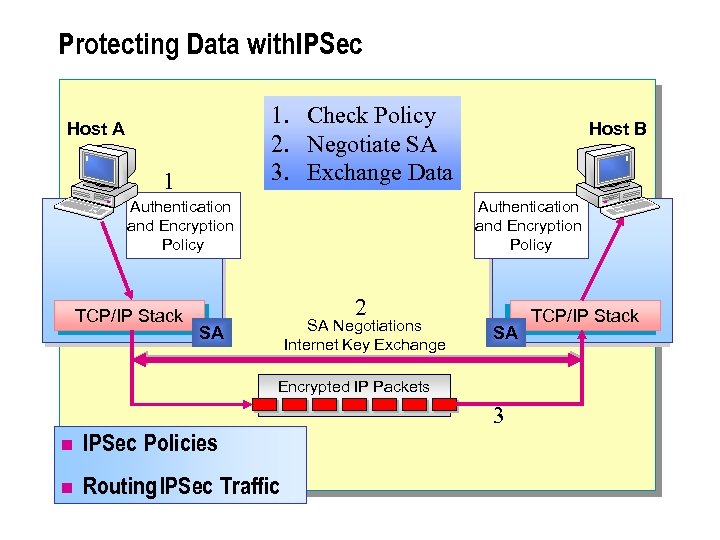 Protecting Data with. IPSec 1. Check Policy 2. Negotiate SA 3. Exchange Data Host A 1 Authentication and Encryption Policy TCP/IP Stack Host B Authentication and Encryption Policy 2 SA Negotiations Internet Key Exchange SA SA Encrypted IP Packets 3 n IPSec Policies n Routing IPSec Traffic TCP/IP Stack
Protecting Data with. IPSec 1. Check Policy 2. Negotiate SA 3. Exchange Data Host A 1 Authentication and Encryption Policy TCP/IP Stack Host B Authentication and Encryption Policy 2 SA Negotiations Internet Key Exchange SA SA Encrypted IP Packets 3 n IPSec Policies n Routing IPSec Traffic TCP/IP Stack
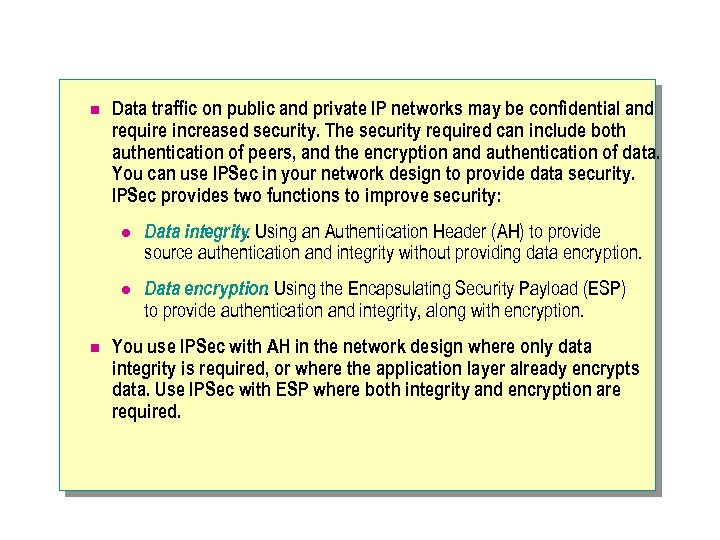 n Data traffic on public and private IP networks may be confidential and require increased security. The security required can include both authentication of peers, and the encryption and authentication of data. You can use IPSec in your network design to provide data security. IPSec provides two functions to improve security: l l n Data integrity. Using an Authentication Header (AH) to provide source authentication and integrity without providing data encryption. Data encryption. Using the Encapsulating Security Payload (ESP) to provide authentication and integrity, along with encryption. You use IPSec with AH in the network design where only data integrity is required, or where the application layer already encrypts data. Use IPSec with ESP where both integrity and encryption are required.
n Data traffic on public and private IP networks may be confidential and require increased security. The security required can include both authentication of peers, and the encryption and authentication of data. You can use IPSec in your network design to provide data security. IPSec provides two functions to improve security: l l n Data integrity. Using an Authentication Header (AH) to provide source authentication and integrity without providing data encryption. Data encryption. Using the Encapsulating Security Payload (ESP) to provide authentication and integrity, along with encryption. You use IPSec with AH in the network design where only data integrity is required, or where the application layer already encrypts data. Use IPSec with ESP where both integrity and encryption are required.
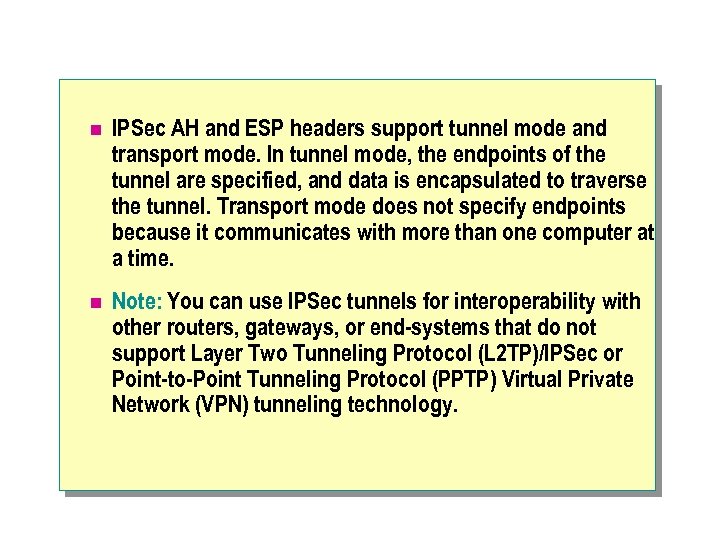 n IPSec AH and ESP headers support tunnel mode and transport mode. In tunnel mode, the endpoints of the tunnel are specified, and data is encapsulated to traverse the tunnel. Transport mode does not specify endpoints because it communicates with more than one computer at a time. n Note: You can use IPSec tunnels for interoperability with other routers, gateways, or end-systems that do not support Layer Two Tunneling Protocol (L 2 TP)/IPSec or Point-to-Point Tunneling Protocol (PPTP) Virtual Private Network (VPN) tunneling technology.
n IPSec AH and ESP headers support tunnel mode and transport mode. In tunnel mode, the endpoints of the tunnel are specified, and data is encapsulated to traverse the tunnel. Transport mode does not specify endpoints because it communicates with more than one computer at a time. n Note: You can use IPSec tunnels for interoperability with other routers, gateways, or end-systems that do not support Layer Two Tunneling Protocol (L 2 TP)/IPSec or Point-to-Point Tunneling Protocol (PPTP) Virtual Private Network (VPN) tunneling technology.
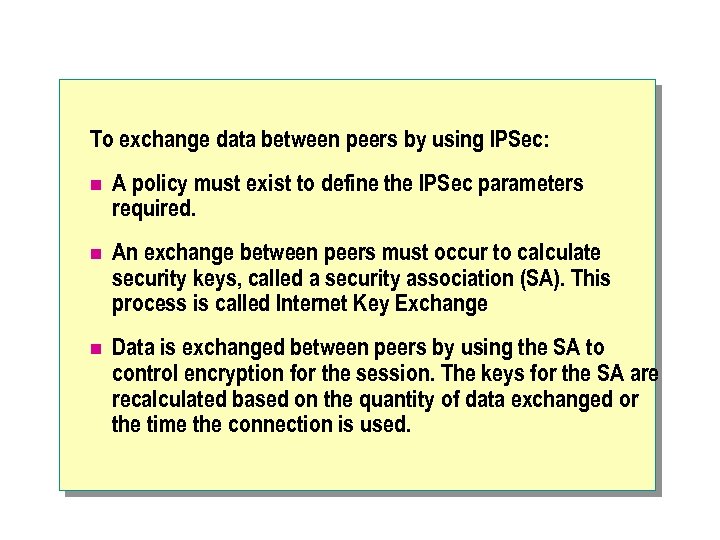 To exchange data between peers by using IPSec: n A policy must exist to define the IPSec parameters required. n An exchange between peers must occur to calculate security keys, called a security association (SA). This process is called Internet Key Exchange n Data is exchanged between peers by using the SA to control encryption for the session. The keys for the SA are recalculated based on the quantity of data exchanged or the time the connection is used.
To exchange data between peers by using IPSec: n A policy must exist to define the IPSec parameters required. n An exchange between peers must occur to calculate security keys, called a security association (SA). This process is called Internet Key Exchange n Data is exchanged between peers by using the SA to control encryption for the session. The keys for the SA are recalculated based on the quantity of data exchanged or the time the connection is used.
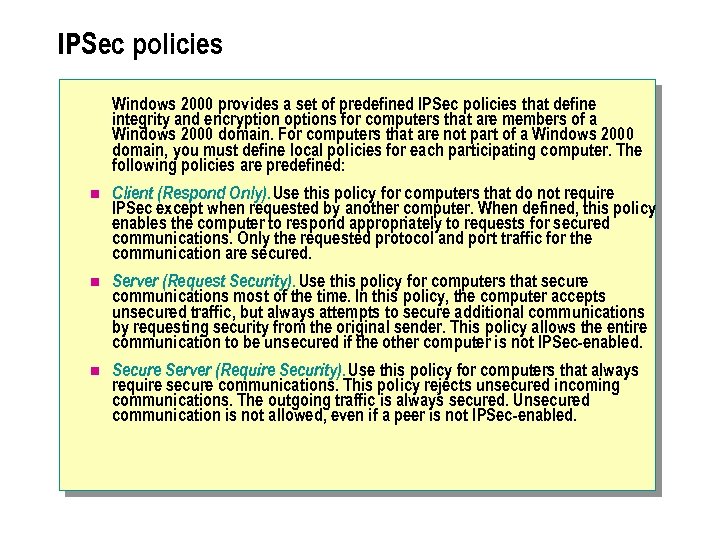 IPSec policies Windows 2000 provides a set of predefined IPSec policies that define integrity and encryption options for computers that are members of a Windows 2000 domain. For computers that are not part of a Windows 2000 domain, you must define local policies for each participating computer. The following policies are predefined: n Client (Respond Only). Use this policy for computers that do not require IPSec except when requested by another computer. When defined, this policy enables the computer to respond appropriately to requests for secured communications. Only the requested protocol and port traffic for the communication are secured. n Server (Request Security). Use this policy for computers that secure communications most of the time. In this policy, the computer accepts unsecured traffic, but always attempts to secure additional communications by requesting security from the original sender. This policy allows the entire communication to be unsecured if the other computer is not IPSec-enabled. n Secure Server (Require Security). Use this policy for computers that always require secure communications. This policy rejects unsecured incoming communications. The outgoing traffic is always secured. Unsecured communication is not allowed, even if a peer is not IPSec-enabled.
IPSec policies Windows 2000 provides a set of predefined IPSec policies that define integrity and encryption options for computers that are members of a Windows 2000 domain. For computers that are not part of a Windows 2000 domain, you must define local policies for each participating computer. The following policies are predefined: n Client (Respond Only). Use this policy for computers that do not require IPSec except when requested by another computer. When defined, this policy enables the computer to respond appropriately to requests for secured communications. Only the requested protocol and port traffic for the communication are secured. n Server (Request Security). Use this policy for computers that secure communications most of the time. In this policy, the computer accepts unsecured traffic, but always attempts to secure additional communications by requesting security from the original sender. This policy allows the entire communication to be unsecured if the other computer is not IPSec-enabled. n Secure Server (Require Security). Use this policy for computers that always require secure communications. This policy rejects unsecured incoming communications. The outgoing traffic is always secured. Unsecured communication is not allowed, even if a peer is not IPSec-enabled.
 n Only one of the policies may be assigned on a given computer, so your security plan must specify the required policy or define a custom policy. You can customize the predefined policies to meet the given security requirements.
n Only one of the policies may be assigned on a given computer, so your security plan must specify the required policy or define a custom policy. You can customize the predefined policies to meet the given security requirements.
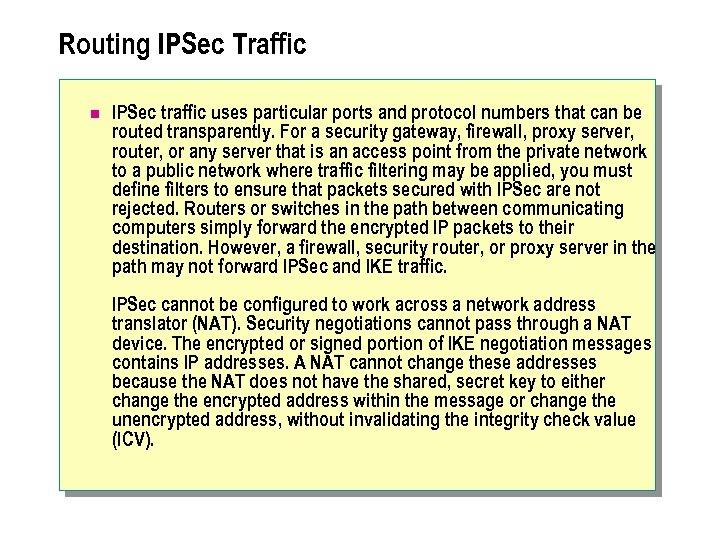 Routing IPSec Traffic n IPSec traffic uses particular ports and protocol numbers that can be routed transparently. For a security gateway, firewall, proxy server, router, or any server that is an access point from the private network to a public network where traffic filtering may be applied, you must define filters to ensure that packets secured with IPSec are not rejected. Routers or switches in the path between communicating computers simply forward the encrypted IP packets to their destination. However, a firewall, security router, or proxy server in the path may not forward IPSec and IKE traffic. IPSec cannot be configured to work across a network address translator (NAT). Security negotiations cannot pass through a NAT device. The encrypted or signed portion of IKE negotiation messages contains IP addresses. A NAT cannot change these addresses because the NAT does not have the shared, secret key to either change the encrypted address within the message or change the unencrypted address, without invalidating the integrity check value (ICV).
Routing IPSec Traffic n IPSec traffic uses particular ports and protocol numbers that can be routed transparently. For a security gateway, firewall, proxy server, router, or any server that is an access point from the private network to a public network where traffic filtering may be applied, you must define filters to ensure that packets secured with IPSec are not rejected. Routers or switches in the path between communicating computers simply forward the encrypted IP packets to their destination. However, a firewall, security router, or proxy server in the path may not forward IPSec and IKE traffic. IPSec cannot be configured to work across a network address translator (NAT). Security negotiations cannot pass through a NAT device. The encrypted or signed portion of IKE negotiation messages contains IP addresses. A NAT cannot change these addresses because the NAT does not have the shared, secret key to either change the encrypted address within the message or change the unencrypted address, without invalidating the integrity check value (ICV).
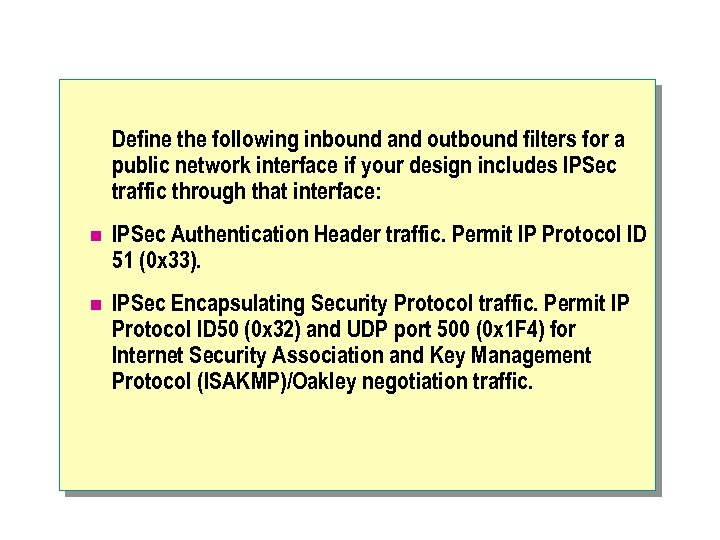 Define the following inbound and outbound filters for a public network interface if your design includes IPSec traffic through that interface: n IPSec Authentication Header traffic. Permit IP Protocol ID 51 (0 x 33). n IPSec Encapsulating Security Protocol traffic. Permit IP Protocol ID 50 (0 x 32) and UDP port 500 (0 x 1 F 4) for Internet Security Association and Key Management Protocol (ISAKMP)/Oakley negotiation traffic.
Define the following inbound and outbound filters for a public network interface if your design includes IPSec traffic through that interface: n IPSec Authentication Header traffic. Permit IP Protocol ID 51 (0 x 33). n IPSec Encapsulating Security Protocol traffic. Permit IP Protocol ID 50 (0 x 32) and UDP port 500 (0 x 1 F 4) for Internet Security Association and Key Management Protocol (ISAKMP)/Oakley negotiation traffic.
 IPSec Protection Levels n IPSec Authentication Protocols n IPSec Encryption Algorithms n Diffie-Hellman Groups
IPSec Protection Levels n IPSec Authentication Protocols n IPSec Encryption Algorithms n Diffie-Hellman Groups
 n If there is a risk of unauthorized interception, you must use integrity/HASH algorithms and data encryption to protect the data that is sent between peers. The options available for IPSec allow definition of the integrity/HASH algorithms and encryption protocols that are used to provide data protection.
n If there is a risk of unauthorized interception, you must use integrity/HASH algorithms and data encryption to protect the data that is sent between peers. The options available for IPSec allow definition of the integrity/HASH algorithms and encryption protocols that are used to provide data protection.
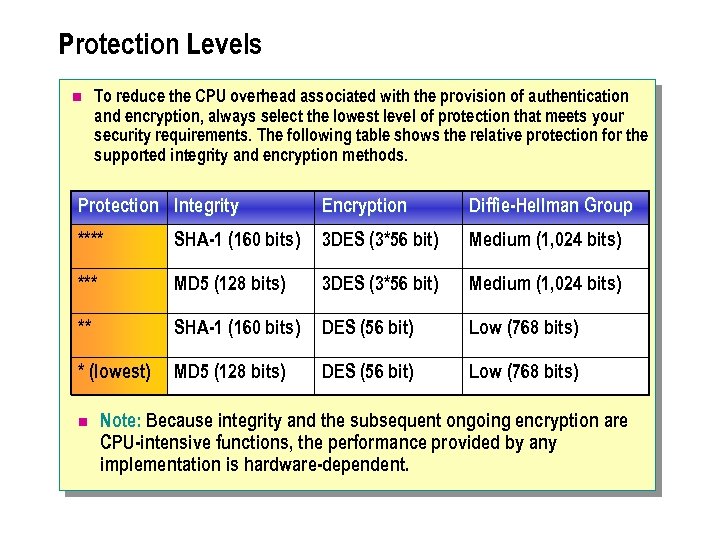 Protection Levels n To reduce the CPU overhead associated with the provision of authentication and encryption, always select the lowest level of protection that meets your security requirements. The following table shows the relative protection for the supported integrity and encryption methods. Protection Integrity Encryption Diffie-Hellman Group **** SHA-1 (160 bits) 3 DES (3*56 bit) Medium (1, 024 bits) *** MD 5 (128 bits) 3 DES (3*56 bit) Medium (1, 024 bits) ** SHA-1 (160 bits) DES (56 bit) Low (768 bits) * (lowest) MD 5 (128 bits) DES (56 bit) Low (768 bits) n Note: Because integrity and the subsequent ongoing encryption are CPU-intensive functions, the performance provided by any implementation is hardware-dependent.
Protection Levels n To reduce the CPU overhead associated with the provision of authentication and encryption, always select the lowest level of protection that meets your security requirements. The following table shows the relative protection for the supported integrity and encryption methods. Protection Integrity Encryption Diffie-Hellman Group **** SHA-1 (160 bits) 3 DES (3*56 bit) Medium (1, 024 bits) *** MD 5 (128 bits) 3 DES (3*56 bit) Medium (1, 024 bits) ** SHA-1 (160 bits) DES (56 bit) Low (768 bits) * (lowest) MD 5 (128 bits) DES (56 bit) Low (768 bits) n Note: Because integrity and the subsequent ongoing encryption are CPU-intensive functions, the performance provided by any implementation is hardware-dependent.
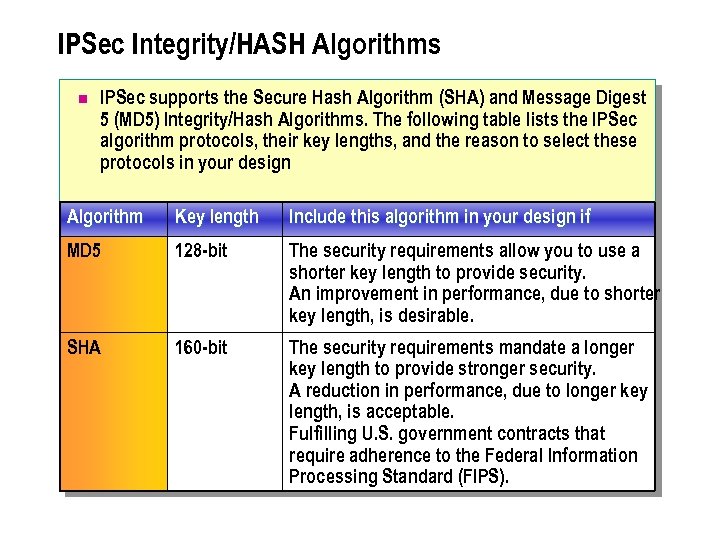 IPSec Integrity/HASH Algorithms n IPSec supports the Secure Hash Algorithm (SHA) and Message Digest 5 (MD 5) Integrity/Hash Algorithms. The following table lists the IPSec algorithm protocols, their key lengths, and the reason to select these protocols in your design Algorithm Key length Include this algorithm in your design if MD 5 128 -bit The security requirements allow you to use a shorter key length to provide security. An improvement in performance, due to shorter key length, is desirable. SHA 160 -bit The security requirements mandate a longer key length to provide stronger security. A reduction in performance, due to longer key length, is acceptable. Fulfilling U. S. government contracts that require adherence to the Federal Information Processing Standard (FIPS).
IPSec Integrity/HASH Algorithms n IPSec supports the Secure Hash Algorithm (SHA) and Message Digest 5 (MD 5) Integrity/Hash Algorithms. The following table lists the IPSec algorithm protocols, their key lengths, and the reason to select these protocols in your design Algorithm Key length Include this algorithm in your design if MD 5 128 -bit The security requirements allow you to use a shorter key length to provide security. An improvement in performance, due to shorter key length, is desirable. SHA 160 -bit The security requirements mandate a longer key length to provide stronger security. A reduction in performance, due to longer key length, is acceptable. Fulfilling U. S. government contracts that require adherence to the Federal Information Processing Standard (FIPS).
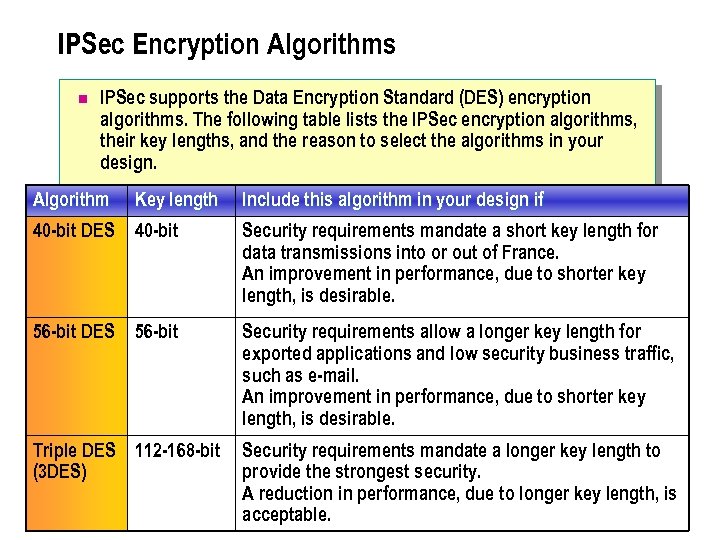 IPSec Encryption Algorithms n IPSec supports the Data Encryption Standard (DES) encryption algorithms. The following table lists the IPSec encryption algorithms, their key lengths, and the reason to select the algorithms in your design. Algorithm Key length Include this algorithm in your design if 40 -bit DES 40 -bit Security requirements mandate a short key length for data transmissions into or out of France. An improvement in performance, due to shorter key length, is desirable. 56 -bit DES 56 -bit Security requirements allow a longer key length for exported applications and low security business traffic, such as e-mail. An improvement in performance, due to shorter key length, is desirable. Triple DES 112 -168 -bit (3 DES) Security requirements mandate a longer key length to provide the strongest security. A reduction in performance, due to longer key length, is acceptable.
IPSec Encryption Algorithms n IPSec supports the Data Encryption Standard (DES) encryption algorithms. The following table lists the IPSec encryption algorithms, their key lengths, and the reason to select the algorithms in your design. Algorithm Key length Include this algorithm in your design if 40 -bit DES 40 -bit Security requirements mandate a short key length for data transmissions into or out of France. An improvement in performance, due to shorter key length, is desirable. 56 -bit DES 56 -bit Security requirements allow a longer key length for exported applications and low security business traffic, such as e-mail. An improvement in performance, due to shorter key length, is desirable. Triple DES 112 -168 -bit (3 DES) Security requirements mandate a longer key length to provide the strongest security. A reduction in performance, due to longer key length, is acceptable.
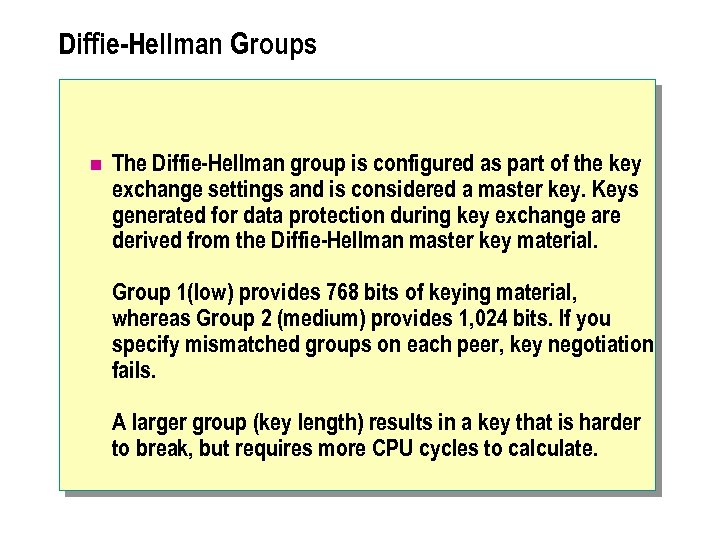 Diffie-Hellman Groups n The Diffie-Hellman group is configured as part of the key exchange settings and is considered a master key. Keys generated for data protection during key exchange are derived from the Diffie-Hellman master key material. Group 1(low) provides 768 bits of keying material, whereas Group 2 (medium) provides 1, 024 bits. If you specify mismatched groups on each peer, key negotiation fails. A larger group (key length) results in a key that is harder to break, but requires more CPU cycles to calculate.
Diffie-Hellman Groups n The Diffie-Hellman group is configured as part of the key exchange settings and is considered a master key. Keys generated for data protection during key exchange are derived from the Diffie-Hellman master key material. Group 1(low) provides 768 bits of keying material, whereas Group 2 (medium) provides 1, 024 bits. If you specify mismatched groups on each peer, key negotiation fails. A larger group (key length) results in a key that is harder to break, but requires more CPU cycles to calculate.
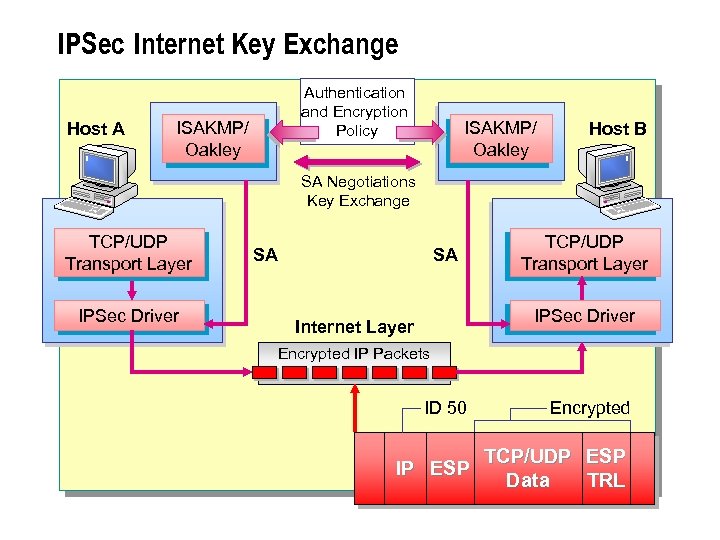 IPSec Internet Key Exchange Host A Authentication and Encryption Policy ISAKMP/ Oakley Host B SA Negotiations Key Exchange TCP/UDP Transport Layer IPSec Driver SA SA TCP/UDP Transport Layer IPSec Driver Internet Layer Encrypted IP Packets ID 50 IP ESP Encrypted TCP/UDP Data ESP TRL
IPSec Internet Key Exchange Host A Authentication and Encryption Policy ISAKMP/ Oakley Host B SA Negotiations Key Exchange TCP/UDP Transport Layer IPSec Driver SA SA TCP/UDP Transport Layer IPSec Driver Internet Layer Encrypted IP Packets ID 50 IP ESP Encrypted TCP/UDP Data ESP TRL
 n The exchange of authenticated and encrypted data between peers that use IPSec requires negotiation of the security algorithms. The negotiation between peers is a two-phase process called Internet Key Exchange. IPSec Internet Key Exchange
n The exchange of authenticated and encrypted data between peers that use IPSec requires negotiation of the security algorithms. The negotiation between peers is a two-phase process called Internet Key Exchange. IPSec Internet Key Exchange
 n With IPSec, only the sender and recipient know the negotiated security keys when a connection is established. IKE is the process used to calculate the security keys; it uses two IETF protocols, the Internet Security Association and Key Management Protocol (ISAKMP) and the Oakley key generation protocol. ISAKMP centralizes security association (SA) management, thereby reducing the connection time. Oakley generates and manages the authenticated keys used to secure the information.
n With IPSec, only the sender and recipient know the negotiated security keys when a connection is established. IKE is the process used to calculate the security keys; it uses two IETF protocols, the Internet Security Association and Key Management Protocol (ISAKMP) and the Oakley key generation protocol. ISAKMP centralizes security association (SA) management, thereby reducing the connection time. Oakley generates and manages the authenticated keys used to secure the information.
 IPSec communication between hosts requires that SAs be negotiated between peers. You can use the following peer authentication methods with IPSec: n The Kerberos version 5 security protocol. This is the default. authentication technology used for any clients running the Kerberos V 5 protocol that are members of a trusted domain. n Digital Certificates These are used for authentication between. computers that cannot run the Kerberos V 5 security protocol. Examples of such interaction include Internet access, remote access to corporate resources, and communication with external business partners. n Preshared keys. This is a shared, secret key, previously agreed upon by two users. Both parties must manually configure IPSec to use this preshared key. This is a simple method for authenticating computers that is not based on Windows 2000 -based stand-alone computers, or any clients not running the Kerberos V 5 protocol.
IPSec communication between hosts requires that SAs be negotiated between peers. You can use the following peer authentication methods with IPSec: n The Kerberos version 5 security protocol. This is the default. authentication technology used for any clients running the Kerberos V 5 protocol that are members of a trusted domain. n Digital Certificates These are used for authentication between. computers that cannot run the Kerberos V 5 security protocol. Examples of such interaction include Internet access, remote access to corporate resources, and communication with external business partners. n Preshared keys. This is a shared, secret key, previously agreed upon by two users. Both parties must manually configure IPSec to use this preshared key. This is a simple method for authenticating computers that is not based on Windows 2000 -based stand-alone computers, or any clients not running the Kerberos V 5 protocol.
 n Select Kerberos V 5 if your design includes the Active Directory™ directory service or supports the Kerberos V 5 protocol. Select certificate and shared key methods to use IPSec within untrusted domains and when Kerberos V 5 cannot be supported. Implementing IPSec by using a shared key can be a security risk when transferring keys. Kerberos V 5 and digital certificates are recommended for best security practice. n Note: RFC 2401 provides an architectural overview of IPSec and the applicable RFCs required in implementation. These applicable RFCs provide detailed information on the available authentication options.
n Select Kerberos V 5 if your design includes the Active Directory™ directory service or supports the Kerberos V 5 protocol. Select certificate and shared key methods to use IPSec within untrusted domains and when Kerberos V 5 cannot be supported. Implementing IPSec by using a shared key can be a security risk when transferring keys. Kerberos V 5 and digital certificates are recommended for best security practice. n Note: RFC 2401 provides an architectural overview of IPSec and the applicable RFCs required in implementation. These applicable RFCs provide detailed information on the available authentication options.
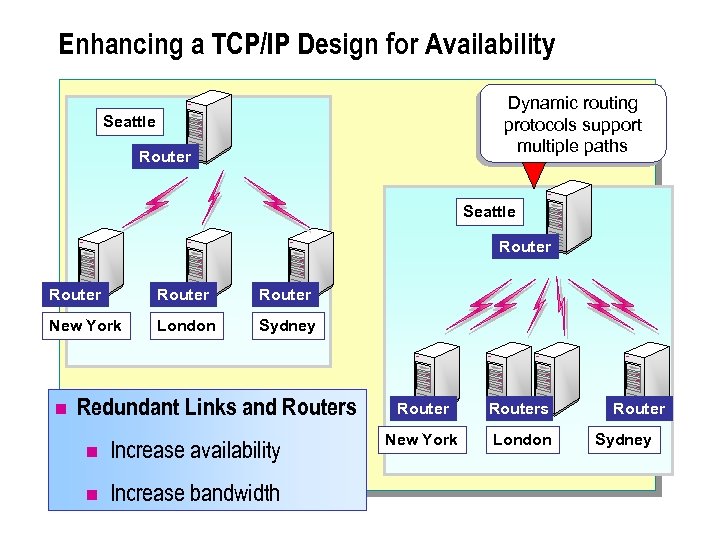 Enhancing a TCP/IP Design for Availability Dynamic routing protocols support multiple paths Seattle Router Router New York London Sydney n Redundant Links and Routers n Increase availability n Increase bandwidth Routers New York London Router Sydney
Enhancing a TCP/IP Design for Availability Dynamic routing protocols support multiple paths Seattle Router Router New York London Sydney n Redundant Links and Routers n Increase availability n Increase bandwidth Routers New York London Router Sydney
 n The availability of a TCP/IP network design is measured by the percentage of time users are able to transfer data by using the TCP/IP network infrastructure. To improve the availability of a routed network, your design must include redundant links and routers between locations where the highest availability is required. The inclusion of redundant routed paths in your design can improve both the availability and performance (bandwidth) of the network. n You can configure cost metrics for the routed paths to constrain traffic to a single link where the backup is a dialon-demand interface, or allow concurrent use of multiple routes where they are available.
n The availability of a TCP/IP network design is measured by the percentage of time users are able to transfer data by using the TCP/IP network infrastructure. To improve the availability of a routed network, your design must include redundant links and routers between locations where the highest availability is required. The inclusion of redundant routed paths in your design can improve both the availability and performance (bandwidth) of the network. n You can configure cost metrics for the routed paths to constrain traffic to a single link where the backup is a dialon-demand interface, or allow concurrent use of multiple routes where they are available.
 n Set the link cost metric for each route to be equal if the links are available concurrently and there is no monetary cost penalty. Set different cost metrics if a link provides dial-on-demand backup and monetary costs prohibit running multiple links concurrently. Routers can provide built-in load balancing across multiple links and paths if the routes are concurrently available and advanced routing protocols are used. Load balancing is possible with unequal cost metrics if protocols such as Interior Gateway Routing Protocol (IGRP) are used. The router uses the cost metrics to determine which paths the packets take, and the administrator can adjust the amount of load balancing. This is considered only if the speed of the redundant links differs greatly, and the links are concurrently available.
n Set the link cost metric for each route to be equal if the links are available concurrently and there is no monetary cost penalty. Set different cost metrics if a link provides dial-on-demand backup and monetary costs prohibit running multiple links concurrently. Routers can provide built-in load balancing across multiple links and paths if the routes are concurrently available and advanced routing protocols are used. Load balancing is possible with unequal cost metrics if protocols such as Interior Gateway Routing Protocol (IGRP) are used. The router uses the cost metrics to determine which paths the packets take, and the administrator can adjust the amount of load balancing. This is considered only if the speed of the redundant links differs greatly, and the links are concurrently available.
 u. Optimizing a TCP/IP Design for Performance n Optimizing Subnet Designs n Optimizing IP Performance on the Network n Optimizing Remote Subnets n Ensuring Performance with. Qo. S n Qo. S Connections n Discussion: Evaluating TCP/IP Availability and Performance Requirements
u. Optimizing a TCP/IP Design for Performance n Optimizing Subnet Designs n Optimizing IP Performance on the Network n Optimizing Remote Subnets n Ensuring Performance with. Qo. S n Qo. S Connections n Discussion: Evaluating TCP/IP Availability and Performance Requirements
 The performance of a TCP/IP network is set at a base level by the underlying physical network topology. In this lesson you will learn about enhancing the TCP/IP performance for particular applications by. n Optimizing the subnet designs. n Optimizing IP performance on the network. n Optimizing remote subnets. n Prioritizing traffic by using Qo. S. n Using Qo. S connections.
The performance of a TCP/IP network is set at a base level by the underlying physical network topology. In this lesson you will learn about enhancing the TCP/IP performance for particular applications by. n Optimizing the subnet designs. n Optimizing IP performance on the network. n Optimizing remote subnets. n Prioritizing traffic by using Qo. S. n Using Qo. S connections.
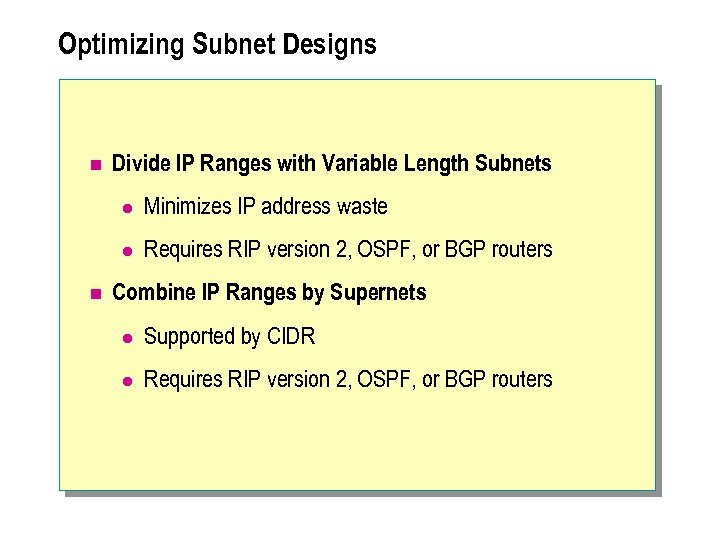 Optimizing Subnet Designs n Divide IP Ranges with Variable Length Subnets l l n Minimizes IP address waste Requires RIP version 2, OSPF, or BGP routers Combine IP Ranges by Supernets l Supported by CIDR l Requires RIP version 2, OSPF, or BGP routers
Optimizing Subnet Designs n Divide IP Ranges with Variable Length Subnets l l n Minimizes IP address waste Requires RIP version 2, OSPF, or BGP routers Combine IP Ranges by Supernets l Supported by CIDR l Requires RIP version 2, OSPF, or BGP routers
 n For most real-world enterprise networks, typical public IP addresses provide an address scheme that is either too large or too small. If the address scheme for a subnet is too large, IP addresses are unused and wasted. If the address scheme is too small, multiple address ranges and a more complicated routed path are required to achieve the goals of the network design.
n For most real-world enterprise networks, typical public IP addresses provide an address scheme that is either too large or too small. If the address scheme for a subnet is too large, IP addresses are unused and wasted. If the address scheme is too small, multiple address ranges and a more complicated routed path are required to achieve the goals of the network design.
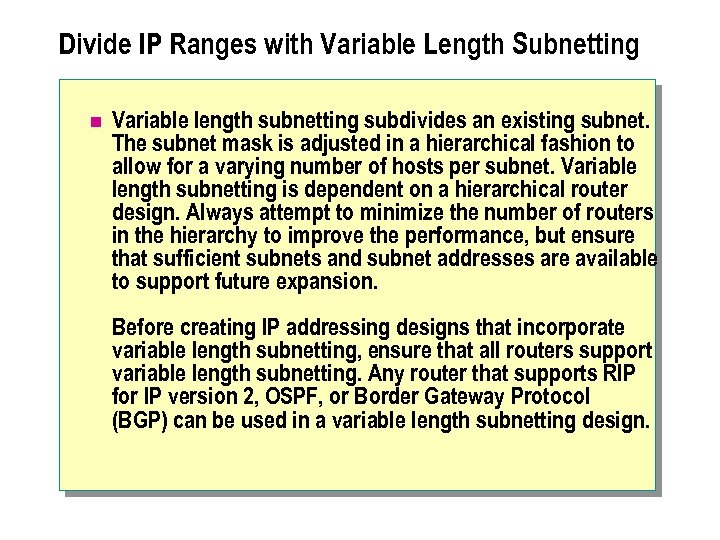 Divide IP Ranges with Variable Length Subnetting n Variable length subnetting subdivides an existing subnet. The subnet mask is adjusted in a hierarchical fashion to allow for a varying number of hosts per subnet. Variable length subnetting is dependent on a hierarchical router design. Always attempt to minimize the number of routers in the hierarchy to improve the performance, but ensure that sufficient subnets and subnet addresses are available to support future expansion. Before creating IP addressing designs that incorporate variable length subnetting, ensure that all routers support variable length subnetting. Any router that supports RIP for IP version 2, OSPF, or Border Gateway Protocol (BGP) can be used in a variable length subnetting design.
Divide IP Ranges with Variable Length Subnetting n Variable length subnetting subdivides an existing subnet. The subnet mask is adjusted in a hierarchical fashion to allow for a varying number of hosts per subnet. Variable length subnetting is dependent on a hierarchical router design. Always attempt to minimize the number of routers in the hierarchy to improve the performance, but ensure that sufficient subnets and subnet addresses are available to support future expansion. Before creating IP addressing designs that incorporate variable length subnetting, ensure that all routers support variable length subnetting. Any router that supports RIP for IP version 2, OSPF, or Border Gateway Protocol (BGP) can be used in a variable length subnetting design.
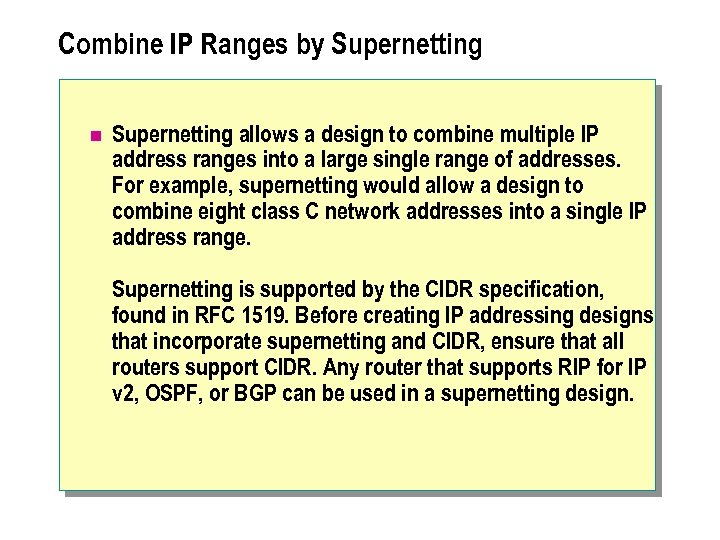 Combine IP Ranges by Supernetting n Supernetting allows a design to combine multiple IP address ranges into a large single range of addresses. For example, supernetting would allow a design to combine eight class C network addresses into a single IP address range. Supernetting is supported by the CIDR specification, found in RFC 1519. Before creating IP addressing designs that incorporate supernetting and CIDR, ensure that all routers support CIDR. Any router that supports RIP for IP v 2, OSPF, or BGP can be used in a supernetting design.
Combine IP Ranges by Supernetting n Supernetting allows a design to combine multiple IP address ranges into a large single range of addresses. For example, supernetting would allow a design to combine eight class C network addresses into a single IP address range. Supernetting is supported by the CIDR specification, found in RFC 1519. Before creating IP addressing designs that incorporate supernetting and CIDR, ensure that all routers support CIDR. Any router that supports RIP for IP v 2, OSPF, or BGP can be used in a supernetting design.
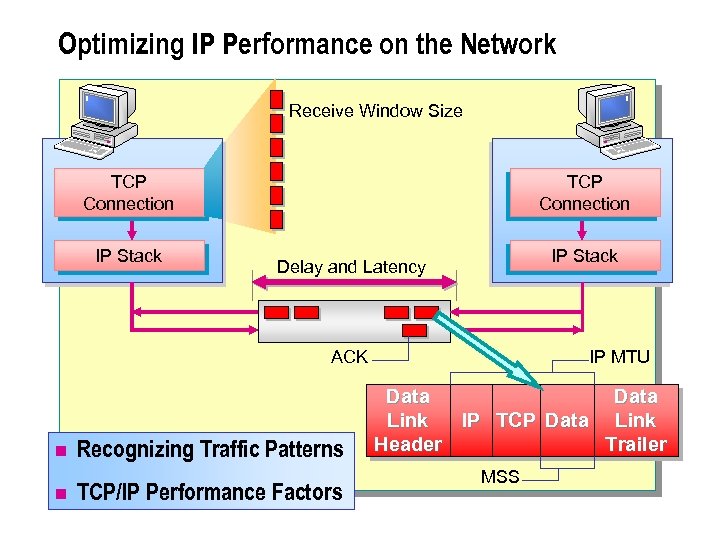 Optimizing IP Performance on the Network Receive Window Size TCP Connection IP Stack Delay and Latency ACK n n Recognizing Traffic Patterns TCP/IP Performance Factors IP MTU Data Link IP TCP Data Link Header Trailer MSS
Optimizing IP Performance on the Network Receive Window Size TCP Connection IP Stack Delay and Latency ACK n n Recognizing Traffic Patterns TCP/IP Performance Factors IP MTU Data Link IP TCP Data Link Header Trailer MSS
 n To optimize the flow of TCP/IP data within an internetwork requires the classification of the traffic flow to understand where configuring and tuning the TCP/IP implementation may allow performance gains.
n To optimize the flow of TCP/IP data within an internetwork requires the classification of the traffic flow to understand where configuring and tuning the TCP/IP implementation may allow performance gains.
 Recognizing Traffic Patterns The transactions involved between hosts across a network vary from simple datagram interactions with low packet counts to complex authenticated transfers with security and verifications involved. In general, you can categorize packet traffic into two major groups, both of which are sensitive to particular characteristics of a network. n Delay and Latency sensitive traffic Consists mainly of single packet. transfers that must be acknowledged before communications can continue. Logon, authentication, and encryption negotiations are extreme examples of this form of traffic. n Bandwidth sensitive traffic. Consists of principally unidirectional. communications where a large amount of traffic flows in one direction and acknowledgments flow in the other. Client/server, thin client, and Web-based applications exhibit this type of traffic flow.
Recognizing Traffic Patterns The transactions involved between hosts across a network vary from simple datagram interactions with low packet counts to complex authenticated transfers with security and verifications involved. In general, you can categorize packet traffic into two major groups, both of which are sensitive to particular characteristics of a network. n Delay and Latency sensitive traffic Consists mainly of single packet. transfers that must be acknowledged before communications can continue. Logon, authentication, and encryption negotiations are extreme examples of this form of traffic. n Bandwidth sensitive traffic. Consists of principally unidirectional. communications where a large amount of traffic flows in one direction and acknowledgments flow in the other. Client/server, thin client, and Web-based applications exhibit this type of traffic flow.
 n Many applications exhibit characteristics with hybrids of these traffic types, and must be designed to minimize performance limitations when used in a WAN environment.
n Many applications exhibit characteristics with hybrids of these traffic types, and must be designed to minimize performance limitations when used in a WAN environment.
 TCP/IP Performance Factors n The TCP/IP implementation in Windows 2000 is largely self-tuning, but some design choices made for both the network infrastructure, and the software installation, can influence the performance that you can ultimately achieve. In particular, when WAN networks span large distances, the delay through a network becomes a significant factor in any design considerations.
TCP/IP Performance Factors n The TCP/IP implementation in Windows 2000 is largely self-tuning, but some design choices made for both the network infrastructure, and the software installation, can influence the performance that you can ultimately achieve. In particular, when WAN networks span large distances, the delay through a network becomes a significant factor in any design considerations.
 Principal factors that influence TCP/IP performance are: n TCP/IP Receive Window Size. This is the buffer required to receive packets in a TCP stream before an acknowledgment is sent. For Ethernet-based TCP connections, the window is normally set to 17, 520 bytes, or 16 KB rounded up to 12 Maximum Segment Size (MSS)-sized segments. Where network delay is high, you can increase the minimum Window size offered for a connection by modifying the registry. n Delay/Bandwidth product High bandwidth/high delay networks, such. as satellite links, require special consideration when both configuring the network transports and designing the applications being used. When network delay becomes significant, always select the largest bandwidth available for links to maximize performance. n Packet loss on the network This is usually caused due to errors or. congestion in routers.
Principal factors that influence TCP/IP performance are: n TCP/IP Receive Window Size. This is the buffer required to receive packets in a TCP stream before an acknowledgment is sent. For Ethernet-based TCP connections, the window is normally set to 17, 520 bytes, or 16 KB rounded up to 12 Maximum Segment Size (MSS)-sized segments. Where network delay is high, you can increase the minimum Window size offered for a connection by modifying the registry. n Delay/Bandwidth product High bandwidth/high delay networks, such. as satellite links, require special consideration when both configuring the network transports and designing the applications being used. When network delay becomes significant, always select the largest bandwidth available for links to maximize performance. n Packet loss on the network This is usually caused due to errors or. congestion in routers.
 n There are certain factors that influence performance, but because they are part of the existing ISO layer one and two infrastructure, you may not be able to configure them. These factors are: l l n Maximum Transmission Unit (MTU). This is usually set by the underlying network technology. For example, Ethernet provides a 1, 500 byte MTU, whereas Token Ring can support up to 17, 914 bytes. Maximum Segment Size (MSS). This is the TCP/UDP payload that can be carried in the MTU. For example, the MSS for an Ethernet MTU of 1, 500 bytes is 1, 460 bytes. In network environments that include links with large delay components, your network design may be required to place network services, authentication, and application servers on both sides of the links to achieve acceptable client performance.
n There are certain factors that influence performance, but because they are part of the existing ISO layer one and two infrastructure, you may not be able to configure them. These factors are: l l n Maximum Transmission Unit (MTU). This is usually set by the underlying network technology. For example, Ethernet provides a 1, 500 byte MTU, whereas Token Ring can support up to 17, 914 bytes. Maximum Segment Size (MSS). This is the TCP/UDP payload that can be carried in the MTU. For example, the MSS for an Ethernet MTU of 1, 500 bytes is 1, 460 bytes. In network environments that include links with large delay components, your network design may be required to place network services, authentication, and application servers on both sides of the links to achieve acceptable client performance.
 Optimizing Remote Subnets n Private Point-to-Point and Multi-point Connections l l n For point-to-point, assign a subnet for each connection For multi-point, all connections share a common subnet VPN Connections over the Internet l Require a public address for VPN server l Require an address from the VPN address pool
Optimizing Remote Subnets n Private Point-to-Point and Multi-point Connections l l n For point-to-point, assign a subnet for each connection For multi-point, all connections share a common subnet VPN Connections over the Internet l Require a public address for VPN server l Require an address from the VPN address pool
 n Remote networks require special consideration when you develop an IP addressing scheme to ensure that traffic is properly routed and that Internet access is maintained.
n Remote networks require special consideration when you develop an IP addressing scheme to ensure that traffic is properly routed and that Internet access is maintained.
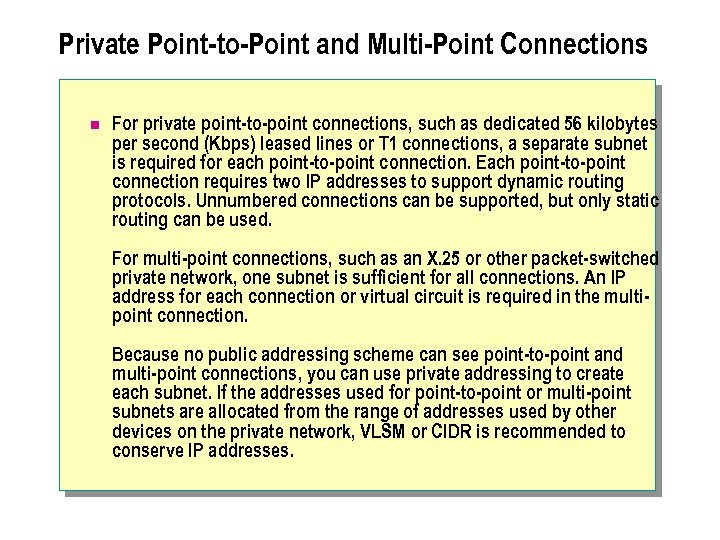 Private Point-to-Point and Multi-Point Connections n For private point-to-point connections, such as dedicated 56 kilobytes per second (Kbps) leased lines or T 1 connections, a separate subnet is required for each point-to-point connection. Each point-to-point connection requires two IP addresses to support dynamic routing protocols. Unnumbered connections can be supported, but only static routing can be used. For multi-point connections, such as an X. 25 or other packet-switched private network, one subnet is sufficient for all connections. An IP address for each connection or virtual circuit is required in the multipoint connection. Because no public addressing scheme can see point-to-point and multi-point connections, you can use private addressing to create each subnet. If the addresses used for point-to-point or multi-point subnets are allocated from the range of addresses used by other devices on the private network, VLSM or CIDR is recommended to conserve IP addresses.
Private Point-to-Point and Multi-Point Connections n For private point-to-point connections, such as dedicated 56 kilobytes per second (Kbps) leased lines or T 1 connections, a separate subnet is required for each point-to-point connection. Each point-to-point connection requires two IP addresses to support dynamic routing protocols. Unnumbered connections can be supported, but only static routing can be used. For multi-point connections, such as an X. 25 or other packet-switched private network, one subnet is sufficient for all connections. An IP address for each connection or virtual circuit is required in the multipoint connection. Because no public addressing scheme can see point-to-point and multi-point connections, you can use private addressing to create each subnet. If the addresses used for point-to-point or multi-point subnets are allocated from the range of addresses used by other devices on the private network, VLSM or CIDR is recommended to conserve IP addresses.
 VPN Connections over the Internet n To connect to a VPN client, each VPN server requires a public address. This address becomes one end of the communications tunnel. The VPN client receives an address from the VPN server's address pool. When communicating over the VPN connection, the VPN client uses the issued address to access intranetwork resources. n Any IP addressing design must account for the public address and the range of private network addresses required by the VPN server design. A private network address is required for each VPN client that simultaneously accesses the intranetwork.
VPN Connections over the Internet n To connect to a VPN client, each VPN server requires a public address. This address becomes one end of the communications tunnel. The VPN client receives an address from the VPN server's address pool. When communicating over the VPN connection, the VPN client uses the issued address to access intranetwork resources. n Any IP addressing design must account for the public address and the range of private network addresses required by the VPN server design. A private network address is required for each VPN client that simultaneously accesses the intranetwork.
 Ensuring Performance with. Qo. S n Reserve Bandwidth for Particular Users or Data Types n Prioritize Access to Bandwidth Based on User Needs n Partition Bandwidth Between Traffic n Prevent Non-Adaptive Protocols from Overusing Network Resources
Ensuring Performance with. Qo. S n Reserve Bandwidth for Particular Users or Data Types n Prioritize Access to Bandwidth Based on User Needs n Partition Bandwidth Between Traffic n Prevent Non-Adaptive Protocols from Overusing Network Resources
 n Data traffic routed across an IP network might have to travel through a series of routers. By default, each router in the path handles the traffic on a first-come, first-served (best-effort) basis. Time-sensitive streams of data such as video streaming, real-time audio, and video conferencing require immediate response to their data, or the receiving applications may fail. The Windows 2000 implementation of Qo. S provides selectable bandwidth reservation and priority levels for traffic flows. Qo. S provides a unidirectional mechanism by which you can manage network resources, whether on the local LAN segment, the core network, or the WAN, to provide the required service levels. Qo. S can run on any network topology that supports TCP/IP.
n Data traffic routed across an IP network might have to travel through a series of routers. By default, each router in the path handles the traffic on a first-come, first-served (best-effort) basis. Time-sensitive streams of data such as video streaming, real-time audio, and video conferencing require immediate response to their data, or the receiving applications may fail. The Windows 2000 implementation of Qo. S provides selectable bandwidth reservation and priority levels for traffic flows. Qo. S provides a unidirectional mechanism by which you can manage network resources, whether on the local LAN segment, the core network, or the WAN, to provide the required service levels. Qo. S can run on any network topology that supports TCP/IP.
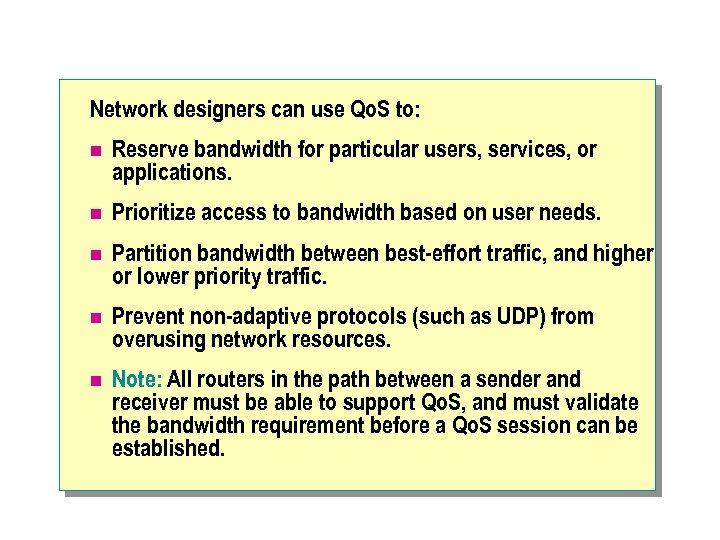 Network designers can use Qo. S to: n Reserve bandwidth for particular users, services, or applications. n Prioritize access to bandwidth based on user needs. n Partition bandwidth between best-effort traffic, and higher or lower priority traffic. n Prevent non-adaptive protocols (such as UDP) from overusing network resources. n Note: All routers in the path between a sender and receiver must be able to support Qo. S, and must validate the bandwidth requirement before a Qo. S session can be established.
Network designers can use Qo. S to: n Reserve bandwidth for particular users, services, or applications. n Prioritize access to bandwidth based on user needs. n Partition bandwidth between best-effort traffic, and higher or lower priority traffic. n Prevent non-adaptive protocols (such as UDP) from overusing network resources. n Note: All routers in the path between a sender and receiver must be able to support Qo. S, and must validate the bandwidth requirement before a Qo. S session can be established.
 Include Qo. S in your design if: n Bandwidth allocation is required. n It is supported by your planned applications. n All intermediate routers support Resource Reservation Protocol (RSVP).
Include Qo. S in your design if: n Bandwidth allocation is required. n It is supported by your planned applications. n All intermediate routers support Resource Reservation Protocol (RSVP).
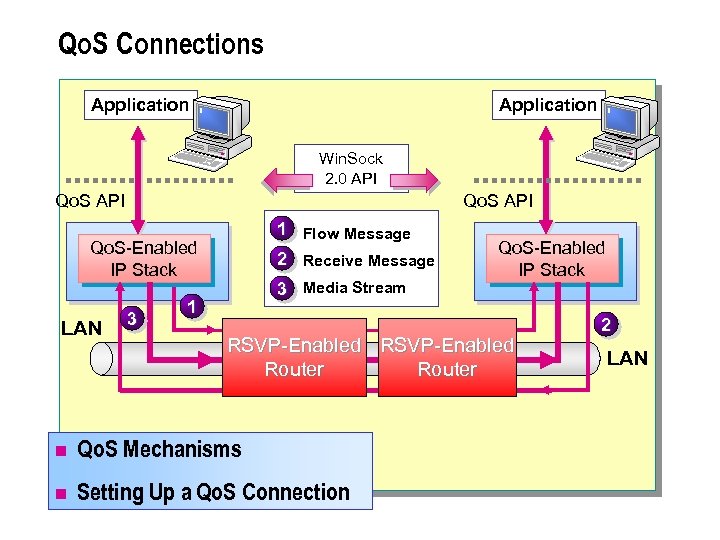 Qo. S Connections Application Win. Sock 2. 0 API Qo. S API 1 Flow Message 2 Receive Message Qo. S-Enabled IP Stack LAN 3 3 Media Stream 1 Qo. S-Enabled IP Stack RSVP-Enabled Router n Qo. S Mechanisms n Setting Up a Qo. S Connection 2 LAN
Qo. S Connections Application Win. Sock 2. 0 API Qo. S API 1 Flow Message 2 Receive Message Qo. S-Enabled IP Stack LAN 3 3 Media Stream 1 Qo. S-Enabled IP Stack RSVP-Enabled Router n Qo. S Mechanisms n Setting Up a Qo. S Connection 2 LAN
 n Implementing Qo. S enables real-time programs to make the most efficient use of network bandwidth. The goal of a Qo. S implementation is a guaranteed delivery system for network traffic, such as IP packets.
n Implementing Qo. S enables real-time programs to make the most efficient use of network bandwidth. The goal of a Qo. S implementation is a guaranteed delivery system for network traffic, such as IP packets.
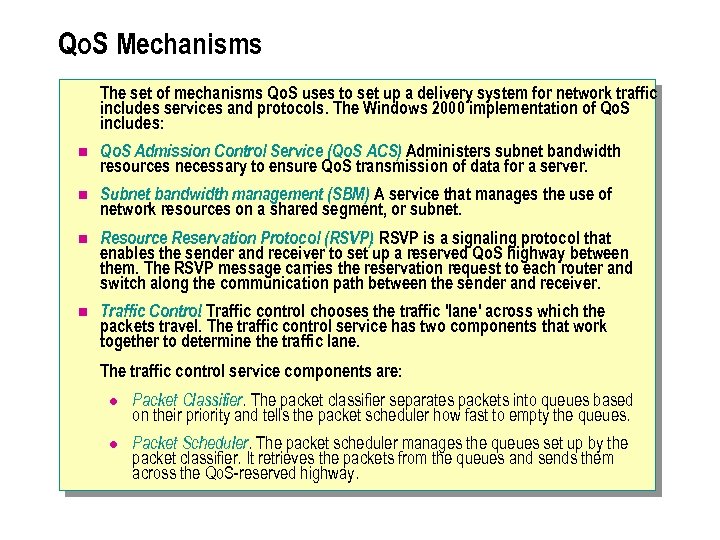 Qo. S Mechanisms The set of mechanisms Qo. S uses to set up a delivery system for network traffic includes services and protocols. The Windows 2000 implementation of Qo. S includes: n Qo. S Admission Control Service (Qo. S ACS) Administers subnet bandwidth. resources necessary to ensure Qo. S transmission of data for a server. n Subnet bandwidth management (SBM) A service that manages the use of. network resources on a shared segment, or subnet. n Resource Reservation Protocol (RSVP). RSVP is a signaling protocol that enables the sender and receiver to set up a reserved Qo. S highway between them. The RSVP message carries the reservation request to each router and switch along the communication path between the sender and receiver. n Traffic Control Traffic control chooses the traffic 'lane' across which the. packets travel. The traffic control service has two components that work together to determine the traffic lane. The traffic control service components are: l Packet Classifier. The packet classifier separates packets into queues based on their priority and tells the packet scheduler how fast to empty the queues. l Packet Scheduler. The packet scheduler manages the queues set up by the packet classifier. It retrieves the packets from the queues and sends them across the Qo. S-reserved highway.
Qo. S Mechanisms The set of mechanisms Qo. S uses to set up a delivery system for network traffic includes services and protocols. The Windows 2000 implementation of Qo. S includes: n Qo. S Admission Control Service (Qo. S ACS) Administers subnet bandwidth. resources necessary to ensure Qo. S transmission of data for a server. n Subnet bandwidth management (SBM) A service that manages the use of. network resources on a shared segment, or subnet. n Resource Reservation Protocol (RSVP). RSVP is a signaling protocol that enables the sender and receiver to set up a reserved Qo. S highway between them. The RSVP message carries the reservation request to each router and switch along the communication path between the sender and receiver. n Traffic Control Traffic control chooses the traffic 'lane' across which the. packets travel. The traffic control service has two components that work together to determine the traffic lane. The traffic control service components are: l Packet Classifier. The packet classifier separates packets into queues based on their priority and tells the packet scheduler how fast to empty the queues. l Packet Scheduler. The packet scheduler manages the queues set up by the packet classifier. It retrieves the packets from the queues and sends them across the Qo. S-reserved highway.
 Setting Up a Qo. S Connection n RSVP is the means by which end nodes communicate with each Qo. Saware network device (included in the hop path between RSVP session members), and negotiate Qo. S parameters and network usage admission. The RSVP protocol is used to exchange PATH and RESV messages with the network. A PATH message, which the sender initiates, describes the Qo. S parameters of the traffic, the sender's address, and the destination address of the traffic. The RESV message, returned by the receiver, describes the Qo. S parameters of the traffic to be received. When the sender receives the RESV message, the Qo. S data flow begins. The Qo. S Service Provider constructs and periodically updates the PATH and RESV messages on behalf of an application. You can also configure sending applications, such as those controlling multicast transmissions, to begin sending immediately on a best-effort basis, which is then upgraded to Qo. S on receipt of the RESV message.
Setting Up a Qo. S Connection n RSVP is the means by which end nodes communicate with each Qo. Saware network device (included in the hop path between RSVP session members), and negotiate Qo. S parameters and network usage admission. The RSVP protocol is used to exchange PATH and RESV messages with the network. A PATH message, which the sender initiates, describes the Qo. S parameters of the traffic, the sender's address, and the destination address of the traffic. The RESV message, returned by the receiver, describes the Qo. S parameters of the traffic to be received. When the sender receives the RESV message, the Qo. S data flow begins. The Qo. S Service Provider constructs and periodically updates the PATH and RESV messages on behalf of an application. You can also configure sending applications, such as those controlling multicast transmissions, to begin sending immediately on a best-effort basis, which is then upgraded to Qo. S on receipt of the RESV message.
 n For example, a sending host wanting to reserve bandwidth, sends path messages toward the intended recipient, through an RSVP-enabled Windows Sockets (Win. Sock) service provider. These path messages, which describe the bandwidth requirements and relevant parameters of the data to be sent, are propagated to all intermediate routers along the path. A receiving host confirms the flow and network path by sending reserve messages back through the network, describing the bandwidth characteristics of data from the sender. As these reserve messages propagate back toward the sender, intermediate routers decide whether or not to accept the proposed reservation and commit bandwidth resources. If all routers commit the required resources, the sender can begin sending data.
n For example, a sending host wanting to reserve bandwidth, sends path messages toward the intended recipient, through an RSVP-enabled Windows Sockets (Win. Sock) service provider. These path messages, which describe the bandwidth requirements and relevant parameters of the data to be sent, are propagated to all intermediate routers along the path. A receiving host confirms the flow and network path by sending reserve messages back through the network, describing the bandwidth characteristics of data from the sender. As these reserve messages propagate back toward the sender, intermediate routers decide whether or not to accept the proposed reservation and commit bandwidth resources. If all routers commit the required resources, the sender can begin sending data.
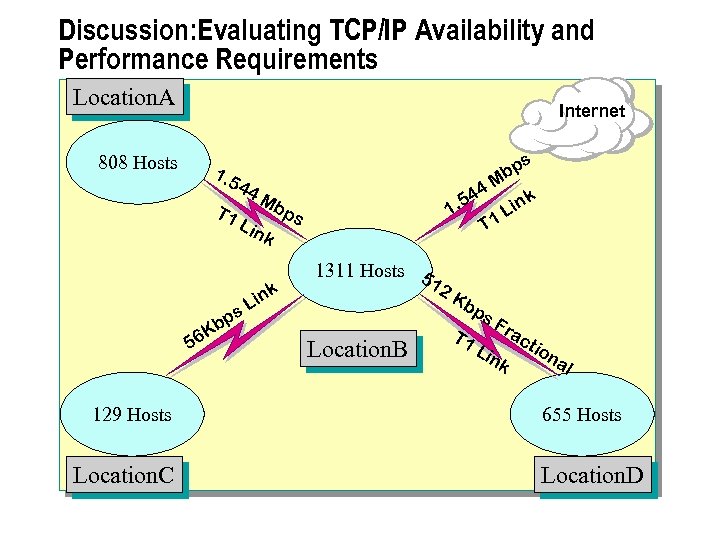 Discussion: Evaluating TCP/IP Availability and Performance Requirements Location. A Internet 808 Hosts s 1. 5 T 1 44 Lin k Lin s p Kb 56 129 Hosts Location. C . 54 1 Mb k ps 1311 Hosts 5 12 Location. B Kb T 1 4 p Mb T 1 ink L ps Fr ac tio Lin na k l 655 Hosts Location. D
Discussion: Evaluating TCP/IP Availability and Performance Requirements Location. A Internet 808 Hosts s 1. 5 T 1 44 Lin k Lin s p Kb 56 129 Hosts Location. C . 54 1 Mb k ps 1311 Hosts 5 12 Location. B Kb T 1 4 p Mb T 1 ink L ps Fr ac tio Lin na k l 655 Hosts Location. D
 n To enhance the availability and performance of a TCP/IP solution, you must decide on the required bandwidth and how to improve the performance of TCP/IP-based solutions. The following scenario describes an organization's current network configuration.
n To enhance the availability and performance of a TCP/IP solution, you must decide on the required bandwidth and how to improve the performance of TCP/IP-based solutions. The following scenario describes an organization's current network configuration.
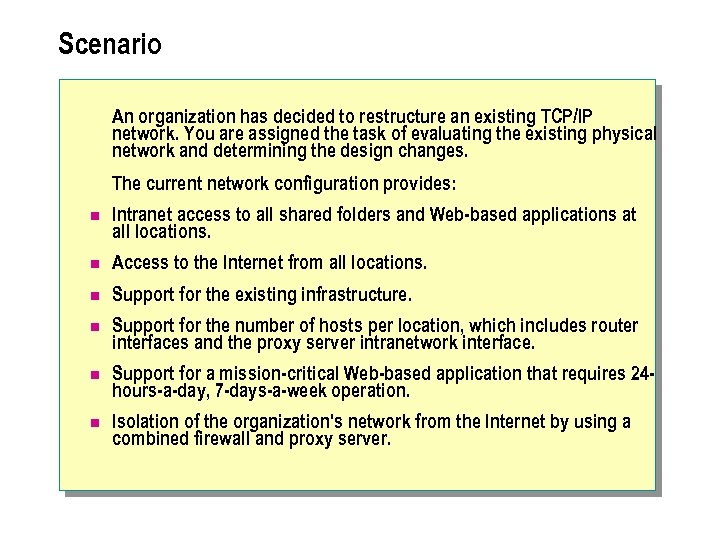 Scenario An organization has decided to restructure an existing TCP/IP network. You are assigned the task of evaluating the existing physical network and determining the design changes. The current network configuration provides: n Intranet access to all shared folders and Web-based applications at all locations. n Access to the Internet from all locations. n Support for the existing infrastructure. n Support for the number of hosts per location, which includes router interfaces and the proxy server intranetwork interface. n Support for a mission-critical Web-based application that requires 24 hours-a-day, 7 -days-a-week operation. n Isolation of the organization's network from the Internet by using a combined firewall and proxy server.
Scenario An organization has decided to restructure an existing TCP/IP network. You are assigned the task of evaluating the existing physical network and determining the design changes. The current network configuration provides: n Intranet access to all shared folders and Web-based applications at all locations. n Access to the Internet from all locations. n Support for the existing infrastructure. n Support for the number of hosts per location, which includes router interfaces and the proxy server intranetwork interface. n Support for a mission-critical Web-based application that requires 24 hours-a-day, 7 -days-a-week operation. n Isolation of the organization's network from the Internet by using a combined firewall and proxy server.
 Design Requirements n Your assessment of the existing network configuration, and your investigation of the future configuration requirements, reveals the following design requirements, which you must meet in your solution.
Design Requirements n Your assessment of the existing network configuration, and your investigation of the future configuration requirements, reveals the following design requirements, which you must meet in your solution.
 Existing configuration information n The network currently uses 172. 20. 0. 0/16 as the private address block from which all host addresses are allocated. n Company policy mandates that client computers are turned off when not in use, but servers and other networkrelated devices are left on. n The average usage of network link from Location. B to Location. A is 70 percent. n The average usage of network link from Location. B to Location. C is 100 percent. n The average usage of network link from Location. B to Location. D is 60 percent.
Existing configuration information n The network currently uses 172. 20. 0. 0/16 as the private address block from which all host addresses are allocated. n Company policy mandates that client computers are turned off when not in use, but servers and other networkrelated devices are left on. n The average usage of network link from Location. B to Location. A is 70 percent. n The average usage of network link from Location. B to Location. C is 100 percent. n The average usage of network link from Location. B to Location. D is 60 percent.
 Future configuration requirements n A Win. Sock II video conferencing application will be run between Location. A and Location. B. Each instance of the application requires sustained throughput of 48 Kbps in each direction for audio and video. n Private addressing will be used based on the current private address block used, and the site router interfaces will keep the same address and subnet mask. n New site routers are to be installed and these devices will restrict the host population per segment to 200 or less.
Future configuration requirements n A Win. Sock II video conferencing application will be run between Location. A and Location. B. Each instance of the application requires sustained throughput of 48 Kbps in each direction for audio and video. n Private addressing will be used based on the current private address block used, and the site router interfaces will keep the same address and subnet mask. n New site routers are to be installed and these devices will restrict the host population per segment to 200 or less.
 Lab A: Designing a TCP/IP Solution
Lab A: Designing a TCP/IP Solution
 Objectives n After completing this lab, you will be able to: n Evaluate a scenario to determine the requirements for a TCP/IP design. n Design a TCP/IP solution for the given scenario.
Objectives n After completing this lab, you will be able to: n Evaluate a scenario to determine the requirements for a TCP/IP design. n Design a TCP/IP solution for the given scenario.
 Exercise 1 Designing a TCP/IP Solution n In this exercise, you will design a TCP/IP solution for the given scenario. To design your solution, review the information provided in the scenario, study the diagram, and follow the design decisions. Make your design decisions based on the requirements provided and complete the design worksheet.
Exercise 1 Designing a TCP/IP Solution n In this exercise, you will design a TCP/IP solution for the given scenario. To design your solution, review the information provided in the scenario, study the diagram, and follow the design decisions. Make your design decisions based on the requirements provided and complete the design worksheet.
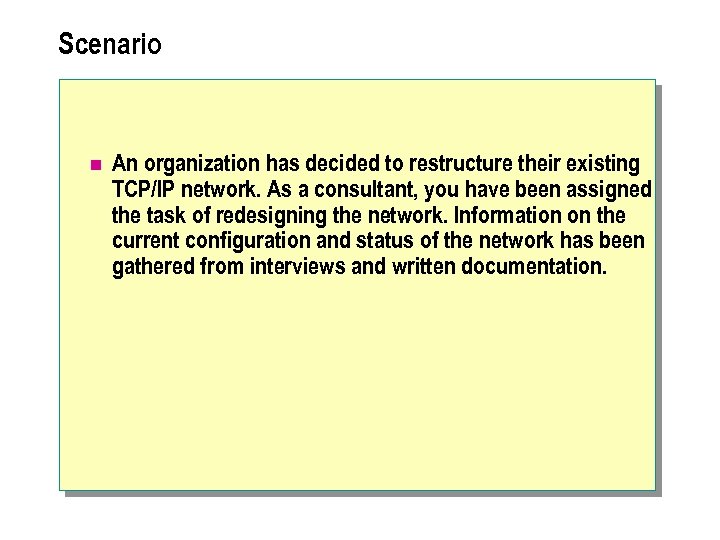 Scenario n An organization has decided to restructure their existing TCP/IP network. As a consultant, you have been assigned the task of redesigning the network. Information on the current configuration and status of the network has been gathered from interviews and written documentation.
Scenario n An organization has decided to restructure their existing TCP/IP network. As a consultant, you have been assigned the task of redesigning the network. Information on the current configuration and status of the network has been gathered from interviews and written documentation.
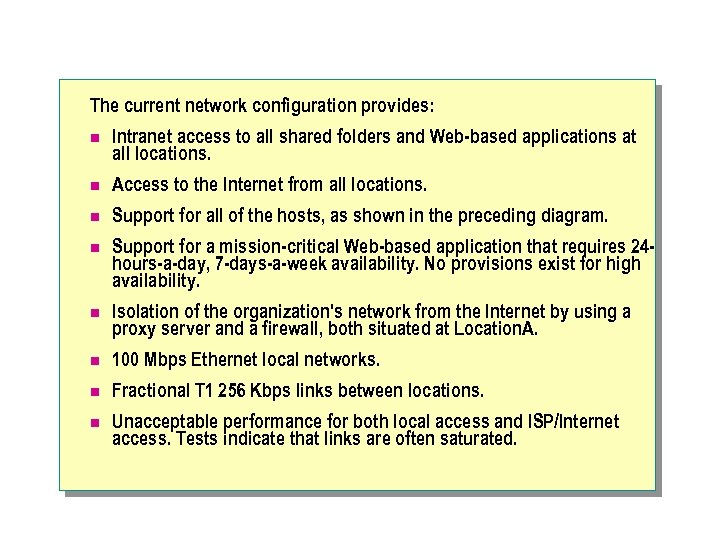 The current network configuration provides: n Intranet access to all shared folders and Web-based applications at all locations. n Access to the Internet from all locations. n Support for all of the hosts, as shown in the preceding diagram. n Support for a mission-critical Web-based application that requires 24 hours-a-day, 7 -days-a-week availability. No provisions exist for high availability. n Isolation of the organization's network from the Internet by using a proxy server and a firewall, both situated at Location. A. n 100 Mbps Ethernet local networks. n Fractional T 1 256 Kbps links between locations. n Unacceptable performance for both local access and ISP/Internet access. Tests indicate that links are often saturated.
The current network configuration provides: n Intranet access to all shared folders and Web-based applications at all locations. n Access to the Internet from all locations. n Support for all of the hosts, as shown in the preceding diagram. n Support for a mission-critical Web-based application that requires 24 hours-a-day, 7 -days-a-week availability. No provisions exist for high availability. n Isolation of the organization's network from the Internet by using a proxy server and a firewall, both situated at Location. A. n 100 Mbps Ethernet local networks. n Fractional T 1 256 Kbps links between locations. n Unacceptable performance for both local access and ISP/Internet access. Tests indicate that links are often saturated.
 High Level Network Design n The following diagram shows the existing high-level network design.
High Level Network Design n The following diagram shows the existing high-level network design.
 Design Requirements and Limitations n Investigation of the current network, user traffic patterns, and future network requirements reveals the following additional information that you must consider when making your design decisions:
Design Requirements and Limitations n Investigation of the current network, user traffic patterns, and future network requirements reveals the following additional information that you must consider when making your design decisions:
 Network Information n New routers, which are combined ISO layer 2 switches and routers, will be used in all locations. The routers support CIDR and VLSM. Each router can support four interfaces, where each interface represents one subnet supporting a maximum of 121 clients. Multiple routers can be stacked to create a single logical router. n Link upgrades must use one of the bandwidth options available that are fractional T 1 of 256 Kbps, 384 Kbps, 512 Kbps, 768 Kbps, 1, 024 Kbps, and Full T 1 of 1. 544 Mbps. n The links between locations are either T 1 or Fractional T 1 and support the full Ethernet MTU of 1, 500 bytes. Therefore, you do not need to consider the possibility of routers fragmenting packets. n The links between locations will be resized to suit the required performance. Bandwidth options available are fractional T 1 of 256 Kbps, 384 Kbps, 512 Kbps, 768 Kbps, 1, 024 Kbps, and Full T 1 of 1. 544 Mbps n There is no significant delay between locations. Therefore, you do not need to consider the placement of authentication servers or the effect delay has on throughput for the clients. n The current network configuration uses a private address block that uses 172. 16. 0. 0/16. You will reuse this private address block in the new design. n The current link to the ISP and the Internet is established, and the ISP has issued the organization one public IP address. This address will be used for the firewall interface (or proxy interface) to the ISP, and the Internet.
Network Information n New routers, which are combined ISO layer 2 switches and routers, will be used in all locations. The routers support CIDR and VLSM. Each router can support four interfaces, where each interface represents one subnet supporting a maximum of 121 clients. Multiple routers can be stacked to create a single logical router. n Link upgrades must use one of the bandwidth options available that are fractional T 1 of 256 Kbps, 384 Kbps, 512 Kbps, 768 Kbps, 1, 024 Kbps, and Full T 1 of 1. 544 Mbps. n The links between locations are either T 1 or Fractional T 1 and support the full Ethernet MTU of 1, 500 bytes. Therefore, you do not need to consider the possibility of routers fragmenting packets. n The links between locations will be resized to suit the required performance. Bandwidth options available are fractional T 1 of 256 Kbps, 384 Kbps, 512 Kbps, 768 Kbps, 1, 024 Kbps, and Full T 1 of 1. 544 Mbps n There is no significant delay between locations. Therefore, you do not need to consider the placement of authentication servers or the effect delay has on throughput for the clients. n The current network configuration uses a private address block that uses 172. 16. 0. 0/16. You will reuse this private address block in the new design. n The current link to the ISP and the Internet is established, and the ISP has issued the organization one public IP address. This address will be used for the firewall interface (or proxy interface) to the ISP, and the Internet.
 Client Information n The clients use a Web-based application to access their e -mail server, which is maintained by the ISP. The ISP also supplies Internet access. n The client data flows are analyzed. The data flows shown will result in a maximum of 50 percent average utilization.
Client Information n The clients use a Web-based application to access their e -mail server, which is maintained by the ISP. The ISP also supplies Internet access. n The client data flows are analyzed. The data flows shown will result in a maximum of 50 percent average utilization.
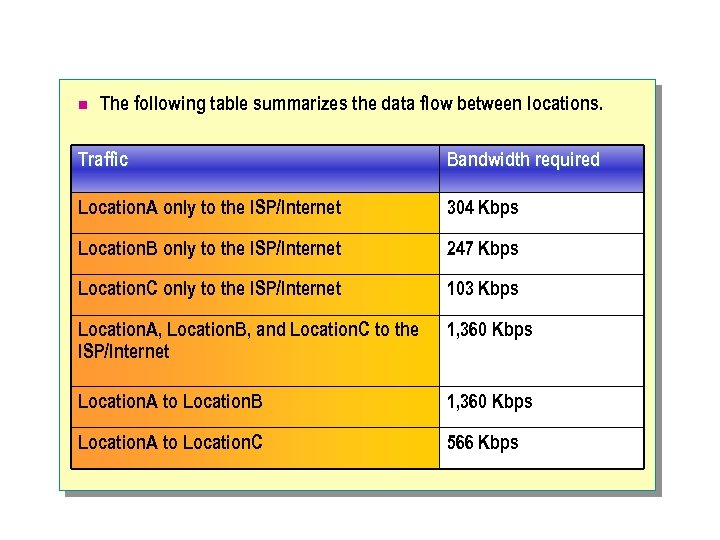 n The following table summarizes the data flow between locations. Traffic Bandwidth required Location. A only to the ISP/Internet 304 Kbps Location. B only to the ISP/Internet 247 Kbps Location. C only to the ISP/Internet 103 Kbps Location. A, Location. B, and Location. C to the ISP/Internet 1, 360 Kbps Location. A to Location. B 1, 360 Kbps Location. A to Location. C 566 Kbps
n The following table summarizes the data flow between locations. Traffic Bandwidth required Location. A only to the ISP/Internet 304 Kbps Location. B only to the ISP/Internet 247 Kbps Location. C only to the ISP/Internet 103 Kbps Location. A, Location. B, and Location. C to the ISP/Internet 1, 360 Kbps Location. A to Location. B 1, 360 Kbps Location. A to Location. C 566 Kbps
 The host counts given in the diagrams include all current IP address requirements. Investigations reveal that the client counts for each location, including the expected growth, are as follows: n Location. A will support 360 clients. n Location. B will support 293 clients. n Location. C will support 122 clients.
The host counts given in the diagrams include all current IP address requirements. Investigations reveal that the client counts for each location, including the expected growth, are as follows: n Location. A will support 360 clients. n Location. B will support 293 clients. n Location. C will support 122 clients.
 Services and Applications n There are file and print servers at each location. All clients store their data on local servers and print to local printers. Therefore, you do not need to allow for data flows between locations for file and print services. n There are DHCP and WINS servers at each location. Investigations reveal that replication of data between WINS servers will have no significant effect on the design. The operations group will configure and setup these services; therefore, do not consider them in your design. n The ISP maintains the organization's Internet Information Services (IIS) Web server and the server running Microsoft Exchange Server. Therefore, you do not need to consider DNS requirements in your design.
Services and Applications n There are file and print servers at each location. All clients store their data on local servers and print to local printers. Therefore, you do not need to allow for data flows between locations for file and print services. n There are DHCP and WINS servers at each location. Investigations reveal that replication of data between WINS servers will have no significant effect on the design. The operations group will configure and setup these services; therefore, do not consider them in your design. n The ISP maintains the organization's Internet Information Services (IIS) Web server and the server running Microsoft Exchange Server. Therefore, you do not need to consider DNS requirements in your design.
 Instructions n Use the following guidelines to complete the tasks in the design worksheet: n Select the new size for link 1, 2, and 3 by analyzing the client data flow requirements of the TCP/IP network. Consider the impact of network path delay when using satellite or long distance links because this impacts the placement of services and the selection of link speeds within the network. n Review the number of physical subnets required and the client load to ensure adequate peer performance. Review the OSI layer one and layer two network structure, and bandwidth utilization to ensure TCP/IP can be supported while providing the required performance. n Plan, review, and record TCP/IP physical routing structure elements including routers, subnet IP addresses, and subnet masks. (Class, VLSM, and CIDR must be selected. ) n Review and record boundaries where the MTU changes within the routed network. Note any routes where the MTU cannot be established, so that further investigation may occur. n Select the Interior Gateway Protocol (RIPv 1, RIPv 2, or OSPF) to be supported on the Windows 2000 network. Establish the basis on which you made your selection.
Instructions n Use the following guidelines to complete the tasks in the design worksheet: n Select the new size for link 1, 2, and 3 by analyzing the client data flow requirements of the TCP/IP network. Consider the impact of network path delay when using satellite or long distance links because this impacts the placement of services and the selection of link speeds within the network. n Review the number of physical subnets required and the client load to ensure adequate peer performance. Review the OSI layer one and layer two network structure, and bandwidth utilization to ensure TCP/IP can be supported while providing the required performance. n Plan, review, and record TCP/IP physical routing structure elements including routers, subnet IP addresses, and subnet masks. (Class, VLSM, and CIDR must be selected. ) n Review and record boundaries where the MTU changes within the routed network. Note any routes where the MTU cannot be established, so that further investigation may occur. n Select the Interior Gateway Protocol (RIPv 1, RIPv 2, or OSPF) to be supported on the Windows 2000 network. Establish the basis on which you made your selection.
 Design Worksheet n In the space provided below, list the required solution and/or actions that are necessary to meet the requirements. 1. Determine the capacities of the Links 1, 2, and 3. 2. Determine the number of routers and sub nets required for client populations in each location. 3. Select address ranges and subnet masks for all router. Show whether selected addresses require classbased, VLSM, or CIDR support in the routers. You do not need to calculat e the address range for every subnet; calculate only the base address for the routers. 4. Describe any MTU issues within the network. 5. Select the routing protocol you would implement in this design. Why?
Design Worksheet n In the space provided below, list the required solution and/or actions that are necessary to meet the requirements. 1. Determine the capacities of the Links 1, 2, and 3. 2. Determine the number of routers and sub nets required for client populations in each location. 3. Select address ranges and subnet masks for all router. Show whether selected addresses require classbased, VLSM, or CIDR support in the routers. You do not need to calculat e the address range for every subnet; calculate only the base address for the routers. 4. Describe any MTU issues within the network. 5. Select the routing protocol you would implement in this design. Why?

 Review n Introducing TCP/IP n Designing a Functional TCP/IP Solution n Securing a TCP/IP Solution n Enhancing a TCP/IP Design for Availability n Optimizing a TCP/IP Design for Performance
Review n Introducing TCP/IP n Designing a Functional TCP/IP Solution n Securing a TCP/IP Solution n Enhancing a TCP/IP Design for Availability n Optimizing a TCP/IP Design for Performance


