eb0ed6eb37466af80f18566bc064e081.ppt
- Количество слайдов: 53
 Modeling of Wireless Sensor Networks for Localization and Mobile Targets Tracking 用於無線感測網路定位與移動目標物追蹤之模型 Prasan Kumar Sahoo Dept. of Information Management Vanung University 沙庫瑪 萬能科技大學資訊管理學系 Present by C. T. Lee 2007 / 4 / 16, 30 1/53
Modeling of Wireless Sensor Networks for Localization and Mobile Targets Tracking 用於無線感測網路定位與移動目標物追蹤之模型 Prasan Kumar Sahoo Dept. of Information Management Vanung University 沙庫瑪 萬能科技大學資訊管理學系 Present by C. T. Lee 2007 / 4 / 16, 30 1/53
 ¡ Educational Background 中央大學資訊 程博士候選人 Ph. D. in Mathematics from Utkal University, India with advisor from Department of Mathematics, Indian Institute of Technology (IIT), Kharagpur, India, April, 2002. Master of Technology [M. Tech] in Computer Science from Indian Institute of Technology (IIT), Kharagpur, India. Master of Science [M. Sc. ] in Mathematics from Utkal University, India. 2
¡ Educational Background 中央大學資訊 程博士候選人 Ph. D. in Mathematics from Utkal University, India with advisor from Department of Mathematics, Indian Institute of Technology (IIT), Kharagpur, India, April, 2002. Master of Technology [M. Tech] in Computer Science from Indian Institute of Technology (IIT), Kharagpur, India. Master of Science [M. Sc. ] in Mathematics from Utkal University, India. 2
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 3
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 3
 Introduction ¡ Target detection and tracking can be classified into four different categories. 1. The first category is to find out the trajectory of the target. 2. The second category is to wake up the sensors by using predictive strategy in order to keep track with the target. 3. The third category is to use the predictive strategy to reduce the transmitted data between the sink and each sensor node. 4. The last category is to obtain more accurate information of the target. 4
Introduction ¡ Target detection and tracking can be classified into four different categories. 1. The first category is to find out the trajectory of the target. 2. The second category is to wake up the sensors by using predictive strategy in order to keep track with the target. 3. The third category is to use the predictive strategy to reduce the transmitted data between the sink and each sensor node. 4. The last category is to obtain more accurate information of the target. 4
 Introduction ¡ In this report Authors propose the boundary node selection algorithms. They also propose a target detection protocol to track the entry and exit of the single target. Design of an extended linear feedback model taking binary exponential backoff mechanism of IEEE 802. 15. 4 CSMA/CA based wireless sensor network to analyze the energy consumption issues of the one hop sensors. 5
Introduction ¡ In this report Authors propose the boundary node selection algorithms. They also propose a target detection protocol to track the entry and exit of the single target. Design of an extended linear feedback model taking binary exponential backoff mechanism of IEEE 802. 15. 4 CSMA/CA based wireless sensor network to analyze the energy consumption issues of the one hop sensors. 5
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 6
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 6
 Boundary node Selection and Target Detection Protocols ¡ In this work, it is assumed that all sensors are randomly and densely deployed over the monitoring region. ¡ The sensing range is variable, which may be larger or smaller than the communication range. 7
Boundary node Selection and Target Detection Protocols ¡ In this work, it is assumed that all sensors are randomly and densely deployed over the monitoring region. ¡ The sensing range is variable, which may be larger or smaller than the communication range. 7
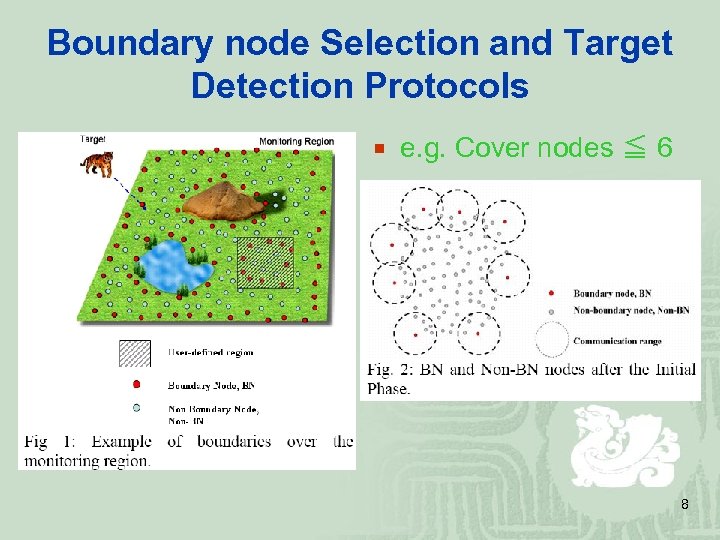 Boundary node Selection and Target Detection Protocols ¡ e. g. Cover nodes ≦ 6 8
Boundary node Selection and Target Detection Protocols ¡ e. g. Cover nodes ≦ 6 8
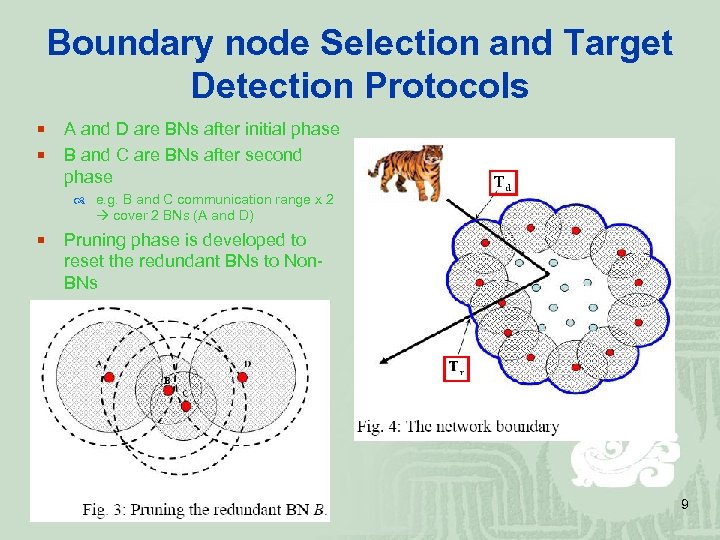 Boundary node Selection and Target Detection Protocols ¡ ¡ A and D are BNs after initial phase B and C are BNs after second phase e. g. B and C communication range x 2 cover 2 BNs (A and D) ¡ Pruning phase is developed to reset the redundant BNs to Non. BNs 9
Boundary node Selection and Target Detection Protocols ¡ ¡ A and D are BNs after initial phase B and C are BNs after second phase e. g. B and C communication range x 2 cover 2 BNs (A and D) ¡ Pruning phase is developed to reset the redundant BNs to Non. BNs 9
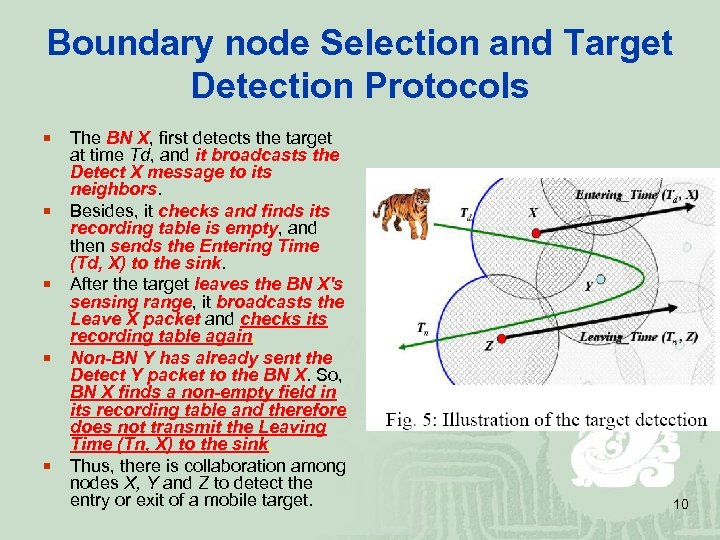 Boundary node Selection and Target Detection Protocols ¡ ¡ ¡ The BN X, first detects the target at time Td, and it broadcasts the Detect X message to its neighbors. Besides, it checks and finds its recording table is empty, and then sends the Entering Time (Td, X) to the sink. After the target leaves the BN X's sensing range, it broadcasts the Leave X packet and checks its recording table again. Non-BN Y has already sent the Detect Y packet to the BN X. So, BN X finds a non-empty field in its recording table and therefore does not transmit the Leaving Time (Tn, X) to the sink. Thus, there is collaboration among nodes X, Y and Z to detect the entry or exit of a mobile target. 10
Boundary node Selection and Target Detection Protocols ¡ ¡ ¡ The BN X, first detects the target at time Td, and it broadcasts the Detect X message to its neighbors. Besides, it checks and finds its recording table is empty, and then sends the Entering Time (Td, X) to the sink. After the target leaves the BN X's sensing range, it broadcasts the Leave X packet and checks its recording table again. Non-BN Y has already sent the Detect Y packet to the BN X. So, BN X finds a non-empty field in its recording table and therefore does not transmit the Leaving Time (Tn, X) to the sink. Thus, there is collaboration among nodes X, Y and Z to detect the entry or exit of a mobile target. 10
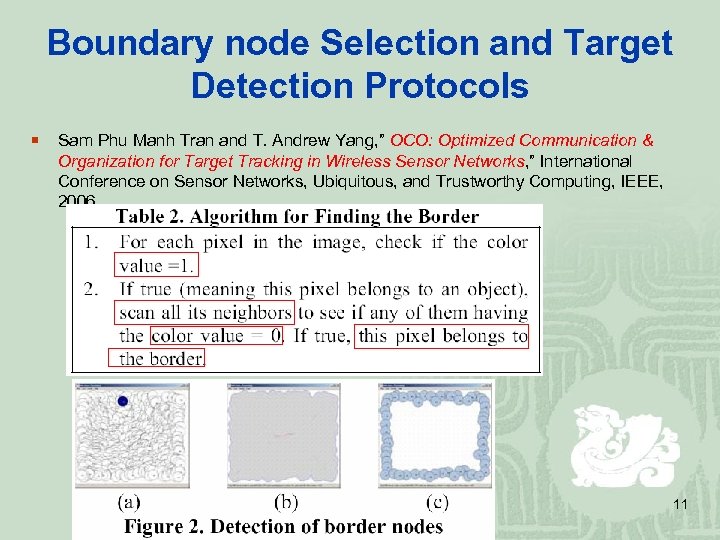 Boundary node Selection and Target Detection Protocols ¡ Sam Phu Manh Tran and T. Andrew Yang, ” OCO: Optimized Communication & Organization for Target Tracking in Wireless Sensor Networks, ” International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, IEEE, 2006. 11
Boundary node Selection and Target Detection Protocols ¡ Sam Phu Manh Tran and T. Andrew Yang, ” OCO: Optimized Communication & Organization for Target Tracking in Wireless Sensor Networks, ” International Conference on Sensor Networks, Ubiquitous, and Trustworthy Computing, IEEE, 2006. 11
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 12
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 12
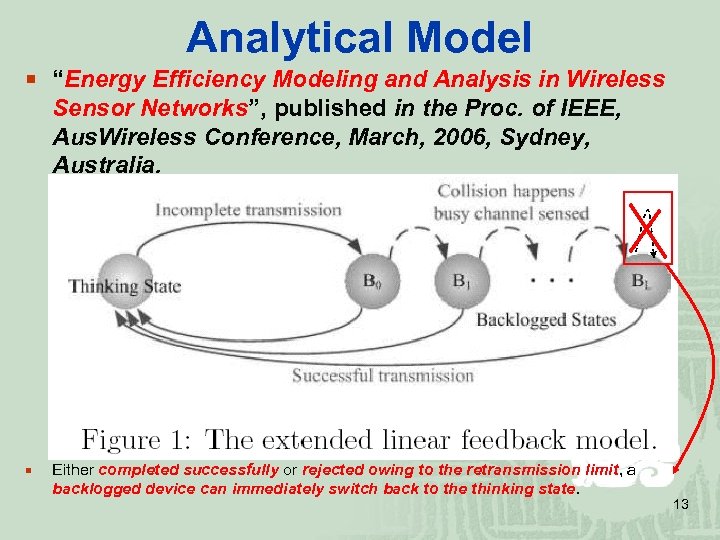 Analytical Model ¡ “Energy Efficiency Modeling and Analysis in Wireless Sensor Networks”, published in the Proc. of IEEE, Aus. Wireless Conference, March, 2006, Sydney, Australia. ¡ Either completed successfully or rejected owing to the retransmission limit, a backlogged device can immediately switch back to the thinking state. 13
Analytical Model ¡ “Energy Efficiency Modeling and Analysis in Wireless Sensor Networks”, published in the Proc. of IEEE, Aus. Wireless Conference, March, 2006, Sydney, Australia. ¡ Either completed successfully or rejected owing to the retransmission limit, a backlogged device can immediately switch back to the thinking state. 13
 Analytical Model ¡ Authors consider a homogeneous WSNs that consists of N ¡ ¡ number of nodes where nodes may be in the thinking or backlogged state, alternatively. Let B 0, B 1, . . . , BL represent those backlogged states. Nodes in thinking state may generate new packets with probability g. It remains in backlogged state if the medium sensed by it is busy due to the data transmission by other nodes of the network or due to collision of its packets with others. L + 1 number of backlog states are considered, where L is the retry limit which is application oriented or set as default value as per IEEE 802. 15. 4 standard. 14
Analytical Model ¡ Authors consider a homogeneous WSNs that consists of N ¡ ¡ number of nodes where nodes may be in the thinking or backlogged state, alternatively. Let B 0, B 1, . . . , BL represent those backlogged states. Nodes in thinking state may generate new packets with probability g. It remains in backlogged state if the medium sensed by it is busy due to the data transmission by other nodes of the network or due to collision of its packets with others. L + 1 number of backlog states are considered, where L is the retry limit which is application oriented or set as default value as per IEEE 802. 15. 4 standard. 14
 Analytical Model ¡ Let, W 0 be the initial size of the contention window. ¡ The contention window of the r-th retransmission is defined as Wr = W 0 x 2 r. ¡ Backoff Time = INT(CW x Random()) x Slot Time 15
Analytical Model ¡ Let, W 0 be the initial size of the contention window. ¡ The contention window of the r-th retransmission is defined as Wr = W 0 x 2 r. ¡ Backoff Time = INT(CW x Random()) x Slot Time 15
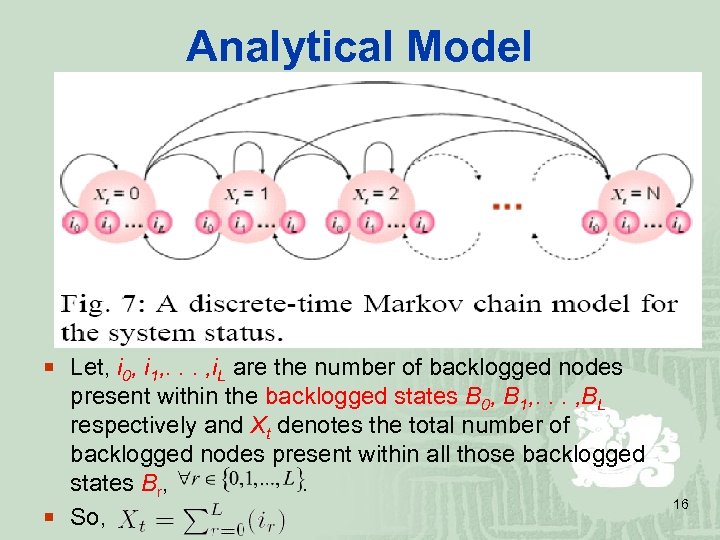 Analytical Model ¡ Let, i 0, i 1, . . . , i. L are the number of backlogged nodes present within the backlogged states B 0, B 1, . . . , BL respectively and Xt denotes the total number of backlogged nodes present within all those backlogged states Br, . ¡ So, 16
Analytical Model ¡ Let, i 0, i 1, . . . , i. L are the number of backlogged nodes present within the backlogged states B 0, B 1, . . . , BL respectively and Xt denotes the total number of backlogged nodes present within all those backlogged states Br, . ¡ So, 16
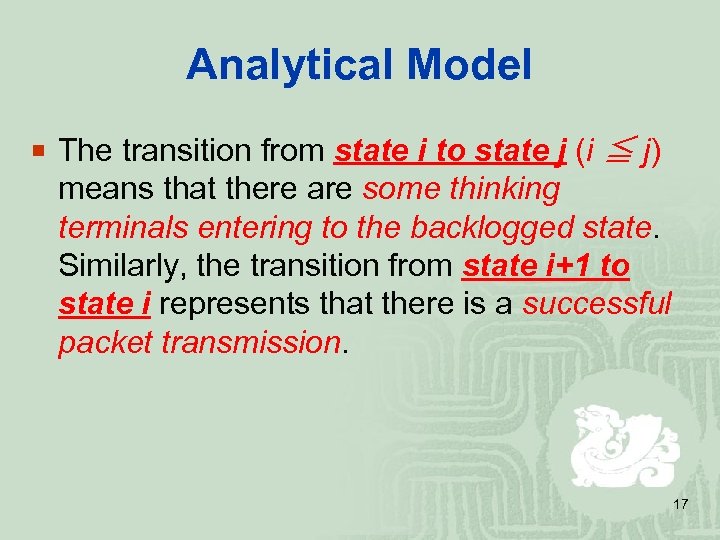 Analytical Model ¡ The transition from state i to state j (i ≦ j) means that there are some thinking terminals entering to the backlogged state. Similarly, the transition from state i+1 to state i represents that there is a successful packet transmission. 17
Analytical Model ¡ The transition from state i to state j (i ≦ j) means that there are some thinking terminals entering to the backlogged state. Similarly, the transition from state i+1 to state i represents that there is a successful packet transmission. 17
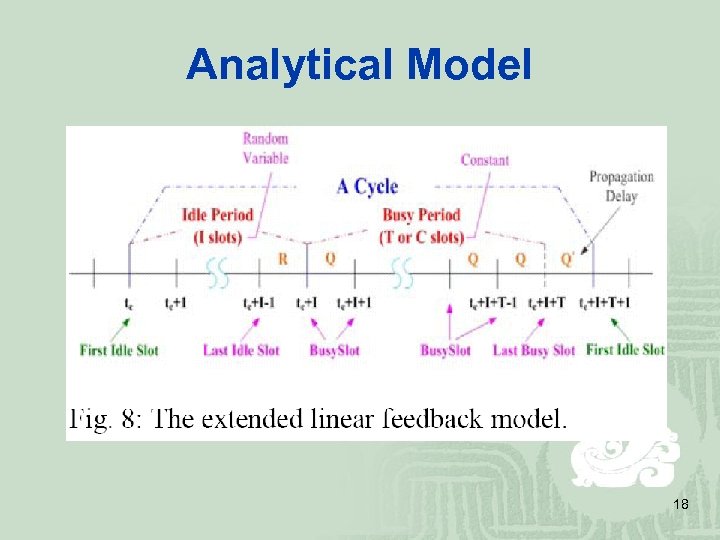 Analytical Model 18
Analytical Model 18
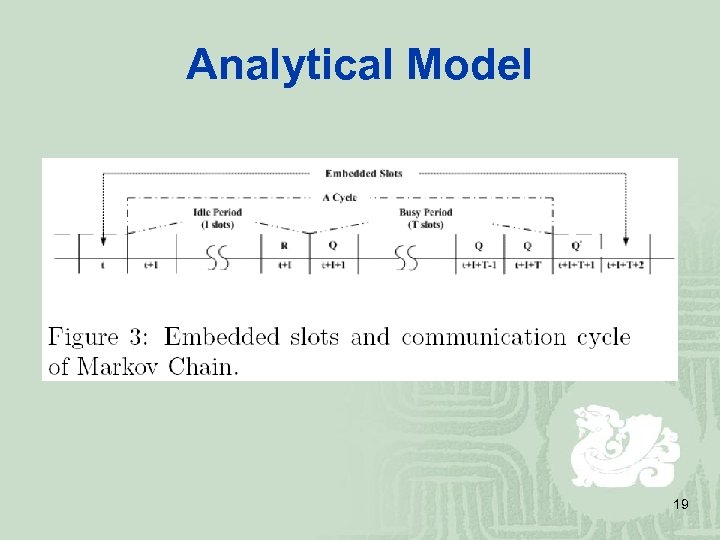 Analytical Model 19
Analytical Model 19
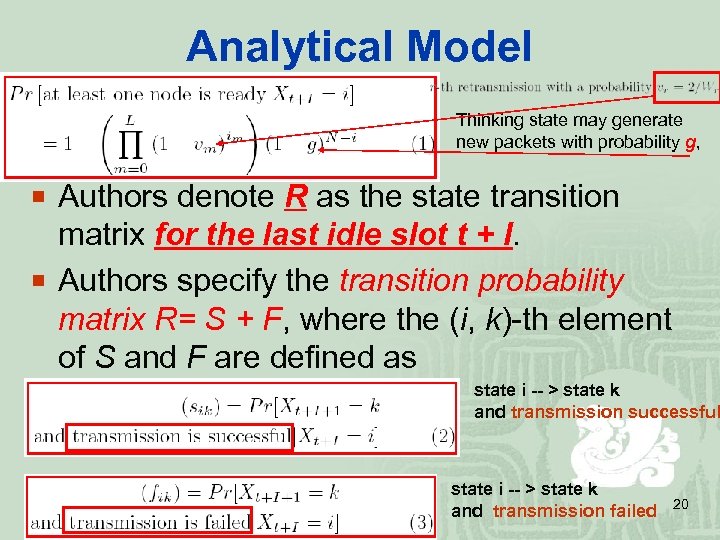 Analytical Model Thinking state may generate new packets with probability g, ¡ Authors denote R as the state transition matrix for the last idle slot t + I. ¡ Authors specify the transition probability matrix R= S + F, where the (i, k)-th element of S and F are defined as state i -- > state k and transmission successful state i -- > state k and transmission failed 20
Analytical Model Thinking state may generate new packets with probability g, ¡ Authors denote R as the state transition matrix for the last idle slot t + I. ¡ Authors specify the transition probability matrix R= S + F, where the (i, k)-th element of S and F are defined as state i -- > state k and transmission successful state i -- > state k and transmission failed 20
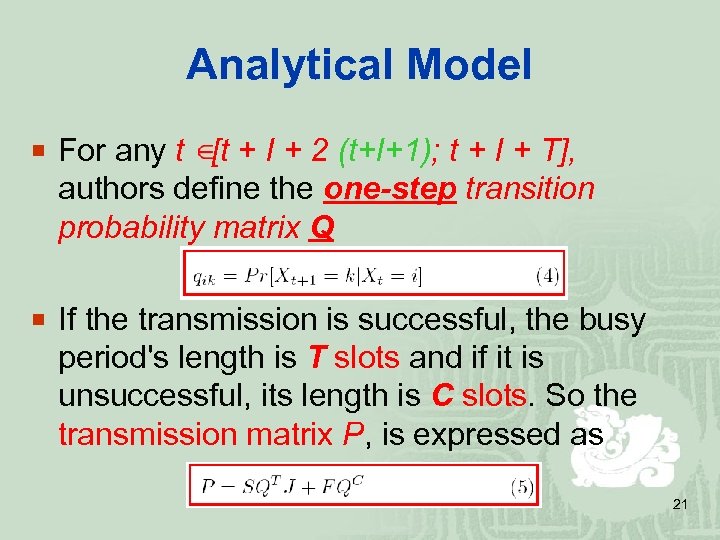 Analytical Model ¡ For any t [t + I + 2 (t+I+1); t + I + T], authors define the one-step transition probability matrix Q ¡ If the transmission is successful, the busy period's length is T slots and if it is unsuccessful, its length is C slots. So the transmission matrix P, is expressed as 21
Analytical Model ¡ For any t [t + I + 2 (t+I+1); t + I + T], authors define the one-step transition probability matrix Q ¡ If the transmission is successful, the busy period's length is T slots and if it is unsuccessful, its length is C slots. So the transmission matrix P, is expressed as 21
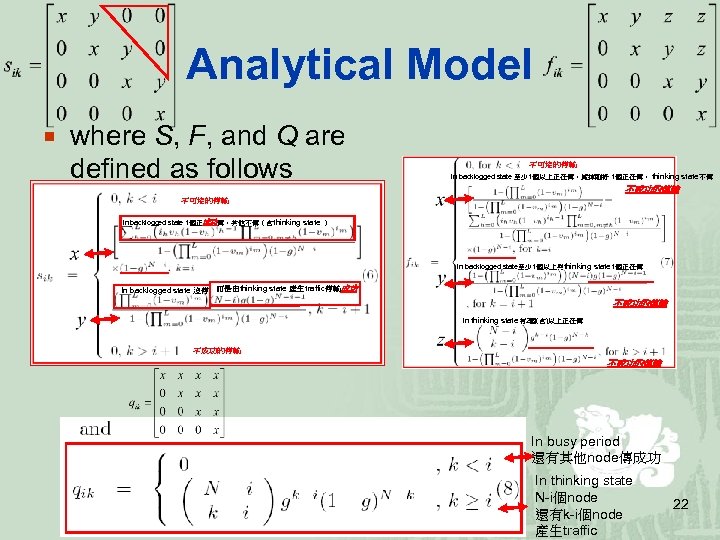 Analytical Model ¡ where S, F, and Q are defined as follows 不可能的傳輸 In backlogged state 至少 1個以上正在傳,減掉剛好 1個正在傳, thinking state 不傳 不成功的傳輸 不可能的傳輸 In backlogged state 1個正成功傳,其他不傳(含thinking state ) In backlogged state至少 1個以上與thinking state 1個正在傳 In backlogged state 沒傳 而是由thinking state 產生traffic傳輸成功 不成功的傳輸 In thinking state 有2個(含)以上正在傳 不成功的傳輸 In busy period 還有其他node傳成功 In thinking state N-i個node 還有k-i個node 產生traffic 22
Analytical Model ¡ where S, F, and Q are defined as follows 不可能的傳輸 In backlogged state 至少 1個以上正在傳,減掉剛好 1個正在傳, thinking state 不傳 不成功的傳輸 不可能的傳輸 In backlogged state 1個正成功傳,其他不傳(含thinking state ) In backlogged state至少 1個以上與thinking state 1個正在傳 In backlogged state 沒傳 而是由thinking state 產生traffic傳輸成功 不成功的傳輸 In thinking state 有2個(含)以上正在傳 不成功的傳輸 In busy period 還有其他node傳成功 In thinking state N-i個node 還有k-i個node 產生traffic 22
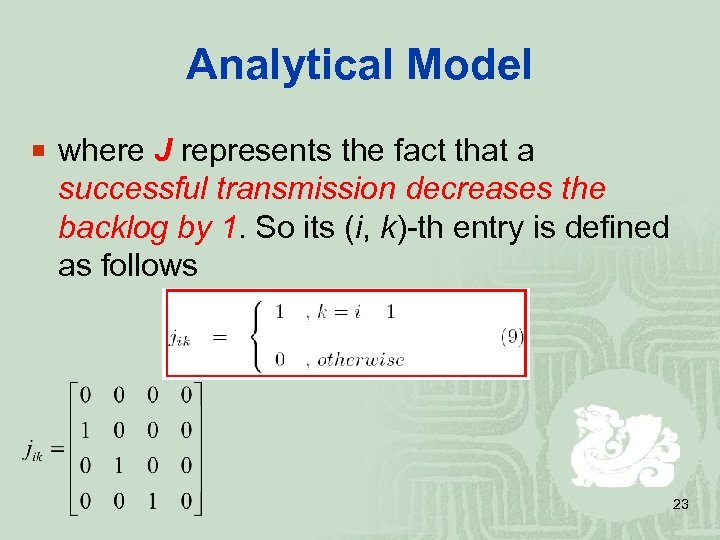 Analytical Model ¡ where J represents the fact that a successful transmission decreases the backlog by 1. So its (i, k)-th entry is defined as follows 23
Analytical Model ¡ where J represents the fact that a successful transmission decreases the backlog by 1. So its (i, k)-th entry is defined as follows 23
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 24
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 24
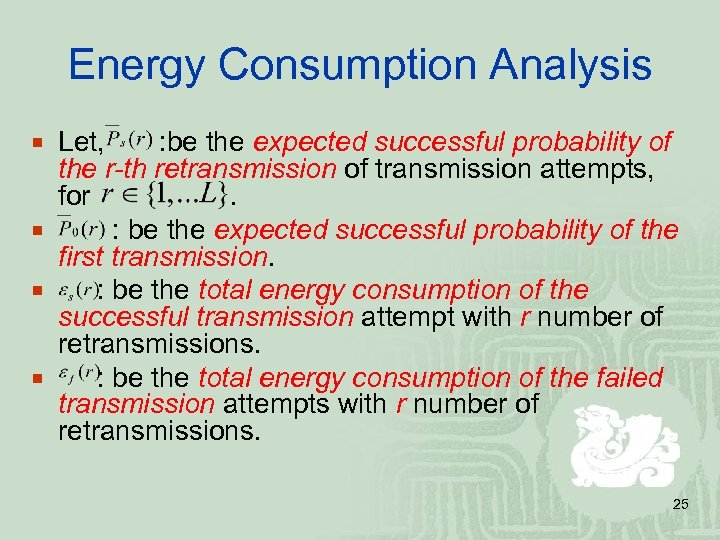 Energy Consumption Analysis ¡ Let, : be the expected successful probability of the r-th retransmission of transmission attempts, for. ¡ : be the expected successful probability of the first transmission. ¡ : be the total energy consumption of the successful transmission attempt with r number of retransmissions. ¡ : be the total energy consumption of the failed transmission attempts with r number of retransmissions. 25
Energy Consumption Analysis ¡ Let, : be the expected successful probability of the r-th retransmission of transmission attempts, for. ¡ : be the expected successful probability of the first transmission. ¡ : be the total energy consumption of the successful transmission attempt with r number of retransmissions. ¡ : be the total energy consumption of the failed transmission attempts with r number of retransmissions. 25
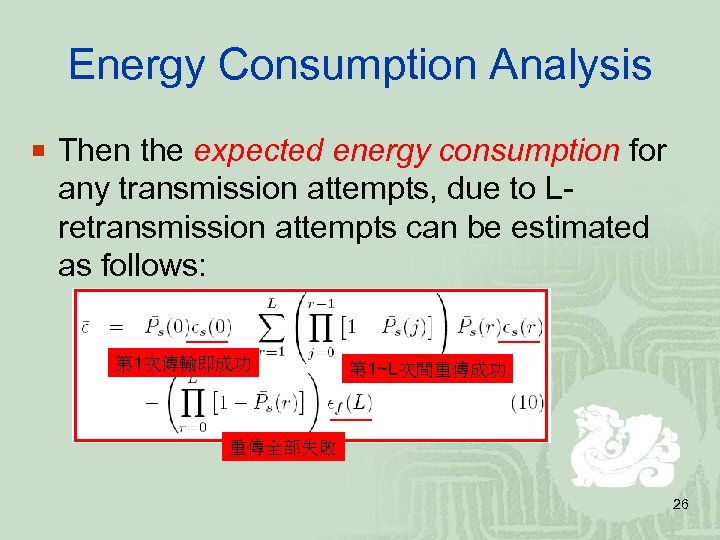 Energy Consumption Analysis ¡ Then the expected energy consumption for any transmission attempts, due to Lretransmission attempts can be estimated as follows: 第 1次傳輸即成功 第 1~L次間重傳成功 重傳全部失敗 26
Energy Consumption Analysis ¡ Then the expected energy consumption for any transmission attempts, due to Lretransmission attempts can be estimated as follows: 第 1次傳輸即成功 第 1~L次間重傳成功 重傳全部失敗 26
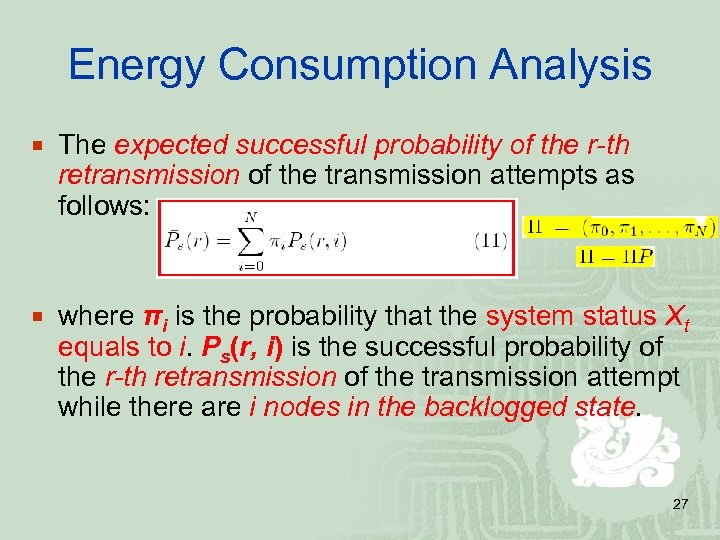 Energy Consumption Analysis ¡ The expected successful probability of the r-th retransmission of the transmission attempts as follows: ¡ where πi is the probability that the system status Xt equals to i. Ps(r, i) is the successful probability of the r-th retransmission of the transmission attempt while there are i nodes in the backlogged state. 27
Energy Consumption Analysis ¡ The expected successful probability of the r-th retransmission of the transmission attempts as follows: ¡ where πi is the probability that the system status Xt equals to i. Ps(r, i) is the successful probability of the r-th retransmission of the transmission attempt while there are i nodes in the backlogged state. 27
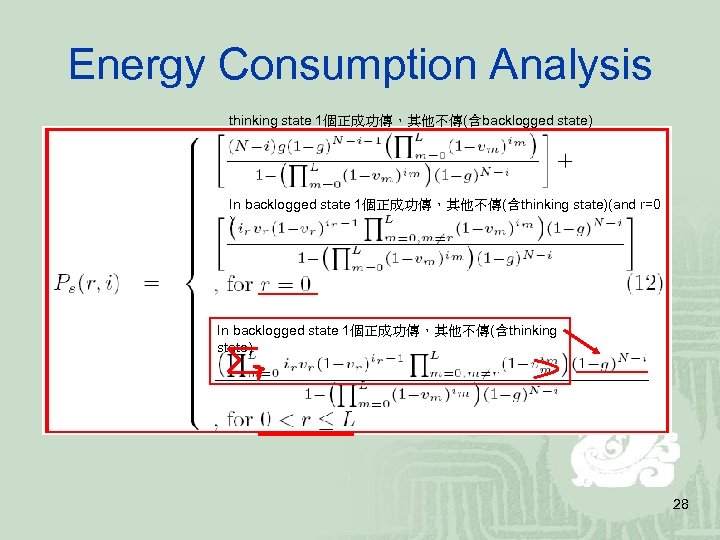 Energy Consumption Analysis thinking state 1個正成功傳,其他不傳(含backlogged state) In backlogged state 1個正成功傳,其他不傳(含thinking state)(and r=0 ) In backlogged state 1個正成功傳,其他不傳(含thinking state) 28
Energy Consumption Analysis thinking state 1個正成功傳,其他不傳(含backlogged state) In backlogged state 1個正成功傳,其他不傳(含thinking state)(and r=0 ) In backlogged state 1個正成功傳,其他不傳(含thinking state) 28
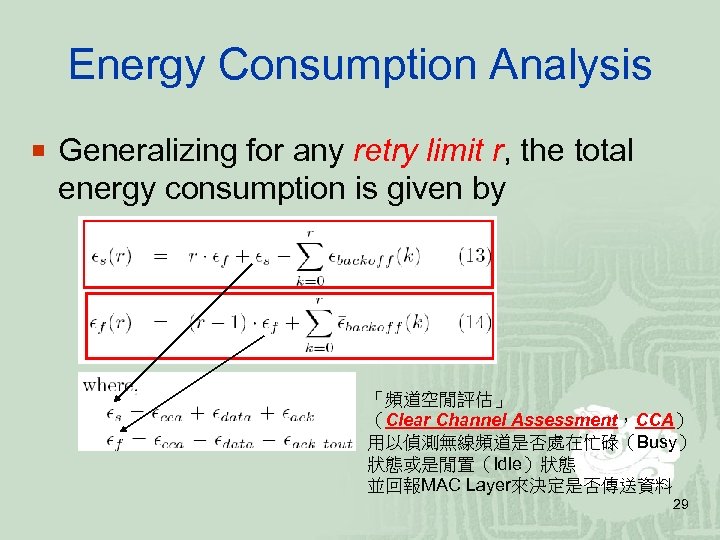 Energy Consumption Analysis ¡ Generalizing for any retry limit r, the total energy consumption is given by 「頻道空閒評估」 (Clear Channel Assessment,CCA) 用以偵測無線頻道是否處在忙碌(Busy) 狀態或是閒置(Idle)狀態 並回報MAC Layer來決定是否傳送資料 29
Energy Consumption Analysis ¡ Generalizing for any retry limit r, the total energy consumption is given by 「頻道空閒評估」 (Clear Channel Assessment,CCA) 用以偵測無線頻道是否處在忙碌(Busy) 狀態或是閒置(Idle)狀態 並回報MAC Layer來決定是否傳送資料 29
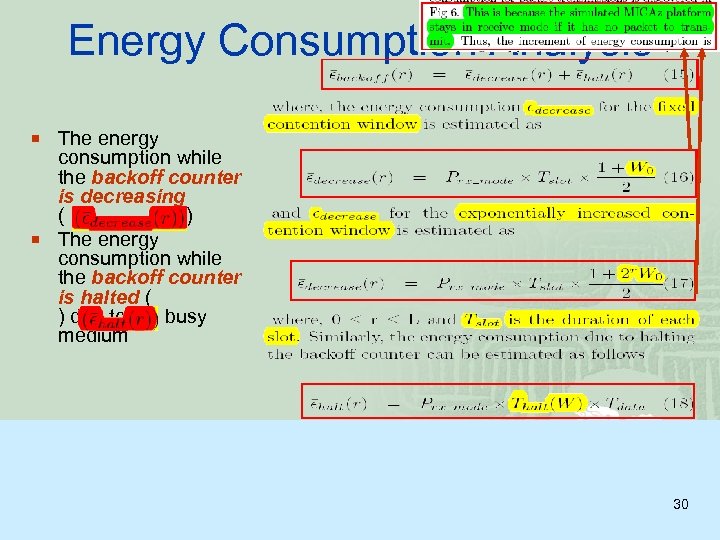 Energy Consumption Analysis ¡ The energy consumption while the backoff counter is decreasing ( ) ¡ The energy consumption while the backoff counter is halted ( ) due to the busy medium 30
Energy Consumption Analysis ¡ The energy consumption while the backoff counter is decreasing ( ) ¡ The energy consumption while the backoff counter is halted ( ) due to the busy medium 30
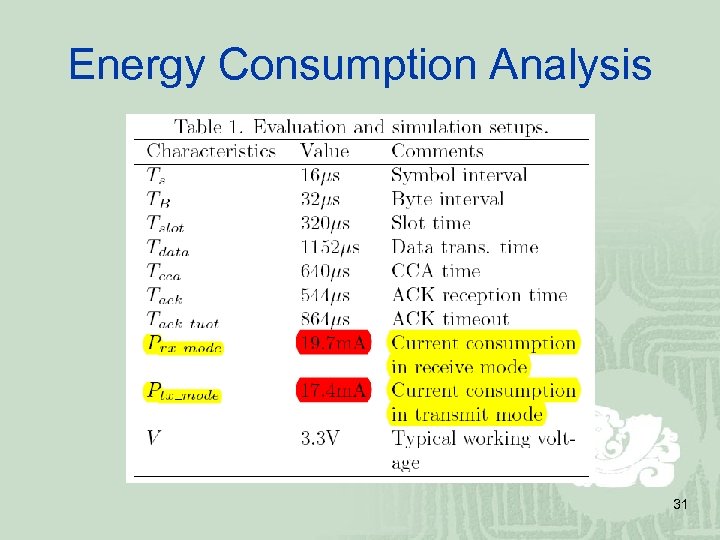 Energy Consumption Analysis 31
Energy Consumption Analysis 31
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 32
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 32
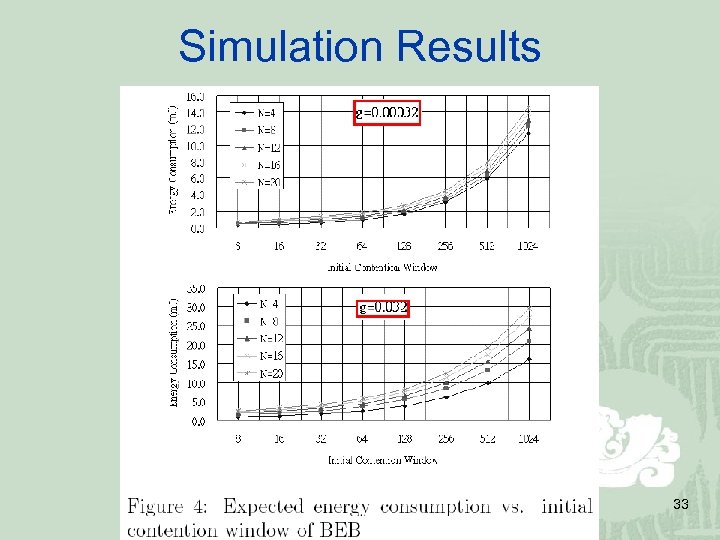 Simulation Results 33
Simulation Results 33
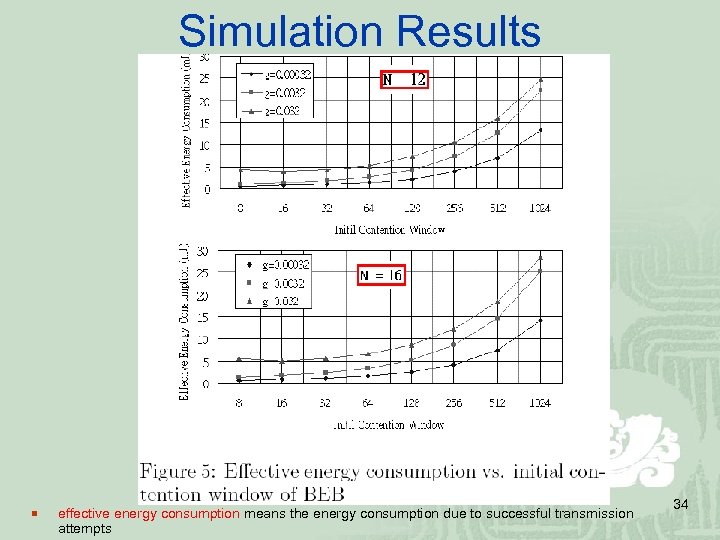 Simulation Results ¡ effective energy consumption means the energy consumption due to successful transmission attempts 34
Simulation Results ¡ effective energy consumption means the energy consumption due to successful transmission attempts 34
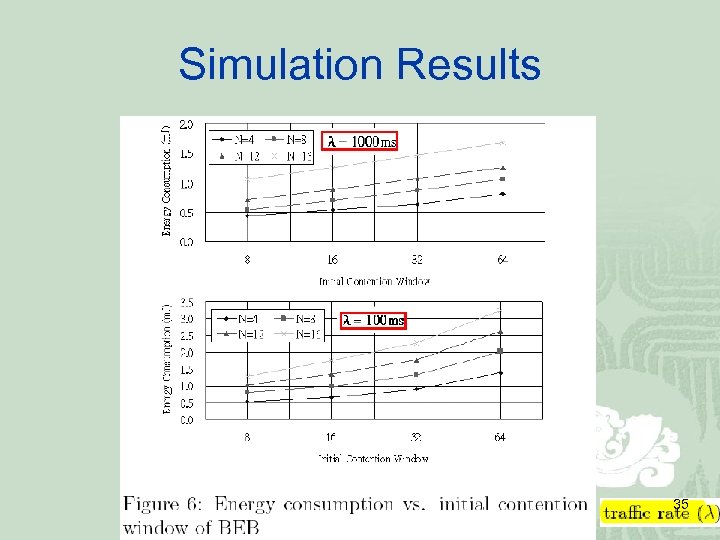 Simulation Results 35
Simulation Results 35
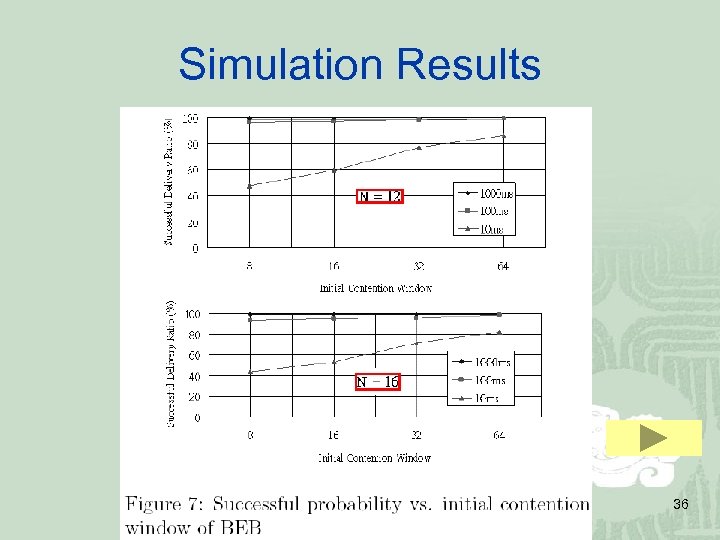 Simulation Results 36
Simulation Results 36
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 37
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 37
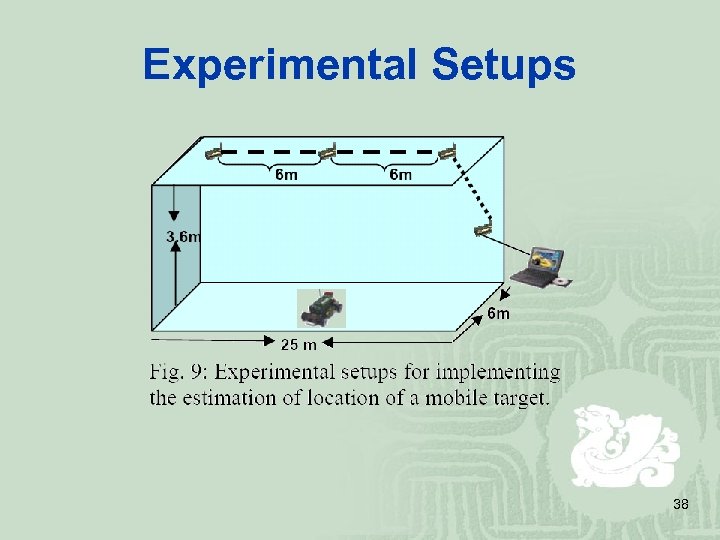 Experimental Setups 38
Experimental Setups 38
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 39
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 39
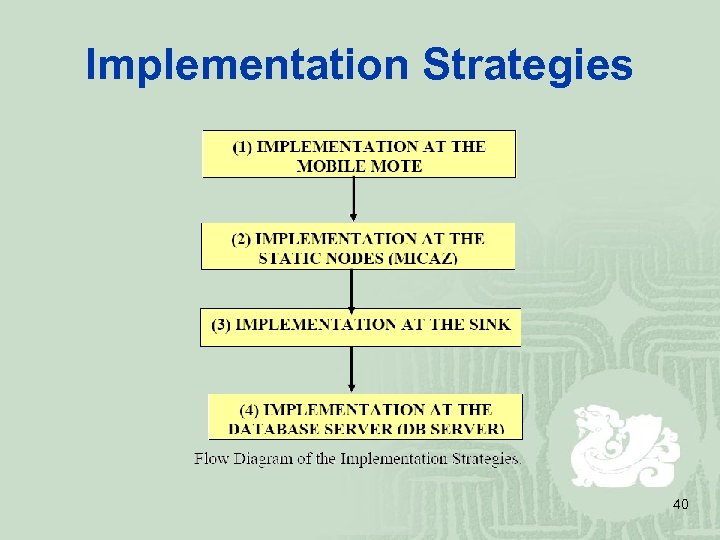 Implementation Strategies 40
Implementation Strategies 40
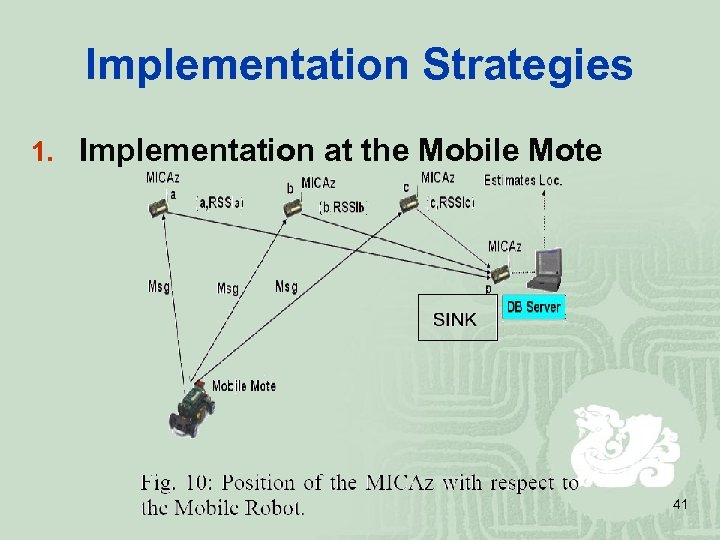 Implementation Strategies 1. Implementation at the Mobile Mote 41
Implementation Strategies 1. Implementation at the Mobile Mote 41
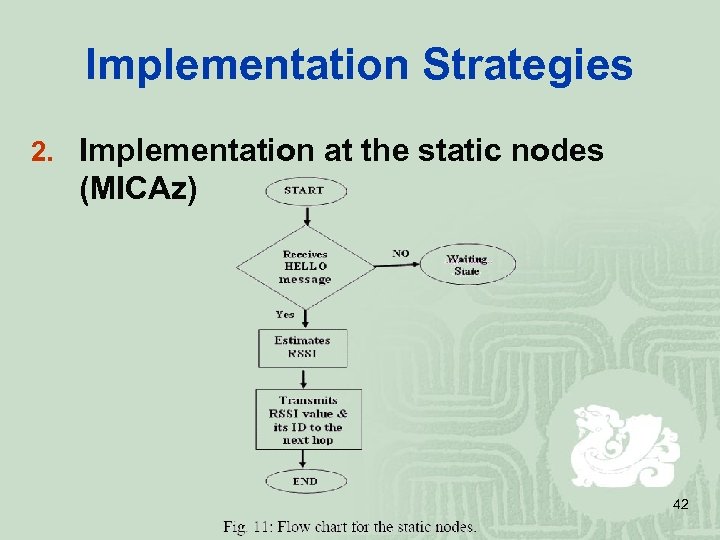 Implementation Strategies 2. Implementation at the static nodes (MICAz) 42
Implementation Strategies 2. Implementation at the static nodes (MICAz) 42
 Implementation Strategies 3. Implementation at the SINK Upon receiving the RSSI values from different static MICAz, The sink compares the RSSI values with corresponding ID of the MICAz. 43
Implementation Strategies 3. Implementation at the SINK Upon receiving the RSSI values from different static MICAz, The sink compares the RSSI values with corresponding ID of the MICAz. 43
 Implementation Strategies 4. Implementation at the Database (Notebook) In order to store the position of the mobile target, authors execute “XListen. exe” in the notebook with a SQL server. Once the “XListen. exe” is executed, the raw data is saved to DBTest. txt. Then authors use JAVA SDK to read those raw data and save it to the SQL database. This JAVA code estimates the position of the target if it is nearer or farther to any static MICAz. 44
Implementation Strategies 4. Implementation at the Database (Notebook) In order to store the position of the mobile target, authors execute “XListen. exe” in the notebook with a SQL server. Once the “XListen. exe” is executed, the raw data is saved to DBTest. txt. Then authors use JAVA SDK to read those raw data and save it to the SQL database. This JAVA code estimates the position of the target if it is nearer or farther to any static MICAz. 44
 Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 45
Outline ¡ Introduction ¡ Boundary node Selection and Target ¡ ¡ ¡ Detection Protocols Analytical Model Energy Consumption Analysis Simulation Results Experimental Setups Implementation Strategies Conclusion and Future Work 45
 Conclusion ¡ Performance analysis show that the energy consumption of packet transmission in wireless sensor networks is increased with the increment of contention window traffic load network population ¡ An optimal contention window can be derived from the use of fixed contention window to achieve the best effective energy consumption. 46
Conclusion ¡ Performance analysis show that the energy consumption of packet transmission in wireless sensor networks is increased with the increment of contention window traffic load network population ¡ An optimal contention window can be derived from the use of fixed contention window to achieve the best effective energy consumption. 46
 Future Work ¡ Multi-layer boundary nodes problem Set cover problem ¡ Maximize subject to 1. Energy constraint 2. Coverage constraint ¡ Tradeoff Energy consumption vs. Successful delivery ratio 47
Future Work ¡ Multi-layer boundary nodes problem Set cover problem ¡ Maximize subject to 1. Energy constraint 2. Coverage constraint ¡ Tradeoff Energy consumption vs. Successful delivery ratio 47
![References [1] T. He, S. Krishnamurthy, L. Luo, T. Yan, L. Gu, R. Stoleru, References [1] T. He, S. Krishnamurthy, L. Luo, T. Yan, L. Gu, R. Stoleru,](https://present5.com/presentation/eb0ed6eb37466af80f18566bc064e081/image-48.jpg) References [1] T. He, S. Krishnamurthy, L. Luo, T. Yan, L. Gu, R. Stoleru, G. Zhou, Q. Cao, P. Vicaire, J. A. Stankovic, T. F. Abdelzaher, J. Hui and B. Krogh, ``Vigil. Net: An Integrated Sensor Network System for Energy-efficient Surveillance, " ACM Trans. on Sensor Networks, Vol. 2, Issue 1, pp. 1 -38, Feb. 2006. [2] J. Aslam, Z. Butler, F. Constantin, V. Crespi, G. Cybenko, and D. Rus, ``Tracking a Moving Object with a Binary Sensor Network, " in Proc. 1 st International Conference on Embedded Networked Sensor Systems, pp. 150 -161, Los Angeles, California, USA, Nov. 2003. [3] K. Mechitov, S. Sundresh, Y. Kwon, and G. Agha, ``Cooperative Tracking with Binary. Detection Sensor Networks, " in Proc. 1 st International Conference on Embedded Networked Sensor Systems, pp. 332 -333, Los Angeles, California, USA, Nov. 2003. [4] S. P. M. Tran and T. A. Yang, ``A Novel Target Movement Model and Energy Efficient Target Tracking in Sensor Networks, " in Proc. 37 th SIGCSE Technical Symposium on Computer Science Education, Vol. 38, Issue 1, pp. 97 -101, Houston, Texas, USA, Mar. 2006. [5] Y. Xu, J. Winter, and W. C. Lee, ``Prediction Based Strategies for Energy Saving in Object Tracking Sensor Networks, " in Proc. IEEE International Conference on Mobile Data Management, pp. 346 -357, Berkeley, California, USA, Jan. 2004. [6] Y. Xu, J. Winter, and W. C. Lee, ``Dual Prediction-based Reporting Mechanism for Object Tracking Sensor Networks, " in Proc. 1 st Annual International Conference on Mobile and Ubiquitous Systems: Networking and Services, pp. 154 -163, Boston, Massachusetts, USA, Aug. 2004. [7] C. Y. Lin, W. C. Peng and Y. C. Tseng, ``Efficient in-Network Moving Object Tracking in Wireless Sensor Networks, “ IEEE Trans. on Mobile Computing, Vol. 5, Issue 8, pp. 1044 -1056, Aug. 2006. [8] G. T. Sibley, M. H. Rahimi, G. S. Sukhatme, “Robomote: A Tiny Mobile Robot Platform 48 for Large-Scale Sensor Networks, " in Proc. IEEE International Conference on Robotics and Automation, pp. 1143 -1148, USA, Sep. , 2002.
References [1] T. He, S. Krishnamurthy, L. Luo, T. Yan, L. Gu, R. Stoleru, G. Zhou, Q. Cao, P. Vicaire, J. A. Stankovic, T. F. Abdelzaher, J. Hui and B. Krogh, ``Vigil. Net: An Integrated Sensor Network System for Energy-efficient Surveillance, " ACM Trans. on Sensor Networks, Vol. 2, Issue 1, pp. 1 -38, Feb. 2006. [2] J. Aslam, Z. Butler, F. Constantin, V. Crespi, G. Cybenko, and D. Rus, ``Tracking a Moving Object with a Binary Sensor Network, " in Proc. 1 st International Conference on Embedded Networked Sensor Systems, pp. 150 -161, Los Angeles, California, USA, Nov. 2003. [3] K. Mechitov, S. Sundresh, Y. Kwon, and G. Agha, ``Cooperative Tracking with Binary. Detection Sensor Networks, " in Proc. 1 st International Conference on Embedded Networked Sensor Systems, pp. 332 -333, Los Angeles, California, USA, Nov. 2003. [4] S. P. M. Tran and T. A. Yang, ``A Novel Target Movement Model and Energy Efficient Target Tracking in Sensor Networks, " in Proc. 37 th SIGCSE Technical Symposium on Computer Science Education, Vol. 38, Issue 1, pp. 97 -101, Houston, Texas, USA, Mar. 2006. [5] Y. Xu, J. Winter, and W. C. Lee, ``Prediction Based Strategies for Energy Saving in Object Tracking Sensor Networks, " in Proc. IEEE International Conference on Mobile Data Management, pp. 346 -357, Berkeley, California, USA, Jan. 2004. [6] Y. Xu, J. Winter, and W. C. Lee, ``Dual Prediction-based Reporting Mechanism for Object Tracking Sensor Networks, " in Proc. 1 st Annual International Conference on Mobile and Ubiquitous Systems: Networking and Services, pp. 154 -163, Boston, Massachusetts, USA, Aug. 2004. [7] C. Y. Lin, W. C. Peng and Y. C. Tseng, ``Efficient in-Network Moving Object Tracking in Wireless Sensor Networks, “ IEEE Trans. on Mobile Computing, Vol. 5, Issue 8, pp. 1044 -1056, Aug. 2006. [8] G. T. Sibley, M. H. Rahimi, G. S. Sukhatme, “Robomote: A Tiny Mobile Robot Platform 48 for Large-Scale Sensor Networks, " in Proc. IEEE International Conference on Robotics and Automation, pp. 1143 -1148, USA, Sep. , 2002.
![References (Authors) [9] “Power Control Based Topology Construction for the Distributed Wireless Sensor Networks”, References (Authors) [9] “Power Control Based Topology Construction for the Distributed Wireless Sensor Networks”,](https://present5.com/presentation/eb0ed6eb37466af80f18566bc064e081/image-49.jpg) References (Authors) [9] “Power Control Based Topology Construction for the Distributed Wireless Sensor Networks”, accepted for publication in Computer Communications (SCI), September, 2006. [10] “Energy Efficiency Modeling and Analysis in Wireless Sensor Networks”, published in the Proc. of IEEE, Aus. Wireless Conference, March, 2006, Sydney, Australia. [11] “Boundary Node Selection and Target Detection in Wireless Sensor Network”, under review of IEEE, ICITA, China, 2007. [12] “A Routing Protocol for the Bluetooth Scatternet” published online in Wireless Personal Communications (SCI), September, 2006. 49
References (Authors) [9] “Power Control Based Topology Construction for the Distributed Wireless Sensor Networks”, accepted for publication in Computer Communications (SCI), September, 2006. [10] “Energy Efficiency Modeling and Analysis in Wireless Sensor Networks”, published in the Proc. of IEEE, Aus. Wireless Conference, March, 2006, Sydney, Australia. [11] “Boundary Node Selection and Target Detection in Wireless Sensor Network”, under review of IEEE, ICITA, China, 2007. [12] “A Routing Protocol for the Bluetooth Scatternet” published online in Wireless Personal Communications (SCI), September, 2006. 49
 50
50
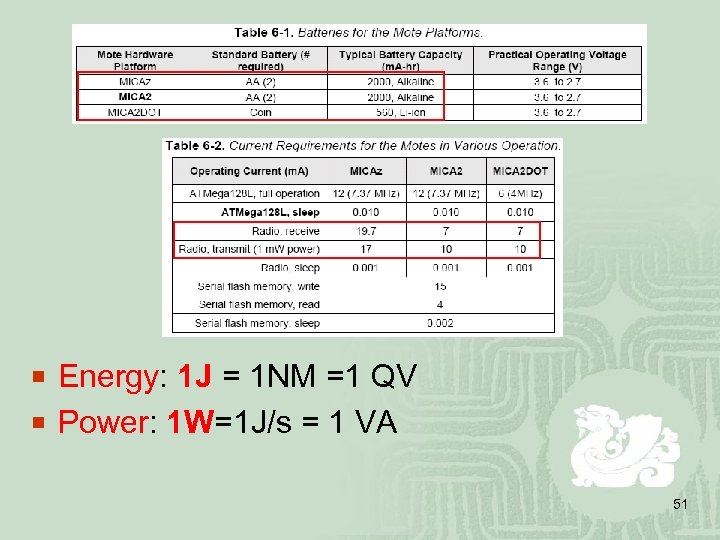 ¡ Energy: 1 J = 1 NM =1 QV ¡ Power: 1 W=1 J/s = 1 VA 51
¡ Energy: 1 J = 1 NM =1 QV ¡ Power: 1 W=1 J/s = 1 VA 51
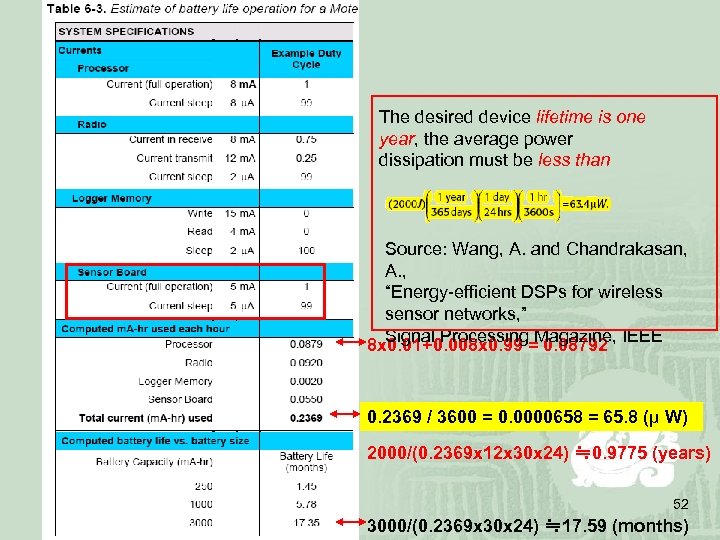 The desired device lifetime is one year, the average power dissipation must be less than Source: Wang, A. and Chandrakasan, A. , “Energy-efficient DSPs for wireless sensor networks, ” Signal Processing Magazine, IEEE 8 x 0. 01+0. 008 x 0. 99 = 0. 08792 0. 2369 / 3600 = 0. 0000658 = 65. 8 (μ W) 2000/(0. 2369 x 12 x 30 x 24) ≒ 0. 9775 (years) 52 3000/(0. 2369 x 30 x 24) ≒ 17. 59 (months)
The desired device lifetime is one year, the average power dissipation must be less than Source: Wang, A. and Chandrakasan, A. , “Energy-efficient DSPs for wireless sensor networks, ” Signal Processing Magazine, IEEE 8 x 0. 01+0. 008 x 0. 99 = 0. 08792 0. 2369 / 3600 = 0. 0000658 = 65. 8 (μ W) 2000/(0. 2369 x 12 x 30 x 24) ≒ 0. 9775 (years) 52 3000/(0. 2369 x 30 x 24) ≒ 17. 59 (months)
 Q&A Thank You for Your Attention. 53/53
Q&A Thank You for Your Attention. 53/53


