6718c622319a202e495c5a8a2cd2c9b7.ppt
- Количество слайдов: 94

Mobile Handsets: A Panoramic Overview Dong Xuan Associate Professor CSE Dept. , The Ohio State University

Outline • • • Introduction Handset Architecture Handset Operating Systems Networking Applications Security Risks and Mitigation Strategies

What Is A Mobile Handset? • A mobile handset (handset) is an electronic device that provides services to users, e. g. : – – Managing address book Scheduling calendar Cellular telephony Accessing Internet, email • Handsets include smartphones and PDAs Example handsets: Apple i. Phone, Black. Berry Storm, Palm Treo. Pro

Handsets: Your Next Computer? • Handsets’ small form factor, mobility have yielded meteoric sales [1] – 3. 3 billion mobile phone subscriptions as of Jan. 2008 – 2. 7 billion subscriptions correspond to one person; some people have multiple phones! • Rapid replacement rate: young adults replace phones every 6 months in South Korea [1] • These statistics are just for phones • Your handset: your next computer? [2]
![What’s Inside a Mobile Handset? Source: [3] What’s Inside a Mobile Handset? Source: [3]](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-5.jpg)
What’s Inside a Mobile Handset? Source: [3]
Handset Architecture (1) • Handsets use several hardware components: – – – – Microprocessor ROM RAM Digital signal processor Radio module Microphone and speaker Hardware interfaces LCD display

Handset Architecture (2) • Handsets store system data in electronically-erasable programmable read -only memory (EEPROM) – Service providers can reprogram phones without requiring physical access to memory chips • OS is stored in ROM (nonvolatile memory) • Most handsets also include subscriber identity module (SIM) cards
Handset Microprocessors • Handsets use embedded processors – Intel, ARM architectures dominate market. Examples include: • Black. Berry 8700, uses Intel PXA 901 chip [4] • i. Phone, uses Samsung ARM 1100 chip [5] – Low power use and code size are crucial [3] – Microprocessor vendors often package all the chip’s functionality in a single chip (packageon-package) for maximum flexibility
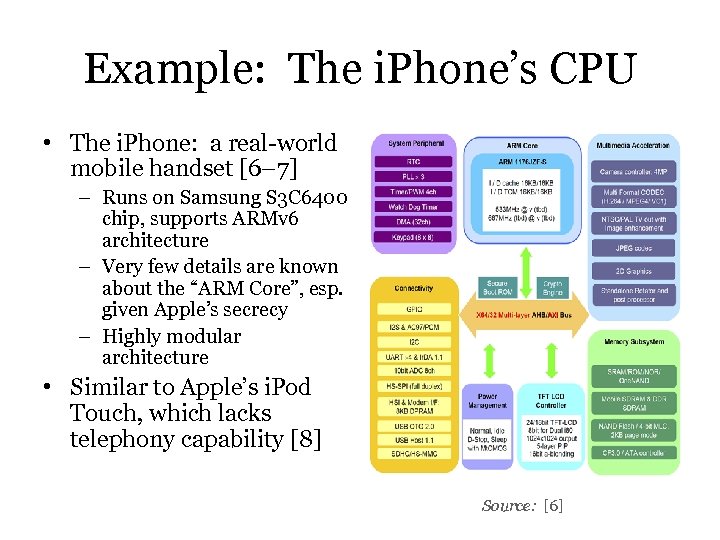
Example: The i. Phone’s CPU • The i. Phone: a real-world mobile handset [6– 7] – Runs on Samsung S 3 C 6400 chip, supports ARMv 6 architecture – Very few details are known about the “ARM Core”, esp. given Apple’s secrecy – Highly modular architecture • Similar to Apple’s i. Pod Touch, which lacks telephony capability [8] Source: [6]
SIM Cards • They include their own microprocessor and 16 KB – 4 MB EEPROM • They come in two sizes • Their versatility arises from portability of information – SIM card identifies subscriber to network – Stores personal information, address books, messages, service-related information
Other Memory Cards • Some handsets include other peripheral memory cards: – Compact Flash – Multimedia Card – Secure Digital • Handsets synchronize with a computer • Nowadays, computers include slots of various sizes to hold these memory cards

Handset Operating Systems • Currently, handsets run several OSes: – – – Symbian OS i. Phone OS (an embedded version of OS X) Windows Mobile Black. Berry OS Google Android Platform (based on Linux) • With the exceptions of Symbian and Android, these OSes are proprietary[9– 10] • Telecom carriers frequently “lock down” handset firmware, OSes to prevent user modifications

Handset OS Usage • According to British analysis firm Canalys, handset OS usage in 3 Q 2008 had the following ranking (most to least): [11] 1. 2. 3. 4. 5. 6. • • Symbian OS i. Phone OS Black. Berry OS Windows Mobile Linux (Android, etc. ) Others i. Phone OS surged ahead of Black. Berry OS, but with new Black. Berries and Android phones, this ranking may easily change in the future [11] We’ll now examine each OS individually

Symbian OS • • • Dominant OS in the mobile handset market Runs exclusively on ARM processors Owned by British firm Symbian Ltd. Descendant of Psion EPOC OS (dev. in 1990 s) Sony Ericsson, Nokia, et al. bought shares in the firm until Nokia bought Symbian in 2008, formed Symbian Foundation to further future open handset development [12] • Nokia plans to open-source the OS by 2009 [9]
![Design of Symbian OS • Based on Psion EPOC; desktop OS features include: [13] Design of Symbian OS • Based on Psion EPOC; desktop OS features include: [13]](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-15.jpg)
Design of Symbian OS • Based on Psion EPOC; desktop OS features include: [13] – “Bare-bones” microkernel (nanokernel) – Pre-emptive multitasking – Memory protection • Handset-centric design, can operate several months without reboot • Supports multiple UIs based on smartphone form factor (e. g. , 320 × 240)

Symbian OS Devices • Numerous handsets use Symbian OS; UIs largely based on manufacturer & device – Nokia S 60: includes J 2 ME, std. UI (mostly Nokia phones) – Nokia S 80: QWERTY keyboard, Web browser, enterprise office-doc. support (older Nokia Communicators) – Nokia S 90: used only on Nokia 7710 – UIQ: Sony Ericsson/Motorola GUI platform used primarily on those companies’ handsets – FOMA platform: closed-dev. software platform used by handsets on NTT Do. Co. Mo’s network (Japan)
![Symbian OS v 9 Architecture Source: [15] (heavily modified) Symbian OS v 9 Architecture Source: [15] (heavily modified)](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-17.jpg)
Symbian OS v 9 Architecture Source: [15] (heavily modified)

Symbian OS Development • Native language is C++ – Nokia provides free Eclipse-based Carbide. c++ development tools, Carbide. vs Visual Studio plugin – Mac & Linux development is possible • Can program in many other languages: C, Java, Ruby, Python, Perl, OPL, Visual Basic, Simkin • Applications needing any capabilities beyond bare minimum must be cryptographically signed (see http: //www. symbiansigned. com) • Can also program in Adobe Flash Lite (mobile version of Flash)

i. Phone OS • Runs on both the i. Phone and i. Pod Touch • Variation of Mach microkernel-based OS X that fits in 512 MB flash memory, runs on ARM architecture [21] • Four abstraction layers: Core OS, Core Services, Media, Cocoa Touch [22] • Core Animation and Power. VR MBX 3 D hardware provide interface animations • 320 × 480 LCD display that supports multitouch gestures

i. Phone Developer Program • i. Phone Developer Program provides dev. tools, i. Phone emulator, means to upload to App Store (SDK) • To download SDK, you must apply to be a member, pay fees – Standard Developer: $99 – Enterprise Developer: $299 – Exception: Apple’s free i. Phone Developer University Program for higher-ed. institutions [23] • SDK only runs on Mac OS X Leopard on Intelbased Macs (go figure)

i. Phone Web App Development • You can develop Web apps for i. Phone – so long as they run on Safari [24] • Safari features: [25– 26] – Auto-resizes Web pages to fit browser size – Multi-touch functionality – XHTML 1. 1, CSS 2. 1, Java. Script, W 3 C DOM Level 2, AJAX technology, cookies, … • Does not support Flash or Java • i. Phone Web apps should: – Minimize user awareness of browser experience – Reproduce control style, layout, behavior of i. Phone apps – Integrate with built-in i. Phone features & services

Black. Berry OS • Black. Berry OS is Research in Motion’s (RIM’s) proprietary OS for its Black. Berry handsets • Provides multitasking, heavily uses Black. Berry input devices, e. g. , thumbwheel • Current OS 4 provides a subset of Java’s Mobile Information Device Profile (MIDP) 2. 0 • Developers can use these APIs, proprietary APIs to write software • All applications must be digitally signedso to “link” an app with the developer

Black. Berry Software • Email from Black. Berry service, MS Exchange, Domino, Yahoo, etc. can be “pushed” to the handset • Can view PDF, MS Word, Excel, Power. Point attachments • Black. Berry Browser (only supports Java. Script) • Other online apps include: – Black. Berry Maps – Facebook services – Yahoo Messenger, Google Talk • Calendar, Address Book, and PIM Sync via USB • GPS • See http: //www. blackberry. com for much more information about handset and desktop software
Black. Berry Wireless Platform • RIM provides standards-based platform and developer tools to develop and deploy custom wireless applications – HTML Web browser – Java Mobile Edition development tools –. NET applications • Black. Berry handsets support standard networking protocols and connect to any type of server application
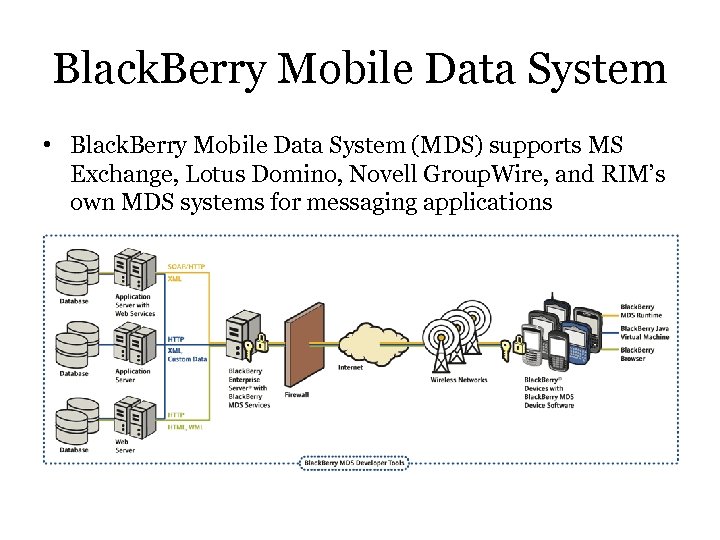
Black. Berry Mobile Data System • Black. Berry Mobile Data System (MDS) supports MS Exchange, Lotus Domino, Novell Group. Wire, and RIM’s own MDS systems for messaging applications

Black. Berry Mobile Voice System • With this service, there’s only one business number Black. Berry users must remember • Calls are routed to a Black. Berry handset, regardless of whether the call is directed to an office or mobile phone [27] • Provides security and authentication through Black. Berry Enterprise Servers [28] • IT administrators can lock down handsets, route calls through their telecom infrastructure, etc. [27– 28]
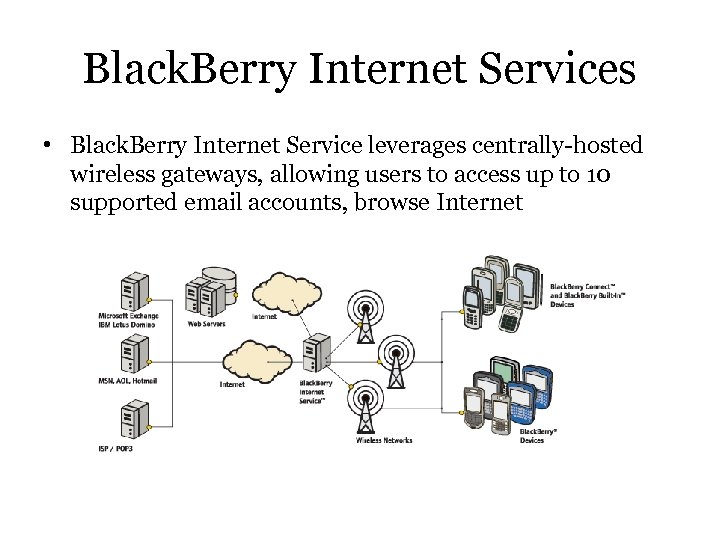
Black. Berry Internet Services • Black. Berry Internet Service leverages centrally-hosted wireless gateways, allowing users to access up to 10 supported email accounts, browse Internet

Black. Berry Developer Tools • RIM provides several development tools: – Black. Berry MDS Studio • Developers can quickly create rich client apps using component-based drag-and-drop approach • Tool requires MDS runtime – Black. Berry plugin for MS Visual Studio (development on MDS platform) – Black. Berry Java Development Environment (JDE) • Provides IDE, simulation tools for Java ME app for Javabased Black. Berry so developers can create standalone or client-server apps

Windows Mobile • Windows Mobile is powered by Microsoft’s Windows CE embedded OS; Windows CE runs on x 86, MIPS, ARM, Hitachi Super. H processors • Latest version, 6. 1, includes Windows Live services, Exchange 2007 mail access • Designed to closely mimic desktop Windows: – Windows Mobile 6. 1 includes mobile versions of Office applications, Outlook (w/HTML email), Internet Explorer, Windows Media Player – SQL Server 2005 included in ROM –. NET Compact Framework 2. 0 included
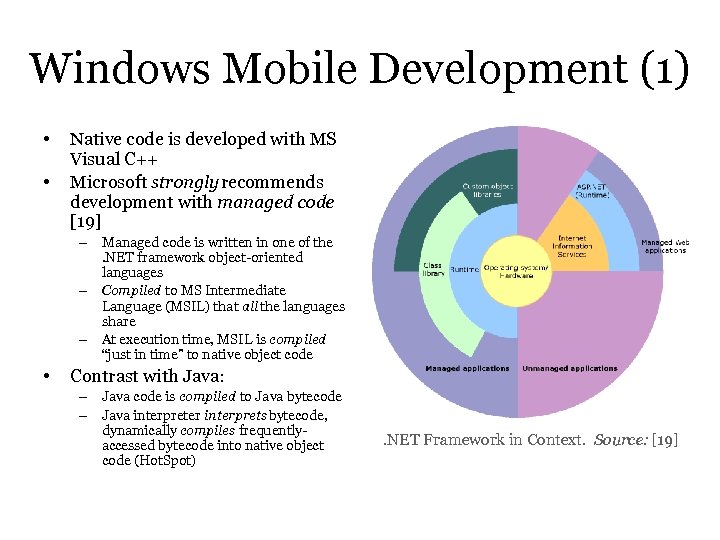
Windows Mobile Development (1) • • Native code is developed with MS Visual C++ Microsoft strongly recommends development with managed code [19] – Managed code is written in one of the. NET framework object-oriented languages – Compiled to MS Intermediate Language (MSIL) that all the languages share – At execution time, MSIL is compiled “just in time” to native object code • Contrast with Java: – Java code is compiled to Java bytecode – Java interpreter interprets bytecode, dynamically compiles frequentlyaccessed bytecode into native object code (Hot. Spot) . NET Framework in Context. Source: [19]

Windows Mobile Development (2) • Windows Mobile development tools include: – Plugins for MS Visual Studio 2005, 2008, etc. – SDKs for Windows Mobile-based handsets – Microsoft gives away Visual Studio to students for free with its Dream. Spark program [20]

Android Mobile Handset Platform • • Android is a software development platform for mobile handsets that is based on Linux Developed by Google and Open Handset Alliance (OHA) for different handset manufacturers – The Alliance includes T-Mobile, Sprint Nextel, Google, Intel, Samsung, Wind River Systems, et al. [29] – Its purpose is to build a fully free and open mobile handset platform to facilitate development of handsets, software, services [30] • First Android-based handset is TMobile G 1 [31]
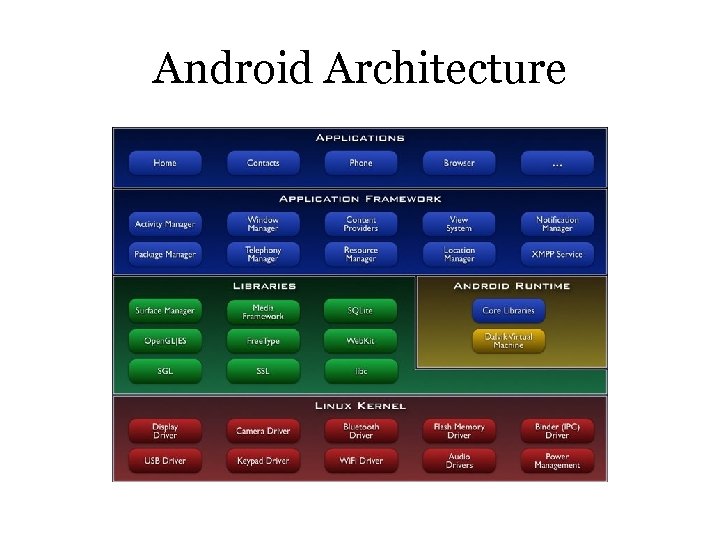
Android Architecture

Android Features and Software • Features – – 3 D: Open. GL ES 1. 0 SQLite: Database engine Web. Kit: Web browser Dalvik: Register-based VM similar to Java VM [32] – Free. Type: Bitmap and vector font rendering – Connectivity: Bluetooth, 802. 11, GPS • Core Applications – Email client, SMS program, calendar, Google Maps (and Apps), browser, etc. – Written in Java • App Framework – Full access to same framework APIs – Architecture designed for component reuse • Runtime – Core C++ library – Multiple Dalvik VMs run in a process, rely on Linux kernel for process isolation [32]

Android SDK • Android SDK provides required tools and APIs to develop apps on Android platform using Java – Android is licensed under the Apache open-source license – The Android Development Tools (ADT) Eclipse plugin eases development – Download the Android SDK at http: //code. google. com/android/ and the Eclipse plugin at https: //dl-ssl. google. com/android/eclipse

Palm OS • Palm OS originally designed by Palm Computing Inc. for Palm handsets, sold to Japanese firm ACCESS [16] • From Jan. 2004 – Jun. 2005, there has been no development on Palm OS past v 6. 1 [16] • ACCESS and Palm are working on new versions of the OS that are Linux-based [16] – ACCESS’ version is called the ACCESS Linux Platform – Palm’s version will be called Palm OS; should be available Q 1 2009

Handset Networking • Handsets communicate with each other and with service providers via many networking technologies • There are two “classes” of these technologies: – Cellular telephony – Wireless networking • Most handsets support both, some also support physical connections such as USB
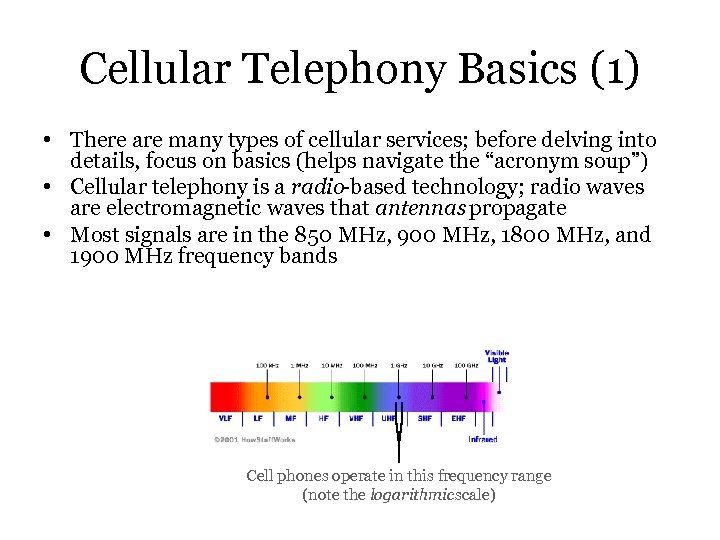
Cellular Telephony Basics (1) • There are many types of cellular services; before delving into details, focus on basics (helps navigate the “acronym soup”) • Cellular telephony is a radio-based technology; radio waves are electromagnetic waves that antennas propagate • Most signals are in the 850 MHz, 900 MHz, 1800 MHz, and 1900 MHz frequency bands Cell phones operate in this frequency range (note the logarithmic scale)
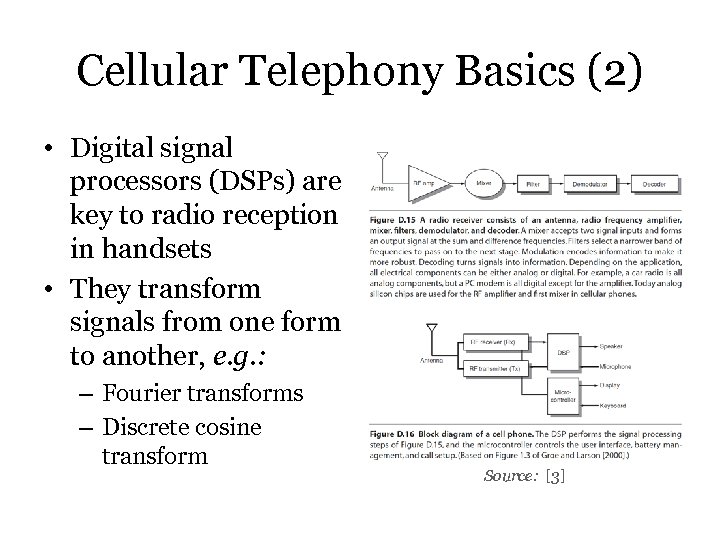
Cellular Telephony Basics (2) • Digital signal processors (DSPs) are key to radio reception in handsets • They transform signals from one form to another, e. g. : – Fourier transforms – Discrete cosine transform Source: [3]
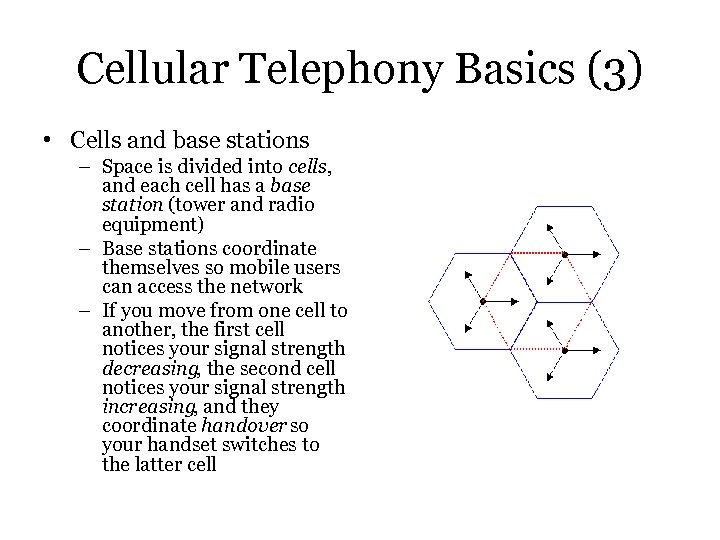
Cellular Telephony Basics (3) • Cells and base stations – Space is divided into cells, and each cell has a base station (tower and radio equipment) – Base stations coordinate themselves so mobile users can access the network – If you move from one cell to another, the first cell notices your signal strength decreasing, the second cell notices your signal strength increasing, and they coordinate handover so your handset switches to the latter cell
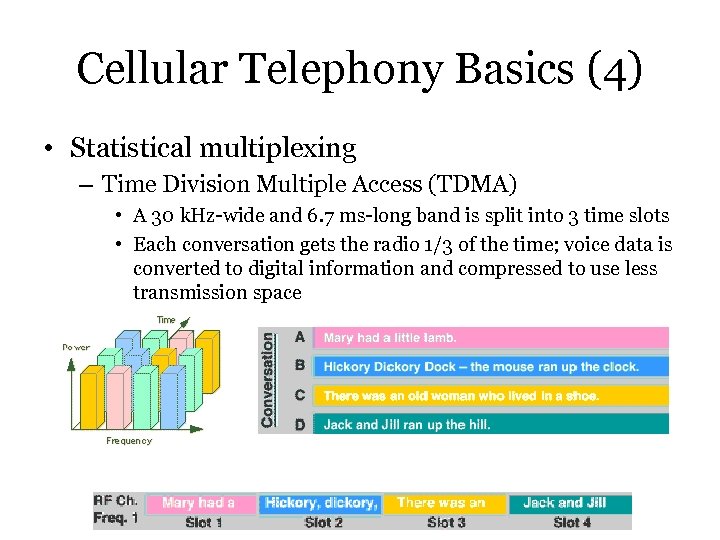
Cellular Telephony Basics (4) • Statistical multiplexing – Time Division Multiple Access (TDMA) • A 30 k. Hz-wide and 6. 7 ms-long band is split into 3 time slots • Each conversation gets the radio 1/3 of the time; voice data is converted to digital information and compressed to use less transmission space
Cellular Telephony Basics (5) • Statistical multiplexing cont’d. – Frequency Division Multiple Access (FDMA) • Analogous to TDMA, but each conversation uses a different frequency in the same band – Code Division Multiple Access (CDMA) [38] • Uses spread-spectrum technology and different pseudo-noise codes so multiple users share the same physical channel

Cellular Telephony • It is useful to think of cellular telephony in terms of generations: [33– 37] – – 0 G: Briefcase-size mobile radio telephones 1 G: Analog cellular telephony 2 G: Digital cellular telephony 3 G: High-speed digital cellular telephony (including video telephony) – 4 G: IP-based “anytime, anywhere” voice, data, and multimedia telephony at faster data rates than 3 G (to be deployed in 2012– 2015) • We will focus on 2 G and 3 G technologies

Cellular Telephony – 2 G • There are two main 2 G technologies: – Global System for Mobile communications (GSM), which uses TDMA [39] – Interim Standard 95 (IS-95, aka cdma. One™), which uses CDMA [40] • There are other TDMA networks such as PDC (Japan-only), i. DEN (Nextel-only), and IS-136 (now converted to GSM) • We won’t worry about these
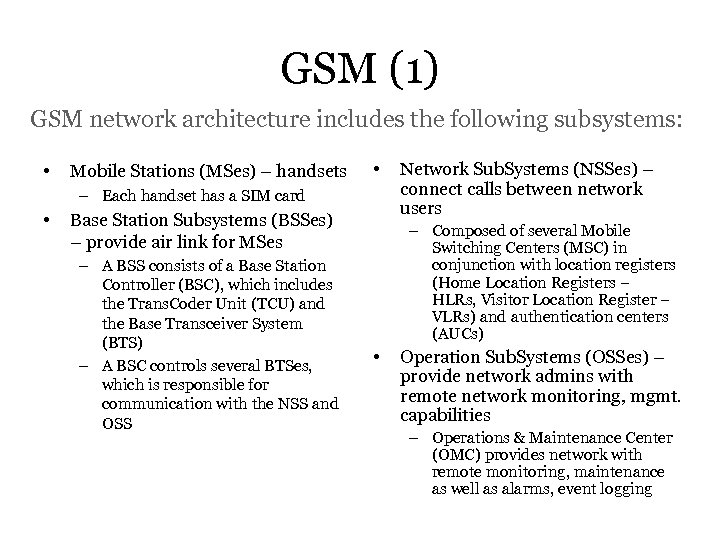
GSM (1) GSM network architecture includes the following subsystems: • Mobile Stations (MSes) – handsets • – Each handset has a SIM card • Base Station Subsystems (BSSes) – provide air link for MSes – A BSS consists of a Base Station Controller (BSC), which includes the Trans. Coder Unit (TCU) and the Base Transceiver System (BTS) – A BSC controls several BTSes, which is responsible for communication with the NSS and OSS Network Sub. Systems (NSSes) – connect calls between network users – Composed of several Mobile Switching Centers (MSC) in conjunction with location registers (Home Location Registers – HLRs, Visitor Location Register – VLRs) and authentication centers (AUCs) • Operation Sub. Systems (OSSes) – provide network admins with remote network monitoring, mgmt. capabilities – Operations & Maintenance Center (OMC) provides network with remote monitoring, maintenance as well as alarms, event logging
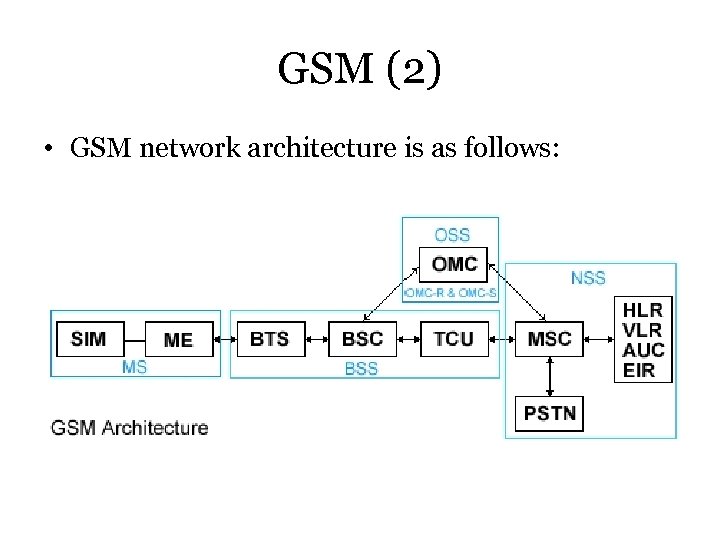
GSM (2) • GSM network architecture is as follows:
![GSM (3) • Short Message Service (SMS) [41] – 1985 GSM standard that allows GSM (3) • Short Message Service (SMS) [41] – 1985 GSM standard that allows](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-47.jpg)
GSM (3) • Short Message Service (SMS) [41] – 1985 GSM standard that allows messages of at most 160 chars. (incl. spaces) to be sent between handsets and other stations – Over 2. 4 billion people use it; multi-billion $ industry • General Packet Radio Service (GPRS) – GSM upgrade that provides IP-based packet data transmission up to 114 kbps – Users can “simultaneously” make calls and send data – GPRS provides “always on” Internet access and the Multimedia Messaging Service (MMS) whereby users can send rich text, audio, video messages to each other [42] – Performance degrades as number of users increase – GPRS is an example of 2. 5 G telephony – 2 G service similar to 3 G
![GSM (4) • Enhanced Data rate for GSM Evolution (EDGE) [43] – GSM revision GSM (4) • Enhanced Data rate for GSM Evolution (EDGE) [43] – GSM revision](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-48.jpg)
GSM (4) • Enhanced Data rate for GSM Evolution (EDGE) [43] – GSM revision that provides 3× GPRS’ data rate (max. 236. 8 kbps); considered 3 G tech. – Deployed on GSM networks starting in 2003 – EDGE Evolution increases bit rates to (theoretical) max. of 1 Mbps, decreases latency from 200 ms to 100 ms

IS-95, CDMA 2000, and 3 G • Qualcomm developed IS-95 in the 1990 s as first CDMAbased mobile standard [40] • Unlike GSM, which is open, Qualcomm owns patents on CDMA technology • CDMA 2000, IS-95’s hybrid 2. 5 G/3 G successor, is supplanting it [44] • The Telecommunications Industry Association owns the trademarks “cdma. One” and “CDMA 2000” in the U. S. • There are two competing 3 G technologies: the Universal Mobile Telecommunications System (UMTS) and CDMA 2000
UMTS and HSPA • The UMTS is an international standard designed to replace GSM (aka 3 GSM) [45] • UMTS is a 3 G standard and is being developed into a 4 G standard • Its air interface is Wideband CDMA (W-CDMA), which was developed by NTT Do. Co. Mo for Japan’s 3 G wireless network [46] • W-CDMA has been deployed in Europe and Asia • In theory, High Speed Packet Access (HSPA) protocols extend UTMS’ performance to 14. 4 Mbps and 5. 76 Mbps downlink and uplink, respectively [47] • In practice, max speeds are 7. 2 Mbps and 1. 4 – 5. 8 Mbps, respectively (depending on carrier)

Other Handset Networks • Many handsets not only support cellular telephony, they support other networking technologies as well: – Wireless • Bluetooth (100 m max, 10 m for handsets) • IEEE 802. 11 (longer range) • Infrared Data Association (Ir. DA) – Wired • USB, etc.

Bluetooth (1) • Bluetooth is a technology specification for small form factor, low-cost, short-range wireless links between mobile handsets, Internet connectivity • Max range is 100 m in 2. 4 GHz frequency band (handsets: 10 m radios) • There is possible interference with IEEE 802. 11 b WLANs operating in this band • Max bandwidth is 3 Mbps for Bluetooth 2. x with Enhanced Data Rate

Bluetooth (2) • Link Types – Synchronous Connection-Oriented (SCO) • Useful for circuit-switched services, e. g. , voice, where low delay and high Qo. S are required • Offered channels are symmetric and synchronous – Asynchronous Connection-Less (ACL) • More efficient for data transfer, other async. services • Link offers packet switching, transmission (Xmission) slots granted by polling access scheme • A piconet is a collection of up to 8 Bluetooth units where one is a master that controls Xmission, hopping scheme, others are slaves – Master tells slave, “I want to send, ” and slave receives – Slaves can send on slots only when they agree with master – One connection can have several links of either type, but there’s a 3 voice call limit within a piconet
Bluetooth (3) • Piconets and scatternets – One device can be connected in two or more piconets, which is termed a scatternet • But a device can only be a master to one piconet at a time • In order for device to be part of scatternet, support for hold, park, or sniff mode is needed – Master/slave roles are not necessarily fixed and can be changed during connection – Master/slave switch needed in scatternet
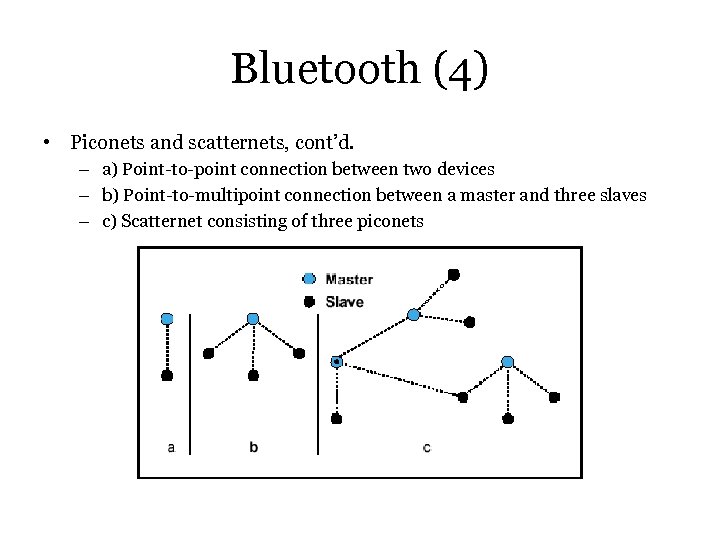
Bluetooth (4) • Piconets and scatternets, cont’d. – a) Point-to-point connection between two devices – b) Point-to-multipoint connection between a master and three slaves – c) Scatternet consisting of three piconets
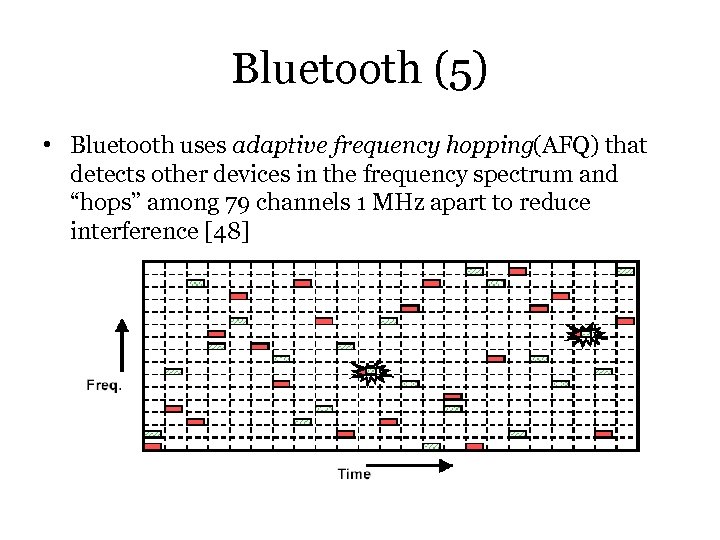
Bluetooth (5) • Bluetooth uses adaptive frequency hopping(AFQ) that detects other devices in the frequency spectrum and “hops” among 79 channels 1 MHz apart to reduce interference [48]
Bluetooth (6) • • Connections established via page messages if recipient address is unknown, ; master’s inquiry message is needed (that gives access code, asks for slave’s Bluetooth address and system clock) Units are in standby mode before connections are made Page message is sent on 16 frequencies 128 times; if no response, message is sent on 16 different frequencies 128 times Max. connection time is 2. 56 seconds
Bluetooth (7) • Bluetooth Special Interest Group (SIG) has defined numerous usage models for the technology that describe primary Bluetooth applications & intended devices • Profiles define the protocols & protocol features that support a usage model • See [49] for more information

IEEE 802. 11 Networks • The IEEE 802. 11 standards specify how electronic devices communicate with each other in wireless fidelity (Wi-Fi) networks • Many handsets can communicate with each other this way • There are many 802. 11 standards [53]; we’ll only look at 802. 11 b, 802. 11 g, and Wi. Max here • Other 802. 11 standards provide greater security, which we’ll discuss later
![IEEE 802. 11 & Wi. Max Specs. • 802. 11 b (1999): [51, 53] IEEE 802. 11 & Wi. Max Specs. • 802. 11 b (1999): [51, 53]](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-60.jpg)
IEEE 802. 11 & Wi. Max Specs. • 802. 11 b (1999): [51, 53] – Operates in the 2. 4 GHz frequency band – Provides max 11 Mbps data rate – 38 m indoor range • 802. 11 g (2003): [51, 53] – Operates in either 2. 4 GHz or 5 GHz frequency bands – Provides max 54 Mbps data rate – 38 m indoor range • Wi. Max (802. 16): [52] – Operates in 2. 3 GHz, 2. 5 – 2. 6 GHz frequency bands – Provides max 40 Mbps data rate now, 300 Mbps later – 3 km cell range
Ir. DA • The Infrared Data Association (Ir. DA) provides protocols to transfer data between handsets, other devices using infrared light [54] – Similar in principle to a remote control – Data rate is 16 Mbps now, 300 – 500 Mbps later – Range is 1 m, communicating devices must have a “line of sight” – Deployed in over 500 million devices
Wired Networks: USB • The Universal Serial Bus (USB) is a ubiquitous standard for transferring data between computers (including handsets!) [55] – By definition, data is transferred one bit at a time – USB 1. 1 (1998): max 1. 5 Mbps (low-speed), 12 Mbps (full-speed) – USB 2. 0 (2000): max 480 Mbps – USB 3. 0 (to be released in 2009 – 2010): max 5 Gbps

Handset Applications • Many handset applications mirror those of computers, e. g. , managing one’s schedule, Web browsing, etc. • But handsets’ mobility is opening up new markets – Global mobile gaming market value expected to reach € 2. 6 billion ($3. 27 billion) in 2012 – Global mobile advertising market value expected to reach € 1. 77 billion ($2. 23 billion) in 2012 • Also, handsets make mobile and location-based services possible, which we’ll discuss next

Mobile & Location-based Services • Carnegie Mellon University’s (CMU’s) Human Computer Interaction Institute has developed several such services that we’ll examine – Mobile social computing • in. Touch: Coordination for families, small groups • Whisper Mobile: Coordinating groups for social events – Large-scale mobile collaboration • Hitchhiking: estimating places’ busyness – Mobile data • Gurun. Go: Linking desktop, mobile devices – Usable privacy and security • Contextual instant messaging • People Finder • CMU’s Grey resource-control system – Memory support • Memory karaoke

Mobile Social Computing • Mobile social computing – in. Touch: Coordination for families, small groups – Whisper Mobile: Coordinating groups for social events • Large-scale mobile collaboration – Hitchhiking: estimating places’ busyness • Mobile data – Gurun. Go: Linking desktop, mobile devices • Usable privacy and security – Contextual instant messaging – CMU’s Grey resource-control system
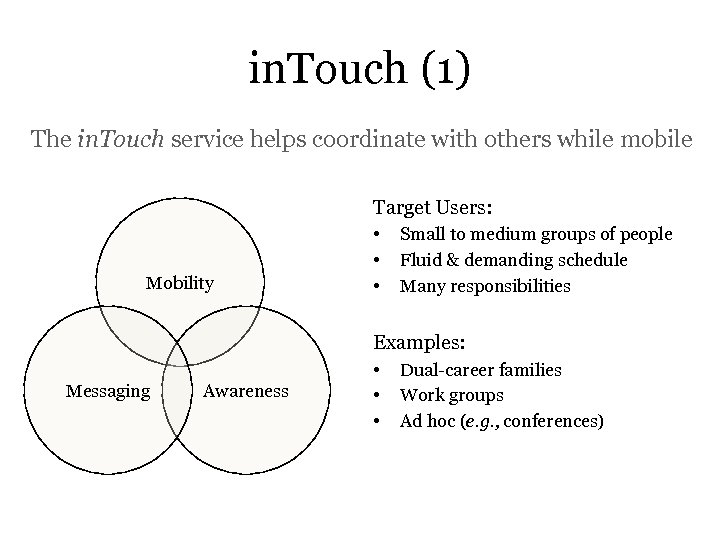
in. Touch (1) The in. Touch service helps coordinate with others while mobile Target Users: Mobility • • • Small to medium groups of people Fluid & demanding schedule Many responsibilities Examples: Messaging Awareness • • • Dual-career families Work groups Ad hoc (e. g. , conferences)
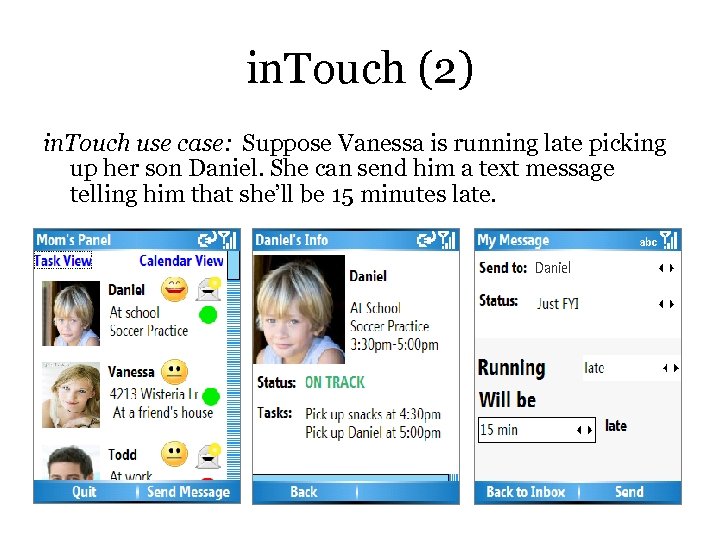
in. Touch (2) in. Touch use case: Suppose Vanessa is running late picking up her son Daniel. She can send him a text message telling him that she’ll be 15 minutes late. Daniel
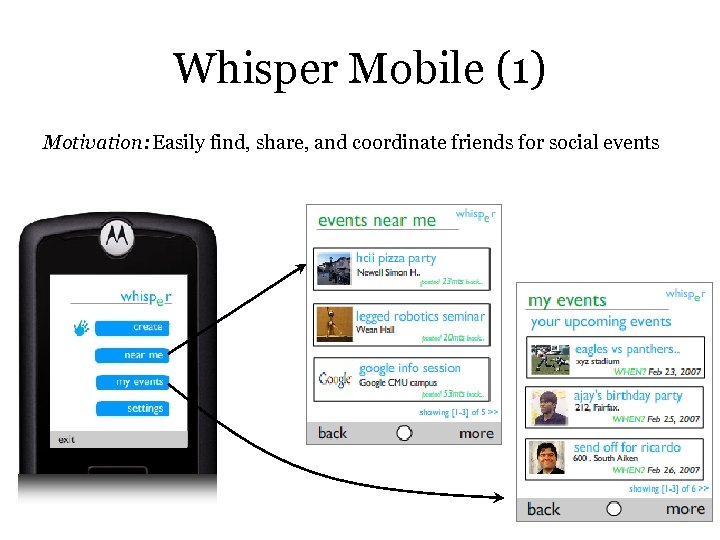
Whisper Mobile (1) Motivation: Easily find, share, and coordinate friends for social events
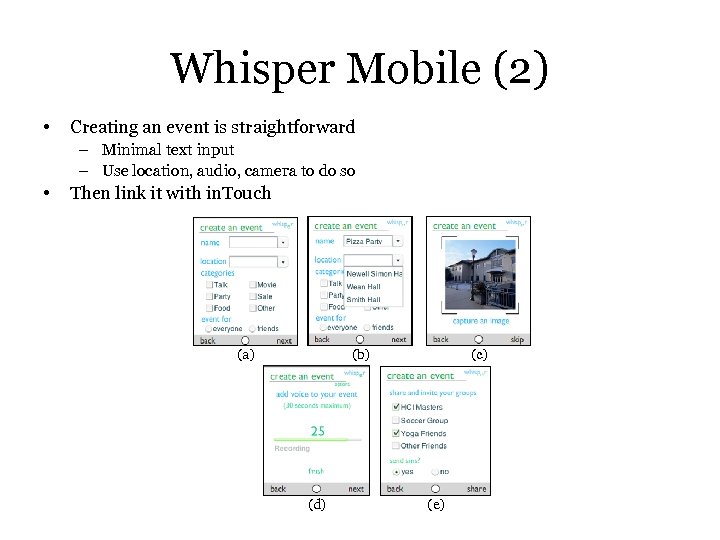
Whisper Mobile (2) • Creating an event is straightforward – Minimal text input – Use location, audio, camera to do so • Then link it with in. Touch (a) (b) (d) (c) (e)

Large-Scale Mobile Collaboration • Mobile social computing – in. Touch: Coordination for families, small groups – Whisper Mobile: Coordinating groups for social events • Large-scale mobile collaboration – Hitchhiking: estimating places’ busyness • Mobile data – Gurun. Go: Linking desktop, mobile devices • Usable privacy and security – Contextual instant messaging – CMU’s Grey resource-control system

Hitchhiking (1) • Many location-based services focus on “where you are” • Hitchhiking looks at places’ busyness, e. g. , – “Is the café busy? ” – “How long are the airport lines? ” • Approach: estimate number of people in a place by counting number of handsets there and upload number and location to servers (anonymized for privacy) • Locations can be viewed on a map, e. g. , Microsoft’s Sensor. Map

Hitchhiking (2)

Mobile Data • Mobile social computing – in. Touch: Coordination for families, small groups – Whisper Mobile: Coordinating groups for social events • Large-scale mobile collaboration – Hitchhiking: estimating places’ busyness • Mobile data – Gurun. Go: Linking desktop, mobile devices • Usable privacy and security – Contextual instant messaging – CMU’s Grey resource-control system

Gurun. Go (1) • Goal: Easily access useful info while mobile • Motivations: – People print out online maps rather than copy them to handset (easier, small mobile form factor) – People browse the Web differently on desktops and handsets • Gurun. Go allows people to explicitly copy info to handsets, implicitly copy maps to handsets and generate speech-based directions

Gurun. Go (2) Example of speech-based directions:

Usable Privacy and Security • Mobile social computing – in. Touch: Coordination for families, small groups – Whisper Mobile: Coordinating groups for social events • Large-scale mobile collaboration – Hitchhiking: estimating places’ busyness • Mobile data – Gurun. Go: Linking desktop, mobile devices • Usable privacy and security – Contextual instant messaging – CMU’s Grey resource-control system

Contextual Instant Messaging • CMU developed a custom AIM client, bot that people can query “howbusyis screenname” • Robot respects userspecified privacy settings – Users can create groups, put screen names in them – Users can specify what each group can see • System generates audit logs for security
Grey Resource Control • CMU developed a distributed handset-based resource control system – Resources include office doors, electronic files, etc. • Flexible, end user-specified policies: – Proactive: Manually create policy before request, e. g. , “Alice can always enter my office” – Reactive: Generates policy based on request, e. g. , “Can I enter your office? ” • • CMU connected Grey with Bluetooth-enabled office doors There were security and usability issues with the system

A Large-Scale Mobile App Gawker Stalker – people spotting celebrities in New York City

Handset Security Issues (1) • People store a wealth of information on their handsets and don’t think about securing them! • Naturally, this makes handsets targets for miscreants – whether they’re “script kiddies” or Mafia cybercriminals – due to what’s stored on them: – – – – Incoming, outgoing, missed calls SMS (text) and MMS messages E-mail Instant-messaging (IM) logs Multimedia, e. g. , pictures, music, videos Personal calendars Address books • Clearly, handset security is a vitally important challenge

Handset Malware History (1) • Hackers are already attacking handsets – Most well-known case: a 17 -year-old broke into Paris Hilton’s Sidekick handset [58] – Less well-known: worms, viruses, and Trojans have targeted handsets since 2004 • 2004: [59] – Cabir worm released by “ 29 A, ” targets Symbian phones via Bluetooth – Duts virus, released by same group, targets Windows Mobile phones – Brador Trojan released by same group, opens backdoor on Windows Mobile [63]
![Handset Malware History (2) • 2005: [60] – Comm. Warrior worm released; replicates via Handset Malware History (2) • 2005: [60] – Comm. Warrior worm released; replicates via](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-82.jpg)
Handset Malware History (2) • 2005: [60] – Comm. Warrior worm released; replicates via Bluetooth, MMS messages to all contacts in address book – Doomboot Trojan released; claims to be “Doom 2” video game, installs Cabir and Comm. Warrior • 2006: [59– 60] – Red. Browser Trojan released; claims to be a Java program, secretly sends premium-rate SMS messages to a Russian phone number – Flexi. Spy spyware released; sends log of phone calls, copies of SMS/MMS messages to Internet server for third party to view • 2008: [61] – First i. Phone Trojan released – Of course, other mobile malware has been released; some malware completely disables the handset – There is also the possibility of mobile botnets [62]

Key Handset Security Problems • “At this point, mobile device capabilityis far ahead of security. ” – Prof. Patrick Traynor, Georgia Tech (emphasis added) [62] • Handset information can be stolen [63] – Transient information: Enhanced 911 can provide user location information – Static information: “Blue. Snarfing” attacks (connection without owner’s knowledge), cracking Wired Equivalent Privacy (WEP) and Wi-Fi Protected Access (WPA) [64] • Theft of service attacks, e. g. , premium-rate calls/SMS messages [63] • Denial-of-service attacks [63] – Flooding attacks overload the handset radio with garbage – Power-draining attacks attempt to drain the battery • Botnets and Do. S attacks against networks are likely in the future [62] • Cybercriminals make 10× as much as security researchers! [69]

Mitigation Strategies • Handset manufacturers, OS & software vendors, and researchers have worked to counter threats – Symbian OS requires apps to be cryptographically signed in order for them to run without user approval – Some handset manufacturers have joined the Trusted Computing Group (TCG) and added hardware to thwart malware tampering with the device [60] – The i. Phone runs each application in a “sandbox” to prevent malware from running on the device [68] – Heterogeneous handset OSes make massive malware outbreaks difficult – Vendors like Mc. Afee, Symantec, and Trend Micro sell security software for handsets; F-Secure has bundled its software with Hong Kong provider CSL’s handsets [65] – Researchers have worked on modeling malware propagation on networks, detecting power-draining attacks, etc. [66– 67]
![The Challenges Ahead • “[Because] the mobile communications field is evolving so quickly, it The Challenges Ahead • “[Because] the mobile communications field is evolving so quickly, it](https://present5.com/presentation/6718c622319a202e495c5a8a2cd2c9b7/image-85.jpg)
The Challenges Ahead • “[Because] the mobile communications field is evolving so quickly, it presents a unique opportunity to design security properly—an opportunity we missed with the PC. ” – Prof. Patrick Traynor [62] • Since most people buy a new handset every 2 years it’s vital to , ensure the security of handset hardware, OSes, applications, and networks while maintaining usability [62] • One suggested approach is to give handsets a “hard” power-off switch so they don’t have power when turned off [63]] • Academic research will play a key role in this, as will user education to counter social engineering • Given the sensitivity of information stored on handsets, cybercriminals may well find effective ways to use them to continue their nefarious acts, e. g. , bot herding, data theft, etc. , even with different operating systems, power constraints, and carriers • Though we may not hear news of handset attacks as often as those against (Windows) PCs, we cannot fall into a false sense of security

Questions? Thank you!

References (1) 1. 2. 3. 4. 5. 6. 7. 8. T. T. Ahonen, “When there is a mobile phone for half the planet: Understanding the biggest technology”, 16 Jan. 2008, http: //communities-dominate. blogs. com/ brands/2008/01/when-there-is-a. html A. Wolfe, “Is the Smartphone Your Next Computer? ”, Information. Week, 4 Oct. 2008, http: //www. informationweek. com/news/personal_tech/smartphones/ show. Article. jhtml? article. ID=210605369 J. L. Hennessy and D. A. Patterson, Computer Architecture: A Quantitative Approach, 4 th ed. , Elsevier, 2007 Research in Motion, “Black. Berry 8700 c Technical Specifications”, http: //www. blackberry. com/products/pdfs/blackberry 8700 c_ent. pdf R. Block, “i. Phone processor found: 620 MHz ARM CPU”, Engadget, 1 Jul. 2007, http: //www. engadget. com/2007/07/01/iphone-processor-found-620 mhz-arm/ Samsung Semiconductor, “Product Technical Brief: S 3 C 6400, Jun. 2007”, http: //www. samsung. com/global/system/business/semiconductor/product/2007 /8/21/661267 ptb_s 3 c 6400_rev 15. pdf Wikipedia, “i. Phone”, updated 15 Nov. 2008, http: //en. wikipedia. org/wiki/Iphone Wikipedia, “i. Pod Touch”, updated 14 Nov. 2008, http: //en. wikipedia. org/wiki/ Ipod_touch

References (2) 9. 10. 11. 12. 13. 14. 15. 16. N. Cubrilovic, “Symbian Goes Open Source – Courtesy of Nokia”, Tech. Crunch. IT, 24 Jun. 2008, http: //www. techcrunchit. com/2008/06/24/symbian-goes-opensource-courtesy-of-nokia/ “Android – An Open Handset Alliance Project”, http: //code. google. com/android/ Canalys, “Global smart phone shipments rise 28%: Nokia retains lead, but Apple moves into number two position”, 6 Nov. 2008, Press Release, http: //canalys. com/pr/2008/r 2008112. htm Nokia, “Nokia to acquire Symbian Limited to enable evolution of the leading open mobile platform”, 24 Jun. 2008, Press Release, http: //www. nokia. com/A 4136001? newsid=1230415 Wikipedia, “Symbian OS”, updated 13 Nov. 2008, http: //en. wikipedia. org/wiki/ Symbian_os Symbian Ltd. , “Symbian OS”, http: //www. symbian. com/symbianos/ B. Morris, “Symbian OS Architecture Overview”, Wireless Developer Forum UK ’ 06, Symbian Software Ltd. , http: //developer. symbian. com/wiki/download/attachments/1376/Ben_Morris. pp t? version=1 Wikipedia, “Palm OS”, updated 3 Nov. 2008, http: //en. wikipedia. org/wiki/ Palm_os

References (3) 17. 18. 19. 20. 21. 22. 23. 24. Wikipedia, “Windows Mobile”, updated 13 Nov. 2008, http: //en. wikipedia. org/ wiki/Windows_mobile Wikipedia, “Windows CE”, updated 12 Nov. 2008, http: //en. wikipedia. org/wiki/ Windows_CE Microsoft Corp. , “. NET Framework Conceptual Overview”, MSDN, 2008, http: //msdn. microsoft. com/en-us/library/zw 4 w 595 w(printer). aspx Microsoft Corp. , “Microsoft Gives Students Access to Technical Software at No Charge to Inspire Success and Make a Difference”, 18 Feb. 2008, Press Release, http: //www. microsoft. com/Presspass/press/2008/feb 08/02 -18 GSDPR. mspx K. Haslem, “Macworld Expo: Optimised OS X sits on ‘versatile’ Flash”, 12 Jan. 2007, Macworld http: //www. macworld. co. uk/ipod-itunes/news/ , index. cfm? newsid=16927 Wikipedia, “i. Phone OS”, updated 16 Nov. 2008, http: //en. wikipedia. org/wiki/ IPhone_OS Apple Inc. , “i. Phone Developer University Program”, 2008, http: //developer. apple. com/iphone/program/university. html Apple Inc. , “Apple Developer Connection – Web Apps Dev Center”, 2008, http: //developer. apple. com/webapps/

References (4) 25. 26. 27. 28. 29. 30. 31. 32. Apple Inc. , “Apple – i. Phone – Features – Safari”, 2008, http: //www. apple. com/iphone/features/safari. html Apple Inc. , “Safari 3. 1 Product Overview”, Jun. 2008, http: //images. apple. com/safari/docs/Safari_Product_Overview 20080602. pdf Research in Motion, “Black. Berry Mobile Voice System”, 2008, http: //na. blackberry. com/eng/services/blackberry_mvs/ A. Succo, “RIM exec sees Black. Berry product as shaping telephony”, 22 May 2008, Info. World, http: //www. infoworld. com/news/feeds/08/05/22/RIM-exec-sees. Black. Berry-product-as-shaping-telephony. html Open Handset Alliance, “Members”, http: //www. openhandsetalliance. com/ oha_members. html Open Handset Alliance, “Overview”, http: //www. openhandsetalliance. com/ oha_overview. html Wikipedia, “Android (mobile device platform)”, updated 16 Nov. 2008, http: //en. wikipedia. org/wiki/Android_(mobile_device_platform) Google Inc. , “What Is Android? ”, 2008, http: //code. google. com/android/what-isandroid. html#runtime

References (5) 33. 34. 35. 36. 37. 38. 39. 40. 41. 42. 43. 44. Wikipedia, “Mobile radio telephone”, updated 6 Jul. 2008, http: //en. wikipedia. org/wiki/0 G Wikipedia, “ 1 G”, updated 6 Aug. 2008, http: //en. wikipedia. org/wiki/1 G Wikipedia, “ 2 G”, updated 18 Nov. 2008, http: //en. wikipedia. org/wiki/2 G Wikipedia, “ 3 G”, updated 19 Nov. 2008, http: //en. wikipedia. org/wiki/3 G Wikipedia, “ 4 G”, updated 11 Nov. 2008, http: //en. wikipedia. org/wiki/4 G Wikipedia, “Code division multiple access”, updated 30 Oct. 2008, http: //en. wikipedia. org/wiki/Code_division_multiple_access Wikipedia, “GSM”, updated 14 Nov. 2008, http: //en. wikipedia. org/wiki/GSM Wikipedia, “IS-95”, updated 10 Oct. 2008, http: //en. wikipedia. org/wiki/IS-95 Wikipedia, “Short message service”, updated 19 Nov. 2008, http: //en. wikipedia. org/wiki/Short_message_service Wikipedia, “Multimedia messaging service”, updated 3 Nov. 2008, http: //en. wikipedia. org/wiki/Multimedia_Messaging_Service Wikipedia, “Enhanced Data Rates for GSM Evolution”, updated 19 Nov. 2008, http: //en. wikipedia. org/ wiki/Enhanced_Data_Rates_for_GSM_Evolution Wikipedia, “CDMA 2000”, updated 17 Nov. 2008, http: //en. wikipedia. org/wiki/ CDMA 2000

References (6) 45. 46. 47. 48. 49. 50. 51. 52. 53. 54. Wikipedia, “Universal Mobile Telecommunications System”, updated 18 Nov. 2008, http: //en. wikipedia. org/wiki/Universal_Mobile_Telecommunications_System Wikipedia, “W-CDMA (UTMS)”, updated 19 Oct. 2008, http: //en. wikipedia. org/ wiki/W-CDMA_(UMTS) Wikipedia, “High Speed Packet Access”, updated 15 Oct. 2008, http: //en. wikipedia. org/wiki/High_Speed_Packet_Access Bluetooth SIG, “Basics”, 2008, http: //www. bluetooth. com/Bluetooth/ Technology/Basics. htm Bluetooth SIG, “Profiles Overview”, 2008, http: //www. bluetooth. com/Bluetooth/ Technology/Works/Profiles_Overview. htm Wikipedia, “Wi-Fi”, updated 18 Nov. 2008, http: //en. wikipedia. org/wiki/Wi-fi Wikipedia, “Wi-Fi technical information”, updated 31 Oct. 2008, http: //en. wikipedia. org/wiki/Wi-Fi_Technical_Information Wi. Max Forum, “Frequently Asked Questions”, http: //www. wimaxforum. org/ documents/faq/ Wikipedia, “IEEE 802. 11”, updated 16 Nov. 2008, http: //en. wikipedia. org/wiki/ 802. 11 Infrared Data Association, “Welcome to Ir. DA”, http: //www. irda. org/ displaycommon. cfm? an=1&subarticlenbr=14

References (7) 55. 56. 57. 58. 59. 60. 61. 62. Wikipedia, “Universal Serial Bus”, updated 19 Nov. 2008, http: //en. wikipedia. org/wiki/Usb Screen Digest, “i. Phone breathes new life into mobile gaming market”, 31 Jul. 2008, Press Release, http: //www. screendigest. com/press/releases/ pr_31_07_2008/view. html Screen Digest, “Mobile media advertising opportunities: The market for advertising”, 2 May 2008, http: //www. screendigest. com/reports/ 08 mobilemediaadvert/pdf/08 chinacabletv-pdf/view. html B. Krebs, “Teen Pleads Guilty to Hacking Paris Hilton’s Phone”, Washington Post, 13 Sep. 2005, http: //www. washingtonpost. com/wp-dyn/content/article/2005/ 09/13/AR 2005091301423_pf. html D. Emm, “Mobile malware – new avenues”, Network Security 2006 Nov. 2006, , : 11, pp. 4– 6 M. Hypponen, “Malware Goes Mobile”, Scientific American, Nov. 2006, pp. 70– 77, http: //www. cs. virginia. edu/~robins/Malware_Goes_Mobile. pdf Panda. Labs, “Panda. Labs Quarterly Report: January–March 2008”, http: //pandalabs. pandasecurity. com/blogs/images/Panda. Labs/2008/04/01/Qua rterly_Report_Panda. Labs_Q 1_2008. pdf Georgia Tech Information Security Center, “Emerging Cyber Threats Report for 2009”, http: //www. gtiscsecuritysummit. com/pdf/Cyber. Threats. Report 2009. pdf

References (8) 63. 64. 65. 66. 67. 68. 69. D. Dagon et al. , “Mobile Phones as Computing Devices: The Viruses are Coming!”, IEEE Pervasive Computing Oct. – Dec. 2004, pp. 11– 15 , G. Fleishman, “Battered, but not broken: understanding the WPA crack”, Ars Technica, 6 Nov. 2008, http: //arstechnica. com/articles/paedia/wpa-cracked. ars “CSL Unveils Mobile Security Service”, China Tech News, 31 Mar. 2008, http: //www. chinatechnews. com/2008/03/31/6562 -csl-unveils-mobile-securityservice/ C. Fleizach et al. , “Can You Infect Me Now? Malware Propagation in Mobile Phone Networks”, Proc. of ACM Workshop on Recurring Malcode (WORM ’ 07) , Alexandria, VA, USA, 2 Nov. 2007, pp. 61– 68. H. Kim et al. , “Detecting Energy-Greedy Anomalies and Mobile Malware Variants”, Proc. of the 6 th Int’l Conf. on Mobile Systems, Applications, and Services (Mobi. Sys ’ 08), Breckenridge, CO, USA, 17– 20 Jun. 2008, pp. 239– 252. E. Sadun, “Programming with Safety Scissors and Glitter Glue”, Inside i. Phone, 10 Oct. 2008, http: //blogs. oreilly. com/iphone/2008/10/programming-with-safetyscisso. html T. Claburn, “The Cybercrime Economy”, Information. Week, 9 Apr. 2008, http: //www. informationweek. com/blog/main/archives/2008/04/ the_cyber_crime. html
6718c622319a202e495c5a8a2cd2c9b7.ppt