554c238f598dd3193c46136be8e4c123.ppt
- Количество слайдов: 22
 Mix-Zones for Location Privacy in Vehicular Networks Julien Freudiger Maxim Raya, Márk Félegyházi, Panos Papadimitratos, and Jean-Pierre Hubaux August 14, 2007 Wi. N-ITS, Vancouver, BC, Canada
Mix-Zones for Location Privacy in Vehicular Networks Julien Freudiger Maxim Raya, Márk Félegyházi, Panos Papadimitratos, and Jean-Pierre Hubaux August 14, 2007 Wi. N-ITS, Vancouver, BC, Canada
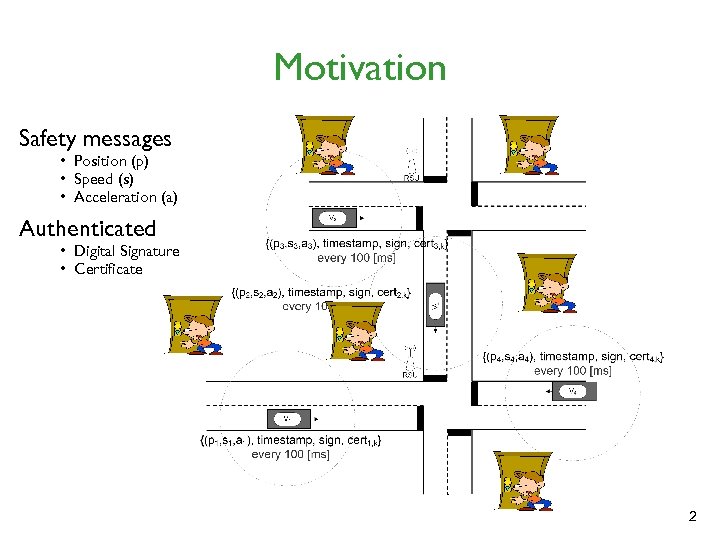 Motivation Safety messages • Position (p) • Speed (s) • Acceleration (a) Authenticated • Digital Signature • Certificate 2
Motivation Safety messages • Position (p) • Speed (s) • Acceleration (a) Authenticated • Digital Signature • Certificate 2
 No location privacy 3
No location privacy 3
 Outline 1. System and Threat Model 2. Mix-Zones 3. Vehicular Mix-Networks 4. Simulation Results 4
Outline 1. System and Threat Model 2. Mix-Zones 3. Vehicular Mix-Networks 4. Simulation Results 4
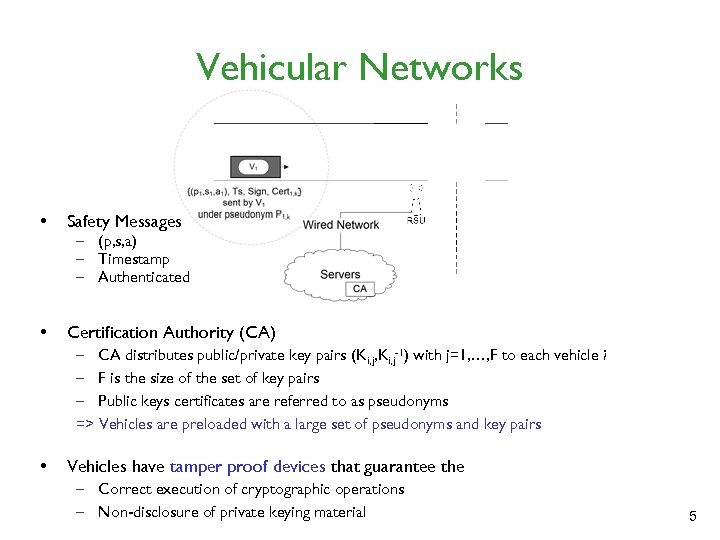 Vehicular Networks • Safety Messages • Certification Authority (CA) – (p, s, a) – Timestamp – Authenticated – CA distributes public/private key pairs (Ki, j, Ki, j-1) with j=1, …, F to each vehicle i – F is the size of the set of key pairs – Public keys certificates are referred to as pseudonyms => Vehicles are preloaded with a large set of pseudonyms and key pairs • Vehicles have tamper proof devices that guarantee the – Correct execution of cryptographic operations – Non-disclosure of private keying material 5
Vehicular Networks • Safety Messages • Certification Authority (CA) – (p, s, a) – Timestamp – Authenticated – CA distributes public/private key pairs (Ki, j, Ki, j-1) with j=1, …, F to each vehicle i – F is the size of the set of key pairs – Public keys certificates are referred to as pseudonyms => Vehicles are preloaded with a large set of pseudonyms and key pairs • Vehicles have tamper proof devices that guarantee the – Correct execution of cryptographic operations – Non-disclosure of private keying material 5
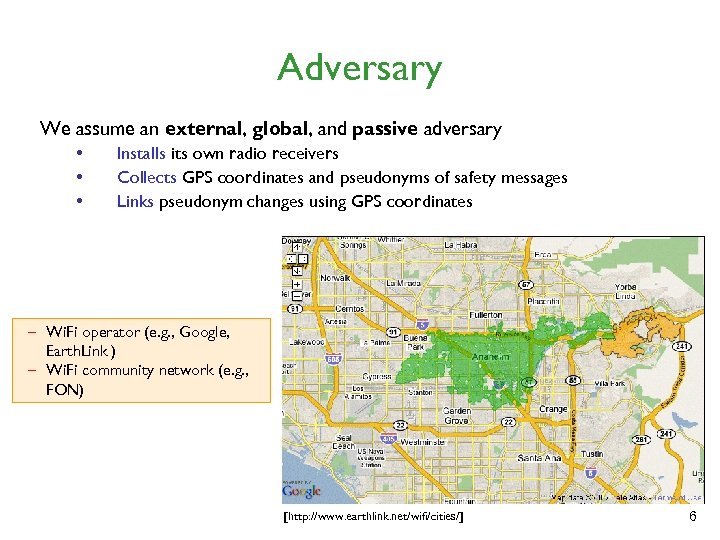 Adversary We assume an external, global, and passive adversary • • • Installs its own radio receivers Collects GPS coordinates and pseudonyms of safety messages Links pseudonym changes using GPS coordinates – Wi. Fi operator (e. g. , Google, Earth. Link ) – Wi. Fi community network (e. g. , FON) [http: //www. earthlink. net/wifi/cities/] 6
Adversary We assume an external, global, and passive adversary • • • Installs its own radio receivers Collects GPS coordinates and pseudonyms of safety messages Links pseudonym changes using GPS coordinates – Wi. Fi operator (e. g. , Google, Earth. Link ) – Wi. Fi community network (e. g. , FON) [http: //www. earthlink. net/wifi/cities/] 6
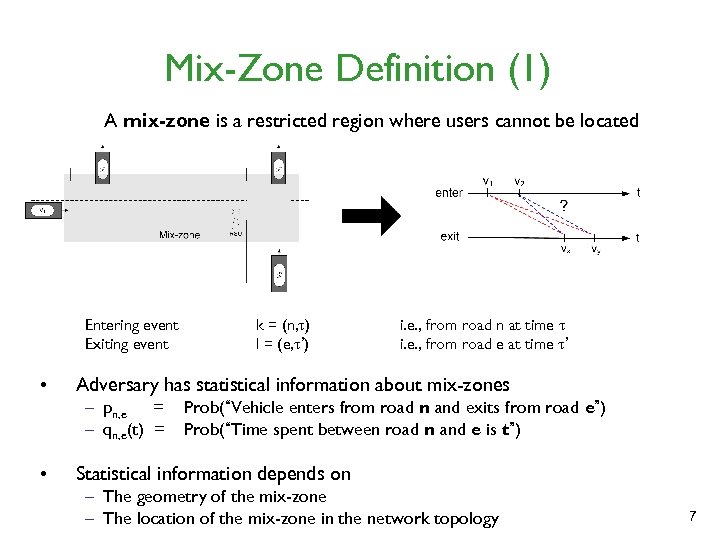 Mix-Zone Definition (1) A mix-zone is a restricted region where users cannot be located Entering event Exiting event • i. e. , from road n at time i. e. , from road e at time ’ Adversary has statistical information about mix-zones – pn, e = – qn, e(t) = • k = (n, ) l = (e, ’) Prob(“Vehicle enters from road n and exits from road e”) Prob(“Time spent between road n and e is t”) Statistical information depends on – The geometry of the mix-zone – The location of the mix-zone in the network topology 7
Mix-Zone Definition (1) A mix-zone is a restricted region where users cannot be located Entering event Exiting event • i. e. , from road n at time i. e. , from road e at time ’ Adversary has statistical information about mix-zones – pn, e = – qn, e(t) = • k = (n, ) l = (e, ’) Prob(“Vehicle enters from road n and exits from road e”) Prob(“Time spent between road n and e is t”) Statistical information depends on – The geometry of the mix-zone – The location of the mix-zone in the network topology 7
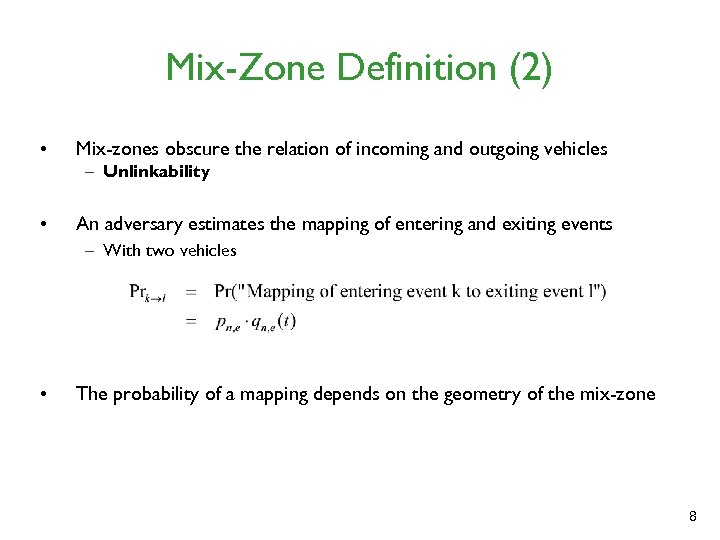 Mix-Zone Definition (2) • Mix-zones obscure the relation of incoming and outgoing vehicles – Unlinkability • An adversary estimates the mapping of entering and exiting events – With two vehicles • The probability of a mapping depends on the geometry of the mix-zone 8
Mix-Zone Definition (2) • Mix-zones obscure the relation of incoming and outgoing vehicles – Unlinkability • An adversary estimates the mapping of entering and exiting events – With two vehicles • The probability of a mapping depends on the geometry of the mix-zone 8
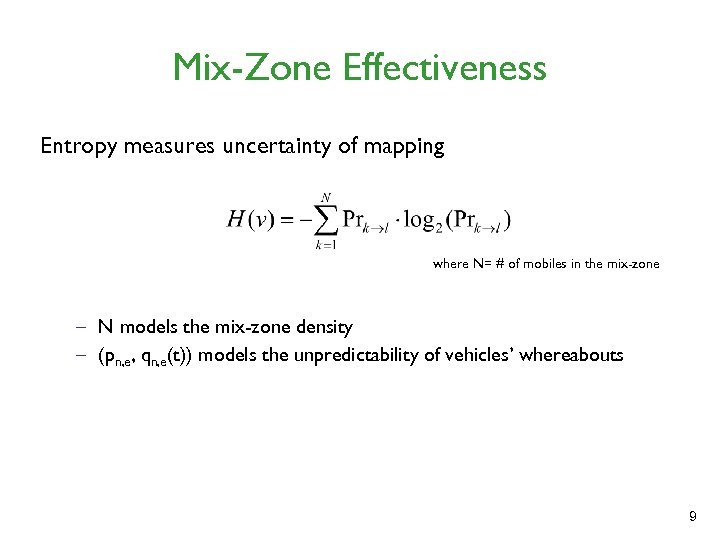 Mix-Zone Effectiveness Entropy measures uncertainty of mapping where N= # of mobiles in the mix-zone – N models the mix-zone density – (pn, e, qn, e(t)) models the unpredictability of vehicles’ whereabouts 9
Mix-Zone Effectiveness Entropy measures uncertainty of mapping where N= # of mobiles in the mix-zone – N models the mix-zone density – (pn, e, qn, e(t)) models the unpredictability of vehicles’ whereabouts 9
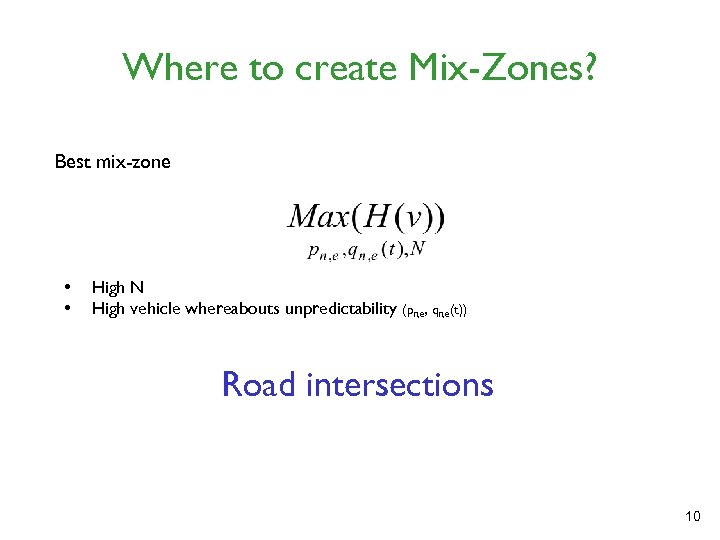 Where to create Mix-Zones? Best mix-zone • • High N High vehicle whereabouts unpredictability (pn, e, qn, e(t)) Road intersections 10
Where to create Mix-Zones? Best mix-zone • • High N High vehicle whereabouts unpredictability (pn, e, qn, e(t)) Road intersections 10
 High Uncertainty 11
High Uncertainty 11
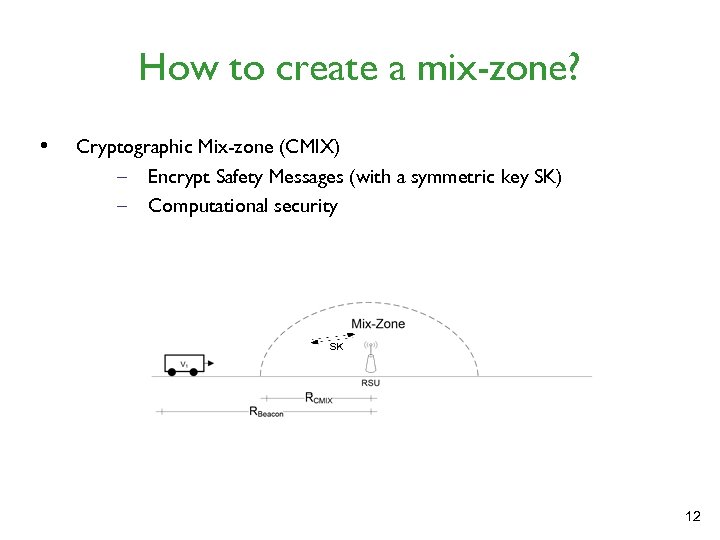 How to create a mix-zone? • Cryptographic Mix-zone (CMIX) – Encrypt Safety Messages (with a symmetric key SK) – Computational security 12
How to create a mix-zone? • Cryptographic Mix-zone (CMIX) – Encrypt Safety Messages (with a symmetric key SK) – Computational security 12
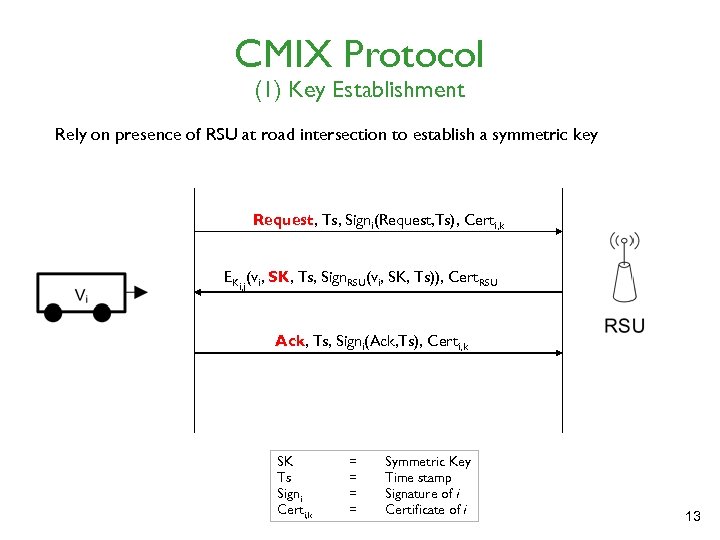 CMIX Protocol (1) Key Establishment Rely on presence of RSU at road intersection to establish a symmetric key Request, Ts, Signi(Request, Ts), Certi, k EKi, j(vi, SK, Ts, Sign. RSU(vi, SK, Ts)), Cert. RSU Ack, Ts, Signi(Ack, Ts), Certi, k SK Ts Signi Certi, k = = Symmetric Key Time stamp Signature of i Certificate of i 13
CMIX Protocol (1) Key Establishment Rely on presence of RSU at road intersection to establish a symmetric key Request, Ts, Signi(Request, Ts), Certi, k EKi, j(vi, SK, Ts, Sign. RSU(vi, SK, Ts)), Cert. RSU Ack, Ts, Signi(Ack, Ts), Certi, k SK Ts Signi Certi, k = = Symmetric Key Time stamp Signature of i Certificate of i 13
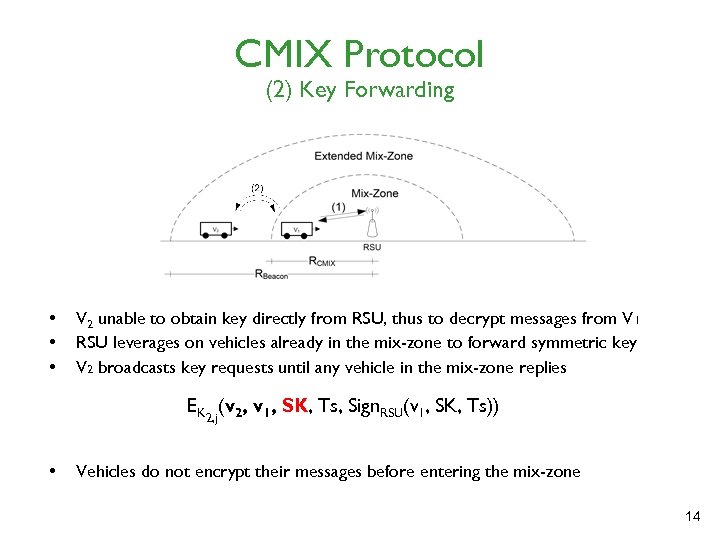 CMIX Protocol (2) Key Forwarding • • • V 2 unable to obtain key directly from RSU, thus to decrypt messages from V 1 RSU leverages on vehicles already in the mix-zone to forward symmetric key V 2 broadcasts key requests until any vehicle in the mix-zone replies EK 2, j(v 2, v 1, SK, Ts, Sign. RSU(v 1, SK, Ts)) • Vehicles do not encrypt their messages before entering the mix-zone 14
CMIX Protocol (2) Key Forwarding • • • V 2 unable to obtain key directly from RSU, thus to decrypt messages from V 1 RSU leverages on vehicles already in the mix-zone to forward symmetric key V 2 broadcasts key requests until any vehicle in the mix-zone replies EK 2, j(v 2, v 1, SK, Ts, Sign. RSU(v 1, SK, Ts)) • Vehicles do not encrypt their messages before entering the mix-zone 14
 CMIX Protocol (3) Key Update • RSU initiates key update to – renew keys – revoke keys • Update is triggered when – Mix-zone is empty • CA is informed of new SK for liability issues • Asynchronous key updates across mix-zones improve system security 15
CMIX Protocol (3) Key Update • RSU initiates key update to – renew keys – revoke keys • Update is triggered when – Mix-zone is empty • CA is informed of new SK for liability issues • Asynchronous key updates across mix-zones improve system security 15
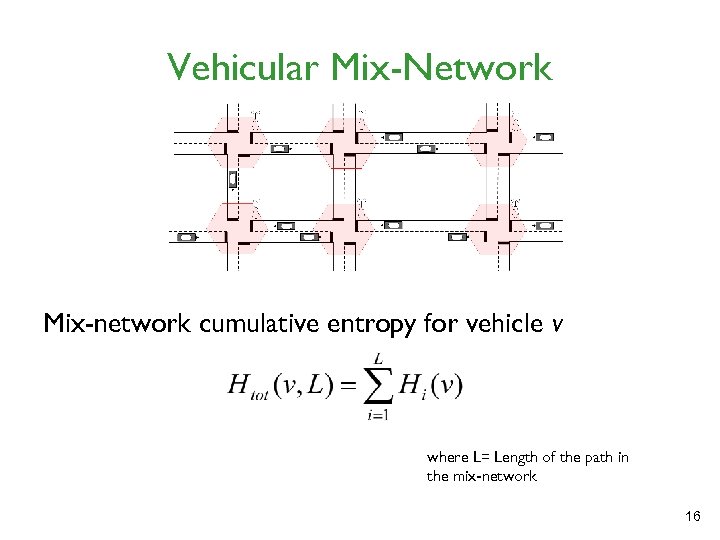 Vehicular Mix-Network Mix-network cumulative entropy for vehicle v where L= Length of the path in the mix-network 16
Vehicular Mix-Network Mix-network cumulative entropy for vehicle v where L= Length of the path in the mix-network 16
 Simulation Setup • 10 X 10 Manhattan network with 4 roads/intersection • N ~ Poisson( ) vehicles per intersection at network initialization • Vehicle inter arrival time ~ Uniform[0, T] models – High traffic congestion – Low traffic congestion • Intersection characteristics – qn, e(t) ~ N( n, e, n, e) for each intersection – pn, e randomly chosen for each intersection 17
Simulation Setup • 10 X 10 Manhattan network with 4 roads/intersection • N ~ Poisson( ) vehicles per intersection at network initialization • Vehicle inter arrival time ~ Uniform[0, T] models – High traffic congestion – Low traffic congestion • Intersection characteristics – qn, e(t) ~ N( n, e, n, e) for each intersection – pn, e randomly chosen for each intersection 17
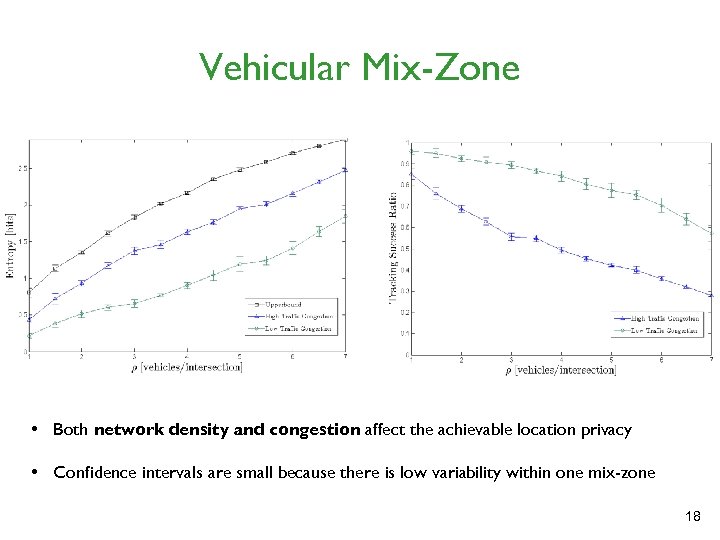 Vehicular Mix-Zone • Both network density and congestion affect the achievable location privacy • Confidence intervals are small because there is low variability within one mix-zone 18
Vehicular Mix-Zone • Both network density and congestion affect the achievable location privacy • Confidence intervals are small because there is low variability within one mix-zone 18
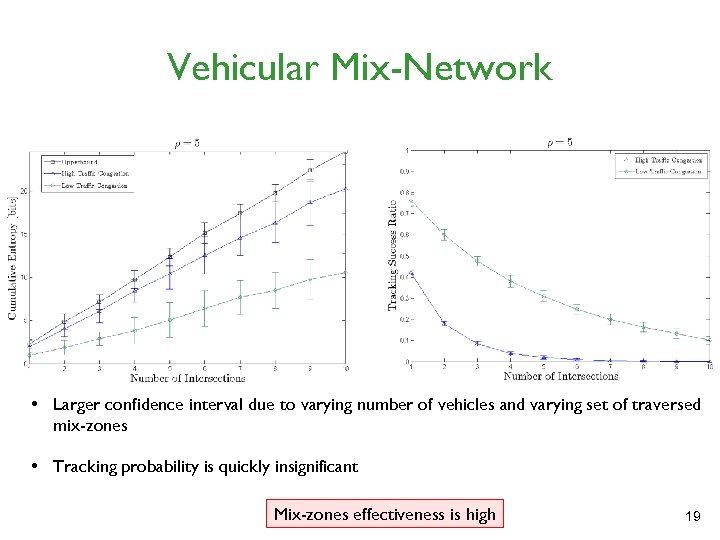 Vehicular Mix-Network • Larger confidence interval due to varying number of vehicles and varying set of traversed mix-zones • Tracking probability is quickly insignificant Mix-zones effectiveness is high 19
Vehicular Mix-Network • Larger confidence interval due to varying number of vehicles and varying set of traversed mix-zones • Tracking probability is quickly insignificant Mix-zones effectiveness is high 19
 Conclusions • Mix-zone effectiveness depends on – Intersection’s congestion – Vehicle’s density – Vehicles’ whereabouts unpredictability • Vehicular mix-network effectiveness – Has large variance – But is overall high • Need more simulations – With realistic traffic traces • Efficiency of vehicular mix-network is independent of CMIX protocol – Alternative CMIX protocols could exploit location 20
Conclusions • Mix-zone effectiveness depends on – Intersection’s congestion – Vehicle’s density – Vehicles’ whereabouts unpredictability • Vehicular mix-network effectiveness – Has large variance – But is overall high • Need more simulations – With realistic traffic traces • Efficiency of vehicular mix-network is independent of CMIX protocol – Alternative CMIX protocols could exploit location 20
 References • L. Buttyán, T. Holczer, and I. Vajda. On the Effectiveness of Changing Pseudonyms to Provide Location Privacy in VANETs. ESAS 2007 • A. R. Beresford. Mix-zones: User privacy in location-aware services. Per. Sec 2004 • L. Huang, K. Matsuura, H. Yamane, and K. Sezaki. Silent cascade: Enhancing location privacy without communication Qo. S degradation. SPC 2005 • M. Li, K. Sampigethaya, L. Huang, and R. Poovendran. Swing & Swap: User-centric Approaches Towards Maximizing Location Privacy. WPES 2006 • M. Raya, P. Papadimitratos, and J. -P. Hubaux. Securing Vehicular Communications. IEEE Wireless Communications magazine, 2006 21
References • L. Buttyán, T. Holczer, and I. Vajda. On the Effectiveness of Changing Pseudonyms to Provide Location Privacy in VANETs. ESAS 2007 • A. R. Beresford. Mix-zones: User privacy in location-aware services. Per. Sec 2004 • L. Huang, K. Matsuura, H. Yamane, and K. Sezaki. Silent cascade: Enhancing location privacy without communication Qo. S degradation. SPC 2005 • M. Li, K. Sampigethaya, L. Huang, and R. Poovendran. Swing & Swap: User-centric Approaches Towards Maximizing Location Privacy. WPES 2006 • M. Raya, P. Papadimitratos, and J. -P. Hubaux. Securing Vehicular Communications. IEEE Wireless Communications magazine, 2006 21
 CMIX Protocol Analysis • Transmission Complexity – Key requests scale with network condition – Avoid key reply flooding by backoff mechanism and key acknowledgement • Computational Complexity – The number of exponentiations is manageable – Load is shared among vehicles in the CMIX • Security – Impersonation/Instantiation attacks are unfeasible – Denial of service attacks are hard – Cost to become internal adversary is high 22
CMIX Protocol Analysis • Transmission Complexity – Key requests scale with network condition – Avoid key reply flooding by backoff mechanism and key acknowledgement • Computational Complexity – The number of exponentiations is manageable – Load is shared among vehicles in the CMIX • Security – Impersonation/Instantiation attacks are unfeasible – Denial of service attacks are hard – Cost to become internal adversary is high 22


