7c8c9b8adcd692ec6abdcd3b4744e985.ppt
- Количество слайдов: 31
 Mitigating Rogue Access Points in Corporate Environments (Design, Implementation and Deployment of a Wireless IDS) FIRST Singapore – June 29, 2005 Laurent BUTTI – France Telecom Division R&D firstname. lastname AT francetelecom dot com The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 1 - June 29, 2005
Mitigating Rogue Access Points in Corporate Environments (Design, Implementation and Deployment of a Wireless IDS) FIRST Singapore – June 29, 2005 Laurent BUTTI – France Telecom Division R&D firstname. lastname AT francetelecom dot com The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 1 - June 29, 2005
 Introduction The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 2 - June 29, 2005
Introduction The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 2 - June 29, 2005
 Context s Wireless networks are widely available in corporate environments QWireless infrastructures for employee access (IPsec or WPA/WPA 2) QWireless infrastructures for guest access (captive portal) QWireless chipsets shipped by default on most laptops today s These facts fatally lead to several weaknesses QInformation leaking about your wireless infrastructure and laptops QError-prone configurations and uncontrolled experimental networks QUncontrolled adhoc networks that may represent a critical hole (double-attachment) s New security mechanisms (WPA/IEEE 802. 11 i) can not address these issues! D 3 - June 29, 2005
Context s Wireless networks are widely available in corporate environments QWireless infrastructures for employee access (IPsec or WPA/WPA 2) QWireless infrastructures for guest access (captive portal) QWireless chipsets shipped by default on most laptops today s These facts fatally lead to several weaknesses QInformation leaking about your wireless infrastructure and laptops QError-prone configurations and uncontrolled experimental networks QUncontrolled adhoc networks that may represent a critical hole (double-attachment) s New security mechanisms (WPA/IEEE 802. 11 i) can not address these issues! D 3 - June 29, 2005
 Need a Wireless IDS? s Combine the context with attacker’s panoply QAccess point mode available with most *nix drivers and firmwares QLightweight access points to be plugged in corporate networks QWardriving tools (obvious process to a more intrusive attack) QFrame injection attacks that may be disrupting s Difficulties to know the status of wireless networks QJust ask your sysadmins to tell you about this! QAttacks in action? Wardriving and man-in-the-middle attacks are impossible to detect without any specific tools! QIs there any legitimate or illegitimate access points? s Your wireless environment may be vulnerable… QYou should observe it carefully thanks to a wireless IDS! D 4 - June 29, 2005
Need a Wireless IDS? s Combine the context with attacker’s panoply QAccess point mode available with most *nix drivers and firmwares QLightweight access points to be plugged in corporate networks QWardriving tools (obvious process to a more intrusive attack) QFrame injection attacks that may be disrupting s Difficulties to know the status of wireless networks QJust ask your sysadmins to tell you about this! QAttacks in action? Wardriving and man-in-the-middle attacks are impossible to detect without any specific tools! QIs there any legitimate or illegitimate access points? s Your wireless environment may be vulnerable… QYou should observe it carefully thanks to a wireless IDS! D 4 - June 29, 2005
 Preliminary Choices s Wireless networks were already deployed QEmployee corporate access thanks to IPsec w/ IKE and certificates QEmployee corporate access thanks to WPA w/ EAP-TLS QGuest access thanks to captive portals w/ temporary logins s Overlay wireless IDS solution seems to be straightforward QSpecialized IDS software and dedicated sensors s We decided to design a new tool from scratch QFit our needs and the low-cost requirement QImprove our skills in wireless security area s This presentation will expose our feedbacks on QDesign, Implementation and Deployment of a Wireless IDS QMitigating Rogue Access Points in Corporate Environments D 5 - June 29, 2005
Preliminary Choices s Wireless networks were already deployed QEmployee corporate access thanks to IPsec w/ IKE and certificates QEmployee corporate access thanks to WPA w/ EAP-TLS QGuest access thanks to captive portals w/ temporary logins s Overlay wireless IDS solution seems to be straightforward QSpecialized IDS software and dedicated sensors s We decided to design a new tool from scratch QFit our needs and the low-cost requirement QImprove our skills in wireless security area s This presentation will expose our feedbacks on QDesign, Implementation and Deployment of a Wireless IDS QMitigating Rogue Access Points in Corporate Environments D 5 - June 29, 2005
 Wireless IDS Design and Implementation The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 6 - June 29, 2005
Wireless IDS Design and Implementation The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 6 - June 29, 2005
 Requirements: Overlay Wireless IDS (1/2) s Portable QIndependent of lower layers (any IEEE a/b/g/? monitor capable wireless card) QShould run on any *nix operating system s Flexible and lightweight QCode should not be modified when adding a new event pattern QShould run on embedded devices (e. g. WRT 54 G) with low memory and CPU constraints s Channel hopping compliant QShould not trigger false positives s Enhanced features QEfficient aggregation and correlation QNew MAC spoofing detection engines QNew equipment tracking capabilities D 7 - June 29, 2005
Requirements: Overlay Wireless IDS (1/2) s Portable QIndependent of lower layers (any IEEE a/b/g/? monitor capable wireless card) QShould run on any *nix operating system s Flexible and lightweight QCode should not be modified when adding a new event pattern QShould run on embedded devices (e. g. WRT 54 G) with low memory and CPU constraints s Channel hopping compliant QShould not trigger false positives s Enhanced features QEfficient aggregation and correlation QNew MAC spoofing detection engines QNew equipment tracking capabilities D 7 - June 29, 2005
 Requirements: Overlay Wireless IDS (2/2) s Low-cost QAs overlay solutions may be expensive, low-cost wireless probes and backend tools are mandatory s Ease of use QMust be managed thanks to a WEB interface (log readability, administration…) D 8 - June 29, 2005
Requirements: Overlay Wireless IDS (2/2) s Low-cost QAs overlay solutions may be expensive, low-cost wireless probes and backend tools are mandatory s Ease of use QMust be managed thanks to a WEB interface (log readability, administration…) D 8 - June 29, 2005
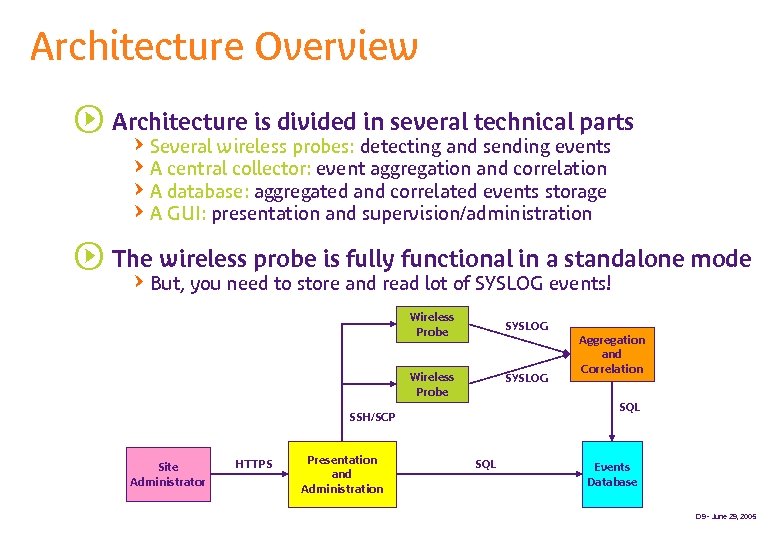 Architecture Overview s Architecture is divided in several technical parts QSeveral wireless probes: detecting and sending events QA central collector: event aggregation and correlation QA database: aggregated and correlated events storage QA GUI: presentation and supervision/administration s The wireless probe is fully functional in a standalone mode QBut, you need to store and read lot of SYSLOG events! Wireless Probe SYSLOG SQL SSH/SCP Site Administrator HTTPS Presentation and Administration Aggregation and Correlation SQL Events Database D 9 - June 29, 2005
Architecture Overview s Architecture is divided in several technical parts QSeveral wireless probes: detecting and sending events QA central collector: event aggregation and correlation QA database: aggregated and correlated events storage QA GUI: presentation and supervision/administration s The wireless probe is fully functional in a standalone mode QBut, you need to store and read lot of SYSLOG events! Wireless Probe SYSLOG SQL SSH/SCP Site Administrator HTTPS Presentation and Administration Aggregation and Correlation SQL Events Database D 9 - June 29, 2005
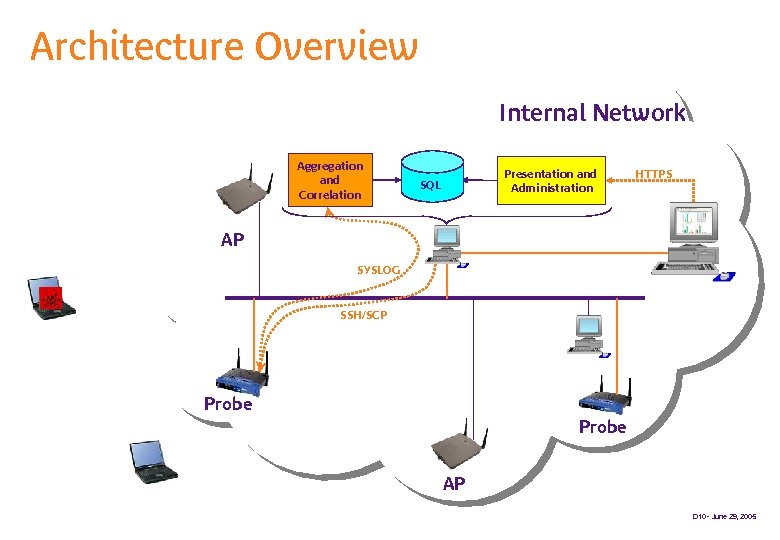 Architecture Overview Internal Network Aggregation and Correlation Presentation and Administration SQL HTTPS AP SYSLOG SSH/SCP Probe AP D 10 - June 29, 2005
Architecture Overview Internal Network Aggregation and Correlation Presentation and Administration SQL HTTPS AP SYSLOG SSH/SCP Probe AP D 10 - June 29, 2005
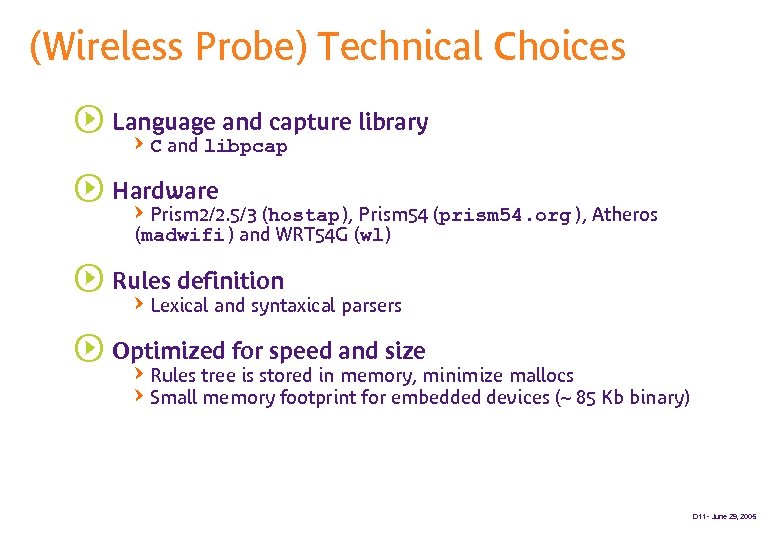 (Wireless Probe) Technical Choices s Language and capture library QC and libpcap s Hardware QPrism 2/2. 5/3 (hostap ), Prism 54 (prism 54. org ), Atheros (madwifi ) and WRT 54 G (wl) s Rules definition QLexical and syntaxical parsers s Optimized for speed and size QRules tree is stored in memory, minimize mallocs QSmall memory footprint for embedded devices (~ 85 Kb binary) D 11 - June 29, 2005
(Wireless Probe) Technical Choices s Language and capture library QC and libpcap s Hardware QPrism 2/2. 5/3 (hostap ), Prism 54 (prism 54. org ), Atheros (madwifi ) and WRT 54 G (wl) s Rules definition QLexical and syntaxical parsers s Optimized for speed and size QRules tree is stored in memory, minimize mallocs QSmall memory footprint for embedded devices (~ 85 Kb binary) D 11 - June 29, 2005
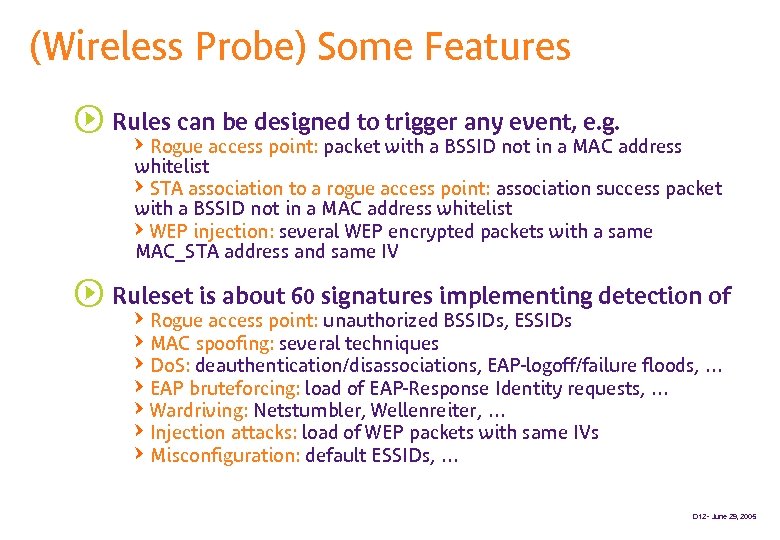 (Wireless Probe) Some Features s Rules can be designed to trigger any event, e. g. QRogue access point: packet with a BSSID not in a MAC address whitelist QSTA association to a rogue access point: association success packet with a BSSID not in a MAC address whitelist QWEP injection: several WEP encrypted packets with a same MAC_STA address and same IV s Ruleset is about 60 signatures implementing detection of QRogue access point: unauthorized BSSIDs, ESSIDs QMAC spoofing: several techniques QDo. S: deauthentication/disassociations, EAP-logoff/failure floods, … QEAP bruteforcing: load of EAP-Response Identity requests, … QWardriving: Netstumbler, Wellenreiter, … QInjection attacks: load of WEP packets with same IVs QMisconfiguration: default ESSIDs, … D 12 - June 29, 2005
(Wireless Probe) Some Features s Rules can be designed to trigger any event, e. g. QRogue access point: packet with a BSSID not in a MAC address whitelist QSTA association to a rogue access point: association success packet with a BSSID not in a MAC address whitelist QWEP injection: several WEP encrypted packets with a same MAC_STA address and same IV s Ruleset is about 60 signatures implementing detection of QRogue access point: unauthorized BSSIDs, ESSIDs QMAC spoofing: several techniques QDo. S: deauthentication/disassociations, EAP-logoff/failure floods, … QEAP bruteforcing: load of EAP-Response Identity requests, … QWardriving: Netstumbler, Wellenreiter, … QInjection attacks: load of WEP packets with same IVs QMisconfiguration: default ESSIDs, … D 12 - June 29, 2005
 (Wireless Probe) WRT 54 G Port s Linksys WRT 54 G (802. 11 b/g access point) QHardware (v 1. 0) – RAM: 16 MB, Flash: 4 MB – CPU: BCM 94702 (125 MHz MIPS) – Ethernet: ADMtek ADM 6996 5 port 10/100 switch QOthers – WPA compliant – Wireless driver is proprietary – Firmware source code is released under the GPL license s We used Open. WRT’s firmware QUpgrading new firmware by HTTP (Linksys’s) or TFTP with "nvram set boot_wait=on " QCross-compilation of new binaries (MIPS) QPackage construction with ipkg QMust configure starting scripts D 13 - June 29, 2005
(Wireless Probe) WRT 54 G Port s Linksys WRT 54 G (802. 11 b/g access point) QHardware (v 1. 0) – RAM: 16 MB, Flash: 4 MB – CPU: BCM 94702 (125 MHz MIPS) – Ethernet: ADMtek ADM 6996 5 port 10/100 switch QOthers – WPA compliant – Wireless driver is proprietary – Firmware source code is released under the GPL license s We used Open. WRT’s firmware QUpgrading new firmware by HTTP (Linksys’s) or TFTP with "nvram set boot_wait=on " QCross-compilation of new binaries (MIPS) QPackage construction with ipkg QMust configure starting scripts D 13 - June 29, 2005
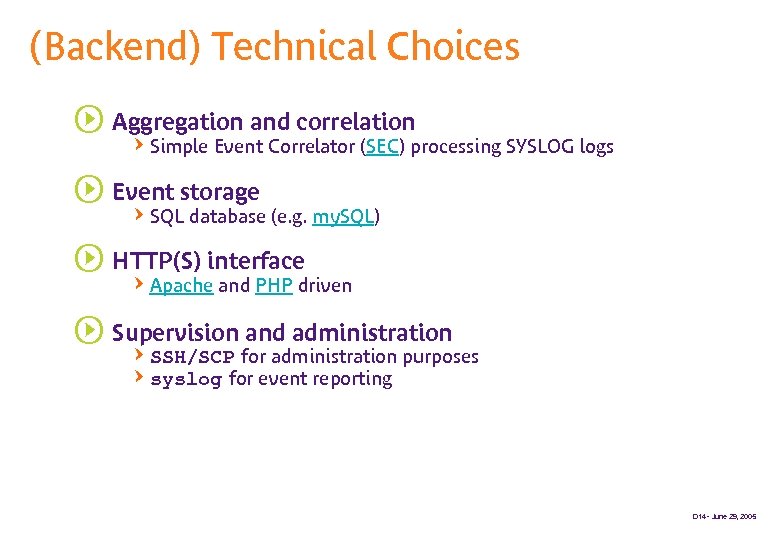 (Backend) Technical Choices s Aggregation and correlation QSimple Event Correlator (SEC) processing SYSLOG logs s Event storage QSQL database (e. g. my. SQL) s HTTP(S) interface QApache and PHP driven s Supervision and administration QSSH/SCP for administration purposes Qsyslog for event reporting D 14 - June 29, 2005
(Backend) Technical Choices s Aggregation and correlation QSimple Event Correlator (SEC) processing SYSLOG logs s Event storage QSQL database (e. g. my. SQL) s HTTP(S) interface QApache and PHP driven s Supervision and administration QSSH/SCP for administration purposes Qsyslog for event reporting D 14 - June 29, 2005
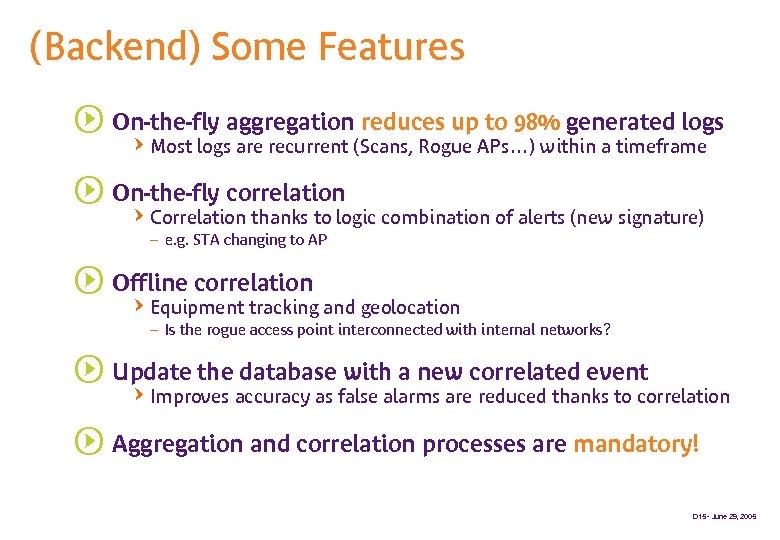 (Backend) Some Features s On-the-fly aggregation reduces up to 98% generated logs QMost logs are recurrent (Scans, Rogue APs…) within a timeframe s On-the-fly correlation QCorrelation thanks to logic combination of alerts (new signature) – e. g. STA changing to AP s Offline correlation QEquipment tracking and geolocation – Is the rogue access point interconnected with internal networks? s Update the database with a new correlated event QImproves accuracy as false alarms are reduced thanks to correlation s Aggregation and correlation processes are mandatory! D 15 - June 29, 2005
(Backend) Some Features s On-the-fly aggregation reduces up to 98% generated logs QMost logs are recurrent (Scans, Rogue APs…) within a timeframe s On-the-fly correlation QCorrelation thanks to logic combination of alerts (new signature) – e. g. STA changing to AP s Offline correlation QEquipment tracking and geolocation – Is the rogue access point interconnected with internal networks? s Update the database with a new correlated event QImproves accuracy as false alarms are reduced thanks to correlation s Aggregation and correlation processes are mandatory! D 15 - June 29, 2005
 Detection and Mitigation The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 16 - June 29, 2005
Detection and Mitigation The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 16 - June 29, 2005
 Case Study: Rogue Access Points s You must address QMisconfigured legitimate access points QIllegitimately connected access points (by malicious people or not) s Processing steps QDetection: Detect rogue access points QEvaluation: Determine if rogue access points are interconnected with internal networks and if possible their physical location QMitigation: Mitigate the risks of rogue access points interconnected with internal networks s Of course, you must know all BSSIDs/ESSIDs of your legitimate access points… D 17 - June 29, 2005
Case Study: Rogue Access Points s You must address QMisconfigured legitimate access points QIllegitimately connected access points (by malicious people or not) s Processing steps QDetection: Detect rogue access points QEvaluation: Determine if rogue access points are interconnected with internal networks and if possible their physical location QMitigation: Mitigate the risks of rogue access points interconnected with internal networks s Of course, you must know all BSSIDs/ESSIDs of your legitimate access points… D 17 - June 29, 2005
 Rogue Access Points: Detection s Rogue access points not spoofing a legitimate BSSID QDetected thanks to a MAC address white list (BSSID mismatch) s Rogue access points spoofing a legitimate BSSID QDetected thanks to a correlation of several MAC spoofing techniques – – “Layer 2” sequence numbers variations (thanks to Joshua Wright) “Layer 2” signal strength variations “Layer 2” timestamp inconsistencies “Layer 2” tagged parameters inconsistencies s But, these techniques cannot determine if rogue access points are interconnected to internal networks! D 18 - June 29, 2005
Rogue Access Points: Detection s Rogue access points not spoofing a legitimate BSSID QDetected thanks to a MAC address white list (BSSID mismatch) s Rogue access points spoofing a legitimate BSSID QDetected thanks to a correlation of several MAC spoofing techniques – – “Layer 2” sequence numbers variations (thanks to Joshua Wright) “Layer 2” signal strength variations “Layer 2” timestamp inconsistencies “Layer 2” tagged parameters inconsistencies s But, these techniques cannot determine if rogue access points are interconnected to internal networks! D 18 - June 29, 2005
 Rogue Access Points: Evaluation s Evaluation will help us to determine QIf rogue access points are interconnected to internal networks QThe exact location of rogue access points QThe approximate physical location of rogue access points s ‘Automatic’ association with a wireless probe to a rogue access point QRetrieve the ESSID thanks to syslog events QAssociation, act as a DHCP client and send a packet to the internal network and/or to the Internet QIf resultcode == success , this is a critical vulnerability!!! QOf course, this must be used with caution – Do not connect to (millions of) fake access points! – De-activate bridge, put firewall rules on your wireless interface… D 19 - June 29, 2005
Rogue Access Points: Evaluation s Evaluation will help us to determine QIf rogue access points are interconnected to internal networks QThe exact location of rogue access points QThe approximate physical location of rogue access points s ‘Automatic’ association with a wireless probe to a rogue access point QRetrieve the ESSID thanks to syslog events QAssociation, act as a DHCP client and send a packet to the internal network and/or to the Internet QIf resultcode == success , this is a critical vulnerability!!! QOf course, this must be used with caution – Do not connect to (millions of) fake access points! – De-activate bridge, put firewall rules on your wireless interface… D 19 - June 29, 2005
 Rogue Access Points: Evaluation s Seek in switches MAC tables QSource and destination MAC addresses of data frames QBSSID +1/– 1 MAC addresses QPerformed thanks to Netdisco an Open Source network management tool s Equipment geolocation thanks to signal strength analysis QUse the RSSI (Received Signal Strength Index) QAvailable in PRISM Monitoring Header in monitor mode QHard to design an efficient technique (calibration, propagation model, attenuation model, interferences…) QDefine if an access point is within corporate physical perimeter s But these techniques cannot mitigate rogue access points! D 20 - June 29, 2005
Rogue Access Points: Evaluation s Seek in switches MAC tables QSource and destination MAC addresses of data frames QBSSID +1/– 1 MAC addresses QPerformed thanks to Netdisco an Open Source network management tool s Equipment geolocation thanks to signal strength analysis QUse the RSSI (Received Signal Strength Index) QAvailable in PRISM Monitoring Header in monitor mode QHard to design an efficient technique (calibration, propagation model, attenuation model, interferences…) QDefine if an access point is within corporate physical perimeter s But these techniques cannot mitigate rogue access points! D 20 - June 29, 2005
 Rogue Access Points: Mitigation s Switch port shutdown thanks to evaluation results QAs false alarms are always possible, switch port shutdown is up to the decision of the site administrator QOur tool only provides necessary information to take an action QYou must be sure! De-activating legitimate access points is not an option! s Radio containment capabilities could be developed (seeking some clues for wl driver injection!) QDEAUTH/DISASSOC frames may be sent to prevent clients from associating to rogue access points QYou must be sure! Do. Sing neighbors is not an option! s These techniques are effective, but must be activated with caution! D 21 - June 29, 2005
Rogue Access Points: Mitigation s Switch port shutdown thanks to evaluation results QAs false alarms are always possible, switch port shutdown is up to the decision of the site administrator QOur tool only provides necessary information to take an action QYou must be sure! De-activating legitimate access points is not an option! s Radio containment capabilities could be developed (seeking some clues for wl driver injection!) QDEAUTH/DISASSOC frames may be sent to prevent clients from associating to rogue access points QYou must be sure! Do. Sing neighbors is not an option! s These techniques are effective, but must be activated with caution! D 21 - June 29, 2005
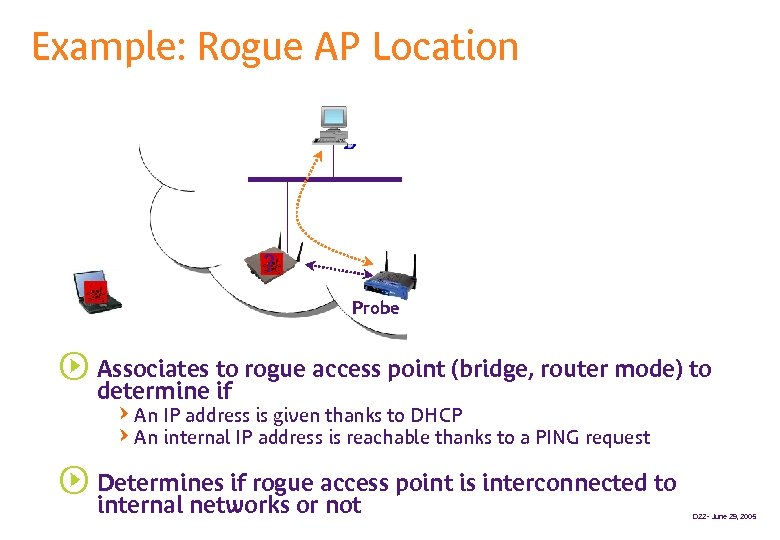 Example: Rogue AP Location ? Probe s Associates to rogue access point (bridge, router mode) to determine if QAn IP address is given thanks to DHCP QAn internal IP address is reachable thanks to a PING request s Determines if rogue access point is interconnected to internal networks or not D 22 - June 29, 2005
Example: Rogue AP Location ? Probe s Associates to rogue access point (bridge, router mode) to determine if QAn IP address is given thanks to DHCP QAn internal IP address is reachable thanks to a PING request s Determines if rogue access point is interconnected to internal networks or not D 22 - June 29, 2005
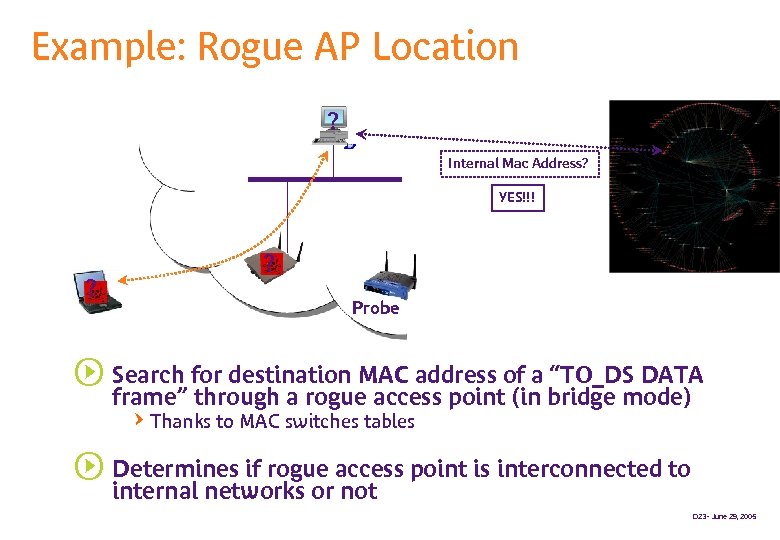 Example: Rogue AP Location ? Internal Mac Address? YES!!! ? ? Probe s Search for destination MAC address of a “TO_DS DATA frame” through a rogue access point (in bridge mode) QThanks to MAC switches tables s Determines if rogue access point is interconnected to internal networks or not D 23 - June 29, 2005
Example: Rogue AP Location ? Internal Mac Address? YES!!! ? ? Probe s Search for destination MAC address of a “TO_DS DATA frame” through a rogue access point (in bridge mode) QThanks to MAC switches tables s Determines if rogue access point is interconnected to internal networks or not D 23 - June 29, 2005
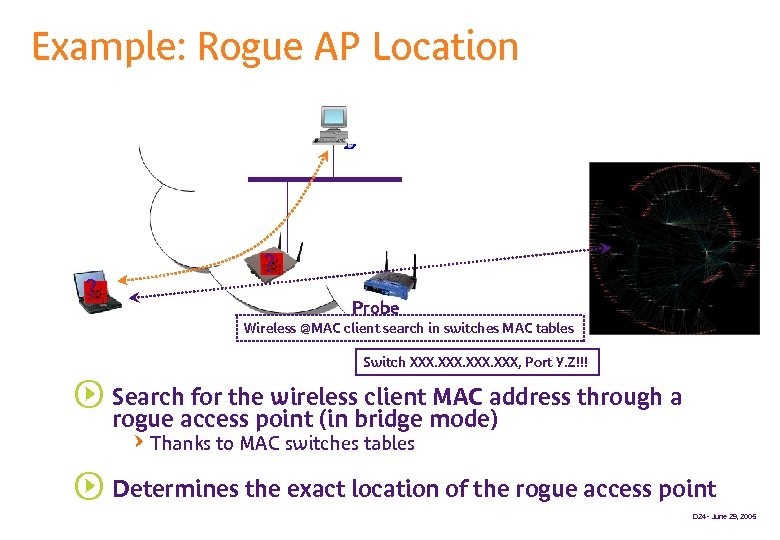 Example: Rogue AP Location ? ? Probe Wireless @MAC client search in switches MAC tables Switch XXX, Port Y. Z!!! s Search for the wireless client MAC address through a rogue access point (in bridge mode) QThanks to MAC switches tables s Determines the exact location of the rogue access point D 24 - June 29, 2005
Example: Rogue AP Location ? ? Probe Wireless @MAC client search in switches MAC tables Switch XXX, Port Y. Z!!! s Search for the wireless client MAC address through a rogue access point (in bridge mode) QThanks to MAC switches tables s Determines the exact location of the rogue access point D 24 - June 29, 2005
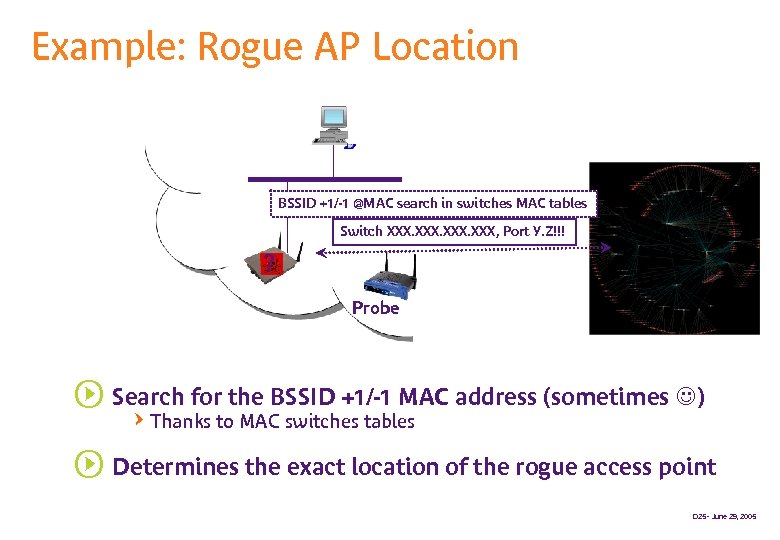 Example: Rogue AP Location BSSID +1/-1 @MAC search in switches MAC tables Switch XXX, Port Y. Z!!! ? Probe s Search for the BSSID +1/-1 MAC address (sometimes ) QThanks to MAC switches tables s Determines the exact location of the rogue access point D 25 - June 29, 2005
Example: Rogue AP Location BSSID +1/-1 @MAC search in switches MAC tables Switch XXX, Port Y. Z!!! ? Probe s Search for the BSSID +1/-1 MAC address (sometimes ) QThanks to MAC switches tables s Determines the exact location of the rogue access point D 25 - June 29, 2005
 Feedbacks and Guidelines The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 26 - June 29, 2005
Feedbacks and Guidelines The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 26 - June 29, 2005
 Mitigating Rogue AP Guidelines s Have a physical security policy especially for RJ 45 plugs in meeting rooms! s Consider IEEE 802. 1 X network access control on your RJ 45 s s Know the configuration of your wireless infrastructure (BSSIDs, ESSIDs, crypto-protocols…) s Harden laptops’ configuration (prevent from associating to interfering or rogue access points, avoid double attachment and information leaking) s Deploy a Wireless IDS to achieve observation at radio level D 27 - June 29, 2005
Mitigating Rogue AP Guidelines s Have a physical security policy especially for RJ 45 plugs in meeting rooms! s Consider IEEE 802. 1 X network access control on your RJ 45 s s Know the configuration of your wireless infrastructure (BSSIDs, ESSIDs, crypto-protocols…) s Harden laptops’ configuration (prevent from associating to interfering or rogue access points, avoid double attachment and information leaking) s Deploy a Wireless IDS to achieve observation at radio level D 27 - June 29, 2005
 Wireless IDS Deployment Guidelines s Cost-effective solution fitting your environment s Must have minimal impacts on your architecture s Should have equipment tracking and location s Tune your rule-set for performance and effectiveness s Deploy enough wireless probes at edge of your physical perimeter s Evaluate packet losses on your wireless probes s Do not trust anything! Audit your deployment! (are attacks really detected? ) D 28 - June 29, 2005
Wireless IDS Deployment Guidelines s Cost-effective solution fitting your environment s Must have minimal impacts on your architecture s Should have equipment tracking and location s Tune your rule-set for performance and effectiveness s Deploy enough wireless probes at edge of your physical perimeter s Evaluate packet losses on your wireless probes s Do not trust anything! Audit your deployment! (are attacks really detected? ) D 28 - June 29, 2005
 Feedbacks s Developing a robust wireless IDS is not trivial QYou must deal with load of events (hundreds per second) s Building an efficient GUI for sysadmins is not trivial QThat’s the challenge! s Difficulties to identify all interfering access points QWhat about neighbors, hot spots, … QYou must be sure! s False positive rate is a classic issue for IDS technologies QMinimize this rate thanks to enhanced correlation s Performance issues QLightweight wireless probe may have packet losses QSQL table may become huge D 29 - June 29, 2005
Feedbacks s Developing a robust wireless IDS is not trivial QYou must deal with load of events (hundreds per second) s Building an efficient GUI for sysadmins is not trivial QThat’s the challenge! s Difficulties to identify all interfering access points QWhat about neighbors, hot spots, … QYou must be sure! s False positive rate is a classic issue for IDS technologies QMinimize this rate thanks to enhanced correlation s Performance issues QLightweight wireless probe may have packet losses QSQL table may become huge D 29 - June 29, 2005
 Conclusions s Wi-Fi technologies are changing corporate security policies QMisconfigurations and rogue access point are critical vulnerabilities QEven non-enabled Wi-Fi corporate may be vulnerable s Can you tell me about the status of your wireless networks? QWireless IDS seems to become mandatory s Wireless IDS should detect most wireless security issues QHelp to detect abnormal events that cannot be seen by classic stuff QHelp to detect, evaluate and locate rogue access points QHelp to react on security incidents s Must be combined with a Yagi antenna! QHow could you locate the guy Do. Sing the FIRST wireless networks? !? QOr the guy with a fake FIRST access point who will exploit a remote root on your system? !? D 30 - June 29, 2005
Conclusions s Wi-Fi technologies are changing corporate security policies QMisconfigurations and rogue access point are critical vulnerabilities QEven non-enabled Wi-Fi corporate may be vulnerable s Can you tell me about the status of your wireless networks? QWireless IDS seems to become mandatory s Wireless IDS should detect most wireless security issues QHelp to detect abnormal events that cannot be seen by classic stuff QHelp to detect, evaluate and locate rogue access points QHelp to react on security incidents s Must be combined with a Yagi antenna! QHow could you locate the guy Do. Sing the FIRST wireless networks? !? QOr the guy with a fake FIRST access point who will exploit a remote root on your system? !? D 30 - June 29, 2005
 Questions? Thanks for your attention The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 31 - June 29, 2005
Questions? Thanks for your attention The present document contains information that remains the property of France Telecom. The recipient’s acceptance of this document implies his or her acknowledgement of the confidential nature of its contents and his or her obligation not to reproduce, transmit to a third party, disclose or use for commercial purposes any of its contents whatsoever without France Telecom’s prior written agreement. D 31 - June 29, 2005


