305930fe636d9cb18e3603fe3a9a5e34.ppt
- Количество слайдов: 20
 Mitigate Unauthorized Tracking in RFID Discovery Service Qiang Yan 1, Robert H. Deng 1, Zheng Yan 2, Yingjiu Li 1, Tieyan Li 3 1 Singapore Management University, Singapore 2 Nokia Research Center, Finland 3 Institute for Infocomm Research, Singapore September 2010
Mitigate Unauthorized Tracking in RFID Discovery Service Qiang Yan 1, Robert H. Deng 1, Zheng Yan 2, Yingjiu Li 1, Tieyan Li 3 1 Singapore Management University, Singapore 2 Nokia Research Center, Finland 3 Institute for Infocomm Research, Singapore September 2010
 Outline • Background & Motivation • Discovery Service based Tracking Attack • Pseudonym-based Design – Basic ideas – Scheme I: supporting flexible tag level tracking – Scheme II: supporting user revocation • Conclusion
Outline • Background & Motivation • Discovery Service based Tracking Attack • Pseudonym-based Design – Basic ideas – Scheme I: supporting flexible tag level tracking – Scheme II: supporting user revocation • Conclusion
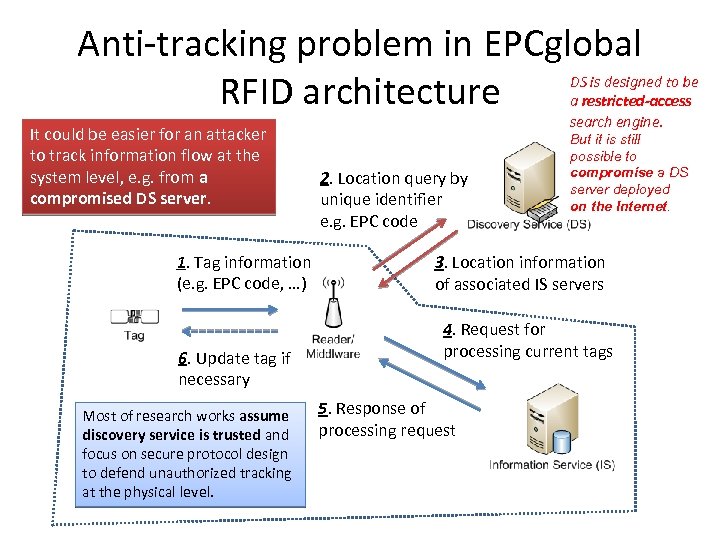 Anti-tracking problem in EPCglobal RFID architecture It could be easier for an attacker to track information flow at the system level, e. g. from a compromised DS server. 1. Tag information (e. g. EPC code, …) 6. Update tag if necessary Most of research works assume discovery service is trusted and focus on secure protocol design to defend unauthorized tracking at the physical level. DS is designed to be a restricted-access search engine. 2. Location query by unique identifier e. g. EPC code But it is still possible to compromise a DS server deployed on the Internet. 3. Location information of associated IS servers 4. Request for processing current tags 5. Response of processing request
Anti-tracking problem in EPCglobal RFID architecture It could be easier for an attacker to track information flow at the system level, e. g. from a compromised DS server. 1. Tag information (e. g. EPC code, …) 6. Update tag if necessary Most of research works assume discovery service is trusted and focus on secure protocol design to defend unauthorized tracking at the physical level. DS is designed to be a restricted-access search engine. 2. Location query by unique identifier e. g. EPC code But it is still possible to compromise a DS server deployed on the Internet. 3. Location information of associated IS servers 4. Request for processing current tags 5. Response of processing request
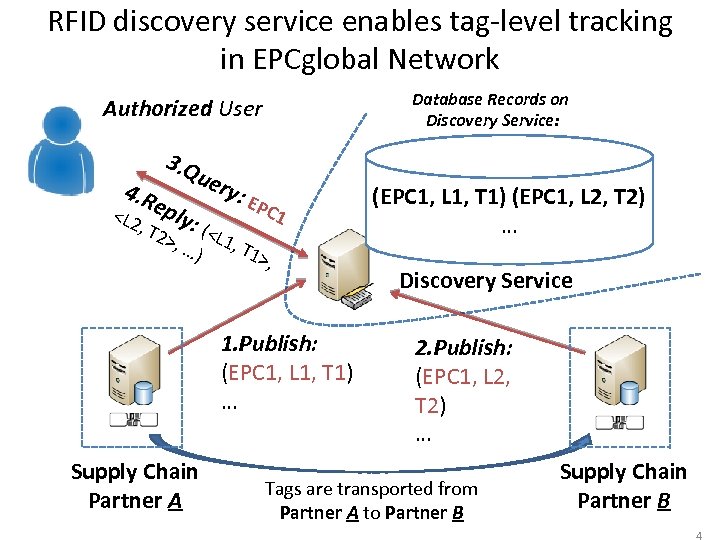 RFID discovery service enables tag-level tracking in EPCglobal Network Database Records on Discovery Service: Authorized User 4. R 3. Q
RFID discovery service enables tag-level tracking in EPCglobal Network Database Records on Discovery Service: Authorized User 4. R 3. Q
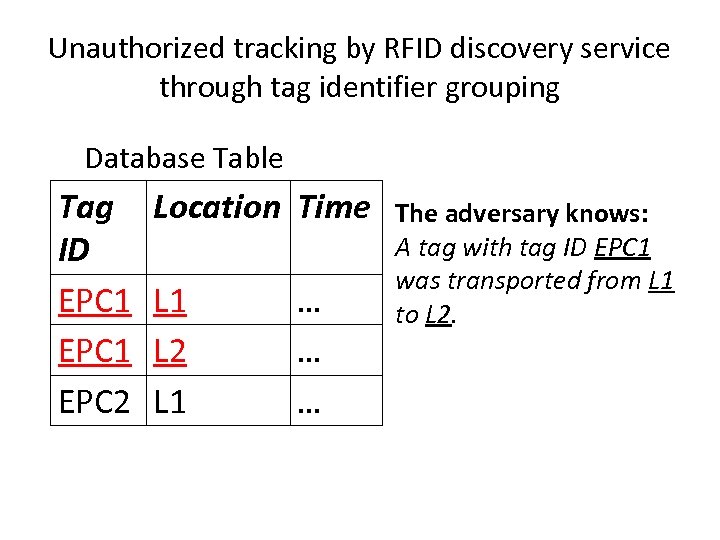 Unauthorized tracking by RFID discovery service through tag identifier grouping Database Table Tag ID EPC 1 EPC 2 Location Time L 1 L 2 L 1 … … … The adversary knows: A tag with tag ID EPC 1 was transported from L 1 to L 2.
Unauthorized tracking by RFID discovery service through tag identifier grouping Database Table Tag ID EPC 1 EPC 2 Location Time L 1 L 2 L 1 … … … The adversary knows: A tag with tag ID EPC 1 was transported from L 1 to L 2.
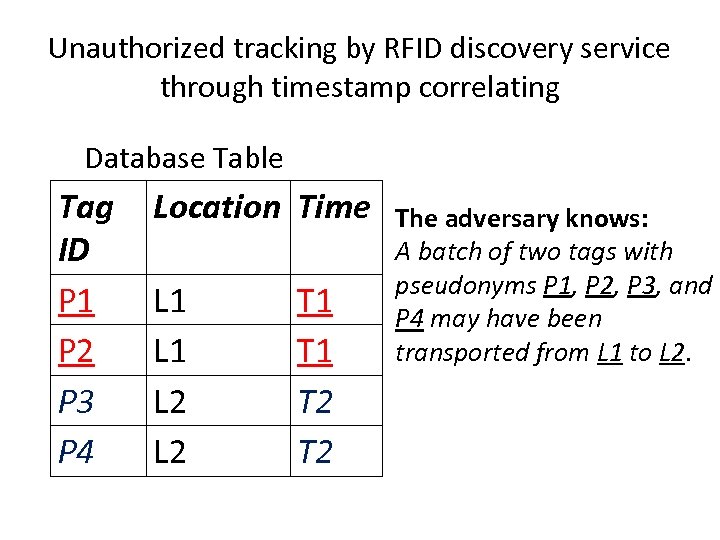 Unauthorized tracking by RFID discovery service through timestamp correlating Database Table Tag ID P 1 P 2 P 3 P 4 Location Time L 1 L 2 T 1 T 2 The adversary knows: A batch of two tags with pseudonyms P 1, P 2, P 3, and P 4 may have been transported from L 1 to L 2.
Unauthorized tracking by RFID discovery service through timestamp correlating Database Table Tag ID P 1 P 2 P 3 P 4 Location Time L 1 L 2 T 1 T 2 The adversary knows: A batch of two tags with pseudonyms P 1, P 2, P 3, and P 4 may have been transported from L 1 to L 2.
 Threat Model – a semi-trusted RFID discovery service • RFID discovery service will obey the regulations but try to learn the tracking information. • It is always able to – understand the system design – read static contents of database
Threat Model – a semi-trusted RFID discovery service • RFID discovery service will obey the regulations but try to learn the tracking information. • It is always able to – understand the system design – read static contents of database
 Threat Model – other roles • Other outliers (weaker than RFID discovery service) – Only be able to eavesdrop network messages • Supply chain partners and authorized users (Trusted) – Do not disclose the secret keys. – Do not collude with the adversaries.
Threat Model – other roles • Other outliers (weaker than RFID discovery service) – Only be able to eavesdrop network messages • Supply chain partners and authorized users (Trusted) – Do not disclose the secret keys. – Do not collude with the adversaries.
 Basic ideas to mitigate this threat • For tag identifier grouping: – Minimize the correlation between records – by using different pseudonym to index multiple records of the same tag • For timestamp correlating: – Hide plaintext timestamps – by storing the ciphertext timestamps
Basic ideas to mitigate this threat • For tag identifier grouping: – Minimize the correlation between records – by using different pseudonym to index multiple records of the same tag • For timestamp correlating: – Hide plaintext timestamps – by storing the ciphertext timestamps
 Pseudonym Indexing • Location records of each individual tag indexed by multiple pseudonyms. • Pseudonym = Func (original tag ID, secret key) • Func is a pseudonym generation function – Deterministic – Unlinkable – e. g. HMAC
Pseudonym Indexing • Location records of each individual tag indexed by multiple pseudonyms. • Pseudonym = Func (original tag ID, secret key) • Func is a pseudonym generation function – Deterministic – Unlinkable – e. g. HMAC
 Timestamp Encryption • Supply chain partner should publish the encrypted timestamps to RFID discovery service. – RFID discovery service should not log the record creation time. • Timestamp is not a index field. – apply non-deterministic encryption algorithms. , e. g. CPA-secure encryption algorithms, AES-CBC – Easy for key management.
Timestamp Encryption • Supply chain partner should publish the encrypted timestamps to RFID discovery service. – RFID discovery service should not log the record creation time. • Timestamp is not a index field. – apply non-deterministic encryption algorithms. , e. g. CPA-secure encryption algorithms, AES-CBC – Easy for key management.
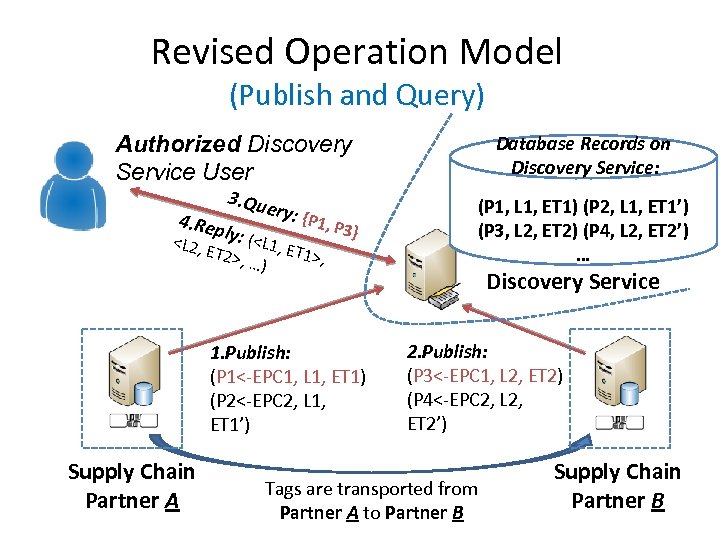 Revised Operation Model (Publish and Query) Authorized Discovery Service User 4. Rep 3. Qu ery: { P 1, P 3
Revised Operation Model (Publish and Query) Authorized Discovery Service User 4. Rep 3. Qu ery: { P 1, P 3
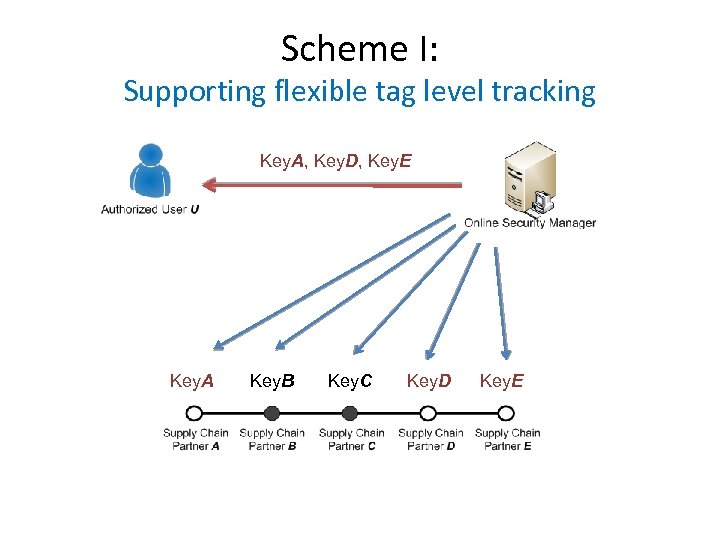 Scheme I: Supporting flexible tag level tracking Key. A, Key. D, Key. E Key. A Key. B Key. C Key. D Key. E
Scheme I: Supporting flexible tag level tracking Key. A, Key. D, Key. E Key. A Key. B Key. C Key. D Key. E
 Drawbacks of Scheme I • Security manager has to be online – Who will be the security manager, after all? – Applies to static user group – User revocation is not supported • To support user revocation – Assign new keys to supply chain partners – However, key update can not be handled well if user group is large with frequent revocations. – How about periodic updating? Not so good, either.
Drawbacks of Scheme I • Security manager has to be online – Who will be the security manager, after all? – Applies to static user group – User revocation is not supported • To support user revocation – Assign new keys to supply chain partners – However, key update can not be handled well if user group is large with frequent revocations. – How about periodic updating? Not so good, either.
 Key Primitive Used in Scheme II • Security manager could be offline, we use Proxy Re-encryption – Proxy re-encryption allows a proxy to transform a ciphertext computed under Alice's public key into one that can be decrypted using Bob's private key. During ciphertext transformation, referred to as re-encryption, the proxy learns nothing about the underlying plaintext. – A proxy re-encryption scheme is represented as a tuple of (possibly probabilistic) polynomial time algorithms (KG, RG, E, R, D):
Key Primitive Used in Scheme II • Security manager could be offline, we use Proxy Re-encryption – Proxy re-encryption allows a proxy to transform a ciphertext computed under Alice's public key into one that can be decrypted using Bob's private key. During ciphertext transformation, referred to as re-encryption, the proxy learns nothing about the underlying plaintext. – A proxy re-encryption scheme is represented as a tuple of (possibly probabilistic) polynomial time algorithms (KG, RG, E, R, D):
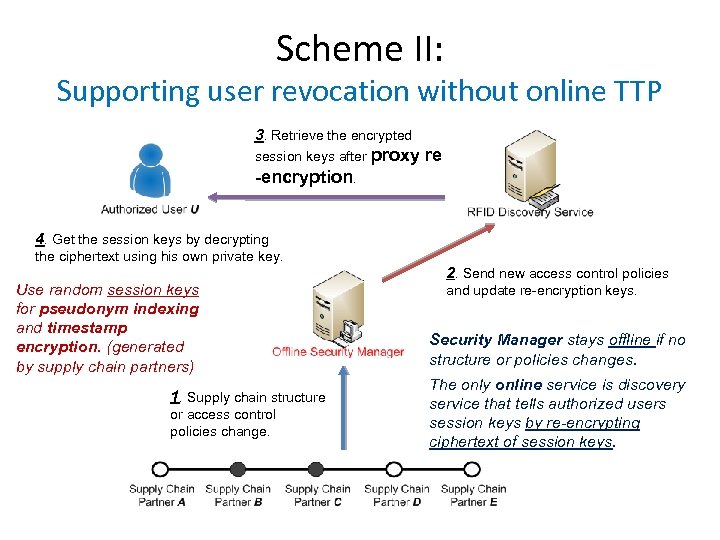 Scheme II: Supporting user revocation without online TTP 3. Retrieve the encrypted session keys after proxy re -encryption. 4. Get the session keys by decrypting the ciphertext using his own private key. Use random session keys for pseudonym indexing and timestamp encryption. (generated by supply chain partners) 1. Supply chain structure or access control policies change. 2. Send new access control policies and update re-encryption keys. Security Manager stays offline if no structure or policies changes. The only online service is discovery service that tells authorized users session keys by re-encrypting ciphertext of session keys.
Scheme II: Supporting user revocation without online TTP 3. Retrieve the encrypted session keys after proxy re -encryption. 4. Get the session keys by decrypting the ciphertext using his own private key. Use random session keys for pseudonym indexing and timestamp encryption. (generated by supply chain partners) 1. Supply chain structure or access control policies change. 2. Send new access control policies and update re-encryption keys. Security Manager stays offline if no structure or policies changes. The only online service is discovery service that tells authorized users session keys by re-encrypting ciphertext of session keys.
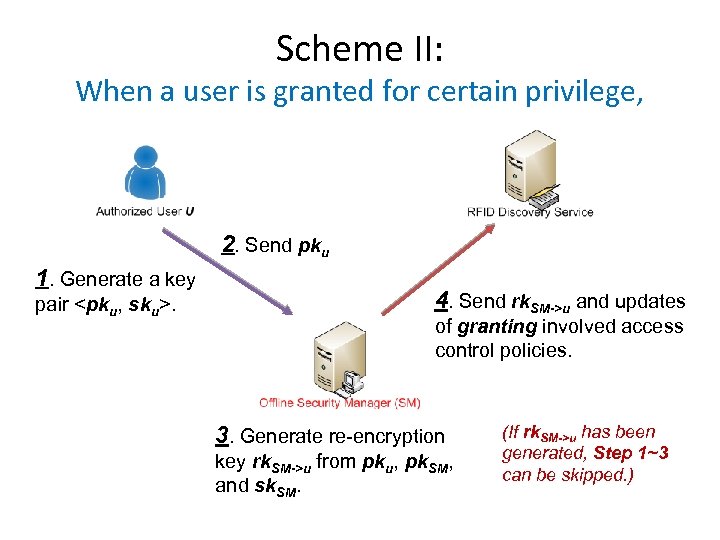 Scheme II: When a user is granted for certain privilege, 2. Send pku 1. Generate a key pair
Scheme II: When a user is granted for certain privilege, 2. Send pku 1. Generate a key pair
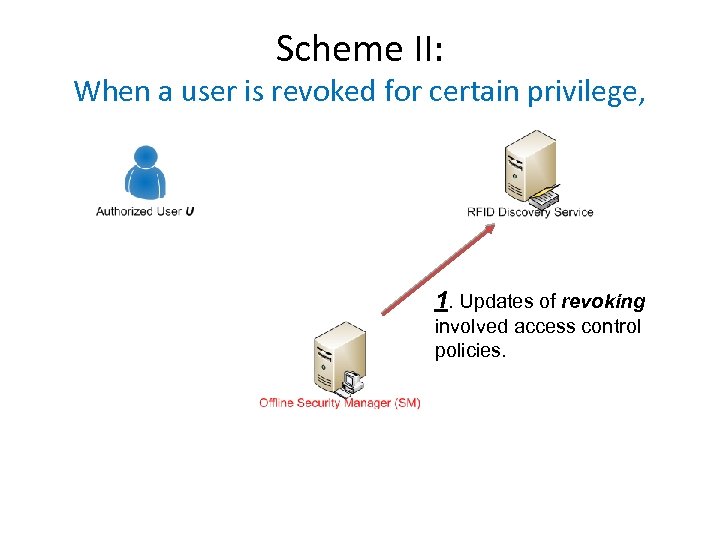 Scheme II: When a user is revoked for certain privilege, 1. Updates of revoking involved access control policies.
Scheme II: When a user is revoked for certain privilege, 1. Updates of revoking involved access control policies.
 Other Privacy Issues • Tracking information disclosure from access patterns – Split related pseudonyms into separate queries – Introduce delays or dummy data in publishing location records to Discovery Service • Tracking information disclosure from collusion attack – Trusted Computing Technique (use TPMs) • The accomplices can use the secrets with knowing them.
Other Privacy Issues • Tracking information disclosure from access patterns – Split related pseudonyms into separate queries – Introduce delays or dummy data in publishing location records to Discovery Service • Tracking information disclosure from collusion attack – Trusted Computing Technique (use TPMs) • The accomplices can use the secrets with knowing them.
 Conclusion • This work – Identified the threat of unauthorized tracking by RFID discovery service. – Proposed pseudonym-based solutions to mitigate this threat.
Conclusion • This work – Identified the threat of unauthorized tracking by RFID discovery service. – Proposed pseudonym-based solutions to mitigate this threat.


