5b2798d80fb9e424c8429a3f1136a0f3.ppt
- Количество слайдов: 101
 MIS 300 100 Top Hits for Slides for the Course With emphasis on the 2 nd half Top 100 1
MIS 300 100 Top Hits for Slides for the Course With emphasis on the 2 nd half Top 100 1
 Contents • • General Model of Problem Solving MIS; DSS; GSS; ESS Specialized Systems Management Support Systems Technological Leadership System Development Risk Management and Security Computer Crime and Ethics Top 100 2
Contents • • General Model of Problem Solving MIS; DSS; GSS; ESS Specialized Systems Management Support Systems Technological Leadership System Development Risk Management and Security Computer Crime and Ethics Top 100 2
 Focus of the Course First six weeks: Information technology and how it works, definitions, IT as a business enabler and platform Last six weeks: What information technology can do for users; user roles; producing and managing information technology; effects of IT Top 100 3
Focus of the Course First six weeks: Information technology and how it works, definitions, IT as a business enabler and platform Last six weeks: What information technology can do for users; user roles; producing and managing information technology; effects of IT Top 100 3
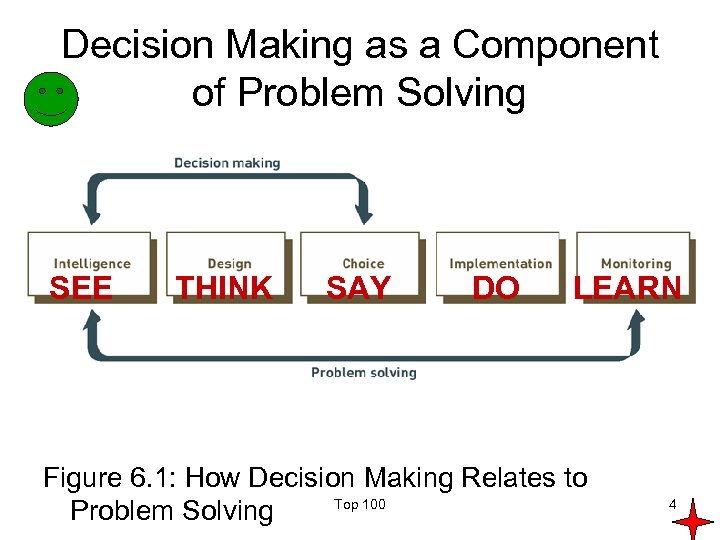 Decision Making as a Component of Problem Solving SEE THINK SAY DO LEARN Figure 6. 1: How Decision Making Relates to Top 100 Problem Solving 4
Decision Making as a Component of Problem Solving SEE THINK SAY DO LEARN Figure 6. 1: How Decision Making Relates to Top 100 Problem Solving 4
 Decision Making as a Component of Problem Solving (continued) • Problem solving: a process that goes beyond decision making to include the implementation stage • Implementation stage: a solution is put into effect • Monitoring stage: decision makers evaluate the implementation Top 100 5
Decision Making as a Component of Problem Solving (continued) • Problem solving: a process that goes beyond decision making to include the implementation stage • Implementation stage: a solution is put into effect • Monitoring stage: decision makers evaluate the implementation Top 100 5
 Programmed Versus Nonprogrammed Decisions • Programmed decisions – Decisions made using a rule, procedure, or quantitative method – Easy to computerize using traditional information systems Top 100 6
Programmed Versus Nonprogrammed Decisions • Programmed decisions – Decisions made using a rule, procedure, or quantitative method – Easy to computerize using traditional information systems Top 100 6
 Programmed Versus Nonprogrammed Decisions (continued) • Nonprogrammed decisions – Decision that deals with unusual or exceptional situations – Not easily quantifiable Top 100 7
Programmed Versus Nonprogrammed Decisions (continued) • Nonprogrammed decisions – Decision that deals with unusual or exceptional situations – Not easily quantifiable Top 100 7
 Optimization, Satisficing, and Heuristic Approaches • Optimization model: a process that finds the best solution, usually the one that will best help the organization meet its goals • Satisficing model: a process that finds a good—but not necessarily the best— problem solution • Heuristics: commonly accepted guidelines or procedures that usually find a good solution Top 100 8
Optimization, Satisficing, and Heuristic Approaches • Optimization model: a process that finds the best solution, usually the one that will best help the organization meet its goals • Satisficing model: a process that finds a good—but not necessarily the best— problem solution • Heuristics: commonly accepted guidelines or procedures that usually find a good solution Top 100 8
 An Overview of Management Information Systems: Management Information Systems in Perspective • A management information system (MIS) provides managers with information that supports effective decision making and provides feedback on daily operations • The use of MISs spans all levels of management Top 100 9
An Overview of Management Information Systems: Management Information Systems in Perspective • A management information system (MIS) provides managers with information that supports effective decision making and provides feedback on daily operations • The use of MISs spans all levels of management Top 100 9
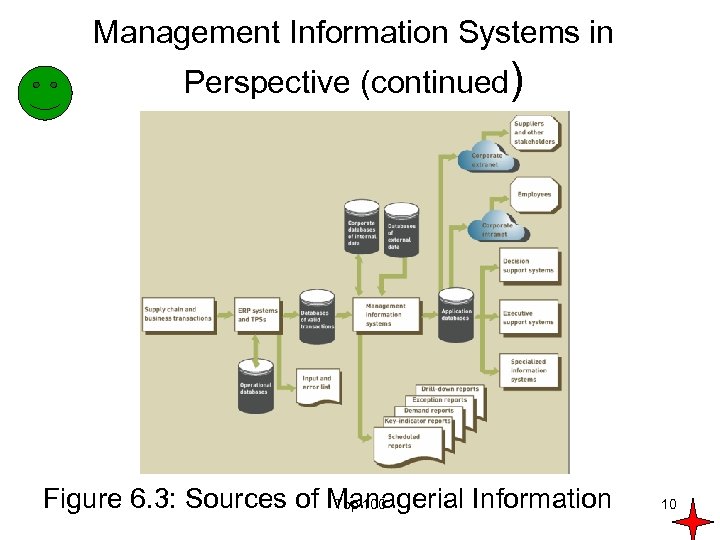 Management Information Systems in Perspective (continued) Figure 6. 3: Sources of Managerial Information Top 100 10
Management Information Systems in Perspective (continued) Figure 6. 3: Sources of Managerial Information Top 100 10
 Outputs of a Management Information System • Scheduled report: produced periodically, or on a schedule • Key-indicator report: summary of the previous day’s critical activities • Demand report: developed to give certain information at someone’s request • Exception report: automatically produced when a situation is unusual or requires management action • Drill-down report: provides increasingly 11 detailed data about a Top 100 situation
Outputs of a Management Information System • Scheduled report: produced periodically, or on a schedule • Key-indicator report: summary of the previous day’s critical activities • Demand report: developed to give certain information at someone’s request • Exception report: automatically produced when a situation is unusual or requires management action • Drill-down report: provides increasingly 11 detailed data about a Top 100 situation
 Functional Aspects of the MIS • Most organizations are structured along functional lines or areas • The MIS can be divided along functional lines to produce reports tailored to individual functions • This tends to lead to fragmentation, the sort of effect that ERP is designed to counter! Top 100 12
Functional Aspects of the MIS • Most organizations are structured along functional lines or areas • The MIS can be divided along functional lines to produce reports tailored to individual functions • This tends to lead to fragmentation, the sort of effect that ERP is designed to counter! Top 100 12
 An Overview of Decision Support Systems • A DSS is an organized collection of people, procedures, software, databases, and devices used to support problemspecific decision making and problem solving • The focus of a DSS is on decision-making effectiveness when faced with unstructured or semistructured business problems Top 100 13
An Overview of Decision Support Systems • A DSS is an organized collection of people, procedures, software, databases, and devices used to support problemspecific decision making and problem solving • The focus of a DSS is on decision-making effectiveness when faced with unstructured or semistructured business problems Top 100 13
 Capabilities of a Decision Support System • • Support all problem-solving phases Support different decision frequencies Support different problem structures Support various decision-making levels Top 100 14
Capabilities of a Decision Support System • • Support all problem-solving phases Support different decision frequencies Support different problem structures Support various decision-making levels Top 100 14
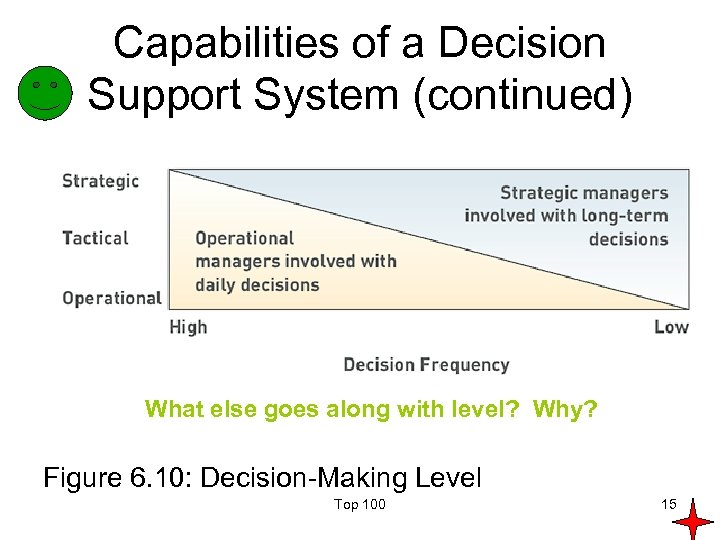 Capabilities of a Decision Support System (continued) What else goes along with level? Why? Figure 6. 10: Decision-Making Level Top 100 15
Capabilities of a Decision Support System (continued) What else goes along with level? Why? Figure 6. 10: Decision-Making Level Top 100 15
 Components of a DSS • Model base: provides decision makers access to a variety of models and assists them in decision making • Database • External database access • Access to the Internet and corporate intranet, networks, and other computer systems • Dialogue manager: allows decision makers to easily access and manipulate the DSS and to use common business terms and phrases Top 100 16
Components of a DSS • Model base: provides decision makers access to a variety of models and assists them in decision making • Database • External database access • Access to the Internet and corporate intranet, networks, and other computer systems • Dialogue manager: allows decision makers to easily access and manipulate the DSS and to use common business terms and phrases Top 100 16
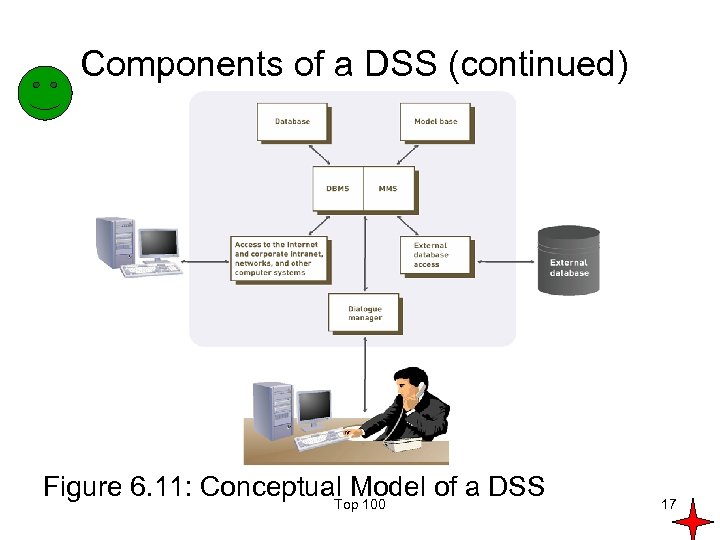 Components of a DSS (continued) Figure 6. 11: Conceptual Model of a DSS Top 100 17
Components of a DSS (continued) Figure 6. 11: Conceptual Model of a DSS Top 100 17
 Group Support Systems • Group support system (GSS) – Consists of most elements in a DSS, plus software to provide effective support in group decision making – Also called group decision support system or computerized collaborative work system Top 100 18
Group Support Systems • Group support system (GSS) – Consists of most elements in a DSS, plus software to provide effective support in group decision making – Also called group decision support system or computerized collaborative work system Top 100 18
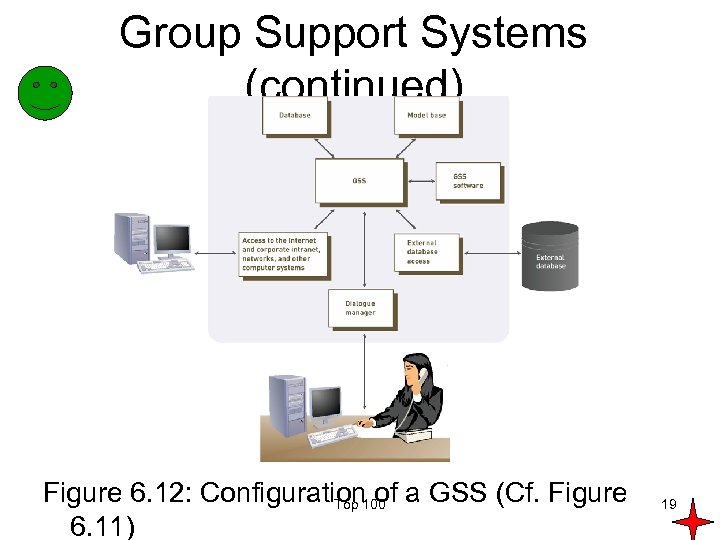 Group Support Systems (continued) Figure 6. 12: Configuration 100 a GSS (Cf. Figure Top of 6. 11) 19
Group Support Systems (continued) Figure 6. 12: Configuration 100 a GSS (Cf. Figure Top of 6. 11) 19
 Characteristics of a GSS That Enhance Decision Making • • Special design Ease of use Flexibility Decision-making support Anonymous input Reduction of negative group behavior Parallel communication Automated record keeping Top 100 20
Characteristics of a GSS That Enhance Decision Making • • Special design Ease of use Flexibility Decision-making support Anonymous input Reduction of negative group behavior Parallel communication Automated record keeping Top 100 20
 Executive Support Systems • Executive support system (ESS): specialized DSS that includes all hardware, software, data, procedures, and people used to assist senior-level executives within the organization Top 100 21
Executive Support Systems • Executive support system (ESS): specialized DSS that includes all hardware, software, data, procedures, and people used to assist senior-level executives within the organization Top 100 21
 Executive Support Systems in Perspective • • Tailored to individual executives Easy to use Drill-down capable Support the need for external data Can help when uncertainty is high Future-oriented Linked to value-added processes Top 100 22
Executive Support Systems in Perspective • • Tailored to individual executives Easy to use Drill-down capable Support the need for external data Can help when uncertainty is high Future-oriented Linked to value-added processes Top 100 22
 Capabilities of Executive Support Systems • Support for defining an overall vision • Support for strategic planning • Support for strategic organizing and staffing • Support for strategic control • Support for crisis management Top 100 23
Capabilities of Executive Support Systems • Support for defining an overall vision • Support for strategic planning • Support for strategic organizing and staffing • Support for strategic control • Support for crisis management Top 100 23
 An Overview of Artificial Intelligence • Artificial intelligence (AI): the ability of computers to mimic or duplicate the functions of the human brain • Artificial intelligence systems: the people, procedures, hardware, software, data, and knowledge needed to develop computer systems and machines that demonstrate the characteristics of intelligence Top 100 24
An Overview of Artificial Intelligence • Artificial intelligence (AI): the ability of computers to mimic or duplicate the functions of the human brain • Artificial intelligence systems: the people, procedures, hardware, software, data, and knowledge needed to develop computer systems and machines that demonstrate the characteristics of intelligence Top 100 24
 The Nature of Intelligence • Learn from experiences and apply knowledge acquired from experience • Handle complex situations • Solve problems when important information is missing • Determine what is important • React quickly and correctly to a new situation • By definition, a computer is unintelligent • The hallmark of intelligence is generating information out of experience. Top 100 25
The Nature of Intelligence • Learn from experiences and apply knowledge acquired from experience • Handle complex situations • Solve problems when important information is missing • Determine what is important • React quickly and correctly to a new situation • By definition, a computer is unintelligent • The hallmark of intelligence is generating information out of experience. Top 100 25
 The Nature of Intelligence (continued) • • Understand visual images Process and manipulate symbols Be creative and imaginative Use heuristics Top 100 26
The Nature of Intelligence (continued) • • Understand visual images Process and manipulate symbols Be creative and imaginative Use heuristics Top 100 26
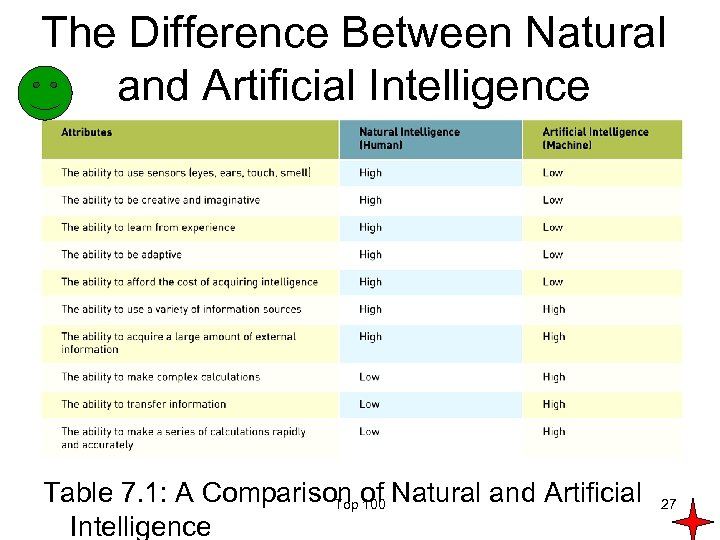 The Difference Between Natural and Artificial Intelligence Table 7. 1: A Comparison of Natural and Artificial Top 100 Intelligence 27
The Difference Between Natural and Artificial Intelligence Table 7. 1: A Comparison of Natural and Artificial Top 100 Intelligence 27
 Expert Systems • Hardware and software that stores knowledge and makes inferences, similar to a human expert • Used in many business applications Top 100 28
Expert Systems • Hardware and software that stores knowledge and makes inferences, similar to a human expert • Used in many business applications Top 100 28
 Robotics • Mechanical or computer devices that perform tasks that either require a high degree of precision or are tedious or hazardous for humans • Contemporary robotics combines highprecision machine capabilities with sophisticated controlling software • Many applications of robotics exist today • Research into robots is continuing Top 100 29
Robotics • Mechanical or computer devices that perform tasks that either require a high degree of precision or are tedious or hazardous for humans • Contemporary robotics combines highprecision machine capabilities with sophisticated controlling software • Many applications of robotics exist today • Research into robots is continuing Top 100 29
 Vision Systems • The hardware and software that permit computers to capture, store, and manipulate visual images and pictures • Used by the U. S. Justice Department to perform fingerprint analysis • Used for identifying people based on facial features Top 100 30
Vision Systems • The hardware and software that permit computers to capture, store, and manipulate visual images and pictures • Used by the U. S. Justice Department to perform fingerprint analysis • Used for identifying people based on facial features Top 100 30
 Natural Language Processing • Processing that allows the computer to understand react to statements and commands made in a “natural” language, such as English • Three levels of voice recognition – Command: recognition of dozens to hundreds of words – Discrete: recognition of dictated speech with pauses between words Top 100 31 – Continuous: recognition of natural speech
Natural Language Processing • Processing that allows the computer to understand react to statements and commands made in a “natural” language, such as English • Three levels of voice recognition – Command: recognition of dozens to hundreds of words – Discrete: recognition of dictated speech with pauses between words Top 100 31 – Continuous: recognition of natural speech
 An Overview of Expert Systems: Characteristics and Limitations of an Expert System • Can explain its reasoning or suggested decisions • Can display “intelligent” behavior • Can draw conclusions from complex relationships • Can provide portable knowledge • Can deal with uncertainty Top 100 32
An Overview of Expert Systems: Characteristics and Limitations of an Expert System • Can explain its reasoning or suggested decisions • Can display “intelligent” behavior • Can draw conclusions from complex relationships • Can provide portable knowledge • Can deal with uncertainty Top 100 32
 Characteristics and Limitations of an Expert System (continued) • • • Not widely used or tested Difficult to use Limited to relatively narrow problems Cannot readily deal with “mixed” knowledge Possibility of error Cannot refine its own knowledge Difficult to maintain May have high development costs Raises legal and ethical concerns Top 100 33
Characteristics and Limitations of an Expert System (continued) • • • Not widely used or tested Difficult to use Limited to relatively narrow problems Cannot readily deal with “mixed” knowledge Possibility of error Cannot refine its own knowledge Difficult to maintain May have high development costs Raises legal and ethical concerns Top 100 33
 When to Use Expert Systems • Provide a high potential payoff or significantly reduce downside risk • Capture and preserve irreplaceable human expertise • Solve a problem that is not easily solved using traditional programming techniques • Develop a system more consistent than human experts Top 100 34
When to Use Expert Systems • Provide a high potential payoff or significantly reduce downside risk • Capture and preserve irreplaceable human expertise • Solve a problem that is not easily solved using traditional programming techniques • Develop a system more consistent than human experts Top 100 34
 When to Use Expert Systems (continued) • Provide expertise needed at a number of locations at the same time or in a hostile environment that is dangerous to human health • Provide expertise that is expensive or rare • Develop a solution faster than human experts can • Provide expertise needed for training and development to share the wisdom and experience of human experts with a large number of people Do you see a Top 100 potential problem here? 35
When to Use Expert Systems (continued) • Provide expertise needed at a number of locations at the same time or in a hostile environment that is dangerous to human health • Provide expertise that is expensive or rare • Develop a solution faster than human experts can • Provide expertise needed for training and development to share the wisdom and experience of human experts with a large number of people Do you see a Top 100 potential problem here? 35
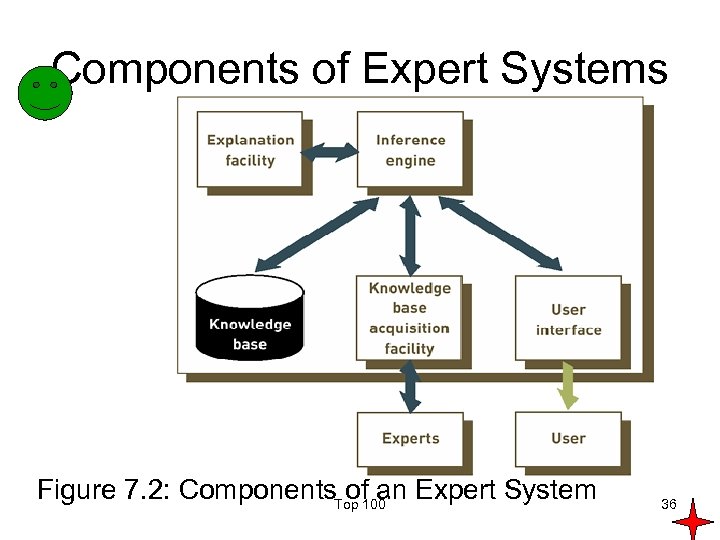 Components of Expert Systems Figure 7. 2: Components. Top 100 Expert System of an 36
Components of Expert Systems Figure 7. 2: Components. Top 100 Expert System of an 36
 The Explanation Facility • Allows a user or decision maker to understand how the expert system arrived at certain conclusions or results • For example: it allows a doctor to find out the logic or rationale of the diagnosis made by a medical expert system Top 100 37
The Explanation Facility • Allows a user or decision maker to understand how the expert system arrived at certain conclusions or results • For example: it allows a doctor to find out the logic or rationale of the diagnosis made by a medical expert system Top 100 37
 The Knowledge Acquisition Facility • Provides convenient and efficient means of capturing and storing all the components of the knowledge base • Acts as an interface between experts and the knowledge base Top 100 38
The Knowledge Acquisition Facility • Provides convenient and efficient means of capturing and storing all the components of the knowledge base • Acts as an interface between experts and the knowledge base Top 100 38
 Participants in Developing and Using Expert Systems • Domain expert: individual or group that has the expertise or knowledge one is trying to capture in the expert system • Knowledge engineer: an individual who has training or experience in the design, development, implementation, and maintenance of an expert system • Knowledge user: individual or group that uses and benefits from the expert system Top 100 39
Participants in Developing and Using Expert Systems • Domain expert: individual or group that has the expertise or knowledge one is trying to capture in the expert system • Knowledge engineer: an individual who has training or experience in the design, development, implementation, and maintenance of an expert system • Knowledge user: individual or group that uses and benefits from the expert system Top 100 39
 Applications of Expert Systems and Artificial Intelligence • • Credit granting and loan analysis Catching cheats and terrorists Information management and retrieval AI and expert systems embedded in products Plant layout and manufacturing Hospitals and medical facilities Help desks and assistance Employee performance evaluations Top 100 40
Applications of Expert Systems and Artificial Intelligence • • Credit granting and loan analysis Catching cheats and terrorists Information management and retrieval AI and expert systems embedded in products Plant layout and manufacturing Hospitals and medical facilities Help desks and assistance Employee performance evaluations Top 100 40
 What Is SUPPORTED? Tools for bringing things to conclusion • Managers are employed to create conclusions, to make things happen • Thus, any support they receive can be Tools for only of two types: helping others see that things happen or have happened – To make it easier to make – To make others think things have happened (i. e. , to increase the perception of things happening) Top 100 41
What Is SUPPORTED? Tools for bringing things to conclusion • Managers are employed to create conclusions, to make things happen • Thus, any support they receive can be Tools for only of two types: helping others see that things happen or have happened – To make it easier to make – To make others think things have happened (i. e. , to increase the perception of things happening) Top 100 41
 What Is a Conclusion? • • • A Decision Agreement or consensus Realization of a model or plan Addition to knowledge Increase in confidence Any (presumed positive) change in resources (such as cash, staff, customers, etc. ) Top 100 42
What Is a Conclusion? • • • A Decision Agreement or consensus Realization of a model or plan Addition to knowledge Increase in confidence Any (presumed positive) change in resources (such as cash, staff, customers, etc. ) Top 100 42
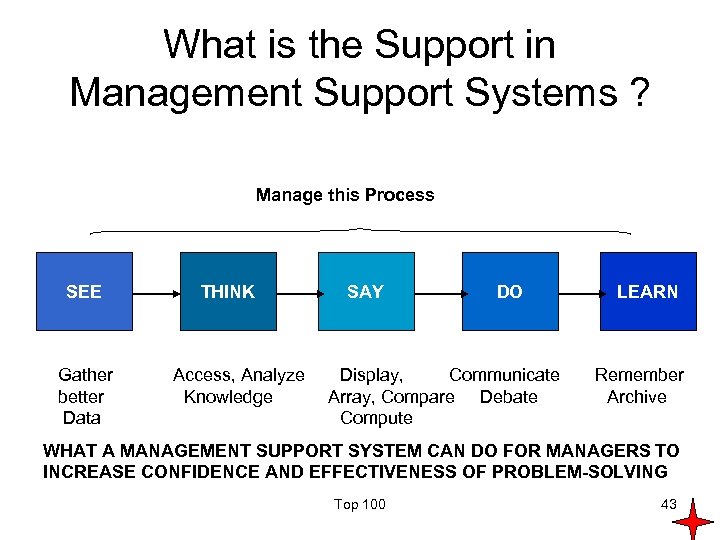 What is the Support in Management Support Systems ? Manage this Process SEE Gather better Data THINK Access, Analyze Knowledge SAY DO Display, Communicate Array, Compare Debate Compute LEARN Remember Archive WHAT A MANAGEMENT SUPPORT SYSTEM CAN DO FOR MANAGERS TO INCREASE CONFIDENCE AND EFFECTIVENESS OF PROBLEM-SOLVING Top 100 43
What is the Support in Management Support Systems ? Manage this Process SEE Gather better Data THINK Access, Analyze Knowledge SAY DO Display, Communicate Array, Compare Debate Compute LEARN Remember Archive WHAT A MANAGEMENT SUPPORT SYSTEM CAN DO FOR MANAGERS TO INCREASE CONFIDENCE AND EFFECTIVENESS OF PROBLEM-SOLVING Top 100 43
 What Kinds of Tools Are There • Display and Data Formatting (Presentation) • Data Search and Processing (MIS) • Suggested Action (Consulting) • Evaluation of Action (DSS) • Logical Conclusion (Expert System) • Action (Operational System) Top 100 44
What Kinds of Tools Are There • Display and Data Formatting (Presentation) • Data Search and Processing (MIS) • Suggested Action (Consulting) • Evaluation of Action (DSS) • Logical Conclusion (Expert System) • Action (Operational System) Top 100 44
 How These Tools Differ • Each one incorporates more “knowledge” than those above. • The value of the knowledge is higher and the knowledge is more specific. • Each removes some of the burden from the problem solver in generating and evaluating solutions Top 100 45
How These Tools Differ • Each one incorporates more “knowledge” than those above. • The value of the knowledge is higher and the knowledge is more specific. • Each removes some of the burden from the problem solver in generating and evaluating solutions Top 100 45
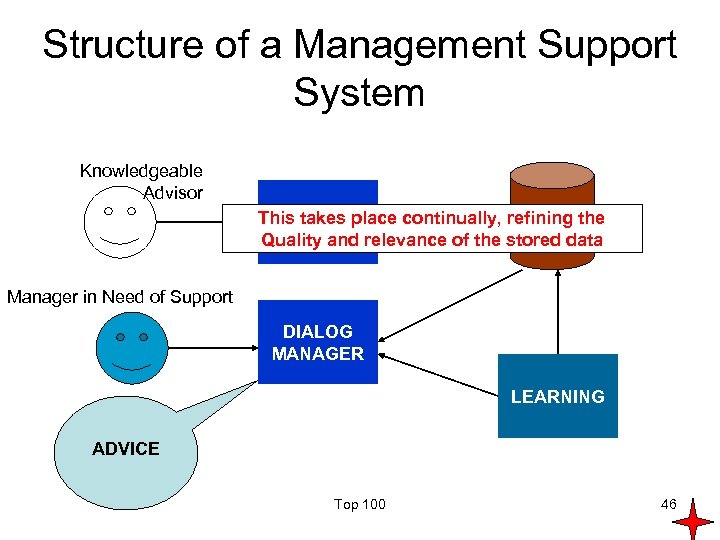 Structure of a Management Support System Knowledgeable Advisor MODEL This takes place continually, refining the CAPTURE BASE Quality and relevance of the stored data Manager in Need of Support DIALOG MANAGER LEARNING ADVICE Top 100 46
Structure of a Management Support System Knowledgeable Advisor MODEL This takes place continually, refining the CAPTURE BASE Quality and relevance of the stored data Manager in Need of Support DIALOG MANAGER LEARNING ADVICE Top 100 46
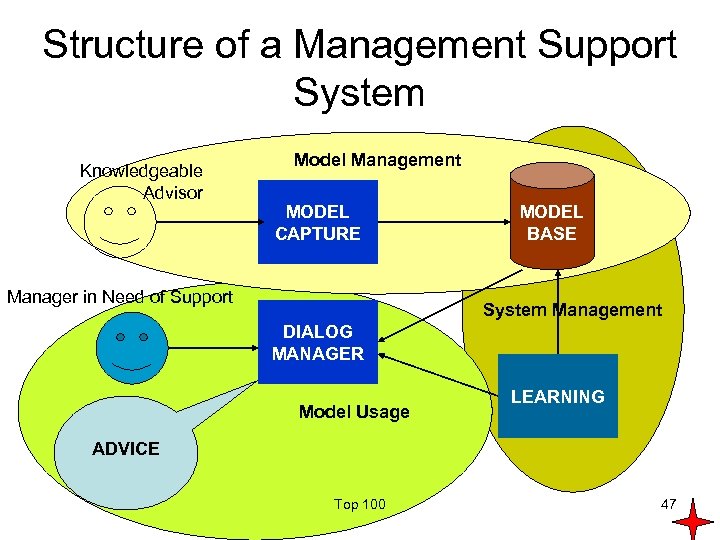 Structure of a Management Support System Knowledgeable Advisor Model Management MODEL CAPTURE Manager in Need of Support MODEL BASE System Management DIALOG MANAGER Model Usage LEARNING ADVICE Top 100 47
Structure of a Management Support System Knowledgeable Advisor Model Management MODEL CAPTURE Manager in Need of Support MODEL BASE System Management DIALOG MANAGER Model Usage LEARNING ADVICE Top 100 47
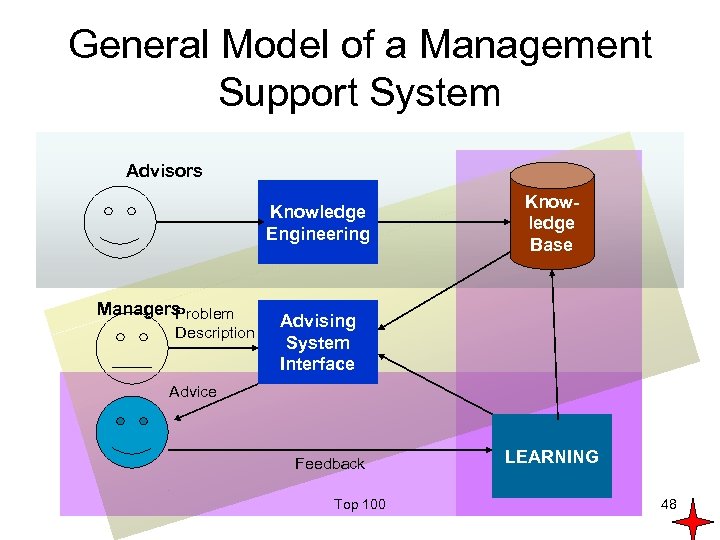 General Model of a Management Support System Advisors Knowledge Engineering Managers Problem Description Knowledge Base Advising System Interface Advice Feedback Top 100 LEARNING 48
General Model of a Management Support System Advisors Knowledge Engineering Managers Problem Description Knowledge Base Advising System Interface Advice Feedback Top 100 LEARNING 48
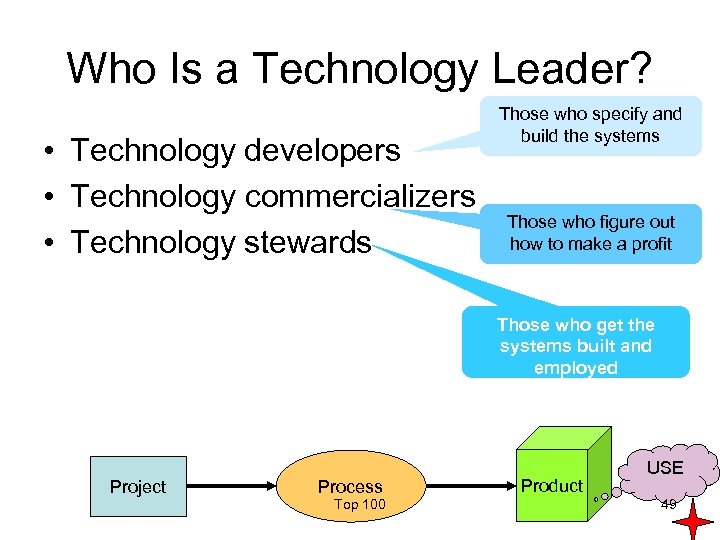 Who Is a Technology Leader? • Technology developers • Technology commercializers • Technology stewards Those who specify and build the systems Those who figure out how to make a profit Those who get the systems built and employed Project Process Top 100 Product USE 49
Who Is a Technology Leader? • Technology developers • Technology commercializers • Technology stewards Those who specify and build the systems Those who figure out how to make a profit Those who get the systems built and employed Project Process Top 100 Product USE 49
 Who Is a Technology Leader? • Technology stewards – User management – Project managers & clients – Process managers – Product owners Top 100 50
Who Is a Technology Leader? • Technology stewards – User management – Project managers & clients – Process managers – Product owners Top 100 50
 Technology Leadership • Three components: – – Assessment Forecasting Management Transfer • A technological leader fosters technological innovation, and understands the technology life cycle. • Such a leader initiates and steers commercialization of technological advances, links business and technology strategies, manages technology R&D and understands technological revolutions. Top 100 51
Technology Leadership • Three components: – – Assessment Forecasting Management Transfer • A technological leader fosters technological innovation, and understands the technology life cycle. • Such a leader initiates and steers commercialization of technological advances, links business and technology strategies, manages technology R&D and understands technological revolutions. Top 100 51
 Technology Management Components • Technology Assessment – Evaluating technologies as they are created – To make wise investments, understand the true costs, improve existing technologies, and develop ways of employing technologies • Technology Forecasting – Predicting what technologies are going to be available – To strategize technology use, second-guess the competition, stay on Top 100 of the technology wave top 52
Technology Management Components • Technology Assessment – Evaluating technologies as they are created – To make wise investments, understand the true costs, improve existing technologies, and develop ways of employing technologies • Technology Forecasting – Predicting what technologies are going to be available – To strategize technology use, second-guess the competition, stay on Top 100 of the technology wave top 52
 Technology Management Components • Technology Management – Developing and using appropriate technologies – To lead the technology, employ it in the best way, and to profit from technology use. • Technology Transfer – Helping others learn the benefits and uses of appropriate technologies – Making technologies available to others Top 100 53
Technology Management Components • Technology Management – Developing and using appropriate technologies – To lead the technology, employ it in the best way, and to profit from technology use. • Technology Transfer – Helping others learn the benefits and uses of appropriate technologies – Making technologies available to others Top 100 53
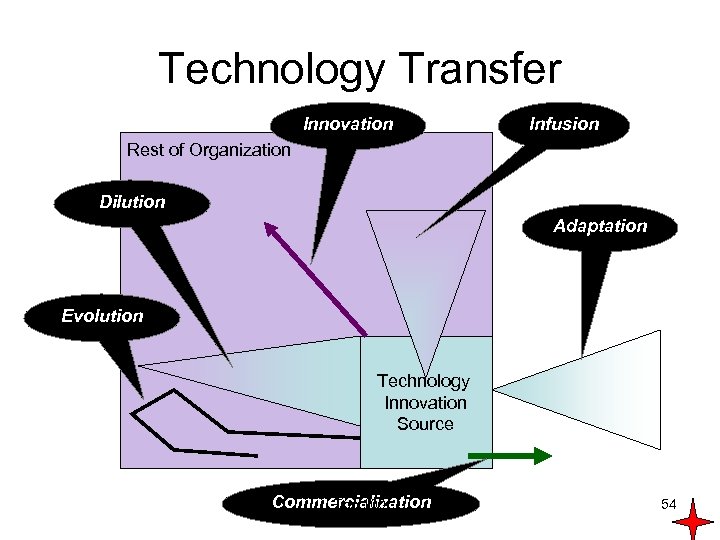 Technology Transfer Innovation Infusion Rest of Organization Dilution Adaptation Evolution Technology Innovation Source Commercialization Top 100 54
Technology Transfer Innovation Infusion Rest of Organization Dilution Adaptation Evolution Technology Innovation Source Commercialization Top 100 54
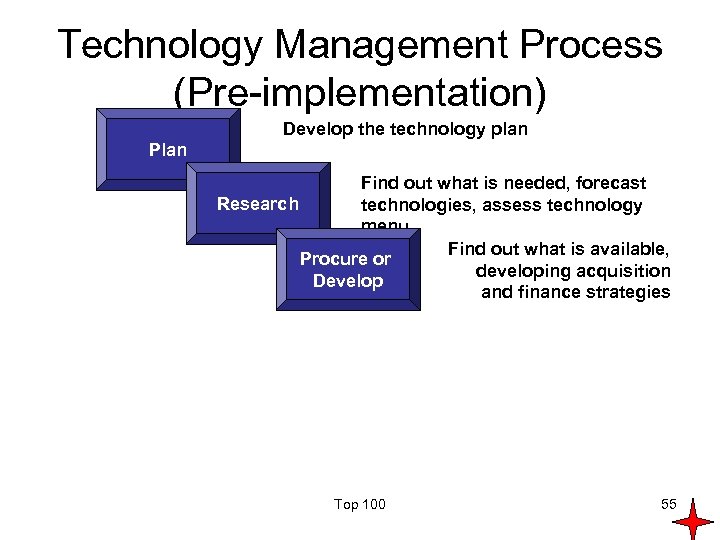 Technology Management Process (Pre-implementation) Develop the technology plan Plan Find out what is needed, forecast Research technologies, assess technology menu Find out what is available, Procure or developing acquisition Develop and finance strategies Top 100 55
Technology Management Process (Pre-implementation) Develop the technology plan Plan Find out what is needed, forecast Research technologies, assess technology menu Find out what is available, Procure or developing acquisition Develop and finance strategies Top 100 55
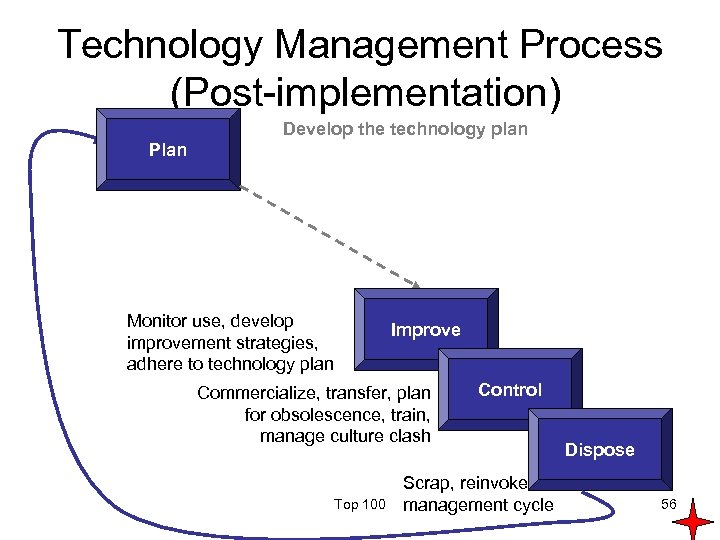 Technology Management Process (Post-implementation) Develop the technology plan Plan Monitor use, develop improvement strategies, adhere to technology plan Improve Commercialize, transfer, plan for obsolescence, train, manage culture clash Top 100 Control Scrap, reinvoke management cycle Dispose 56
Technology Management Process (Post-implementation) Develop the technology plan Plan Monitor use, develop improvement strategies, adhere to technology plan Improve Commercialize, transfer, plan for obsolescence, train, manage culture clash Top 100 Control Scrap, reinvoke management cycle Dispose 56
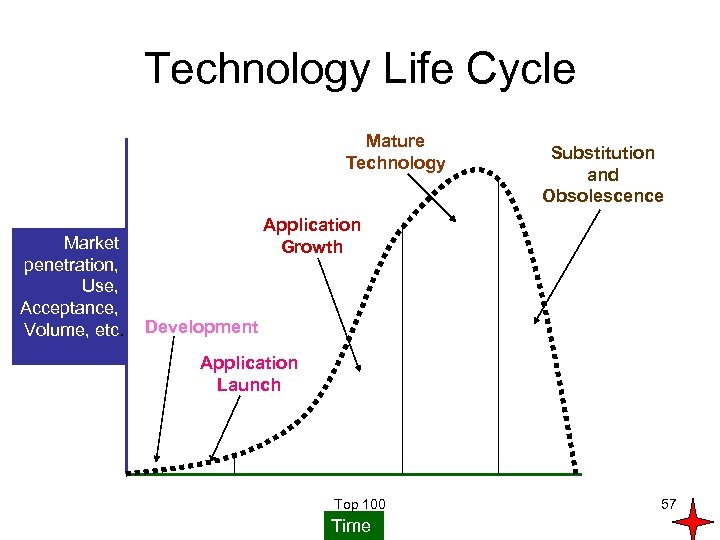 Technology Life Cycle Mature Technology Market penetration, Use, Acceptance, Volume, etc. Substitution and Obsolescence Application Growth Development Application Launch Top 100 Time 57
Technology Life Cycle Mature Technology Market penetration, Use, Acceptance, Volume, etc. Substitution and Obsolescence Application Growth Development Application Launch Top 100 Time 57
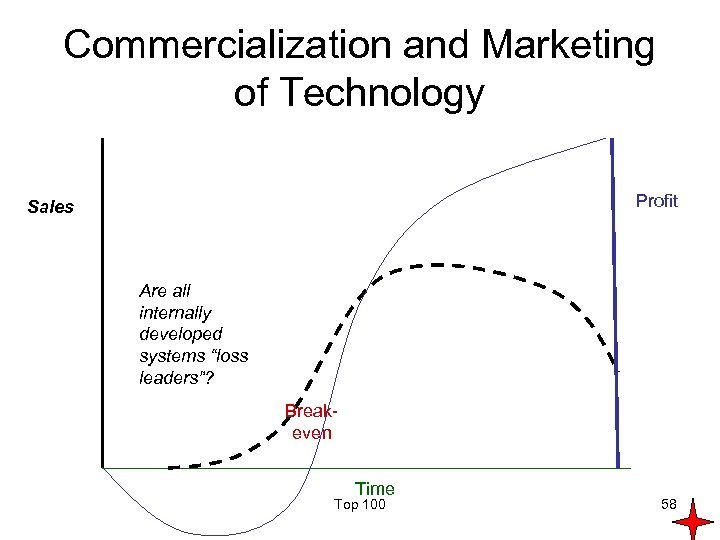 Commercialization and Marketing of Technology Profit Sales Are all internally developed systems “loss leaders”? Breakeven Time Top 100 58
Commercialization and Marketing of Technology Profit Sales Are all internally developed systems “loss leaders”? Breakeven Time Top 100 58
 An Overview of Systems Development: Participants in Systems Development • Development team – Responsible for determining the objectives of the information system and delivering a system that meets these objectives – Usually consists of stakeholders, users, managers, systems development specialists, and various support personnel Top 100 59
An Overview of Systems Development: Participants in Systems Development • Development team – Responsible for determining the objectives of the information system and delivering a system that meets these objectives – Usually consists of stakeholders, users, managers, systems development specialists, and various support personnel Top 100 59
 Systems Development Methods • The systems development process is also called a systems development life cycle (SDLC) • Traditional systems development life cycle • Prototyping • Rapid application development (RAD) • End-user development Top 100 60
Systems Development Methods • The systems development process is also called a systems development life cycle (SDLC) • Traditional systems development life cycle • Prototyping • Rapid application development (RAD) • End-user development Top 100 60
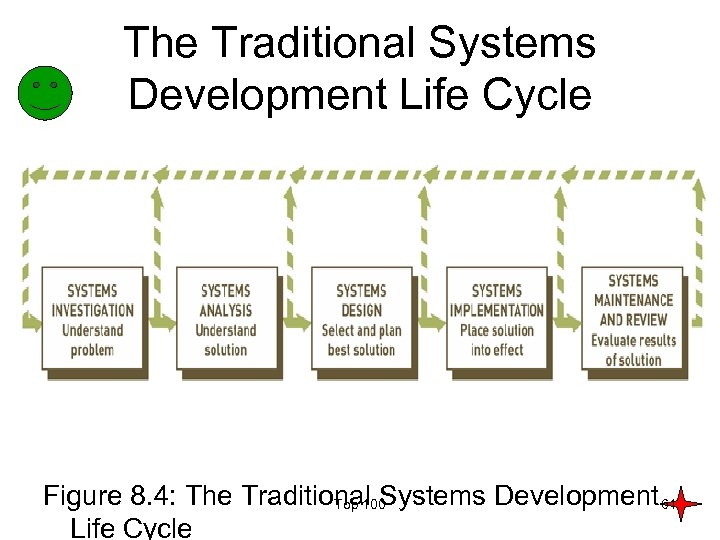 The Traditional Systems Development Life Cycle Figure 8. 4: The Traditional Systems Development 61 Top 100 Life Cycle
The Traditional Systems Development Life Cycle Figure 8. 4: The Traditional Systems Development 61 Top 100 Life Cycle
 The Traditional Systems Development Life Cycle (continued) • Systems investigation: problems and opportunities are identified and considered in light of the goals of the business • Systems analysis: study of existing systems and work processes to identify strengths, weaknesses, and opportunities for improvement • Systems design: defines how. These two at the often take place information system will do what same time. do it must Top 100 62 to obtain the problem’s solution
The Traditional Systems Development Life Cycle (continued) • Systems investigation: problems and opportunities are identified and considered in light of the goals of the business • Systems analysis: study of existing systems and work processes to identify strengths, weaknesses, and opportunities for improvement • Systems design: defines how. These two at the often take place information system will do what same time. do it must Top 100 62 to obtain the problem’s solution
 The Traditional Systems Development Life Cycle (continued) • Systems implementation: the creation or acquiring of various system components detailed in the systems design, assembling them, and placing the new or modified system into operation • Systems maintenance and review: ensures that the system operates, and modifies the system so that it continues to meet changing business needs Top 100 63
The Traditional Systems Development Life Cycle (continued) • Systems implementation: the creation or acquiring of various system components detailed in the systems design, assembling them, and placing the new or modified system into operation • Systems maintenance and review: ensures that the system operates, and modifies the system so that it continues to meet changing business needs Top 100 63
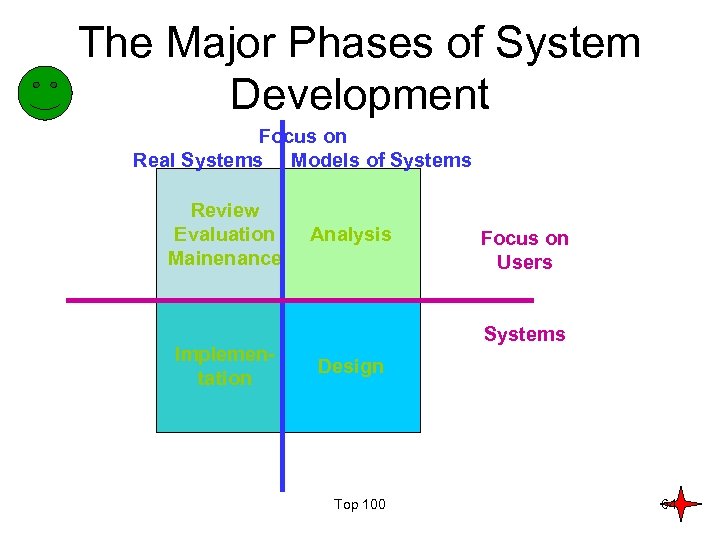 The Major Phases of System Development Focus on Real Systems Models of Systems Review Evaluation Mainenance Implementation Analysis Focus on Users Systems Design Top 100 64
The Major Phases of System Development Focus on Real Systems Models of Systems Review Evaluation Mainenance Implementation Analysis Focus on Users Systems Design Top 100 64
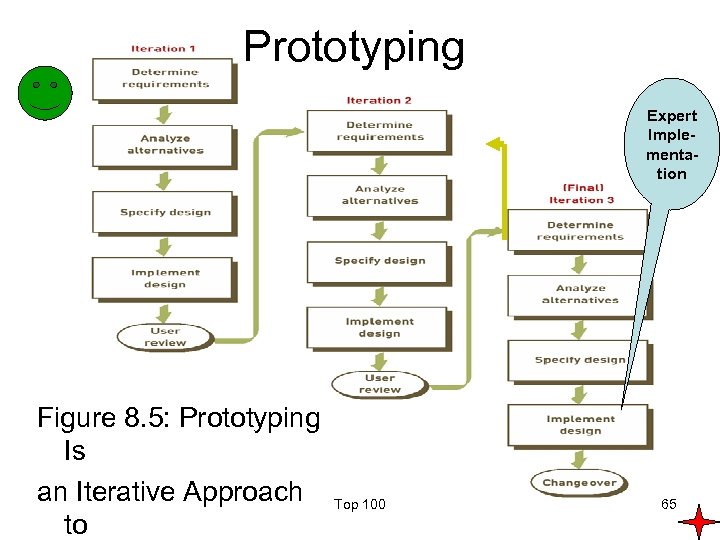 Prototyping Expert Implementation Figure 8. 5: Prototyping Is an Iterative Approach to Top 100 65
Prototyping Expert Implementation Figure 8. 5: Prototyping Is an Iterative Approach to Top 100 65
 The End-User Systems Development Life Cycle • Any systems development project in which the primary effort is undertaken by a combination of business managers and users • End-user-developed systems can be structured as complementary to, rather than in conflict with, existing and emerging information systems Top 100 66
The End-User Systems Development Life Cycle • Any systems development project in which the primary effort is undertaken by a combination of business managers and users • End-user-developed systems can be structured as complementary to, rather than in conflict with, existing and emerging information systems Top 100 66
 Outsourcing and On Demand Computing • An outside consulting firm or computer company that specializes in systems development can be hired to take over some or all of the development and operations activities • Outsourcing can involve a large number of countries and companies in bringing new products and services to market Top 100 67
Outsourcing and On Demand Computing • An outside consulting firm or computer company that specializes in systems development can be hired to take over some or all of the development and operations activities • Outsourcing can involve a large number of countries and companies in bringing new products and services to market Top 100 67
 Systems Investigation • What primary problems might a new or enhanced system solve? • What opportunities might a new or enhanced system provide? • What new hardware, software, databases, telecommunications, personnel, or procedures will improve an existing system or are required in a new system? • What are the potential costs (variable and fixed)? • What are the associated risks? Top 100 68
Systems Investigation • What primary problems might a new or enhanced system solve? • What opportunities might a new or enhanced system provide? • What new hardware, software, databases, telecommunications, personnel, or procedures will improve an existing system or are required in a new system? • What are the potential costs (variable and fixed)? • What are the associated risks? Top 100 68
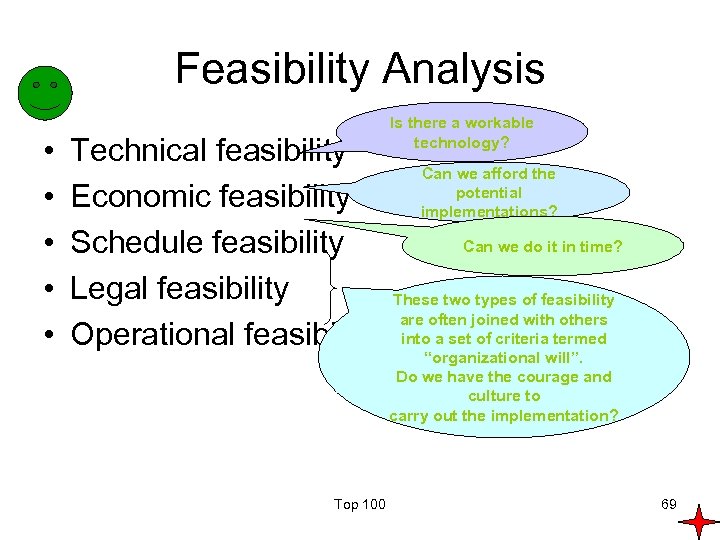 Feasibility Analysis • • • Technical feasibility Economic feasibility Schedule feasibility Legal feasibility Operational feasibility Top 100 Is there a workable technology? Can we afford the potential implementations? Can we do it in time? These two types of feasibility are often joined with others into a set of criteria termed “organizational will”. Do we have the courage and culture to carry out the implementation? 69
Feasibility Analysis • • • Technical feasibility Economic feasibility Schedule feasibility Legal feasibility Operational feasibility Top 100 Is there a workable technology? Can we afford the potential implementations? Can we do it in time? These two types of feasibility are often joined with others into a set of criteria termed “organizational will”. Do we have the courage and culture to carry out the implementation? 69
 The Systems Investigation Report • Summarizes the results of systems investigation and the process of feasibility analysis • Recommends a course of action: continue on into systems analysis, modify the project in some manner, or drop it Top 100 70
The Systems Investigation Report • Summarizes the results of systems investigation and the process of feasibility analysis • Recommends a course of action: continue on into systems analysis, modify the project in some manner, or drop it Top 100 70
 Systems Analysis • Answers the question “What must the information system do to solve the problem? ” • Primary outcome: a prioritized list of system requirements Top 100 71
Systems Analysis • Answers the question “What must the information system do to solve the problem? ” • Primary outcome: a prioritized list of system requirements Top 100 71
 Data Analysis • A set of diagramming techniques • Data modeling – Entity-relationship (ER) diagrams – Relatively easy to understand; a narrative of what entities (actors, objects) produce or use what information • Activity modeling – Data-flow diagrams (DFDs) – Conceptual, intuitive, should be shared with potential users for verification Top 100 72
Data Analysis • A set of diagramming techniques • Data modeling – Entity-relationship (ER) diagrams – Relatively easy to understand; a narrative of what entities (actors, objects) produce or use what information • Activity modeling – Data-flow diagrams (DFDs) – Conceptual, intuitive, should be shared with potential users for verification Top 100 72
 The Systems Analysis Report • The systems analysis report should cover: – The strengths and weaknesses of the existing system from a stakeholder’s perspective – The user/stakeholder requirements for the new system (also called the functional requirements) – The organizational requirements for the new system – A description of what the new information system should do to solve the problem Top 100 73
The Systems Analysis Report • The systems analysis report should cover: – The strengths and weaknesses of the existing system from a stakeholder’s perspective – The user/stakeholder requirements for the new system (also called the functional requirements) – The organizational requirements for the new system – A description of what the new information system should do to solve the problem Top 100 73
 Systems Design • Answers the question “How will the information system do what it must do to solve a problem? ” • Has two dimensions: logical and physical • Logical design: description of the functional requirements of a system: a model of the user • Physical design: specification of the characteristics of the system components necessary to put the logical design into action: a model of the system Top 100 74
Systems Design • Answers the question “How will the information system do what it must do to solve a problem? ” • Has two dimensions: logical and physical • Logical design: description of the functional requirements of a system: a model of the user • Physical design: specification of the characteristics of the system components necessary to put the logical design into action: a model of the system Top 100 74
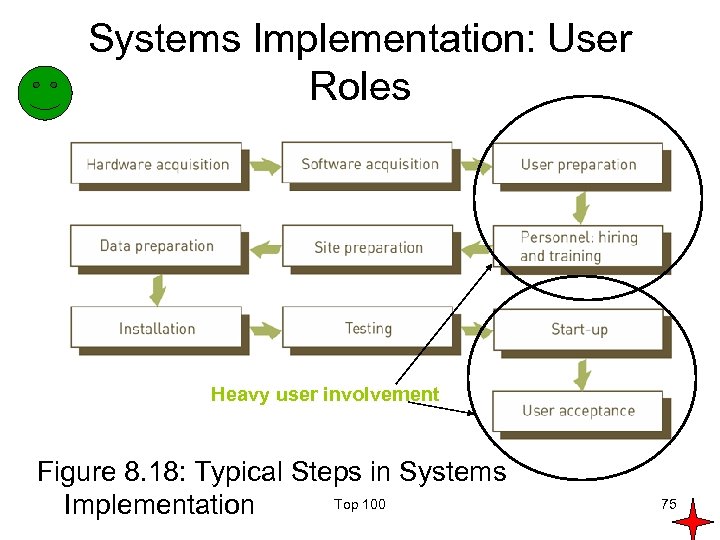 Systems Implementation: User Roles Heavy user involvement Figure 8. 18: Typical Steps in Systems Top 100 Implementation 75
Systems Implementation: User Roles Heavy user involvement Figure 8. 18: Typical Steps in Systems Top 100 Implementation 75
 Personnel: Hiring and Training • • • IS manager Systems analysts Computer programmers Data-entry operators Hiring users: describe the job; match the skills • Users may take up to three months to learn the new jobs. Top 100 76
Personnel: Hiring and Training • • • IS manager Systems analysts Computer programmers Data-entry operators Hiring users: describe the job; match the skills • Users may take up to three months to learn the new jobs. Top 100 76
 Data Preparation • Also called data conversion • Ensuring all files and databases are ready to be used with new computer software and systems • With mission-critical data, generally a really expensive proposition Top 100 77
Data Preparation • Also called data conversion • Ensuring all files and databases are ready to be used with new computer software and systems • With mission-critical data, generally a really expensive proposition Top 100 77
 Testing • Unit testing: testing of individual programs • System testing: testing the entire system of programs • Volume testing: testing the application with a large amount of data • Integration testing: testing all related systems together • Acceptance testing: conducting any tests required by Top 100 user the 78
Testing • Unit testing: testing of individual programs • System testing: testing the entire system of programs • Volume testing: testing the application with a large amount of data • Integration testing: testing all related systems together • Acceptance testing: conducting any tests required by Top 100 user the 78
 Installation • The process of physically placing the computer equipment on the site and making it operational • Normally the manufacturer is responsible for installing computer equipment • Someone from the organization (usually the IS manager) should oversee the process Top 100 79
Installation • The process of physically placing the computer equipment on the site and making it operational • Normally the manufacturer is responsible for installing computer equipment • Someone from the organization (usually the IS manager) should oversee the process Top 100 79
 Start-Up • The process of making the final tested information system fully operational • Direct conversion (also called plunge or direct cutover – “Black Monday” effect) • Phase-in approach (function by function; perhaps department by department) • Pilot start-up (a test area, function or department) • Parallel start-up (where mission critical information is required or involved, where Top 100 absolutely reliable service is needed) 80
Start-Up • The process of making the final tested information system fully operational • Direct conversion (also called plunge or direct cutover – “Black Monday” effect) • Phase-in approach (function by function; perhaps department by department) • Pilot start-up (a test area, function or department) • Parallel start-up (where mission critical information is required or involved, where Top 100 absolutely reliable service is needed) 80
 User Acceptance • User-acceptance document: formal agreement signed by the user that states that a phase of the installation or the complete system is approved Top 100 81
User Acceptance • User-acceptance document: formal agreement signed by the user that states that a phase of the installation or the complete system is approved Top 100 81
 Systems Operation and Maintenance • Systems operation: use of a new or modified system • Systems maintenance: checking, changing, and enhancing the system to make it more useful in achieving user and organizational goals Top 100 82
Systems Operation and Maintenance • Systems operation: use of a new or modified system • Systems maintenance: checking, changing, and enhancing the system to make it more useful in achieving user and organizational goals Top 100 82
 Systems Review • Process of analyzing systems to make sure that they are operating as intended • Often compares the performance and benefits of the system as it was designed with the actual performance and benefits of the system in operation • Event-driven review: review triggered by a problem or opportunity, such as an error, a corporate merger, or a new market for products • Time-driven review: review performed after a Top 100 83 specified amount of time
Systems Review • Process of analyzing systems to make sure that they are operating as intended • Often compares the performance and benefits of the system as it was designed with the actual performance and benefits of the system in operation • Event-driven review: review triggered by a problem or opportunity, such as an error, a corporate merger, or a new market for products • Time-driven review: review performed after a Top 100 83 specified amount of time
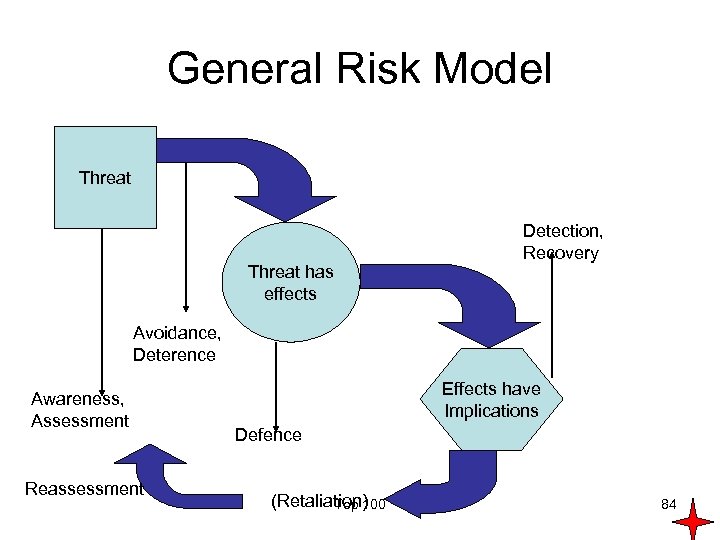 General Risk Model Threat has effects Detection, Recovery Avoidance, Deterence Awareness, Assessment Reassessment Effects have Implications Defence (Retaliation) Top 100 84
General Risk Model Threat has effects Detection, Recovery Avoidance, Deterence Awareness, Assessment Reassessment Effects have Implications Defence (Retaliation) Top 100 84
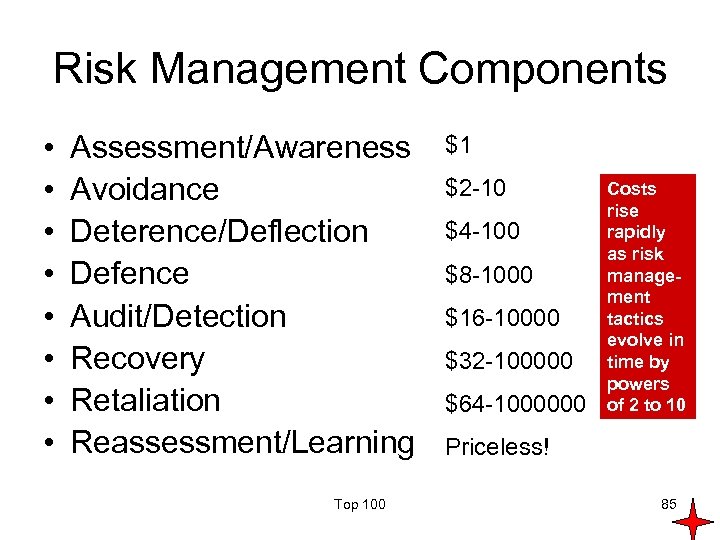 Risk Management Components • • Assessment/Awareness Avoidance Deterence/Deflection Defence Audit/Detection Recovery Retaliation Reassessment/Learning Top 100 $1 $2 -10 $4 -100 $8 -1000 $16 -10000 $32 -100000 $64 -1000000 Costs rise rapidly as risk management tactics evolve in time by powers of 2 to 10 Priceless! 85
Risk Management Components • • Assessment/Awareness Avoidance Deterence/Deflection Defence Audit/Detection Recovery Retaliation Reassessment/Learning Top 100 $1 $2 -10 $4 -100 $8 -1000 $16 -10000 $32 -100000 $64 -1000000 Costs rise rapidly as risk management tactics evolve in time by powers of 2 to 10 Priceless! 85
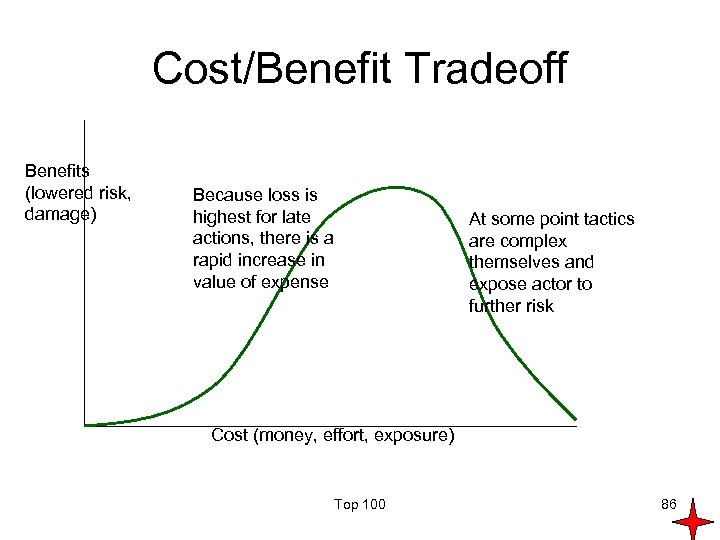 Cost/Benefit Tradeoff Benefits (lowered risk, damage) Because loss is highest for late actions, there is a rapid increase in value of expense At some point tactics are complex themselves and expose actor to further risk Cost (money, effort, exposure) Top 100 86
Cost/Benefit Tradeoff Benefits (lowered risk, damage) Because loss is highest for late actions, there is a rapid increase in value of expense At some point tactics are complex themselves and expose actor to further risk Cost (money, effort, exposure) Top 100 86
 Computer Waste and Mistakes • Computer waste – The inappropriate use of computer technology and resources • Computer-related mistakes – Errors, failures, and other computer problems that make computer output incorrect or not useful Top 100 87
Computer Waste and Mistakes • Computer waste – The inappropriate use of computer technology and resources • Computer-related mistakes – Errors, failures, and other computer problems that make computer output incorrect or not useful Top 100 87
 Computer Waste • Discarding of technology • Unused systems • Personal use of corporate time and technology • Spam • Poorly designed systems • Unintelligent system use Top 100 88
Computer Waste • Discarding of technology • Unused systems • Personal use of corporate time and technology • Spam • Poorly designed systems • Unintelligent system use Top 100 88
 Computer-Related Mistakes • Mistakes can be caused by unclear expectations and a lack of feedback • A systems analyst might specify a system that is not what is needed or wanted • A programmer might develop a program that contains errors • Users might accept a system that is not what is needed or what is wanted • A data-entry clerk might enter the wrong 89 Top 100 data
Computer-Related Mistakes • Mistakes can be caused by unclear expectations and a lack of feedback • A systems analyst might specify a system that is not what is needed or wanted • A programmer might develop a program that contains errors • Users might accept a system that is not what is needed or what is wanted • A data-entry clerk might enter the wrong 89 Top 100 data
 Computer Crime • Often defies detection • The amount stolen or diverted can be substantial • The crime is “clean” and nonviolent (so far!) • The number of IT-related security incidents is increasing dramatically • Computer crime is now global Top 100 90
Computer Crime • Often defies detection • The amount stolen or diverted can be substantial • The crime is “clean” and nonviolent (so far!) • The number of IT-related security incidents is increasing dramatically • Computer crime is now global Top 100 90
 The Computer as a Tool to Commit Crime • Criminals need two capabilities to commit most computer crimes: – Knowing how to gain access to the computer system – Knowing how to manipulate the system to produce the desired result • Social engineering • Dumpster diving Top 100 91
The Computer as a Tool to Commit Crime • Criminals need two capabilities to commit most computer crimes: – Knowing how to gain access to the computer system – Knowing how to manipulate the system to produce the desired result • Social engineering • Dumpster diving Top 100 91
 Identity Theft • An imposter obtains key pieces of personal identification information, such as Social Security or driver’s license numbers, in order to impersonate someone else • The information is then used to obtain credit, merchandise, and services in the name of the victim or to provide thief with false credentials • Identity Theft and Assumption Deterrence Act of 1998 Top 100 92
Identity Theft • An imposter obtains key pieces of personal identification information, such as Social Security or driver’s license numbers, in order to impersonate someone else • The information is then used to obtain credit, merchandise, and services in the name of the victim or to provide thief with false credentials • Identity Theft and Assumption Deterrence Act of 1998 Top 100 92
 Data Alteration and Destruction • Virus: a computer program capable of attaching to disks or other files and replicating itself repeatedly, typically without the user’s knowledge or permission • Worm: an independent program that replicates its own program files until it interrupts the operation of networks and computer systems Top 100 93
Data Alteration and Destruction • Virus: a computer program capable of attaching to disks or other files and replicating itself repeatedly, typically without the user’s knowledge or permission • Worm: an independent program that replicates its own program files until it interrupts the operation of networks and computer systems Top 100 93
 Data Alteration and Destruction – 2 • Trojan horse: a program that appears to be useful but actually masks a destructive program • Logic bomb: an application or system virus designed to “explode” or execute at a specified time and date Top 100 94
Data Alteration and Destruction – 2 • Trojan horse: a program that appears to be useful but actually masks a destructive program • Logic bomb: an application or system virus designed to “explode” or execute at a specified time and date Top 100 94
 Using Antivirus Programs • Antivirus program: program or utility that prevents viruses and recovers from them if they infect a computer • An antivirus software should be run and updated often Top 100 95
Using Antivirus Programs • Antivirus program: program or utility that prevents viruses and recovers from them if they infect a computer • An antivirus software should be run and updated often Top 100 95
 Privacy Issues • With information systems, privacy deals with the collection and use or misuse of data • Privacy and the federal government • Privacy at work: you don’t have any • E-mail privacy: doesn’t exist • Privacy and the Internet: caveat emptor Top 100 96
Privacy Issues • With information systems, privacy deals with the collection and use or misuse of data • Privacy and the federal government • Privacy at work: you don’t have any • E-mail privacy: doesn’t exist • Privacy and the Internet: caveat emptor Top 100 96
 Privacy: The Basic Issue • Information about the individual may or may not “belong” to the individual as “property” • English common law, the basis of our general law, recognizes property rights as inherent and inviolable (in general) • Intellectual assets differ in many ways from physical property – Eg. Copyable without damage – Eg. Valuable only for brief period of time – Eg. Can cause damage as well as be an asset Top 100 97
Privacy: The Basic Issue • Information about the individual may or may not “belong” to the individual as “property” • English common law, the basis of our general law, recognizes property rights as inherent and inviolable (in general) • Intellectual assets differ in many ways from physical property – Eg. Copyable without damage – Eg. Valuable only for brief period of time – Eg. Can cause damage as well as be an asset Top 100 97
 Information about Oneself • • • In general this does NOT belong to the individual Example: “public figure” Example: customer records Example: Employee records Example: One’s image (visual or audio) Information in general is inherent in an activity and belongs to that activity; the owner of the activity is the owner of the information. • This is not a well-developed field with clear-cut principles that juries and judges adhere to. Top 100 98
Information about Oneself • • • In general this does NOT belong to the individual Example: “public figure” Example: customer records Example: Employee records Example: One’s image (visual or audio) Information in general is inherent in an activity and belongs to that activity; the owner of the activity is the owner of the information. • This is not a well-developed field with clear-cut principles that juries and judges adhere to. Top 100 98
 Corporate Privacy Policies • Should address a customer’s knowledge, control, notice, and consent over the storage and use of information • May cover who has access to private data and when it may be used • A good database design practice is to assign a single unique identifier to each customer Top 100 99
Corporate Privacy Policies • Should address a customer’s knowledge, control, notice, and consent over the storage and use of information • May cover who has access to private data and when it may be used • A good database design practice is to assign a single unique identifier to each customer Top 100 99
 Individual Efforts to Protect Privacy • Find out what is stored about you in existing databases • Be careful when you share information about yourself • Be proactive to protect your privacy • When purchasing anything from a Web site, make sure that you safeguard your credit card numbers, passwords, and personal information Top 100
Individual Efforts to Protect Privacy • Find out what is stored about you in existing databases • Be careful when you share information about yourself • Be proactive to protect your privacy • When purchasing anything from a Web site, make sure that you safeguard your credit card numbers, passwords, and personal information Top 100
 Foreign Language Guide Book What you want to express What to say in ITish • “It’s cute but it doesn’t do what it’s supposed to do. ” • “I know YOU think it’s great technology, but it doesn’t meet my needs. ” • “Wow! This is really going to make me look good on the job!” • “IT DOESN’T WORK!” • “I DON’T WANT IT!” • “THANKS!” Top 100 101
Foreign Language Guide Book What you want to express What to say in ITish • “It’s cute but it doesn’t do what it’s supposed to do. ” • “I know YOU think it’s great technology, but it doesn’t meet my needs. ” • “Wow! This is really going to make me look good on the job!” • “IT DOESN’T WORK!” • “I DON’T WANT IT!” • “THANKS!” Top 100 101


