5cfad4c31cb5c26f906f2631cfeddd43.ppt
- Количество слайдов: 44

Military Threat Model and Cryptographic Response MK-128 February 2009 Mike Kurdziel Ph. D michael. kurdziel@harris. com RIT 1 assuredcommunications™ d-MMM-y
Overview • Background • Threat modeling – Definition – Example threat models – Government/military COMSEC threat model • Military and government baseline requirements – Maxims of military cryptography – Design objectives – Design requirements • MK-128 algorithm design • Citadel. TM device overview Citadel® Product Brief 2 assuredcommunications™

Background • USG allows export of high grade crypto when in the national interest – U. S. Executive Order E. O. 13026, November 1996 – U. S. Encryption Policy Update, January 2002 • Changes in military & government threat requires a new solution – Cold war threat is gone – Terrorist threat requires coalition response – Interoperability and exportability gain importance Citadel® Product Brief 3 assuredcommunications™

Threat Modeling RIT 4 assuredcommunications™ d-MMM-y
Threat Modeling “Threat Modeling attempts to model the thought processes of an adversary who is attempting to achieve a set of goals with respect to a defined system” [15] – In our case, a tactical radio network – Looking at the system from the adversary’s perspective Citadel® Product Brief 5 assuredcommunications™
Threat Model – Definition • Adversary’s capabilities – Expertise – Funding – Other resources • i. e. Computing power, system data, analysis data • Potentially vulnerable system components or entry points – Communication channel – Physical security – User errors and compromises • Target or Objectives – Asset of value – Adversary’s motivation • Advantage to the adversary – Provides input to the Threat Profile Citadel® Product Brief 6 assuredcommunications™
Methodology • Develop Threat Model → Develop Threat Profile → Indentify vulnerabilities → Construct Threat Tree → Conduct Penetration Tests • Prioritize vulnerabilities → Close vulnerabilities Citadel® Product Brief 7 assuredcommunications™
Example Communications Threat Models • Personal – Consumer products – Internet applications • Industrial – Communication equipment – Computer networks – Company Archives • Government/military – – – Communication equipment Computer networks C 3 systems Access systems Classified storage Citadel® Product Brief 8 assuredcommunications™

Personal Threat Model • Adversary characterization – Criminal intent on theft • Basic skills, resources & funding – Target value restricts sophistication of attacks • Vulnerable components – Service providers – Physical security of equipment – User errors • Target – Data with monetary value • Credit card numbers, bank account numbers, etc. • Low relative value Citadel® Product Brief 9 assuredcommunications™

Industrial Threat Model • Adversary characterization – Criminal intent on large gain theft – Hacker is also possible • Vulnerable components – – Service providers Physical security of equipment Broad access User errors • Target – Data with significant monetary value • i. e. Intellectual property, proprietary data, business plans, etc. ; Info with higher relative value • Visibility, attention, etc. Citadel® Product Brief 10 assuredcommunications™

Government/Military Threat Model • Adversary characterization – National intelligence agency level threat • World class skills • Leading edge cryptanalysis expertise which exceeds the public sector – Funding • Monetary resources of a government • High impact strategic advantage investment – Computing resources • World class general computing and custom hardware resources • NSA stated goal to lead public sector by 5 years Citadel® Product Brief 11 assuredcommunications™

Government/Military Threat Model • Vulnerable components – Channel • Adversary has direct access to wireless comms channels • High quality crypto is only way to secure channel – Equipment less vulnerable • Designed to be fail safe – Users less likely to introduce errors • Background investigations common, malicious intent less likely • Personnel trained in secure military communications Citadel® Product Brief 12 assuredcommunications™

Government/Military Threat Model • Target – Strategic and tactical military data – Classified government/military info – Diplomatic communication – Census data – Anything that provides a strategic or tactical advantage • Value often can not be assessed by the adversary until after a full compromise • All information is a potential target Citadel® Product Brief 13 assuredcommunications™

Military & Government Baseline Requirements RIT 14 assuredcommunications™ d-MMM-y

Maxims Of Military Cryptography • Never underrate the adversary • Cryptographic user faults and other infringements of security discipline need to be taken into account when assessing strength • Expert knowledge in cryptanalysis required for design and analysis – Considered essential by all credible experts – Can not rely on key length as security metric – Only a cryptanalyst, if anybody, can judge the security of a crypto system Citadel® Product Brief 15 assuredcommunications™

Maxims Of Military Cryptography • Security can not depend on non-disclosure – Assume “adversary knows the system being used” – Assume this adversary has superior resources (equipment, data, skill and funding) • Not in the public domain – Controversial point – Prevents proliferation from increasing the target value – Prevents cryptanalysis developments from being researched and published – National algorithms or properly customized algorithms are desirable Citadel® Product Brief 16 assuredcommunications™

Maxims Of Military Cryptography • No compromise to objective of high cryptographic strength – No engineering tradeoffs for gate count, power, speed, cost, etc. • Solution must be designed with no observable weaknesses - even if a method does not exist to exploit them – No vulnerabilities to known cryptanalysis techniques – No sensitive information can exit device through “side channels” • No non-random patterns in CT stream • No extraneous signals correlated with sensitive data – i. e. Current draw or processing delay Citadel® Product Brief 17 assuredcommunications™

Maxims Of Military Cryptography • Cryptographic strength must be re-evaluated periodically in light of technology and cryptanalysis technique developments • Superficial complications can be illusory and provide the cryptographer with a false sense of security – Avoid them Citadel® Product Brief 18 assuredcommunications™

Design Objectives • Algorithm should be customizable – Security Autonomy • Straight forward to describe, evaluate, design – Readily available and recognized reference material – Understandable design structures • Designed to withstand an expertly executed brute force attack – Adversary has world class computing power • NSA, “Our goal is to maintain a 5 year lead on industry” • Simple case study given in [11] Citadel® Product Brief 19 assuredcommunications™

Design Objectives – Algorithm rendered in hardware and specifically designed to execute slowly in software • Increases the cost of the attack • Goal is to force the requirement for custom hardware • Also prevents a replacement attack – Algorithm design should include computationally expensive operations • Large I/O and irreducible operations • Non-linear operations • Operations that are complicated in software, but trivial in hardware (i. e. bit swapping) – Other recommendations • Use key scheduler designs that add key load latency – Increases key test time with custom hardware Citadel® Product Brief 20 assuredcommunications™
Design Objectives – Minimum key length of 115 bits (algorithm fielded in the year 2002) [2] • Need 50 years of security, – 20 years of fielded service and 30 years of legacy • Analysis uses very conservative 50 year projections of general purpose computing power and custom hardware performance • Always include at least an order of magnitude of margin Citadel® Product Brief 21 assuredcommunications™
Design Requirements • • Prefer Block algorithm structure, Non-iterative Optimized substitution Expansion operation Secure key schedule – – No weak keys No complementation property Non-linear Complex Citadel® Product Brief 22 assuredcommunications™
Design Requirements • • Mixed mode arithmetic Non-linear operation(s) Entropy preserving operation(s) Irreducible operations with large I/O Non-iterative structure Non-invertable operation(s) Uniformly distributed output Citadel® Product Brief 23 assuredcommunications™
MK-128 Algorithm Design These items/technical data are controlled by the US Department of State, International Traffic in Arms Regulations (ITAR) 22 CFR Parts 120 -130 and cannot be exported from the United States or shared with a Non-US Citizen without prior approval from the United States Government. RIT 24 assuredcommunications™ d-MMM-y

Design Approach • “Secure by design” philosophy – No such thing as theoretically secure for a practical system • Identify and design against benchmark analysis techniques • Learn from others strengths and vulnerabilities • Goal: security in the knowledge of the key Citadel® Product Brief 25 assuredcommunications™
Design Approach • Benchmark techniques – Differential cryptanalysis – Linear cryptanalysis – “One-off” analysis – Statistical testing Citadel® Product Brief 26 assuredcommunications™
Design Approach • Learn from strengths and vulnerabilities of other algorithms – Strong Algorithms • IDEA • SAFER • Triple DES • LOKI 91 • GOST • MMB • BLOWFISH • 3 -WAY • RC 5 • AES • Serpent Citadel® Product Brief 27 – Weak Algorithms • DES • RC 4 • LUCIFER • MADRYGA • NEWDES • FEAL • LOKI 89 assuredcommunications™
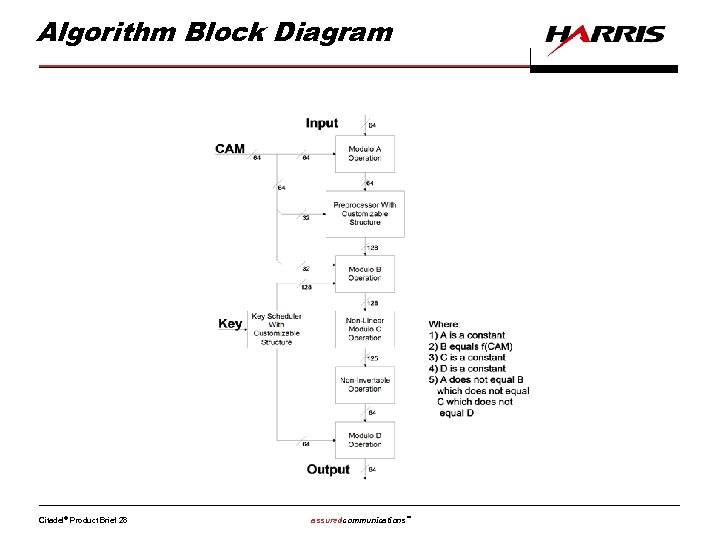
Algorithm Block Diagram Citadel® Product Brief 28 assuredcommunications™
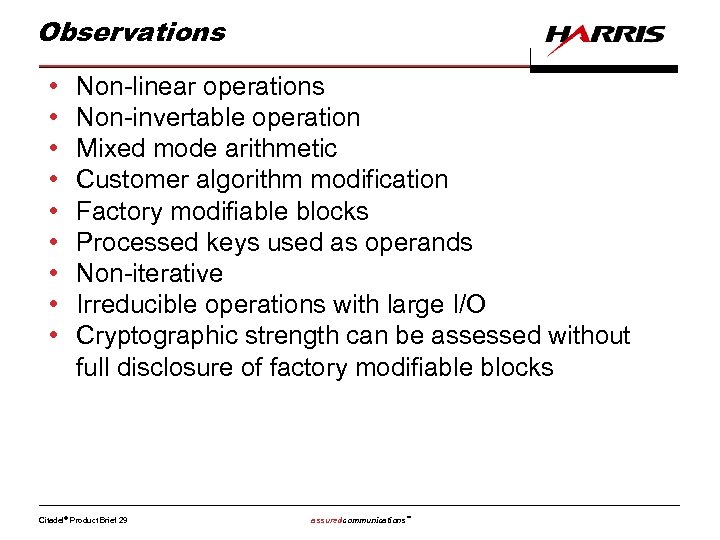
Observations • • • Non-linear operations Non-invertable operation Mixed mode arithmetic Customer algorithm modification Factory modifiable blocks Processed keys used as operands Non-iterative Irreducible operations with large I/O Cryptographic strength can be assessed without full disclosure of factory modifiable blocks Citadel® Product Brief 29 assuredcommunications™
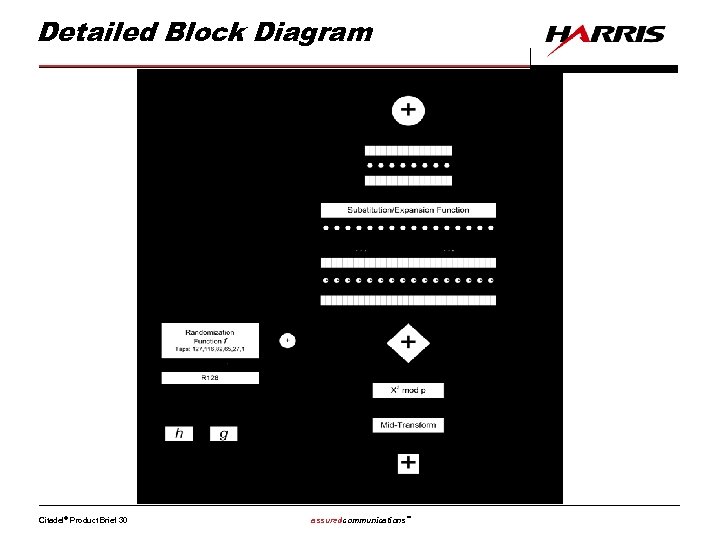
Detailed Block Diagram Citadel® Product Brief 30 assuredcommunications™
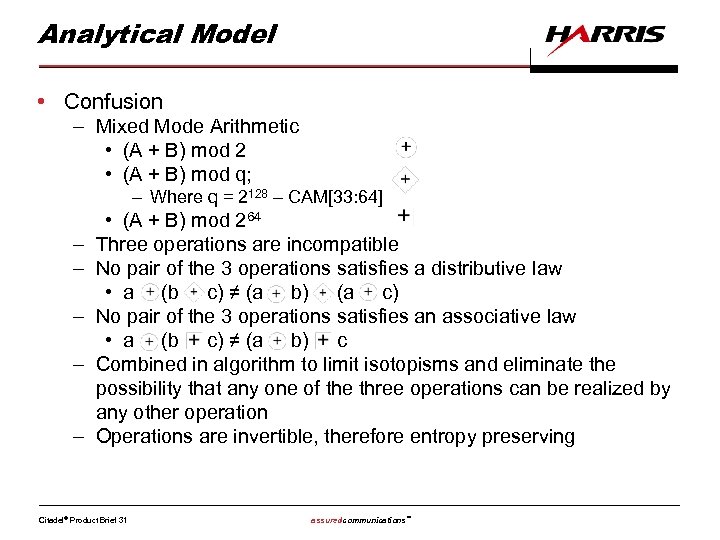
Analytical Model • Confusion – Mixed Mode Arithmetic • (A + B) mod 2 • (A + B) mod q; – Where q = 2128 – CAM[33: 64] – – – • (A + B) mod 264 Three operations are incompatible No pair of the 3 operations satisfies a distributive law • a (b c) ≠ (a b) (a c) No pair of the 3 operations satisfies an associative law • a (b c) ≠ (a b) c Combined in algorithm to limit isotopisms and eliminate the possibility that any one of the three operations can be realized by any other operation Operations are invertible, therefore entropy preserving Citadel® Product Brief 31 assuredcommunications™
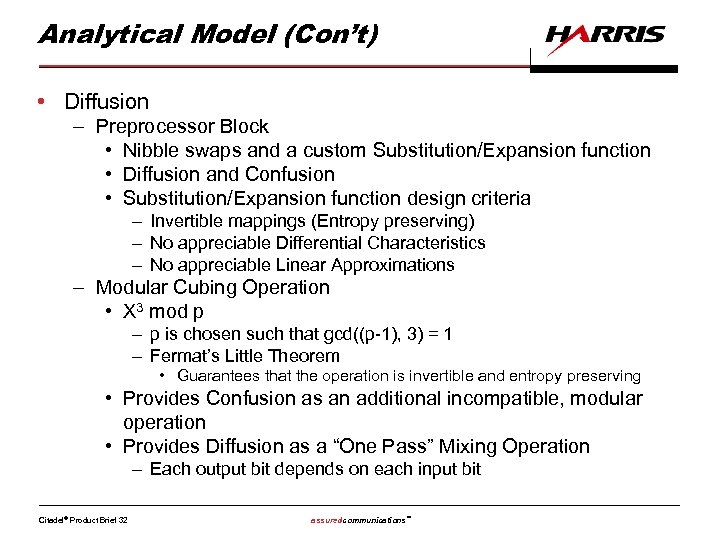
Analytical Model (Con’t) • Diffusion – Preprocessor Block • Nibble swaps and a custom Substitution/Expansion function • Diffusion and Confusion • Substitution/Expansion function design criteria – Invertible mappings (Entropy preserving) – No appreciable Differential Characteristics – No appreciable Linear Approximations – Modular Cubing Operation • X 3 mod p – p is chosen such that gcd((p-1), 3) = 1 – Fermat’s Little Theorem • Guarantees that the operation is invertible and entropy preserving • Provides Confusion as an additional incompatible, modular operation • Provides Diffusion as a “One Pass” Mixing Operation – Each output bit depends on each input bit Citadel® Product Brief 32 assuredcommunications™

Citadel® Device Overview RIT 33 assuredcommunications™ d-MMM-y

Citadel® Device Overview • Digital encryption/decryption engine with key management support features • Designed to military/government threat model • Harris proprietary military grade algorithm • 128 bit key length • Independent validation • Standardized crypto solution for many of the world’s militaries Citadel® Product Brief 34 assuredcommunications™
Technology • 0. 6 M TLM CMOS technology • Compact 80 -pin Thin Quad Flat Pack • Extended Temperature (-40 o. C To +85 o. C) • 3. 3 or 5 Volt Operation • Typical Power - 50 mw @ 5 V/256 kbps, 12 mw @ 3. 3 V/256 kbps • 5 Mbps Max Data Rate Citadel® Product Brief 35 assuredcommunications™
Encryption Options • Standard Harris Citadel® Algorithm (MK-128) • Harris Cryptographic Customization (HCC) – Unique algorithm programmed at Harris – Fully revalidated by Harris • Customer Algorithm Modification (CAM) – Customer determines unique configuration (>1019 variations) – Configuration Set at customer facility – Reconfigurations do not require revalidating – Configuration cannot be extracted from Citadel® Product Brief 36 assuredcommunications™
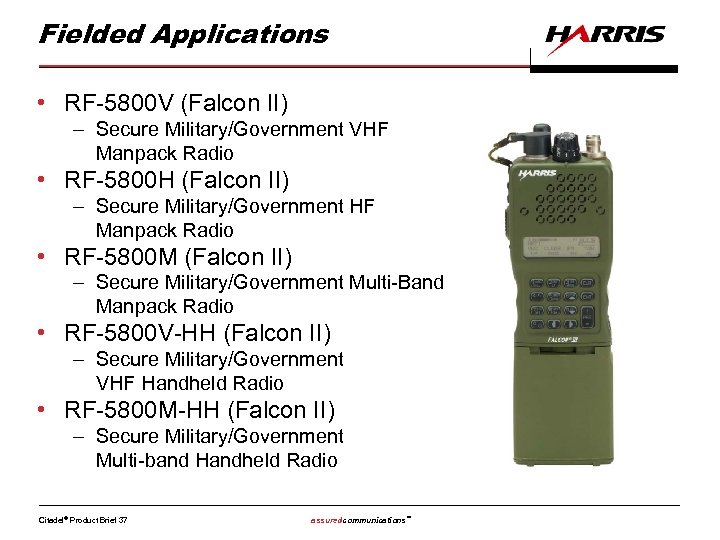
Fielded Applications • RF-5800 V (Falcon II) – Secure Military/Government VHF Manpack Radio • RF-5800 H (Falcon II) – Secure Military/Government HF Manpack Radio • RF-5800 M (Falcon II) – Secure Military/Government Multi-Band Manpack Radio • RF-5800 V-HH (Falcon II) – Secure Military/Government VHF Handheld Radio • RF-5800 M-HH (Falcon II) – Secure Military/Government Multi-band Handheld Radio Citadel® Product Brief 37 assuredcommunications™

Conclusion and References These items/technical data are controlled by the US Department of State, International Traffic in Arms Regulations (ITAR) 22 CFR Parts 120 -130 and cannot be exported from the United States or shared with a Non-US Citizen without prior approval from the United States Government. RIT 38 assuredcommunications™ d-MMM-y
Conclusion & Questions Citadel® Product Brief 39 assuredcommunications™
![References • [1] F. L. Bauer; “Decrypted Secrets 2 nd ed. ”, Springer. Verilag, References • [1] F. L. Bauer; “Decrypted Secrets 2 nd ed. ”, Springer. Verilag,](https://present5.com/presentation/5cfad4c31cb5c26f906f2631cfeddd43/image-40.jpg)
References • [1] F. L. Bauer; “Decrypted Secrets 2 nd ed. ”, Springer. Verilag, 2000 • [2] Matt Blaze, Whitfield Diffie, Ronald L. Rivest, Bruce Schneier, Tsutomu Shimomura, Eric Thompson, and Michael Wiener, “Minimal Key Lengths for Symmetric Ciphers to Provide Adequate Commercial Security” • [3] I. Ben-Aroya and E. Biham, "Differential Cryptanalysis of Lucifer, " Advances in Cryptology CRYPTO '93 Proceedings, Springer-Verilag, 1994, pp. 187 -199 Citadel® Product Brief 40 assuredcommunications™
![References (Con’t) • [4] FIPS-PUB-74, "Guidelines for Implementing and Using The NBS Data Encryption References (Con’t) • [4] FIPS-PUB-74, "Guidelines for Implementing and Using The NBS Data Encryption](https://present5.com/presentation/5cfad4c31cb5c26f906f2631cfeddd43/image-41.jpg)
References (Con’t) • [4] FIPS-PUB-74, "Guidelines for Implementing and Using The NBS Data Encryption Standard", Federal Information Processing Standards Publication 74, 1 April 1981 • [5] FIPS-PUB-81, "DES Modes of Operation", Federal Information Processing Standards Publication 81, 2 December 1980 • [6] Knuth, Donald; "The Art of Computer Programming: Vol. II, Seminumerical Algorithms", Addison Wesley Publishing Company, 1969 • [7] M. Kurdziel, R. Clements, “Harris Customizable Cryptographic Architecture, ” Proc. IEEE, Mil. Comm. Conf. , pp. 1033 -1037, Oct. 1998 Citadel® Product Brief 41 assuredcommunications™
![References (Con’t) • [8] M. Kurdziel, J. Fitton, “Baseline Requirements for Government and Military References (Con’t) • [8] M. Kurdziel, J. Fitton, “Baseline Requirements for Government and Military](https://present5.com/presentation/5cfad4c31cb5c26f906f2631cfeddd43/image-42.jpg)
References (Con’t) • [8] M. Kurdziel, J. Fitton, “Baseline Requirements for Government and Military Encryption Algorithms”, Proc. IEEE, Mil. Comm. Conf. , Oct. 2002 • [9] B. Schneier, “Applied Cryptography 2 nd ed. ”, John Wiley and Sons, 1996 • [10] Simmons, J. S. , ed. ; "Contemporary Cryptology, The Science of Information Integrity", IEEE Press, 1992 • [11] M. Kurdziel, R. Clements, G. Dennis “Customizable Cryptographic Architecture for Government and Military Communications Applications, ” Proc. IEEE, Mil. Comm. Conf. , Nov. 2004 Citadel® Product Brief 42 assuredcommunications™
![References (Con’t) • [12] National Institute of Standards and Technology (NIST), NIST FIPS PUB References (Con’t) • [12] National Institute of Standards and Technology (NIST), NIST FIPS PUB](https://present5.com/presentation/5cfad4c31cb5c26f906f2631cfeddd43/image-43.jpg)
References (Con’t) • [12] National Institute of Standards and Technology (NIST), NIST FIPS PUB 197 “Advanced Encryption Standard (AES), ” U. S. Department of Commerce, May, 2002 • [13] National Institute of Standards and Technology (NIST), NIST FIPS PUB 140 -2 “Requirements for Cryptographic Modules, ” U. S. Department of Commerce, May, 2001 • [14] M. Kurdziel, G. Dennis, “An AES Variant for Military/Government COMSEC Applications, ” Proc. IEEE, Mil. Comm. Conf. , Oct. 2003 Citadel® Product Brief 43 assuredcommunications™
![References (Con’t) • [15] Frank Swiderski, Window Snyder, “Threat Modeling” Microsoft Press, 2004 Citadel® References (Con’t) • [15] Frank Swiderski, Window Snyder, “Threat Modeling” Microsoft Press, 2004 Citadel®](https://present5.com/presentation/5cfad4c31cb5c26f906f2631cfeddd43/image-44.jpg)
References (Con’t) • [15] Frank Swiderski, Window Snyder, “Threat Modeling” Microsoft Press, 2004 Citadel® Product Brief 44 assuredcommunications™
5cfad4c31cb5c26f906f2631cfeddd43.ppt