b82fcb1759862c4a80e7efb3a6fd6130.ppt
- Количество слайдов: 23
 MIDDLEWARE SYSTEMS RESEARCH GROUP A Taxonomy for Denial of Service Attacks in Content-based Publish/Subscribe Systems Alex Wun, Alex Cheung, Hans-Arno Jacobsen Department of Electrical and Computer Engineering Department of Computer Science University of Toronto
MIDDLEWARE SYSTEMS RESEARCH GROUP A Taxonomy for Denial of Service Attacks in Content-based Publish/Subscribe Systems Alex Wun, Alex Cheung, Hans-Arno Jacobsen Department of Electrical and Computer Engineering Department of Computer Science University of Toronto
 Current State of Denial of Service l Prominent Do. S news in 2007: ¡ 6 of 13 Root DNS servers attacked [ICANN 2007] ¡ DC++ P 2 P networks used in attacks [DCPP 2007] ¡ Estonian sites: government, bank, police [Yahoo 2007] ¡ Plenty more … l Do. S problems are not going away
Current State of Denial of Service l Prominent Do. S news in 2007: ¡ 6 of 13 Root DNS servers attacked [ICANN 2007] ¡ DC++ P 2 P networks used in attacks [DCPP 2007] ¡ Estonian sites: government, bank, police [Yahoo 2007] ¡ Plenty more … l Do. S problems are not going away
 Research Goals l Stimulate discussion about Do. S in CPS ¡ Avoid repeating old Do. S weaknesses (e. g. , IPv 6 source routing) l Identify ¡ Will new Do. S Concerns Do. S attacks in CPS systems be any different? ¡ What are the prominent issues? ¡ How can potential Do. S attacks be classified?
Research Goals l Stimulate discussion about Do. S in CPS ¡ Avoid repeating old Do. S weaknesses (e. g. , IPv 6 source routing) l Identify ¡ Will new Do. S Concerns Do. S attacks in CPS systems be any different? ¡ What are the prominent issues? ¡ How can potential Do. S attacks be classified?
 Our Contributions l Study impact of CPS features on Do. S effects ¡ Distributed event delivery ¡ Content-based processing overhead ¡ State maintenance l Classify potential Do. S attack characteristics l Identify CPS concepts with Do. S implications
Our Contributions l Study impact of CPS features on Do. S effects ¡ Distributed event delivery ¡ Content-based processing overhead ¡ State maintenance l Classify potential Do. S attack characteristics l Identify CPS concepts with Do. S implications
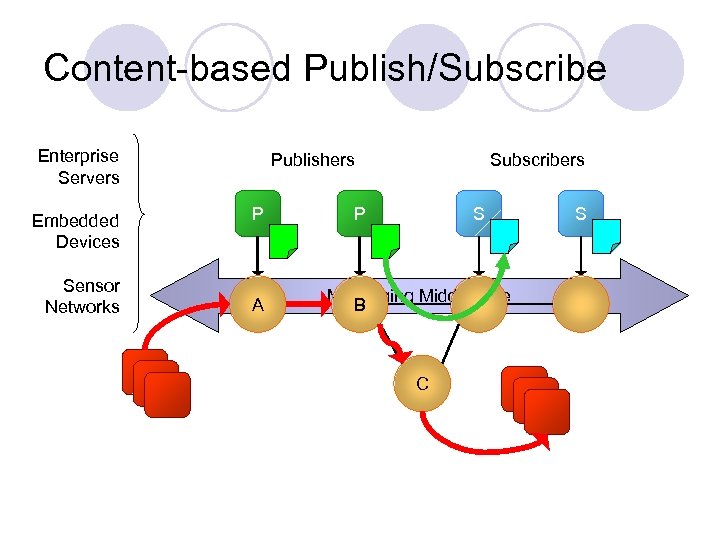 Content-based Publish/Subscribe Enterprise Servers Embedded Devices Sensor Networks Publishers P A Subscribers P S Messaging Middleware B C S
Content-based Publish/Subscribe Enterprise Servers Embedded Devices Sensor Networks Publishers P A Subscribers P S Messaging Middleware B C S
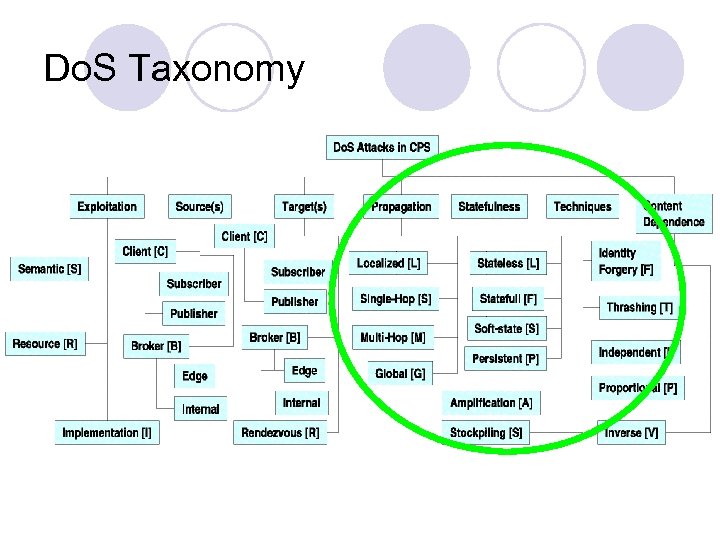 Do. S Taxonomy
Do. S Taxonomy
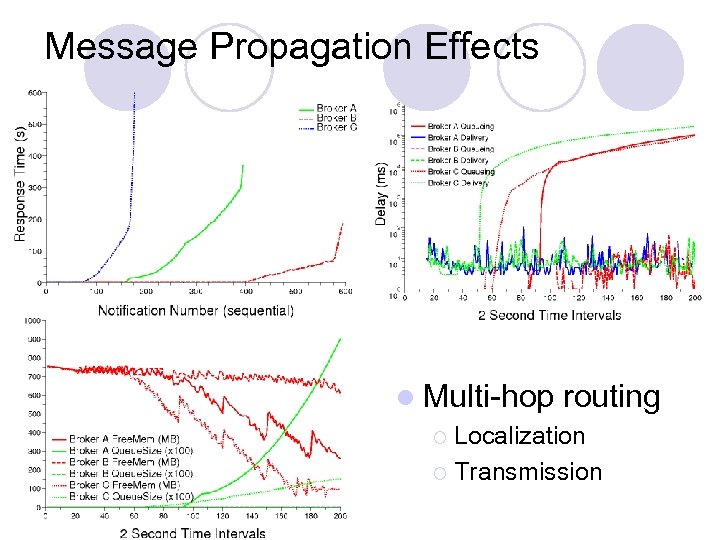 Message Propagation Effects l Multi-hop routing ¡ Localization ¡ Transmission
Message Propagation Effects l Multi-hop routing ¡ Localization ¡ Transmission
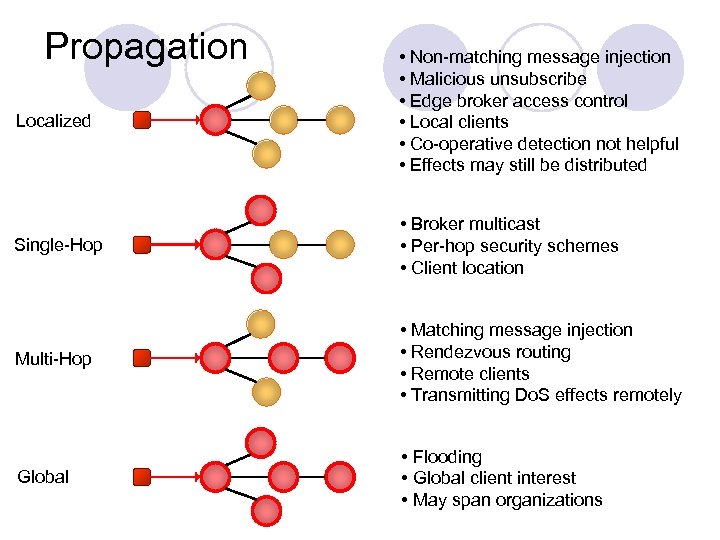 Propagation Localized • Non-matching message injection • Malicious unsubscribe • Edge broker access control • Local clients • Co-operative detection not helpful • Effects may still be distributed Single-Hop • Broker multicast • Per-hop security schemes • Client location Multi-Hop • Matching message injection • Rendezvous routing • Remote clients • Transmitting Do. S effects remotely Global • Flooding • Global client interest • May span organizations
Propagation Localized • Non-matching message injection • Malicious unsubscribe • Edge broker access control • Local clients • Co-operative detection not helpful • Effects may still be distributed Single-Hop • Broker multicast • Per-hop security schemes • Client location Multi-Hop • Matching message injection • Rendezvous routing • Remote clients • Transmitting Do. S effects remotely Global • Flooding • Global client interest • May span organizations
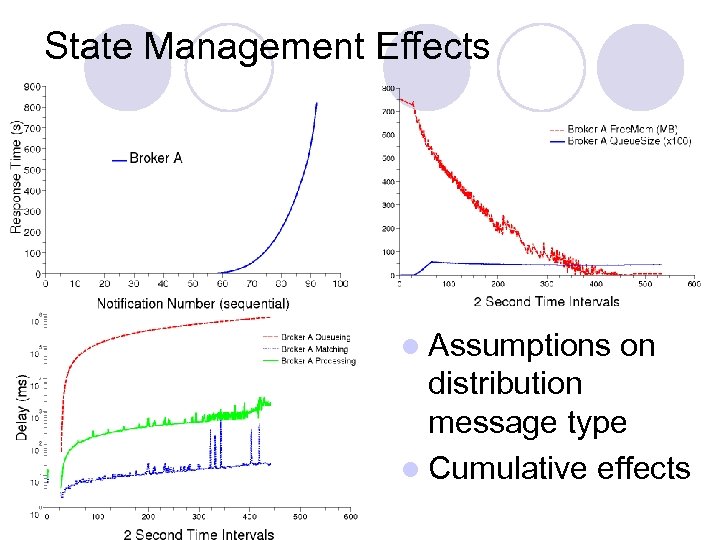 State Management Effects l Assumptions on distribution message type l Cumulative effects
State Management Effects l Assumptions on distribution message type l Cumulative effects
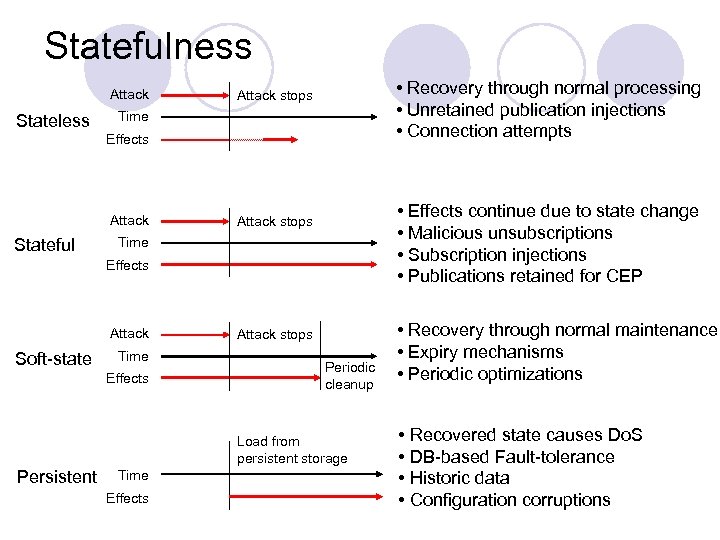 Statefulness Attack Stateless • Recovery through normal processing • Unretained publication injections • Connection attempts Attack stops Time Effects Attack Stateful • Effects continue due to state change • Malicious unsubscriptions • Subscription injections • Publications retained for CEP Attack stops Time Effects Attack Soft-state Time Effects Attack stops Periodic cleanup Load from persistent storage Persistent Time Effects • Recovery through normal maintenance • Expiry mechanisms • Periodic optimizations • Recovered state causes Do. S • DB-based Fault-tolerance • Historic data • Configuration corruptions
Statefulness Attack Stateless • Recovery through normal processing • Unretained publication injections • Connection attempts Attack stops Time Effects Attack Stateful • Effects continue due to state change • Malicious unsubscriptions • Subscription injections • Publications retained for CEP Attack stops Time Effects Attack Soft-state Time Effects Attack stops Periodic cleanup Load from persistent storage Persistent Time Effects • Recovery through normal maintenance • Expiry mechanisms • Periodic optimizations • Recovered state causes Do. S • DB-based Fault-tolerance • Historic data • Configuration corruptions
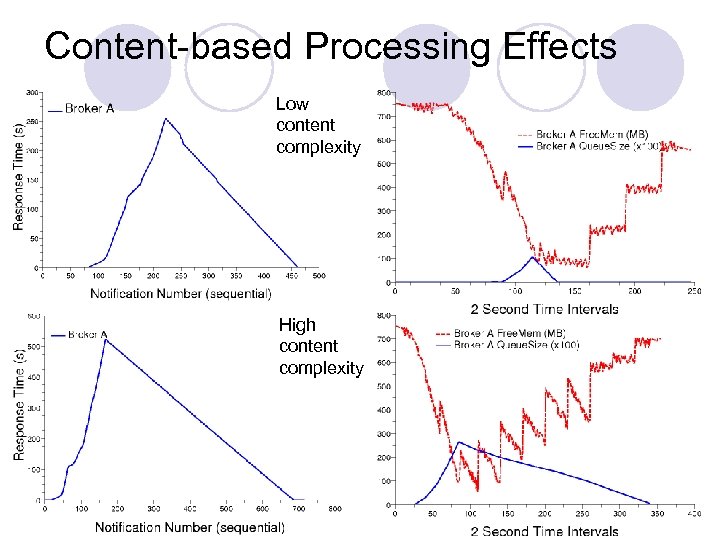 Content-based Processing Effects Low content complexity High content complexity
Content-based Processing Effects Low content complexity High content complexity
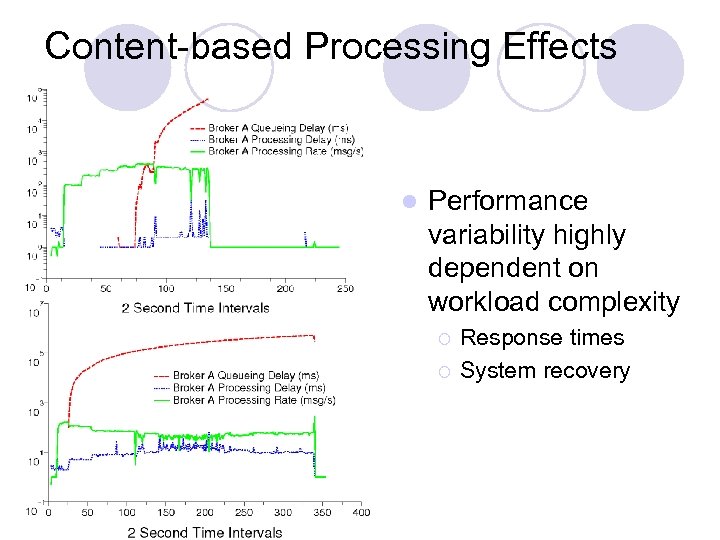 Content-based Processing Effects l Performance variability highly dependent on workload complexity ¡ ¡ Response times System recovery
Content-based Processing Effects l Performance variability highly dependent on workload complexity ¡ ¡ Response times System recovery
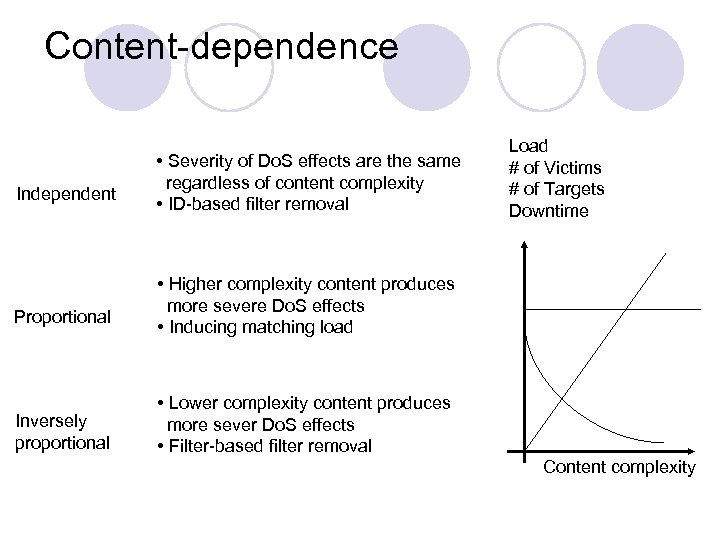 Content-dependence Independent Proportional Inversely proportional • Severity of Do. S effects are the same regardless of content complexity • ID-based filter removal Load # of Victims # of Targets Downtime • Higher complexity content produces more severe Do. S effects • Inducing matching load • Lower complexity content produces more sever Do. S effects • Filter-based filter removal Content complexity
Content-dependence Independent Proportional Inversely proportional • Severity of Do. S effects are the same regardless of content complexity • ID-based filter removal Load # of Victims # of Targets Downtime • Higher complexity content produces more severe Do. S effects • Inducing matching load • Lower complexity content produces more sever Do. S effects • Filter-based filter removal Content complexity
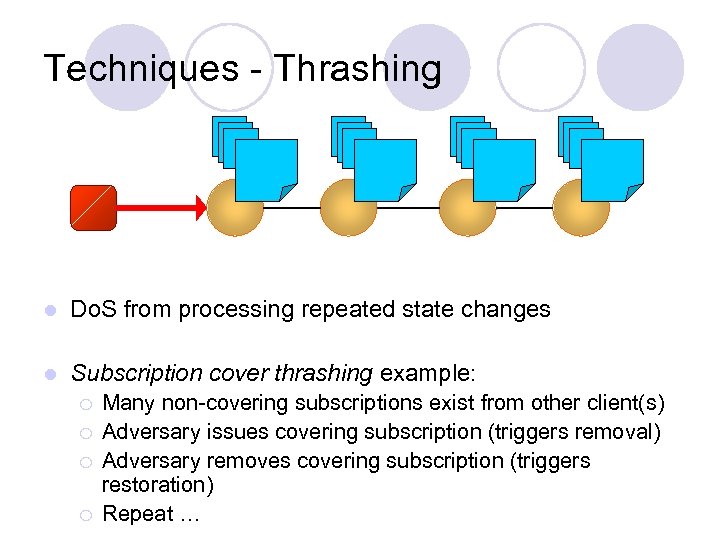 Techniques - Thrashing l Do. S from processing repeated state changes l Subscription cover thrashing example: ¡ ¡ Many non-covering subscriptions exist from other client(s) Adversary issues covering subscription (triggers removal) Adversary removes covering subscription (triggers restoration) Repeat …
Techniques - Thrashing l Do. S from processing repeated state changes l Subscription cover thrashing example: ¡ ¡ Many non-covering subscriptions exist from other client(s) Adversary issues covering subscription (triggers removal) Adversary removes covering subscription (triggers restoration) Repeat …
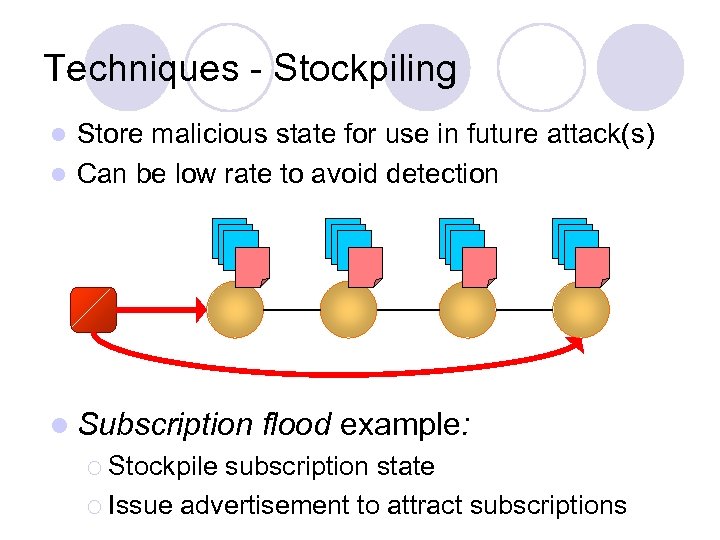 Techniques - Stockpiling Store malicious state for use in future attack(s) l Can be low rate to avoid detection l l Subscription ¡ Stockpile flood example: subscription state ¡ Issue advertisement to attract subscriptions
Techniques - Stockpiling Store malicious state for use in future attack(s) l Can be low rate to avoid detection l l Subscription ¡ Stockpile flood example: subscription state ¡ Issue advertisement to attract subscriptions
 Techniques - Traffic Amplification Malicious traffic of adversary multiplied l Known to be a problem in traditional Internet l ¡ ¡ ¡ l Smurf attack Source routing Reflection (connection retries) Fundamental to many CPS features? ¡ ¡ ¡ Highly generic subscriptions and advertisements Uncovering and Unmerging Historic data
Techniques - Traffic Amplification Malicious traffic of adversary multiplied l Known to be a problem in traditional Internet l ¡ ¡ ¡ l Smurf attack Source routing Reflection (connection retries) Fundamental to many CPS features? ¡ ¡ ¡ Highly generic subscriptions and advertisements Uncovering and Unmerging Historic data
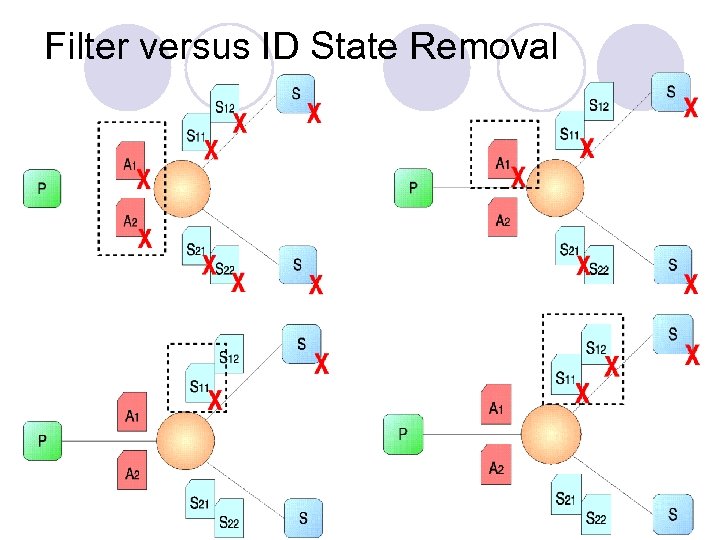 Filter versus ID State Removal
Filter versus ID State Removal
![Related Work l Mirkovic ¡ DDo. S and Reiher [Mirkovic 2004] taxonomy in traditional Related Work l Mirkovic ¡ DDo. S and Reiher [Mirkovic 2004] taxonomy in traditional](https://present5.com/presentation/b82fcb1759862c4a80e7efb3a6fd6130/image-18.jpg) Related Work l Mirkovic ¡ DDo. S and Reiher [Mirkovic 2004] taxonomy in traditional Internet domain l Srivatsa and Liu [Srivatsa 2005] ¡ Authentication l Wang to limit flooding-based Do. S et al. [Wang 2002] ¡ Discussed concerns Do. S briefly along with other security
Related Work l Mirkovic ¡ DDo. S and Reiher [Mirkovic 2004] taxonomy in traditional Internet domain l Srivatsa and Liu [Srivatsa 2005] ¡ Authentication l Wang to limit flooding-based Do. S et al. [Wang 2002] ¡ Discussed concerns Do. S briefly along with other security
 Conclusion l CPS characteristics with Do. S implications ¡ ¡ ¡ l Message propagation (remote attacks) Content complexity (highly variable performance) State maintenance (assumptions on message type distribution) Abusing features for Do. S ¡ ¡ ¡ Stockpiling Traffic Amplification Filter Removal (Thrashing, Victims)
Conclusion l CPS characteristics with Do. S implications ¡ ¡ ¡ l Message propagation (remote attacks) Content complexity (highly variable performance) State maintenance (assumptions on message type distribution) Abusing features for Do. S ¡ ¡ ¡ Stockpiling Traffic Amplification Filter Removal (Thrashing, Victims)
![References l [ICANN 2007] ¡ l [DCPP 2007] ¡ l A Taxonomy of DDo. References l [ICANN 2007] ¡ l [DCPP 2007] ¡ l A Taxonomy of DDo.](https://present5.com/presentation/b82fcb1759862c4a80e7efb3a6fd6130/image-20.jpg) References l [ICANN 2007] ¡ l [DCPP 2007] ¡ l A Taxonomy of DDo. S Attack and DDo. S Defense Mechanisms, ACM SIGCOMM [Srivatsa 2005] ¡ l http: //fe 48. news. sp 1. yahoo. com/s/infoworld/20070517/tc_infoworld/886 10 [Mirkovic 2004] ¡ l http: //dcpp. wordpress. com/2007/05/22/denying-distributed-attacks/ [Yahoo 2007] ¡ l http: //icann. org/announcements/factsheet-dns-attack-08 mar 07_v 1. 1. pdf Securing Publish-Subscribe Overlay Services with Event. Guard, ACM Conference on Computer and Communications Security [Wang 2002] ¡ Security Issues and Requirements for Internet-Scale Publish-Subscribe Systems, Hawaii International Conference on System Sciences
References l [ICANN 2007] ¡ l [DCPP 2007] ¡ l A Taxonomy of DDo. S Attack and DDo. S Defense Mechanisms, ACM SIGCOMM [Srivatsa 2005] ¡ l http: //fe 48. news. sp 1. yahoo. com/s/infoworld/20070517/tc_infoworld/886 10 [Mirkovic 2004] ¡ l http: //dcpp. wordpress. com/2007/05/22/denying-distributed-attacks/ [Yahoo 2007] ¡ l http: //icann. org/announcements/factsheet-dns-attack-08 mar 07_v 1. 1. pdf Securing Publish-Subscribe Overlay Services with Event. Guard, ACM Conference on Computer and Communications Security [Wang 2002] ¡ Security Issues and Requirements for Internet-Scale Publish-Subscribe Systems, Hawaii International Conference on System Sciences
 MIDDLEWARE SYSTEMS RESEARCH GROUP Extra Slides
MIDDLEWARE SYSTEMS RESEARCH GROUP Extra Slides
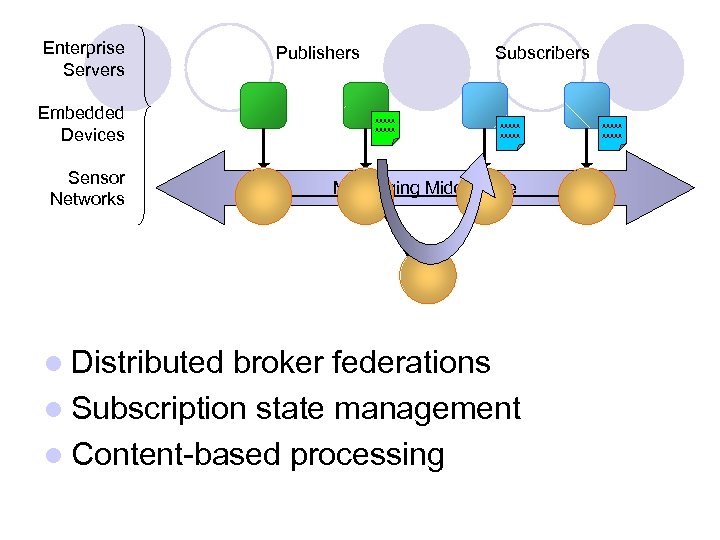 Enterprise Servers Embedded Devices Sensor Networks l Distributed Publishers Subscribers xxxxx Messaging Middleware broker federations l Subscription state management l Content-based processing xxxxx
Enterprise Servers Embedded Devices Sensor Networks l Distributed Publishers Subscribers xxxxx Messaging Middleware broker federations l Subscription state management l Content-based processing xxxxx
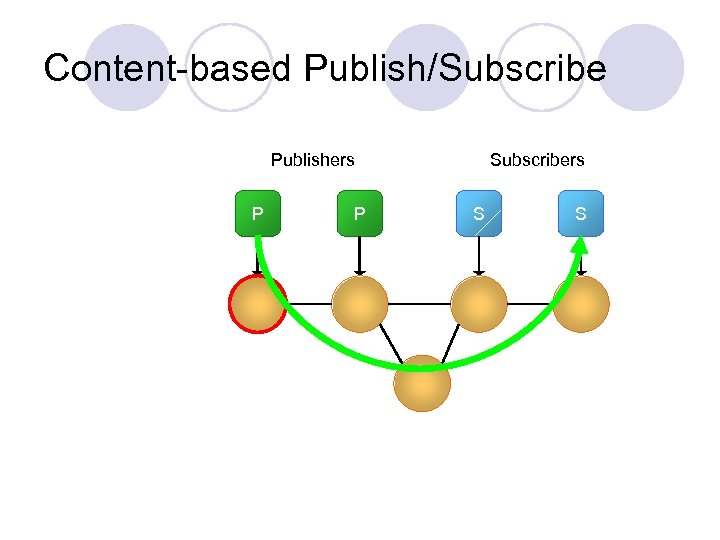 Content-based Publish/Subscribe Publishers P P Subscribers S S
Content-based Publish/Subscribe Publishers P P Subscribers S S


