b59874fa45c4a41e0c1317df2720af42.ppt
- Количество слайдов: 66
 Microsoft Patch & Update Management Solutions And Strategy Scott Johnson General Manager Rocky Mountain District Microsoft Corporation Jason R. Graefe Enterprise Management Specialist Microsoft Corporation Josh Pointer Senior Consultant II Microsoft Corporation
Microsoft Patch & Update Management Solutions And Strategy Scott Johnson General Manager Rocky Mountain District Microsoft Corporation Jason R. Graefe Enterprise Management Specialist Microsoft Corporation Josh Pointer Senior Consultant II Microsoft Corporation
 Agenda Current Situation Scott Johnson Solution Components & Roadmap Jason R. Graefe Best Practices & Available Tools Josh Pointer Questions
Agenda Current Situation Scott Johnson Solution Components & Roadmap Jason R. Graefe Best Practices & Available Tools Josh Pointer Questions
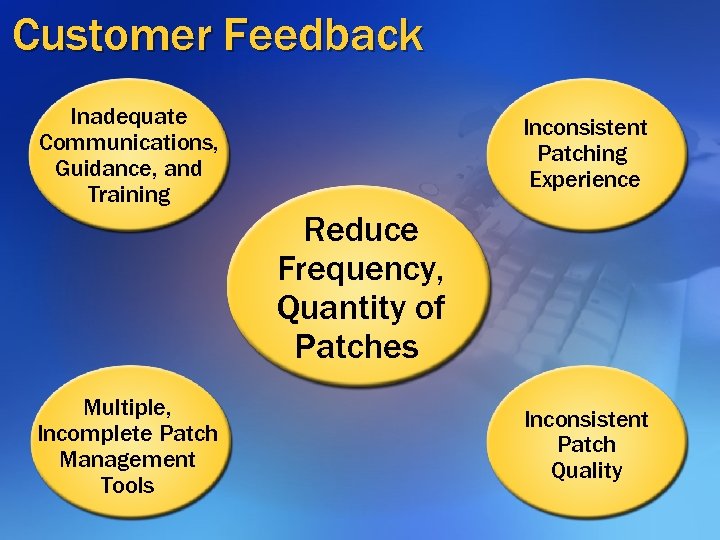 Customer Feedback Inadequate Communications, Guidance, and Training Inconsistent Patching Experience Reduce Frequency, Quantity of Patches Multiple, Incomplete Patch Management Tools Inconsistent Patch Quality
Customer Feedback Inadequate Communications, Guidance, and Training Inconsistent Patching Experience Reduce Frequency, Quantity of Patches Multiple, Incomplete Patch Management Tools Inconsistent Patch Quality
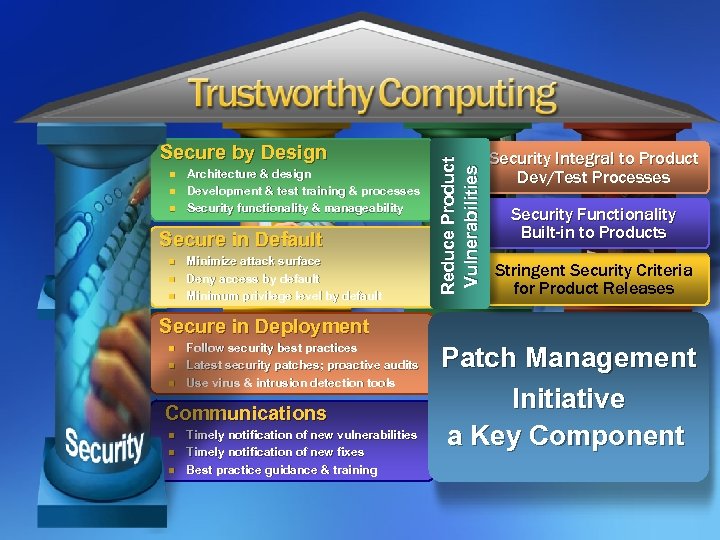 n n n Architecture & design Development & test training & processes Security functionality & manageability Secure in Default n n n Minimize attack surface Deny access by default Minimum privilege level by default Reduce Product Vulnerabilities Secure by Design Security Integral to Product Dev/Test Processes Security Functionality Built-in to Products Stringent Security Criteria for Product Releases Secure in Deployment n n n Follow security best practices Latest security patches; proactive audits Use virus & intrusion detection tools Communications n n n Timely notification of new vulnerabilities Timely notification of new fixes Best practice guidance & training Patch Management Initiative a Key Component
n n n Architecture & design Development & test training & processes Security functionality & manageability Secure in Default n n n Minimize attack surface Deny access by default Minimum privilege level by default Reduce Product Vulnerabilities Secure by Design Security Integral to Product Dev/Test Processes Security Functionality Built-in to Products Stringent Security Criteria for Product Releases Secure in Deployment n n n Follow security best practices Latest security patches; proactive audits Use virus & intrusion detection tools Communications n n n Timely notification of new vulnerabilities Timely notification of new fixes Best practice guidance & training Patch Management Initiative a Key Component
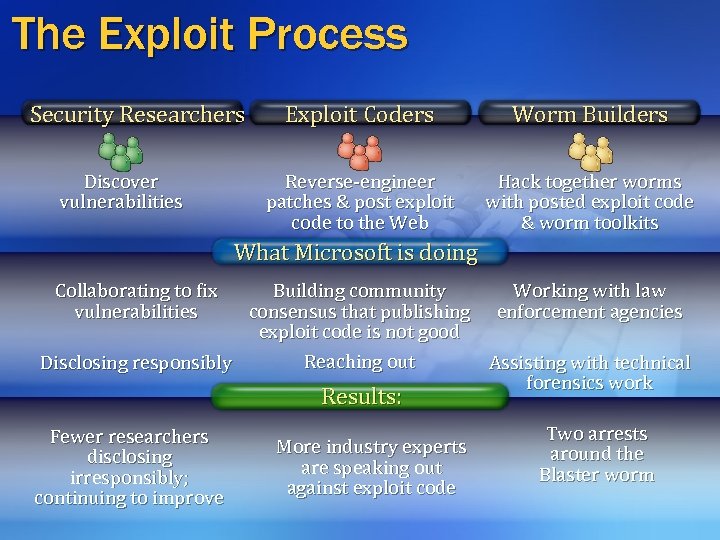 The Exploit Process Security Researchers Discover vulnerabilities Exploit Coders Worm Builders Reverse-engineer patches & post exploit code to the Web Hack together worms with posted exploit code & worm toolkits What Microsoft is doing Collaborating to fix vulnerabilities Building community Working with law consensus that publishing enforcement agencies exploit code is not good Reaching out Disclosing responsibly Assisting with technical forensics work Results: Fewer researchers disclosing irresponsibly; continuing to improve More industry experts are speaking out against exploit code Two arrests around the Blaster worm
The Exploit Process Security Researchers Discover vulnerabilities Exploit Coders Worm Builders Reverse-engineer patches & post exploit code to the Web Hack together worms with posted exploit code & worm toolkits What Microsoft is doing Collaborating to fix vulnerabilities Building community Working with law consensus that publishing enforcement agencies exploit code is not good Reaching out Disclosing responsibly Assisting with technical forensics work Results: Fewer researchers disclosing irresponsibly; continuing to improve More industry experts are speaking out against exploit code Two arrests around the Blaster worm
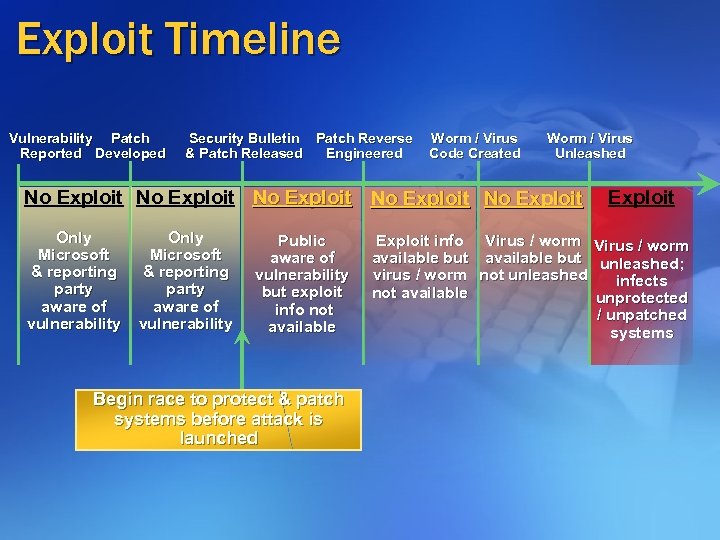 Exploit Timeline Vulnerability Patch Reported Developed Security Bulletin Patch Reverse & Patch Released Engineered Worm / Virus Code Created Worm / Virus Unleashed No Exploit No Exploit Only Microsoft & reporting party aware of vulnerability Public aware of vulnerability but exploit info not available Begin race to protect & patch systems before attack is launched Exploit info Virus / worm available but unleashed; virus / worm not unleashed infects not available unprotected / unpatched systems
Exploit Timeline Vulnerability Patch Reported Developed Security Bulletin Patch Reverse & Patch Released Engineered Worm / Virus Code Created Worm / Virus Unleashed No Exploit No Exploit Only Microsoft & reporting party aware of vulnerability Public aware of vulnerability but exploit info not available Begin race to protect & patch systems before attack is launched Exploit info Virus / worm available but unleashed; virus / worm not unleashed infects not available unprotected / unpatched systems
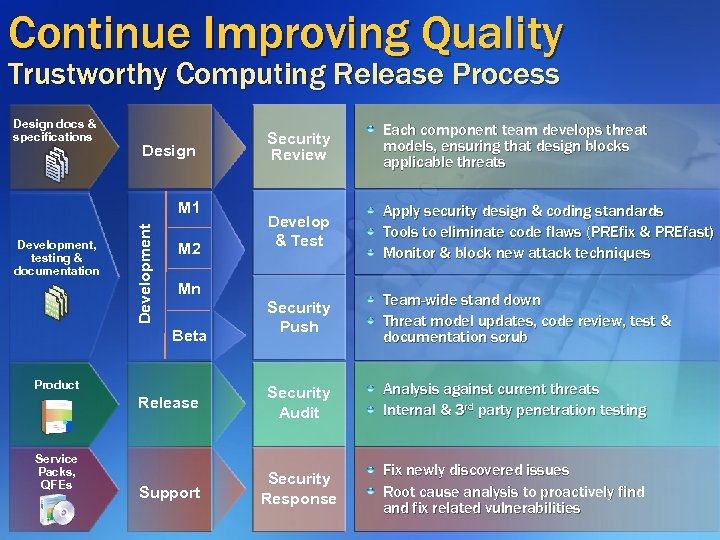 Continue Improving Quality Trustworthy Computing Release Process Design docs & specifications Security Review Each component team develops threat models, ensuring that design blocks applicable threats Develop & Test Apply security design & coding standards Tools to eliminate code flaws (PREfix & PREfast) Monitor & block new attack techniques Security Push Team-wide stand down Threat model updates, code review, test & documentation scrub Release Security Audit Analysis against current threats Internal & 3 rd party penetration testing Support Security Response Fix newly discovered issues Root cause analysis to proactively find and fix related vulnerabilities Design Development, testing & documentation Development M 1 M 2 Mn Beta Product Service Packs, QFEs
Continue Improving Quality Trustworthy Computing Release Process Design docs & specifications Security Review Each component team develops threat models, ensuring that design blocks applicable threats Develop & Test Apply security design & coding standards Tools to eliminate code flaws (PREfix & PREfast) Monitor & block new attack techniques Security Push Team-wide stand down Threat model updates, code review, test & documentation scrub Release Security Audit Analysis against current threats Internal & 3 rd party penetration testing Support Security Response Fix newly discovered issues Root cause analysis to proactively find and fix related vulnerabilities Design Development, testing & documentation Development M 1 M 2 Mn Beta Product Service Packs, QFEs
 Addressing The Situation Security and patch management priority #1 – bar none – at Microsoft problem Industry problem Ongoing battle with malicious hackers Need comprehensive, tactical and strategic approach to addressing the situation Trustworthy Computing Initiative Security framework and focus Patch Management Initiative
Addressing The Situation Security and patch management priority #1 – bar none – at Microsoft problem Industry problem Ongoing battle with malicious hackers Need comprehensive, tactical and strategic approach to addressing the situation Trustworthy Computing Initiative Security framework and focus Patch Management Initiative
 Patch Management Initiative Goals Informed & Prepared Customers Accurate, effective, easily discoverable, and timely information Process and best practice guidance; training Consistent & Superior Update Experience Consistent formats and mechanisms for discovery, applicability evaluation, uninstallation, etc. of patches and updates Superior Patch Quality Consistently high quality Consistently small patch sizes Minimize reboots on patch installation Best Patch & Update Management Solutions The right set of functionality Easy to deploy, administer, use Interoperability with third party solutions Cross divisional team with mission to resolve key patch management issues
Patch Management Initiative Goals Informed & Prepared Customers Accurate, effective, easily discoverable, and timely information Process and best practice guidance; training Consistent & Superior Update Experience Consistent formats and mechanisms for discovery, applicability evaluation, uninstallation, etc. of patches and updates Superior Patch Quality Consistently high quality Consistently small patch sizes Minimize reboots on patch installation Best Patch & Update Management Solutions The right set of functionality Easy to deploy, administer, use Interoperability with third party solutions Cross divisional team with mission to resolve key patch management issues
 Patch Management Initiative Progress to Date (October 2003) Informed & Prepared Customers Rationalized patch severity rating levels Better security bulletins and KB articles Security Readiness Kit; Patch Management guidance, etc. Consistent & Superior Update Experience Standardized patch and update terminology Standardized patch naming and installer switch options* Installer consolidation plan in place – will go from ~8 to 2 Reduced patch release frequency from 1/week to 1/month Superior Patch Quality Improved patch testing process and coverage Expanded test process to include customers Reduced reboots by 10%; reduced patch size by up to 75%** Best Patch & Update Management Solutions Developed Patch & Update Management tools roadmap SUS 2. 0 in development: significantly enhanced capabilities SMS 2003 (to be launched 11/2003) delivers expanded patch and update management capabilities More on the Patch Management Initiative in the Roadmap Section of this presentation… *Update. exe now using standardized switches; Windows Installer will use these in MSI 3. 0 **75% for Windows Update installs, more than 25% for other patches
Patch Management Initiative Progress to Date (October 2003) Informed & Prepared Customers Rationalized patch severity rating levels Better security bulletins and KB articles Security Readiness Kit; Patch Management guidance, etc. Consistent & Superior Update Experience Standardized patch and update terminology Standardized patch naming and installer switch options* Installer consolidation plan in place – will go from ~8 to 2 Reduced patch release frequency from 1/week to 1/month Superior Patch Quality Improved patch testing process and coverage Expanded test process to include customers Reduced reboots by 10%; reduced patch size by up to 75%** Best Patch & Update Management Solutions Developed Patch & Update Management tools roadmap SUS 2. 0 in development: significantly enhanced capabilities SMS 2003 (to be launched 11/2003) delivers expanded patch and update management capabilities More on the Patch Management Initiative in the Roadmap Section of this presentation… *Update. exe now using standardized switches; Windows Installer will use these in MSI 3. 0 **75% for Windows Update installs, more than 25% for other patches
 Solution Components Jason R. Graefe Enterprise Management Technology Specialist Microsoft Corporation
Solution Components Jason R. Graefe Enterprise Management Technology Specialist Microsoft Corporation
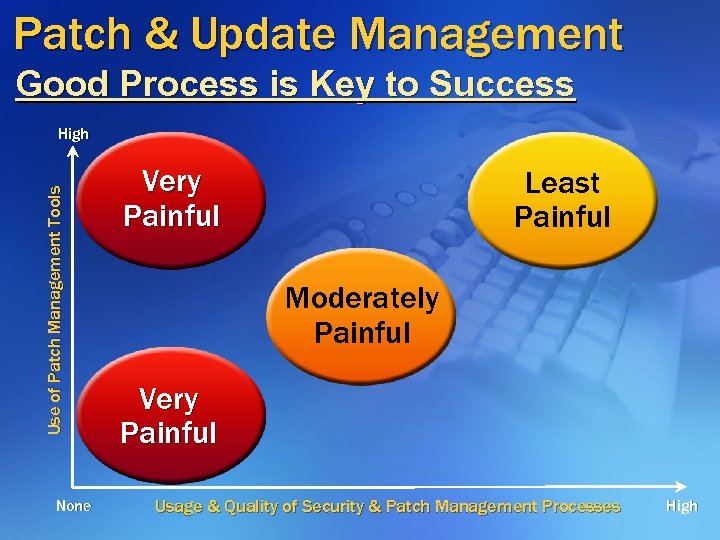 Patch & Update Management Good Process is Key to Success Use of Patch Management Tools High None Very Painful Least Painful Moderately Painful Very Painful Usage & Quality of Security & Patch Management Processes High
Patch & Update Management Good Process is Key to Success Use of Patch Management Tools High None Very Painful Least Painful Moderately Painful Very Painful Usage & Quality of Security & Patch Management Processes High
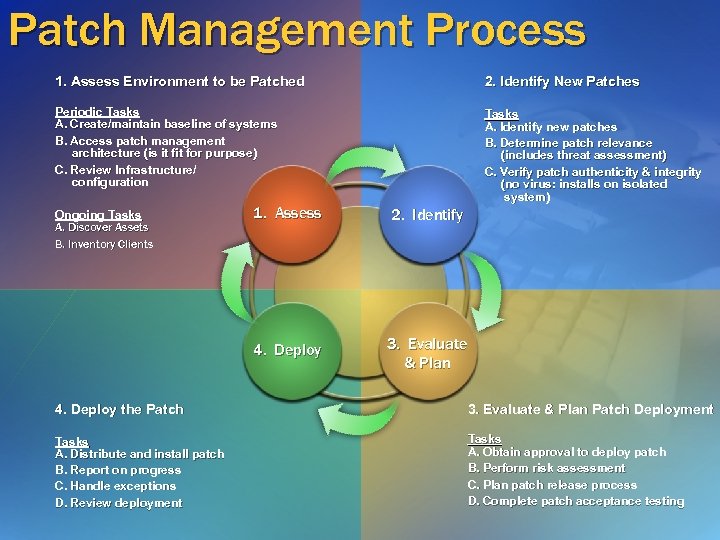 Patch Management Process 1. Assess Environment to be Patched 2. Identify New Patches Periodic Tasks A. Create/maintain baseline of systems B. Access patch management architecture (is it for purpose) C. Review Infrastructure/ configuration Tasks A. Identify new patches B. Determine patch relevance (includes threat assessment) C. Verify patch authenticity & integrity (no virus: installs on isolated system) 1. Assess 2. Identify 4. Deploy Ongoing Tasks A. Discover Assets B. Inventory Clients 3. Evaluate & Plan 4. Deploy the Patch 3. Evaluate & Plan Patch Deployment Tasks A. Distribute and install patch B. Report on progress C. Handle exceptions D. Review deployment Tasks A. Obtain approval to deploy patch B. Perform risk assessment C. Plan patch release process D. Complete patch acceptance testing
Patch Management Process 1. Assess Environment to be Patched 2. Identify New Patches Periodic Tasks A. Create/maintain baseline of systems B. Access patch management architecture (is it for purpose) C. Review Infrastructure/ configuration Tasks A. Identify new patches B. Determine patch relevance (includes threat assessment) C. Verify patch authenticity & integrity (no virus: installs on isolated system) 1. Assess 2. Identify 4. Deploy Ongoing Tasks A. Discover Assets B. Inventory Clients 3. Evaluate & Plan 4. Deploy the Patch 3. Evaluate & Plan Patch Deployment Tasks A. Distribute and install patch B. Report on progress C. Handle exceptions D. Review deployment Tasks A. Obtain approval to deploy patch B. Perform risk assessment C. Plan patch release process D. Complete patch acceptance testing
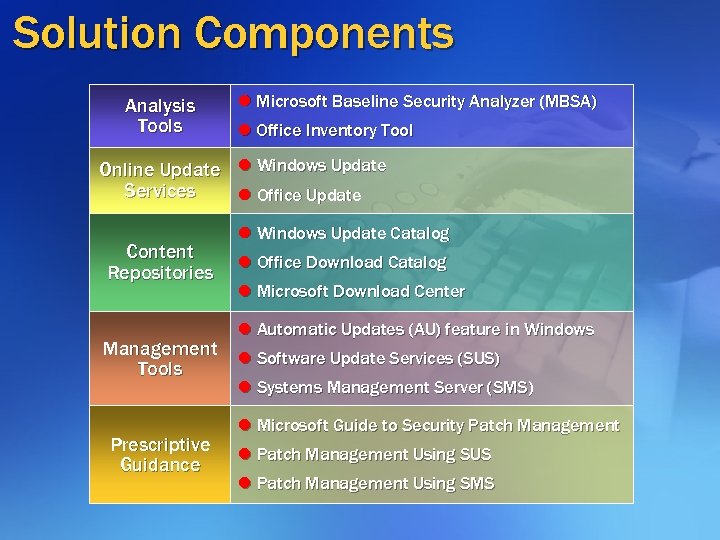 Solution Components Analysis Tools l Microsoft Baseline Security Analyzer (MBSA) l Office Inventory Tool Online Update l Windows Update Services l Office Update Content Repositories Management Tools Prescriptive Guidance l Windows Update Catalog l Office Download Catalog l Microsoft Download Center l Automatic Updates (AU) feature in Windows l Software Update Services (SUS) l Systems Management Server (SMS) l Microsoft Guide to Security Patch Management l Patch Management Using SUS l Patch Management Using SMS
Solution Components Analysis Tools l Microsoft Baseline Security Analyzer (MBSA) l Office Inventory Tool Online Update l Windows Update Services l Office Update Content Repositories Management Tools Prescriptive Guidance l Windows Update Catalog l Office Download Catalog l Microsoft Download Center l Automatic Updates (AU) feature in Windows l Software Update Services (SUS) l Systems Management Server (SMS) l Microsoft Guide to Security Patch Management l Patch Management Using SUS l Patch Management Using SMS
 Current Tool Overview
Current Tool Overview
 MBSA: What It Does Helps identify vulnerable Windows systems Scans for missing security patches and common security mis-configurations Scans various versions of Windows and other Microsoft applications New Update Assess Identify Evaluate & Plan Deploy Scans local or multiple remote systems via GUI or command line invocation Generates XML scan reports on each scanned system Runs on Windows Server 2003, Windows 2000 and Windows XP Integrates with SUS & SMS
MBSA: What It Does Helps identify vulnerable Windows systems Scans for missing security patches and common security mis-configurations Scans various versions of Windows and other Microsoft applications New Update Assess Identify Evaluate & Plan Deploy Scans local or multiple remote systems via GUI or command line invocation Generates XML scan reports on each scanned system Runs on Windows Server 2003, Windows 2000 and Windows XP Integrates with SUS & SMS
 MBSA: Benefits Automates identification of missing security patches & security mis-configurations Allows administrator to centrally scan a large number of systems simultaneously Works for broad range of Microsoftware (not just Windows and Office)
MBSA: Benefits Automates identification of missing security patches & security mis-configurations Allows administrator to centrally scan a large number of systems simultaneously Works for broad range of Microsoftware (not just Windows and Office)
 Office Inventory Tool: What It Is Two components Scanning & logging – inventory. exe Reporting – convert. exe Inventory. exe Compares Windows Installer database information on target computer against catalog in invcif. exe to identify missing updates Generates log file containing this information New Update Assess Identify Evaluate & Plan Convert. exe Combines above log data with update information list in Patchdata. xml to generate report of missing updates Report available in XML, CSV, or MOF format Update inventory reports used To manually update client or administrative installations By SMS* to update SMS inventory and deliver & install missing updates on target computers Deploy *Consumes report in MOF format
Office Inventory Tool: What It Is Two components Scanning & logging – inventory. exe Reporting – convert. exe Inventory. exe Compares Windows Installer database information on target computer against catalog in invcif. exe to identify missing updates Generates log file containing this information New Update Assess Identify Evaluate & Plan Convert. exe Combines above log data with update information list in Patchdata. xml to generate report of missing updates Report available in XML, CSV, or MOF format Update inventory reports used To manually update client or administrative installations By SMS* to update SMS inventory and deliver & install missing updates on target computers Deploy *Consumes report in MOF format
 Windows Update: What It Is Microsoft online service (windowsupdate. microsoft. com): Identifies missing Windows OS* patches / updates on accessing computer Generates targeted list of missing updates Installs user selected missing updates Provides update installation history New Update Assess Identify Supplemented by Windows Update Catalog site which provides: Comprehensive repository for all Windows and ‘Designed for Windows’ logo device driver updates Search – to find desired update Manual download of desired updates Evaluate & Plan Download history for accessing computer Deploy *Windows 98 and later versions. Note: also updates 64 -bit editions of Windows Server
Windows Update: What It Is Microsoft online service (windowsupdate. microsoft. com): Identifies missing Windows OS* patches / updates on accessing computer Generates targeted list of missing updates Installs user selected missing updates Provides update installation history New Update Assess Identify Supplemented by Windows Update Catalog site which provides: Comprehensive repository for all Windows and ‘Designed for Windows’ logo device driver updates Search – to find desired update Manual download of desired updates Evaluate & Plan Download history for accessing computer Deploy *Windows 98 and later versions. Note: also updates 64 -bit editions of Windows Server
 Windows Update: Benefits Single location for Windows patches & updates Automates scanning and installation for patches & updates Easy to use… even for consumers / home users Keeps system up-to-date with latest security & critical patches
Windows Update: Benefits Single location for Windows patches & updates Automates scanning and installation for patches & updates Easy to use… even for consumers / home users Keeps system up-to-date with latest security & critical patches
 Office Update: What It Is Microsoft online service: (http: //office. microsoft. com/officeupdate –> ‘Check for Updates’) Identifies missing Microsoft Office* updates Generates targeted list of missing updates Installs selected missing updates** Also detects & displays report of installed updates New Update Assess Identify Supplemented by Office Download Catalog site which provides: Comprehensive repository for Microsoft Office updates*** and other Office downloads Downloads organized by product, version, and type Manual download of desired updates Evaluate & Plan Deploy *Office 2000 and later versions ***Office 1997 and later versions **As selected by user
Office Update: What It Is Microsoft online service: (http: //office. microsoft. com/officeupdate –> ‘Check for Updates’) Identifies missing Microsoft Office* updates Generates targeted list of missing updates Installs selected missing updates** Also detects & displays report of installed updates New Update Assess Identify Supplemented by Office Download Catalog site which provides: Comprehensive repository for Microsoft Office updates*** and other Office downloads Downloads organized by product, version, and type Manual download of desired updates Evaluate & Plan Deploy *Office 2000 and later versions ***Office 1997 and later versions **As selected by user
 Office Update: Benefits Single location for Office patches & updates Automates scanning and installation for patches & updates Easy to use… even for consumers / home users Keeps Office up-to-date with latest security & critical patches and service packs
Office Update: Benefits Single location for Office patches & updates Automates scanning and installation for patches & updates Easy to use… even for consumers / home users Keeps Office up-to-date with latest security & critical patches and service packs
 Microsoft Download Center: What It Is Microsoft web site (www. microsoft. com/downloads) Comprehensive repository for all Microsoftware downloads Includes downloads for ‘Released to Web’ products, upgrades, & features; New Update Assess Identify Evaluate & Plan Deploy Patches & other updates Other download types (documentation, etc. ) Provides various search and search results sorting options
Microsoft Download Center: What It Is Microsoft web site (www. microsoft. com/downloads) Comprehensive repository for all Microsoftware downloads Includes downloads for ‘Released to Web’ products, upgrades, & features; New Update Assess Identify Evaluate & Plan Deploy Patches & other updates Other download types (documentation, etc. ) Provides various search and search results sorting options
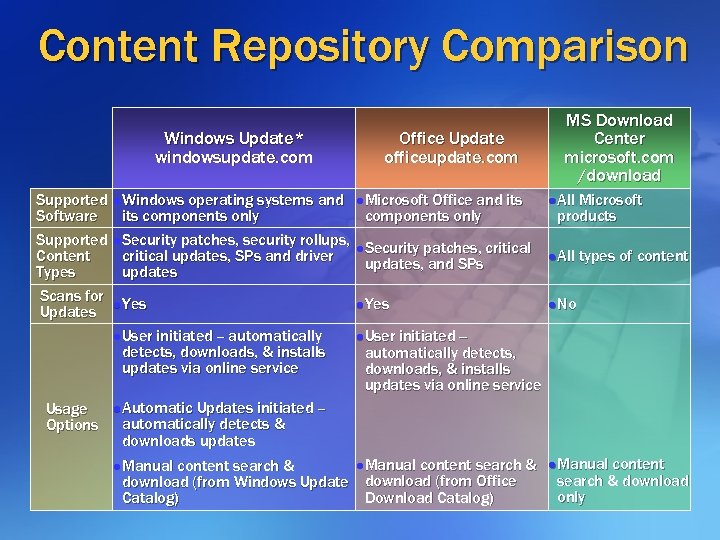 Content Repository Comparison Windows Update* windowsupdate. com Supported Software Supported Content Types Scans for Updates l Windows Office Update officeupdate. com operating systems and its components only l Security patches, security rollups, critical updates, SPs and driver updates l Microsoft l Yes l User initiated -- automatically detects, downloads, & installs updates via online service Usage Options Office and its components only MS Download Center microsoft. com /download l Security patches, critical updates, and SPs l All Microsoft products l All types of content l No initiated -automatically detects, downloads, & installs updates via online service l Automatic Updates initiated – automatically detects & downloads updates l Manual content search & download (from Windows Update download (from Office Download Catalog) l Manual content search & download only
Content Repository Comparison Windows Update* windowsupdate. com Supported Software Supported Content Types Scans for Updates l Windows Office Update officeupdate. com operating systems and its components only l Security patches, security rollups, critical updates, SPs and driver updates l Microsoft l Yes l User initiated -- automatically detects, downloads, & installs updates via online service Usage Options Office and its components only MS Download Center microsoft. com /download l Security patches, critical updates, and SPs l All Microsoft products l All types of content l No initiated -automatically detects, downloads, & installs updates via online service l Automatic Updates initiated – automatically detects & downloads updates l Manual content search & download (from Windows Update download (from Office Download Catalog) l Manual content search & download only
 SUS 1. 0: What it Does Deploys Windows security patches, security rollups, critical updates*, and service packs only Deploys above content for Windows 2000, Windows Server 2003 and Windows XP only Provides patch download, deployment, and installation configuration options New Update Bandwidth optimized content deployment Assess Provides central administrative control over which patches can be installed from Windows Update Identify Provides basic patch installation status logging Evaluate & Plan Deploy *Including critical driver updates
SUS 1. 0: What it Does Deploys Windows security patches, security rollups, critical updates*, and service packs only Deploys above content for Windows 2000, Windows Server 2003 and Windows XP only Provides patch download, deployment, and installation configuration options New Update Bandwidth optimized content deployment Assess Provides central administrative control over which patches can be installed from Windows Update Identify Provides basic patch installation status logging Evaluate & Plan Deploy *Including critical driver updates
 SUS Benefits Gives administrators control over patch & update management Works with Group Policy* to prevent installs of non-approved updates from Windows Update Allows staging & testing of updates before installation Simplifies & automates key aspects of the patch management process Ease of use alleviates difficulty of keeping supported systems up-to-date, reducing security risks *Note: Use of SUS does not require implementation of Active Directory or Group Policy
SUS Benefits Gives administrators control over patch & update management Works with Group Policy* to prevent installs of non-approved updates from Windows Update Allows staging & testing of updates before installation Simplifies & automates key aspects of the patch management process Ease of use alleviates difficulty of keeping supported systems up-to-date, reducing security risks *Note: Use of SUS does not require implementation of Active Directory or Group Policy
 SMS 2003: What it Does Identifies & deploys missing Windows and Office security patches on target systems Can deploy any patch, update, or application in Windows environments Inventory management & inventory based targeting of software installs New Update Assess Identify Evaluate & Plan Deploy Install verification and detailed reporting Flexible scheduling of content sync & installs Central, full administrative control over installs Bandwidth optimized content distribution Software metering and remote control capabilities
SMS 2003: What it Does Identifies & deploys missing Windows and Office security patches on target systems Can deploy any patch, update, or application in Windows environments Inventory management & inventory based targeting of software installs New Update Assess Identify Evaluate & Plan Deploy Install verification and detailed reporting Flexible scheduling of content sync & installs Central, full administrative control over installs Bandwidth optimized content distribution Software metering and remote control capabilities
 SMS 2003 Patch Management: Benefits Gives administrators control over patch management Allows staging & testing of updates before installation Fine-grained control of patch management options Automates key aspects of the patch management process Can update a broad range of Microsoft products (not limited to Windows and Office) Can also be used to update third party software and deploy & install any software update or application High level of flexibility via use of scripting
SMS 2003 Patch Management: Benefits Gives administrators control over patch management Allows staging & testing of updates before installation Fine-grained control of patch management options Automates key aspects of the patch management process Can update a broad range of Microsoft products (not limited to Windows and Office) Can also be used to update third party software and deploy & install any software update or application High level of flexibility via use of scripting
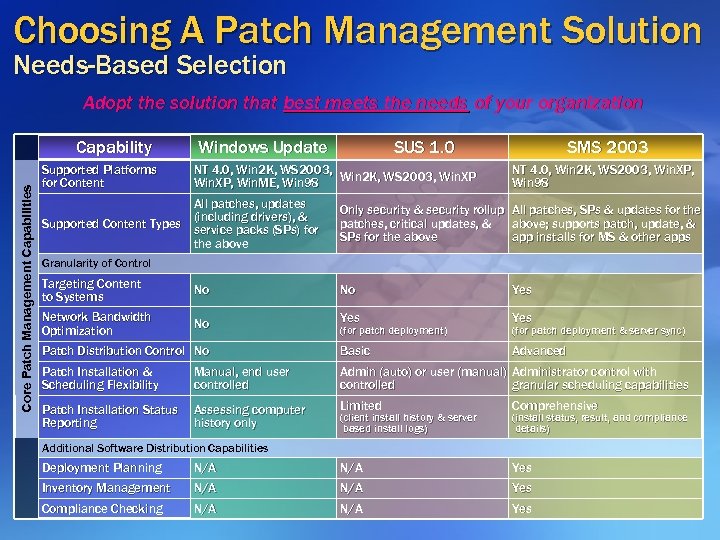 Choosing A Patch Management Solution Needs-Based Selection Adopt the solution that best meets the needs of your organization Core Patch Management Capabilities Capability Supported Platforms for Content Windows Update SUS 1. 0 NT 4. 0, Win 2 K, WS 2003, Win. XP, Win. ME, Win 98 All patches, updates (including drivers), & Supported Content Types service packs (SPs) for the above SMS 2003 NT 4. 0, Win 2 K, WS 2003, Win. XP, Win 98 Only security & security rollup patches, critical updates, & SPs for the above All patches, SPs & updates for the above; supports patch, update, & app installs for MS & other apps Granularity of Control Targeting Content to Systems No No Yes Network Bandwidth Optimization No Yes Patch Distribution Control No Basic Advanced Patch Installation & Scheduling Flexibility Manual, end user controlled Admin (auto) or user (manual) Administrator control with controlled granular scheduling capabilities Patch Installation Status Reporting Assessing computer history only Limited Comprehensive (for patch deployment) (client install history & server based install logs) (for patch deployment & server sync) (install status, result, and compliance details) Additional Software Distribution Capabilities Deployment Planning N/A Yes Inventory Management N/A Yes Compliance Checking N/A Yes
Choosing A Patch Management Solution Needs-Based Selection Adopt the solution that best meets the needs of your organization Core Patch Management Capabilities Capability Supported Platforms for Content Windows Update SUS 1. 0 NT 4. 0, Win 2 K, WS 2003, Win. XP, Win. ME, Win 98 All patches, updates (including drivers), & Supported Content Types service packs (SPs) for the above SMS 2003 NT 4. 0, Win 2 K, WS 2003, Win. XP, Win 98 Only security & security rollup patches, critical updates, & SPs for the above All patches, SPs & updates for the above; supports patch, update, & app installs for MS & other apps Granularity of Control Targeting Content to Systems No No Yes Network Bandwidth Optimization No Yes Patch Distribution Control No Basic Advanced Patch Installation & Scheduling Flexibility Manual, end user controlled Admin (auto) or user (manual) Administrator control with controlled granular scheduling capabilities Patch Installation Status Reporting Assessing computer history only Limited Comprehensive (for patch deployment) (client install history & server based install logs) (for patch deployment & server sync) (install status, result, and compliance details) Additional Software Distribution Capabilities Deployment Planning N/A Yes Inventory Management N/A Yes Compliance Checking N/A Yes
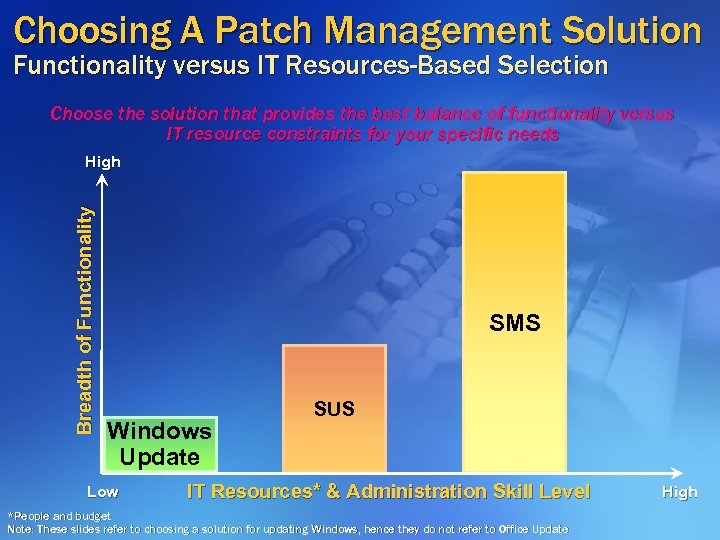 Choosing A Patch Management Solution Functionality versus IT Resources-Based Selection Choose the solution that provides the best balance of functionality versus IT resource constraints for your specific needs Breadth of Functionality High SMS Windows Update Low SUS IT Resources* & Administration Skill Level *People and budget Note: These slides refer to choosing a solution for updating Windows, hence they do not refer to Office Update High
Choosing A Patch Management Solution Functionality versus IT Resources-Based Selection Choose the solution that provides the best balance of functionality versus IT resource constraints for your specific needs Breadth of Functionality High SMS Windows Update Low SUS IT Resources* & Administration Skill Level *People and budget Note: These slides refer to choosing a solution for updating Windows, hence they do not refer to Office Update High
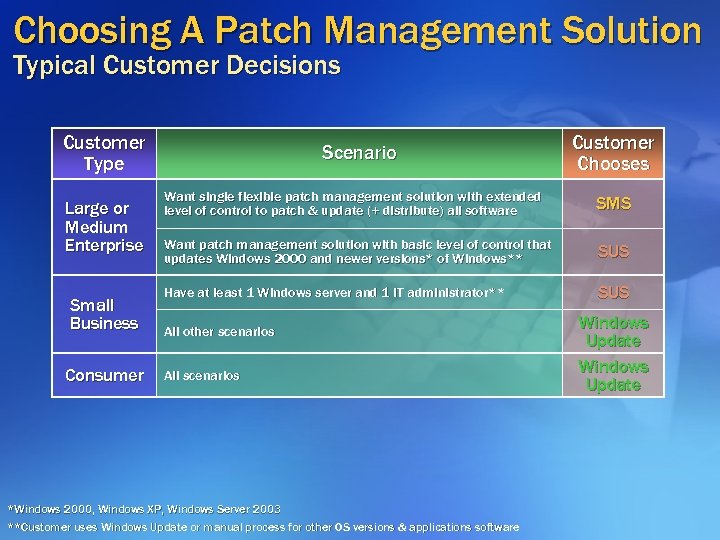 Choosing A Patch Management Solution Typical Customer Decisions Customer Type Large or Medium Enterprise Small Business Consumer Scenario Customer Chooses Want single flexible patch management solution with extended level of control to patch & update (+ distribute) all software SMS Want patch management solution with basic level of control that updates Windows 2000 and newer versions* of Windows** SUS Have at least 1 Windows server and 1 IT administrator** SUS All other scenarios All scenarios *Windows 2000, Windows XP, Windows Server 2003 **Customer uses Windows Update or manual process for other OS versions & applications software Windows Update
Choosing A Patch Management Solution Typical Customer Decisions Customer Type Large or Medium Enterprise Small Business Consumer Scenario Customer Chooses Want single flexible patch management solution with extended level of control to patch & update (+ distribute) all software SMS Want patch management solution with basic level of control that updates Windows 2000 and newer versions* of Windows** SUS Have at least 1 Windows server and 1 IT administrator** SUS All other scenarios All scenarios *Windows 2000, Windows XP, Windows Server 2003 **Customer uses Windows Update or manual process for other OS versions & applications software Windows Update
 Patch Management Guidance: What it Is Prescriptive guidance from Microsoft for effective patch management Uses Microsoft Operations Framework (MOF) Based on ITIL* (defacto standard for IT best practices) Details requirements for effective patch management: Technical & operational pre-requisites Operational processes & how technology supports them Daily, weekly, monthly & as-needed tasks to be performed Testing options Three patch management guidance offerings Microsoft Guide to Security Patch Management** Patch Management using Software Update Services*** Patch Management using Systems Management Server*** *Information Technology Infrastructure Library **Emphasizes security patching & overall security management ***Comprehensive coverage of patch management using the specified technology
Patch Management Guidance: What it Is Prescriptive guidance from Microsoft for effective patch management Uses Microsoft Operations Framework (MOF) Based on ITIL* (defacto standard for IT best practices) Details requirements for effective patch management: Technical & operational pre-requisites Operational processes & how technology supports them Daily, weekly, monthly & as-needed tasks to be performed Testing options Three patch management guidance offerings Microsoft Guide to Security Patch Management** Patch Management using Software Update Services*** Patch Management using Systems Management Server*** *Information Technology Infrastructure Library **Emphasizes security patching & overall security management ***Comprehensive coverage of patch management using the specified technology
 Solutions Component Roadmap
Solutions Component Roadmap
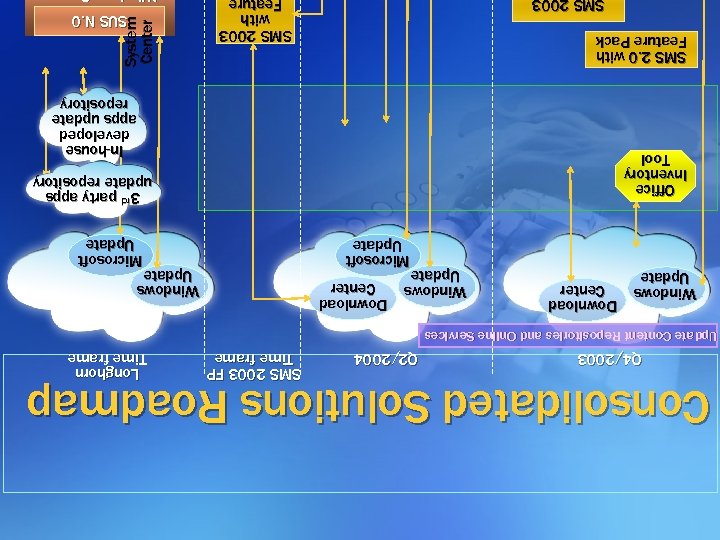 Consolidated Solutions Roadmap Q 4/2003 Q 2/2004 SMS 2003 FP Time frame Longhorn Time frame Update Content Repositories and Online Services Windows Update Download Center Windows Update Microsoft Update 3 rd party apps 3 party apps update repository Office Inventory Tool In-house developed apps update repository System Center SMS 2. 0 with Feature Pack SMS 2003 with Feature SMS 2003 SUS N. 0
Consolidated Solutions Roadmap Q 4/2003 Q 2/2004 SMS 2003 FP Time frame Longhorn Time frame Update Content Repositories and Online Services Windows Update Download Center Windows Update Microsoft Update 3 rd party apps 3 party apps update repository Office Inventory Tool In-house developed apps update repository System Center SMS 2. 0 with Feature Pack SMS 2003 with Feature SMS 2003 SUS N. 0
 Windows Update And Office Update Microsoft Update H 2 2004 Today Microsoft Update Online service and update repository for updating all Microsoftware Built on SUS infrastructure Includes automated scanning, update install, and reporting capabilities available in Windows Update Microsoft Update Office Windows Update SUS SMS
Windows Update And Office Update Microsoft Update H 2 2004 Today Microsoft Update Online service and update repository for updating all Microsoftware Built on SUS infrastructure Includes automated scanning, update install, and reporting capabilities available in Windows Update Microsoft Update Office Windows Update SUS SMS
 Patch Management Functionality Future Direction Longer-term (Longhorn time frame) SUS functionality integrated into Windows SUS supports updating of all Microsoftware SUS infrastructure can be used to build patch management solutions for 3 rd party and in-house built software SMS patch management built on SUS infrastructure and delivers advanced patch management functionality Near-term SUS 2. 0 (Spring 2004) Single infrastructure for patch management Support for additional Microsoft products Significant improvements in patch management functionality SMS 2003 Update Management Feature Pack (H 2 2004) Leverages SUS for update scanning & download Leverages SUS client (Automatic Updates) for installs
Patch Management Functionality Future Direction Longer-term (Longhorn time frame) SUS functionality integrated into Windows SUS supports updating of all Microsoftware SUS infrastructure can be used to build patch management solutions for 3 rd party and in-house built software SMS patch management built on SUS infrastructure and delivers advanced patch management functionality Near-term SUS 2. 0 (Spring 2004) Single infrastructure for patch management Support for additional Microsoft products Significant improvements in patch management functionality SMS 2003 Update Management Feature Pack (H 2 2004) Leverages SUS for update scanning & download Leverages SUS client (Automatic Updates) for installs
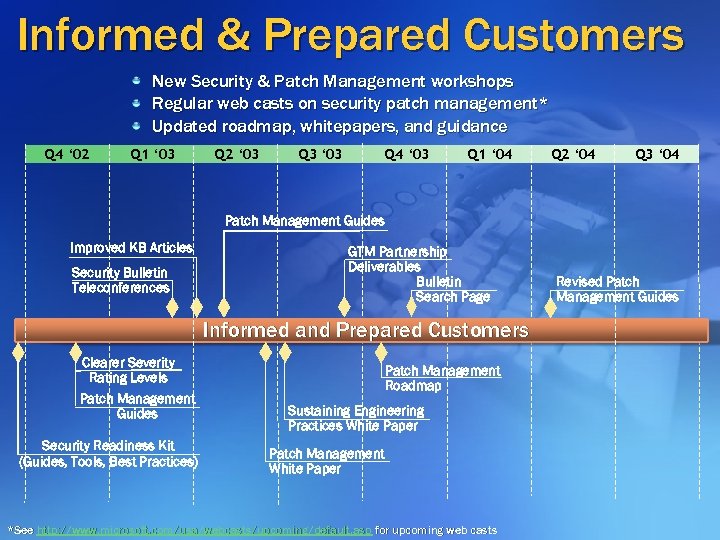 Informed & Prepared Customers New Security & Patch Management workshops Regular web casts on security patch management* Updated roadmap, whitepapers, and guidance Q 4 ‘ 02 Q 1 ‘ 03 Q 2 ‘ 03 Q 3 ‘ 03 Q 4 ‘ 03 Q 1 ‘ 04 Q 2 ‘ 04 Q 3 ‘ 04 Patch Management Guides Improved KB Articles Security Bulletin Teleconferences GTM Partnership Deliverables Bulletin Search Page Informed and Prepared Customers Clearer Severity Rating Levels Patch Management Guides Security Readiness Kit (Guides, Tools, Best Practices) Patch Management Roadmap Sustaining Engineering Practices White Paper Patch Management White Paper *See http: //www. microsoft. com/usa/webcasts/upcoming/default. asp for upcoming web casts Revised Patch Management Guides
Informed & Prepared Customers New Security & Patch Management workshops Regular web casts on security patch management* Updated roadmap, whitepapers, and guidance Q 4 ‘ 02 Q 1 ‘ 03 Q 2 ‘ 03 Q 3 ‘ 03 Q 4 ‘ 03 Q 1 ‘ 04 Q 2 ‘ 04 Q 3 ‘ 04 Patch Management Guides Improved KB Articles Security Bulletin Teleconferences GTM Partnership Deliverables Bulletin Search Page Informed and Prepared Customers Clearer Severity Rating Levels Patch Management Guides Security Readiness Kit (Guides, Tools, Best Practices) Patch Management Roadmap Sustaining Engineering Practices White Paper Patch Management White Paper *See http: //www. microsoft. com/usa/webcasts/upcoming/default. asp for upcoming web casts Revised Patch Management Guides
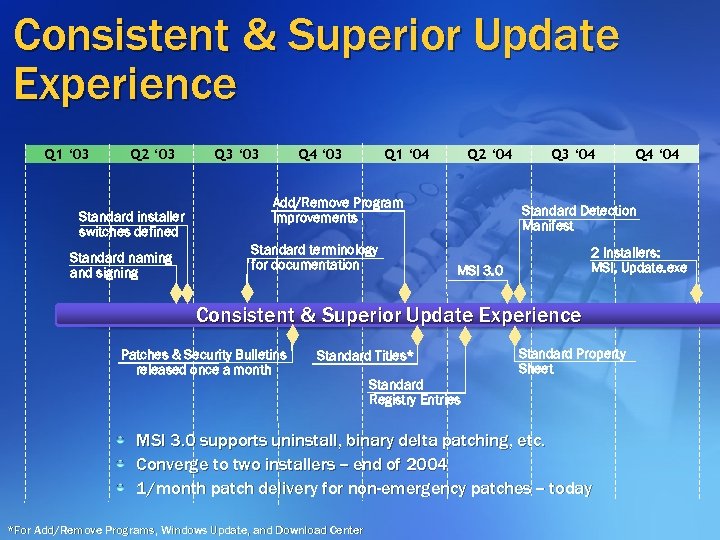 Consistent & Superior Update Experience Q 1 ‘ 03 Q 2 ‘ 03 Standard installer switches defined Standard naming and signing Q 3 ‘ 03 Q 4 ‘ 03 Q 1 ‘ 04 Q 2 ‘ 04 Add/Remove Program Improvements Standard terminology for documentation Q 3 ‘ 04 Standard Detection Manifest 2 Installers: MSI, Update. exe MSI 3. 0 Consistent & Superior Update Experience Patches & Security Bulletins released once a month Standard Titles* Standard Property Sheet Standard Registry Entries MSI 3. 0 supports uninstall, binary delta patching, etc. Converge to two installers -- end of 2004 1/month patch delivery for non-emergency patches -- today *For Add/Remove Programs, Windows Update, and Download Center Q 4 ‘ 04
Consistent & Superior Update Experience Q 1 ‘ 03 Q 2 ‘ 03 Standard installer switches defined Standard naming and signing Q 3 ‘ 03 Q 4 ‘ 03 Q 1 ‘ 04 Q 2 ‘ 04 Add/Remove Program Improvements Standard terminology for documentation Q 3 ‘ 04 Standard Detection Manifest 2 Installers: MSI, Update. exe MSI 3. 0 Consistent & Superior Update Experience Patches & Security Bulletins released once a month Standard Titles* Standard Property Sheet Standard Registry Entries MSI 3. 0 supports uninstall, binary delta patching, etc. Converge to two installers -- end of 2004 1/month patch delivery for non-emergency patches -- today *For Add/Remove Programs, Windows Update, and Download Center Q 4 ‘ 04
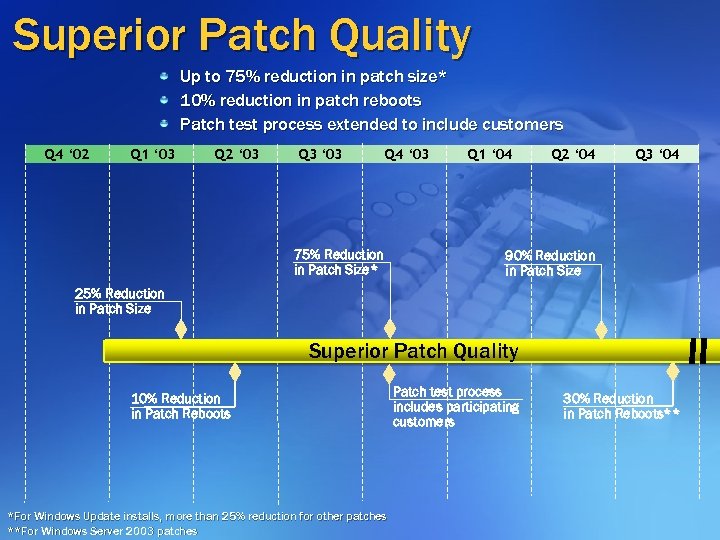 Superior Patch Quality Up to 75% reduction in patch size* 10% reduction in patch reboots Patch test process extended to include customers Q 4 ‘ 02 Q 1 ‘ 03 Q 2 ‘ 03 Q 3 ‘ 03 Q 4 ‘ 03 75% Reduction in Patch Size* Q 1 ‘ 04 Q 2 ‘ 04 Q 3 ‘ 04 90% Reduction in Patch Size 25% Reduction in Patch Size Superior Patch Quality 10% Reduction in Patch Reboots *For Windows Update installs, more than 25% reduction for other patches **For Windows Server 2003 patches Patch test process includes participating customers 30% Reduction in Patch Reboots**
Superior Patch Quality Up to 75% reduction in patch size* 10% reduction in patch reboots Patch test process extended to include customers Q 4 ‘ 02 Q 1 ‘ 03 Q 2 ‘ 03 Q 3 ‘ 03 Q 4 ‘ 03 75% Reduction in Patch Size* Q 1 ‘ 04 Q 2 ‘ 04 Q 3 ‘ 04 90% Reduction in Patch Size 25% Reduction in Patch Size Superior Patch Quality 10% Reduction in Patch Reboots *For Windows Update installs, more than 25% reduction for other patches **For Windows Server 2003 patches Patch test process includes participating customers 30% Reduction in Patch Reboots**
 Patch Management Tools In Depth Josh Pointer Senior Consultant II Microsoft Corporation
Patch Management Tools In Depth Josh Pointer Senior Consultant II Microsoft Corporation
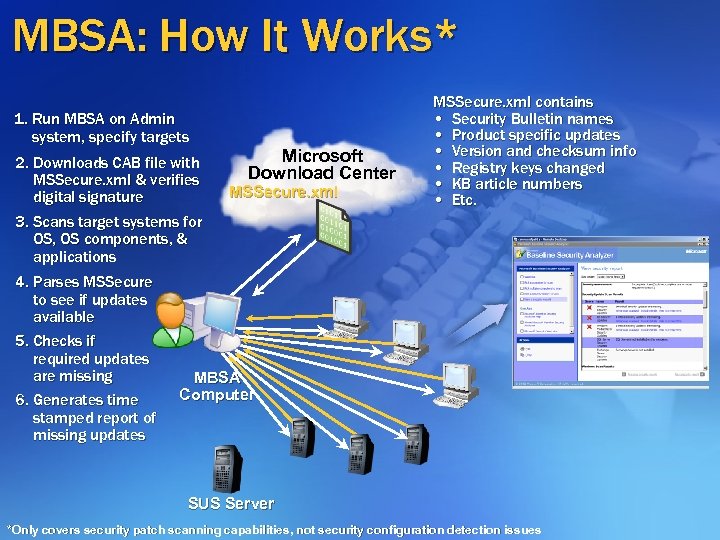 MBSA: How It Works* 1. Run MBSA on Admin system, specify targets 2. Downloads CAB file with MSSecure. xml & verifies digital signature 3. Scans target systems for OS, OS components, & applications 4. Parses MSSecure to see if updates available 5. Checks if required updates are missing 6. Generates time stamped report of missing updates Microsoft Download Center MSSecure. xml contains • Security Bulletin names • Product specific updates • Version and checksum info • Registry keys changed • KB article numbers • Etc. MBSA Computer SUS Server *Only covers security patch scanning capabilities, not security configuration detection issues
MBSA: How It Works* 1. Run MBSA on Admin system, specify targets 2. Downloads CAB file with MSSecure. xml & verifies digital signature 3. Scans target systems for OS, OS components, & applications 4. Parses MSSecure to see if updates available 5. Checks if required updates are missing 6. Generates time stamped report of missing updates Microsoft Download Center MSSecure. xml contains • Security Bulletin names • Product specific updates • Version and checksum info • Registry keys changed • KB article numbers • Etc. MBSA Computer SUS Server *Only covers security patch scanning capabilities, not security configuration detection issues
 MBSA Update Scanning Functionality Overall direction MBSA update scanning functionality integrated into Windows patch management functionality MBSA becomes Windows vulnerability assessment & mitigation engine Near- and Intermediate-term plans MBSA 1. 2 (Q 4 2003) Improves report consistency, product coverage, and locale support Integrates Office Update Inventory Tool MBSA 2. 0 (Q 2 2004) Update scanning functionality migrates to SUS 2. 0 / Microsoft Update MBSA leverages SUS 2. 0 for update scanning
MBSA Update Scanning Functionality Overall direction MBSA update scanning functionality integrated into Windows patch management functionality MBSA becomes Windows vulnerability assessment & mitigation engine Near- and Intermediate-term plans MBSA 1. 2 (Q 4 2003) Improves report consistency, product coverage, and locale support Integrates Office Update Inventory Tool MBSA 2. 0 (Q 2 2004) Update scanning functionality migrates to SUS 2. 0 / Microsoft Update MBSA leverages SUS 2. 0 for update scanning
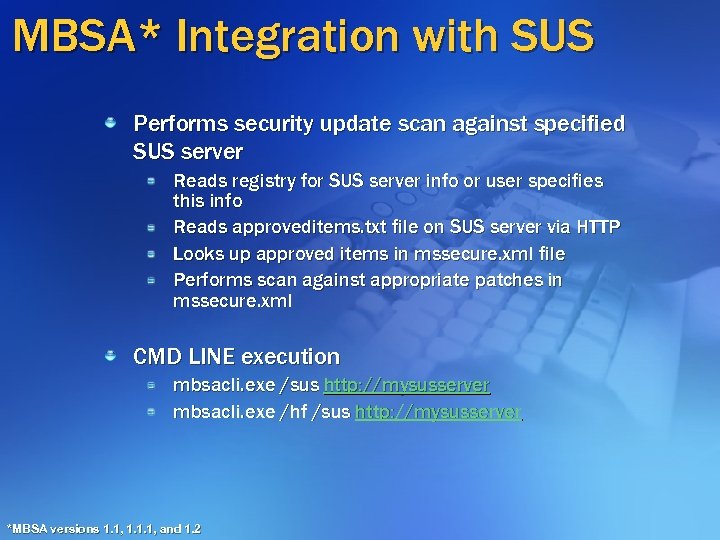 MBSA* Integration with SUS Performs security update scan against specified SUS server Reads registry for SUS server info or user specifies this info Reads approveditems. txt file on SUS server via HTTP Looks up approved items in mssecure. xml file Performs scan against appropriate patches in mssecure. xml CMD LINE execution mbsacli. exe /sus http: //mysusserver mbsacli. exe /hf /sus http: //mysusserver *MBSA versions 1. 1, 1. 1. 1, and 1. 2
MBSA* Integration with SUS Performs security update scan against specified SUS server Reads registry for SUS server info or user specifies this info Reads approveditems. txt file on SUS server via HTTP Looks up approved items in mssecure. xml file Performs scan against appropriate patches in mssecure. xml CMD LINE execution mbsacli. exe /sus http: //mysusserver mbsacli. exe /hf /sus http: //mysusserver *MBSA versions 1. 1, 1. 1. 1, and 1. 2
 MBSA Integration with SMS* Scans SMS clients for missing security updates using MBSA CLI Pushes mbsacli. exe to each client to do local scan (mbsacli. exe /hf) Parses textual output of patch numbers SMS Administrators can centrally distribute security updates to clients SMS 2. 0 and SMS 2003 use MBSA 1. 1. 1 *Requires SMS 2003 or SUS Feature Pack for SMS 2. 0
MBSA Integration with SMS* Scans SMS clients for missing security updates using MBSA CLI Pushes mbsacli. exe to each client to do local scan (mbsacli. exe /hf) Parses textual output of patch numbers SMS Administrators can centrally distribute security updates to clients SMS 2. 0 and SMS 2003 use MBSA 1. 1. 1 *Requires SMS 2003 or SUS Feature Pack for SMS 2. 0
 MBSA 1. 2 Better international support Japanese, French, German locale support Expanded product support MDAC, MSXML, JVM, Content Mgt Server, Commerce Server, Biz. Talk, Host Integration Server and Office Improved consistency of reports Support for alternate file versions in mssecure. xml (“OR” logic to consider multiple sets of file details) Handle case of non-security updates overwriting pervious security updates Handle multiple patches for a product targeted at different OS versions Handle uniproc/multiproc patches, QFE/GDR branch patches, etc. Office Update Inventory Tool integration (local scans only) Enhanced IE security zone checks
MBSA 1. 2 Better international support Japanese, French, German locale support Expanded product support MDAC, MSXML, JVM, Content Mgt Server, Commerce Server, Biz. Talk, Host Integration Server and Office Improved consistency of reports Support for alternate file versions in mssecure. xml (“OR” logic to consider multiple sets of file details) Handle case of non-security updates overwriting pervious security updates Handle multiple patches for a product targeted at different OS versions Handle uniproc/multiproc patches, QFE/GDR branch patches, etc. Office Update Inventory Tool integration (local scans only) Enhanced IE security zone checks
 MBSA 2. 0 Integration with SUS 2. 0 / Microsoft Update Centralized report storage (SQL, net share) Configurable/pluggable engine checks (engine framework, SDK) Integrates tools like IISLockdown & SQLScan Infrastructure to support future mitigation (via MOM, SMS, etc. )
MBSA 2. 0 Integration with SUS 2. 0 / Microsoft Update Centralized report storage (SQL, net share) Configurable/pluggable engine checks (engine framework, SDK) Integrates tools like IISLockdown & SQLScan Infrastructure to support future mitigation (via MOM, SMS, etc. )
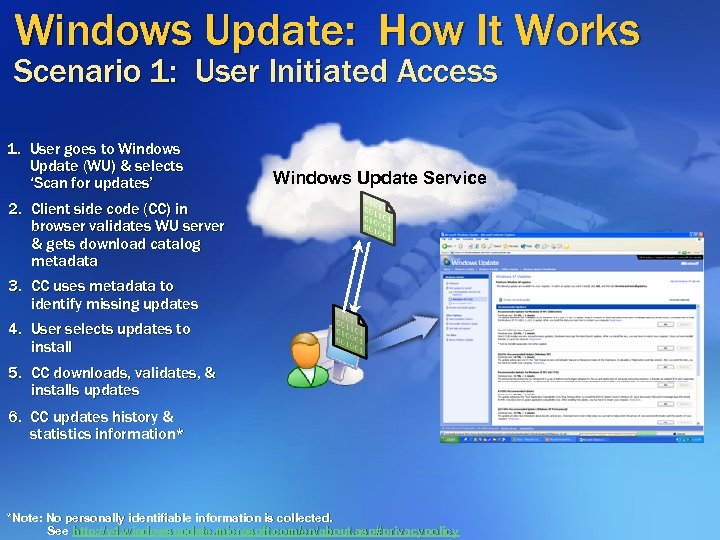 Windows Update: How It Works Scenario 1: User Initiated Access 1. User goes to Windows Update (WU) & selects ‘Scan for updates’ Windows Update Service 2. Client side code (CC) in browser validates WU server & gets download catalog metadata 3. CC uses metadata to identify missing updates 4. User selects updates to install 5. CC downloads, validates, & installs updates 6. CC updates history & statistics information* *Note: No personally identifiable information is collected. See http: //v 4. windowsupdate. microsoft. com/en/about. asp#privacypolicy
Windows Update: How It Works Scenario 1: User Initiated Access 1. User goes to Windows Update (WU) & selects ‘Scan for updates’ Windows Update Service 2. Client side code (CC) in browser validates WU server & gets download catalog metadata 3. CC uses metadata to identify missing updates 4. User selects updates to install 5. CC downloads, validates, & installs updates 6. CC updates history & statistics information* *Note: No personally identifiable information is collected. See http: //v 4. windowsupdate. microsoft. com/en/about. asp#privacypolicy
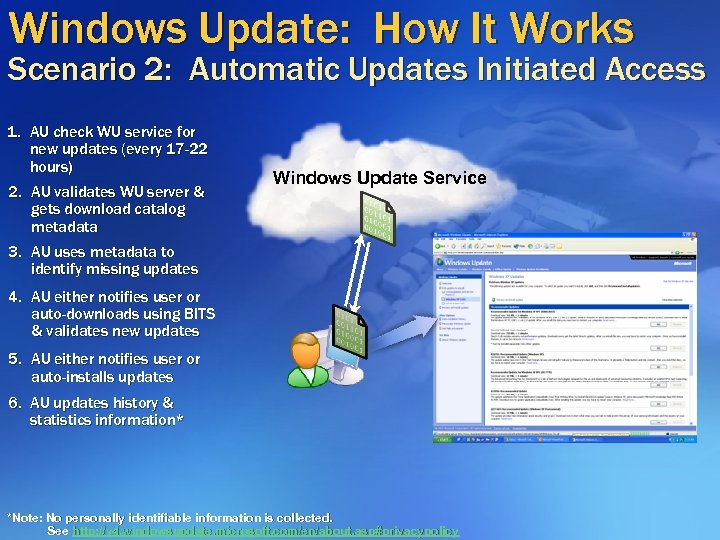 Windows Update: How It Works Scenario 2: Automatic Updates Initiated Access 1. AU check WU service for new updates (every 17 -22 hours) 2. AU validates WU server & gets download catalog metadata 3. AU uses metadata to identify missing updates Windows Update Service 4. AU either notifies user or auto-downloads using BITS & validates new updates 5. AU either notifies user or auto-installs updates 6. AU updates history & statistics information* *Note: No personally identifiable information is collected. See http: //v 4. windowsupdate. microsoft. com/en/about. asp#privacypolicy
Windows Update: How It Works Scenario 2: Automatic Updates Initiated Access 1. AU check WU service for new updates (every 17 -22 hours) 2. AU validates WU server & gets download catalog metadata 3. AU uses metadata to identify missing updates Windows Update Service 4. AU either notifies user or auto-downloads using BITS & validates new updates 5. AU either notifies user or auto-installs updates 6. AU updates history & statistics information* *Note: No personally identifiable information is collected. See http: //v 4. windowsupdate. microsoft. com/en/about. asp#privacypolicy
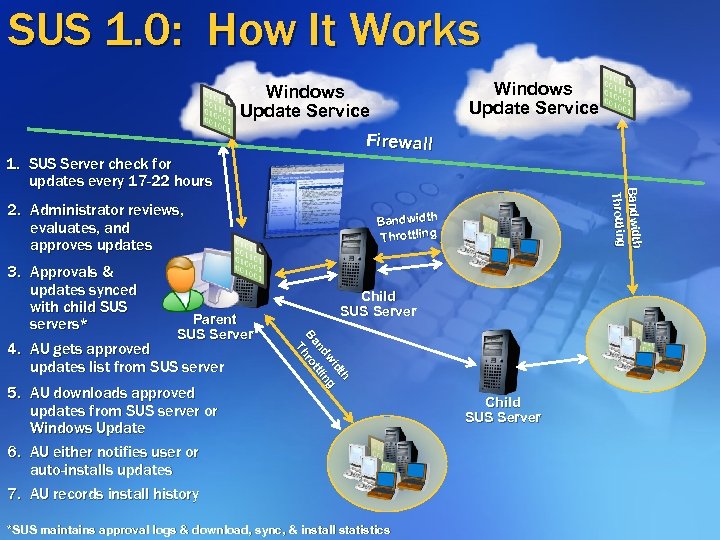 SUS 1. 0: How It Works Windows Update Service Firewall 2. Administrator reviews, evaluates, and approves updates 5. AU downloads approved updates from SUS server or Windows Update 6. AU either notifies user or auto-installs updates 7. AU records install history Bandwidth Throttling Child SUS Server h h dtt d wi ng w ng nd tttlli Ba hro B r T 3. Approvals & updates synced with child SUS Parent servers* SUS Server 4. AU gets approved updates list from SUS server th and Bandwidth g Throttling Thro 1. SUS Server check for updates every 17 -22 hours *SUS maintains approval logs & download, sync, & install statistics Child SUS Server
SUS 1. 0: How It Works Windows Update Service Firewall 2. Administrator reviews, evaluates, and approves updates 5. AU downloads approved updates from SUS server or Windows Update 6. AU either notifies user or auto-installs updates 7. AU records install history Bandwidth Throttling Child SUS Server h h dtt d wi ng w ng nd tttlli Ba hro B r T 3. Approvals & updates synced with child SUS Parent servers* SUS Server 4. AU gets approved updates list from SUS server th and Bandwidth g Throttling Thro 1. SUS Server check for updates every 17 -22 hours *SUS maintains approval logs & download, sync, & install statistics Child SUS Server
 Client Component: Automatic Updates Centrally configurable to get updates either from corporate SUS server or Windows Update service Can auto-download and install patches under admin control Consolidates multiple reboots to a single reboot when installing multiple patches Included in Windows 2000 SP 3, Windows XP SP 1, and Windows Server 2003 Localized in 24 languages
Client Component: Automatic Updates Centrally configurable to get updates either from corporate SUS server or Windows Update service Can auto-download and install patches under admin control Consolidates multiple reboots to a single reboot when installing multiple patches Included in Windows 2000 SP 3, Windows XP SP 1, and Windows Server 2003 Localized in 24 languages
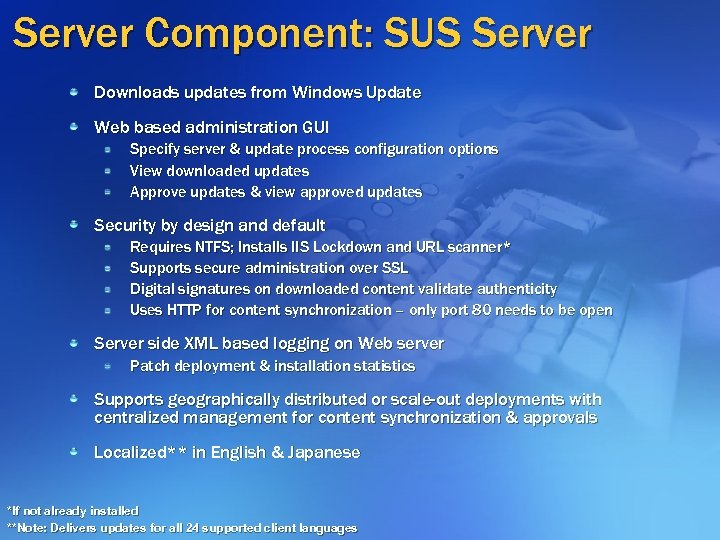 Server Component: SUS Server Downloads updates from Windows Update Web based administration GUI Specify server & update process configuration options View downloaded updates Approve updates & view approved updates Security by design and default Requires NTFS; Installs IIS Lockdown and URL scanner* Supports secure administration over SSL Digital signatures on downloaded content validate authenticity Uses HTTP for content synchronization – only port 80 needs to be open Server side XML based logging on Web server Patch deployment & installation statistics Supports geographically distributed or scale-out deployments with centralized management for content synchronization & approvals Localized** in English & Japanese *If not already installed **Note: Delivers updates for all 24 supported client languages
Server Component: SUS Server Downloads updates from Windows Update Web based administration GUI Specify server & update process configuration options View downloaded updates Approve updates & view approved updates Security by design and default Requires NTFS; Installs IIS Lockdown and URL scanner* Supports secure administration over SSL Digital signatures on downloaded content validate authenticity Uses HTTP for content synchronization – only port 80 needs to be open Server side XML based logging on Web server Patch deployment & installation statistics Supports geographically distributed or scale-out deployments with centralized management for content synchronization & approvals Localized** in English & Japanese *If not already installed **Note: Delivers updates for all 24 supported client languages
 SUS 2. 0 Support for additional Microsoft products Office 2003, SQL Server 2000, Exchange 2000, + additional products over time* Enhanced infrastructure for patch management Data Model - supercedence, update dependency & bundle relationships Server APIs (. NET) and remoteable Client APIs (COM) for flexibility Administrative control Pre-deployment checks; Initiate install & uninstall Set polling frequencies & install deadlines Target updates to groups of machines; Policy (AD) or list based group definitions Rules for auto-handing of updates Deployment & targeting Download subset of WU content (e. g. , Win. XP but not Win 2 K) Automatically deploys / updates SUS clients *Support for product versions listed here will be available when SUS 2. 0 is released; support for additional versions and products will be delivered over time without the need to upgrade or redeploy SUS 2. 0
SUS 2. 0 Support for additional Microsoft products Office 2003, SQL Server 2000, Exchange 2000, + additional products over time* Enhanced infrastructure for patch management Data Model - supercedence, update dependency & bundle relationships Server APIs (. NET) and remoteable Client APIs (COM) for flexibility Administrative control Pre-deployment checks; Initiate install & uninstall Set polling frequencies & install deadlines Target updates to groups of machines; Policy (AD) or list based group definitions Rules for auto-handing of updates Deployment & targeting Download subset of WU content (e. g. , Win. XP but not Win 2 K) Automatically deploys / updates SUS clients *Support for product versions listed here will be available when SUS 2. 0 is released; support for additional versions and products will be delivered over time without the need to upgrade or redeploy SUS 2. 0
 SUS 2. 0 (2) Bandwidth efficiency Uses BITS for client-server and server-server communication (download throttling & checkpoint restart, limit max bandwidth usage, etc. ) Support for ‘delta compression’ technologies Configurable update subscriptions Configurable to only download updates at deployment time Scale out Hierarchical & replica topology Summary event roll-up Status reporting Deployment status aggregation per machine/per update/per group Download / install success, failure, and error info Custom reports using read-only SQL queries
SUS 2. 0 (2) Bandwidth efficiency Uses BITS for client-server and server-server communication (download throttling & checkpoint restart, limit max bandwidth usage, etc. ) Support for ‘delta compression’ technologies Configurable update subscriptions Configurable to only download updates at deployment time Scale out Hierarchical & replica topology Summary event roll-up Status reporting Deployment status aggregation per machine/per update/per group Download / install success, failure, and error info Custom reports using read-only SQL queries
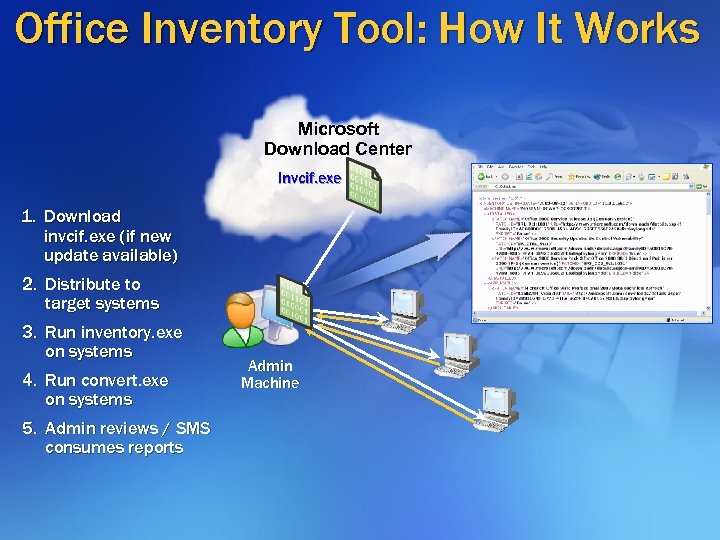 Office Inventory Tool: How It Works Microsoft Download Center Invcif. exe 1. Download invcif. exe (if new update available) 2. Distribute to target systems 3. Run inventory. exe on systems 4. Run convert. exe on systems 5. Admin reviews / SMS consumes reports Admin Machine
Office Inventory Tool: How It Works Microsoft Download Center Invcif. exe 1. Download invcif. exe (if new update available) 2. Distribute to target systems 3. Run inventory. exe on systems 4. Run convert. exe on systems 5. Admin reviews / SMS consumes reports Admin Machine
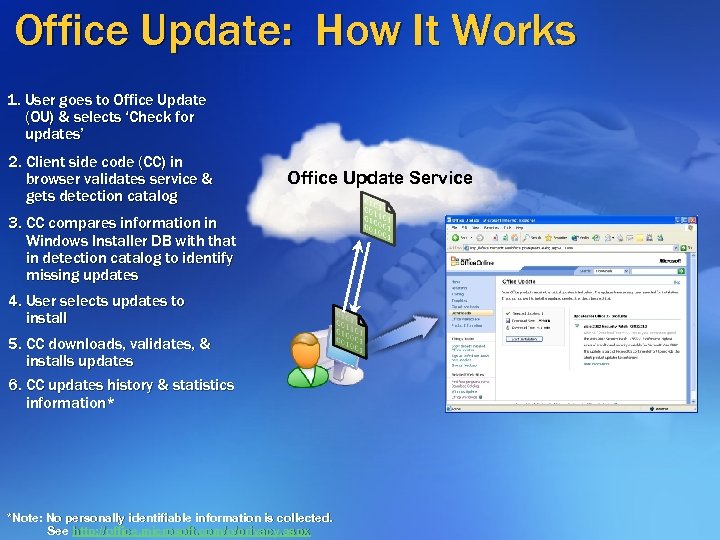 Office Update: How It Works 1. User goes to Office Update (OU) & selects ‘Check for updates’ 2. Client side code (CC) in browser validates service & gets detection catalog Office Update Service 3. CC compares information in Windows Installer DB with that in detection catalog to identify missing updates 4. User selects updates to install 5. CC downloads, validates, & installs updates 6. CC updates history & statistics information* *Note: No personally identifiable information is collected. See http: //office. microsoft. com/o/privacy. aspx
Office Update: How It Works 1. User goes to Office Update (OU) & selects ‘Check for updates’ 2. Client side code (CC) in browser validates service & gets detection catalog Office Update Service 3. CC compares information in Windows Installer DB with that in detection catalog to identify missing updates 4. User selects updates to install 5. CC downloads, validates, & installs updates 6. CC updates history & statistics information* *Note: No personally identifiable information is collected. See http: //office. microsoft. com/o/privacy. aspx
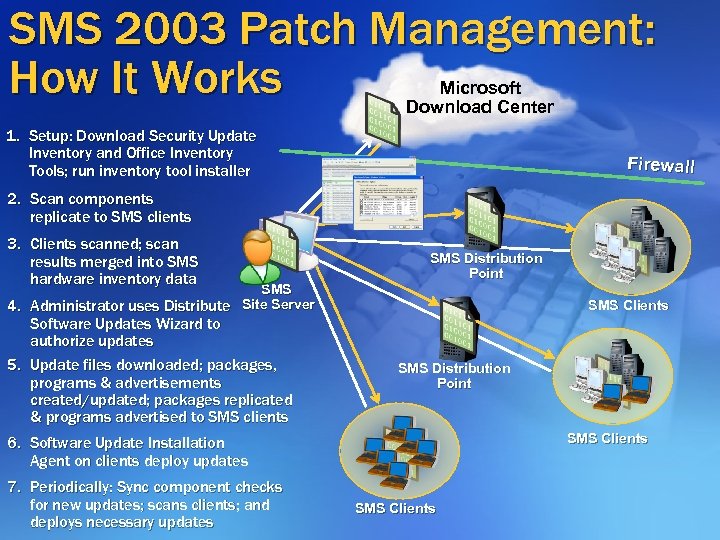 SMS 2003 Patch Management: How It Works Microsoft Download Center 1. Setup: Download Security Update Inventory and Office Inventory Tools; run inventory tool installer Firewall 2. Scan components replicate to SMS clients 3. Clients scanned; scan results merged into SMS hardware inventory data SMS 4. Administrator uses Distribute Site Server Software Updates Wizard to authorize updates 5. Update files downloaded; packages, programs & advertisements created/updated; packages replicated & programs advertised to SMS clients SMS Distribution Point SMS Clients 6. Software Update Installation Agent on clients deploy updates 7. Periodically: Sync component checks for new updates; scans clients; and deploys necessary updates SMS Clients
SMS 2003 Patch Management: How It Works Microsoft Download Center 1. Setup: Download Security Update Inventory and Office Inventory Tools; run inventory tool installer Firewall 2. Scan components replicate to SMS clients 3. Clients scanned; scan results merged into SMS hardware inventory data SMS 4. Administrator uses Distribute Site Server Software Updates Wizard to authorize updates 5. Update files downloaded; packages, programs & advertisements created/updated; packages replicated & programs advertised to SMS clients SMS Distribution Point SMS Clients 6. Software Update Installation Agent on clients deploy updates 7. Periodically: Sync component checks for new updates; scans clients; and deploys necessary updates SMS Clients
 SMS 2003 Patch Management: Functionality System scanning & patch content download Content from Microsoft Download Center MBSA & Office Inventory plug-ins scan for missing patches Supports updating of remote & mobile devices Updates various versions of Windows, Office, SQL, Exchange, and Windows Media Player without need for update packaging / scripting Administrator control Update targeting based on AD, non-AD groups, WMI properties; additional options via scripting Patches content is downloaded from a central SMS repository only when the deployment process is initiated by the SMS administrator Specific start and end times (change windows); multiple change windows Easily move patches from testing into production Reference system patch configurations can be used as a template to verify or enforce compliance of systems that must mimic reference system configuration
SMS 2003 Patch Management: Functionality System scanning & patch content download Content from Microsoft Download Center MBSA & Office Inventory plug-ins scan for missing patches Supports updating of remote & mobile devices Updates various versions of Windows, Office, SQL, Exchange, and Windows Media Player without need for update packaging / scripting Administrator control Update targeting based on AD, non-AD groups, WMI properties; additional options via scripting Patches content is downloaded from a central SMS repository only when the deployment process is initiated by the SMS administrator Specific start and end times (change windows); multiple change windows Easily move patches from testing into production Reference system patch configurations can be used as a template to verify or enforce compliance of systems that must mimic reference system configuration
 SMS 2003 Patch Management: Functionality (2) Patch download & installation Delta replication (site-site, server-server) of patches Uses BITS* for mobile / remote client-server Uses SMB* for LAN / priority situations Reminders and rescheduling of install / reboot & enforcement dates Optimized graceful reboots, but forced when enforcement date arrives Per-patch reboot-needed detection to reduce reboots Status & Compliance Reporting Deployment status as patches are attempted Standard and customized reports through read-only SQL queries Determine actual baselines in the environment before changing the environment SLA measurement and rate-of-spread *Requires SMS Advanced Client
SMS 2003 Patch Management: Functionality (2) Patch download & installation Delta replication (site-site, server-server) of patches Uses BITS* for mobile / remote client-server Uses SMB* for LAN / priority situations Reminders and rescheduling of install / reboot & enforcement dates Optimized graceful reboots, but forced when enforcement date arrives Per-patch reboot-needed detection to reduce reboots Status & Compliance Reporting Deployment status as patches are attempted Standard and customized reports through read-only SQL queries Determine actual baselines in the environment before changing the environment SLA measurement and rate-of-spread *Requires SMS Advanced Client
 SMS Update Management Futures Coming next SMS 2003 SP 1 Feature update to SMS 2003 Key enhancement: enable use SUS 2. 0 / Automatic Updates to scan systems, distribute updates, and install updates
SMS Update Management Futures Coming next SMS 2003 SP 1 Feature update to SMS 2003 Key enhancement: enable use SUS 2. 0 / Automatic Updates to scan systems, distribute updates, and install updates
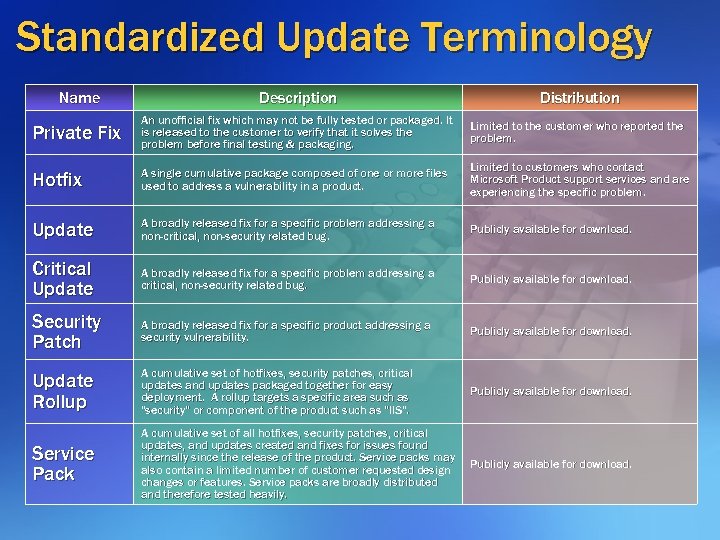 Standardized Update Terminology Name Description Distribution Private Fix An unofficial fix which may not be fully tested or packaged. It is released to the customer to verify that it solves the problem before final testing & packaging. Limited to the customer who reported the problem. Hotfix A single cumulative package composed of one or more files used to address a vulnerability in a product. Limited to customers who contact Microsoft Product support services and are experiencing the specific problem. Update A broadly released fix for a specific problem addressing a non-critical, non-security related bug. Publicly available for download. Critical Update A broadly released fix for a specific problem addressing a critical, non-security related bug. Publicly available for download. Security Patch A broadly released fix for a specific product addressing a security vulnerability. Publicly available for download. Update Rollup A cumulative set of hotfixes, security patches, critical hotfixes, updates and updates packaged together for easy deployment. A rollup targets a specific area such as "security" or component of the product such as "IIS". Publicly available for download. Service Pack A cumulative set of all hotfixes, security patches, critical hotfixes, updates, and updates created and fixes for issues found internally since the release of the product. Service packs may also contain a limited number of customer requested design changes or features. Service packs are broadly distributed and therefore tested heavily. Publicly available for download.
Standardized Update Terminology Name Description Distribution Private Fix An unofficial fix which may not be fully tested or packaged. It is released to the customer to verify that it solves the problem before final testing & packaging. Limited to the customer who reported the problem. Hotfix A single cumulative package composed of one or more files used to address a vulnerability in a product. Limited to customers who contact Microsoft Product support services and are experiencing the specific problem. Update A broadly released fix for a specific problem addressing a non-critical, non-security related bug. Publicly available for download. Critical Update A broadly released fix for a specific problem addressing a critical, non-security related bug. Publicly available for download. Security Patch A broadly released fix for a specific product addressing a security vulnerability. Publicly available for download. Update Rollup A cumulative set of hotfixes, security patches, critical hotfixes, updates and updates packaged together for easy deployment. A rollup targets a specific area such as "security" or component of the product such as "IIS". Publicly available for download. Service Pack A cumulative set of all hotfixes, security patches, critical hotfixes, updates, and updates created and fixes for issues found internally since the release of the product. Service packs may also contain a limited number of customer requested design changes or features. Service packs are broadly distributed and therefore tested heavily. Publicly available for download.
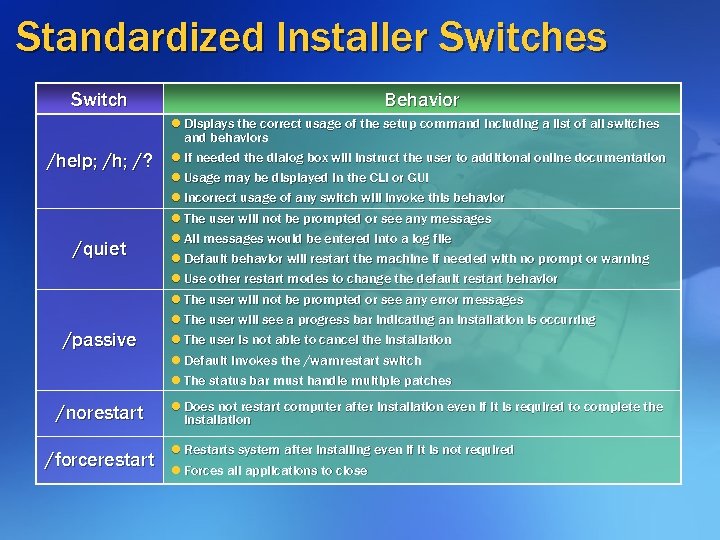 Standardized Installer Switches Switch /help; /h; /? /quiet /passive /norestart /forcerestart Behavior l Displays the correct usage of the setup command including a list of all switches and behaviors l If needed the dialog box will instruct the user to additional online documentation l Usage may be displayed in the CLI or GUI l Incorrect usage of any switch will invoke this behavior l The user will not be prompted or see any messages l All messages would be entered into a log file l Default behavior will restart the machine if needed with no prompt or warning l Use other restart modes to change the default restart behavior l The user will not be prompted or see any error messages l The user will see a progress bar indicating an installation is occurring l The user is not able to cancel the installation l Default invokes the /warnrestart switch l The status bar must handle multiple patches l Does not restart computer after installation even if it is required to complete the installation l Restarts system after installing even if it is not required l Forces all applications to close
Standardized Installer Switches Switch /help; /h; /? /quiet /passive /norestart /forcerestart Behavior l Displays the correct usage of the setup command including a list of all switches and behaviors l If needed the dialog box will instruct the user to additional online documentation l Usage may be displayed in the CLI or GUI l Incorrect usage of any switch will invoke this behavior l The user will not be prompted or see any messages l All messages would be entered into a log file l Default behavior will restart the machine if needed with no prompt or warning l Use other restart modes to change the default restart behavior l The user will not be prompted or see any error messages l The user will see a progress bar indicating an installation is occurring l The user is not able to cancel the installation l Default invokes the /warnrestart switch l The status bar must handle multiple patches l Does not restart computer after installation even if it is required to complete the installation l Restarts system after installing even if it is not required l Forces all applications to close
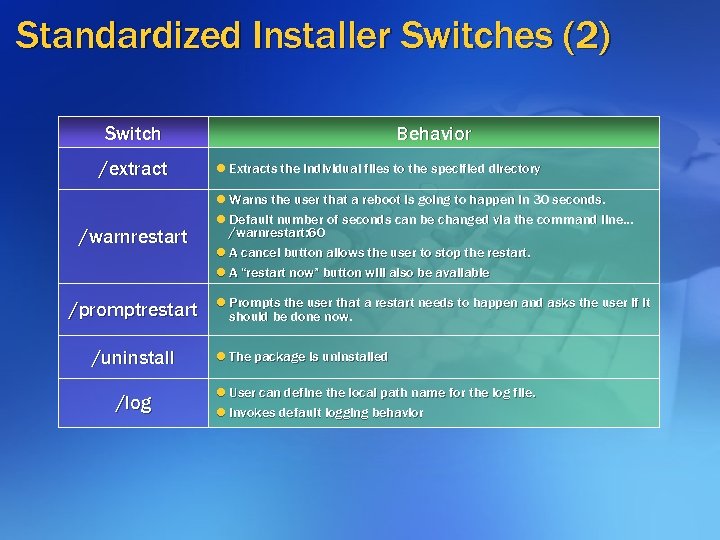 Standardized Installer Switches (2) Switch /extract /warnrestart /promptrestart /uninstall /log Behavior l Extracts the individual files to the specified directory l Warns the user that a reboot is going to happen in 30 seconds. l Default number of seconds can be changed via the command line… /warnrestart: 60 l A cancel button allows the user to stop the restart. l A “restart now” button will also be available l Prompts the user that a restart needs to happen and asks the user if it should be done now. l The package is uninstalled l User can define the local path name for the log file. l Invokes default logging behavior
Standardized Installer Switches (2) Switch /extract /warnrestart /promptrestart /uninstall /log Behavior l Extracts the individual files to the specified directory l Warns the user that a reboot is going to happen in 30 seconds. l Default number of seconds can be changed via the command line… /warnrestart: 60 l A cancel button allows the user to stop the restart. l A “restart now” button will also be available l Prompts the user that a restart needs to happen and asks the user if it should be done now. l The package is uninstalled l User can define the local path name for the log file. l Invokes default logging behavior
 Consolidating Multiple Reboots Increases system uptime since multiple reboots are eliminated when multiple hotfixes are being installed For Windows NT 4. 0 and Windows 2000 pre-SP 3 Use the QChain command line utility For Windows XP, Windows 2000 SP 3 and above, and Windows Server 2003 updates The hotfix installer for these OS versions includes functionality to support multiple hotfix installations
Consolidating Multiple Reboots Increases system uptime since multiple reboots are eliminated when multiple hotfixes are being installed For Windows NT 4. 0 and Windows 2000 pre-SP 3 Use the QChain command line utility For Windows XP, Windows 2000 SP 3 and above, and Windows Server 2003 updates The hotfix installer for these OS versions includes functionality to support multiple hotfix installations
 Consolidating Reboots for Hotfixes QChain for Win. NT and Win 2 K pre-SP 3 @echo off setlocal set PATHTOFIXES=E: Hotfix %PATHTOFIXES%patch_a. exe -z -m %PATHTOFIXES%patch_b. exe -z -m %PATHTOFIXES%patch_c. exe -z -m %PATHTOFIXES%qchain. exe • –m switch specifies unattended setup mode • –z switch suppresses system restart when install is completed
Consolidating Reboots for Hotfixes QChain for Win. NT and Win 2 K pre-SP 3 @echo off setlocal set PATHTOFIXES=E: Hotfix %PATHTOFIXES%patch_a. exe -z -m %PATHTOFIXES%patch_b. exe -z -m %PATHTOFIXES%patch_c. exe -z -m %PATHTOFIXES%qchain. exe • –m switch specifies unattended setup mode • –z switch suppresses system restart when install is completed
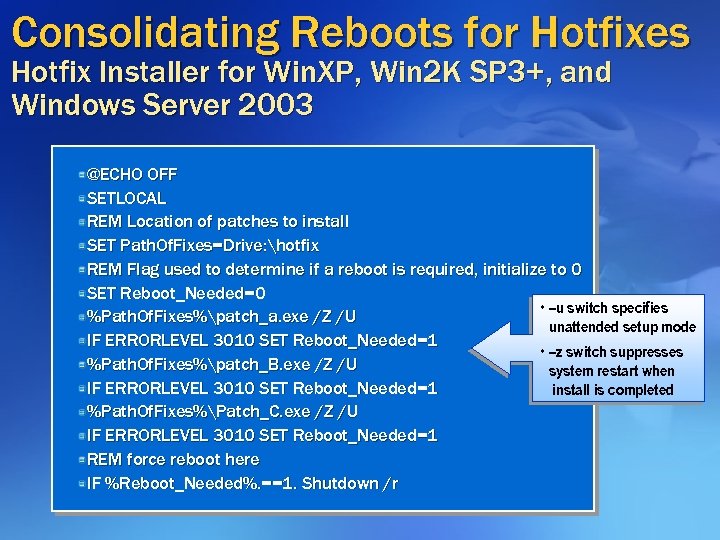 Consolidating Reboots for Hotfixes Hotfix Installer for Win. XP, Win 2 K SP 3+, and Windows Server 2003 @ECHO OFF SETLOCAL REM Location of patches to install SET Path. Of. Fixes=Drive: hotfix REM Flag used to determine if a reboot is required, initialize to 0 SET Reboot_Needed=0 • –u switch specifies %Path. Of. Fixes%patch_a. exe /Z /U unattended setup mode IF ERRORLEVEL 3010 SET Reboot_Needed=1 • –z switch suppresses %Path. Of. Fixes%patch_B. exe /Z /U system restart when IF ERRORLEVEL 3010 SET Reboot_Needed=1 install is completed %Path. Of. Fixes%Patch_C. exe /Z /U IF ERRORLEVEL 3010 SET Reboot_Needed=1 REM force reboot here IF %Reboot_Needed%. ==1. Shutdown /r
Consolidating Reboots for Hotfixes Hotfix Installer for Win. XP, Win 2 K SP 3+, and Windows Server 2003 @ECHO OFF SETLOCAL REM Location of patches to install SET Path. Of. Fixes=Drive: hotfix REM Flag used to determine if a reboot is required, initialize to 0 SET Reboot_Needed=0 • –u switch specifies %Path. Of. Fixes%patch_a. exe /Z /U unattended setup mode IF ERRORLEVEL 3010 SET Reboot_Needed=1 • –z switch suppresses %Path. Of. Fixes%patch_B. exe /Z /U system restart when IF ERRORLEVEL 3010 SET Reboot_Needed=1 install is completed %Path. Of. Fixes%Patch_C. exe /Z /U IF ERRORLEVEL 3010 SET Reboot_Needed=1 REM force reboot here IF %Reboot_Needed%. ==1. Shutdown /r
 © 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.
© 2003 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary.


