447e262079083c580230fc20454bb378.ppt
- Количество слайдов: 128
 Microsoft Internet Security and Acceleration (ISA) Server 2004 Powerful Protection for Microsoft Applications
Microsoft Internet Security and Acceleration (ISA) Server 2004 Powerful Protection for Microsoft Applications
 Learning Objectives Protecting Microsoft Applications with ISA Server 2004 This training will show the solutions, advantages, benefits, competitive landscape, and selling opportunities for Microsoft® ISA Server 2004, as well as provide customerready resources. 2
Learning Objectives Protecting Microsoft Applications with ISA Server 2004 This training will show the solutions, advantages, benefits, competitive landscape, and selling opportunities for Microsoft® ISA Server 2004, as well as provide customerready resources. 2
 Agenda 1. ISA Server 2004 Overview Advanced Protection, Ease of Use, Fast Secure Access (Slides 4– 43) 2. Protecting Microsoft Applications Technical Details (Slides 44– 94) 3. Selling Strategies and Partner Offerings (Slides 95– 124) 4. Introduction to Hands-on Labs (Slides 125 -127) 3
Agenda 1. ISA Server 2004 Overview Advanced Protection, Ease of Use, Fast Secure Access (Slides 4– 43) 2. Protecting Microsoft Applications Technical Details (Slides 44– 94) 3. Selling Strategies and Partner Offerings (Slides 95– 124) 4. Introduction to Hands-on Labs (Slides 125 -127) 3
 1. ISA Server 2004 Overview Advanced Protection, Ease of Use, Fast Secure Access
1. ISA Server 2004 Overview Advanced Protection, Ease of Use, Fast Secure Access
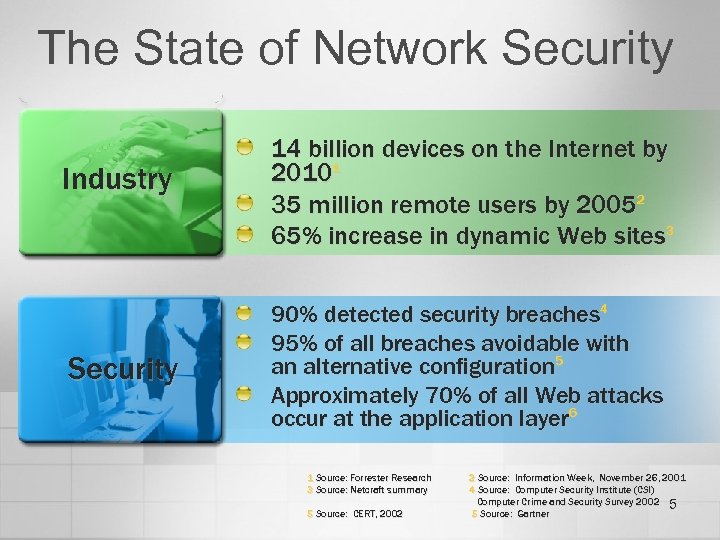 The State of Network Security Industry Security 14 billion devices on the Internet by 20101 35 million remote users by 20052 65% increase in dynamic Web sites 3 90% detected security breaches 4 95% of all breaches avoidable with an alternative configuration 5 Approximately 70% of all Web attacks occur at the application layer 6 1 Source: Forrester Research 3 Source: Netcraft summary 5 Source: CERT, 2002 2 Source: Information Week, November 26, 2001 4 Source: Computer Security Institute (CSI) Computer Crime and Security Survey 2002 5 5 Source: Gartner
The State of Network Security Industry Security 14 billion devices on the Internet by 20101 35 million remote users by 20052 65% increase in dynamic Web sites 3 90% detected security breaches 4 95% of all breaches avoidable with an alternative configuration 5 Approximately 70% of all Web attacks occur at the application layer 6 1 Source: Forrester Research 3 Source: Netcraft summary 5 Source: CERT, 2002 2 Source: Information Week, November 26, 2001 4 Source: Computer Security Institute (CSI) Computer Crime and Security Survey 2002 5 5 Source: Gartner
 The Role of Firewalls ¢ ¢ Firewalls block attacks before they reach their target Firewalls can protect multiple systems n n ¢ Firewalls can act as a central access point n ¢ ¢ Firewall protection can buy time before all protected servers are secured Firewalls can help protect client computers that are not properly protected Combined firewall and VPN gateway Firewalls provide centralized logging of network access Crucial component of defense-in-depth 6
The Role of Firewalls ¢ ¢ Firewalls block attacks before they reach their target Firewalls can protect multiple systems n n ¢ Firewalls can act as a central access point n ¢ ¢ Firewall protection can buy time before all protected servers are secured Firewalls can help protect client computers that are not properly protected Combined firewall and VPN gateway Firewalls provide centralized logging of network access Crucial component of defense-in-depth 6
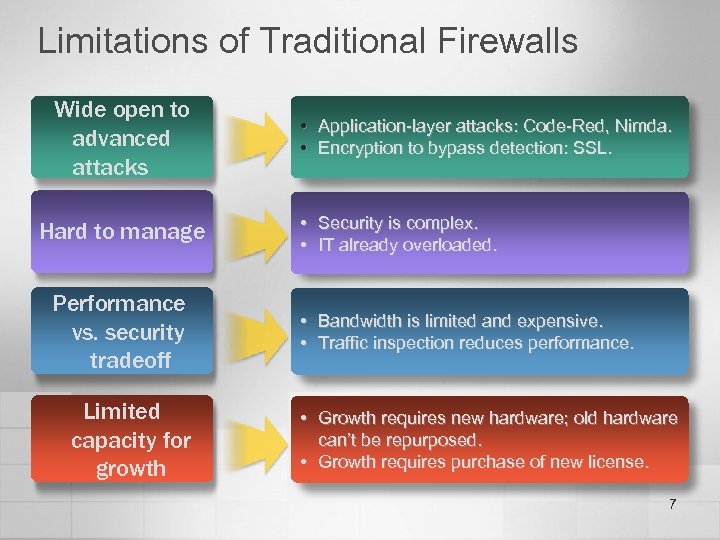 Limitations of Traditional Firewalls Wide open to advanced attacks Hard to manage Performance vs. security tradeoff Limited capacity for growth • Application-layer attacks: Code-Red, Nimda. • Encryption to bypass detection: SSL. • Security is complex. • IT already overloaded. • Bandwidth is limited and expensive. • Traffic inspection reduces performance. • Growth requires new hardware; old hardware can’t be repurposed. • Growth requires purchase of new license. 7
Limitations of Traditional Firewalls Wide open to advanced attacks Hard to manage Performance vs. security tradeoff Limited capacity for growth • Application-layer attacks: Code-Red, Nimda. • Encryption to bypass detection: SSL. • Security is complex. • IT already overloaded. • Bandwidth is limited and expensive. • Traffic inspection reduces performance. • Growth requires new hardware; old hardware can’t be repurposed. • Growth requires purchase of new license. 7
 What Is ISA Server 2004? Microsoft ISA Server 2004 is Microsoft’s flagship security product and a cornerstone of the company’s Trustworthy Computing initiative. ISA Server 2004 is an applicationlayer firewall, VPN, and Web-cache solution that provides advanced protection, fast and secure Web access, and is very easy to use. ISA Server 2004 can provide security as a perimeter firewall at the Internet edge, can be used to protect Microsoft applications such as Microsoft Exchange and other servers on the internal network, as well as be configured as a Web-caching server to ensure fast, secure Web access—all in one package. 8
What Is ISA Server 2004? Microsoft ISA Server 2004 is Microsoft’s flagship security product and a cornerstone of the company’s Trustworthy Computing initiative. ISA Server 2004 is an applicationlayer firewall, VPN, and Web-cache solution that provides advanced protection, fast and secure Web access, and is very easy to use. ISA Server 2004 can provide security as a perimeter firewall at the Internet edge, can be used to protect Microsoft applications such as Microsoft Exchange and other servers on the internal network, as well as be configured as a Web-caching server to ensure fast, secure Web access—all in one package. 8
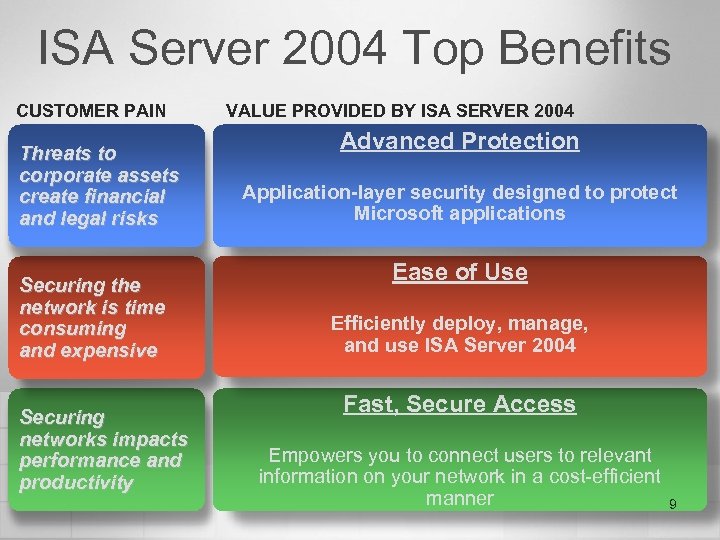 ISA Server 2004 Top Benefits CUSTOMER PAIN Threats to corporate assets create financial and legal risks Securing the network is time consuming and expensive Securing networks impacts performance and productivity VALUE PROVIDED BY ISA SERVER 2004 Advanced Protection Application-layer security designed to protect Microsoft applications Ease of Use Efficiently deploy, manage, and use ISA Server 2004 Fast, Secure Access Empowers you to connect users to relevant information on your network in a cost-efficient manner 9
ISA Server 2004 Top Benefits CUSTOMER PAIN Threats to corporate assets create financial and legal risks Securing the network is time consuming and expensive Securing networks impacts performance and productivity VALUE PROVIDED BY ISA SERVER 2004 Advanced Protection Application-layer security designed to protect Microsoft applications Ease of Use Efficiently deploy, manage, and use ISA Server 2004 Fast, Secure Access Empowers you to connect users to relevant information on your network in a cost-efficient manner 9
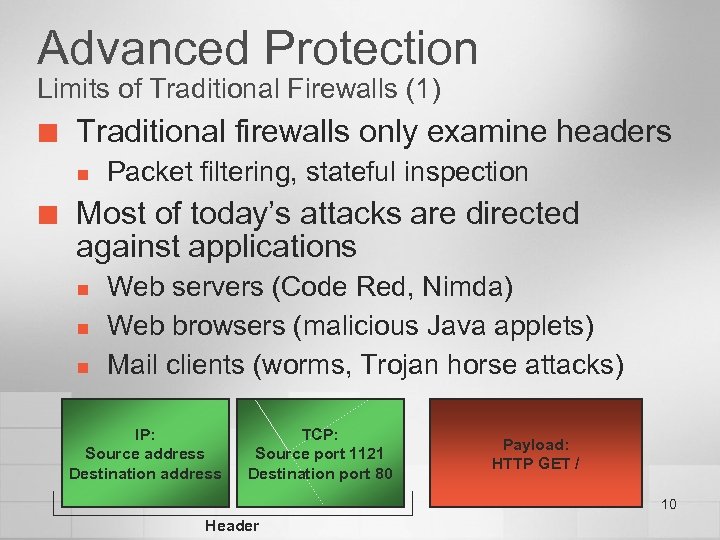 Advanced Protection Limits of Traditional Firewalls (1) ¢ Traditional firewalls only examine headers n ¢ Packet filtering, stateful inspection Most of today’s attacks are directed against applications n n n Web servers (Code Red, Nimda) Web browsers (malicious Java applets) Mail clients (worms, Trojan horse attacks) IP: Source address Destination address TCP: Source port 1121 Destination port 80 Payload: HTTP GET / 10 Header
Advanced Protection Limits of Traditional Firewalls (1) ¢ Traditional firewalls only examine headers n ¢ Packet filtering, stateful inspection Most of today’s attacks are directed against applications n n n Web servers (Code Red, Nimda) Web browsers (malicious Java applets) Mail clients (worms, Trojan horse attacks) IP: Source address Destination address TCP: Source port 1121 Destination port 80 Payload: HTTP GET / 10 Header
 Advanced Protection Limits of Traditional Firewalls (2) ¢ Applications encapsulate traffic in HTTP traffic n ¢ ¢ Examples: Peer-to-peer, instant messaging Encrypted traffic can’t be inspected by traditional firewalls Dynamic port assignments require too many incoming ports to be opened n Examples: FTP, RPC Packet filtering and stateful inspection are not enough to protect against today’s attacks! 11
Advanced Protection Limits of Traditional Firewalls (2) ¢ Applications encapsulate traffic in HTTP traffic n ¢ ¢ Examples: Peer-to-peer, instant messaging Encrypted traffic can’t be inspected by traditional firewalls Dynamic port assignments require too many incoming ports to be opened n Examples: FTP, RPC Packet filtering and stateful inspection are not enough to protect against today’s attacks! 11
 Advanced Protection Application-Layer Filtering with ISA Server 2004 ¢ ¢ Application-layer filtering in ISA Server 2004 examines the payload ISA Server 2004 blocks traffic that uses allowed ports but contains disallowed data n ¢ Example: Traffic to a Web server that contains a Web server attack ISA Server 2004 allows you to use complex protocols across a firewall “To provide edge security in this application-centric world…application-level firewalls will be required…. ” —John Pescatore, Gartner 12
Advanced Protection Application-Layer Filtering with ISA Server 2004 ¢ ¢ Application-layer filtering in ISA Server 2004 examines the payload ISA Server 2004 blocks traffic that uses allowed ports but contains disallowed data n ¢ Example: Traffic to a Web server that contains a Web server attack ISA Server 2004 allows you to use complex protocols across a firewall “To provide edge security in this application-centric world…application-level firewalls will be required…. ” —John Pescatore, Gartner 12
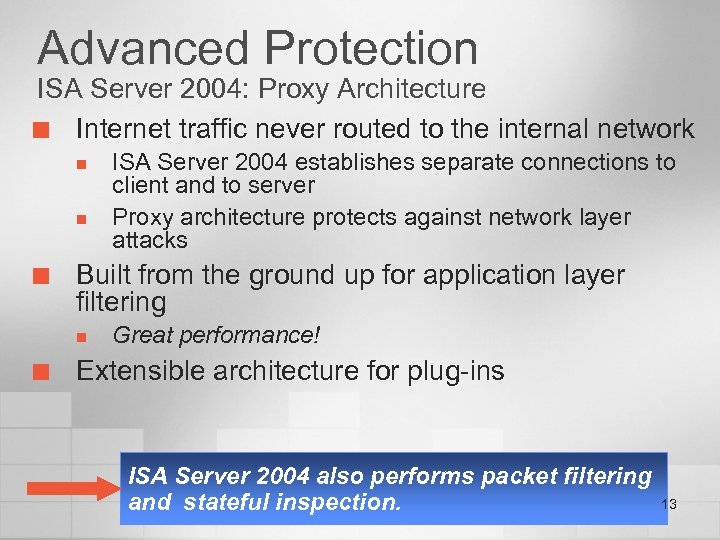 Advanced Protection ISA Server 2004: Proxy Architecture ¢ Internet traffic never routed to the internal network n n ¢ Built from the ground up for application layer filtering n ¢ ISA Server 2004 establishes separate connections to client and to server Proxy architecture protects against network layer attacks Great performance! Extensible architecture for plug-ins ISA Server 2004 also performs packet filtering and stateful inspection. 13
Advanced Protection ISA Server 2004: Proxy Architecture ¢ Internet traffic never routed to the internal network n n ¢ Built from the ground up for application layer filtering n ¢ ISA Server 2004 establishes separate connections to client and to server Proxy architecture protects against network layer attacks Great performance! Extensible architecture for plug-ins ISA Server 2004 also performs packet filtering and stateful inspection. 13
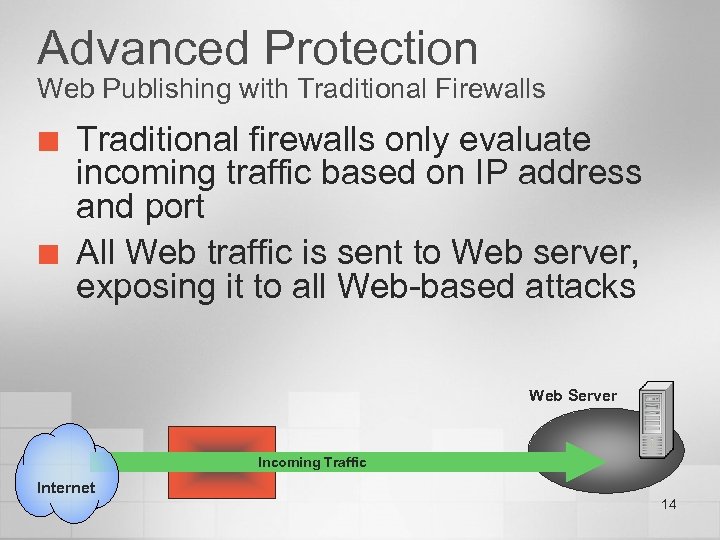 Advanced Protection Web Publishing with Traditional Firewalls ¢ ¢ Traditional firewalls only evaluate incoming traffic based on IP address and port All Web traffic is sent to Web server, exposing it to all Web-based attacks Web Server Incoming Traffic Internet 14
Advanced Protection Web Publishing with Traditional Firewalls ¢ ¢ Traditional firewalls only evaluate incoming traffic based on IP address and port All Web traffic is sent to Web server, exposing it to all Web-based attacks Web Server Incoming Traffic Internet 14
 Advanced Protection Secure Web Publishing with ISA Server 2004 ¢ ¢ ¢ Inspection of Web request and responses and protection of Microsoft Internet Information Services (IIS) from exploits Blocking of malformed URLs to stop Webbased attacks Optional inspection of incoming SSL traffic Web Server Incoming Traffic Internet 15
Advanced Protection Secure Web Publishing with ISA Server 2004 ¢ ¢ ¢ Inspection of Web request and responses and protection of Microsoft Internet Information Services (IIS) from exploits Blocking of malformed URLs to stop Webbased attacks Optional inspection of incoming SSL traffic Web Server Incoming Traffic Internet 15
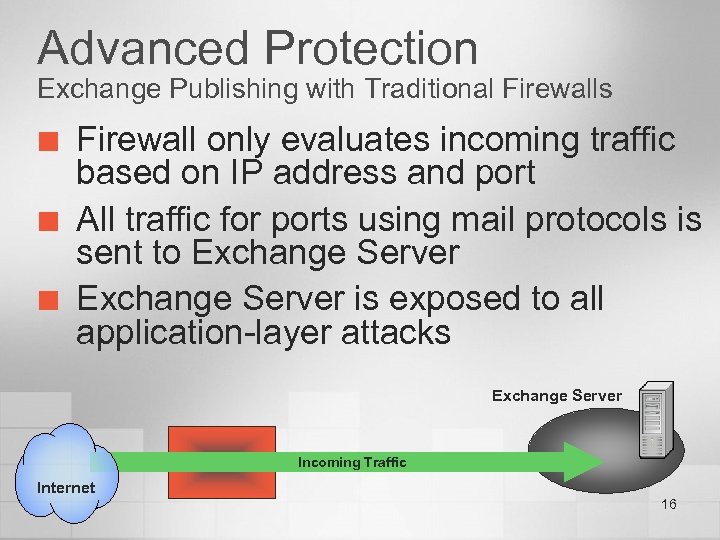 Advanced Protection Exchange Publishing with Traditional Firewalls ¢ ¢ ¢ Firewall only evaluates incoming traffic based on IP address and port All traffic for ports using mail protocols is sent to Exchange Server is exposed to all application-layer attacks Exchange Server Incoming Traffic Internet 16
Advanced Protection Exchange Publishing with Traditional Firewalls ¢ ¢ ¢ Firewall only evaluates incoming traffic based on IP address and port All traffic for ports using mail protocols is sent to Exchange Server is exposed to all application-layer attacks Exchange Server Incoming Traffic Internet 16
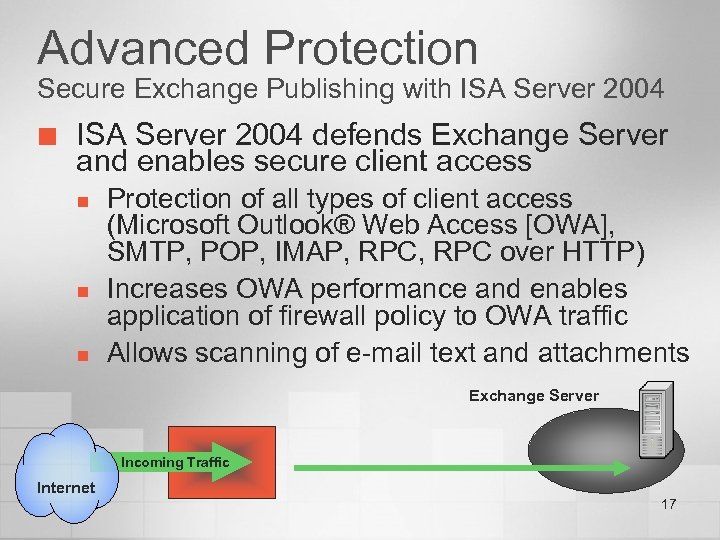 Advanced Protection Secure Exchange Publishing with ISA Server 2004 ¢ ISA Server 2004 defends Exchange Server and enables secure client access n n n Protection of all types of client access (Microsoft Outlook® Web Access [OWA], SMTP, POP, IMAP, RPC over HTTP) Increases OWA performance and enables application of firewall policy to OWA traffic Allows scanning of e-mail text and attachments Exchange Server Incoming Traffic Internet 17
Advanced Protection Secure Exchange Publishing with ISA Server 2004 ¢ ISA Server 2004 defends Exchange Server and enables secure client access n n n Protection of all types of client access (Microsoft Outlook® Web Access [OWA], SMTP, POP, IMAP, RPC over HTTP) Increases OWA performance and enables application of firewall policy to OWA traffic Allows scanning of e-mail text and attachments Exchange Server Incoming Traffic Internet 17
 Advanced Protection The Need to Provide Secure VPN Access ¢ Companies need to provide remote access n n n ¢ VPNs are a cost-effective way to leverage the Internet n n ¢ Branch offices Business partners Home offices and traveling users No dial-up connections or leased lines required VPNs use existing Internet connection VPNs create security concerns and increase administrative work n n VPNs create new administration tasks VPNs create new ways to access the corporate network ISA Server 2004 simplifies VPN administration and provides VPN security 18
Advanced Protection The Need to Provide Secure VPN Access ¢ Companies need to provide remote access n n n ¢ VPNs are a cost-effective way to leverage the Internet n n ¢ Branch offices Business partners Home offices and traveling users No dial-up connections or leased lines required VPNs use existing Internet connection VPNs create security concerns and increase administrative work n n VPNs create new administration tasks VPNs create new ways to access the corporate network ISA Server 2004 simplifies VPN administration and provides VPN security 18
 Advanced Protection How ISA Server 2004 Secures VPN Client Connections ¢ ¢ All communications over the Internet are encrypted Broad protocol support n n ¢ Authentication n ¢ ¢ PPTP and L 2 TP/IPSec NAT traversal (NAT-T) for connectivity across any network (requires Microsoft Windows Server™ 2003) Microsoft Active Directory® uses existing Microsoft Windows® accounts, supports PKI for two-factor authentication RADIUS uses non-Windows-based accounts databases with standards-based integration Secur. ID provides strong, two-factor authentication using tokens and RSA authentication servers Integration of VPN traffic into firewall policy Network access quarantine to ensure secure client configuration 19
Advanced Protection How ISA Server 2004 Secures VPN Client Connections ¢ ¢ All communications over the Internet are encrypted Broad protocol support n n ¢ Authentication n ¢ ¢ PPTP and L 2 TP/IPSec NAT traversal (NAT-T) for connectivity across any network (requires Microsoft Windows Server™ 2003) Microsoft Active Directory® uses existing Microsoft Windows® accounts, supports PKI for two-factor authentication RADIUS uses non-Windows-based accounts databases with standards-based integration Secur. ID provides strong, two-factor authentication using tokens and RSA authentication servers Integration of VPN traffic into firewall policy Network access quarantine to ensure secure client configuration 19
 Advanced Protection How ISA Server 2004 Connects Networks ¢ Broad protocol support n n n ¢ PPTP L 2 TP/IPSec tunnel mode for interoperability with existing VPN gateways: fully tested and supported Authentication and encryption n n Uses Windows RRAS capabilities Range of authentication methods n ¢ Active Directory, RADIUS, passwords, certificates Configurable encryption methods help ensure confidentiality of communications Fine-grained control over traffic between networks 20
Advanced Protection How ISA Server 2004 Connects Networks ¢ Broad protocol support n n n ¢ PPTP L 2 TP/IPSec tunnel mode for interoperability with existing VPN gateways: fully tested and supported Authentication and encryption n n Uses Windows RRAS capabilities Range of authentication methods n ¢ Active Directory, RADIUS, passwords, certificates Configurable encryption methods help ensure confidentiality of communications Fine-grained control over traffic between networks 20
 Summary: Advanced Protection ¢ ¢ ISA Server 2004 was designed with most common customer scenarios in mind ISA Server 2004 protects networks while enabling connectivity ISA Server 2004 is optimized for application-layer filtering A broad range of partner offerings extends protection capabilities ISA Server 2004 is a crucial component in protecting Microsoft networks and applications 21
Summary: Advanced Protection ¢ ¢ ISA Server 2004 was designed with most common customer scenarios in mind ISA Server 2004 protects networks while enabling connectivity ISA Server 2004 is optimized for application-layer filtering A broad range of partner offerings extends protection capabilities ISA Server 2004 is a crucial component in protecting Microsoft networks and applications 21
 Ease of Use New, Easy-to-Use Administration Tools ¢ ISA Server 2004 Management Console completely redesigned from previous version n n All tools for each task in one place Easy to learn ¢ ¢ Ease of use can reduce risk of security breaches due to misconfiguration Local or remote administration Use the same tool to configure and monitor the firewall, cache, and VPN gateway 22
Ease of Use New, Easy-to-Use Administration Tools ¢ ISA Server 2004 Management Console completely redesigned from previous version n n All tools for each task in one place Easy to learn ¢ ¢ Ease of use can reduce risk of security breaches due to misconfiguration Local or remote administration Use the same tool to configure and monitor the firewall, cache, and VPN gateway 22
 Ease of Use Overview ¢ Simplified administration tools n n ¢ Reduces training costs Helps prevent insecure configurations Unified firewall policy n Helps keep administration costs low 23
Ease of Use Overview ¢ Simplified administration tools n n ¢ Reduces training costs Helps prevent insecure configurations Unified firewall policy n Helps keep administration costs low 23
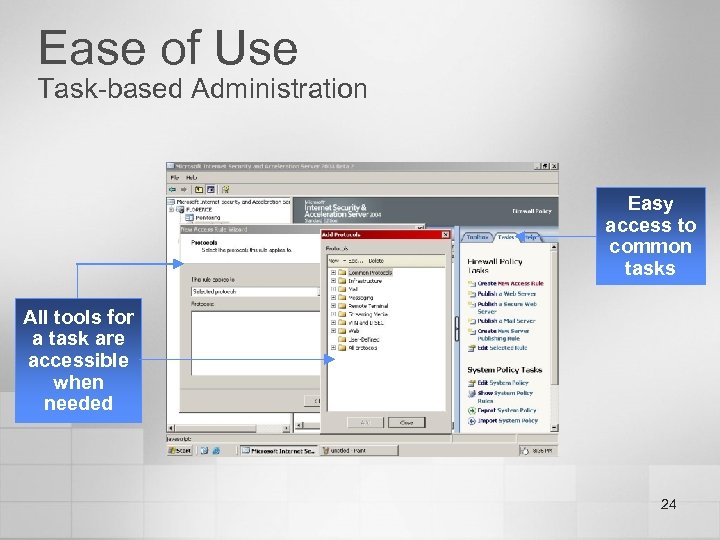 Ease of Use Task-based Administration Easy access to common tasks All tools for a task are accessible when needed 24
Ease of Use Task-based Administration Easy access to common tasks All tools for a task are accessible when needed 24
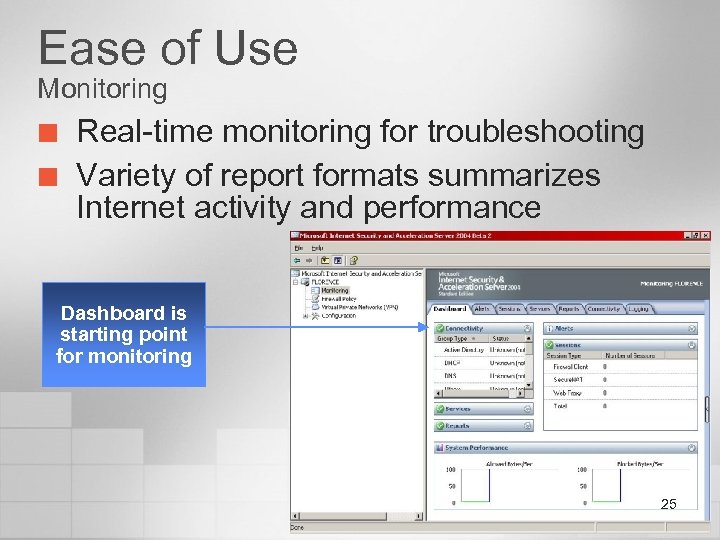 Ease of Use Monitoring ¢ ¢ Real-time monitoring for troubleshooting Variety of report formats summarizes Internet activity and performance Dashboard is starting point for monitoring 25
Ease of Use Monitoring ¢ ¢ Real-time monitoring for troubleshooting Variety of report formats summarizes Internet activity and performance Dashboard is starting point for monitoring 25
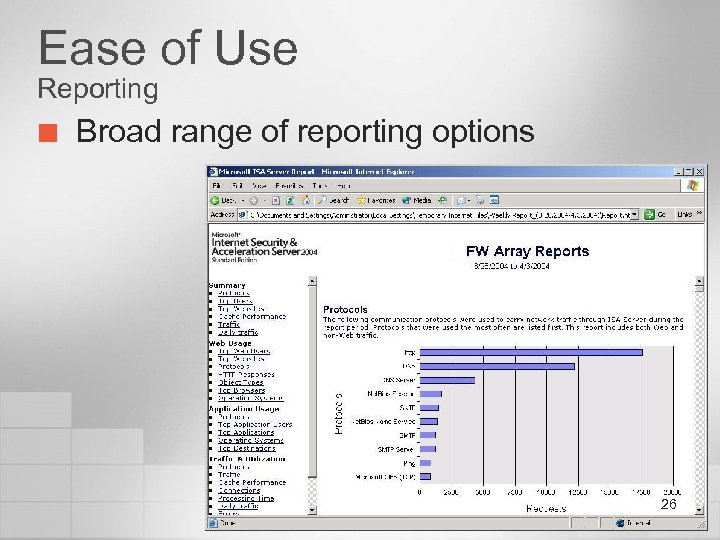 Ease of Use Reporting ¢ Broad range of reporting options 26
Ease of Use Reporting ¢ Broad range of reporting options 26
 Ease of Use Easy Deployment ¢ Multiple network support n n ¢ Works with your existing network infrastructure Leverages previous IT investments Broad client support n n Supports any device that uses TCP/IP Firewall Client adds features for Windows clients Low administrative overhead during initial deployment and network maintenance. 27
Ease of Use Easy Deployment ¢ Multiple network support n n ¢ Works with your existing network infrastructure Leverages previous IT investments Broad client support n n Supports any device that uses TCP/IP Firewall Client adds features for Windows clients Low administrative overhead during initial deployment and network maintenance. 27
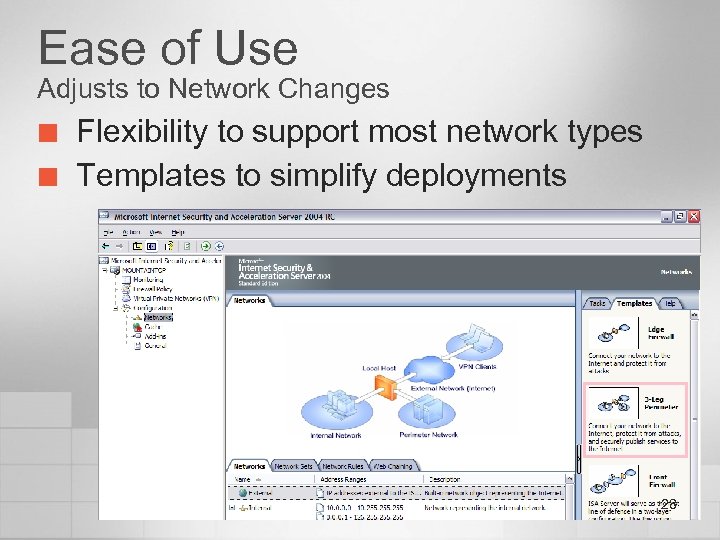 Ease of Use Adjusts to Network Changes ¢ ¢ Flexibility to support most network types Templates to simplify deployments 28
Ease of Use Adjusts to Network Changes ¢ ¢ Flexibility to support most network types Templates to simplify deployments 28
 Ease of Use Easy Scalability ¢ Scale up n ¢ Upgrade to faster hardware and repurpose existing server(s) without the need to purchase a different ISA Server 2004 license Scale out n n Easily copy configuration settings with XML export Maintain existing rules and settings Choice of options to grow with company needs. 29
Ease of Use Easy Scalability ¢ Scale up n ¢ Upgrade to faster hardware and repurpose existing server(s) without the need to purchase a different ISA Server 2004 license Scale out n n Easily copy configuration settings with XML export Maintain existing rules and settings Choice of options to grow with company needs. 29
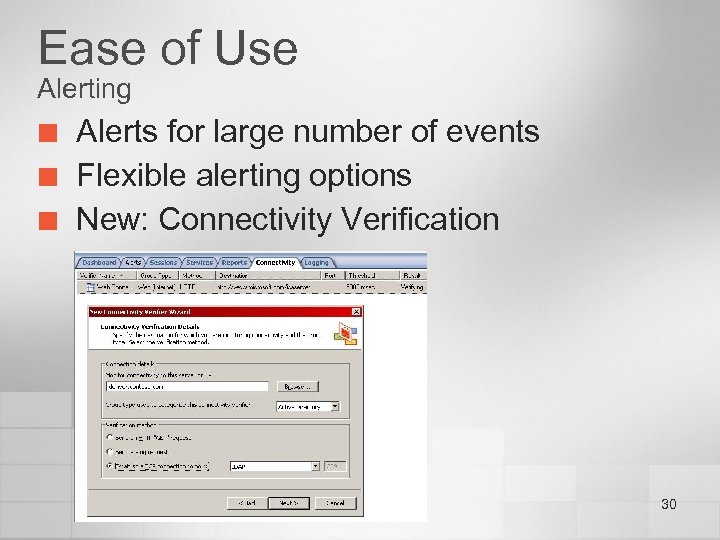 Ease of Use Alerting ¢ ¢ ¢ Alerts for large number of events Flexible alerting options New: Connectivity Verification 30
Ease of Use Alerting ¢ ¢ ¢ Alerts for large number of events Flexible alerting options New: Connectivity Verification 30
 Ease of User-based Access Control ¢ ¢ Prevalence of DHCP on internal networks makes IP-based access control obsolete ISA Server 2004 supports the use of native Windows security credentials to build highly granular firewall access rules RADIUS for universal integration with non. Windows user accounts and for authentication in perimeter networks Credentials are passed transparently, eliminating need for additional tedious logon procedures at firewall 31
Ease of User-based Access Control ¢ ¢ Prevalence of DHCP on internal networks makes IP-based access control obsolete ISA Server 2004 supports the use of native Windows security credentials to build highly granular firewall access rules RADIUS for universal integration with non. Windows user accounts and for authentication in perimeter networks Credentials are passed transparently, eliminating need for additional tedious logon procedures at firewall 31
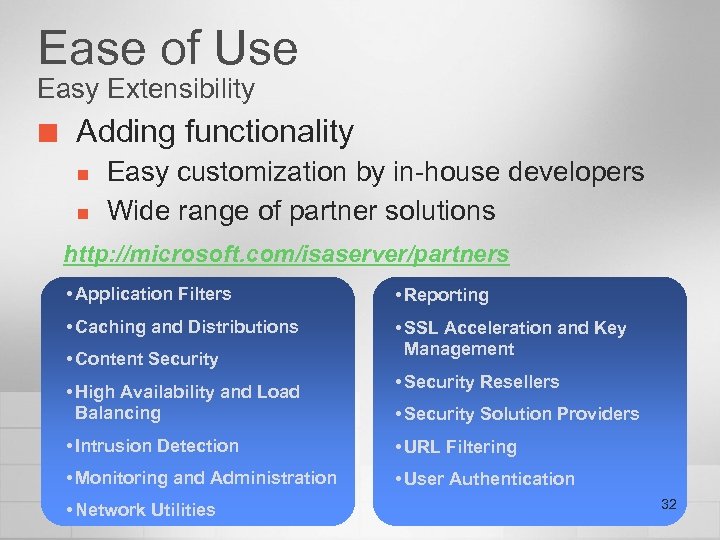 Ease of Use Easy Extensibility ¢ Adding functionality n n Easy customization by in-house developers Wide range of partner solutions http: //microsoft. com/isaserver/partners • Application Filters • Reporting • Caching and Distributions • SSL Acceleration and Key Management • Content Security • High Availability and Load Balancing • Security Resellers • Security Solution Providers • Intrusion Detection • URL Filtering • Monitoring and Administration • User Authentication • Network Utilities 32
Ease of Use Easy Extensibility ¢ Adding functionality n n Easy customization by in-house developers Wide range of partner solutions http: //microsoft. com/isaserver/partners • Application Filters • Reporting • Caching and Distributions • SSL Acceleration and Key Management • Content Security • High Availability and Load Balancing • Security Resellers • Security Solution Providers • Intrusion Detection • URL Filtering • Monitoring and Administration • User Authentication • Network Utilities 32
 Ease of Use Extensible Open Platform ¢ Most administrative tasks can be scripted n n n ¢ Scripting automates tasks Scripting saves time and ensures consistency SDK provides access to easy-to-use procedures for scripting Custom Web and application filters n Custom filters allow secondary inspection and manipulation of traffic n Examples: Advanced content inspection, advanced authorization, etc. Easy object model ensures quick results 33
Ease of Use Extensible Open Platform ¢ Most administrative tasks can be scripted n n n ¢ Scripting automates tasks Scripting saves time and ensures consistency SDK provides access to easy-to-use procedures for scripting Custom Web and application filters n Custom filters allow secondary inspection and manipulation of traffic n Examples: Advanced content inspection, advanced authorization, etc. Easy object model ensures quick results 33
 Summary: Ease of Use ¢ ¢ ISA Server 2004 tools make firewall administration easy Easy configuration can help prevent configuration mistakes ISA Server 2004 adapts to existing network configurations and changes Extensive logging, monitoring, and reporting capabilities ISA Server 2004 is a crucial component in protecting Microsoft networks and applications 34
Summary: Ease of Use ¢ ¢ ISA Server 2004 tools make firewall administration easy Easy configuration can help prevent configuration mistakes ISA Server 2004 adapts to existing network configurations and changes Extensive logging, monitoring, and reporting capabilities ISA Server 2004 is a crucial component in protecting Microsoft networks and applications 34
 Fast, Secure Access Integrated VPN ¢ ¢ ¢ Secure site-to-site connections Secure remote access conections Broad protocol support 35
Fast, Secure Access Integrated VPN ¢ ¢ ¢ Secure site-to-site connections Secure remote access conections Broad protocol support 35
 Fast, Secure Access Web-Caching Benefits ¢ Frequently requested Web content is cached for local delivery n n Users get faster access to frequently requested Web content Existing bandwidth is used more efficiently ISA Server 2004 is the only major firewall with built-in, state-of-the-art Web caching 36
Fast, Secure Access Web-Caching Benefits ¢ Frequently requested Web content is cached for local delivery n n Users get faster access to frequently requested Web content Existing bandwidth is used more efficiently ISA Server 2004 is the only major firewall with built-in, state-of-the-art Web caching 36
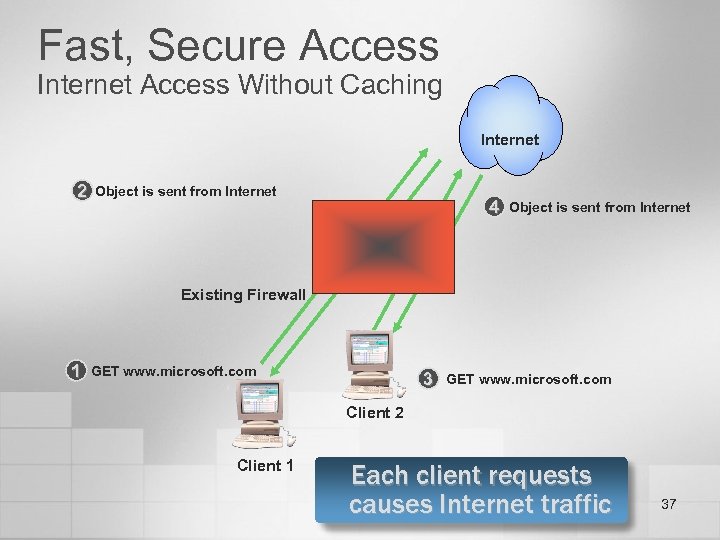 Fast, Secure Access Internet Access Without Caching Internet 2 Object is sent from Internet 4 Object is sent from Internet Existing Firewall 1 GET www. microsoft. com 3 GET www. microsoft. com Client 2 Client 1 Each client requests causes Internet traffic 37
Fast, Secure Access Internet Access Without Caching Internet 2 Object is sent from Internet 4 Object is sent from Internet Existing Firewall 1 GET www. microsoft. com 3 GET www. microsoft. com Client 2 Client 1 Each client requests causes Internet traffic 37
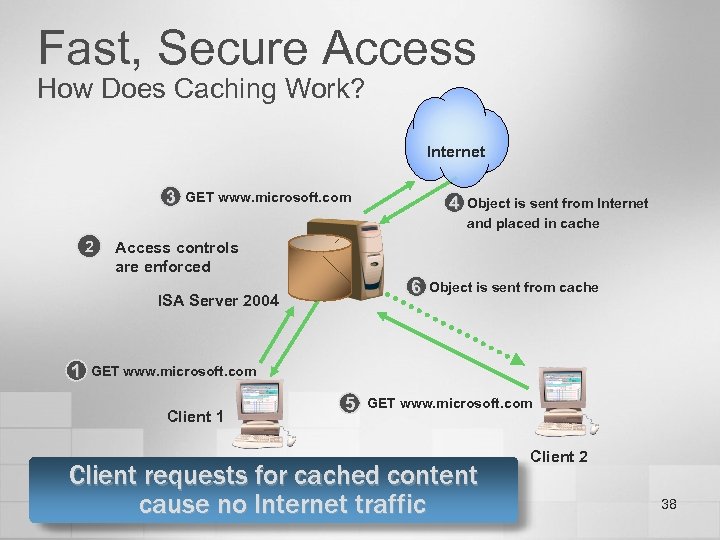 Fast, Secure Access How Does Caching Work? Internet 3 2 GET www. microsoft. com Object is sent from Internet and placed in cache Access controls are enforced 6 ISA Server 2004 1 4 Object is sent from cache GET www. microsoft. com Client 1 5 GET www. microsoft. com Client requests for cached content cause no Internet traffic Client 2 38
Fast, Secure Access How Does Caching Work? Internet 3 2 GET www. microsoft. com Object is sent from Internet and placed in cache Access controls are enforced 6 ISA Server 2004 1 4 Object is sent from cache GET www. microsoft. com Client 1 5 GET www. microsoft. com Client requests for cached content cause no Internet traffic Client 2 38
 Fast, Secure Access Effects of Caching ¢ Reduces bandwidth requirements n ¢ Reduces server workload n ¢ Request for published Web content are served from the cache without additional requests to the published server Distributes bandwidth n ¢ Requests from multiple users for an object only require one download from Internet Most frequently accessed content can be downloaded during off hours and before users request it Ensures that objects are up-to-date n ISA Server requests an updated version when the object has changed on the Web server 39
Fast, Secure Access Effects of Caching ¢ Reduces bandwidth requirements n ¢ Reduces server workload n ¢ Request for published Web content are served from the cache without additional requests to the published server Distributes bandwidth n ¢ Requests from multiple users for an object only require one download from Internet Most frequently accessed content can be downloaded during off hours and before users request it Ensures that objects are up-to-date n ISA Server requests an updated version when the object has changed on the Web server 39
 Fast, Secure Access Business Benefits of Caching ¢ Improved productivity n n ¢ Many Web pages are displayed faster No waiting for Web objects that are cached Better resource utilization n n No need to purchase additional bandwidth Fully integrated, minimal administration 40
Fast, Secure Access Business Benefits of Caching ¢ Improved productivity n n ¢ Many Web pages are displayed faster No waiting for Web objects that are cached Better resource utilization n n No need to purchase additional bandwidth Fully integrated, minimal administration 40
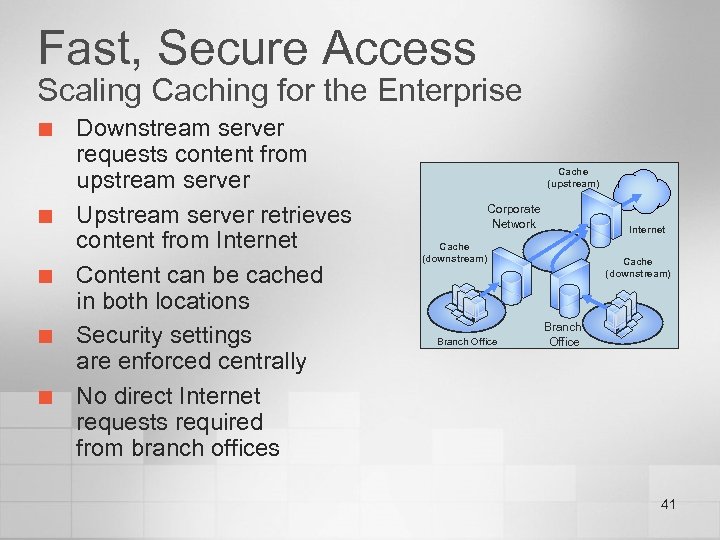 Fast, Secure Access Scaling Caching for the Enterprise ¢ ¢ ¢ Downstream server requests content from upstream server Upstream server retrieves content from Internet Content can be cached in both locations Security settings are enforced centrally No direct Internet requests required from branch offices Cache (upstream) Corporate Network Internet Cache (downstream) Branch Office Cache (downstream) ) Branch Office 41
Fast, Secure Access Scaling Caching for the Enterprise ¢ ¢ ¢ Downstream server requests content from upstream server Upstream server retrieves content from Internet Content can be cached in both locations Security settings are enforced centrally No direct Internet requests required from branch offices Cache (upstream) Corporate Network Internet Cache (downstream) Branch Office Cache (downstream) ) Branch Office 41
 Fast, Secure Access Granular Access Control ¢ Full control over Internet access by users n n n ¢ Enforce corporate policies Control access by protocol, user, location, destination, schedule Fine-grained control of Web content Partner solutions extend access control All network traffic blocked unless specifically allowed Flexible firewall policy n n Easy to create broad rules or detailed policy Unified firewall policy makes it easy to review and troubleshoot access rules 42
Fast, Secure Access Granular Access Control ¢ Full control over Internet access by users n n n ¢ Enforce corporate policies Control access by protocol, user, location, destination, schedule Fine-grained control of Web content Partner solutions extend access control All network traffic blocked unless specifically allowed Flexible firewall policy n n Easy to create broad rules or detailed policy Unified firewall policy makes it easy to review and troubleshoot access rules 42
 Summary: Fast, Secure Access ¢ ¢ ¢ Integrated VPN for secure site-to-site and remote access connections Optimized for application-layer filtering Caching accelerates access to frequently used Web content Granular rules allow a high level of Internet access control Additional filtering is possible with third-part solutions provided by Microsoft partners ISA Server 2004 is a crucial component in protecting Microsoft networks and applications 43
Summary: Fast, Secure Access ¢ ¢ ¢ Integrated VPN for secure site-to-site and remote access connections Optimized for application-layer filtering Caching accelerates access to frequently used Web content Granular rules allow a high level of Internet access control Additional filtering is possible with third-part solutions provided by Microsoft partners ISA Server 2004 is a crucial component in protecting Microsoft networks and applications 43
 2. Protecting Microsoft Applications Technical Details
2. Protecting Microsoft Applications Technical Details
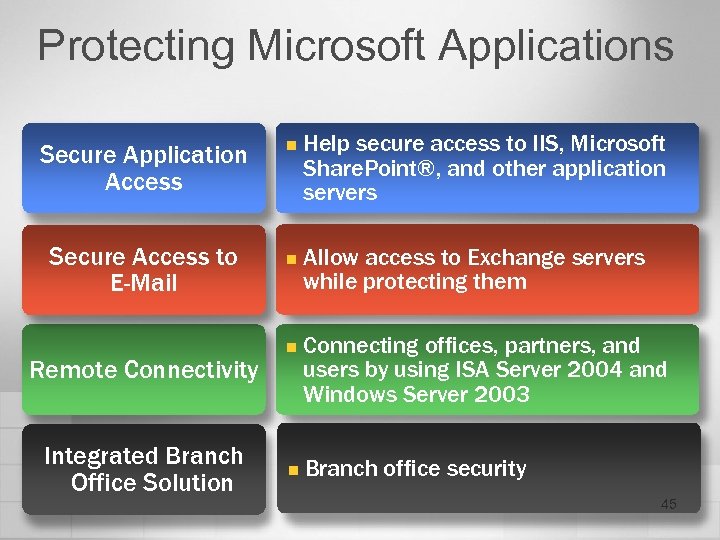 Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 45
Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 45
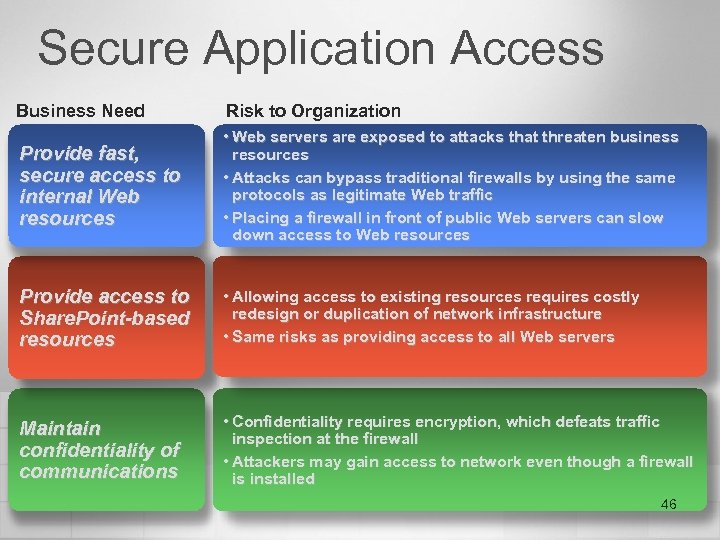 Secure Application Access Business Need Risk to Organization Provide fast, secure access to internal Web resources • Web servers are exposed to attacks that threaten business resources • Attacks can bypass traditional firewalls by using the same protocols as legitimate Web traffic • Placing a firewall in front of public Web servers can slow down access to Web resources Provide access to Share. Point-based resources • Allowing access to existing resources requires costly redesign or duplication of network infrastructure • Same risks as providing access to all Web servers Maintain confidentiality of communications • Confidentiality requires encryption, which defeats traffic inspection at the firewall • Attackers may gain access to network even though a firewall is installed 46
Secure Application Access Business Need Risk to Organization Provide fast, secure access to internal Web resources • Web servers are exposed to attacks that threaten business resources • Attacks can bypass traditional firewalls by using the same protocols as legitimate Web traffic • Placing a firewall in front of public Web servers can slow down access to Web resources Provide access to Share. Point-based resources • Allowing access to existing resources requires costly redesign or duplication of network infrastructure • Same risks as providing access to all Web servers Maintain confidentiality of communications • Confidentiality requires encryption, which defeats traffic inspection at the firewall • Attackers may gain access to network even though a firewall is installed 46
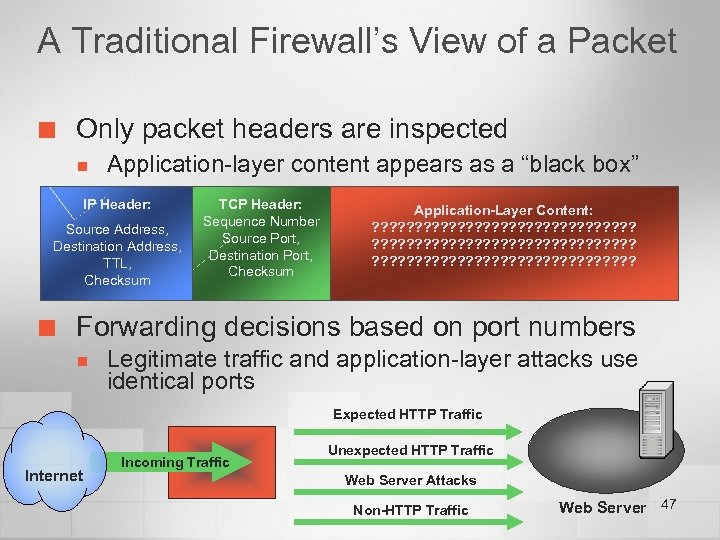 A Traditional Firewall’s View of a Packet ¢ Only packet headers are inspected n Application-layer content appears as a “black box” IP Header: Source Address, Destination Address, TTL, Checksum ¢ TCP Header: Sequence Number Source Port, Destination Port, Checksum Application-Layer Content: ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? Forwarding decisions based on port numbers n Legitimate traffic and application-layer attacks use identical ports Expected HTTP Traffic Internet Incoming Traffic Unexpected HTTP Traffic Web Server Attacks Non-HTTP Traffic Web Server 47
A Traditional Firewall’s View of a Packet ¢ Only packet headers are inspected n Application-layer content appears as a “black box” IP Header: Source Address, Destination Address, TTL, Checksum ¢ TCP Header: Sequence Number Source Port, Destination Port, Checksum Application-Layer Content: ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? ? Forwarding decisions based on port numbers n Legitimate traffic and application-layer attacks use identical ports Expected HTTP Traffic Internet Incoming Traffic Unexpected HTTP Traffic Web Server Attacks Non-HTTP Traffic Web Server 47
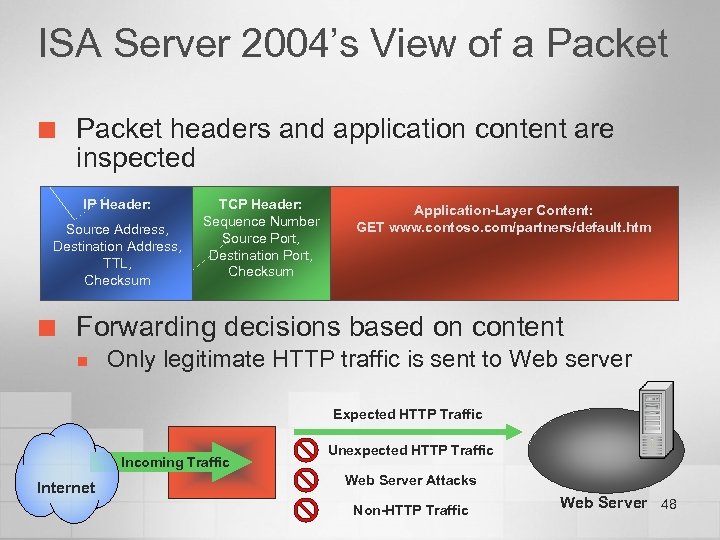 ISA Server 2004’s View of a Packet ¢ Packet headers and application content are inspected IP Header: Source Address, Destination Address, TTL, Checksum ¢ TCP Header: Sequence Number Source Port, Destination Port, Checksum Application-Layer Content: GET www. contoso. com/partners/default. htm Forwarding decisions based on content n Only legitimate HTTP traffic is sent to Web server Expected HTTP Traffic Incoming Traffic Internet Unexpected HTTP Traffic Web Server Attacks Non-HTTP Traffic Web Server 48
ISA Server 2004’s View of a Packet ¢ Packet headers and application content are inspected IP Header: Source Address, Destination Address, TTL, Checksum ¢ TCP Header: Sequence Number Source Port, Destination Port, Checksum Application-Layer Content: GET www. contoso. com/partners/default. htm Forwarding decisions based on content n Only legitimate HTTP traffic is sent to Web server Expected HTTP Traffic Incoming Traffic Internet Unexpected HTTP Traffic Web Server Attacks Non-HTTP Traffic Web Server 48
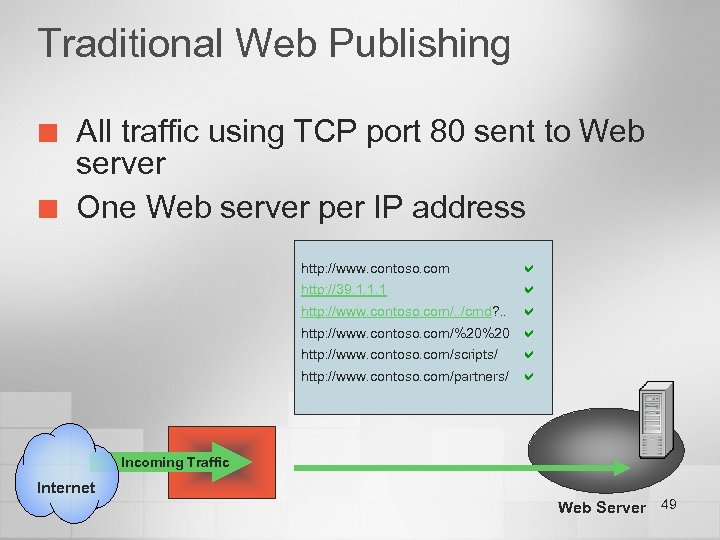 Traditional Web Publishing ¢ ¢ All traffic using TCP port 80 sent to Web server One Web server per IP address http: //www. contoso. com http: //39. 1. 1. 1 http: //www. contoso. com/. . /cmd? . . http: //www. contoso. com/%20%20 http: //www. contoso. com/scripts/ http: //www. contoso. com/partners/ Incoming Traffic Internet Web Server 49
Traditional Web Publishing ¢ ¢ All traffic using TCP port 80 sent to Web server One Web server per IP address http: //www. contoso. com http: //39. 1. 1. 1 http: //www. contoso. com/. . /cmd? . . http: //www. contoso. com/%20%20 http: //www. contoso. com/scripts/ http: //www. contoso. com/partners/ Incoming Traffic Internet Web Server 49
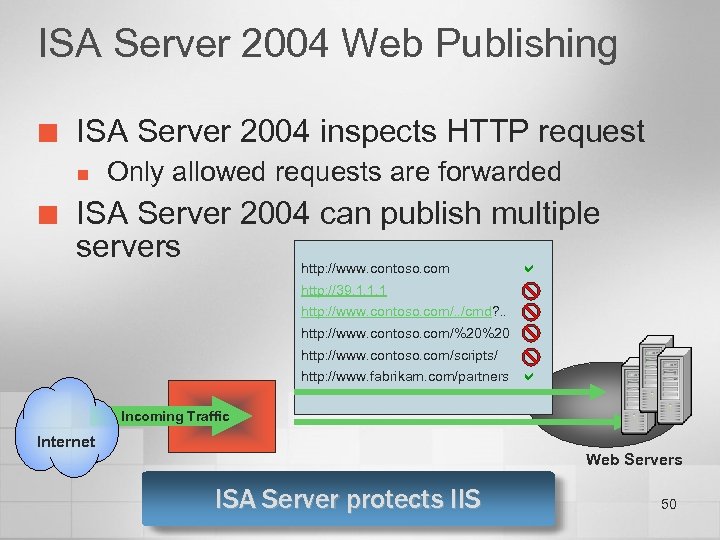 ISA Server 2004 Web Publishing ¢ ISA Server 2004 inspects HTTP request n ¢ Only allowed requests are forwarded ISA Server 2004 can publish multiple servers http: //www. contoso. com http: //39. 1. 1. 1 http: //www. contoso. com/. . /cmd? . . http: //www. contoso. com/%20%20 http: //www. contoso. com/scripts/ http: //www. fabrikam. com/partners Incoming Traffic Internet Web Servers ISA Server protects IIS 50
ISA Server 2004 Web Publishing ¢ ISA Server 2004 inspects HTTP request n ¢ Only allowed requests are forwarded ISA Server 2004 can publish multiple servers http: //www. contoso. com http: //39. 1. 1. 1 http: //www. contoso. com/. . /cmd? . . http: //www. contoso. com/%20%20 http: //www. contoso. com/scripts/ http: //www. fabrikam. com/partners Incoming Traffic Internet Web Servers ISA Server protects IIS 50
 How ISA Server 2004 Secures SSL Traffic ¢ ¢ SSL: Confidentiality but No Traffic Inspection SSL Bridging: 1. 2. 3. Client on Internet encrypts communications ISA Server 2004 decrypts and inspects traffic ISA Server 2004 sends allowed traffic to published server, re-encrypting it if required 51
How ISA Server 2004 Secures SSL Traffic ¢ ¢ SSL: Confidentiality but No Traffic Inspection SSL Bridging: 1. 2. 3. Client on Internet encrypts communications ISA Server 2004 decrypts and inspects traffic ISA Server 2004 sends allowed traffic to published server, re-encrypting it if required 51
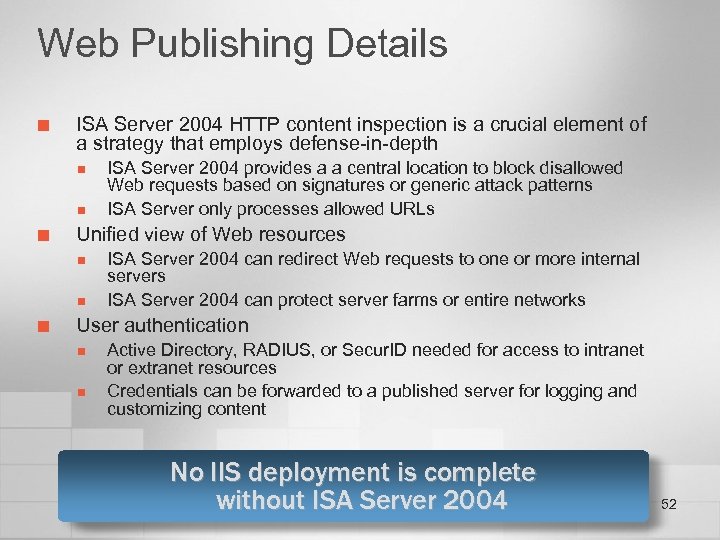 Web Publishing Details ¢ ISA Server 2004 HTTP content inspection is a crucial element of a strategy that employs defense-in-depth n n ¢ Unified view of Web resources n n ¢ ISA Server 2004 provides a a central location to block disallowed Web requests based on signatures or generic attack patterns ISA Server only processes allowed URLs ISA Server 2004 can redirect Web requests to one or more internal servers ISA Server 2004 can protect server farms or entire networks User authentication n n Active Directory, RADIUS, or Secur. ID needed for access to intranet or extranet resources Credentials can be forwarded to a published server for logging and customizing content No IIS deployment is complete without ISA Server 2004 52
Web Publishing Details ¢ ISA Server 2004 HTTP content inspection is a crucial element of a strategy that employs defense-in-depth n n ¢ Unified view of Web resources n n ¢ ISA Server 2004 provides a a central location to block disallowed Web requests based on signatures or generic attack patterns ISA Server only processes allowed URLs ISA Server 2004 can redirect Web requests to one or more internal servers ISA Server 2004 can protect server farms or entire networks User authentication n n Active Directory, RADIUS, or Secur. ID needed for access to intranet or extranet resources Credentials can be forwarded to a published server for logging and customizing content No IIS deployment is complete without ISA Server 2004 52
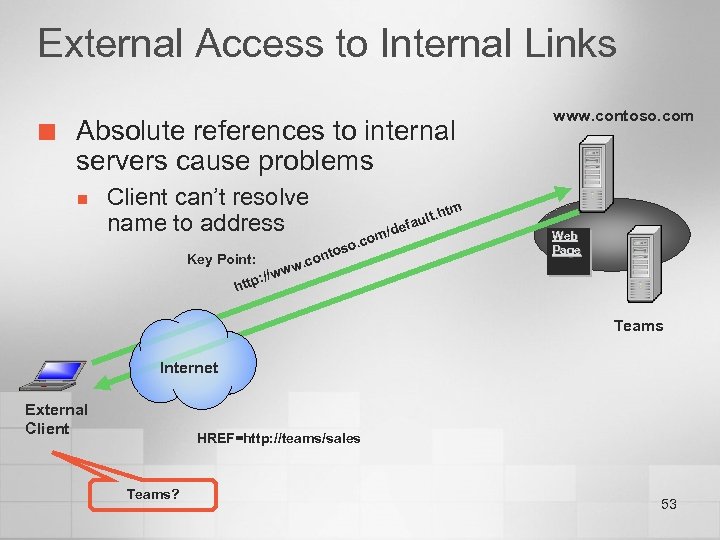 External Access to Internal Links ¢ Absolute references to internal servers cause problems n Client can’t resolve name to address Key Point: o so. c o m ont w. c w lt. fau /de www. contoso. com htm Web Page //w : http Teams Internet External Client HREF=http: //teams/sales Teams? 53
External Access to Internal Links ¢ Absolute references to internal servers cause problems n Client can’t resolve name to address Key Point: o so. c o m ont w. c w lt. fau /de www. contoso. com htm Web Page //w : http Teams Internet External Client HREF=http: //teams/sales Teams? 53
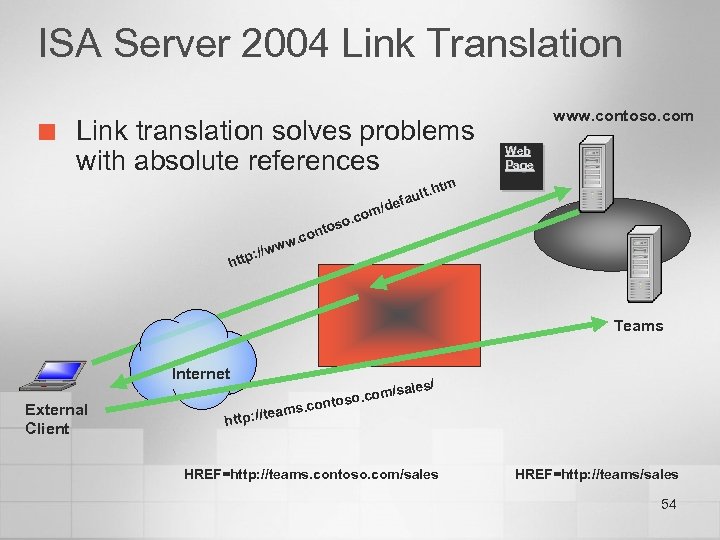 ISA Server 2004 Link Translation ¢ Link translation solves problems with absolute references Web Page htm om . con w //ww : http o. c tos lt. fau /de www. contoso. com Teams Internet External Client /sales/ o. com ontos ms. c ea http: //t HREF=http: //teams. contoso. com/sales HREF=http: //teams/sales 54
ISA Server 2004 Link Translation ¢ Link translation solves problems with absolute references Web Page htm om . con w //ww : http o. c tos lt. fau /de www. contoso. com Teams Internet External Client /sales/ o. com ontos ms. c ea http: //t HREF=http: //teams. contoso. com/sales HREF=http: //teams/sales 54
 Link Translation Details ¢ ¢ Link translation is crucial for providing simultaneous internal and external access to Share. Point sites Translates hyperlinks within Web responses from published server n n n Translates intranet computer names to names that can be externally resolved Can replace http: // https: // for SSL bridging Automatic translation sufficient for most scenarios, administrator-defined translation for extended functionality No Share. Point deployment is complete without ISA Server 2004 55
Link Translation Details ¢ ¢ Link translation is crucial for providing simultaneous internal and external access to Share. Point sites Translates hyperlinks within Web responses from published server n n n Translates intranet computer names to names that can be externally resolved Can replace http: // https: // for SSL bridging Automatic translation sufficient for most scenarios, administrator-defined translation for extended functionality No Share. Point deployment is complete without ISA Server 2004 55
 Easy Configuration and Administration of Application Access Web Publishing Wizards make configuration easy and prevent configuration mistakes, monitoring tools show Web usage 56
Easy Configuration and Administration of Application Access Web Publishing Wizards make configuration easy and prevent configuration mistakes, monitoring tools show Web usage 56
 How ISA Server 2004 Enables Access to Non-Web Resources ¢ Access to some corporate resources requires protocols other than HTTP n n n ¢ ¢ FTP servers for access to files Database servers in perimeter network or internal network Public DNS servers to locate company’s servers Server publishing allows secure access to non. Web resources ISA Server 2004 supports all IP-based protocols n Application-layer filtering for selected protocols: SMTP, FTP, DNS, RPC, etc. 57
How ISA Server 2004 Enables Access to Non-Web Resources ¢ Access to some corporate resources requires protocols other than HTTP n n n ¢ ¢ FTP servers for access to files Database servers in perimeter network or internal network Public DNS servers to locate company’s servers Server publishing allows secure access to non. Web resources ISA Server 2004 supports all IP-based protocols n Application-layer filtering for selected protocols: SMTP, FTP, DNS, RPC, etc. 57
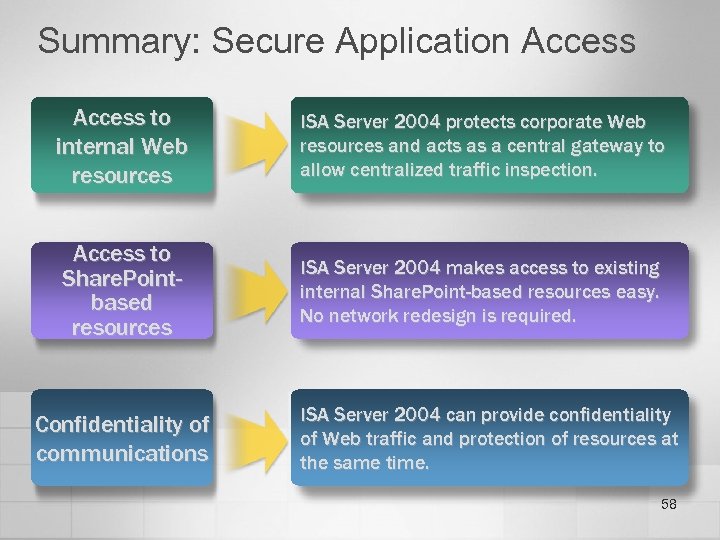 Summary: Secure Application Access to internal Web resources ISA Server 2004 protects corporate Web resources and acts as a central gateway to allow centralized traffic inspection. Access to Share. Pointbased resources ISA Server 2004 makes access to existing internal Share. Point-based resources easy. No network redesign is required. Confidentiality of communications ISA Server 2004 can provide confidentiality of Web traffic and protection of resources at the same time. 58
Summary: Secure Application Access to internal Web resources ISA Server 2004 protects corporate Web resources and acts as a central gateway to allow centralized traffic inspection. Access to Share. Pointbased resources ISA Server 2004 makes access to existing internal Share. Point-based resources easy. No network redesign is required. Confidentiality of communications ISA Server 2004 can provide confidentiality of Web traffic and protection of resources at the same time. 58
 Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 59
Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 59
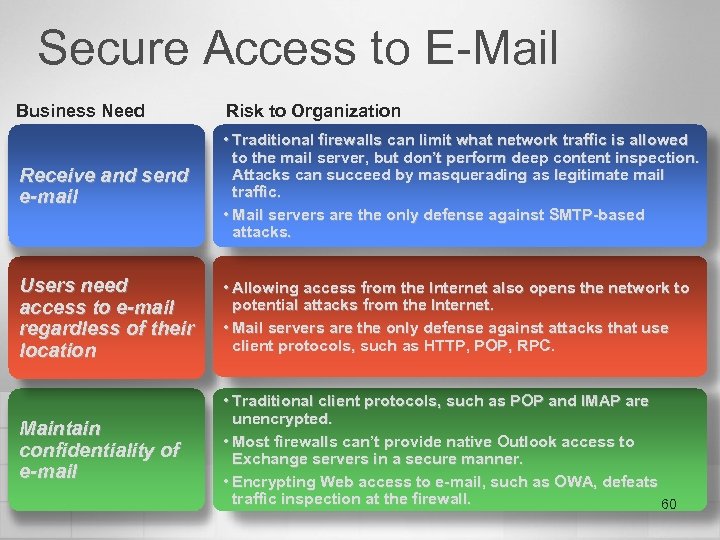 Secure Access to E-Mail Business Need Risk to Organization Receive and send e-mail • Traditional firewalls can limit what network traffic is allowed to the mail server, but don’t perform deep content inspection. Attacks can succeed by masquerading as legitimate mail traffic. • Mail servers are the only defense against SMTP-based attacks. Users need access to e-mail regardless of their location • Allowing access from the Internet also opens the network to potential attacks from the Internet. • Mail servers are the only defense against attacks that use client protocols, such as HTTP, POP, RPC. Maintain confidentiality of e-mail • Traditional client protocols, such as POP and IMAP are unencrypted. • Most firewalls can’t provide native Outlook access to Exchange servers in a secure manner. • Encrypting Web access to e-mail, such as OWA, defeats traffic inspection at the firewall. 60
Secure Access to E-Mail Business Need Risk to Organization Receive and send e-mail • Traditional firewalls can limit what network traffic is allowed to the mail server, but don’t perform deep content inspection. Attacks can succeed by masquerading as legitimate mail traffic. • Mail servers are the only defense against SMTP-based attacks. Users need access to e-mail regardless of their location • Allowing access from the Internet also opens the network to potential attacks from the Internet. • Mail servers are the only defense against attacks that use client protocols, such as HTTP, POP, RPC. Maintain confidentiality of e-mail • Traditional client protocols, such as POP and IMAP are unencrypted. • Most firewalls can’t provide native Outlook access to Exchange servers in a secure manner. • Encrypting Web access to e-mail, such as OWA, defeats traffic inspection at the firewall. 60
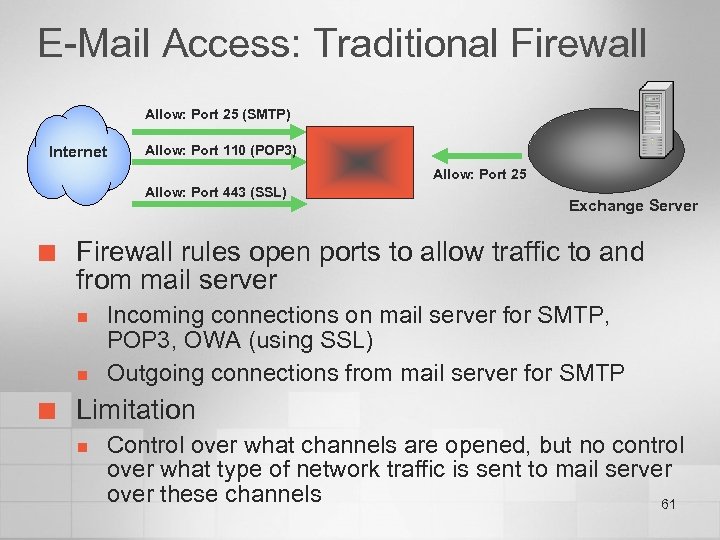 E-Mail Access: Traditional Firewall Allow: Port 25 (SMTP) Internet Allow: Port 110 (POP 3) Allow: Port 25 Allow: Port 443 (SSL) ¢ Firewall rules open ports to allow traffic to and from mail server n n ¢ Exchange Server Incoming connections on mail server for SMTP, POP 3, OWA (using SSL) Outgoing connections from mail server for SMTP Limitation n Control over what channels are opened, but no control over what type of network traffic is sent to mail server over these channels 61
E-Mail Access: Traditional Firewall Allow: Port 25 (SMTP) Internet Allow: Port 110 (POP 3) Allow: Port 25 Allow: Port 443 (SSL) ¢ Firewall rules open ports to allow traffic to and from mail server n n ¢ Exchange Server Incoming connections on mail server for SMTP, POP 3, OWA (using SSL) Outgoing connections from mail server for SMTP Limitation n Control over what channels are opened, but no control over what type of network traffic is sent to mail server over these channels 61
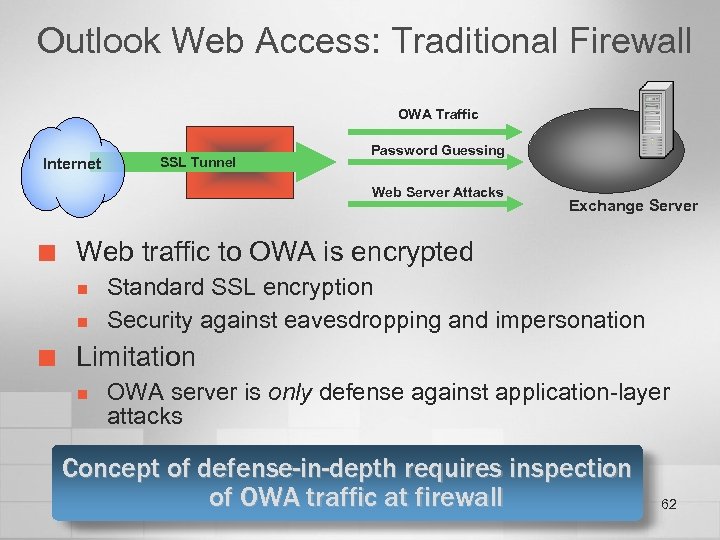 Outlook Web Access: Traditional Firewall OWA Traffic Internet SSL Tunnel Password Guessing Web Server Attacks ¢ Web traffic to OWA is encrypted n n ¢ Exchange Server Standard SSL encryption Security against eavesdropping and impersonation Limitation n OWA server is only defense against application-layer attacks Concept of defense-in-depth requires inspection of OWA traffic at firewall 62
Outlook Web Access: Traditional Firewall OWA Traffic Internet SSL Tunnel Password Guessing Web Server Attacks ¢ Web traffic to OWA is encrypted n n ¢ Exchange Server Standard SSL encryption Security against eavesdropping and impersonation Limitation n OWA server is only defense against application-layer attacks Concept of defense-in-depth requires inspection of OWA traffic at firewall 62
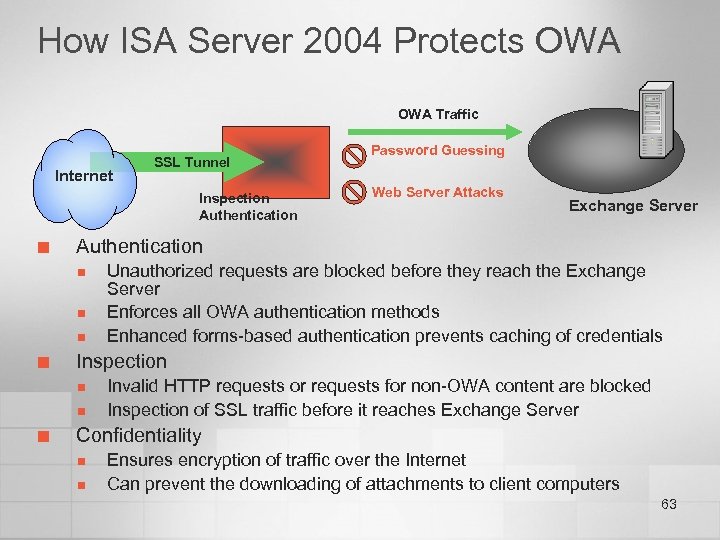 How ISA Server 2004 Protects OWA Traffic Internet SSL Tunnel Inspection Authentication ¢ n n Exchange Server Unauthorized requests are blocked before they reach the Exchange Server Enforces all OWA authentication methods Enhanced forms-based authentication prevents caching of credentials Inspection n n ¢ Web Server Attacks Authentication n ¢ Password Guessing Invalid HTTP requests or requests for non-OWA content are blocked Inspection of SSL traffic before it reaches Exchange Server Confidentiality n n Ensures encryption of traffic over the Internet Can prevent the downloading of attachments to client computers 63
How ISA Server 2004 Protects OWA Traffic Internet SSL Tunnel Inspection Authentication ¢ n n Exchange Server Unauthorized requests are blocked before they reach the Exchange Server Enforces all OWA authentication methods Enhanced forms-based authentication prevents caching of credentials Inspection n n ¢ Web Server Attacks Authentication n ¢ Password Guessing Invalid HTTP requests or requests for non-OWA content are blocked Inspection of SSL traffic before it reaches Exchange Server Confidentiality n n Ensures encryption of traffic over the Internet Can prevent the downloading of attachments to client computers 63
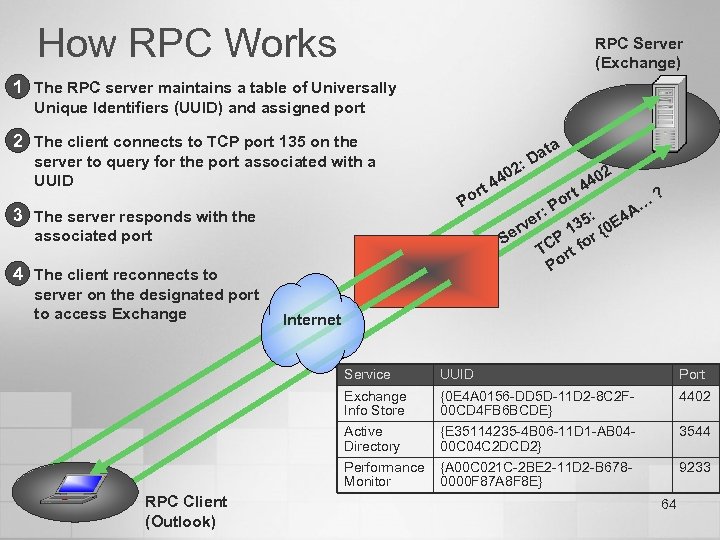 How RPC Works RPC Server (Exchange) 1 The RPC server maintains a table of Universally Unique Identifiers (UUID) and assigned port 2 The client connects to TCP port 135 on the server to query for the port associated with a UUID 3 The server responds with the 2: Po r: e rv Se associated port 4 The client reconnects to server on the designated port to access Exchange rt 0 44 ata D t or P 2 0 44 A… ? 4 5: 13 r {0 E P TC rt fo Po Internet Service Port Exchange Info Store {0 E 4 A 0156 -DD 5 D-11 D 2 -8 C 2 F 00 CD 4 FB 6 BCDE} 4402 Active Directory {E 35114235 -4 B 06 -11 D 1 -AB 0400 C 04 C 2 DCD 2} 3544 Performance Monitor RPC Client (Outlook) UUID {A 00 C 021 C-2 BE 2 -11 D 2 -B 6780000 F 87 A 8 F 8 E} 9233 64
How RPC Works RPC Server (Exchange) 1 The RPC server maintains a table of Universally Unique Identifiers (UUID) and assigned port 2 The client connects to TCP port 135 on the server to query for the port associated with a UUID 3 The server responds with the 2: Po r: e rv Se associated port 4 The client reconnects to server on the designated port to access Exchange rt 0 44 ata D t or P 2 0 44 A… ? 4 5: 13 r {0 E P TC rt fo Po Internet Service Port Exchange Info Store {0 E 4 A 0156 -DD 5 D-11 D 2 -8 C 2 F 00 CD 4 FB 6 BCDE} 4402 Active Directory {E 35114235 -4 B 06 -11 D 1 -AB 0400 C 04 C 2 DCD 2} 3544 Performance Monitor RPC Client (Outlook) UUID {A 00 C 021 C-2 BE 2 -11 D 2 -B 6780000 F 87 A 8 F 8 E} 9233 64
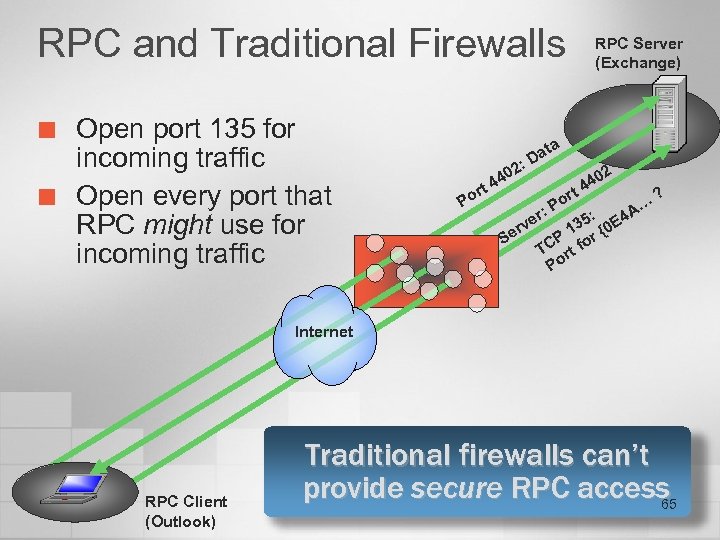 RPC and Traditional Firewalls ¢ ¢ Open port 135 for incoming traffic Open every port that RPC might use for incoming traffic 2: Po rt 0 44 ata D r: e rv Se RPC Server (Exchange) t or P 2 0 44 A… ? 4 5: 13 r {0 E P TC rt fo Po Internet RPC Client (Outlook) Traditional firewalls can’t provide secure RPC access 65
RPC and Traditional Firewalls ¢ ¢ Open port 135 for incoming traffic Open every port that RPC might use for incoming traffic 2: Po rt 0 44 ata D r: e rv Se RPC Server (Exchange) t or P 2 0 44 A… ? 4 5: 13 r {0 E P TC rt fo Po Internet RPC Client (Outlook) Traditional firewalls can’t provide secure RPC access 65
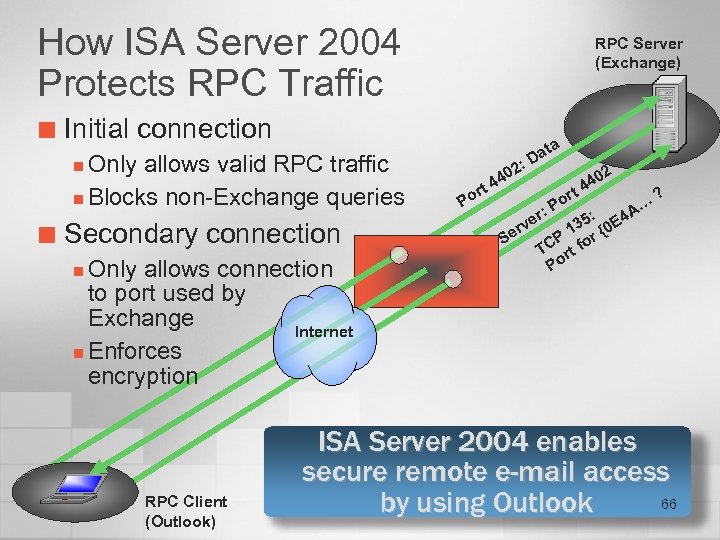 How ISA Server 2004 Protects RPC Traffic ¢ RPC Server (Exchange) Initial connection Only allows valid RPC traffic n Blocks non-Exchange queries 2: n ¢ Secondary connection Only allows connection to port used by Exchange Internet n Enforces encryption n RPC Client (Outlook) Po rt 0 44 ata D r: Se e rv t or P 2 0 44 A… ? 4 5: 13 r {0 E P TC rt fo Po ISA Server 2004 enables secure remote e-mail access 66 by using Outlook
How ISA Server 2004 Protects RPC Traffic ¢ RPC Server (Exchange) Initial connection Only allows valid RPC traffic n Blocks non-Exchange queries 2: n ¢ Secondary connection Only allows connection to port used by Exchange Internet n Enforces encryption n RPC Client (Outlook) Po rt 0 44 ata D r: Se e rv t or P 2 0 44 A… ? 4 5: 13 r {0 E P TC rt fo Po ISA Server 2004 enables secure remote e-mail access 66 by using Outlook
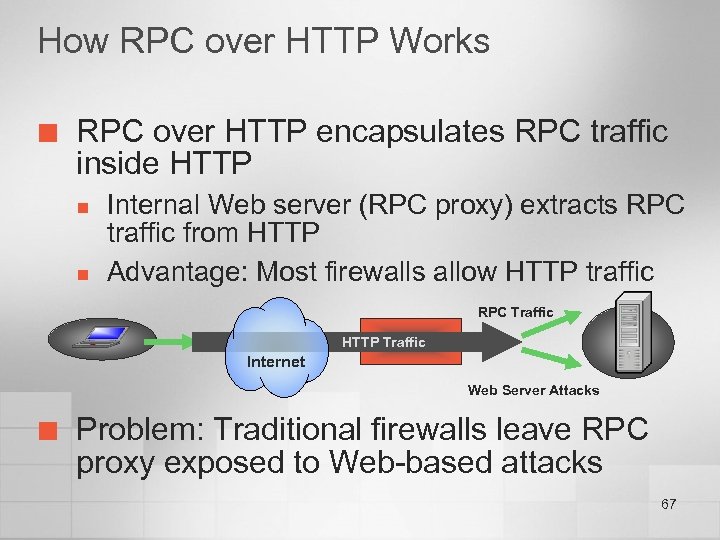 How RPC over HTTP Works ¢ RPC over HTTP encapsulates RPC traffic inside HTTP n n Internal Web server (RPC proxy) extracts RPC traffic from HTTP Advantage: Most firewalls allow HTTP traffic RPC Traffic HTTP Traffic Internet Web Server Attacks ¢ Problem: Traditional firewalls leave RPC proxy exposed to Web-based attacks 67
How RPC over HTTP Works ¢ RPC over HTTP encapsulates RPC traffic inside HTTP n n Internal Web server (RPC proxy) extracts RPC traffic from HTTP Advantage: Most firewalls allow HTTP traffic RPC Traffic HTTP Traffic Internet Web Server Attacks ¢ Problem: Traditional firewalls leave RPC proxy exposed to Web-based attacks 67
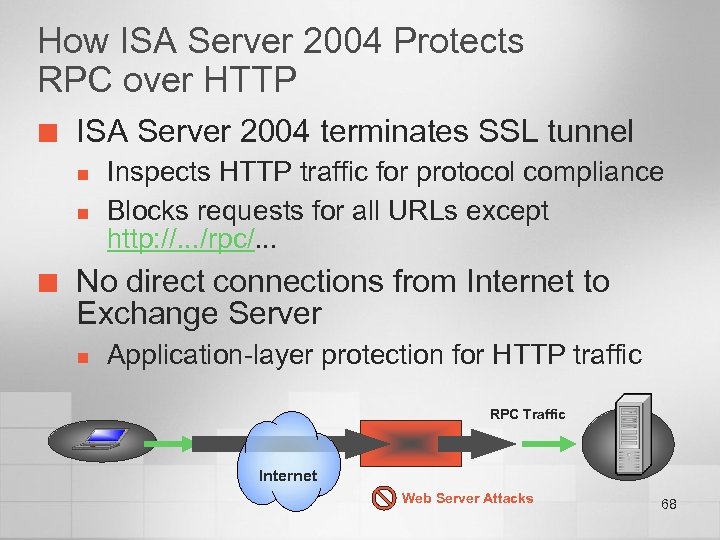 How ISA Server 2004 Protects RPC over HTTP ¢ ISA Server 2004 terminates SSL tunnel n n ¢ Inspects HTTP traffic for protocol compliance Blocks requests for all URLs except http: //. . . /rpc/. . . No direct connections from Internet to Exchange Server n Application-layer protection for HTTP traffic RPC Traffic Internet Web Server Attacks 68
How ISA Server 2004 Protects RPC over HTTP ¢ ISA Server 2004 terminates SSL tunnel n n ¢ Inspects HTTP traffic for protocol compliance Blocks requests for all URLs except http: //. . . /rpc/. . . No direct connections from Internet to Exchange Server n Application-layer protection for HTTP traffic RPC Traffic Internet Web Server Attacks 68
 How ISA Server 2004 Protects SMTP Traffic ¢ SMTP-based Attacks n n ¢ Invalid, overly long, or unusual SMTP commands to attack a mail server or to gather recipient information Attacks against recipients by including malicious content, such as worms ISA Server 2004 Protects Mail Servers n n Enforces compliance of SMTP commands with standards Blocks disallowed SMTP commands Blocks messages with disallowed attachment types, content, recipient, or sender Blocks non-SMTP traffic No Exchange Server deployment is complete without ISA Server 2004 69
How ISA Server 2004 Protects SMTP Traffic ¢ SMTP-based Attacks n n ¢ Invalid, overly long, or unusual SMTP commands to attack a mail server or to gather recipient information Attacks against recipients by including malicious content, such as worms ISA Server 2004 Protects Mail Servers n n Enforces compliance of SMTP commands with standards Blocks disallowed SMTP commands Blocks messages with disallowed attachment types, content, recipient, or sender Blocks non-SMTP traffic No Exchange Server deployment is complete without ISA Server 2004 69
 Easy Configuration and Administration of E-Mail Access Mail Publishing Wizard makes configuration easy and prevents configuration mistakes 70
Easy Configuration and Administration of E-Mail Access Mail Publishing Wizard makes configuration easy and prevents configuration mistakes 70
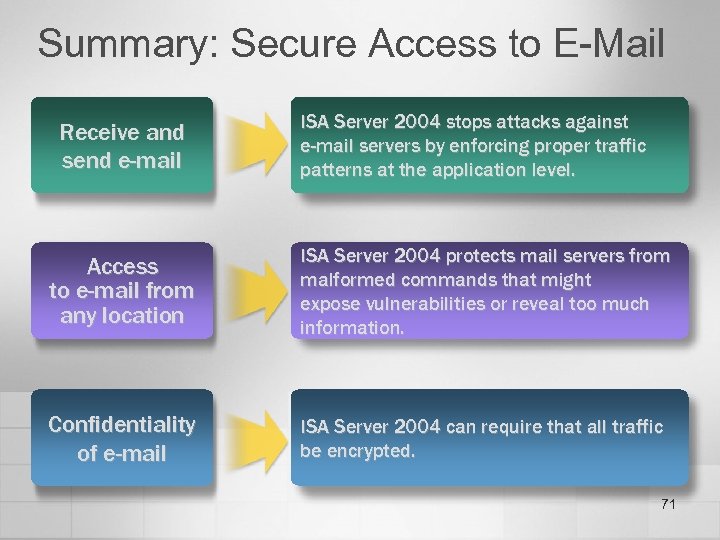 Summary: Secure Access to E-Mail Receive and send e-mail ISA Server 2004 stops attacks against e-mail servers by enforcing proper traffic patterns at the application level. Access to e-mail from any location ISA Server 2004 protects mail servers from malformed commands that might expose vulnerabilities or reveal too much information. Confidentiality of e-mail ISA Server 2004 can require that all traffic be encrypted. 71
Summary: Secure Access to E-Mail Receive and send e-mail ISA Server 2004 stops attacks against e-mail servers by enforcing proper traffic patterns at the application level. Access to e-mail from any location ISA Server 2004 protects mail servers from malformed commands that might expose vulnerabilities or reveal too much information. Confidentiality of e-mail ISA Server 2004 can require that all traffic be encrypted. 71
 Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 72
Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 72
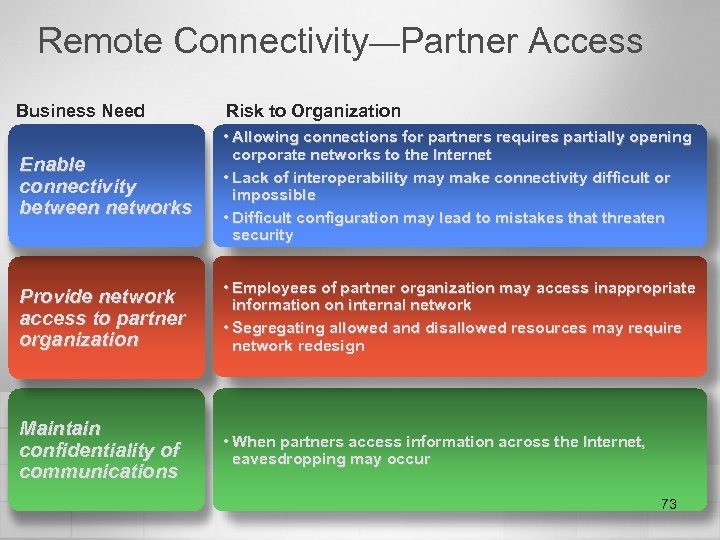 Remote Connectivity—Partner Access Business Need Risk to Organization Enable connectivity between networks • Allowing connections for partners requires partially opening corporate networks to the Internet • Lack of interoperability make connectivity difficult or impossible • Difficult configuration may lead to mistakes that threaten security Provide network access to partner organization • Employees of partner organization may access inappropriate information on internal network • Segregating allowed and disallowed resources may require network redesign Maintain confidentiality of communications • When partners access information across the Internet, eavesdropping may occur 73
Remote Connectivity—Partner Access Business Need Risk to Organization Enable connectivity between networks • Allowing connections for partners requires partially opening corporate networks to the Internet • Lack of interoperability make connectivity difficult or impossible • Difficult configuration may lead to mistakes that threaten security Provide network access to partner organization • Employees of partner organization may access inappropriate information on internal network • Segregating allowed and disallowed resources may require network redesign Maintain confidentiality of communications • When partners access information across the Internet, eavesdropping may occur 73
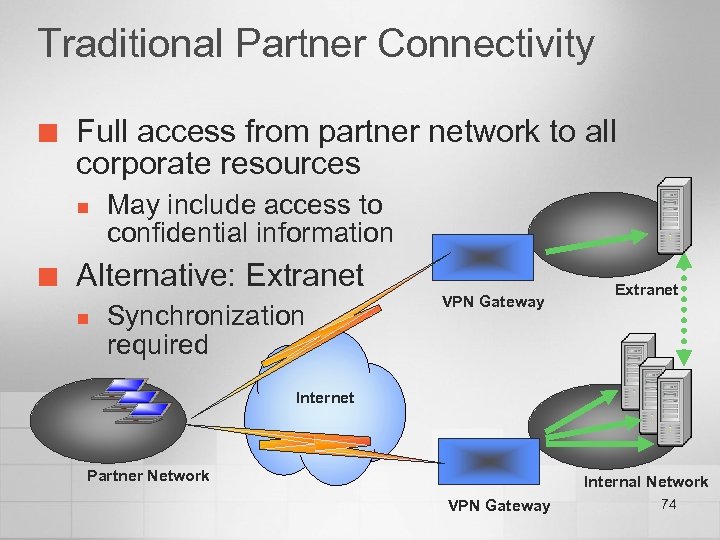 Traditional Partner Connectivity ¢ Full access from partner network to all corporate resources n ¢ May include access to confidential information Alternative: Extranet n Synchronization required VPN Gateway Extranet Internet Partner Network Internal Network VPN Gateway 74
Traditional Partner Connectivity ¢ Full access from partner network to all corporate resources n ¢ May include access to confidential information Alternative: Extranet n Synchronization required VPN Gateway Extranet Internet Partner Network Internal Network VPN Gateway 74
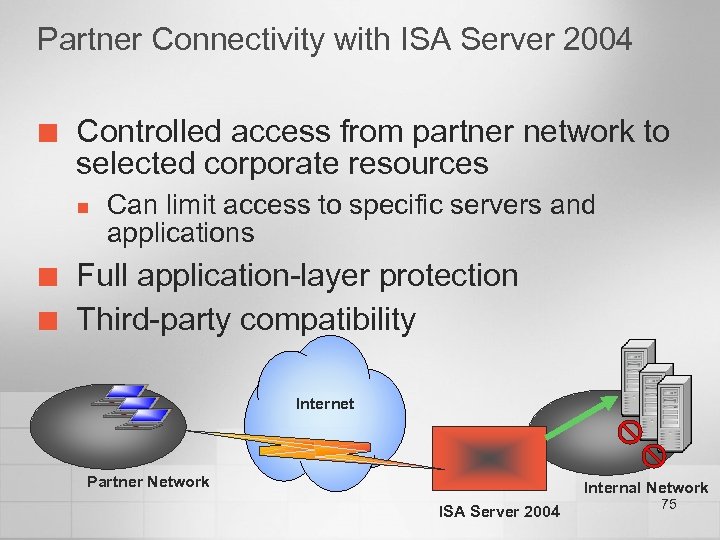 Partner Connectivity with ISA Server 2004 ¢ Controlled access from partner network to selected corporate resources n ¢ ¢ Can limit access to specific servers and applications Full application-layer protection Third-party compatibility Internet Partner Network Internal Network ISA Server 2004 75
Partner Connectivity with ISA Server 2004 ¢ Controlled access from partner network to selected corporate resources n ¢ ¢ Can limit access to specific servers and applications Full application-layer protection Third-party compatibility Internet Partner Network Internal Network ISA Server 2004 75
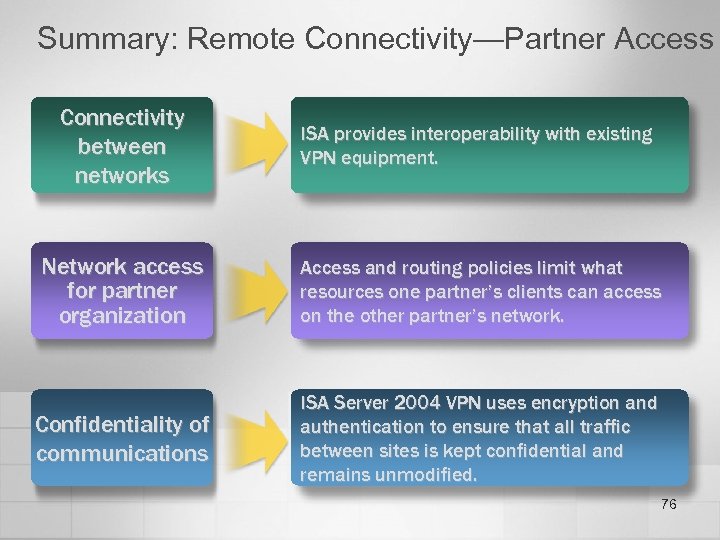 Summary: Remote Connectivity—Partner Access Connectivity between networks ISA provides interoperability with existing VPN equipment. Network access for partner organization Access and routing policies limit what resources one partner’s clients can access on the other partner’s network. Confidentiality of communications ISA Server 2004 VPN uses encryption and authentication to ensure that all traffic between sites is kept confidential and remains unmodified. 76
Summary: Remote Connectivity—Partner Access Connectivity between networks ISA provides interoperability with existing VPN equipment. Network access for partner organization Access and routing policies limit what resources one partner’s clients can access on the other partner’s network. Confidentiality of communications ISA Server 2004 VPN uses encryption and authentication to ensure that all traffic between sites is kept confidential and remains unmodified. 76
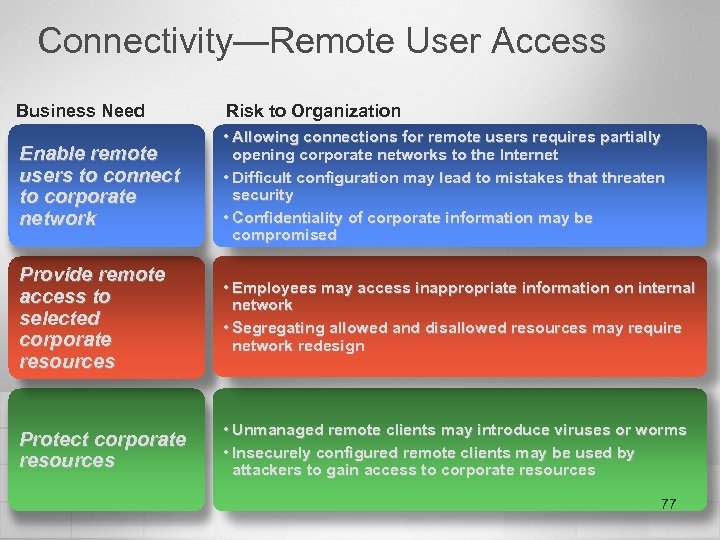 Connectivity—Remote User Access Business Need Risk to Organization Enable remote users to connect to corporate network • Allowing connections for remote users requires partially opening corporate networks to the Internet • Difficult configuration may lead to mistakes that threaten security • Confidentiality of corporate information may be compromised Provide remote access to selected corporate resources • Employees may access inappropriate information on internal network • Segregating allowed and disallowed resources may require network redesign Protect corporate resources • Unmanaged remote clients may introduce viruses or worms • Insecurely configured remote clients may be used by attackers to gain access to corporate resources 77
Connectivity—Remote User Access Business Need Risk to Organization Enable remote users to connect to corporate network • Allowing connections for remote users requires partially opening corporate networks to the Internet • Difficult configuration may lead to mistakes that threaten security • Confidentiality of corporate information may be compromised Provide remote access to selected corporate resources • Employees may access inappropriate information on internal network • Segregating allowed and disallowed resources may require network redesign Protect corporate resources • Unmanaged remote clients may introduce viruses or worms • Insecurely configured remote clients may be used by attackers to gain access to corporate resources 77
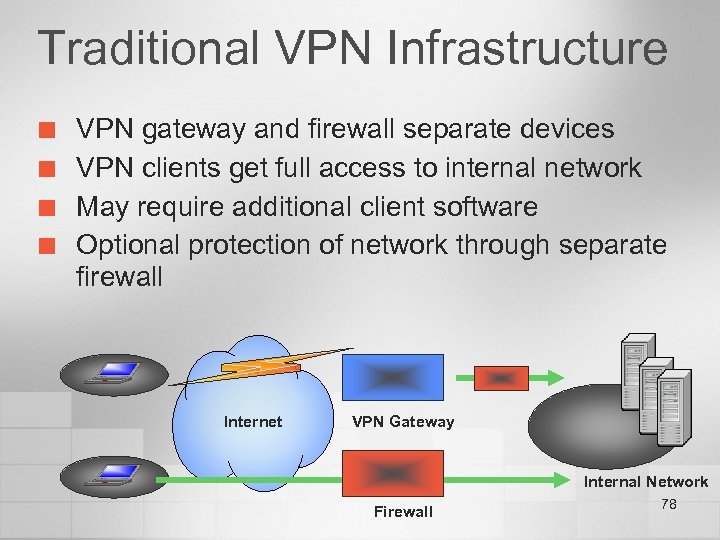 Traditional VPN Infrastructure ¢ ¢ VPN gateway and firewall separate devices VPN clients get full access to internal network May require additional client software Optional protection of network through separate firewall Internet VPN Gateway Internal Network Firewall 78
Traditional VPN Infrastructure ¢ ¢ VPN gateway and firewall separate devices VPN clients get full access to internal network May require additional client software Optional protection of network through separate firewall Internet VPN Gateway Internal Network Firewall 78
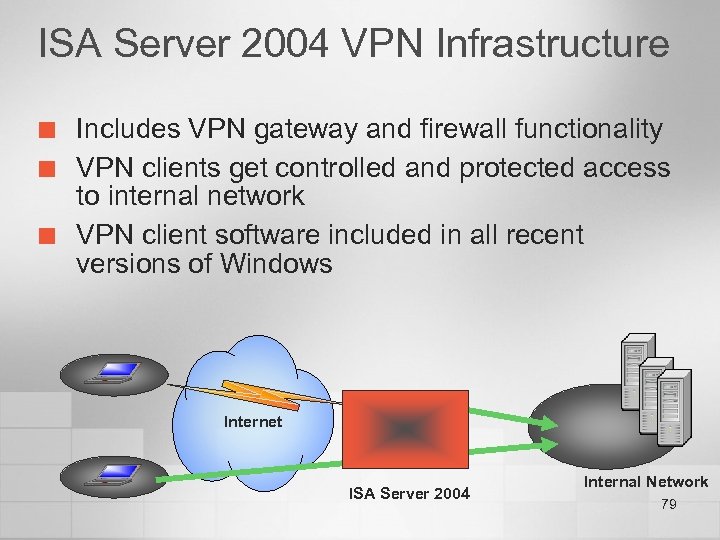 ISA Server 2004 VPN Infrastructure ¢ ¢ ¢ Includes VPN gateway and firewall functionality VPN clients get controlled and protected access to internal network VPN client software included in all recent versions of Windows Internet ISA Server 2004 Internal Network 79
ISA Server 2004 VPN Infrastructure ¢ ¢ ¢ Includes VPN gateway and firewall functionality VPN clients get controlled and protected access to internal network VPN client software included in all recent versions of Windows Internet ISA Server 2004 Internal Network 79
 Protecting Networks with ISA Server 2004 Network Access Quarantine ¢ Client script checks whether client meets corporate security policies n n n ¢ ¢ Personal firewall enabled? Latest virus definitions used? Required patches installed? If checks succeed, client gets full access If checks fail client gets disconnected after time-out period Goal: Prevent VPN clients that don’t meet security requirements from accessing network 80
Protecting Networks with ISA Server 2004 Network Access Quarantine ¢ Client script checks whether client meets corporate security policies n n n ¢ ¢ Personal firewall enabled? Latest virus definitions used? Required patches installed? If checks succeed, client gets full access If checks fail client gets disconnected after time-out period Goal: Prevent VPN clients that don’t meet security requirements from accessing network 80
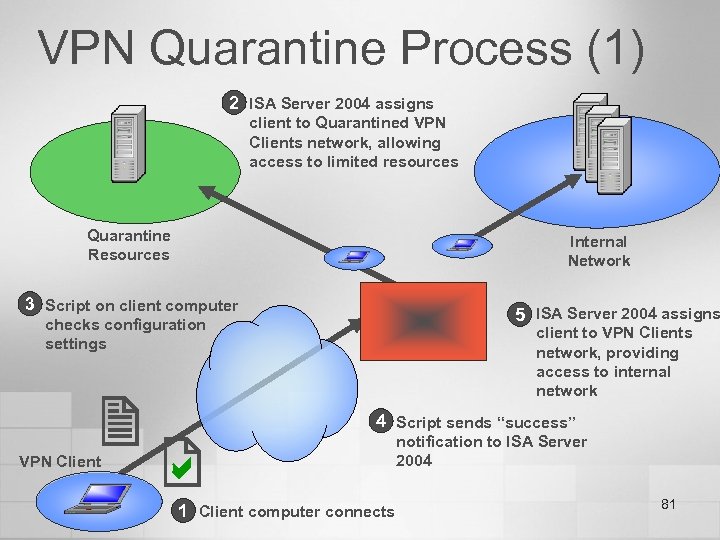 VPN Quarantine Process (1) 2 ISA Server 2004 assigns client to Quarantined VPN Clients network, allowing access to limited resources Quarantine Resources Internal Network 3 Script on client computer 5 ISA Server 2004 assigns checks configuration settings VPN Client client to VPN Clients network, providing access to internal network 4 Script sends “success” 1 Client computer connects notification to ISA Server 2004 81
VPN Quarantine Process (1) 2 ISA Server 2004 assigns client to Quarantined VPN Clients network, allowing access to limited resources Quarantine Resources Internal Network 3 Script on client computer 5 ISA Server 2004 assigns checks configuration settings VPN Client client to VPN Clients network, providing access to internal network 4 Script sends “success” 1 Client computer connects notification to ISA Server 2004 81
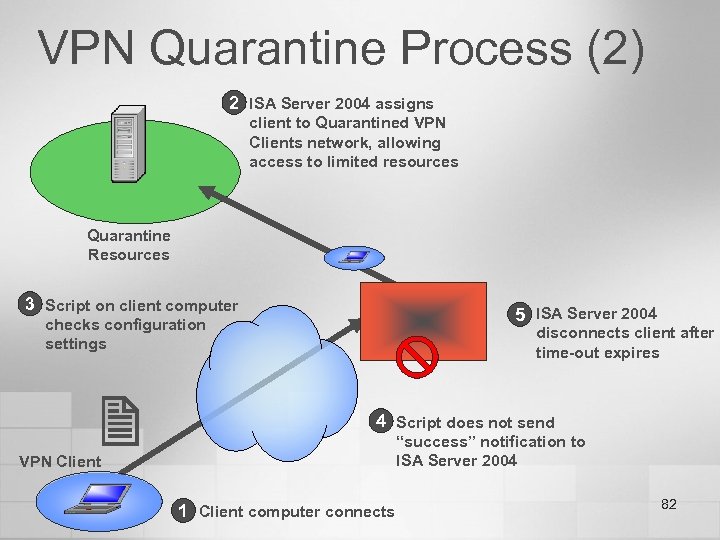 VPN Quarantine Process (2) 2 ISA Server 2004 assigns client to Quarantined VPN Clients network, allowing access to limited resources Quarantine Resources 3 Script on client computer 5 ISA Server 2004 checks configuration settings disconnects client after time-out expires 4 Script does not send “success” notification to ISA Server 2004 VPN Client 1 Client computer connects 82
VPN Quarantine Process (2) 2 ISA Server 2004 assigns client to Quarantined VPN Clients network, allowing access to limited resources Quarantine Resources 3 Script on client computer 5 ISA Server 2004 checks configuration settings disconnects client after time-out expires 4 Script does not send “success” notification to ISA Server 2004 VPN Client 1 Client computer connects 82
 Ease of Use for VPNs 83
Ease of Use for VPNs 83
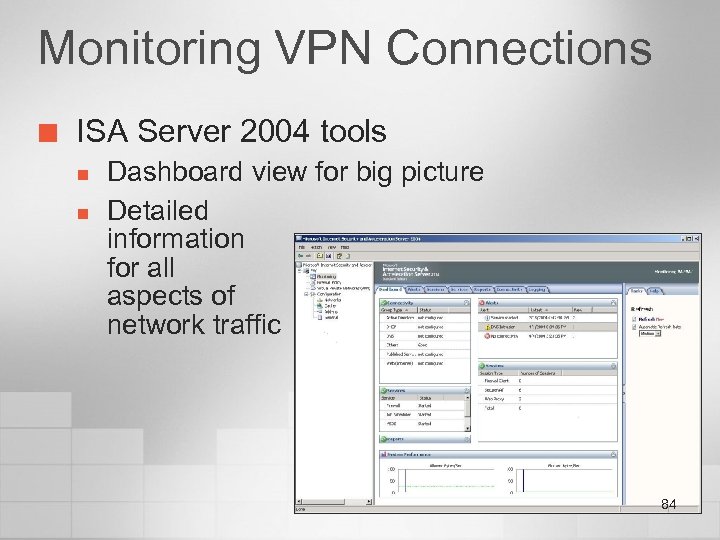 Monitoring VPN Connections ¢ ISA Server 2004 tools n n Dashboard view for big picture Detailed information for all aspects of network traffic 84
Monitoring VPN Connections ¢ ISA Server 2004 tools n n Dashboard view for big picture Detailed information for all aspects of network traffic 84
 Summary: Connectivity—Remote User Access Remote connectivity ISA Server 2004 allows remote access to the corporate network from anywhere. Access to selected corporate resources ISA Server 2004 allows control over which resources corporate resources remote users can access. Protection of corporate resources ISA Server 2004 protects the corporate network and the VPN clients. 85
Summary: Connectivity—Remote User Access Remote connectivity ISA Server 2004 allows remote access to the corporate network from anywhere. Access to selected corporate resources ISA Server 2004 allows control over which resources corporate resources remote users can access. Protection of corporate resources ISA Server 2004 protects the corporate network and the VPN clients. 85
 Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 86
Protecting Microsoft Applications Secure Application Access Secure Access to E-Mail Remote Connectivity Integrated Branch Office Solution n Help secure access to IIS, Microsoft Share. Point®, and other application servers n Allow access to Exchange servers while protecting them n Connecting offices, partners, and users by using ISA Server 2004 and Windows Server 2003 n Branch office security 86
 Integrated Branch Office Solution Business Need Risk to Organization Connect branch office networks to the main network • Branch office connections must be established across an insecure network and confidentiality of corporate information may be compromised • Equipment from multiple vendors may not work with each other • Site-to-site connectivity can be difficult to configure Provide secure Internet access from branch offices • Employee access at branch offices may expose the network to worms, viruses, and hacker attacks • Employees at branch offices may access inappropriate content • Maintaining a consistent configuration is difficult Utilize limited bandwidth at the branch office efficiently • Branch office connectivity may not be sufficient to allow for efficient Internet access • Bandwidth used for Internet access can slow down access to corporate network 87
Integrated Branch Office Solution Business Need Risk to Organization Connect branch office networks to the main network • Branch office connections must be established across an insecure network and confidentiality of corporate information may be compromised • Equipment from multiple vendors may not work with each other • Site-to-site connectivity can be difficult to configure Provide secure Internet access from branch offices • Employee access at branch offices may expose the network to worms, viruses, and hacker attacks • Employees at branch offices may access inappropriate content • Maintaining a consistent configuration is difficult Utilize limited bandwidth at the branch office efficiently • Branch office connectivity may not be sufficient to allow for efficient Internet access • Bandwidth used for Internet access can slow down access to corporate network 87
 How ISA Server 2004 Enables Branch Office Connections ¢ Broad protocol support n n n ¢ PPTP L 2 TP/IPSec tunnel mode for interoperability with existing VPN gateways: fully tested and supported Authentication and encryption n n Leverages Windows remote access capabilities Range of authentication methods n ¢ Active Directory, RADIUS, passwords, certificates Configurable encryption methods help ensure confidentiality of communications Fine-grained control over traffic between networks 88
How ISA Server 2004 Enables Branch Office Connections ¢ Broad protocol support n n n ¢ PPTP L 2 TP/IPSec tunnel mode for interoperability with existing VPN gateways: fully tested and supported Authentication and encryption n n Leverages Windows remote access capabilities Range of authentication methods n ¢ Active Directory, RADIUS, passwords, certificates Configurable encryption methods help ensure confidentiality of communications Fine-grained control over traffic between networks 88
 Easy Configuration and Administration of Branch Office Connections ¢ ¢ ¢ Administrators can duplicate existing ISA Server 2004 configuration using XML export/import Easy-to-use wizards simplify administration for branch office administrators Remote administration using MMC, Terminal Services, or Remote Desktop Connection Full integration with Active Directory Easy-to-use monitoring tools Unified policy user interface allows administration of all network access in one location Administrators can use one tool to control all network traffic at branch office 89
Easy Configuration and Administration of Branch Office Connections ¢ ¢ ¢ Administrators can duplicate existing ISA Server 2004 configuration using XML export/import Easy-to-use wizards simplify administration for branch office administrators Remote administration using MMC, Terminal Services, or Remote Desktop Connection Full integration with Active Directory Easy-to-use monitoring tools Unified policy user interface allows administration of all network access in one location Administrators can use one tool to control all network traffic at branch office 89
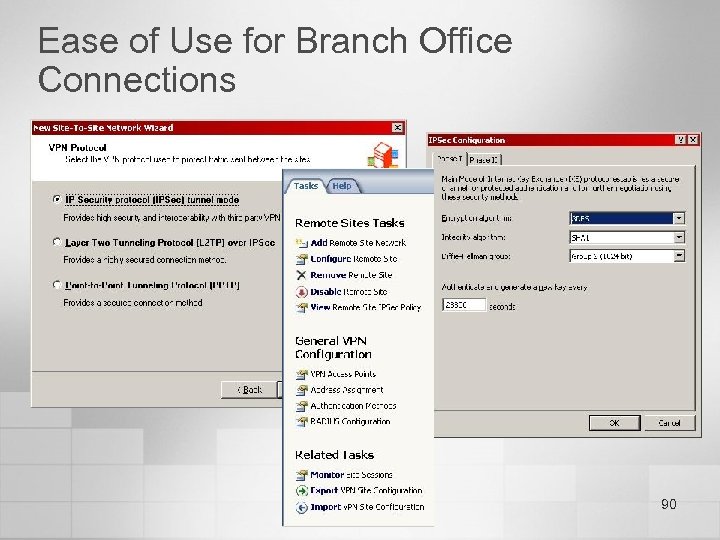 Ease of Use for Branch Office Connections 90
Ease of Use for Branch Office Connections 90
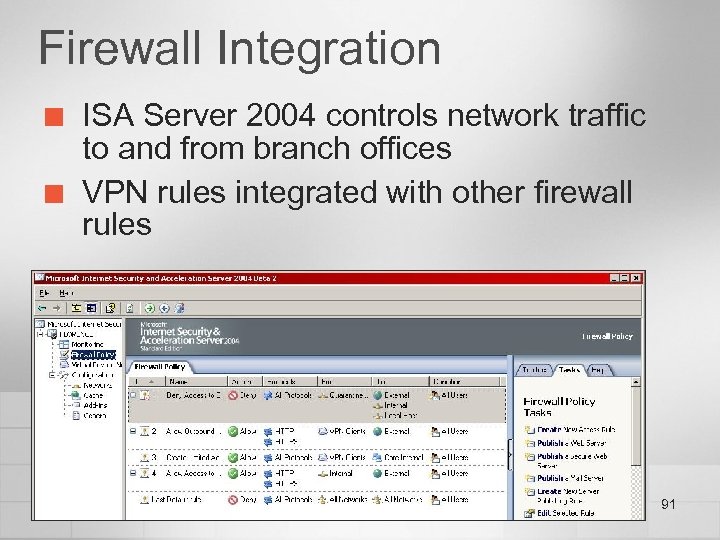 Firewall Integration ¢ ¢ ISA Server 2004 controls network traffic to and from branch offices VPN rules integrated with other firewall rules 91
Firewall Integration ¢ ¢ ISA Server 2004 controls network traffic to and from branch offices VPN rules integrated with other firewall rules 91
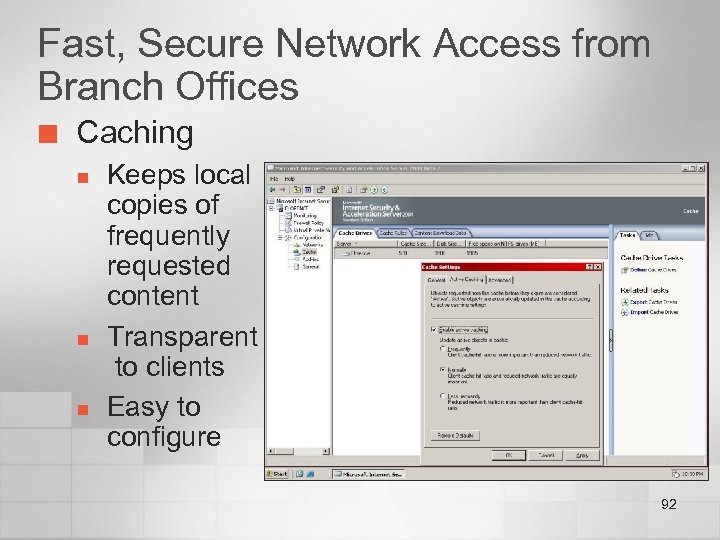 Fast, Secure Network Access from Branch Offices ¢ Caching n n n Keeps local copies of frequently requested content Transparent to clients Easy to configure 92
Fast, Secure Network Access from Branch Offices ¢ Caching n n n Keeps local copies of frequently requested content Transparent to clients Easy to configure 92
 Integrated Solution ¢ Realize savings through integration n n One-stop solution for Internet access Provides firewall, access control, publishing, and VPN in a single solution Provides centralized administration and logging ISA Server 2004 can easily scale as organization grows Ideal solution for branch offices 93
Integrated Solution ¢ Realize savings through integration n n One-stop solution for Internet access Provides firewall, access control, publishing, and VPN in a single solution Provides centralized administration and logging ISA Server 2004 can easily scale as organization grows Ideal solution for branch offices 93
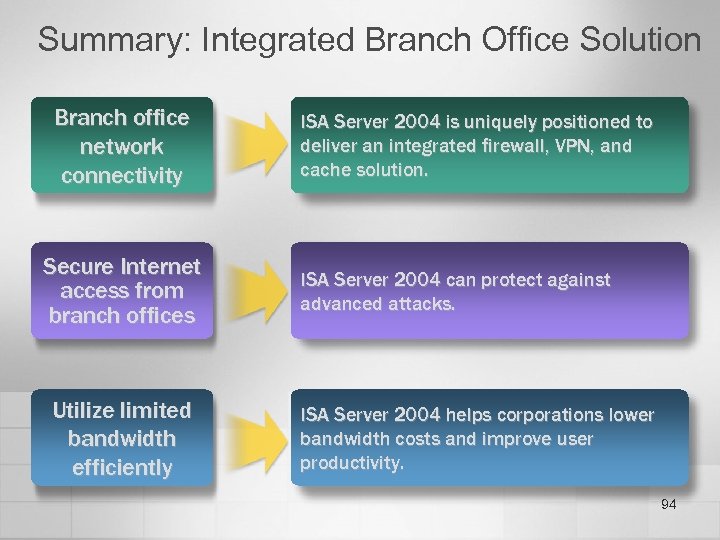 Summary: Integrated Branch Office Solution Branch office network connectivity Secure Internet access from branch offices Utilize limited bandwidth efficiently ISA Server 2004 is uniquely positioned to deliver an integrated firewall, VPN, and cache solution. ISA Server 2004 can protect against advanced attacks. ISA Server 2004 helps corporations lower bandwidth costs and improve user productivity. 94
Summary: Integrated Branch Office Solution Branch office network connectivity Secure Internet access from branch offices Utilize limited bandwidth efficiently ISA Server 2004 is uniquely positioned to deliver an integrated firewall, VPN, and cache solution. ISA Server 2004 can protect against advanced attacks. ISA Server 2004 helps corporations lower bandwidth costs and improve user productivity. 94
 3. Selling Strategies and Partner Offerings
3. Selling Strategies and Partner Offerings
 ISA Server 2004 Sales Opportunities When to Recommend ¢ Recommend ISA Server 2004 to customers who: n n n Need a new or supplemental firewall Use IIS, Share. Point Portal Server, Exchange Server, or Windows Server 2003 Experience slow network performance Run ISA Server 2000 Run Microsoft Small Business Server (SBS) 96
ISA Server 2004 Sales Opportunities When to Recommend ¢ Recommend ISA Server 2004 to customers who: n n n Need a new or supplemental firewall Use IIS, Share. Point Portal Server, Exchange Server, or Windows Server 2003 Experience slow network performance Run ISA Server 2000 Run Microsoft Small Business Server (SBS) 96
 ISA Server 2004 Sales Opportunities New or Supplemental Firewall ¢ Advanced Protection n ¢ Ease of Use n n ¢ Advanced application-layer filtering Quick and easy to configure Fits into existing Microsoft environment Fast, Secure Access Implement Internet access control n Achieve bandwidth and network efficiency n Immediate security and savings ISA Server 2004 provides the best protection for Microsoft-based networks n 97
ISA Server 2004 Sales Opportunities New or Supplemental Firewall ¢ Advanced Protection n ¢ Ease of Use n n ¢ Advanced application-layer filtering Quick and easy to configure Fits into existing Microsoft environment Fast, Secure Access Implement Internet access control n Achieve bandwidth and network efficiency n Immediate security and savings ISA Server 2004 provides the best protection for Microsoft-based networks n 97
 ISA Server 2004 Sales Opportunities New or Supplemental Firewall ¢ Use as main firewall n ¢ Add new functionality to existing firewalls n n n ¢ ISA Server 2004 provides all the protection customers expect from a firewall, VPN, and caching solution Caching Access control Application-layer inspection Defense-in-depth by using multiple firewall products ISA Server 2004 adds value by itself or when used in conjunction with an existing traditional firewall 98
ISA Server 2004 Sales Opportunities New or Supplemental Firewall ¢ Use as main firewall n ¢ Add new functionality to existing firewalls n n n ¢ ISA Server 2004 provides all the protection customers expect from a firewall, VPN, and caching solution Caching Access control Application-layer inspection Defense-in-depth by using multiple firewall products ISA Server 2004 adds value by itself or when used in conjunction with an existing traditional firewall 98
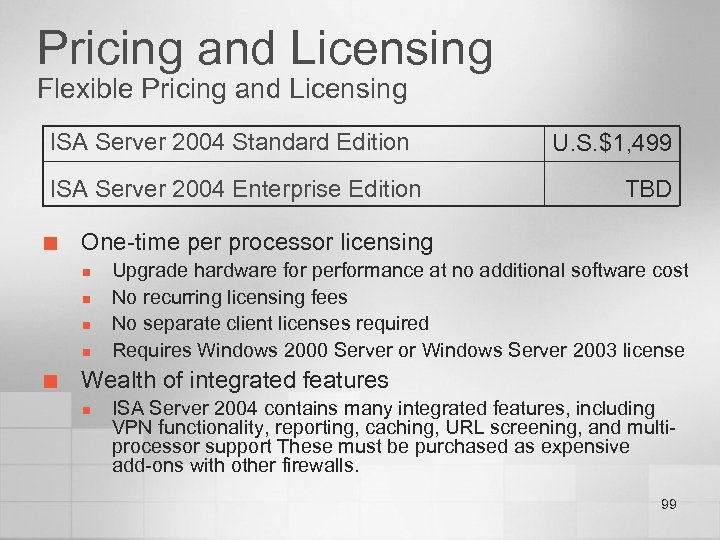 Pricing and Licensing Flexible Pricing and Licensing ISA Server 2004 Standard Edition ISA Server 2004 Enterprise Edition ¢ TBD One-time per processor licensing n n ¢ U. S. $1, 499 Upgrade hardware for performance at no additional software cost No recurring licensing fees No separate client licenses required Requires Windows 2000 Server or Windows Server 2003 license Wealth of integrated features n ISA Server 2004 contains many integrated features, including VPN functionality, reporting, caching, URL screening, and multiprocessor support These must be purchased as expensive add-ons with other firewalls. 99
Pricing and Licensing Flexible Pricing and Licensing ISA Server 2004 Standard Edition ISA Server 2004 Enterprise Edition ¢ TBD One-time per processor licensing n n ¢ U. S. $1, 499 Upgrade hardware for performance at no additional software cost No recurring licensing fees No separate client licenses required Requires Windows 2000 Server or Windows Server 2003 license Wealth of integrated features n ISA Server 2004 contains many integrated features, including VPN functionality, reporting, caching, URL screening, and multiprocessor support These must be purchased as expensive add-ons with other firewalls. 99
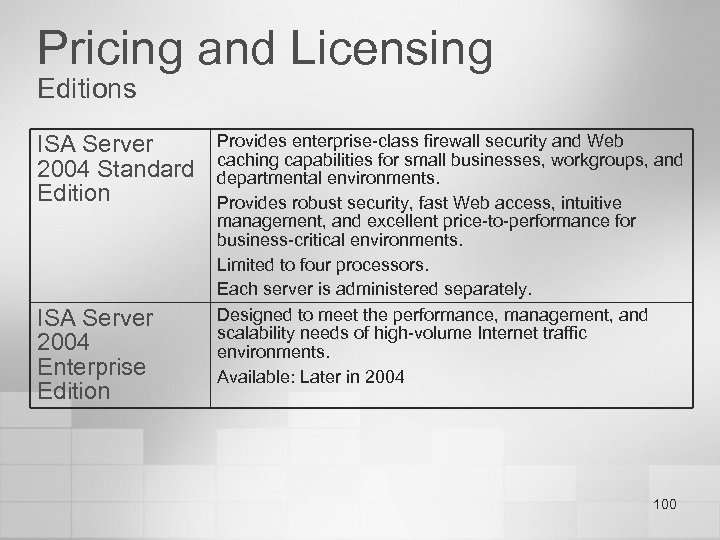 Pricing and Licensing Editions ISA Server 2004 Standard Edition ISA Server 2004 Enterprise Edition Provides enterprise-class firewall security and Web caching capabilities for small businesses, workgroups, and departmental environments. Provides robust security, fast Web access, intuitive management, and excellent price-to-performance for business-critical environments. Limited to four processors. Each server is administered separately. Designed to meet the performance, management, and scalability needs of high-volume Internet traffic environments. Available: Later in 2004 100
Pricing and Licensing Editions ISA Server 2004 Standard Edition ISA Server 2004 Enterprise Edition Provides enterprise-class firewall security and Web caching capabilities for small businesses, workgroups, and departmental environments. Provides robust security, fast Web access, intuitive management, and excellent price-to-performance for business-critical environments. Limited to four processors. Each server is administered separately. Designed to meet the performance, management, and scalability needs of high-volume Internet traffic environments. Available: Later in 2004 100
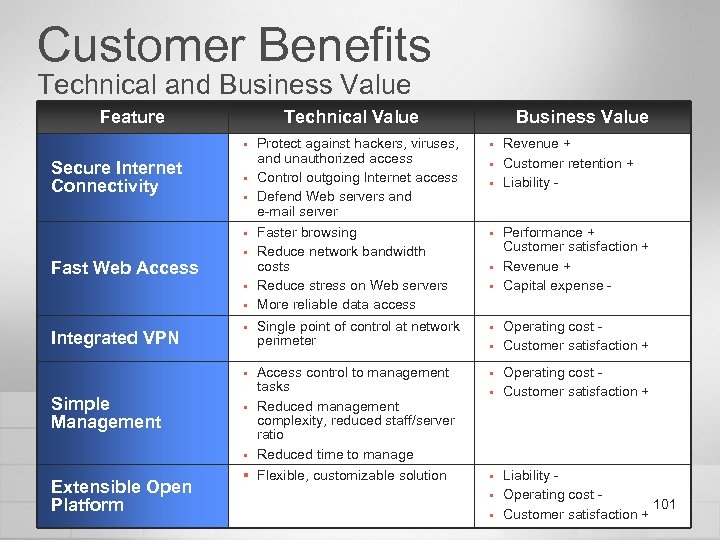 Customer Benefits Technical and Business Value Feature Technical Value § Secure Internet Connectivity § § § Fast Web Access § § § Integrated VPN § § Simple Management § § Extensible Open Platform Business Value Protect against hackers, viruses, and unauthorized access Control outgoing Internet access Defend Web servers and e-mail server § Faster browsing Reduce network bandwidth costs Reduce stress on Web servers More reliable data access § Single point of control at network perimeter § Access control to management tasks Reduced management complexity, reduced staff/server ratio Reduced time to manage § § Flexible, customizable solution § § § § § Revenue + Customer retention + Liability Performance + Customer satisfaction + Revenue + Capital expense Operating cost Customer satisfaction + Liability Operating cost 101 Customer satisfaction +
Customer Benefits Technical and Business Value Feature Technical Value § Secure Internet Connectivity § § § Fast Web Access § § § Integrated VPN § § Simple Management § § Extensible Open Platform Business Value Protect against hackers, viruses, and unauthorized access Control outgoing Internet access Defend Web servers and e-mail server § Faster browsing Reduce network bandwidth costs Reduce stress on Web servers More reliable data access § Single point of control at network perimeter § Access control to management tasks Reduced management complexity, reduced staff/server ratio Reduced time to manage § § Flexible, customizable solution § § § § § Revenue + Customer retention + Liability Performance + Customer satisfaction + Revenue + Capital expense Operating cost Customer satisfaction + Liability Operating cost 101 Customer satisfaction +
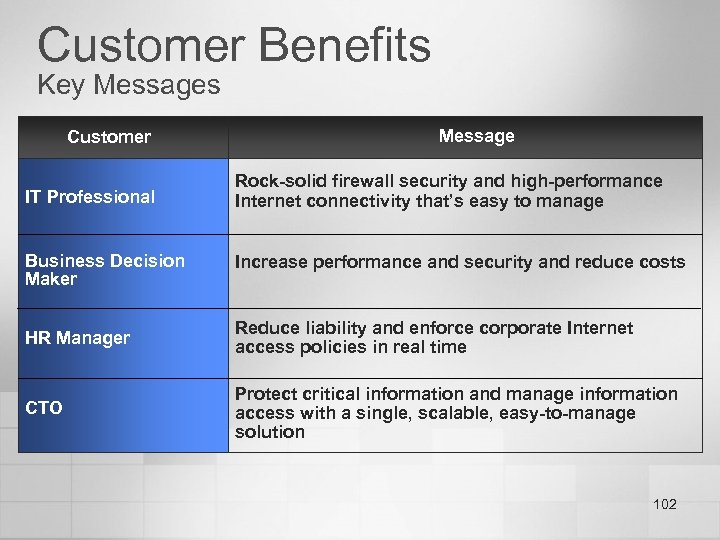 Customer Benefits Key Messages Customer Message IT Professional Rock-solid firewall security and high-performance Internet connectivity that’s easy to manage Business Decision Maker Increase performance and security and reduce costs HR Manager Reduce liability and enforce corporate Internet access policies in real time CTO Protect critical information and manage information access with a single, scalable, easy-to-manage solution 102
Customer Benefits Key Messages Customer Message IT Professional Rock-solid firewall security and high-performance Internet connectivity that’s easy to manage Business Decision Maker Increase performance and security and reduce costs HR Manager Reduce liability and enforce corporate Internet access policies in real time CTO Protect critical information and manage information access with a single, scalable, easy-to-manage solution 102
 ISA Server 2004 Sales Opportunities Use with IIS and Share. Point ¢ ¢ Built from the ground up to support Web protocols Efficient content checking Protection of critical resources Allows controlled, authenticated external access to Share. Point resources No IIS or Share. Point deployment is complete without ISA Server 2004 103
ISA Server 2004 Sales Opportunities Use with IIS and Share. Point ¢ ¢ Built from the ground up to support Web protocols Efficient content checking Protection of critical resources Allows controlled, authenticated external access to Share. Point resources No IIS or Share. Point deployment is complete without ISA Server 2004 103
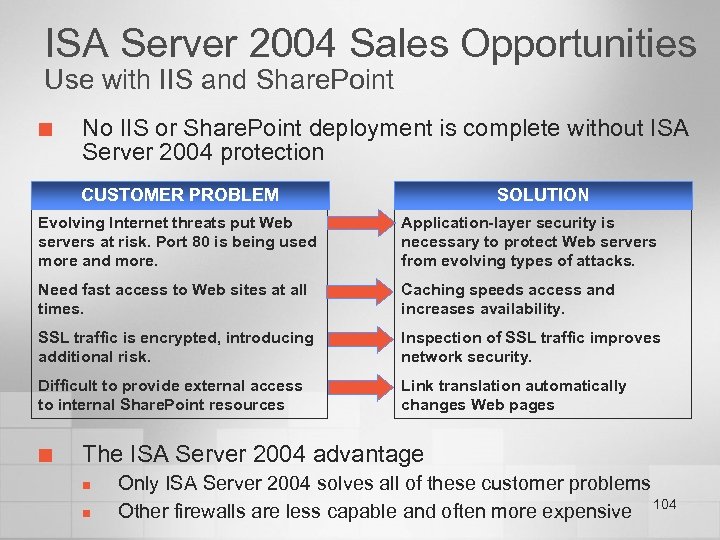 ISA Server 2004 Sales Opportunities Use with IIS and Share. Point ¢ No IIS or Share. Point deployment is complete without ISA Server 2004 protection CUSTOMER PROBLEM SOLUTION Evolving Internet threats put Web servers at risk. Port 80 is being used more and more. Application-layer security is necessary to protect Web servers from evolving types of attacks. Need fast access to Web sites at all times. Caching speeds access and increases availability. SSL traffic is encrypted, introducing additional risk. Inspection of SSL traffic improves network security. Difficult to provide external access to internal Share. Point resources Link translation automatically changes Web pages ¢ The ISA Server 2004 advantage n n Only ISA Server 2004 solves all of these customer problems Other firewalls are less capable and often more expensive 104
ISA Server 2004 Sales Opportunities Use with IIS and Share. Point ¢ No IIS or Share. Point deployment is complete without ISA Server 2004 protection CUSTOMER PROBLEM SOLUTION Evolving Internet threats put Web servers at risk. Port 80 is being used more and more. Application-layer security is necessary to protect Web servers from evolving types of attacks. Need fast access to Web sites at all times. Caching speeds access and increases availability. SSL traffic is encrypted, introducing additional risk. Inspection of SSL traffic improves network security. Difficult to provide external access to internal Share. Point resources Link translation automatically changes Web pages ¢ The ISA Server 2004 advantage n n Only ISA Server 2004 solves all of these customer problems Other firewalls are less capable and often more expensive 104
 ISA Server 2004 Sales Opportunities Use with Exchange Server ¢ Support for OWA n ¢ Support for secure access to Exchange Server using the native Outlook protocols n ¢ ¢ Secures and accelerates access Users can use their regular client Support for all major mail protocols Content checking to reduce unwanted and dangerous e-mail No Exchange deployment is complete without ISA Server 2004 105
ISA Server 2004 Sales Opportunities Use with Exchange Server ¢ Support for OWA n ¢ Support for secure access to Exchange Server using the native Outlook protocols n ¢ ¢ Secures and accelerates access Users can use their regular client Support for all major mail protocols Content checking to reduce unwanted and dangerous e-mail No Exchange deployment is complete without ISA Server 2004 105
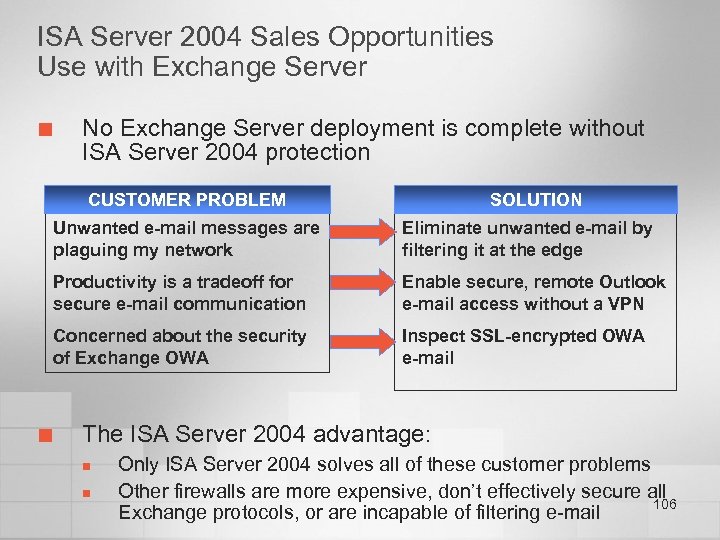 ISA Server 2004 Sales Opportunities Use with Exchange Server ¢ No Exchange Server deployment is complete without ISA Server 2004 protection CUSTOMER PROBLEM SOLUTION Unwanted e-mail messages are plaguing my network Eliminate unwanted e-mail by filtering it at the edge Productivity is a tradeoff for secure e-mail communication Enable secure, remote Outlook e-mail access without a VPN Concerned about the security of Exchange OWA Inspect SSL-encrypted OWA e-mail ¢ The ISA Server 2004 advantage: n n Only ISA Server 2004 solves all of these customer problems Other firewalls are more expensive, don’t effectively secure all 106 Exchange protocols, or are incapable of filtering e-mail
ISA Server 2004 Sales Opportunities Use with Exchange Server ¢ No Exchange Server deployment is complete without ISA Server 2004 protection CUSTOMER PROBLEM SOLUTION Unwanted e-mail messages are plaguing my network Eliminate unwanted e-mail by filtering it at the edge Productivity is a tradeoff for secure e-mail communication Enable secure, remote Outlook e-mail access without a VPN Concerned about the security of Exchange OWA Inspect SSL-encrypted OWA e-mail ¢ The ISA Server 2004 advantage: n n Only ISA Server 2004 solves all of these customer problems Other firewalls are more expensive, don’t effectively secure all 106 Exchange protocols, or are incapable of filtering e-mail
 ISA Server 2004 Sales Opportunities Use with Windows Server 2003 ¢ Integrates with Active Directory n n ¢ Builds on security features of Windows Server 2003 n n ¢ ¢ Uses existing user accounts for access control Centralized, easy administration Full-featured VPN capabilities with the ease of use of ISA Server 2004 Security templates and Group Policy to lock down computers ISA Server 2004 is built for Windows protocols Support for Network Access Quarantine 107
ISA Server 2004 Sales Opportunities Use with Windows Server 2003 ¢ Integrates with Active Directory n n ¢ Builds on security features of Windows Server 2003 n n ¢ ¢ Uses existing user accounts for access control Centralized, easy administration Full-featured VPN capabilities with the ease of use of ISA Server 2004 Security templates and Group Policy to lock down computers ISA Server 2004 is built for Windows protocols Support for Network Access Quarantine 107
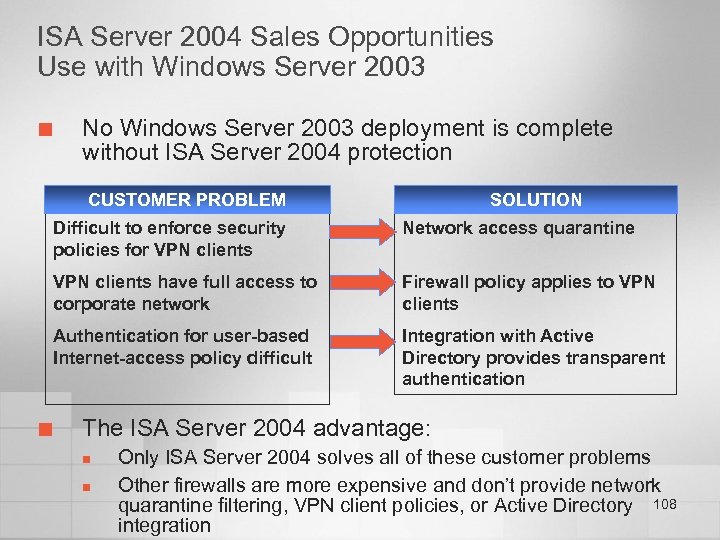 ISA Server 2004 Sales Opportunities Use with Windows Server 2003 ¢ No Windows Server 2003 deployment is complete without ISA Server 2004 protection CUSTOMER PROBLEM SOLUTION Difficult to enforce security policies for VPN clients Network access quarantine VPN clients have full access to corporate network Firewall policy applies to VPN clients Authentication for user-based Internet-access policy difficult Integration with Active Directory provides transparent authentication ¢ The ISA Server 2004 advantage: n n Only ISA Server 2004 solves all of these customer problems Other firewalls are more expensive and don’t provide network quarantine filtering, VPN client policies, or Active Directory 108 integration
ISA Server 2004 Sales Opportunities Use with Windows Server 2003 ¢ No Windows Server 2003 deployment is complete without ISA Server 2004 protection CUSTOMER PROBLEM SOLUTION Difficult to enforce security policies for VPN clients Network access quarantine VPN clients have full access to corporate network Firewall policy applies to VPN clients Authentication for user-based Internet-access policy difficult Integration with Active Directory provides transparent authentication ¢ The ISA Server 2004 advantage: n n Only ISA Server 2004 solves all of these customer problems Other firewalls are more expensive and don’t provide network quarantine filtering, VPN client policies, or Active Directory 108 integration
 ISA Server 2004 Sales Opportunities Slow Network Performance ¢ ISA Server 2004 provides immediate performance enhancements n n Caching increases response time for Web requests, increasing user productivity Caching reduces bandwidth requirements, saving money Can be implemented easily and without interruption in service Does not require network reconfiguration Immediate, measurable benefits for existing networks 109
ISA Server 2004 Sales Opportunities Slow Network Performance ¢ ISA Server 2004 provides immediate performance enhancements n n Caching increases response time for Web requests, increasing user productivity Caching reduces bandwidth requirements, saving money Can be implemented easily and without interruption in service Does not require network reconfiguration Immediate, measurable benefits for existing networks 109
 ISA Server 2004 Sales Opportunities Reasons to Upgrade from ISA Server 2000 ¢ Improve on ISA Server 2000 n n n More advanced application-layer protection Improved ease of use High performance • Multiple network support • Support for more protocols • New policy model • Packet filtering on all interfaces • Application-layer filtering • Better performance • Integrated policy enforcement for VPN clients • VPN client quarantine • Better RPC publishing • New authentication options • Real-time monitoring • Easier administration tools 110
ISA Server 2004 Sales Opportunities Reasons to Upgrade from ISA Server 2000 ¢ Improve on ISA Server 2000 n n n More advanced application-layer protection Improved ease of use High performance • Multiple network support • Support for more protocols • New policy model • Packet filtering on all interfaces • Application-layer filtering • Better performance • Integrated policy enforcement for VPN clients • VPN client quarantine • Better RPC publishing • New authentication options • Real-time monitoring • Easier administration tools 110
 ISA Server 2004 Sales Opportunities Use with Microsoft Small Business Server ¢ ISA Server 2004 is included only with SBS Premium Edition n ¢ SBS limited to 75 users n ¢ As organization grows, investment in SBS can be leveraged by moving firewall policies to a separate server that is running the same firewall software Moving ISA Server 2004 to a separate computer increases security n ¢ SBS Standard Edition only includes very limited firewall functionality Many customers want firewall to be separate from SBS Many security professionals recommend moving the firewall functionality to a separate computer to increase security Added protection for small businesses 111
ISA Server 2004 Sales Opportunities Use with Microsoft Small Business Server ¢ ISA Server 2004 is included only with SBS Premium Edition n ¢ SBS limited to 75 users n ¢ As organization grows, investment in SBS can be leveraged by moving firewall policies to a separate server that is running the same firewall software Moving ISA Server 2004 to a separate computer increases security n ¢ SBS Standard Edition only includes very limited firewall functionality Many customers want firewall to be separate from SBS Many security professionals recommend moving the firewall functionality to a separate computer to increase security Added protection for small businesses 111
 ISA Server 2004 Partner Products (1) Enhance existing features and add new features ¢ Application Filters n ¢ Caching and Distribution n ¢ Enhance ISA Server with network-level scalability, fault tolerance, and load balancing. Intrusion Detection n ¢ Intercept viruses, malicious code or other inappropriate content at your network's Internet gateway. High Availability and Load Balancing n ¢ Improve the caching capabilities of ISA Server or create content distribution networks that store content closer to end users and provide centralized delivery, management, and support for different content types. Content Security n ¢ Improve security and interoperability for other protocols with applicationlayer inspection Recognize and react in real time to hacking attempts. Monitor incoming traffic, and trigger responses according to alarms and events. Monitoring and Administration n Extend the maintenance and management features of ISA Server to make day-to-day monitoring and administration tasks easier. 112
ISA Server 2004 Partner Products (1) Enhance existing features and add new features ¢ Application Filters n ¢ Caching and Distribution n ¢ Enhance ISA Server with network-level scalability, fault tolerance, and load balancing. Intrusion Detection n ¢ Intercept viruses, malicious code or other inappropriate content at your network's Internet gateway. High Availability and Load Balancing n ¢ Improve the caching capabilities of ISA Server or create content distribution networks that store content closer to end users and provide centralized delivery, management, and support for different content types. Content Security n ¢ Improve security and interoperability for other protocols with applicationlayer inspection Recognize and react in real time to hacking attempts. Monitor incoming traffic, and trigger responses according to alarms and events. Monitoring and Administration n Extend the maintenance and management features of ISA Server to make day-to-day monitoring and administration tasks easier. 112
 ISA Server 2004 Partner Products (2) Enhancing existing features and add new features ¢ Reporting n ¢ SSL Acceleration and Key Management n ¢ Engage with authorized service partners to help build your Microsoft secure-connected infrastructure URL Filtering n ¢ Purchase ISA Server from authorized resellers who have technical product expertise Security Solution Providers n ¢ Use these hardware add-ons to improve the performance of SSL communications and the security of private keys used in creating SSL sessions, server identification, and PKI components Security Resellers n ¢ Review traffic through ISA Server, and develop reports that can be used for calculating departmental charge-backs, identifying inappropriate usage, and categorizing Internet use Restrict access to non-work-related sites, and filter sites that have objectionable or restricted content User Authentication n Provide support for additional authentication methods and technologies for ISA Server VPN and Web access 113
ISA Server 2004 Partner Products (2) Enhancing existing features and add new features ¢ Reporting n ¢ SSL Acceleration and Key Management n ¢ Engage with authorized service partners to help build your Microsoft secure-connected infrastructure URL Filtering n ¢ Purchase ISA Server from authorized resellers who have technical product expertise Security Solution Providers n ¢ Use these hardware add-ons to improve the performance of SSL communications and the security of private keys used in creating SSL sessions, server identification, and PKI components Security Resellers n ¢ Review traffic through ISA Server, and develop reports that can be used for calculating departmental charge-backs, identifying inappropriate usage, and categorizing Internet use Restrict access to non-work-related sites, and filter sites that have objectionable or restricted content User Authentication n Provide support for additional authentication methods and technologies for ISA Server VPN and Web access 113
 A Community of Partners Many Partners Have ISA Server 2000 Track Record 114
A Community of Partners Many Partners Have ISA Server 2000 Track Record 114
 ISA Server 2004 Partners (1) A Growing Community ¢ ¢ ¢ Activ. Card AAA Server deployed with ISA Server 2004 is expected to help enterprise customers further protect their digital assets by ensuring and tracking user identities across a network from anywhere, at any time. Akonix plans to use the application-layer filtering capabilities of ISA Server 2004 to direct all instant messaging traffic to Akonix’s awardwinning L 7 Enterprise IM gateway to implement usage policies, content filtering, virus scanning, logging, and compliance programs Authenex plans to integrate AOne™, a two-factor authentication and Web access control solution, with ISA Server 2004 to deliver a powerful, all-in-one suite of two-factor network security applications. The combination of Cerberian Web Manager and ISA Server 2004 will provide ISA Server 2004 customers with three additional levels of dynamic Internet content-filtering services via Cerberian’s database of more than five million ratings and domains, and Cerberian’s Dynamic Real-Time Rating and Dynamic Background Rating technologies. * This page is based on pre. Fast Scout Virtual. Web Internet filtering and release information. 115 monitoring software will support ISA Server 2004.
ISA Server 2004 Partners (1) A Growing Community ¢ ¢ ¢ Activ. Card AAA Server deployed with ISA Server 2004 is expected to help enterprise customers further protect their digital assets by ensuring and tracking user identities across a network from anywhere, at any time. Akonix plans to use the application-layer filtering capabilities of ISA Server 2004 to direct all instant messaging traffic to Akonix’s awardwinning L 7 Enterprise IM gateway to implement usage policies, content filtering, virus scanning, logging, and compliance programs Authenex plans to integrate AOne™, a two-factor authentication and Web access control solution, with ISA Server 2004 to deliver a powerful, all-in-one suite of two-factor network security applications. The combination of Cerberian Web Manager and ISA Server 2004 will provide ISA Server 2004 customers with three additional levels of dynamic Internet content-filtering services via Cerberian’s database of more than five million ratings and domains, and Cerberian’s Dynamic Real-Time Rating and Dynamic Background Rating technologies. * This page is based on pre. Fast Scout Virtual. Web Internet filtering and release information. 115 monitoring software will support ISA Server 2004.
 ISA Server 2004 Partners (2) A Growing Community ¢ ¢ ¢ Forum Systems will offer integration of its XWall™ Web Services Firewall with ISA Server 2004. Dyna. Comm i: filter from Future. Soft is a reliable, feature-rich enterprise Internet filtering solution for Microsoft ISA Server 2004. GFI Download. Security for ISA Server 2004 enables you to assert control over what files your users download from HTTP and FTP sites. n. Cipher hardware security modules (HSMs) will interoperate with ISA Server 2004 to more securely and more efficiently handle the advanced security functions performed by ISA Server 2004. Network Associates Mc. Afee Security. Shield for Microsoft ISA Server 2004 is designed to provide anti-virus protection, virus outbreak management, content scanning and, as part of an optional upgrade, anti-spam protection for Microsoft ISA Server 2004. Panda Software Panda ISASecure Antivirus module has been designed to help further protect Internet traffic passing through ISA Server 2004. * This page is based on prerelease information. 116
ISA Server 2004 Partners (2) A Growing Community ¢ ¢ ¢ Forum Systems will offer integration of its XWall™ Web Services Firewall with ISA Server 2004. Dyna. Comm i: filter from Future. Soft is a reliable, feature-rich enterprise Internet filtering solution for Microsoft ISA Server 2004. GFI Download. Security for ISA Server 2004 enables you to assert control over what files your users download from HTTP and FTP sites. n. Cipher hardware security modules (HSMs) will interoperate with ISA Server 2004 to more securely and more efficiently handle the advanced security functions performed by ISA Server 2004. Network Associates Mc. Afee Security. Shield for Microsoft ISA Server 2004 is designed to provide anti-virus protection, virus outbreak management, content scanning and, as part of an optional upgrade, anti-spam protection for Microsoft ISA Server 2004. Panda Software Panda ISASecure Antivirus module has been designed to help further protect Internet traffic passing through ISA Server 2004. * This page is based on prerelease information. 116
 ISA Server 2004 Partners (3) A Growing Community ¢ ¢ ¢ Rain. Connect from Rainfinity, provides continuous or always-on Internet access by distributing traffic among multiple independent ISP links. Surf. Control Web Filter puts you in control of Internet usage with a range of flexible, scalable, and high-performance solutions to best fit your Internet content-filtering needs. Venation V-WEB 4 provides a powerful and cost-effective platform for accelerating business-critical applications and content. Web. Spy facilitates the effective management of an organization's Internet resources. Whale Communications is planning to use the advanced functionality in the ISA Server 2004 to produce a prototype of a nextgeneration secure-access appliance. * This page is based on prerelease information. Check www. microsoft. com/isaserver/partners for an up-to-date list of available solutions 117
ISA Server 2004 Partners (3) A Growing Community ¢ ¢ ¢ Rain. Connect from Rainfinity, provides continuous or always-on Internet access by distributing traffic among multiple independent ISP links. Surf. Control Web Filter puts you in control of Internet usage with a range of flexible, scalable, and high-performance solutions to best fit your Internet content-filtering needs. Venation V-WEB 4 provides a powerful and cost-effective platform for accelerating business-critical applications and content. Web. Spy facilitates the effective management of an organization's Internet resources. Whale Communications is planning to use the advanced functionality in the ISA Server 2004 to produce a prototype of a nextgeneration secure-access appliance. * This page is based on prerelease information. Check www. microsoft. com/isaserver/partners for an up-to-date list of available solutions 117
 ISA Server 2004–Based Appliances More Options for Customers ¢ Extending ISA Server 2004 Benefits n n n ¢ Added Value and Customer Choice n n n ¢ Hardened configuration for reduced attack surface Easy to purchase, set up, and deploy Benefits of both a hardware and software solution Out-of-box configuration tools Web-based administration Customized and fully integrated deployment options New Worldwide Industry Partnerships n n Celestix Networks, Hewlett-Packard, and Network Engines Additional future partners 118
ISA Server 2004–Based Appliances More Options for Customers ¢ Extending ISA Server 2004 Benefits n n n ¢ Added Value and Customer Choice n n n ¢ Hardened configuration for reduced attack surface Easy to purchase, set up, and deploy Benefits of both a hardware and software solution Out-of-box configuration tools Web-based administration Customized and fully integrated deployment options New Worldwide Industry Partnerships n n Celestix Networks, Hewlett-Packard, and Network Engines Additional future partners 118
 Competitive Benefits ¢ ¢ ¢ ¢ Best Integration with Microsoft Windows and Microsoft Solutions More Technologies Built-in More Advanced Filtering Integrated Firewall and Caching Provides Better Security Better, More Broad Support Faster Learning Curve Lower Total Cost of Ownership ISA Server 2004 is a viable solution to common security and Web performance problems, with distinct advantages over other available solutions 119
Competitive Benefits ¢ ¢ ¢ ¢ Best Integration with Microsoft Windows and Microsoft Solutions More Technologies Built-in More Advanced Filtering Integrated Firewall and Caching Provides Better Security Better, More Broad Support Faster Learning Curve Lower Total Cost of Ownership ISA Server 2004 is a viable solution to common security and Web performance problems, with distinct advantages over other available solutions 119
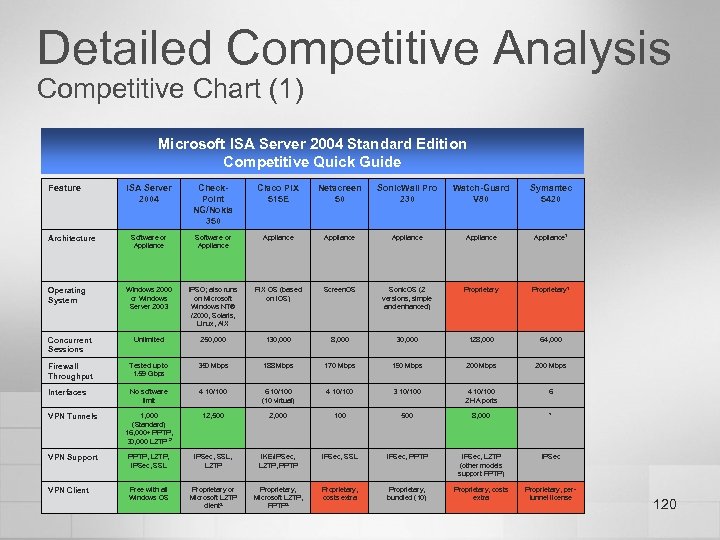 Detailed Competitive Analysis Competitive Chart (1) Microsoft ISA Server 2004 Standard Edition Competitive Quick Guide Feature ISA Server 2004 Check. Point NG/Nokia 350 Cisco PIX 515 E Netscreen 50 Sonic. Wall Pro 230 Watch-Guard V 80 Symantec 5420 Software or Appliance Appliance 1 Windows 2000 or Windows Server 2003 IPSO; also runs on Microsoft Windows NT® /2000, Solaris, Linux, AIX PIX OS (based on IOS) Screen. OS Sonic. OS (2 versions, simple and enhanced) Proprietary 1 Concurrent Sessions Unlimited 250, 000 130, 000 8, 000 30, 000 128, 000 64, 000 Firewall Throughput Tested up to 1. 59 Gbps 350 Mbps 188 Mbps 170 Mbps 190 Mbps 200 Mbps Interfaces No software limit 4 10/100 6 10/100 (10 virtual) 4 10/100 3 10/100 4 10/100 2 HA ports 6 VPN Tunnels 1, 000 (Standard) 16, 000+ PPTP, 30, 000 L 2 TP 2 12, 500 2, 000 100 500 8, 000 * VPN Support PPTP, L 2 TP, IPSec, SSL, L 2 TP IKE/IPSec, L 2 TP, PPTP IPSec, SSL IPSec, PPTP IPSec, L 2 TP (other models support PPTP) IPSec VPN Client Free with all Windows OS Proprietary or Microsoft L 2 TP client 3 Proprietary, Microsoft L 2 TP, PPTP 3 Proprietary, costs extra Proprietary, bundled (10) Proprietary, costs extra Proprietary, pertunnel license Architecture Operating System 120
Detailed Competitive Analysis Competitive Chart (1) Microsoft ISA Server 2004 Standard Edition Competitive Quick Guide Feature ISA Server 2004 Check. Point NG/Nokia 350 Cisco PIX 515 E Netscreen 50 Sonic. Wall Pro 230 Watch-Guard V 80 Symantec 5420 Software or Appliance Appliance 1 Windows 2000 or Windows Server 2003 IPSO; also runs on Microsoft Windows NT® /2000, Solaris, Linux, AIX PIX OS (based on IOS) Screen. OS Sonic. OS (2 versions, simple and enhanced) Proprietary 1 Concurrent Sessions Unlimited 250, 000 130, 000 8, 000 30, 000 128, 000 64, 000 Firewall Throughput Tested up to 1. 59 Gbps 350 Mbps 188 Mbps 170 Mbps 190 Mbps 200 Mbps Interfaces No software limit 4 10/100 6 10/100 (10 virtual) 4 10/100 3 10/100 4 10/100 2 HA ports 6 VPN Tunnels 1, 000 (Standard) 16, 000+ PPTP, 30, 000 L 2 TP 2 12, 500 2, 000 100 500 8, 000 * VPN Support PPTP, L 2 TP, IPSec, SSL, L 2 TP IKE/IPSec, L 2 TP, PPTP IPSec, SSL IPSec, PPTP IPSec, L 2 TP (other models support PPTP) IPSec VPN Client Free with all Windows OS Proprietary or Microsoft L 2 TP client 3 Proprietary, Microsoft L 2 TP, PPTP 3 Proprietary, costs extra Proprietary, bundled (10) Proprietary, costs extra Proprietary, pertunnel license Architecture Operating System 120
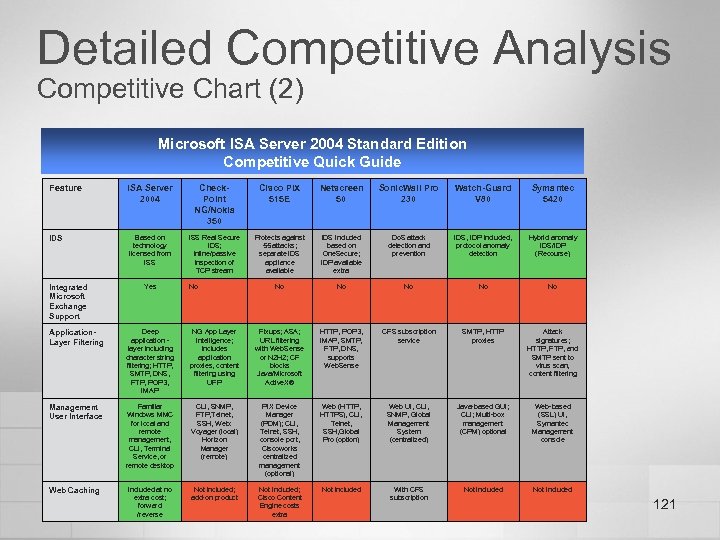 Detailed Competitive Analysis Competitive Chart (2) Microsoft ISA Server 2004 Standard Edition Competitive Quick Guide Feature ISA Server 2004 Check. Point NG/Nokia 350 Cisco PIX 515 E Netscreen 50 Sonic. Wall Pro 230 Watch-Guard V 80 Symantec 5420 IDS Based on technology licensed from ISS Real Secure IDS; inline/passive inspection of TCP stream Protects against 55 attacks; separate IDS appliance available IDS included based on One. Secure; IDP available extra Do. S attack detection and prevention IDS, IDP included, protocol anomaly detection Hybrid anomaly IDS/IDP (Recourse) No No No Integrated Microsoft Exchange Support Yes No Application. Layer Filtering Deep application layer including character string filtering; HTTP, SMTP, DNS, FTP, POP 3, IMAP NG App Layer Intelligence; includes application proxies, content filtering using UFP Fixups; ASA; URL filtering with Web. Sense or N 2 H 2; CF blocks Java/Microsoft Active. X® HTTP, POP 3, IMAP, SMTP, FTP, DNS, supports Web. Sense CFS subscription service SMTP, HTTP proxies Attack signatures; HTTP, FTP, and SMTP sent to virus scan, content filtering Management User Interface Familiar Windows MMC for local and remote management, CLI, Terminal Service, or remote desktop CLI, SNMP, FTP, Telnet, SSH, Web: Voyager (local) Horizon Manager (remote) PIX Device Manager (PDM); CLI, Telnet, SSH, console port, Ciscoworks centralized management (optional) Web (HTTP, HTTPS), CLI, Telnet, SSH, Global Pro (option) Web UI, CLI, SNMP, Global Management System (centralized) Java-based GUI; CLI; Multi-box management (CPM) optional Web-based (SSL) UI, Symantec Management console Web Caching Included at no extra cost; forward /reverse Not included; add-on product Not included; Cisco Content Engine costs extra Not included With CFS subscription Not included 121
Detailed Competitive Analysis Competitive Chart (2) Microsoft ISA Server 2004 Standard Edition Competitive Quick Guide Feature ISA Server 2004 Check. Point NG/Nokia 350 Cisco PIX 515 E Netscreen 50 Sonic. Wall Pro 230 Watch-Guard V 80 Symantec 5420 IDS Based on technology licensed from ISS Real Secure IDS; inline/passive inspection of TCP stream Protects against 55 attacks; separate IDS appliance available IDS included based on One. Secure; IDP available extra Do. S attack detection and prevention IDS, IDP included, protocol anomaly detection Hybrid anomaly IDS/IDP (Recourse) No No No Integrated Microsoft Exchange Support Yes No Application. Layer Filtering Deep application layer including character string filtering; HTTP, SMTP, DNS, FTP, POP 3, IMAP NG App Layer Intelligence; includes application proxies, content filtering using UFP Fixups; ASA; URL filtering with Web. Sense or N 2 H 2; CF blocks Java/Microsoft Active. X® HTTP, POP 3, IMAP, SMTP, FTP, DNS, supports Web. Sense CFS subscription service SMTP, HTTP proxies Attack signatures; HTTP, FTP, and SMTP sent to virus scan, content filtering Management User Interface Familiar Windows MMC for local and remote management, CLI, Terminal Service, or remote desktop CLI, SNMP, FTP, Telnet, SSH, Web: Voyager (local) Horizon Manager (remote) PIX Device Manager (PDM); CLI, Telnet, SSH, console port, Ciscoworks centralized management (optional) Web (HTTP, HTTPS), CLI, Telnet, SSH, Global Pro (option) Web UI, CLI, SNMP, Global Management System (centralized) Java-based GUI; CLI; Multi-box management (CPM) optional Web-based (SSL) UI, Symantec Management console Web Caching Included at no extra cost; forward /reverse Not included; add-on product Not included; Cisco Content Engine costs extra Not included With CFS subscription Not included 121
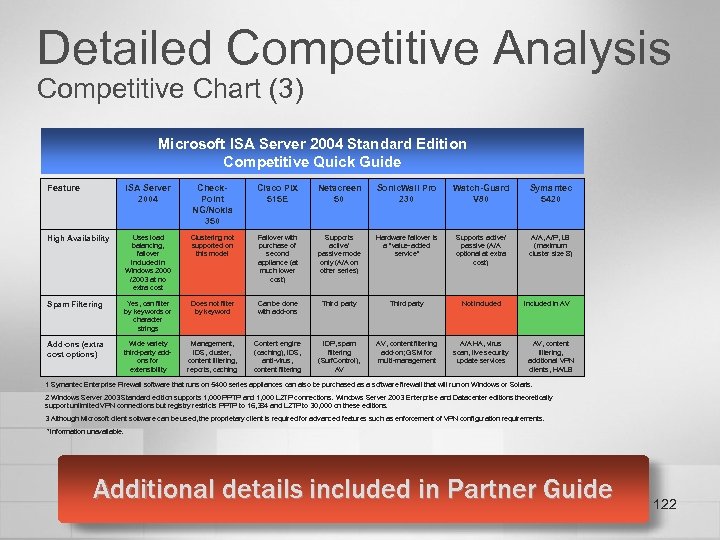 Detailed Competitive Analysis Competitive Chart (3) Microsoft ISA Server 2004 Standard Edition Competitive Quick Guide Feature ISA Server 2004 Check. Point NG/Nokia 350 Cisco PIX 515 E Netscreen 50 Sonic. Wall Pro 230 Watch-Guard V 80 Symantec 5420 High Availability Uses load balancing, failover included in Windows 2000 /2003 at no extra cost Clustering not supported on this model Failover with purchase of second appliance (at much lower cost) Supports active/ passive mode only (A/A on other series) Hardware failover is a “value-added service” Supports active/ passive (A/A optional at extra cost) A/A, A/P, LB (maximum cluster size 8) Spam Filtering Yes, can filter by keywords or character strings Does not filter by keyword Can be done with add-ons Third party Not included Add-ons (extra cost options) Wide variety third-party addons for extensibility Management, IDS, cluster, content filtering, reports, caching Content engine (caching), IDS, anti-virus, content filtering IDP, spam filtering (Surf. Control), AV AV, content filtering add-on; GSM for multi-management A/A HA, virus scan, live security update services Included in AV AV, content filtering, additional VPN clients, HA/LB 1 Symantec Enterprise Firewall software that runs on 5400 series appliances can also be purchased as a software firewall that will run on Windows or Solaris. 2 Windows Server 2003 Standard edition supports 1, 000 PPTP and 1, 000 L 2 TP connections. Windows Server 2003 Enterprise and Datacenter editions theoretically support unlimited VPN connections but registry restricts PPTP to 16, 384 and L 2 TP to 30, 000 on these editions. 3 Although Microsoft client software can be used, the proprietary client is required for advanced features such as enforcement of VPN configuration requirements. *Information unavailable. Additional details included in Partner Guide 122
Detailed Competitive Analysis Competitive Chart (3) Microsoft ISA Server 2004 Standard Edition Competitive Quick Guide Feature ISA Server 2004 Check. Point NG/Nokia 350 Cisco PIX 515 E Netscreen 50 Sonic. Wall Pro 230 Watch-Guard V 80 Symantec 5420 High Availability Uses load balancing, failover included in Windows 2000 /2003 at no extra cost Clustering not supported on this model Failover with purchase of second appliance (at much lower cost) Supports active/ passive mode only (A/A on other series) Hardware failover is a “value-added service” Supports active/ passive (A/A optional at extra cost) A/A, A/P, LB (maximum cluster size 8) Spam Filtering Yes, can filter by keywords or character strings Does not filter by keyword Can be done with add-ons Third party Not included Add-ons (extra cost options) Wide variety third-party addons for extensibility Management, IDS, cluster, content filtering, reports, caching Content engine (caching), IDS, anti-virus, content filtering IDP, spam filtering (Surf. Control), AV AV, content filtering add-on; GSM for multi-management A/A HA, virus scan, live security update services Included in AV AV, content filtering, additional VPN clients, HA/LB 1 Symantec Enterprise Firewall software that runs on 5400 series appliances can also be purchased as a software firewall that will run on Windows or Solaris. 2 Windows Server 2003 Standard edition supports 1, 000 PPTP and 1, 000 L 2 TP connections. Windows Server 2003 Enterprise and Datacenter editions theoretically support unlimited VPN connections but registry restricts PPTP to 16, 384 and L 2 TP to 30, 000 on these editions. 3 Although Microsoft client software can be used, the proprietary client is required for advanced features such as enforcement of VPN configuration requirements. *Information unavailable. Additional details included in Partner Guide 122
 Partner Guide Resources ¢ Plan n ¢ Market/Sell n ¢ Utilize tools and resources to help you sell ISA Server products and services. Leverage Microsoft’s customer-ready materials to incorporate into your own presentations and distribute to your customers. Read and leverage various datasheets, sales presentations, telesales scripts, and other marketing materials that will help you communicate the benefits of deploying and using ISA Server 2004. Service/Support n ¢ Review the Partner Revenue Opportunities with ISA Server 2004 document to determine areas of specialization. Learn about the advantages that ISA Server 2004 brings to Exchange Server, IIS, Share. Point, and Windows Server 2003 deployments. View case studies to learn about the benefits that ISA Server 2004 has brought to customers. Leverage the ISA Server 2004 Configuration Guide, deployment kits, and white papers to get the background information you need to plan ISA Server 2004 deployments, complete with the step-by-step procedures needed for proper installation and configuration. Install the ISA Server 2004 evaluation software to test the benefits of ISA Server in a production environment. Train/Enable n Complete the Hands-on Labs on CD 2. 123
Partner Guide Resources ¢ Plan n ¢ Market/Sell n ¢ Utilize tools and resources to help you sell ISA Server products and services. Leverage Microsoft’s customer-ready materials to incorporate into your own presentations and distribute to your customers. Read and leverage various datasheets, sales presentations, telesales scripts, and other marketing materials that will help you communicate the benefits of deploying and using ISA Server 2004. Service/Support n ¢ Review the Partner Revenue Opportunities with ISA Server 2004 document to determine areas of specialization. Learn about the advantages that ISA Server 2004 brings to Exchange Server, IIS, Share. Point, and Windows Server 2003 deployments. View case studies to learn about the benefits that ISA Server 2004 has brought to customers. Leverage the ISA Server 2004 Configuration Guide, deployment kits, and white papers to get the background information you need to plan ISA Server 2004 deployments, complete with the step-by-step procedures needed for proper installation and configuration. Install the ISA Server 2004 evaluation software to test the benefits of ISA Server in a production environment. Train/Enable n Complete the Hands-on Labs on CD 2. 123
 Web Resources ¢ ISA Server 2004 official site n ¢ ISA Server 2004 partners n ¢ http: //www. microsoft. com/isaserver/partners/ Partner Campaign Kits n ¢ http: //www. microsoft. com/isaserver http: //members. microsoft. com/partner/ ISA Server 2004 user community (not affiliated with Microsoft) n http: //www. isaserver. org 124
Web Resources ¢ ISA Server 2004 official site n ¢ ISA Server 2004 partners n ¢ http: //www. microsoft. com/isaserver/partners/ Partner Campaign Kits n ¢ http: //www. microsoft. com/isaserver http: //members. microsoft. com/partner/ ISA Server 2004 user community (not affiliated with Microsoft) n http: //www. isaserver. org 124
 4. Introduction to Hands-on Training
4. Introduction to Hands-on Training
 Hands-on Labs Six Scenarios ¢ ¢ ¢ Lab A: What's New in ISA Server 2004 Lab B: Configuring Outbound Internet Access Lab C: Publishing Web Servers Lab D: Publishing an Exchange Server Lab E: Enabling VPN Connections Lab F: Using Monitoring, Alerting, and Logging 126
Hands-on Labs Six Scenarios ¢ ¢ ¢ Lab A: What's New in ISA Server 2004 Lab B: Configuring Outbound Internet Access Lab C: Publishing Web Servers Lab D: Publishing an Exchange Server Lab E: Enabling VPN Connections Lab F: Using Monitoring, Alerting, and Logging 126
 Hands-on Labs Format ¢ ¢ Hands-on Training uses Microsoft Virtual PC Four virtual computers: n n ¢ ¢ Internal computer (Domain Controller, Exchange Server) ISA Server 2004 Web server in perimeter network External computer Setup guide and instructions included on Partner CD Each scenario can be completed independently in about 30 -60 minutes Each scenario contains detailed explanations Each scenario presents a complete solution 127
Hands-on Labs Format ¢ ¢ Hands-on Training uses Microsoft Virtual PC Four virtual computers: n n ¢ ¢ Internal computer (Domain Controller, Exchange Server) ISA Server 2004 Web server in perimeter network External computer Setup guide and instructions included on Partner CD Each scenario can be completed independently in about 30 -60 minutes Each scenario contains detailed explanations Each scenario presents a complete solution 127
 © 2003 -2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary. 128
© 2003 -2004 Microsoft Corporation. All rights reserved. This presentation is for informational purposes only. Microsoft makes no warranties, express or implied, in this summary. 128


