de9380f7685982feee1134197f4e1d91.ppt
- Количество слайдов: 18

Member Economies Update ─ Chinese Taipei ─ Presented by Dr. Perry Liu Director, Information Security Service Center, Project Resource Division, Institute for Information Industry Oct. , 25, 2005 www. afact. org AFACT 1

Outlines • IT Security Standard Activities • Other IT Security Activities www. afact. org AFACT 2

Standards Related Institutions • BSMI (Bureau of Standards, Metrology and Inspection) – MOEA is standards authority, BSMI under MOEA is responsible for implementation matters, it has • National Standards Review Council • National Standards Technical Committees • Information & Communication National Standards Promotion Committees • National Information & Communication Initiative Committee (NICI) ─ Technology & Standards Team • National Information & Communication Security Taskforce (NICST) ─ Standards & Specifications Group www. afact. org AFACT 3

National Standards Technical Committees • Major Responsibilities – Drawing up and reviewing draft national standards – Interpreting national standards • Organizations – 26 Technical Committees,169 Sub-committees • TC 22: Information & Communication – SC 1 Terminology and Basic Rule – SC 2 Code – SC 3 Software – SC 4 Hardware – SC 5 Chinese Information and Coding – SC 6 Communication Technology – SC 7 Data Processing AFACT – SC 8 Information and Communication Security www. afact. org 4

IT Security Standard Efforts • Certification & Accreditation Scheme • IT Security Assurance Framework • Fundamental Security Technique Standards www. afact. org AFACT 5

IT Security Standard Efforts • Certification & Accreditation Scheme – CNAB (Chinese National Accreditation Board) • Accreditation of CBs: Mgmt System, Environment Mgmt System, Auditor Training, Auditor, Product • Information Security Mgmt System – CNLA (Chinese National Laboratory Accreditation) • Accreditation of Labs: Calibration, Mechanics, Chemistry…etc. , 12 areas • Information Security Testing/Calibration Lab – TAF (Taiwan Accreditation Foundation) • Merge of CNAB and CNLA – BSMI • QMS: ISO 9001: 2000 • EMS: 14001: 2004 • OHSMS: OHSAS 18001 • ISMS: CNS 17800 (currently very few organizations were certified under CNS 1788. however BS 7799 -2 have more than 50) www. afact. org AFACT 6

IT Security Standard Efforts • Certification & Accreditation Scheme Mgmt Sys Accreditation Product Cert. Body Accreditation ISO/IEC Guide 61 EA-7/03 (ISO/IEC Guide 62) CNS 14731 ISO/IEC Guide 65 Mgmt Sys Cert. Body ISO/IEC 17799 (ISO 9000, 9001) CNS 17799, 17800 Organization Lab Accreditation ISO/IEC Guide 58 ISO/IEC 17025 Product Cert. Body Testing Lab ISO 15408 & Product-specific Std. CNS 15408 1 -3 IT Security Product www. afact. org AFACT 7

IT Security Standard Efforts • IT Security Assurance Framework Design Process (Product、 System or Service) Environment (Personnel and Organization) Deployment Operation Assurance Method B Assurance Method A Assurance Method Deliverable Integration Assurance Method D Assurance Method E C Assurance Method F Assurance Method G www. afact. org Assurance Method H AFACT 8

IT Security Standard Efforts • IT Security Assurance Framework – Related assurance std. applicability Design/ Implementation Integration Deployment/ Transfer Operation Process ISO/IEC 21827 ISO/IEC 15504 ISO/IEC 13335 ISO/IEC 21827 ISO/IEC 15504 ISO/IEC 17799 ISO/IEC 13335 ISO/IEC 21827 ISO/IEC 15504 Deliverable (Product、 System or Service) ISO/IEC 14598 ISO/IEC 15408 ISO/IEC 12207 ISO/IEC 15288 Environment (Personnel and Organization) (ISO 13407) ISO 9000 ISO/IEC 17025 www. afact. org AFACT 9

IT Security Standard Efforts • IT Security Assurance Framework – Related CNS assurance std status ISO Number CNS Number Approval CNS 14837 ISO/IEC TR 13335 -1 CNS 14929 -1 ISO/IEC TR 13335 -2 CNS 14929 -2 ISO/IEC TR 13335 -3 CNS 14929 -3 ISO/IEC TR 13335 -4 CNS 14929 -4 ISO/IEC 12207 Drafting Planning ISO/IEC TR 13335 -5 ISO/IEC 14598 -1 ISO/IEC 14598 -2 ISO/IEC 14598 -3 ISO/IEC 14598 -4 ISO/IEC 14598 -5 ISO/IEC 14598 -6 ISO/IEC 15288 AFACT www. afact. org 10
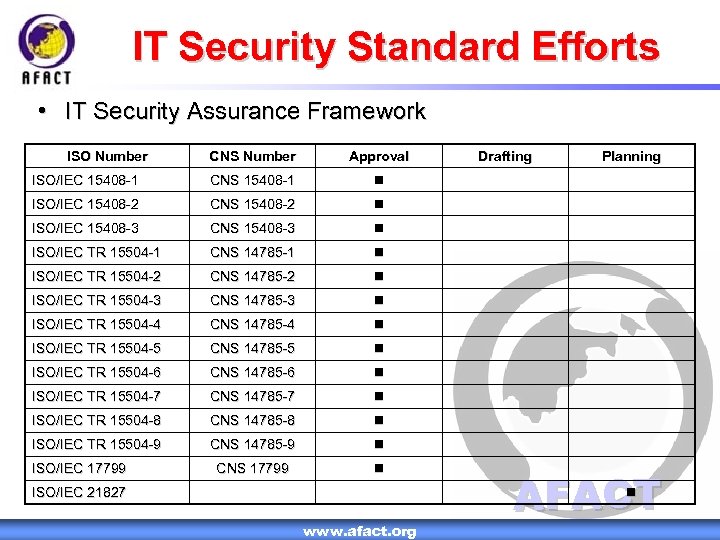
IT Security Standard Efforts • IT Security Assurance Framework ISO Number CNS Number Approval ISO/IEC 15408 -1 CNS 15408 -1 ISO/IEC 15408 -2 CNS 15408 -2 ISO/IEC 15408 -3 CNS 15408 -3 ISO/IEC TR 15504 -1 CNS 14785 -1 ISO/IEC TR 15504 -2 CNS 14785 -2 ISO/IEC TR 15504 -3 CNS 14785 -3 ISO/IEC TR 15504 -4 CNS 14785 -4 ISO/IEC TR 15504 -5 CNS 14785 -5 ISO/IEC TR 15504 -6 CNS 14785 -6 ISO/IEC TR 15504 -7 CNS 14785 -7 ISO/IEC TR 15504 -8 CNS 14785 -8 ISO/IEC TR 15504 -9 CNS 14785 -9 CNS 17799 ISO/IEC 21827 Drafting Planning AFACT www. afact. org 11

Other IT Security Activities • e-Taiwan Infrastructure Security related Project (initiated by National Info. and Comm. Initiative Committee, NICI) – Natural Person Certificate Project • 868, 415 certificates have been issued until 2005/06/20 • More than 80 k families use NPC in declaring tax this May (1, 100+ last year) – Establish National Security Operation Center (NSOC) • Started operation since this February • Formed Incident Data Exchange Common Format Taskforce, and testing IODEFbased data exchange with SOCs of Acer, e-Cop, Trade. Van etc. – Establish Certificate Interoperability Mechanism • Bridge CA completed interoperability testing between 4 CAs • 4 more companies got funding to develop exemplary PKI applications – Information Security Product Certification Scheme • Smart Card evaluation laboratory has completely established • Firewall evaluation laboratory is now developing, it will be completely established before the end of 2005 • AFACT NICI’s focus is to establishment the necessary infrastructure of e-Taiwan and m-Taiwan www. afact. org 12

Other IT Security Activities • NICST (National Information & Communication Security Taskforce) – Focus on establishing Info. & Comm. Security mechanisms in public sectors, e. g. , NCERT, law & regulation, NSOC operation NICST National Security Council General Convenor: Vice Premier Deputy General Convenor: NICI Task Force Convenor, RDEC Chairman CEO: STAG Executive Secretary Committee Member: Ministers and Mayors of Taipei and Kaohsiung Advisory Committee NCERT R&R Subgroups Info & Comm Security Tech Center Report & Response (RDEC) General Business (STAG) Law & Cyber Crime (MOJ, MOI) Audit Service (DGBAS) Std. & Spec. (MOEA) Info Gathering & Analysis (NSC) www. afact. org National Defense (MND) Gov Admin (RDEC) Academic (MOE) Business 1 (MOEA) Business 2 (MOTC) Business 3 (MOF) Business 4 (DOH) AFACT 13

Other IT Security Activities • Info. & Comm. Security Technology Center (ICST) – CSIRT of NICST, project fund from RDEC – Staffed by III (PRD-ISSC) Enhancement • Awareness, Training and Promotion • Internet Services (Web, news letter) • GSN Vulnerability Scan & Patch Monitoring • Hacker behavior and Malicious code • Security Operation Center (NSOC) • Integrated Warning System Research ICST Missions • Law and Regulation • Industry Development Trend • IT Security Common Guidelines Cooperation Response • Front Desk Consulting Services • Emergency Response Project • Forensics and Recovery www. afact. org • NICST Technical Staff • International Cooperation • Industry and Academia Alliance AFACT 14

Other IT Security Activities • IT Security Common Guidelines & Directions for Agencies Information Info System Info Service Scope Categorize Classify Security Control Selection & Implementation Info Classification Guideline 2005 Focus Security Req Baseline System Security Planning Guideline Product Sourcing Guideline Incident Report & Response Direction System Risk Guideline Firewall Mgmt Guideline Sys Security Control Baseline Patch Mgmt Guideline Outsourcing Security Guideline File Protection Guideline Impact Level Classification Direction 2 nd Phase Email Security Guideline Web Security Guideline Network Security Testing Guideline Anti-virus Guideline VPN Guideline System Evaluation Guideline Cert. & Accreditation Guideline System BCP Guideline Remote Access and Broadband Guideline System and Impact Mapping Guideline SDLC Security Guideline 3 rd IDS Guideline Training Guideline Evaluation Certification Authorization System Interfacing Security Guideline Wireless Security Guideline e-Identity Guideline System Audit Guideline Computer Forensics Guideline VOIP Security Guideline Mobile Code Security Guideline Infrastructure Security Guideline www. afact. org AFACT 15

Other IT Security Activities • ICST ─ 2005 Education/Training Focus Audience Citizens Approaches Enhance awareness Contents Channels • Online Web • Online Forum • e-Paper • Exhibitions Animation/Quiz • Anti-Virus/Hacking/Spam how to • What is computer crime • Why social engineering a threat • NCSI e-College • RDEC e-Learning Web • Seminars • Directives Best Practice & Guidelines Agency Officials General Officials Baseline Training IT Officers IT Technicians Auditors In-depth Training & Certification IT Technicians In-depth Training • ISMS for Agency Officials • Incident Response Mechanism • Data Encryption and Protection • Information Security and Outsourcing • BS 7799 LA Training (40 hrs) • BS 7799 Establishment Training (40 hrs) • IT Security Auditing Training (16 hrs) • Information Technology Expert Training (93 hrs) www. afact. org • Training Courses • Seminars • Certifying Exam AFACT • Training Courses • Exam 16

Other IT Security Activities • Security Legislation – National Intelligence Collection Law (enacted on Feb 5, 2005) • Anti-terrorism purpose • Authorize specific government intelligence collect information in secret by means of detection, interception electronic communication, surveillance, and compel ISP disclose records etc. – Cyber-crime Chapter in Criminal Code (enacted on June 3, 2003) • Unauthorized access • Illegal interception • Illegal interference • Programmer who create hacker tool specifically for the perpetration of the above types of crime – Criminal Procedure Law Amendment (enacted on Sep 1, 2003) • Introduce more restricted evidence investigation rule • Hearsay rule application for example www. afact. org AFACT 17

Other IT Security Activities • Security Legislation (cont. ) – Video Voyeurism Prevention in Criminal code (enacted on Feb 2, 2005) • Whoever has the intent to capture an image of a private area of an individual by videotape, photograph, film, or record electronically without their consent is punishable. – The Computer-Processed Personal Data Protection Law Amendment (on the floor of Congress, Mar 4, 2005 ) • Protect the rights to search or read the data, reproduce data, supplement or revise data, stop further processing or use of data; and delete data. – Controlling the Abuse of Commercial Electronic Mail Statute (on the floor of Congress, Mar 4, 2005 ) • Anti-spam purpose. www. afact. org AFACT 18
de9380f7685982feee1134197f4e1d91.ppt