a4b04eb7461072974b504699d24da688.ppt
- Количество слайдов: 86
 Medium Access Control for Wireless Links CS 515 Mobile and Wireless Networking Ibrahim Korpeoglu Computer Engineering Department Bilkent University 1
Medium Access Control for Wireless Links CS 515 Mobile and Wireless Networking Ibrahim Korpeoglu Computer Engineering Department Bilkent University 1
 Outline n n What we have see so far? PHY layer functions and parameters General Wireless System Architecture Media Access Control q Classes of MAC protocols q Simplex and Duplex Channels Coordinated MAC Schemes q FDMA q TDMA n q Capacity of TDMA systems and which factors affect the capacity. Spread Spectrum Access Methods n FHMA q n n n Case study: Bluetooth CDMA Hybrid Spread Spectrum Schemes. Random MAC Schemes q q q CS 515 CSMA MACA and MACAW Case Study: IEEE 802. 11 MAC © Ibrahim Korpeoglu 2
Outline n n What we have see so far? PHY layer functions and parameters General Wireless System Architecture Media Access Control q Classes of MAC protocols q Simplex and Duplex Channels Coordinated MAC Schemes q FDMA q TDMA n q Capacity of TDMA systems and which factors affect the capacity. Spread Spectrum Access Methods n FHMA q n n n Case study: Bluetooth CDMA Hybrid Spread Spectrum Schemes. Random MAC Schemes q q q CS 515 CSMA MACA and MACAW Case Study: IEEE 802. 11 MAC © Ibrahim Korpeoglu 2
 What we have seen so far? n Physical layer functions q Get stream of bits and transport them to the other end. n q Modulation/Demodulation We have seen that this is not an easy task q q CS 515 Large-scale path loss and Small-scale fading and multipath effects causes the received power at the receiver to § Fluctuate (hard to decode the symbols (bits)) § To decrease (Affects of interfering sources increases) Received signal power level affect the quality of the signals (information) that is transported. § Received signal power level defines the Signal-to-Noise (SNR) ratio © Ibrahim Korpeoglu 3
What we have seen so far? n Physical layer functions q Get stream of bits and transport them to the other end. n q Modulation/Demodulation We have seen that this is not an easy task q q CS 515 Large-scale path loss and Small-scale fading and multipath effects causes the received power at the receiver to § Fluctuate (hard to decode the symbols (bits)) § To decrease (Affects of interfering sources increases) Received signal power level affect the quality of the signals (information) that is transported. § Received signal power level defines the Signal-to-Noise (SNR) ratio © Ibrahim Korpeoglu 3
 What we have seen so far? n We have seen q That SNR and bandwidth of a channel affects n n q q n n Datarate – bps) of the wireless channel by Shannon limit The bit error rate (BER) on the channel. That multipath fading results in a wireless channel error model that changes states between good (low-error rate) and bad (high error-rate) Large-scale path loss defines the range of stations for different environments (LOS, urban, …) The above factors are important channel characteristics that affect the design of wireless systems architectures and design of the protocols and applications for wireless links/networks In short, we have seen so far some of Fundamental Concepts of Wireless Communication. CS 515 © Ibrahim Korpeoglu 4
What we have seen so far? n We have seen q That SNR and bandwidth of a channel affects n n q q n n Datarate – bps) of the wireless channel by Shannon limit The bit error rate (BER) on the channel. That multipath fading results in a wireless channel error model that changes states between good (low-error rate) and bad (high error-rate) Large-scale path loss defines the range of stations for different environments (LOS, urban, …) The above factors are important channel characteristics that affect the design of wireless systems architectures and design of the protocols and applications for wireless links/networks In short, we have seen so far some of Fundamental Concepts of Wireless Communication. CS 515 © Ibrahim Korpeoglu 4
 What we will do now? n We will look now to the protocols, algorithms, schemes that are developed over this wireless channels. q q q CS 515 How can we share a wireless channel: § Results in Wireless Media Access Control Protocols How we can change base stations: Results in Handoff algorithms and protocols How can we seamlessly support mobile applications over wireless links: § Results in mobility protocols like Mobile IP, Cellular IP, etc. How can we design efficient transport protocols over wireless links: § Results in solutions like SNOOP, I-TCP, M-TCP, etc. How different wireless networks/systems are designed? § Bluetooth, IEEE 802. 11, GSM, etc. © Ibrahim Korpeoglu 5
What we will do now? n We will look now to the protocols, algorithms, schemes that are developed over this wireless channels. q q q CS 515 How can we share a wireless channel: § Results in Wireless Media Access Control Protocols How we can change base stations: Results in Handoff algorithms and protocols How can we seamlessly support mobile applications over wireless links: § Results in mobility protocols like Mobile IP, Cellular IP, etc. How can we design efficient transport protocols over wireless links: § Results in solutions like SNOOP, I-TCP, M-TCP, etc. How different wireless networks/systems are designed? § Bluetooth, IEEE 802. 11, GSM, etc. © Ibrahim Korpeoglu 5
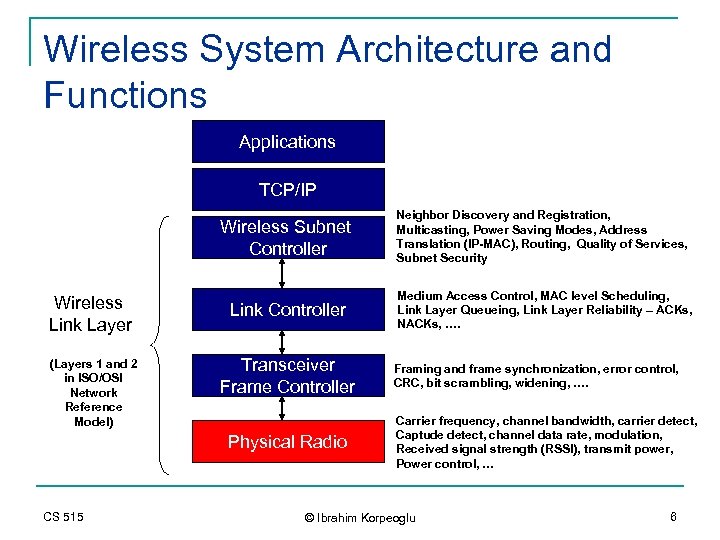 Wireless System Architecture and Functions Applications TCP/IP Wireless Subnet Controller Wireless Link Layer (Layers 1 and 2 in ISO/OSI Network Reference Model) Neighbor Discovery and Registration, Multicasting, Power Saving Modes, Address Translation (IP-MAC), Routing, Quality of Services, Subnet Security Link Controller Medium Access Control, MAC level Scheduling, Link Layer Queueing, Link Layer Reliability – ACKs, NACKs, …. Transceiver Frame Controller Physical Radio CS 515 Framing and frame synchronization, error control, CRC, bit scrambling, widening, …. Carrier frequency, channel bandwidth, carrier detect, Captude detect, channel data rate, modulation, Received signal strength (RSSI), transmit power, Power control, … © Ibrahim Korpeoglu 6
Wireless System Architecture and Functions Applications TCP/IP Wireless Subnet Controller Wireless Link Layer (Layers 1 and 2 in ISO/OSI Network Reference Model) Neighbor Discovery and Registration, Multicasting, Power Saving Modes, Address Translation (IP-MAC), Routing, Quality of Services, Subnet Security Link Controller Medium Access Control, MAC level Scheduling, Link Layer Queueing, Link Layer Reliability – ACKs, NACKs, …. Transceiver Frame Controller Physical Radio CS 515 Framing and frame synchronization, error control, CRC, bit scrambling, widening, …. Carrier frequency, channel bandwidth, carrier detect, Captude detect, channel data rate, modulation, Received signal strength (RSSI), transmit power, Power control, … © Ibrahim Korpeoglu 6
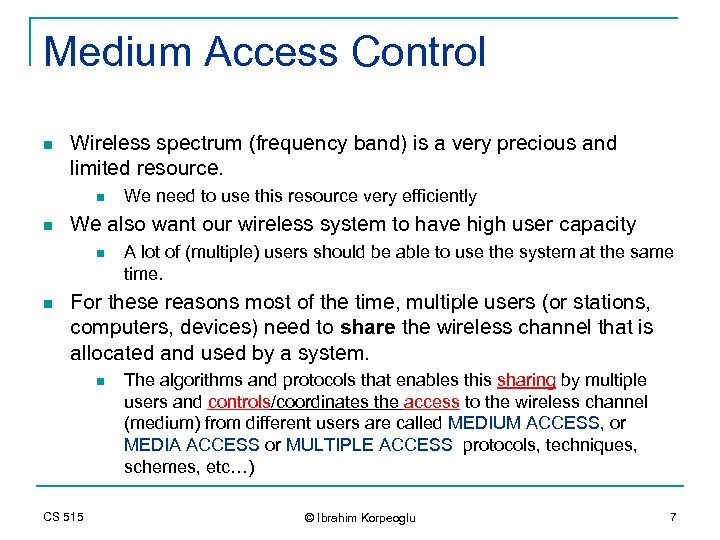 Medium Access Control n Wireless spectrum (frequency band) is a very precious and limited resource. n n We also want our wireless system to have high user capacity n n We need to use this resource very efficiently A lot of (multiple) users should be able to use the system at the same time. For these reasons most of the time, multiple users (or stations, computers, devices) need to share the wireless channel that is allocated and used by a system. n CS 515 The algorithms and protocols that enables this sharing by multiple users and controls/coordinates the access to the wireless channel (medium) from different users are called MEDIUM ACCESS, or MEDIA ACCESS or MULTIPLE ACCESS protocols, techniques, schemes, etc…) © Ibrahim Korpeoglu 7
Medium Access Control n Wireless spectrum (frequency band) is a very precious and limited resource. n n We also want our wireless system to have high user capacity n n We need to use this resource very efficiently A lot of (multiple) users should be able to use the system at the same time. For these reasons most of the time, multiple users (or stations, computers, devices) need to share the wireless channel that is allocated and used by a system. n CS 515 The algorithms and protocols that enables this sharing by multiple users and controls/coordinates the access to the wireless channel (medium) from different users are called MEDIUM ACCESS, or MEDIA ACCESS or MULTIPLE ACCESS protocols, techniques, schemes, etc…) © Ibrahim Korpeoglu 7
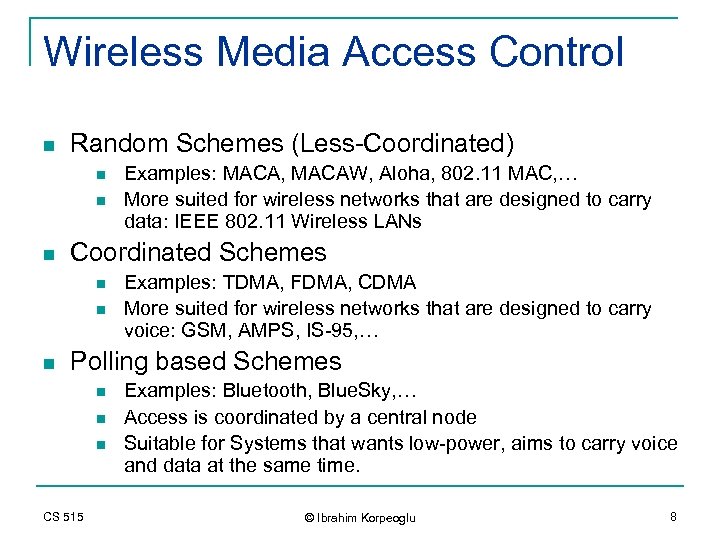 Wireless Media Access Control n Random Schemes (Less-Coordinated) n n n Coordinated Schemes n n n Examples: MACA, MACAW, Aloha, 802. 11 MAC, … More suited for wireless networks that are designed to carry data: IEEE 802. 11 Wireless LANs Examples: TDMA, FDMA, CDMA More suited for wireless networks that are designed to carry voice: GSM, AMPS, IS-95, … Polling based Schemes n n n CS 515 Examples: Bluetooth, Blue. Sky, … Access is coordinated by a central node Suitable for Systems that wants low-power, aims to carry voice and data at the same time. © Ibrahim Korpeoglu 8
Wireless Media Access Control n Random Schemes (Less-Coordinated) n n n Coordinated Schemes n n n Examples: MACA, MACAW, Aloha, 802. 11 MAC, … More suited for wireless networks that are designed to carry data: IEEE 802. 11 Wireless LANs Examples: TDMA, FDMA, CDMA More suited for wireless networks that are designed to carry voice: GSM, AMPS, IS-95, … Polling based Schemes n n n CS 515 Examples: Bluetooth, Blue. Sky, … Access is coordinated by a central node Suitable for Systems that wants low-power, aims to carry voice and data at the same time. © Ibrahim Korpeoglu 8
 Duplexing q q q It is sharing the media between two parties. If the communication between two parties is one way, the it is called simplex communication. If the communication between two parties is two- way, then it is called duplex communication. Simplex communication is achieved by default by using a single wireless channel (frequency band) to transmit from sender to receiver. Duplex communication achieved by: q q q CS 515 Time Division (TDD) Frequency Division (FDD) Some other method like a random access method © Ibrahim Korpeoglu 9
Duplexing q q q It is sharing the media between two parties. If the communication between two parties is one way, the it is called simplex communication. If the communication between two parties is two- way, then it is called duplex communication. Simplex communication is achieved by default by using a single wireless channel (frequency band) to transmit from sender to receiver. Duplex communication achieved by: q q q CS 515 Time Division (TDD) Frequency Division (FDD) Some other method like a random access method © Ibrahim Korpeoglu 9
 Duplexing n Usually the two parties that want to communication in a duplex manner (both send and receive) are: n n n A mobile station A base station Two famous methods for duplexing in cellular systems are: n n CS 515 TDD: Time Division Duplex FDD: Frequency Division Duplex © Ibrahim Korpeoglu 10
Duplexing n Usually the two parties that want to communication in a duplex manner (both send and receive) are: n n n A mobile station A base station Two famous methods for duplexing in cellular systems are: n n CS 515 TDD: Time Division Duplex FDD: Frequency Division Duplex © Ibrahim Korpeoglu 10
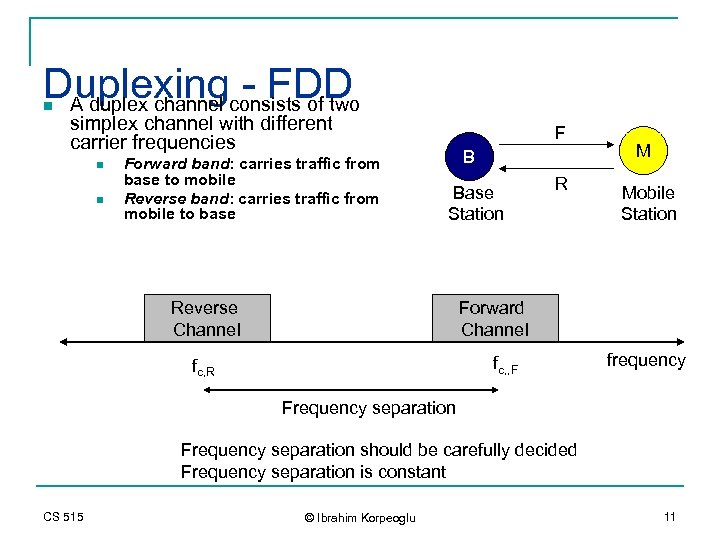 Duplexingconsists of two - FDD A duplex channel n simplex channel with different carrier frequencies n n Forward band: carries traffic from base to mobile Reverse band: carries traffic from mobile to base F B Base Station Reverse Channel R M Mobile Station Forward Channel fc, , F fc, R frequency Frequency separation should be carefully decided Frequency separation is constant CS 515 © Ibrahim Korpeoglu 11
Duplexingconsists of two - FDD A duplex channel n simplex channel with different carrier frequencies n n Forward band: carries traffic from base to mobile Reverse band: carries traffic from mobile to base F B Base Station Reverse Channel R M Mobile Station Forward Channel fc, , F fc, R frequency Frequency separation should be carefully decided Frequency separation is constant CS 515 © Ibrahim Korpeoglu 11
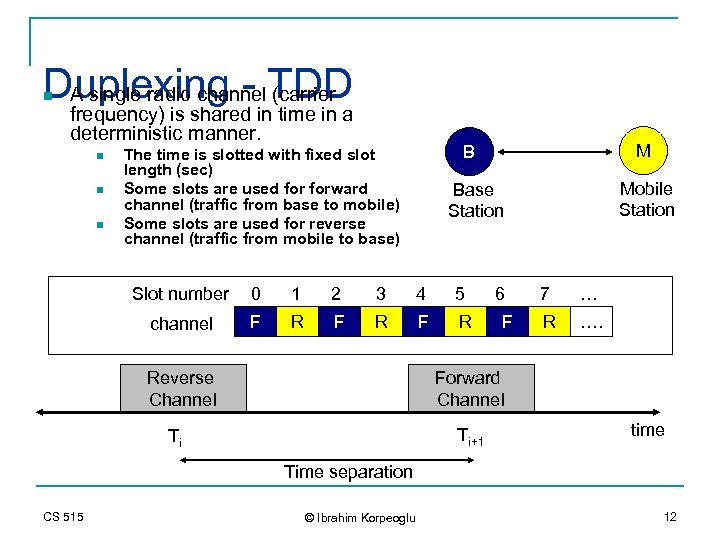 Duplexing - TDD A single radio channel (carrier n frequency) is shared in time in a deterministic manner. n n n Mobile Station Base Station Slot number 0 1 2 3 4 5 channel F R F R Reverse Channel M B The time is slotted with fixed slot length (sec) Some slots are used forward channel (traffic from base to mobile) Some slots are used for reverse channel (traffic from mobile to base) 6 F 7 … R …. Forward Channel Ti+1 Ti time Time separation CS 515 © Ibrahim Korpeoglu 12
Duplexing - TDD A single radio channel (carrier n frequency) is shared in time in a deterministic manner. n n n Mobile Station Base Station Slot number 0 1 2 3 4 5 channel F R F R Reverse Channel M B The time is slotted with fixed slot length (sec) Some slots are used forward channel (traffic from base to mobile) Some slots are used for reverse channel (traffic from mobile to base) 6 F 7 … R …. Forward Channel Ti+1 Ti time Time separation CS 515 © Ibrahim Korpeoglu 12
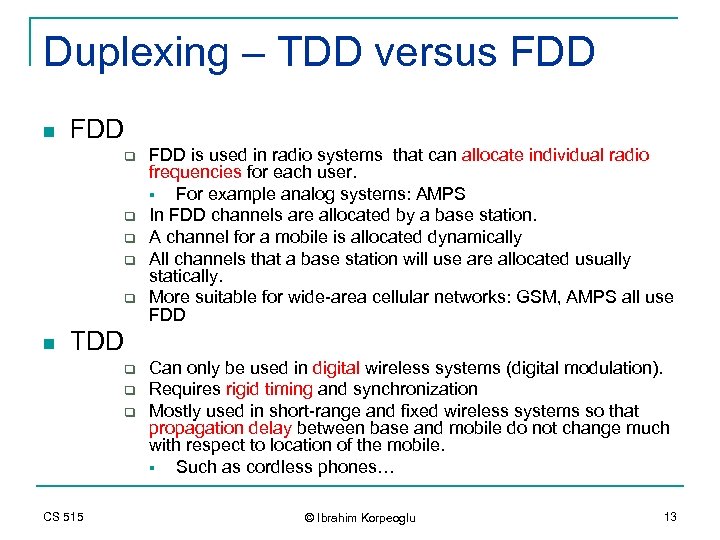 Duplexing – TDD versus FDD n FDD q q q n FDD is used in radio systems that can allocate individual radio frequencies for each user. § For example analog systems: AMPS In FDD channels are allocated by a base station. A channel for a mobile is allocated dynamically All channels that a base station will use are allocated usually statically. More suitable for wide-area cellular networks: GSM, AMPS all use FDD TDD q q q CS 515 Can only be used in digital wireless systems (digital modulation). Requires rigid timing and synchronization Mostly used in short-range and fixed wireless systems so that propagation delay between base and mobile do not change much with respect to location of the mobile. § Such as cordless phones… © Ibrahim Korpeoglu 13
Duplexing – TDD versus FDD n FDD q q q n FDD is used in radio systems that can allocate individual radio frequencies for each user. § For example analog systems: AMPS In FDD channels are allocated by a base station. A channel for a mobile is allocated dynamically All channels that a base station will use are allocated usually statically. More suitable for wide-area cellular networks: GSM, AMPS all use FDD TDD q q q CS 515 Can only be used in digital wireless systems (digital modulation). Requires rigid timing and synchronization Mostly used in short-range and fixed wireless systems so that propagation delay between base and mobile do not change much with respect to location of the mobile. § Such as cordless phones… © Ibrahim Korpeoglu 13
 Multiple Access - Coordinated n n We will look now sharing the media by more than two users. Three major multiple access schemes q Time Division Multiple Access (TDMA) n q Frequency Division Multiple Access (FDMA) n q Usually used narrowband systems Code Division Multiple Access n CS 515 Could be used in narrowband or wideband systems Used in wideband systems. © Ibrahim Korpeoglu 14
Multiple Access - Coordinated n n We will look now sharing the media by more than two users. Three major multiple access schemes q Time Division Multiple Access (TDMA) n q Frequency Division Multiple Access (FDMA) n q Usually used narrowband systems Code Division Multiple Access n CS 515 Could be used in narrowband or wideband systems Used in wideband systems. © Ibrahim Korpeoglu 14
 Narrow- and Wideband Systems n Narrowband System q The channel bandwidth (frequency band allocated for the channel is small) q q n More precisely, the channel bandwidth is large compared to the coherence bandwidth of the channel (remember that coherence bandwidth is related with reciprocal of the delay spread of multipath channel) AMPS is a narrowband system (channel bandwidth is 30 k. Hz in one-way) Wideband Systems q The channel bandwidth is large q q CS 515 More precisely, the channel bandwidth is much larger that the coherence bandwidth of the multipath channel. A large number of users can access the same channel (frequency band) at the same time. © Ibrahim Korpeoglu 15
Narrow- and Wideband Systems n Narrowband System q The channel bandwidth (frequency band allocated for the channel is small) q q n More precisely, the channel bandwidth is large compared to the coherence bandwidth of the channel (remember that coherence bandwidth is related with reciprocal of the delay spread of multipath channel) AMPS is a narrowband system (channel bandwidth is 30 k. Hz in one-way) Wideband Systems q The channel bandwidth is large q q CS 515 More precisely, the channel bandwidth is much larger that the coherence bandwidth of the multipath channel. A large number of users can access the same channel (frequency band) at the same time. © Ibrahim Korpeoglu 15
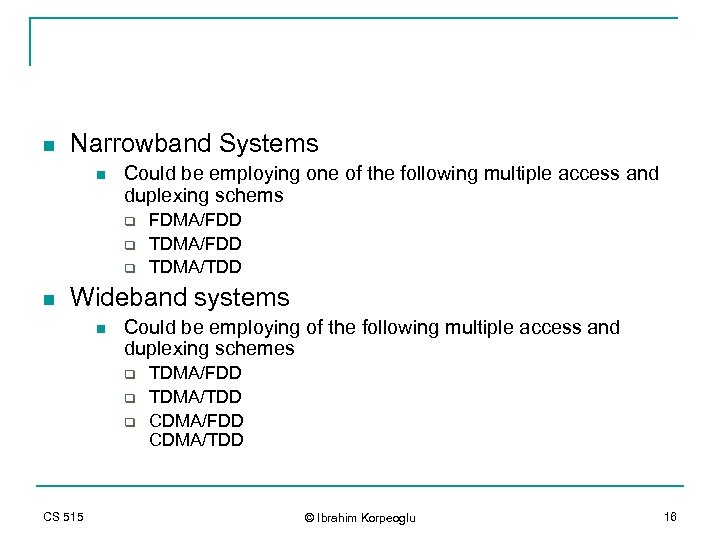 n Narrowband Systems n Could be employing one of the following multiple access and duplexing schems q q q n FDMA/FDD TDMA/TDD Wideband systems n Could be employing of the following multiple access and duplexing schemes q q q CS 515 TDMA/FDD TDMA/TDD CDMA/FDD CDMA/TDD © Ibrahim Korpeoglu 16
n Narrowband Systems n Could be employing one of the following multiple access and duplexing schems q q q n FDMA/FDD TDMA/TDD Wideband systems n Could be employing of the following multiple access and duplexing schemes q q q CS 515 TDMA/FDD TDMA/TDD CDMA/FDD CDMA/TDD © Ibrahim Korpeoglu 16
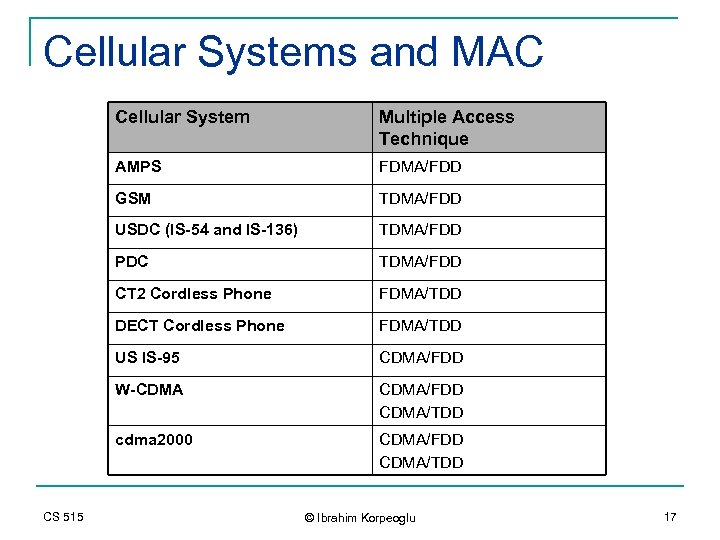 Cellular Systems and MAC Cellular System AMPS FDMA/FDD GSM TDMA/FDD USDC (IS-54 and IS-136) TDMA/FDD PDC TDMA/FDD CT 2 Cordless Phone FDMA/TDD DECT Cordless Phone FDMA/TDD US IS-95 CDMA/FDD W-CDMA/FDD CDMA/TDD cdma 2000 CS 515 Multiple Access Technique CDMA/FDD CDMA/TDD © Ibrahim Korpeoglu 17
Cellular Systems and MAC Cellular System AMPS FDMA/FDD GSM TDMA/FDD USDC (IS-54 and IS-136) TDMA/FDD PDC TDMA/FDD CT 2 Cordless Phone FDMA/TDD DECT Cordless Phone FDMA/TDD US IS-95 CDMA/FDD W-CDMA/FDD CDMA/TDD cdma 2000 CS 515 Multiple Access Technique CDMA/FDD CDMA/TDD © Ibrahim Korpeoglu 17
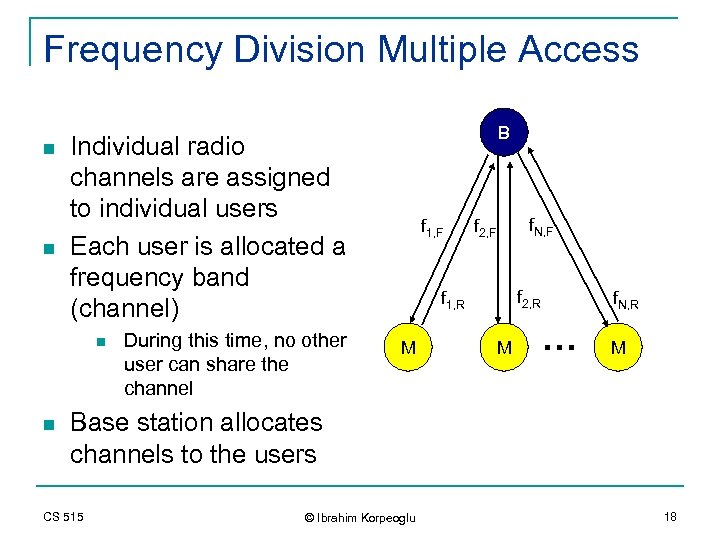 Frequency Division Multiple Access n n Individual radio channels are assigned to individual users Each user is allocated a frequency band (channel) n n B During this time, no other user can share the channel f 1, F f. N, F f 2, R f 1, R M M f. N, R … M Base station allocates channels to the users CS 515 © Ibrahim Korpeoglu 18
Frequency Division Multiple Access n n Individual radio channels are assigned to individual users Each user is allocated a frequency band (channel) n n B During this time, no other user can share the channel f 1, F f. N, F f 2, R f 1, R M M f. N, R … M Base station allocates channels to the users CS 515 © Ibrahim Korpeoglu 18
 Features of FDMA n n n CS 515 An FDMA channel carries one phone circuit at a time If channel allocated to a user is idle, then it is not used by someone else: waste of resource. Mobile and base can transmit and receive simultaneously Bandwidth of FDMA channels are relatively low. Symbol time is usually larger (low data rate) than the delay spread of the multipath channel (implies that intersymbol interference is low) Lower complexity systems that TDMA systems. © Ibrahim Korpeoglu 19
Features of FDMA n n n CS 515 An FDMA channel carries one phone circuit at a time If channel allocated to a user is idle, then it is not used by someone else: waste of resource. Mobile and base can transmit and receive simultaneously Bandwidth of FDMA channels are relatively low. Symbol time is usually larger (low data rate) than the delay spread of the multipath channel (implies that intersymbol interference is low) Lower complexity systems that TDMA systems. © Ibrahim Korpeoglu 19
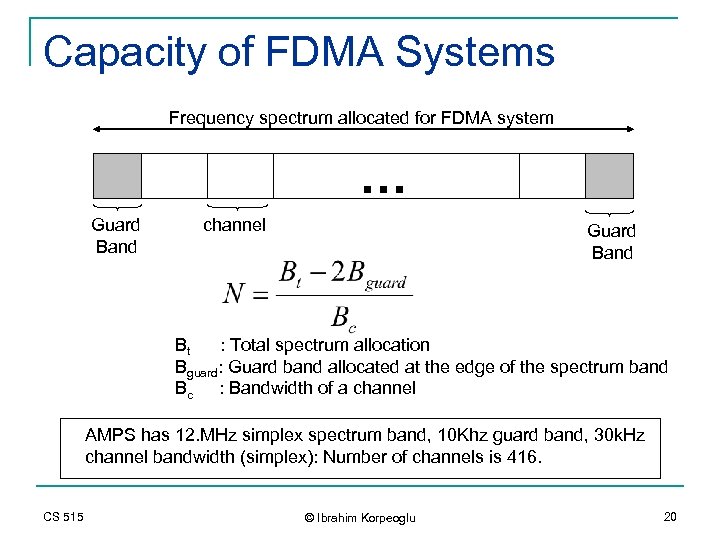 Capacity of FDMA Systems Frequency spectrum allocated for FDMA system … Guard Band channel Guard Band Bt : Total spectrum allocation Bguard: Guard band allocated at the edge of the spectrum band Bc : Bandwidth of a channel AMPS has 12. MHz simplex spectrum band, 10 Khz guard band, 30 k. Hz channel bandwidth (simplex): Number of channels is 416. CS 515 © Ibrahim Korpeoglu 20
Capacity of FDMA Systems Frequency spectrum allocated for FDMA system … Guard Band channel Guard Band Bt : Total spectrum allocation Bguard: Guard band allocated at the edge of the spectrum band Bc : Bandwidth of a channel AMPS has 12. MHz simplex spectrum band, 10 Khz guard band, 30 k. Hz channel bandwidth (simplex): Number of channels is 416. CS 515 © Ibrahim Korpeoglu 20
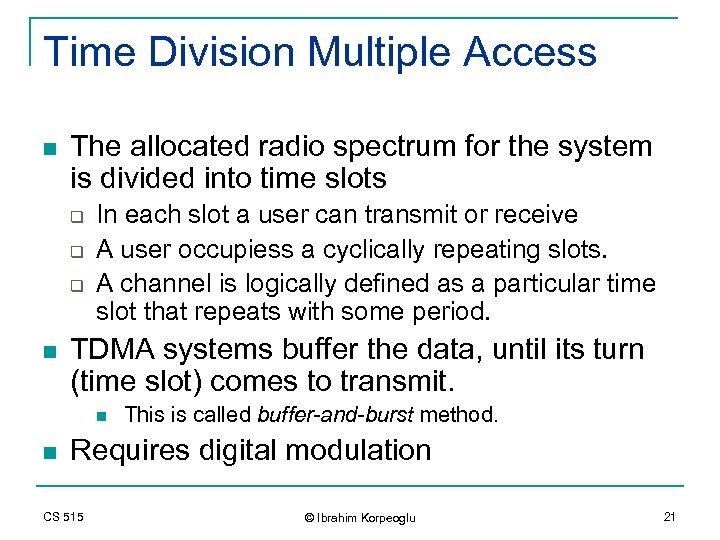 Time Division Multiple Access n The allocated radio spectrum for the system is divided into time slots q q q n In each slot a user can transmit or receive A user occupiess a cyclically repeating slots. A channel is logically defined as a particular time slot that repeats with some period. TDMA systems buffer the data, until its turn (time slot) comes to transmit. n n This is called buffer-and-burst method. Requires digital modulation CS 515 © Ibrahim Korpeoglu 21
Time Division Multiple Access n The allocated radio spectrum for the system is divided into time slots q q q n In each slot a user can transmit or receive A user occupiess a cyclically repeating slots. A channel is logically defined as a particular time slot that repeats with some period. TDMA systems buffer the data, until its turn (time slot) comes to transmit. n n This is called buffer-and-burst method. Requires digital modulation CS 515 © Ibrahim Korpeoglu 21
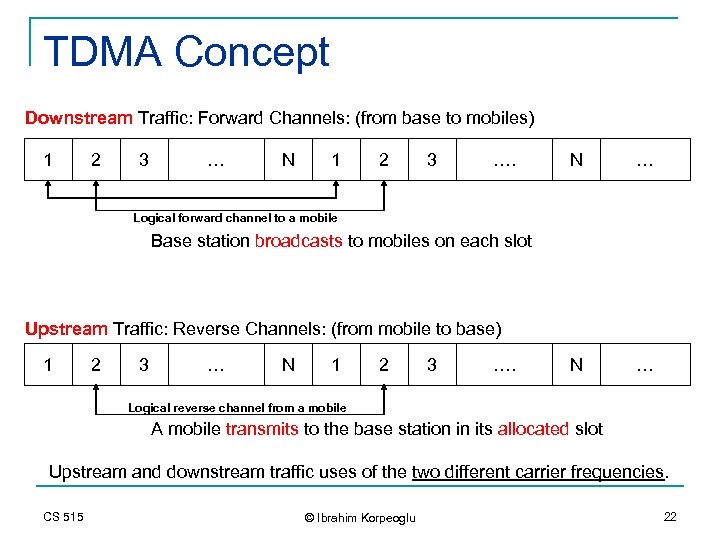 TDMA Concept Downstream Traffic: Forward Channels: (from base to mobiles) 1 2 3 … N 1 2 3 …. N … Logical forward channel to a mobile Base station broadcasts to mobiles on each slot Upstream Traffic: Reverse Channels: (from mobile to base) 1 2 3 … N 1 2 3 …. Logical reverse channel from a mobile A mobile transmits to the base station in its allocated slot Upstream and downstream traffic uses of the two different carrier frequencies. CS 515 © Ibrahim Korpeoglu 22
TDMA Concept Downstream Traffic: Forward Channels: (from base to mobiles) 1 2 3 … N 1 2 3 …. N … Logical forward channel to a mobile Base station broadcasts to mobiles on each slot Upstream Traffic: Reverse Channels: (from mobile to base) 1 2 3 … N 1 2 3 …. Logical reverse channel from a mobile A mobile transmits to the base station in its allocated slot Upstream and downstream traffic uses of the two different carrier frequencies. CS 515 © Ibrahim Korpeoglu 22
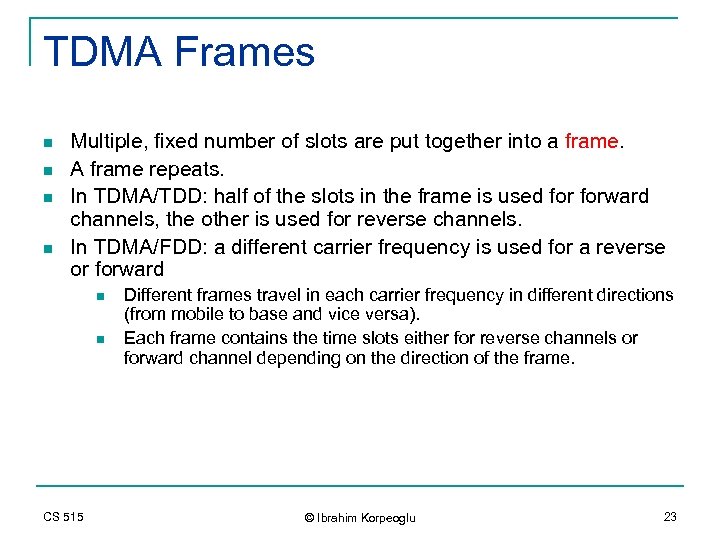 TDMA Frames n n Multiple, fixed number of slots are put together into a frame. A frame repeats. In TDMA/TDD: half of the slots in the frame is used forward channels, the other is used for reverse channels. In TDMA/FDD: a different carrier frequency is used for a reverse or forward n n CS 515 Different frames travel in each carrier frequency in different directions (from mobile to base and vice versa). Each frame contains the time slots either for reverse channels or forward channel depending on the direction of the frame. © Ibrahim Korpeoglu 23
TDMA Frames n n Multiple, fixed number of slots are put together into a frame. A frame repeats. In TDMA/TDD: half of the slots in the frame is used forward channels, the other is used for reverse channels. In TDMA/FDD: a different carrier frequency is used for a reverse or forward n n CS 515 Different frames travel in each carrier frequency in different directions (from mobile to base and vice versa). Each frame contains the time slots either for reverse channels or forward channel depending on the direction of the frame. © Ibrahim Korpeoglu 23
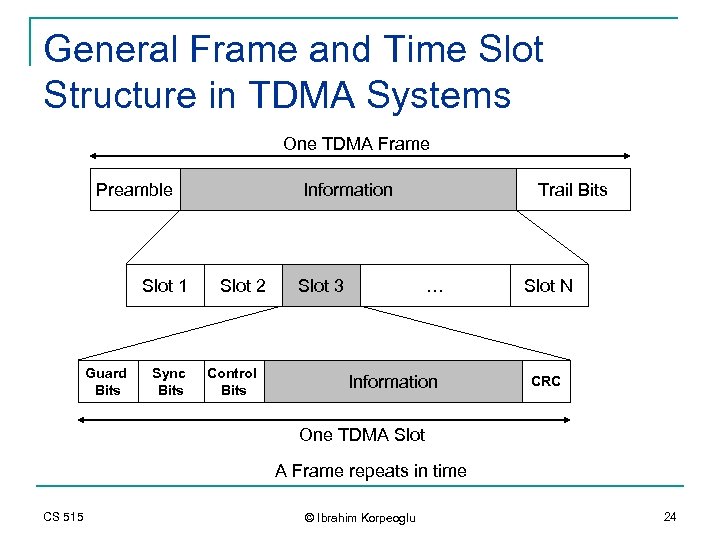 General Frame and Time Slot Structure in TDMA Systems One TDMA Frame Preamble Slot 1 Guard Bits Sync Bits Information Slot 2 Control Bits Slot 3 Trail Bits … Information Slot N CRC One TDMA Slot A Frame repeats in time CS 515 © Ibrahim Korpeoglu 24
General Frame and Time Slot Structure in TDMA Systems One TDMA Frame Preamble Slot 1 Guard Bits Sync Bits Information Slot 2 Control Bits Slot 3 Trail Bits … Information Slot N CRC One TDMA Slot A Frame repeats in time CS 515 © Ibrahim Korpeoglu 24
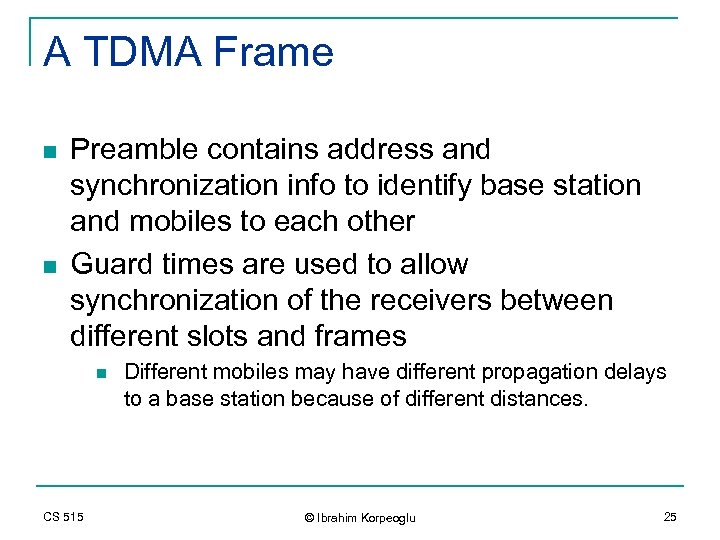 A TDMA Frame n n Preamble contains address and synchronization info to identify base station and mobiles to each other Guard times are used to allow synchronization of the receivers between different slots and frames n CS 515 Different mobiles may have different propagation delays to a base station because of different distances. © Ibrahim Korpeoglu 25
A TDMA Frame n n Preamble contains address and synchronization info to identify base station and mobiles to each other Guard times are used to allow synchronization of the receivers between different slots and frames n CS 515 Different mobiles may have different propagation delays to a base station because of different distances. © Ibrahim Korpeoglu 25
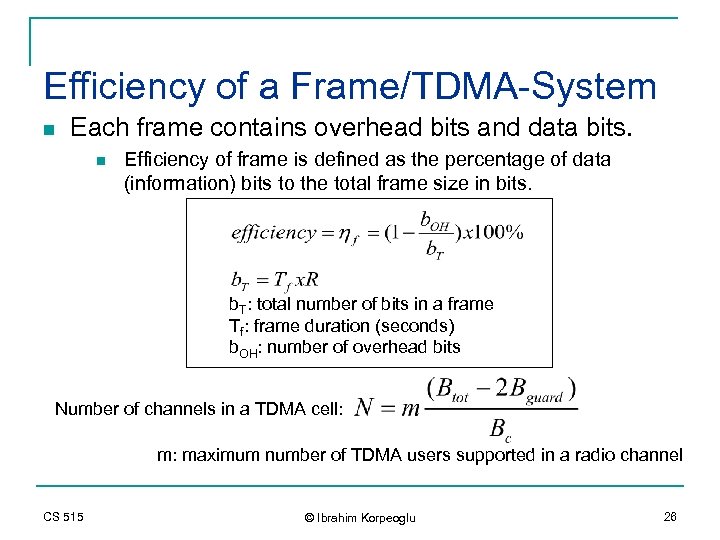 Efficiency of a Frame/TDMA-System n Each frame contains overhead bits and data bits. n Efficiency of frame is defined as the percentage of data (information) bits to the total frame size in bits. b. T: total number of bits in a frame Tf: frame duration (seconds) b. OH: number of overhead bits Number of channels in a TDMA cell: m: maximum number of TDMA users supported in a radio channel CS 515 © Ibrahim Korpeoglu 26
Efficiency of a Frame/TDMA-System n Each frame contains overhead bits and data bits. n Efficiency of frame is defined as the percentage of data (information) bits to the total frame size in bits. b. T: total number of bits in a frame Tf: frame duration (seconds) b. OH: number of overhead bits Number of channels in a TDMA cell: m: maximum number of TDMA users supported in a radio channel CS 515 © Ibrahim Korpeoglu 26
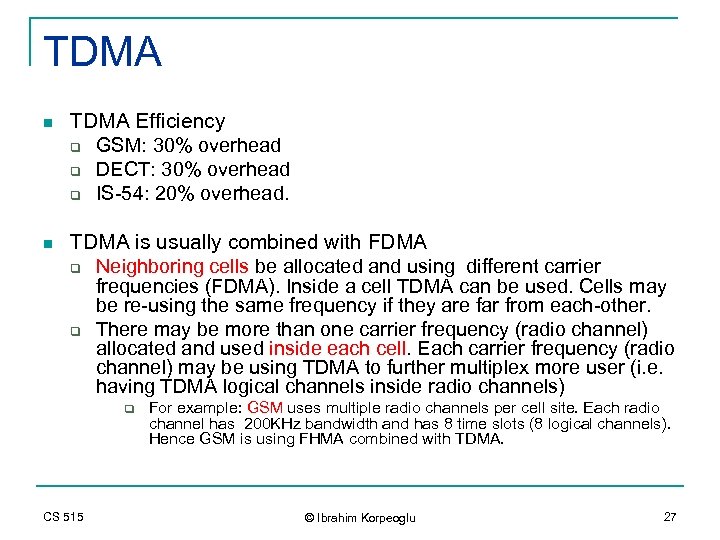 TDMA n TDMA Efficiency q GSM: 30% overhead q DECT: 30% overhead q IS-54: 20% overhead. n TDMA is usually combined with FDMA q Neighboring cells be allocated and using different carrier frequencies (FDMA). Inside a cell TDMA can be used. Cells may be re-using the same frequency if they are far from each-other. q There may be more than one carrier frequency (radio channel) allocated and used inside each cell. Each carrier frequency (radio channel) may be using TDMA to further multiplex more user (i. e. having TDMA logical channels inside radio channels) q CS 515 For example: GSM uses multiple radio channels per cell site. Each radio channel has 200 KHz bandwidth and has 8 time slots (8 logical channels). Hence GSM is using FHMA combined with TDMA. © Ibrahim Korpeoglu 27
TDMA n TDMA Efficiency q GSM: 30% overhead q DECT: 30% overhead q IS-54: 20% overhead. n TDMA is usually combined with FDMA q Neighboring cells be allocated and using different carrier frequencies (FDMA). Inside a cell TDMA can be used. Cells may be re-using the same frequency if they are far from each-other. q There may be more than one carrier frequency (radio channel) allocated and used inside each cell. Each carrier frequency (radio channel) may be using TDMA to further multiplex more user (i. e. having TDMA logical channels inside radio channels) q CS 515 For example: GSM uses multiple radio channels per cell site. Each radio channel has 200 KHz bandwidth and has 8 time slots (8 logical channels). Hence GSM is using FHMA combined with TDMA. © Ibrahim Korpeoglu 27
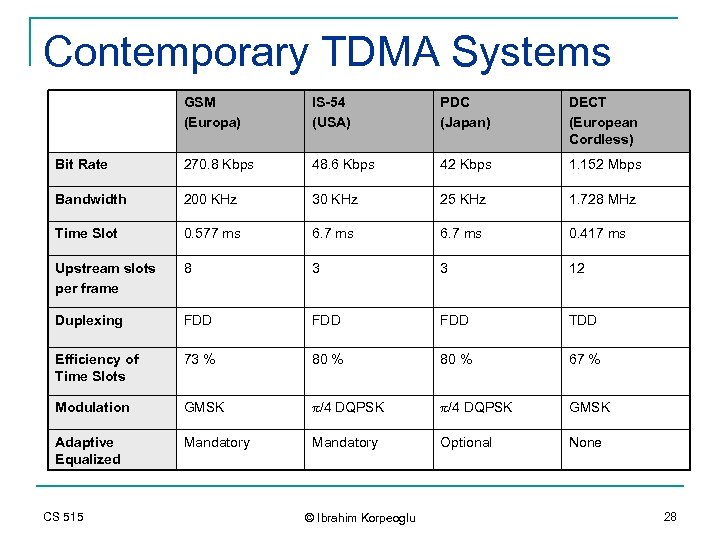 Contemporary TDMA Systems GSM (Europa) IS-54 (USA) PDC (Japan) DECT (European Cordless) Bit Rate 270. 8 Kbps 48. 6 Kbps 42 Kbps 1. 152 Mbps Bandwidth 200 KHz 30 KHz 25 KHz 1. 728 MHz Time Slot 0. 577 ms 6. 7 ms 0. 417 ms Upstream slots per frame 8 3 3 12 Duplexing FDD FDD TDD Efficiency of Time Slots 73 % 80 % 67 % Modulation GMSK p/4 DQPSK GMSK Adaptive Equalized Mandatory Optional None CS 515 © Ibrahim Korpeoglu 28
Contemporary TDMA Systems GSM (Europa) IS-54 (USA) PDC (Japan) DECT (European Cordless) Bit Rate 270. 8 Kbps 48. 6 Kbps 42 Kbps 1. 152 Mbps Bandwidth 200 KHz 30 KHz 25 KHz 1. 728 MHz Time Slot 0. 577 ms 6. 7 ms 0. 417 ms Upstream slots per frame 8 3 3 12 Duplexing FDD FDD TDD Efficiency of Time Slots 73 % 80 % 67 % Modulation GMSK p/4 DQPSK GMSK Adaptive Equalized Mandatory Optional None CS 515 © Ibrahim Korpeoglu 28
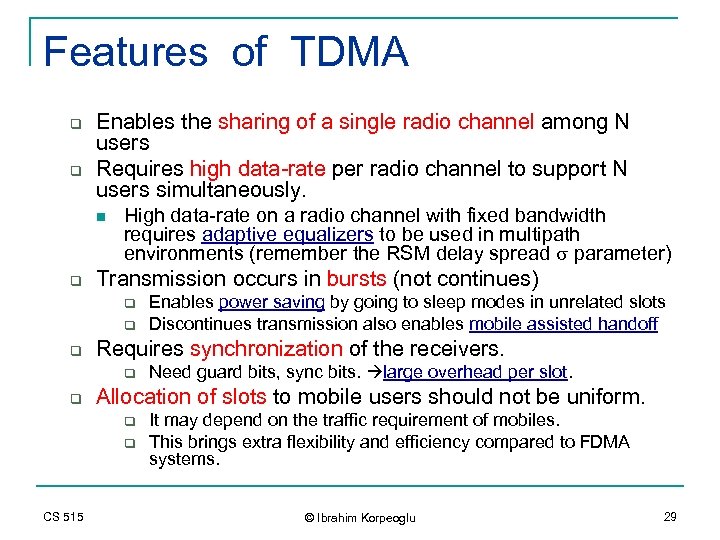 Features of TDMA q q Enables the sharing of a single radio channel among N users Requires high data-rate per radio channel to support N users simultaneously. n q High data-rate on a radio channel with fixed bandwidth requires adaptive equalizers to be used in multipath environments (remember the RSM delay spread s parameter) Transmission occurs in bursts (not continues) q q q Requires synchronization of the receivers. q q Need guard bits, sync bits. large overhead per slot. Allocation of slots to mobile users should not be uniform. q q CS 515 Enables power saving by going to sleep modes in unrelated slots Discontinues transmission also enables mobile assisted handoff It may depend on the traffic requirement of mobiles. This brings extra flexibility and efficiency compared to FDMA systems. © Ibrahim Korpeoglu 29
Features of TDMA q q Enables the sharing of a single radio channel among N users Requires high data-rate per radio channel to support N users simultaneously. n q High data-rate on a radio channel with fixed bandwidth requires adaptive equalizers to be used in multipath environments (remember the RSM delay spread s parameter) Transmission occurs in bursts (not continues) q q q Requires synchronization of the receivers. q q Need guard bits, sync bits. large overhead per slot. Allocation of slots to mobile users should not be uniform. q q CS 515 Enables power saving by going to sleep modes in unrelated slots Discontinues transmission also enables mobile assisted handoff It may depend on the traffic requirement of mobiles. This brings extra flexibility and efficiency compared to FDMA systems. © Ibrahim Korpeoglu 29
 Capacity of TDMA Systems n Capacity can be expressed as q System Capacity (the capacity of the overall system covering a region) q q Cell Capacity q CS 515 Depends on: § Range of cells § Whether the system can support macro-cells, micro-cells or picocells. Depends on the radio link performance between a base-sation and mobiles: § The lowest C/I (carrier-to-interence) ratio the system can operate for example quality of transmission. This in turn depends on the speech coding technique, desired speech quality, etc. § Data-rate over the channel which depends modulation efficiency (bits_per_second/Hz) and channel bandwidth. § The frequency re-use factor © Ibrahim Korpeoglu 30
Capacity of TDMA Systems n Capacity can be expressed as q System Capacity (the capacity of the overall system covering a region) q q Cell Capacity q CS 515 Depends on: § Range of cells § Whether the system can support macro-cells, micro-cells or picocells. Depends on the radio link performance between a base-sation and mobiles: § The lowest C/I (carrier-to-interence) ratio the system can operate for example quality of transmission. This in turn depends on the speech coding technique, desired speech quality, etc. § Data-rate over the channel which depends modulation efficiency (bits_per_second/Hz) and channel bandwidth. § The frequency re-use factor © Ibrahim Korpeoglu 30
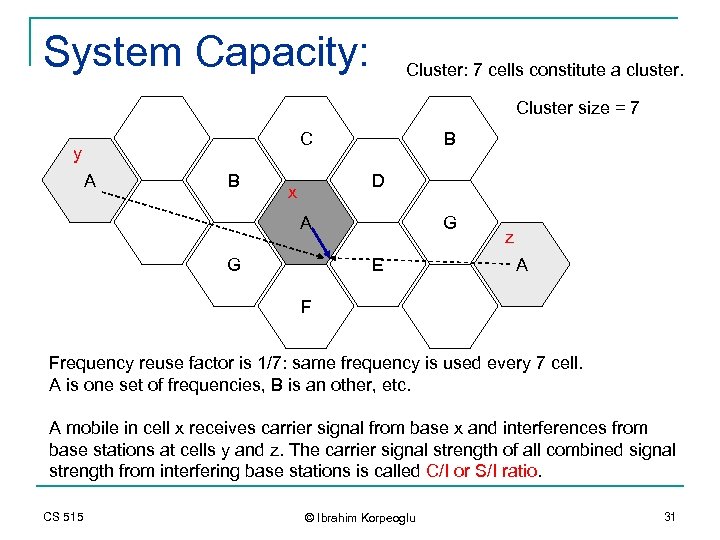 System Capacity: Cluster: 7 cells constitute a cluster. Cluster size = 7 C y A B B D x A G G E z A F Frequency reuse factor is 1/7: same frequency is used every 7 cell. A is one set of frequencies, B is an other, etc. A mobile in cell x receives carrier signal from base x and interferences from base stations at cells y and z. The carrier signal strength of all combined signal strength from interfering base stations is called C/I or S/I ratio. CS 515 © Ibrahim Korpeoglu 31
System Capacity: Cluster: 7 cells constitute a cluster. Cluster size = 7 C y A B B D x A G G E z A F Frequency reuse factor is 1/7: same frequency is used every 7 cell. A is one set of frequencies, B is an other, etc. A mobile in cell x receives carrier signal from base x and interferences from base stations at cells y and z. The carrier signal strength of all combined signal strength from interfering base stations is called C/I or S/I ratio. CS 515 © Ibrahim Korpeoglu 31
 C/I affect on capacity q C/I ratio affects the cluster size, hence the frequency reuse factor. q q q Cluster size affects the cell capacity n q CS 515 Frequency_reuse_factor = 1 / cluster_size Cluster size can be 3, 7, 12, 13, … (it affects the maximum number of frequencies that can be used in a cell) A low C/I requirement for appropriate quality enables smaller cluster sizes, hence larger frequency reuse factor, meaning that larger cell capacities © Ibrahim Korpeoglu 32
C/I affect on capacity q C/I ratio affects the cluster size, hence the frequency reuse factor. q q q Cluster size affects the cell capacity n q CS 515 Frequency_reuse_factor = 1 / cluster_size Cluster size can be 3, 7, 12, 13, … (it affects the maximum number of frequencies that can be used in a cell) A low C/I requirement for appropriate quality enables smaller cluster sizes, hence larger frequency reuse factor, meaning that larger cell capacities © Ibrahim Korpeoglu 32
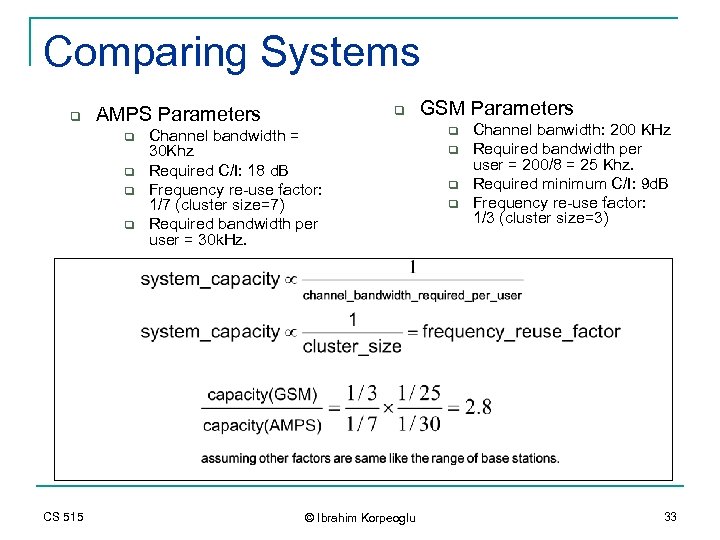 Comparing Systems q AMPS Parameters q q CS 515 q Channel bandwidth = 30 Khz Required C/I: 18 d. B Frequency re-use factor: 1/7 (cluster size=7) Required bandwidth per user = 30 k. Hz. © Ibrahim Korpeoglu GSM Parameters q q Channel banwidth: 200 KHz Required bandwidth per user = 200/8 = 25 Khz. Required minimum C/I: 9 d. B Frequency re-use factor: 1/3 (cluster size=3) 33
Comparing Systems q AMPS Parameters q q CS 515 q Channel bandwidth = 30 Khz Required C/I: 18 d. B Frequency re-use factor: 1/7 (cluster size=7) Required bandwidth per user = 30 k. Hz. © Ibrahim Korpeoglu GSM Parameters q q Channel banwidth: 200 KHz Required bandwidth per user = 200/8 = 25 Khz. Required minimum C/I: 9 d. B Frequency re-use factor: 1/3 (cluster size=3) 33
 Spread Spectrum Access n n SSMA uses signals that have transmission bandwidth that is several orders of magnitued larger than minimum required RF bandwidth. Provides q q n Immunity to multipath interference Robust multiple access. Two techniques q q Frequency Hopped Multiple Access (FHMA) Direct Sequence Multiple Access (DSMA) q CS 515 Also called Code Division Multiple Access – CDMA © Ibrahim Korpeoglu 34
Spread Spectrum Access n n SSMA uses signals that have transmission bandwidth that is several orders of magnitued larger than minimum required RF bandwidth. Provides q q n Immunity to multipath interference Robust multiple access. Two techniques q q Frequency Hopped Multiple Access (FHMA) Direct Sequence Multiple Access (DSMA) q CS 515 Also called Code Division Multiple Access – CDMA © Ibrahim Korpeoglu 34
 Frequency Hopping (FHMA) n n Digital muliple access technique A wideband radio channel is used. n n Same wideband spectrum is used The carrier frequency of users are varied in a pseudo-random fashion. q q Each user is using a narrowband channel (spectrum) at a specific instance of time. The random change in frequency make the change of using the same narrowband channel very low. n The sender receiver change frequency (calling hopping) using the same pseudo-random sequence, hence they are synchronized. n Rate of hopping versus Symbol rate n If hopping rate is greather: Called Fast Frequency Hopping q n If symbol rate is greater: Called Slow Frequency Hopping q q CS 515 One bit transmitted in multiple hops. Multiple bits are transmitted in a hopping period GSM and Bluetooth are example systems © Ibrahim Korpeoglu 35
Frequency Hopping (FHMA) n n Digital muliple access technique A wideband radio channel is used. n n Same wideband spectrum is used The carrier frequency of users are varied in a pseudo-random fashion. q q Each user is using a narrowband channel (spectrum) at a specific instance of time. The random change in frequency make the change of using the same narrowband channel very low. n The sender receiver change frequency (calling hopping) using the same pseudo-random sequence, hence they are synchronized. n Rate of hopping versus Symbol rate n If hopping rate is greather: Called Fast Frequency Hopping q n If symbol rate is greater: Called Slow Frequency Hopping q q CS 515 One bit transmitted in multiple hops. Multiple bits are transmitted in a hopping period GSM and Bluetooth are example systems © Ibrahim Korpeoglu 35
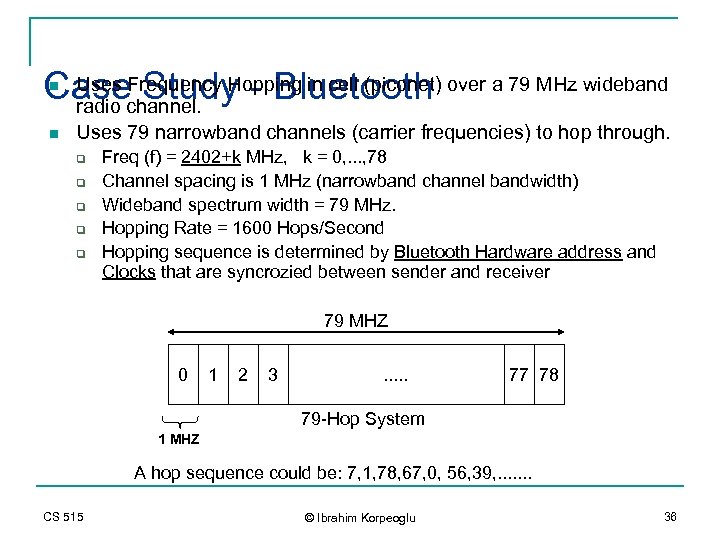 Uses Frequency - Bluetooth Casechannel. Hopping in cell (piconet) over a 79 MHz wideband Study radio n n Uses 79 narrowband channels (carrier frequencies) to hop through. q q q Freq (f) = 2402+k MHz, k = 0, . . . , 78 Channel spacing is 1 MHz (narrowband channel bandwidth) Wideband spectrum width = 79 MHz. Hopping Rate = 1600 Hops/Second Hopping sequence is determined by Bluetooth Hardware address and Clocks that are syncrozied between sender and receiver 79 MHZ 0 1 2 3 . . . 77 78 79 -Hop System 1 MHZ A hop sequence could be: 7, 1, 78, 67, 0, 56, 39, . . . . CS 515 © Ibrahim Korpeoglu 36
Uses Frequency - Bluetooth Casechannel. Hopping in cell (piconet) over a 79 MHz wideband Study radio n n Uses 79 narrowband channels (carrier frequencies) to hop through. q q q Freq (f) = 2402+k MHz, k = 0, . . . , 78 Channel spacing is 1 MHz (narrowband channel bandwidth) Wideband spectrum width = 79 MHz. Hopping Rate = 1600 Hops/Second Hopping sequence is determined by Bluetooth Hardware address and Clocks that are syncrozied between sender and receiver 79 MHZ 0 1 2 3 . . . 77 78 79 -Hop System 1 MHZ A hop sequence could be: 7, 1, 78, 67, 0, 56, 39, . . . . CS 515 © Ibrahim Korpeoglu 36
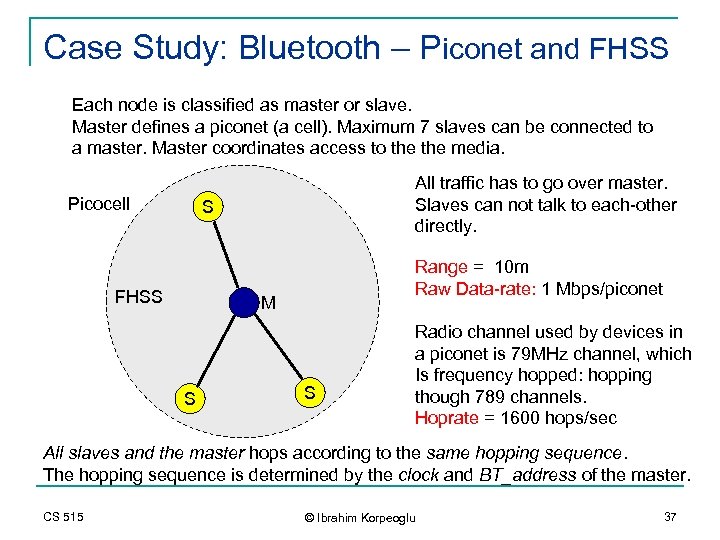 Case Study: Bluetooth – Piconet and FHSS Each node is classified as master or slave. Master defines a piconet (a cell). Maximum 7 slaves can be connected to a master. Master coordinates access to the media. Picocell All traffic has to go over master. Slaves can not talk to each-other directly. S FHSS Range = 10 m Raw Data-rate: 1 Mbps/piconet M S S Radio channel used by devices in a piconet is 79 MHz channel, which Is frequency hopped: hopping though 789 channels. Hoprate = 1600 hops/sec All slaves and the master hops according to the same hopping sequence. The hopping sequence is determined by the clock and BT_address of the master. CS 515 © Ibrahim Korpeoglu 37
Case Study: Bluetooth – Piconet and FHSS Each node is classified as master or slave. Master defines a piconet (a cell). Maximum 7 slaves can be connected to a master. Master coordinates access to the media. Picocell All traffic has to go over master. Slaves can not talk to each-other directly. S FHSS Range = 10 m Raw Data-rate: 1 Mbps/piconet M S S Radio channel used by devices in a piconet is 79 MHz channel, which Is frequency hopped: hopping though 789 channels. Hoprate = 1600 hops/sec All slaves and the master hops according to the same hopping sequence. The hopping sequence is determined by the clock and BT_address of the master. CS 515 © Ibrahim Korpeoglu 37
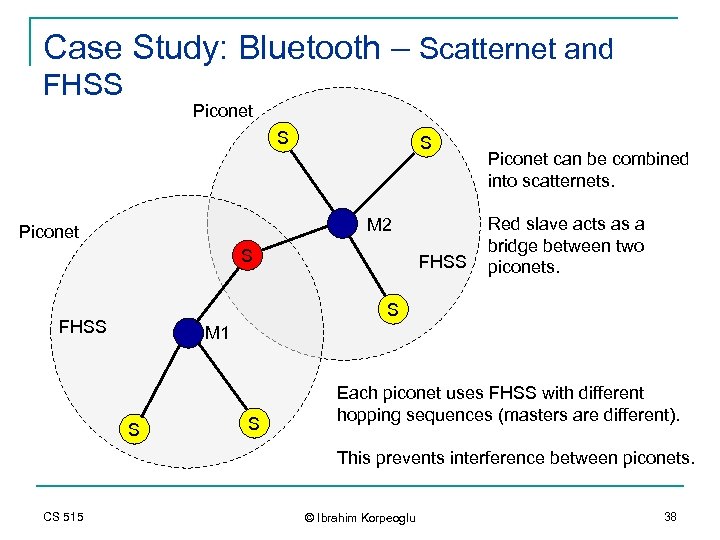 Case Study: Bluetooth – Scatternet and FHSS Piconet S S M 2 Piconet S FHSS Piconet can be combined into scatternets. Red slave acts as a bridge between two piconets. S FHSS M 1 S S Each piconet uses FHSS with different hopping sequences (masters are different). This prevents interference between piconets. CS 515 © Ibrahim Korpeoglu 38
Case Study: Bluetooth – Scatternet and FHSS Piconet S S M 2 Piconet S FHSS Piconet can be combined into scatternets. Red slave acts as a bridge between two piconets. S FHSS M 1 S S Each piconet uses FHSS with different hopping sequences (masters are different). This prevents interference between piconets. CS 515 © Ibrahim Korpeoglu 38
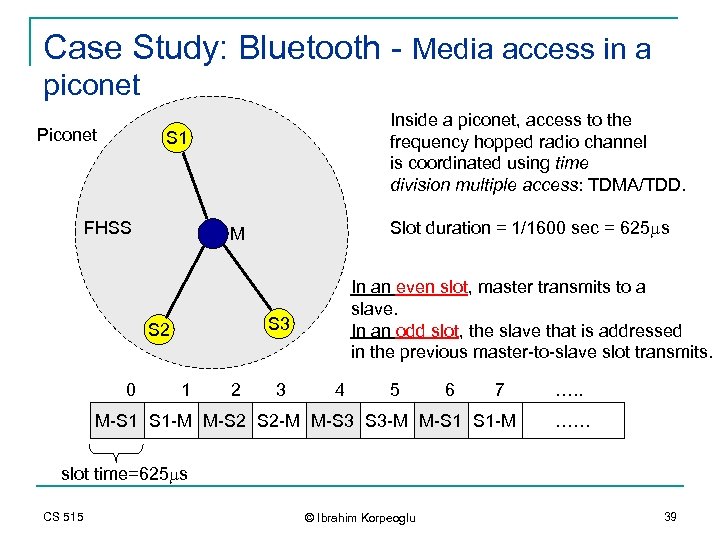 Case Study: Bluetooth - Media access in a piconet Piconet Inside a piconet, access to the frequency hopped radio channel is coordinated using time division multiple access: TDMA/TDD. S 1 FHSS In an even slot, master transmits to a slave. In an odd slot, the slave that is addressed in the previous master-to-slave slot transmits. S 3 S 2 0 Slot duration = 1/1600 sec = 625 ms M 1 2 3 4 5 6 7 M-S 1 S 1 -M M-S 2 S 2 -M M-S 3 S 3 -M M-S 1 S 1 -M …. . …… slot time=625 ms CS 515 © Ibrahim Korpeoglu 39
Case Study: Bluetooth - Media access in a piconet Piconet Inside a piconet, access to the frequency hopped radio channel is coordinated using time division multiple access: TDMA/TDD. S 1 FHSS In an even slot, master transmits to a slave. In an odd slot, the slave that is addressed in the previous master-to-slave slot transmits. S 3 S 2 0 Slot duration = 1/1600 sec = 625 ms M 1 2 3 4 5 6 7 M-S 1 S 1 -M M-S 2 S 2 -M M-S 3 S 3 -M M-S 1 S 1 -M …. . …… slot time=625 ms CS 515 © Ibrahim Korpeoglu 39
 Code Division Multiple Access (CDMA) n n n In CDMA, the narrowband message signal is multiplied by a very large bandwidth signal called spreading signal (code) before modulation and transmission over the air. This is called spreading. CDMA is also called DSSS (Direct Sequence Spread Spectrum). DSSS is a more general term. Message consists of symbols n n Spreading signal (code) consists of chips n n n n Has symbol period and hence, symbol rate Has Chip period and hence, chip rate Spreading signal use a pseudo-noise (PN) sequence (a pseudo-random sequence) PN sequence is called a codeword Each user has its own cordword Codewords are orthogonal. (low autocorrelation) Chip rate is oder of magnitude larger than the symbol rate. The receiver correlator distinguishes the senders signal by examining the wideband signal with the same time-synchronized spreading code The sent signal is recovered by despreading process at the receiver. CS 515 © Ibrahim Korpeoglu 40
Code Division Multiple Access (CDMA) n n n In CDMA, the narrowband message signal is multiplied by a very large bandwidth signal called spreading signal (code) before modulation and transmission over the air. This is called spreading. CDMA is also called DSSS (Direct Sequence Spread Spectrum). DSSS is a more general term. Message consists of symbols n n Spreading signal (code) consists of chips n n n n Has symbol period and hence, symbol rate Has Chip period and hence, chip rate Spreading signal use a pseudo-noise (PN) sequence (a pseudo-random sequence) PN sequence is called a codeword Each user has its own cordword Codewords are orthogonal. (low autocorrelation) Chip rate is oder of magnitude larger than the symbol rate. The receiver correlator distinguishes the senders signal by examining the wideband signal with the same time-synchronized spreading code The sent signal is recovered by despreading process at the receiver. CS 515 © Ibrahim Korpeoglu 40
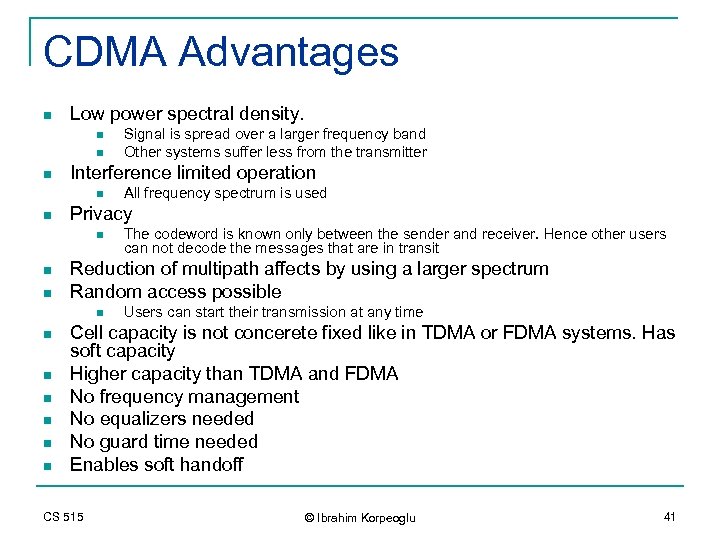 CDMA Advantages n Low power spectral density. n n n Interference limited operation n n n n The codeword is known only between the sender and receiver. Hence other users can not decode the messages that are in transit Reduction of multipath affects by using a larger spectrum Random access possible n n All frequency spectrum is used Privacy n n Signal is spread over a larger frequency band Other systems suffer less from the transmitter Users can start their transmission at any time Cell capacity is not concerete fixed like in TDMA or FDMA systems. Has soft capacity Higher capacity than TDMA and FDMA No frequency management No equalizers needed No guard time needed Enables soft handoff CS 515 © Ibrahim Korpeoglu 41
CDMA Advantages n Low power spectral density. n n n Interference limited operation n n n n The codeword is known only between the sender and receiver. Hence other users can not decode the messages that are in transit Reduction of multipath affects by using a larger spectrum Random access possible n n All frequency spectrum is used Privacy n n Signal is spread over a larger frequency band Other systems suffer less from the transmitter Users can start their transmission at any time Cell capacity is not concerete fixed like in TDMA or FDMA systems. Has soft capacity Higher capacity than TDMA and FDMA No frequency management No equalizers needed No guard time needed Enables soft handoff CS 515 © Ibrahim Korpeoglu 41
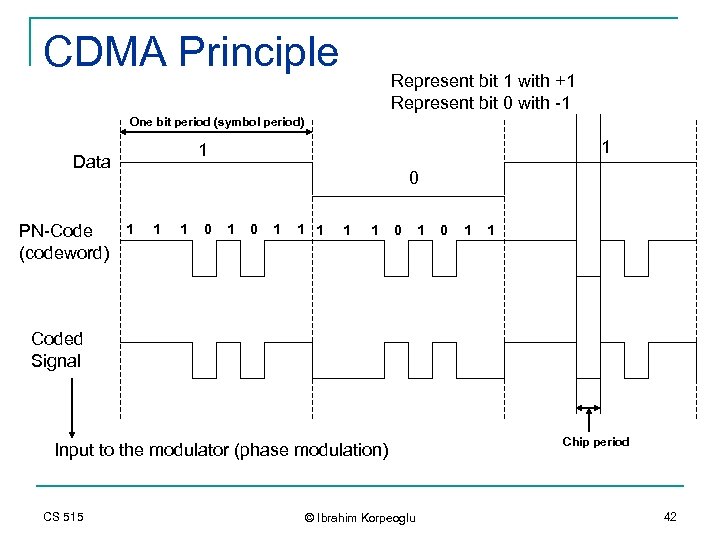 CDMA Principle Represent bit 1 with +1 Represent bit 0 with -1 One bit period (symbol period) PN-Code (codeword) 1 1 Data 0 1 1 1 0 1 0 1 1 Coded Signal Input to the modulator (phase modulation) CS 515 © Ibrahim Korpeoglu Chip period 42
CDMA Principle Represent bit 1 with +1 Represent bit 0 with -1 One bit period (symbol period) PN-Code (codeword) 1 1 Data 0 1 1 1 0 1 0 1 1 Coded Signal Input to the modulator (phase modulation) CS 515 © Ibrahim Korpeoglu Chip period 42
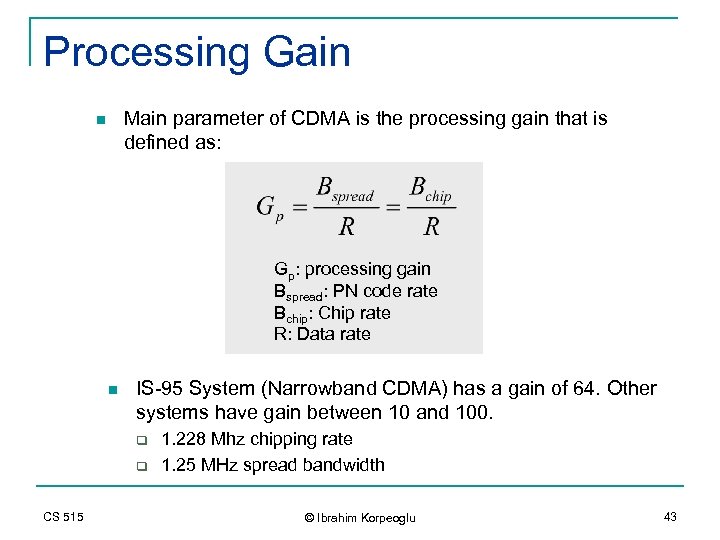 Processing Gain Main parameter of CDMA is the processing gain that is defined as: n Gp: processing gain Bspread: PN code rate Bchip: Chip rate R: Data rate n IS-95 System (Narrowband CDMA) has a gain of 64. Other systems have gain between 10 and 100. q q CS 515 1. 228 Mhz chipping rate 1. 25 MHz spread bandwidth © Ibrahim Korpeoglu 43
Processing Gain Main parameter of CDMA is the processing gain that is defined as: n Gp: processing gain Bspread: PN code rate Bchip: Chip rate R: Data rate n IS-95 System (Narrowband CDMA) has a gain of 64. Other systems have gain between 10 and 100. q q CS 515 1. 228 Mhz chipping rate 1. 25 MHz spread bandwidth © Ibrahim Korpeoglu 43
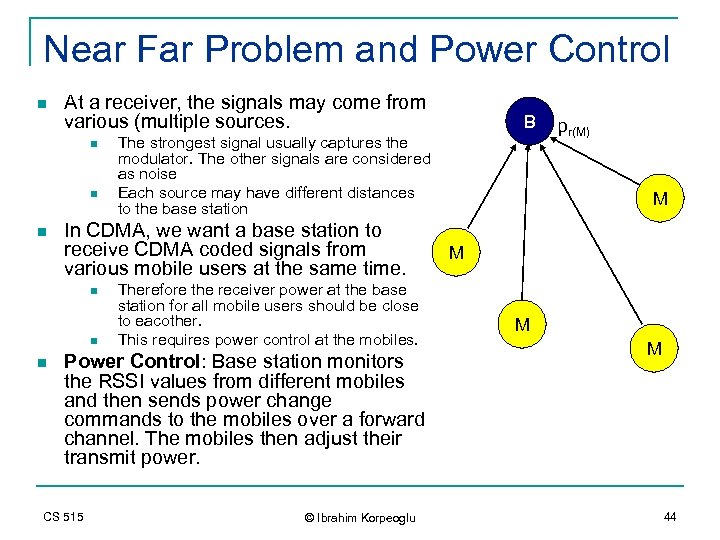 Near Far Problem and Power Control n At a receiver, the signals may come from various (multiple sources. n n n The strongest signal usually captures the modulator. The other signals are considered as noise Each source may have different distances to the base station In CDMA, we want a base station to receive CDMA coded signals from various mobile users at the same time. n Therefore the receiver power at the base station for all mobile users should be close to eacother. This requires power control at the mobiles. Power Control: Base station monitors the RSSI values from different mobiles and then sends power change commands to the mobiles over a forward channel. The mobiles then adjust their transmit power. CS 515 B © Ibrahim Korpeoglu pr(M) M M 44
Near Far Problem and Power Control n At a receiver, the signals may come from various (multiple sources. n n n The strongest signal usually captures the modulator. The other signals are considered as noise Each source may have different distances to the base station In CDMA, we want a base station to receive CDMA coded signals from various mobile users at the same time. n Therefore the receiver power at the base station for all mobile users should be close to eacother. This requires power control at the mobiles. Power Control: Base station monitors the RSSI values from different mobiles and then sends power change commands to the mobiles over a forward channel. The mobiles then adjust their transmit power. CS 515 B © Ibrahim Korpeoglu pr(M) M M 44
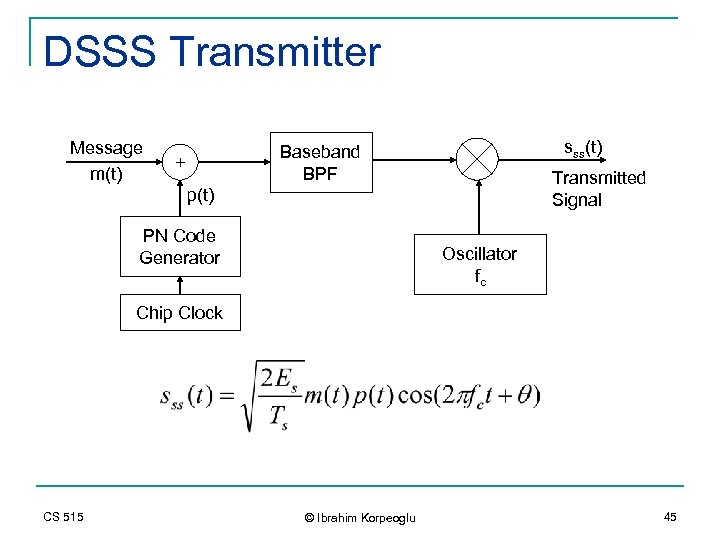 DSSS Transmitter Message m(t) sss(t) Baseband BPF + Transmitted Signal p(t) PN Code Generator Oscillator fc Chip Clock CS 515 © Ibrahim Korpeoglu 45
DSSS Transmitter Message m(t) sss(t) Baseband BPF + Transmitted Signal p(t) PN Code Generator Oscillator fc Chip Clock CS 515 © Ibrahim Korpeoglu 45
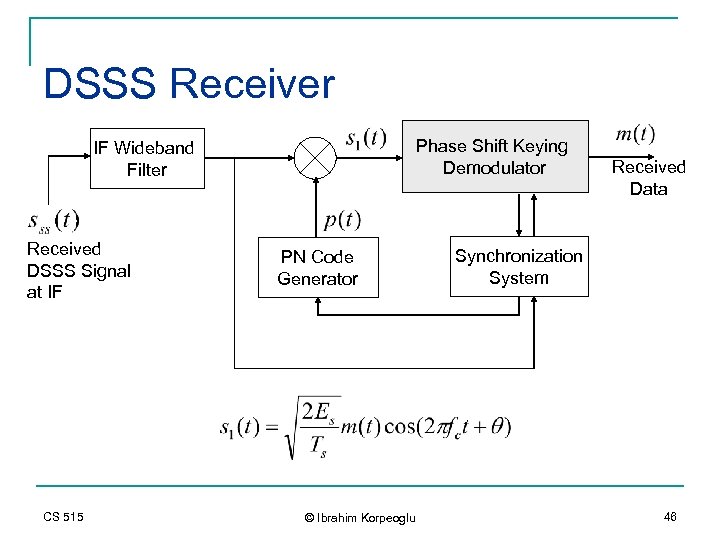 DSSS Receiver Phase Shift Keying Demodulator IF Wideband Filter Received DSSS Signal at IF CS 515 PN Code Generator © Ibrahim Korpeoglu Received Data Synchronization System 46
DSSS Receiver Phase Shift Keying Demodulator IF Wideband Filter Received DSSS Signal at IF CS 515 PN Code Generator © Ibrahim Korpeoglu Received Data Synchronization System 46
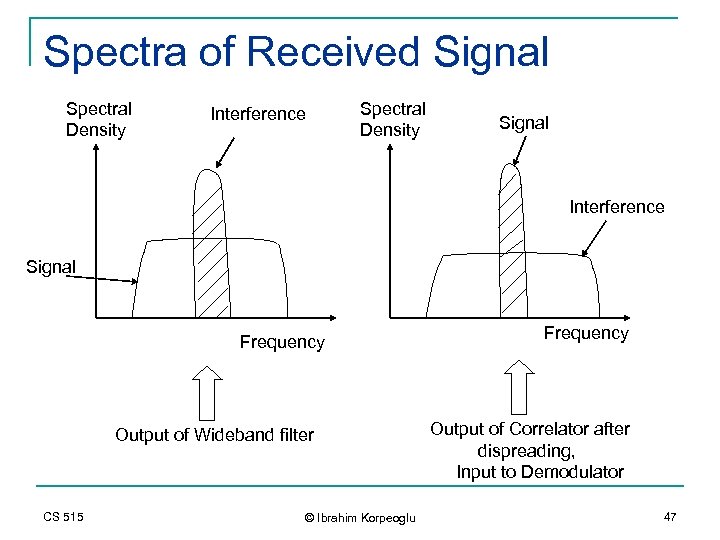 Spectra of Received Signal Spectral Density Interference Spectral Density Signal Interference Signal Frequency Output of Wideband filter CS 515 © Ibrahim Korpeoglu Frequency Output of Correlator after dispreading, Input to Demodulator 47
Spectra of Received Signal Spectral Density Interference Spectral Density Signal Interference Signal Frequency Output of Wideband filter CS 515 © Ibrahim Korpeoglu Frequency Output of Correlator after dispreading, Input to Demodulator 47
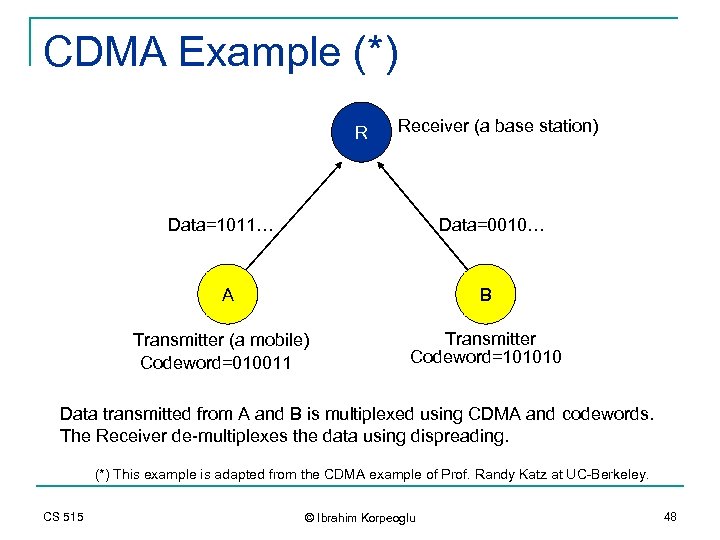 CDMA Example (*) R Receiver (a base station) Data=1011… Data=0010… A B Transmitter (a mobile) Codeword=010011 Transmitter Codeword=101010 Data transmitted from A and B is multiplexed using CDMA and codewords. The Receiver de-multiplexes the data using dispreading. (*) This example is adapted from the CDMA example of Prof. Randy Katz at UC-Berkeley. CS 515 © Ibrahim Korpeoglu 48
CDMA Example (*) R Receiver (a base station) Data=1011… Data=0010… A B Transmitter (a mobile) Codeword=010011 Transmitter Codeword=101010 Data transmitted from A and B is multiplexed using CDMA and codewords. The Receiver de-multiplexes the data using dispreading. (*) This example is adapted from the CDMA example of Prof. Randy Katz at UC-Berkeley. CS 515 © Ibrahim Korpeoglu 48
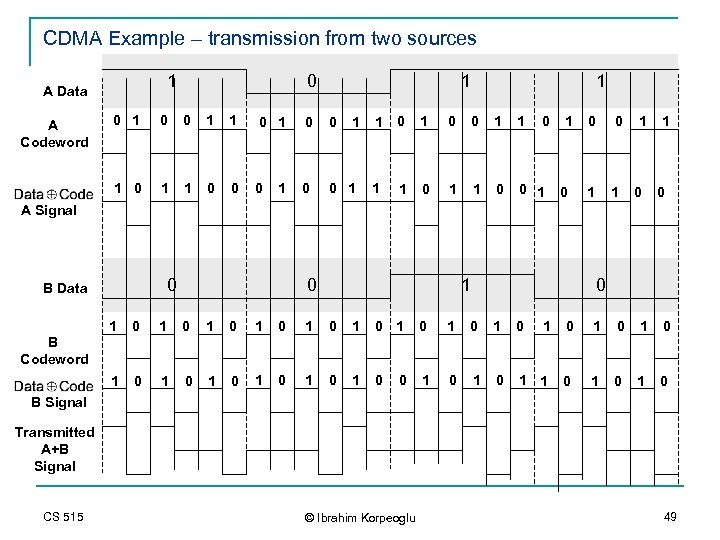 CDMA Example – transmission from two sources 1 A Data 0 1 1 0 1 0 0 1 1 1 0 A Codeword 1 1 0 0 0 1 1 1 0 0 1 1 0 A Signal 0 B Data 0 1 0 1 0 1 0 1 0 1 0 1 1 0 1 0 B Codeword 0 B Signal Transmitted A+B Signal CS 515 © Ibrahim Korpeoglu 49
CDMA Example – transmission from two sources 1 A Data 0 1 1 0 1 0 0 1 1 1 0 A Codeword 1 1 0 0 0 1 1 1 0 0 1 1 0 A Signal 0 B Data 0 1 0 1 0 1 0 1 0 1 0 1 1 0 1 0 B Codeword 0 B Signal Transmitted A+B Signal CS 515 © Ibrahim Korpeoglu 49
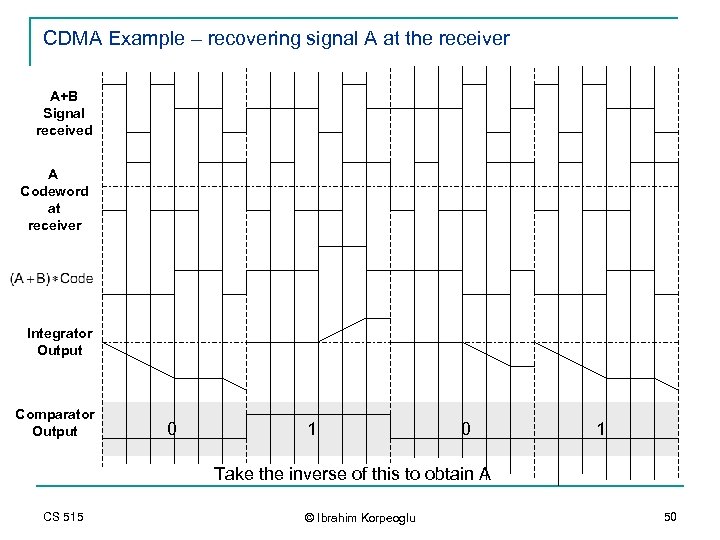 CDMA Example – recovering signal A at the receiver A+B Signal received A Codeword at receiver Integrator Output Comparator Output 0 1 Take the inverse of this to obtain A CS 515 © Ibrahim Korpeoglu 50
CDMA Example – recovering signal A at the receiver A+B Signal received A Codeword at receiver Integrator Output Comparator Output 0 1 Take the inverse of this to obtain A CS 515 © Ibrahim Korpeoglu 50
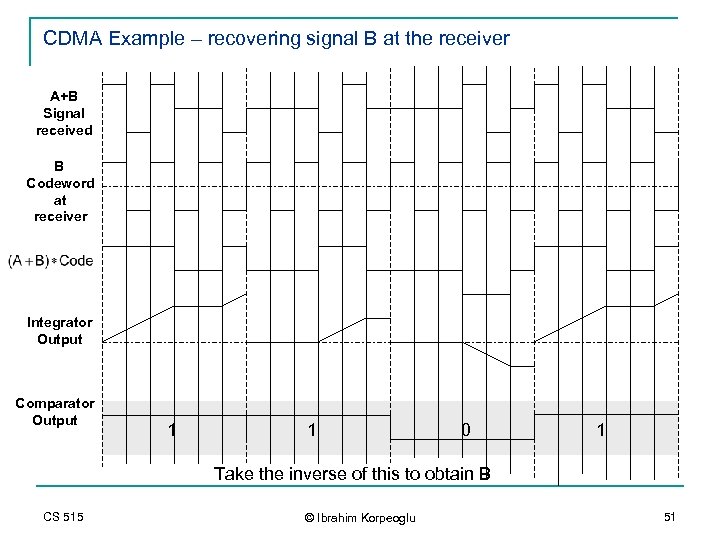 CDMA Example – recovering signal B at the receiver A+B Signal received B Codeword at receiver Integrator Output Comparator Output 1 1 0 1 Take the inverse of this to obtain B CS 515 © Ibrahim Korpeoglu 51
CDMA Example – recovering signal B at the receiver A+B Signal received B Codeword at receiver Integrator Output Comparator Output 1 1 0 1 Take the inverse of this to obtain B CS 515 © Ibrahim Korpeoglu 51
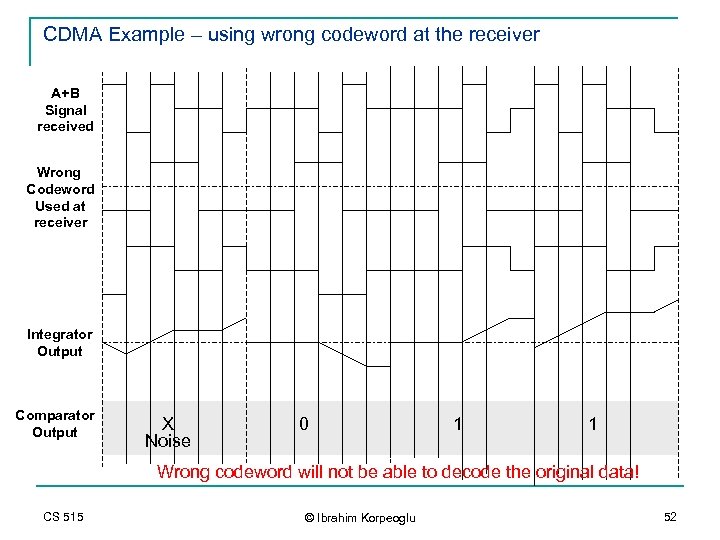 CDMA Example – using wrong codeword at the receiver A+B Signal received Wrong Codeword Used at receiver Integrator Output Comparator Output X Noise 0 1 1 Wrong codeword will not be able to decode the original data! CS 515 © Ibrahim Korpeoglu 52
CDMA Example – using wrong codeword at the receiver A+B Signal received Wrong Codeword Used at receiver Integrator Output Comparator Output X Noise 0 1 1 Wrong codeword will not be able to decode the original data! CS 515 © Ibrahim Korpeoglu 52
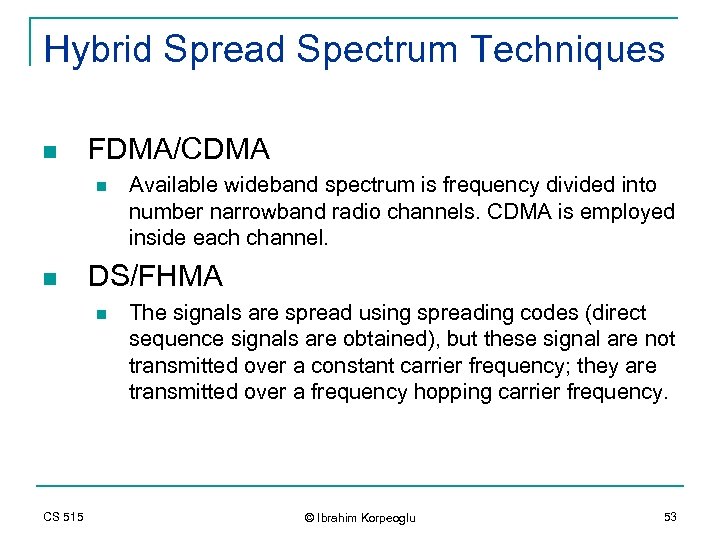 Hybrid Spread Spectrum Techniques n FDMA/CDMA n n DS/FHMA n CS 515 Available wideband spectrum is frequency divided into number narrowband radio channels. CDMA is employed inside each channel. The signals are spread using spreading codes (direct sequence signals are obtained), but these signal are not transmitted over a constant carrier frequency; they are transmitted over a frequency hopping carrier frequency. © Ibrahim Korpeoglu 53
Hybrid Spread Spectrum Techniques n FDMA/CDMA n n DS/FHMA n CS 515 Available wideband spectrum is frequency divided into number narrowband radio channels. CDMA is employed inside each channel. The signals are spread using spreading codes (direct sequence signals are obtained), but these signal are not transmitted over a constant carrier frequency; they are transmitted over a frequency hopping carrier frequency. © Ibrahim Korpeoglu 53
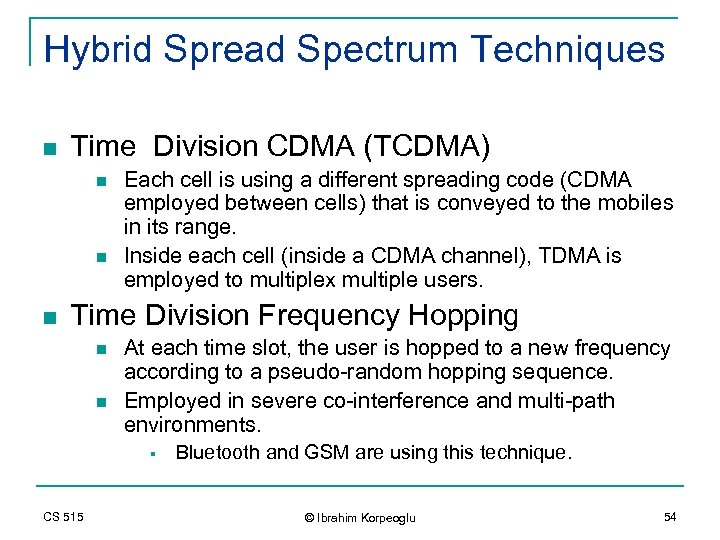 Hybrid Spread Spectrum Techniques n Time Division CDMA (TCDMA) n n n Each cell is using a different spreading code (CDMA employed between cells) that is conveyed to the mobiles in its range. Inside each cell (inside a CDMA channel), TDMA is employed to multiplex multiple users. Time Division Frequency Hopping n n At each time slot, the user is hopped to a new frequency according to a pseudo-random hopping sequence. Employed in severe co-interference and multi-path environments. § CS 515 Bluetooth and GSM are using this technique. © Ibrahim Korpeoglu 54
Hybrid Spread Spectrum Techniques n Time Division CDMA (TCDMA) n n n Each cell is using a different spreading code (CDMA employed between cells) that is conveyed to the mobiles in its range. Inside each cell (inside a CDMA channel), TDMA is employed to multiplex multiple users. Time Division Frequency Hopping n n At each time slot, the user is hopped to a new frequency according to a pseudo-random hopping sequence. Employed in severe co-interference and multi-path environments. § CS 515 Bluetooth and GSM are using this technique. © Ibrahim Korpeoglu 54
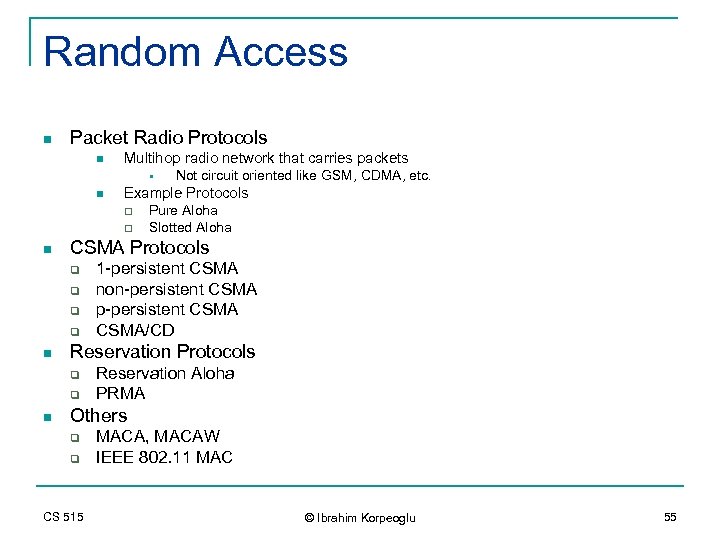 Random Access n Packet Radio Protocols n Multihop radio network that carries packets § n Example Protocols q q n q q q 1 -persistent CSMA non-persistent CSMA p-persistent CSMA/CD Reservation Protocols q q n Pure Aloha Slotted Aloha CSMA Protocols q n Not circuit oriented like GSM, CDMA, etc. Reservation Aloha PRMA Others q q CS 515 MACA, MACAW IEEE 802. 11 MAC © Ibrahim Korpeoglu 55
Random Access n Packet Radio Protocols n Multihop radio network that carries packets § n Example Protocols q q n q q q 1 -persistent CSMA non-persistent CSMA p-persistent CSMA/CD Reservation Protocols q q n Pure Aloha Slotted Aloha CSMA Protocols q n Not circuit oriented like GSM, CDMA, etc. Reservation Aloha PRMA Others q q CS 515 MACA, MACAW IEEE 802. 11 MAC © Ibrahim Korpeoglu 55
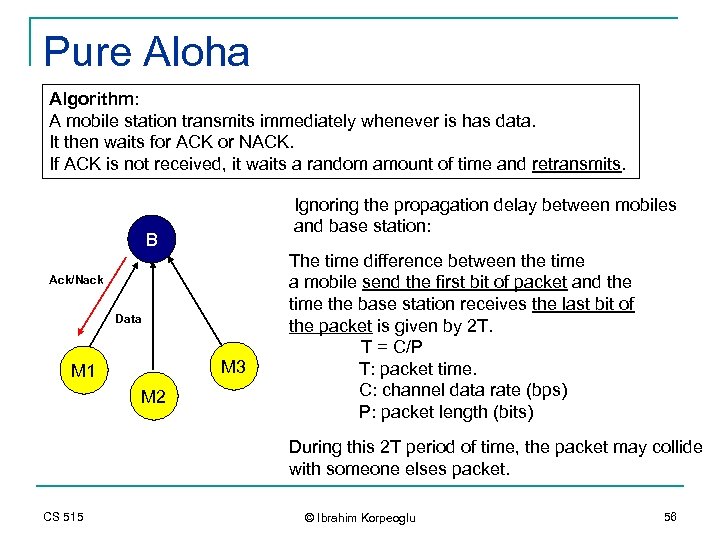 Pure Aloha Algorithm: A mobile station transmits immediately whenever is has data. It then waits for ACK or NACK. If ACK is not received, it waits a random amount of time and retransmits. Ignoring the propagation delay between mobiles and base station: B Ack/Nack Data M 3 M 1 M 2 The time difference between the time a mobile send the first bit of packet and the time the base station receives the last bit of the packet is given by 2 T. T = C/P T: packet time. C: channel data rate (bps) P: packet length (bits) During this 2 T period of time, the packet may collide with someone elses packet. CS 515 © Ibrahim Korpeoglu 56
Pure Aloha Algorithm: A mobile station transmits immediately whenever is has data. It then waits for ACK or NACK. If ACK is not received, it waits a random amount of time and retransmits. Ignoring the propagation delay between mobiles and base station: B Ack/Nack Data M 3 M 1 M 2 The time difference between the time a mobile send the first bit of packet and the time the base station receives the last bit of the packet is given by 2 T. T = C/P T: packet time. C: channel data rate (bps) P: packet length (bits) During this 2 T period of time, the packet may collide with someone elses packet. CS 515 © Ibrahim Korpeoglu 56
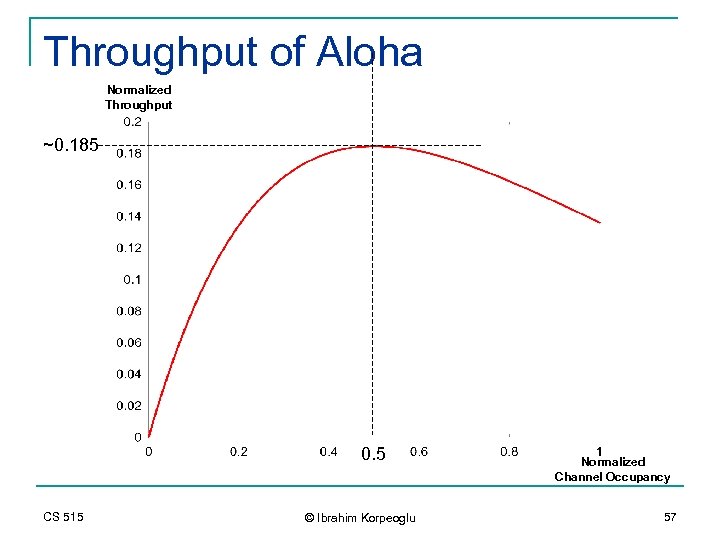 Throughput of Aloha Normalized Throughput ~0. 185 0. 5 CS 515 © Ibrahim Korpeoglu Normalized Channel Occupancy 57
Throughput of Aloha Normalized Throughput ~0. 185 0. 5 CS 515 © Ibrahim Korpeoglu Normalized Channel Occupancy 57
 CSMA: Carrier Sense Multiple Access n n n Aloha does not listen to the carrier before transmission. CSMA listen to the carrier before transmission and transmits if channel is idle. Detection delay and propagation delay are two important parameters for CSMA q q CS 515 Detection delay: time required to sense the carrier and decide if it is idle or busy Propagation delay: distance/speed_of_ligth. The time required for bit to travel from transmitter to the receiver. © Ibrahim Korpeoglu 58
CSMA: Carrier Sense Multiple Access n n n Aloha does not listen to the carrier before transmission. CSMA listen to the carrier before transmission and transmits if channel is idle. Detection delay and propagation delay are two important parameters for CSMA q q CS 515 Detection delay: time required to sense the carrier and decide if it is idle or busy Propagation delay: distance/speed_of_ligth. The time required for bit to travel from transmitter to the receiver. © Ibrahim Korpeoglu 58
 CSMA Variations n 1 -persistent CSMA: n n Non-persistent CSMA: n n When a station receives a negative acknowledgement, it waits a random amount of time before retransmission of the packet altough the carrier is idle. P-persistent CSMA n n A station waits until a channel is idle. When it detects that the channel is idle, it immediately starts transmission P-persistent CSMA is applied to slotted channels. When a station detects that a channel is idle, it starts transmission with probability p in the first available timeslot. CSMA/CD n Same with CSMA, however a station also listen to the carrier while transmitting to see if the transmission collides with someone else transmission. § § CS 515 Can be used in listen-while-talk capable channels (full duplex) In single radio channels, the transmission need to be interrupted in order to sense the channel. © Ibrahim Korpeoglu 59
CSMA Variations n 1 -persistent CSMA: n n Non-persistent CSMA: n n When a station receives a negative acknowledgement, it waits a random amount of time before retransmission of the packet altough the carrier is idle. P-persistent CSMA n n A station waits until a channel is idle. When it detects that the channel is idle, it immediately starts transmission P-persistent CSMA is applied to slotted channels. When a station detects that a channel is idle, it starts transmission with probability p in the first available timeslot. CSMA/CD n Same with CSMA, however a station also listen to the carrier while transmitting to see if the transmission collides with someone else transmission. § § CS 515 Can be used in listen-while-talk capable channels (full duplex) In single radio channels, the transmission need to be interrupted in order to sense the channel. © Ibrahim Korpeoglu 59
 MACA – Medium Access with Collision Avoidance n CSMA protocols sense the carrier, but sensing the carrier does not always releases true information about the status of the wireless channel n There are two problems that are unique to wireless channels (different than wireline channels), that makes CSMA useless in some cases. These problems are: § § CS 515 Hidden terminal problem Exposed terminal problem. © Ibrahim Korpeoglu 60
MACA – Medium Access with Collision Avoidance n CSMA protocols sense the carrier, but sensing the carrier does not always releases true information about the status of the wireless channel n There are two problems that are unique to wireless channels (different than wireline channels), that makes CSMA useless in some cases. These problems are: § § CS 515 Hidden terminal problem Exposed terminal problem. © Ibrahim Korpeoglu 60
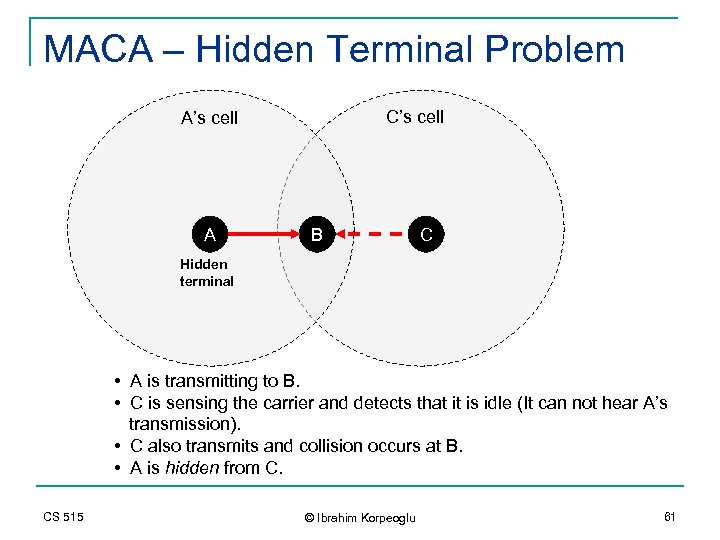 MACA – Hidden Terminal Problem C’s cell A B C Hidden terminal • A is transmitting to B. • C is sensing the carrier and detects that it is idle (It can not hear A’s transmission). • C also transmits and collision occurs at B. • A is hidden from C. CS 515 © Ibrahim Korpeoglu 61
MACA – Hidden Terminal Problem C’s cell A B C Hidden terminal • A is transmitting to B. • C is sensing the carrier and detects that it is idle (It can not hear A’s transmission). • C also transmits and collision occurs at B. • A is hidden from C. CS 515 © Ibrahim Korpeoglu 61
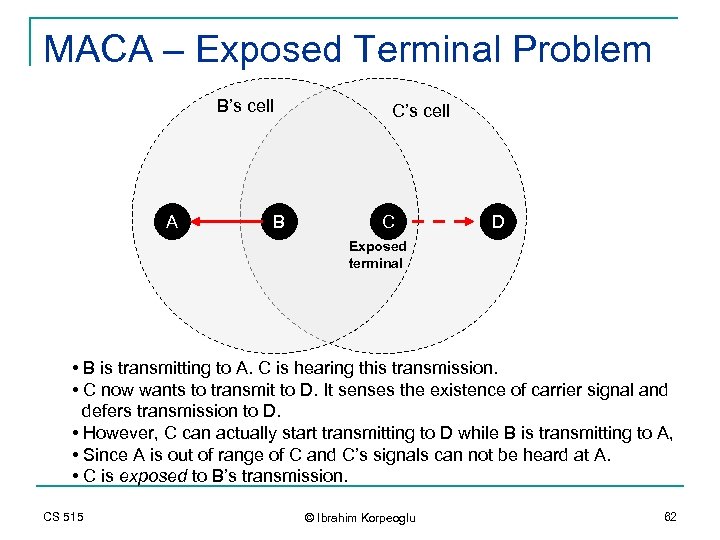 MACA – Exposed Terminal Problem B’s cell A B C’s cell C D Exposed terminal • B is transmitting to A. C is hearing this transmission. • C now wants to transmit to D. It senses the existence of carrier signal and defers transmission to D. • However, C can actually start transmitting to D while B is transmitting to A, • Since A is out of range of C and C’s signals can not be heard at A. • C is exposed to B’s transmission. CS 515 © Ibrahim Korpeoglu 62
MACA – Exposed Terminal Problem B’s cell A B C’s cell C D Exposed terminal • B is transmitting to A. C is hearing this transmission. • C now wants to transmit to D. It senses the existence of carrier signal and defers transmission to D. • However, C can actually start transmitting to D while B is transmitting to A, • Since A is out of range of C and C’s signals can not be heard at A. • C is exposed to B’s transmission. CS 515 © Ibrahim Korpeoglu 62
 MACA Solution Concept Ali, lets talk! I am available. Can, I want to talk to you! Biltepe Mountain Ali CS 515 Veli © Ibrahim Korpeoglu 63
MACA Solution Concept Ali, lets talk! I am available. Can, I want to talk to you! Biltepe Mountain Ali CS 515 Veli © Ibrahim Korpeoglu 63
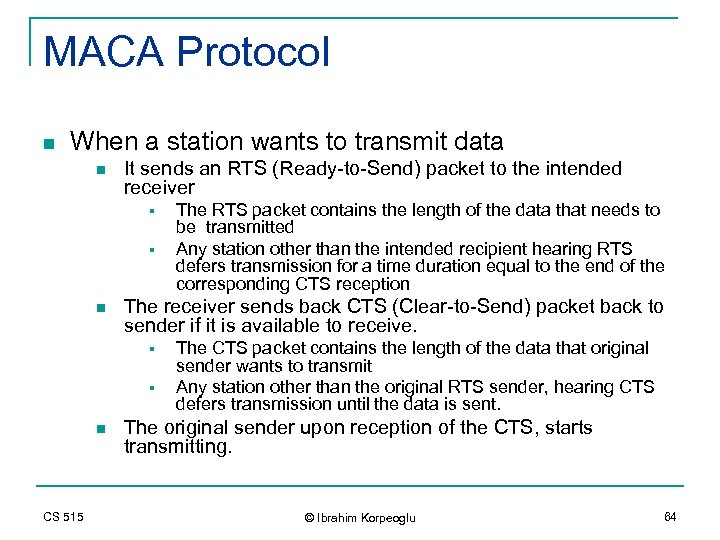 MACA Protocol n When a station wants to transmit data n It sends an RTS (Ready-to-Send) packet to the intended receiver § § n The receiver sends back CTS (Clear-to-Send) packet back to sender if it is available to receive. § § n CS 515 The RTS packet contains the length of the data that needs to be transmitted Any station other than the intended recipient hearing RTS defers transmission for a time duration equal to the end of the corresponding CTS reception The CTS packet contains the length of the data that original sender wants to transmit Any station other than the original RTS sender, hearing CTS defers transmission until the data is sent. The original sender upon reception of the CTS, starts transmitting. © Ibrahim Korpeoglu 64
MACA Protocol n When a station wants to transmit data n It sends an RTS (Ready-to-Send) packet to the intended receiver § § n The receiver sends back CTS (Clear-to-Send) packet back to sender if it is available to receive. § § n CS 515 The RTS packet contains the length of the data that needs to be transmitted Any station other than the intended recipient hearing RTS defers transmission for a time duration equal to the end of the corresponding CTS reception The CTS packet contains the length of the data that original sender wants to transmit Any station other than the original RTS sender, hearing CTS defers transmission until the data is sent. The original sender upon reception of the CTS, starts transmitting. © Ibrahim Korpeoglu 64
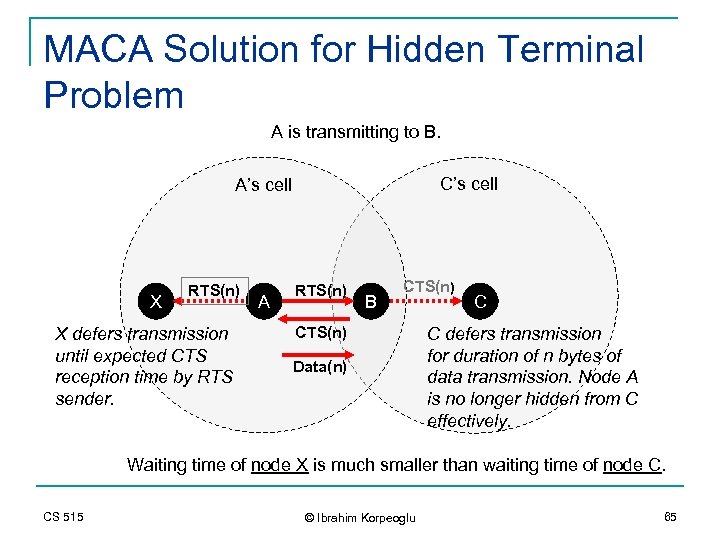 MACA Solution for Hidden Terminal Problem A is transmitting to B. C’s cell A’s cell X RTS(n) X defers transmission until expected CTS reception time by RTS sender. A RTS(n) B CTS(n) Data(n) C C defers transmission for duration of n bytes of data transmission. Node A is no longer hidden from C effectively. Waiting time of node X is much smaller than waiting time of node C. CS 515 © Ibrahim Korpeoglu 65
MACA Solution for Hidden Terminal Problem A is transmitting to B. C’s cell A’s cell X RTS(n) X defers transmission until expected CTS reception time by RTS sender. A RTS(n) B CTS(n) Data(n) C C defers transmission for duration of n bytes of data transmission. Node A is no longer hidden from C effectively. Waiting time of node X is much smaller than waiting time of node C. CS 515 © Ibrahim Korpeoglu 65
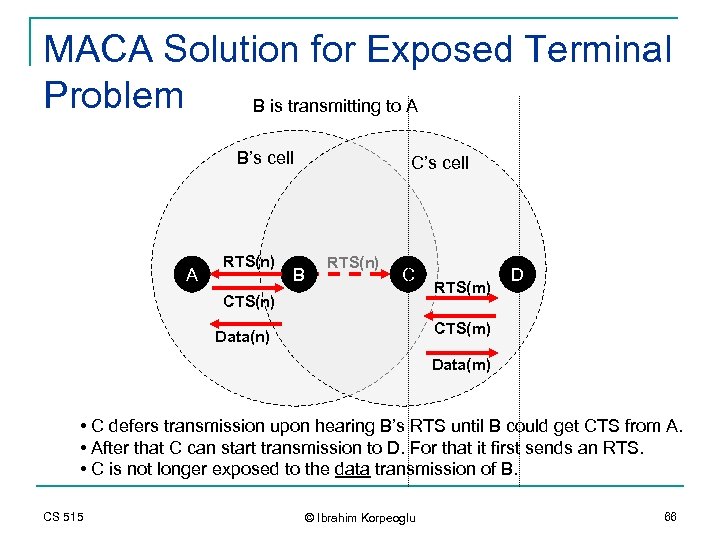 MACA Solution for Exposed Terminal Problem B is transmitting to A B’s cell A RTS(n) B C’s cell RTS(n) C CTS(n) RTS(m) D CTS(m) Data(n) Data(m) • C defers transmission upon hearing B’s RTS until B could get CTS from A. • After that C can start transmission to D. For that it first sends an RTS. • C is not longer exposed to the data transmission of B. CS 515 © Ibrahim Korpeoglu 66
MACA Solution for Exposed Terminal Problem B is transmitting to A B’s cell A RTS(n) B C’s cell RTS(n) C CTS(n) RTS(m) D CTS(m) Data(n) Data(m) • C defers transmission upon hearing B’s RTS until B could get CTS from A. • After that C can start transmission to D. For that it first sends an RTS. • C is not longer exposed to the data transmission of B. CS 515 © Ibrahim Korpeoglu 66
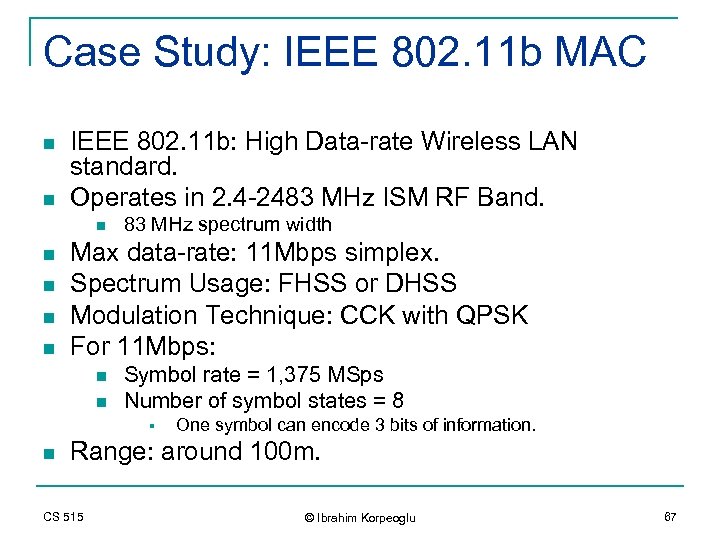 Case Study: IEEE 802. 11 b MAC n n IEEE 802. 11 b: High Data-rate Wireless LAN standard. Operates in 2. 4 -2483 MHz ISM RF Band. n n n 83 MHz spectrum width Max data-rate: 11 Mbps simplex. Spectrum Usage: FHSS or DHSS Modulation Technique: CCK with QPSK For 11 Mbps: n n Symbol rate = 1, 375 MSps Number of symbol states = 8 § n One symbol can encode 3 bits of information. Range: around 100 m. CS 515 © Ibrahim Korpeoglu 67
Case Study: IEEE 802. 11 b MAC n n IEEE 802. 11 b: High Data-rate Wireless LAN standard. Operates in 2. 4 -2483 MHz ISM RF Band. n n n 83 MHz spectrum width Max data-rate: 11 Mbps simplex. Spectrum Usage: FHSS or DHSS Modulation Technique: CCK with QPSK For 11 Mbps: n n Symbol rate = 1, 375 MSps Number of symbol states = 8 § n One symbol can encode 3 bits of information. Range: around 100 m. CS 515 © Ibrahim Korpeoglu 67
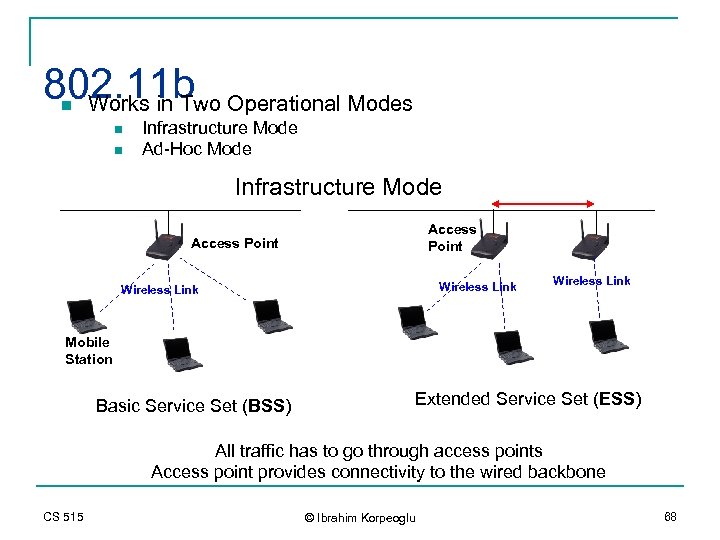 802. 11 b Operational Modes Works in Two n n n Infrastructure Mode Ad-Hoc Mode Infrastructure Mode Access Point Wireless Link Mobile Station Basic Service Set (BSS) Extended Service Set (ESS) All traffic has to go through access points Access point provides connectivity to the wired backbone CS 515 © Ibrahim Korpeoglu 68
802. 11 b Operational Modes Works in Two n n n Infrastructure Mode Ad-Hoc Mode Infrastructure Mode Access Point Wireless Link Mobile Station Basic Service Set (BSS) Extended Service Set (ESS) All traffic has to go through access points Access point provides connectivity to the wired backbone CS 515 © Ibrahim Korpeoglu 68
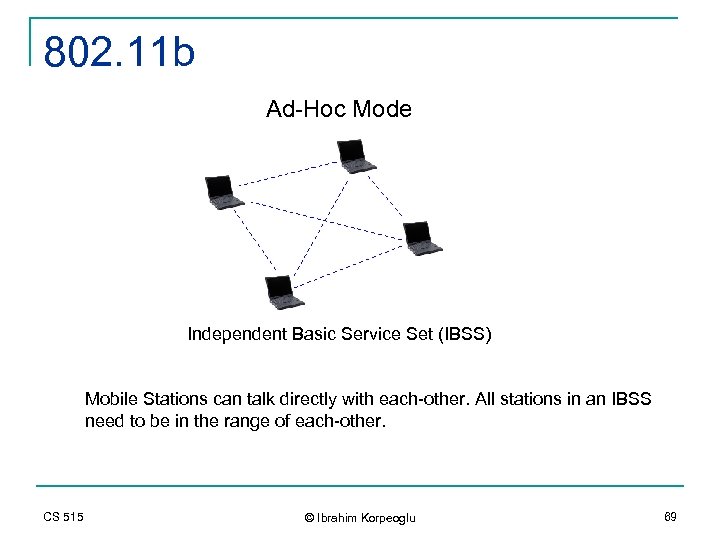 802. 11 b Ad-Hoc Mode Independent Basic Service Set (IBSS) Mobile Stations can talk directly with each-other. All stations in an IBSS need to be in the range of each-other. CS 515 © Ibrahim Korpeoglu 69
802. 11 b Ad-Hoc Mode Independent Basic Service Set (IBSS) Mobile Stations can talk directly with each-other. All stations in an IBSS need to be in the range of each-other. CS 515 © Ibrahim Korpeoglu 69
 802. 11 b MAC Sublayer n Support two different MAC modes depending on the operational mode of the Wireless LAN n 1) DCF: Distributed Coordination Function § § n 2) PCF: Point Coordination Function § § § CS 515 Based on CSMA/CA Carrier Sensing: Physical and Virtual. Connection oriented Contention free service Polling based © Ibrahim Korpeoglu 70
802. 11 b MAC Sublayer n Support two different MAC modes depending on the operational mode of the Wireless LAN n 1) DCF: Distributed Coordination Function § § n 2) PCF: Point Coordination Function § § § CS 515 Based on CSMA/CA Carrier Sensing: Physical and Virtual. Connection oriented Contention free service Polling based © Ibrahim Korpeoglu 70
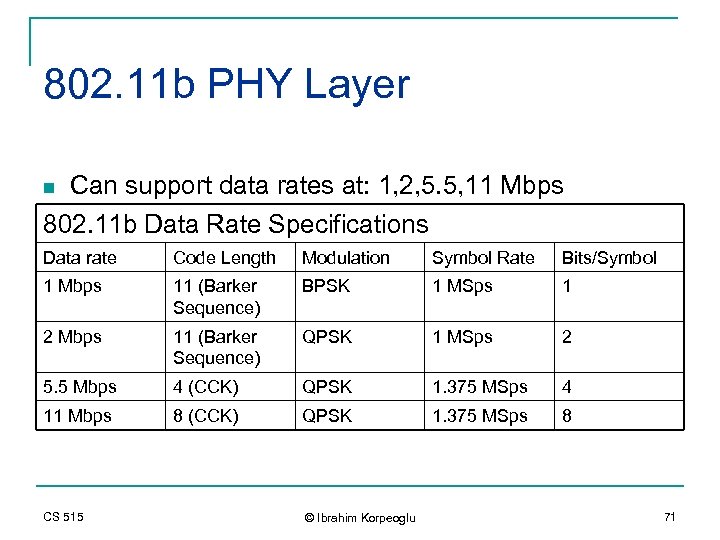 802. 11 b PHY Layer Can support data rates at: 1, 2, 5. 5, 11 Mbps 802. 11 b Data Rate Specifications n Data rate Code Length Modulation Symbol Rate Bits/Symbol 1 Mbps 11 (Barker Sequence) BPSK 1 MSps 1 2 Mbps 11 (Barker Sequence) QPSK 1 MSps 2 5. 5 Mbps 4 (CCK) QPSK 1. 375 MSps 4 11 Mbps 8 (CCK) QPSK 1. 375 MSps 8 CS 515 © Ibrahim Korpeoglu 71
802. 11 b PHY Layer Can support data rates at: 1, 2, 5. 5, 11 Mbps 802. 11 b Data Rate Specifications n Data rate Code Length Modulation Symbol Rate Bits/Symbol 1 Mbps 11 (Barker Sequence) BPSK 1 MSps 1 2 Mbps 11 (Barker Sequence) QPSK 1 MSps 2 5. 5 Mbps 4 (CCK) QPSK 1. 375 MSps 4 11 Mbps 8 (CCK) QPSK 1. 375 MSps 8 CS 515 © Ibrahim Korpeoglu 71
 FHSS n n 2. 4 GHz band is divided into 75 one-MHz subchannels. The sender and receiver hops through this 75 channels in a synchronized manner using a hopping pattern. Can not support more than 2 Mbps data-rate. CS 515 © Ibrahim Korpeoglu 72
FHSS n n 2. 4 GHz band is divided into 75 one-MHz subchannels. The sender and receiver hops through this 75 channels in a synchronized manner using a hopping pattern. Can not support more than 2 Mbps data-rate. CS 515 © Ibrahim Korpeoglu 72
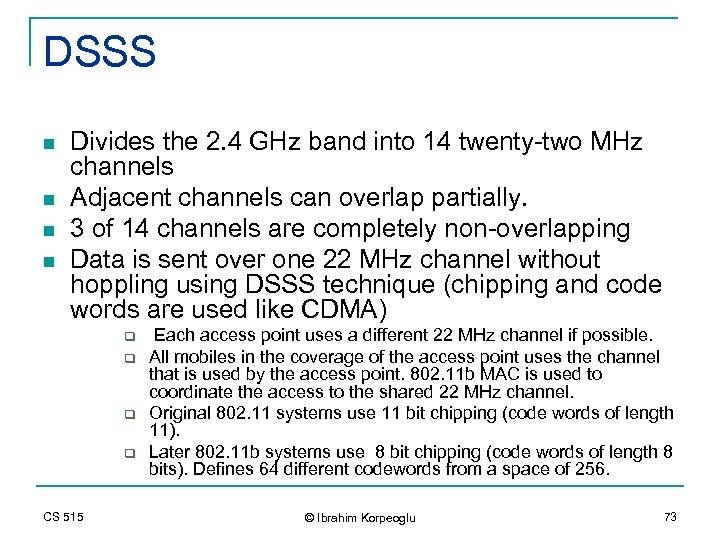 DSSS n n Divides the 2. 4 GHz band into 14 twenty-two MHz channels Adjacent channels can overlap partially. 3 of 14 channels are completely non-overlapping Data is sent over one 22 MHz channel without hoppling using DSSS technique (chipping and code words are used like CDMA) q q CS 515 Each access point uses a different 22 MHz channel if possible. All mobiles in the coverage of the access point uses the channel that is used by the access point. 802. 11 b MAC is used to coordinate the access to the shared 22 MHz channel. Original 802. 11 systems use 11 bit chipping (code words of length 11). Later 802. 11 b systems use 8 bit chipping (code words of length 8 bits). Defines 64 different codewords from a space of 256. © Ibrahim Korpeoglu 73
DSSS n n Divides the 2. 4 GHz band into 14 twenty-two MHz channels Adjacent channels can overlap partially. 3 of 14 channels are completely non-overlapping Data is sent over one 22 MHz channel without hoppling using DSSS technique (chipping and code words are used like CDMA) q q CS 515 Each access point uses a different 22 MHz channel if possible. All mobiles in the coverage of the access point uses the channel that is used by the access point. 802. 11 b MAC is used to coordinate the access to the shared 22 MHz channel. Original 802. 11 systems use 11 bit chipping (code words of length 11). Later 802. 11 b systems use 8 bit chipping (code words of length 8 bits). Defines 64 different codewords from a space of 256. © Ibrahim Korpeoglu 73
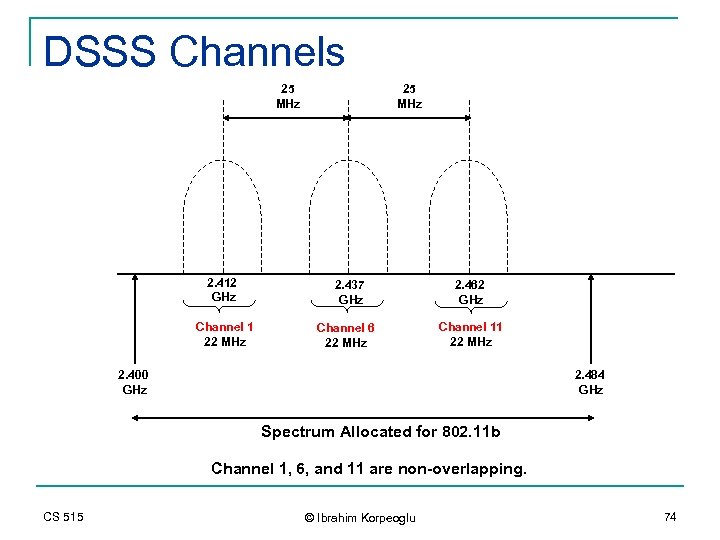 DSSS Channels 25 MHz 2. 412 GHz Channel 1 22 MHz 25 MHz 2. 437 GHz Channel 6 22 MHz 2. 462 GHz Channel 11 22 MHz 2. 400 GHz 2. 484 GHz Spectrum Allocated for 802. 11 b Channel 1, 6, and 11 are non-overlapping. CS 515 © Ibrahim Korpeoglu 74
DSSS Channels 25 MHz 2. 412 GHz Channel 1 22 MHz 25 MHz 2. 437 GHz Channel 6 22 MHz 2. 462 GHz Channel 11 22 MHz 2. 400 GHz 2. 484 GHz Spectrum Allocated for 802. 11 b Channel 1, 6, and 11 are non-overlapping. CS 515 © Ibrahim Korpeoglu 74
 Channel Assignment and Registration. q q q In multi-access environment, the operator should try to allocate non-overlapping channels to the physically adjacent channels. If adjacent access points use overlapping channels, then interference can be high. A mobile station periodically tunes to all channels and evaluates the signal strength received over each channel q q CS 515 Depending on the signal strength received over the channels, a mobile selects an access point and registers with that provided that the access points accepts the mobile. This is also called association. Re-association with a new access point occurs when § the mobile moves away from the current access point. § When the signal conditions changes between the mobile and current access point. § When there a lot of users associated with the current access point. © Ibrahim Korpeoglu 75
Channel Assignment and Registration. q q q In multi-access environment, the operator should try to allocate non-overlapping channels to the physically adjacent channels. If adjacent access points use overlapping channels, then interference can be high. A mobile station periodically tunes to all channels and evaluates the signal strength received over each channel q q CS 515 Depending on the signal strength received over the channels, a mobile selects an access point and registers with that provided that the access points accepts the mobile. This is also called association. Re-association with a new access point occurs when § the mobile moves away from the current access point. § When the signal conditions changes between the mobile and current access point. § When there a lot of users associated with the current access point. © Ibrahim Korpeoglu 75
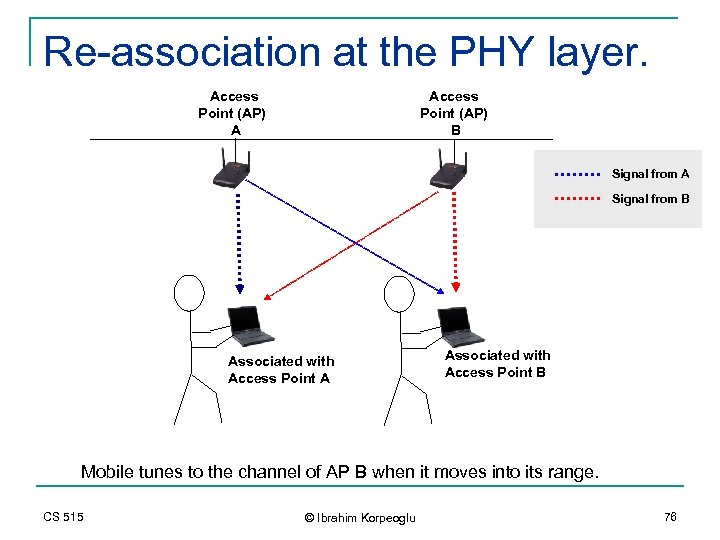 Re-association at the PHY layer. Access Point (AP) A Access Point (AP) B Signal from A Signal from B Associated with Access Point A Associated with Access Point B Mobile tunes to the channel of AP B when it moves into its range. CS 515 © Ibrahim Korpeoglu 76
Re-association at the PHY layer. Access Point (AP) A Access Point (AP) B Signal from A Signal from B Associated with Access Point A Associated with Access Point B Mobile tunes to the channel of AP B when it moves into its range. CS 515 © Ibrahim Korpeoglu 76
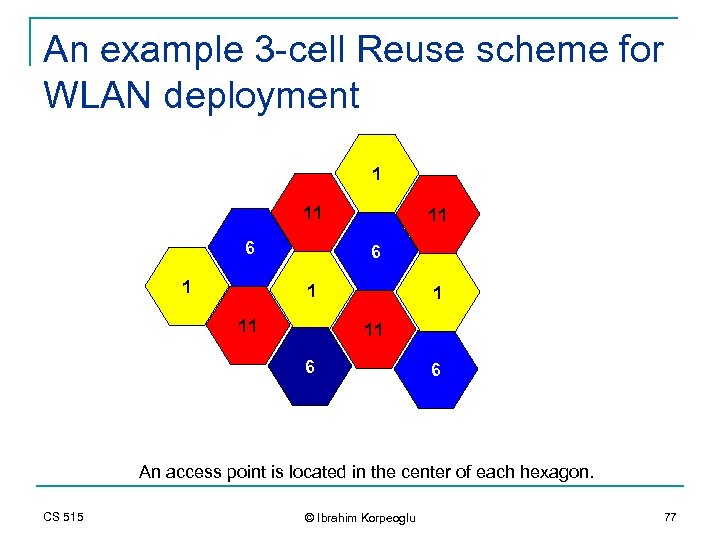 An example 3 -cell Reuse scheme for WLAN deployment 1 11 6 6 An access point is located in the center of each hexagon. CS 515 © Ibrahim Korpeoglu 77
An example 3 -cell Reuse scheme for WLAN deployment 1 11 6 6 An access point is located in the center of each hexagon. CS 515 © Ibrahim Korpeoglu 77
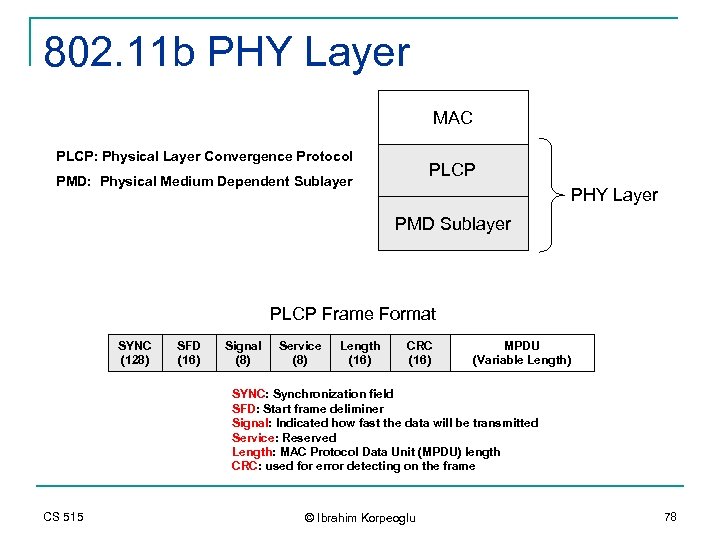 802. 11 b PHY Layer MAC PLCP: Physical Layer Convergence Protocol PLCP PMD: Physical Medium Dependent Sublayer PHY Layer PMD Sublayer PLCP Frame Format SYNC (128) SFD (16) Signal (8) Service (8) Length (16) CRC (16) MPDU (Variable Length) SYNC: Synchronization field SFD: Start frame deliminer Signal: Indicated how fast the data will be transmitted Service: Reserved Length: MAC Protocol Data Unit (MPDU) length CRC: used for error detecting on the frame CS 515 © Ibrahim Korpeoglu 78
802. 11 b PHY Layer MAC PLCP: Physical Layer Convergence Protocol PLCP PMD: Physical Medium Dependent Sublayer PHY Layer PMD Sublayer PLCP Frame Format SYNC (128) SFD (16) Signal (8) Service (8) Length (16) CRC (16) MPDU (Variable Length) SYNC: Synchronization field SFD: Start frame deliminer Signal: Indicated how fast the data will be transmitted Service: Reserved Length: MAC Protocol Data Unit (MPDU) length CRC: used for error detecting on the frame CS 515 © Ibrahim Korpeoglu 78
 802. 11 b MAC Sublayer n n n Supports both infrastructure and ad-hoc modes of operation. CRC is added to each MAC frame Packet fragmentation is supported to chop large higher layer (IP) packets into small pieces. Has advantages: n n CS 515 Probability a packet gets corrupted increases with the packet size. In case of corruption, only a small fragment needs to be re-transmitted. © Ibrahim Korpeoglu 79
802. 11 b MAC Sublayer n n n Supports both infrastructure and ad-hoc modes of operation. CRC is added to each MAC frame Packet fragmentation is supported to chop large higher layer (IP) packets into small pieces. Has advantages: n n CS 515 Probability a packet gets corrupted increases with the packet size. In case of corruption, only a small fragment needs to be re-transmitted. © Ibrahim Korpeoglu 79
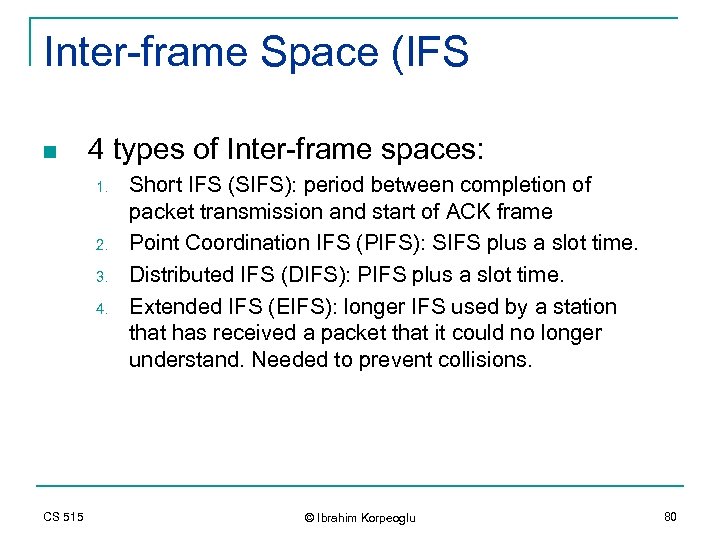 Inter-frame Space (IFS n 4 types of Inter-frame spaces: 1. 2. 3. 4. CS 515 Short IFS (SIFS): period between completion of packet transmission and start of ACK frame Point Coordination IFS (PIFS): SIFS plus a slot time. Distributed IFS (DIFS): PIFS plus a slot time. Extended IFS (EIFS): longer IFS used by a station that has received a packet that it could no longer understand. Needed to prevent collisions. © Ibrahim Korpeoglu 80
Inter-frame Space (IFS n 4 types of Inter-frame spaces: 1. 2. 3. 4. CS 515 Short IFS (SIFS): period between completion of packet transmission and start of ACK frame Point Coordination IFS (PIFS): SIFS plus a slot time. Distributed IFS (DIFS): PIFS plus a slot time. Extended IFS (EIFS): longer IFS used by a station that has received a packet that it could no longer understand. Needed to prevent collisions. © Ibrahim Korpeoglu 80
 MAC Protocol n n 802. 11 b uses CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) MAC protocol. CSMA/CA is the protocol to implement the distributed coordination function (DCF) of the MAC sub-layer. n n CS 515 RTS/CTS is used to avoid collisions. Use of RTS/CTS can be enabled or disabled depending on the traffic load (probability of collisions). © Ibrahim Korpeoglu 81
MAC Protocol n n 802. 11 b uses CSMA/CA (Carrier Sense Multiple Access/Collision Avoidance) MAC protocol. CSMA/CA is the protocol to implement the distributed coordination function (DCF) of the MAC sub-layer. n n CS 515 RTS/CTS is used to avoid collisions. Use of RTS/CTS can be enabled or disabled depending on the traffic load (probability of collisions). © Ibrahim Korpeoglu 81
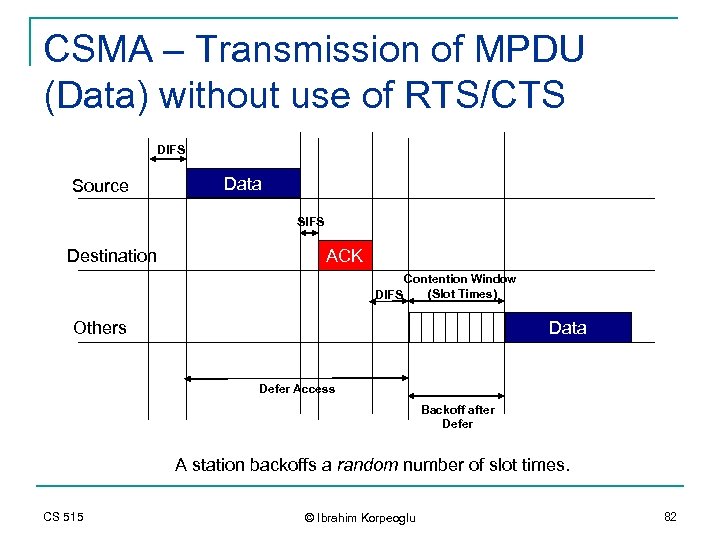 CSMA – Transmission of MPDU (Data) without use of RTS/CTS DIFS Source Data SIFS Destination ACK Contention Window (Slot Times) DIFS Data Others Defer Access Backoff after Defer A station backoffs a random number of slot times. CS 515 © Ibrahim Korpeoglu 82
CSMA – Transmission of MPDU (Data) without use of RTS/CTS DIFS Source Data SIFS Destination ACK Contention Window (Slot Times) DIFS Data Others Defer Access Backoff after Defer A station backoffs a random number of slot times. CS 515 © Ibrahim Korpeoglu 82
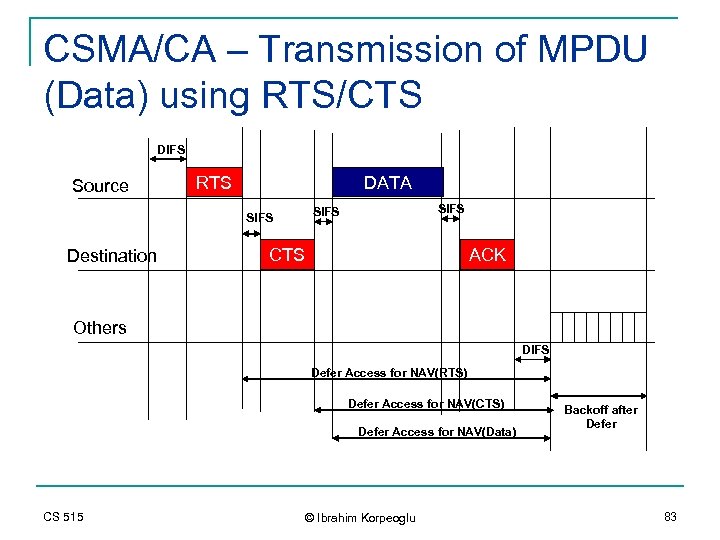 CSMA/CA – Transmission of MPDU (Data) using RTS/CTS DIFS Source RTS DATA Destination SIFS CTS ACK Others DIFS Defer Access for NAV(RTS) Defer Access for NAV(CTS) Defer Access for NAV(Data) CS 515 © Ibrahim Korpeoglu Backoff after Defer 83
CSMA/CA – Transmission of MPDU (Data) using RTS/CTS DIFS Source RTS DATA Destination SIFS CTS ACK Others DIFS Defer Access for NAV(RTS) Defer Access for NAV(CTS) Defer Access for NAV(Data) CS 515 © Ibrahim Korpeoglu Backoff after Defer 83
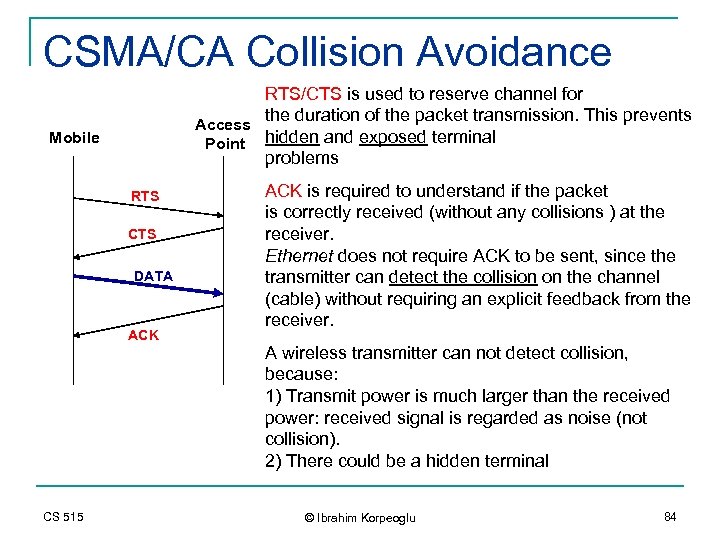 CSMA/CA Collision Avoidance RTS/CTS is used to reserve channel for the duration of the packet transmission. This prevents Access Point hidden and exposed terminal problems Mobile RTS CTS DATA ACK CS 515 ACK is required to understand if the packet is correctly received (without any collisions ) at the receiver. Ethernet does not require ACK to be sent, since the transmitter can detect the collision on the channel (cable) without requiring an explicit feedback from the receiver. A wireless transmitter can not detect collision, because: 1) Transmit power is much larger than the received power: received signal is regarded as noise (not collision). 2) There could be a hidden terminal © Ibrahim Korpeoglu 84
CSMA/CA Collision Avoidance RTS/CTS is used to reserve channel for the duration of the packet transmission. This prevents Access Point hidden and exposed terminal problems Mobile RTS CTS DATA ACK CS 515 ACK is required to understand if the packet is correctly received (without any collisions ) at the receiver. Ethernet does not require ACK to be sent, since the transmitter can detect the collision on the channel (cable) without requiring an explicit feedback from the receiver. A wireless transmitter can not detect collision, because: 1) Transmit power is much larger than the received power: received signal is regarded as noise (not collision). 2) There could be a hidden terminal © Ibrahim Korpeoglu 84
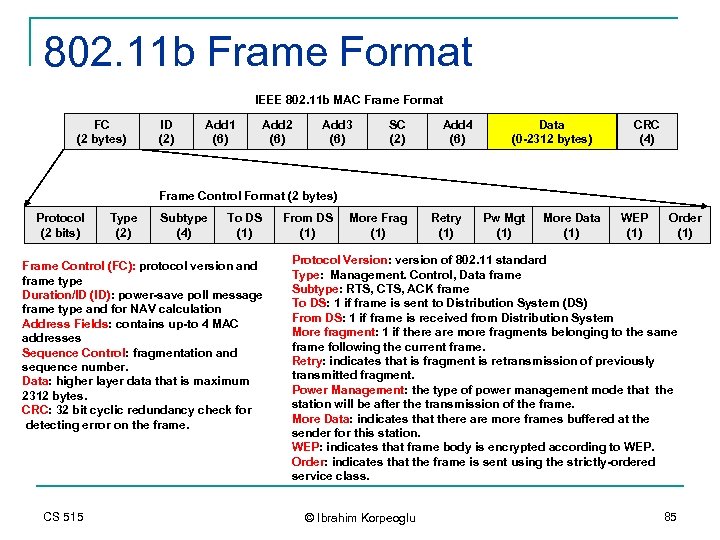 802. 11 b Frame Format IEEE 802. 11 b MAC Frame Format FC (2 bytes) ID (2) Add 1 (6) Add 2 (6) Add 3 (6) SC (2) Add 4 (6) Data (0 -2312 bytes) CRC (4) Frame Control Format (2 bytes) Protocol (2 bits) Type (2) Subtype (4) To DS (1) Frame Control (FC): protocol version and frame type Duration/ID (ID): power-save poll message frame type and for NAV calculation Address Fields: contains up-to 4 MAC addresses Sequence Control: fragmentation and sequence number. Data: higher layer data that is maximum 2312 bytes. CRC: 32 bit cyclic redundancy check for detecting error on the frame. CS 515 From DS (1) More Frag (1) Retry (1) Pw Mgt (1) More Data (1) WEP (1) Order (1) Protocol Version: version of 802. 11 standard Type: Management. Control, Data frame Subtype: RTS, CTS, ACK frame To DS: 1 if frame is sent to Distribution System (DS) From DS: 1 if frame is received from Distribution System More fragment: 1 if there are more fragments belonging to the same frame following the current frame. Retry: indicates that is fragment is retransmission of previously transmitted fragment. Power Management: the type of power management mode that the station will be after the transmission of the frame. More Data: indicates that there are more frames buffered at the sender for this station. WEP: indicates that frame body is encrypted according to WEP. Order: indicates that the frame is sent using the strictly-ordered service class. © Ibrahim Korpeoglu 85
802. 11 b Frame Format IEEE 802. 11 b MAC Frame Format FC (2 bytes) ID (2) Add 1 (6) Add 2 (6) Add 3 (6) SC (2) Add 4 (6) Data (0 -2312 bytes) CRC (4) Frame Control Format (2 bytes) Protocol (2 bits) Type (2) Subtype (4) To DS (1) Frame Control (FC): protocol version and frame type Duration/ID (ID): power-save poll message frame type and for NAV calculation Address Fields: contains up-to 4 MAC addresses Sequence Control: fragmentation and sequence number. Data: higher layer data that is maximum 2312 bytes. CRC: 32 bit cyclic redundancy check for detecting error on the frame. CS 515 From DS (1) More Frag (1) Retry (1) Pw Mgt (1) More Data (1) WEP (1) Order (1) Protocol Version: version of 802. 11 standard Type: Management. Control, Data frame Subtype: RTS, CTS, ACK frame To DS: 1 if frame is sent to Distribution System (DS) From DS: 1 if frame is received from Distribution System More fragment: 1 if there are more fragments belonging to the same frame following the current frame. Retry: indicates that is fragment is retransmission of previously transmitted fragment. Power Management: the type of power management mode that the station will be after the transmission of the frame. More Data: indicates that there are more frames buffered at the sender for this station. WEP: indicates that frame body is encrypted according to WEP. Order: indicates that the frame is sent using the strictly-ordered service class. © Ibrahim Korpeoglu 85
 Mobility n What happens when a station moves between access points n n n Re-association function of the PHY layer associates a mobile with a new access point. Some vendor specific, layer-2 (datalink layer) solutions solves the mobility at layer. Solutions like Mobile IP needed to provide seamless mobility to higher layers (transport and application layers). q n DHCP is also a method but not as convenient as Mobile IP. We will see in the forthcoming classes how Mobile IP works. CS 515 © Ibrahim Korpeoglu 86
Mobility n What happens when a station moves between access points n n n Re-association function of the PHY layer associates a mobile with a new access point. Some vendor specific, layer-2 (datalink layer) solutions solves the mobility at layer. Solutions like Mobile IP needed to provide seamless mobility to higher layers (transport and application layers). q n DHCP is also a method but not as convenient as Mobile IP. We will see in the forthcoming classes how Mobile IP works. CS 515 © Ibrahim Korpeoglu 86


