a7e4aa8c9e64bc5205a6c2d927dd7d2b.ppt
- Количество слайдов: 29
 Medium Access Control for Ad Hoc Wireless Networks: A Survey S. Kumar, V. Raghavan, J. Deng Ad Hoc Networks 4 (2006) 326 -358
Medium Access Control for Ad Hoc Wireless Networks: A Survey S. Kumar, V. Raghavan, J. Deng Ad Hoc Networks 4 (2006) 326 -358
 Medium Access Control • Coordinate access from active nodes – Deal with channel contention • Challenges – Wireless communication channel is prone to errors and problems, e. g. , hidden/exposed node problems & signal attenuation • This paper provides a comprehensive survey
Medium Access Control • Coordinate access from active nodes – Deal with channel contention • Challenges – Wireless communication channel is prone to errors and problems, e. g. , hidden/exposed node problems & signal attenuation • This paper provides a comprehensive survey
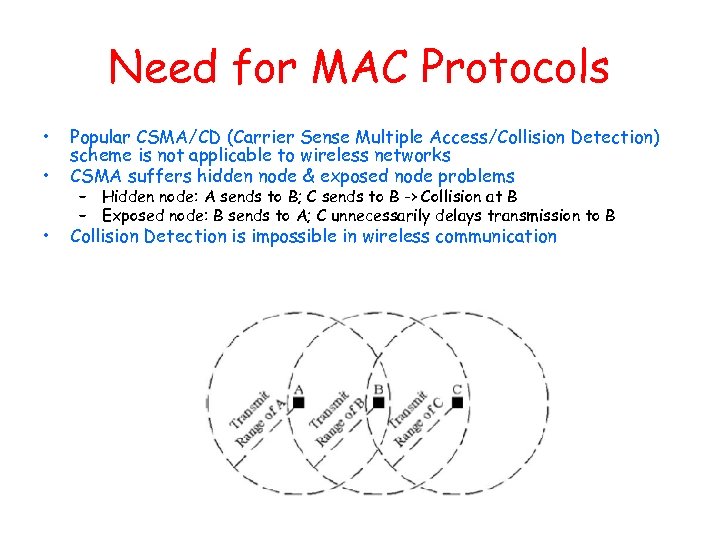 Need for MAC Protocols • • Popular CSMA/CD (Carrier Sense Multiple Access/Collision Detection) scheme is not applicable to wireless networks CSMA suffers hidden node & exposed node problems • Collision Detection is impossible in wireless communication – Hidden node: A sends to B; C sends to B -> Collision at B – Exposed node: B sends to A; C unnecessarily delays transmission to B
Need for MAC Protocols • • Popular CSMA/CD (Carrier Sense Multiple Access/Collision Detection) scheme is not applicable to wireless networks CSMA suffers hidden node & exposed node problems • Collision Detection is impossible in wireless communication – Hidden node: A sends to B; C sends to B -> Collision at B – Exposed node: B sends to A; C unnecessarily delays transmission to B
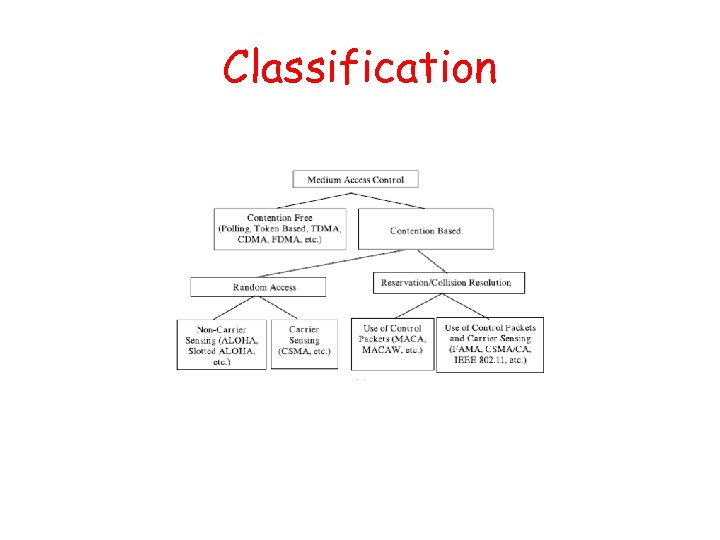
 Classification • Contention-free MAC – TDMA, FDMA, CDMA: Divides channel by time, frequency, or code – More applicable to static networks and/or networks with centralized control • Contention-based MAC – Focus of this survey
Classification • Contention-free MAC – TDMA, FDMA, CDMA: Divides channel by time, frequency, or code – More applicable to static networks and/or networks with centralized control • Contention-based MAC – Focus of this survey
 Classification
Classification
 (Partial) Solutions of Hidden/Exposed Node Problems in CSMA • Use control packets – RTS/CTS (Request-To-Send/Clear-To. Send) – Used by MACA (Multiple Access Control Avoidance) and MACAW (MACA for Wireless LANs) • Use both control packets and carrier sense – CSMA/CA, IEEE 802. 11
(Partial) Solutions of Hidden/Exposed Node Problems in CSMA • Use control packets – RTS/CTS (Request-To-Send/Clear-To. Send) – Used by MACA (Multiple Access Control Avoidance) and MACAW (MACA for Wireless LANs) • Use both control packets and carrier sense – CSMA/CA, IEEE 802. 11
 Dynamic Reservation Approaches: Sender- vs. Receiver-initiated • Sender-initiated – A node wanting to send data takes the initiative of setting up the reservation – Most existing schemes • Receiver-initiated – A receiving node polls a potential transmitting node for data – A node can send data after being polled – MACA-By Invitation • A bit more efficient than MACA in terms of transmit & receive turnaround time
Dynamic Reservation Approaches: Sender- vs. Receiver-initiated • Sender-initiated – A node wanting to send data takes the initiative of setting up the reservation – Most existing schemes • Receiver-initiated – A receiving node polls a potential transmitting node for data – A node can send data after being polled – MACA-By Invitation • A bit more efficient than MACA in terms of transmit & receive turnaround time
 Single vs. Multiple Channel Protocols • Single channel protocols: Control and packets use the same channel • Multiple channel protocols: Frequency hopping or Separate channels for control & data transmission
Single vs. Multiple Channel Protocols • Single channel protocols: Control and packets use the same channel • Multiple channel protocols: Frequency hopping or Separate channels for control & data transmission
 Frequency Hopping Spread Spectrum (FHSS) • Transmit radio signals by switching a carrier among multiple frequency channels using a pseudo random sequence known to the transmitter and receiver – Spread spectrum signals are resistant to noise & interference – Difficult to intercept – Can share a frequency band with other transmissions • Efficient bandwidth utilization
Frequency Hopping Spread Spectrum (FHSS) • Transmit radio signals by switching a carrier among multiple frequency channels using a pseudo random sequence known to the transmitter and receiver – Spread spectrum signals are resistant to noise & interference – Difficult to intercept – Can share a frequency band with other transmissions • Efficient bandwidth utilization
 Direct Sequence Spread Spectrum (DSSS) • Phase modulate a sine wave in a pseudo random manner • • – A pseudo random noise code symbols are called chips – Chip rate is much higher than the information signal bit rate The sequence of chips is known to the receiver Resistant to jamming Multiple users can share a single channel Relative timing correlation
Direct Sequence Spread Spectrum (DSSS) • Phase modulate a sine wave in a pseudo random manner • • – A pseudo random noise code symbols are called chips – Chip rate is much higher than the information signal bit rate The sequence of chips is known to the receiver Resistant to jamming Multiple users can share a single channel Relative timing correlation
 Other criteria for classification • Power-aware • Directional or omnidirectional antennas • Qo. S-aware – – End-to-end (E 2 E) delay Packet loss rate (or the probability) Available bandwidth Challenges: lack of centralized control, limited bandwidth, node mobility, power/computational constraints, error-prone nature of wireless media
Other criteria for classification • Power-aware • Directional or omnidirectional antennas • Qo. S-aware – – End-to-end (E 2 E) delay Packet loss rate (or the probability) Available bandwidth Challenges: lack of centralized control, limited bandwidth, node mobility, power/computational constraints, error-prone nature of wireless media
 I. Non-Qo. S MAC Protocols • General MAC protocols – MACA (Multiple Access Collision Avoidance) – IEEE 802. 11 – MACA-BI • Power aware MAC protocols – PAMAS (Power aware medium access control with signaling) – PCM (Power control medium access control) – PCMA (Power controlled multiple access) • Multiple channel protocols – DBMA (Dual busy tone multiple access), Multichannel CSMA MAC protocol, etc.
I. Non-Qo. S MAC Protocols • General MAC protocols – MACA (Multiple Access Collision Avoidance) – IEEE 802. 11 – MACA-BI • Power aware MAC protocols – PAMAS (Power aware medium access control with signaling) – PCM (Power control medium access control) – PCMA (Power controlled multiple access) • Multiple channel protocols – DBMA (Dual busy tone multiple access), Multichannel CSMA MAC protocol, etc.
 MACA • If node A wants to transmit to B, it first sends an RTS packet to B, indicating the length of the data transmission to follow • B returns A a CTS packet with the expected length of the transmission • A starts transmission when it receives CTS – RTS, CTS packets are much shorter than data packets • A neighboring node overhearing an RTS defers its own transmission until the corresponding CTS would have been finished • A node hearing the CTS defers for the expected length of the data transmission
MACA • If node A wants to transmit to B, it first sends an RTS packet to B, indicating the length of the data transmission to follow • B returns A a CTS packet with the expected length of the transmission • A starts transmission when it receives CTS – RTS, CTS packets are much shorter than data packets • A neighboring node overhearing an RTS defers its own transmission until the corresponding CTS would have been finished • A node hearing the CTS defers for the expected length of the data transmission
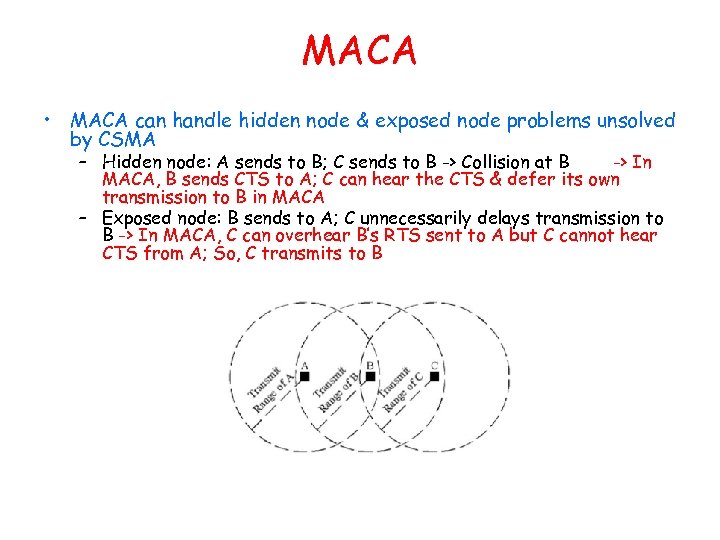 MACA • MACA can handle hidden node & exposed node problems unsolved by CSMA – Hidden node: A sends to B; C sends to B -> Collision at B -> In MACA, B sends CTS to A; C can hear the CTS & defer its own transmission to B in MACA – Exposed node: B sends to A; C unnecessarily delays transmission to B -> In MACA, C can overhear B’s RTS sent to A but C cannot hear CTS from A; So, C transmits to B
MACA • MACA can handle hidden node & exposed node problems unsolved by CSMA – Hidden node: A sends to B; C sends to B -> Collision at B -> In MACA, B sends CTS to A; C can hear the CTS & defer its own transmission to B in MACA – Exposed node: B sends to A; C unnecessarily delays transmission to B -> In MACA, C can overhear B’s RTS sent to A but C cannot hear CTS from A; So, C transmits to B
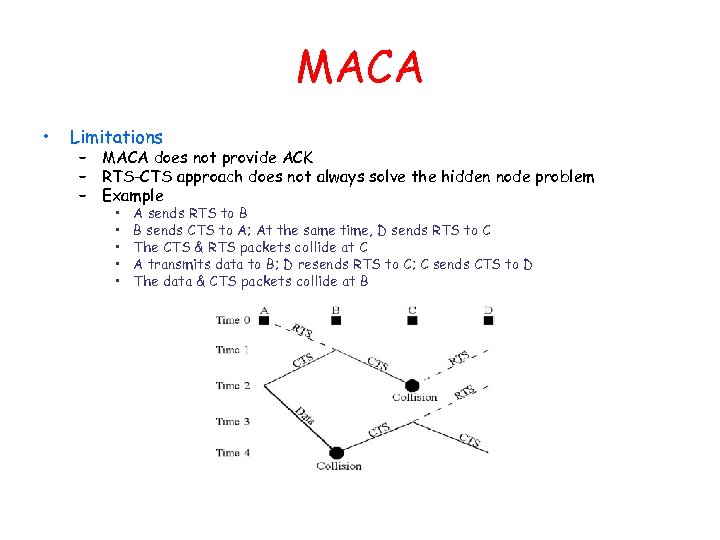 MACA • Limitations – MACA does not provide ACK – RTS-CTS approach does not always solve the hidden node problem – Example • • • A sends RTS to B B sends CTS to A; At the same time, D sends RTS to C The CTS & RTS packets collide at C A transmits data to B; D resends RTS to C; C sends CTS to D The data & CTS packets collide at B
MACA • Limitations – MACA does not provide ACK – RTS-CTS approach does not always solve the hidden node problem – Example • • • A sends RTS to B B sends CTS to A; At the same time, D sends RTS to C The CTS & RTS packets collide at C A transmits data to B; D resends RTS to C; C sends CTS to D The data & CTS packets collide at B
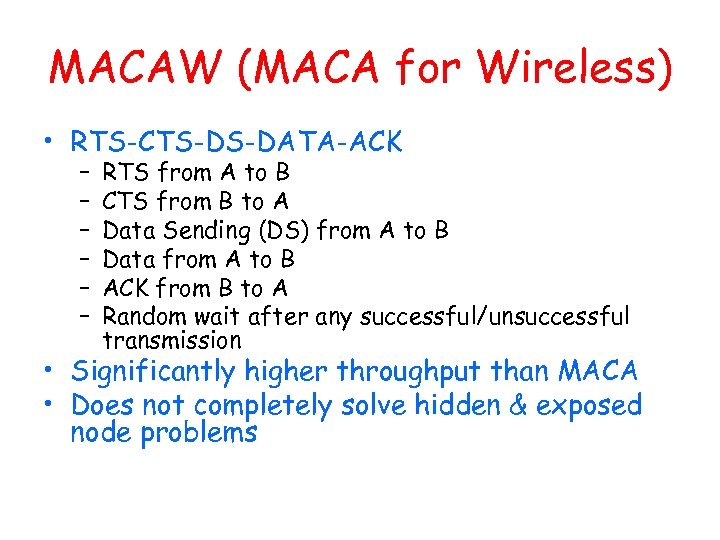 MACAW (MACA for Wireless) • RTS-CTS-DS-DATA-ACK – – – RTS from A to B CTS from B to A Data Sending (DS) from A to B Data from A to B ACK from B to A Random wait after any successful/unsuccessful transmission • Significantly higher throughput than MACA • Does not completely solve hidden & exposed node problems
MACAW (MACA for Wireless) • RTS-CTS-DS-DATA-ACK – – – RTS from A to B CTS from B to A Data Sending (DS) from A to B Data from A to B ACK from B to A Random wait after any successful/unsuccessful transmission • Significantly higher throughput than MACA • Does not completely solve hidden & exposed node problems
 IEEE 802. 11 MAC • Very popular wireless MAC protocol • Two modes: DCF (distributed coordination function) & PCF (point coordination function) • DCF is based on CSMA/CA ≈ CSMA + MACA – RTS-CTS-DATA-ACK – Physical carrier sensing + NAV (network allocation vector) containing time value that indicates the duration up to which the medium is expected to be busy due to transmissions by other nodes – Every packet contains the duration info for the remainder of the message – Every node overhearing a packet continuously updates its own NAV • IFS (inter frame spacing) – Short IFS (SIFS), PCF IFS (PIFS), DCF IFS (DIFS), Extended IFS (EIFS)
IEEE 802. 11 MAC • Very popular wireless MAC protocol • Two modes: DCF (distributed coordination function) & PCF (point coordination function) • DCF is based on CSMA/CA ≈ CSMA + MACA – RTS-CTS-DATA-ACK – Physical carrier sensing + NAV (network allocation vector) containing time value that indicates the duration up to which the medium is expected to be busy due to transmissions by other nodes – Every packet contains the duration info for the remainder of the message – Every node overhearing a packet continuously updates its own NAV • IFS (inter frame spacing) – Short IFS (SIFS), PCF IFS (PIFS), DCF IFS (DIFS), Extended IFS (EIFS)
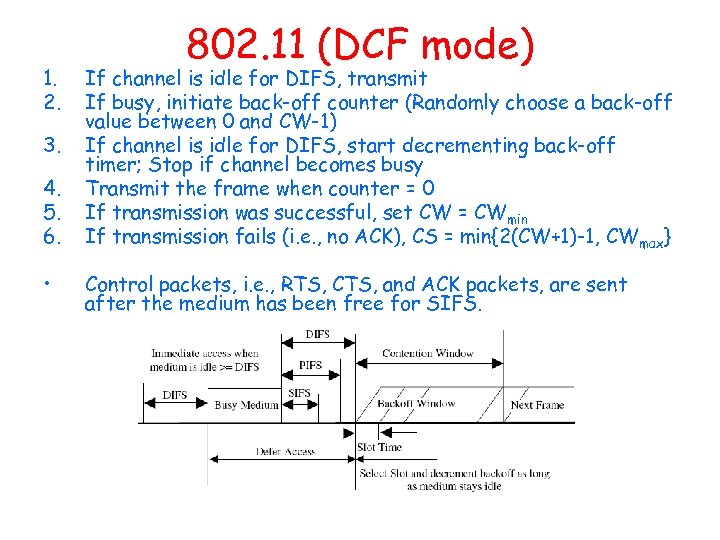 1. 2. 3. 4. 5. 6. • 802. 11 (DCF mode) If channel is idle for DIFS, transmit If busy, initiate back-off counter (Randomly choose a back-off value between 0 and CW-1) If channel is idle for DIFS, start decrementing back-off timer; Stop if channel becomes busy Transmit the frame when counter = 0 If transmission was successful, set CW = CWmin If transmission fails (i. e. , no ACK), CS = min{2(CW+1)-1, CWmax} Control packets, i. e. , RTS, CTS, and ACK packets, are sent after the medium has been free for SIFS.
1. 2. 3. 4. 5. 6. • 802. 11 (DCF mode) If channel is idle for DIFS, transmit If busy, initiate back-off counter (Randomly choose a back-off value between 0 and CW-1) If channel is idle for DIFS, start decrementing back-off timer; Stop if channel becomes busy Transmit the frame when counter = 0 If transmission was successful, set CW = CWmin If transmission fails (i. e. , no ACK), CS = min{2(CW+1)-1, CWmax} Control packets, i. e. , RTS, CTS, and ACK packets, are sent after the medium has been free for SIFS.
 MACA-BI • Receiver initiated • Reduce number of control packets – RTR (Ready To Receive) & DATA rather than RTS-CTS-DATA • Receiver needs a traffic prediction algorithm • Works well given predictable traffic patterns
MACA-BI • Receiver initiated • Reduce number of control packets – RTR (Ready To Receive) & DATA rather than RTS-CTS-DATA • Receiver needs a traffic prediction algorithm • Works well given predictable traffic patterns
 Power aware MAC protocols • Minimize expensive retransmissions due to collisions • Transceivers should be kept in standby mode as much as possible • Switch to low power mode sufficient for the destination to receive the packet • Two categories – Alternate between sleep and awake cycles – Vary transmission power
Power aware MAC protocols • Minimize expensive retransmissions due to collisions • Transceivers should be kept in standby mode as much as possible • Switch to low power mode sufficient for the destination to receive the packet • Two categories – Alternate between sleep and awake cycles – Vary transmission power
 PAMAS (Power aware medium access control with signaling) • RTS-CTS exchanges over a signaling channeling • Data transmission over a separate data channel • Receiver sends out a busy tone, while receiving a data packet over the signaling channel • Nodes listen to the signaling channel to determine when it is optimal to power down transceivers • A node powers itself off if it has nothing to transmit and its neighbor is transmitting • A node powers off if at least one neighbor is transmitting and another is receiving • Use of ACK and transmission of multiple packets can enhance performance • Radio transceiver turnaround time was not considered
PAMAS (Power aware medium access control with signaling) • RTS-CTS exchanges over a signaling channeling • Data transmission over a separate data channel • Receiver sends out a busy tone, while receiving a data packet over the signaling channel • Nodes listen to the signaling channel to determine when it is optimal to power down transceivers • A node powers itself off if it has nothing to transmit and its neighbor is transmitting • A node powers off if at least one neighbor is transmitting and another is receiving • Use of ACK and transmission of multiple packets can enhance performance • Radio transceiver turnaround time was not considered
 PCM: Power Control Medium access control • Send RTS & CTS packets using max available power • Send DATA & ACK with the min power required to communicate between the sender and receiver • Based on the received signal strength of the RTS/CTS packet, adjust the power level for DATA transmission • Drawbacks – Requires rather accurate estimation of the received signal strength, which is hard in wireless communication – Difficult to implement frequent changes in the transmission power level
PCM: Power Control Medium access control • Send RTS & CTS packets using max available power • Send DATA & ACK with the min power required to communicate between the sender and receiver • Based on the received signal strength of the RTS/CTS packet, adjust the power level for DATA transmission • Drawbacks – Requires rather accurate estimation of the received signal strength, which is hard in wireless communication – Difficult to implement frequent changes in the transmission power level
 PCMA: Power controlled multiple access • Control transmit power of the sender – The receiver is just able to receive the packet – Avoid interfering other neighboring nodes not involved in the packet exchange – Two channels: one for busy tone & another for data • Request Power To Send (RTPS) & Accept Power To Send (APTS) on the data channel • Every receiver periodically sends out a busy tone • Sender does carrier sensing
PCMA: Power controlled multiple access • Control transmit power of the sender – The receiver is just able to receive the packet – Avoid interfering other neighboring nodes not involved in the packet exchange – Two channels: one for busy tone & another for data • Request Power To Send (RTPS) & Accept Power To Send (APTS) on the data channel • Every receiver periodically sends out a busy tone • Sender does carrier sensing
 II. Qo. S-Aware MAC protocols • Prioritized Qo. S – Prioritize network flows • Parameterized Qo. S – Reserve resources for E 2 E path – A new stream is not admitted if there’s not enough resources -> Already admitted streams are not affected • Soft-Qo. S: Brief disruptions are acceptable • Dynamic-Qo. S: Range of Qo. S • Different applications, different Qo. S requirements – Audio/video streaming requires reserved share of channel capacity; Soft-Qo. S with some transient violations is acceptable • A lot to do to support audio/video streaming over a wireless channel – Inter-vehicle communication requires guaranteed delivery of short bursts of data within a delay bound • Very little prior work has been done!
II. Qo. S-Aware MAC protocols • Prioritized Qo. S – Prioritize network flows • Parameterized Qo. S – Reserve resources for E 2 E path – A new stream is not admitted if there’s not enough resources -> Already admitted streams are not affected • Soft-Qo. S: Brief disruptions are acceptable • Dynamic-Qo. S: Range of Qo. S • Different applications, different Qo. S requirements – Audio/video streaming requires reserved share of channel capacity; Soft-Qo. S with some transient violations is acceptable • A lot to do to support audio/video streaming over a wireless channel – Inter-vehicle communication requires guaranteed delivery of short bursts of data within a delay bound • Very little prior work has been done!
 Qo. S-aware MAC protocols • For real-time (RT) applications, MAC protocols should support resource reservation for RT traffic in addition to addressing hidden/exposed terminal problems • Synchronous schemes: TDM variations requiring time synchronization • Asynchronous approaches: No need for global time synchronization
Qo. S-aware MAC protocols • For real-time (RT) applications, MAC protocols should support resource reservation for RT traffic in addition to addressing hidden/exposed terminal problems • Synchronous schemes: TDM variations requiring time synchronization • Asynchronous approaches: No need for global time synchronization
 Categories of Qo. S-aware MAC protocols 1. • 2. • • • Use shorter inter-frame spacing & smaller backoff contention window for RT traffic Extension of 802. 11 DCF (e. g. , 802. 11 e) Black burst contention RT nodes jam the channel in proportion to waiting time Observe the channel Node with the longest jam transmits 3. Use reserved time slots to provide bounded & required bandwidth for RT traffic; Non-RT traffic is treated like 802. 11 4. Provide fair channel allocation to different flows unlike 1 -3
Categories of Qo. S-aware MAC protocols 1. • 2. • • • Use shorter inter-frame spacing & smaller backoff contention window for RT traffic Extension of 802. 11 DCF (e. g. , 802. 11 e) Black burst contention RT nodes jam the channel in proportion to waiting time Observe the channel Node with the longest jam transmits 3. Use reserved time slots to provide bounded & required bandwidth for RT traffic; Non-RT traffic is treated like 802. 11 4. Provide fair channel allocation to different flows unlike 1 -3
 RT-MAC • Drop tardy packets – Check before sending a packet, when its backoff timer expires, and when a transmission is unacknowledged – Eliminate possibility of collision • When a packet is actually sent, include the backoff value in the packet • A node hearing the transmission chooses a different backoff value – Advantage: Significantly reduced the mean packet delay, missed deadlines, and collisions compared to 802. 11 – Drawbacks • Contention window may become very large in a network with many nodes • No guarantee on E 2 E delay (or deadline miss ratio)
RT-MAC • Drop tardy packets – Check before sending a packet, when its backoff timer expires, and when a transmission is unacknowledged – Eliminate possibility of collision • When a packet is actually sent, include the backoff value in the packet • A node hearing the transmission chooses a different backoff value – Advantage: Significantly reduced the mean packet delay, missed deadlines, and collisions compared to 802. 11 – Drawbacks • Contention window may become very large in a network with many nodes • No guarantee on E 2 E delay (or deadline miss ratio)
 DCF with priority classes • Use a shorter IFS and backoff time for higher priority data (Deng et al) – Normal node waits for DIFS, but high priority node only waits for PIFS – Small contention window for a high priority flow • EDCF (Enhanced DCF) in 802. 11 e takes a similar approach to supporting Qo. S – Use AIFS[TC], CWmin[TC] & CWmax[TC] instead of DIFS, CWmin & CWmax in DCF where AIFS is arbitration inter frame space and TC is traffic class – AIFS[TC] ≥ DIFS can be enlarged for lower priority classes – CWmin[TC] & CWmax[TC] are set differently according to TC • No deterministic guarantee on delay • Normal traffic suffers higher delay
DCF with priority classes • Use a shorter IFS and backoff time for higher priority data (Deng et al) – Normal node waits for DIFS, but high priority node only waits for PIFS – Small contention window for a high priority flow • EDCF (Enhanced DCF) in 802. 11 e takes a similar approach to supporting Qo. S – Use AIFS[TC], CWmin[TC] & CWmax[TC] instead of DIFS, CWmin & CWmax in DCF where AIFS is arbitration inter frame space and TC is traffic class – AIFS[TC] ≥ DIFS can be enlarged for lower priority classes – CWmin[TC] & CWmax[TC] are set differently according to TC • No deterministic guarantee on delay • Normal traffic suffers higher delay
 Questions?
Questions?


