f56782ea0f77690d7ced3f8377047235.ppt
- Количество слайдов: 9
 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 An Example Idea of FIA Authors: Date: 2010 -05 -20 Name Company Address Phone email Hitoshi MORIOKA ROOT Inc. +81 -92 -771 -7630 hmorioka@root-hq. com Hiroshi MANO ROOT Inc. +81 -3 -5719 -7630 hmano@root-hq. com Paul A Lambert Marvell #33 Ito Bldg. 2 -14 -38 Tenjin, Chuo-ku, Fukuoka 810 -0001 JAPAN 8 F TOC 2 Bldg. 7 -21 -11 Nishi. Gotanda, Shinagawa-ku, Tokyo 141 -0031 JAPAN Marvel lane, MS 2 -201 Santa Clara, CA 95054 +1 -408 -222 -9522 paul@marvell. com Marc Emmelmann TU Berlin Einsteinufer 25 10587 Berlin Germany +49 -30 -314 24580 emmelmann@ieee. org Hiroki Nakano Trans New Technology +81 -75 -213 -1200 cas. nakano@gmail. com cas@trans-nt. com Mineo Takai Space Time Engineering Sumitomo-Seimei Kyoto Bldg. 8 F, 62 Tukiboko-cho Shimogyo-ku, Kyoto 600 -8492 JAPAN 609 Deep Valley Drive, Suite 200 Rolling Hills Estates, CA 90274, USA +1 -310 -265 -4441 mineo@ieee. org Submission Slide 1 Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 An Example Idea of FIA Authors: Date: 2010 -05 -20 Name Company Address Phone email Hitoshi MORIOKA ROOT Inc. +81 -92 -771 -7630 hmorioka@root-hq. com Hiroshi MANO ROOT Inc. +81 -3 -5719 -7630 hmano@root-hq. com Paul A Lambert Marvell #33 Ito Bldg. 2 -14 -38 Tenjin, Chuo-ku, Fukuoka 810 -0001 JAPAN 8 F TOC 2 Bldg. 7 -21 -11 Nishi. Gotanda, Shinagawa-ku, Tokyo 141 -0031 JAPAN Marvel lane, MS 2 -201 Santa Clara, CA 95054 +1 -408 -222 -9522 paul@marvell. com Marc Emmelmann TU Berlin Einsteinufer 25 10587 Berlin Germany +49 -30 -314 24580 emmelmann@ieee. org Hiroki Nakano Trans New Technology +81 -75 -213 -1200 cas. nakano@gmail. com cas@trans-nt. com Mineo Takai Space Time Engineering Sumitomo-Seimei Kyoto Bldg. 8 F, 62 Tukiboko-cho Shimogyo-ku, Kyoto 600 -8492 JAPAN 609 Deep Valley Drive, Suite 200 Rolling Hills Estates, CA 90274, USA +1 -310 -265 -4441 mineo@ieee. org Submission Slide 1 Hitoshi Morioka, ROOT INC.
 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Use Case Scenario • Large number of STAs are constantly entering and exiting the coverage area of an AP within an existing ESS at pedestrian speed. • Every STA passes through the coverage area in a short time. • The authentication process specified by IEEE 802. 11 limits STAs to fully exploit the system capacity A faster initial authentication is needed • FIA aims at amending IEEE 802. 11 with a fast initial authentication mechanisms which – – – Submission Walk scales with a high number of users simultaneously entering a ESS supports a very small dwell time in coverage area of a ESS securely provides initial authentication Slide 2 Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Use Case Scenario • Large number of STAs are constantly entering and exiting the coverage area of an AP within an existing ESS at pedestrian speed. • Every STA passes through the coverage area in a short time. • The authentication process specified by IEEE 802. 11 limits STAs to fully exploit the system capacity A faster initial authentication is needed • FIA aims at amending IEEE 802. 11 with a fast initial authentication mechanisms which – – – Submission Walk scales with a high number of users simultaneously entering a ESS supports a very small dwell time in coverage area of a ESS securely provides initial authentication Slide 2 Hitoshi Morioka, ROOT INC.
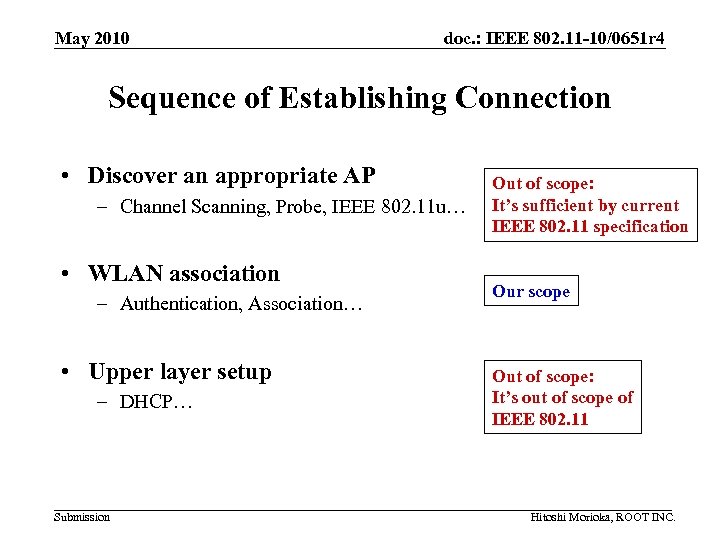 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Sequence of Establishing Connection • Discover an appropriate AP – Channel Scanning, Probe, IEEE 802. 11 u… • WLAN association – Authentication, Association… • Upper layer setup – DHCP… Submission Out of scope: It’s sufficient by current IEEE 802. 11 specification Our scope Out of scope: It’s out of scope of IEEE 802. 11 Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Sequence of Establishing Connection • Discover an appropriate AP – Channel Scanning, Probe, IEEE 802. 11 u… • WLAN association – Authentication, Association… • Upper layer setup – DHCP… Submission Out of scope: It’s sufficient by current IEEE 802. 11 specification Our scope Out of scope: It’s out of scope of IEEE 802. 11 Hitoshi Morioka, ROOT INC.
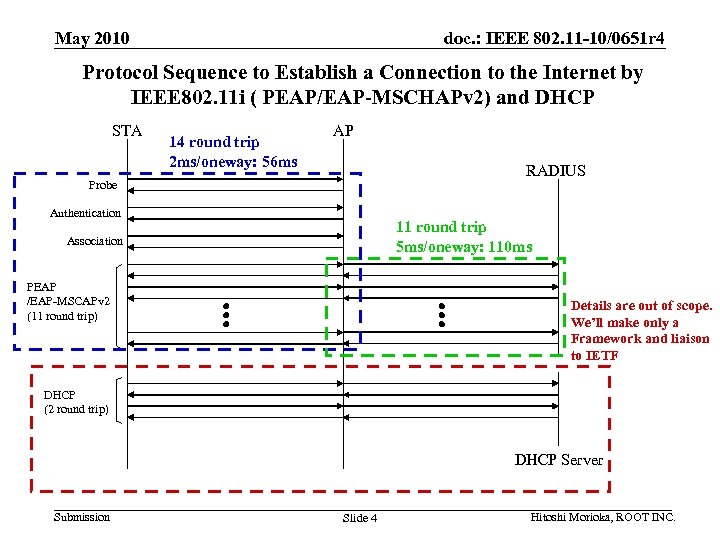 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Protocol Sequence to Establish a Connection to the Internet by IEEE 802. 11 i ( PEAP/EAP-MSCHAPv 2) and DHCP STA 14 round trip 2 ms/oneway: 56 ms AP RADIUS Probe Authentication 11 round trip 5 ms/oneway: 110 ms Association PEAP /EAP-MSCAPv 2 (11 round trip) Details are out of scope. We’ll make only a Framework and liaison to IETF DHCP (2 round trip) DHCP Server Submission Slide 4 Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Protocol Sequence to Establish a Connection to the Internet by IEEE 802. 11 i ( PEAP/EAP-MSCHAPv 2) and DHCP STA 14 round trip 2 ms/oneway: 56 ms AP RADIUS Probe Authentication 11 round trip 5 ms/oneway: 110 ms Association PEAP /EAP-MSCAPv 2 (11 round trip) Details are out of scope. We’ll make only a Framework and liaison to IETF DHCP (2 round trip) DHCP Server Submission Slide 4 Hitoshi Morioka, ROOT INC.
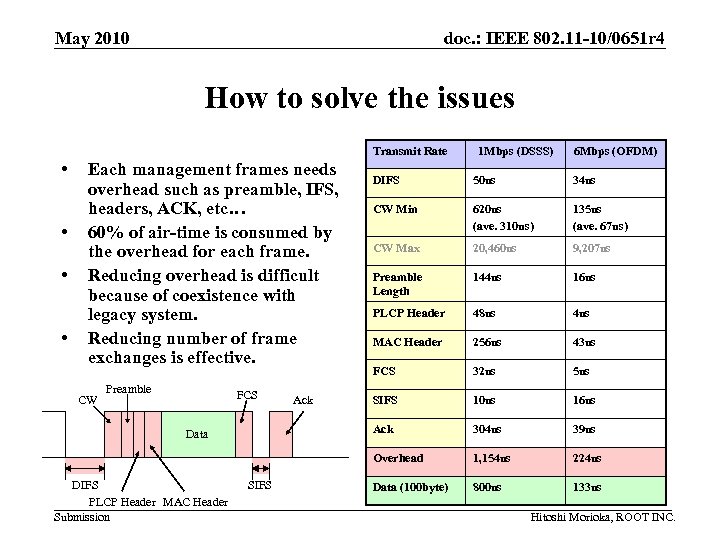 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 How to solve the issues Transmit Rate • Each management frames needs overhead such as preamble, IFS, headers, ACK, etc… 60% of air-time is consumed by the overhead for each frame. Reducing overhead is difficult because of coexistence with legacy system. Reducing number of frame exchanges is effective. 1 Mbps (DSSS) 6 Mbps (OFDM) • • CW Preamble Data DIFS PLCP Header MAC Header Submission SIFS Ack 34 us CW Min 620 us (ave. 310 us) 135 us (ave. 67 us) CW Max 20, 460 us 9, 207 us Preamble Length 144 us 16 us PLCP Header 48 us 4 us MAC Header 256 us 43 us FCS 32 us 5 us SIFS 10 us 16 us Ack FCS 50 us 304 us 39 us Overhead • DIFS 1, 154 us 224 us Data (100 byte) 800 us 133 us Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 How to solve the issues Transmit Rate • Each management frames needs overhead such as preamble, IFS, headers, ACK, etc… 60% of air-time is consumed by the overhead for each frame. Reducing overhead is difficult because of coexistence with legacy system. Reducing number of frame exchanges is effective. 1 Mbps (DSSS) 6 Mbps (OFDM) • • CW Preamble Data DIFS PLCP Header MAC Header Submission SIFS Ack 34 us CW Min 620 us (ave. 310 us) 135 us (ave. 67 us) CW Max 20, 460 us 9, 207 us Preamble Length 144 us 16 us PLCP Header 48 us 4 us MAC Header 256 us 43 us FCS 32 us 5 us SIFS 10 us 16 us Ack FCS 50 us 304 us 39 us Overhead • DIFS 1, 154 us 224 us Data (100 byte) 800 us 133 us Hitoshi Morioka, ROOT INC.
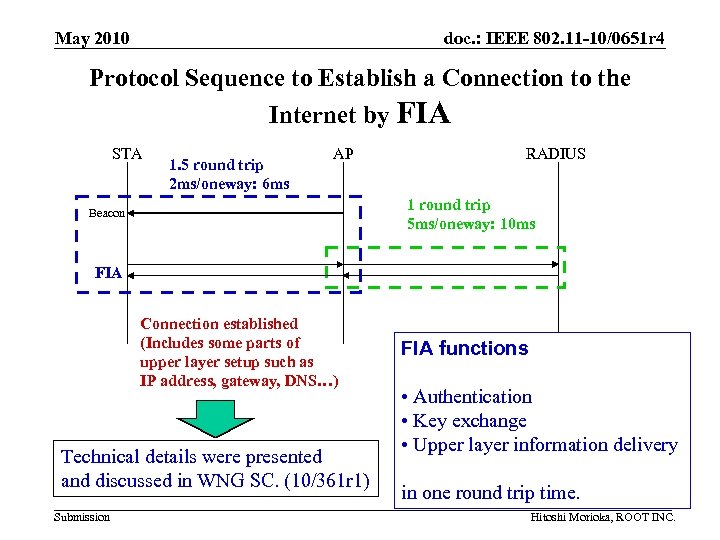 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Protocol Sequence to Establish a Connection to the Internet by FIA STA 1. 5 round trip 2 ms/oneway: 6 ms AP RADIUS 1 round trip 5 ms/oneway: 10 ms Beacon FIA Connection established (Includes some parts of upper layer setup such as IP address, gateway, DNS…) Technical details were presented and discussed in WNG SC. (10/361 r 1) Submission FIA functions • Authentication • Key exchange • Upper layer information delivery in one round trip time. Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Protocol Sequence to Establish a Connection to the Internet by FIA STA 1. 5 round trip 2 ms/oneway: 6 ms AP RADIUS 1 round trip 5 ms/oneway: 10 ms Beacon FIA Connection established (Includes some parts of upper layer setup such as IP address, gateway, DNS…) Technical details were presented and discussed in WNG SC. (10/361 r 1) Submission FIA functions • Authentication • Key exchange • Upper layer information delivery in one round trip time. Hitoshi Morioka, ROOT INC.
 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Feasibility • An example FIA protocol was evaluated and compared with IEEE 802. 11 i by security experts. – Yoshiaki Hori, Kouichi Sakurai, “Security Analysis of MIS Protocol on Wireless LAN comparison with IEEE 802. 11 i, ” Proceedings of the 3 rd international conference on Mobile technology, applications & systems, 2006, ISBN: 1 -59593 -519 -3 http: //portal. acm. org/citation. cfm? id=1292344 Submission Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Feasibility • An example FIA protocol was evaluated and compared with IEEE 802. 11 i by security experts. – Yoshiaki Hori, Kouichi Sakurai, “Security Analysis of MIS Protocol on Wireless LAN comparison with IEEE 802. 11 i, ” Proceedings of the 3 rd international conference on Mobile technology, applications & systems, 2006, ISBN: 1 -59593 -519 -3 http: //portal. acm. org/citation. cfm? id=1292344 Submission Hitoshi Morioka, ROOT INC.
 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Summary • Technical feasibility has been shown. • An example protocol was reviewed by – external security experts (Prof. Kouichi Sakurai. , Prof. Yoshiaki Hori in Kyushu Univ. ) – active participants in IEEE 802. 11 i. Submission Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Summary • Technical feasibility has been shown. • An example protocol was reviewed by – external security experts (Prof. Kouichi Sakurai. , Prof. Yoshiaki Hori in Kyushu Univ. ) – active participants in IEEE 802. 11 i. Submission Hitoshi Morioka, ROOT INC.
 May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Questions & Comments Submission Slide 9 Hitoshi Morioka, ROOT INC.
May 2010 doc. : IEEE 802. 11 -10/0651 r 4 Questions & Comments Submission Slide 9 Hitoshi Morioka, ROOT INC.


