c0abf60543c4bc9a1092f1254815c9ad.ppt
- Количество слайдов: 14
Marking Scheme for Semanticaware Web Application Security 2006. 2. 20. HPC Lab. , POSTECH, Korea Tae Hyung Kim 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
Contents Introduction p Problem Definition p Background p Marking Scheme p Implementation p Discussion p Conclusion p 2 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
Introduction(1/2) p Nearly most of web applications are security critical, but only a small fraction of deployed web applications can afford a detailed security review. p For securing web applications, there are several approaches under research: n Input and output filtering p n Automated testing p n Vulnerability scanner Diversity Defense (against code-injection attacks) p n Web application firewall Instruction-Set Randomization Information flow security p Checking integrity of data from untrusted sources 3 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
Introduction(2/2) p Especially, many companies and researchers try to develop application firewalls for a web application. p Those firewalls are based on a positive model for web applications, because a rule-based firewall needs extra attention to update rules periodically. p However, it is difficult to make a good positive model owing to lack of understanding web application semantics. 4 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
Problem Definition p Lack of understanding the web application semantics degrades web application firewalls: many false positive, false negative and overhead in a detection process. p We propose a new scheme to make security systems or modules aware the semantics of the web application. 5 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
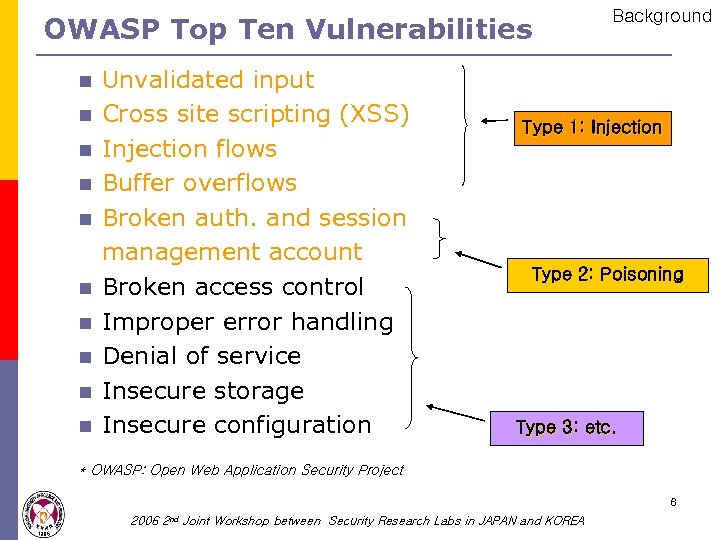
OWASP Top Ten Vulnerabilities n n n n n Unvalidated input Cross site scripting (XSS) Injection flows Buffer overflows Broken auth. and session management account Broken access control Improper error handling Denial of service Insecure storage Insecure configuration Background Type 1: Injection Type 2: Poisoning Type 3: etc. * OWASP: Open Web Application Security Project 6 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
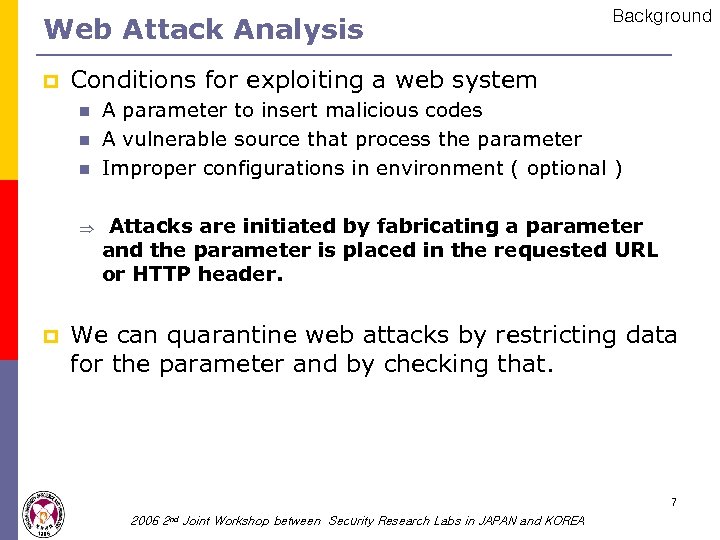
Web Attack Analysis p Conditions for exploiting a web system n n n Þ p Background A parameter to insert malicious codes A vulnerable source that process the parameter Improper configurations in environment ( optional ) Attacks are initiated by fabricating a parameter and the parameter is placed in the requested URL or HTTP header. We can quarantine web attacks by restricting data for the parameter and by checking that. 7 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
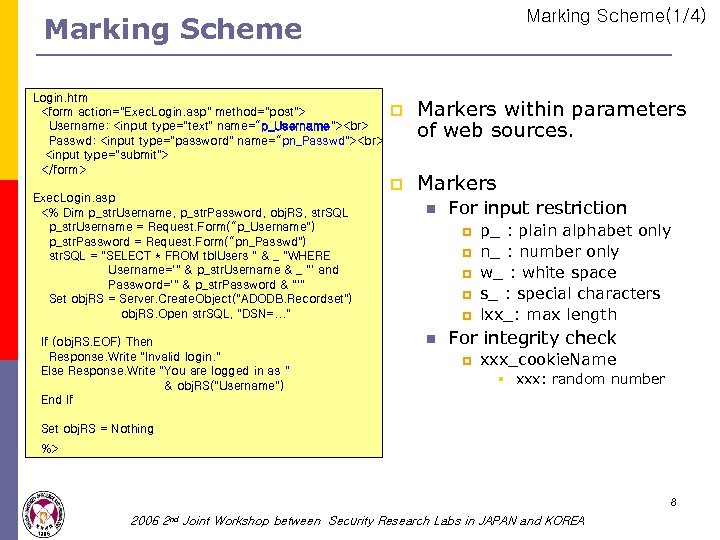
Marking Scheme(1/4) Marking Scheme Login. htm <form action="Exec. Login. asp" method="post"> Username: <input type="text" name=“p_Username"> Passwd: <input type="password" name=“pn_Passwd"> <input type="submit"> </form> Exec. Login. asp <% Dim p_str. Username, p_str. Password, obj. RS, str. SQL p_str. Username = Request. Form(“p_Username") p_str. Password = Request. Form(“pn_Passwd") str. SQL = "SELECT * FROM tbl. Users " & _ "WHERE Username='" & p_str. Username & _ "' and Password='" & p_str. Password & "'" Set obj. RS = Server. Create. Object("ADODB. Recordset") obj. RS. Open str. SQL, "DSN=. . . " If (obj. RS. EOF) Then Response. Write "Invalid login. " Else Response. Write "You are logged in as " & obj. RS("Username") End If p Markers within parameters of web sources. p Markers n For input restriction p p p n p_ : plain alphabet only n_ : number only w_ : white space s_ : special characters lxx_: max length For integrity check p xxx_cookie. Name § xxx: random number Set obj. RS = Nothing %> 8 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
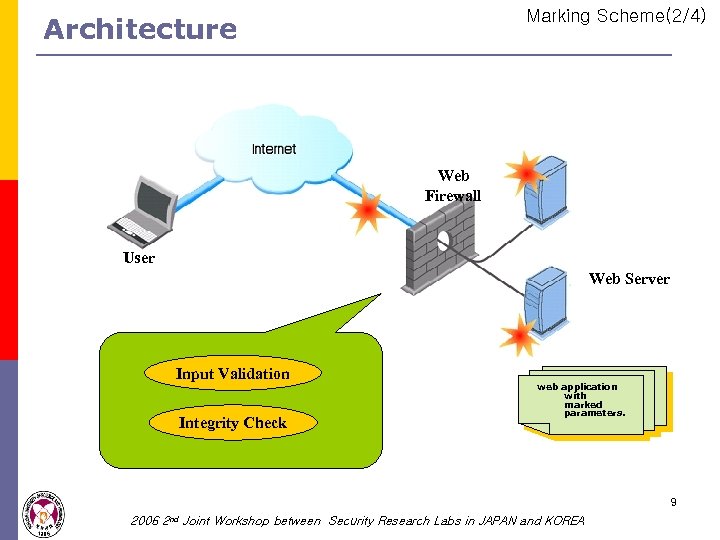
Marking Scheme(2/4) Architecture Web Firewall User Web Server Input Validation Integrity Check web application with marked parameters. 9 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
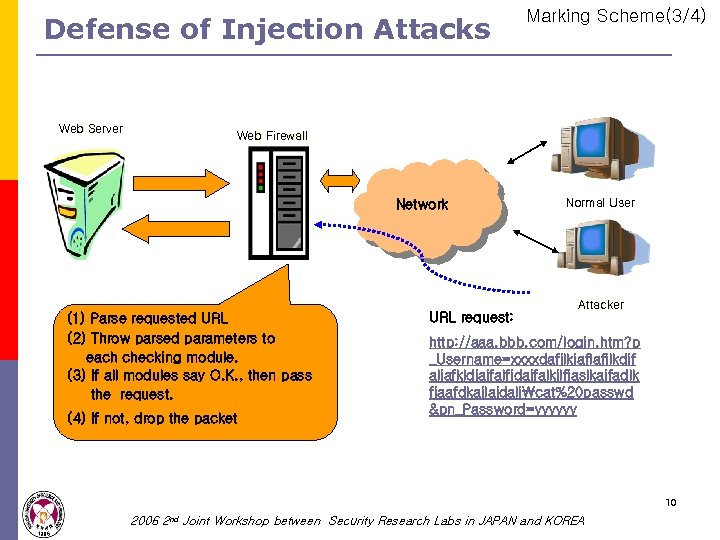
Defense of Injection Attacks Web Server Marking Scheme(3/4) Web Firewall Network (1) Parse requested URL (2) Throw parsed parameters to each checking module. (3) If all modules say O. K. , then pass the request. (4) If not, drop the packet URL request: Normal User Attacker http: //aaa. bbb. com/login. htm? p _Username=xxxxdafjlkjaflafjlkdjf aljafkldjajfalfjdajfalkjlfjaslkajfadlk fjaafdkajlajdaljcat%20 passwd &pn_Password=yyyyyy 10 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
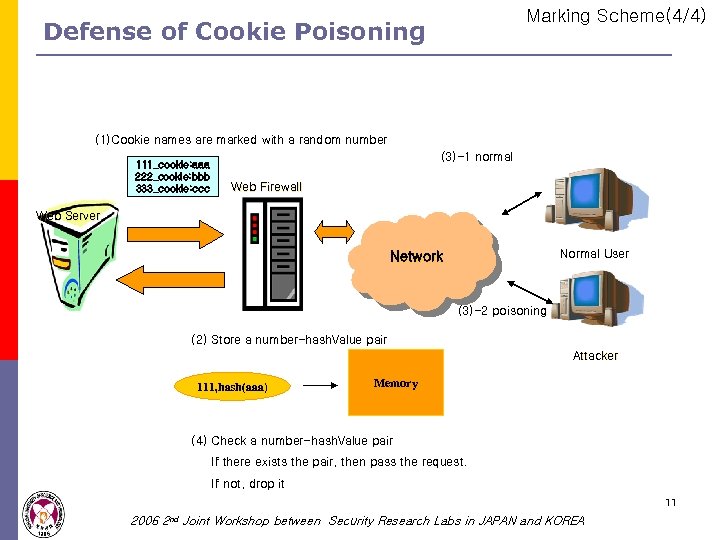
Marking Scheme(4/4) Defense of Cookie Poisoning (1)Cookie names are marked with a random number 111_cookie: aaa 222_cookie: bbb 333_cookie: ccc (3)-1 normal Web Firewall Web Server Normal User Network (3)-2 poisoning (2) Store a number-hash. Value pair Attacker 111, hash(aaa) Memory (4) Check a number-hash. Value pair If there exists the pair, then pass the request. If not, drop it 11 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
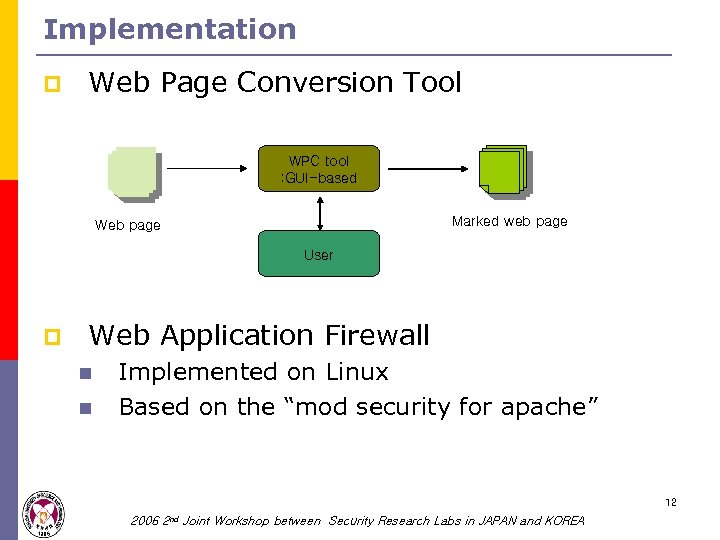
Implementation p Web Page Conversion Tool WPC tool : GUI-based Marked web page Web page User p Web Application Firewall n n Implemented on Linux Based on the “mod security for apache” 12 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
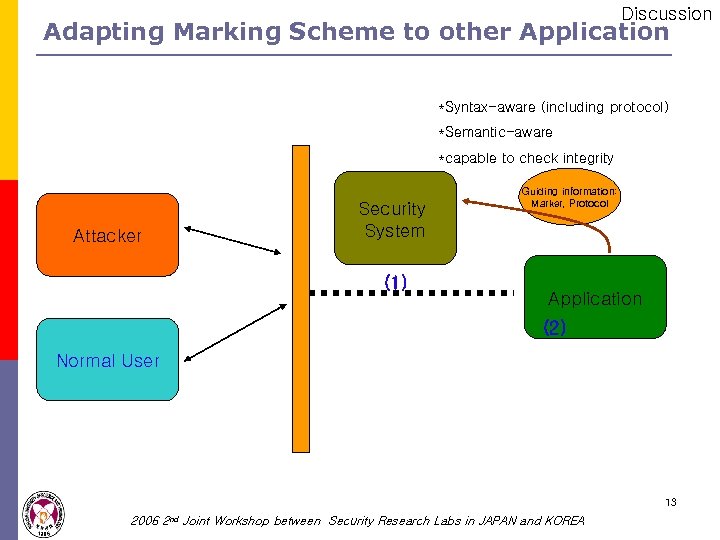
Discussion Adapting Marking Scheme to other Application *Syntax-aware (including protocol) *Semantic-aware *capable to check integrity Attacker Security System (1) Guiding information: Marker, Protocol Application (2) Normal User 13 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA

Conclusion p We propose a new security scheme for securing web application. p This scheme makes the application firewall filtering malicious packets easily and efficiently by helping it aware the semantics of web application. p As a future work, we are required to implement the WPC tool and realize the firewall in detail. And also we need more experiments for improving our scheme. 14 2006 2 nd Joint Workshop between Security Research Labs in JAPAN and KOREA
c0abf60543c4bc9a1092f1254815c9ad.ppt