368f9f235ea8b94cac8b16c534c1cba0.ppt
- Количество слайдов: 23
March “Malware” Madness by Micah Van Maanen Sioux County IT Director

Game #1 Inbox vs. spam Sizing up the competition Ø Ø Ø Ø Ø spam facts Who sends it? Why do they send it? Who does it affect? How did they get my E-mail address? An ounce of prevention Tracing and Reporting spam Blocking spam Identifying spam Sioux County E-mail statistics
spam facts spam is… Unsolicited Commercial E-mail In 1978 the first internet E-mail spam was sent* More than 50% of all spam originates in the U. S** 50% to 85% of all E-mail is spam*** CAN-SPAM (Controlling the Assault of Non-Solicited Pornography and Marketing Act) – has not helped**** Ø Approximately 45% of Sioux County’s E-mail is spam Ø What does Hormel, makers of SPAM think of spam? http: //www. spam. com/ci/ci_in. htm Ø Ø Ø *http: //www. templetons. com/brad/spamterm. html **http: //www. internetnews. com/stats/article. php/3376331 ***http: //www. metafilter. com/mefi/34180 ****http: //www. computerweekly. com/Article 130765. htm

Who sends it? Ø Illegitimate businesses that advertise*: Ø Chain letters Ø Pyramid schemes Ø “Get Rich Quick” or “Make Money Fast” schemes Ø Offers for phone sex lines and ads for pornography Ø Offers of software collecting E-mail addresses and sending spam Ø Offers of bulk E-mailing services Ø Stock offerings for unknown start-up corporations Ø Quack health products or remedies Ø Illegally pirated software (“Wares”) *http: //www. cauce. org/about/problem. shtml

Why do they send it? Ø These types of companies send spam because: Ø It is effective. Over a four-week period 6, 000 people responded to E-mail ads and placed orders for a supplement at $50 per bottle* Ø It is inexpensive (for the sender). A dialup connection and a PC can send hundreds of thousands of messages per hour** Ø It could be you! Ø As much as 30% of all spam is relayed by compromised computers*** *http: //www. wired. com/news/business/0, 1367, 59907, 00. html **http: //www. cauce. org/about/problem. shtml ***http: //www. ftc. gov/bcp/conline/pubs/alerts/whospamalrt. htm

Who does it affect? Ø Everyone that uses the Internet. * Here is how: Ø The cost is shifted from the spammer to you Ø Your ISP must process the spam using up bandwidth and processor time that you pay for Ø They fraudulently change the headers of a message and relay off unsuspecting users Ø Other ISPs must also process and forward the spam using up their bandwidth and processor time Ø Your normal E-mail is displaced. Similar to Junk-Faxing, which without the Anti-Junk-Fax law, would make your fax machine almost useless Ø Your E-mail address belongs to you! You pay for it. You should have the choice to opt-in to receive spam. *http: //www. wired. com/news/business/0, 1367, 59907, 00. html

How did they get my E-mail address? Ø Ø Ø From a newsgroup posting containing your E-mail address From a mailing list that contains your E-mail address From a website that shows your E-mail address From various website and paper forms From your web browser From IRC and chat rooms From AOL Profiles By guessing and cleaning (using spam beacons http: //tinyurl. com/4 vxvp) From white and yellow pages Social engineering Viruses and worms Hacking into sites *http: //www. wired. com/news/business/0, 1367, 59907, 00. html

An ounce of prevention Ø Never respond to spam. They will not remove you from their mailing list* Ø Don’t post your address on your website Ø Use a second E-mail address in newsgroups Ø Don’t give out your E-mail address without knowing how it will be used Ø Use a spam filter Ø Never buy anything advertised in spam Ø Keep your anti-virus / anti-spyware software up to date Ø Use a firewall on high-speed Internet connections *http: //www. spamrecycle. com/antispamthings. htm

Tracing and reporting spam • • Look at E-mail headers for the true sender of the E-mail Run a tracert on the spammers IP Address Send a nice E-mail to postmaster@<isp. com> or abuse@<isp. com> Search Google newsgroups to find extent of spam (just for fun) Or Buy a tool such as Spam. Cop http: //www. spamcop. net/ *http: //www. spamrecycle. com/antispamthings. htm

Blocking spam Ø Use an E-mail client with built-in spam filtering such as Mozilla Thunderbird Ø Buy software to scan your E-mail before you receive it Ø For the enterprise: Ø Ø Server-based products Client-based products Anti-spam services Appliances Ø Create acceptable use policies for E-mail and network Ø Close open SMTP relay servers Ø An alternative for really large networks (not Bayesian): www. turntide. com *http: //www. spamrecycle. com/antispamthings. htm

Identifying spam* Ø Host-based filtering Ø Real-time Black Holes Ø Rule-based filtering Ø Spam Assassin Ø Bayesian statistical analysis Ø Statistical probability Ø White lists Ø Trusted hosts *Inside the Spam Cartel by Spammer-X
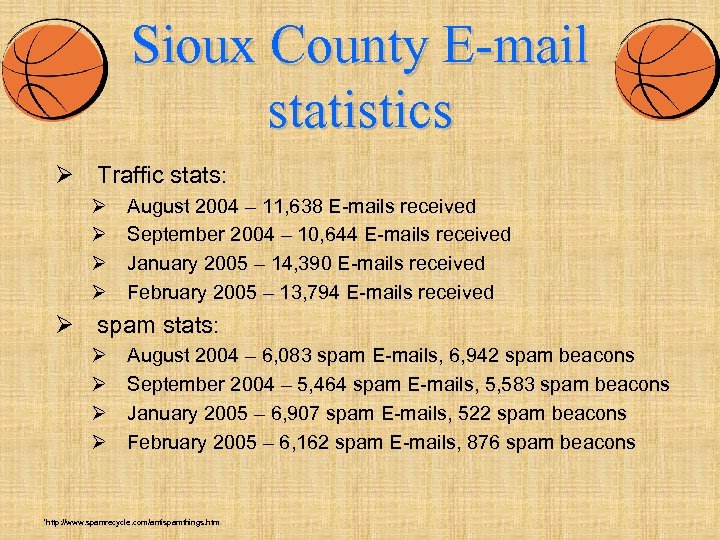
Sioux County E-mail statistics Ø Traffic stats: Ø Ø August 2004 – 11, 638 E-mails received September 2004 – 10, 644 E-mails received January 2005 – 14, 390 E-mails received February 2005 – 13, 794 E-mails received Ø spam stats: Ø Ø August 2004 – 6, 083 spam E-mails, 6, 942 spam beacons September 2004 – 5, 464 spam E-mails, 5, 583 spam beacons January 2005 – 6, 907 spam E-mails, 522 spam beacons February 2005 – 6, 162 spam E-mails, 876 spam beacons *http: //www. spamrecycle. com/antispamthings. htm

spam resources • On the web: – – – http: //www. cauce. org/index. phtml - Coalition Against Unsolicited Commercial E-mail http: //spam. abuse. net/ - A lot of spam info http: //tinyurl. com/6 zyc 7 - Best practices for Outlook http: //www. bath. ac. uk/bucs/email/anatomy. shtml - Anatomy of an E-mail message http: //www. xintercept. com/pkpeek. htm - Pocketknife Peek for Outlook http: //www. dnsstuff. com - Excellent DNS site http: //antispam. radio-showtime. com/ - How to report spam http: //www. mozilla. com - Firefox / Thunderbird website http: //tinyurl. com/3 vzv 8 - Info. World enterprise anti-spam review http: //tinyurl. com/3 r 72 k - Network World enterprise anti-spam review http: //tinyurl. com/59 pc 8 - Inside the Spam Cartel book on Amazon. com

Game #2 Privacy vs. Spyware Sizing up the competition Ø Ø Ø Ø Defining spyware Spyware facts Finding and removing spyware Spyware test results How did I get spyware? Blocking spyware An ounce of prevention Sioux County spyware statistics

Defining spyware Ø Spyware, which includes malware, trackware and adware, is the categorical name for any application that may track your online and/or offline PC activity and is capable of locally saving or transmitting those findings for third parties sometimes with but more often without your knowledge or consent. * Ø The differences between spyware and viruses* Spyware Viruses Profit motivation Harmful Intention Monitor online activities for commercial gain Damage computer system, corrupt files and destroy data Undetectable with anti-virus software Detectable with anti-virus software New technology (less than 5 years) Old technology (more than 20 years) *http: //www. webroot. com

Spyware facts Ø Four in five users (80%) have spyware or adware programs on their computer* Ø The average infected user has 93 spyware / adware components on their computer and the most found on a single computer during the scan was 1, 059* Ø An overwhelming majority of users (89%) who were infected said they didn’t know the programs were on their computer* Ø 90% didn’t know what the programs are or do* Ø 95% never gave permission for the programs to be installed* Ø 86% asked the technicians performing the study to remove the programs* *http: //www. staysafeonline. info/news/NCSA-AOLIn-Home. Study. Release. pdf

Finding and removing spyware Ø You can use any or all of these programs: Ø Ø Ø Ad-aware Spybot Search and Destroy Microsoft Anti. Spyware beta Webroot Spy Sweeper CWShredder Ø Even these programs may not find all spyware. In a recent test of these programs the results are interesting… *http: //www. staysafeonline. info/news/NCSA-AOLIn-Home. Study. Release. pdf
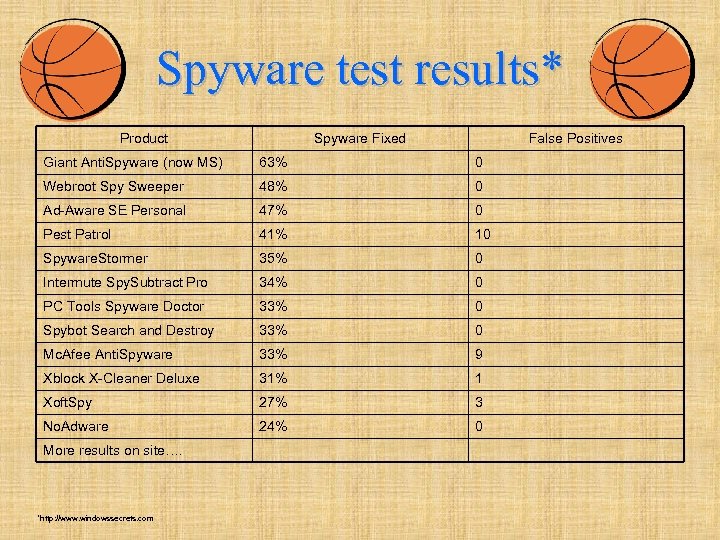
Spyware test results* Product Spyware Fixed False Positives Giant Anti. Spyware (now MS) 63% 0 Webroot Spy Sweeper 48% 0 Ad-Aware SE Personal 47% 0 Pest Patrol 41% 10 Spyware. Stormer 35% 0 Intermute Spy. Subtract Pro 34% 0 PC Tools Spyware Doctor 33% 0 Spybot Search and Destroy 33% 0 Mc. Afee Anti. Spyware 33% 9 Xblock X-Cleaner Deluxe 31% 1 Xoft. Spy 27% 3 No. Adware 24% 0 More results on site…. *http: //www. windowssecrets. com

How did I get spyware? Ø Piggybacked software installation Ø Drive-by downloads Ø Browser add-ons Ø Masquerading as anti-spyware *http: //computer. howstuffworks. com/spyware 2. htm
Blocking spyware Ø Many of today’s anti-spyware products also include permanent protection of your system Ø Home page shield Ø Internet Explorer bad-download blocker Ø Hosts file protection Ø System startup protection Ø Windows registry protection Ø MSN Messenger protection Ø Tracking cookie protection Ø Bad website protection *http: //www. staysafeonline. info/news/NCSA-AOLIn-Home. Study. Release. pdf

An ounce of prevention Ø Ø Ø Use Mozilla Firefox web browser Adjust Internet Explorer security settings Surf safely Keep Windows up to date Keep your anti-virus / anti-spyware software up to date Use a firewall on high-speed Internet connections *http: //www. spamrecycle. com/antispamthings. htm
Sioux County spyware statistics Ø Out of 61 machines 31 had spyware Ø One machine had 41 pieces of spyware Ø Most frequent visitors: Comet cursor, CWS *http: //www. staysafeonline. info/news/NCSA-AOLIn-Home. Study. Release. pdf
Spyware resources • On the web: – – – http: //www. nwfusion. com/reviews/2004/121304 rev. html - Enterprise spyware review http: //www. sysinternals. com/ntw 2 k/freeware/autoruns. shtml - Sysinternals autoruns http: //www. benedelman. org/ - Interesting spyware site http: //spywarewarrior. com/asw-test-guide. htm - spyware test results http: //www. nwnetworks. com/iezones. htm - configuring IE zones
368f9f235ea8b94cac8b16c534c1cba0.ppt