339b692e00101a592b0c49fc71ea38db.ppt
- Количество слайдов: 30
 Managing Information System Security: Principles GP Dhillon Associate Professor Virginia Commonwealth University
Managing Information System Security: Principles GP Dhillon Associate Professor Virginia Commonwealth University
 Shocking news 25% of the organizations did not have an internal audit 50% of the organizations did not have computer audit skills 60% of the organizations had no security awareness 80% of the organizations did not conduct a risk analysis
Shocking news 25% of the organizations did not have an internal audit 50% of the organizations did not have computer audit skills 60% of the organizations had no security awareness 80% of the organizations did not conduct a risk analysis
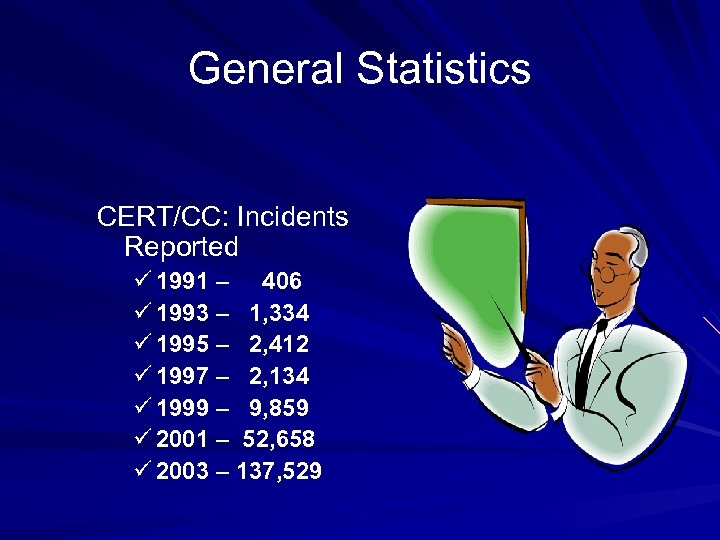 General Statistics CERT/CC: Incidents Reported ü 1991 – 406 ü 1993 – 1, 334 ü 1995 – 2, 412 ü 1997 – 2, 134 ü 1999 – 9, 859 ü 2001 – 52, 658 ü 2003 – 137, 529
General Statistics CERT/CC: Incidents Reported ü 1991 – 406 ü 1993 – 1, 334 ü 1995 – 2, 412 ü 1997 – 2, 134 ü 1999 – 9, 859 ü 2001 – 52, 658 ü 2003 – 137, 529
 Common Myths F “Why should I care, I have nothing to hide. ” F “Why does anyone care about my computer? ” F “It’s too difficult to get access to my computer or personal information…” F “If someone tries to [insert malicious activity here], I will notice!” F “Ignorance is bliss!”
Common Myths F “Why should I care, I have nothing to hide. ” F “Why does anyone care about my computer? ” F “It’s too difficult to get access to my computer or personal information…” F “If someone tries to [insert malicious activity here], I will notice!” F “Ignorance is bliss!”
 Are you at risk? Using the following puts you at risk: ü Computers ü Credit Cards ü Banks ü Airlines ü Automobiles ü …many more…
Are you at risk? Using the following puts you at risk: ü Computers ü Credit Cards ü Banks ü Airlines ü Automobiles ü …many more…
 CIA – the building blocks Confidentiality Integrity Availability
CIA – the building blocks Confidentiality Integrity Availability
 Confidentiality C Ensures privacy. C Applies to both data on disks and network communication. C Accomplished through encryption: P https: // P s/mime P pgp P ssh and ipsec Confidentiality
Confidentiality C Ensures privacy. C Applies to both data on disks and network communication. C Accomplished through encryption: P https: // P s/mime P pgp P ssh and ipsec Confidentiality
 Integrity C Develops trust of the Integrity network and computer systems. C Applies to both data on disks and network communication. C Integrity is increased by proper data and system management.
Integrity C Develops trust of the Integrity network and computer systems. C Applies to both data on disks and network communication. C Integrity is increased by proper data and system management.
 Availability C Another catalyst for trust. C Required for data on disk and network C Prevents Denial o Service attacks, etc. Availability
Availability C Another catalyst for trust. C Required for data on disk and network C Prevents Denial o Service attacks, etc. Availability
 Defending with technology
Defending with technology
 Start with the basics P Basic computer security is through technology is easy; use… FA firewall, FAnti-Virus Software, FPatch your computer quickly, when required, FStrong passwords!
Start with the basics P Basic computer security is through technology is easy; use… FA firewall, FAnti-Virus Software, FPatch your computer quickly, when required, FStrong passwords!
 Firewalls R The most useful tool in your bag of defenses. R Prevents intruders from accessing services on your computer. R Validates/normalizes network traffic. R May provide reports and trend analysis. R Available for all major operating systems – usually for free!
Firewalls R The most useful tool in your bag of defenses. R Prevents intruders from accessing services on your computer. R Validates/normalizes network traffic. R May provide reports and trend analysis. R Available for all major operating systems – usually for free!
 Anti-virus software R Stops viruses and worms sent by email, attachments, downloads, etc. R Detects malicious software through intelligent heuristics. R Available for all major desktop and server operating systems. R A requirement; not an option.
Anti-virus software R Stops viruses and worms sent by email, attachments, downloads, etc. R Detects malicious software through intelligent heuristics. R Available for all major desktop and server operating systems. R A requirement; not an option.
 Patches R (Usually) free updates to your computer; can be downloaded from the Internet. R Available before most exploits surface. R Automated, usually. R Critical to overall security. R Chant: “We Must Patch, We Must Patch…”
Patches R (Usually) free updates to your computer; can be downloaded from the Internet. R Available before most exploits surface. R Automated, usually. R Critical to overall security. R Chant: “We Must Patch, We Must Patch…”
 Strong passwords R Keeps you on-target with best practices. R Is composed of 8 or more characters and includes letters, numbers and 2 special characters, including !@#$%^&. -+-=|]{}: ”. R Not based on any dictionary word from any language. R Changes regularly; not shared.
Strong passwords R Keeps you on-target with best practices. R Is composed of 8 or more characters and includes letters, numbers and 2 special characters, including !@#$%^&. -+-=|]{}: ”. R Not based on any dictionary word from any language. R Changes regularly; not shared.
 Behavioral changes
Behavioral changes
 What technology doesn’t solve P Security technologies adapt as threats appear. They are not able to (easily) combat: F Threats, F Hoaxes, F Scams, F The behavior of others.
What technology doesn’t solve P Security technologies adapt as threats appear. They are not able to (easily) combat: F Threats, F Hoaxes, F Scams, F The behavior of others.
 The clue factor
The clue factor
 Education and awareness R Education and awareness are key to increasing the security posture of the University, and global Internet. F Dispells the FUD (fear, uncertainty, doubt). F Addresses problems before they exist. F Extends the radius of clue. F Creates inclusion in the entire infosecurity effort.
Education and awareness R Education and awareness are key to increasing the security posture of the University, and global Internet. F Dispells the FUD (fear, uncertainty, doubt). F Addresses problems before they exist. F Extends the radius of clue. F Creates inclusion in the entire infosecurity effort.
 Self-education R You can increase your own awareness of security related issues. C Subscribe to mailing lists for security notifications. C Visit security related websites. C Voice your concern on security related issues, helping raise awareness in others.
Self-education R You can increase your own awareness of security related issues. C Subscribe to mailing lists for security notifications. C Visit security related websites. C Voice your concern on security related issues, helping raise awareness in others.
 Test your efforts C Remember: security is about sharing knowledge and contacts, not technology.
Test your efforts C Remember: security is about sharing knowledge and contacts, not technology.
 The ‘RITE’ principles Responsibility (and knowledge of Roles) Integrity (as requirement of Membership) Trust (as distinct from Control) Ethicality (as opposed to Rules)
The ‘RITE’ principles Responsibility (and knowledge of Roles) Integrity (as requirement of Membership) Trust (as distinct from Control) Ethicality (as opposed to Rules)
 “Total” security CIA + RITE
“Total” security CIA + RITE
 Conceptualizing controls Pragmatic controls Formal controls Technical controls
Conceptualizing controls Pragmatic controls Formal controls Technical controls
 Principle #1 Principle 1: Education, training and awareness, although important, are not sufficient conditions for managing information security. A focus on developing a security culture goes a long way in developing and sustaining a secure environment.
Principle #1 Principle 1: Education, training and awareness, although important, are not sufficient conditions for managing information security. A focus on developing a security culture goes a long way in developing and sustaining a secure environment.
 Principle #2 Principle 2: Responsibility, integrity, trust and ethicality are the cornerstones for maintaining a secure environment.
Principle #2 Principle 2: Responsibility, integrity, trust and ethicality are the cornerstones for maintaining a secure environment.
 Principle #3 Principle 3: Establishing a boundary between what can be formalized and what should be norm based is the basis for establishing appropriate control measures.
Principle #3 Principle 3: Establishing a boundary between what can be formalized and what should be norm based is the basis for establishing appropriate control measures.
 Principle #4 Principle 4: Rules for managing information security have little relevance unless they are contextualized.
Principle #4 Principle 4: Rules for managing information security have little relevance unless they are contextualized.
 Principle #5 Principle 5: In managing the security of technical systems a rationally planned grandiose strategy will fall short of achieving the purpose.
Principle #5 Principle 5: In managing the security of technical systems a rationally planned grandiose strategy will fall short of achieving the purpose.
 Principle #6 Principle 6: Formal models for maintaining the confidentiality, integrity and availability (CIA) of information cannot be applied to commercial organizations on a grand scale. Micro-management for achieving CIA is the way forward.
Principle #6 Principle 6: Formal models for maintaining the confidentiality, integrity and availability (CIA) of information cannot be applied to commercial organizations on a grand scale. Micro-management for achieving CIA is the way forward.


