896813fb1326d0f44a61b2ddc4462d22.ppt
- Количество слайдов: 51
 Managing and Supporting XP
Managing and Supporting XP
 Security Using Windows NT/2000/XP n Two goals of security 1. 2. n Secure system resources, including hardware and software, from improper use Secure users’ data from improper access Concept of user accounts is key to understanding Windows XP 2
Security Using Windows NT/2000/XP n Two goals of security 1. 2. n Secure system resources, including hardware and software, from improper use Secure users’ data from improper access Concept of user accounts is key to understanding Windows XP 2
 User Accounts and Profiles n n n Defines a user to Windows Records information about the user (e. g. , user name, account password, group memberships, rights and permissions assigned to the account) Three types Global (domain) user accounts n Local user accounts n Built-in user accounts n 3
User Accounts and Profiles n n n Defines a user to Windows Records information about the user (e. g. , user name, account password, group memberships, rights and permissions assigned to the account) Three types Global (domain) user accounts n Local user accounts n Built-in user accounts n 3
 User Profiles n n Created by the system after user logs on for first time Types n Roaming user profile n Mandatory user profile n Group profile 4
User Profiles n n Created by the system after user logs on for first time Types n Roaming user profile n Mandatory user profile n Group profile 4
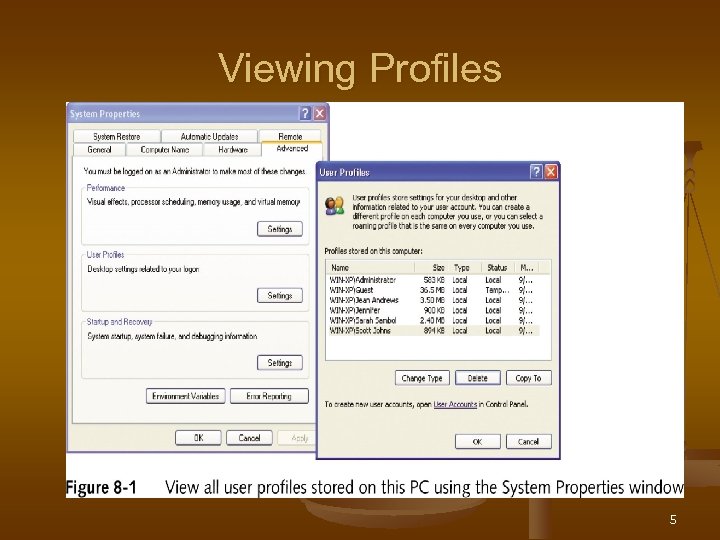 Viewing Profiles 5
Viewing Profiles 5
 Administering Local User Accounts Password guidelines for users and administrators: n n n Usernames can consist of up to 15 characters Passwords can be up to 127 characters Do not use a password that is easy to guess 6
Administering Local User Accounts Password guidelines for users and administrators: n n n Usernames can consist of up to 15 characters Passwords can be up to 127 characters Do not use a password that is easy to guess 6
 Administering Local User Accounts (continued) n n n Use combination of letters, numbers, and non-alphanumeric characters for greatest security Always set a password for the Administrator account Passwords can be controlled by administrator, but generally, users should be allowed to change their own 7
Administering Local User Accounts (continued) n n n Use combination of letters, numbers, and non-alphanumeric characters for greatest security Always set a password for the Administrator account Passwords can be controlled by administrator, but generally, users should be allowed to change their own 7
 Creating a User Account 1. Log on as the Administrator 2. Open Computer Management 3. Expand Local Users and Groups, right-click Users, select New User, enter user data, click Create 8
Creating a User Account 1. Log on as the Administrator 2. Open Computer Management 3. Expand Local Users and Groups, right-click Users, select New User, enter user data, click Create 8
 To Change User Account Type 1. 2. 3. Click Change an account, click the account to be changed Select account data to be changed and click Change the account type Select account type, click Change Account Type, click Back twice 9
To Change User Account Type 1. 2. 3. Click Change an account, click the account to be changed Select account data to be changed and click Change the account type Select account type, click Change Account Type, click Back twice 9
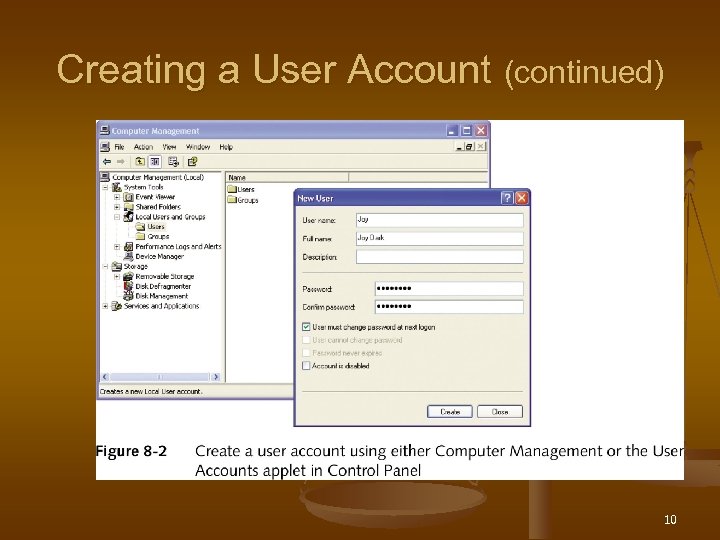 Creating a User Account (continued) 10
Creating a User Account (continued) 10
 User Groups n n Efficient way for administrator to manage multiple user accounts that require same privileges and similar profiles Groups installed by Windows XP Administrators n Backup Operators n Power Users n Limited Users n Guests n 11
User Groups n n Efficient way for administrator to manage multiple user accounts that require same privileges and similar profiles Groups installed by Windows XP Administrators n Backup Operators n Power Users n Limited Users n Guests n 11
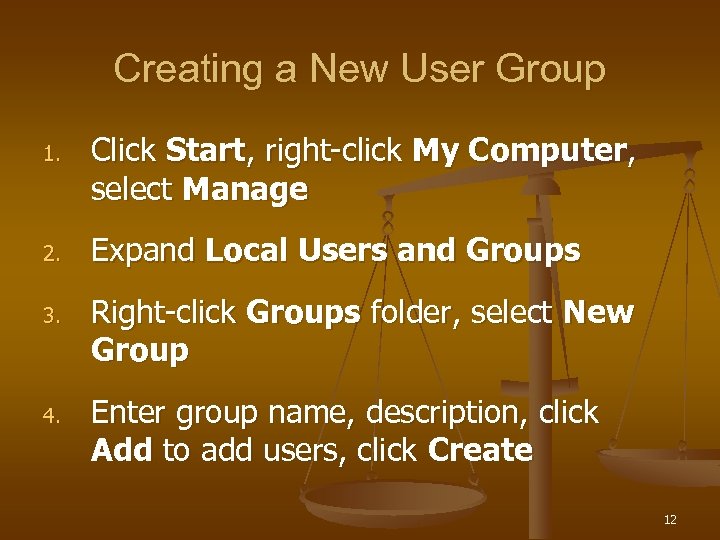 Creating a New User Group 1. 2. 3. 4. Click Start, right-click My Computer, select Manage Expand Local Users and Groups Right-click Groups folder, select New Group Enter group name, description, click Add to add users, click Create 12
Creating a New User Group 1. 2. 3. 4. Click Start, right-click My Computer, select Manage Expand Local Users and Groups Right-click Groups folder, select New Group Enter group name, description, click Add to add users, click Create 12
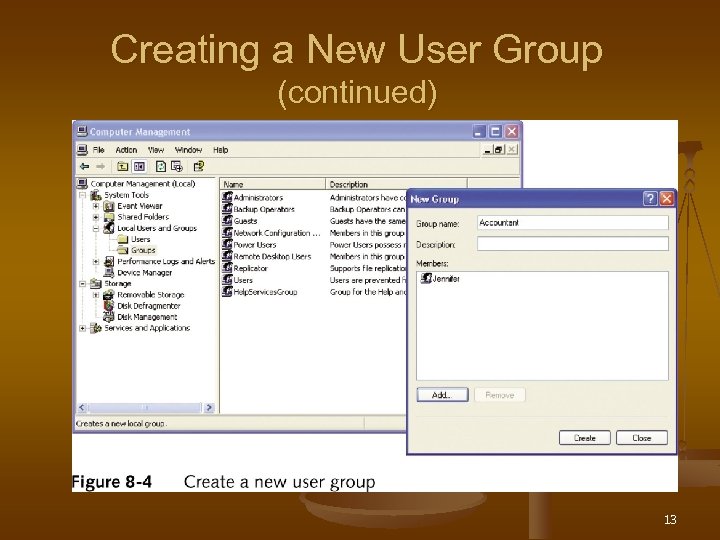 Creating a New User Group (continued) 13
Creating a New User Group (continued) 13
 Disk Quotas n n n Limit how much disk space user has access to Does not specify location of files, just total space allowed on a volume Can be set only if you are using NTFS 14
Disk Quotas n n n Limit how much disk space user has access to Does not specify location of files, just total space allowed on a volume Can be set only if you are using NTFS 14
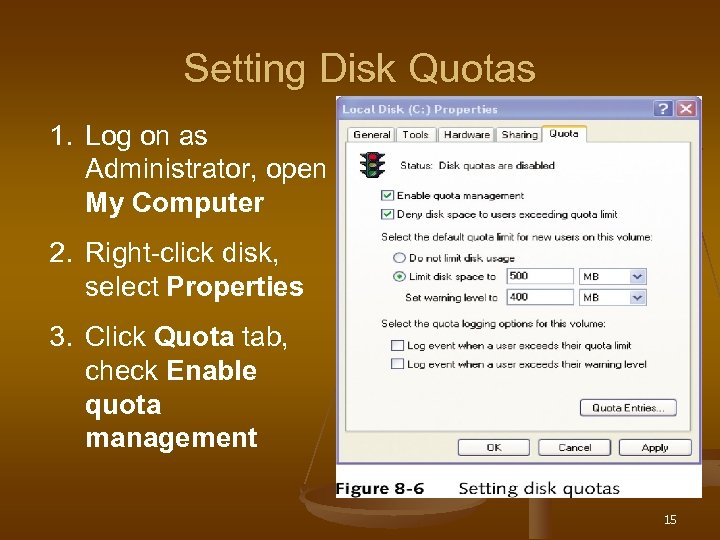 Setting Disk Quotas 1. Log on as Administrator, open My Computer 2. Right-click disk, select Properties 3. Click Quota tab, check Enable quota management 15
Setting Disk Quotas 1. Log on as Administrator, open My Computer 2. Right-click disk, select Properties 3. Click Quota tab, check Enable quota management 15
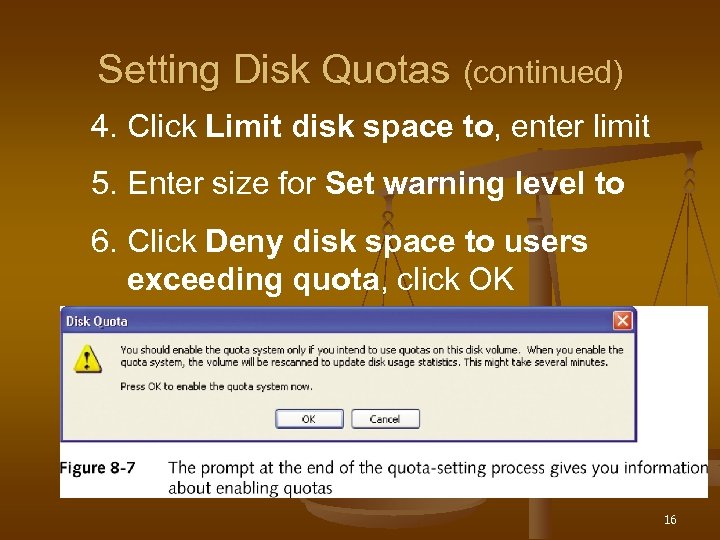 Setting Disk Quotas (continued) 4. Click Limit disk space to, enter limit 5. Enter size for Set warning level to 6. Click Deny disk space to users exceeding quota, click OK 16
Setting Disk Quotas (continued) 4. Click Limit disk space to, enter limit 5. Enter size for Set warning level to 6. Click Deny disk space to users exceeding quota, click OK 16
 EFS (Encrypted File System) n n n Encryption is the process of putting readable data into code that must be translated before it can be accessed Protects data even when someone not authorized to view files or folders has full access to computer’s data storage Applies only to Windows 2000/XP NTFS file system 17
EFS (Encrypted File System) n n n Encryption is the process of putting readable data into code that must be translated before it can be accessed Protects data even when someone not authorized to view files or folders has full access to computer’s data storage Applies only to Windows 2000/XP NTFS file system 17
 How to Use Encryption n n Can be implemented at either the folder or file level Folder level is encouraged and considered a “best practice” strategy 18
How to Use Encryption n n Can be implemented at either the folder or file level Folder level is encouraged and considered a “best practice” strategy 18
 Encrypting Folder Contents 1. 2. 3. 4. Locate the folder to be encrypted Right-click the folder, choose Properties On the General tab, click Advanced Check Encrypt contents to secure data and click OK 19
Encrypting Folder Contents 1. 2. 3. 4. Locate the folder to be encrypted Right-click the folder, choose Properties On the General tab, click Advanced Check Encrypt contents to secure data and click OK 19
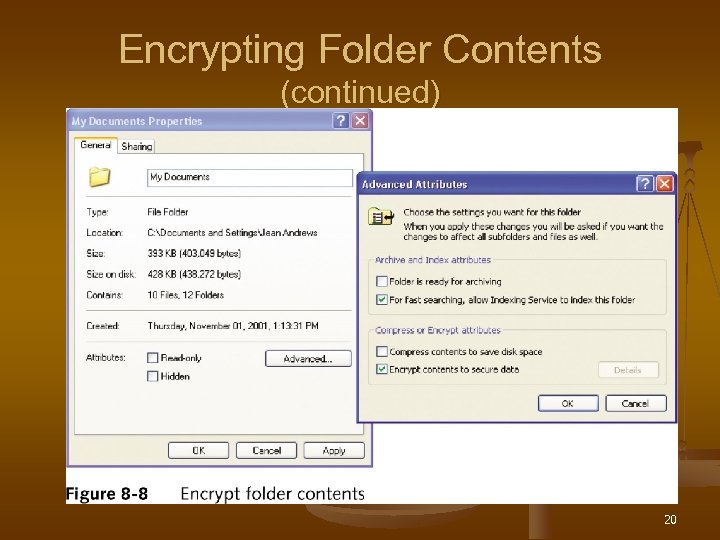 Encrypting Folder Contents (continued) 20
Encrypting Folder Contents (continued) 20
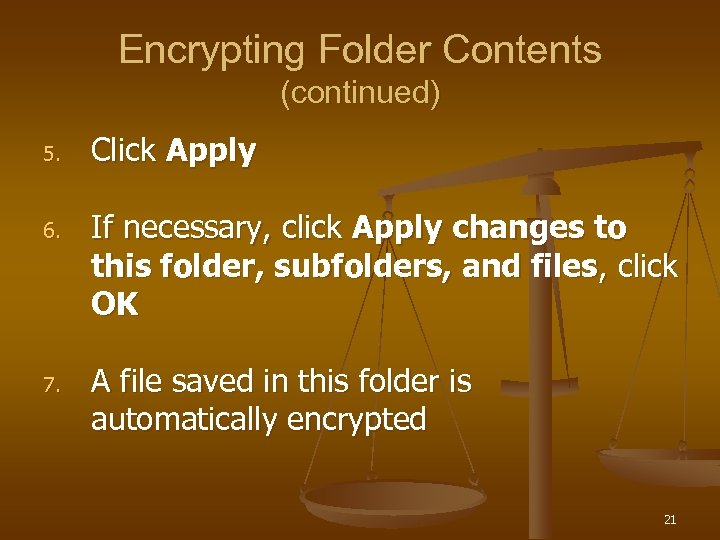 Encrypting Folder Contents (continued) 5. 6. 7. Click Apply If necessary, click Apply changes to this folder, subfolders, and files, click OK A file saved in this folder is automatically encrypted 21
Encrypting Folder Contents (continued) 5. 6. 7. Click Apply If necessary, click Apply changes to this folder, subfolders, and files, click OK A file saved in this folder is automatically encrypted 21
 The Cipher Command n n For use when encrypting a large number of files or folders from a command prompt or using a batch file CIPHER [/E, /D] [/S: dir] [pathname[…]] n /E encrypts specified files or folders n /D decrypts specified files or folders n n /S: dir applies the action to the specified folder (directory) and all its subfolders Pathname is the name of the file/folder and its path that is to be encrypted/decrypted 22
The Cipher Command n n For use when encrypting a large number of files or folders from a command prompt or using a batch file CIPHER [/E, /D] [/S: dir] [pathname[…]] n /E encrypts specified files or folders n /D decrypts specified files or folders n n /S: dir applies the action to the specified folder (directory) and all its subfolders Pathname is the name of the file/folder and its path that is to be encrypted/decrypted 22
 The Windows NT/2000/XP Registry n n n Hierarchical database containing information about all hardware, software, device drivers, network protocols, and user configuration needed by the OS and applications Organization Viewing contents Back up and recovery Making changes 23
The Windows NT/2000/XP Registry n n n Hierarchical database containing information about all hardware, software, device drivers, network protocols, and user configuration needed by the OS and applications Organization Viewing contents Back up and recovery Making changes 23
 How the Registry Is Organized n Logical organization n n Upside-down tree structure of keys, subkeys, and values Physical organization n Stored in five files called hives 24
How the Registry Is Organized n Logical organization n n Upside-down tree structure of keys, subkeys, and values Physical organization n Stored in five files called hives 24
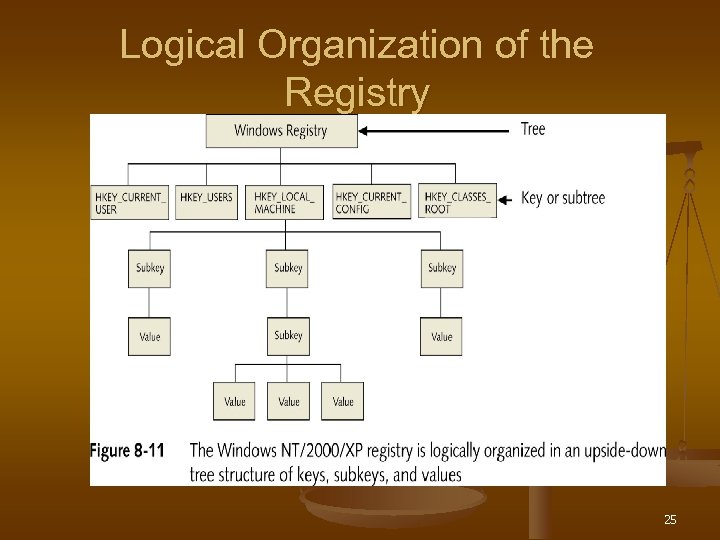 Logical Organization of the Registry 25
Logical Organization of the Registry 25
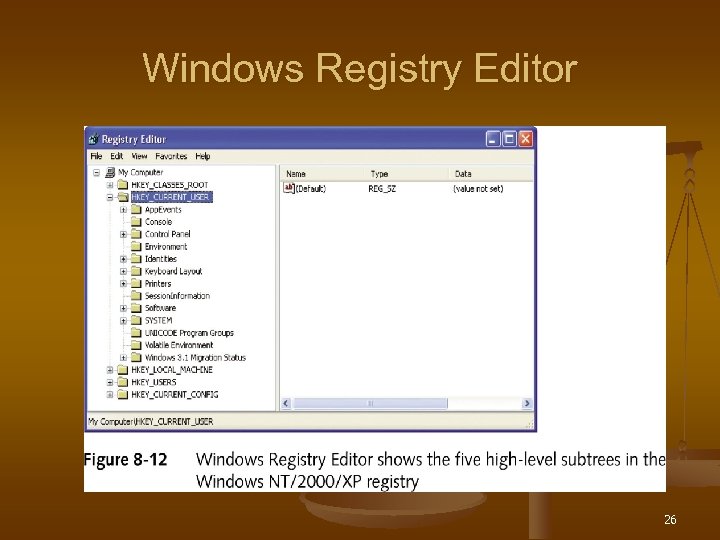 Windows Registry Editor 26
Windows Registry Editor 26
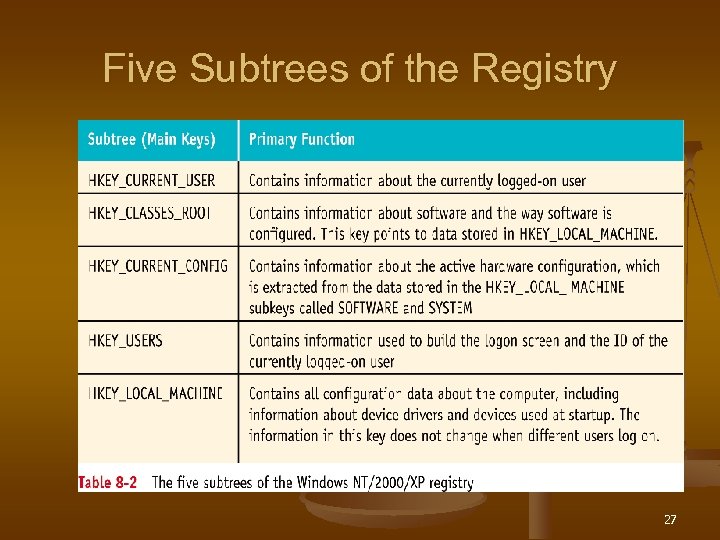 Five Subtrees of the Registry 27
Five Subtrees of the Registry 27
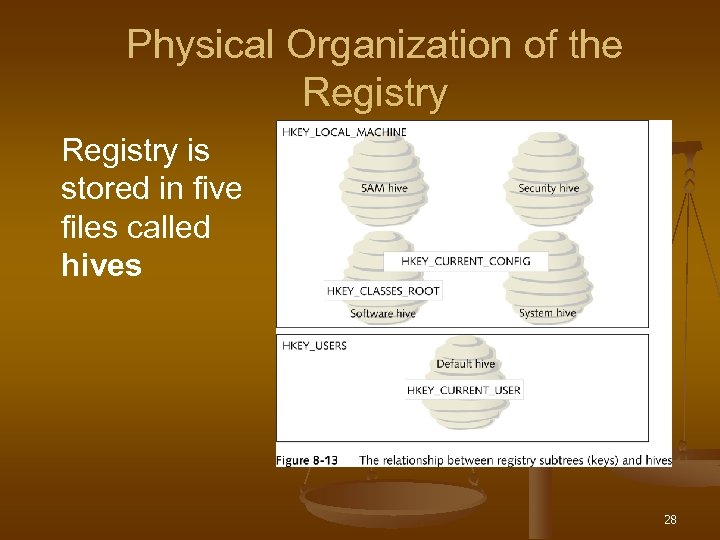 Physical Organization of the Registry is stored in five files called hives 28
Physical Organization of the Registry is stored in five files called hives 28
 Editing the Registry n n n Modified automatically when you make a change (e. g. , in Control Panel or Device Manager) Rare occasions when you might need to edit manually Changes take effect immediately and are permanent 29
Editing the Registry n n n Modified automatically when you make a change (e. g. , in Control Panel or Device Manager) Rare occasions when you might need to edit manually Changes take effect immediately and are permanent 29
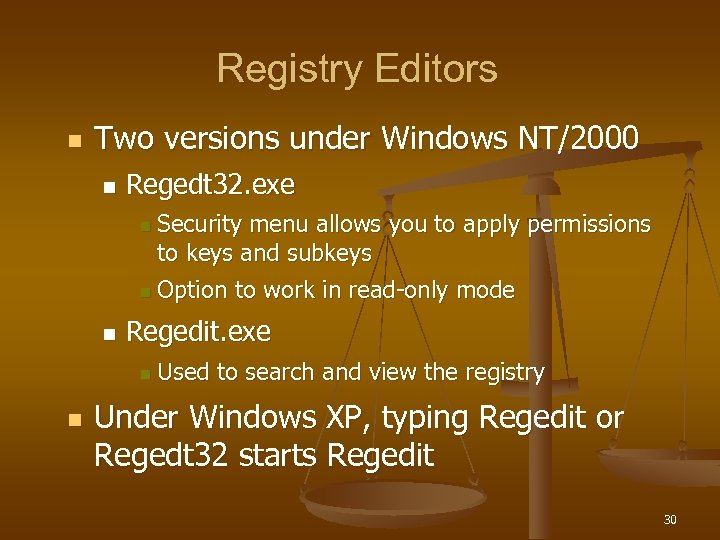 Registry Editors n Two versions under Windows NT/2000 n Regedt 32. exe n n n Option to work in read-only mode Regedit. exe n n Security menu allows you to apply permissions to keys and subkeys Used to search and view the registry Under Windows XP, typing Regedit or Regedt 32 starts Regedit 30
Registry Editors n Two versions under Windows NT/2000 n Regedt 32. exe n n n Option to work in read-only mode Regedit. exe n n Security menu allows you to apply permissions to keys and subkeys Used to search and view the registry Under Windows XP, typing Regedit or Regedt 32 starts Regedit 30
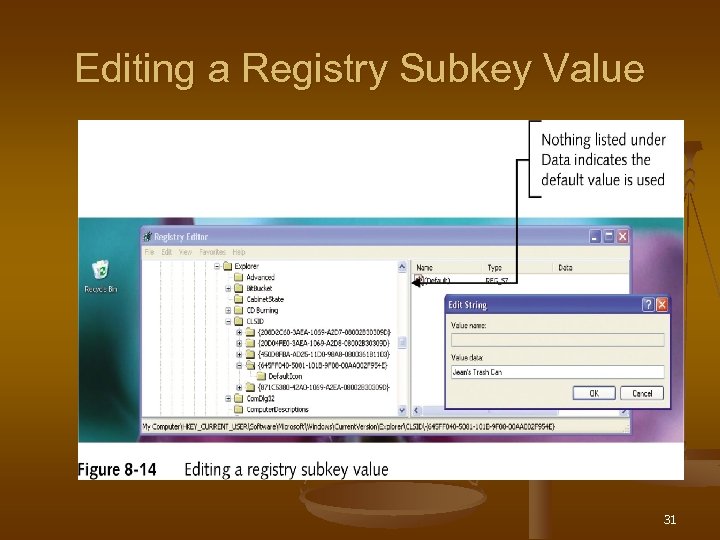 Editing a Registry Subkey Value 31
Editing a Registry Subkey Value 31
 Other Maintenance and Troubleshooting Tools n n n Executed from a command line (. exe file extension) Microsoft Management Console snap-ins (. msc file extension) Built into Windows XP (e. g. , Safe Mode) 32
Other Maintenance and Troubleshooting Tools n n n Executed from a command line (. exe file extension) Microsoft Management Console snap-ins (. msc file extension) Built into Windows XP (e. g. , Safe Mode) 32
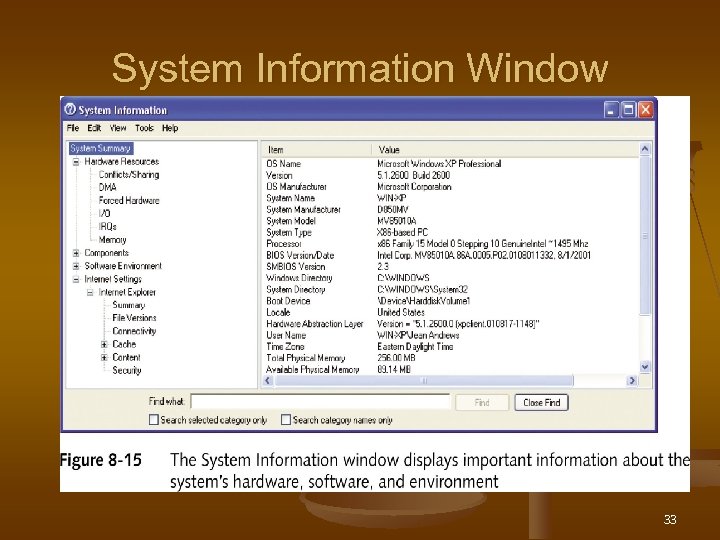 System Information Window 33
System Information Window 33
 Windows Update n n n An automated way to update the OS, applications, and device drivers If no user interaction required, any user can perform an update If decisions must be made, only a user with administrative rights can update 34
Windows Update n n n An automated way to update the OS, applications, and device drivers If no user interaction required, any user can perform an update If decisions must be made, only a user with administrative rights can update 34
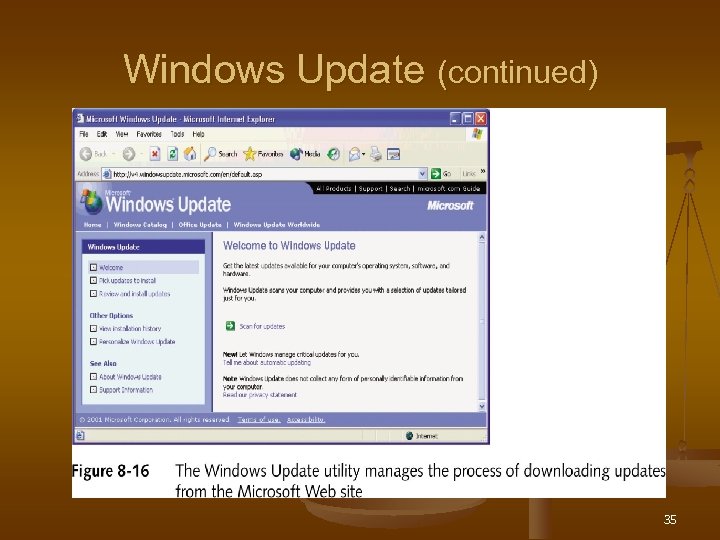 Windows Update (continued) 35
Windows Update (continued) 35
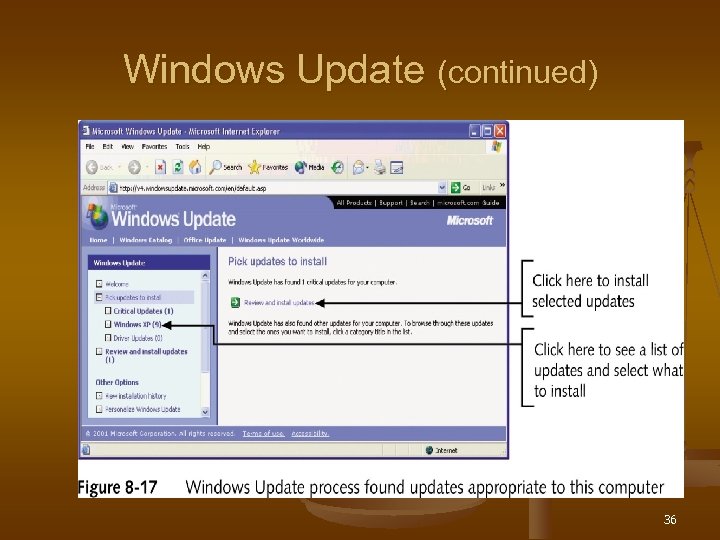 Windows Update (continued) 36
Windows Update (continued) 36
 Troubleshooting the Boot Process n Last Known Good Configuration (and sometimes Driver Rollback) n Safe Mode from Advanced Options menu n System Restore n Windows XP/2000 Boot disk n Recovery Console n Automated System Recovery n Reinstall Windows XP using Windows CD 37
Troubleshooting the Boot Process n Last Known Good Configuration (and sometimes Driver Rollback) n Safe Mode from Advanced Options menu n System Restore n Windows XP/2000 Boot disk n Recovery Console n Automated System Recovery n Reinstall Windows XP using Windows CD 37
 Advanced Options: Safe Mode and Last Known Good Configuration 38
Advanced Options: Safe Mode and Last Known Good Configuration 38
 System Restore n n Similar to Scan. Reg, but cannot be executed from command prompt Process does not affect user data on hard drive but can affect: Installed software and hardware n User settings n OS configuration settings n n Restores system state using a restore point 39
System Restore n n Similar to Scan. Reg, but cannot be executed from command prompt Process does not affect user data on hard drive but can affect: Installed software and hardware n User settings n OS configuration settings n n Restores system state using a restore point 39
 System Restore (continued) To revert the system to a restore point 1. 2. 3. 4. Click Start, All Programs, Accessories, System Tools, and System Restore Click Restore my computer to an earlier time, then click Next Select a restore point, click Next twice Windows XP reboots and restores the system state 40
System Restore (continued) To revert the system to a restore point 1. 2. 3. 4. Click Start, All Programs, Accessories, System Tools, and System Restore Click Restore my computer to an earlier time, then click Next Select a restore point, click Next twice Windows XP reboots and restores the system state 40
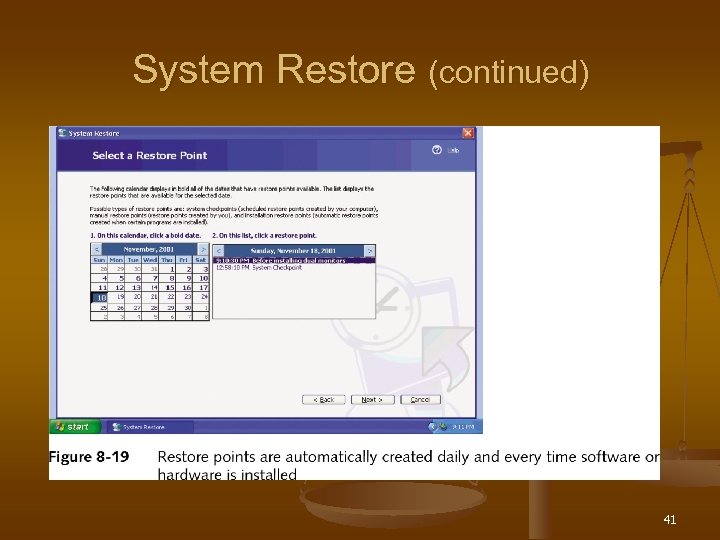 System Restore (continued) 41
System Restore (continued) 41
 MS-DOS Startup Disk n n n Create using Windows Explorer Can access the drive and recover data files (if the hard drive is not using NTFS) Cannot launch Windows XP or be used to recover from a failed installation 42
MS-DOS Startup Disk n n n Create using Windows Explorer Can access the drive and recover data files (if the hard drive is not using NTFS) Cannot launch Windows XP or be used to recover from a failed installation 42
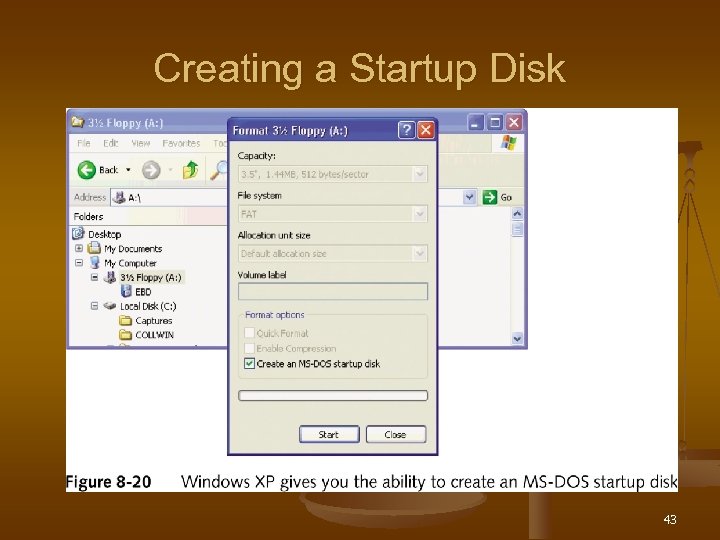 Creating a Startup Disk 43
Creating a Startup Disk 43
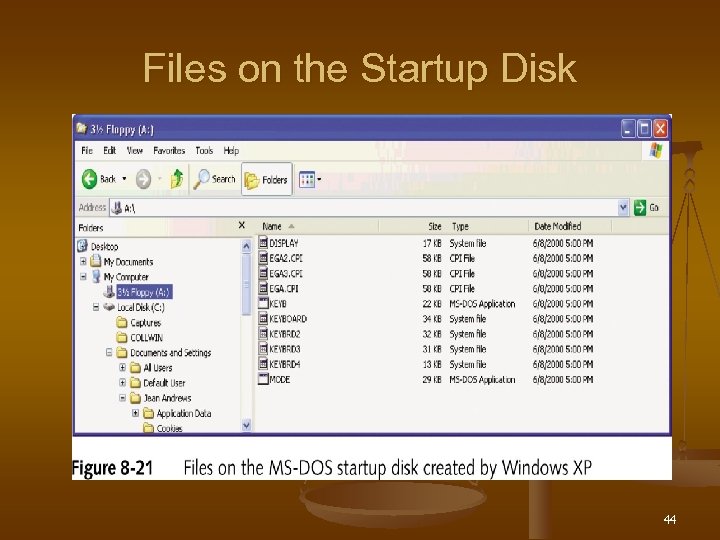 Files on the Startup Disk 44
Files on the Startup Disk 44
 Windows XP Boot Disk Can bypass missing or damaged: n Boot sector n Ntldr n Master boot record n Ntdetect. com n Partition table n Boot. ini n Ntbootdd. sys 45
Windows XP Boot Disk Can bypass missing or damaged: n Boot sector n Ntldr n Master boot record n Ntdetect. com n Partition table n Boot. ini n Ntbootdd. sys 45
 Windows XP Boot Disk (continued) n Format a floppy using Windows 2000/XP and copy the following files to it n n Ntldr and Ntdetect. com If the system boots from a SCSI hard drive, copy the SCSI device driver to the floppy and rename it Ntbootdd. sys Boot. ini Write-protect the floppy disk 46
Windows XP Boot Disk (continued) n Format a floppy using Windows 2000/XP and copy the following files to it n n Ntldr and Ntdetect. com If the system boots from a SCSI hard drive, copy the SCSI device driver to the floppy and rename it Ntbootdd. sys Boot. ini Write-protect the floppy disk 46
 Automated System Recovery n n n Restores system partition to its state when the backup was made Changes made since last backup are lost Periodically make fresh copies of ASR disk set 47
Automated System Recovery n n n Restores system partition to its state when the backup was made Changes made since last backup are lost Periodically make fresh copies of ASR disk set 47
 Using ASR to Restore System 1. 2. 3. 4. 5. Boot the PC from the Windows XP CD Press any key to boot from CD If necessary, Press F 6 to load RAID or SCSI drivers Press F 2 to run Automated System Recovery Process Insert ASR floppy disk 48
Using ASR to Restore System 1. 2. 3. 4. 5. Boot the PC from the Windows XP CD Press any key to boot from CD If necessary, Press F 6 to load RAID or SCSI drivers Press F 2 to run Automated System Recovery Process Insert ASR floppy disk 48
 Using ASR to Restore System (continued) 49
Using ASR to Restore System (continued) 49
 Using ASR to Restore System (continued) n Loads files it needs to run n Repartitions and reformats the drive n Installs Windows from Windows XP CD n Launches the Automated System Recovery Wizard to restore the system state, applications, and data 50
Using ASR to Restore System (continued) n Loads files it needs to run n Repartitions and reformats the drive n Installs Windows from Windows XP CD n Launches the Automated System Recovery Wizard to restore the system state, applications, and data 50
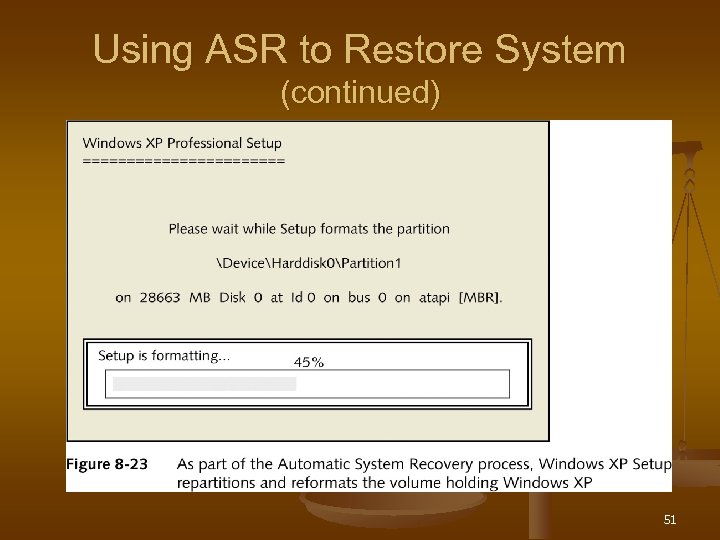 Using ASR to Restore System (continued) 51
Using ASR to Restore System (continued) 51


